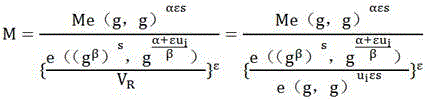
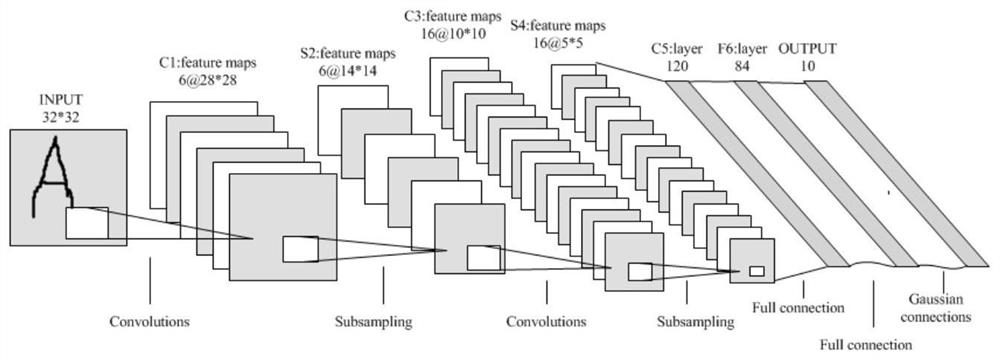
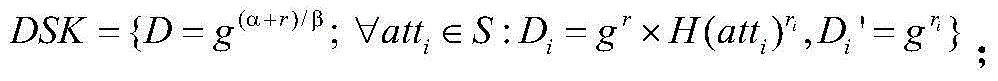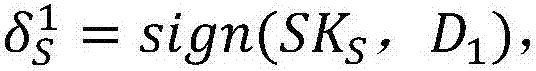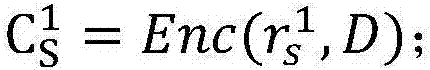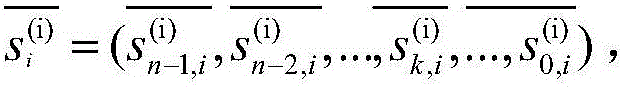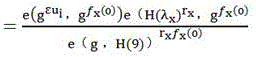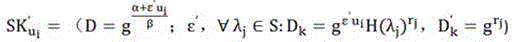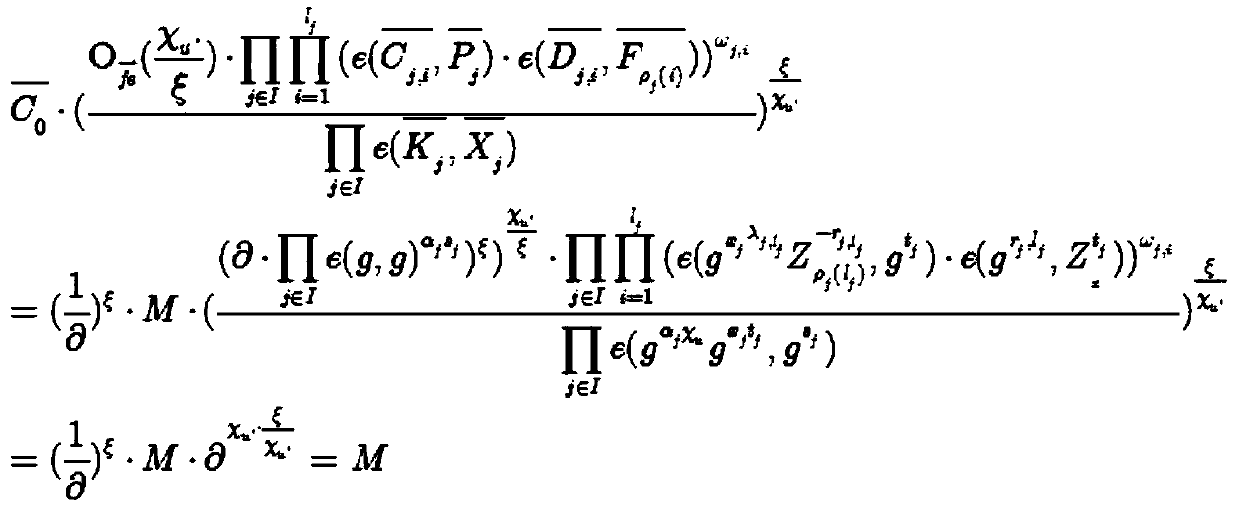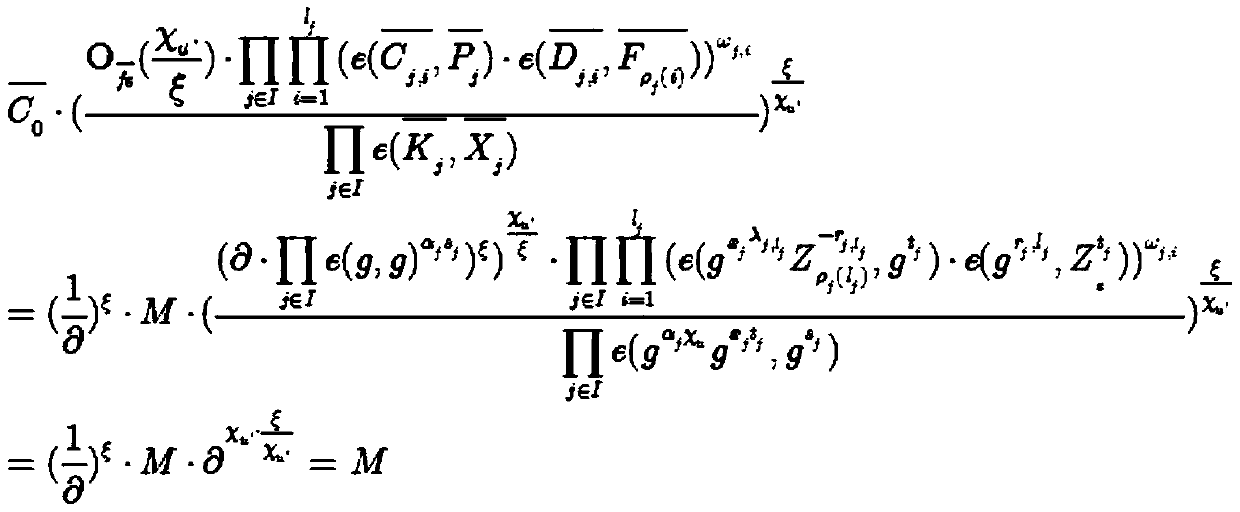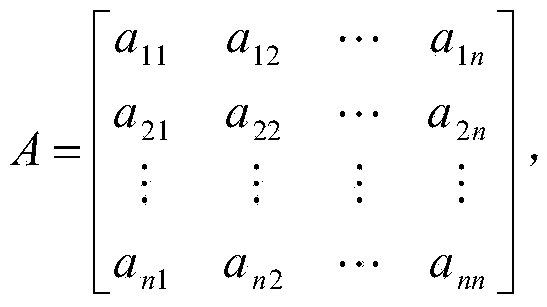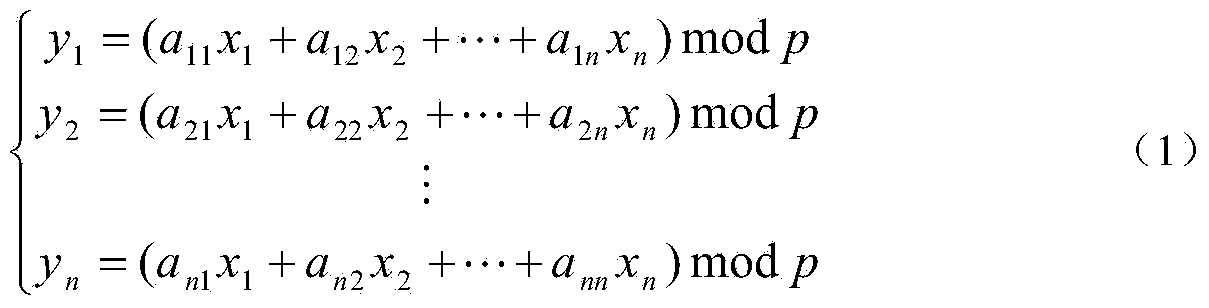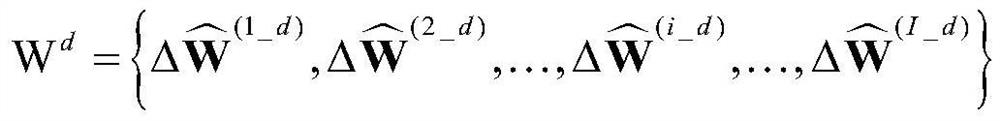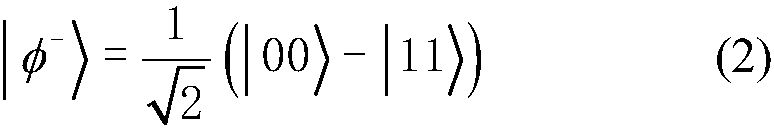Patents
Literature
52results about How to "Resistant to Collusion Attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
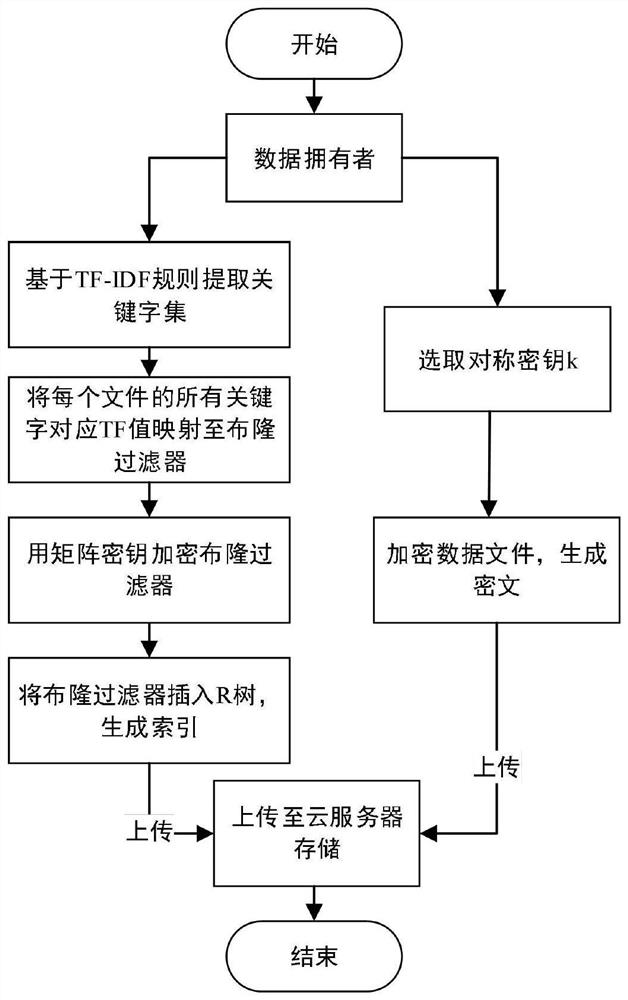
User-oriented cloud storage data integrity protection method
InactiveCN105320899ASave storage spaceAvoid Lost Security RisksDigital data protectionData integrityOriginal data
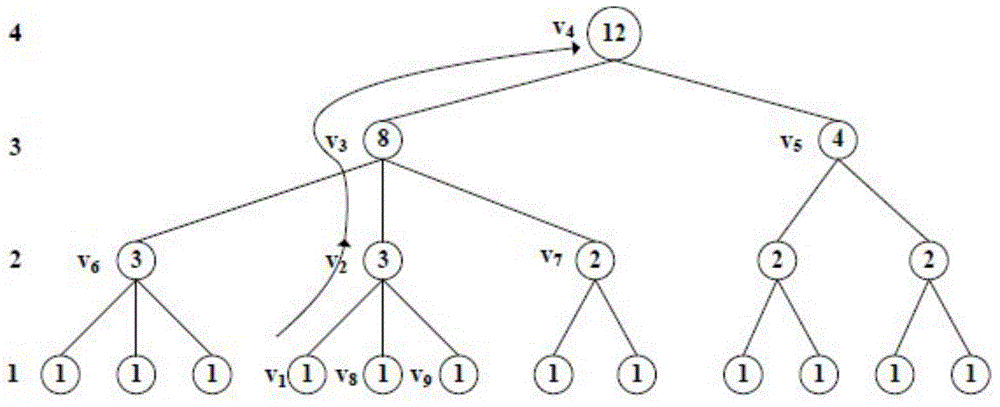
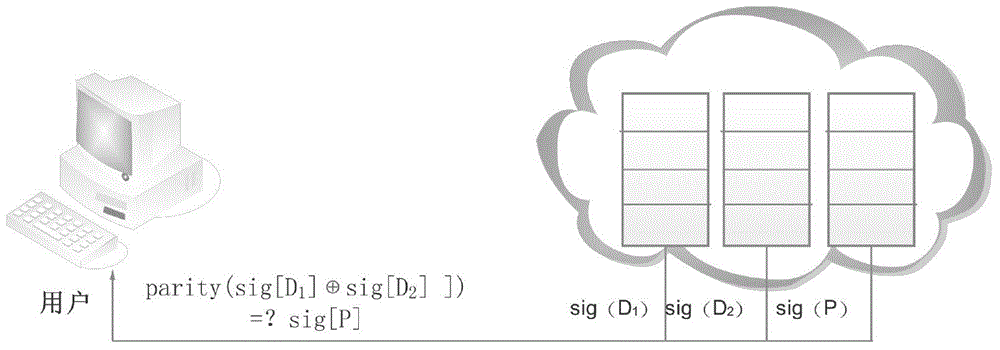
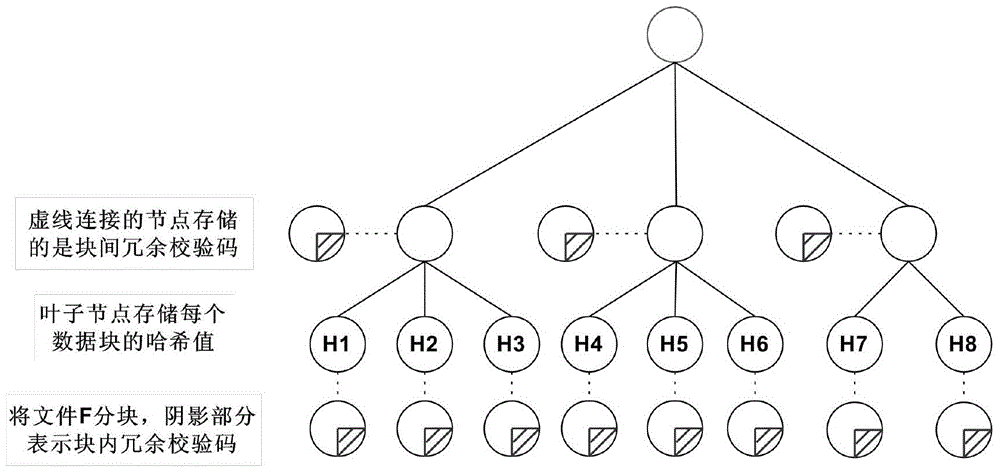
The invention discloses a user-oriented cloud storage data integrity protection method. The method includes the steps of 1, uploading, wherein a user side segments and numbers a file to generate intra-block redundancy check codes, the hash value of each file block is calculated and saved as a range-based 2-3 tree, the hash values are linked into one value and signed with private keys, and inter-block redundancy check codes are generated and encrypted with stream substitution secret keys; 2, verification, wherein a cloud management node sends a verification request to a corresponding cloud storage server, corresponding original data and algebraic signatures of the inter-block redundancy check codes corresponding to the original data are calculated and returned to the user side for data integrity verification, and the step 3 is executed if data destruction is found; 3, recovery, wherein the user side acquires all the file blocks on corresponding branch trees from a cloud side according to tree information and performs error recovery on the file blocks through erasure codes of the file blocks. According to the method, integrity verification and recovery are performed on the dynamic data stored in the cloud side from the user perspective.
