Quantum secret sharing method based on round-robin differential phase-shifting quantum key distribution protocol
A quantum key distribution and quantum secret technology, applied in the field of quantum secret sharing, can solve problems such as low noise tolerance, and achieve the effect of high noise tolerance and easy operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
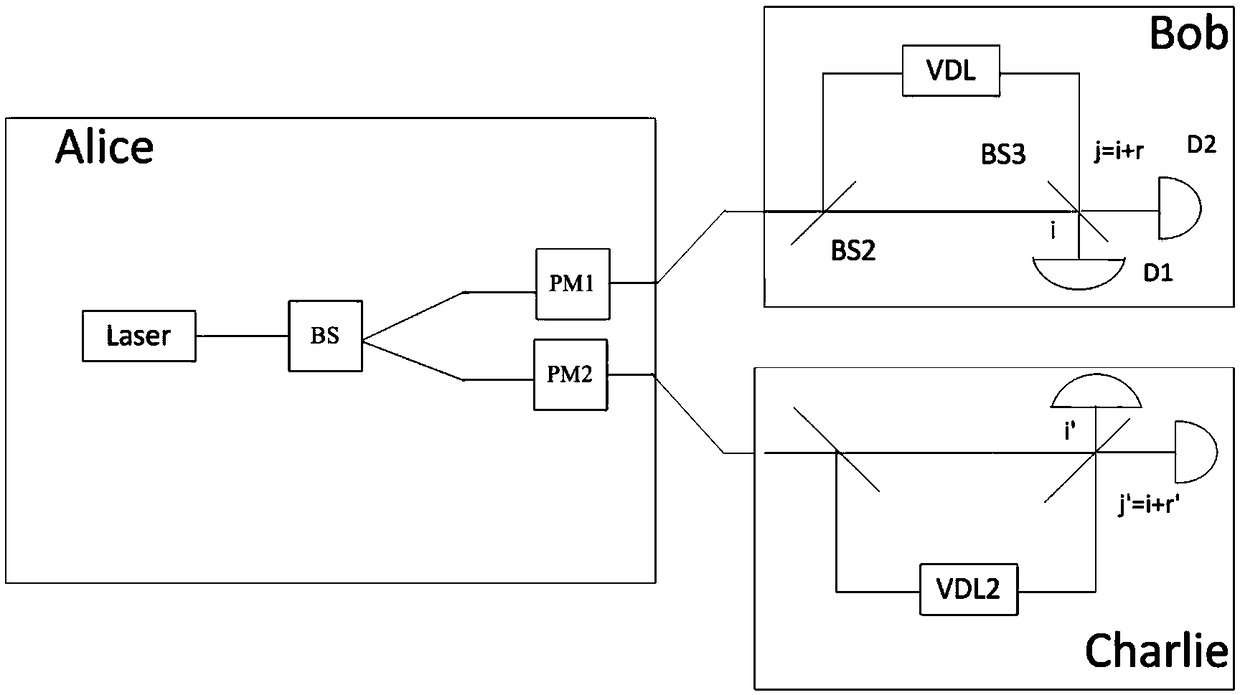
[0021] A quantum secret sharing method based on the cyclic differential phase shift quantum key distribution protocol of the present invention, wherein an application scenario includes a secret distributor Alice, and at least two participants Bob and Charlie, the sender Alice wants a message It is divided into two parts and sent to Bob and Charlie respectively. Only when Bob and Charlie cooperate with each other honestly can Alice’s information be jointly obtained; the quantum secret sharing method includes the following steps:
[0022] Step S1, Alice first generates two strings of L-long random bit sequences: B=S 1b S 2b ... S Lb and C=S 1c S 2c ... S Lc , and then use a single-photon lig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com