Circuit structure for preventing power attacks on grouping algorithm
A symmetric algorithm and attacker's technology, applied in the field of attack defense technology, can solve problems such as area and power consumption increase, computing performance and area impact, and achieve the effect of small performance loss, improved efficiency, and flexible application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
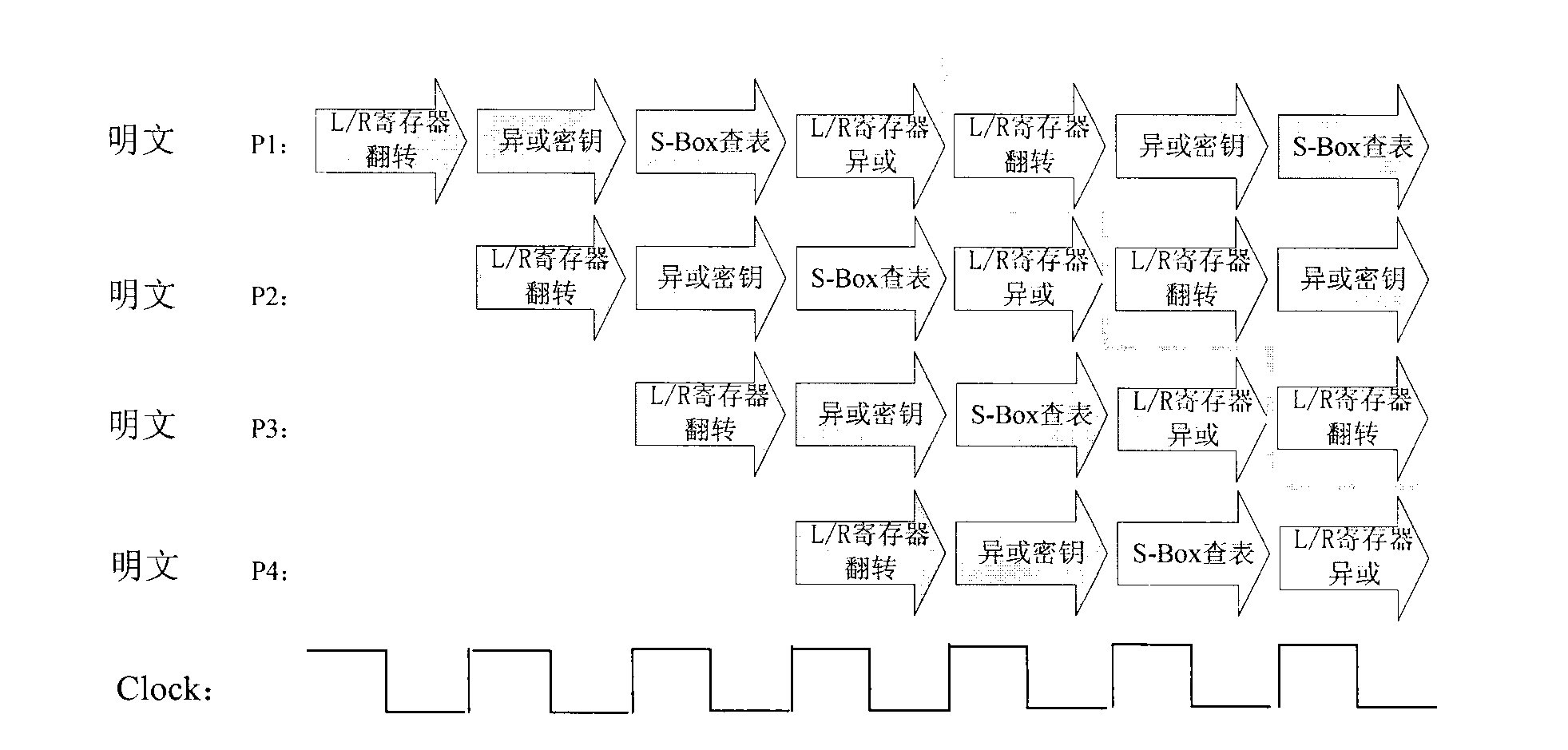
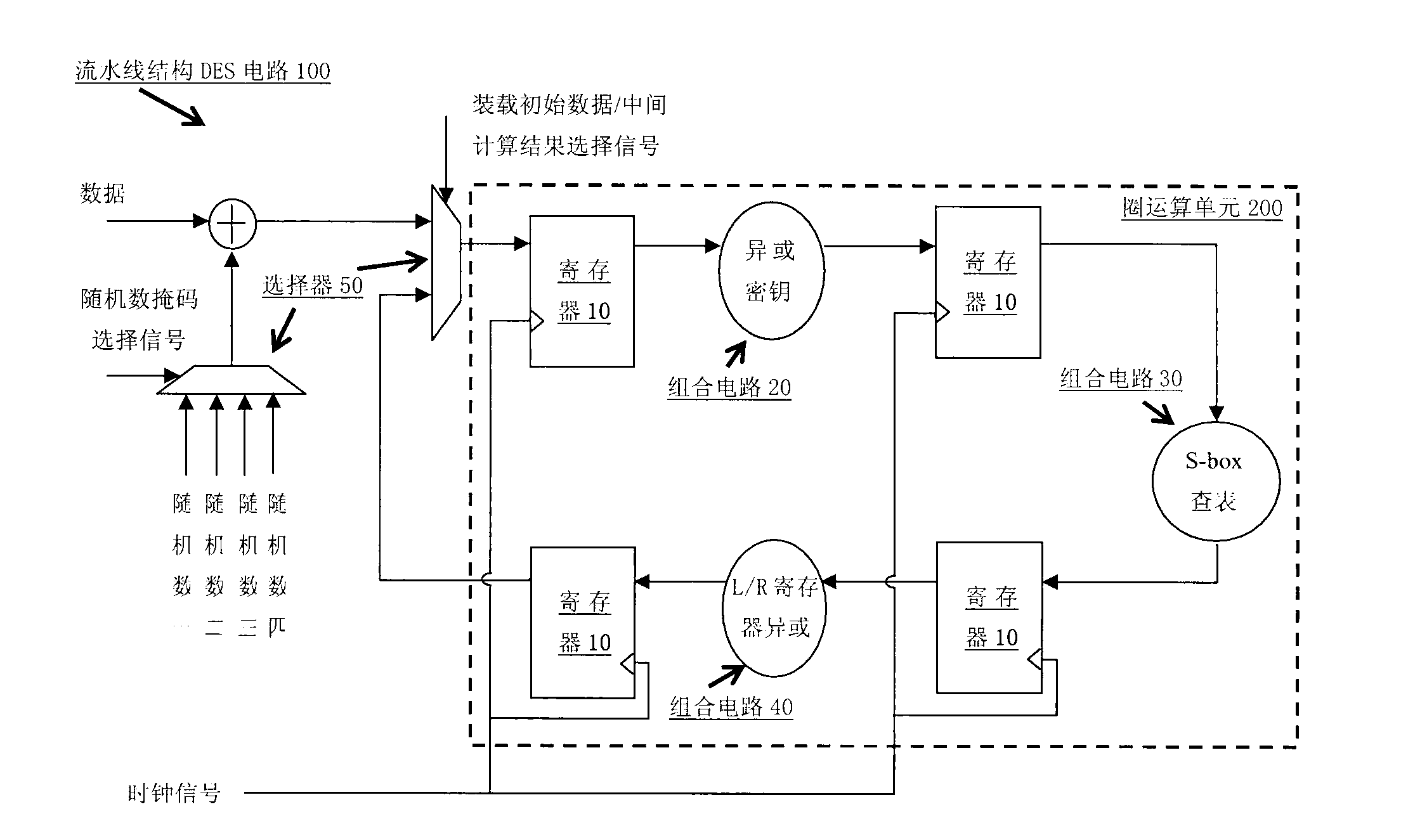
[0016] The specific implementation of the present invention will be described below by taking DES as an example. The present invention divides standard DES operation per circle into four steps, which are respectively L / R register flipping (operation one), XOR key (operation two), S-box look-up table (operation three) and L / R register exclusive Or (operation 4) (but not limited to four steps and not limited to the specific operation of each divided step), registers are inserted between each step to temporarily store the processing results of each stage of the pipeline. The hardware required for the circle operation is multiplexed, so the circuit is a four-stage pipeline structure (depending on the number of steps divided by each circle).
[0017] The power consumption of the cryptographic algorithm circuit usually includes the following parts:
[0018] P total =P op +P data +P el.noise +P const
[0019] where P total Indicates the total power consumption of the circuit,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com