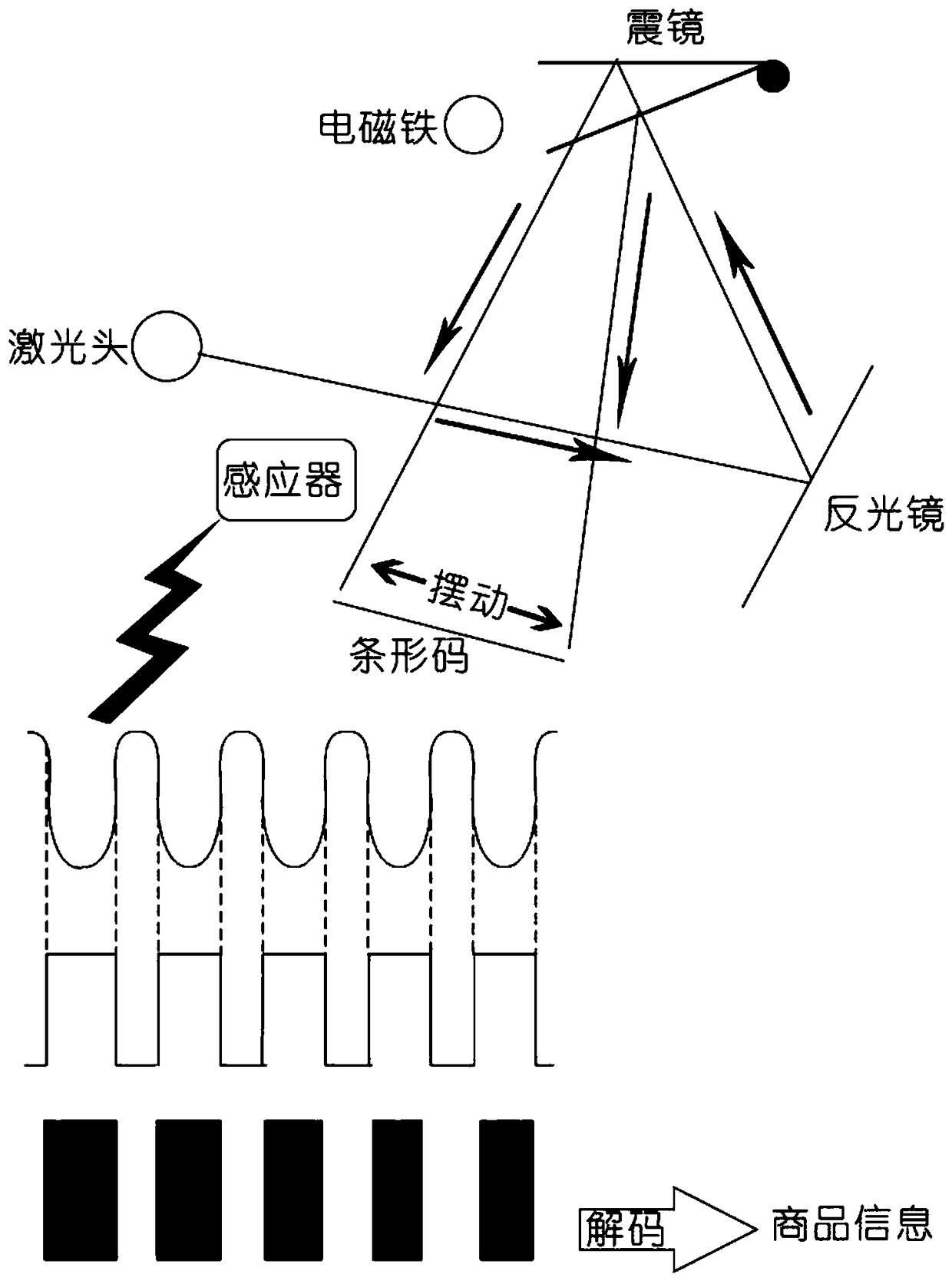
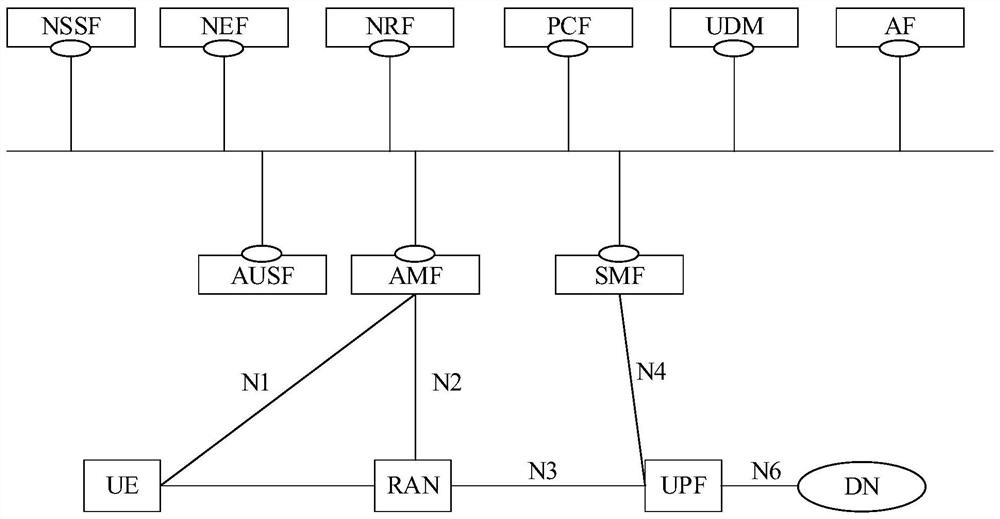
Patents
Literature
91results about How to "Guaranteed normal service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
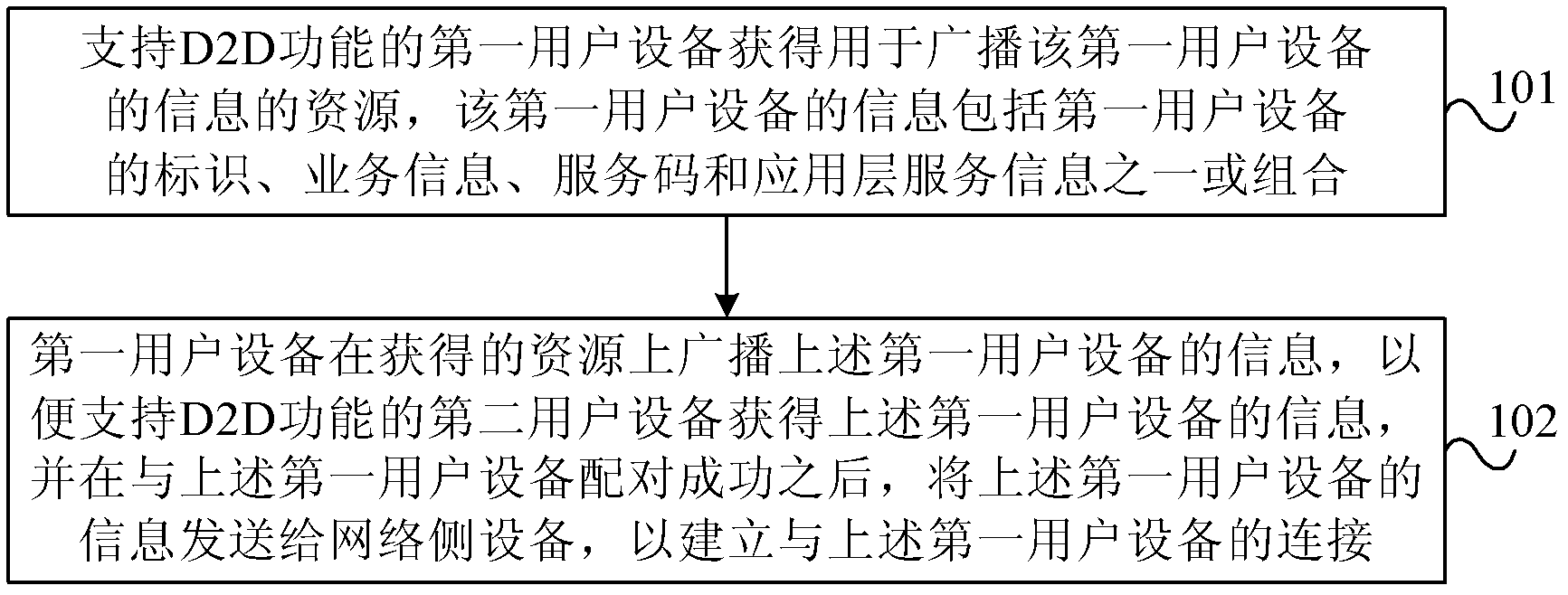
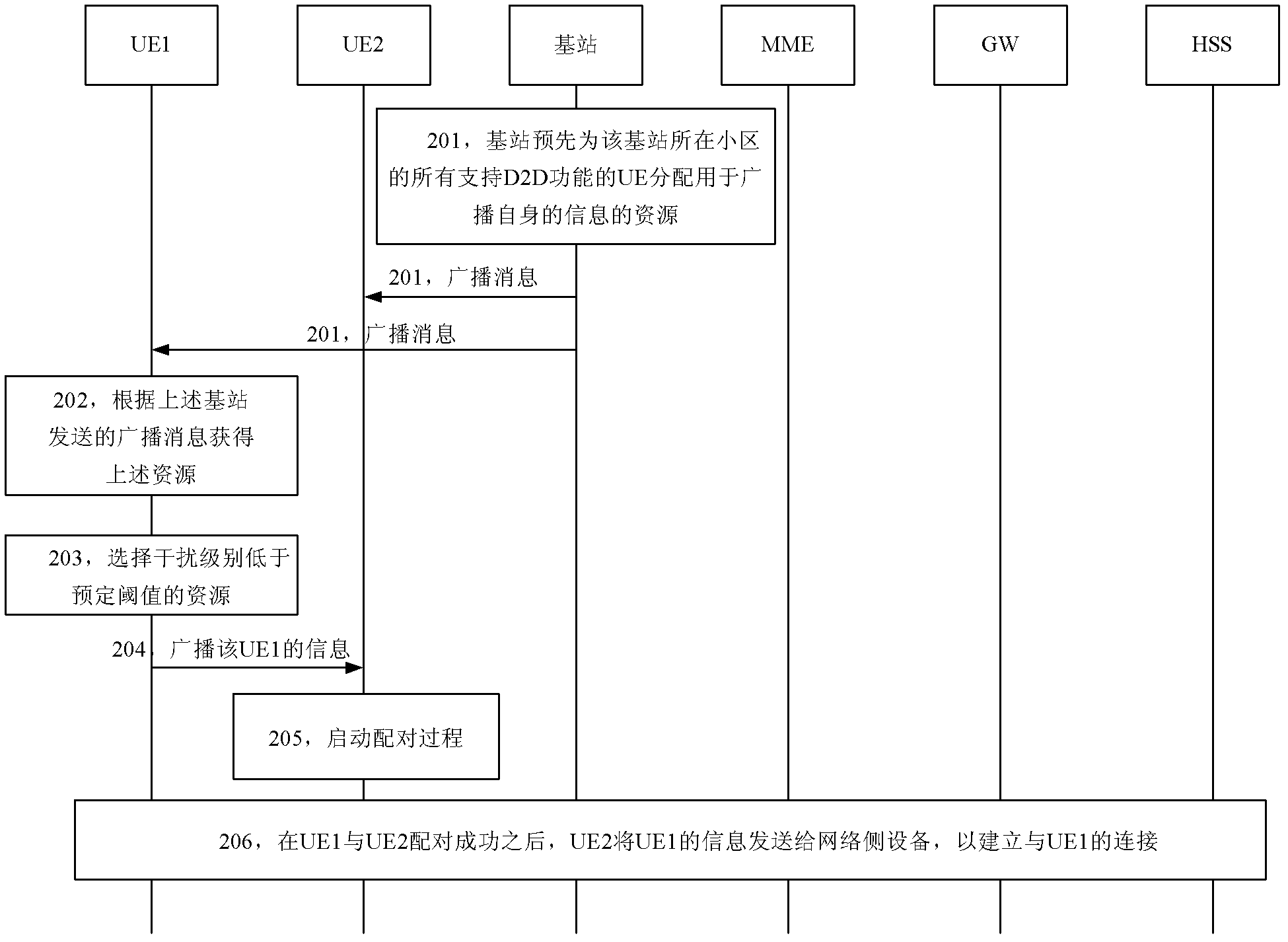
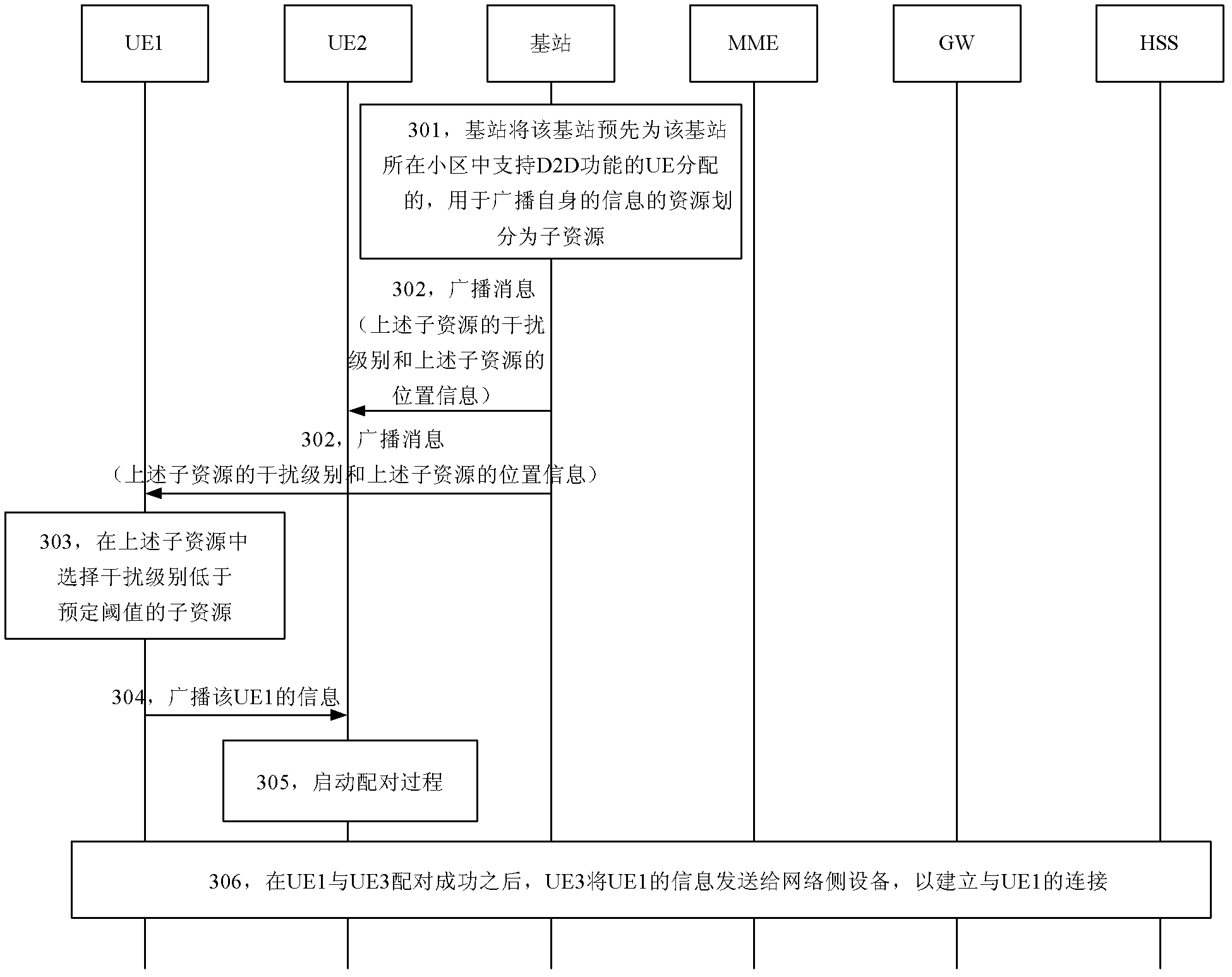
Content publishing method and user device
ActiveCN103037448AGuaranteed normal serviceNetwork traffic/resource managementAssess restrictionQuality of serviceUser device
An embodiment of the invention provides a content publishing method and a user device. The content publishing method includes: a first user device supporting a device to device (D2D) function acquires resources for broadcasting first user device information, and the first user device information comprises one or combination of a first user device identity, service information, a service code and application layer service information; the first user device broadcasts the first user device information on the basis of the acquired resources so as to enable a second user device supporting the D2D function to acquire the first user device information, and the first user device information is sent to a network side device after pairing of the first user device is successful so as to build connection of the first user device. The content publishing method and the user device enable a pairing terminal to acquire quality of service (QoS) information and provide guaranteed service for D2D communication.
Owner:HUAWEI TECH CO LTD
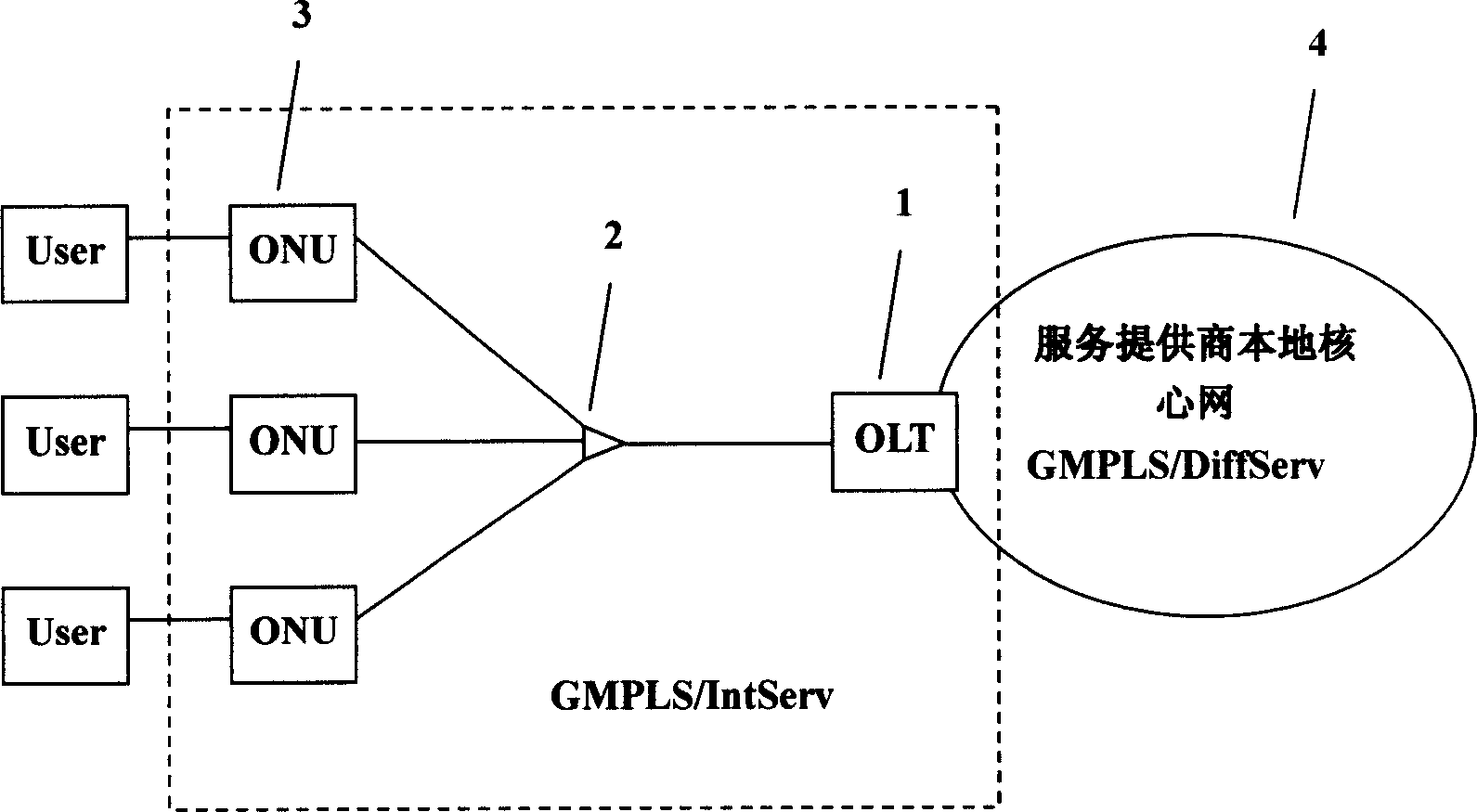
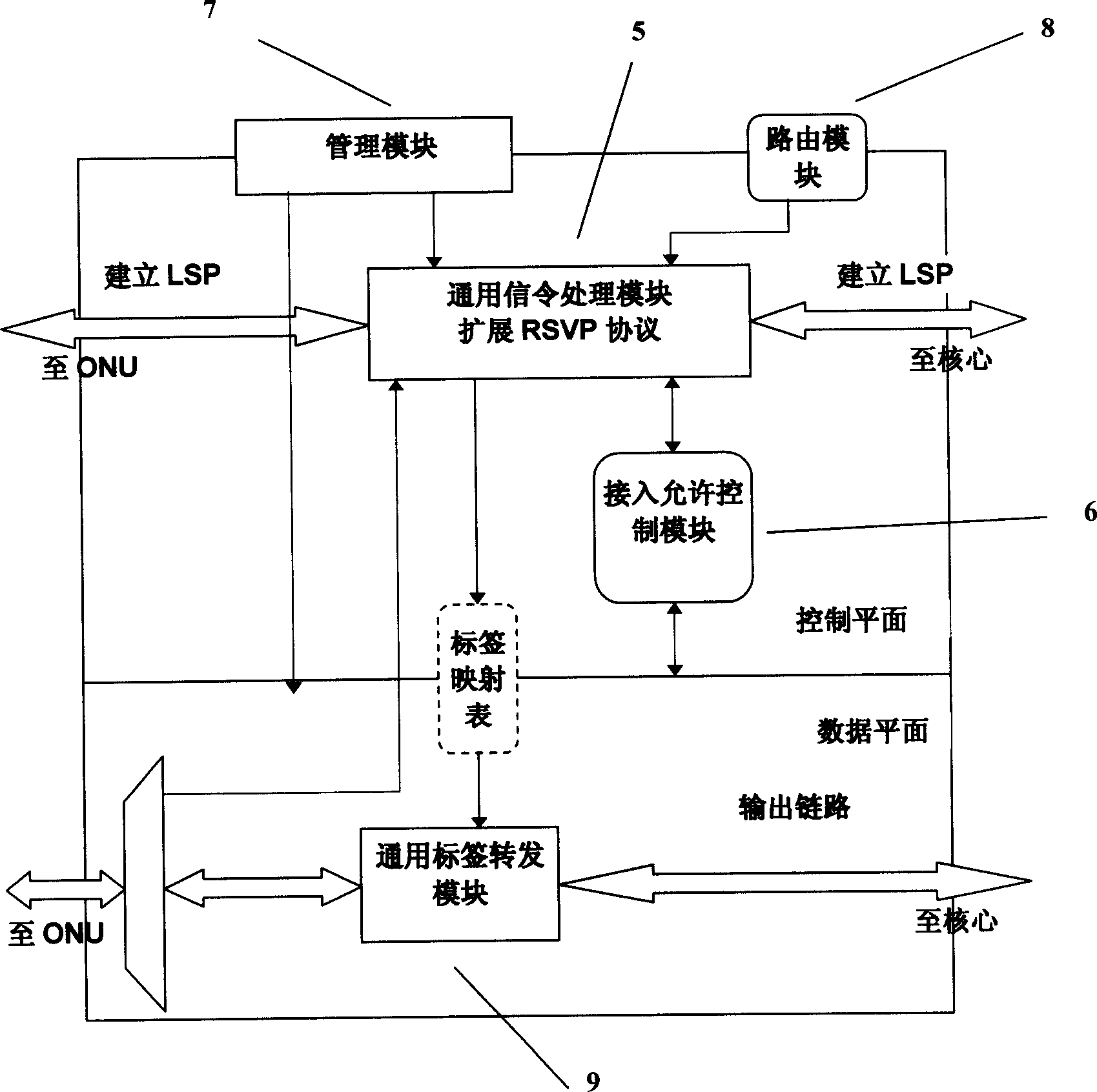
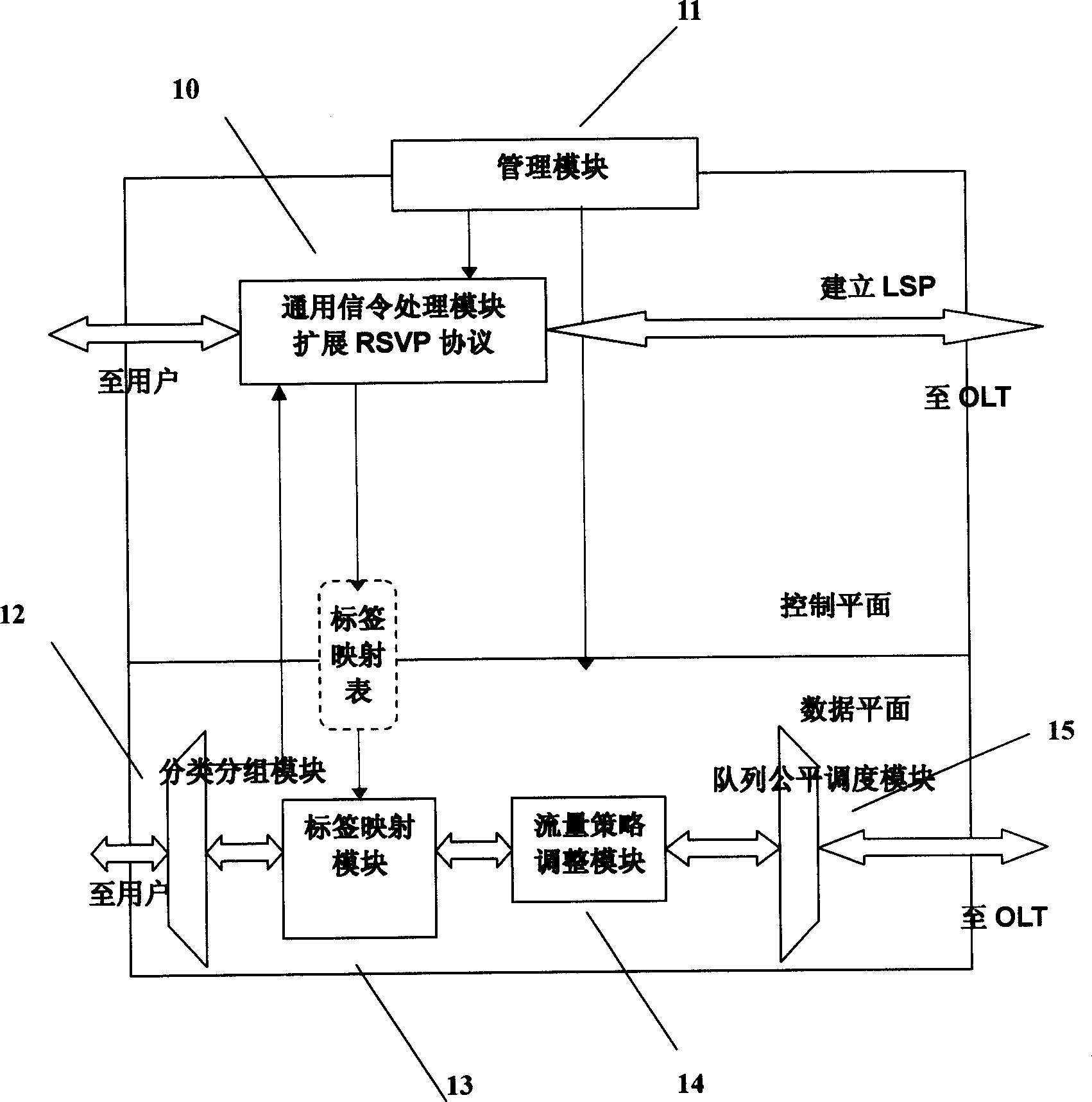
Passive optical network system based on generalized multiprotocol label switching (GMPLS) protocol
InactiveCN1725756ARealize intelligenceRealize intelligent controlTransmissionTelecommunications linkMultiprotocol Label Switching
A passive optical network system based on label exchanging protocol of universal multi-protocol is prepared as connecting optical line terminal OLT to multiple optical network unit ONU by wideband passive optical distribution network , using OLT and ONU as edge router and GMPLS domain of said exchanging protocol for being connected to the other GMPLS router in said multi-protocol by communication link , using OLT as intermediate router of integrated service in system individually for controlling all communication activities , using ONU as inlet router of integrated service in system for executing command of OLT .
