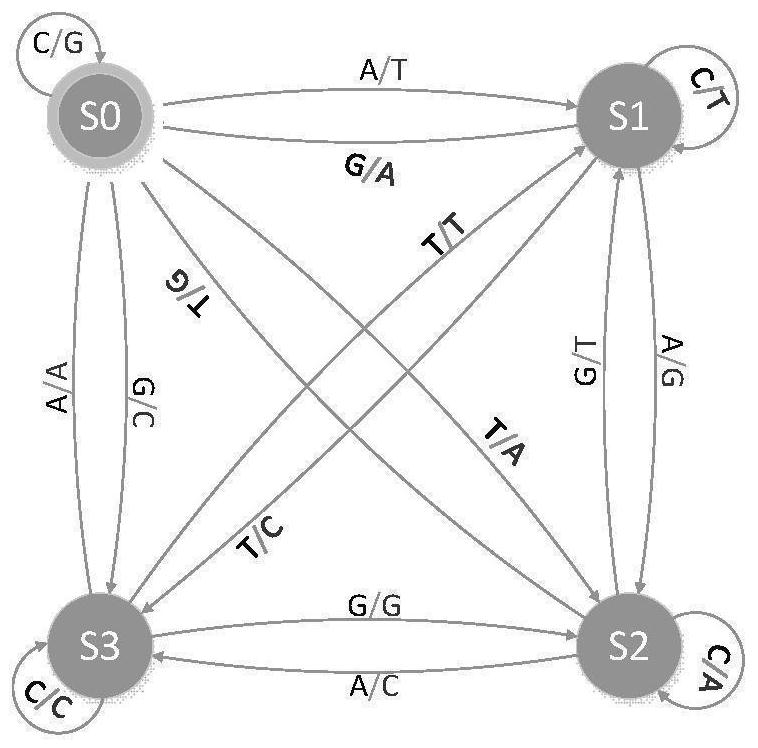
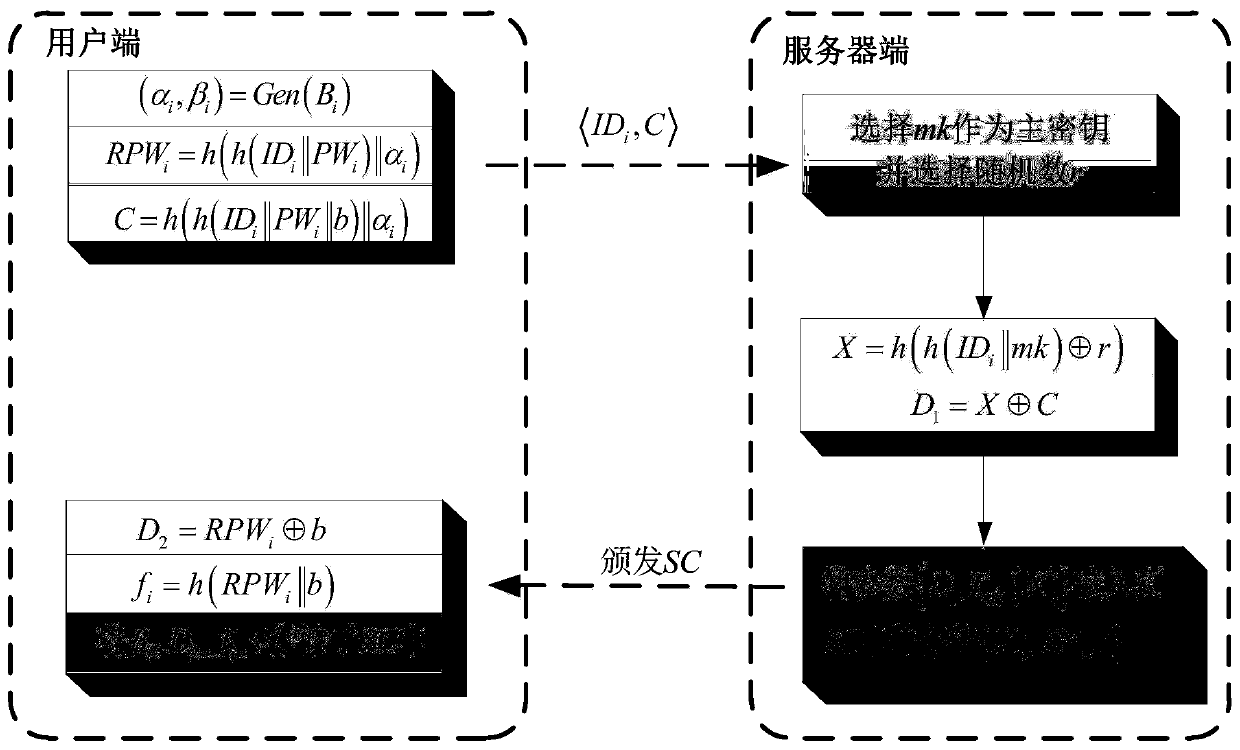
Patents
Literature
157results about How to "Effective attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
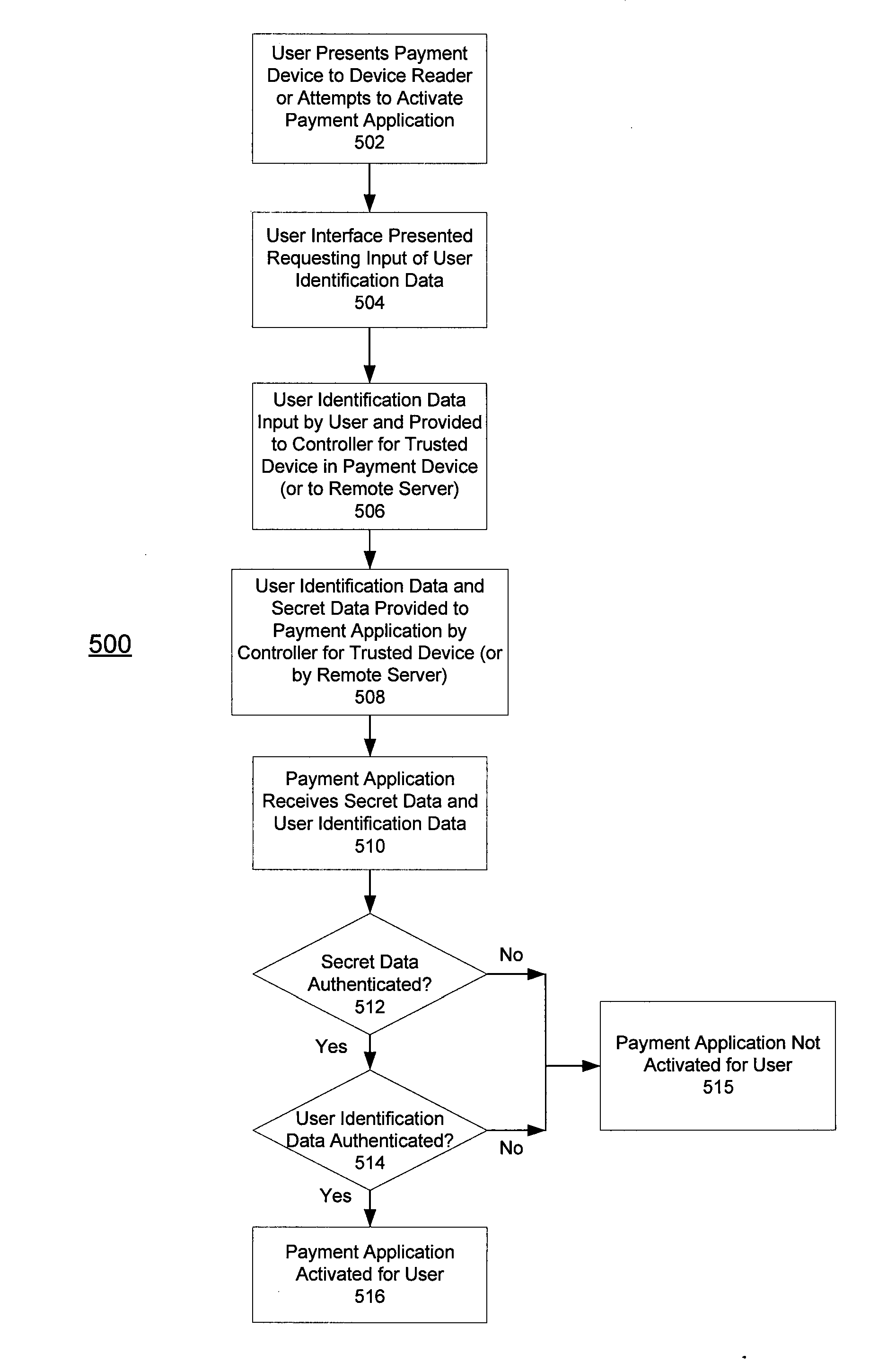
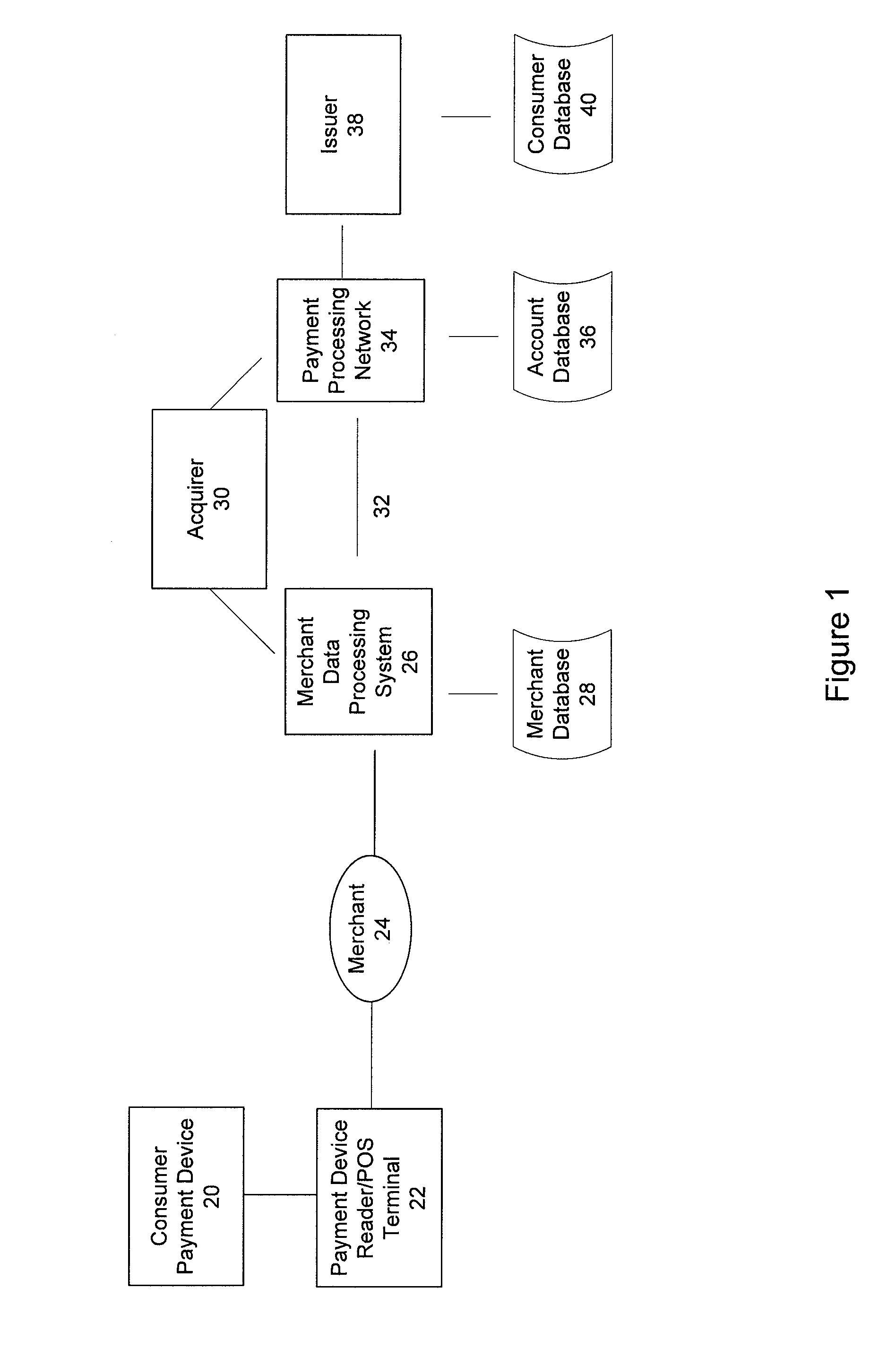
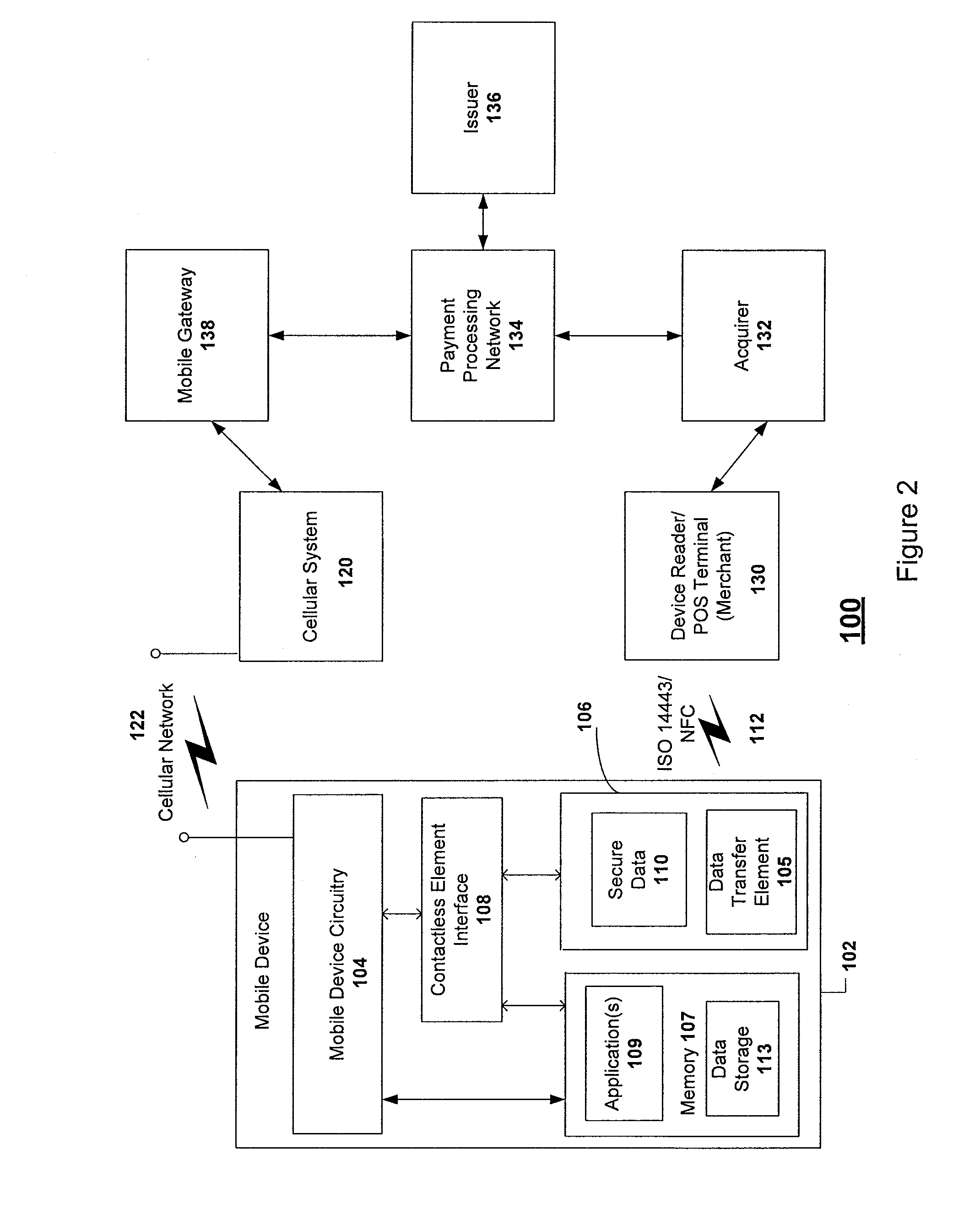
Apparatus and method for preventing unauthorized access to payment application installed in contactless payment device
InactiveUS20100217709A1Prevent unauthorized accessEffective attackFinancePoint-of-sale network systemsTransaction dataApplication software
A system, apparatus, and method for preventing the unauthorized access to a payment application installed on a mobile payment device, or to transaction data stored in the device. The mobile payment device may be a mobile phone that includes a contactless element (such as a contactless smart chip) and that is capable of communication and data transfer using a wireless communications network and a near field communications capability. Unauthorized access to the payment application is prevented by requiring that access control data be received from a trusted source, such as a controller or application in charge of managing inputs from a phone keypad, in order to activate the payment application or to access stored data.
Owner:VISA INT SERVICE ASSOC
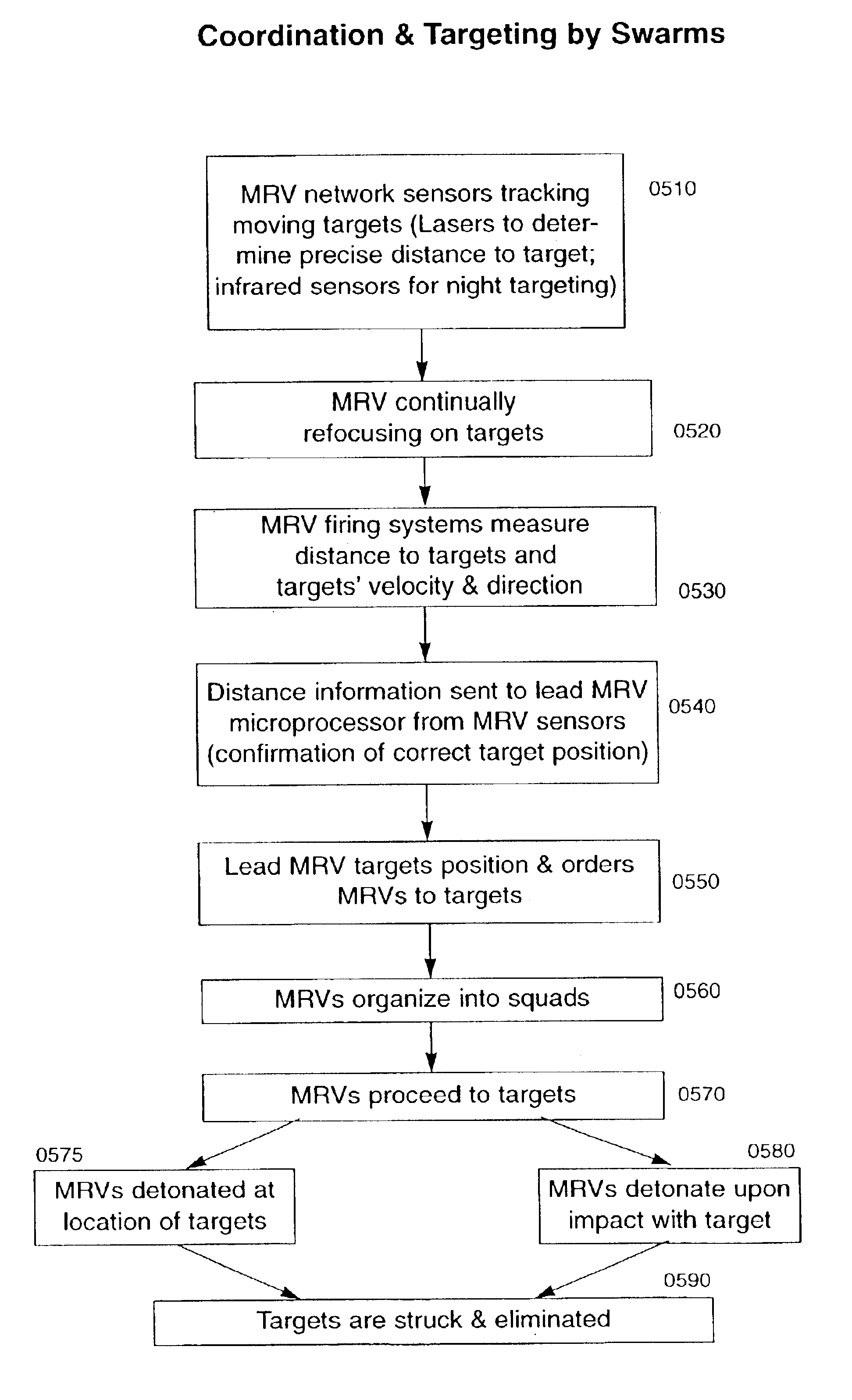
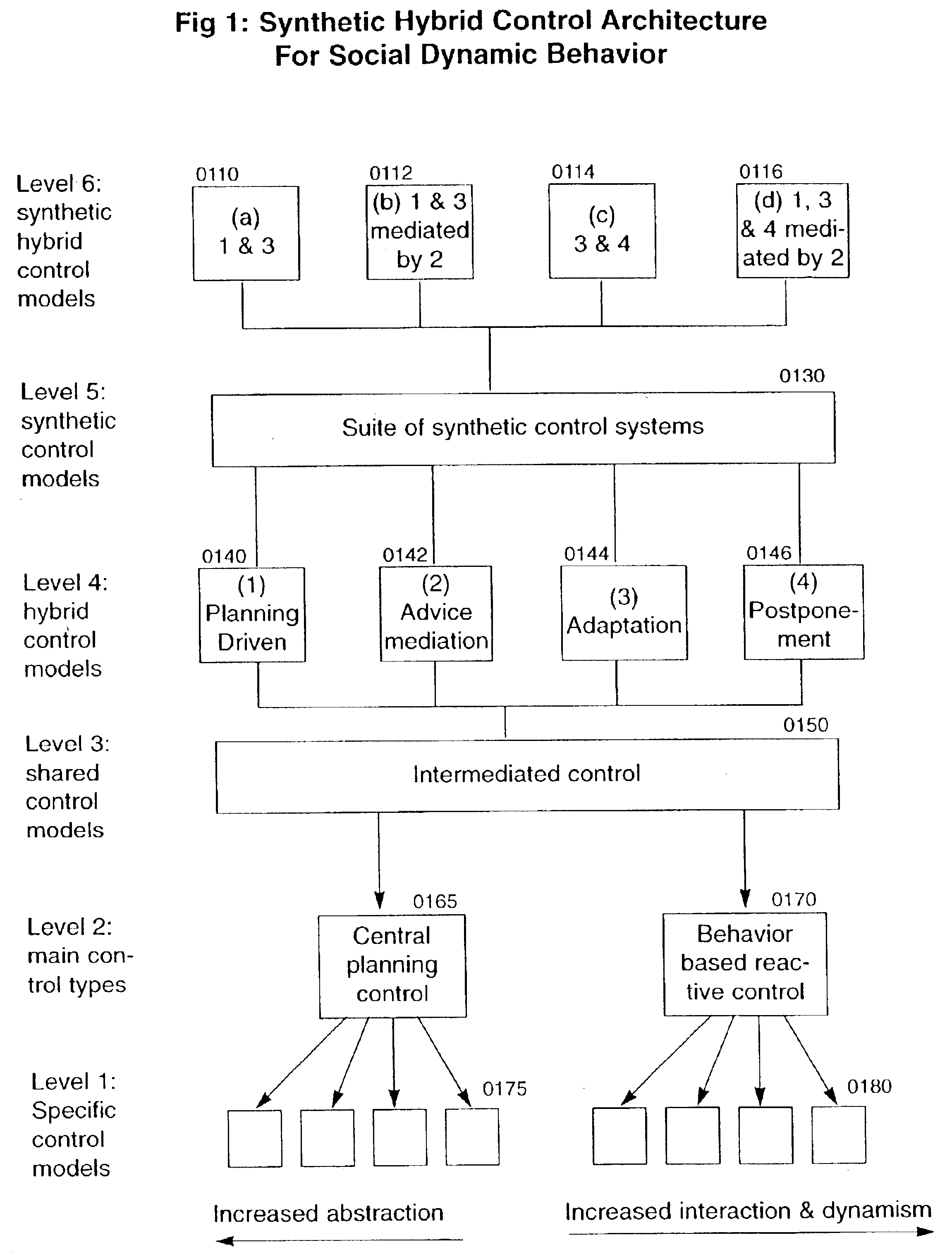
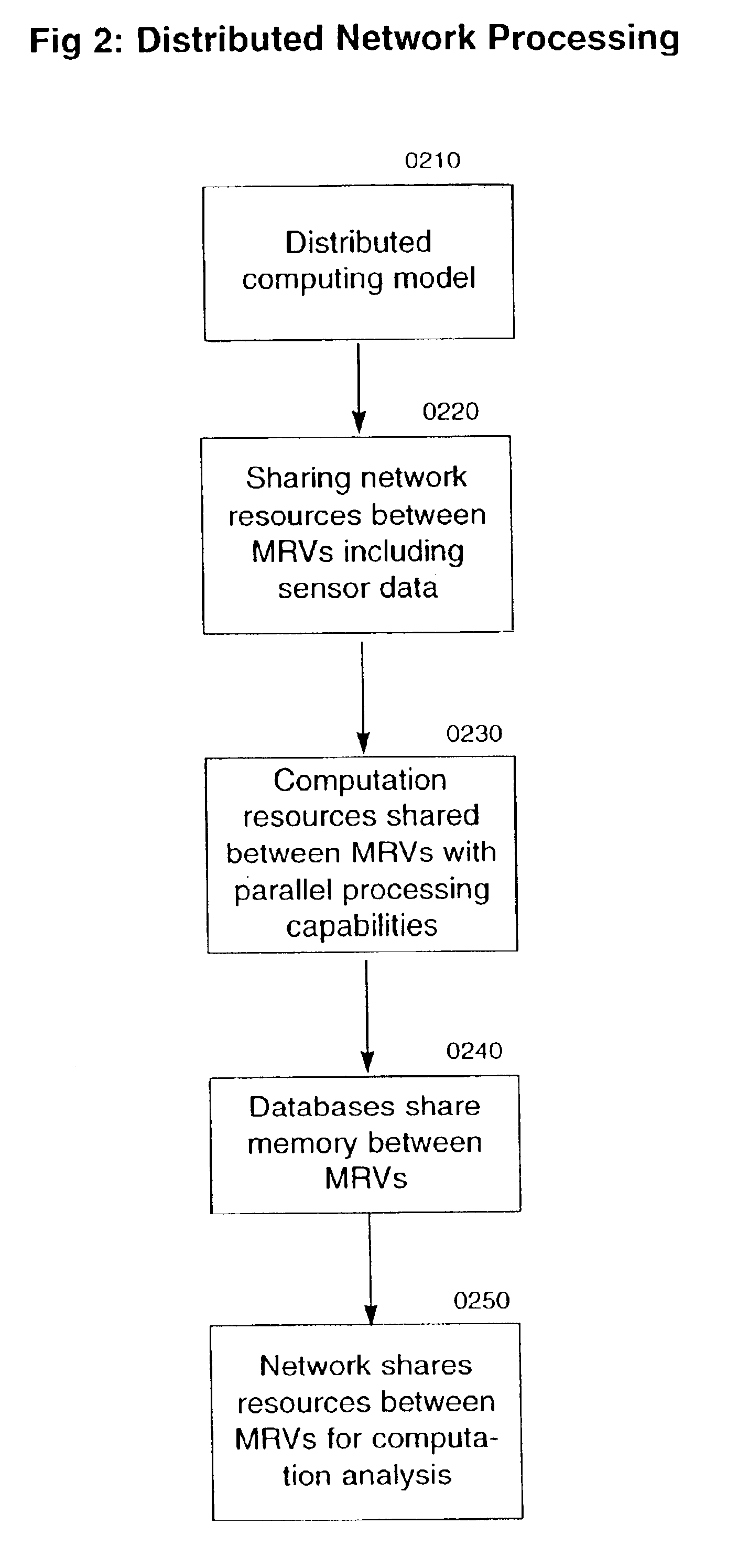
Methods and apparatus for decision making of system of mobile robotic vehicles
InactiveUS6842674B2Effective attackOvercome limitationsInstruments for road network navigationAutonomous decision making processMobile robotContinuation
In a swarm weapon system, decision-making processes are described for the organization of mobile robotic vehicles (MRVs). After MRV drone sensor data is provided to a lead MRV, an initial decision is made by the lead MRV as a result of the selection of a winning simulation that provides the best opportunity for success of a mission. Once this decision is made, actions are organized for the MRVs, which provide feedback for the continuation of the process until the mission is completed.
