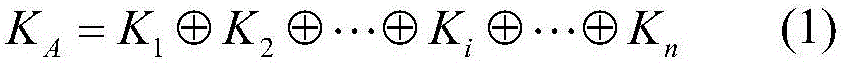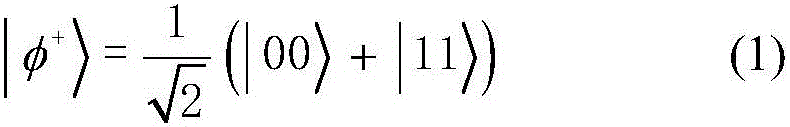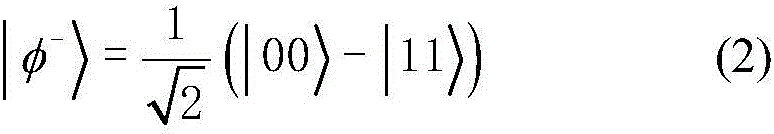Quantum secret sharing method based on Bell state
A quantum secret and secret technology, applied in the field of quantum secret sharing based on the Bell state, can solve the problems of high requirements for the number of measurements and difficulty of measurement, poor practicability, and large number of security checks, etc., to reduce storage The cost, the number of measurements and the difficulty of measurement, the effect of reducing computational complexity, reducing the number of times and difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In this embodiment, a quantum secret sharing method based on the Bell state is that there is a secret distributor Alice, and n participants P 1 ,P 2 ,...,P i ,...,P n ;P i Indicates the i-th participant; 1≤i≤n; the secret distributor Alic distributes a random secret to n participants, and each participant obtains a sub-secret, when n participants share all their sub-secrets When stacked together, the original shared secret can be recovered, and less than n participants will not get any information about the shared secret. The present invention uses the Bell state as a quantum resource, wherein one particle in each Bell state is stored in the quantum register of the secret distributor, and the other particle is transmitted to each participant in a random order, and each participant Performs a single-particle unitary operation on each particle received. Finally, when all the particles are sent back to the secret distributor, the secret distributor Alic performs Bell-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com