Method for enabling elliptic curve cryptography to defend differential power attack
A differential power attack, elliptic curve cryptography technology, applied in the direction of the public key of secure communication, can solve the problems of meaningless mapping, multi-time, cannot be taken as 1, etc., to achieve defense against differential power attack, low cost Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
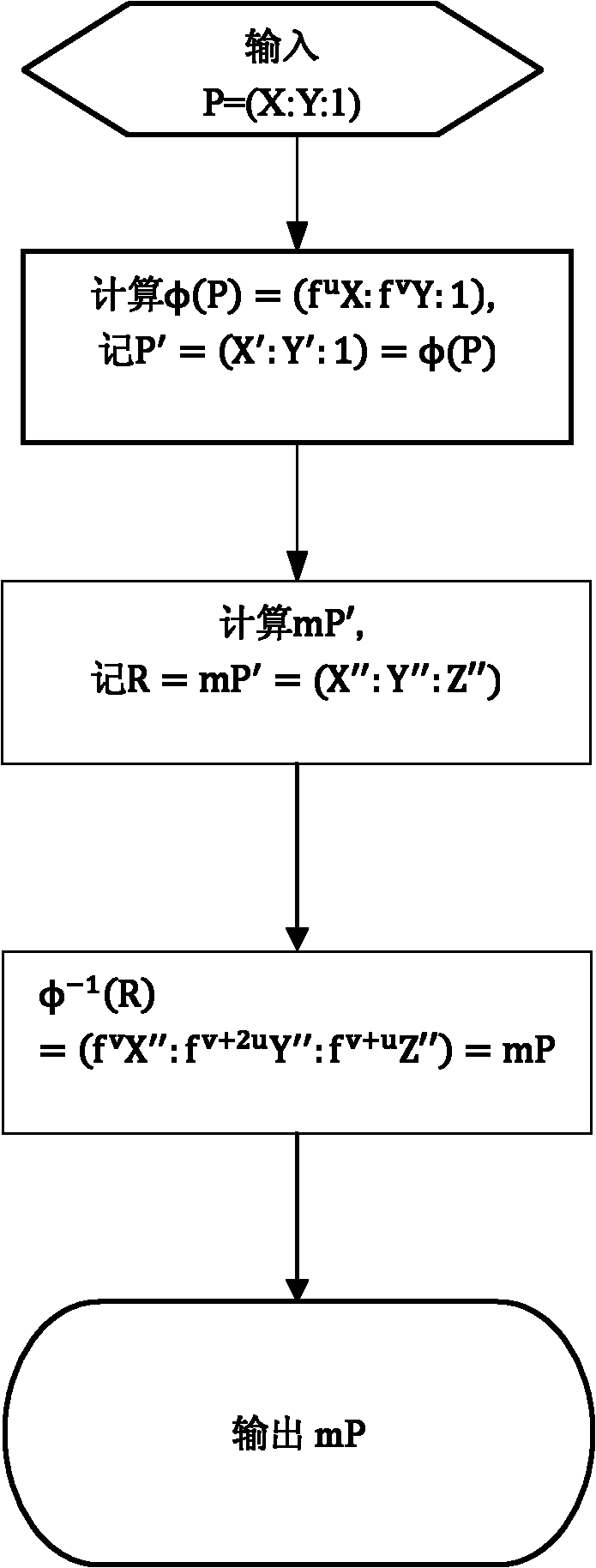
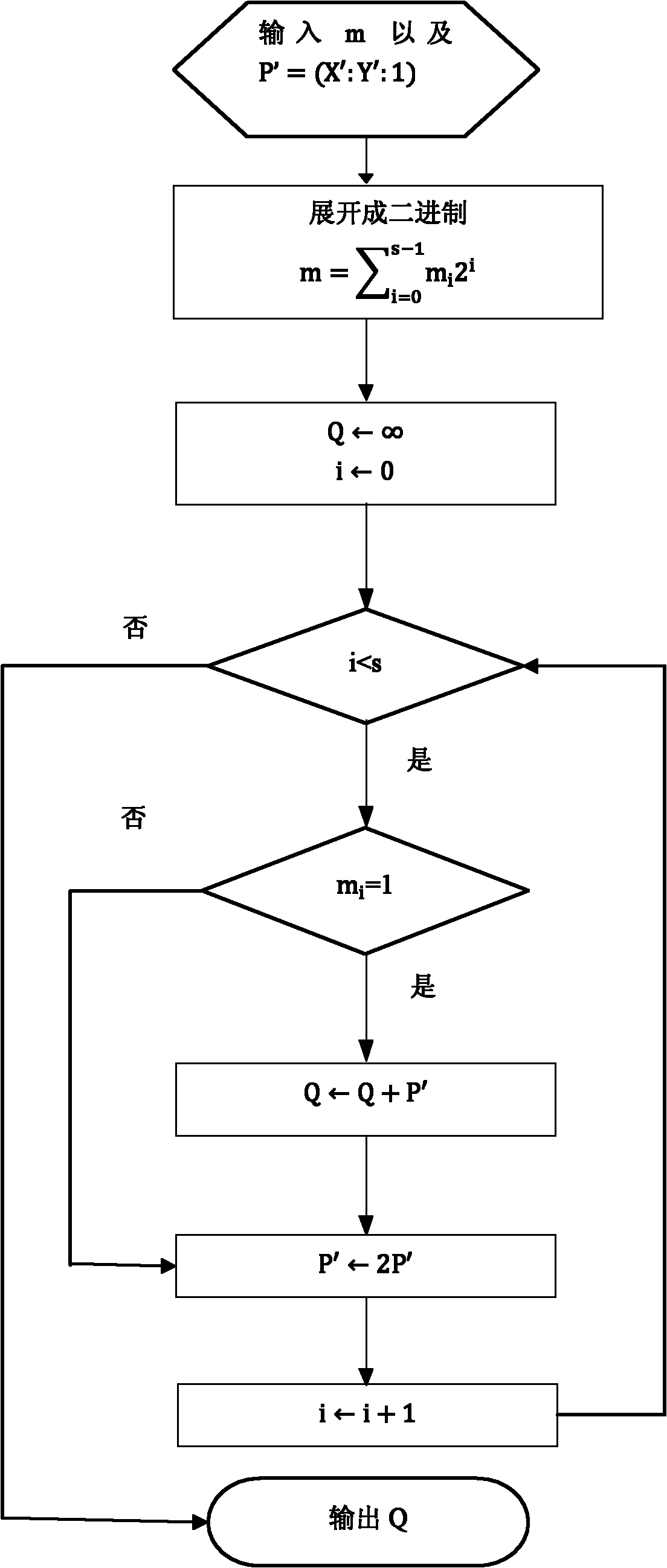
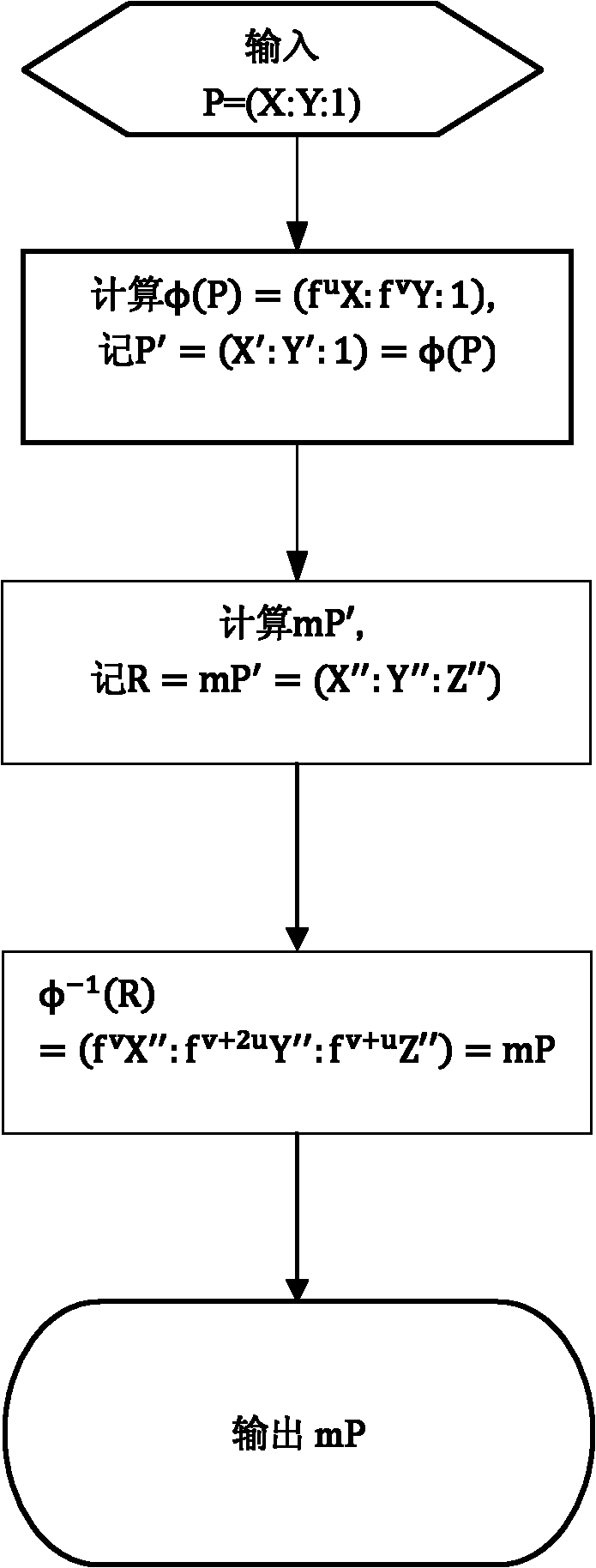
[0066] see figure 1 and combine figure 2 , the present invention provides a scalar multiplication calculation process using a method for defending against differential power consumption attacks to illustrate specific implementation details of the present invention.
[0067] The National Institute of Standards and Technology (NIST) recommends 15 sets of parameters for elliptic curve cryptography. One set of parameters is adopted in this embodiment, which is as follows:
[0068] E: y 2 +xy=x 3 +x 2 +b
[0069] p(t)=t 163 +t 7 +t 6 +t 3 +1
[0070] r=5846006549323611672814742442876390689256843201587
[0071] b=0x2 0a601907 b8c953ca 1481eb10 512f7874 4a3205fd
[0072] P x = 0x3 f0eba162 86a2d57e a0991168 d4994637 e8343e36
[0073] P y = 0x0 d51fbc6c 71a0094f a2cdd545 b11c5c0c 797324f1
[0074] The elliptic curve E( ) in n=163, now take the hexadecimal integer m, m=0xe4040cf925d6ff9b8be31e8263dcf0b831bd55ed, randomly select the hexadecimal integer f=0x8, and u=1,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com