A flood request attaching filtering method based on the stateless of open source core
A filtering method and stateless technology, applied in the field of network security, can solve problems such as lack of intelligence, and achieve the effect of small resource consumption, high intelligence and effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
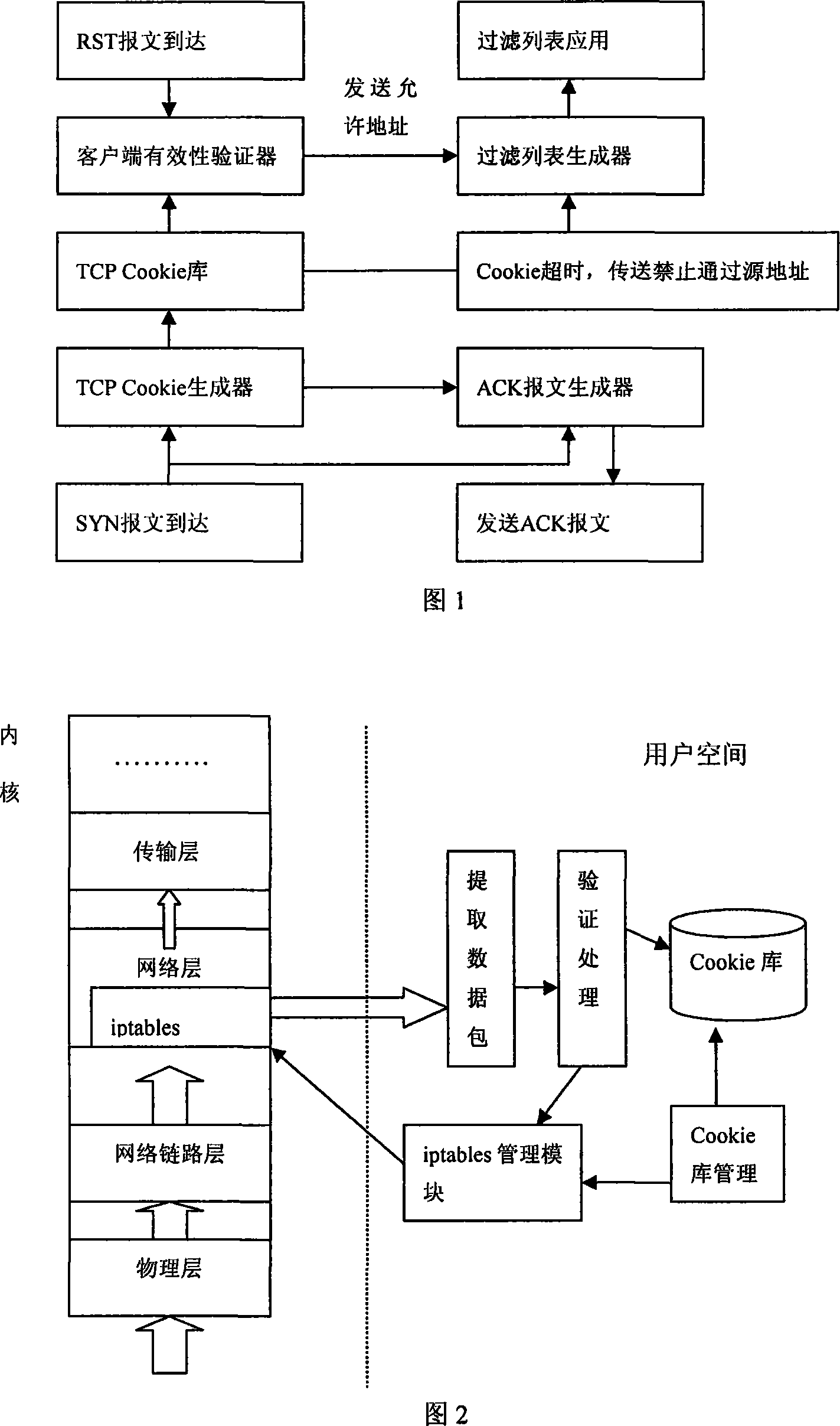
[0056] A typical DDoS uses a three-layer structure to attack. The central console is the host where the attacker resides. The attacker first intrudes into several hosts in the network as proxy consoles for the attack, and then directly attacks the hosts with a proxy console. These hosts are distributed in the network and have different geographical locations.
