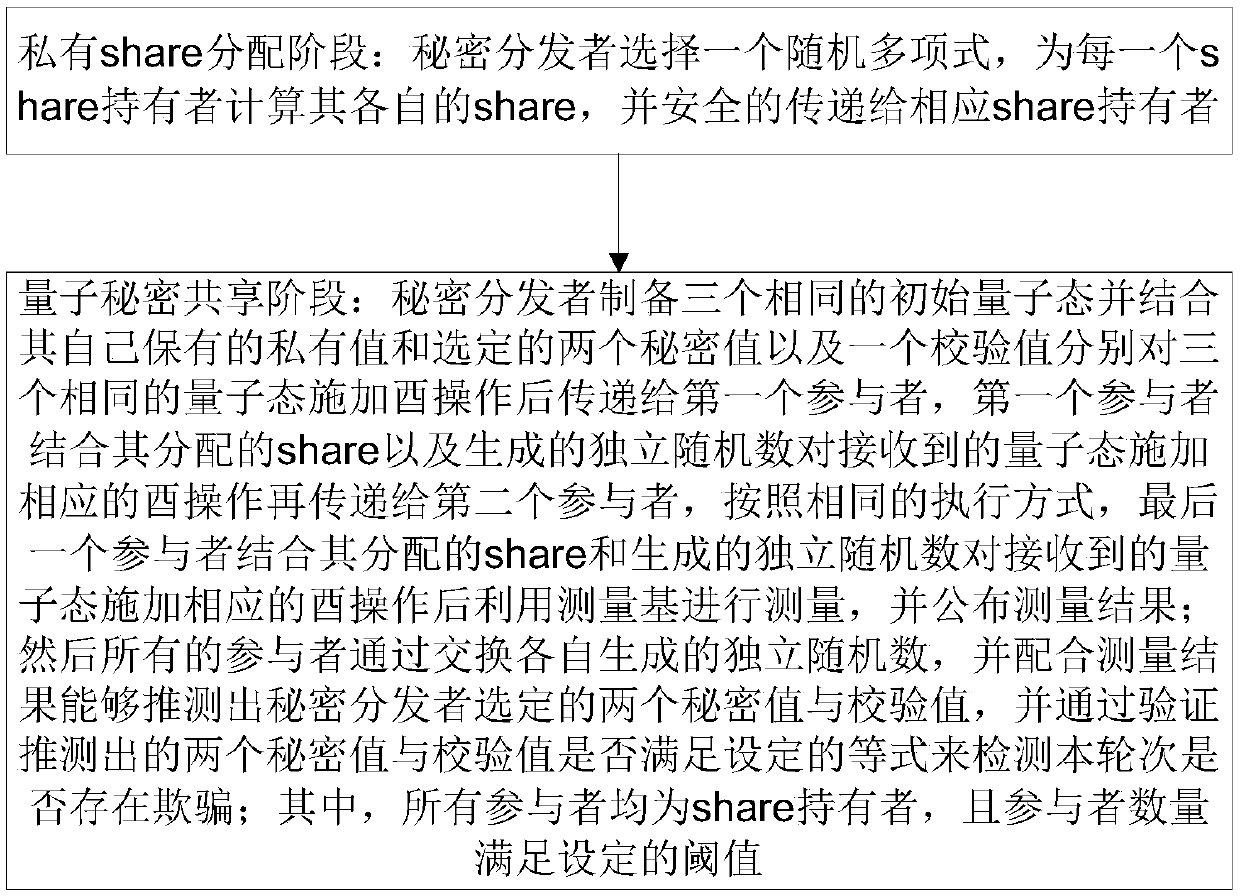
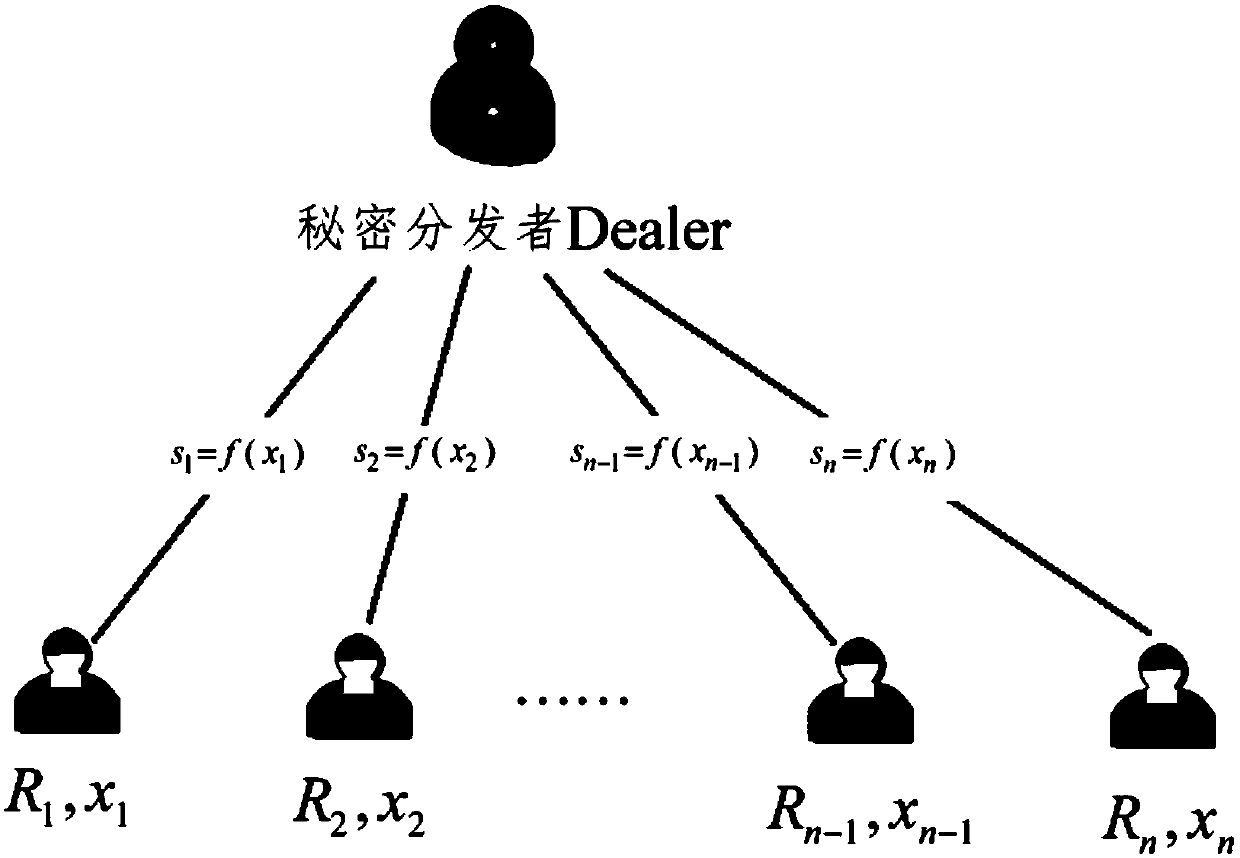
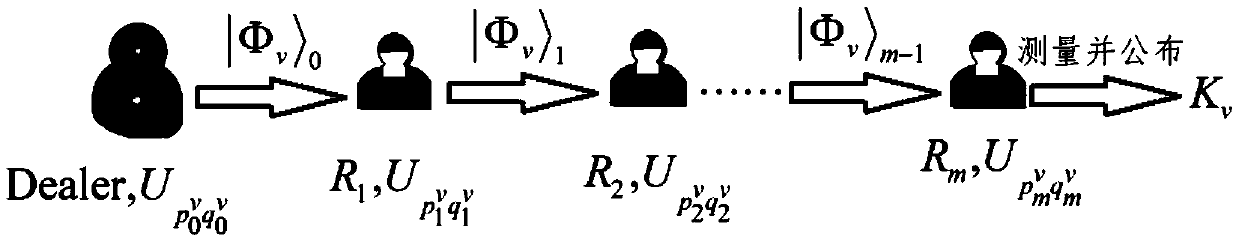
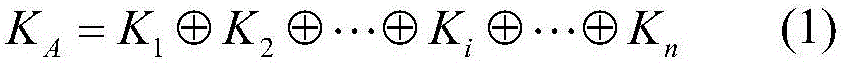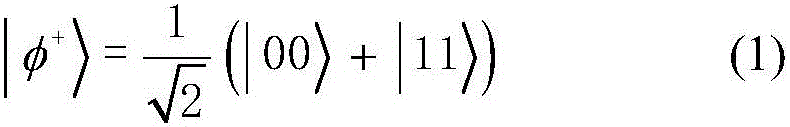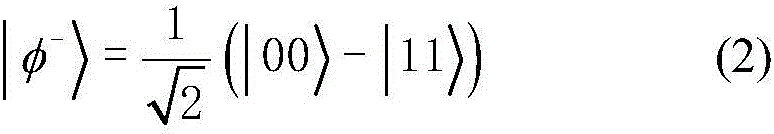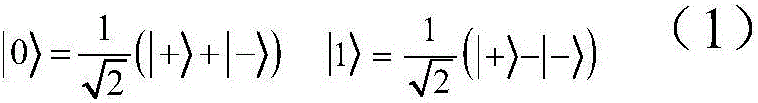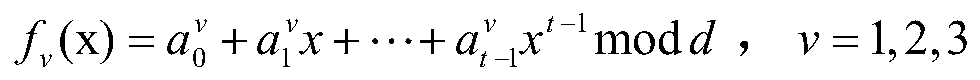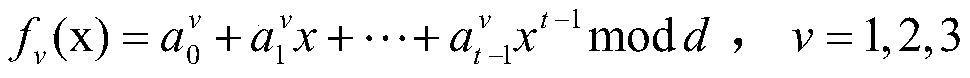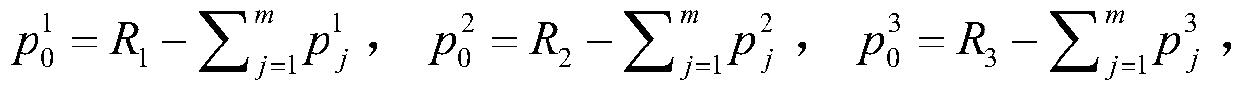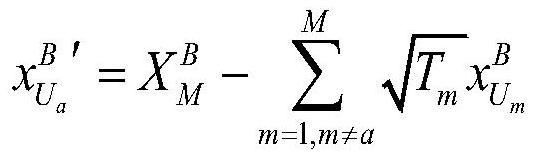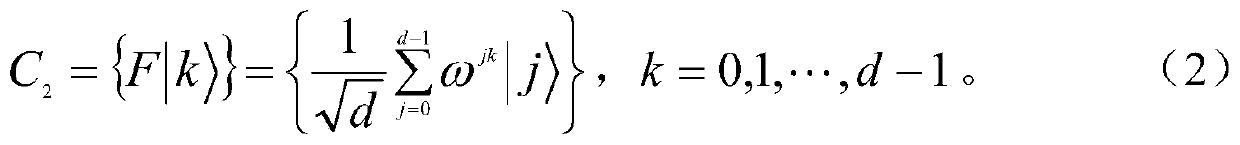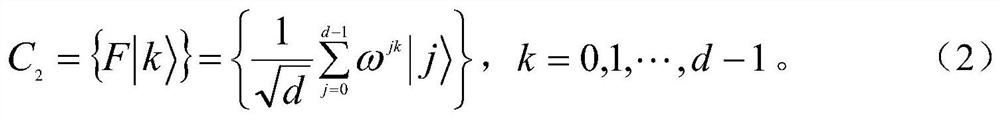Patents
Literature
48 results about "Quantum secret sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
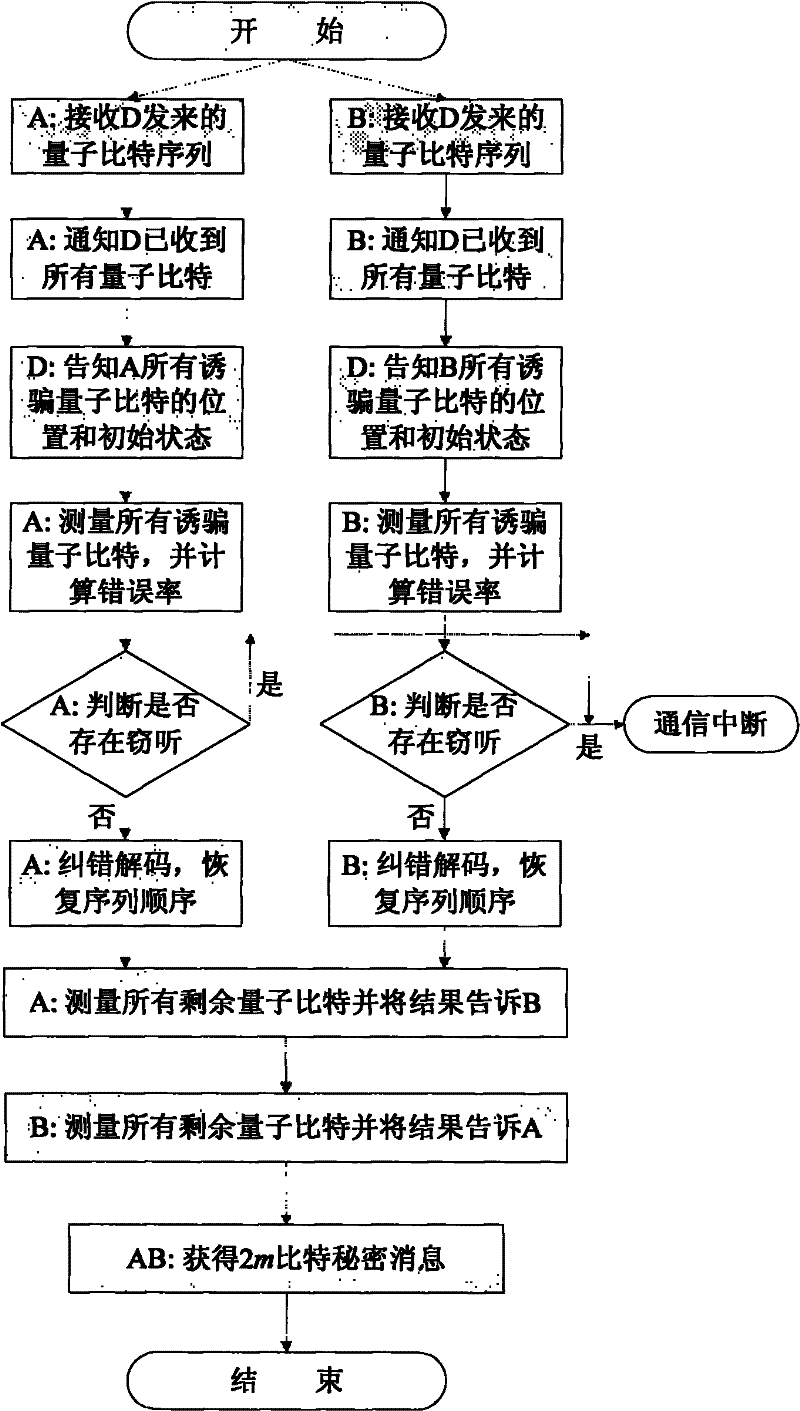
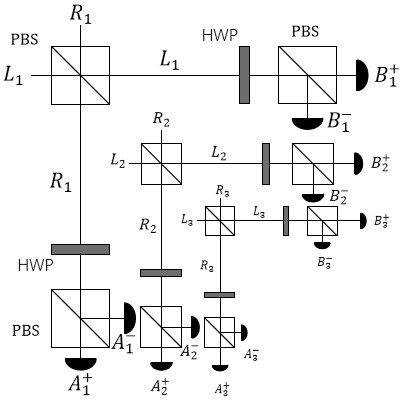
Quantum secret sharing method based on Bell state
InactiveCN106712945ARealize secret sharingReduce complexityKey distribution for secure communicationBell stateQuantum efficiency