Owner:PEKING UNIV
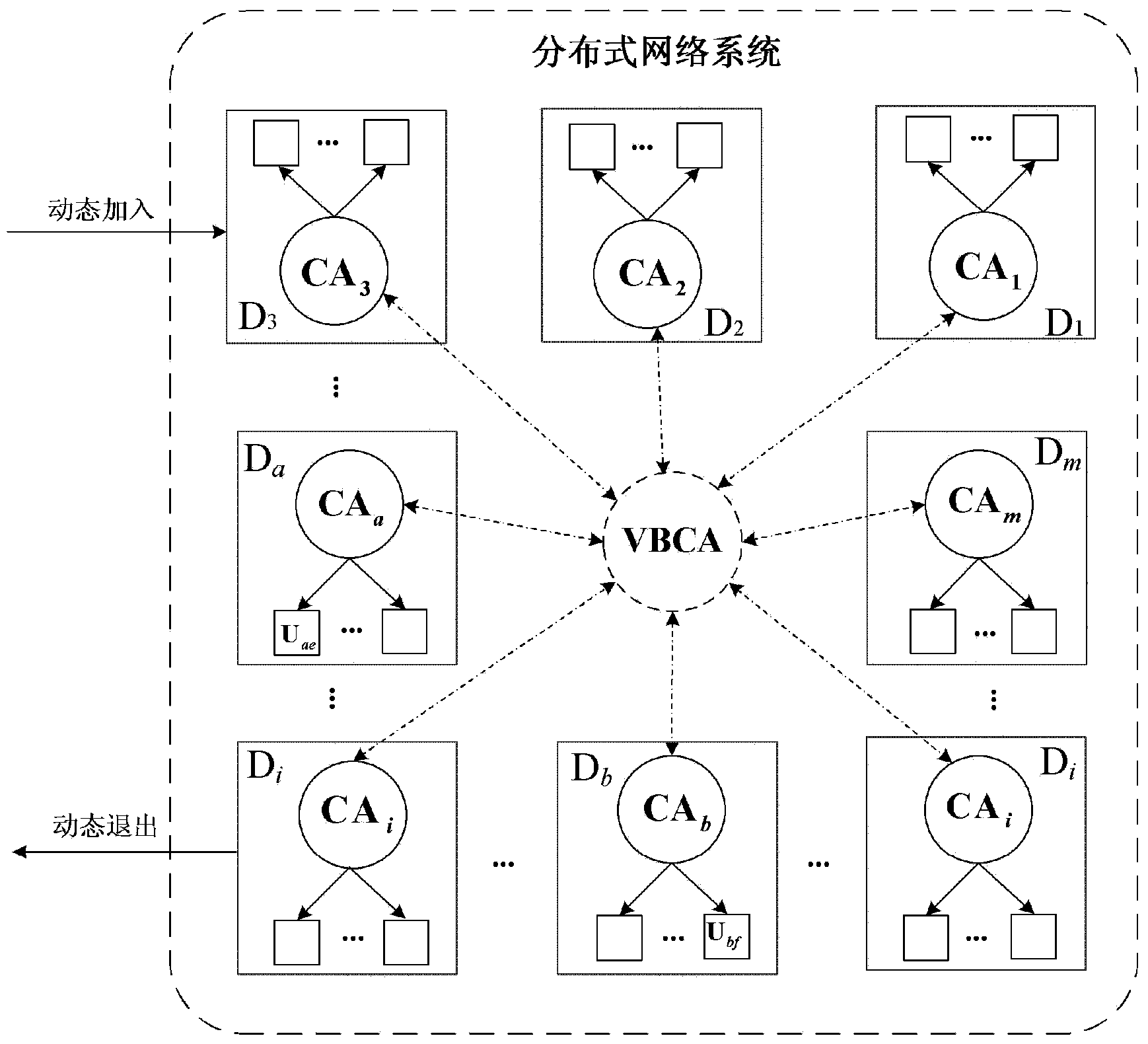
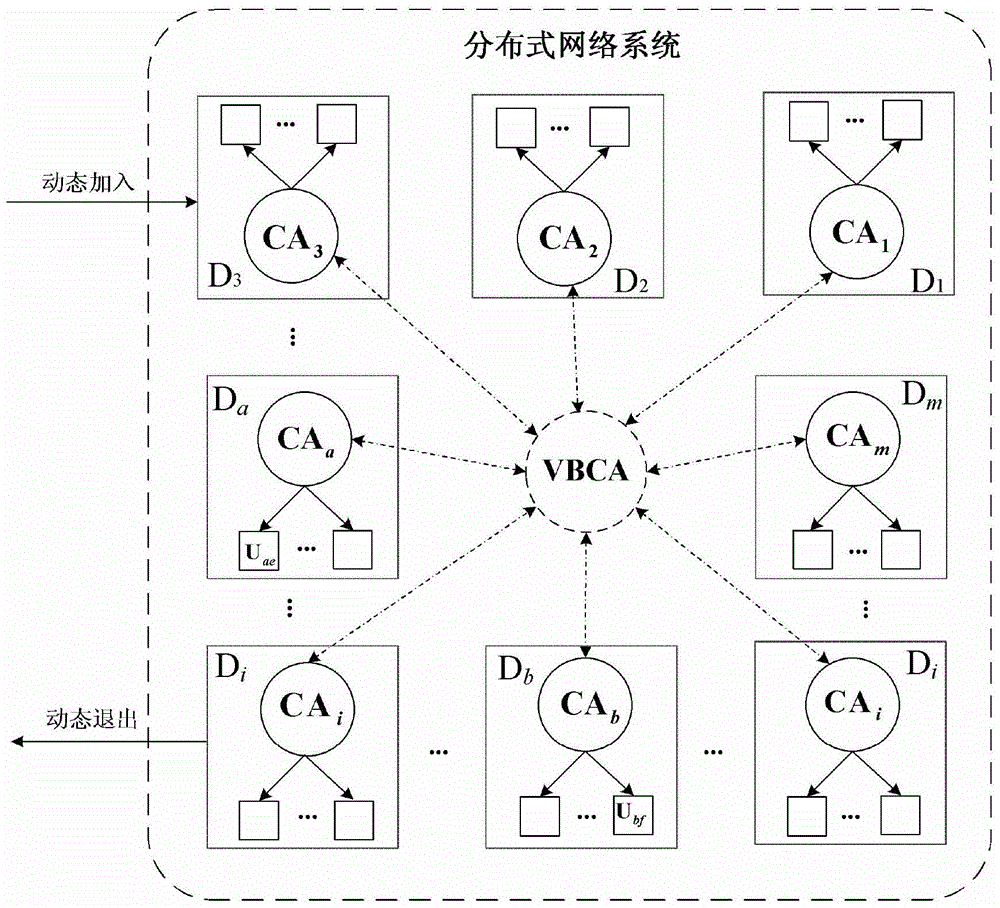
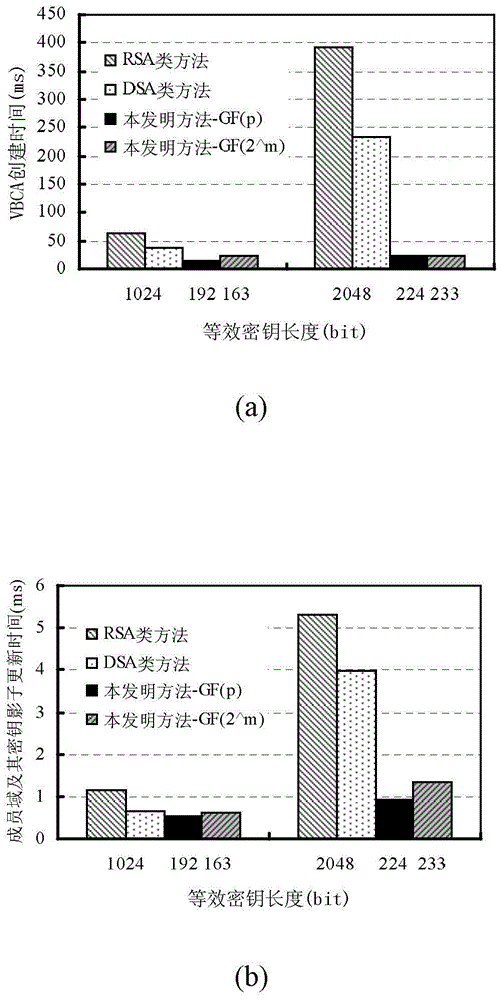
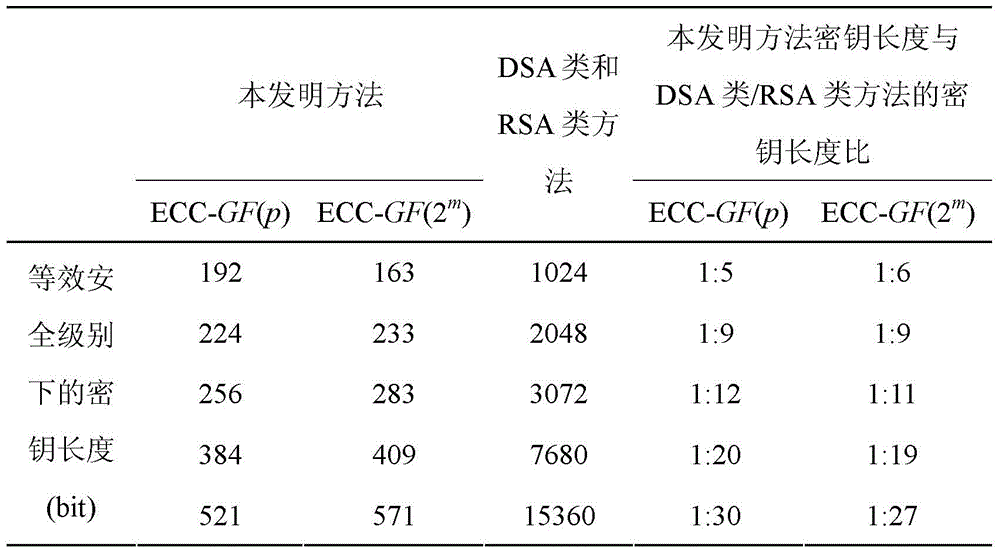
Cross-trust-domain authentication method used for distributed network system
InactiveCN103973451AAvoid creatingReduce maintenance costsUser identity/authority verificationNetworked systemCryptosystem
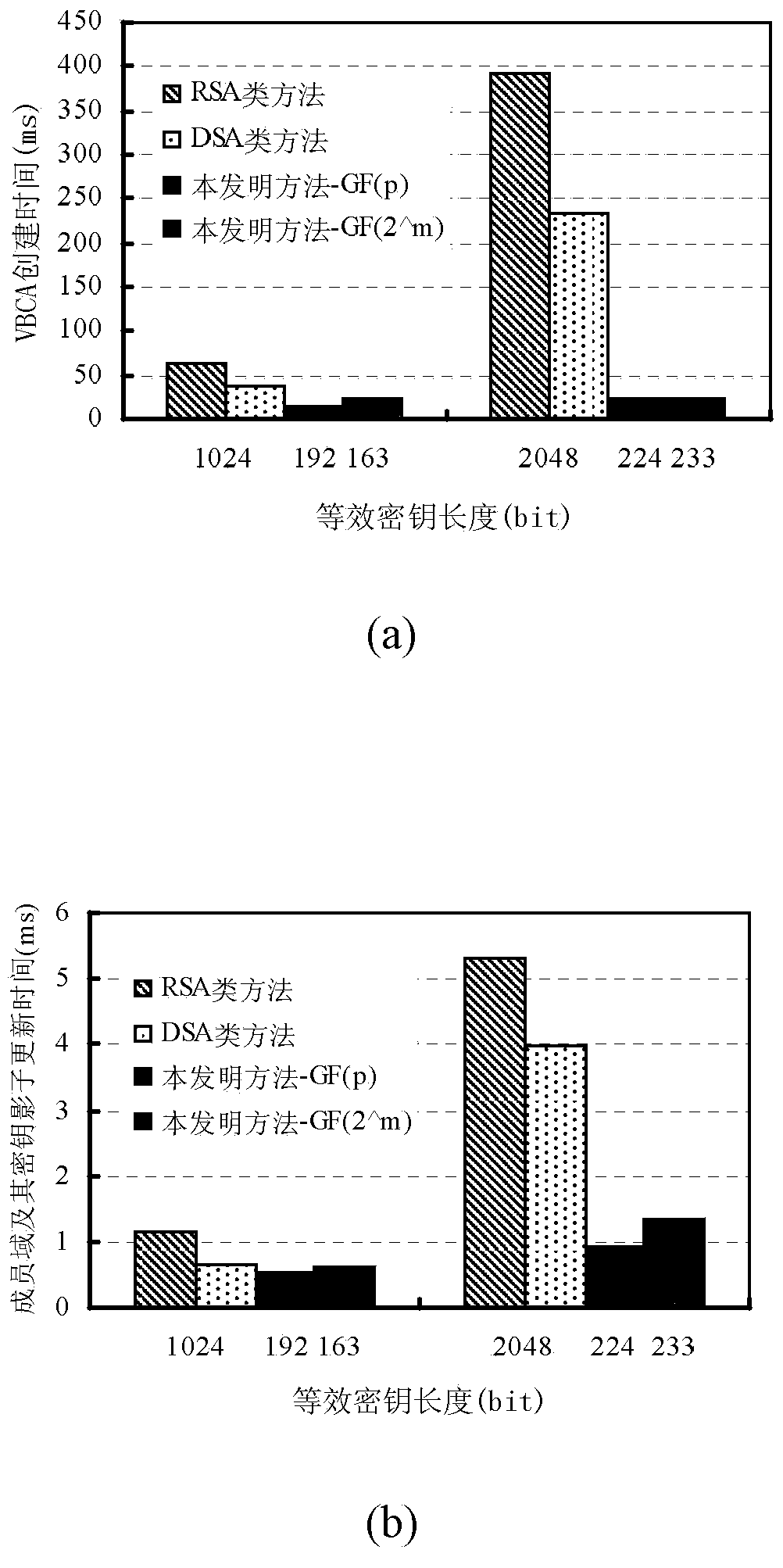
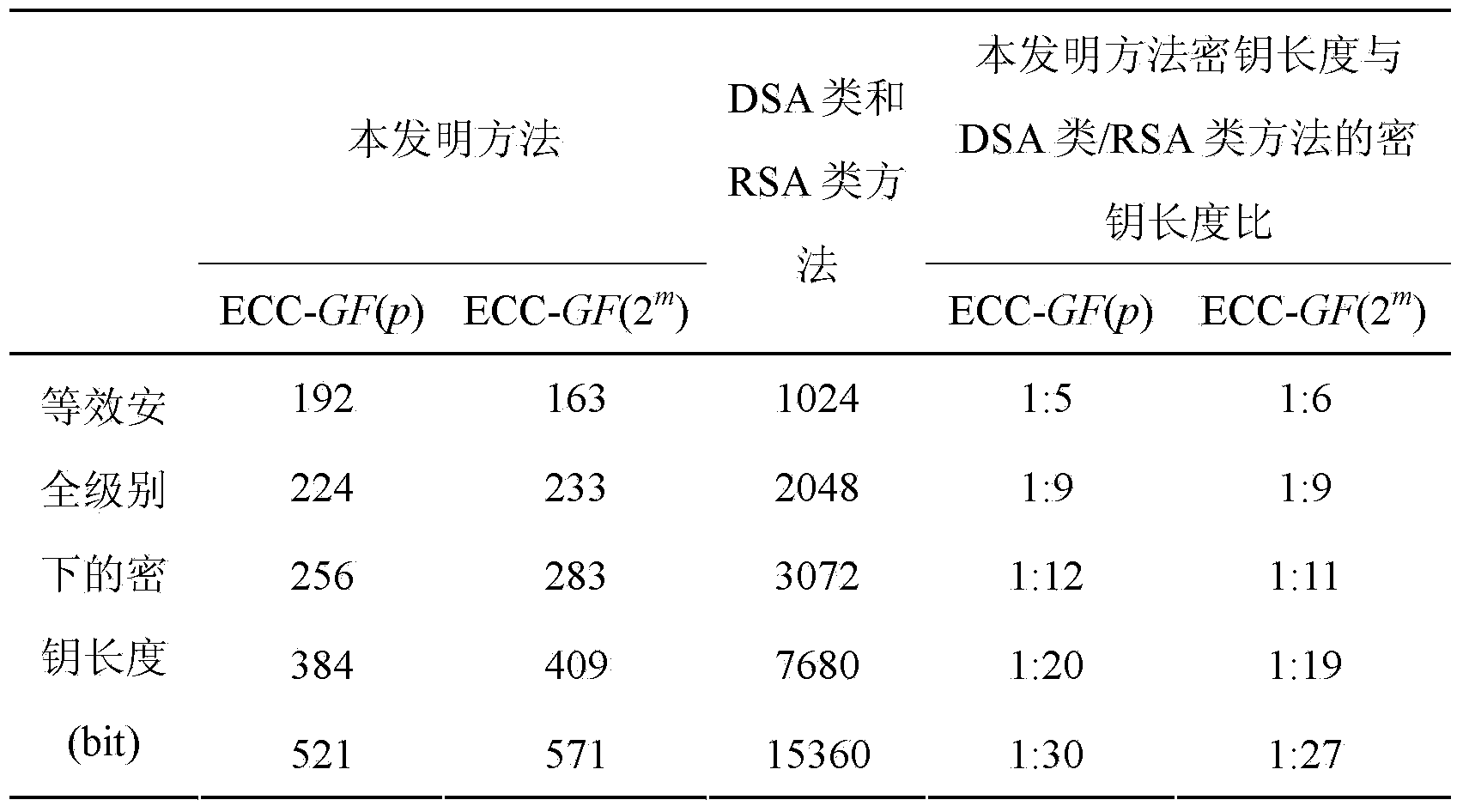
The invention discloses a cross-trust-domain authentication method used for a distributed network system. According to the method, a distributed secrete key generation and threshold signature mechanism based on an elliptical curve cryptosystem is adopted to construct a virtual bridge authentication center (VBAC), and cross-domain interaction authentication between different trust domain entities in the distributed network system is completed through the VBAC. The cross-trust-domain authentication method has the advantages of being universally applicable to various organization structures, agile, dynamic, low in cost, short in authentication path, high in bit safety, high in efficiency and the like, in addition, the method can be realized by hardware easily, can easily solve the problem of cross-domain interaction authentication between the different trust domain entities of the dynamic distributed network system under the condition that terminal resources or the communication bandwidth is limited, and has wide application prospects in cloud computation, a cloud storage network, the internet of things, a wireless sensor network, an agile manufacturing system and a virtual organization.
Owner:SOUTHWEST JIAOTONG UNIV
Quantum secret sharing method based on Bell state
InactiveCN106712945ARealize secret sharingReduce complexityKey distribution for secure communicationBell stateQuantum efficiency