Owner:SHANGHAI JIAO TONG UNIV
Taxi lining area setting controlling method
InactiveCN101551941AMeet fairness requirementsStandardize the queue orderIndication of parksing free spacesWorking environmentParking space
A taxi lining area setting controlling method which includes a taxi parking lining area and a taxi pick-up lining area; the taxi parking lining area is divided into a plurality of lining tracks, while the taxi pick-up lining area has only one track; the taxis in the parking lining area are released into the taxi pick-up lining area successively according to the track sequence; the taxis in each track are divided into a plurality of batches by a certain number, and the taxis enter the taxi pick-up lining area batch by batch and reach pick-up location; and when the current releasing track is empty, the taxis in the next track are released; the taxis park from stall with the lowest number in the track with the lowest number above the track being released, to stall with the highest number, and from the stall with the lowest number in the first track. The invention greatly reduces the taxi driving distance in lining area, obviously reduces the fuel consumption and waste gas emission of taxi, and improves the working environment of taxi parking and lining area.
Owner:TONGJI UNIV
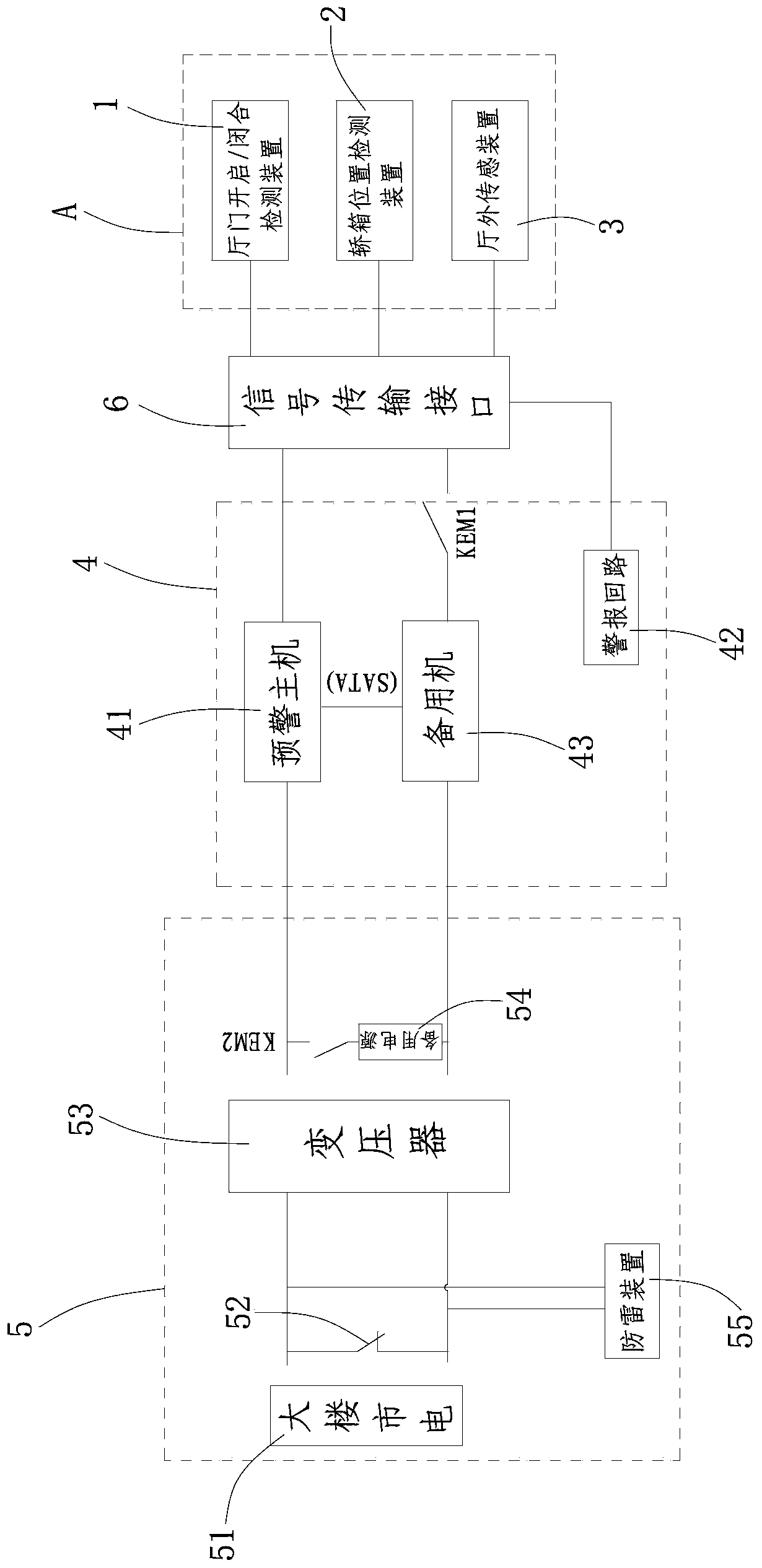
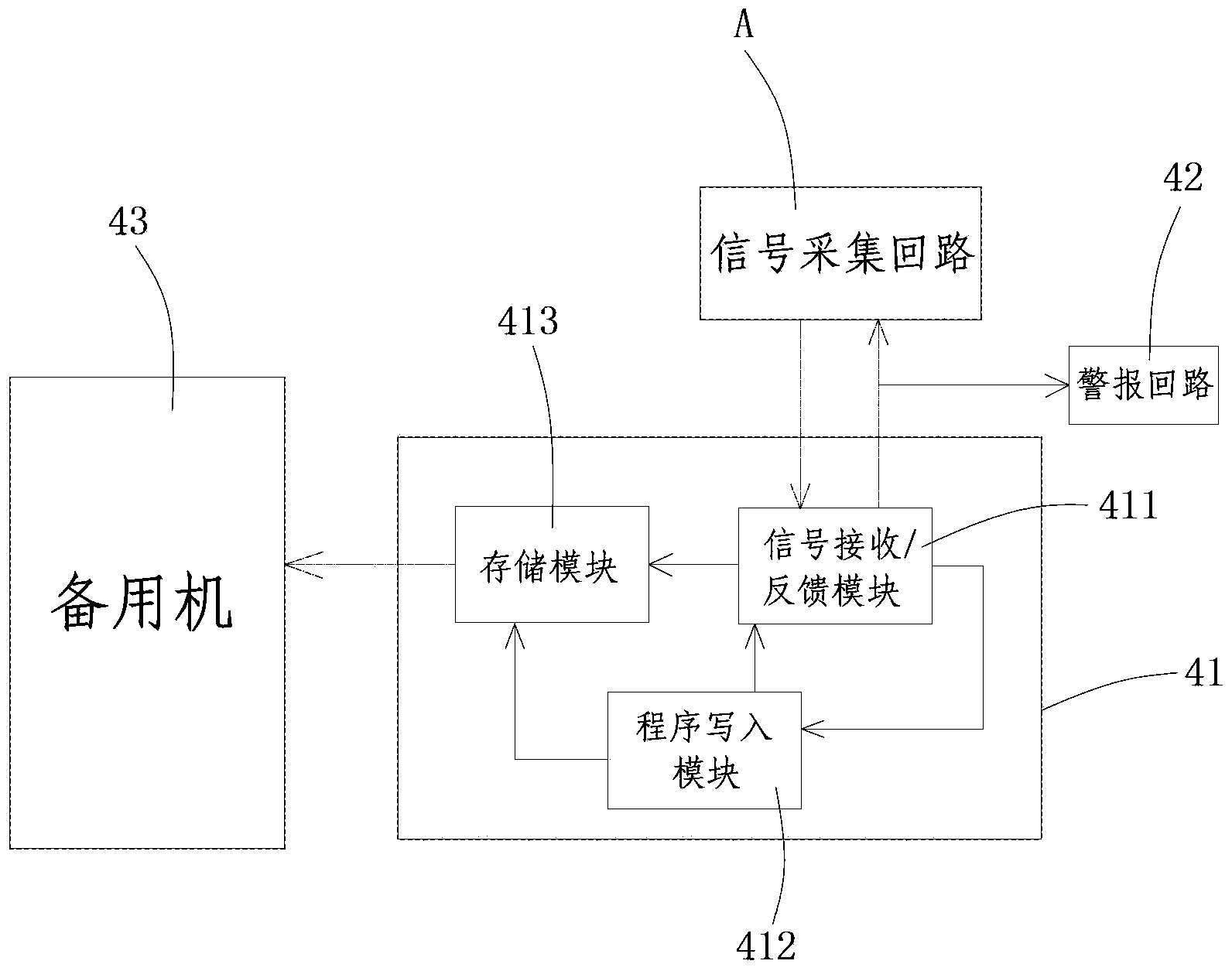
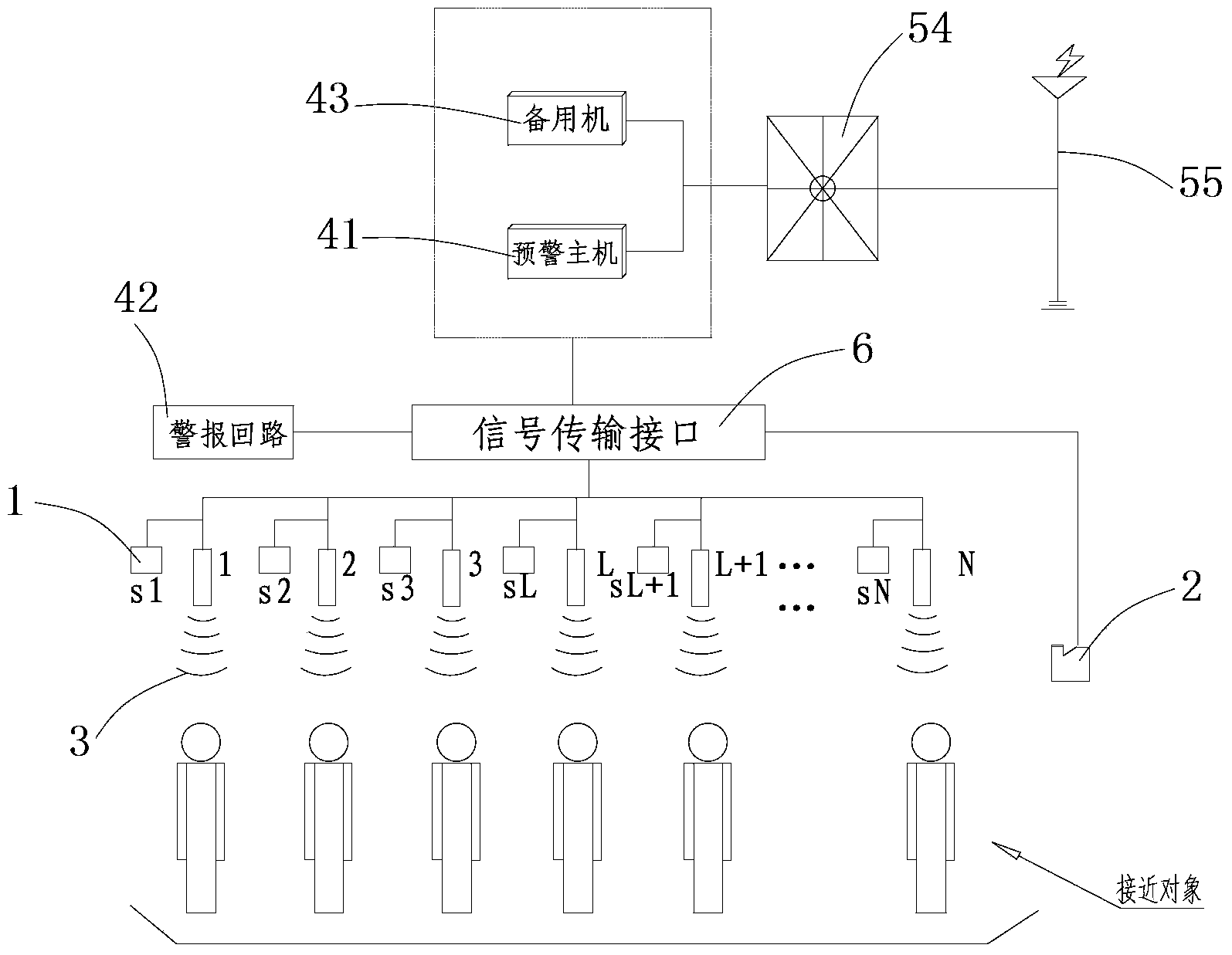
Elevator safety precaution system
ActiveCN103449276AGuarantee the safety of lifeIntelligent monitoring hall door riskElevatorsEngineeringWarning system
The invention relates to an elevator safety precaution system comprising a landing door opening / closing detecting device, a lift car position detecting device, a car outer sensing device, a precaution device and a power device independent to the elevator. The landing door opening / closing detecting device is used for detecting whether the landing door is open or closed or not, the lift car position detecting device is used for detecting whether the lift car is near to the landing door or not, the car outer sensing device is used for detecting approaching condition of people outside the car, the precaution device is used for receiving detecting signals from the landing door opening / closing detecting device, the lift car position detecting device and the car outer sensing device, and judging whether to send precaution signals or not according to the detecting signals, and the power device independent to the elevator is used for supplying power to the precaution system. The elevator safety precaution system can precaution risks of early landing door unlocking and of entering unlocked landing door when monitoring elevator maintenance, so that life safety of passengers and maintenance staff can be guaranteed, and states of the car outer sensing device can be switched over intelligently, long and unnecessary power start is saved, and independent external power source is utilized to prevent losing monitoring capability due to power failure of the elevator.
Owner:HITACHI ELEVATOR CHINA
Computer implemented method for assistance
InactiveUS20190098504A1Prevent theftEasy to useProgram loading/initiatingBuying/selling/leasing transactionsComputerized systemComputer terminal
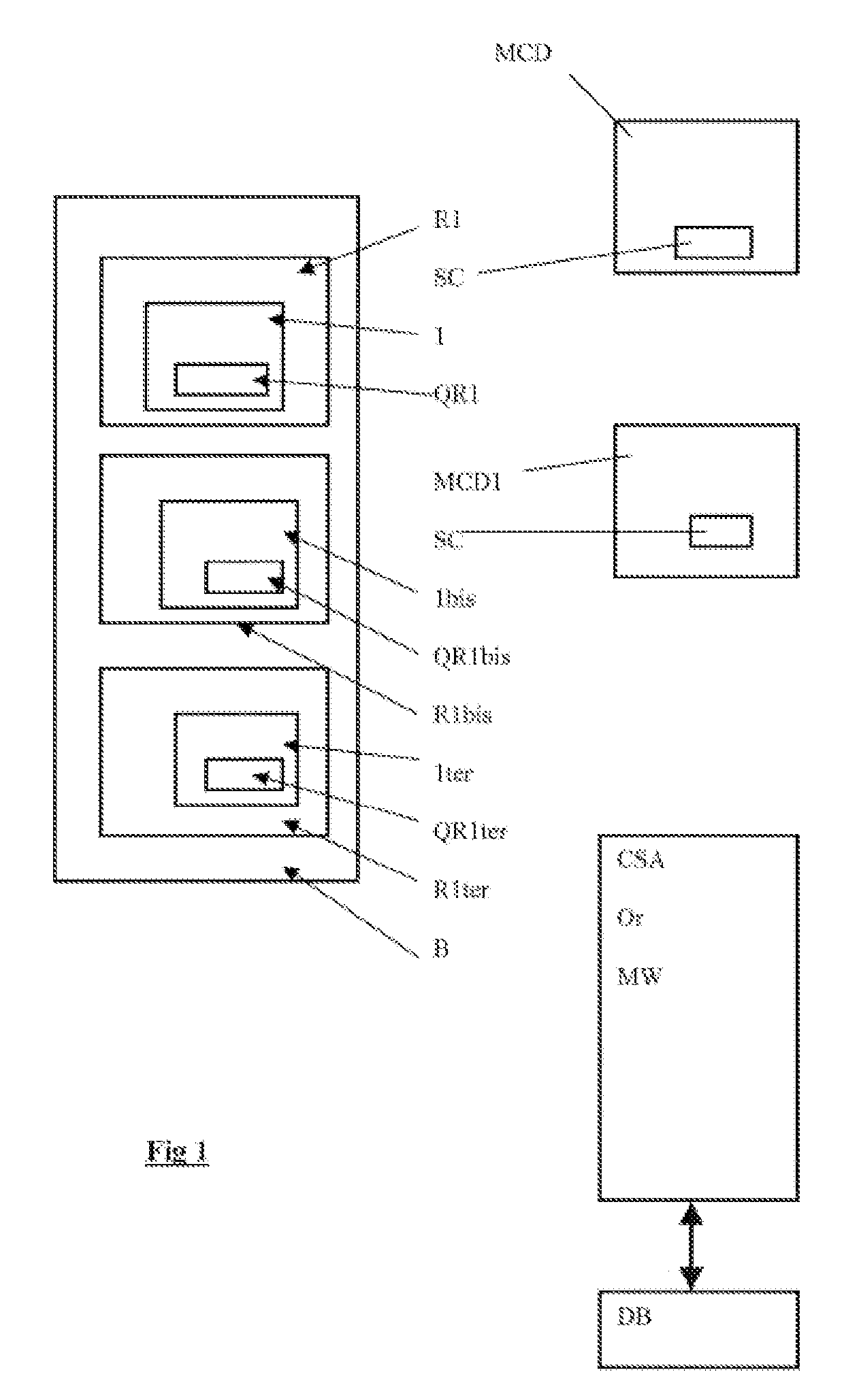
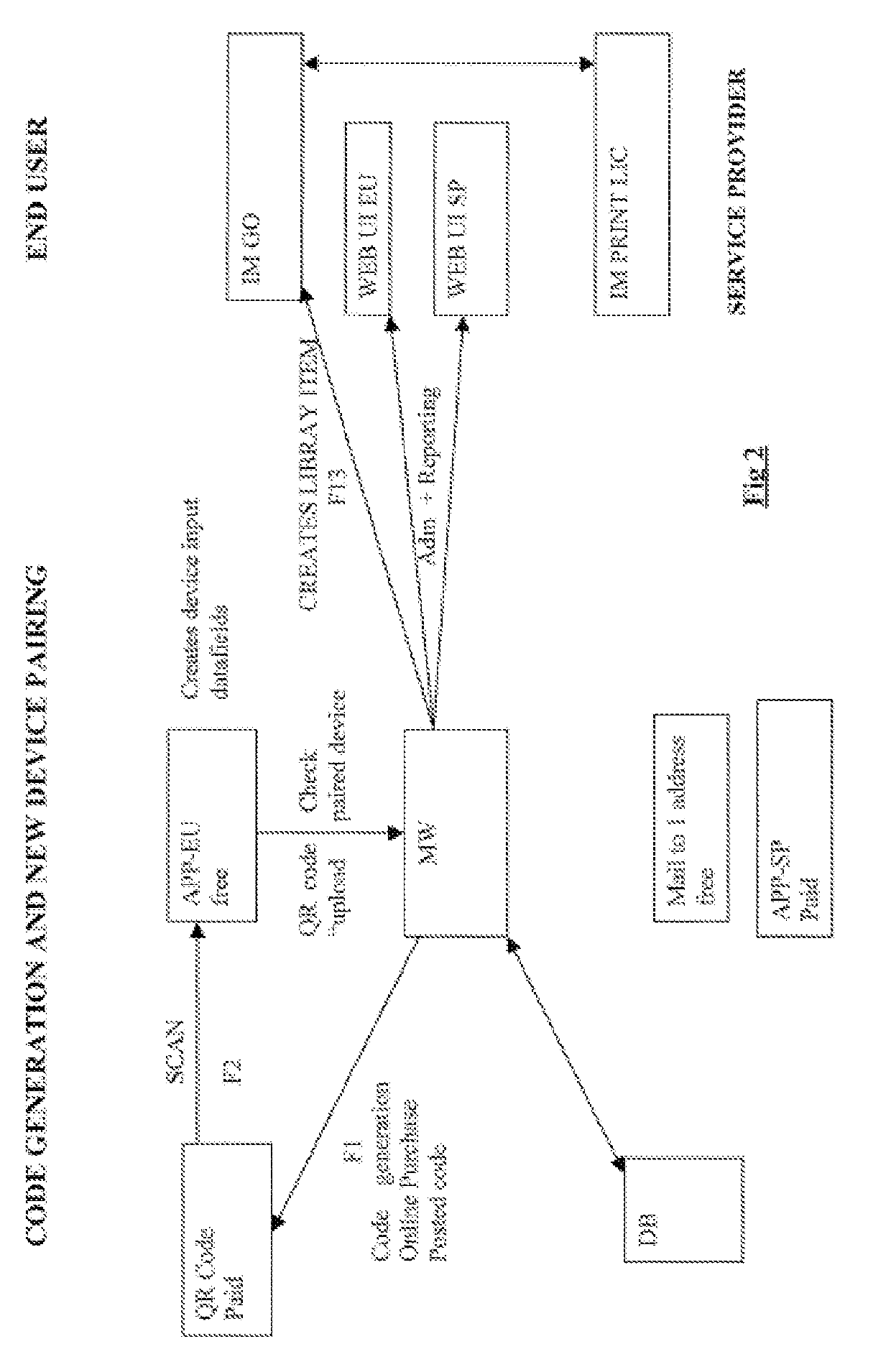
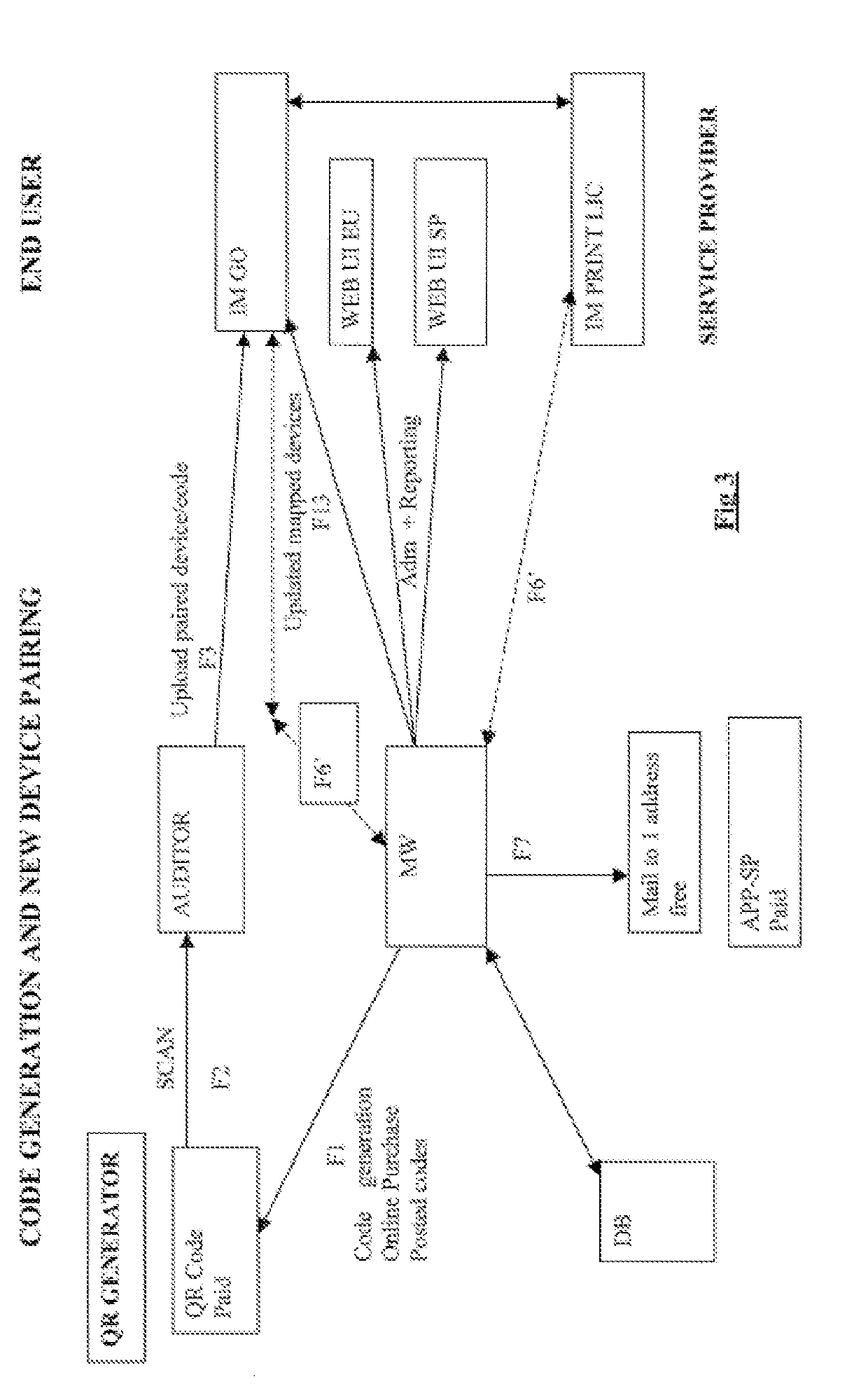
The invention relates to a computer implemented method for assistance for a predetermined asset characterised by asset parameters including at least its type or a sign adapted for characterising at least its type, and advantageously its location or a sign adapted for characterising its location, especially in a building, to an end-user having a mobile communication device with a scanning element or camera, said end-user mobile communication device being adapted to communicate with a computer system for assistance.