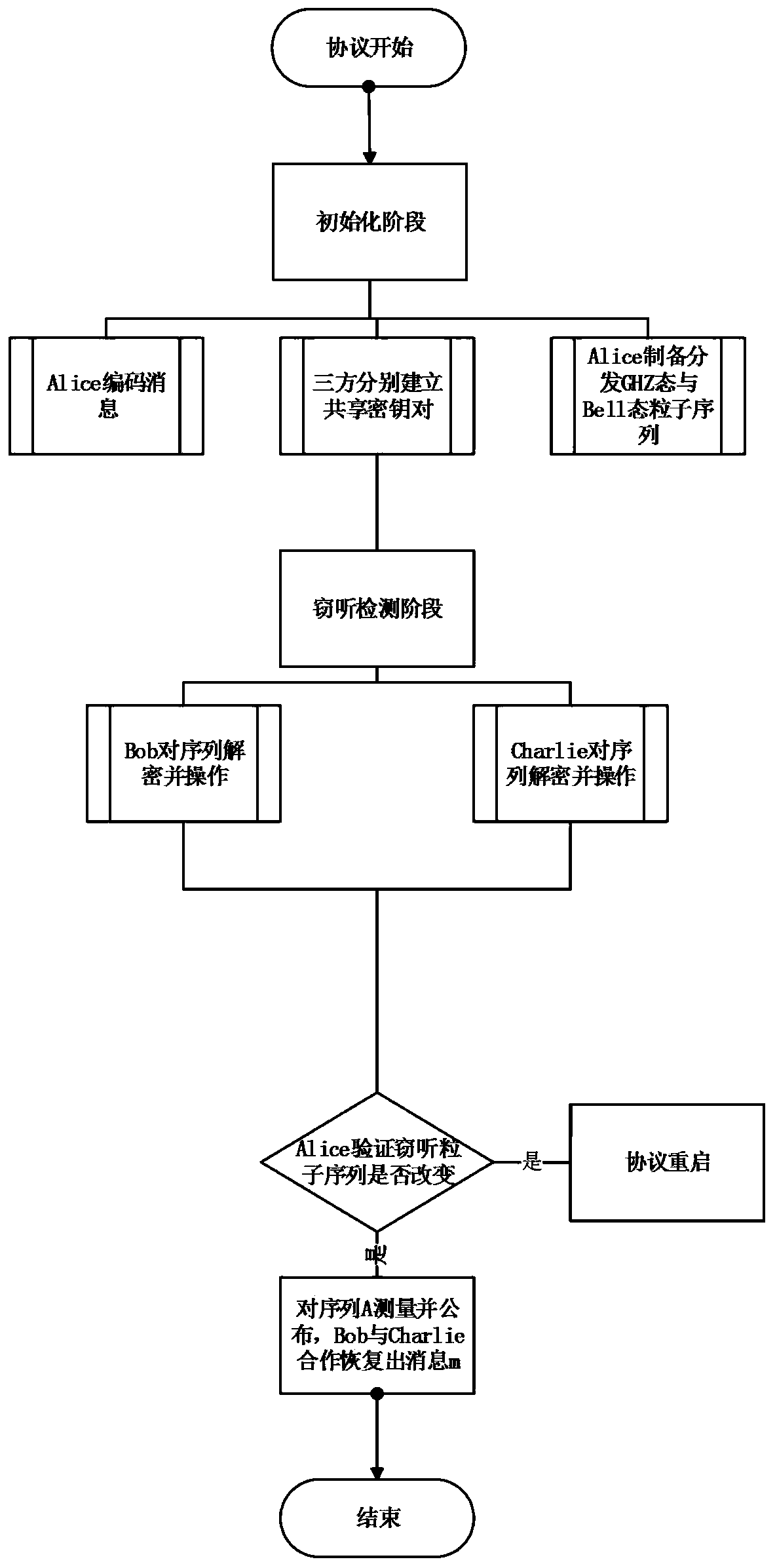
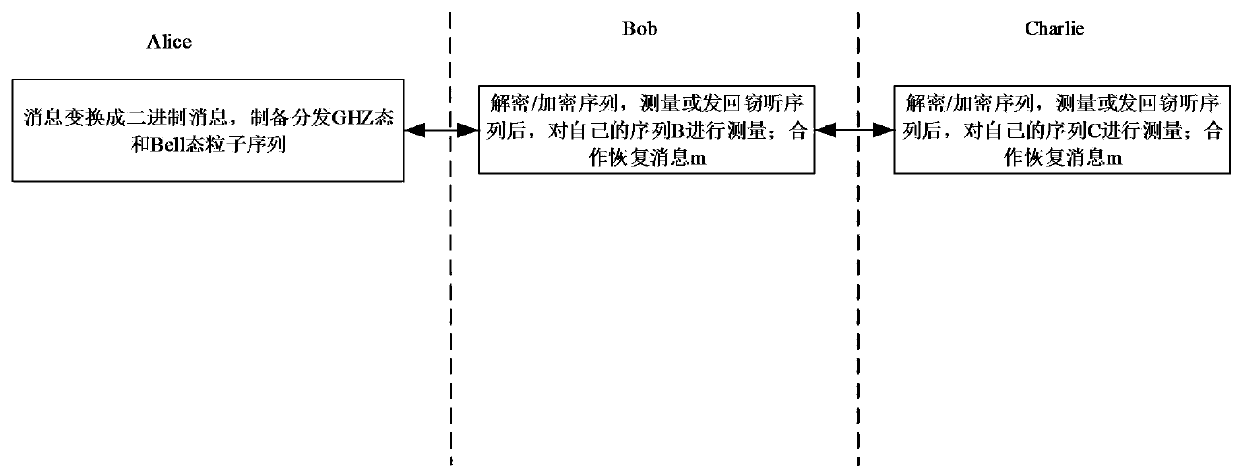
The invention discloses a quantum secret sharing method based on a Bell state. The quantum secret sharing method is characterized by comprising a secret distributor and n participants, the secret distributor distributes a random secret to the n participants, wherein each participant obtains a sub-secret, when the n participants accumulate all sub-secrets, the originally shared secret can be restored, and any information of the shared secret cannot be obtained less than n participants. By adoption of the quantum secret sharing method disclosed by the invention, the problems of participant fraud, low security, complexity and efficiency of channels in the existing quantum secret sharing process are solved, the quantum and classical resources can be saved, the operation complexity is reduced, and higher quantum efficiency is ensured.