Owner:SOLOMON RES
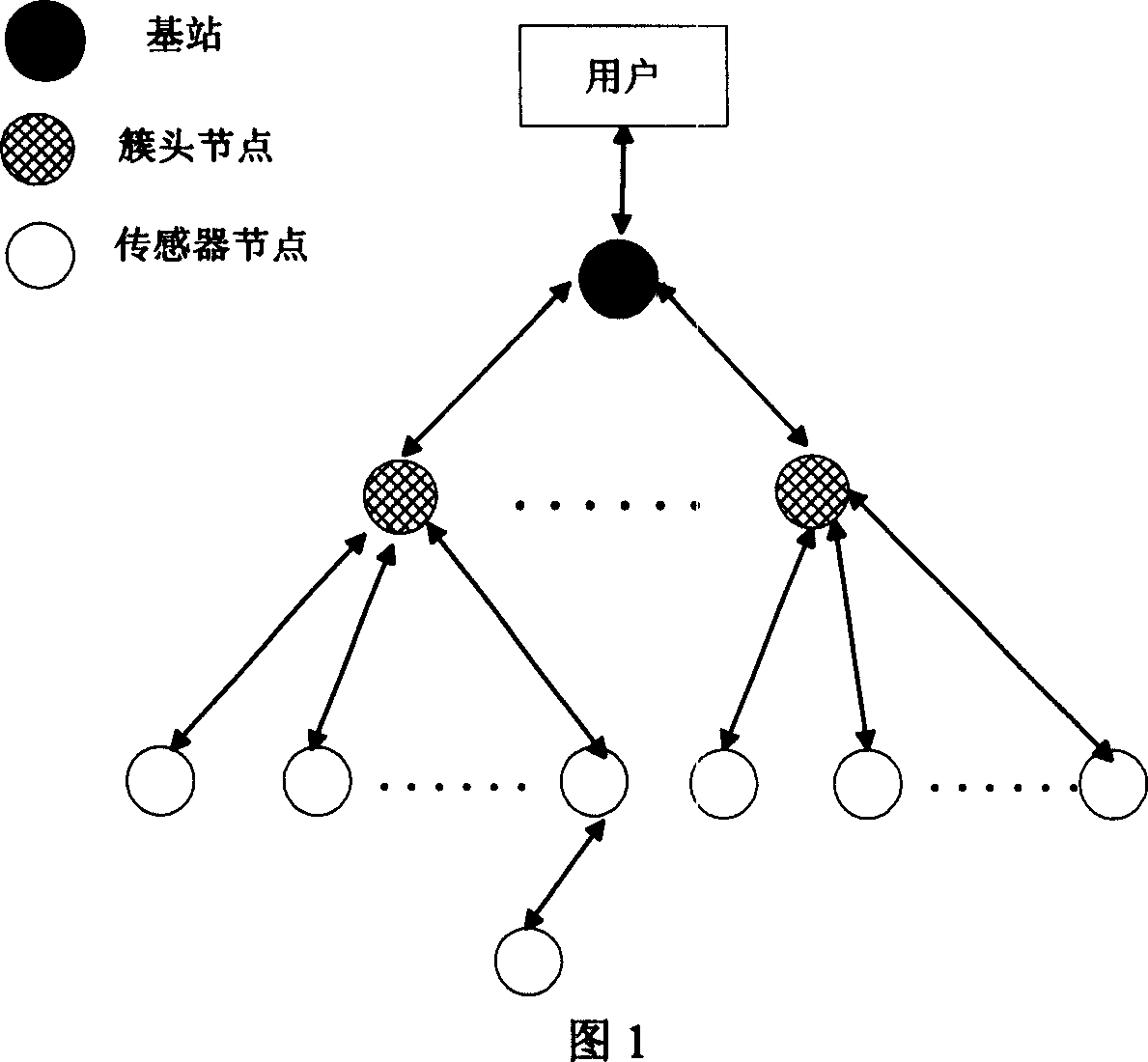
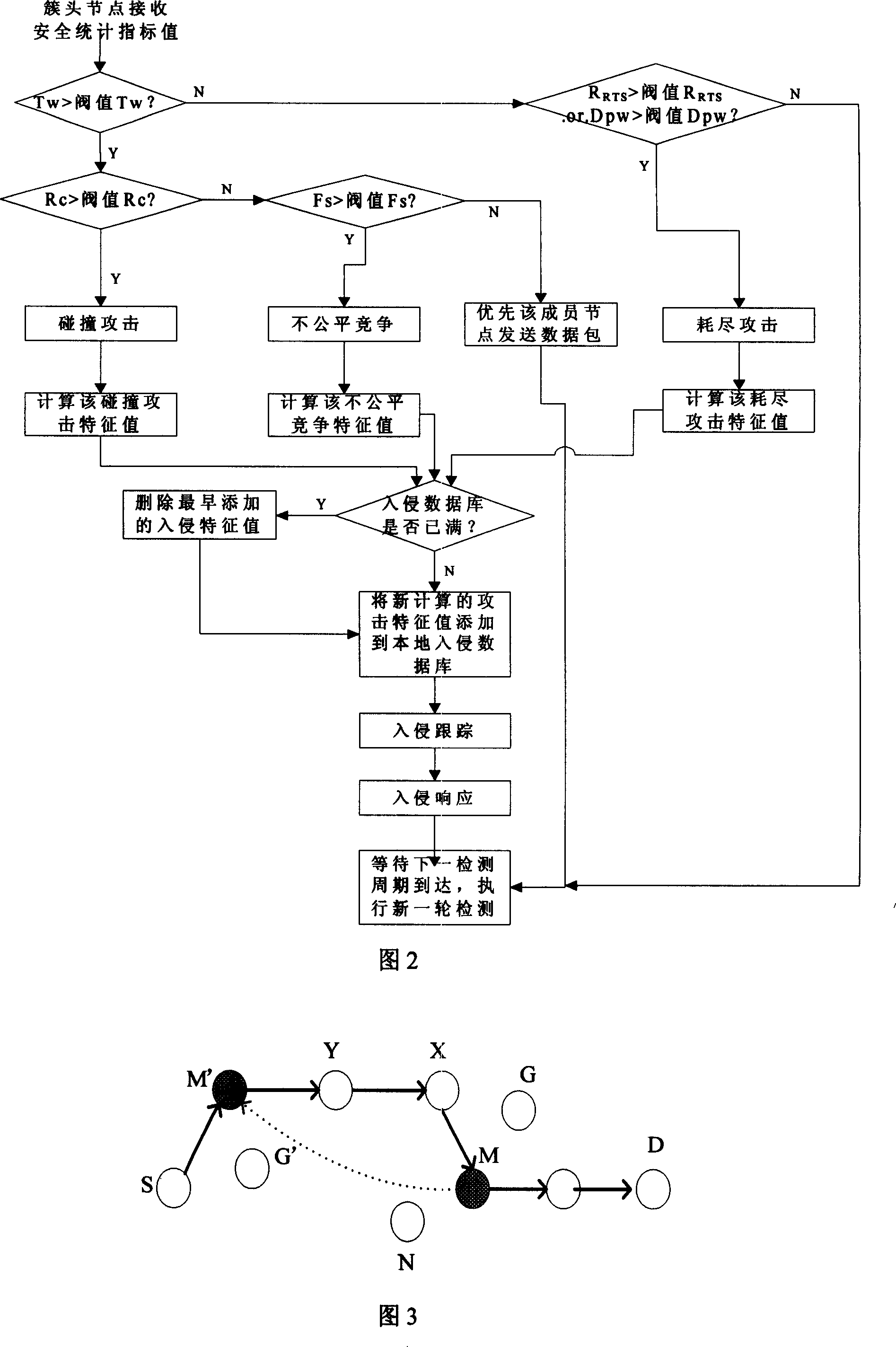
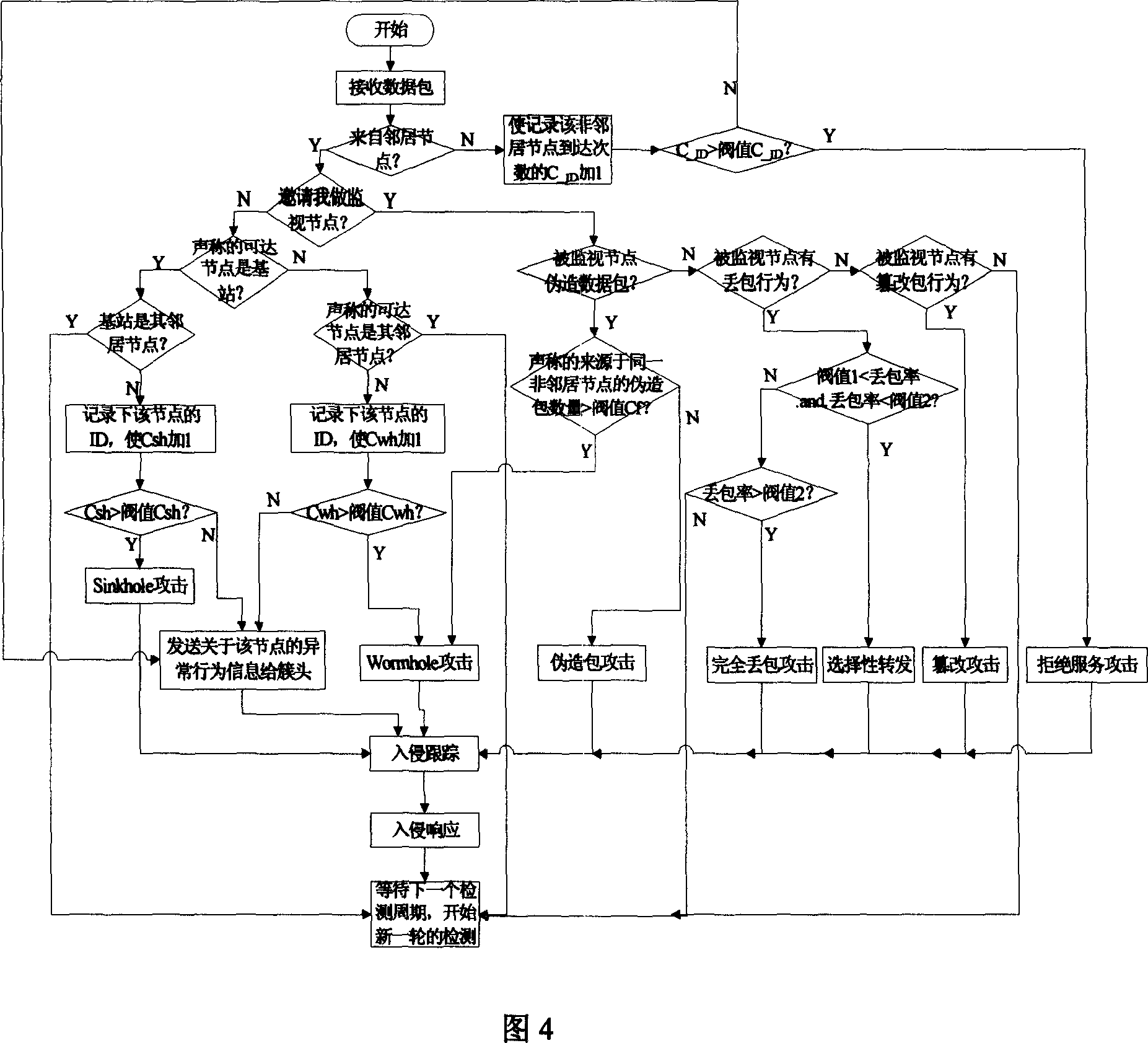
Mixed intrusion detection method of wireless sensor network
InactiveCN101013976AInspections are accelerated and simplifiedEffective detection and suppression of different attacksData switching by path configurationWireless sensor networkingSensor node
The invention relates to one wireless sensor network mixture intruding test method, which comprises the following steps: integrating multiple test method based on host machine, network, integration and abnormal mode, wherein, according to wireless sensor network property and outer and inner attack and distributing the test task onto sensor points, cluster point and base station point combined with host machine and network.
Owner:NANJING UNIV OF POSTS & TELECOMM
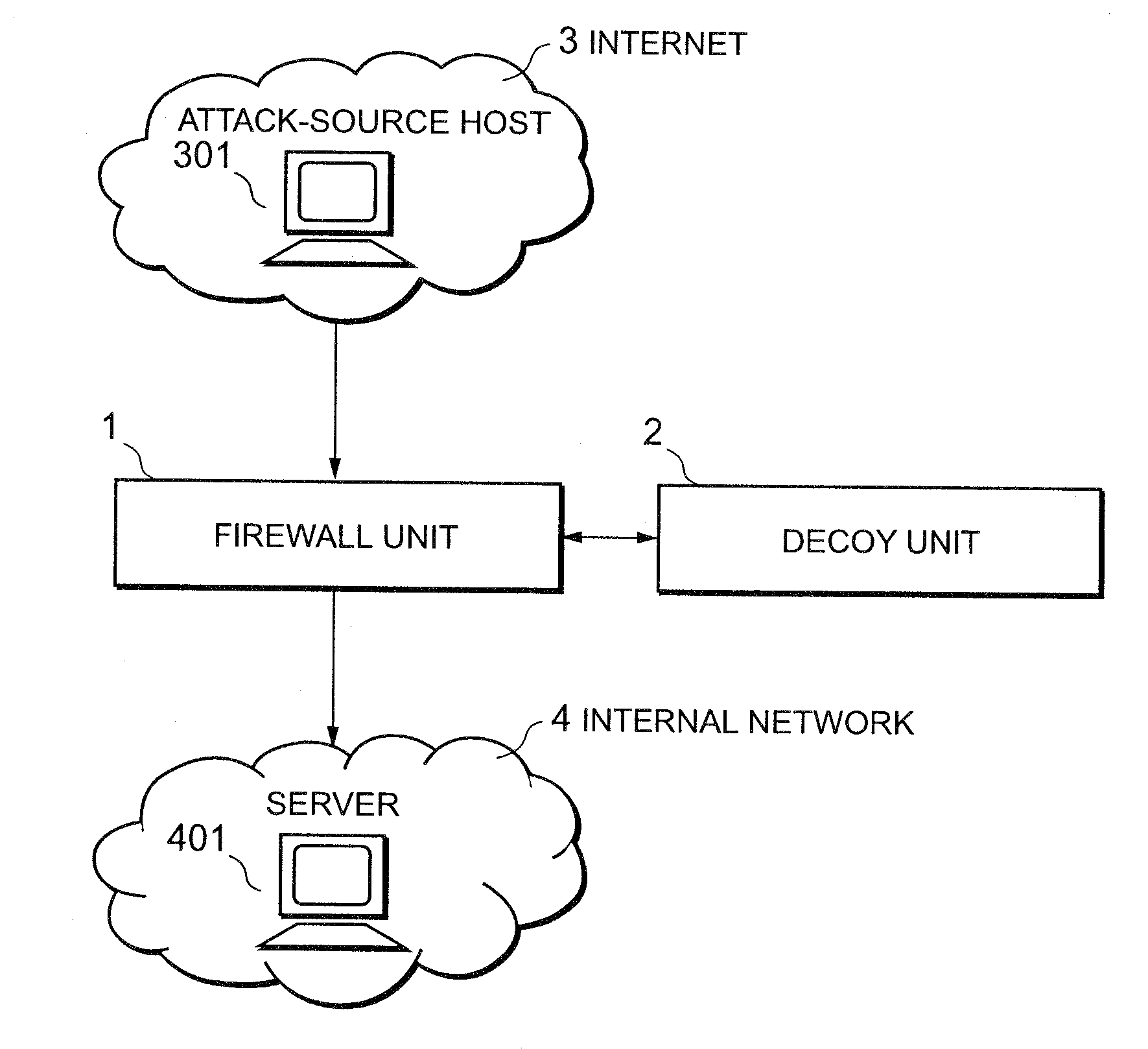
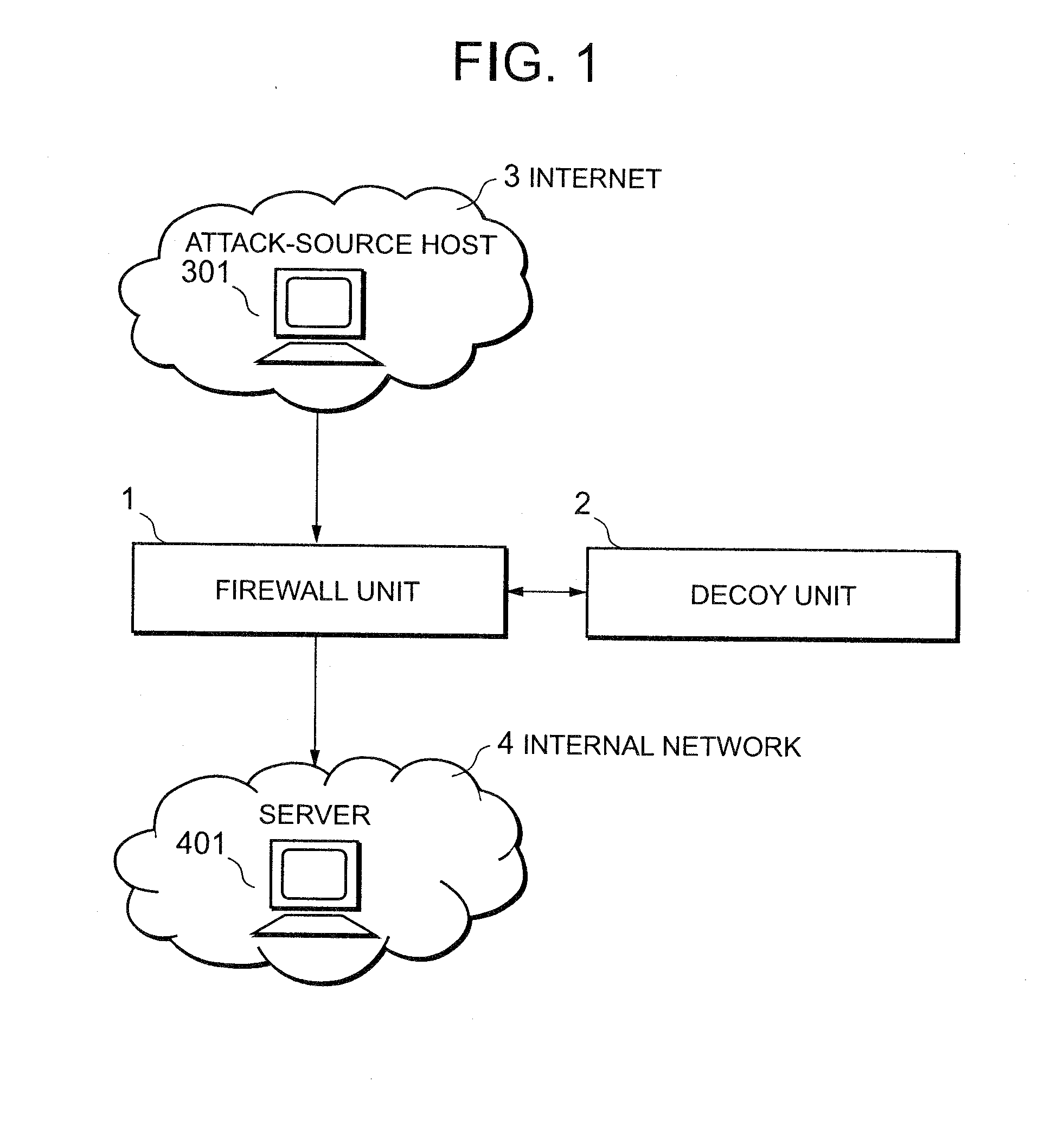
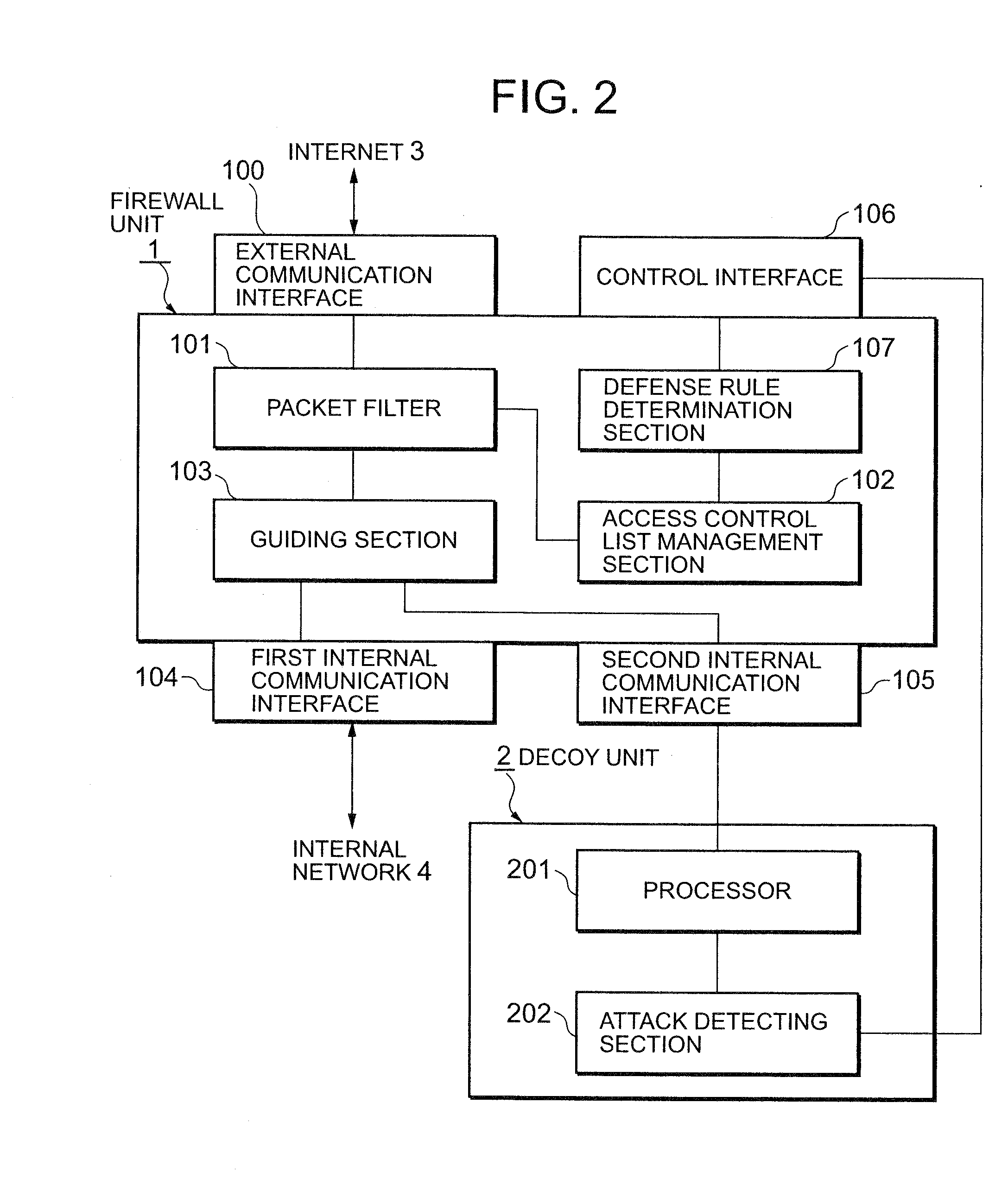
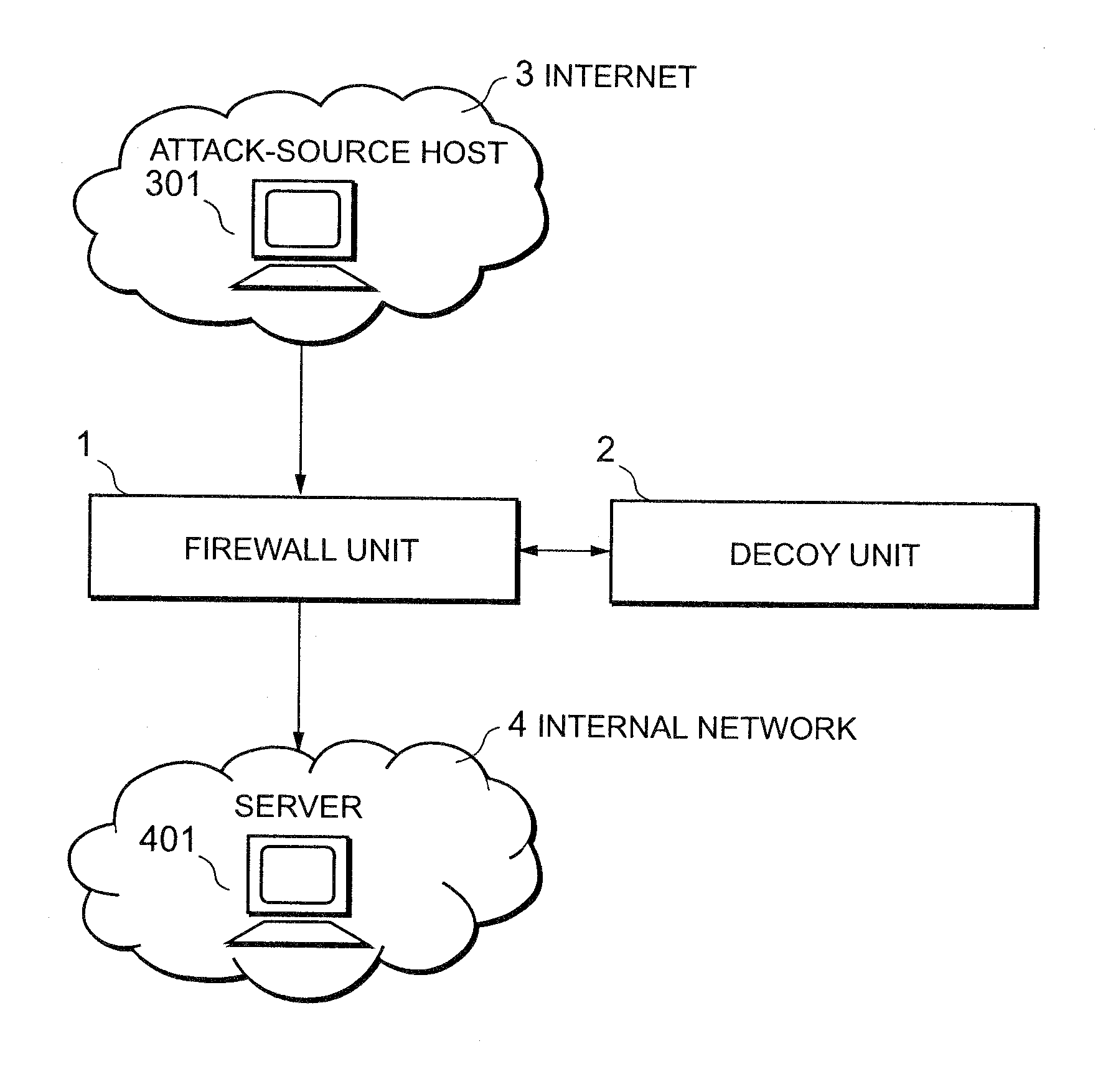
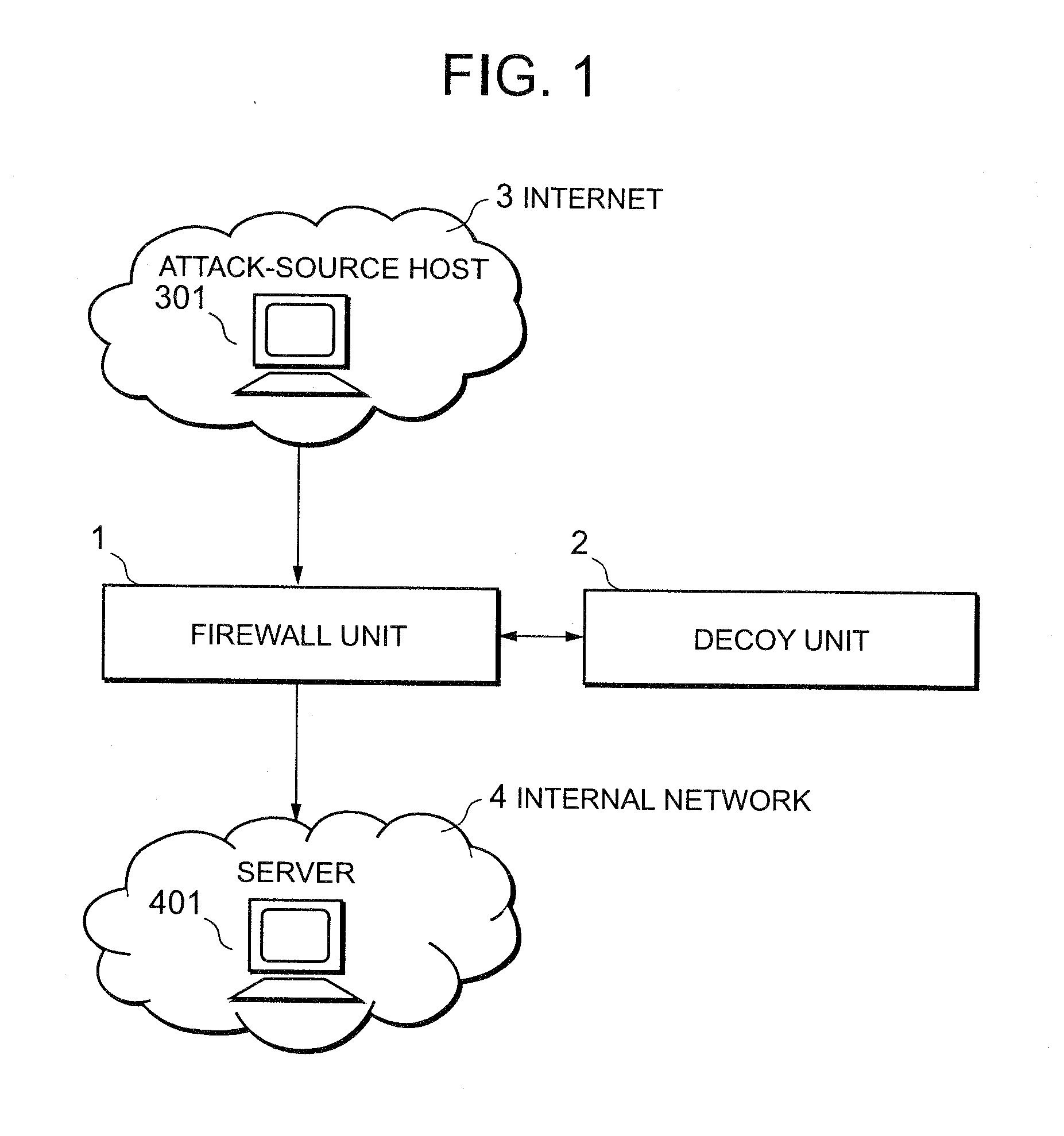
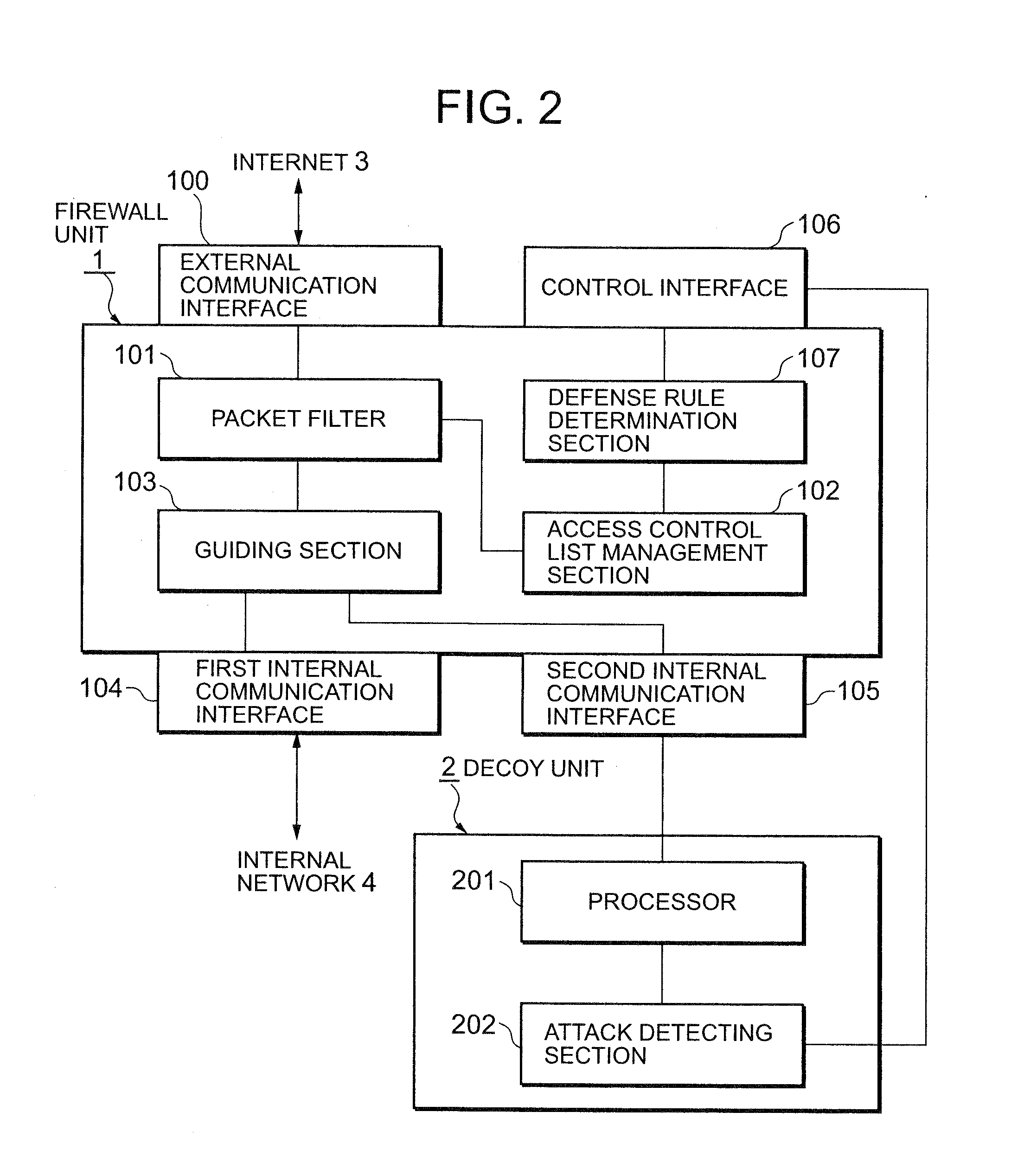
Attack defending system and attack defending method
InactiveUS20080282339A1Effective defenseEffective attackDigital data processing detailsUnauthorized memory use protectionCommunications systemDecoy
Owner:NEC CORP
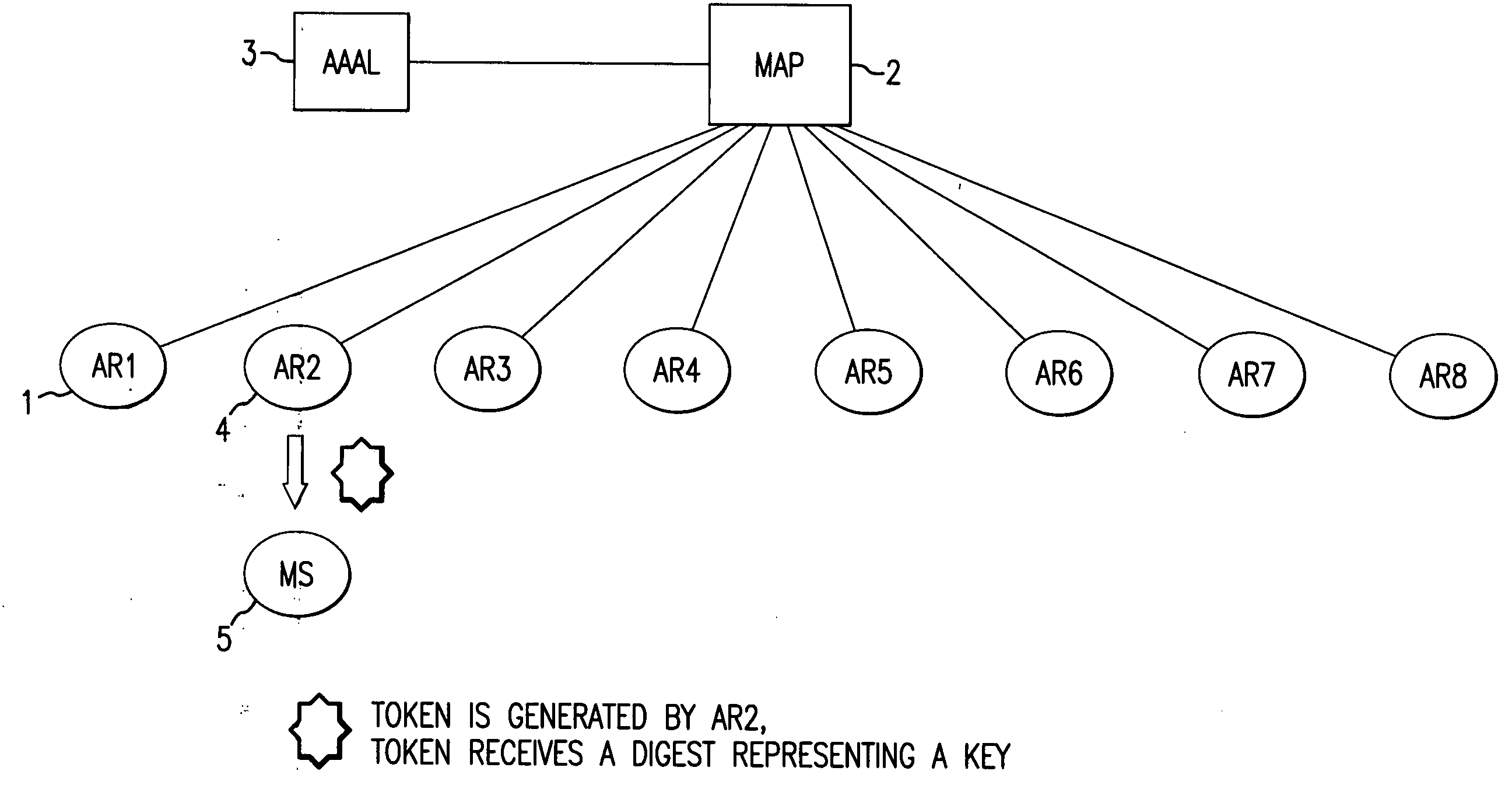
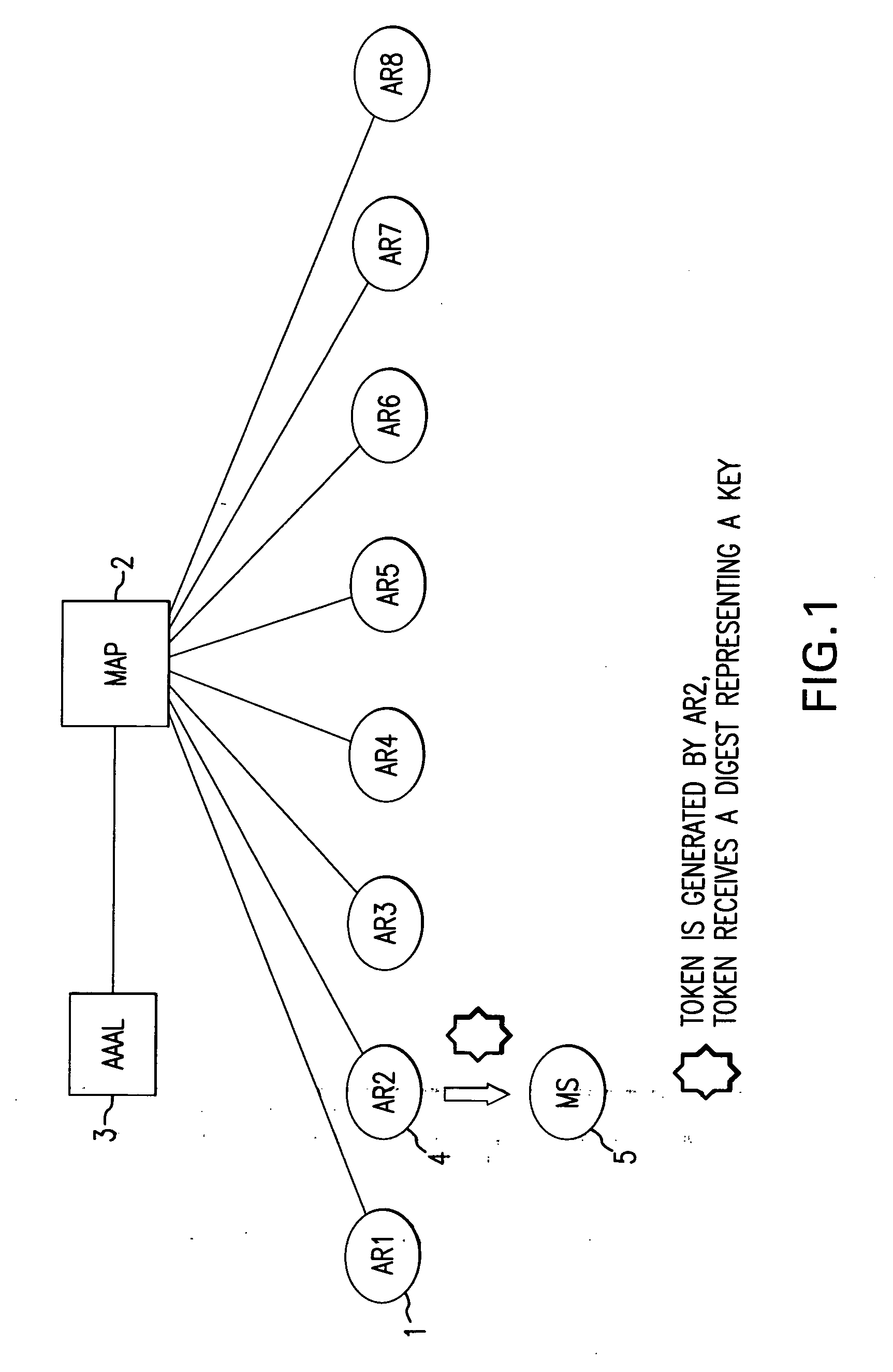
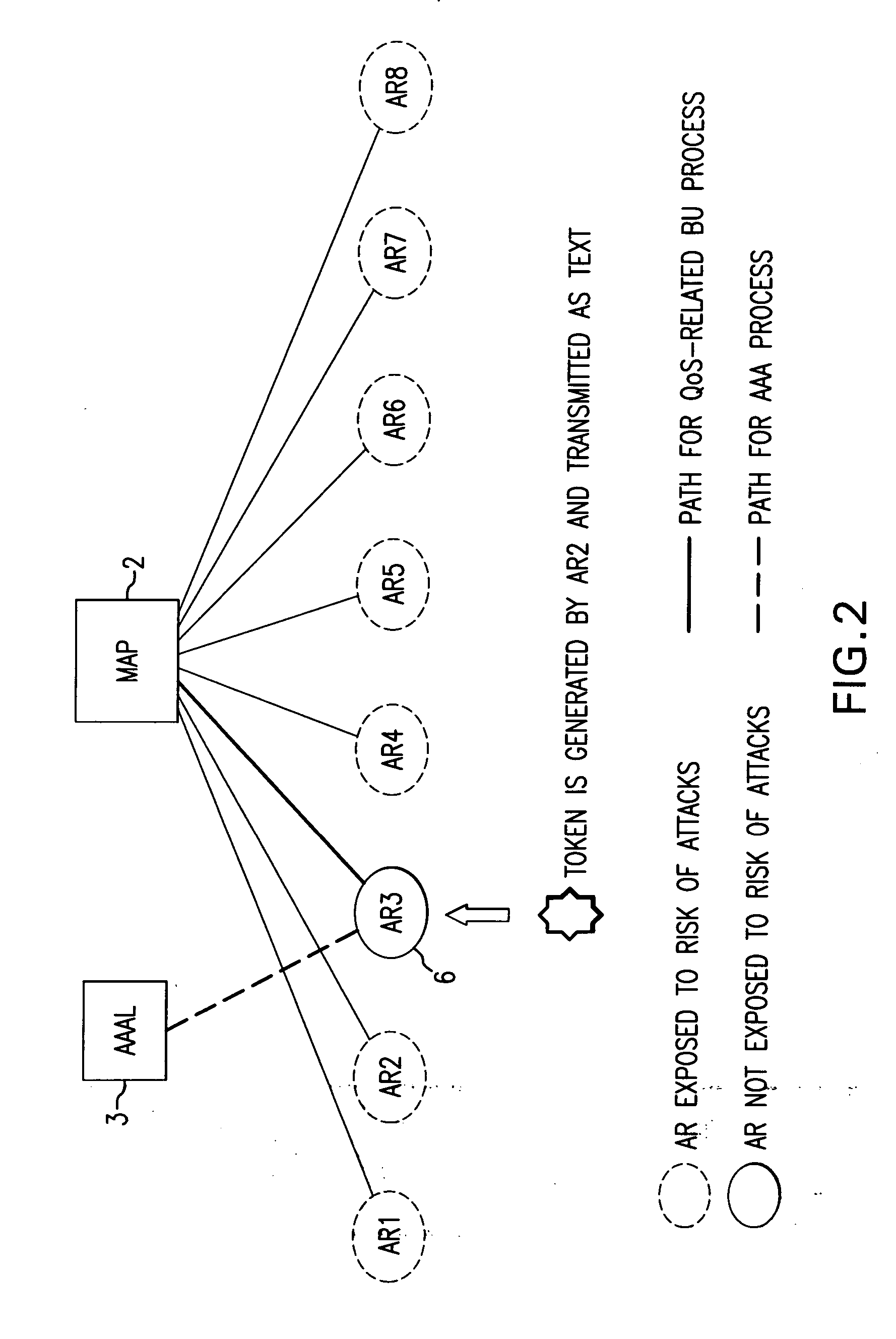
Verifying check-in authentication by using an access authentication token
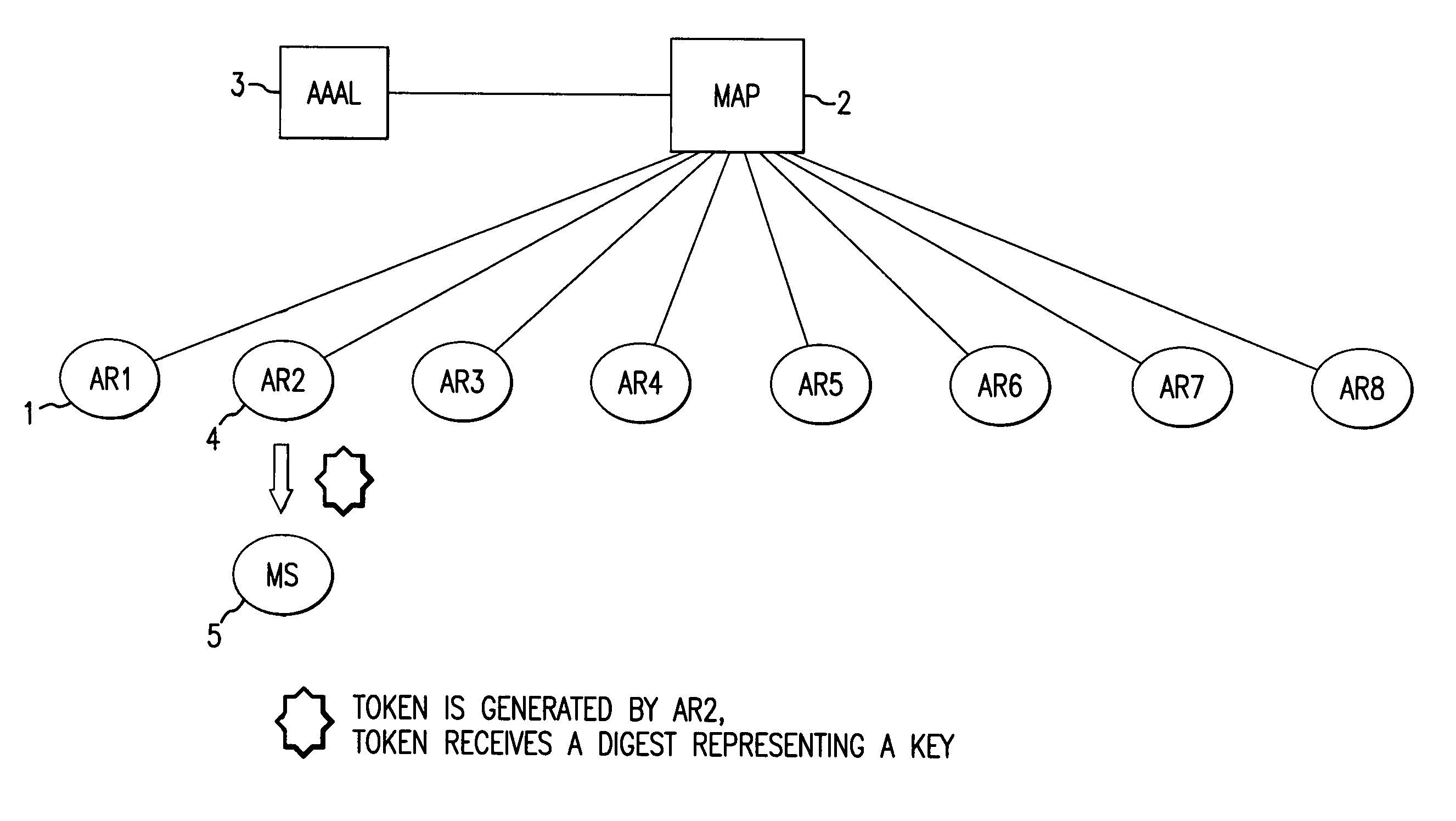
InactiveUS20050079866A1Good Performance GuaranteedEffective protectionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile radioComputer science
A simple and efficient means of checking the registration authorization is proposed by the method and the device for checking the registration authorization prior to the start of the re-registration process based on a registration query from a mobile radio terminal to at least one access device for an intra-domain handover in a mobile communication network. In the network, a token which has been sent by an access device to a mobile radio terminal and has been stored in at least one trust table of at least one access device, is received by at least one further access device during a registration query from a mobile radio terminal and compared with tokens stored in at least one trust table prior to the start of the registration for the purpose of verifying the registration authorization, and the registration is started if an authorization is present.