The invention discloses a quantum secret sharing method based on a Bell state. The quantum secret sharing method is characterized by comprising a secret distributor and n participants, the secret distributor distributes a random secret to the n participants, wherein each participant obtains a sub-secret, when the n participants accumulate all sub-secrets, the originally shared secret can be restored, and any information of the shared secret cannot be obtained less than n participants. By adoption of the quantum secret sharing method disclosed by the invention, the problems of participant fraud, low security, complexity and efficiency of channels in the existing quantum secret sharing process are solved, the quantum and classical resources can be saved, the operation complexity is reduced, and higher quantum efficiency is ensured.
Owner:ANHUI UNIVERSITY
Combining method and system for protecting power utilization privacy and integrity in smart power grid
ActiveCN104639311AGuaranteed privacyIntegrity guaranteedKey distribution for secure communicationDigital data protectionData aggregatorSmart meter
The invention discloses a combining method and system for protecting power utilization privacy and integrity in a smart power grid. According to the method, a smart electric meter arranged for a user is used for recording and reporting the power consumption of the user in real time; a gateway having computing capability is responsible for a data combining function and a relay function; a control center is used for collecting, processing and analyzing the real-time power consumption data of each user, and providing reliable services; a credible center is used for managing a whole system. The method comprises a system initialization stage (1), a user data reporting stage (2), a security data combining stage (3) and combined data recovery extremism (4). By adopting the combining method and system, a safe data combining system is implemented, and the power utilization privacy of the user is protected; meanwhile, the integrity of data is ensured, namely, data communication errors are detected and reported technically, the user is prevented from reporting illegally with a false name, and the reported power consumption is prevented from being illegally captured, modified, faked and the like.