Owner:ANHUI UNIVERSITY
Method for attacking Fourier transform quantum secret sharing systems
InactiveCN101931528AEffective attackKey distribution for secure communicationSecret communicationComputer hardwareQuantum secret sharing
The invention discloses a method for attacking Fourier transform quantum secret sharing systems, and relates to quantum secret communication technology. In the method, a specific measurement base is utilized to perform single particle measurement on the information carrier quantum bit, and partial secret messages are acquired according to a measurement result. According to the quantum-mechanical nature, due to the selection of the measurement base, the state of the measured quantum bit is just the eigen state of the measurement base, and the quantum state after measurement cannot be changed at all. The method can make a dishonest agent independently obtain partial key information, also can make several cooperated agents obtain more key information, and cannot introduce any error for normal communication so as not to be discovered by other users. The invention provides a method for effectively attacking the Fourier transform quantum secret sharing systems, which is simultaneously an effective method for testing the safety of the Fourier transform quantum secret sharing systems.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Error correction method for multi-party quantum secret sharing system
ActiveCN106452761ATakes a long timeNo error correction involvedKey distribution for secure communicationPhotonic quantum communicationComputer hardwareCorrection algorithm
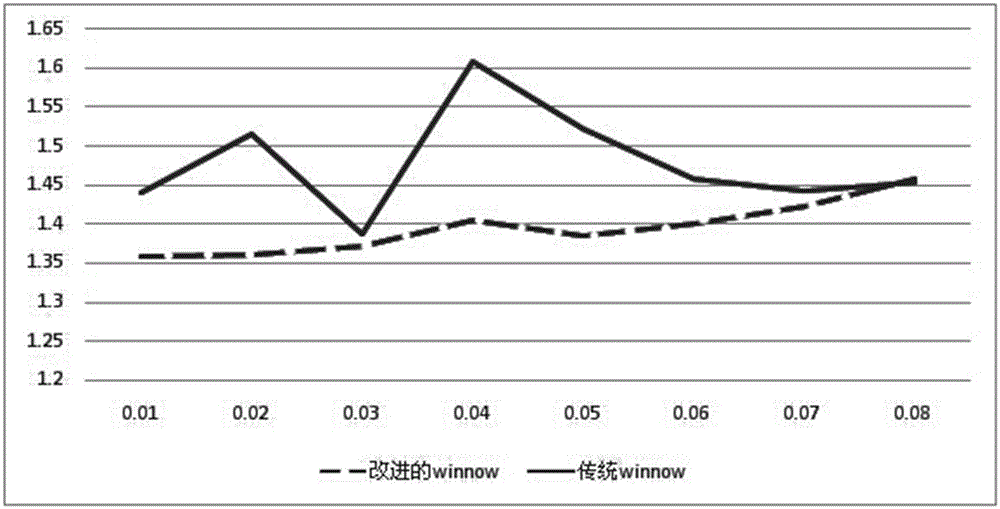
The invention relates to an error correction method for a multi-party quantum secret sharing system. The error correction method comprises the following steps: S1: calculating a system error rate; S2: according to the system error rate, finding the optimal segment length sequence; S3: performing the following steps through loop iteration: S3.1: rearranging data; S3.2: according to the optimal segment length, segmenting an original key of a transmitter and a shared key; calculating parity check sums of segment keys at a transmitting end and a receiving end respectively, and comparing operational results of the transmitting end and the receiving end to obtain the segment keys with different operational results; S3.3: finding error bit positions by a Winnow error correction algorithm; S3.4: according to the error bit positions, negating 0 or 1 values at corresponding positions in the original key of the transmitter, and stopping loop iteration till the maximum number of iterations is reached; S4: checking error correction results; if error correction is successful, ending operation; if the error correction is not successful, discarding the corresponding keys. The invention provides the error correction method which is high in reliability and high in error correction efficiency and is applicable to the multi-party quantum secret sharing system.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
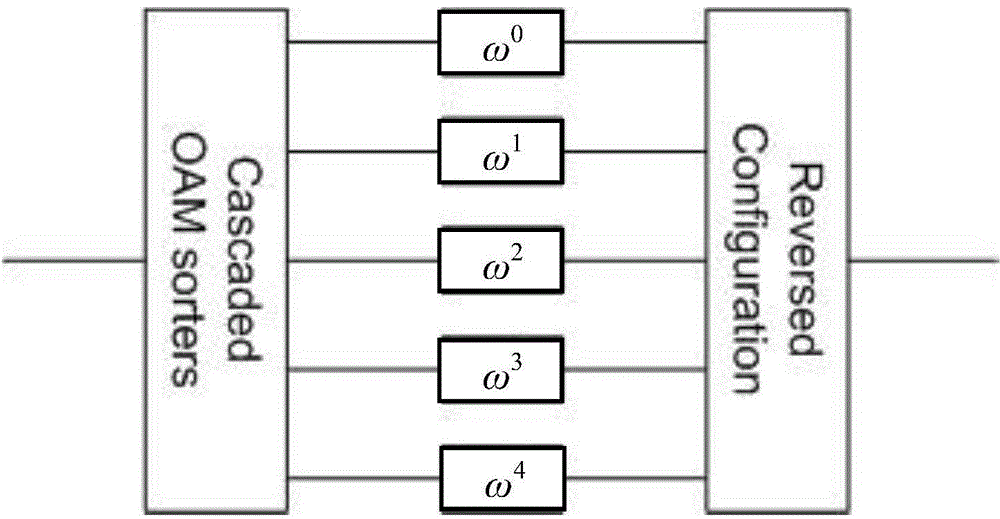
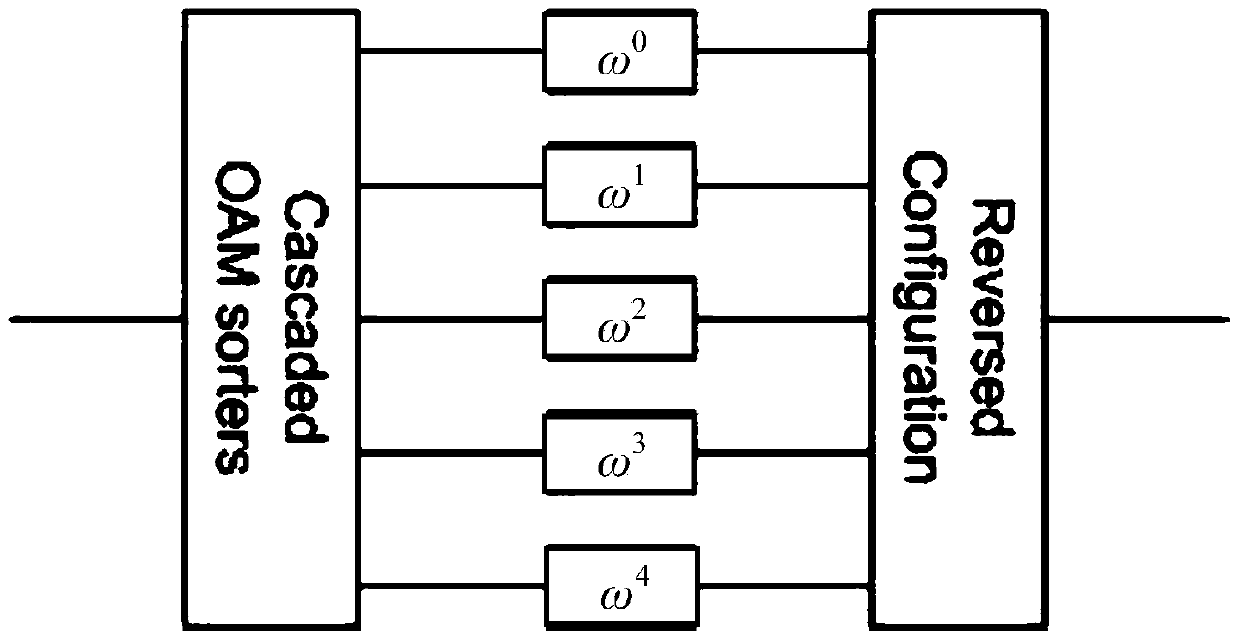
High-capacity quantum secret sharing method based on photon orbit angular momentum coding
ActiveCN104821875AImplement codingImplement decodingKey distribution for secure communicationQuantum secret sharingFrequency spectrum
The invention discloses a high-capacity quantum secret sharing method based on photon orbit angular momentum coding. The method comprises the steps: constructing two unitary operators; giving two groups of complete intrinsic quantum states; carrying out annular quantum secret sharing communication. Based on an intrinsic quantum state space, transmitter side Alice randomly prepares a photon sequence and transmits the photon sequence to Bob. Bob randomly selects verification photons from the photon sequence for measurement described in the specification. The coding of the residual photons is carried out according to a secret key character string, and the coded photons are transmitted to Charlie. Charlie carries out measurement of photon verification of the received photon sequence, and codes the residual photons according to the secret key character string, and transmits the coded photons to Alice. Alice judges whether a communication channel is safe or not, and reads the coding operation which is carried out by Bob and Charlie jointly. The method employs single-photon orbit angular momentum coding to improve the communication capacity and frequency spectrum efficiency of a quantum secret sharing scheme, and does not need multicomponent entangled photon states.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Quantum secret sharing method and sharing system based on quantum walking
ActiveCN110445609ARealize teleportationSafe and feasible technologyKey distribution for secure communicationQuantum secret sharingComputer network
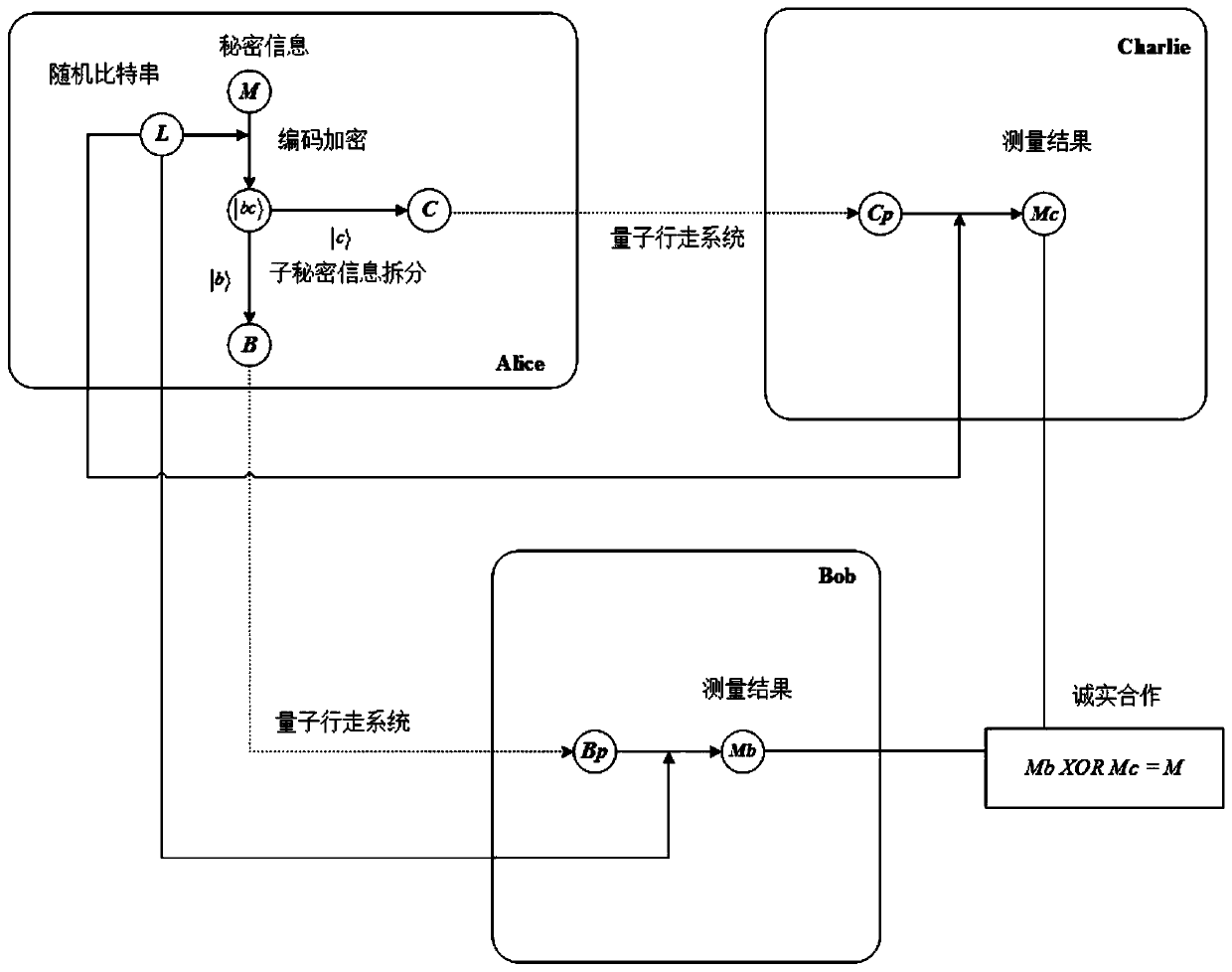
The invention belongs to the technical field of quantum information sharing, and discloses a quantum secret sharing method and sharing system based on quantum walk, and the method comprises the steps:enabling a secret distributor to encode secret information to be shared into a quantum state according to a rule, and enabling an encoding particle to be split into two parts; invisibly transferringthe two pieces of encrypted information to a first participant and a second participant through a quantum walking system; and the first participant and the second participant decrypt the secret information of the secret distributor through cooperation. Characteristics of the quantum walking system are used for invisible state transfer of unknown particles, entanglement is spontaneously generated among the particles, and preparation of entangled particles in a particle preparation stage is avoided to complete invisible state transfer of the particles. According to the quantum secret sharing method based on quantum walking, an invisible state transfer method based on quantum walking is combined with a coding rule, and the quantum secret sharing method based on quantum walking is completed.
Owner:HEFEI LONGTUTEM INFORMATION TECH CO LTD
Quantum secret sharing method capable of resisting intercept-resend attack, man-in-the-middle attack and entanglement attack
ActiveCN106685659AProof of feasibilityProve securityKey distribution for secure communicationMan-in-the-middle attackQuantum secret sharing
The invention belongs to the technical field of information security, and discloses a quantum secret sharing method capable of resisting an intercept-resend attack, a man-in-the-middle attack and an entanglement attack. A secret sharing protocol is designed by utilizing the special characteristic that a five-particle GHZ state has the correlation in an X group. According to the protocol, secret information is split into four parts, the four parts are delivered to four participators to be cared, and the secret information can be decrypted only when the four participators all take participate in. After analysis, the feasibility of the protocol is proved. Security analysis shows that the protocol can resist the intercept-resend attack, the man-in-the-middle attack and the entanglement attack. And meanwhile the trust problem of the participators is analyzed, and it shows that the protocol is secure.
