Software mask defense scheme capable of preventing attack on advanced encryption standard (AES) algorithm based on power analysis
A technology of power consumption analysis and masking, which is applied in the field of information security, can solve the problem that attackers cannot obtain the AES key and reduce the cost of protection, so as to resist high-order differential power consumption attacks, reduce efficiency loss, and prevent high-order Effects of Differential Attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
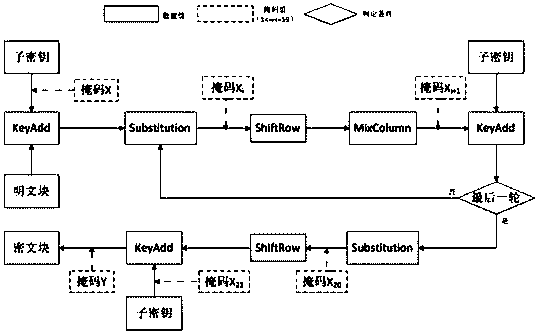
[0021] In the following, the specific implementation of the present invention will be described by taking the software implementation of the AES algorithm and the mask setting performed in each operation as examples. It should be understood that this embodiment is only used to illustrate the present invention and is not intended to limit the scope of the present invention, and modifications to various equivalent forms of the present invention by those skilled in the art all fall within the scope defined by the appended claims of the present application.
[0022] Because the encryption system in the smart card is implemented by software, and any intermediate value in the software-implemented encryption system has a step of storing registers in the calculation process, so all calculation intermediate values are potential attack points. Therefore, unlike hardware mask protection schemes, in order to resist first-order DPA and higher-order DPA, any meta-operation in the ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com