Owner:杭州云渊盛旅科技有限公司
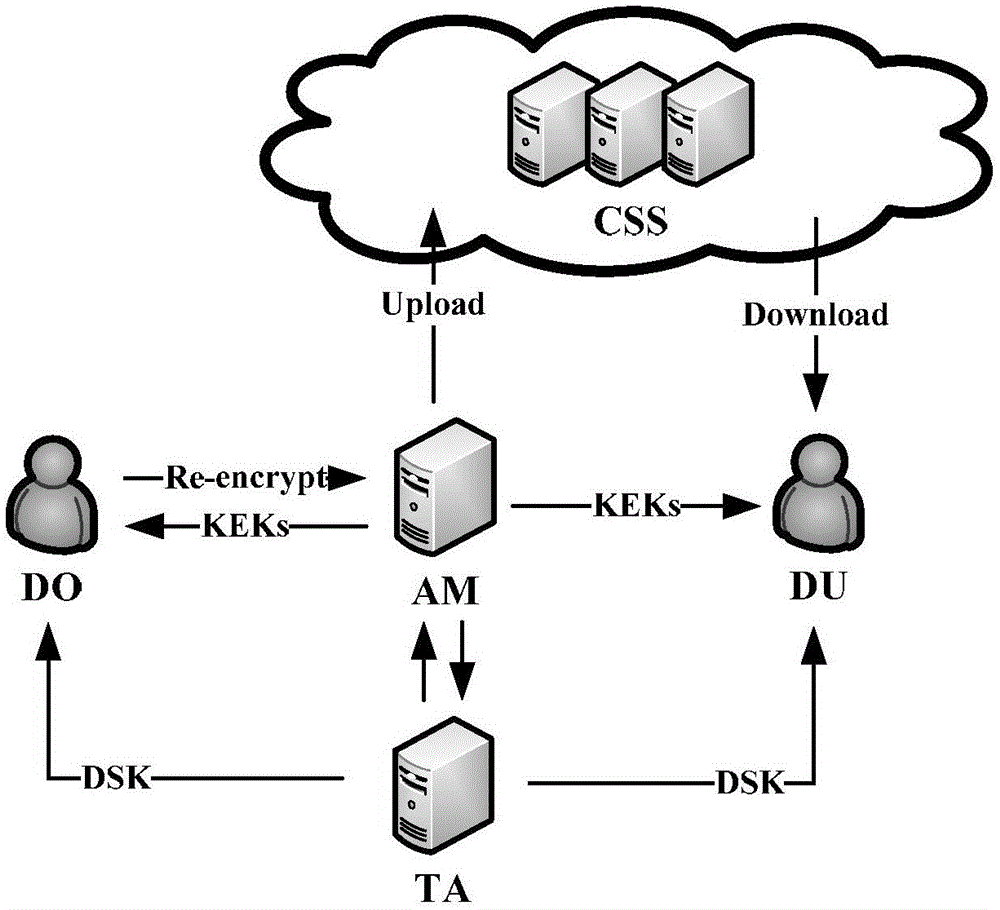
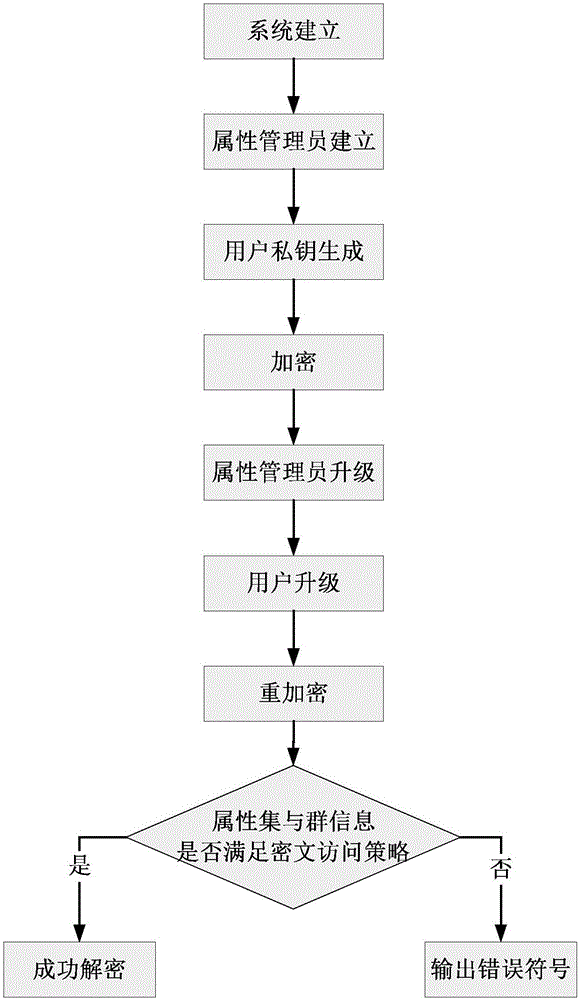
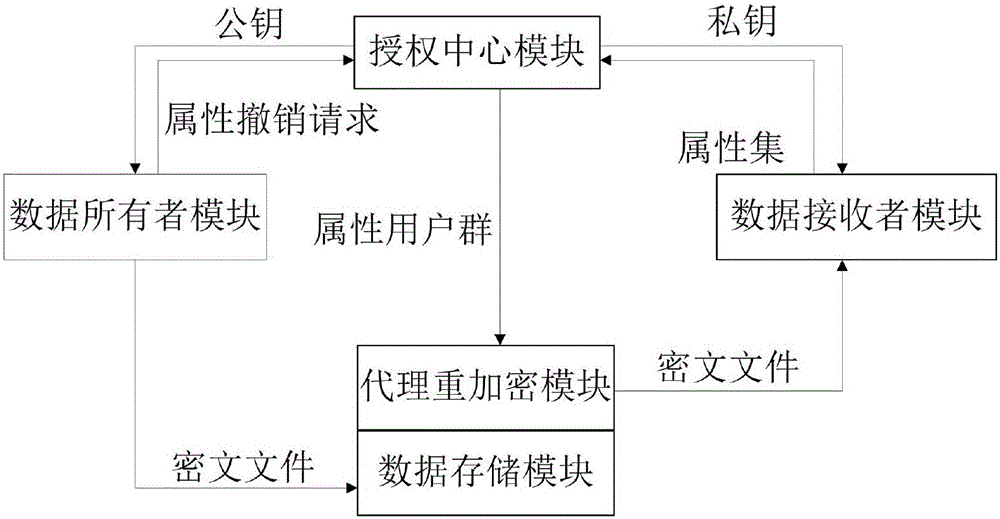
Ciphertext poly attribute base encryption method having efficient attribute revocation capability
ActiveCN105071937ASmall revocation costHigh undo efficiencyUser identity/authority verificationAttribute-based encryptionCiphertext
The invention discloses a ciphertext poly attribute base encryption method having an efficient attribute revocation capability. The method successively comprises the following steps: (1) system establishment, (2) attribute administrator establishment, (3) user private key generation, (4) encryption, (5) decryption, (6) attribute administrator upgrading, (&)user upgrading, and (8) re-encryption. The method has the advantages of less users related in the revocation process, small revocation cost, high revocation efficiency and the like.
Owner:HOHAI UNIV
Encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes
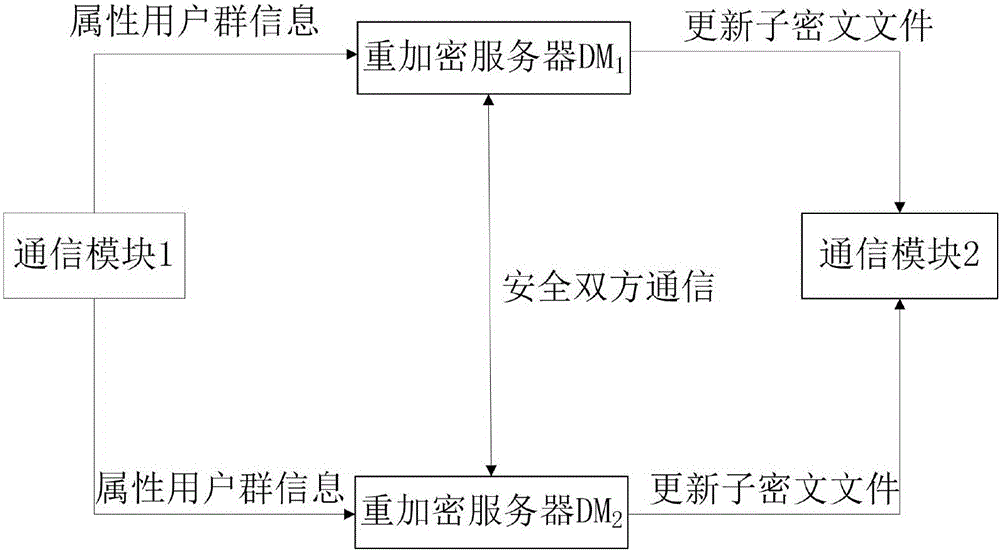
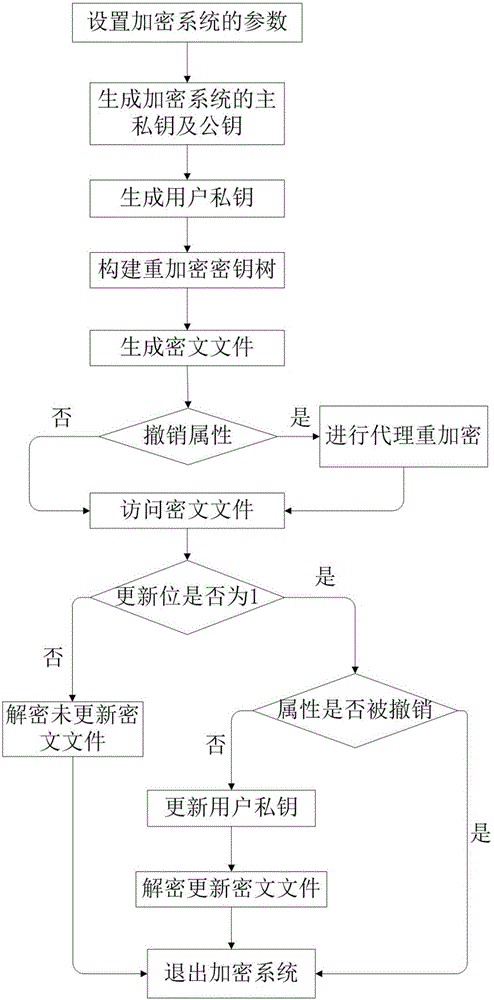
ActiveCN106059768ALeak resistanceOvercoming property revocation flawsKey distribution for secure communicationPublic key for secure communicationCiphertextDisk encryption
The present invention provides an encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes. The method comprises: 1, setting the parameters of an encryption system; 2, generating the main private key and the public key of the encryption system; 3, generating a user private key; 4, building a re-encryption key tree; 5, generating a cryptograph file; 6, cancelling attributes; 7, performing re-encryption agency; 8, accessing the cryptograph file; 9, determining whether the update position of the cryptograph file is 1 or not; 10, decrypting an un-updating cryptograph file; 11, updating the private key; 12, decrypting the update cryptograph file; and 13, quitting the encryption system. Through adoption of a dual-agency re-encryption server model, the encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes can resist the leakage of the re-encryption key. When the attributes are cancelled, an attribute user group is employed to construct the re-encryption key tree so as to effectively, timely and accurately cancel the indirect attributes. When the encryption is performed, the secret is dispersed to resist the conspiracy attack.
Owner:XIDIAN UNIV
Document signing method capable of being outsourced based on block chain technology
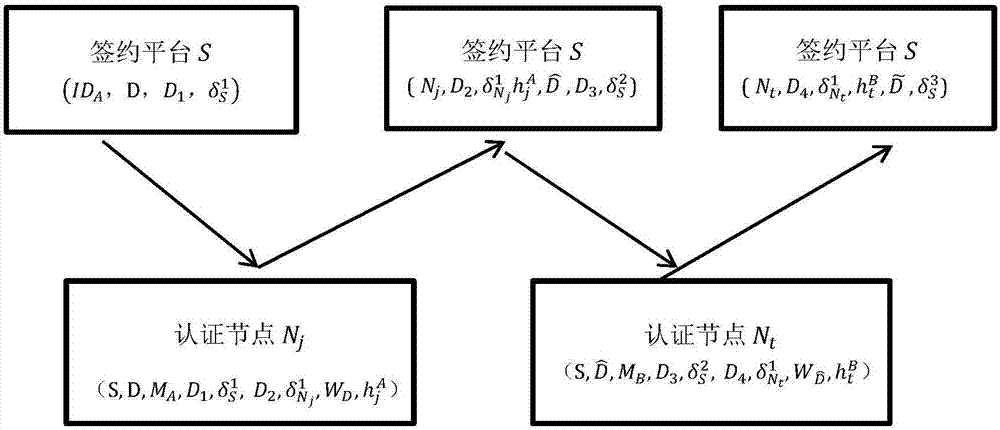
ActiveCN106936566ANo need to saveResistant to Collusion AttacksKey distribution for secure communicationData processing applicationsManagement systemAuthentication
The invention discloses a document signing method capable of being outsourced based on a block chain technology. Signing platforms and block chain authentication nodes are employed. The method comprises a system initialization step, a key management system initialization step, a user registration step and a user signing initiation step. The method is provided based on the block chain technology, outsourcing calculation and a document signing technology. Compared with a traditional document signing method, the method has the advantages that a user does not need to store documents and signatures, document signing processes are recorded in detail and cannot be tampered, the user can outsource the signing operation to the signing platforms, and through existence of multiple block chain authentication nodes, a conspired attack between the signing platforms and the authentication nodes can be resisted.