Owner:CHENGDU UNIV OF INFORMATION TECH
Verifiable threshold quantum secret sharing method for sequential communication
ActiveCN109257169AEnsure safetyImprove practicalityKey distribution for secure communicationQuantum secret sharingTrusted third party
The invention discloses a verifiable threshold quantum secret sharing method for sequential communication, which can recover the secret cooperatively without the participation of all shareholders, sothat the method has more flexibility in application. At that same time, no trusted third party is need, and a verifiable mechanism is provided to detect cheat, so that the security is guarantee, in addition, each round can be legally used for secret sharing, and the practicability is greatly improved.
Owner:UNIV OF SCI & TECH OF CHINA
Quantum secret sharing system, a sharing method thereof and error correction method
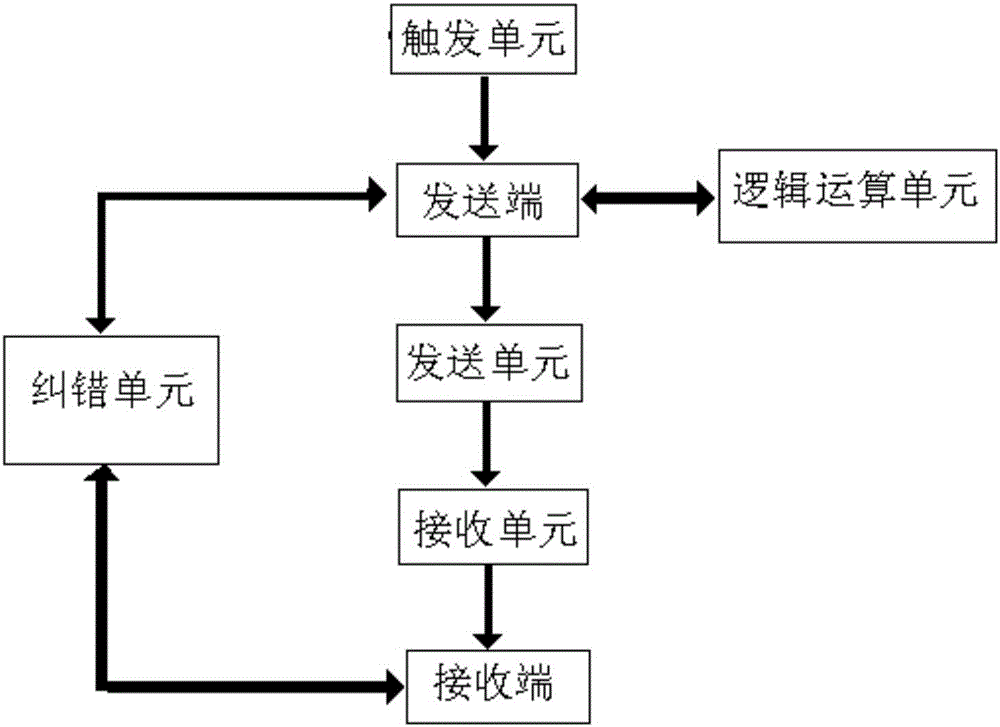
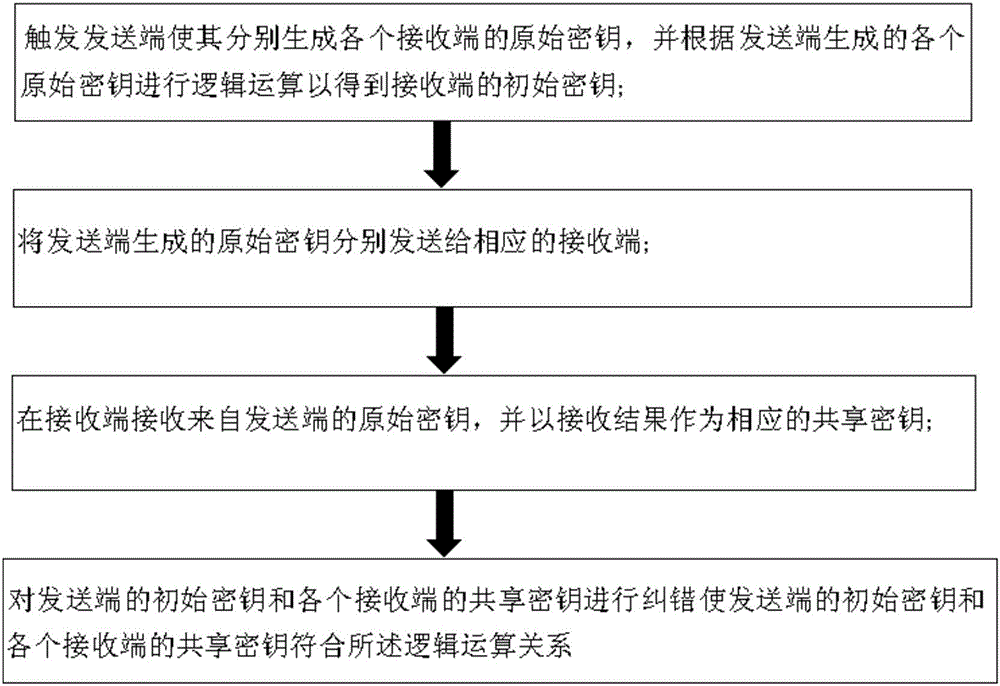
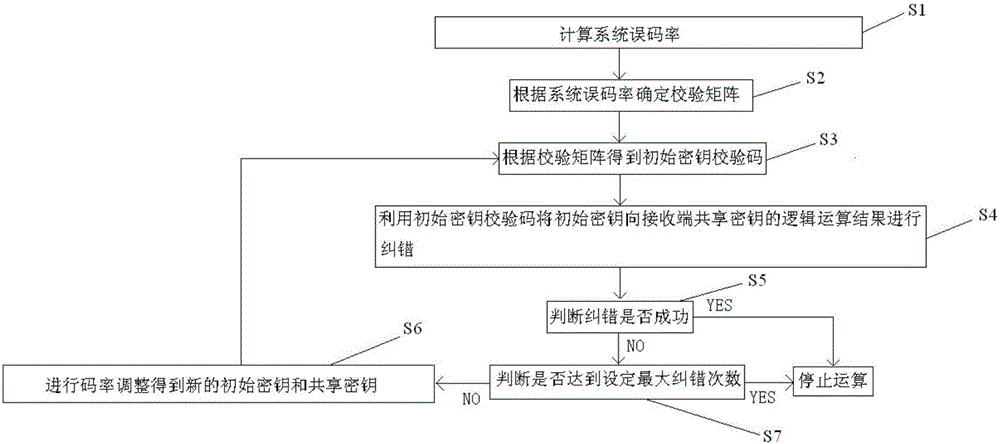
ActiveCN106452757AReduce lossReduce bit errors and other issuesKey distribution for secure communicationComputer hardwareQuantum secret sharing
The invention relates to the technical field of quantum communication, and especially relates to a sharing method of a quantum secret sharing system. The method comprises the following steps: S1: calculating a system error rate; S2: determining a check matrix according to the system error rate; S3: obtaining a check code of an initial key according to the check matrix; S4: performing error correction on a logical operation result of the initial key and a shared key of a receiving terminal by using the check code of the initial key; S5: judging whether the error correction is successful; S6: if the error correction is successful, stopping the operation; and if the error correction is not successful, then adjusting the code rate to obtain a new initial key and a new shared key, and executing steps S3 to S6 by the initial key and the shared key with the code rate adjusted until the error correction is successful or a preset maximum error correction time is reached. The invention further relates to a quantum secret sharing system and a sharing method thereof. According to the sharing method provided by the invention, multi-party information interaction is adopted, the original key is sent to at least two receiving terminals by a sending terminal, and the problems of dissipation, error code and the like in a secret sharing process are reduced.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
Quantum secret sharing method and system without monitoring channel
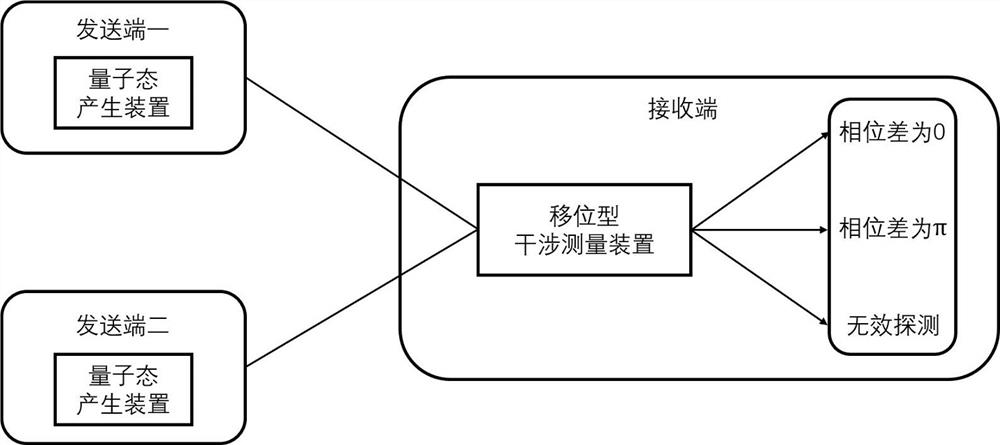
ActiveCN112511303AEasy to operateSolve the problem that cannot be codedKey distribution for secure communicationPhotonic quantum communicationTelecommunicationsQuantum secret sharing
The invention provides a quantum secret sharing method and system without a monitoring channel, and the method comprises the steps: two transmitting ends prepare a bit string with the length of L, enabling the generated bit string information to be coded on the phase of a quantum state with the dimension of L, and transmitting a quantum state sequence to a receiving end; the receiving end performsshift type interference measurement on the two paths of quantum state sequences, generates an original secret key according to a measurement result, and then publishes the positions of the quantum states which are responded under effective measurement to the two sending ends respectively; the two receiving ends find out corresponding bits from own bit strings as original keys according to the positions of the quantum states; and finally, classical error correction, error verification and privacy amplification are performed by the three parties, and finally extracting is performed to obtain akey for quantum secret sharing. According to the method, the requirement of channel monitoring is removed, and theoretically the highest 50% system bit error rate can be tolerated, so that the deviceand the implementation program of the quantum secret sharing scheme are simpler.
Owner:NANJING UNIV
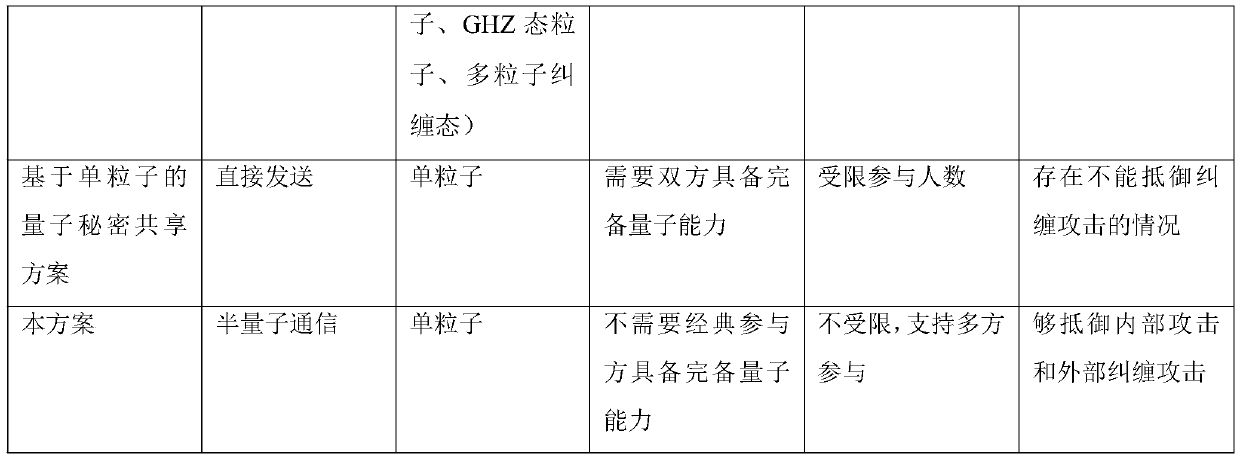
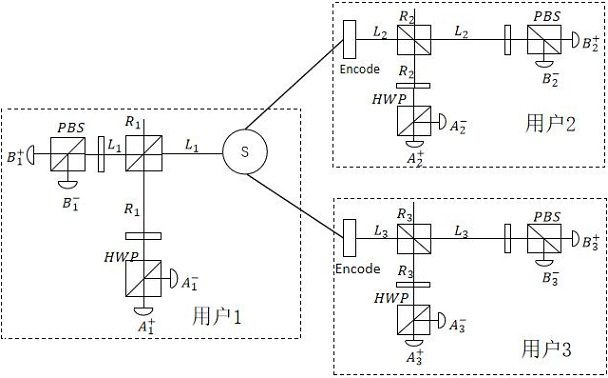
Multi-party semi-quantum secret sharing method and system based on single photon
InactiveCN110474770APracticalReduce resource requirementsKey distribution for secure communicationPhotonic quantum communicationQuantum secret sharingDistributor
The invention belongs to the technical field of semi-quantum communication, and discloses a multi-party semi-quantum secret sharing method and system based on a single photon. The multi-party semi-quantum secret sharing method comprises the steps that a secret distributor splits a classic information code into quantum states; and the participant receives the quantum state through semi-quantum cryptography communication, then recovers a part of secret information through quantum operation, and recovers original secret information through honesty cooperation. The secret sharing scheme does not depend on entangled-state particles, but adopts single particles, so that the secret sharing scheme has higher practicability in practice; according to the protocol, a classic party does not need to have complete quantum capacity, and the requirement for quantum equipment resources is lowered; according to the multi-party semi-quantum secret sharing method, secret sharing between a secret distributor and multiple parties is completed, but not limited to secret sharing among the three parties; and according to the scheme, internal attacks and external entanglement attacks can be resisted, and safety feasibility is achieved.
