Guard system to defend network invansion of unkown attack trick effectively
A technology for unknown attacks and network intrusions, applied in memory systems, program control design, instruments, etc., can solve problems such as inability to deal with intruders, and achieve the effect of defense against network system attacks, simple configuration, and strong comprehensive defense performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
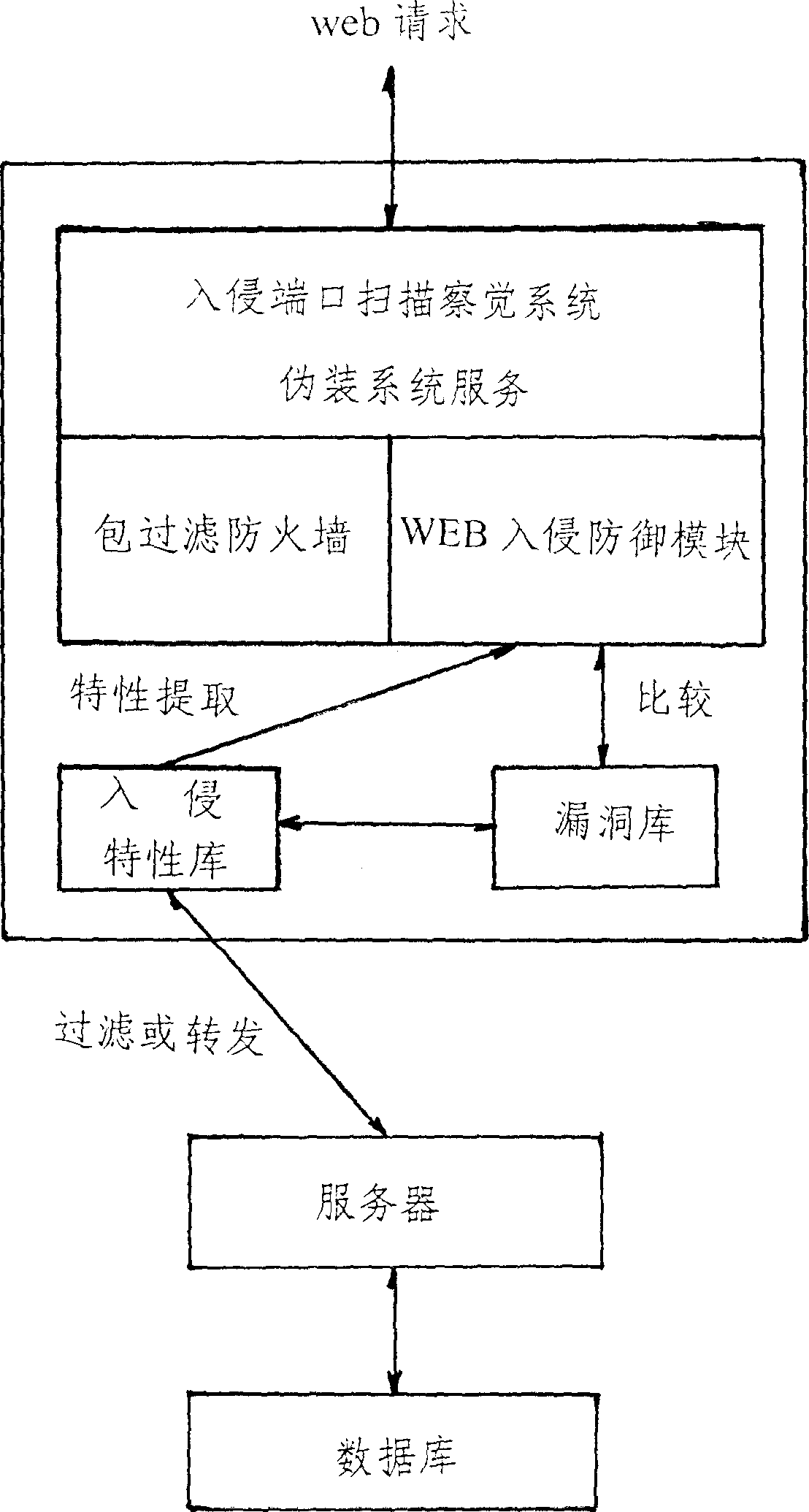
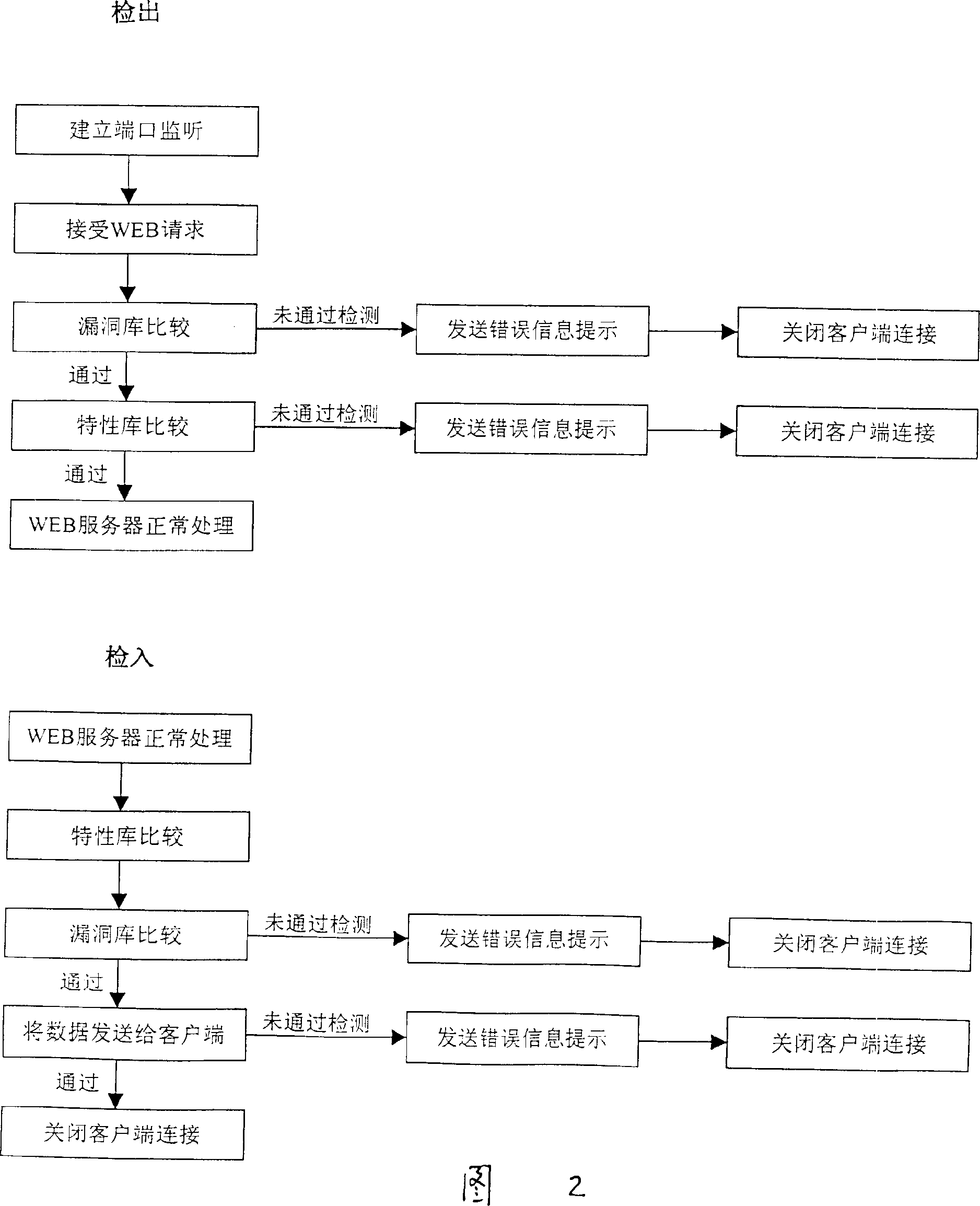