Owner:ISN PARTNERS LTD
Method for implementing remote-call by application program interface system on database
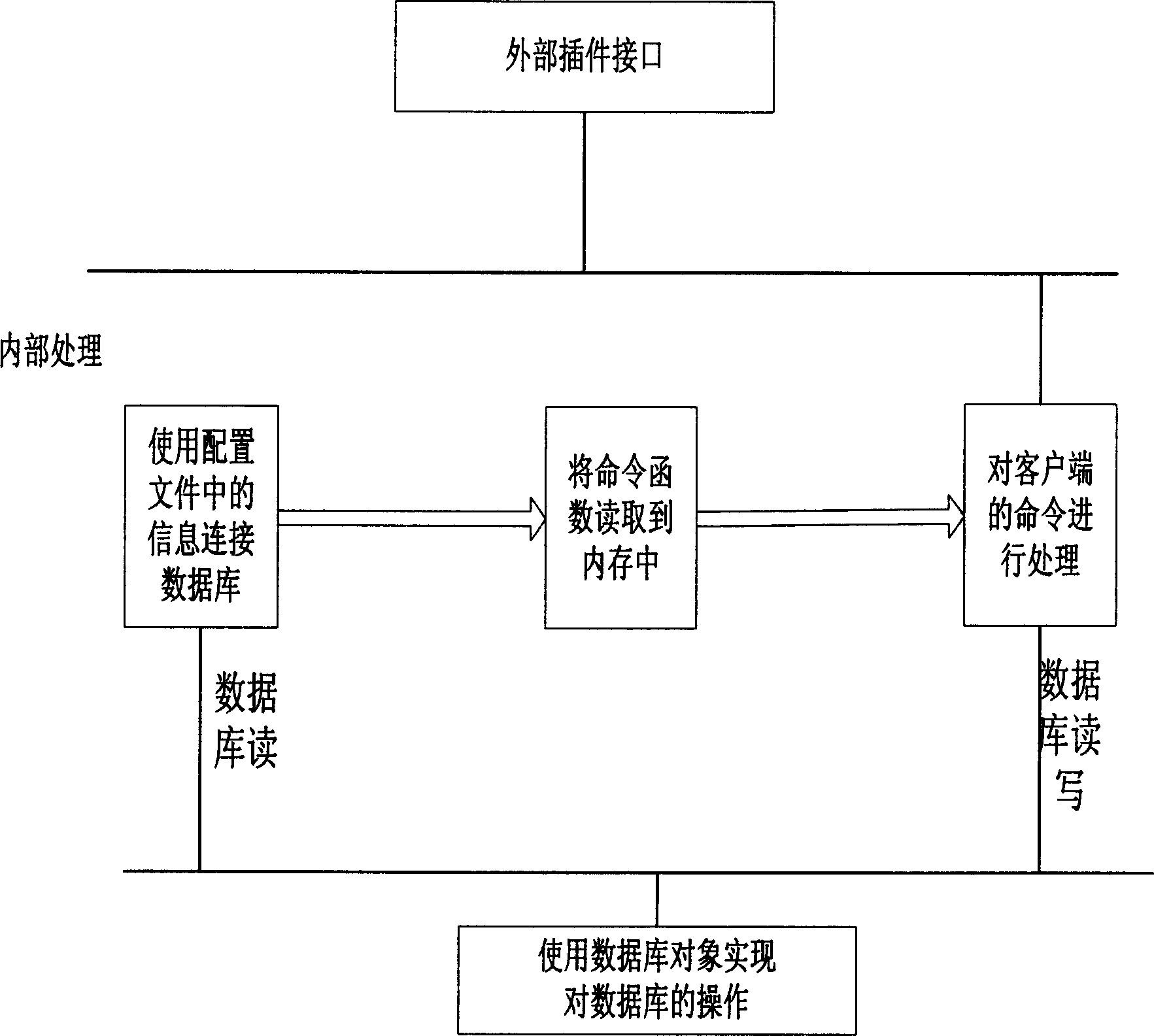
InactiveCN1652078ARealize interconnectionReliable transmissionSpecific program execution arrangementsBase classApplication programming interface
The present invention relates to a method for implementing remote calling by utilizing application program interface system based on data base. The described application program interface system based on data base includes: a. configuration file; b. data base object; the described data base object is generated by utilizing data base class, the operation of the data base is encapsulated by said class, the described data base class provides several subclasses, every subclass can provide identical interface; c. commad configuration file; and d. configuration interface. The described method includes the following steps: 1). establishing connection with data base; 2. analyzing available command; 3). receiving calling command; and 4). executing calling command function.
Owner:HUAWEI TECH CO LTD
Media issuing system and method
InactiveCN1741525AEliminate point-to-point connectionsDecouple dependenciesTransmissionCommerceSoftware busMediaFLO
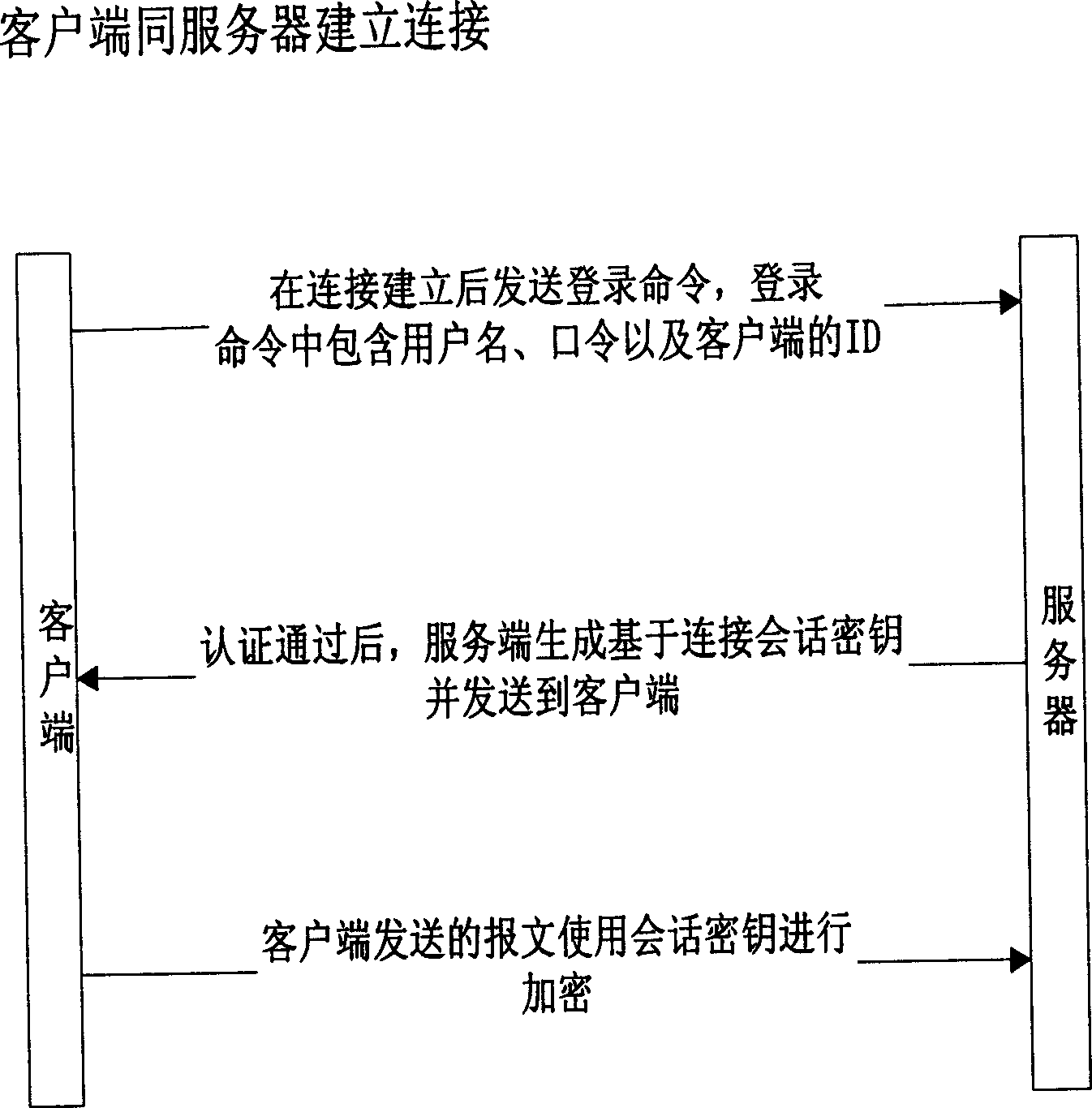
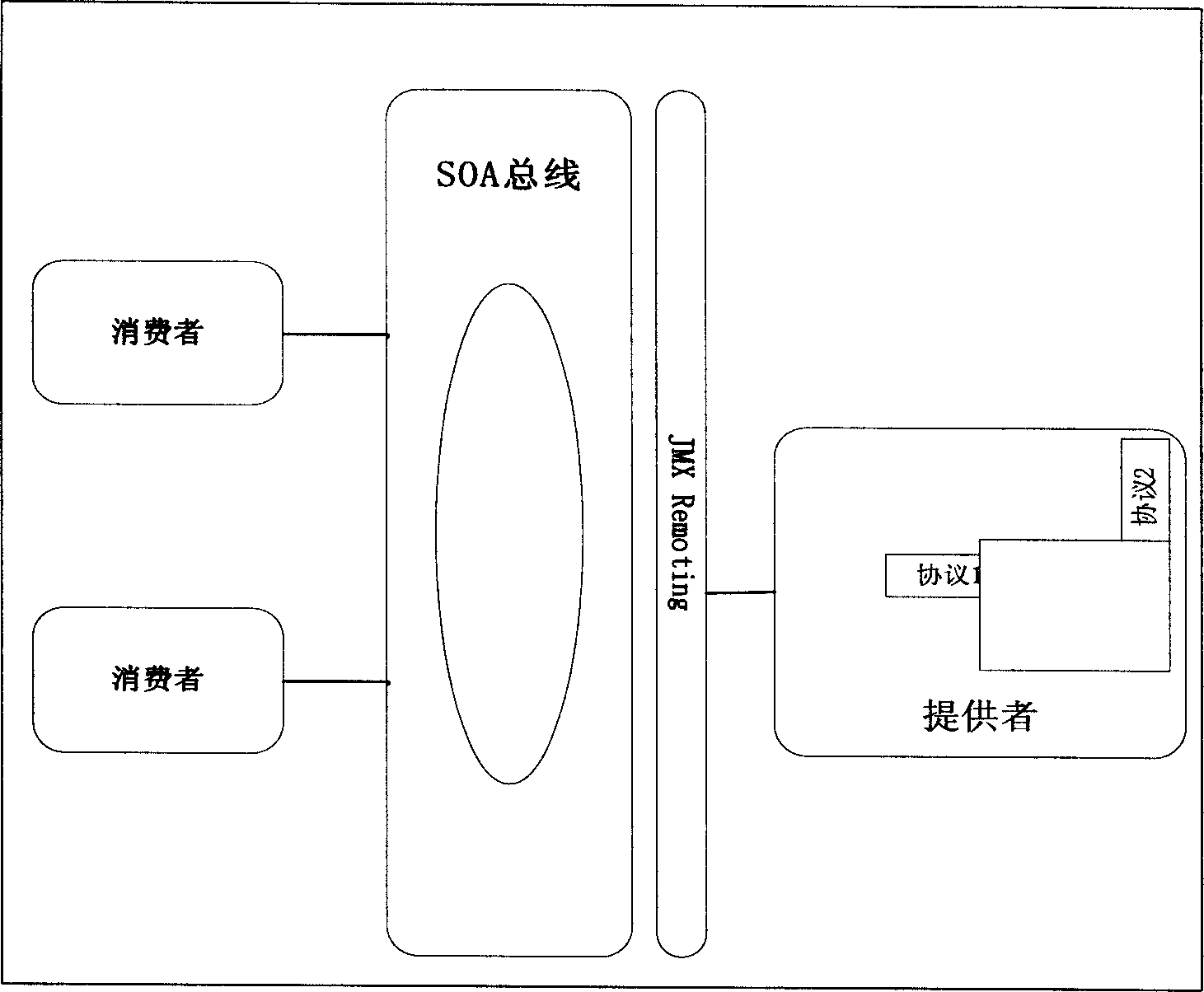
A media issuing system comprises service provider module , service consumer module , internal core layer with management frame of plug and play , transmission layer with JMX and GSSAPI wharehouse for separating network transmission and safe protocol so as to realize different protocol , service layer for packaging base module and function module to ensure Mbean service to load and manage those service dynamically , application layer for exposing interface of all modules being called and managed through user boundary , service bus being used to pass whole system in software bus mode for registering all service components and for managing their related parts .
Owner:北京无限新锐网络科技有限公司
A flood request attaching filtering method based on the stateless of open source core
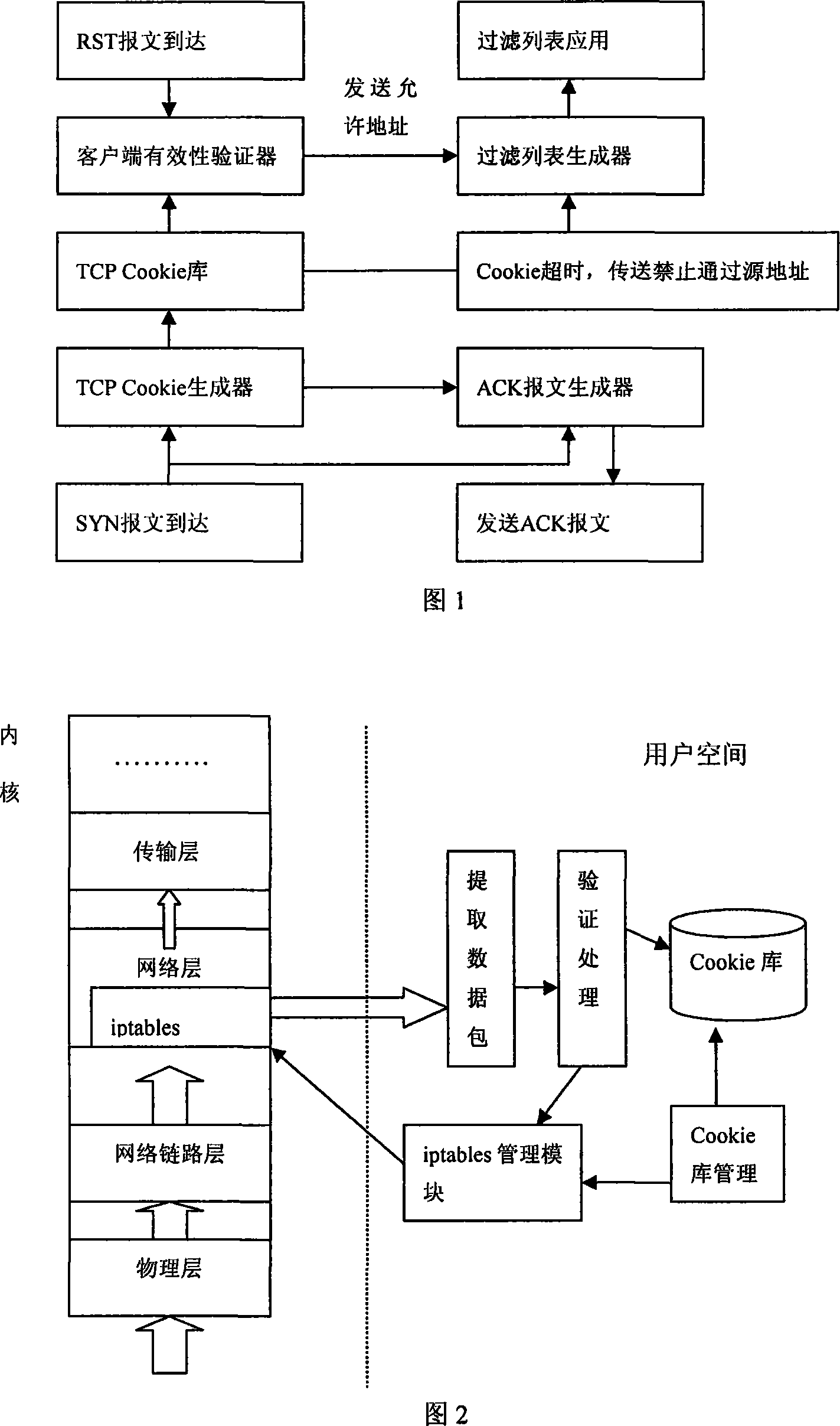
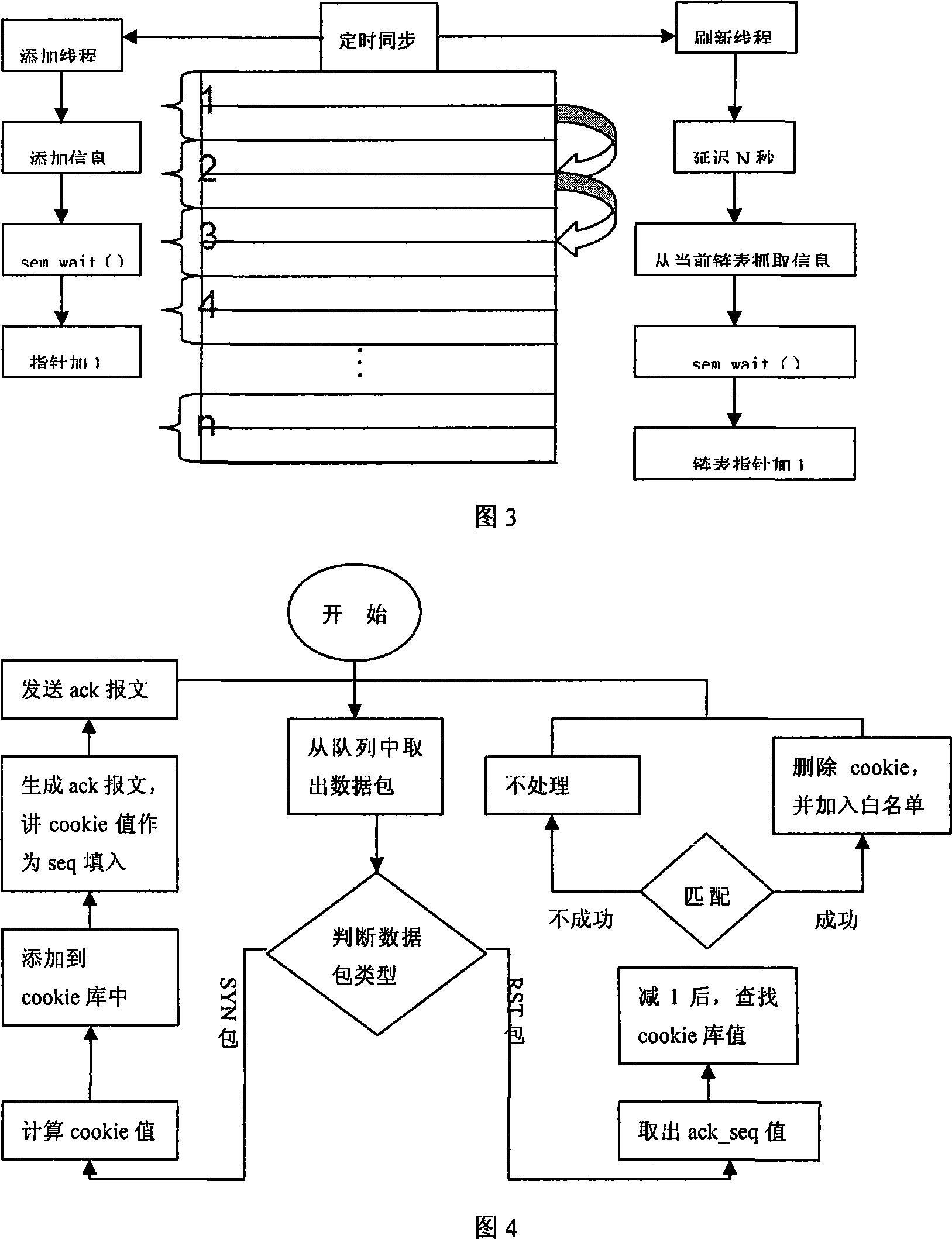
The invention relates to an open source kernel based filtration method of stateless flooding request attacks, which comprises the following steps: the rule list of the filtration of an open source firewall is initialized to generate a white list and a blacklist; a main control module distinguishes and processes the request message and the reset message respectively; the Cookie value of the request message is calculated and is added to a text document library, and a confirmation message is sent back to the message origin; as for the reset message, the confirmation number value thereof is extracted and searched in the text document library after being subtracted by one; a text document library maintenance module deletes the expired information record in every interval t, and informs a firewall operation module to add the address of the origin to the blacklist; the firewall operation module gathers list items when the number of the list items in the white list or the blacklist are very large; after giving the command of filtration stopping, the firewall module needs to empty all the lists and stop the function of a kernel filtration module, and the filtration method is ended. The adoption of the method of the invention can achieve the goal of defending DDoS attacks.