Owner:CHENGDU UNIV OF INFORMATION TECH
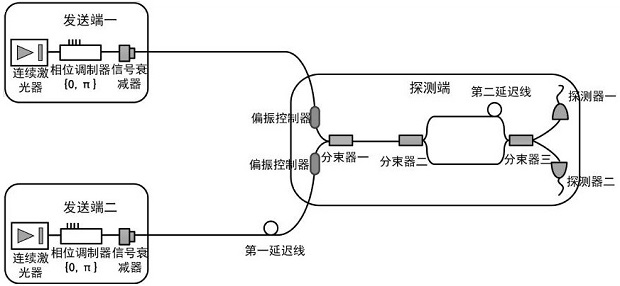
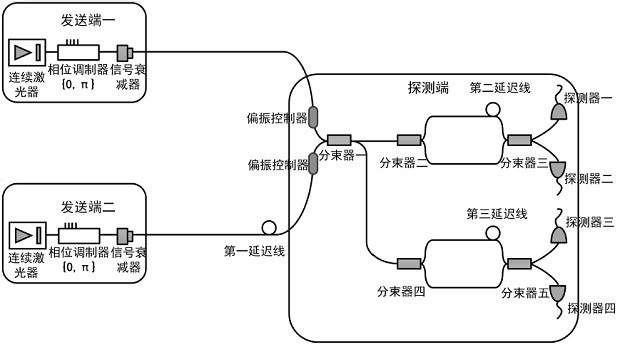
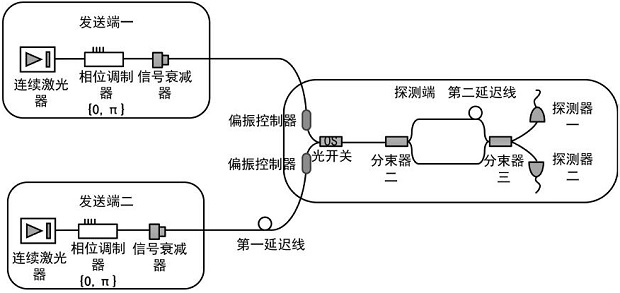
Quantum secret sharing method and system based on differential phase shift
ActiveCN111835515AAchieve sharingDefend against independent attacksKey distribution for secure communicationBeam splitterQuantum secret sharing
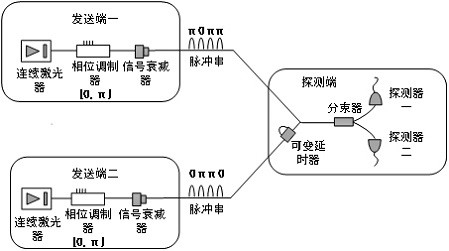
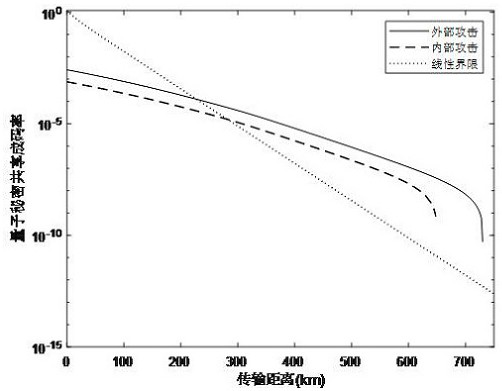
The invention discloses a quantum secret sharing method and system based on differential phase shift, the system comprises a sending end, a detection end and the like, the detection end comprises a receiving unit and a detection unit, the receiving unit comprises a polarization controller and a beam splitter used for beam combination, and the detection unit comprises an unbalanced interferometer and a pair of detectors. The detection end performs detection response according to the interference result and only publishes the response time of each detector, and calculates the gain for coding according to the transmitted data volume and the detection count; the sending ends respectively form original secret keys which are not subjected to post-processing according to the response moments; andthen the detection end randomly selects a plurality of response moments, calculates a system error rate according to a preset rule, and finally performs post-processing on the original key, so that the sending end I and the sending end II share the key of the detection end. Quantum secret sharing between the two sending ends and the detection end can be achieved, the secret key safety is high, and meanwhile the secret key code forming rate and the transmission distance are further increased.
Owner:NANJING UNIV
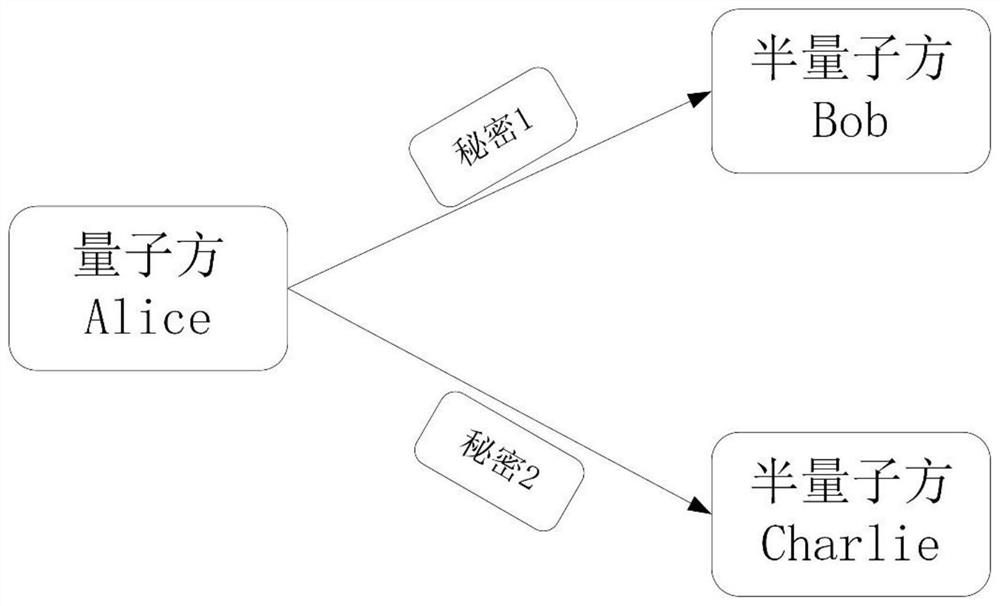
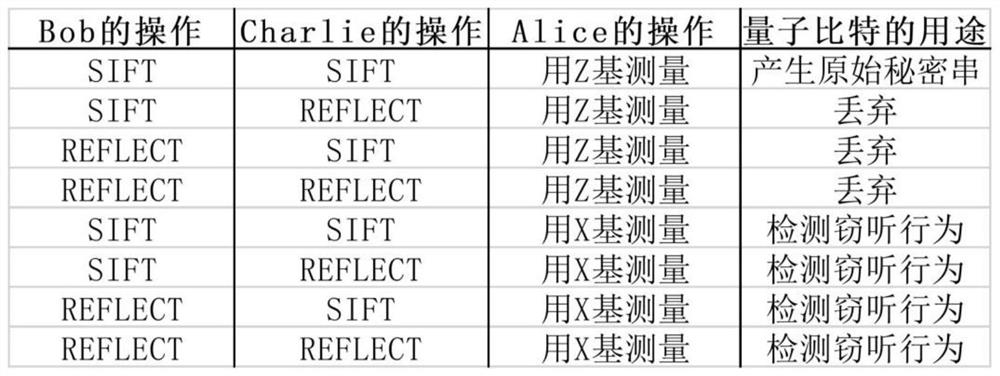
Quantum resource limited semi-quantum secret sharing method
ActiveCN108173656ASimplify Quantum CapabilitiesReduce communication costsKey distribution for secure communicationComputer networkMeasurement device
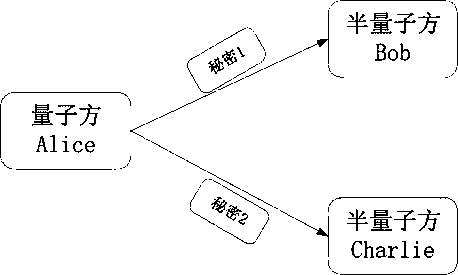
The invention discloses a quantum resource limited semi-quantum secret sharing method. Semi-quantum secret sharing usually includes that a quantum side Alice divides a secret into two parts and sendsthem to quantum resource limited Bob and Charlie respectively, and only when the Bob and the Charlie cooperate, the complete secret be recovered. At present, the typical semi-quantum secret sharing method guarantees the security, but requires the semi-quantum sides Bob and Charlie to perform quantum measurement operations. The measurement device may be unsafe, which increases the hidden danger ofsecret sharing. The present invention enables the resource limited Bob and Charlie to perform secret sharing without a quantum measurement device, and the quantum side Alice does not require quantum memory. In this way, the present invention can greatly reduce the quantum resources required by the three participants, thereby saving the communication cost.
Owner:XIANGTAN UNIV
Quantum secret sharing method and system based on tensor network state dynamic compression
ActiveCN112367167AImprove efficiencyHigh precisionKey distribution for secure communicationQuantum secret sharingSecret share
The invention discloses a quantum secret sharing method and system based on tensor network state dynamic compression, and the method comprises the following steps: S1, enabling a dispatcher to carry out the local equidistant transformation of quantum state secret information needing to be shared in a mode of a matrix product state, and decomposing the quantum state secret information into corresponding secret shares according to the number of participants; S2, enabling the dispatcher to dispatch the decomposed secret share to the corresponding participant; S3, enabling the participants to share the secret shares obtained by themselves; and S4, acquiring the process information of the local equidistant transformation from the distributor by the participants acquiring all secret shares, andrecovering the shared quantum state secret information in combination with decompression. The method and the system have the advantages that all classic participants and quantum participants can use quantum bits with the quantity index higher than that of the quantum bits received by the participants to decompress the state, the obvious storage advantage is achieved, the quantum communication efficiency and precision are improved, and the size of a quantum memory is greatly reduced.