Owner:江苏省南京市南京公证处 +1
Revocable data sharing method based on fog calculation
ActiveCN108833393ARich domainSatisfy Computational OverheadKey distribution for secure communicationPublic key for secure communicationRevocationRights management
The invention belongs to the field of information retrieval and the technical field of its database structure, and discloses a revocable data sharing method based on fog calculation. When a user revocation occurs, it is not necessary to update the keys of other unrevoked users and re-encrypt the ciphertext, only the conversion key of the revoked user needs to be deleted; after the conversion key is deleted, the cloud server cannot perform partial decryption operations for the revoked user, thereby realizing the user's revocation. When an attribute revocation occurs, the keys of all affected users in the system needs to be updated and the ciphertext is re-encrypted to ensure that other users may still decrypt the ciphertext as usual. The invention realizes the data access control in the data network system, has the advantages such as high system access efficiency, low computational cost, and support for dynamic user rights management, and may be used for protecting the privacy data of the user in the data network, reducing the calculation cost of the user, and dynamically managing the authority of the user in the system.
Owner:XIDIAN UNIV
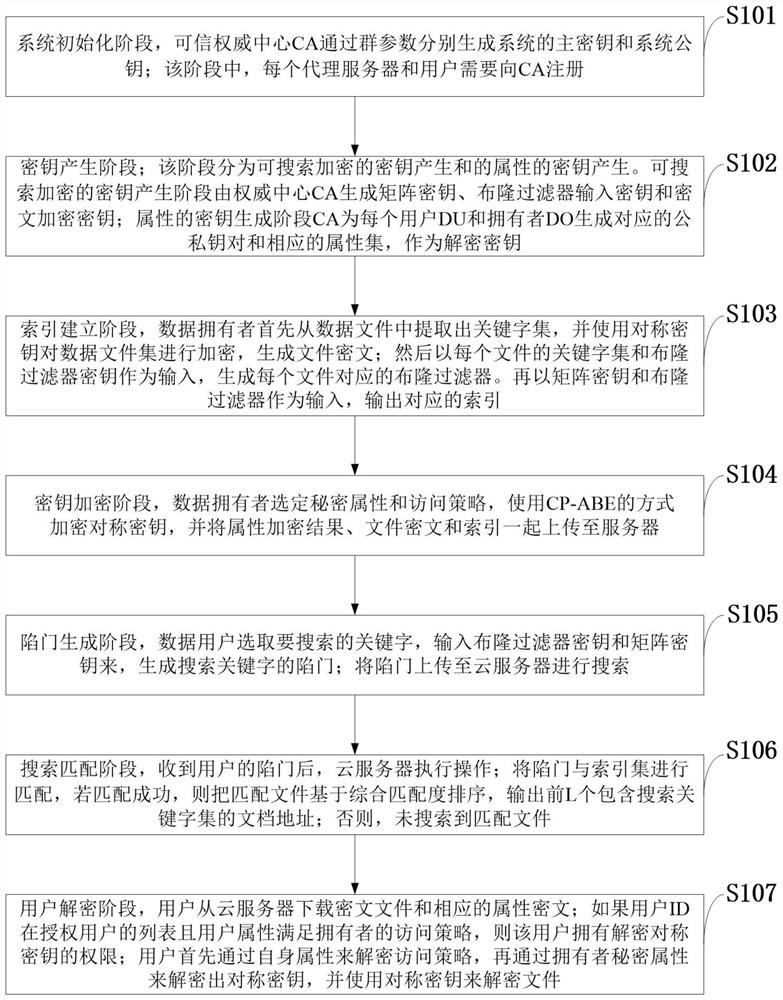
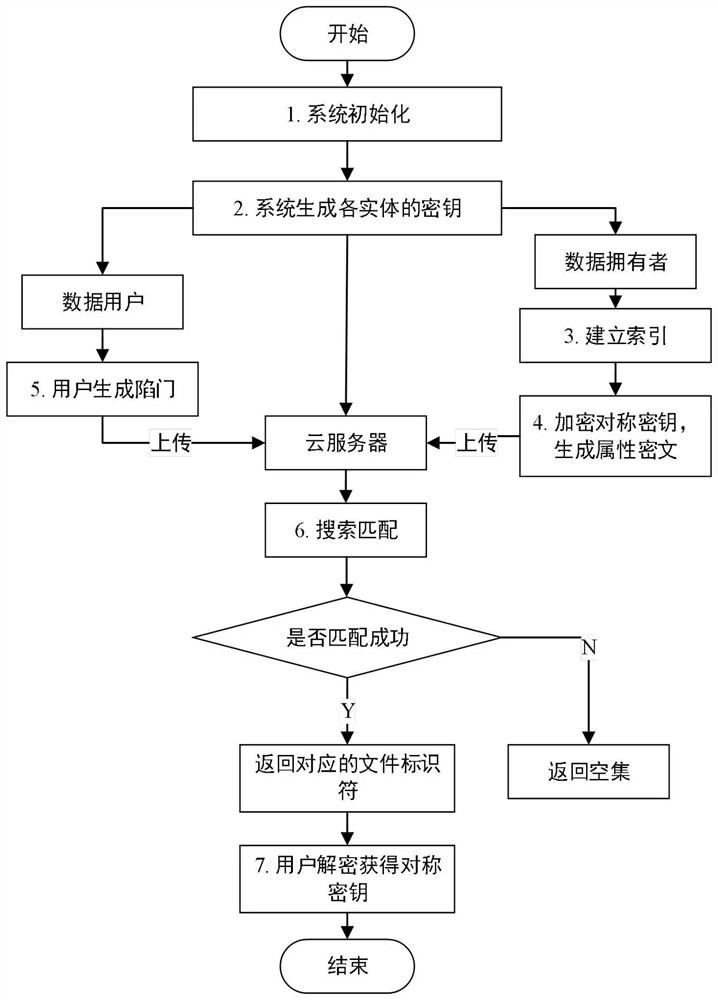
Efficient ciphertext retrieval method based on CP-ABE automatic correction and cloud computing service system
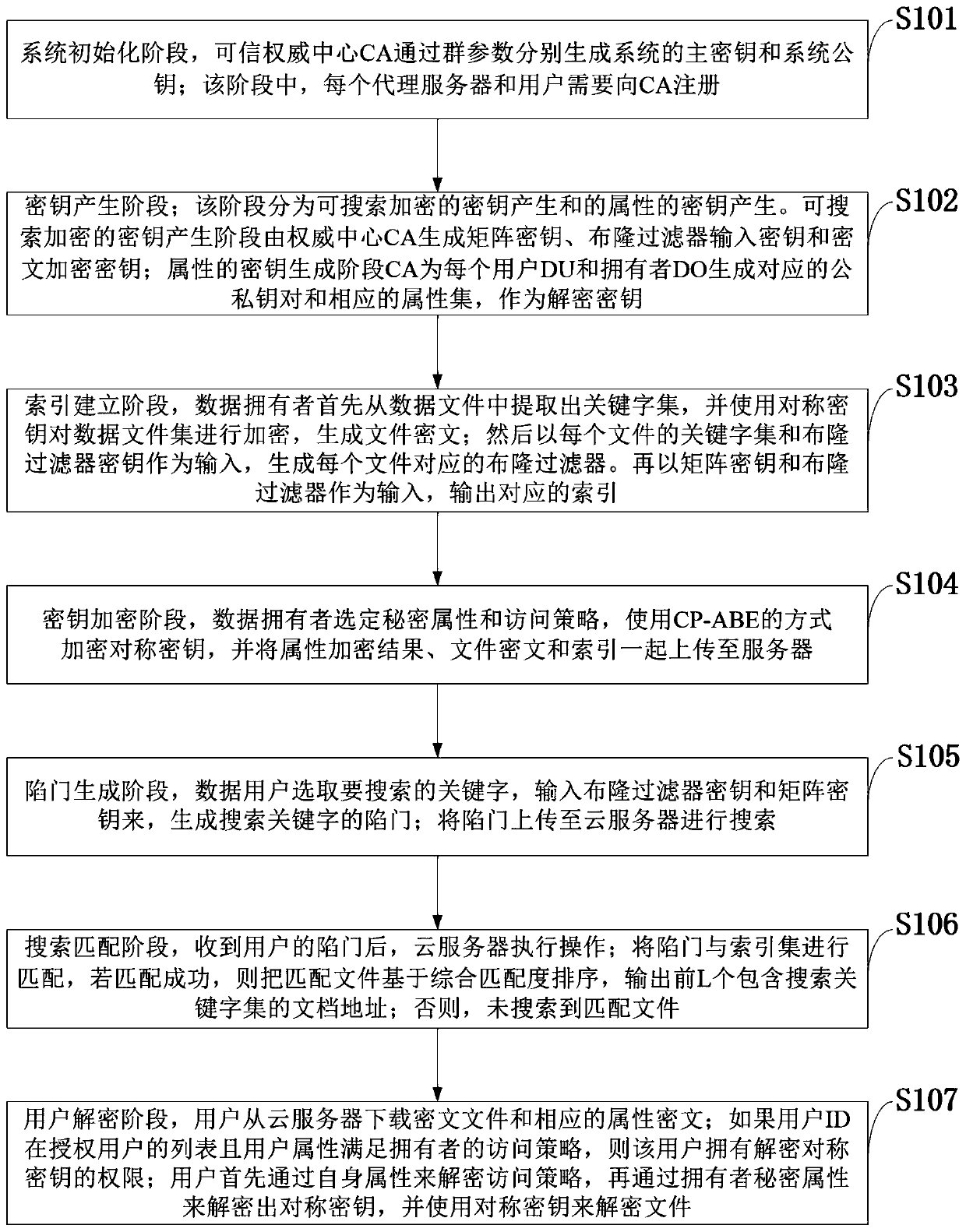
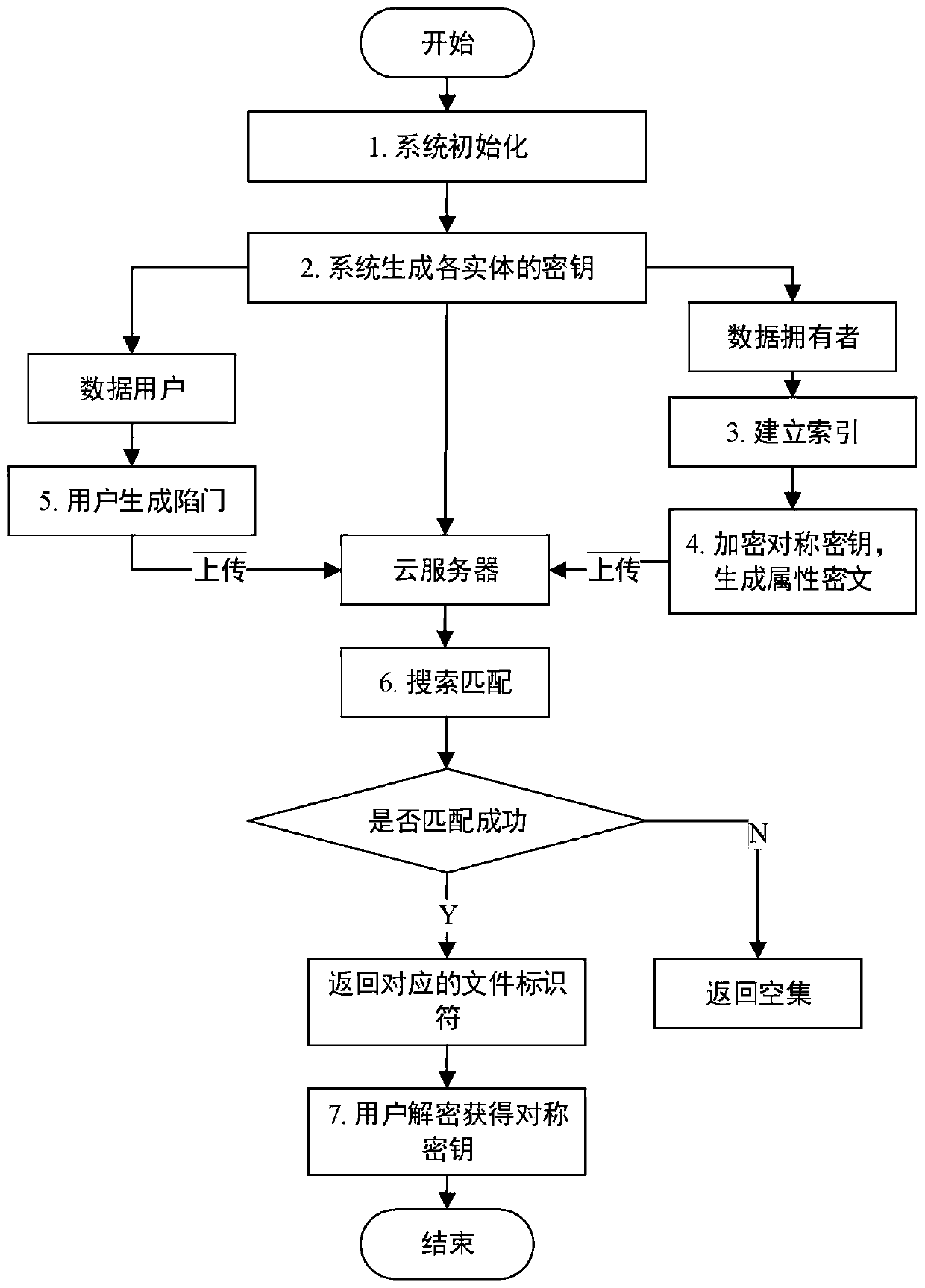
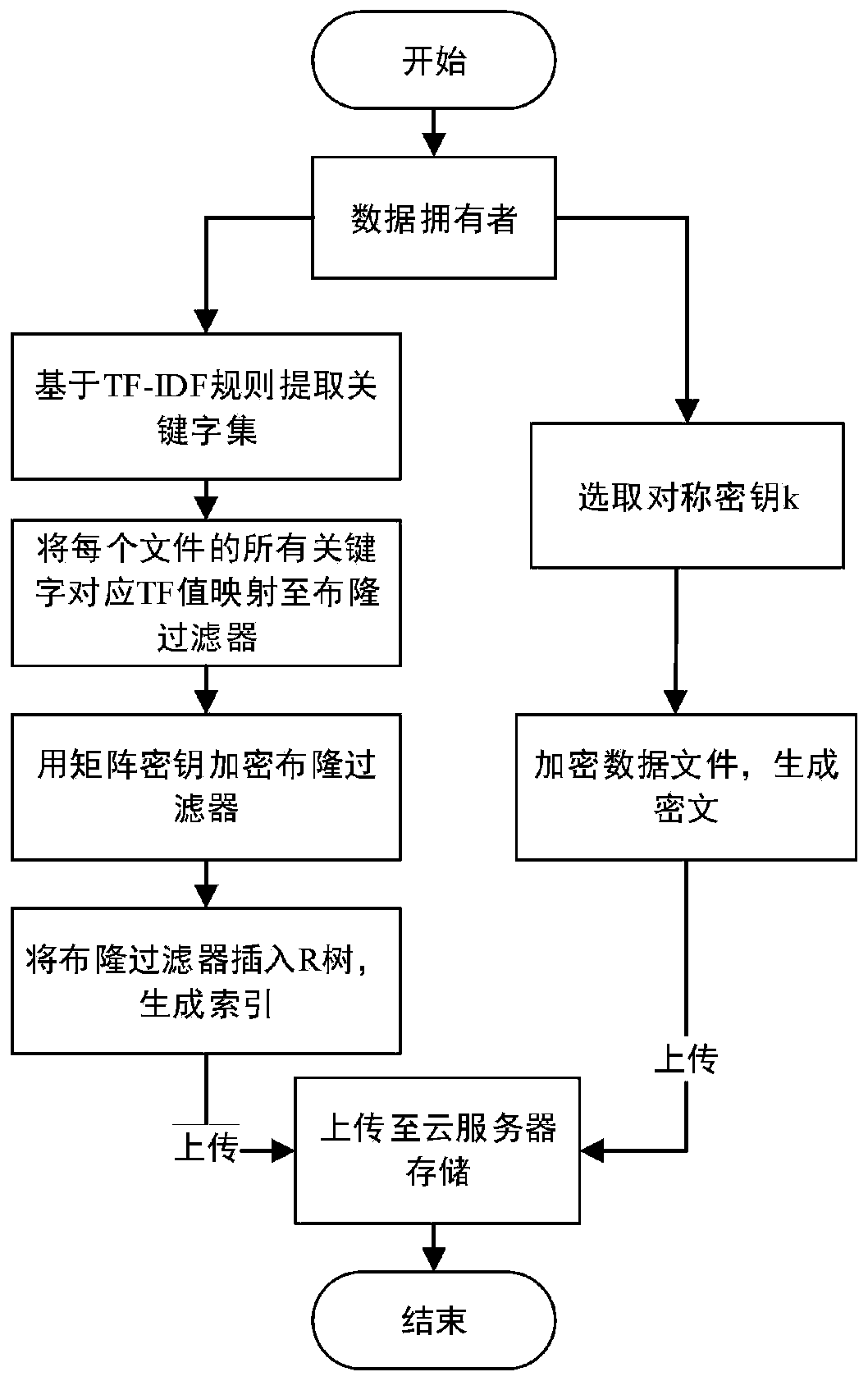
ActiveCN110138561AAvoid Frequency Guessing AttacksReduce complexityKey distribution for secure communicationPublic key for secure communicationGeneration processAccess structure
The invention belongs to the technical field of cloud computing private protection, and discloses an efficient ciphertext retrieval method based on CP-ABE automatic correction and a cloud computing service system. The method comprises the steps of storing an encrypted Bloom filter and a corresponding ciphertext file ID set in a leaf node of the R tree by combining the R tree and the Bloom filter as index structures; using the cloud server to perform the matrix positioning on the R tree according to the search trap door, and then match the encrypted Bloom filters in the leaf nodes; sorting thefiles according to the inner product result of the Bloom filter; introducing a random number in the trap door generation process, wherein different trap doors can be generated even if according to thesame keyword; performing the co-encryption by using the access structure and the owner secret attribute. According to the method, a symmetric key with a small CP-ABE encryption volume is used, so that the fine-grained access control is realized; a multi-agent server is introduced to realize the decentralization, and the collusion between the proxy servers is prevented.