Owner:SIEMENS AG
Solvating system and sealant for medical use in the sinuses and nasal passages
ActiveUS7993675B2Increased drug resistanceReduction and elimination in amountAntibacterial agentsPowder deliveryBiofilmNasal passage
Chronic rhinosinusitis and other bacterial sinus conditions may be treated by applying a solvating system containing a surfactant to a bacterial biofilm in a nasal or sinus cavity, disrupting the biofilm, and applying a protective layer of a polymeric film-forming medical sealant.
Owner:MEDTRONIC XOMED INC
Attack defending system and attack defending method
InactiveUS20080172739A1Effective defenseEffective attackMemory loss protectionError detection/correctionCommunications systemDecoy
An attack defending system allows effective defense against attacks from external networks even when a communication system uses a communication path encryption technique such as SSL. A firewall device and a decoy device are provided. The firewall device refers to the header of an input IP packet and, when it is determined that the input IP packet is suspicious, it is guided into the decoy device. The decoy device monitors a process providing a service to detect the presence or absence of attacks. When an attack has been detected, an alert including the attack-source IP address is sent to the firewall device so as to reject subsequent packets from attack source.
Owner:NEC CORP
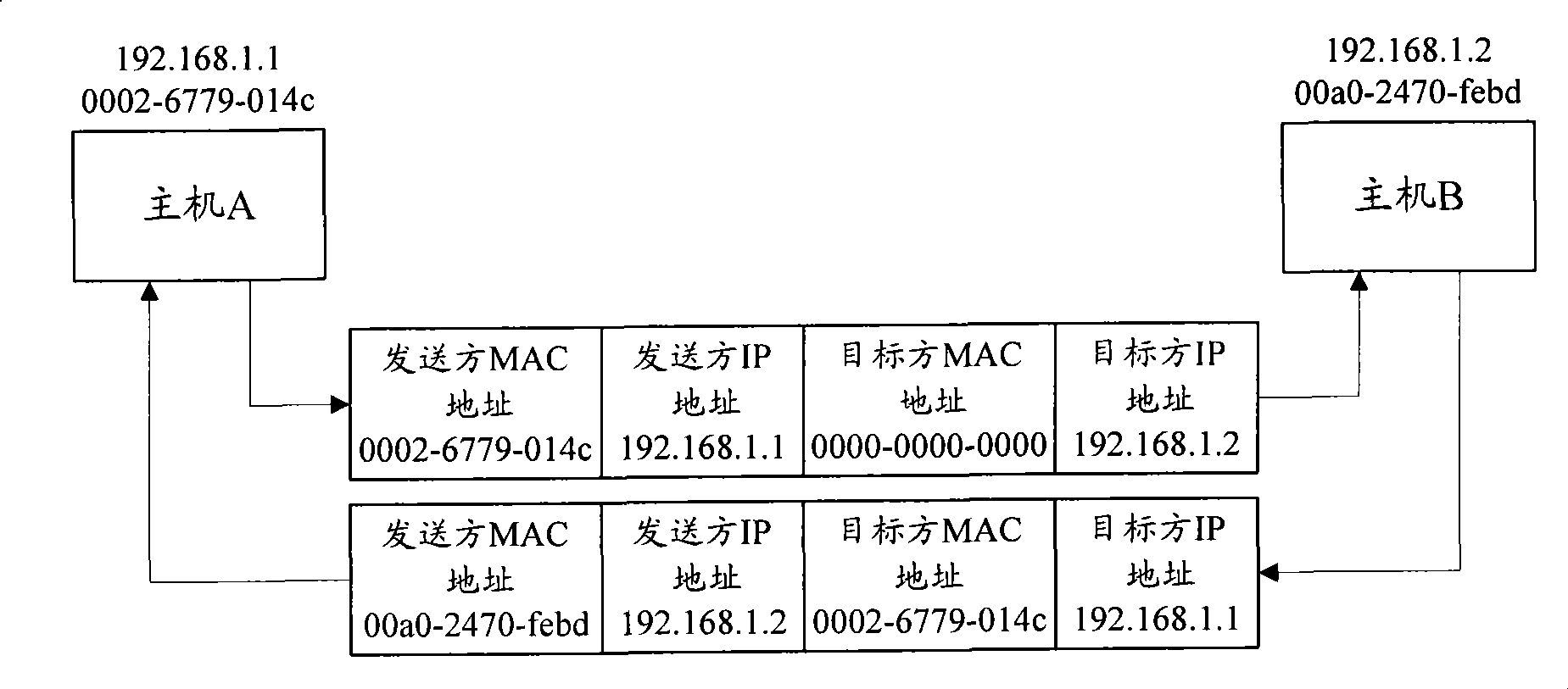
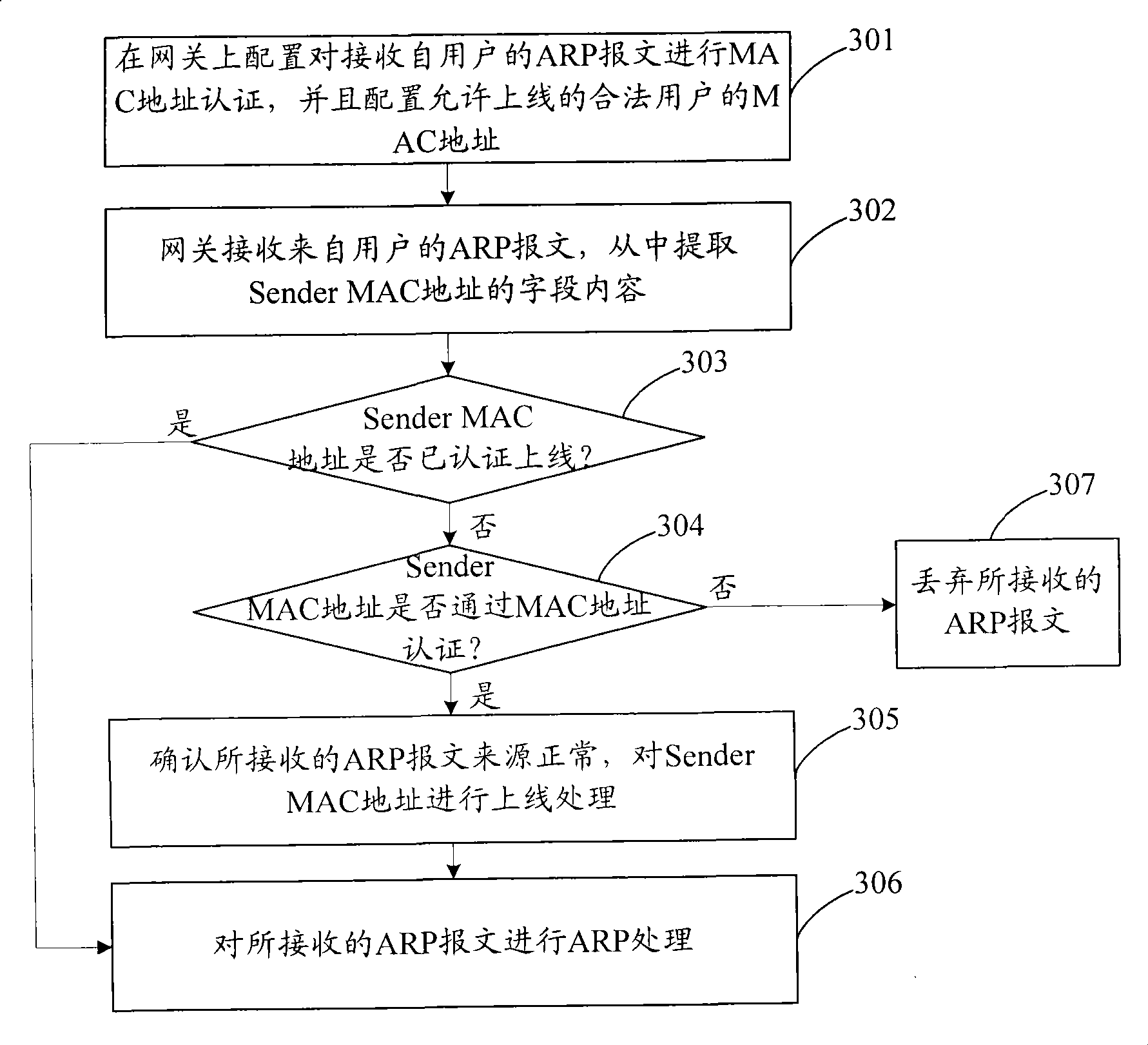
Method and system for defending address analysis protocol message aggression
InactiveCN101415012AEffective interceptionEffective attackData switching networksAddress Resolution ProtocolAddress resolution
The invention discloses a method used for defending address resolution protocol message attack, comprising the steps as follows: media access control MAC address of legal user is configured in advance; network equipment receives the address resolution protocol ARP message coming from the user; the field content of the MAC address of the sender is extracted out of the received ARP message; whether the extracted MAC address of the sender is the MAC address of the legal user configured in advance or not is judged; if not, the received ARP message is abandoned. The invention also discloses a system which can defend the address resolution protocol message attack. The method and the system are suitable for the users which adopt all types and do not need to modify the network equipment greatly.