Owner:SOUTHWEST UNIV
Verifiable quantum secret sharing method
ActiveCN110190961AAvoid attackKey distribution for secure communicationQuantum secret sharingQuantum gate
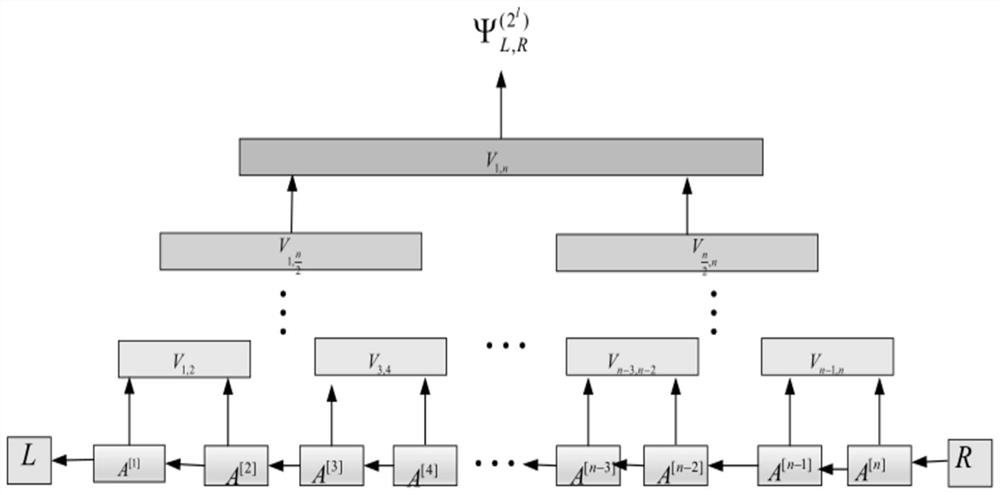
The invention relates to a verifiable quantum secret sharing method, which comprises the following steps that: step 1, Alice calculates fv (xj) (v = 1, 2, 3) as a sub-secret of Bobj, and sends f1 (xj), f2 (xj) and f3 (xj) to the Bobj by using a secure channel; step 2, a participant P1 prepares three same quantum states and sends the three same quantum states to a P2, the participant P2 executes operation similar to the P1 and sends the quantum states to the participant P3, and other participants also execute operation similar to the P1 and send the quantum states to Alice after operation of the last Pm is completed; (4) Alice measures three quantum states and sends measurement results R1, R2 and R3 to m participants P1, P2,..., Pm; and step 3, a secret recovery stage: if m participants P1,P2,..., Pm want to recover secrets M1 and M2, the participants P1, P2,..., Pm submit three random numbers at the same time and calculate and verify whether the secrets M1 and M2 are true or not. According to the method and the device, the problem that the secret of the secret dispatcher is obtained by the first participant through a method of randomly selecting the measurement base to directly measure the coding state sent by the secret dispatcher under the condition that the first participant is not discovered in the existing scheme can be solved.
Owner:LUOYANG NORMAL UNIV
Authenticable semi-quantum secret sharing method and system based on GHZ state
ActiveCN110247768AOptimize usage efficiencyEfficient sharingKey distribution for secure communicationCryptographic attack countermeasuresQuantum secret sharingAttack strategy
The invention belongs to the technical field of information security. The invention discloses an authenticable semi-quantum secret sharing method and system based on a GHZ state, and the method comprises the steps: enabling a strong quantum party to share an n-bit message m secret to a first semi-quantum party and a second semi-quantum party, and obtaining a secret message m after the first semi-quantum party and the second semi-quantum party both know the coding results of the other two parties; by utilizing an absolutely safe quantum key distribution technology, the strong quantum party and the first semi-quantum party sharing keys key ab1 and key ab2; the strong quantum party and the second semi-quantum party sharing the keys keyac1 and keyac2; and the second semi-quantum party and the first semi-quantum party sharing the keybc. In the secret sharing process, bidirectional authentication of the user identity is completed at the same time, security analysis shows that the protocol can resist different attack strategies such as internal attacks and external attacks, and the secret key shared between the users can be used for multiple times; in addition, the method has good particle use efficiency, quantum resources can be saved, and three-party secret sharing can be completed efficiently.
Owner:成都继存科技有限公司
Quantum walking-based quantum secret sharing method and system with credible authentication
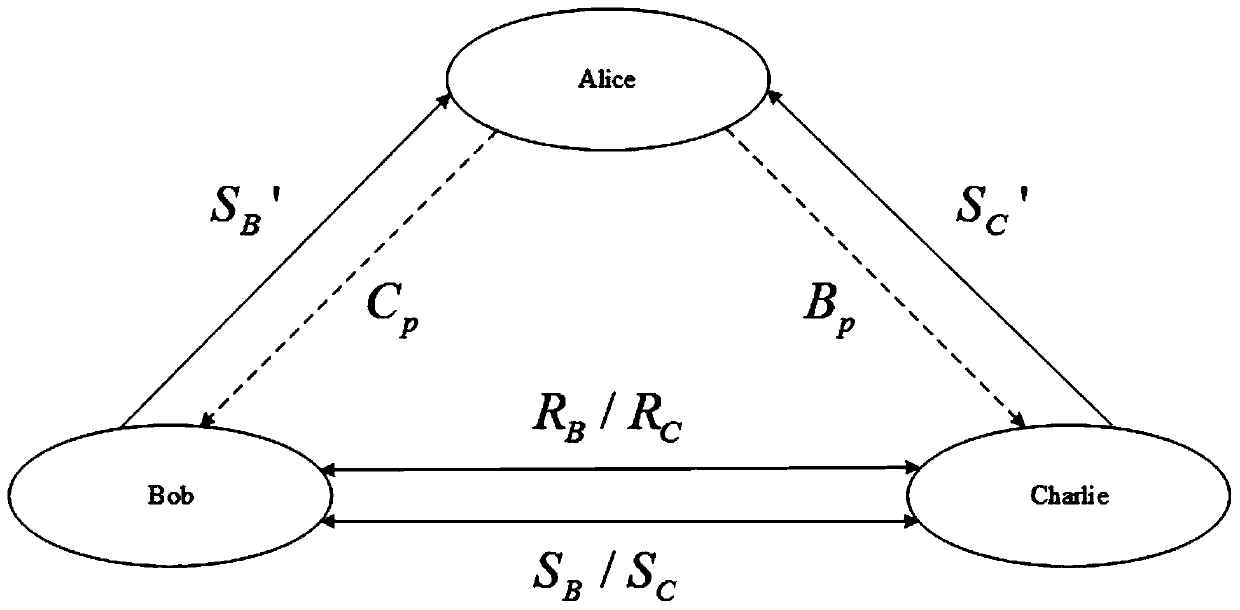
ActiveCN111404691ADetermine securityAvoid attackKey distribution for secure communicationUser identity/authority verificationQuantum secret sharingEngineering
The invention provides a quantum walking-based quantum secret sharing method with credible authentication. The method comprises the following steps: a secret participation end preparing single photonsequences SB and SC, encoding the SB and SC according to an identity authentication key of the secret participation end to obtain SB' and SC ', and sending the SB' and SC' to a secret distribution end; the secret distribution end authenticating the identity of the secret distribution end based on the identity authentication key of the secret participation end; the secret distribution end constructing two quantum walking systems based on the SB and the SC, encoding secret information to be shared to the SB and the SC, and recording secret information encoding particles as MB and MC; the secretdistribution end invisibly transmitting the MB and the MC to the secret participation end; the secret participation ends cooperating with each other to complete identity authentication of the secret distribution end and reconstruction of secret information. According to the trusted identity authentication function and the quantum walking circuit, the safety and practicability of the quantum secretsharing method and system can be improved, and interception / retransmission attacks, entanglement attacks, participant attacks and pretending attacks from the inside and the outside are avoided.
Owner:龙图腾网科技(合肥)股份有限公司
Continuous variable quantum secret sharing implementation method capable of autonomously selecting users, electronic equipment and computer readable storage medium
ActiveCN113055170AAvoid transmissionImprove securityKey distribution for secure communicationComputer networkQuantum secret sharing
The invention discloses a continuous variable quantum secret sharing implementation method capable of autonomously selecting users, electronic equipment and a computer readable storage medium. The method comprises the steps: 1, enabling each participant to generate a dual-mode entangled state, carrying out the projection measurement of a mode A in the dual-mode entangled state, and transmitting a mode B to a data distributor to form original data; step 2, the data distributor selects legal participants from all participants, sorts the legal participants, calculates a regular part when each legal participant is a unique honest participant, and splits the initial secret information according to the regular part; 3, the data distributor sends the sub-secret information to each legal participant according to the sequence, and each legal participant processes the sub-secret information to obtain unique sub-secret information; 4, all the legal participants cooperate with one another to recover the initial secret information; according to the invention, the data distributor can autonomously select part of participants for communication, and the communication safety is improved.
Owner:CENT SOUTH UNIV +1
Quantum secret sharing method based on tensor network and quantum communication system
ActiveCN111865581AImprove scalabilityImprove securityKey distribution for secure communicationUser identity/authority verificationQuantum secret sharingQuantum network
The invention discloses a quantum secret sharing method based on a tensor network and a quantum communication system. A quantum state is reconstructed by utilizing a corresponding relationship betweenclassic information and quantum information; a distributor combines an AKLT model and a matrix product state representation method to realize secret division, and then distributes sub-secrets to participants through a classic authentication channel and a quantum channel; and finally, secret reconstruction is realized based on a tensor network state theory and a (n, n) threshold group recovery protocol. The extendability of secret information and the matrix product representation expandability, transfer characteristics and non-uniqueness of a quantum multi-body state are the biggest innovationpoints of the invention, safety and reliability of quantum communication are guaranteed, and the problem that dynamic construction cannot be achieved through existing quantum state secret sharing issolved. Diversity of matrix product state representation and simple graphic representation corresponding to the tensor network enable the method of the invention to have a good application prospect inthe field of quantum state sharing and information security in a quantum network.
Owner:SOUTHWEST UNIVERSITY
Multi-party quantum secret sharing method based on quantum walk and system thereof
ActiveCN113645034AThe number of people can be expandedVerify correctnessKey distribution for secure communicationComputer networkSecret share
The invention provides a multi-party quantum secret sharing method based on quantum walk and a system thereof, and the method comprises the following steps: S1, firstly constructing a quantum walk subsystem by a secret distributor Alice, and executing the quantum walk to generate an entangled state for secret sharing; S2, enabling a secret distributor Alice splits secret to share and distribute the secret shares to participants, and executing wiretapping detection; after eavesdropping detection, measuring particles in the hand by the participant; and S3, enabling the Alice to randomly select a part of measurement results as samples for verification, and recovering all original secret messages after verification is passed. According to the invention, quantum walking multi-party secret sharing is realized by using the on-ring quantum walking principle.