Owner:XIDIAN UNIV
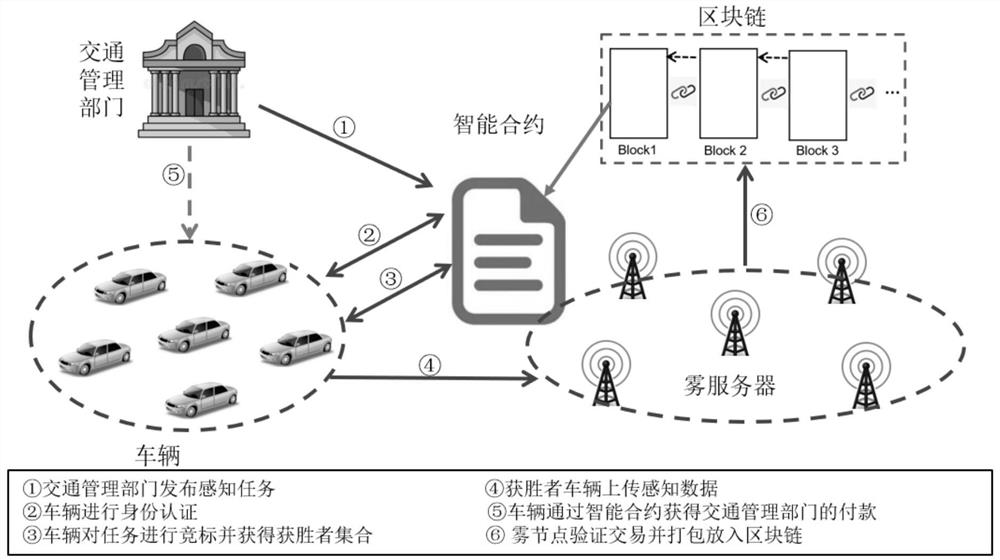
Internet of vehicles crowd sensing incentive method with privacy protection characteristic based on blockchain
ActiveCN113079486AResistant to Collusion AttacksImprove data qualityDiscounts/incentivesParticular environment based servicesThird partyPayment
The invention belongs to the technical field of Internet of Vehicles crowd sensing. The invention provides an Internet of Vehicles crowd sensing incentive method with a privacy protection characteristic based on blockchain, and aims to solve the problems that the privacy protection means of an existing Internet of Vehicles crowd sensing incentive method mostly depend on a third party, the hidden danger of privacy disclosure exists, and the problem of award distribution fairness is solved. According to the method, through an anonymous identity authentication mechanism, a winner selection mechanism for protecting privacy, a fairness-enhanced reward payment scheme and an intelligent contract, the problems of single-point faults, collusion attacks and the like existing in a centralized excitation method are solved; a lightweight privacy protection scheme without the assistance of a trusted third party is realized, and the vehicle identity and bidding privacy are protected; and the fairness of the bidder selection and reward allocation algorithm is enhanced.
Owner:QINGDAO UNIV OF SCI & TECH
Multi-mechanism attribute-based encryption method supporting strategy dynamic updating
InactiveCN106686010AReduce workloadReduce communicationTransmissionCiphertextAttribute-based encryption
The invention discloses a multi-mechanism attribute-based encryption method supporting strategy dynamic updating. The method comprises the seven steps of system initialization, attribute mechanism initialization, secret key generation, data encryption, decryption, dynamic updating secrete key generation and dynamic ciphertext updating. An anonymous secret key distributing protocol is introduced to generate a private key for a user, privacy of the user is effectively protected, and collusion attack of an attribute mechanism is resisted. In addition, a dynamic strategy updating algorithm is adopted, strategy updating of any type is supported, and calculation and communication overhead in traditional strategy updating is greatly reduced. The method is low in communication overhead, supports privacy protection and strategy updating and can be applied to a cloud storage environment.
