DDoS attack defense system and method based on dynamic transformation
An attack defense system and dynamic transformation technology, applied in the field of network security, can solve problems such as massive hardware and bandwidth investment, cost increase, TCP sliding window reduction, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
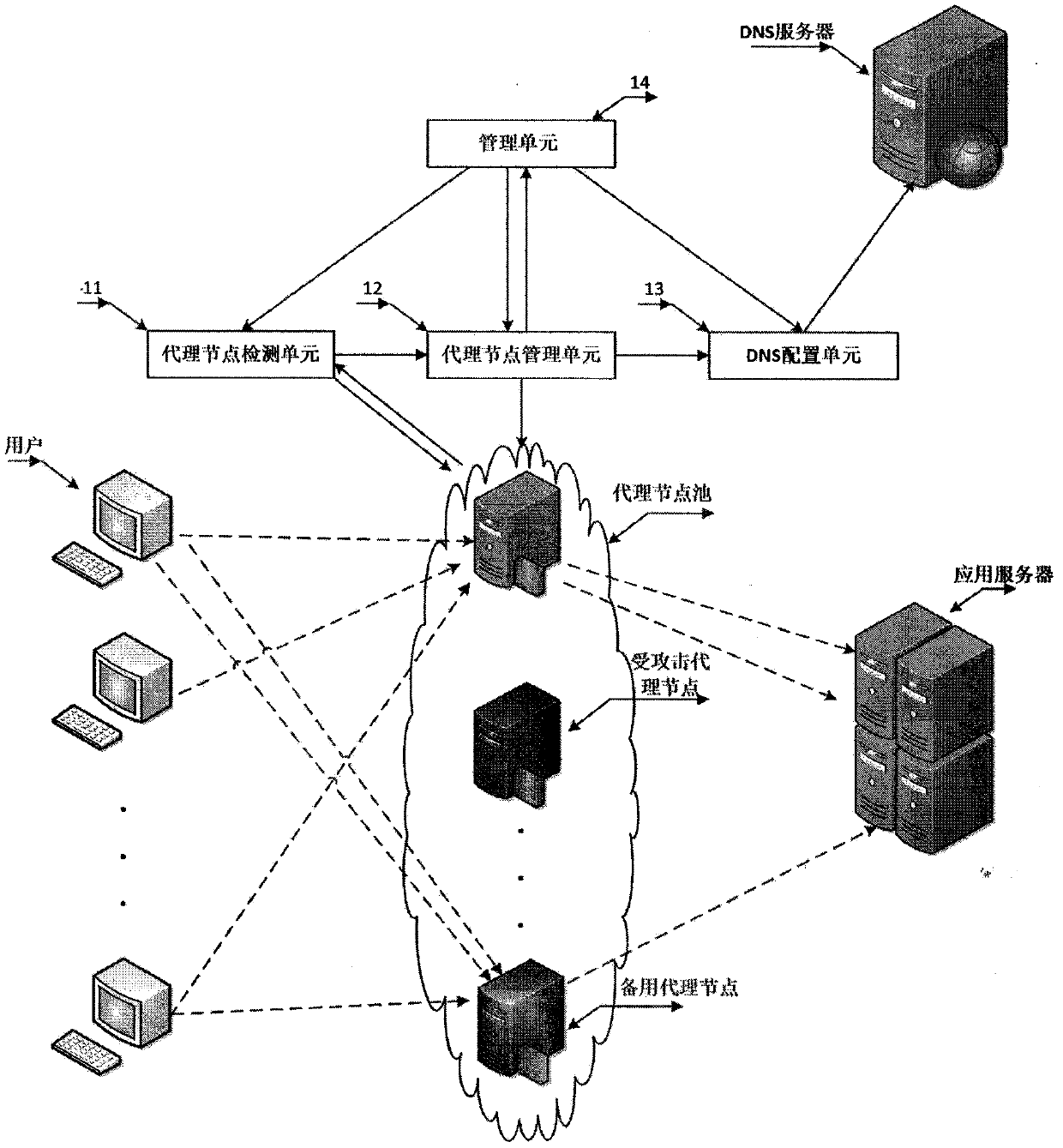
[0078] The first preferred embodiment mainly defends against DDoS traffic attacks, and this embodiment mainly defends against CC (Challenge Collapsar) attacks in DDoS. CC attack is a type of DDoS attack, which means that the attacker combines multiple "broilers" to send a large number of operations that consume more system resources of the application server to the application server, such as some complex database queries, etc. A large number of calculations and system resources are exhausted, and normal services cannot be provided externally. Different from the first embodiment, in this embodiment, the proxy node needs to cache the content on the application server and synchronize it regularly, so that when the user's access request reaches the proxy node, the proxy node will directly respond to the user, only when there is no When the resource requested by the user is found, the access request is sent to the application server.
[0079] In this embodiment, the proxy node de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com