Owner:HUNAN NORMAL UNIVERSITY
High-capacity quantum secret sharing method based on photon orbital angular momentum encoding
ActiveCN104821875BImplement decodingImprove communication capacityKey distribution for secure communicationFrequency spectrumQuantum secret sharing
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method for attacking Fourier transform quantum secret sharing systems
InactiveCN101931528BEffective attackKey distribution for secure communicationSecret communicationComputer hardwareQuantum secret sharing
Owner:BEIJING UNIV OF POSTS & TELECOMM
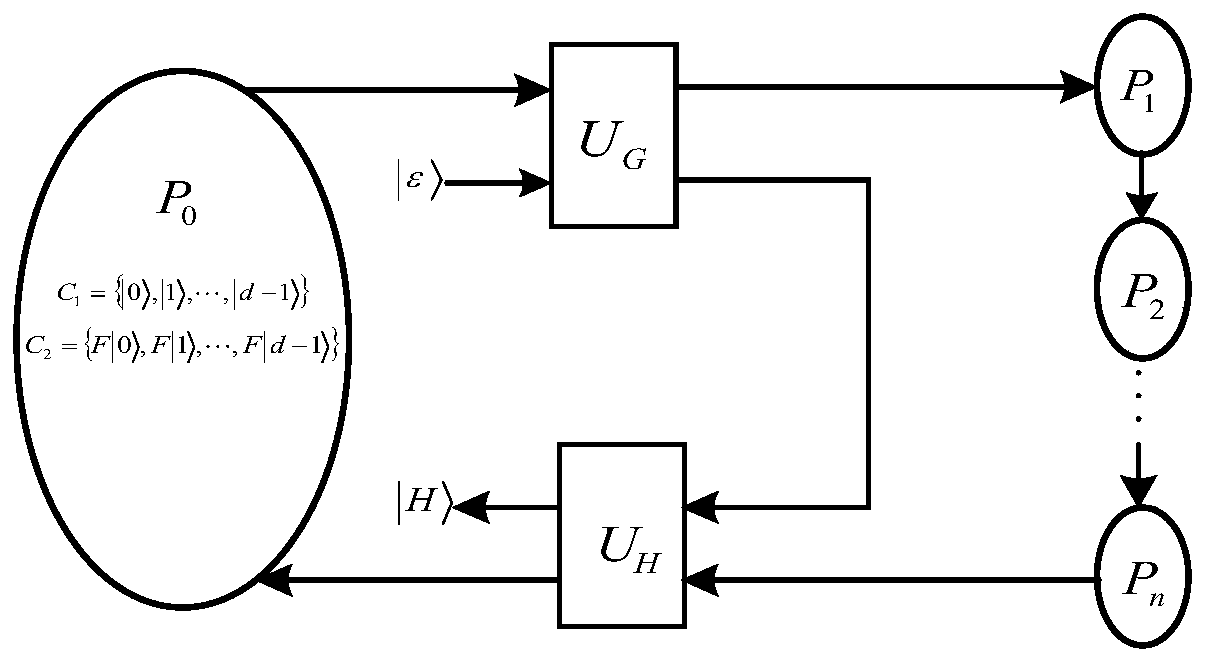
Quantum signature method and quantum secret sharing method using quantum trapdoor one-way function
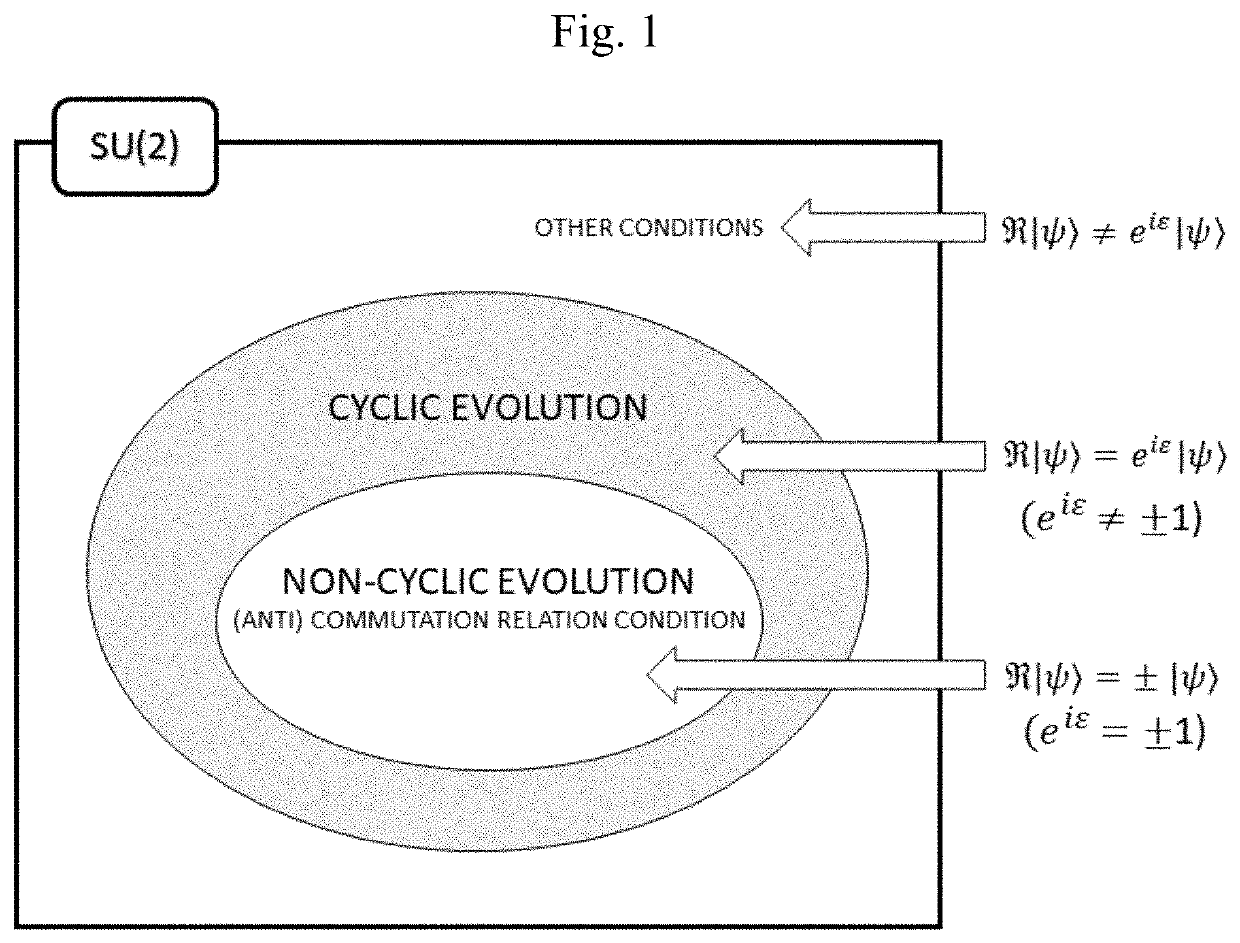
ActiveUS20200287714A1Key distribution for secure communicationPublic key for secure communicationQuantum secret sharingParticle physics
This specification discloses a quantum public-key cryptosystem. The quantum public-key cryptosystem may use two rotation operators R{circumflex over (n)}(θ) and R{circumflex over (m)}(φ) satisfying a cyclic evolution. The two rotation operators R{circumflex over (n)}(θ) and R{circumflex over (m)}(φ) do not have a commutation relation or an anti-commutation relation with each other. The commutation relation or the anti-commutation relation is established when either of the following conditions is satisfied: θ=2iπ, φ=2jπ, or {circumflex over (n)}·{circumflex over (m)}=1 (i, j=integer), and θ=(2k+1)π, φ=(2l+1)π, or {circumflex over (n)}·{circumflex over (m)}=0 (k, l=integer).
Owner:KOREA INST OF SCI & TECH
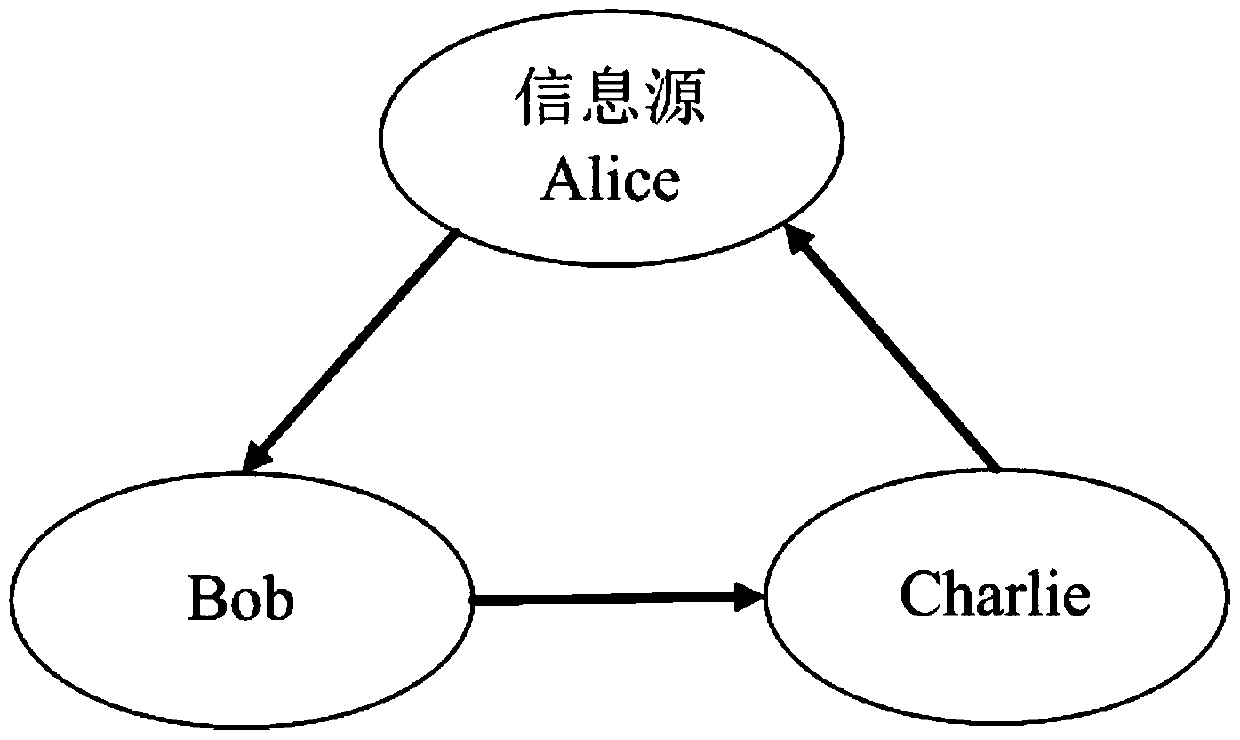
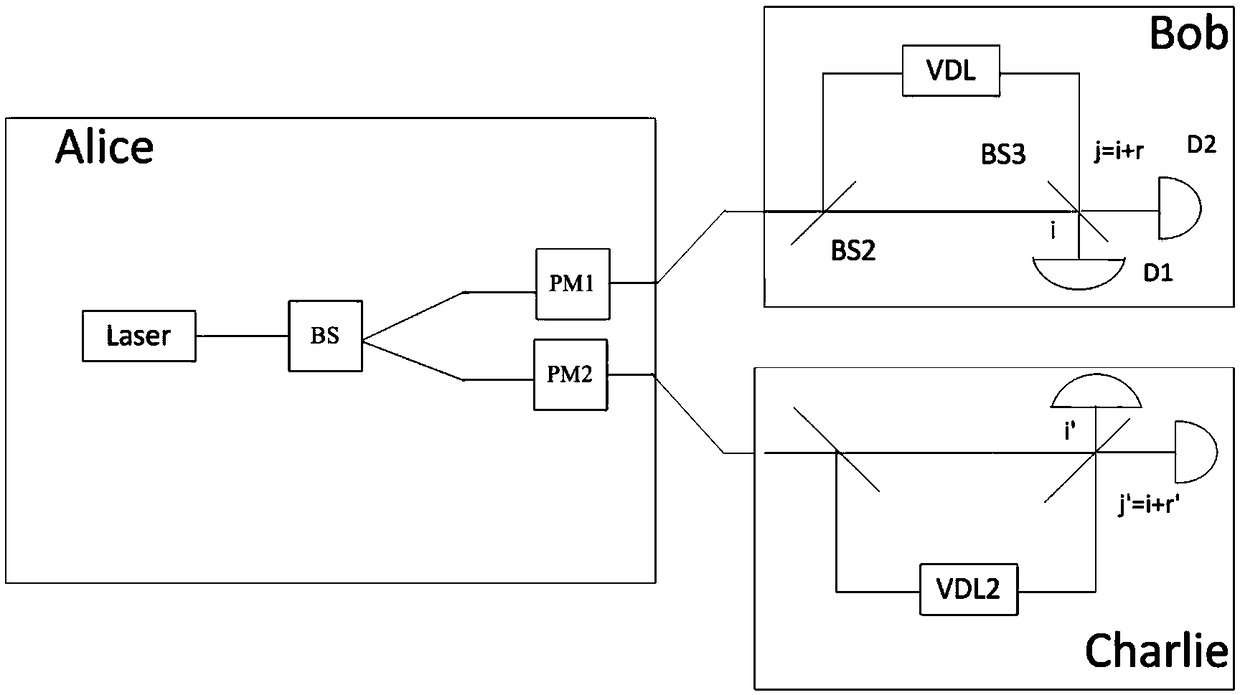
Quantum secret sharing method based on round-robin differential phase-shifting quantum key distribution protocol
InactiveCN108809640AImprove noiseEasy to operateKey distribution for secure communicationDifferential phaseQuantum secret sharing
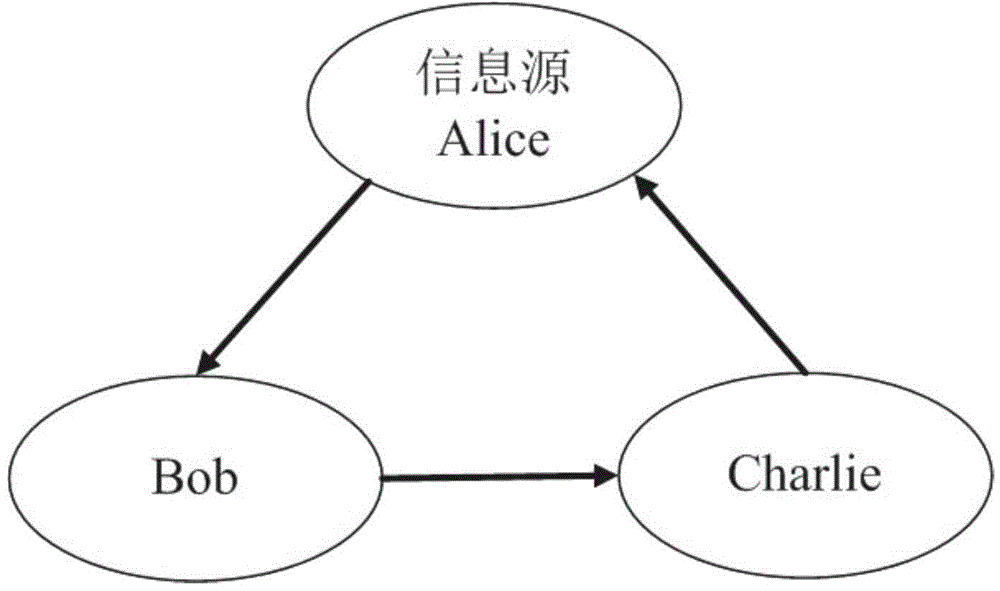
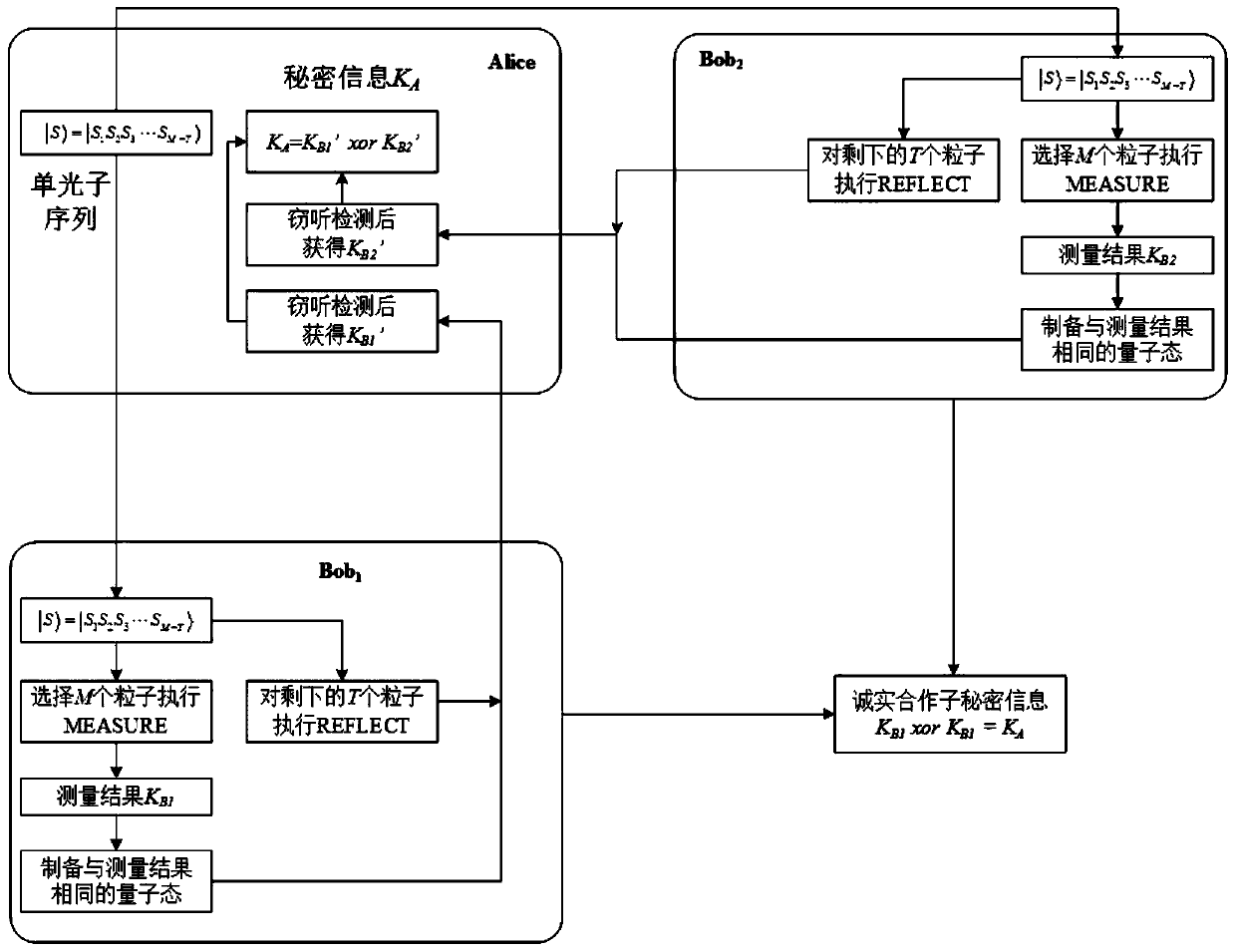
The invention discloses a quantum secret sharing method based on a round-robin differential phase-shifting quantum key distribution protocol. The method comprises a secret distributor Alice and at least two participants Bob and Charlie; the distributor Alice divides one piece of information into two parts to respectively send to the Bob and the Charlie following the cyclic differential phase-shifting quantum key distribution protocol; and the information of the Alice can be acquired as long as the Bob and the Charlie mutually cooperate in honest. The single-photon light source is used in the method disclosed by the invention, the RRDPS-QKD protocol is applied to the quantum secret sharing, and higher noise tolerance and operation convenience are provided.
Owner:南京南瑞国盾量子技术有限公司 +3
Annular multi-party semi-quantum secret sharing method based on d-level single-particle state
The semi-quantum secret sharing concept is popularized to a d-level quantum system, and the annular multi-party semi-quantum secret sharing method based on the d-level single-particle state is provided. In the method provided by the invention, the particles prepared by the quantum party are transmitted in an annular manner, and the classical party does not need to have the measurement capability.The method disclosed by the invention is safe to some famous attacks, such as intercept-resend attack, a measure-resend attack, an entangle-measure attack and a participant attack..
Owner:河北凯通信息技术服务有限公司
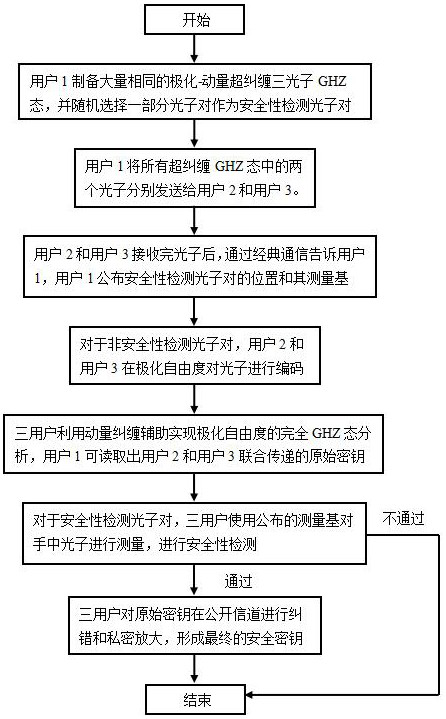
Quantum secret sharing method based on hyper-entanglement assistance
ActiveCN114401088AEliminate leaksEnsure safetyKey distribution for secure communicationPhotonic quantum communicationQuantum secret sharingParticle physics
According to the quantum secret sharing method based on hyper-entanglement assistance, a user 1 prepares a hyper-entanglement three-photon GHZ state and selects a security detection photon pair; and the user 1 sends two photons in all the hyper-entangled GHZ states to the user 2 and the user 3. After the photons are received, the user 1 publishes positions and measurement bases for safety detection of the photons; coding operation is carried out on photon pairs subjected to non-security detection, a user 2 and a user 3, and complete GHZ state analysis of polarization degree of freedom is carried out on the three users. The user 1 obtains the coded polarization GHZ state, and an original key is obtained; and for the photon pair for security detection, the three users use the measurement bases to measure photons in their hands, security detection is carried out, and if the measurement bases pass the security detection, the three users carry out error correction and private amplification on the original key to form a final security key. According to the method, base processing is not needed, the eight polarization GHZ states are completely distinguished, each hyper-entangled GHZ state can transmit a 3-bit key, the key generation efficiency is obviously improved, and the practicability is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Semi-quantum secret sharing method with limited quantum resources