Owner:NANJING UNIV OF POSTS & TELECOMM
Domain name protecting system and method thereof
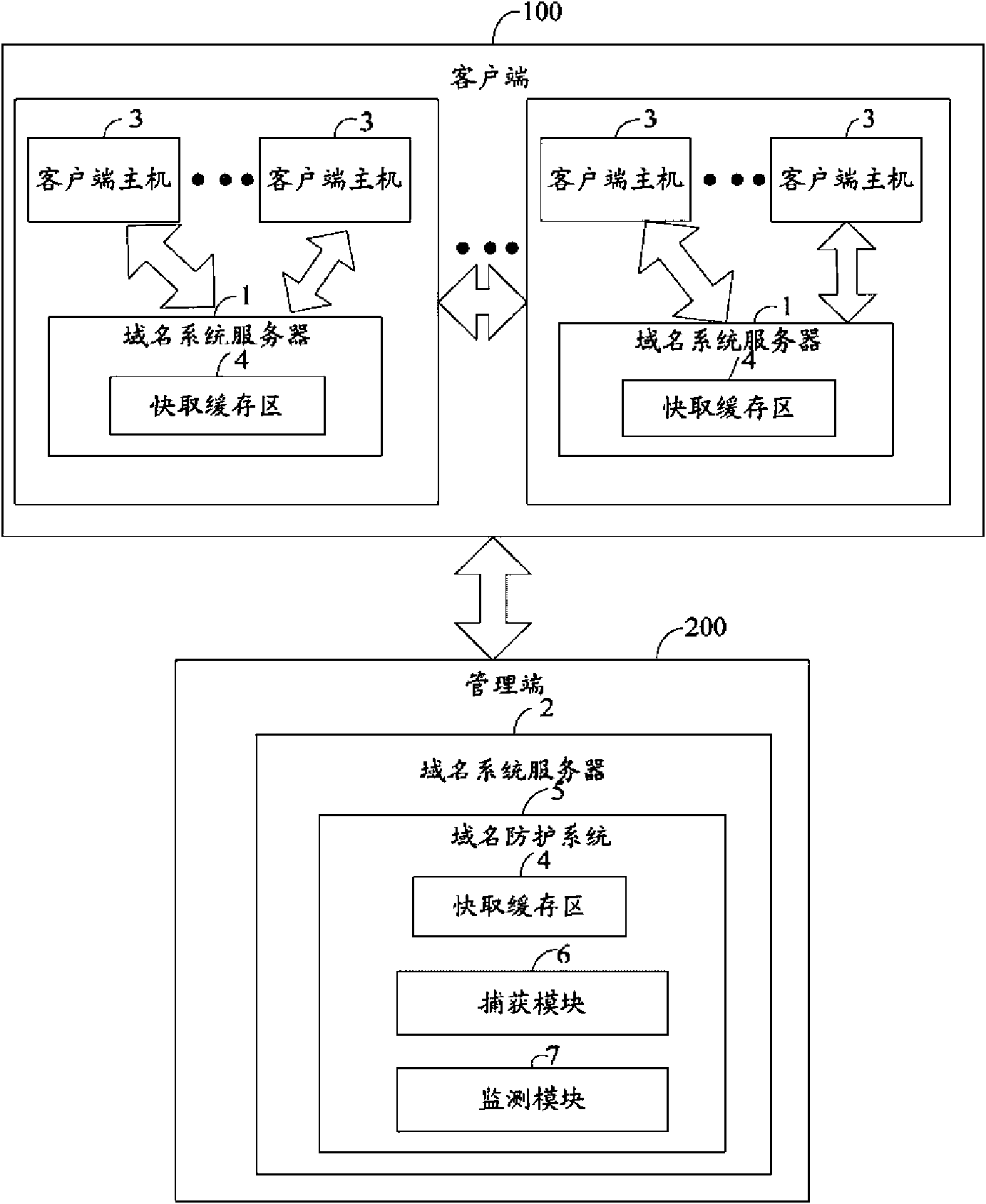
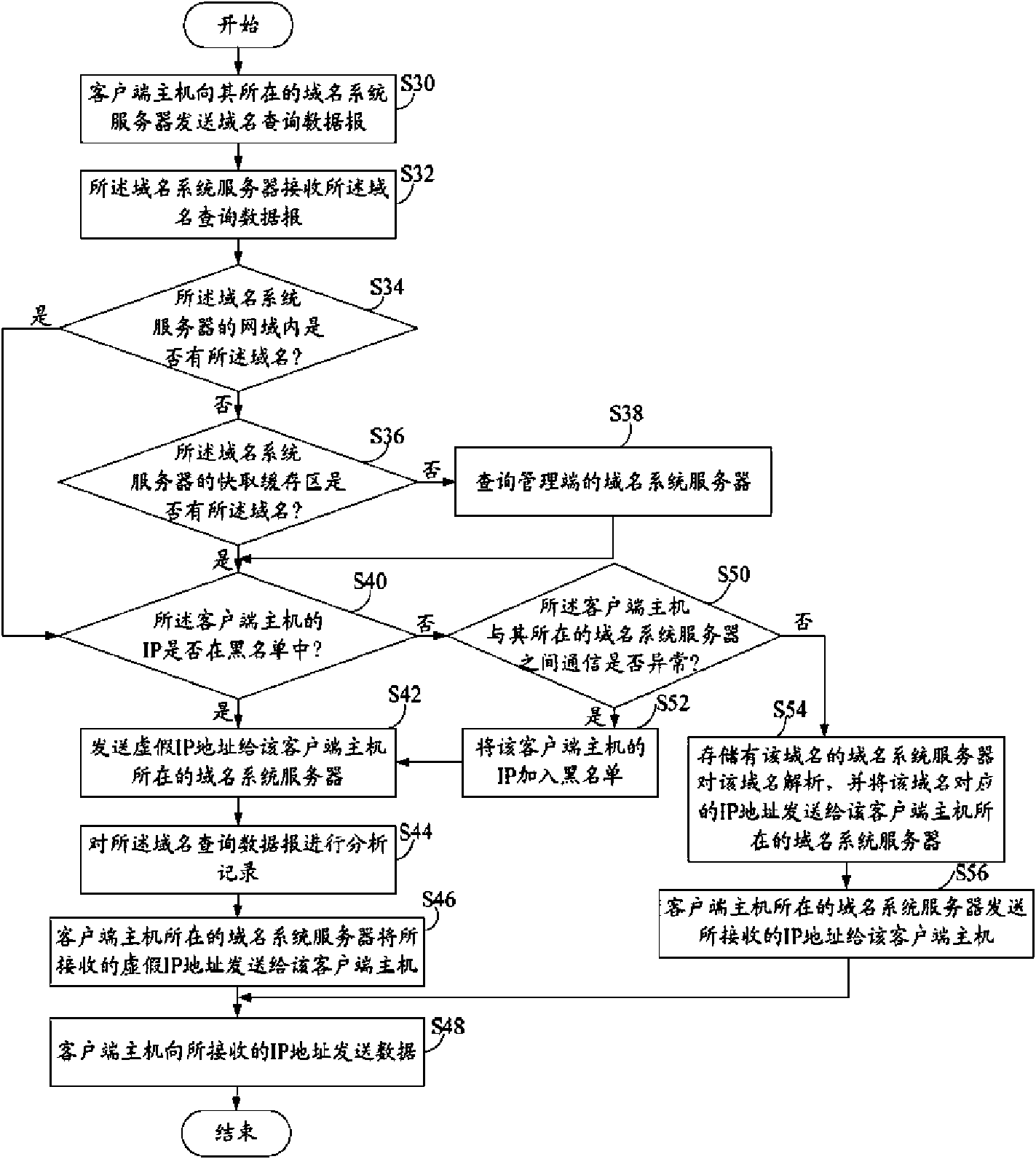
InactiveCN101626375AAvoid Malicious Data AttacksGuaranteed normal serviceData switching networksClient-sideIp address
A domain name protecting method comprises the following steps: a first domain name system server receives domain name inquiry datagram sent from an owned client terminal host computer; a second domain name system server judges whether the IP address of the client terminal host computer is in a black list which is stored in the second domain name system server to record the IP addresses of illegalclient terminal host computers; when the IP address of the client terminal host computer is not in the black list, the second domain name system server judges whether the communication between the client terminal host computer and the first domain name system server is abnormal, if so, the IP address of the client terminal host computer is added in the black list; if the IP address of the client terminal host computer is in the black list, the second domain name system server sends a false IP address to the first domain name system server; the first domain name system server returns the received false IP address to the client terminal host computer. In addition, the invention also provides a domain name protecting system.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Multi-source load balance method and system for proportional polling based on content distribution network
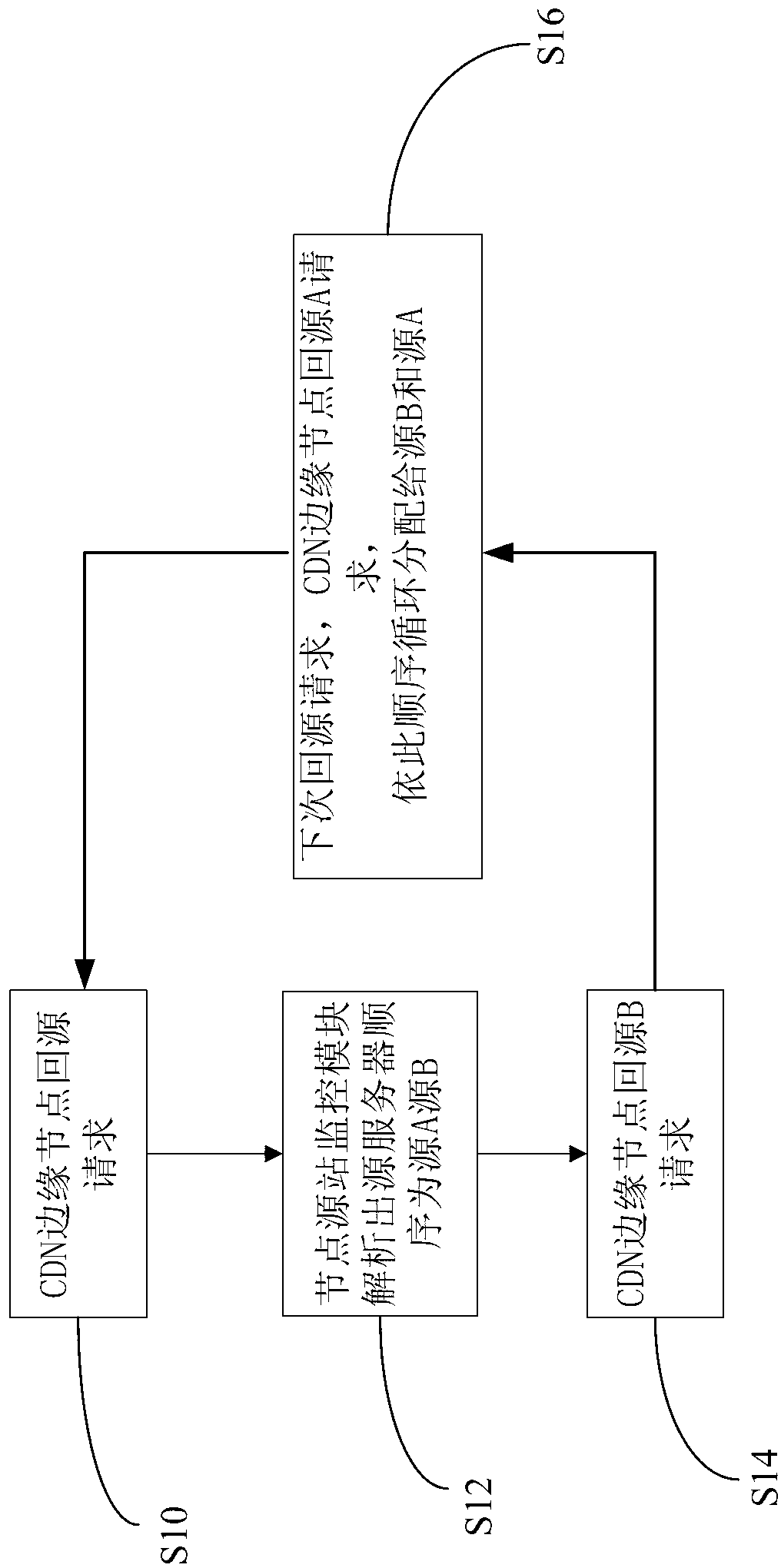
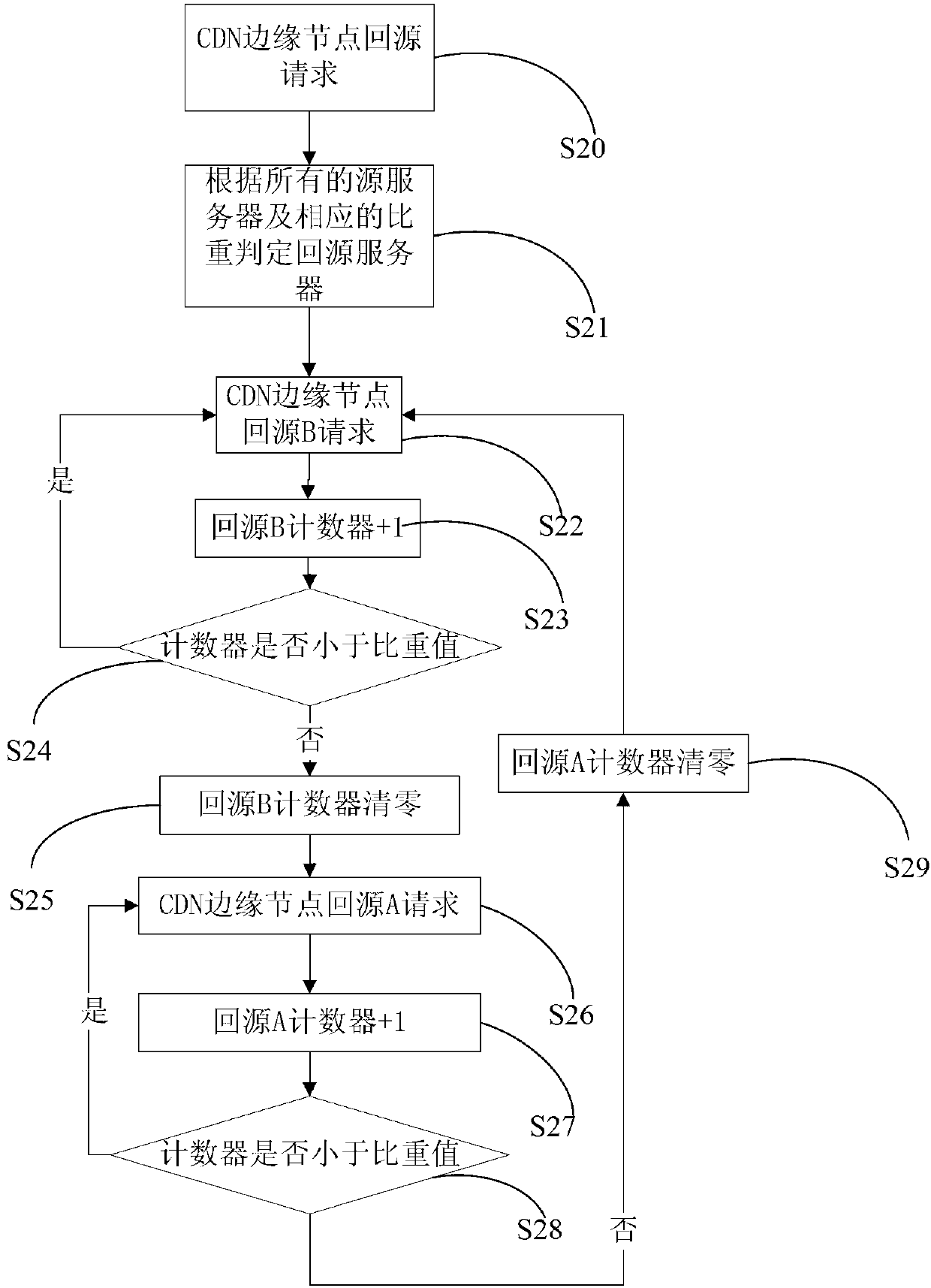
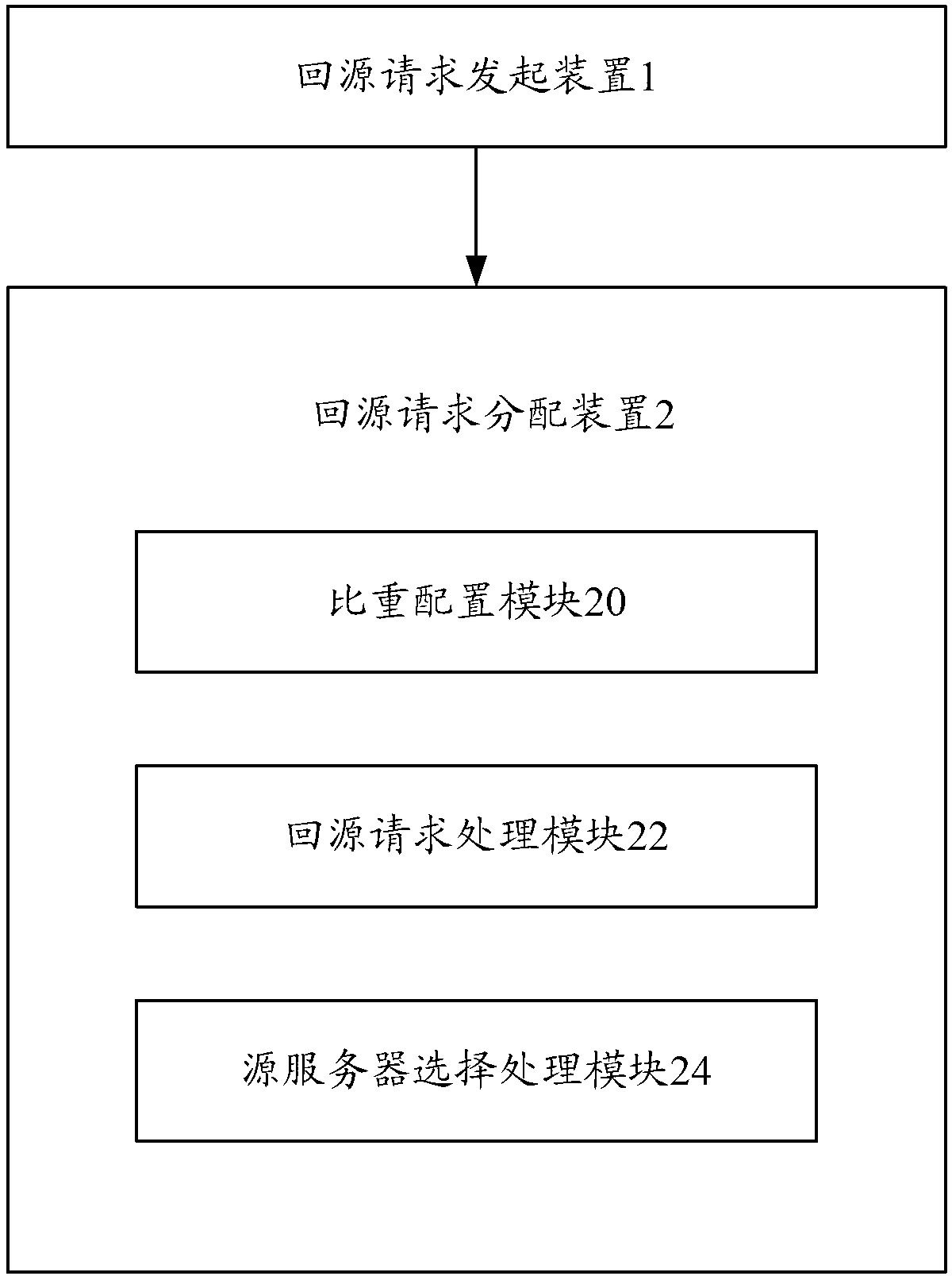
InactiveCN102970381AGuaranteed normal serviceLoad balancingTransmissionSpecific gravityContent distribution
The invention discloses a multi-source load balance method and system for proportional polling based on a content distribution network, which can guarantee normal services of source servers, and realize multi-source load balance on the basis of the normal services of the source servers. According to the technical scheme, the method comprises the following steps of: receiving a file request for source back of a user, wherein an edge node of the content distribution network requires the source back; and configuring the corresponding source servers to implement the source back request according to proportion values of the source servers.
Owner:CHINANETCENT TECH
Elevator automatic spot inspection system
InactiveCN103910260AEfficient collectionGuaranteed normal serviceElevatorsCommunication unitTerminal equipment
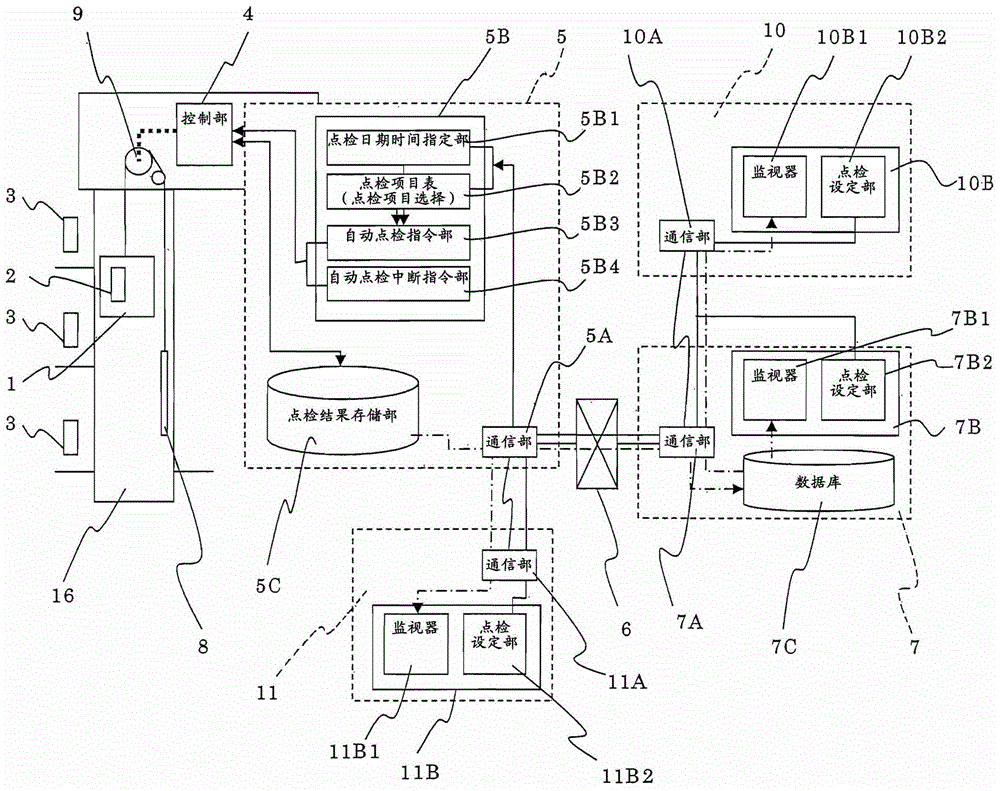
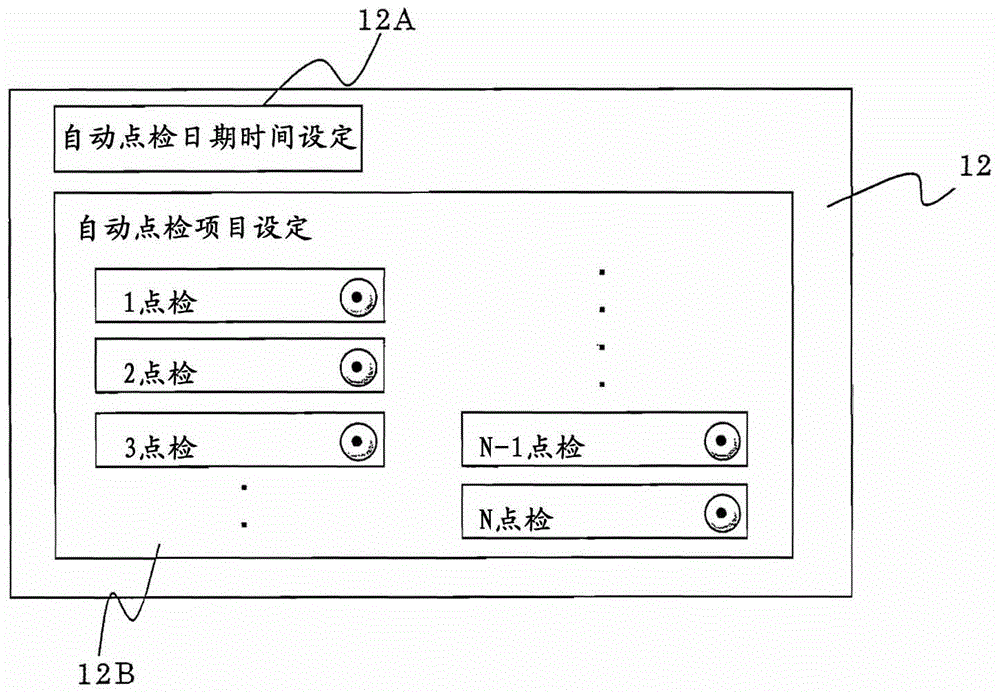
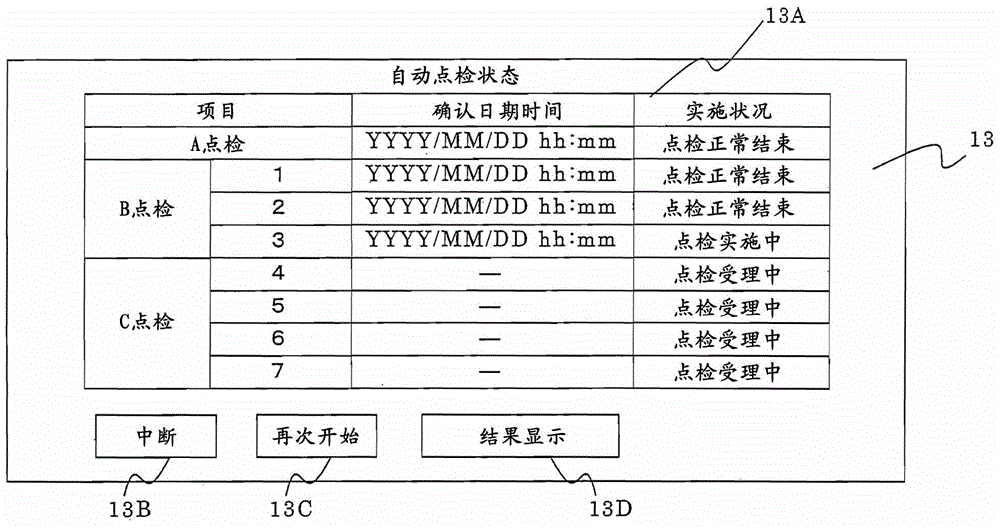
The invention provides an elevator automatic spot inspection system which can perform regular spot inspection and checking of equipment of the elevator and control motions and can efficiently collect data and guarantee services for users. In the system, the setting is carried out in such a way: specifying the date and time of an item selected from a plurality of items required by spot inspection and checking displayed by each terminal device connected with a monitoring device (5) via a communication unit, sending an instruction for automatically carrying out the spot inspection and checking of the selected item in the specified date and time to a control part (4) by an automatic spot inspection instruction part (5B) of the monitoring device (5) and an instruction for stopping the spot inspection and checking, and obtaining the results and storing the results to a spot inspection result storage part (5C) via the control part (4) to be monitored and displayed by the terminal devices, wherein the monitoring device (5) automatically carrying out the spot inspection and checking of an elevator through the control part (4) for controlling the running of an elevator car (1).