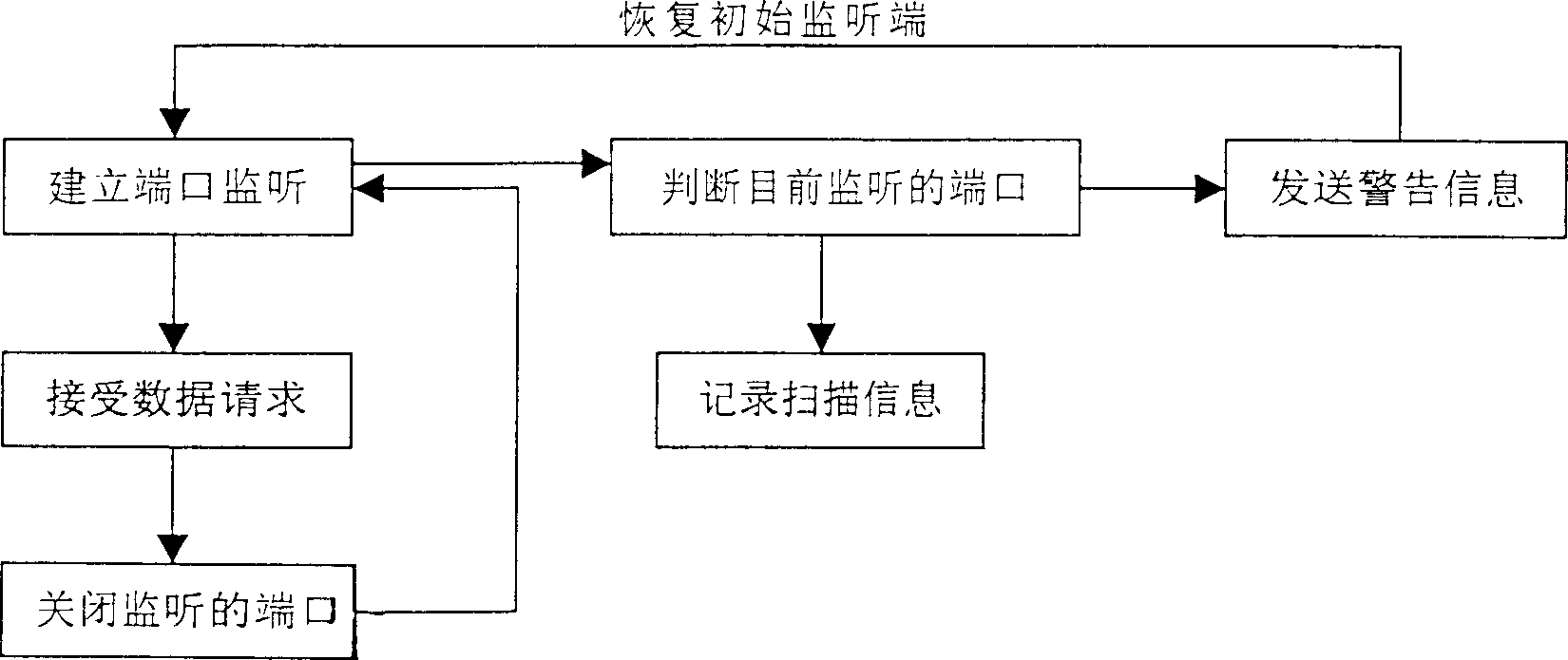
[0010] This network intrusion security defense system, according to the intruder's attack steps, sets up multiple checkpoints, and starts to defend the system from the first step of intrusion, including intrusion port scanning detection, camouflage system service, traditional packet filtering firewall, WEB intrusion prevention module, Vulnerability library module, intrusion feature library module, through the organic combination of these functional modules, and simple configuration and installation on the WEB server, it can play a comprehensive system protection role. After installation and operation, it will start to monitor the security status of the system. If any abnormality is found, the attack will be blocked in time, and an email will be sent to notify the system administrator. In the present invention, the creative data check-in and check-out judgment comes from the filter program subsystem of WEB request legitimacy, which is composed of data check-in and data check-out...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com