ActiveCN108173656BSimplify Quantum CapabilitiesReduce communication costsKey distribution for secure communicationComputer networkQuantum secret sharing
The invention discloses a quantum resource limited semi-quantum secret sharing method. Semi-quantum secret sharing usually includes that a quantum side Alice divides a secret into two parts and sendsthem to quantum resource limited Bob and Charlie respectively, and only when the Bob and the Charlie cooperate, the complete secret be recovered. At present, the typical semi-quantum secret sharing method guarantees the security, but requires the semi-quantum sides Bob and Charlie to perform quantum measurement operations. The measurement device may be unsafe, which increases the hidden danger ofsecret sharing. The present invention enables the resource limited Bob and Charlie to perform secret sharing without a quantum measurement device, and the quantum side Alice does not require quantum memory. In this way, the present invention can greatly reduce the quantum resources required by the three participants, thereby saving the communication cost.
Owner:XIANGTAN UNIV
A quantum secret sharing method based on d-level single particles
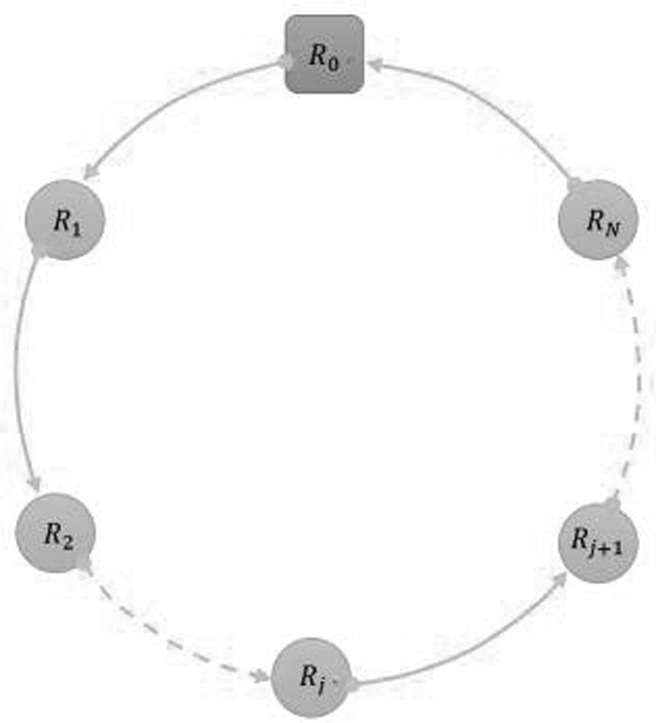
ActiveCN110011797BReduce particle countImprove quantum efficiencyKey distribution for secure communicationQuantum efficiencyQuantum secret sharing
The invention relates to an efficient and practical quantum secret sharing method based on a d-level single particle. A secret distributor prepares a d-level single particle and uses it as an information carrier for circular transmission between each participant. Each participant encodes its sub-secret into the signal particle through a local unitary operation without quantum storage, which improves the practicability of the scheme. The quantum Fourier transform is used to construct two mutually unbiased ground states on the d-level quantum system, and the quantum unclonability is combined to ensure the unconditional security of the scheme in theory. In the present invention, one d-level particle can share two classical bits, and the number of particles required for wiretapping detection is reduced through a combined wiretapping detection method, so as to ensure that the scheme obtains higher quantum efficiency.
Owner:FUJIAN NORMAL UNIV
A tree-type multi-party semi-quantum secret sharing method based on d-level single-particle states
The invention extends the concept of half-quantum secret sharing to a d-level quantum system, and proposes a tree-type multi-party half-quantum secret sharing method based on a d-level single-particle state. In the method of the present invention, the particles prepared by the quantum method are transported in a tree form, and the classical method does not need to have measurement capabilities. The method of the present invention is safe against some well-known attacks, such as intercept-resend attack, measurement-resend attack, entanglement-measurement attack and participant attack.
Owner:廖治文
A Quantum Secret Sharing Method Based on Bell State
InactiveCN106712945BRealize secret sharingReduce complexityKey distribution for secure communicationQuantum efficiencyBell state
The invention discloses a quantum secret sharing method based on a Bell state. The quantum secret sharing method is characterized by comprising a secret distributor and n participants, the secret distributor distributes a random secret to the n participants, wherein each participant obtains a sub-secret, when the n participants accumulate all sub-secrets, the originally shared secret can be restored, and any information of the shared secret cannot be obtained less than n participants. By adoption of the quantum secret sharing method disclosed by the invention, the problems of participant fraud, low security, complexity and efficiency of channels in the existing quantum secret sharing process are solved, the quantum and classical resources can be saved, the operation complexity is reduced, and higher quantum efficiency is ensured.
Owner:ANHUI UNIVERSITY
A multi-party quantum secret sharing method and system based on quantum walk
ActiveCN113645034BThe number of people can be expandedVerify correctnessKey distribution for secure communicationSecret shareQuantum secret sharing
Owner:HUNAN NORMAL UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com