Owner:NEW H3C TECH CO LTD
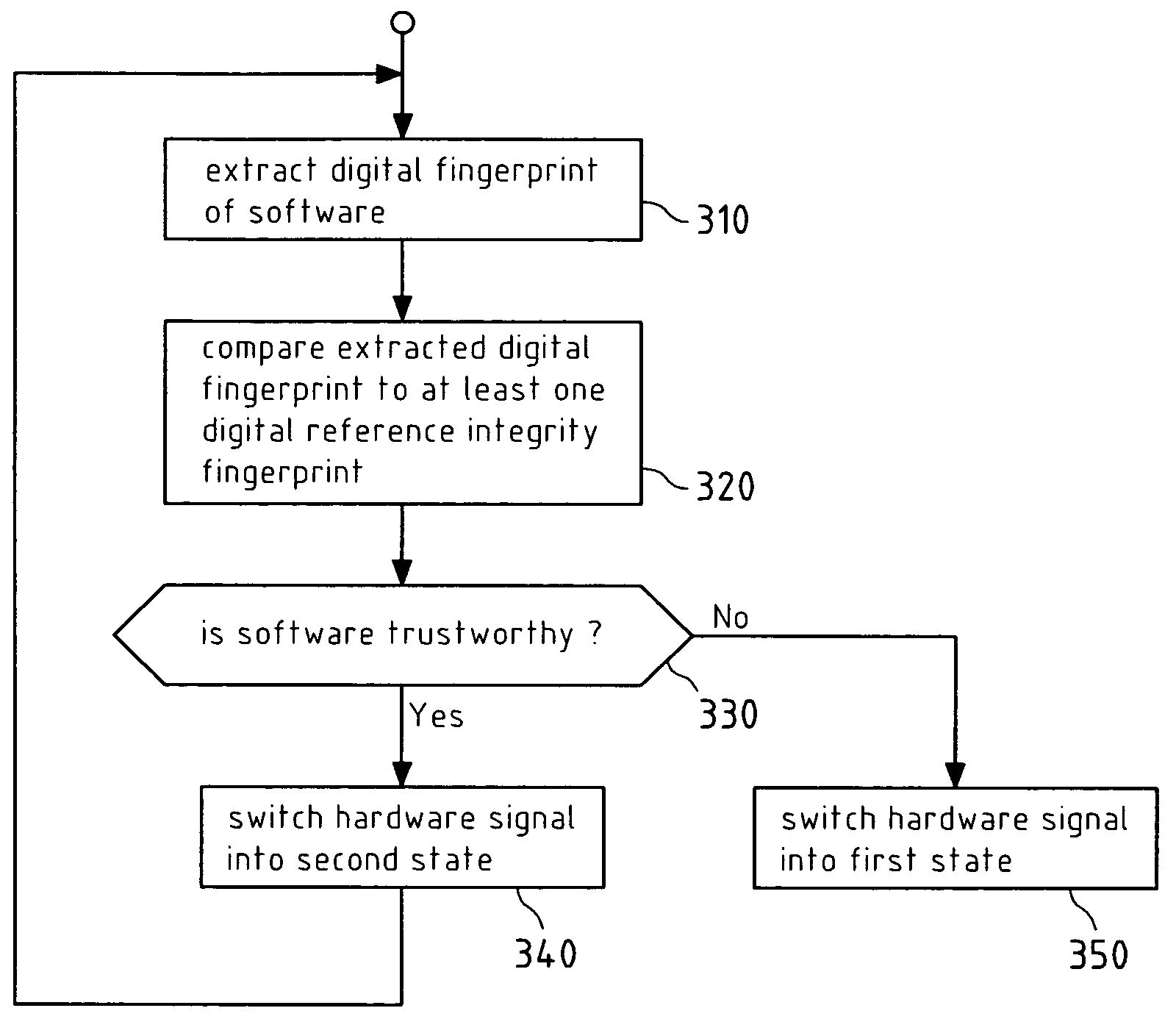
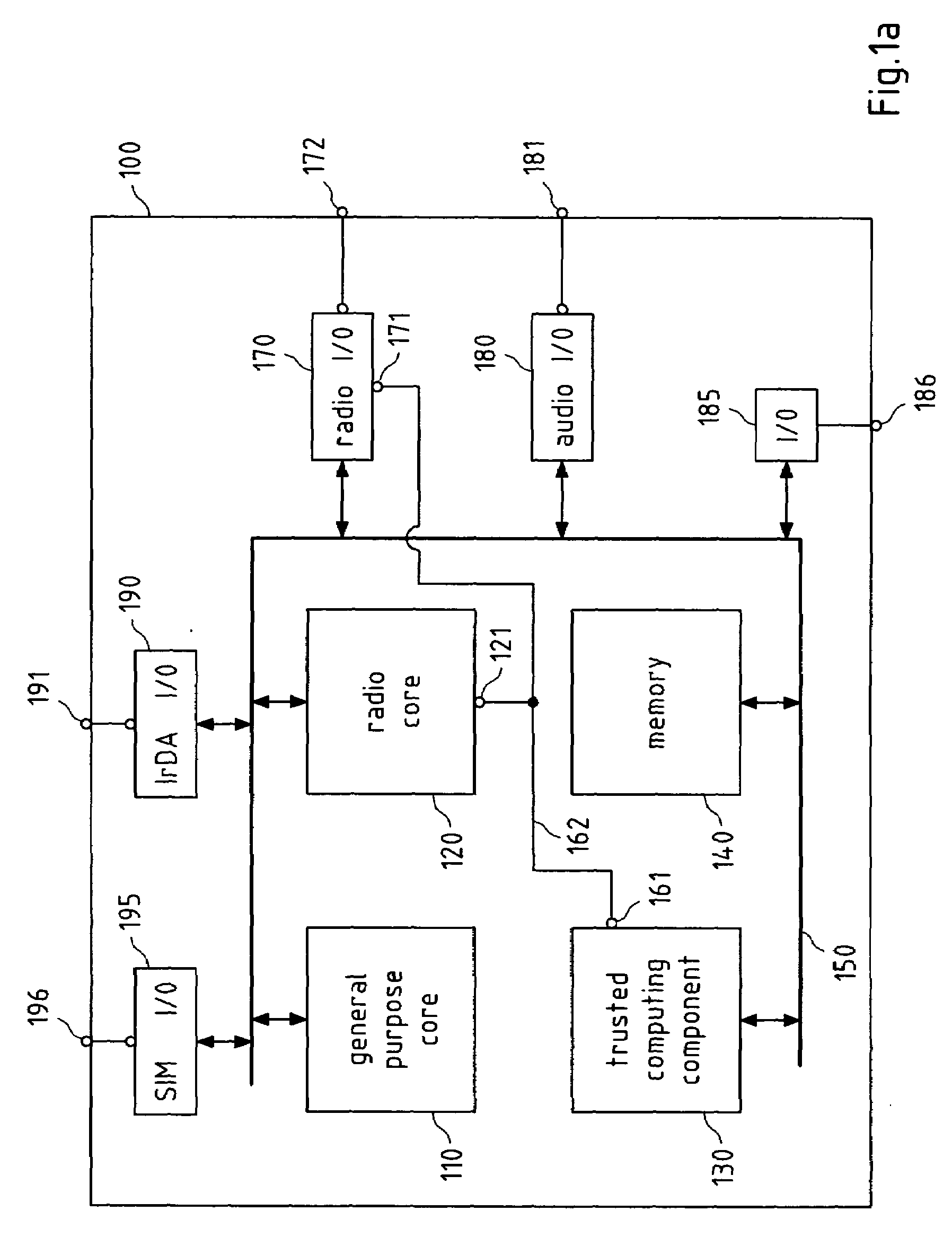
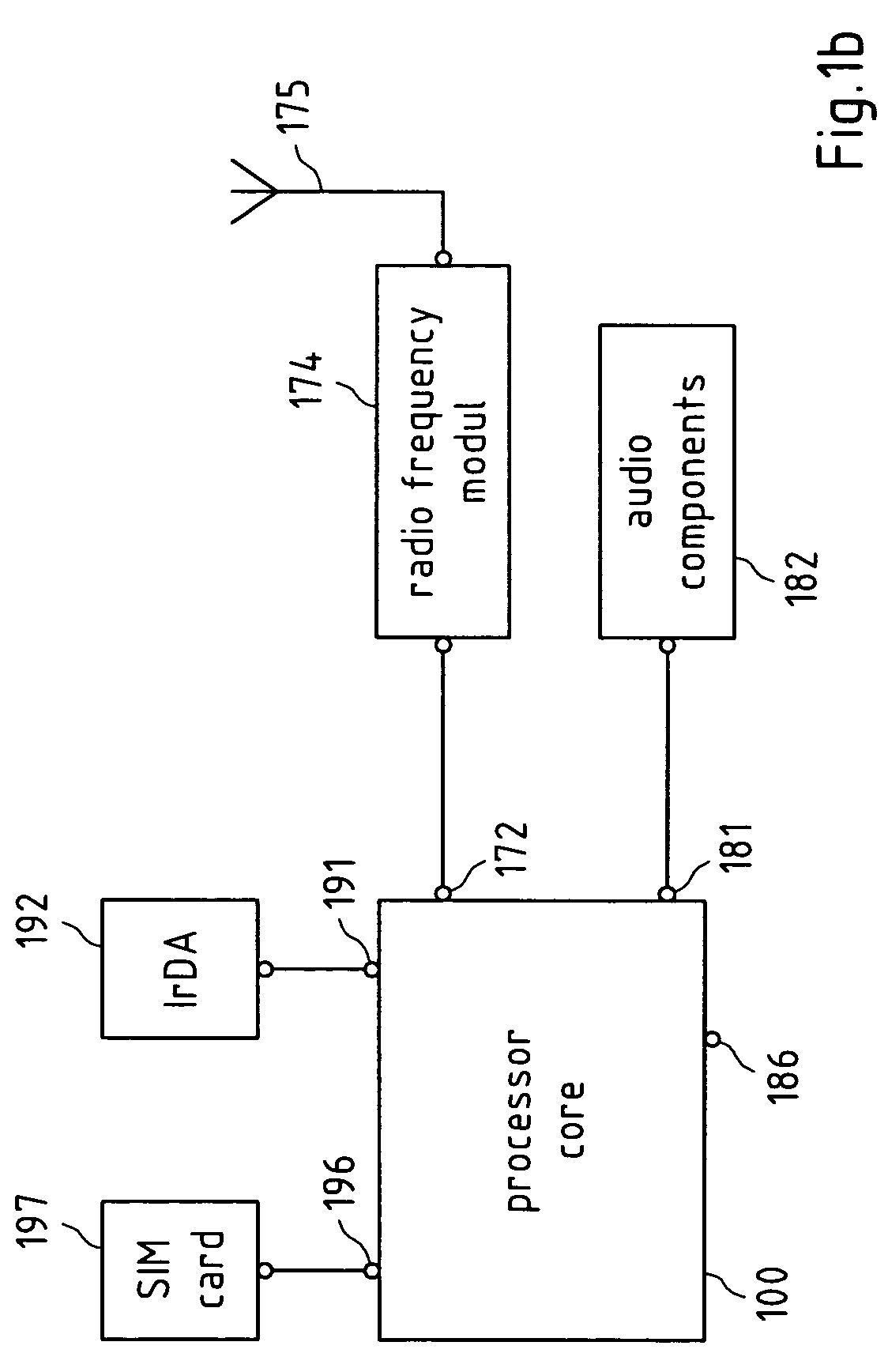
Protecting interfaces on processor architectures
InactiveUS20080077801A1Reduce power consumptionEnhanced radiationDigital data processing detailsUser identity/authority verificationSoftwareTrustworthiness
A method, an apparatus and a computer program product are disclosed for verifying the trustworthiness of a software in an apparatus, and switching a hardware signal in the apparatus into a first state when the software is not trustworthy.
Owner:NOKIA CORP
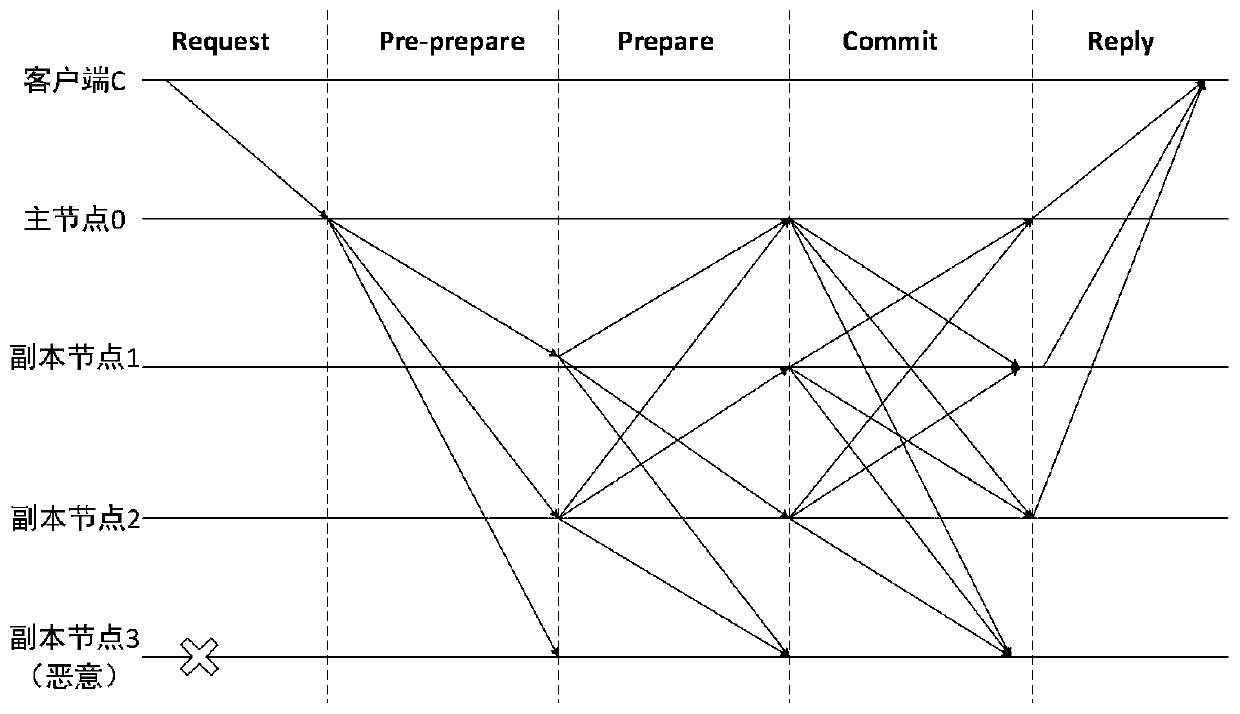
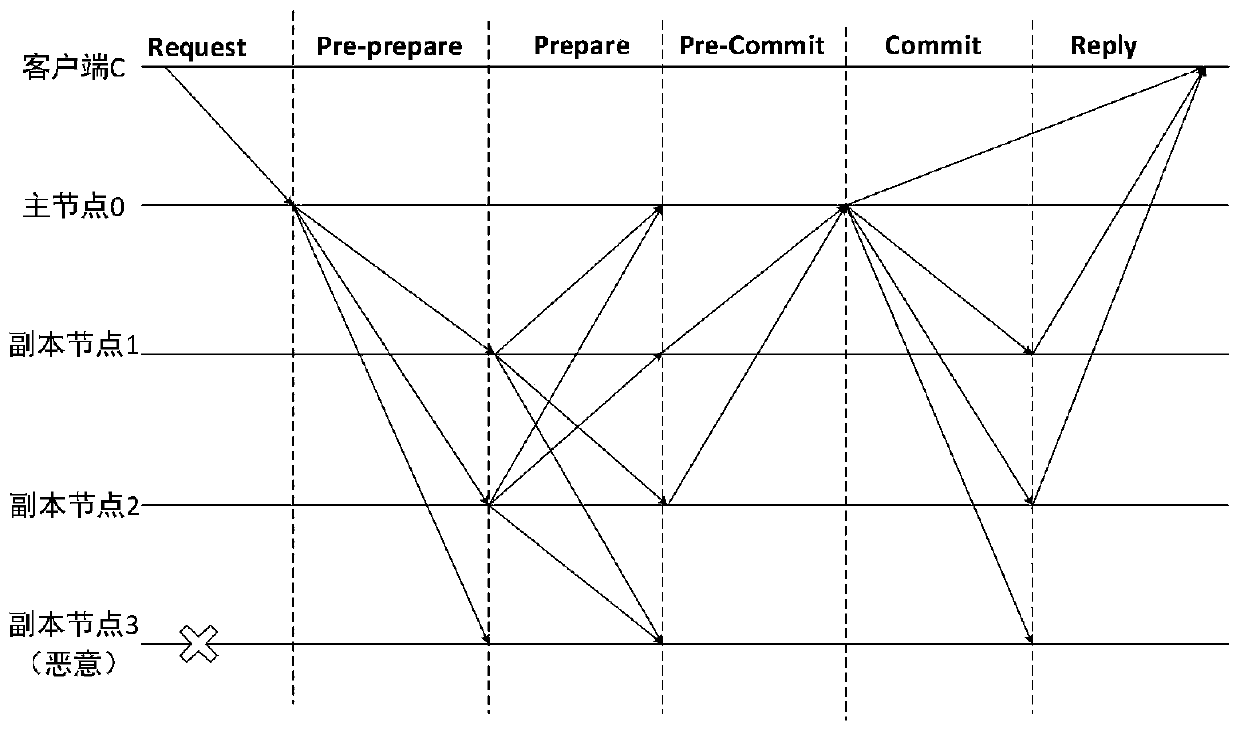
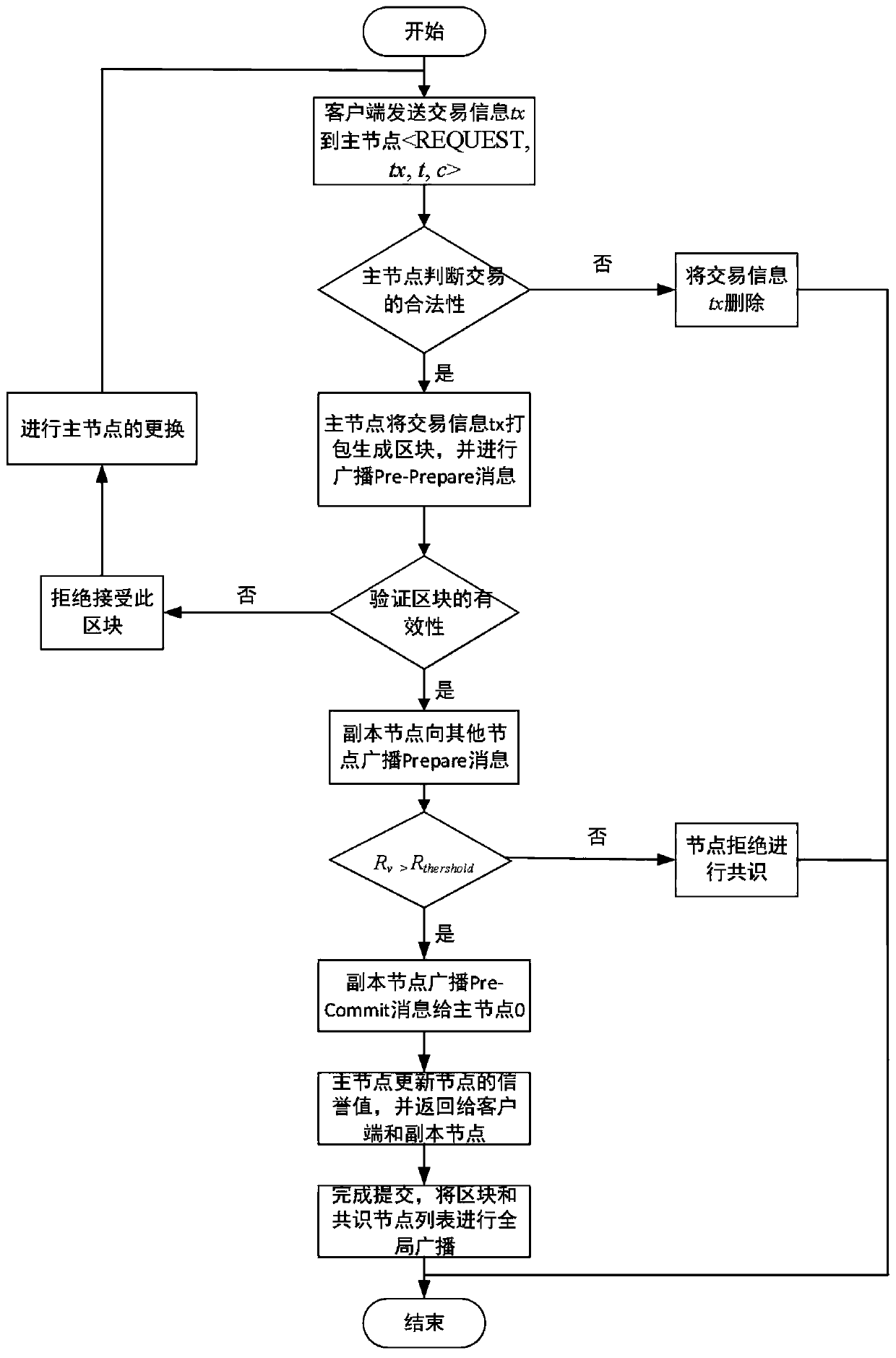
Method for defending Sybil attacks in block chain based on improved PBFT algorithm
InactiveCN110493198AEffective attackReduce the number of communicationsTransmissionBlockchainSybil attack
The invention discloses a method for defending Sybil attacks in a block chain based on an improved PBFT algorithm. According to the method, a PBFT algorithm is improved, an original view change mechanism in the algorithm is deleted, a main node Sp is randomly selected through the credible state of a consensus node, and meanwhile, a Pre-Commit stage is added in a consensus protocol to reduce the communication frequency between nodes; secondly, a reputation model is established to count comprehensive information of each consensus node to calculate a reputation value of the node, and due to the fact that the reputation values of the nodes are different, owned speaking rights are different, and the nodes achieve consensus through voting so as to defend Sybil attacks in the blockchain. According to the method, the frequency of communication between the nodes is reduced, the voting weight of the consensus node corresponds to the owned reputation value by referring to the consensus thought based on share certification in the public chain, and different speaking rights are allocated to the nodes according to the reputation value of the consensus node, so that Sybil attacks in the blockchain can be effectively defended.
Owner:BEIJING UNIV OF TECH
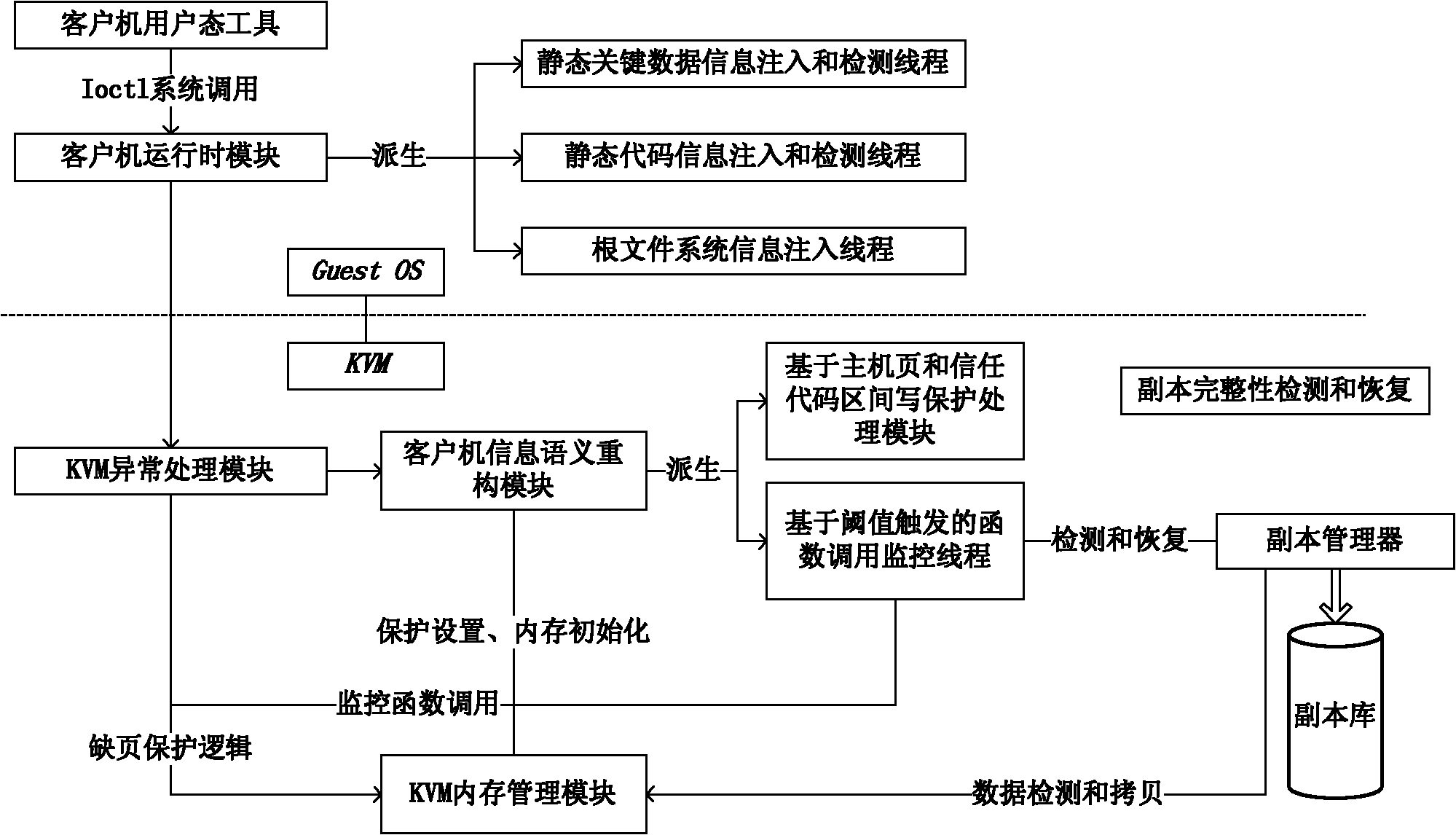
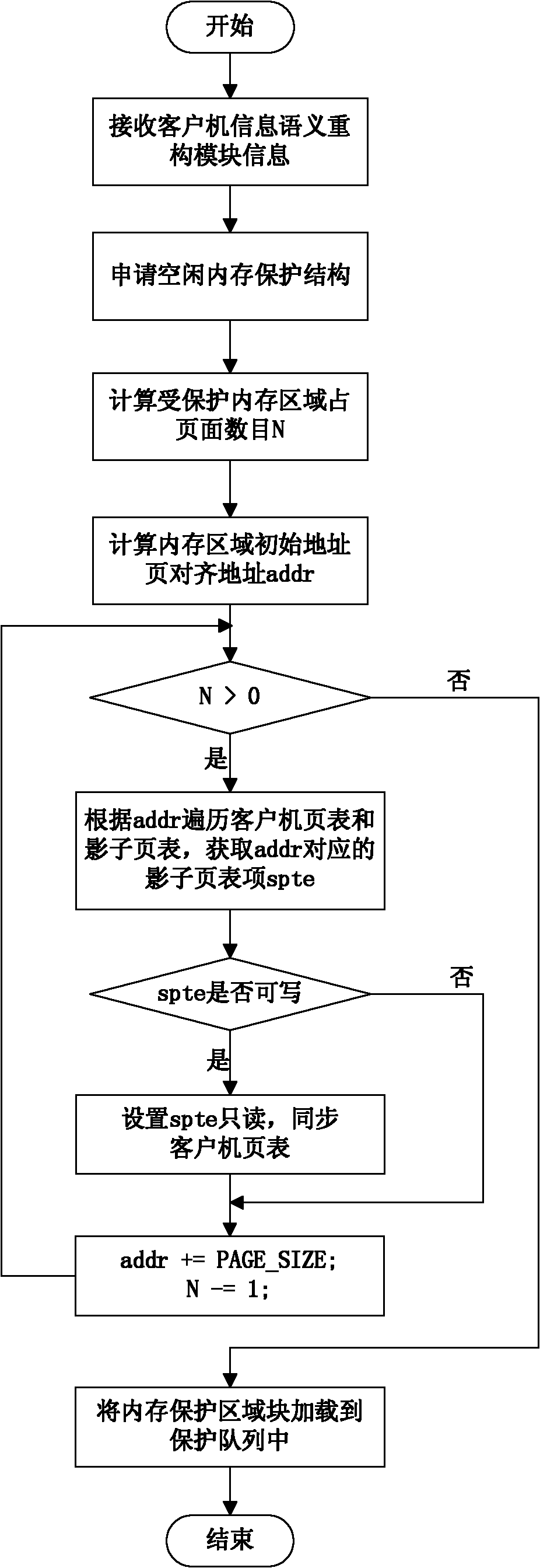
Rootkit detection mechanism and detection method based on kernel-based virtual machine
InactiveCN102194080ARealize isolation preservationEasy to detectPlatform integrity maintainanceData segmentClient machine
The invention provides a rootkit detection method based on a kernel-based virtual machine. By adopting the rootkit detection method, the types of objects attacked by rootkit are subjected to abstract classification into static code segment, static data segment, dynamic distribution function and heap space data, and different protection and detection mechanisms are provided specific to different types; while specific rootkit sensitive information is obtained through a runtime module operating in a client machine, information interaction between the kernel-based virtual machine and the client machine is realized by adding a semantic processing pathway, and by extending a corresponding page-fault exception handler and a vmcall active trap-in mechanism, the normal execution of the client machine is guaranteed under the rootkit detection mechanism. The rootkit detection mechanism and detection method, provided by the invention, can be used for effectively preventing the attack specific to static codes and data segments, and realizing isolated storage, detection and recovery of dynamic information at very low cost under a secure environment.
Owner:XI AN JIAOTONG UNIV +1
Network attack filtering method and device
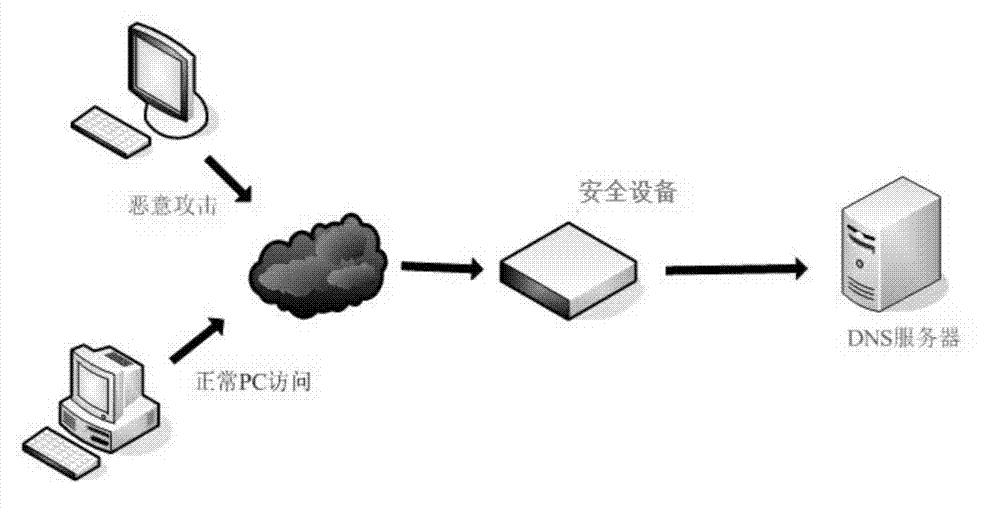
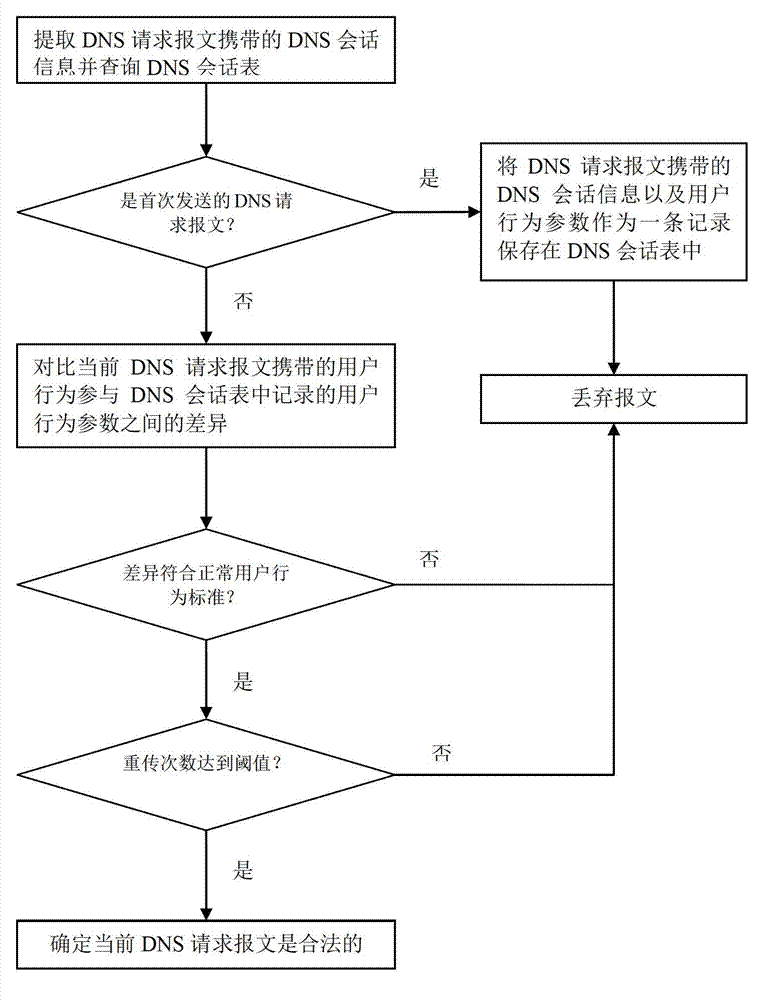
ActiveCN102739683AEffective filteringEffectively filters attacks on DNS serversTransmissionName serverNetwork attack
The invention provides a network attack filtering method which is applied to a safety device and used for providing a service for filtering network attacks to a domain name server (DNS). The method comprises the following steps: A. judging whether the first sending is conducted when a DNS request message of a user is received, if no, transferring to a step B to process; or, abandoning the message and storing the DNS conversation information and an user behavioral parameter in a DNS conversation table; B. obtaining a user behavioral parameter corresponding to the conversation information brought by a current DNS request message from the DNS conversation table, judging whether the difference between the user behavioral parameter brought by the current message and the user behavioral parameter recorded in the DNS conversation table is in accordance with the standard of normal user behavior; if so, judging the message to be legal; and otherwise, abandoning the message. According to the behavioral characteristics of a user protocol stack, the attack to the DNS server is effectively filtered.
