AES algorithm oriented power attack resisting method based on register mask
A register and anti-power consumption technology, applied in encryption devices with shift registers/memory, countermeasures against encryption mechanisms, digital transmission systems, etc., can solve problems such as high hardware resource overhead, high performance overhead, and elimination of correlation , to achieve strong scalability and versatility, low hardware resource overhead, and resistance to power consumption attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The technical solution of the present invention will be further introduced below in combination with specific embodiments.
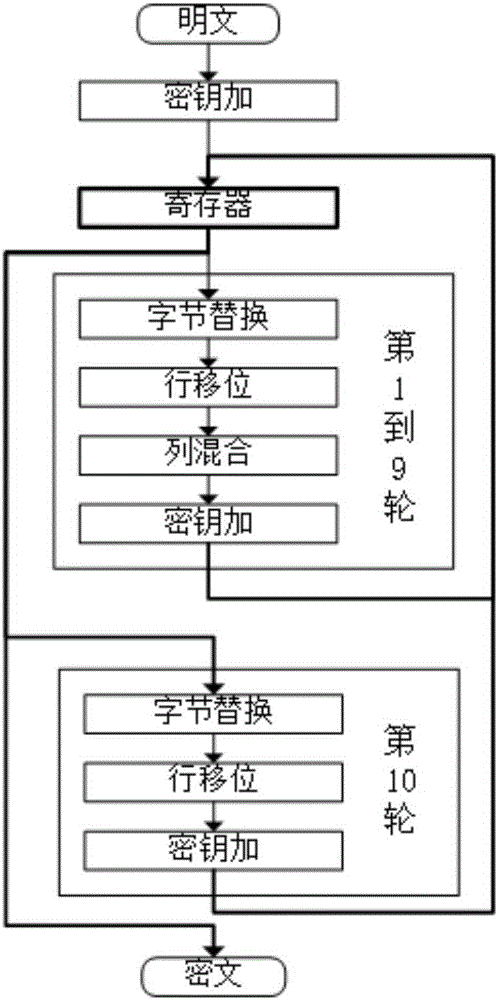
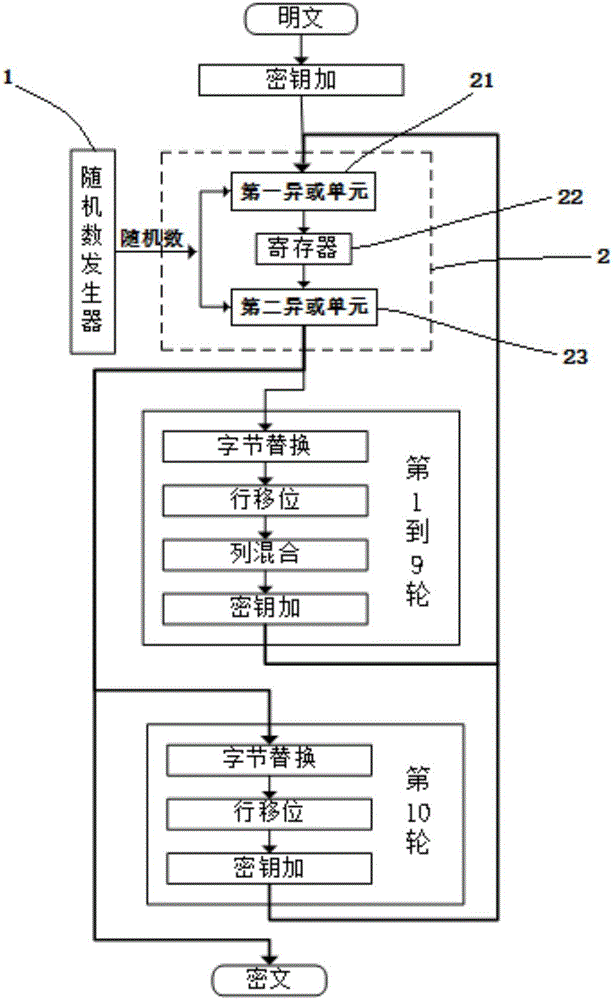
[0022] The traditional AES algorithm block encryption algorithm is composed of 3 parts, which are initial key addition, 9 rounds of the same round operation and the 10th round of final transformation. Each round requires a round key to complete the key addition operation, a total of eleven subkeys, denoted as K n (n=0,...,10). The subkey is obtained by expanding the initial key. The 9-cycle round operation in the middle of the AES algorithm includes four operations: byte replacement, row shift, column mixing, and key addition. The transformation at the end of the tenth round includes three operations: byte replacement, row shift and key addition. AES will generate an intermediate value data at the end of each round, which can be recorded as D n (n=0,…,10), stored in registers, where D 10 is the ciphertext output. Such as figure 1 As shown, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com