Owner:HENAN POLYTECHNIC UNIV
Byzantine fault-tolerant consensus method based on distributed key
ActiveCN111371744AResistant to Collusion AttacksImprove consensus efficiencyKey distribution for secure communicationUser identity/authority verificationByzantine fault toleranceEngineering
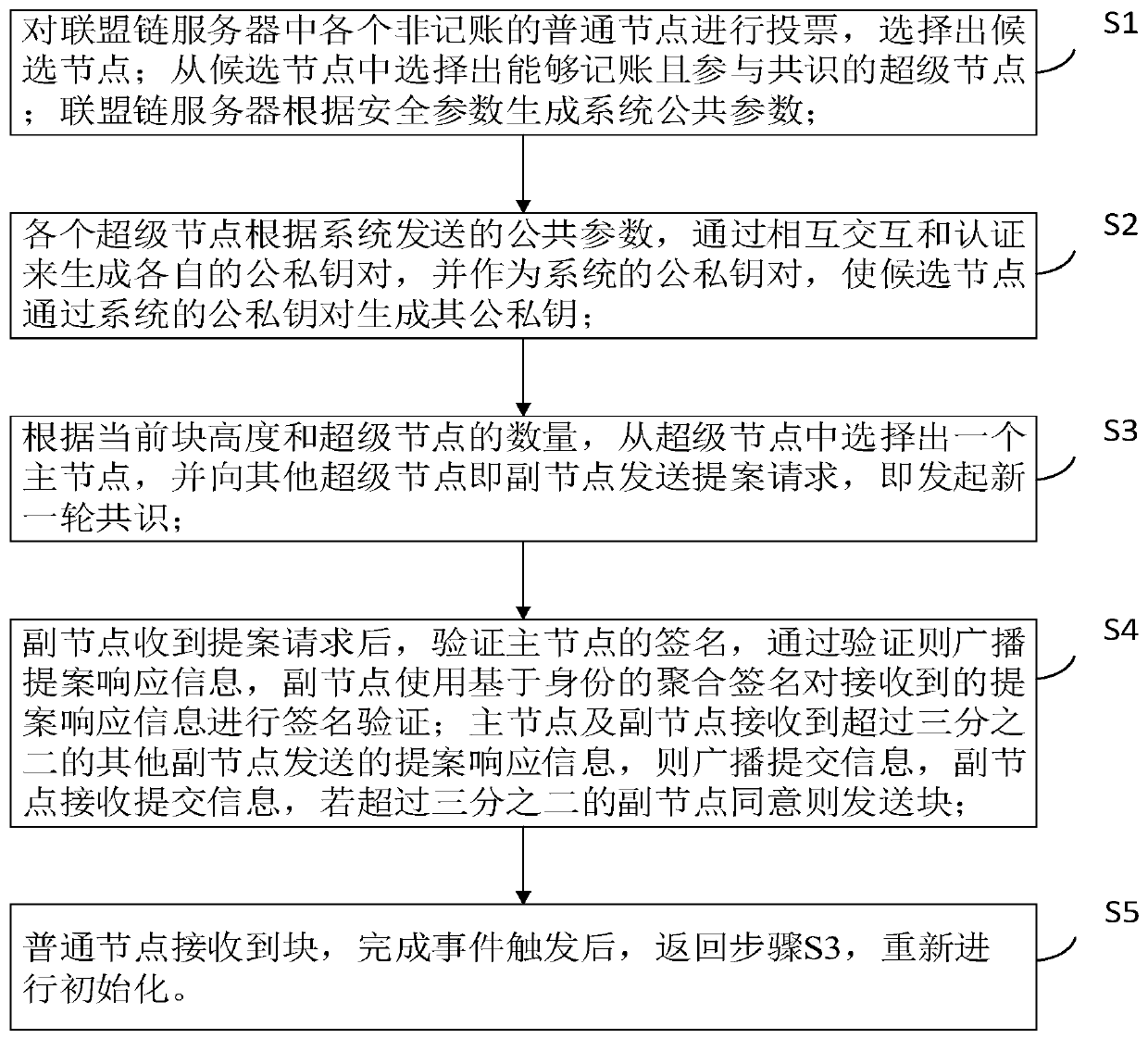
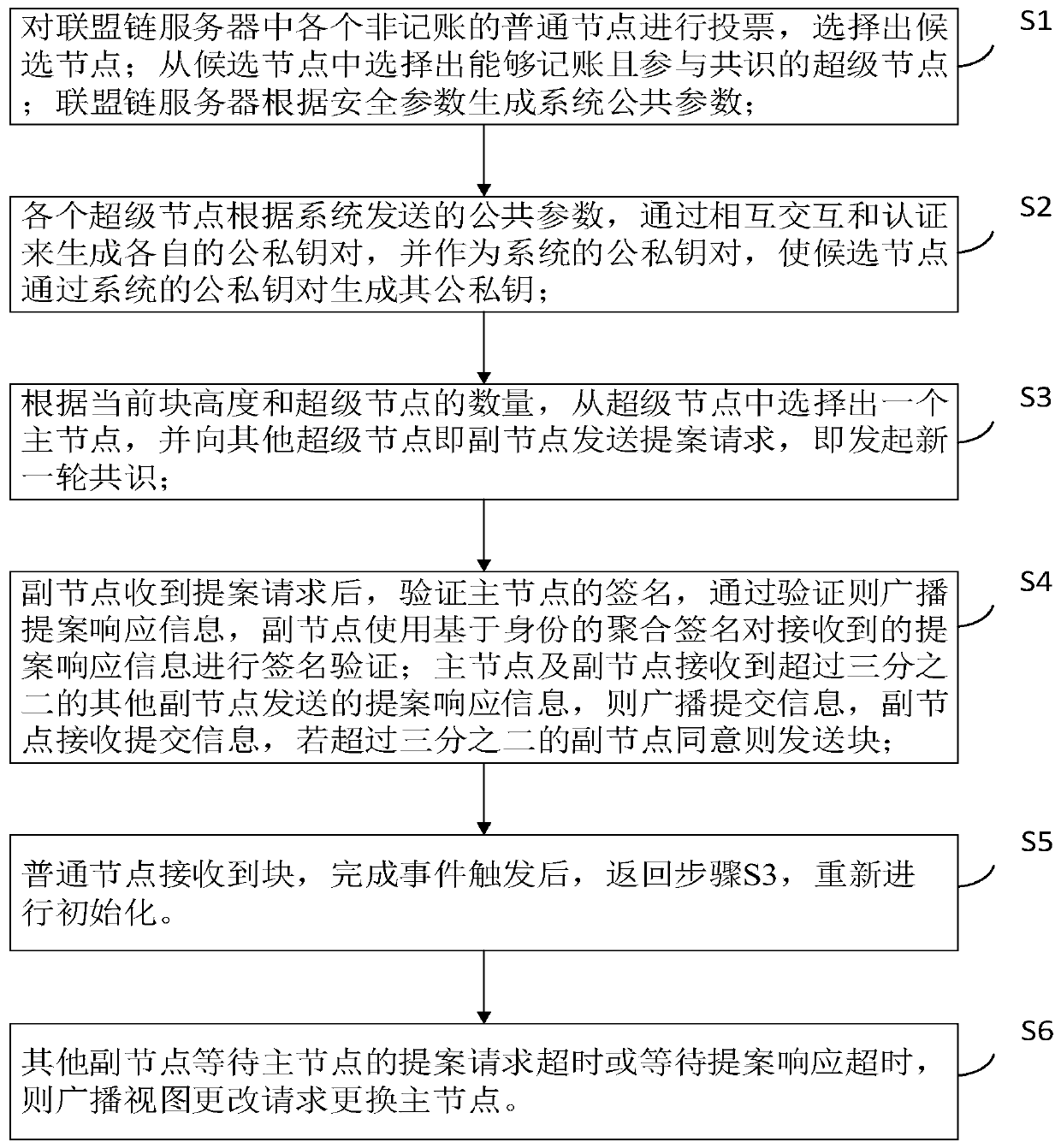
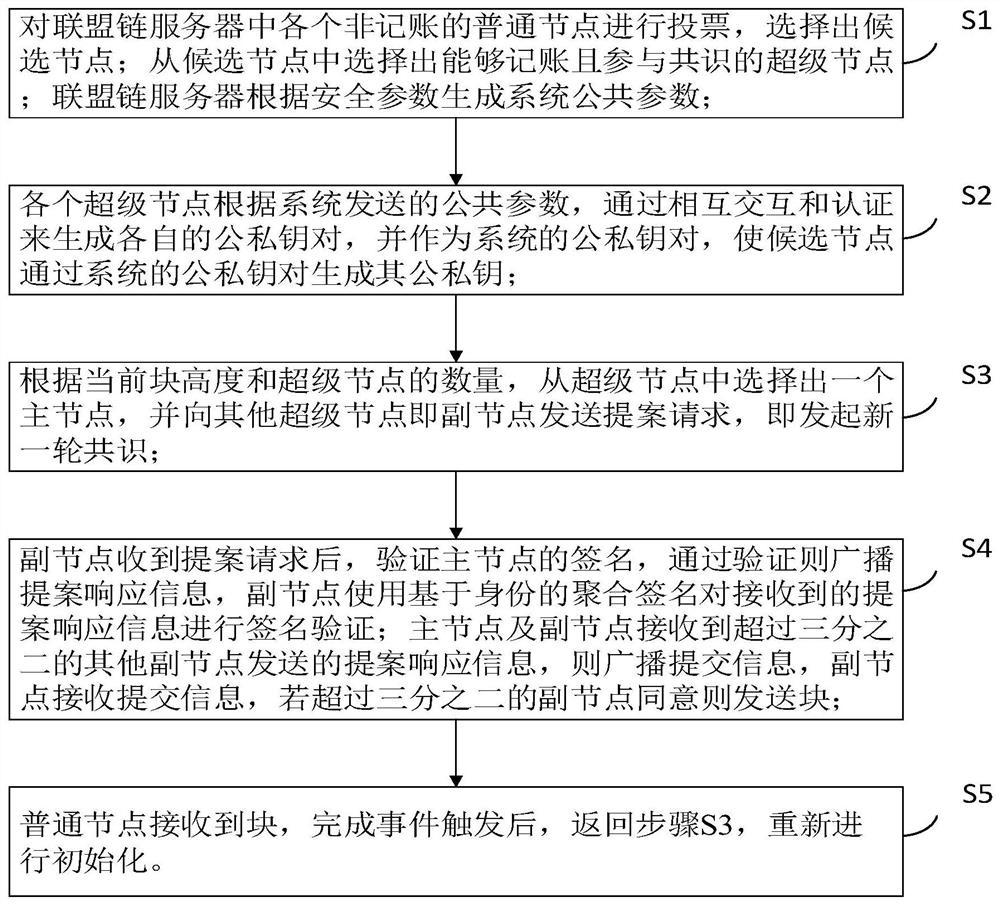
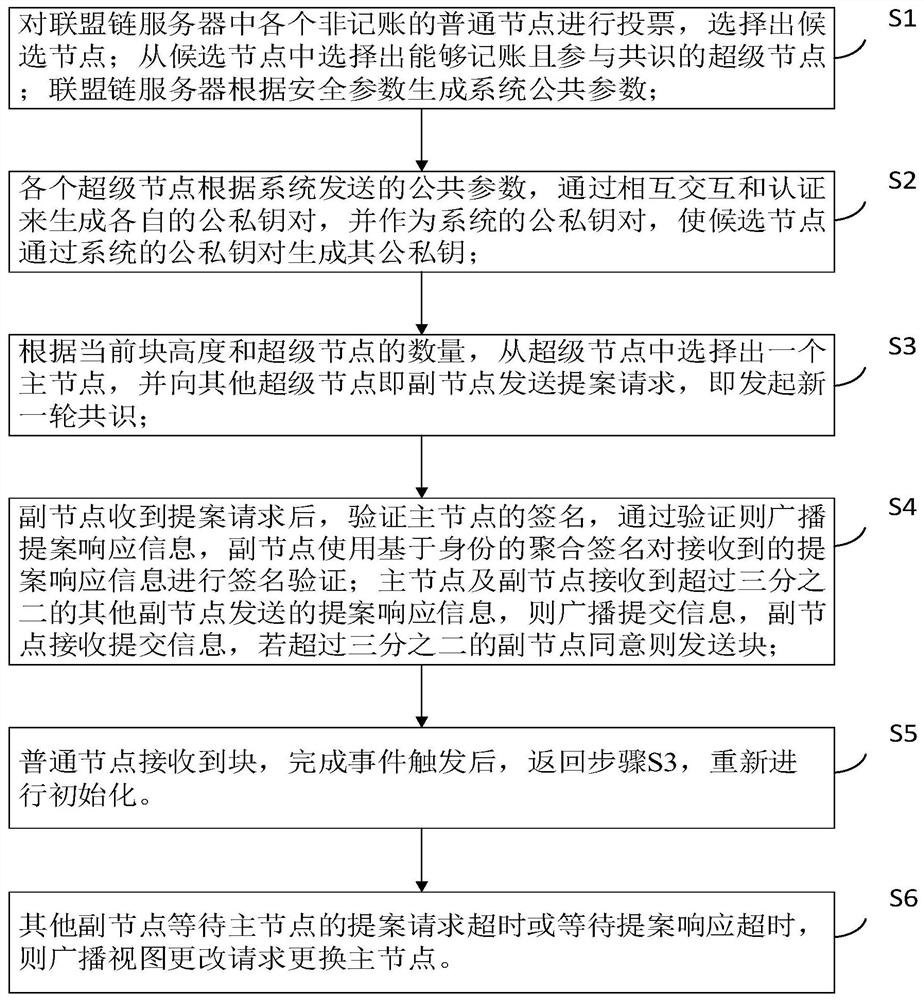
The invention belongs to the field of security authentication in the network space security discipline, and relates to a Byzantine fault-tolerant consensus method based on a distributed key. The method comprises the steps that super nodes participating in consensus are selected, and system common parameters are generated; generating a system public and private key pair and public and private keysof the candidate nodes in a mutual interaction authentication mode according to the public parameters sent by the system; selecting a main node from the super nodes to initiate a proposal request, andstarting a new round of consensus; the secondary node performs individual verification and aggregation verification on the proposal request, and finally determines whether to agree to send the block;after receiving the block, the common node completes time triggering to continue the consensus of the next round, and in the process, if the auxiliary node waits for the case proposal request timeoutor the case proposal response timeout of the main node, the auxiliary node broadcasts the view change request and replaces the main node; according to the invention, the efficiency of reaching the consensus process can be greatly improved.