Owner:HANGZHOU DPTECH TECH
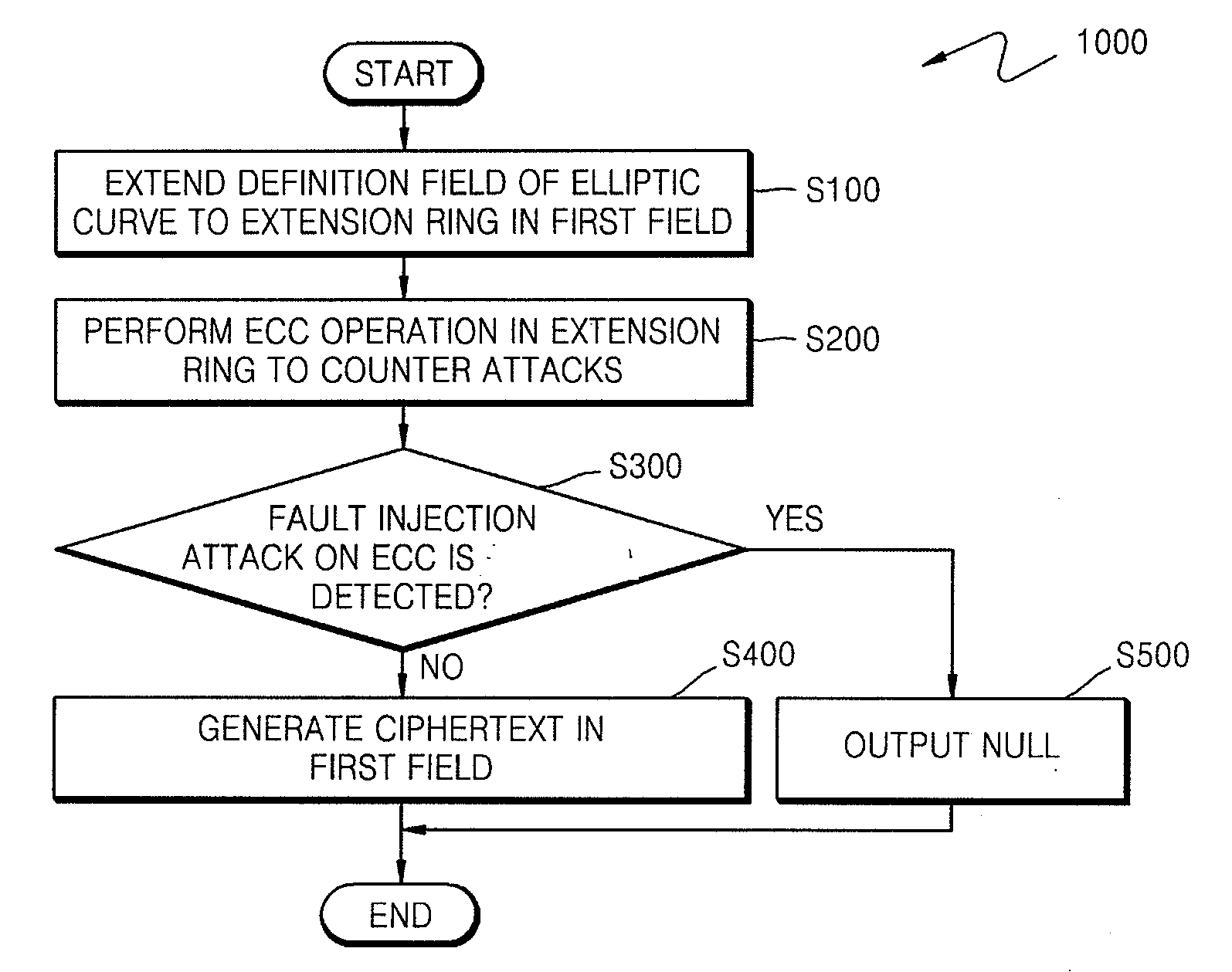
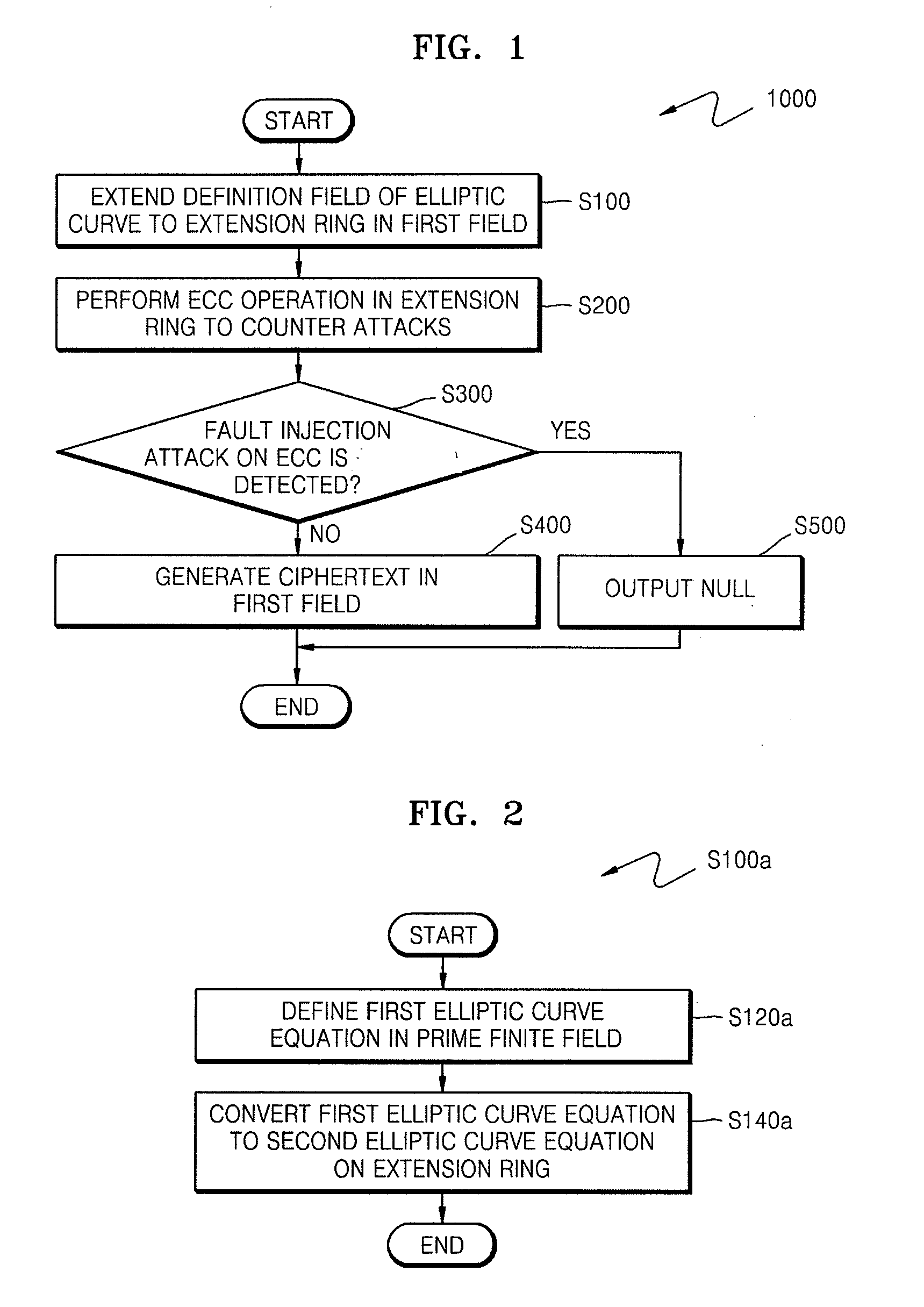
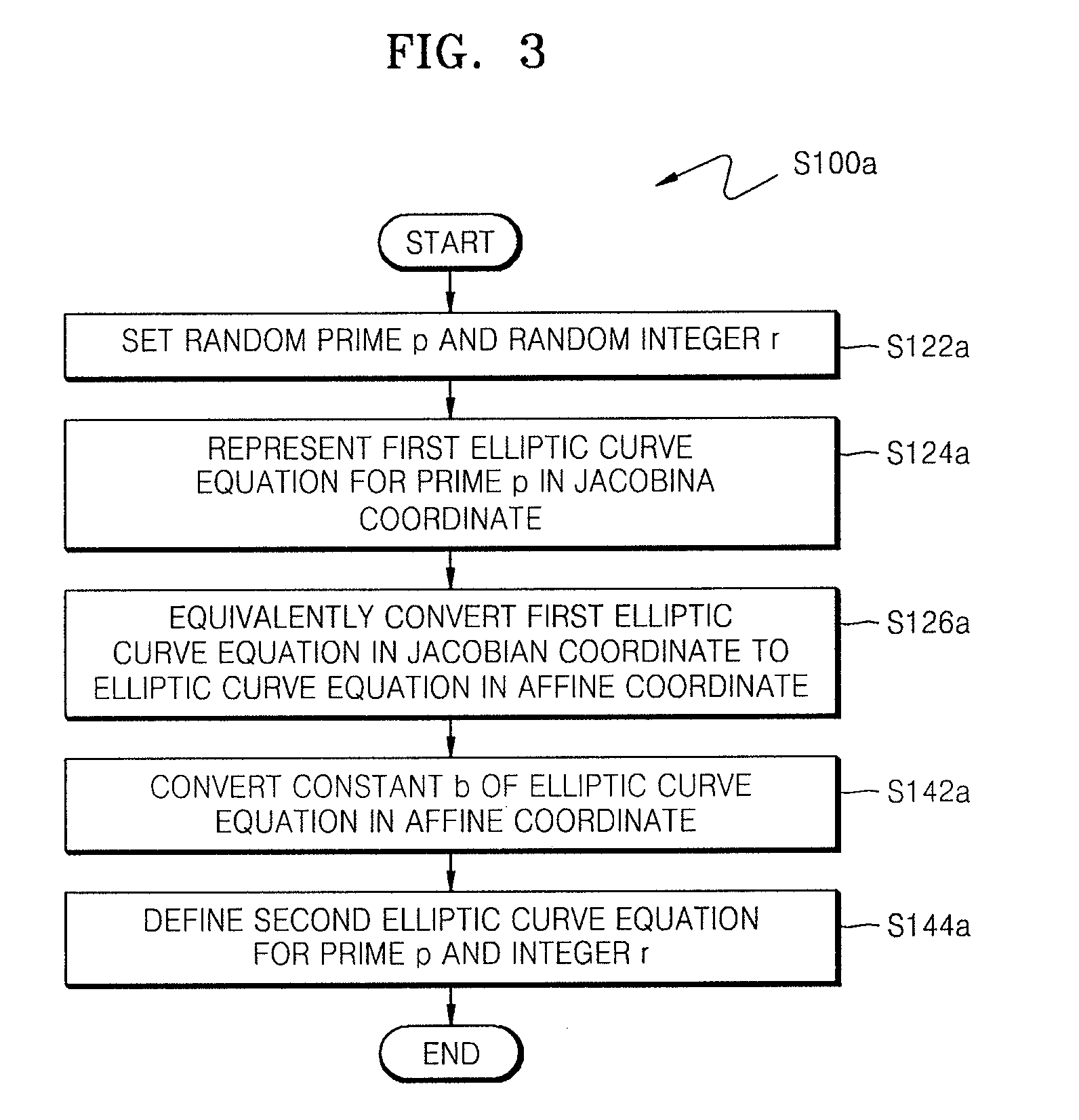
Method of countering side-channel attacks on elliptic curve cryptosystem
ActiveUS20090034720A1Improve securityEfficient fault attack countermeasureMultiple keys/algorithms usageData taking preventionFault detection algorithmCiphertext
A method of countering side-channel attacks on an elliptic curve cryptosystem (ECC) is provided. The method comprises extending a definition field of an elliptic curve of the ECC to an extension ring in a first field; generating a temporary ciphertext in the extension ring and countering attacks on the ECC; and generating a final ciphertext for the first field if a fault injection attack on the ECC is not detected. The countering of attacks on the ECC may comprise countering a power attack on the ECC. Checking if there is a fault injection attack on the ECC may be performed by determining if the temporary ciphertext satisfies a second elliptic curve equation. The fault detection algorithms takes place in a small subring of the extension ring, not in the original field, to minimize the computational overhead. The method can improve the stability of the ECC and reduce computational overhead of the ECC.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and protecting apparatus for defending denial of service attack
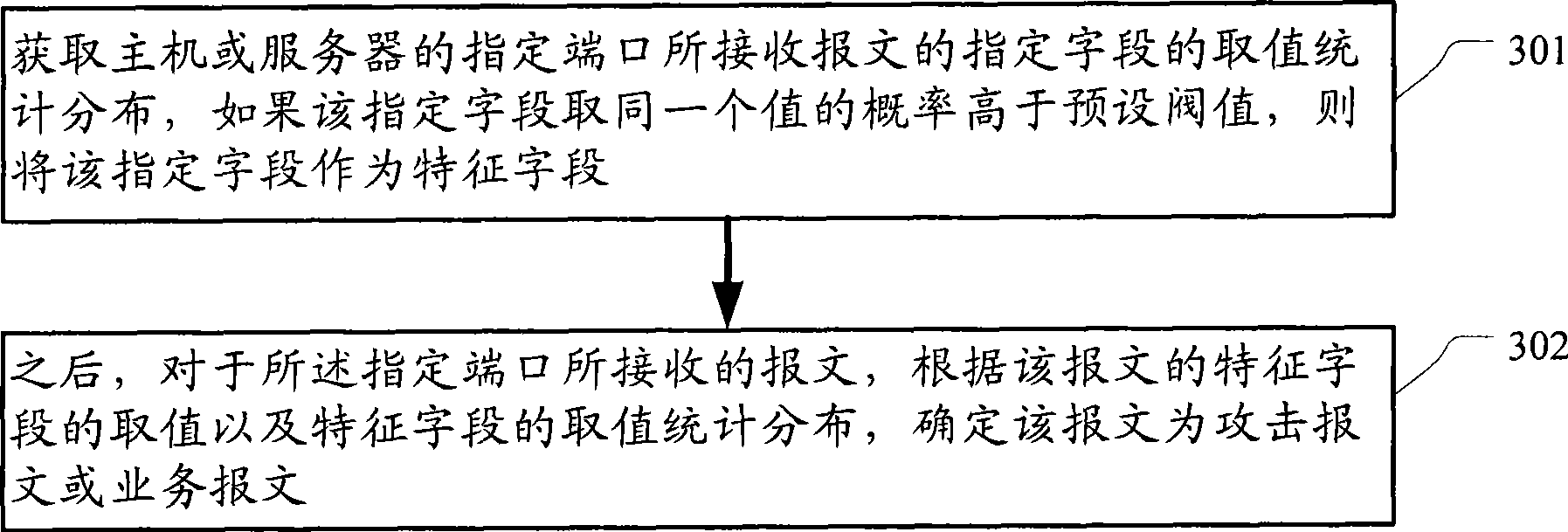
InactiveCN101505219AEffective attackEfficient identificationSecuring communicationLarge capacityTraffic volume
The invention discloses a method for defending a denial of service attack. The method comprises the following steps: acquiring value statistic distribution of an appointed field of a message received by an appointed port of a host or a server; taking the appointed field as a characteristic field if the probability of extracting the same value from the appointed field is higher that a preset threshold; and determining the message to be an attack message or a service message according to the value of the characteristic field of the message and the value statistic distribution of the characteristic field for the message received by the appointed port. The invention also discloses a device for defending the denial of service attack. The technical proposal can effectively identify attack messages in large capacity, and achieves the aim of defending the denial of service attack.
Owner:NEW H3C TECH CO LTD
Security System For Data Communications Including Key Management And Privacy
InactiveUS20160294794A1Easy to controlIncrease elasticityTransmissionCommunications securityInternet privacy
A security system and method that incorporates key management as well as provides privacy for its users. The security system and method removes all incentives for surveilling user communications in the search for personally identifiable information and usage patterns. This goal is achieved by ensuring that a snooper cannot make a distinction between two different users just by observing their communication. The system removes all personally identifiable information from open communication. The security system and method functions to anonymize data communications in relation to the user and the system.
Owner:MANCIC ALEKSANDAR +2
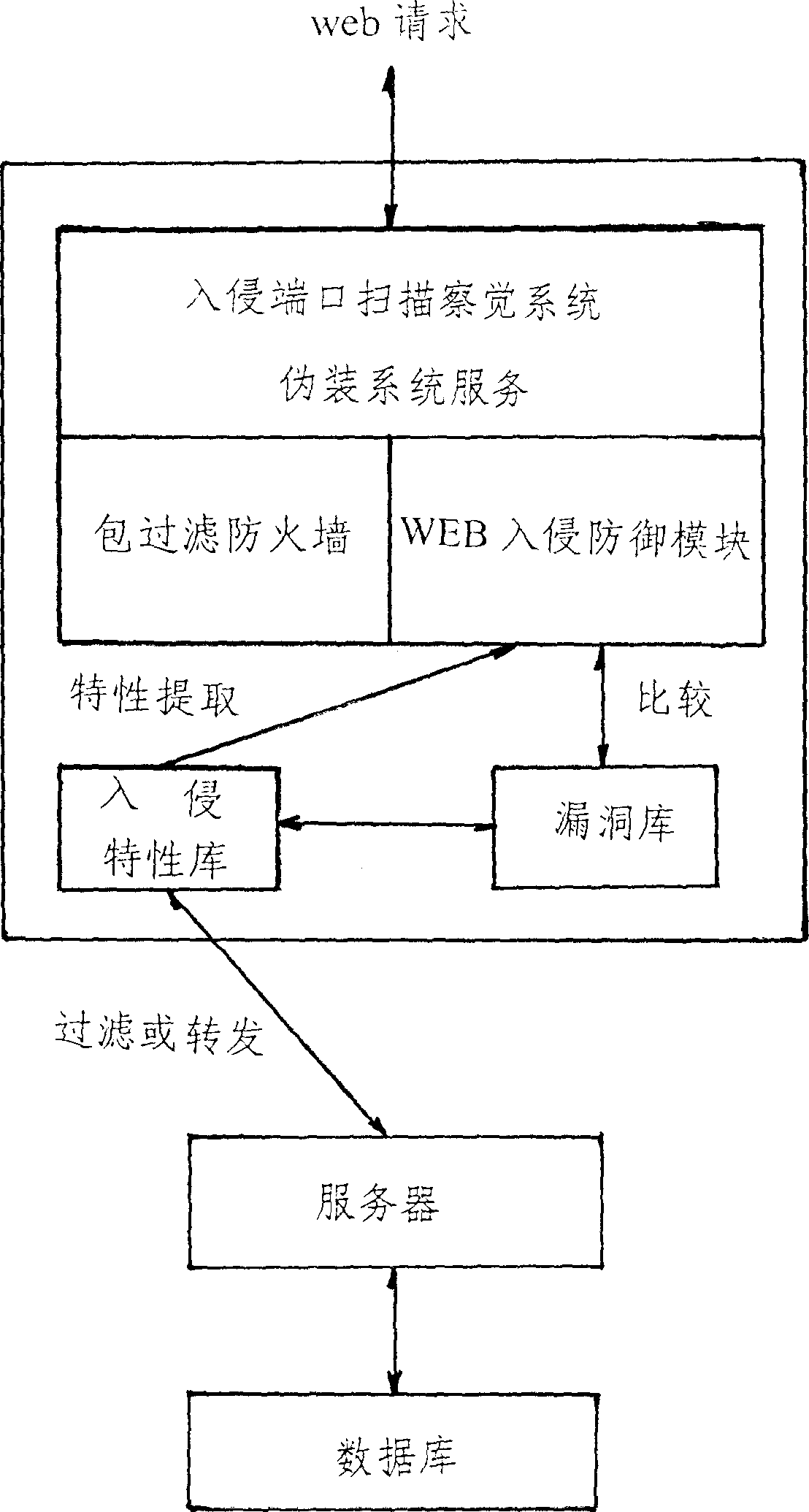
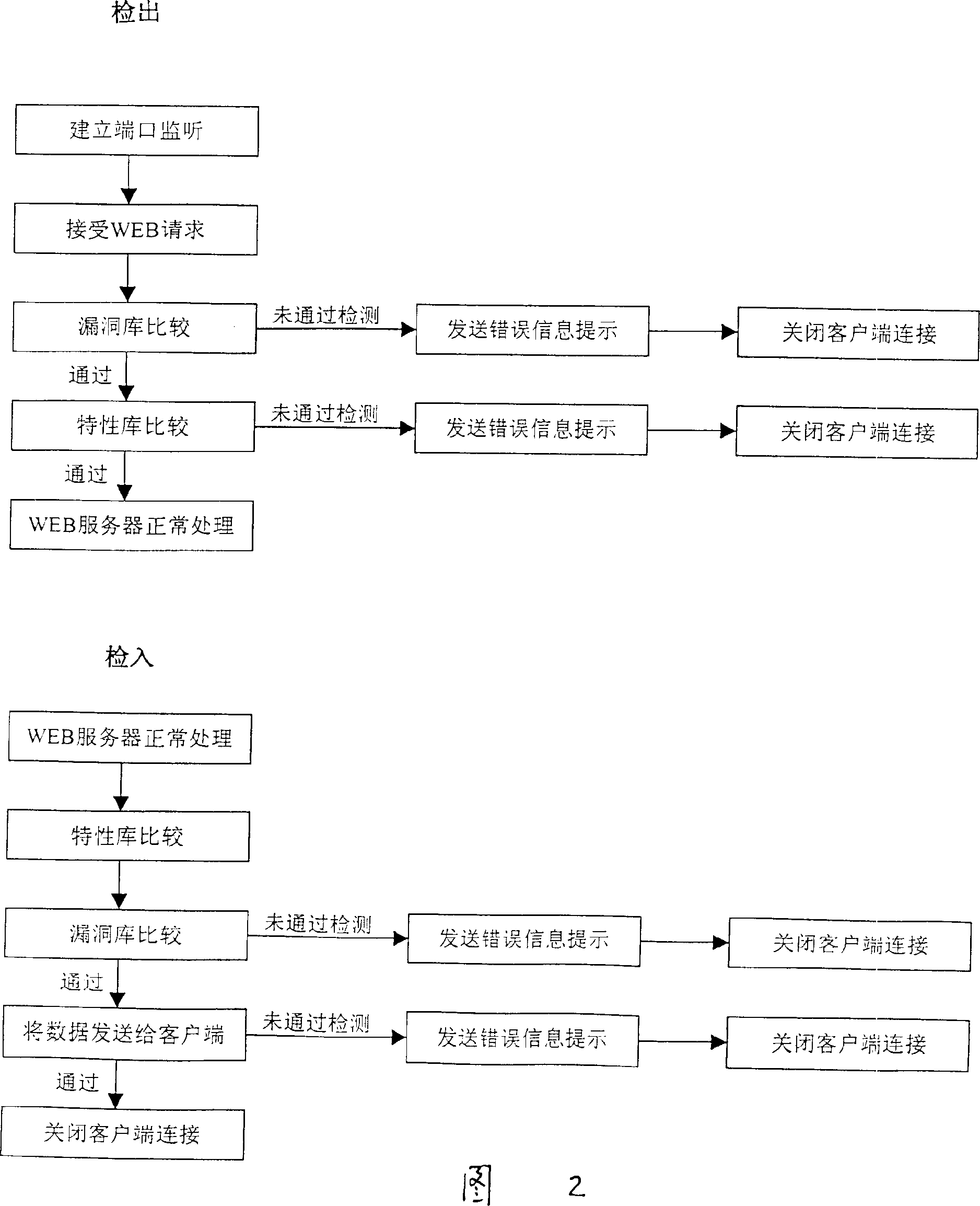
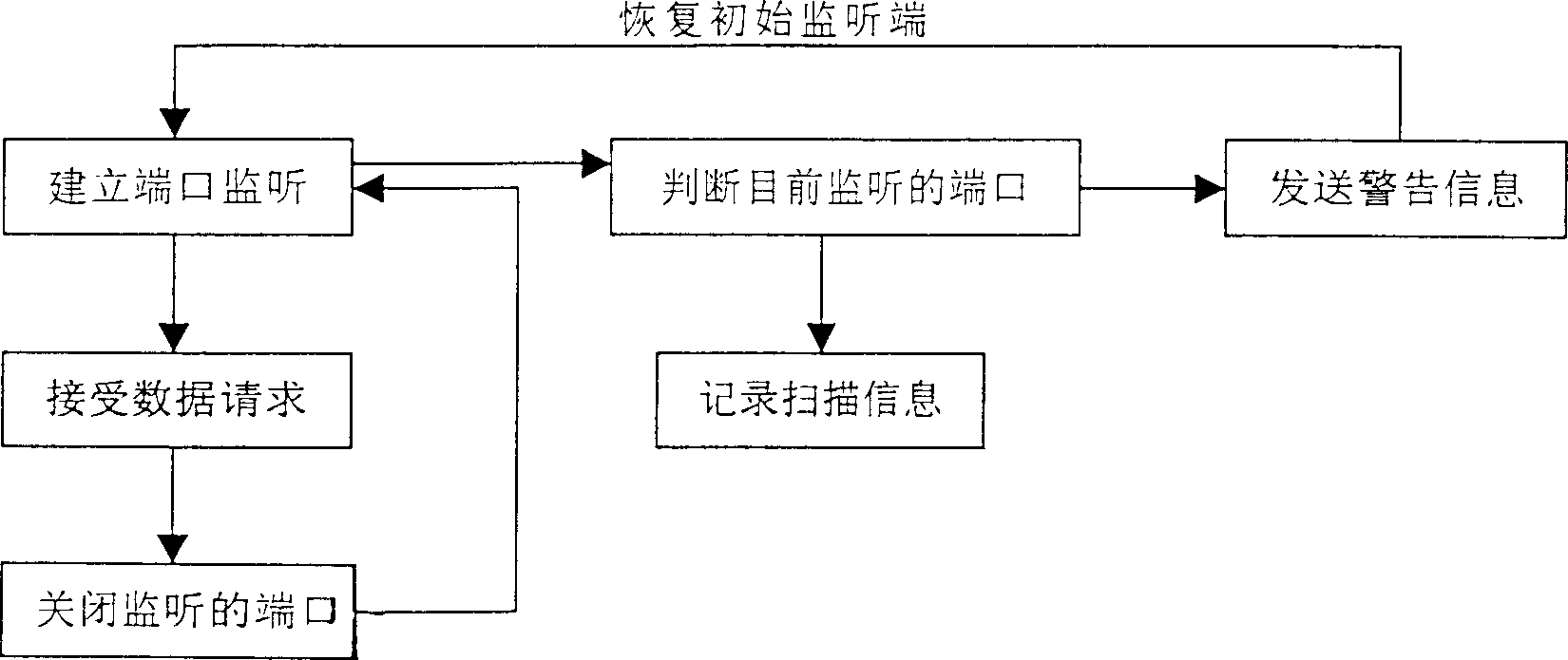
Guard system to defend network invansion of unkown attack trick effectively
The present invention has several guard measures to defend network invasion of known and unknown modes. The guard system consists of invasion port scanning, camouflage system service, WEB invasion defending firewall, traditional package filtering firewall and other subsystem. The guard system features its program-filtering subsystem, in which the validity of request from WEB is judged through thedata sorting based on the data hole base and invasion characteristic base. The program-filtering subsystem can be used to filter out invasion of both known and unknown hole attack. These functional modules may be configured and installed to WEB server to protect the system comprehensively.