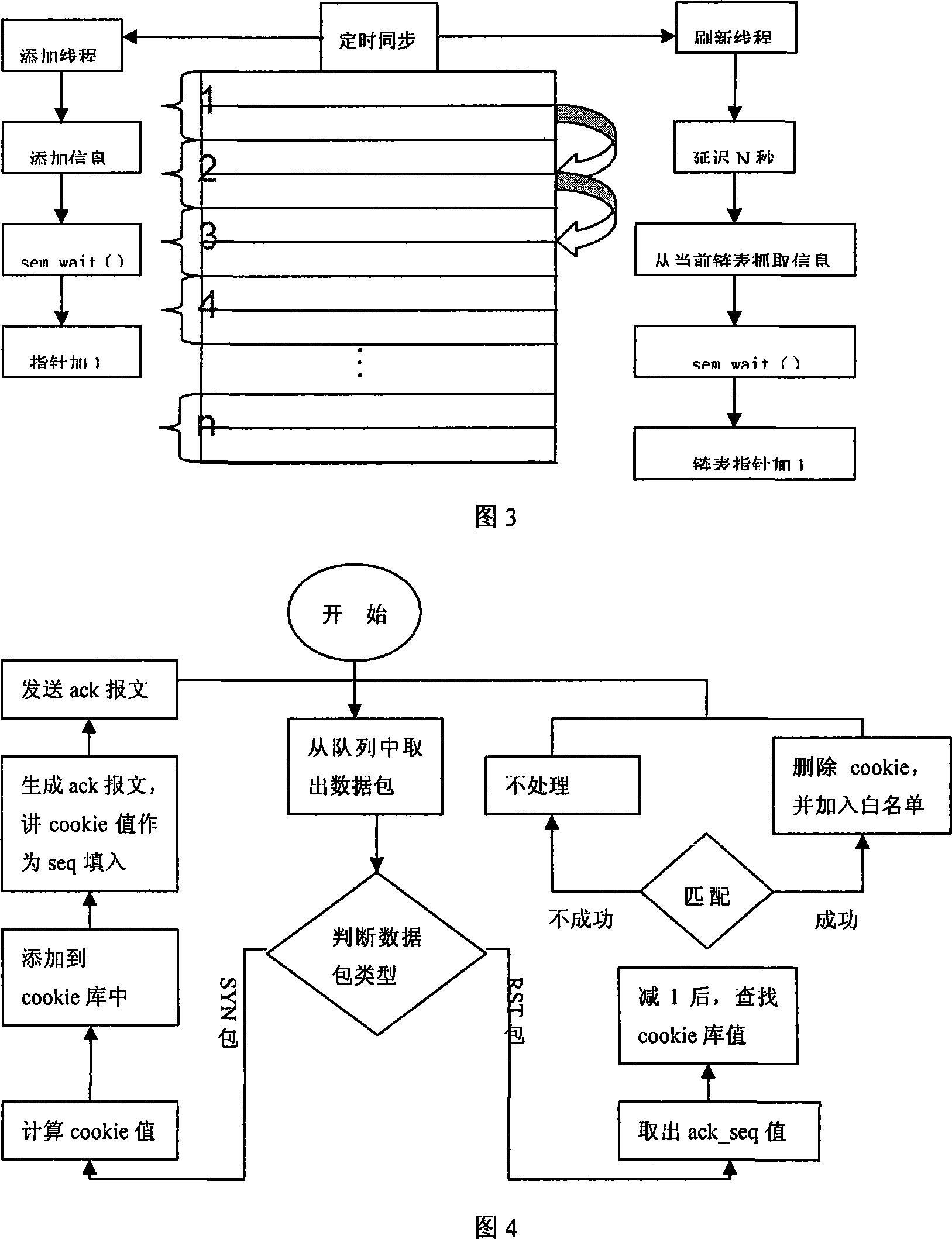
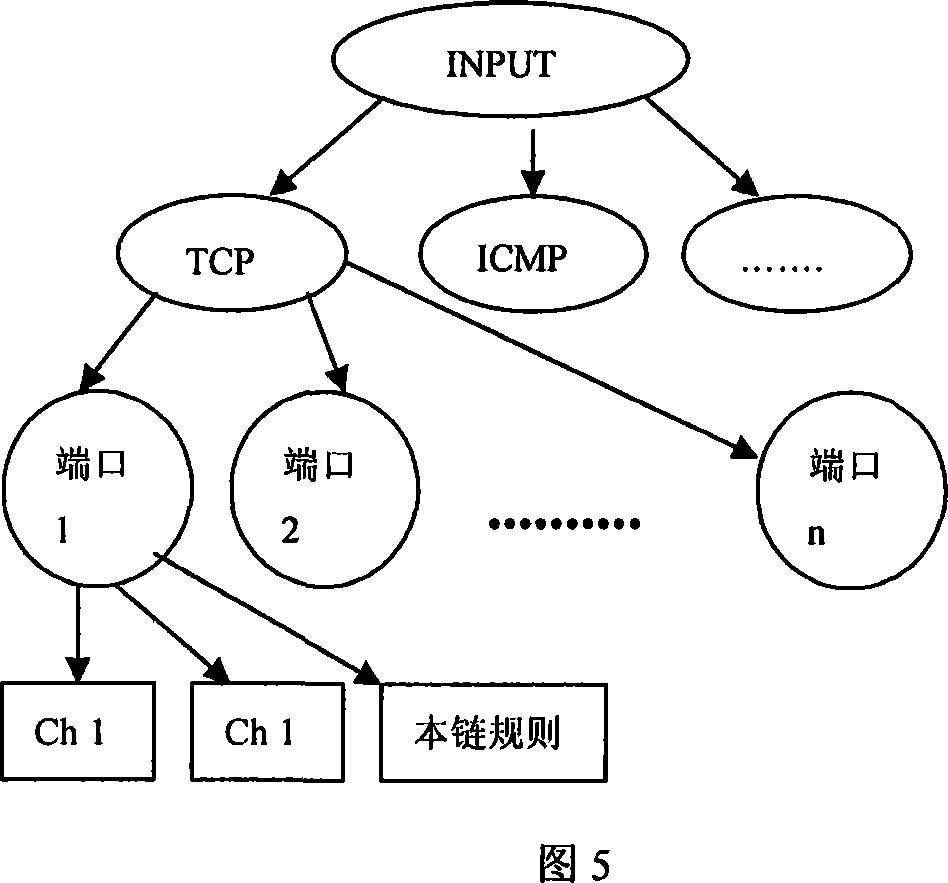
[0057] Below we simulate a syn flood-based DDoS attack on a network. Host A is the server, and host B is the gateway. Through a typical DDoS attack network with a three-layer structure of nine computers, the network service (website access) provided by host A is attacked. B on the gateway starts after detecting the DDoS attack. The filtering module identifies attacks and normal network data packets, and performs filtering processing.
[0058] The steps to start the attack on the attack side are as follows:
[0059] 1 The computer used by the attacker is the console S, which controls the entire attack process. The mai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com