Owner:HITACHI BUILDING SYST CO LTD
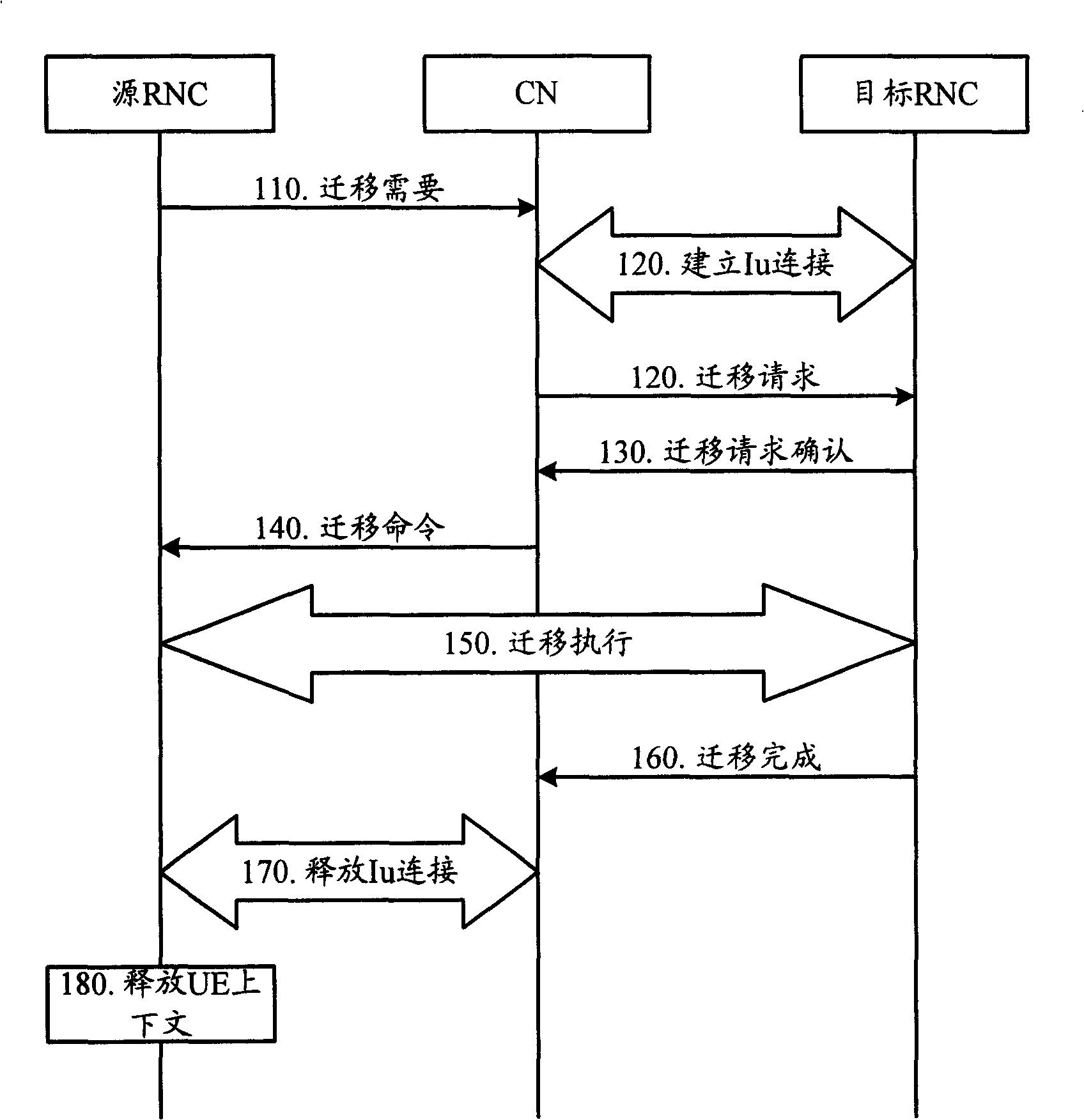
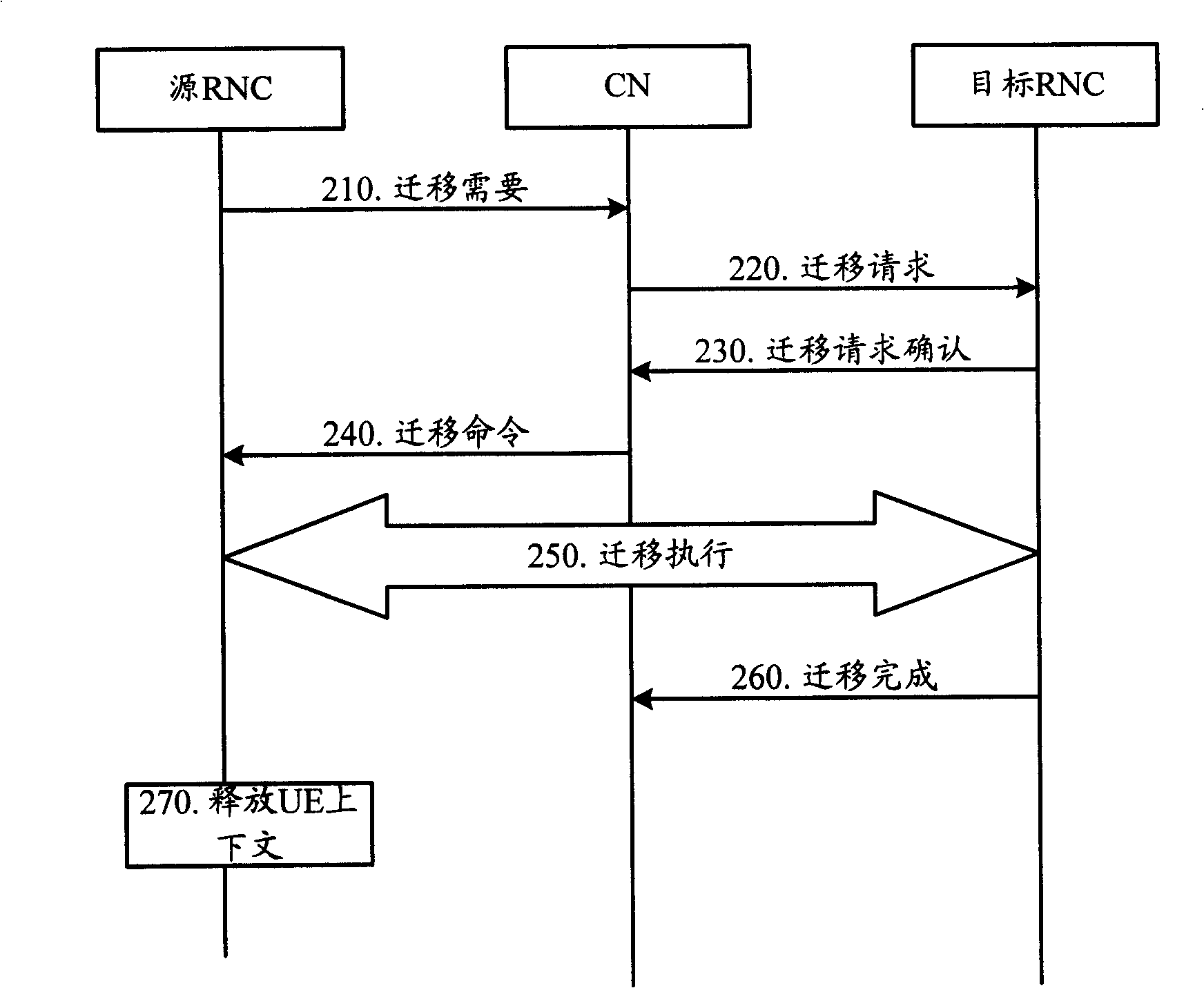
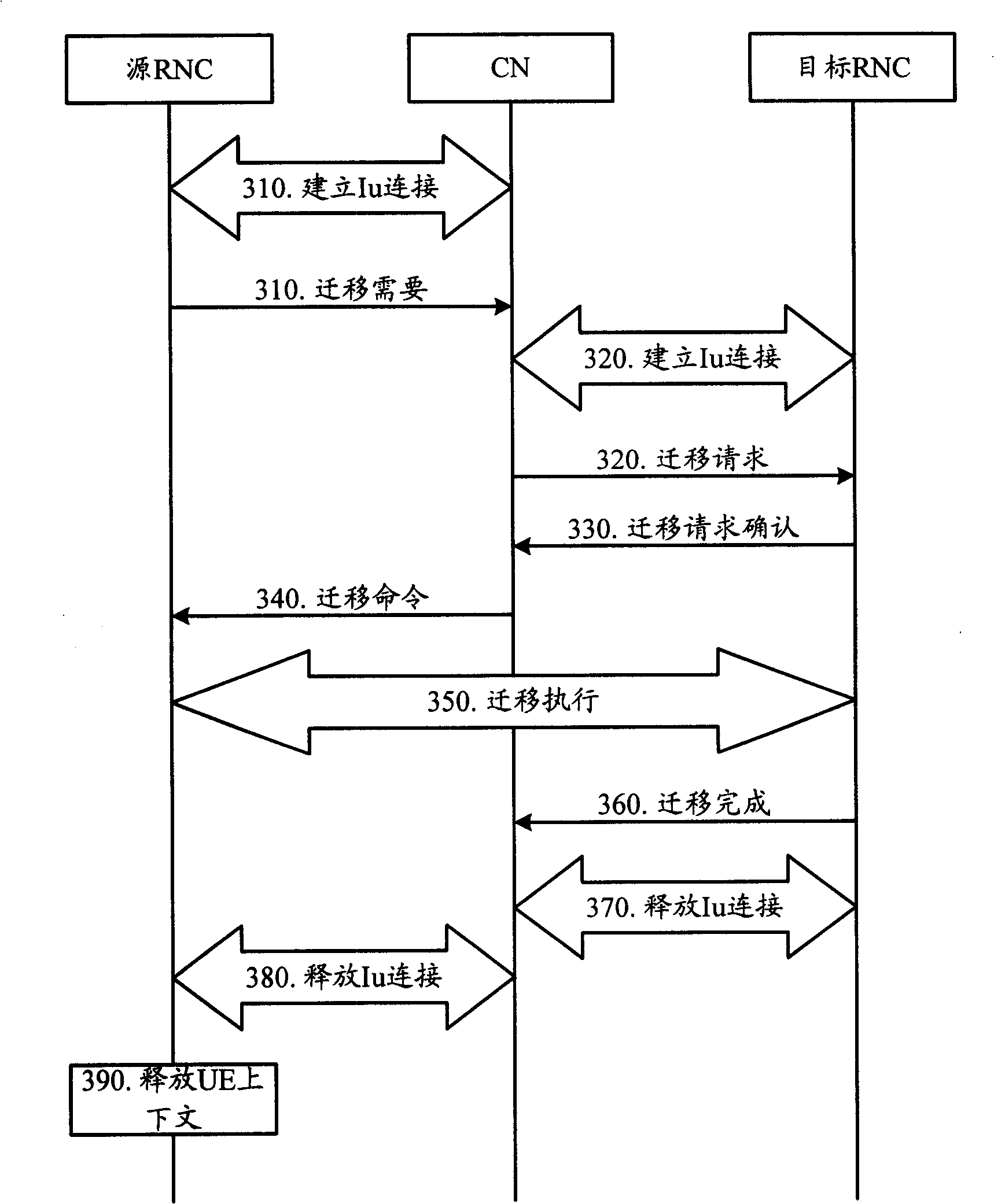
Migration method for service wireless network controller and wireless network controller
InactiveCN101262639AThe migration went smoothlyAchieve migrationRadio/inductive link selection arrangementsTelecommunicationsRadio Network Controller
The invention relates to the wireless communication field, and discloses a migration method serving a radio network controller and the radio network controller, which ensures UE to carry out service RNC migration when receiving MBMS services. When no Iu connection exists between the source RNC and CN, the migration of the service RNC can be carried out by connectionless message interaction; connection can also be established in advance and then is released after the migration is finished; the message interaction required by the service RNC migration can also be carried out by an Iur interface between the source RNC and a target RNC.
Owner:HUAWEI TECH CO LTD
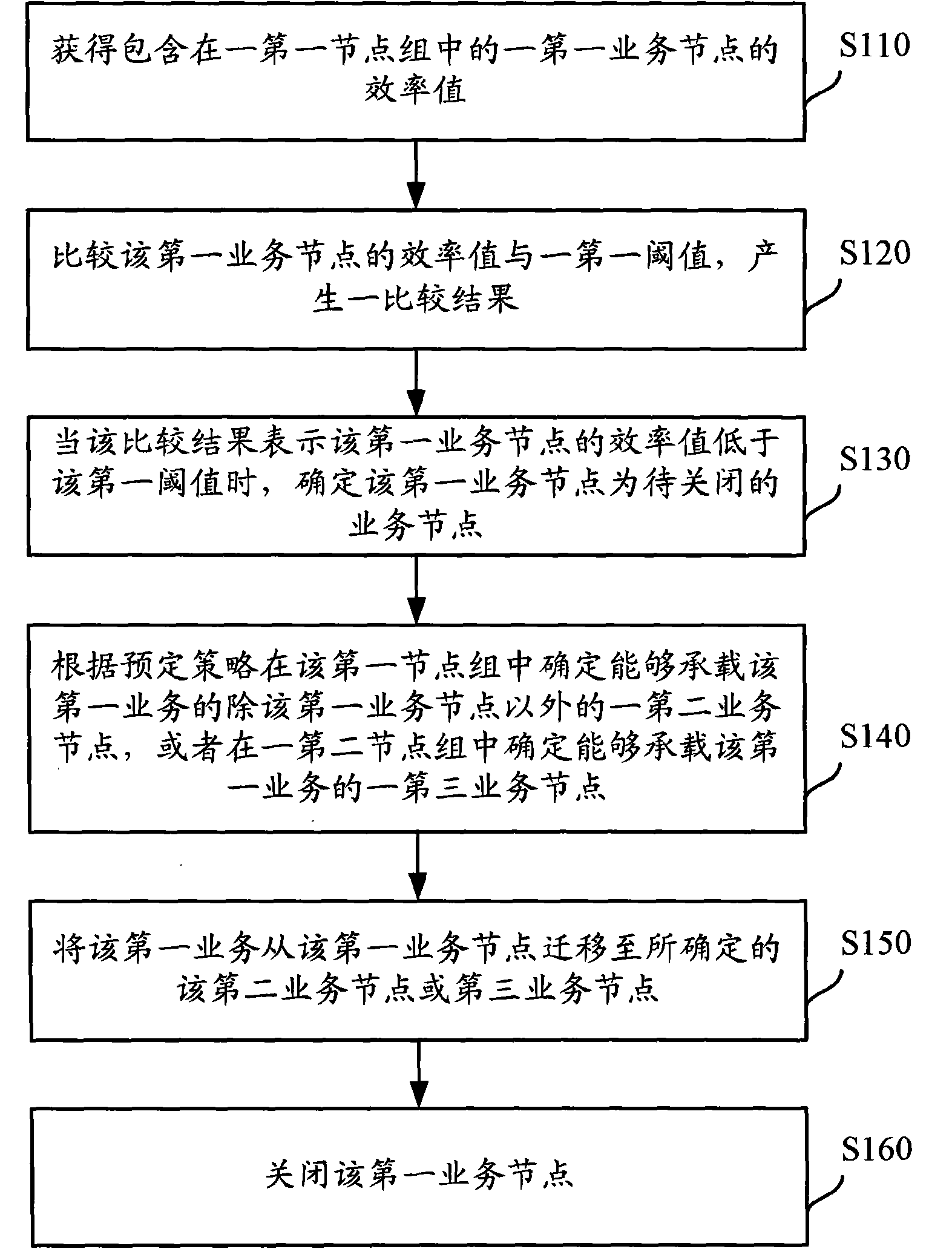
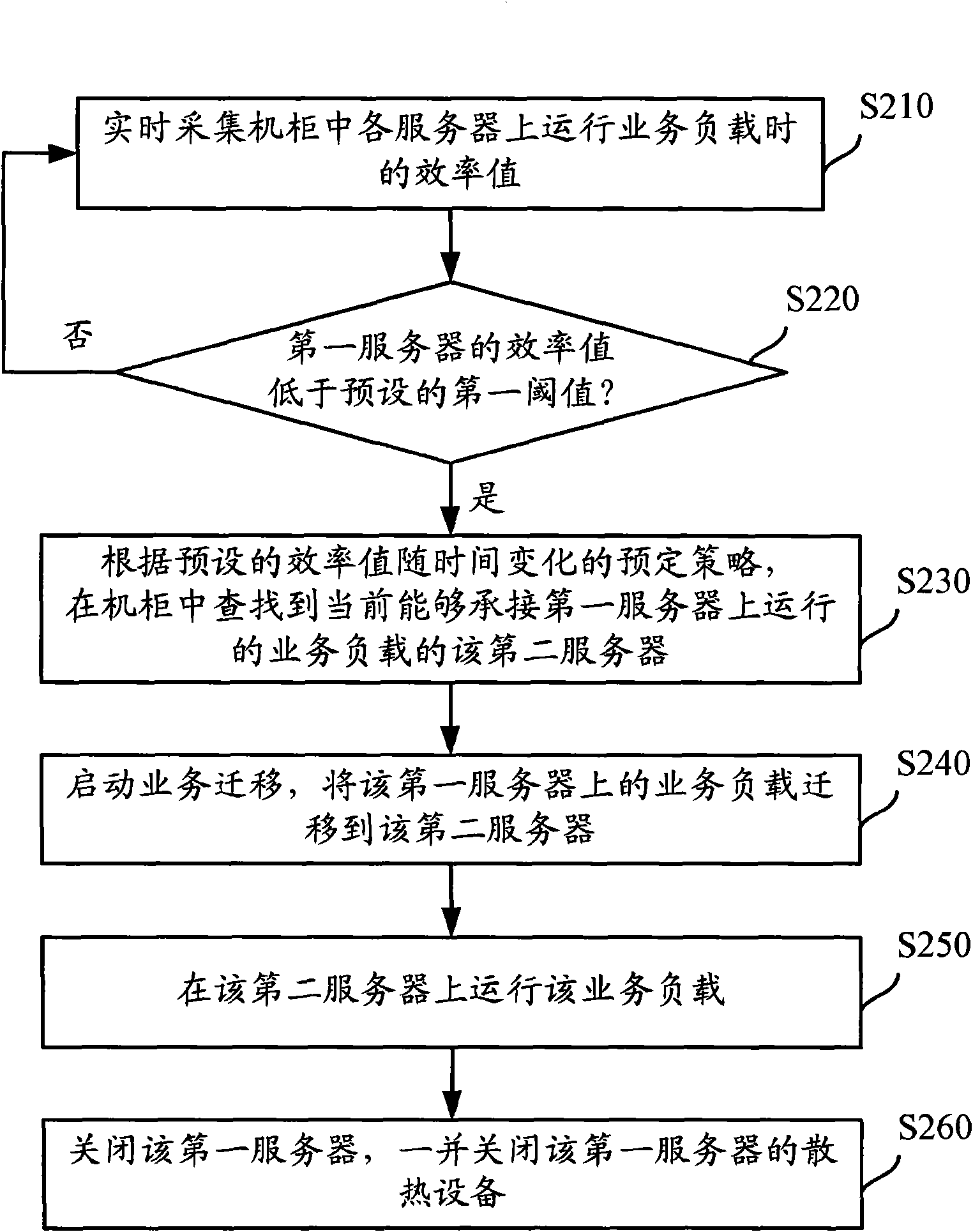
Power consumption control method, management node and data processing center
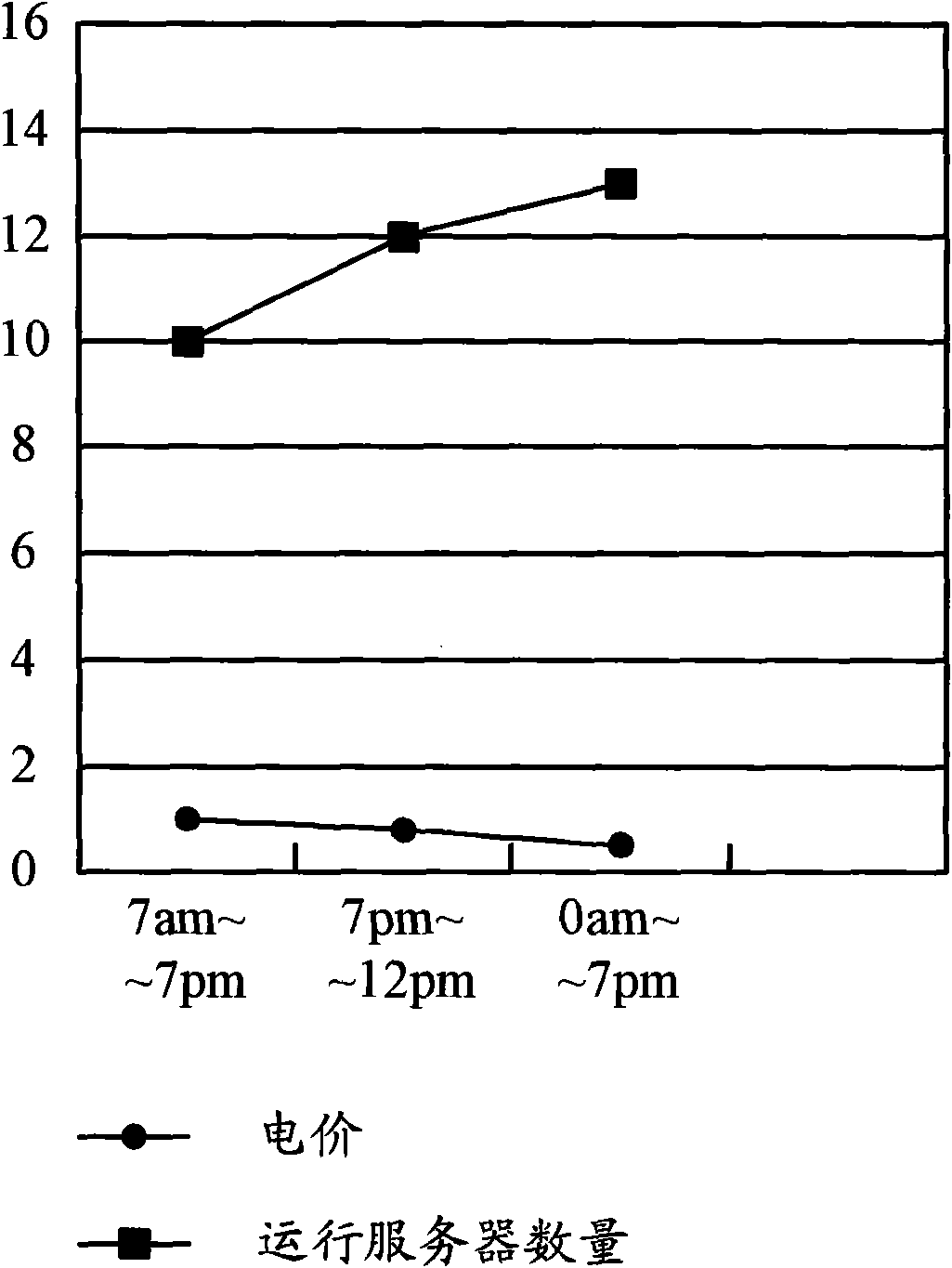
ActiveCN102387024AReduce energy consumptionSolve technical problems with huge energy consumptionEnergy efficient ICTData switching by path configurationData centerEnergy consumption
The invention discloses a power consumption control method, a management node and a data processing center, which aims to solve the technical problem of large energy consumption of big and medium data centers in the prior art. The method comprises the following steps: obtaining the efficiency value of a first service node contained in a first node group; when the efficiency value of the first service node is lower than a first threshold value, determining the first service node as a service node to be closed; according to a preset strategy, determining a second service node which can bear a first service in the first node group, or determining a third service node which can bear the first service in a second node group; transferring the first service to the determined second service node or the determined third service node from the first service node; and closing the first service node. The embodiment disclosed by the invention is characterized in that when service load applied to one service node is lower than a first preset threshold value, the service application operated on the service node is transferred to other service nodes, and the energy consumption of the whole node group is saved.
Owner:LENOVO (BEIJING) LTD
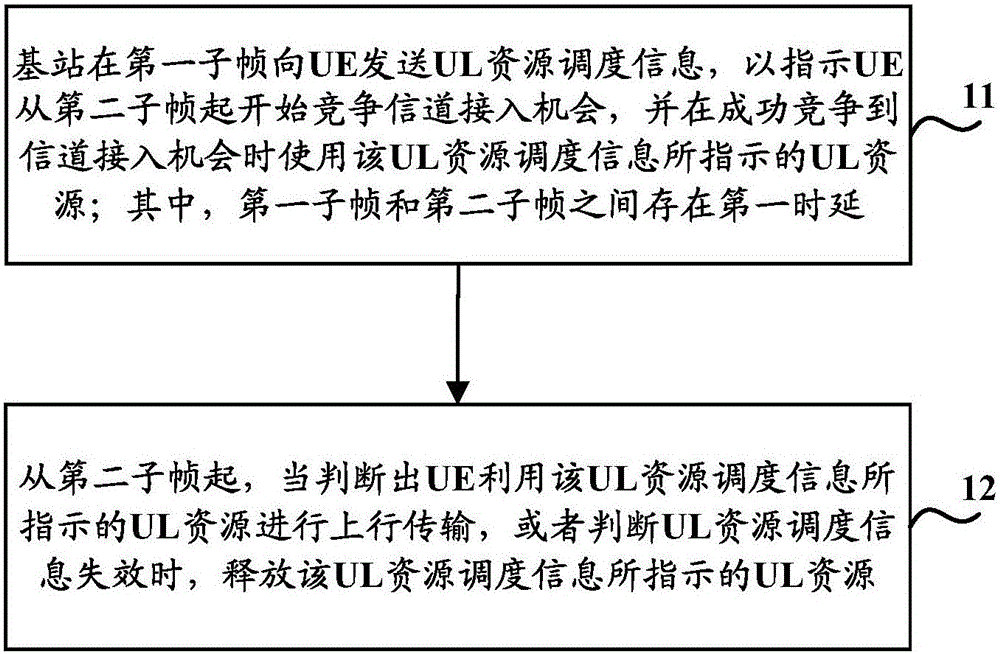
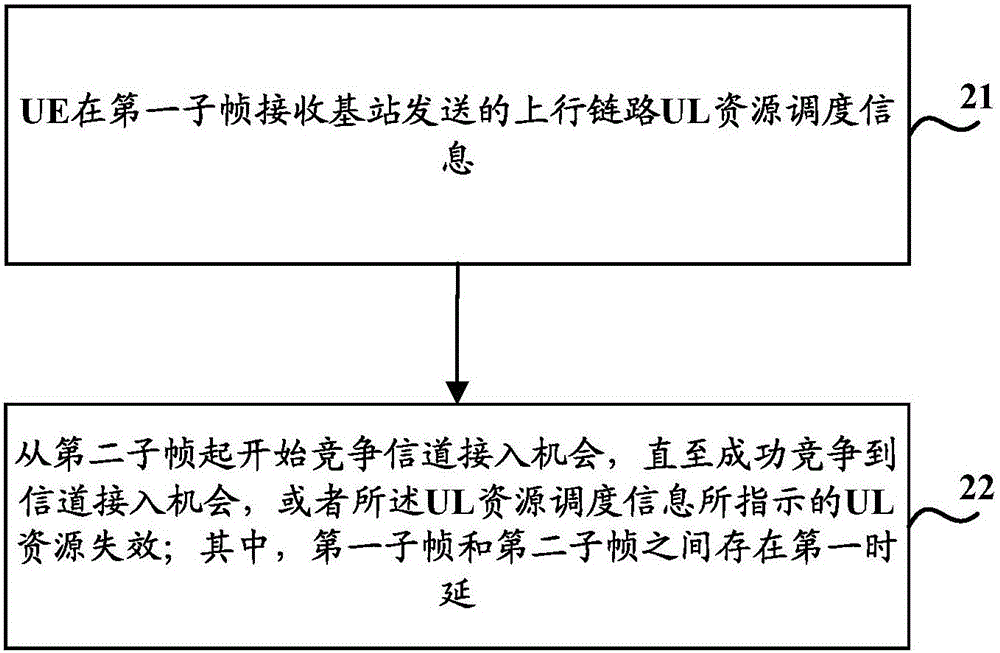
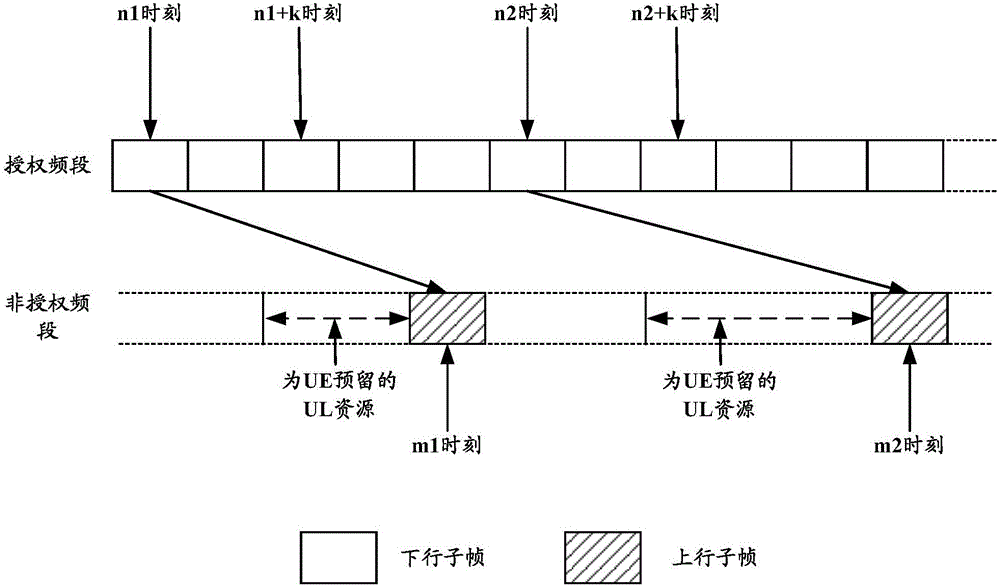
Uplink scheduling method, device and system, and equipment
The invention discloses an uplink scheduling method, device and system, and equipment, and is used for solving problems in the prior art that an uplink scheduling mechanism on an unauthorized frequency band of an LTE system can lead to the large scheduling signaling expense and the scheduling signaling waste at a network side. The method comprises that a base station sends uplink (UL) resource scheduling information to user equipment (UE) at a first subframe, which indicates that the UE starts competing a channel access opportunity from a second subframe, and when the UE successfully gets the channel access opportunity, UL resources indicated by the UL resource scheduling information are used, wherein a first time delay exists between the first subframe and the second subframe; and starting from the second subframe, when a fact that the UE uses UL resources for uplink transmission is determined or a fact that the UL resource scheduling information is invalid is judged, the UL resources indicated by the UL resource scheduling information are released.
Owner:CHINA MOBILE COMM GRP CO LTD
Communication device and method of controlling the same
InactiveCN103457759AGuaranteed normal serviceHigh bandwidthData switching networksComputer hardwareCoupling
Provided is a communication device including a plurality of physical ports, the communication device holding information for associating each of at least one logical port and at least two physical ports, the communication device being configured to: identify, when any one of the plurality of physical ports receives data including user data, one of the at least one logical port as an output destination of the data based on destination information included in the received data;select, based on the data, one of the at least two physical ports associated with the identified logical port as an destination of the data;generate coupling check data relating to one of the plurality of physical ports;transmit the coupling check data from the one of the plurality of physical ports;and transmit data including the user data from the physical port selected by a first processing unit as the output destination.