Owner:四川安盟科技有限责任公司
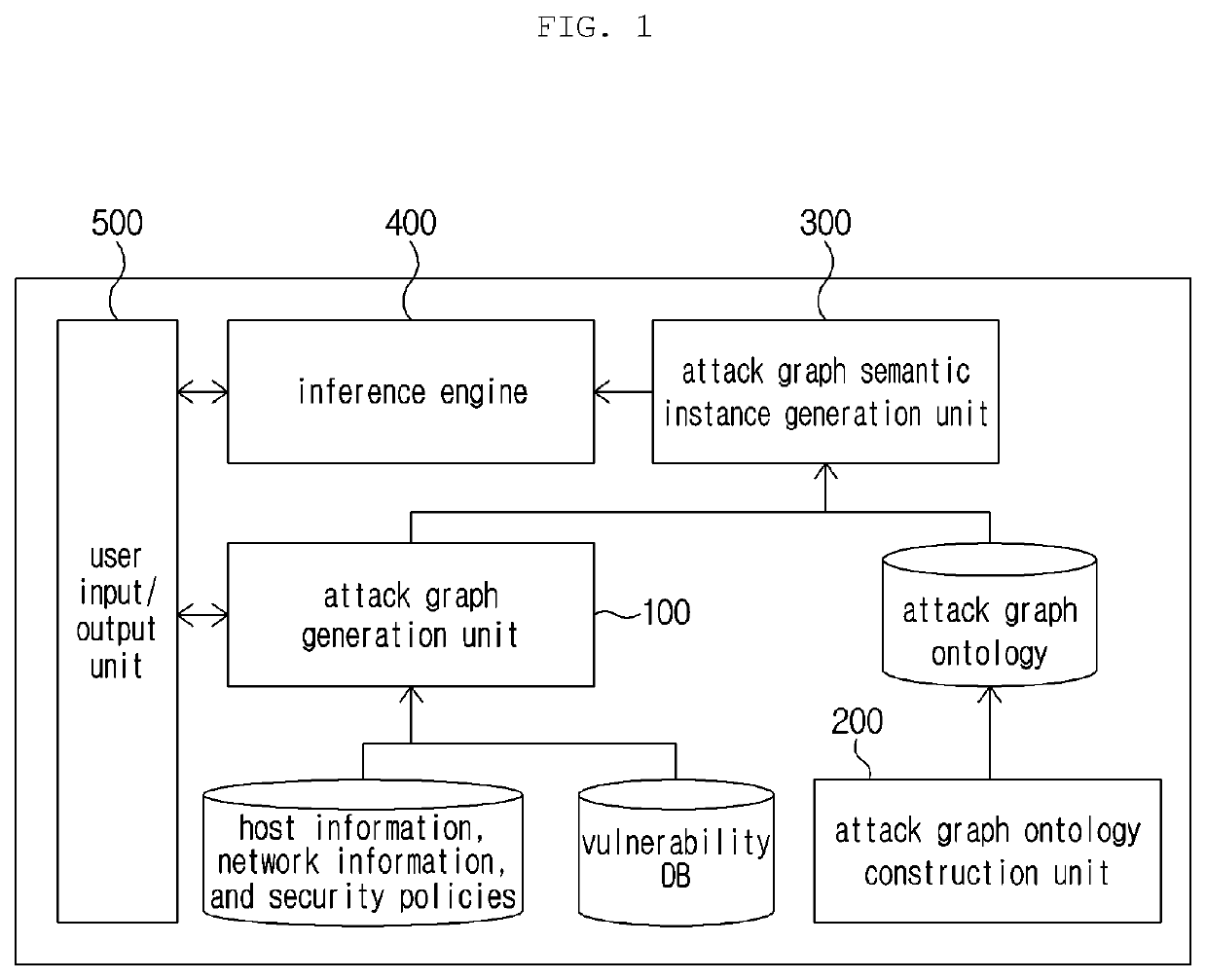
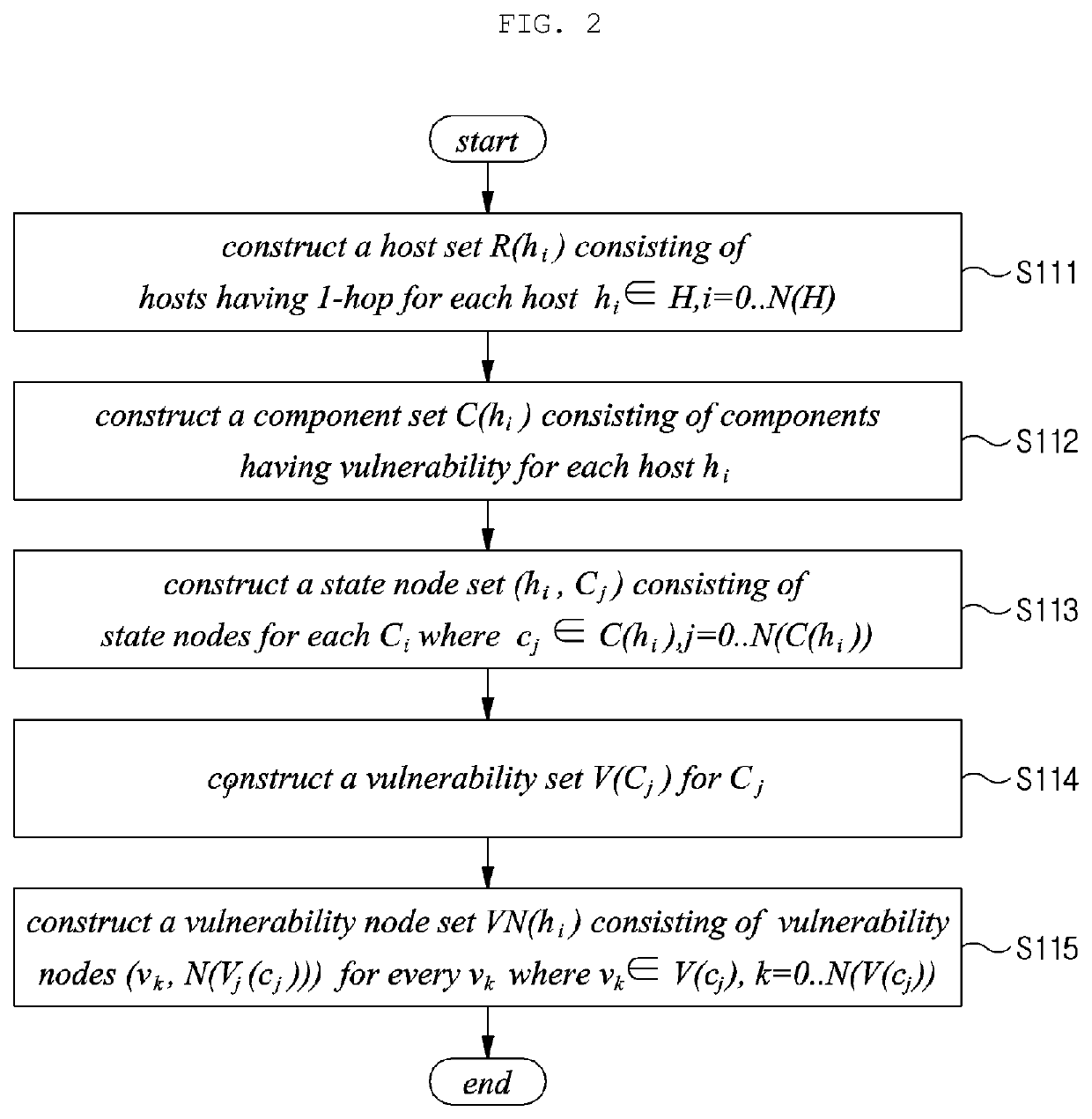
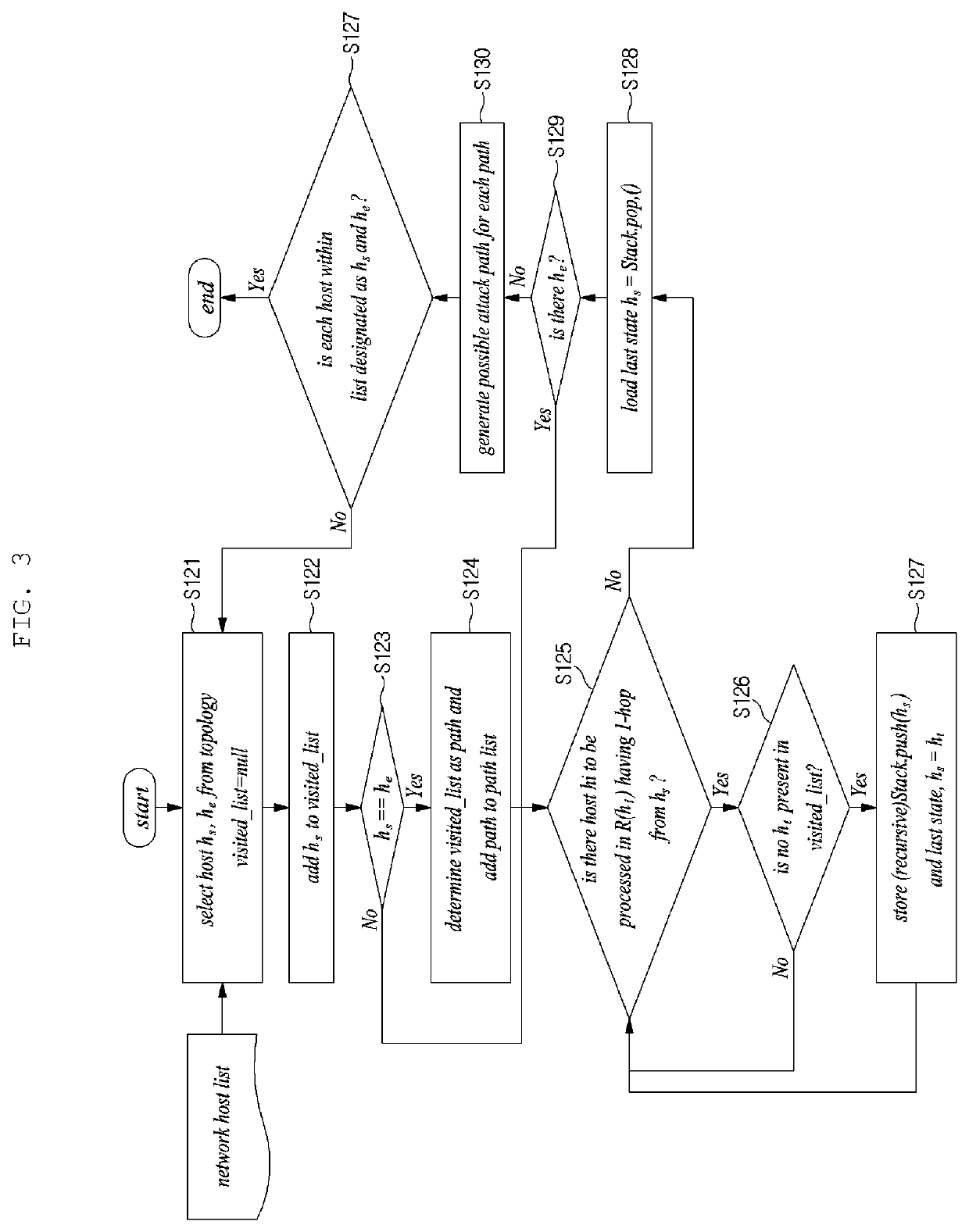
Method and apparatus for generating semantic attack graph
InactiveUS20200099704A1Intuitive informationEfficient identificationData switching networksSpecial data processing applicationsAlgorithmTheoretical computer science
Disclosed are a method and apparatus for searching for an attack path. The apparatus generates an attack graph, generates an attack graph ontology, generates a semantic attack graph by imparting semantics to the attack graph on the basis of the attack graph ontology, and searches for the attack path on the basis of the semantic attack graph.
Owner:ELECTRONICS & TELECOMM RES INST
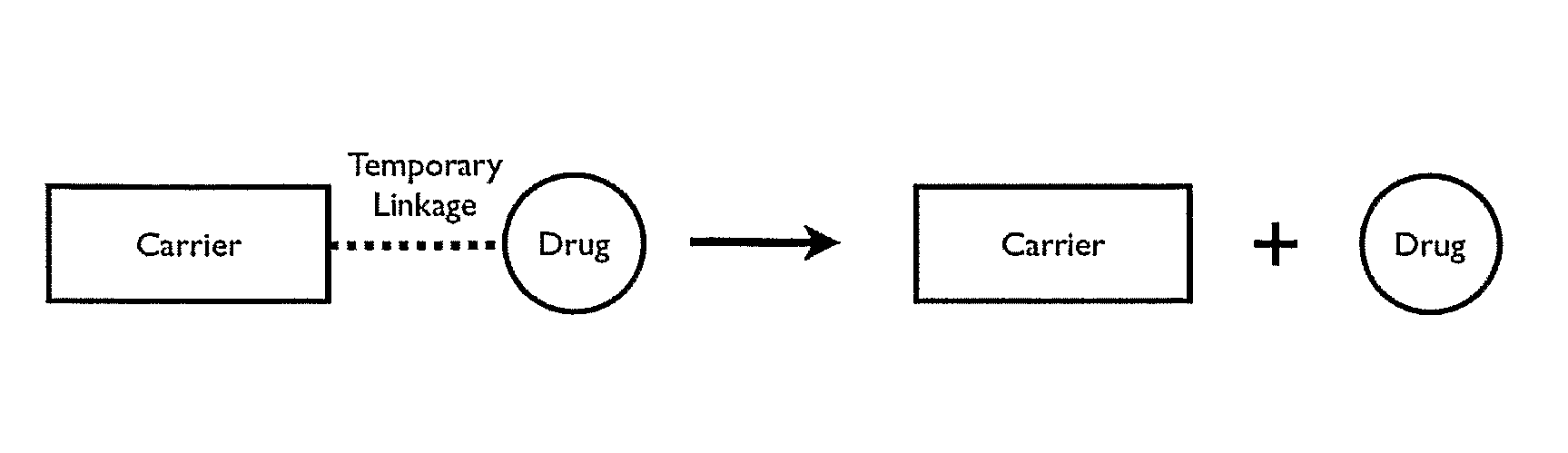
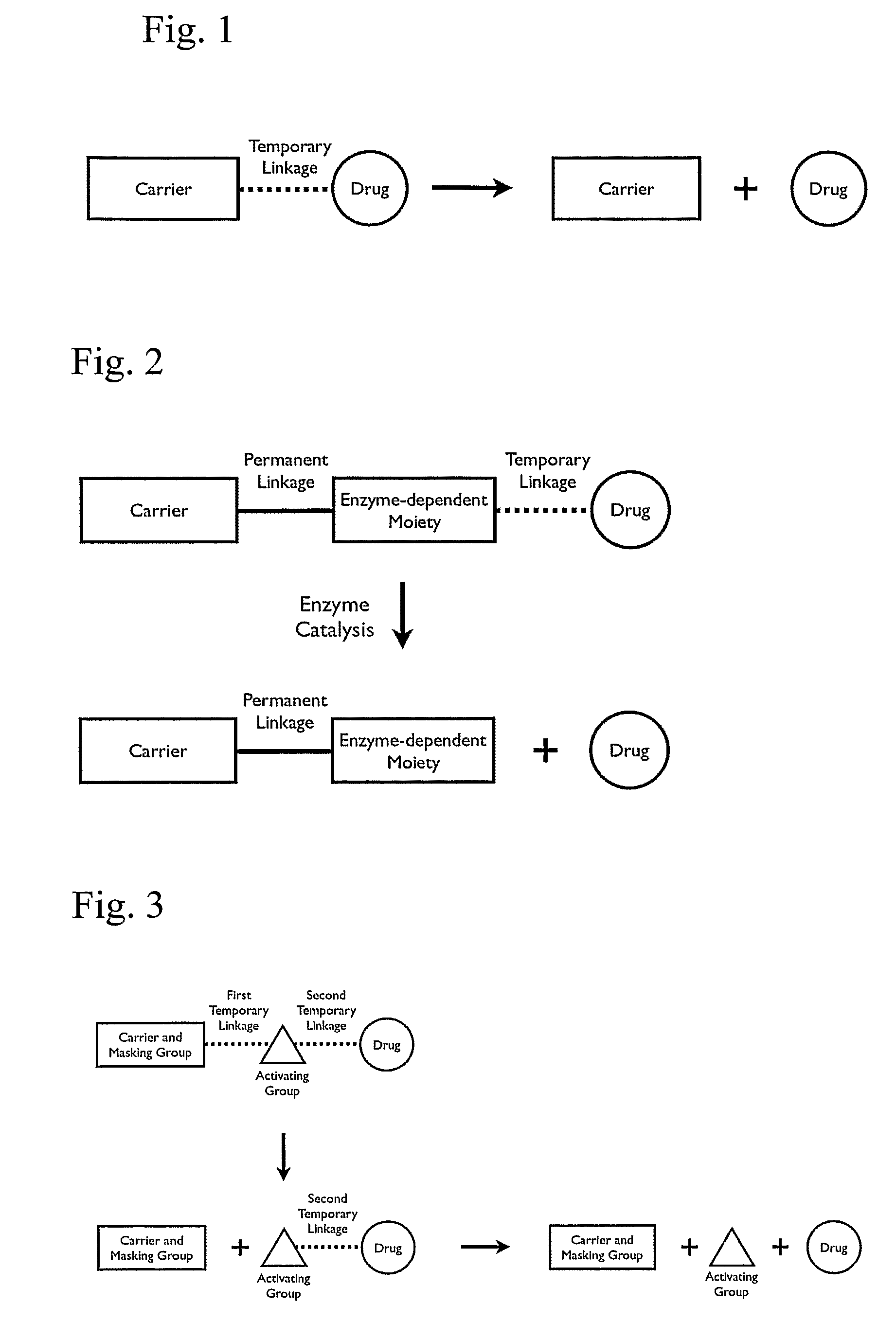
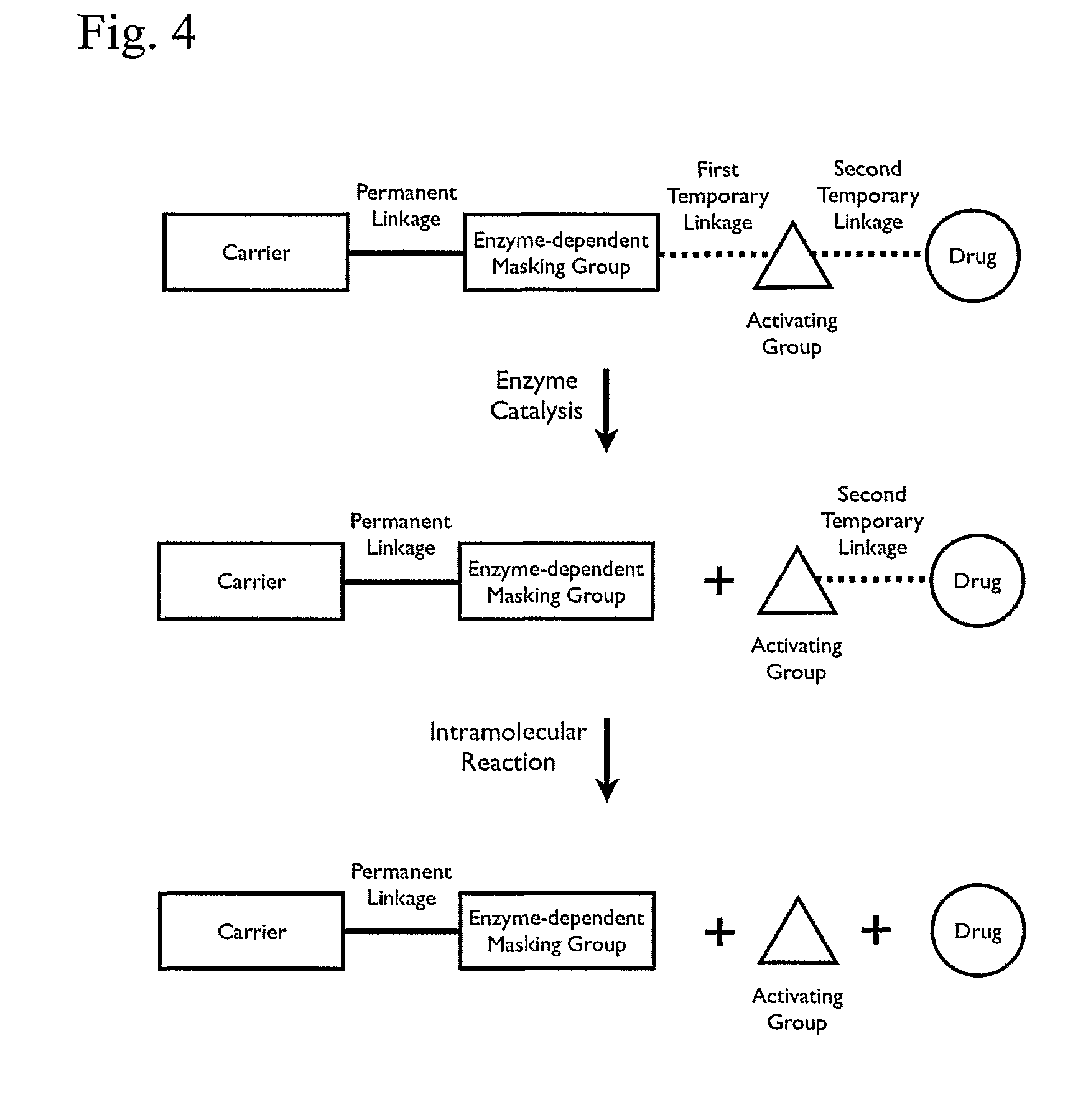
Polymeric prodrug with a self-immolative linker
ActiveUS8377917B2Good predictability and controlLow variabilityBiocideCarbamic acid derivatives preparationPolymeric prodrugMedicinal chemistry
A cascade carrier linked prodrug is described which comprises a biologically active moiety and a masking group having at least one nucleophile and being distinct from the carrier.
Owner:ASCENDIS PHARM GMBH
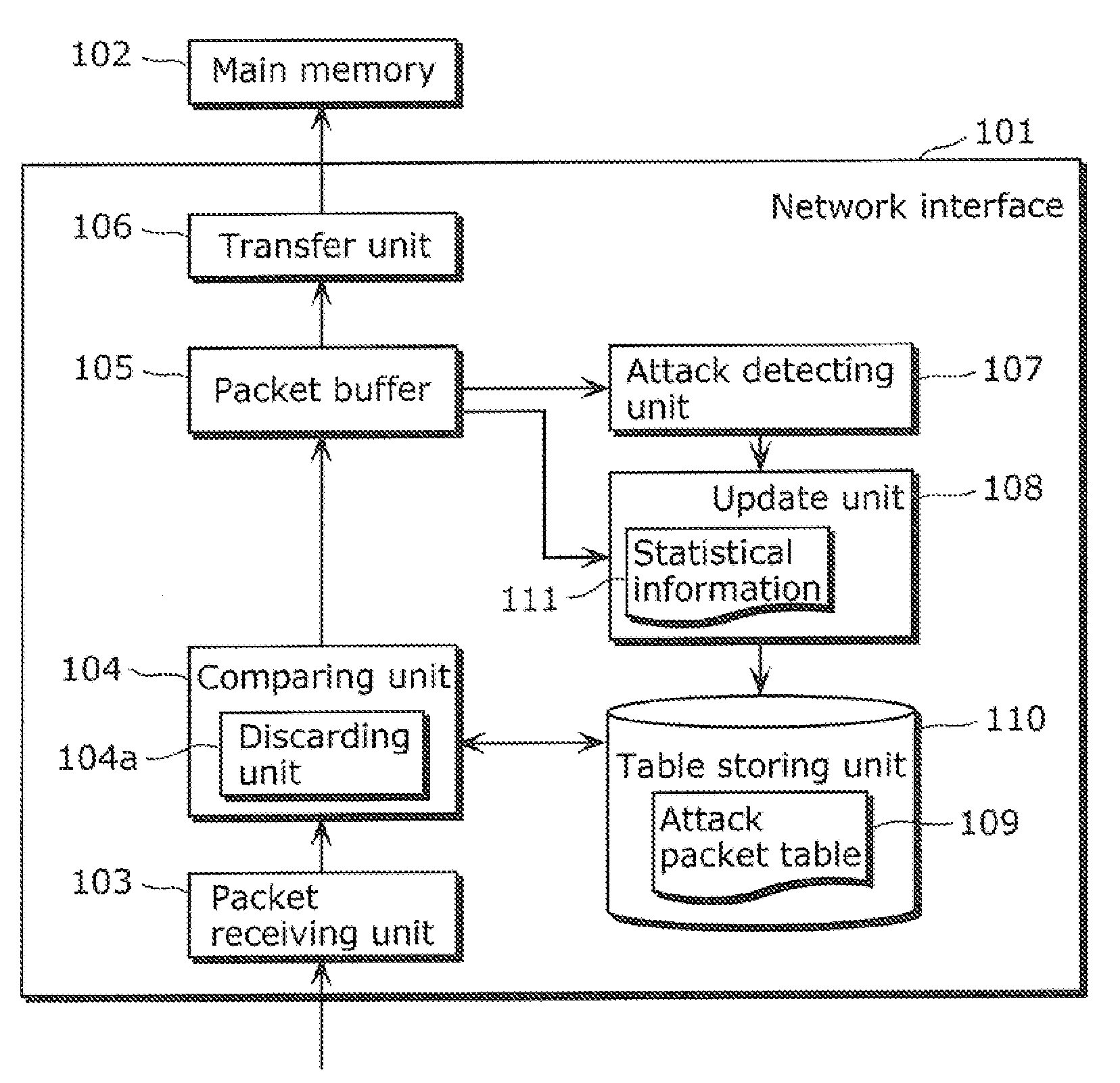
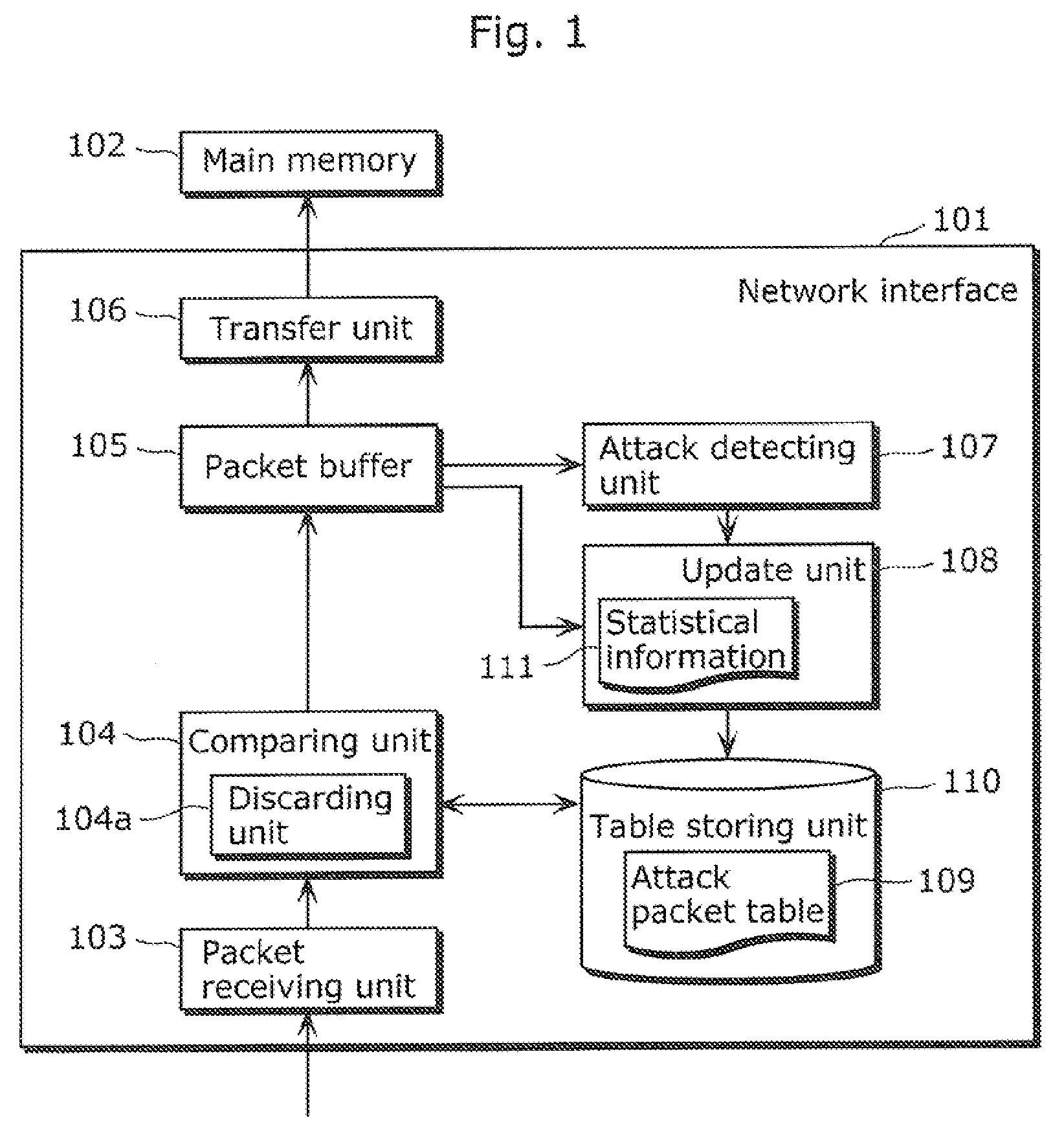
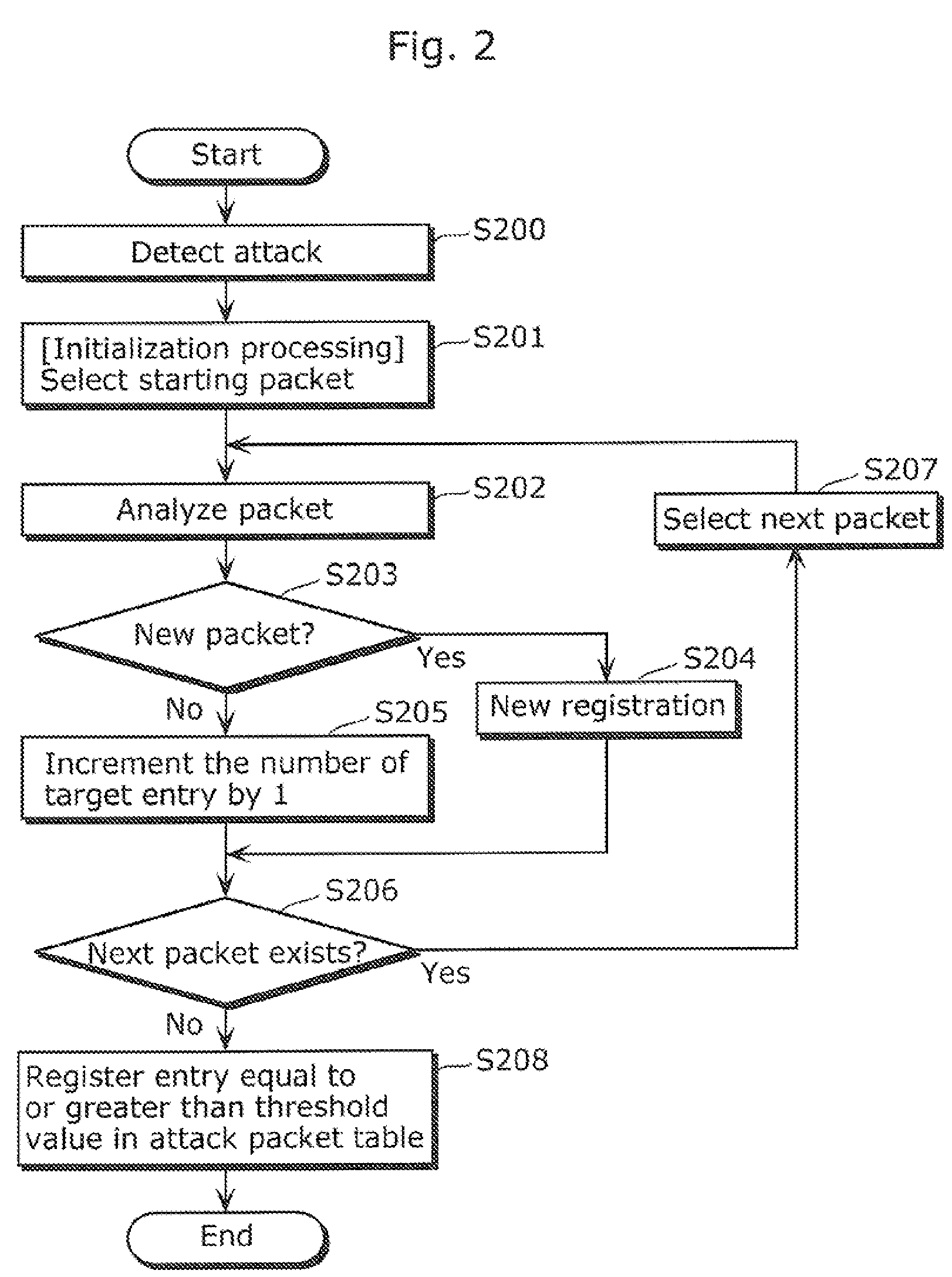
Attack packet detecting apparatus, attack packet detecting method, video receiving apparatus, content recording apparatus, and IP communication apparatus
InactiveUS20110066896A1Efficiently and accurately classifyEfficiently defending attackHardware monitoringNetwork interfaceReal-time computing
A network interface (101) includes: a packet receiving unit (103); a packet buffer (105); and a transfer unit (106) which transfers packets accumulated in the packet buffer to a main memory (102), and further including: an attack detecting unit (107) which detects an attack in which a large number of packets is transmitted, based on an accumulated amount of packets in the packet buffer (105); a table storing unit (110) for storing an attack packet table (109) in which attack packet identification information is registered; an update unit (108) which updates the attack packet table (109), using information obtained from the packets accumulated in the packet buffer; and a discarding unit (104a) which discards the packets received by the packet receiving unit (103) when the packets correspond to the updated attack packet information, before the packets are transferred to the main memory.
Owner:PANASONIC CORP
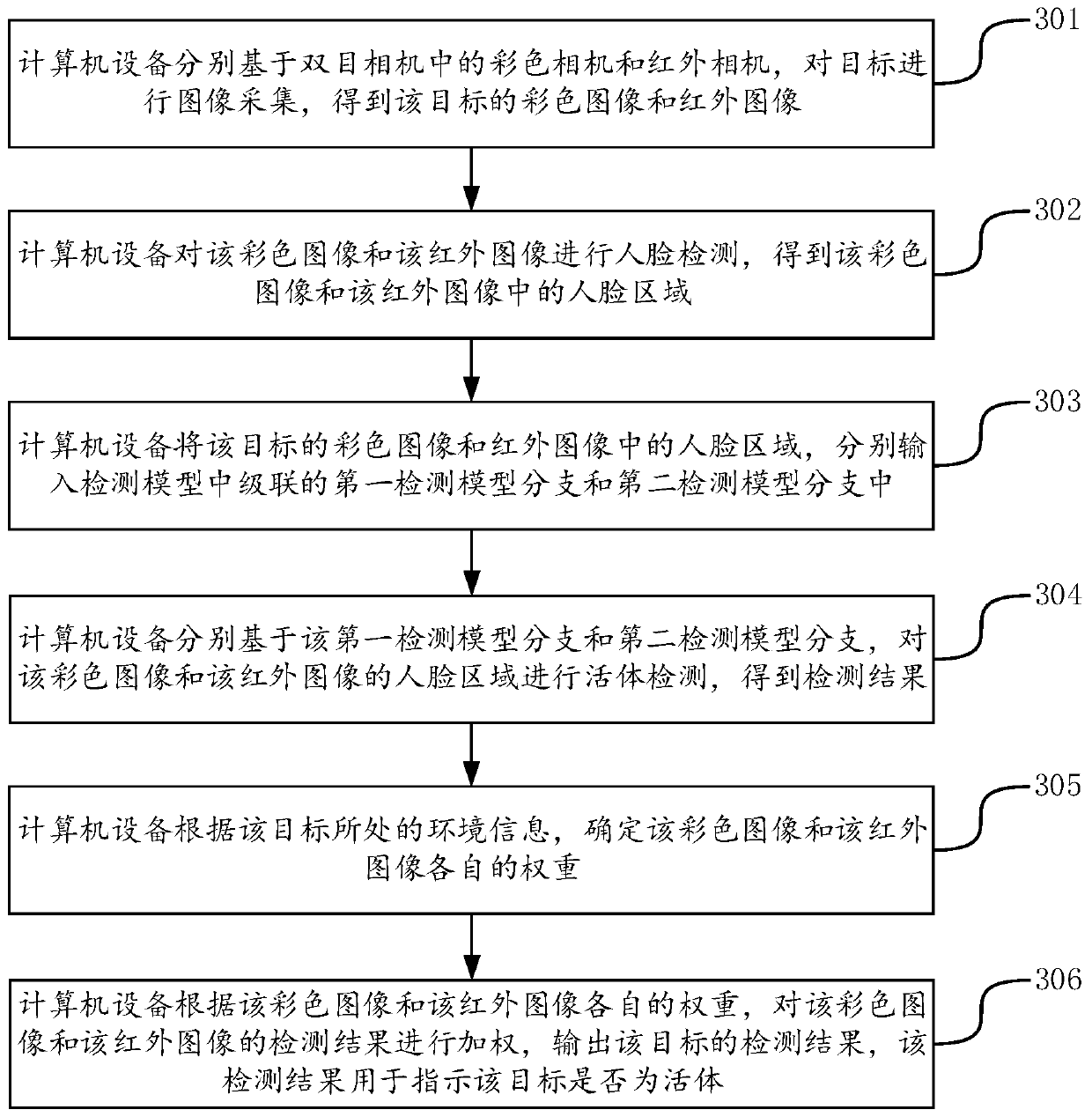
Living body detection method, device and equipment and storage medium
ActiveCN111079576AImprove accuracyEffective attackSpoof detectionColor imageComputer graphics (images)
The invention discloses a living body detection method, device and equipment and a storage medium, and belongs to the technical field of computers. According to the embodiment of the invention, the face areas in the color image and the infrared image of the target are respectively detected through the two cascaded branches in the detection model; whether the target is a living body or not is determined by integrating the detection results of the two images; on one hand, a face region in a color image is detected; according to the method, black-and-white printing and infrared printing images can be effectively defended, detection of a face area in the infrared image is combined, attacks of screen images and color printing images can be effectively defended, and therefore the comprehensive defense effect is achieved, the defense effect is good, practicability is good, and the accuracy of the detection result is good. And on the other hand, different requirements of the two images on theenvironment information are considered in the comprehensive process, and the weight of the two images during combination is determined according to the environment information of the target, so that the accuracy of the detection result obtained by weighting is better, and the defense effect is better.
Owner:TENCENT TECH (SHENZHEN) CO LTD
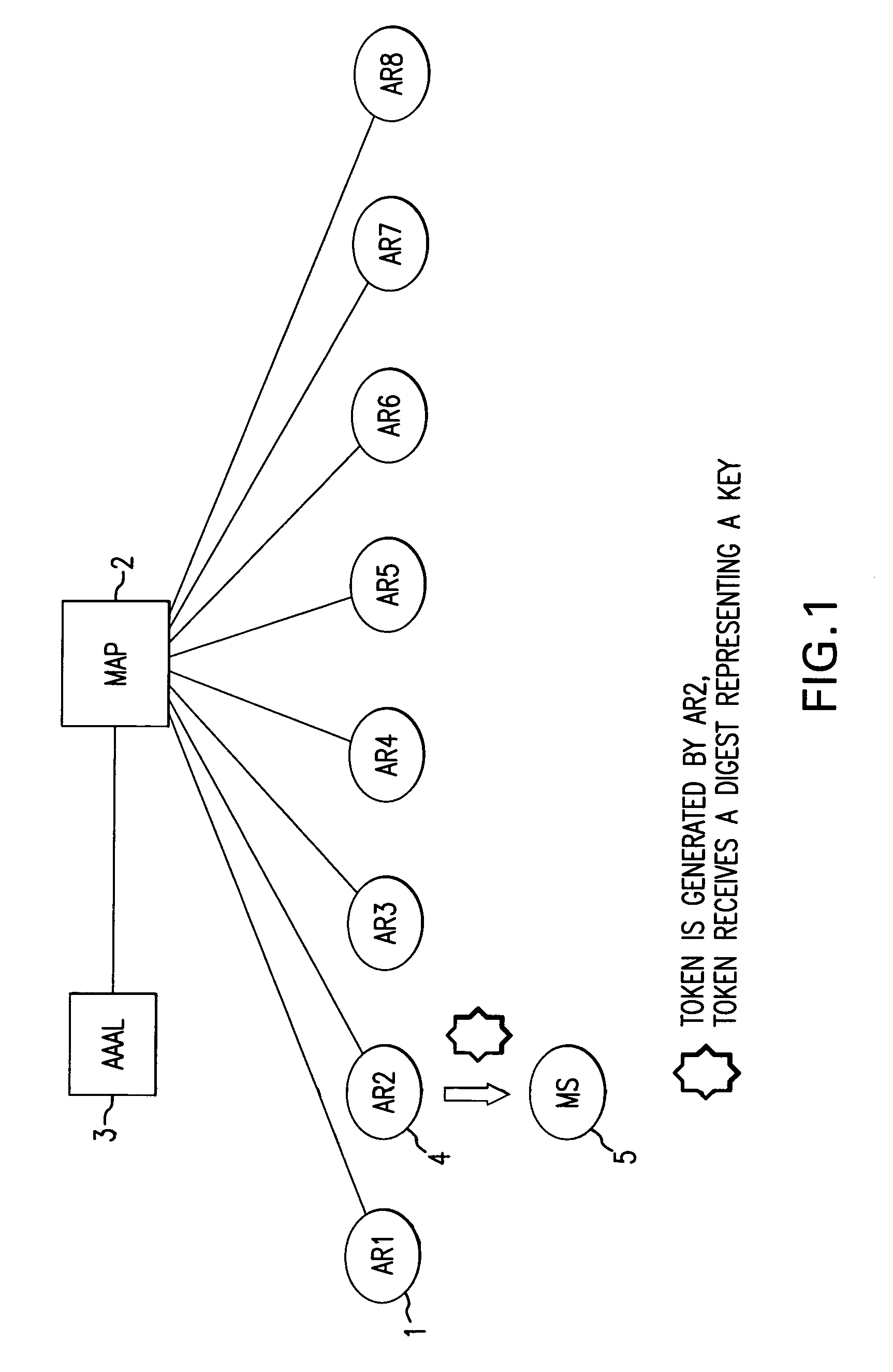
Verifying check-in authentication by using an access authentication token
InactiveUS7171202B2Guaranteed communication performanceEffective protectionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile radioHandover
A simple and efficient means of checking the registration authorization is proposed by the method and the device for checking the registration authorization prior to the start of the re-registration process based on a registration query from a mobile radio terminal to at least one access device for an intra-domain handover in a mobile communication network. In the network, a token which has been sent by an access device to a mobile radio terminal and has been stored in at least one trust table of at least one access device, is received by at least one further access device during a registration query from a mobile radio terminal and compared with tokens stored in at least one trust table prior to the start of the registration for the purpose of verifying the registration authorization, and the registration is started if an authorization is present.
Owner:SIEMENS AG
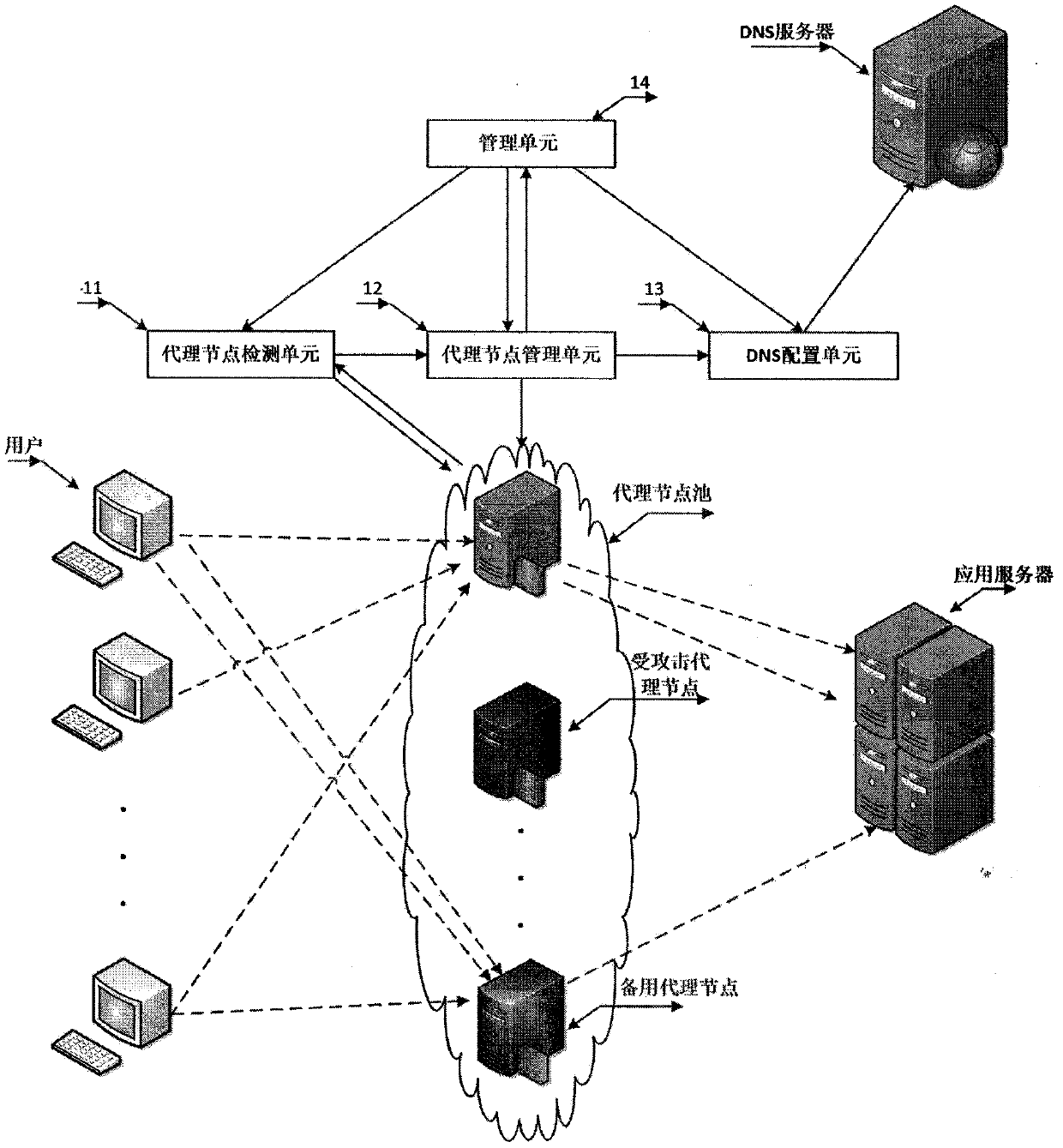
DDoS attack defense system and method based on dynamic transformation
The invention provides a DDoS attack defense system and method based on dynamic transformation, which break through the characteristics of traditional passive defense and static defense. The method has the basic thought that: under normal flow, a small number of proxy nodes are adopted to transmit communication between a user and an application server, so that normal communication requirements aremet, and resources are saved; and when a DDoS attack is received, a large number of dynamic proxy nodes are started to transmit communication between the user and the application server, the standbyproxy node is continuously used for replacing the attacked proxy node, the user flow is migrated to the new proxy node, and the attacked proxy node is closed, so that the DDoS attack strength is rapidly reduced, and the purpose of defending against large-flow attacks with small bandwidth is achieved. In addition, the dynamic change of the proxy node enables the attacker not to obtain the internalnetwork topology structure of the system, so that the scanning detection of the attacker on the system can be effectively blocked. The system does not increase user load, is transparent to users, andprovides continuous and stable service for the users.
Owner:北京卫达信息技术有限公司
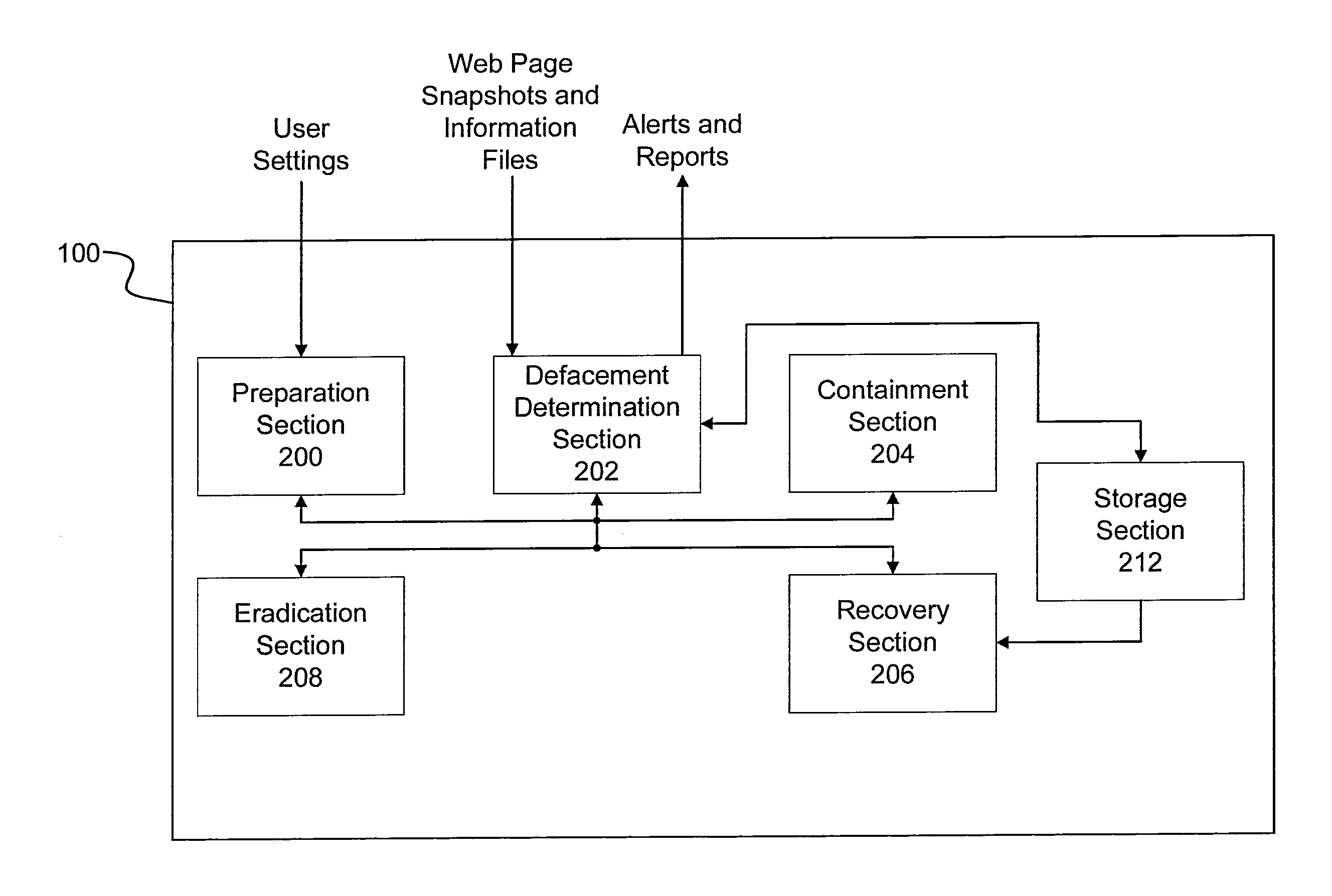
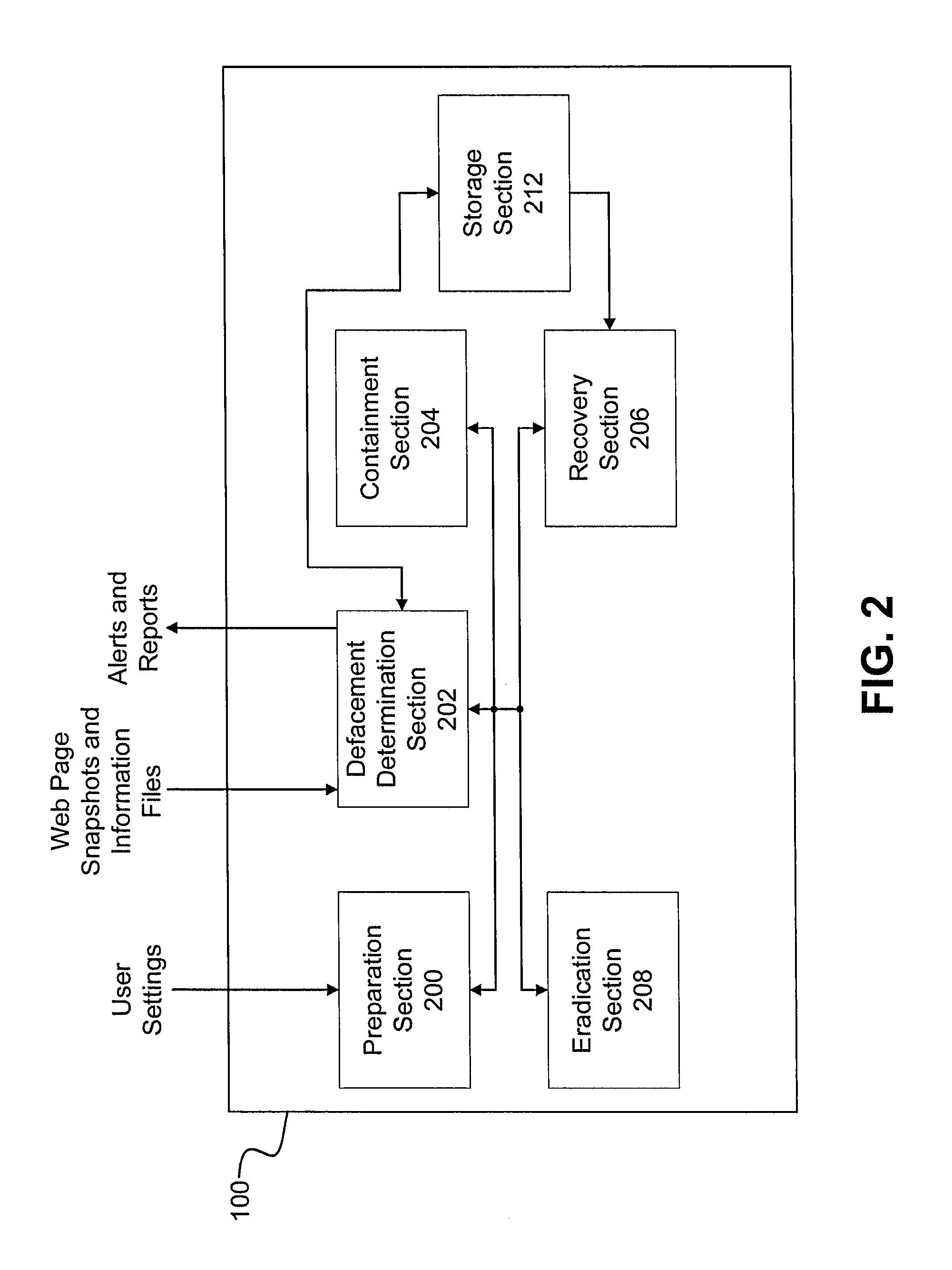
Website defacement incident handling system, method, and computer program storage device
InactiveUS20130097702A1Effective attackMemory loss protectionError detection/correctionWebsite defacementHandling system
A website defacement incident handling system and associated methodology and non-transitory computer program storage device for detecting a defacement of a website and taking appropriate corrective action upon detection of the defacement. The website defacement incident handling system receives web page information and snapshot images corresponding to websites and performs comparisons against corresponding information and snapshot images of a reference website. Probability scores indicating the likelihood that a website has been defaced are calculated based on the comparisons and corrective actions are taken as appropriate to protect the affected website.
Owner:ALHAMED MOHAMMED +1
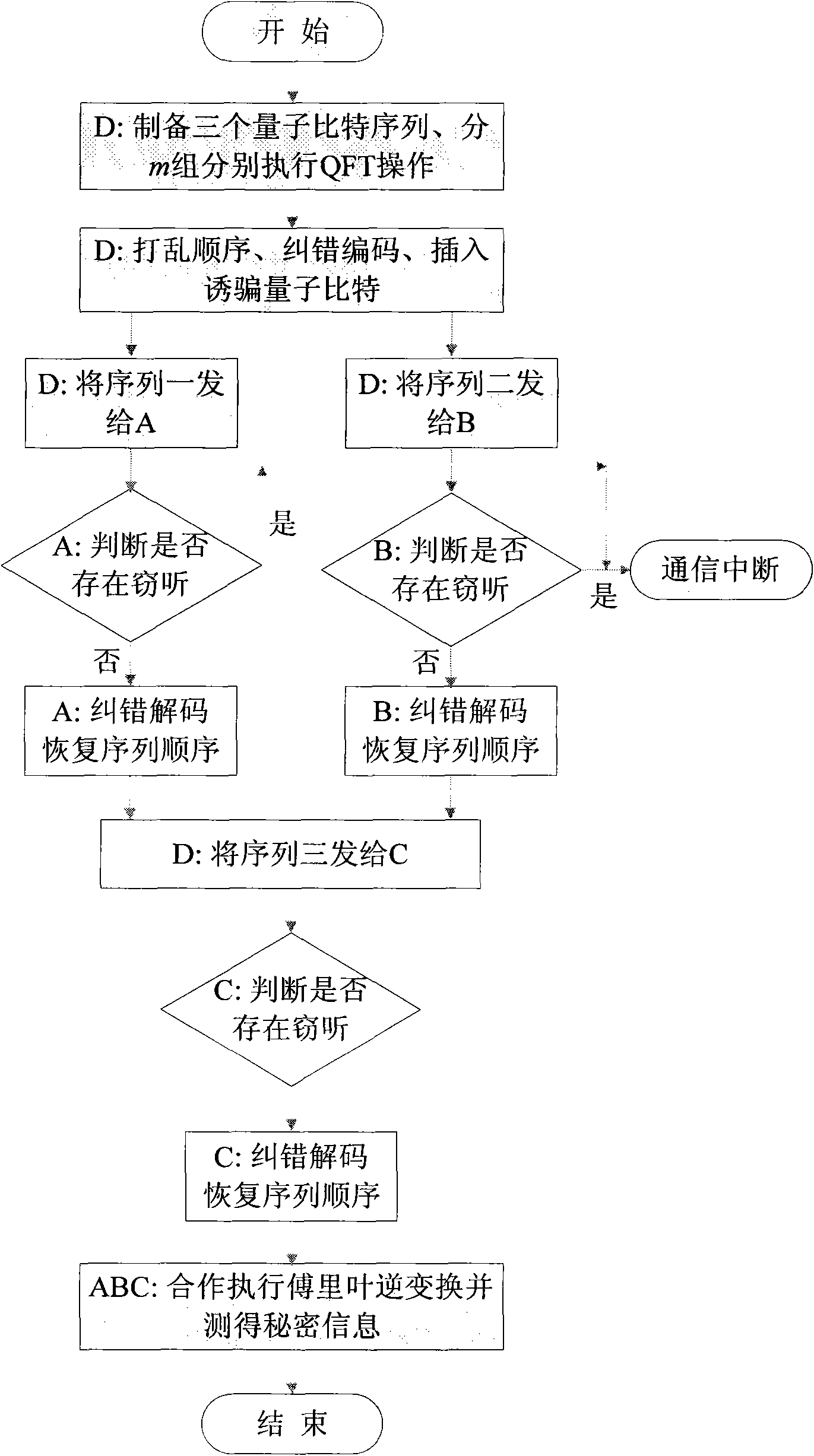
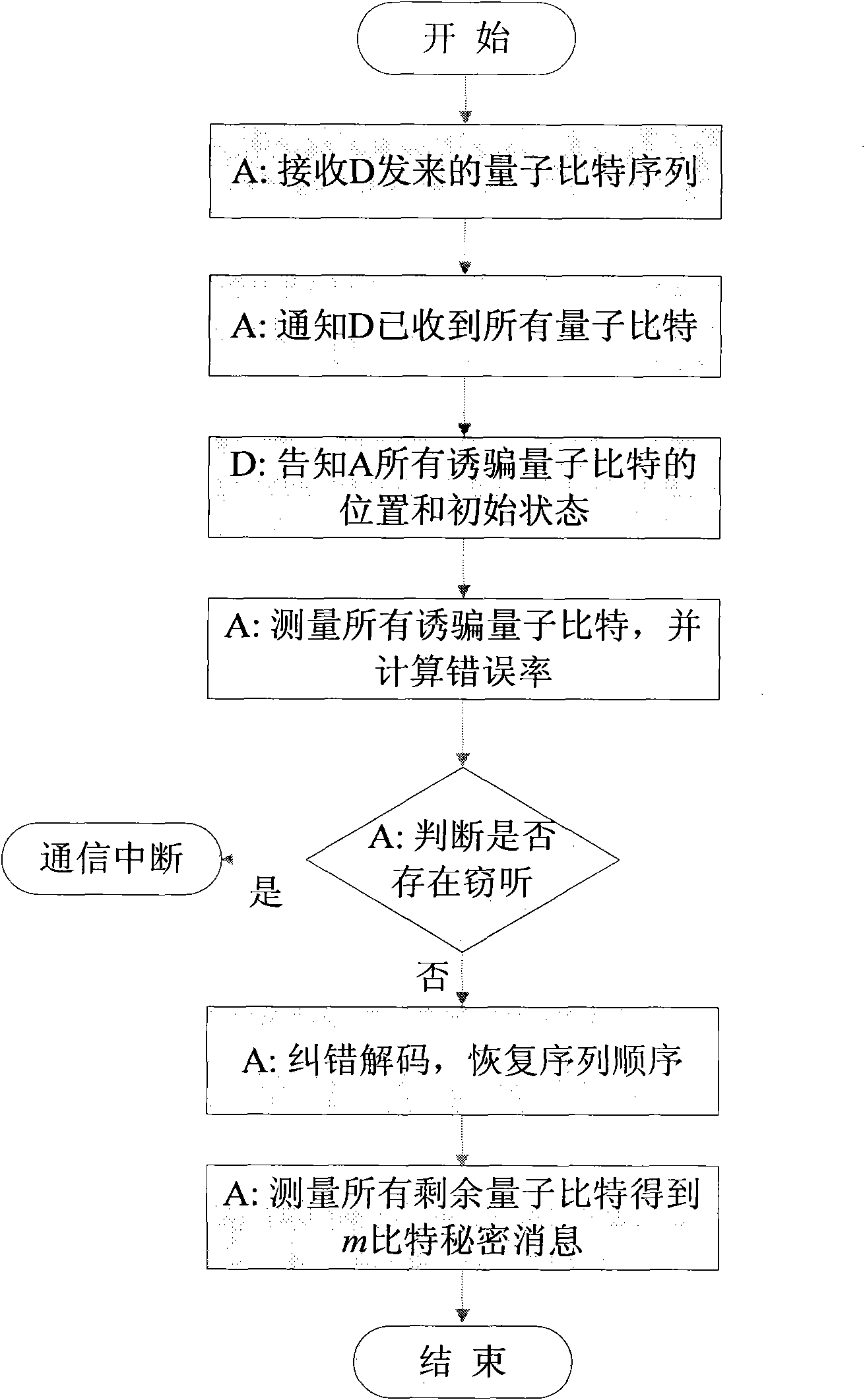
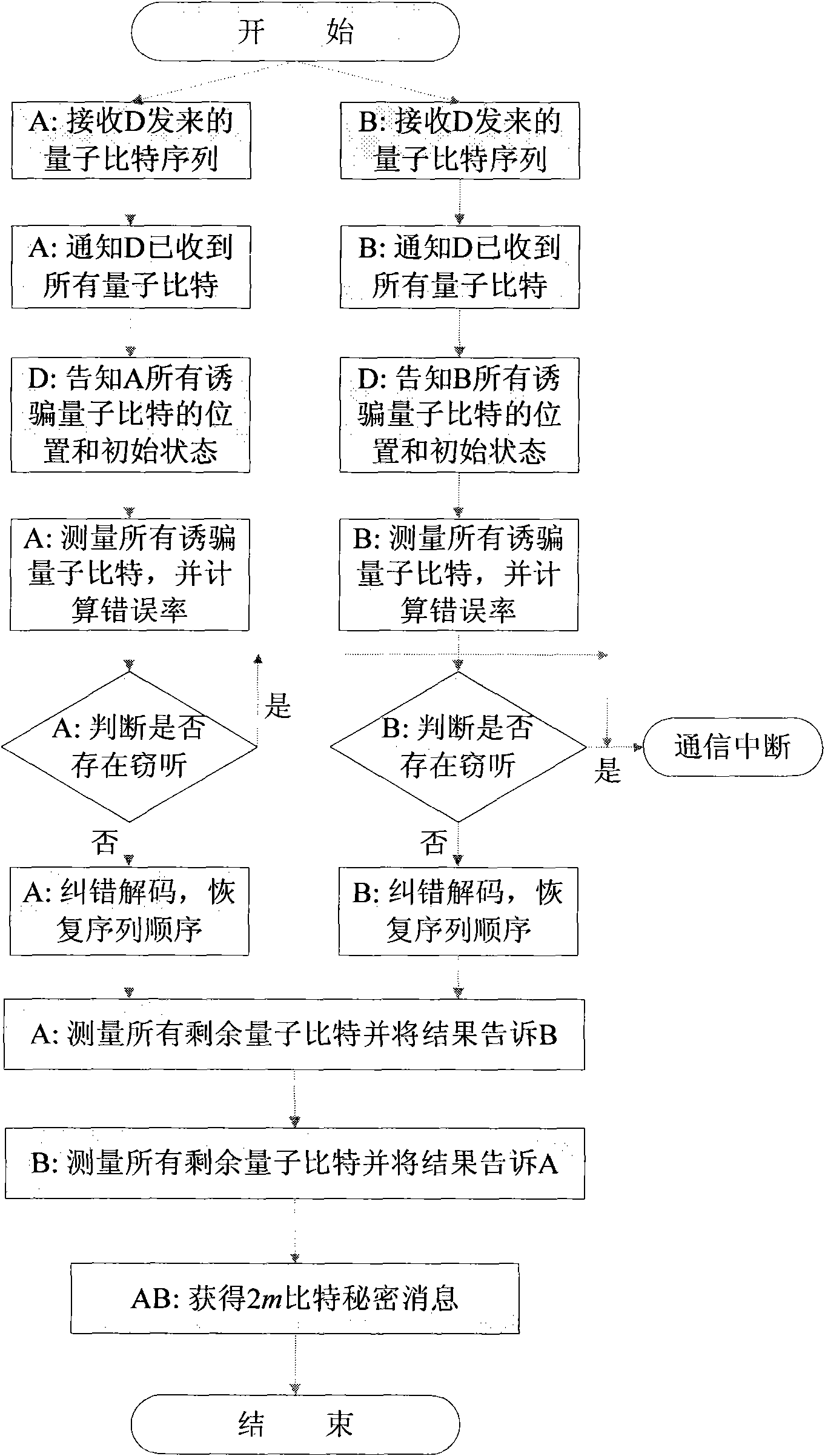
Method for attacking Fourier transform quantum secret sharing systems
InactiveCN101931528AEffective attackKey distribution for secure communicationSecret communicationComputer hardwareQuantum secret sharing
The invention discloses a method for attacking Fourier transform quantum secret sharing systems, and relates to quantum secret communication technology. In the method, a specific measurement base is utilized to perform single particle measurement on the information carrier quantum bit, and partial secret messages are acquired according to a measurement result. According to the quantum-mechanical nature, due to the selection of the measurement base, the state of the measured quantum bit is just the eigen state of the measurement base, and the quantum state after measurement cannot be changed at all. The method can make a dishonest agent independently obtain partial key information, also can make several cooperated agents obtain more key information, and cannot introduce any error for normal communication so as not to be discovered by other users. The invention provides a method for effectively attacking the Fourier transform quantum secret sharing systems, which is simultaneously an effective method for testing the safety of the Fourier transform quantum secret sharing systems.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Attack studying and judging method and system for network attack and defense test platform and medium
ActiveCN111741023AImprove accuracyAutomatic responseTransmissionSpecial data processing applicationsAttackTheoretical computer science
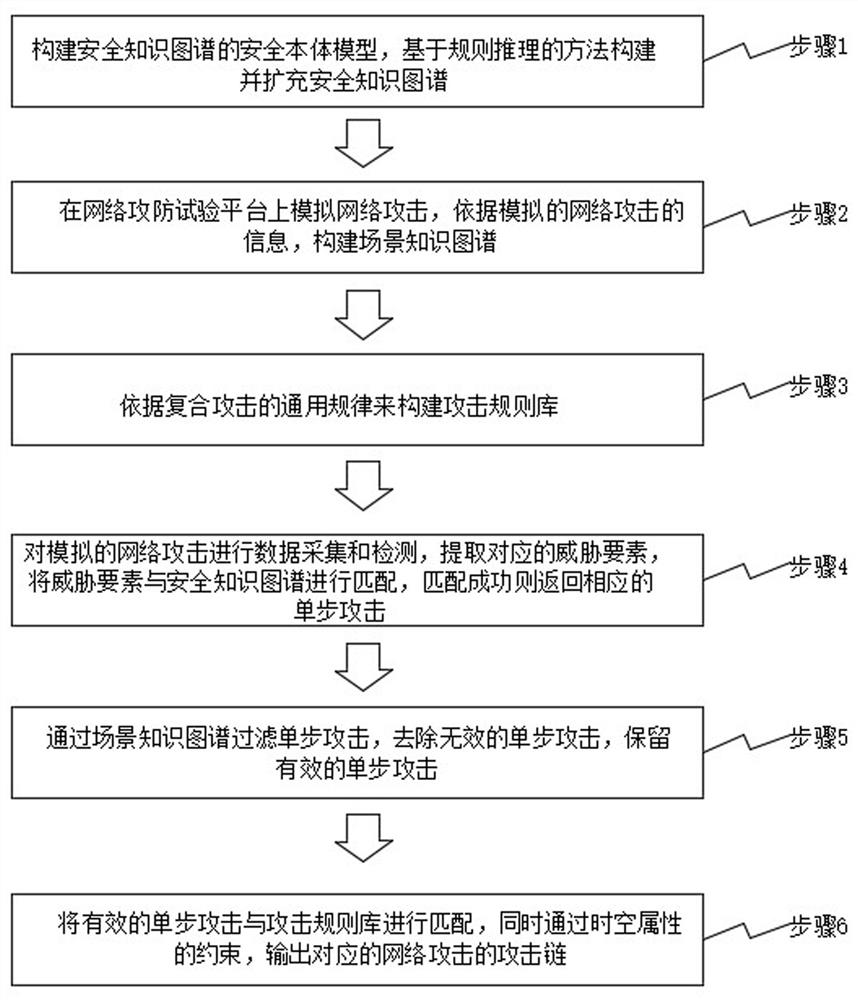
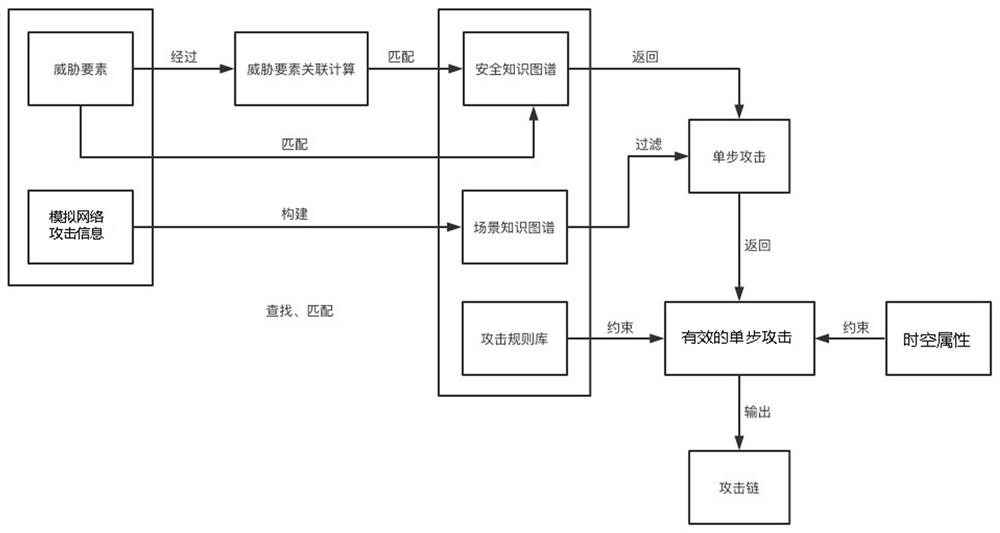
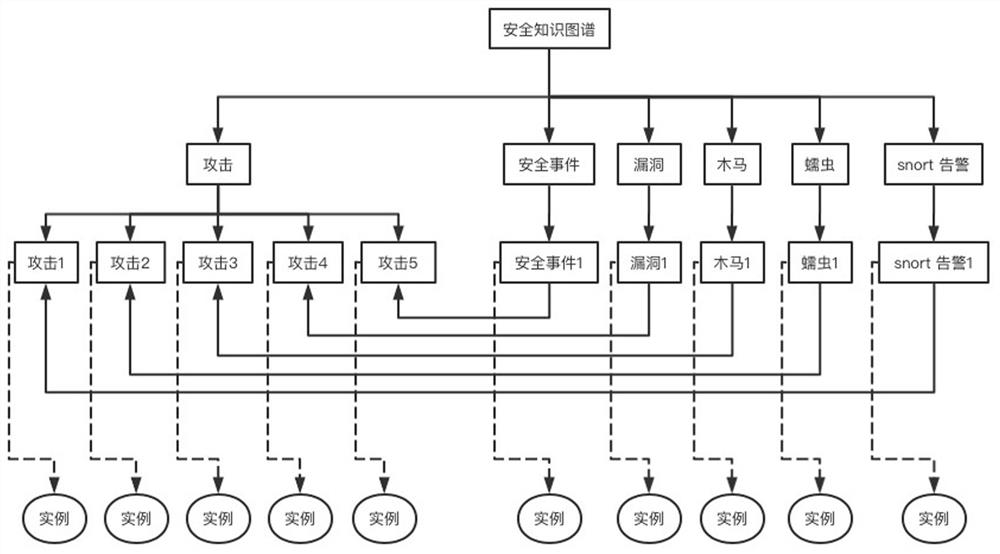