Owner:HITACHI LTD
Method and device for shunting IP stream during 3gpp access switching
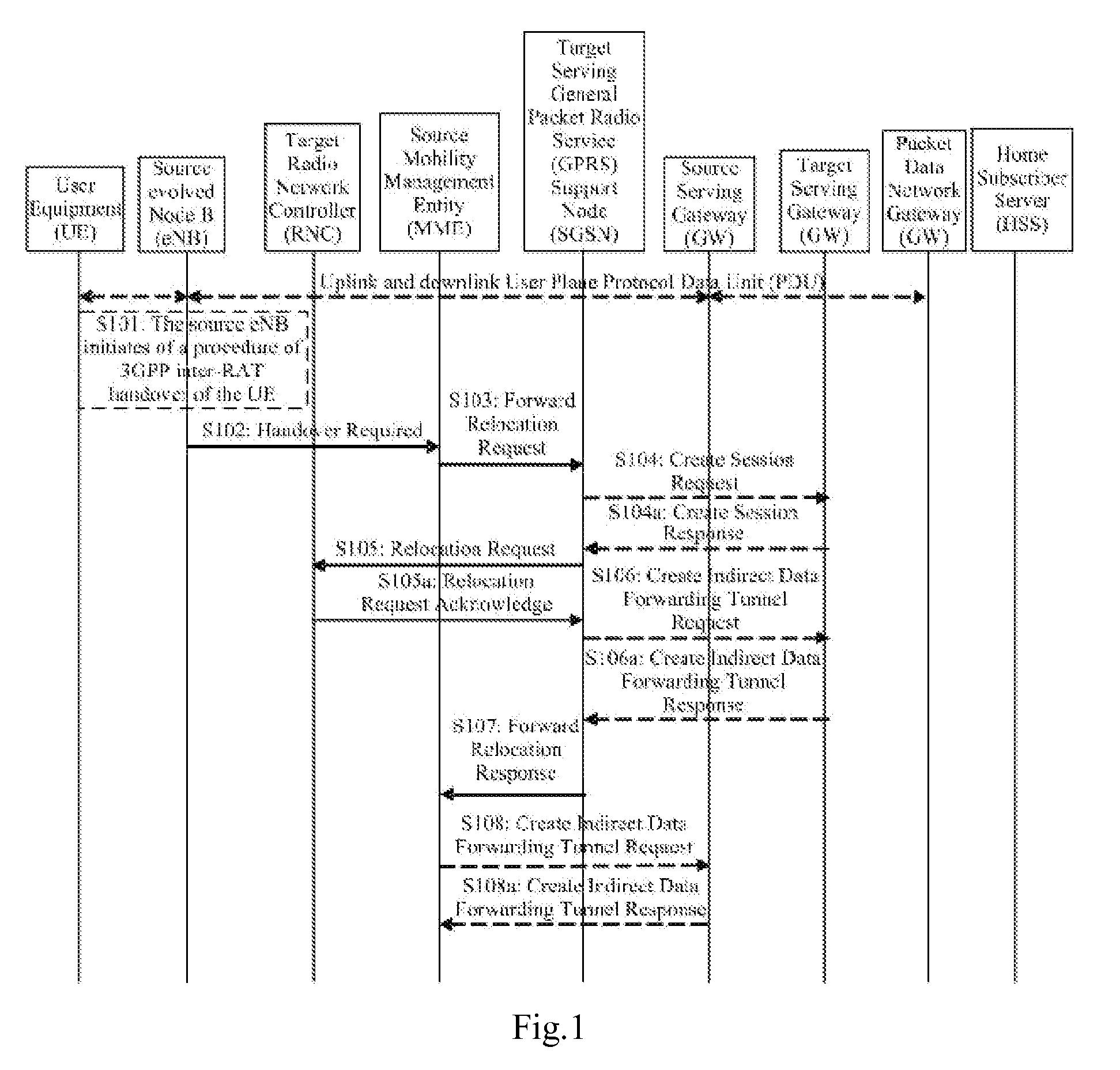
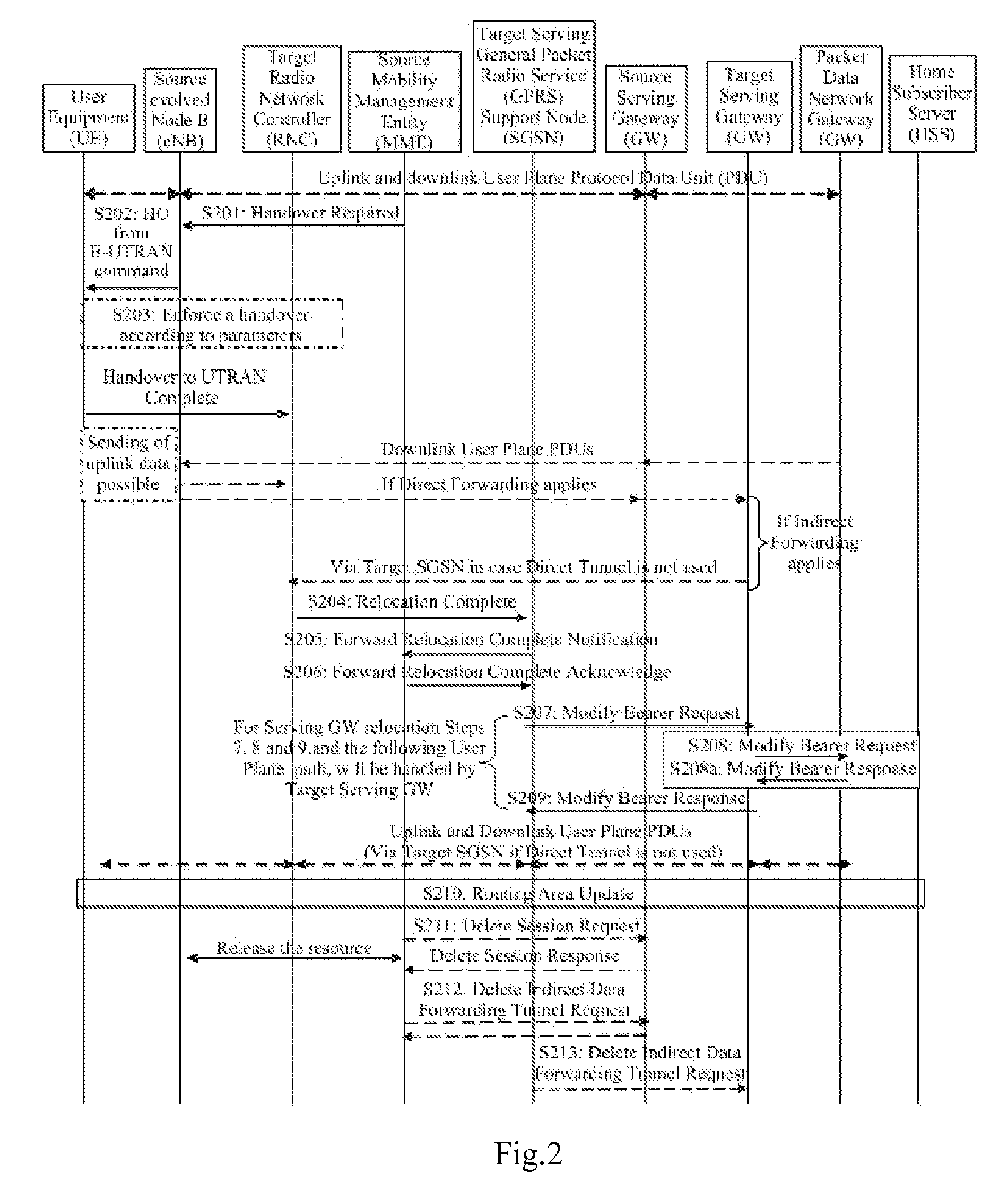
ActiveUS20150223134A1Improve efficiencyGood serviceNetwork traffic/resource managementNetwork topologiesUser equipmentResource allocation
The present application relates to the technology of communications. Disclosed are a method and device for shunting IP streams during 3GPP access switching; after having received a command for 3GPP access switching transmitted by a source 3GPP access device, a user equipment (UE) determines the IP streams to be transferred, and then performs 3GPP access switching and IP stream transferring at the same time, thus improving IP stream transferring efficiency. In addition, the IP streams to be transferred contain an IP stream capable of being transmitted via WLAN access after a target 3GPP access device fails to allocate resources to a bearers for transmitting the IP stream, thereby avoiding service interruption due to bearer loss, and thus improving the QoS ensurance for the service.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Internet-agricultural-product-based sales management system and method
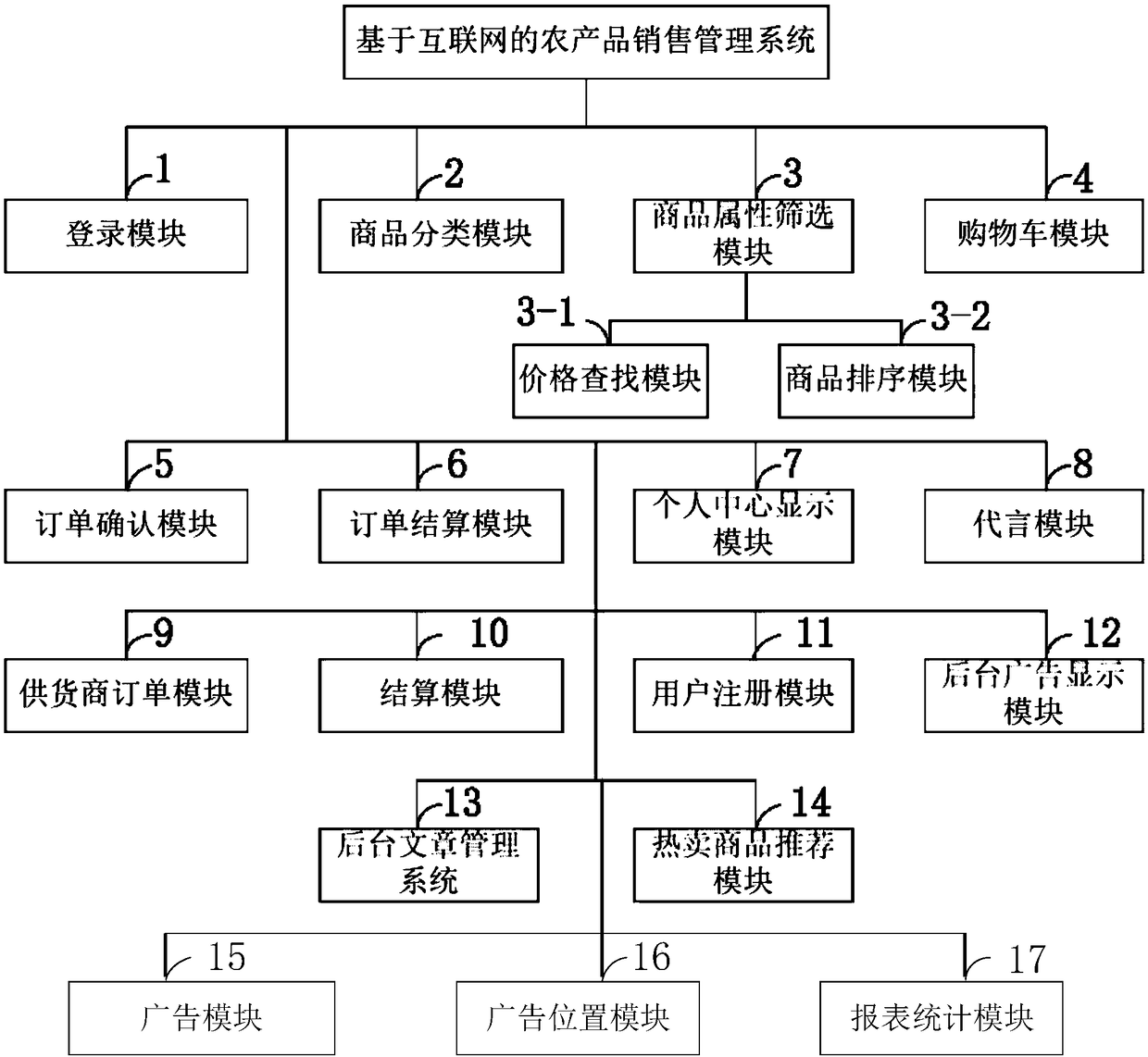
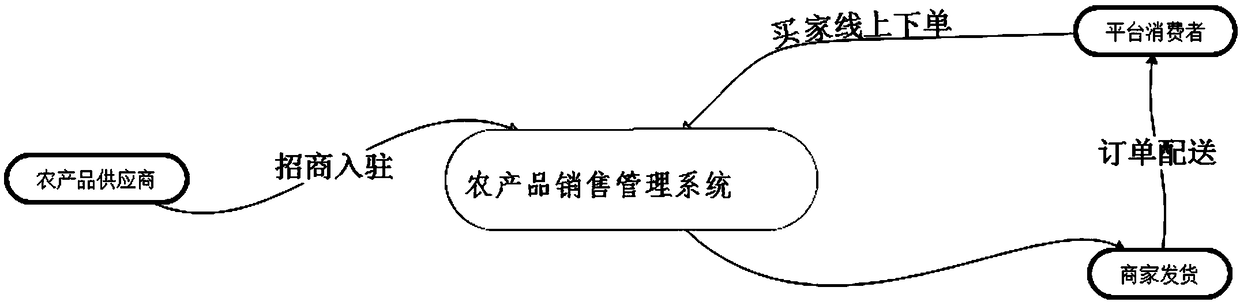
InactiveCN108932655ASolve the problem of quick salesQuick understandingBuying/selling/leasing transactionsThe InternetProduct base
The invention, which belongs to the field of internet technology, discloses an internet-agricultural-product-based sales management system and method. The system is composed of a login module, a commodity classification module, a commodity attribute screening module, a shopping cart module, an order confirmation module, an order settlement module, a personal center display module, an endorsement module, a supplier order module, and a settlement module. The settlement module is used for carrying out offline and online payment by a supplier with combination of a payment code scanning gun according to a money-receiving code of a user. On the basis of the internet related technologies, a scientific and rapid method is provided for farmers for agricultural products sales; the supply and demandof social resources are linked effectively and the product values of agricultural products are promoted by technical ways; the original ecological factors are transformed into advantage ones and thusthe original resource restrictions are changed into economic advantages; and the agricultural resources in poverty-stricken areas are activated and thus the human resources in poverty-stricken areas are mobilized.
Owner:西安拓美网络科技有限公司
Simulator of GNSS receivers
InactiveCN103499821AObservation data is true and accurateGuaranteed normal serviceSatellite radio beaconingTransmissionObservation dataSimulation
Owner:WUHAN UNIV
Report control method and device, equipment and medium
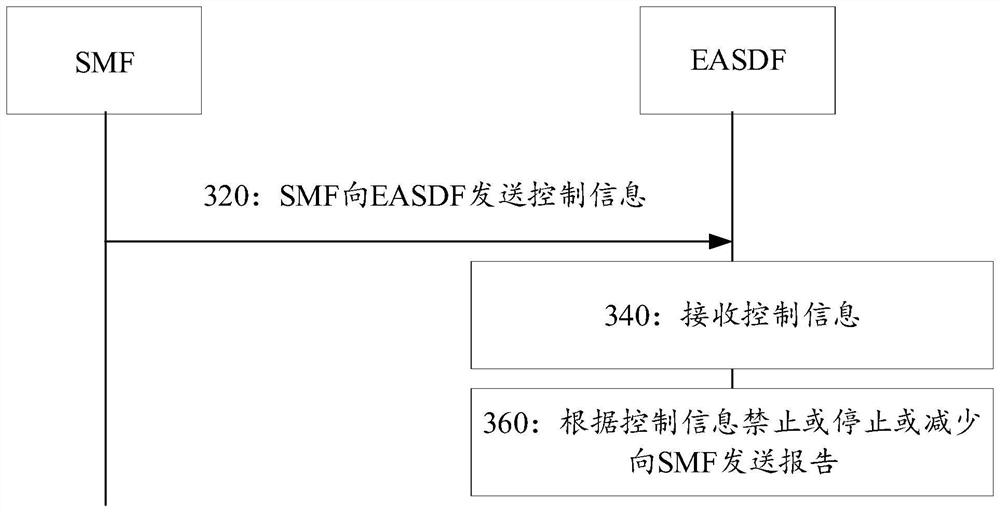
PendingCN113114651AAvoid attackGuaranteed normal serviceTransmissionSecurity arrangementComputer networkAttack
The invention discloses a report control method and device, equipment and a medium, and belongs to the field of mobile communication. The method comprises the following steps that: a SMF sends control information to EASDF, wherein the control information is used for forbidding or stopping or reducing the report sent by the EASDF to the SMF. According to the method and the device, the EASDF cannot send a report to the SMF without limitation, so that DOS attacks initiated by abnormal UE are defended, and a mobile communication system is guaranteed to provide services for more UE as much as possible.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for dynamic measurement of liquid surface morphology and dosage of liquid propellant in storage tank
InactiveCN104154955AImprove measurement accuracy and sensitivityLess equipmentMeasurement devicesOut of planeNumeric Value
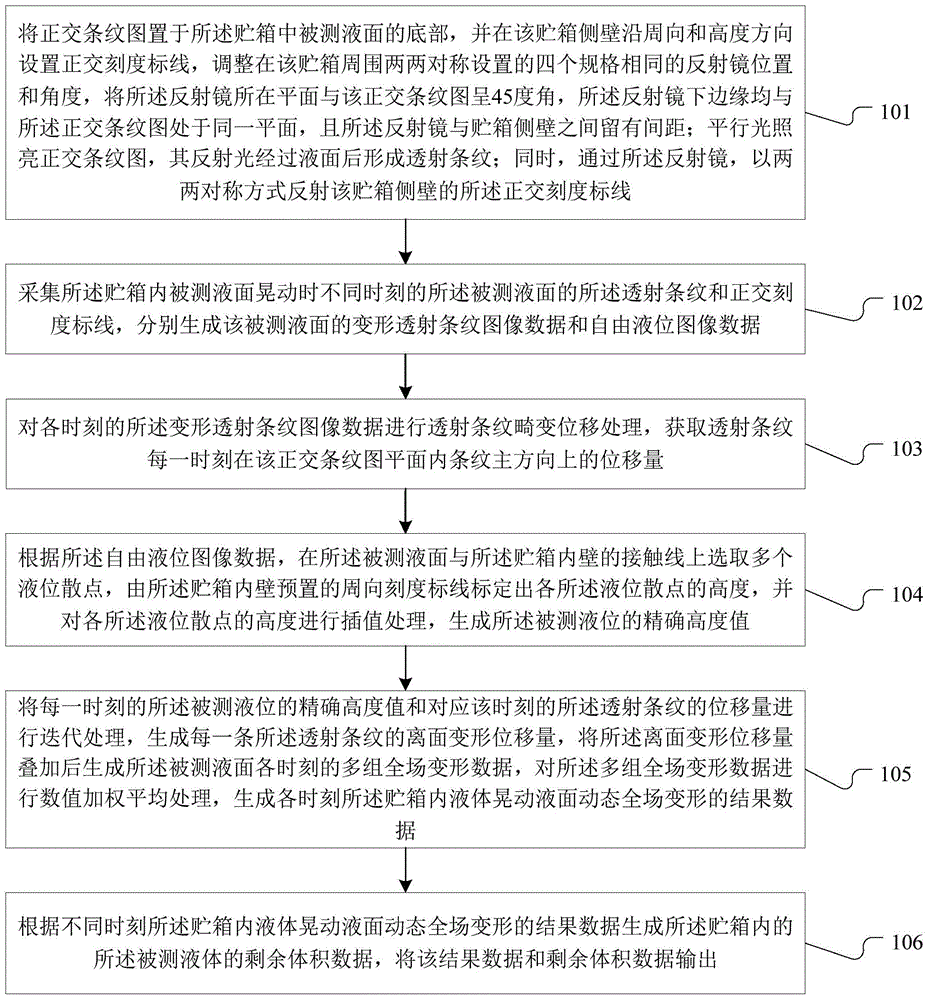
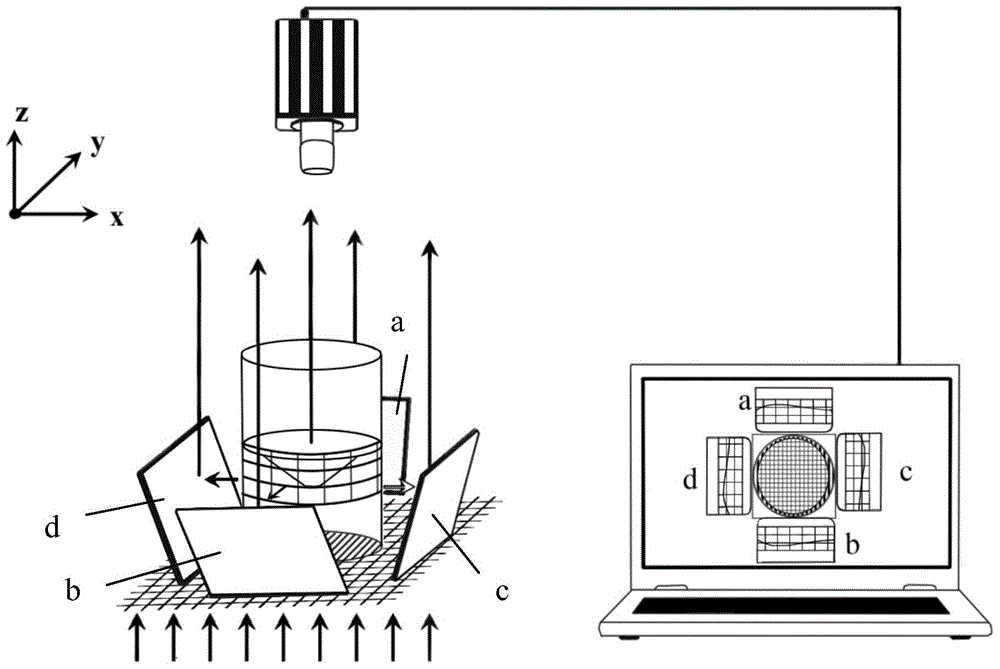
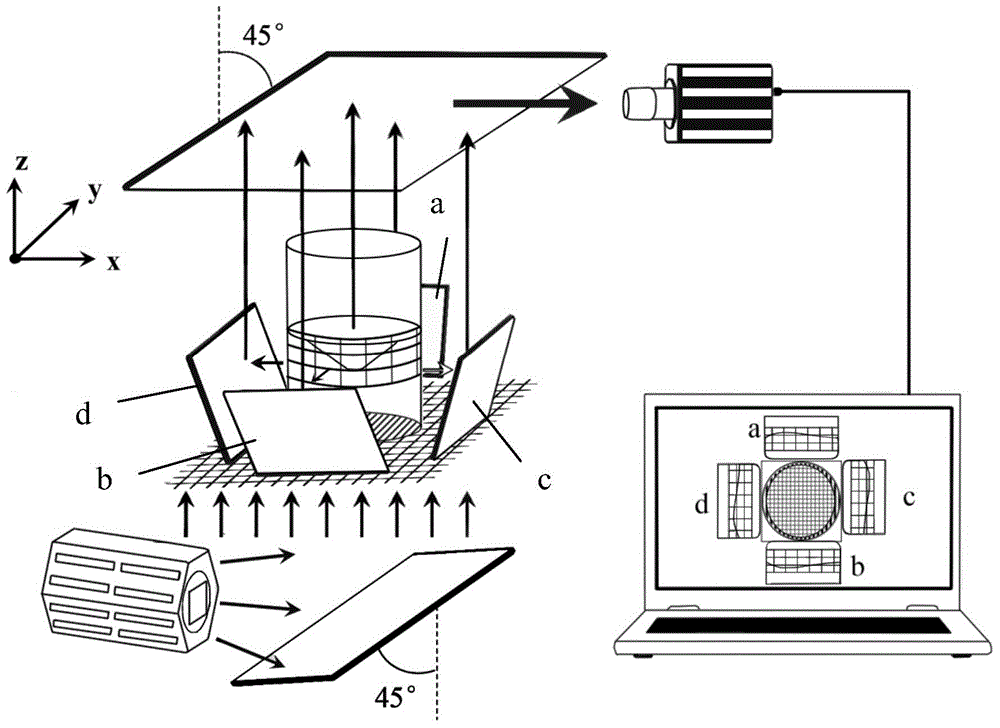
The invention discloses a method and system for dynamic measurement of the liquid surface morphology and the dosage of liquid propellant in a storage tank. An orthogonal stripe pattern is arranged at the bottom of a measured liquid surface in the storage tank, orthogonal scale mark lines are arranged on the side wall of the storage tank, reflectors symmetrically arranged on the periphery of the storage tank are adjusted, transmission stripes and orthogonal scale mark lines are acquired when liquid waggles, and deformation transmission stripe image data and free liquid level image data are generated respectively; the displacement is acquired according to the deformation transmission stripe image data; the accurate height value of the liquid level is generated according to the free liquid level image data; according to the accurate height value and the displacement, the out-of-plane deformation displacement is generated, and then value weighted averaging is performed after multiple groups of whole deformation data are generated so that the result of changes of the whole liquid surface along with time can be obtained; residual volume data of measured liquid can be generated according to the whole deformation result data, and the result data and the residual volume data are output. According to the method and system, multi-directional liquid level height information, liquid surface morphology changes, residual volume and other parameters can be obtained just with one high speed camera.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Spark and MBBO algorithm-based parallel virtual machine aggregation method
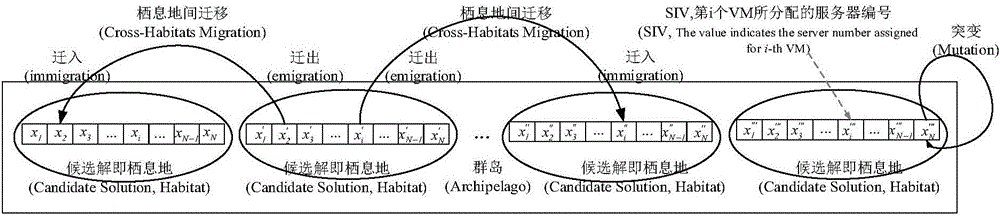
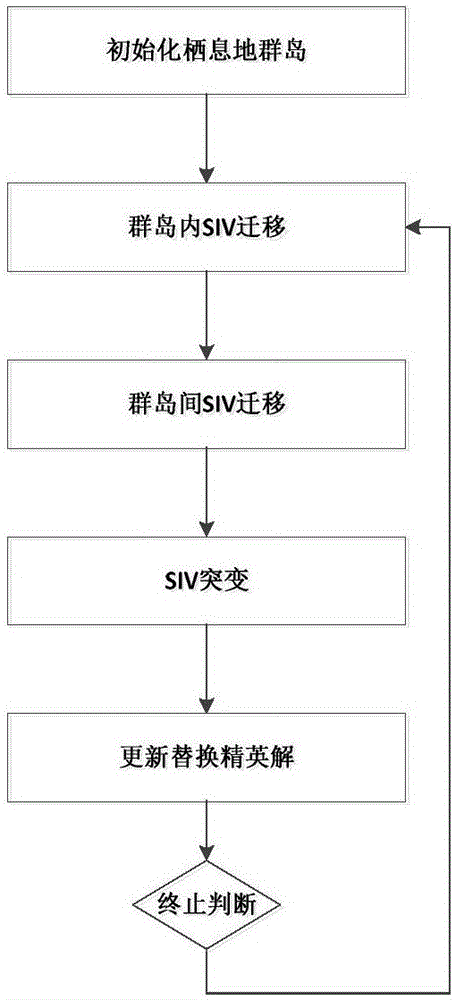
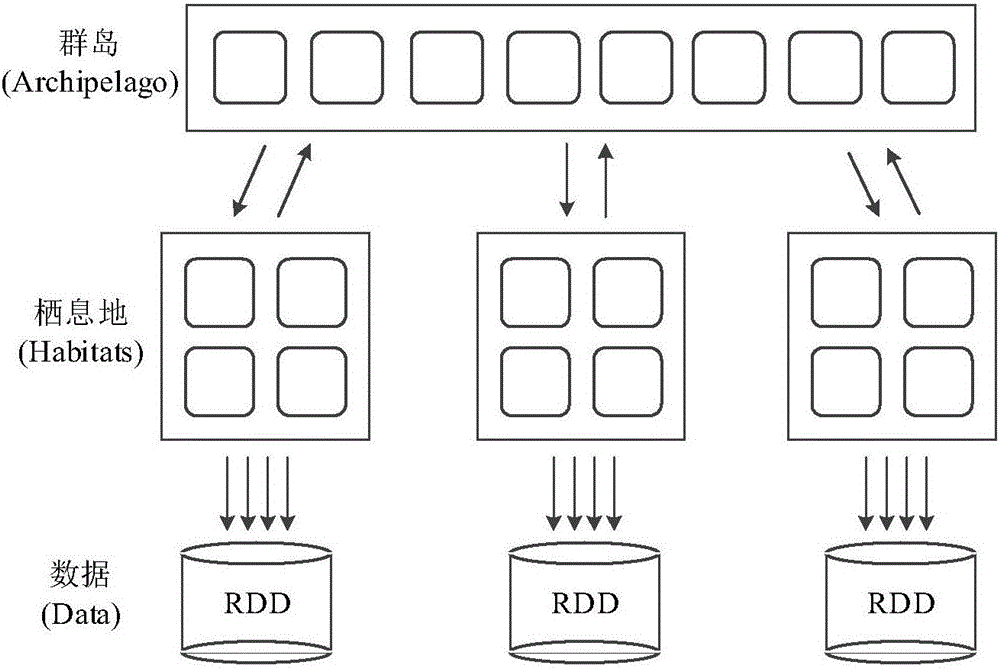
ActiveCN106843997ATake advantage of solver performanceReduce congestionSoftware simulation/interpretation/emulationBiogeographyParallel algorithm
The invention provides a Spark and MBBO (multi-objective biogeography-based optimization) algorithm-based parallel virtual machine aggregation method. Through an extended Spark parallel framework and an MBBO algorithm, an optimal migration solution of a VMC problem can be solved in a relatively short convergence time, and a foundation is laid for subsequent virtual machine parallel migration. The method comprises the following steps of 1, mapping a virtual machine aggregation problem to a biogeography-based optimization algorithm, determining constraint conditions, and clearly determining solving objectives; and 2, based on the extended Spark parallel framework, distributing an initial habitat group meeting the constraint conditions to Spark computing nodes, iteratively executing an MBBO parallel algorithm, stopping algorithm execution until a stop condition is met, and obtaining an optimal solution capable of balancing a plurality of optimization solving objectives. While the extended Spark parallel framework is utilized, a biogeography concept is mapped to an optimization problem.
Owner:XI AN JIAOTONG UNIV
Group call management
ActiveCN105939950AReduce the possibility of misuseImprove efficiencyElevatorsMachine visionComputer science
In elevator journey prioritization often calls for larger groups are prioritized. This is often misused by placing elevator calls for larger groups that are actually travelling. This problem can be reduced by identifying the calling person when placing the call and again in the elevator. The number of people in the elevator can be estimated by using machine vision or weight-based approximation methods. When the number of passengers is not known the possible misuse can be suspected if a person places considerably more group calls as than average.
Owner:KONE OYJ
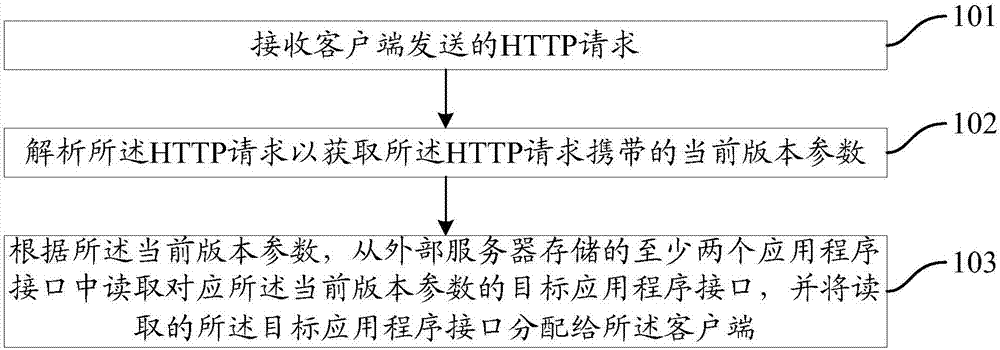
Application program interface allocation method, routing middleware and service system
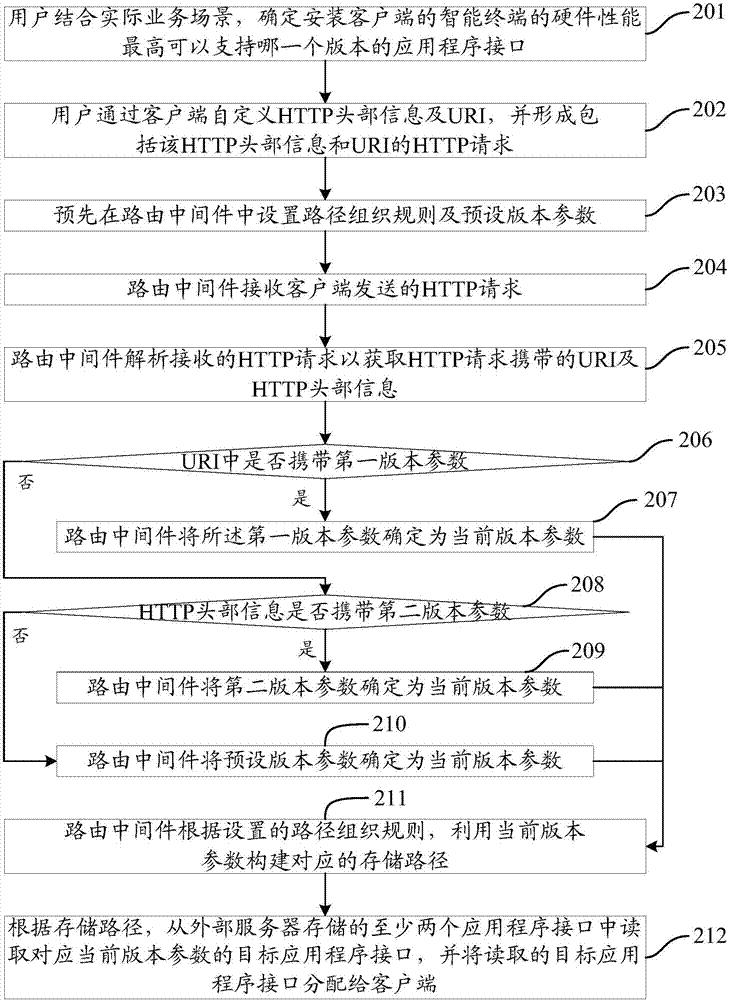
The invention provides an application program interface allocation method, a routing middleware and a service system. The application program interface allocation method is applied to the routing middleware. The application program interface allocation method comprises the following steps: receiving a HTTP request sent by the client; parsing the HTTP request to obtain the current version parameters carried by the HTTP request; and reading the target application program interface corresponding to the current version parameters from at least two application program interfaces stored by an external server according to the current version parameters, and allocating the read target application program interface to the client. By means of the technical scheme provided by the invention, the problem that the intelligent terminal that is installed the client does not support the allocated application program interface can be prevented, and the client can call the service provided by the server through the allocated application program interface can be ensured.
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
Message traffic control method, equipment and system
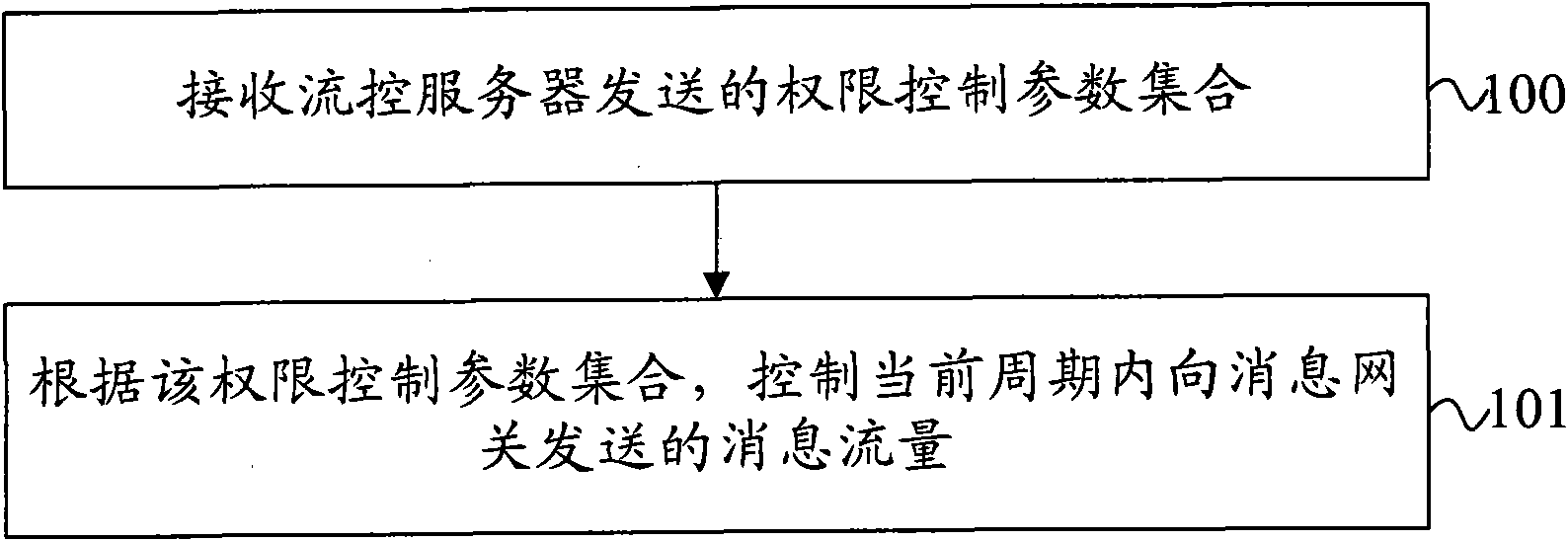
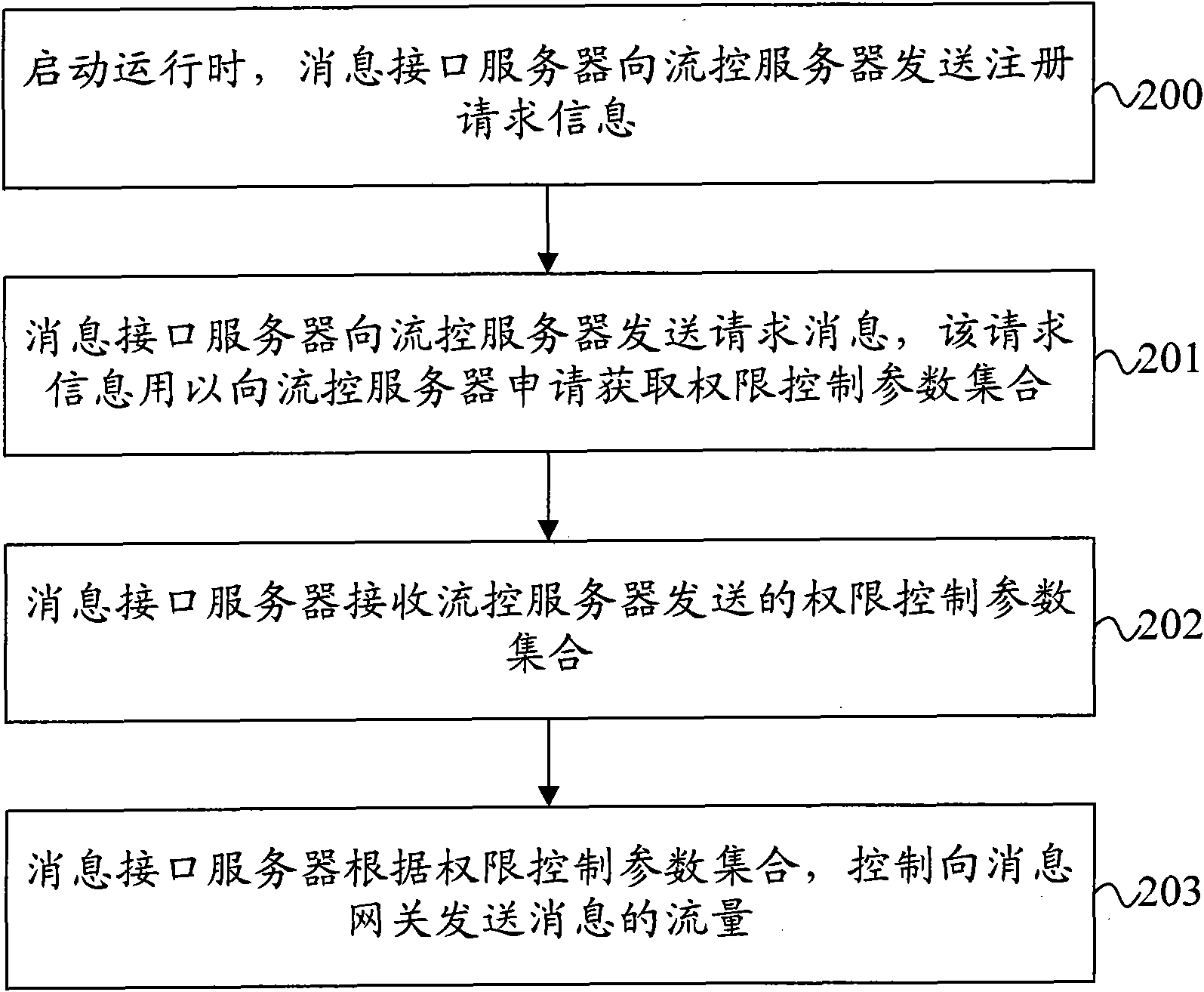
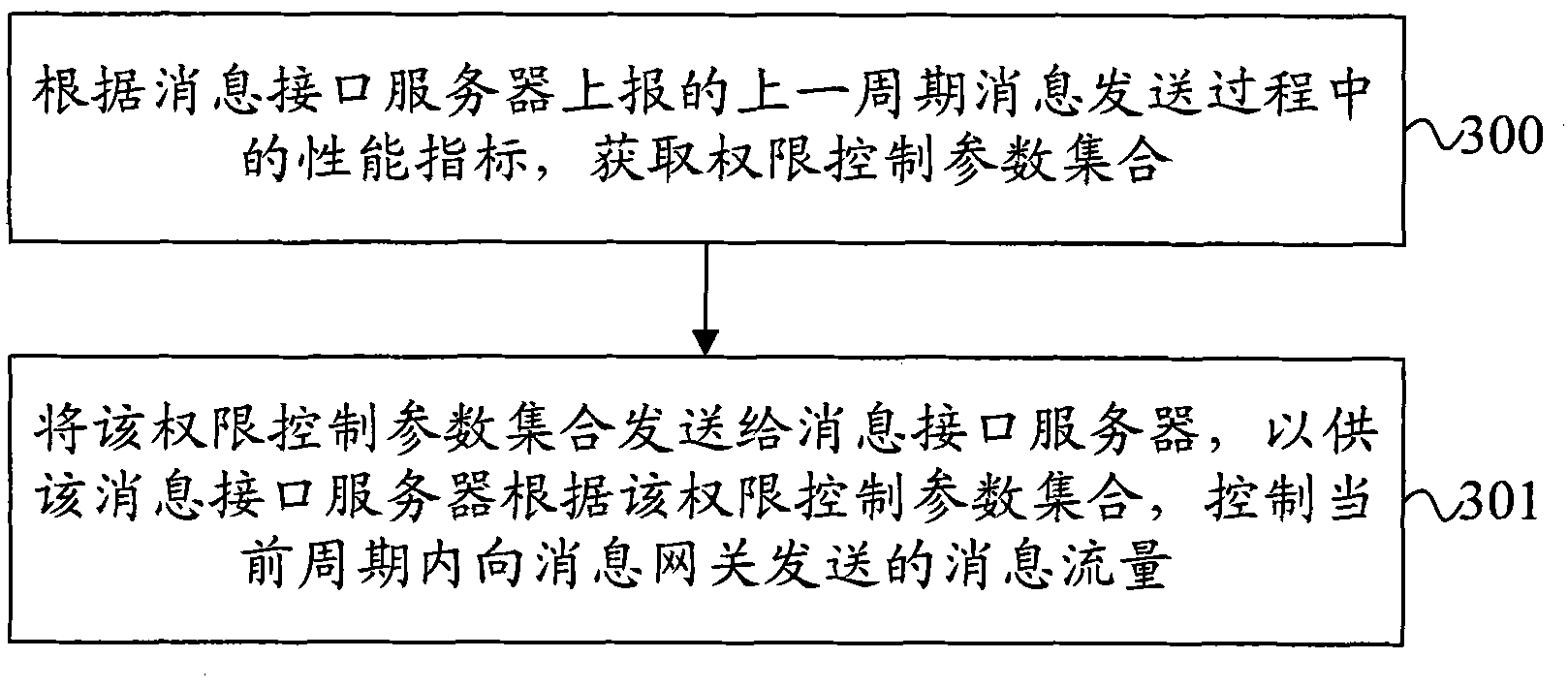
InactiveCN102148750AImprove control efficiencyEnsure synergyData switching networksPerformance indexControl equipment
The invention provides a message traffic control method, message traffic control equipment and a message traffic control system. The message traffic control method comprises the following steps of: receiving a right control parameter set from a traffic control server, wherein the right control parameter set comprises a maximum transmission rate and a transmission time length, and is configured for a message interface server by the traffic control server according to performance indexes of the message interface server in the message transmission process of the last period; and controlling the traffic of messages transmitted to a message gateway in a current period according to the right control parameter set. By the technical scheme of the embodiment of the invention, the message transmission traffic submitted to the message gateway by the message interface server can be timely, dynamically and adaptively controlled and regulated, thereby reducing impact on peripheral network elements of a voice mail service (VMS) system and ensuring coordination and cooperation between the VMS system and the peripheral network elements.
Owner:HUAWEI SOFTWARE TECH
Dynamic cluster-based news service method
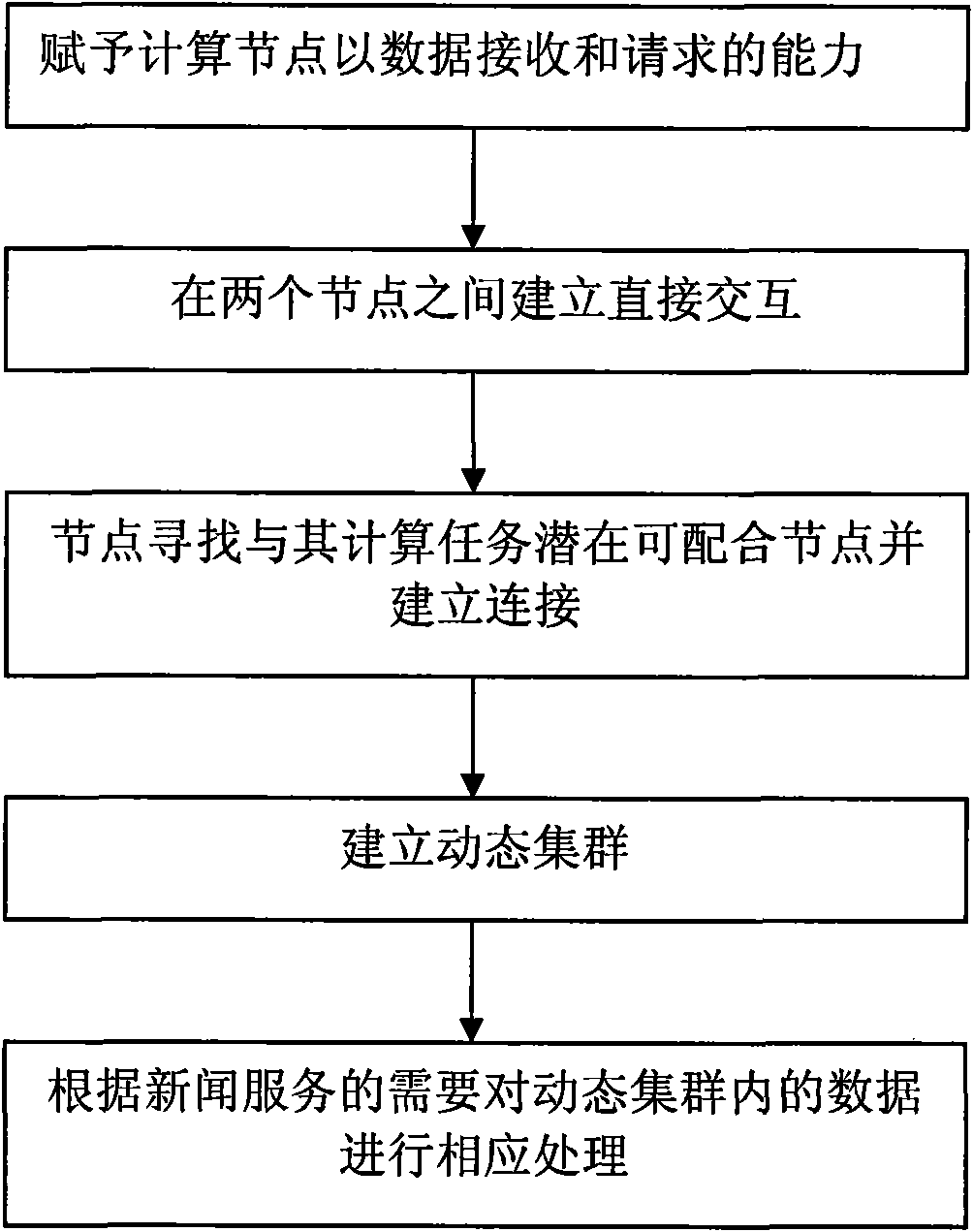
InactiveCN101645911AEnsure fairnessPlay value effectivelyData switching networksThe InternetCluster based
The invention discloses a cluster-based news service method and belongs to the field of Internet application and development. The method comprises: firstly, establishing data receiving and request mechanisms at computing nodes; secondly, establishing direct interaction between any two nodes to allow the nodes to find potential nodes that can be matched with the computing tasks of the nodes and establishing connection between the nodes and the potential nodes; and finally, establishing a dynamic cluster according to a stream network protocol, wherein a news system performs corresponding processing of data in the dynamic cluster according to the needs of news service. The news service method can grasp the change of news timely and accurately for providing various news services such as effective news sequencing and interaction function supply timely and effectively.