The invention provides an attack studying and judging method and system for a network attack and defense test platform and a medium, which can effectively improve the accuracy of studying and judgingcomposite attacks, and the method comprises the following steps: constructing a security ontology model of a security knowledge graph, and constructing and expanding the security knowledge graph basedon a rule reasoning method; simulating network attacks on the network attack and defense test platform, and constructing a scene knowledge graph according to information of the simulated network attacks; constructing an attack rule base according to the general rule of the composite attack; performing data acquisition and detection on the simulated network attack, extracting corresponding a threat element, matching the threat element with the security knowledge graph, and returning the corresponding single-step attack if the matching succeeds; filtering single-step attacks through the scene knowledge graph, removing invalid single-step attacks, and reserving effective single-step attacks; and matching the effective single-step attack with an attack rule base, and outputting an attack chain of the corresponding network attack through the constraint of the space-time attribute.
Owner:NAT UNIV OF DEFENSE TECH
Global navigation satellite system (GNSS) navigation solution generating apparatus and method
ActiveUS20160223678A1Attack can be efficiently overcomeEffective attackPosition fixationSatellite radio beaconingMarine navigationCalculator
Provided is a global navigation satellite system (GNSS) navigation solution generating apparatus and method, the apparatus including a determiner to determine that a spoofing signal exists in a received GNSS signal when a signal having a receiving intensity greater than a predetermined receiving intensity of a normal signal by a predetermined value range is included in the received GNSS signal, a detector to re-detect the normal signal from the GNSS signal when the spoofing signal is determined to exist, and a calculator to generate a GNSS navigation solution by tracking the re-detected normal signal, wherein the predetermined value range is 3 to 5 decibels (dB).
Owner:ELECTRONICS & TELECOMM RES INST
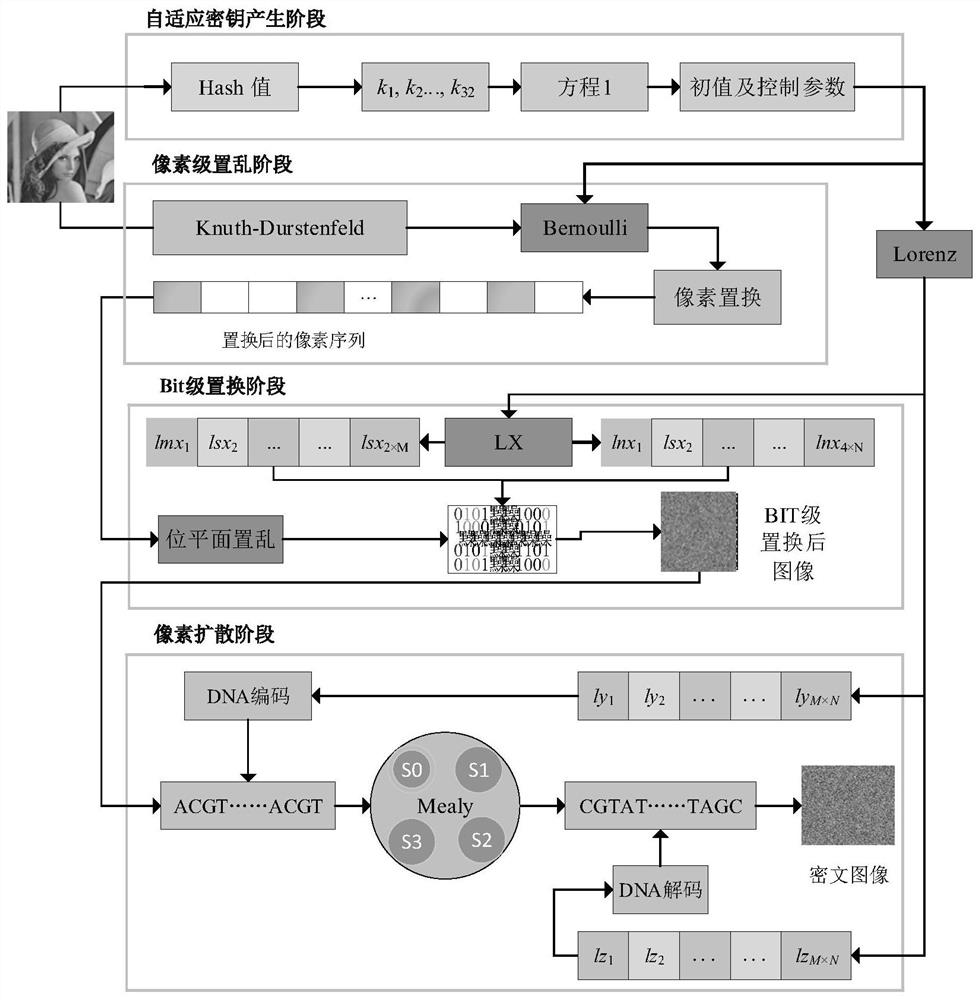
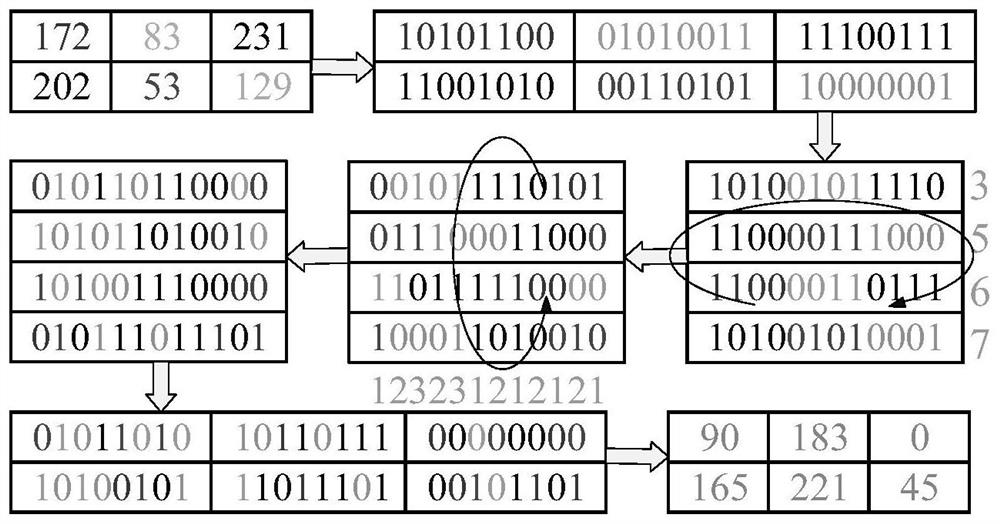
Image encryption method based on chaotic sequence and DNA coding
ActiveCN113225449AEfficient scramblingImplement bit-level obfuscationUser identity/authority verificationSecuring communication by chaotic signalsCiphertextTheoretical computer science
The invention provides an image encryption method based on a chaotic sequence and DNA coding. The method comprises the following steps: calculating a hash value of an image matrix converted from a grayscale image, and updating an initial value of a chaotic system; generating a sequence according to a control parameter of the Bernoulli shift mapping and the updated initial value, wherein the sequence is used as a random value of a Knuth-Durstenfeld shuffling method, and scrambling is carried out on the random value of the Knuth-Durstenfeld shuffling method; carrying out iteration on the Lorenz chaotic system to obtain three sequences; intercepting elements as bits of cyclic shift to perform bit-level scrambling, wherein elements in the sequence are used for selecting codes as a DNA sequence according to a DNA coding rule; performing state conversion by using a Mealy state machine to obtain a new DNA sequence, wherein elements in the sequence are used for DNA coding rule selection for DNA decoding, and a ciphertext image is obtained. According to the method, the randomness of chaos and the nonlinearity of DNA coding and Mealy state conversion are fully utilized, the correlation of adjacent pixels of the image is effectively eliminated, and the security of the ciphertext image is improved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Process for preparing fine particle dispersion for wood preservation
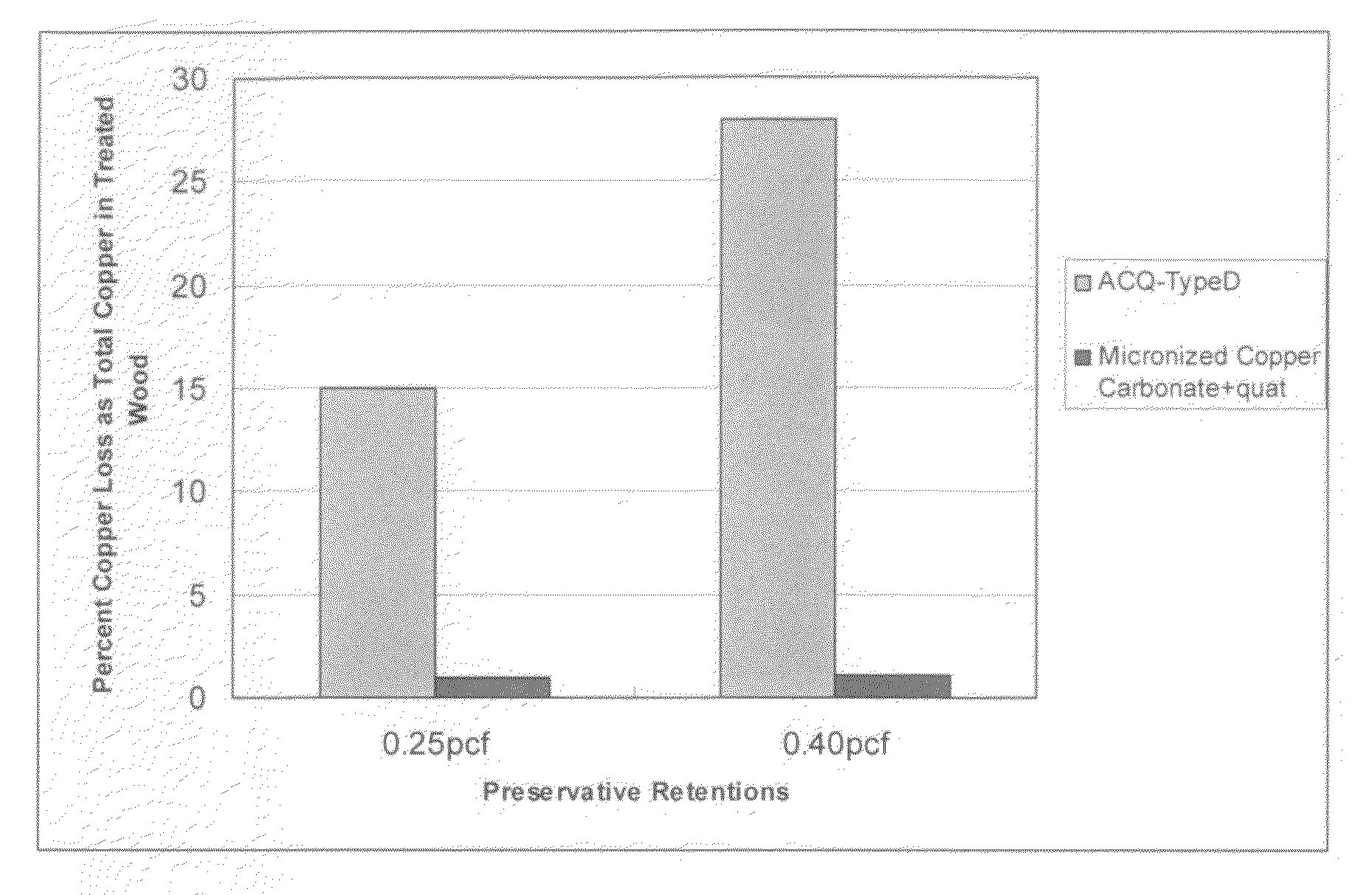
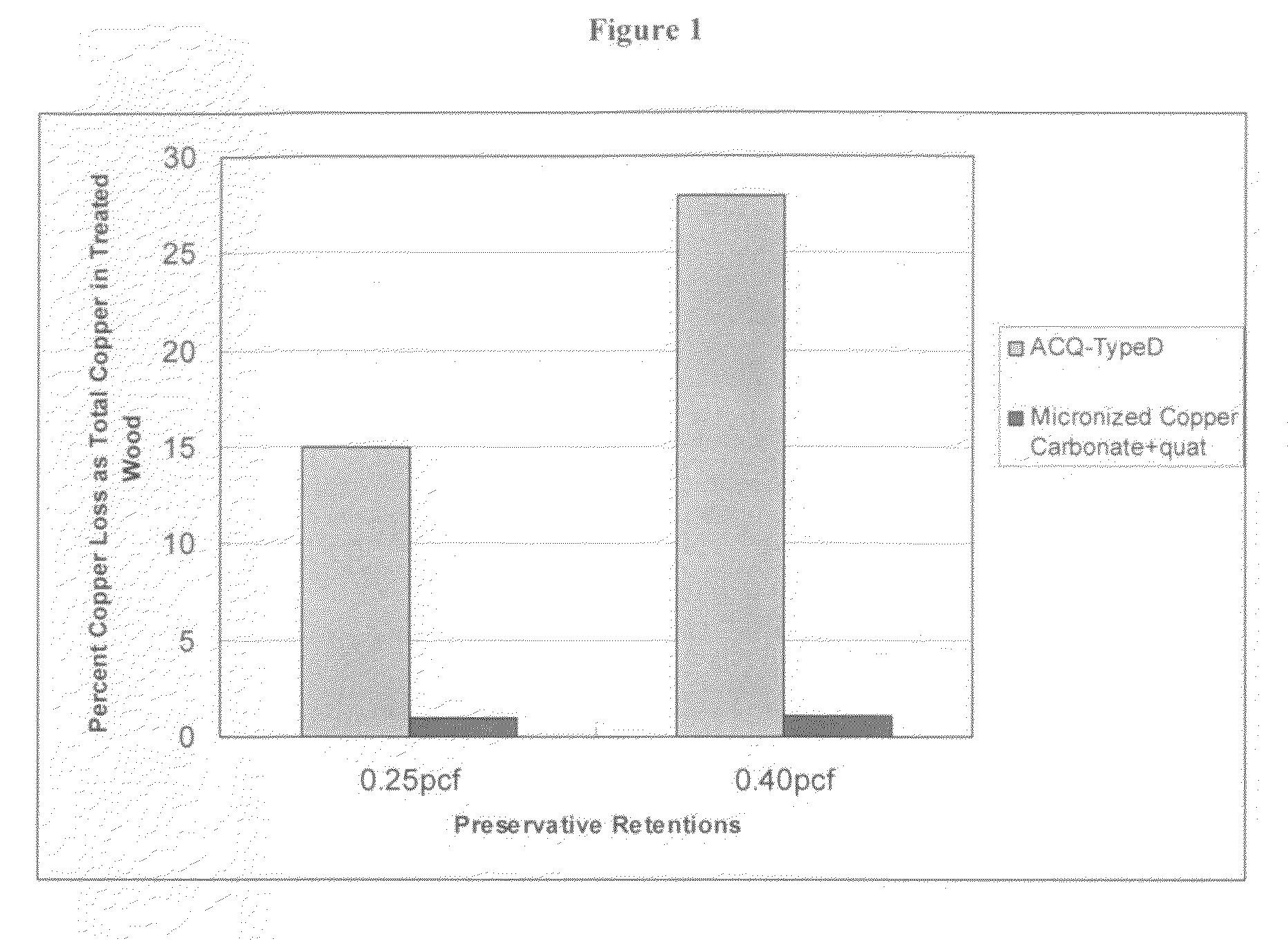
The present invention provide a method for producing micronized solid particles through a two-step process. The solid particles of the invention comprise metals or metal compounds, especially copper and copper compounds. The solid particle of the invention further comprise organic biocides. The invention further provides a wood preservative composition and wood comprising the solid particles of the invention, which may be diluted to the target concentration with or without addition of a co-biocide and vacuum / pressure impregnated into a variety wood species including refractory wood species to effectively preserve the material from fungal and insect attack.
Owner:KOPPERS PERFORMANCE CHEM
anonymous user authentication method for a crowd sensing Internet of Things based on chaotic mapping
ActiveCN109756893ADefense against stealing attacksSecurity requirements haveUser identity/authority verificationSecurity arrangementUser needsPassword
The invention discloses an anonymous user authentication method for a crowd sensing Internet of Things based on chaotic mapping, and relates to an anonymous user authentication method for the crowd sensing Internet of Things. The invention aims to solve the problems that the existing user authentication method is difficult to realize the resistance of various typical attacks and the calculation cost or the communication cost is relatively high. The method comprises the following steps: 1, a user is registered; 2, after the user is registered, the user logs in; When the user logs in, if the network is found to have an attack of stealing the smart card, the step 5 is executed; When the user logs in, if the network is not found to have the attack of stealing the smart card, executing the step3; 3, after the user logs in, the user and the server carry out bidirectional authentication, a secret key between the user and the server is established, and after the secret key is established, ifthe user needs to change the password, the step 4 is executed; If the user does not need to change the password, ending; 4, the user changes the password; And 5, the stolen smart card is removed. Themethod is applied to the field of crowd sensing internet of things anonymous user authentication.
Owner:HEILONGJIANG UNIV
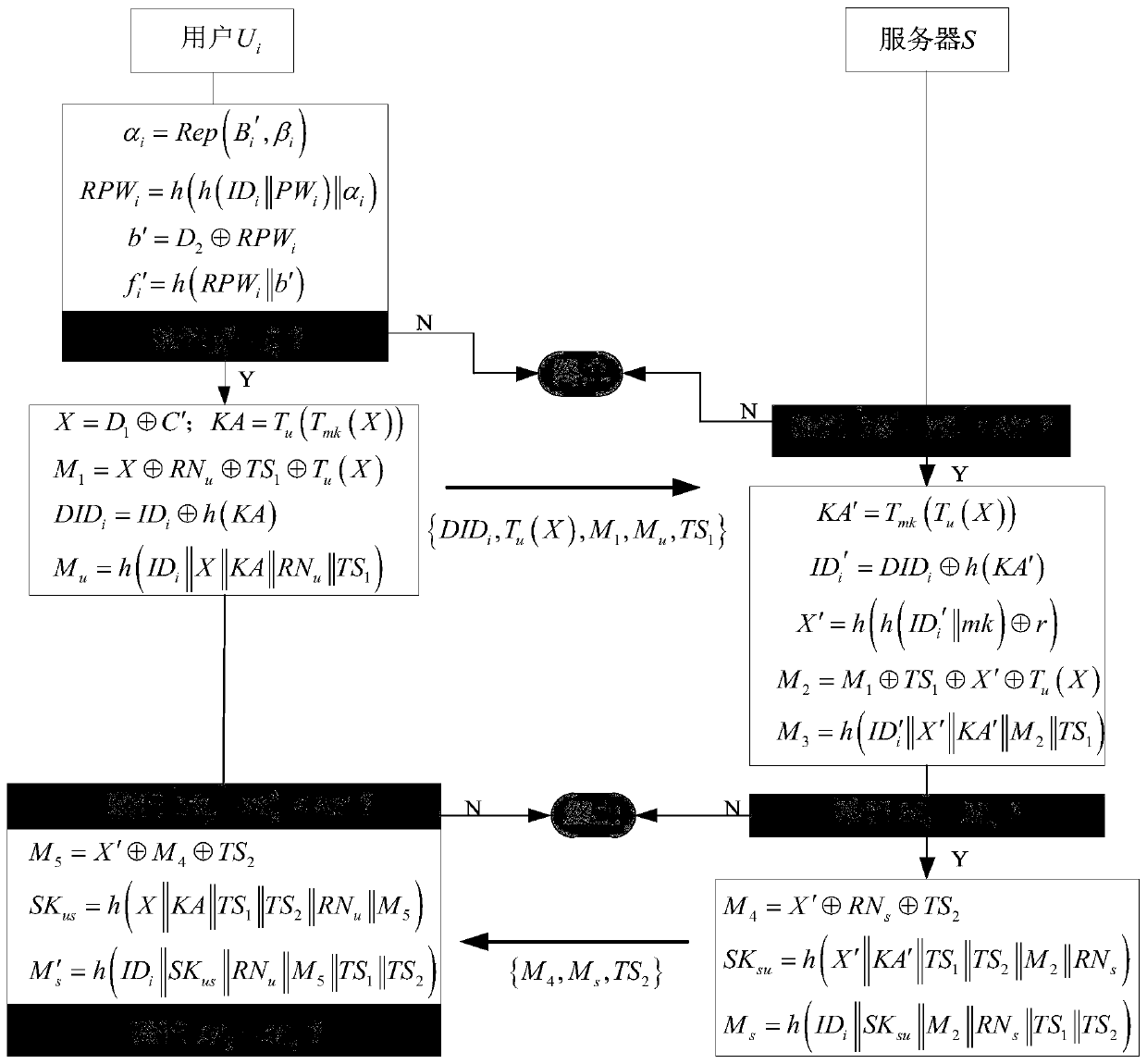
A flood request attaching filtering method based on the stateless of open source core
The invention relates to an open source kernel based filtration method of stateless flooding request attacks, which comprises the following steps: the rule list of the filtration of an open source firewall is initialized to generate a white list and a blacklist; a main control module distinguishes and processes the request message and the reset message respectively; the Cookie value of the request message is calculated and is added to a text document library, and a confirmation message is sent back to the message origin; as for the reset message, the confirmation number value thereof is extracted and searched in the text document library after being subtracted by one; a text document library maintenance module deletes the expired information record in every interval t, and informs a firewall operation module to add the address of the origin to the blacklist; the firewall operation module gathers list items when the number of the list items in the white list or the blacklist are very large; after giving the command of filtration stopping, the firewall module needs to empty all the lists and stop the function of a kernel filtration module, and the filtration method is ended. The adoption of the method of the invention can achieve the goal of defending DDoS attacks.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com