Owner:PEKING UNIV
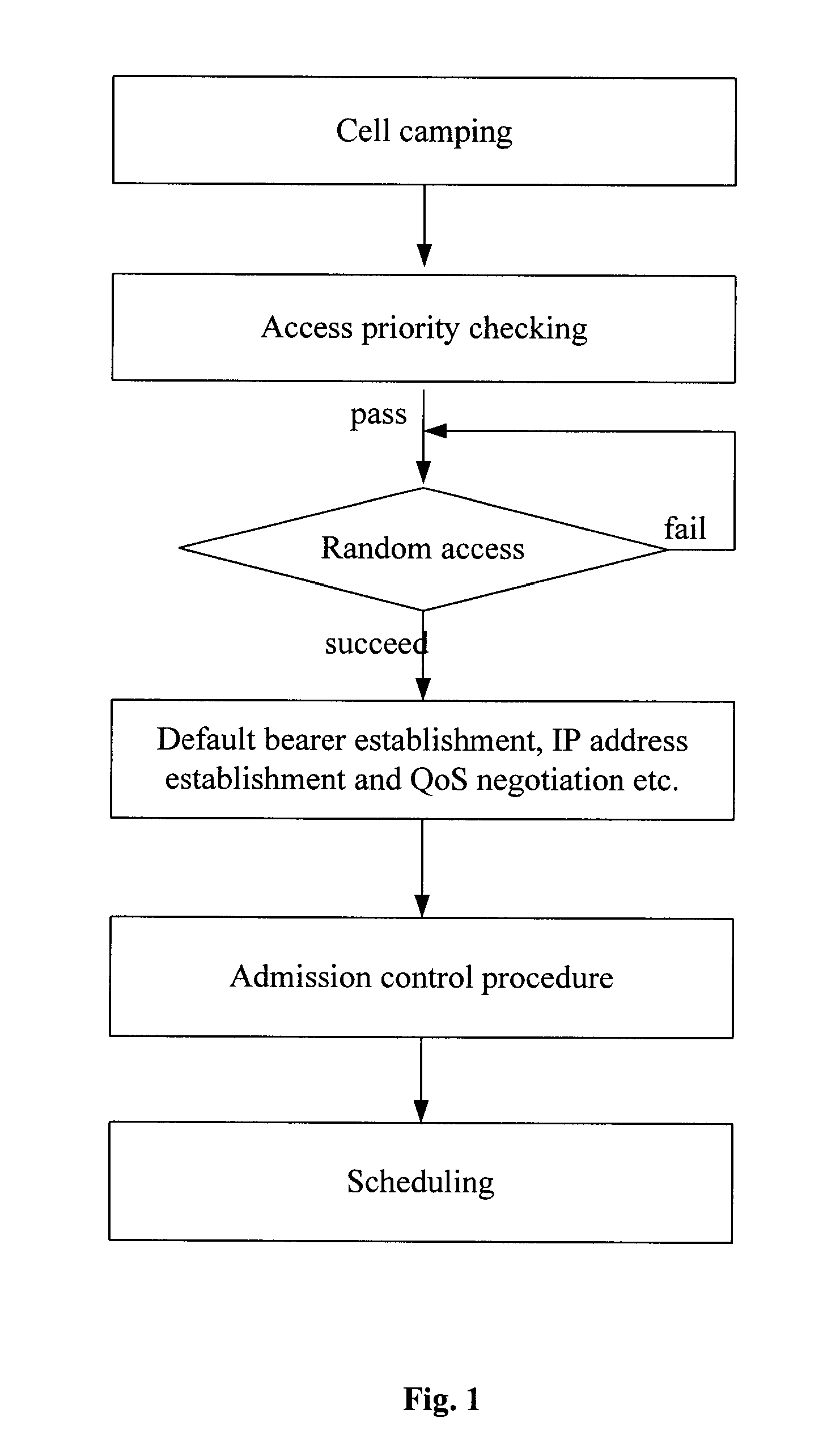
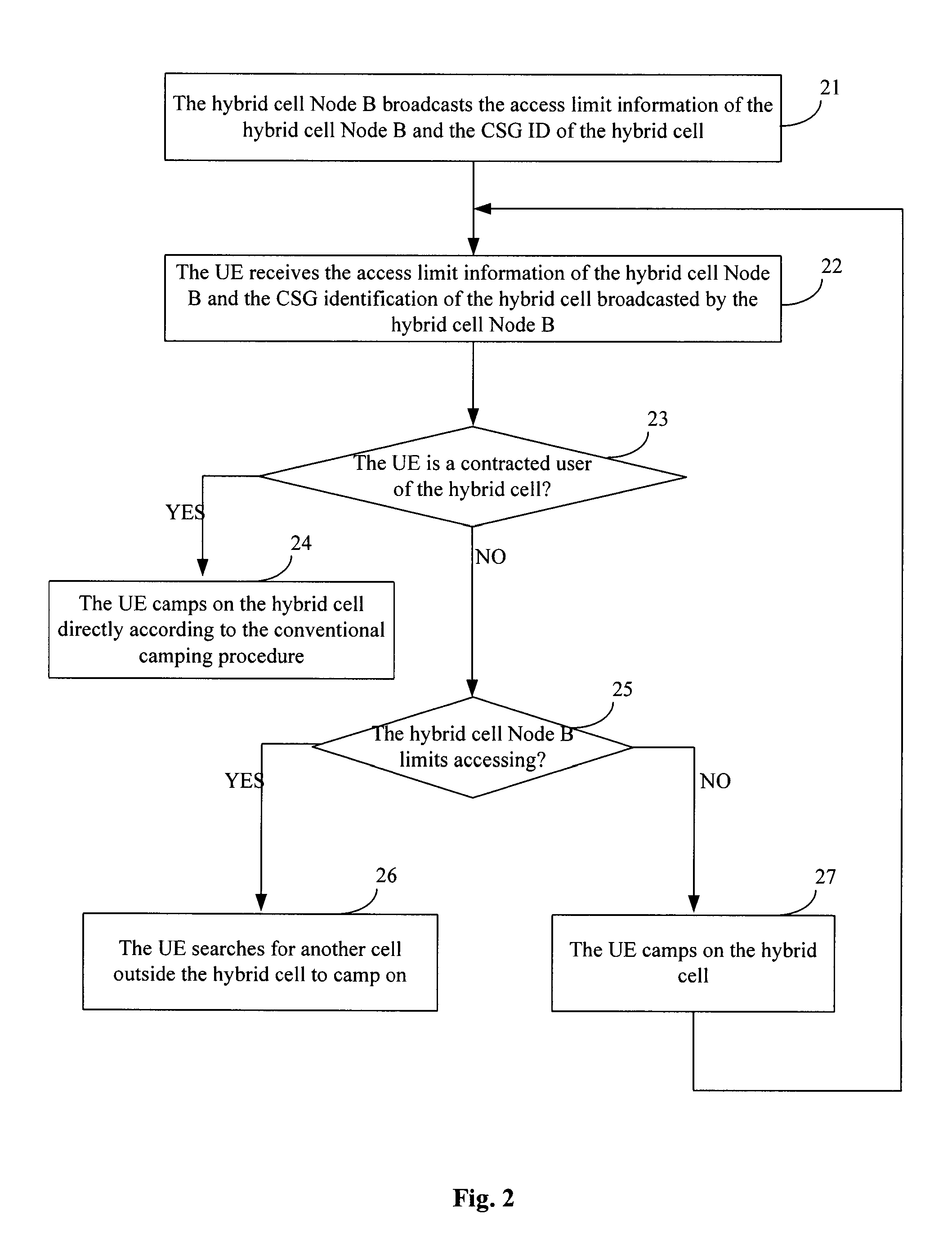
Method of camping on a hybrid cell and checking access priority and device therefor
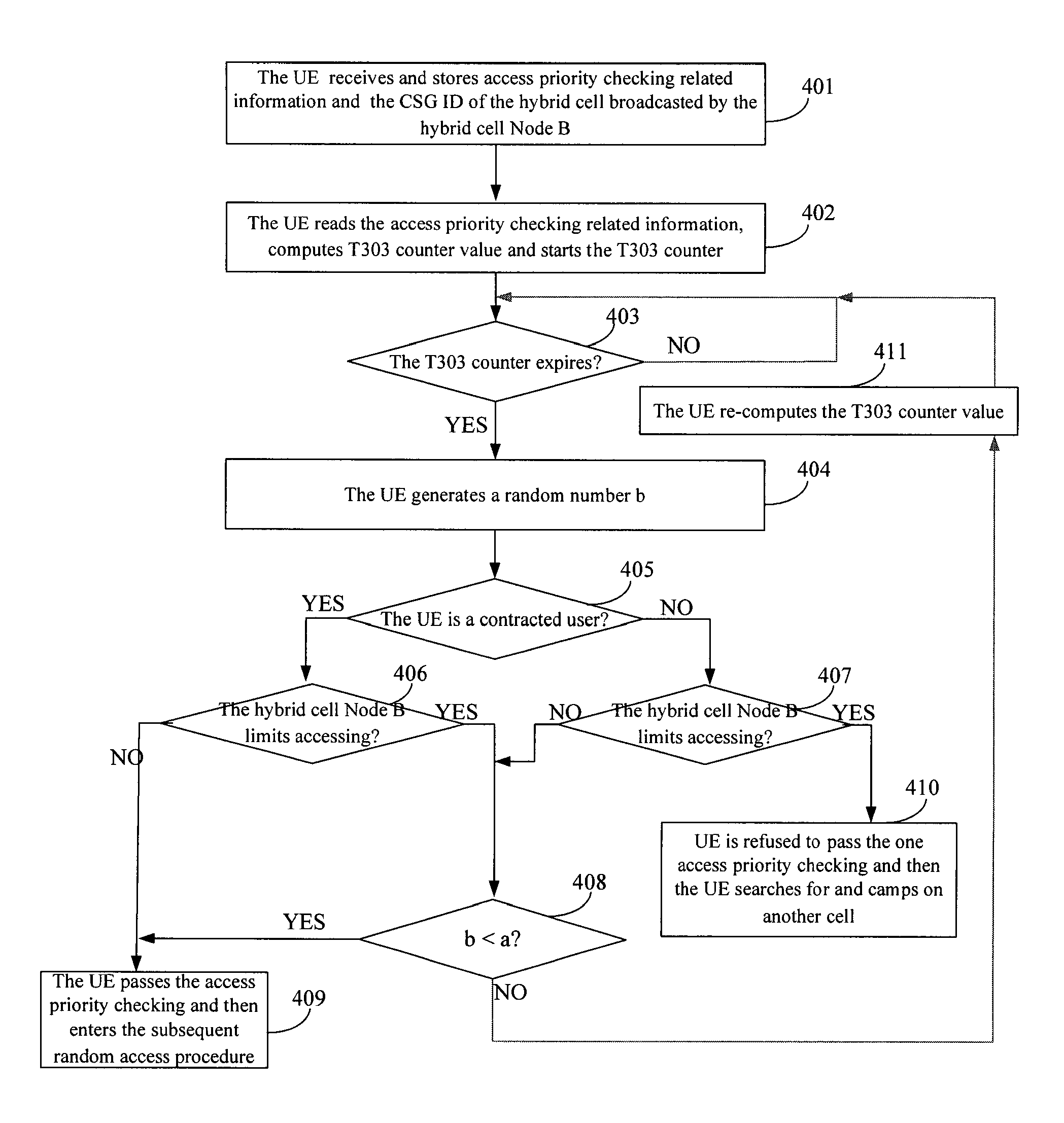
InactiveUS8340705B2Reduce access latencyImprove access efficiencyEnergy efficient ICTAssess restrictionReal-time computingWeb resource
Methods of camping on a hybrid cell and checking access priority and devices therefor are provided. The service of a CSG user is preferably guaranteed by adjusting a UE's camping right and a passing probability of an access priority checking according to the user's contracted characteristic and limit access information of a hybrid cell Node B. At the same time, the initial access delay of a non-CSG user is reduced, the initial access efficiency of the non-CSG user is improved, and the network resource and the UE's power are saved.
Owner:NTT DOCOMO INC
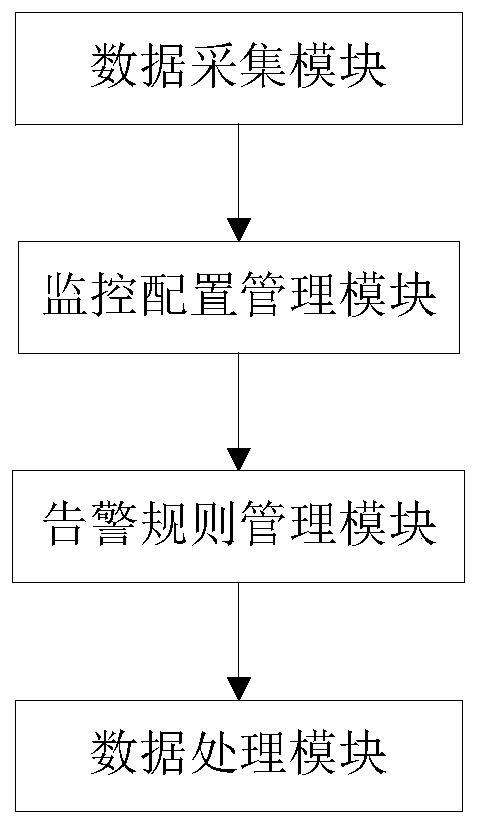
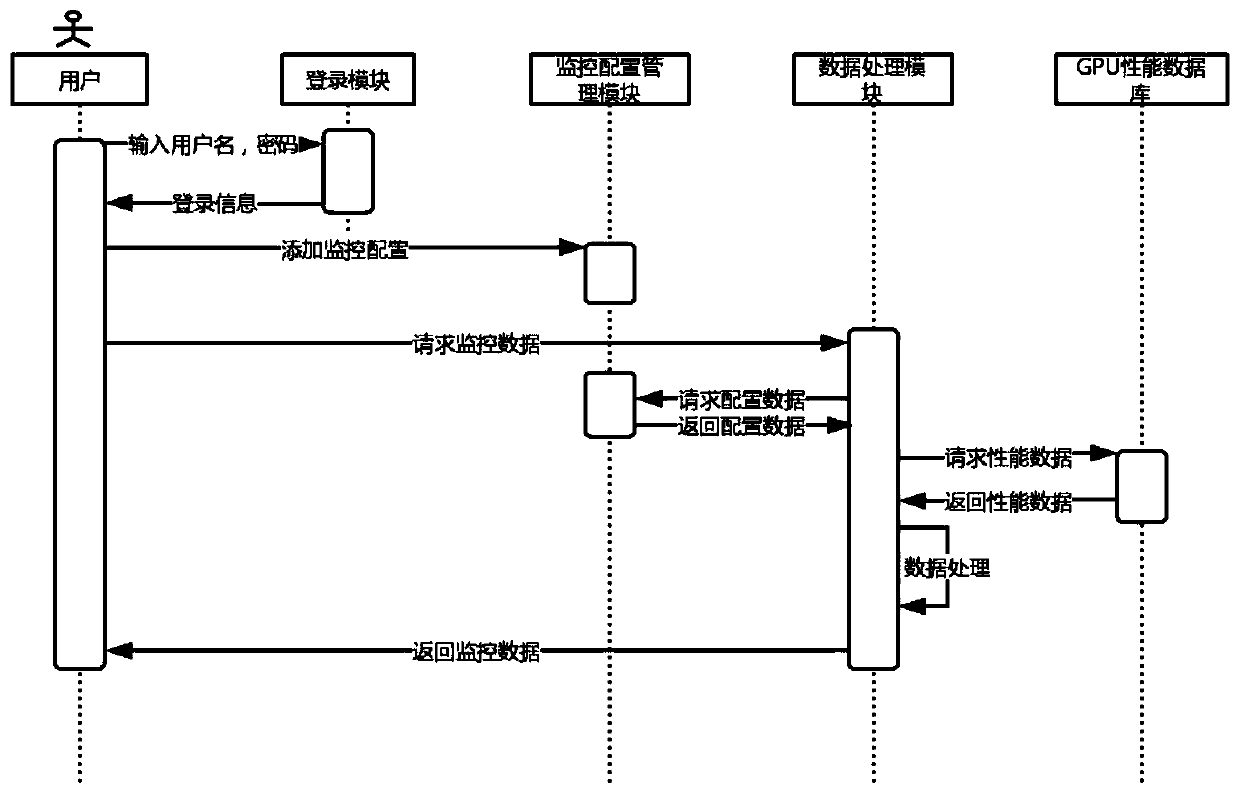
GPU monitoring alarm system with monitoring function customized by cloud platform
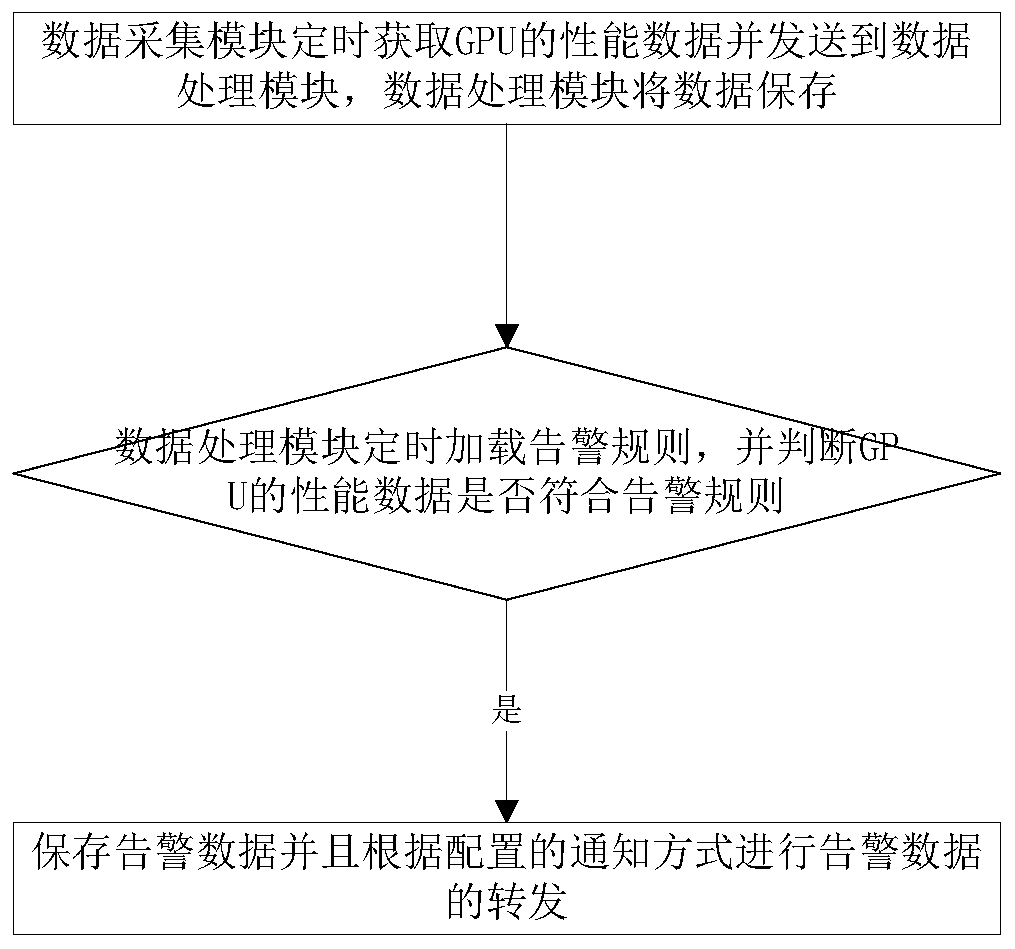
PendingCN110674013AEasy for suppliersMaster the running statusHardware monitoringMonitoring dataData acquisition module
The invention discloses a GPU monitoring alarm system with a monitoring function customized by a cloud platform, and belongs to the monitoring alarm technical field of the cloud platforms. The technical problem to be solved by the invention is how to realize the user-defined monitoring configuration according to the requirements, and generate the monitoring data satisfying the requirements of theusers flexibly. According to the technical scheme, the system comprises a data acquisition module, a monitoring configuration management module, an alarm rule management module and a data processingmodule; the data acquisition module is used for periodically acquiring the performance indexes of a GPU; the monitoring configuration management module is used for configuring a GPU monitoring dimension, a GPU monitoring index, a GPU monitoring period and a GPU monitoring statistical method; the alarm rule management module is used for configuring the alarm rules; the data processing module is used for storing the acquired data and generating the monitoring data according to the monitoring configuration and the acquired data and is used for traversing the alarm rules regularly, generating thealarm data or clearing the alarm data according to the acquired data, and forwarding the alarm data according to a configured notification mode.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Network attack solution method and device, equipment and medium
PendingCN113114650ALimit abuseGuaranteed normal serviceTransmissionSecurity arrangementAttackEngineering
The invention discloses a network attack solution method and device, equipment and a medium, and belongs to the field of mobile communication. The method comprises the following steps: limiting the use of a terminal on a target protocol data unit (PDU) session under the condition that the SMF identifies a network attack of the terminal, wherein the target PDU session carries a target message, and the target message is a message for triggering a network element of a core network to initiate the network attack to the SMF. According to the method and the device, the UE cannot send the target message with the network attack capability to the core network without limitation, so that the DOS attack initiated by the abnormal UE is defended, and a mobile communication system is ensured to provide services for more UE as much as possible.
Owner:TENCENT TECH (SHENZHEN) CO LTD
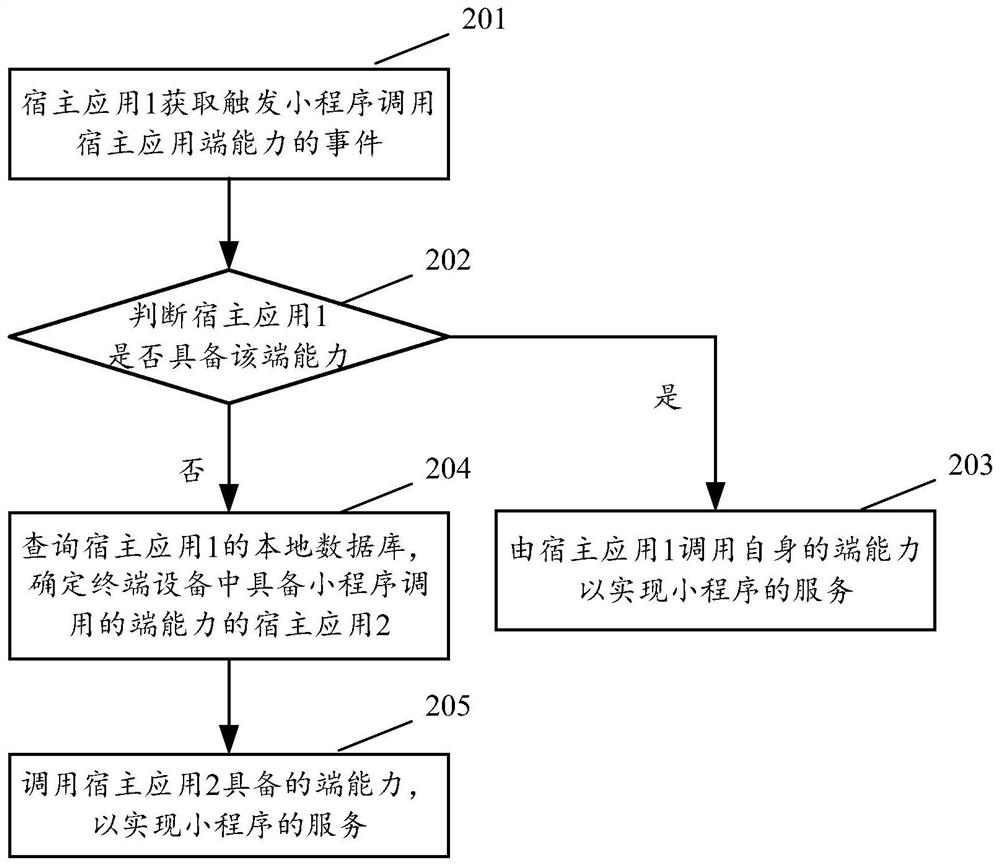
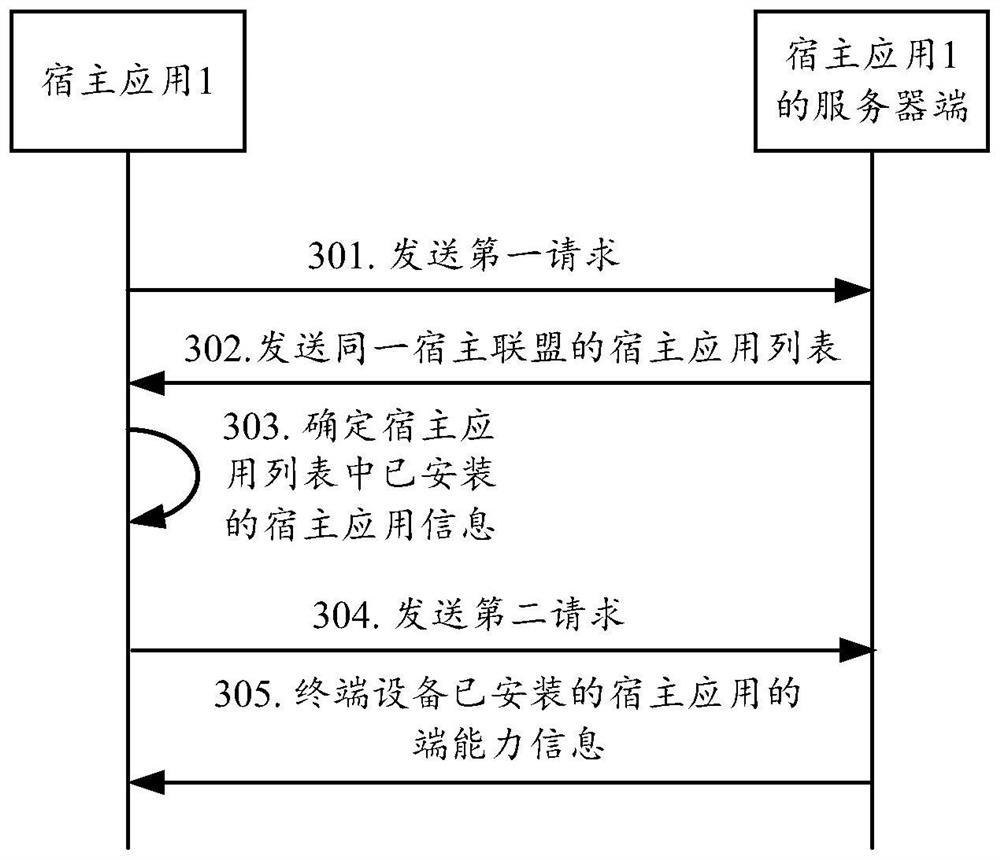
End capability calling method and equipment and computer storage medium
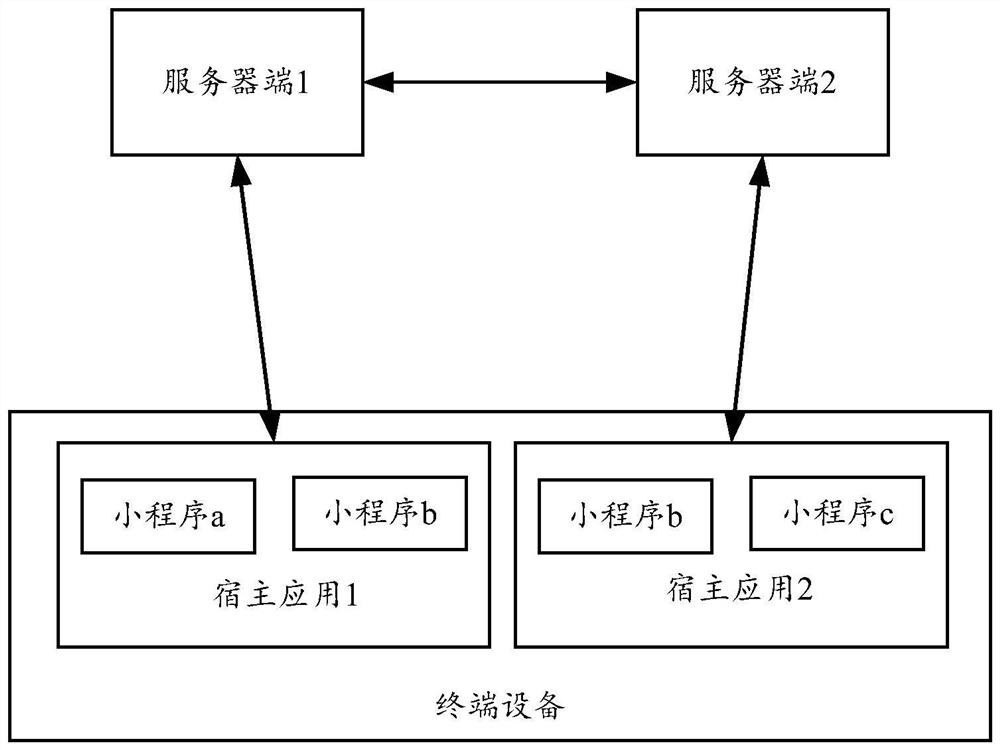
ActiveCN112835632AGuaranteed normal serviceSave resourcesProgram loading/initiatingSoftware engineeringTerminal equipment
The invention provides an end capability calling method and equipment and a computer storage medium. The method executed by a first host application of terminal equipment comprises the following steps: acquiring an event that an applet calls the capability of a host application end; and if the first host application does not have the end capability called by the applet, calling the end capability of a second host application in the terminal equipment. According to the method and the equipment, the end capability of each host application can be shared in the same terminal equipment, and all function codes do not need to be integrated in each host application, so that resources are saved while the service provided by the applet is ensured.
Owner:SHANGHAI LIANSHANG NETWORK TECHNOLOGY CO LTD
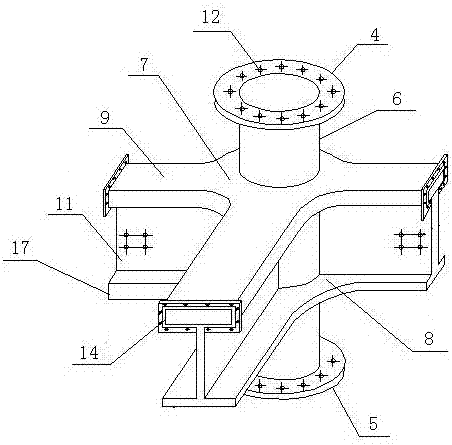
Frame formed from solid-web steel pipe concrete combination columns and combination beam, and construction method thereof
ActiveCN107246109AAvoid breakingPower transmission is clearStrutsProtective buildings/sheltersShaped beamPre stress
The present invention relates to a frame formed from solid-web steel pipe concrete combination columns and a combination beam, and a construction method thereof. The frame is formed by connecting combination columns and a combination beam through a node, wherein the combination beam is horizontally arranged between the combination columns, the node is an outer sleeve integral node filled with self-compacting concrete, the combination column is a segmental solid-web steel pipe concrete combination column, the combination beam is an I-shaped honeycomb concrete beam with an external pre-stress upper flange being rectangular steel pipe, the node is fixedly connected to the combination column through an upper connection ring and a lower connection ring, the node is connected to the combination beam through an end beam connection plate and a node web plate connection plate, and the self-compacting fine-aggregate concrete of the combination beam and the self-compacting fine-aggregate concrete in the upper wing edge steel pipe of the node end beam are communicated to each other. According to the present invention, with the frame and the construction method, the complex problem of the connection node between the solid-web steel pipe concrete combination column and the I-shaped beam having the upper flange being the rectangular steel pipe is solved.
Owner:宁波鼎信土地规划咨询有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com