Owner:芽米科技(广州)有限公司
Agent re-encryption method used for group traffic
InactiveCN103888249AImprove securityResistant to Collusion AttacksSpecial service provision for substationKey distribution for secure communicationPlaintextHash function
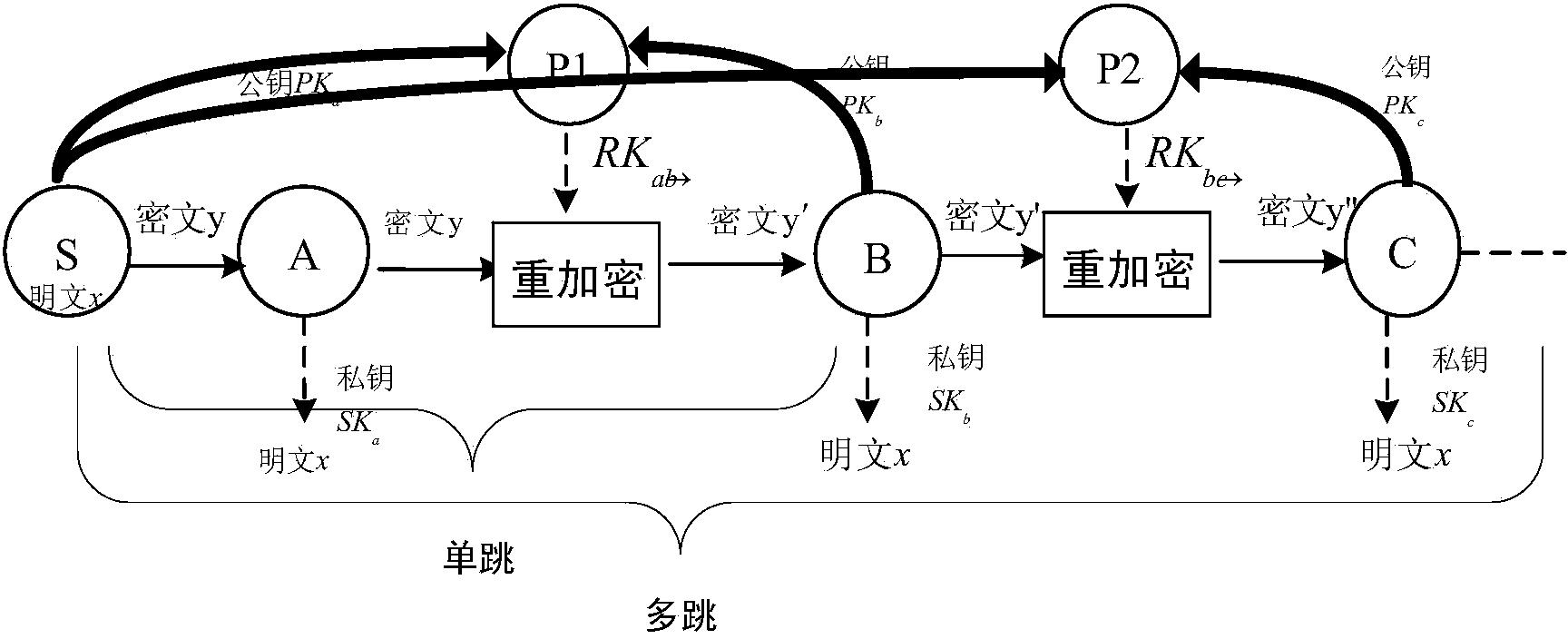
The invention provides an agent re-encryption method used for group traffic. The method comprises the following steps: step one: a sender sets safety parameters and broadcasts the safety parameters to all users; step two: a private key is independently selected, and a public key is generated according to the private key and the public key is disclosed; step three: a Hash function operation and a bilinear pairing operation are performed on a clear text to be encrypted according to the safety parameters and the public key of a principal so that a first-level cipher text is generated; step four: a re-encryption secrete key is generated by the sender according to the safety parameters and the public key of an agent and the re-encryption secrete key is sent to the third part agent; step five: the first-level cipher text is re-encrypted by the third part agent according to the re-encryption secrete key so that a second-level cipher text is generated and sent to the agent; and step six: the principal and the agent are respectively decrypted according to the private key so that the clear text is acquired. According to the method, chosen cipher text attack safety can be achieved, the secret key can be completely disclosed via agent re-encryption and the agent re-encryption secret key is generated by the sender so that collusive attack can be resisted and safety of the clear text can be enhanced.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
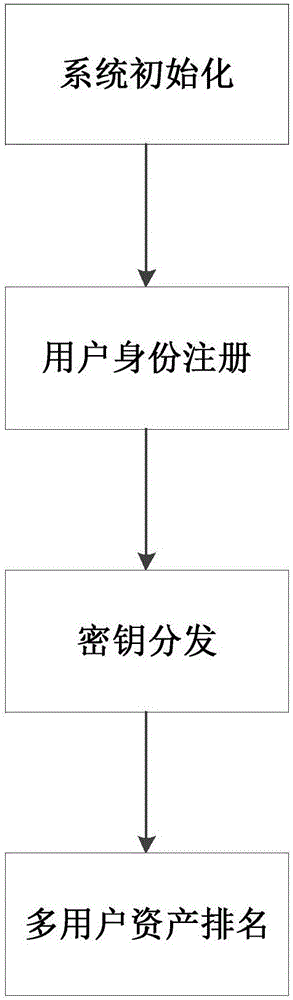
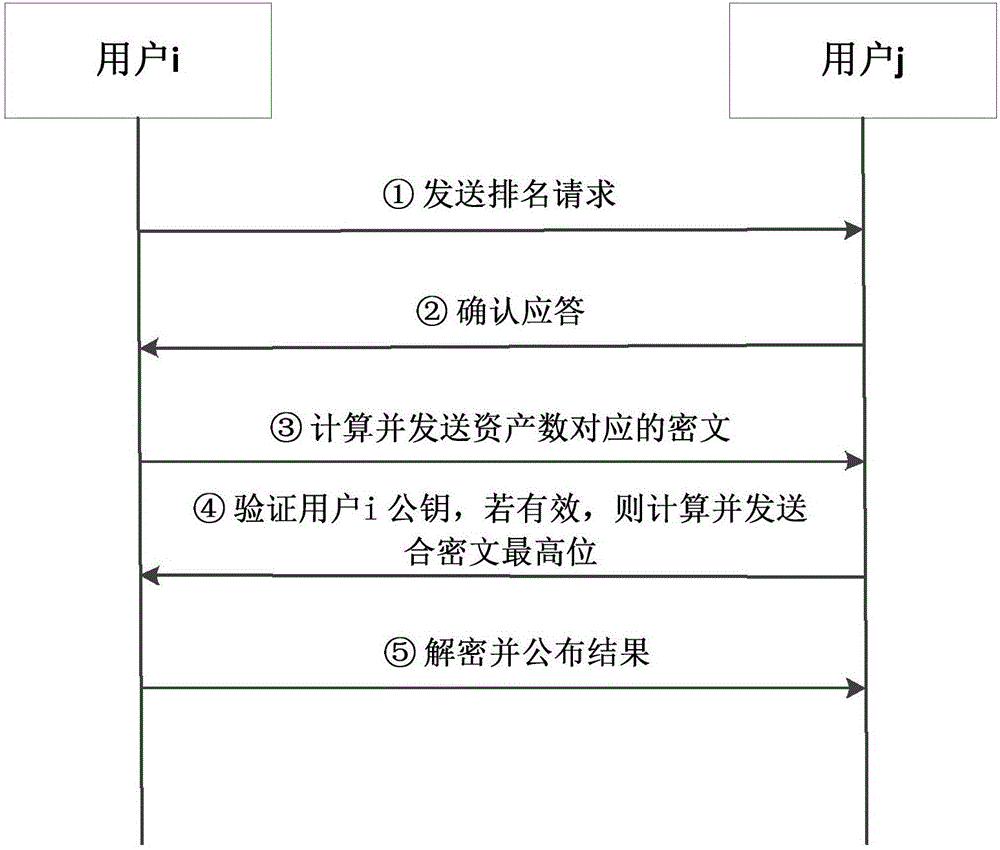
Homomorphic encryption-based virtual asset anonymous ranking method
ActiveCN106506165AAvoid disadvantagesSecurity and privacy protectionUser identity/authority verificationCommunication with homomorphic encryptionNarrow rangeCiphertext
The invention discloses a homomorphic encryption-based virtual asset anonymous ranking method. The main objective of the invention is to solve the problems of user privacy disclosure and the narrow range of single-client ciphertext ranking which are caused by a condition that a private key is directly handed over to a proxy server in the prior art. The implementation process of the method includes the following steps that: 1) a system is initialized, and the signature public and private key and some public parameters of an authorization center (CA) are determined; 2) a user carries out identity registration application in the authorization center (CA); 3) the authorization center (CA) issue a key to the registered user; 4) the user uses his or her own key to participate in asset ranking and directly encrypts his or her asset data through a learning with error (LWE)-based homomorphic encryption algorithm, and ciphertexts are processed, the ranking of virtual assets is realized. With the method of the invention adopted, the protection of the privacy of the user can be realized, and the universality and anti-conspiracy attack ability of ciphertext ranking can be improved. The method can be used for asset supervision in a bitcoin network.
Owner:XIDIAN UNIV
Distributed attribute-based encryption method supporting fine-grit attribute revocation on lattice
ActiveCN108880801ASolve the leakage problemImprove securityKey distribution for secure communicationImage extractionInformation security
The invention discloses a distributed attribute-based encryption method supporting fine-grit attribute revocation on lattice, and belongs to the field of the information security. The method comprisesthe following steps: at the system initialization stage: the linear secret sharing is performed on a target vector at a system initialization stage, a sub-secret sharing value is served as a privatekey of a corresponding attribute authorization mechanism, and the attribute authorization mechanism establishes the corresponding binary revocation tree for the managed system attribute; at the user attribute key and the update key generation stage: the attribute authorization mechanism obtains the secondary sub-secret sharing value of the user attribute by using secondary linear secret sharing, and the computes the user attribute key and the user attribute update key through a primary image extraction algorithm and a left-sampling algorithm; at the encryption stage: an encryption party computes the ciphertext of the message by using the Gaussian noise, the encrypted and preprocessed noise vector and the system public parameter; at the decryption: a decryption party decrypts the ciphertextby using the user attribute key and the user attribute update key. The method disclosed by the invention is high in security, flexible in access policy and supports the fine-grit attribute permissionrevocation.
Owner:芽米科技(广州)有限公司
Safe data sharing method in cloud environment
InactiveCN106612169AResistant to Collusion AttacksImprove securityKey distribution for secure communicationMultiple keys/algorithms usageAttribute-based encryptionRevocation
The invention provides a safe data sharing method in a cloud environment. The safe data sharing method is provided in allusion to a problem of encrypted data access control in the cloud storage environment by combining CP-ABE (ciphertext-policy attribute-based encryption). According to the method, a problem of trusted third party dependency in a CP-ABE algorithm is solved through combining a symmetric key of a cloud storage center and a asymmetric private key of an authorized agency; secondly, user unique identification is added to an attribute private key of a user so as to enable a sharing mechanism to resist collusion attacks from illegal users; and finally, revocation of the user is completed through updating the symmetric key, the backward security of shared data is ensured, and the updating efficiency is improved.
Owner:SICHUAN YONGLIAN INFORMATION TECH CO LTD
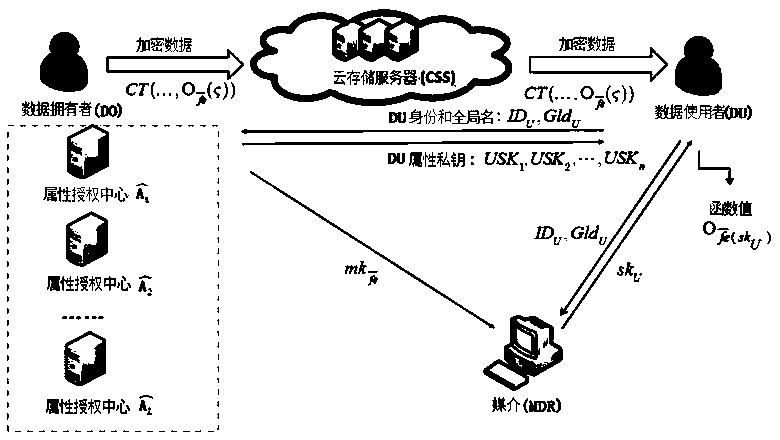
Distributed multi-authorization-party ciphertext policy attribute-based encryption method for medium confusion
ActiveCN110086615ASolving Collusion AttacksEfficient access controlKey distribution for secure communicationObfuscationAuthorization
The invention relates to a distributed multi-authorization-party ciphertext policy attribute-based encryption method for medium confusion, which is characterized in that when a new attribute authorization center is added into a system, the new attribute authorization center is secretly distributed with a pseudorandom function PRF (.). In order to prevent collusion of users who possess all relevantattributes in a certain relevant attribute management domain, a trusted medium (MDR) is employed in this system. A data owner generates a ciphertext CT including a obfuscation function. Because the secure DO is used, online interaction does not need to be maintained. Similarly, the DO transmits a key to the MDR, where the key is a function variable for receiving a key skU obtained by the user U from the MDR. The skU is calculated from a PRF (.), a GidU of U, or the like. U has the ability to calculate a function, but does not reveal the internal program secret. Wherein I represents a set of AAs serial numbers of an attribute authorization center for managing U attributes, if the identity IDU of U is confirmed, a corresponding private key USKj is issued to the user U, and the MDR sends a private key skU to the user U. And finally, the U decrypts the ciphertext CT by using USKj (j belongs to I).
Owner:FUJIAN NORMAL UNIV
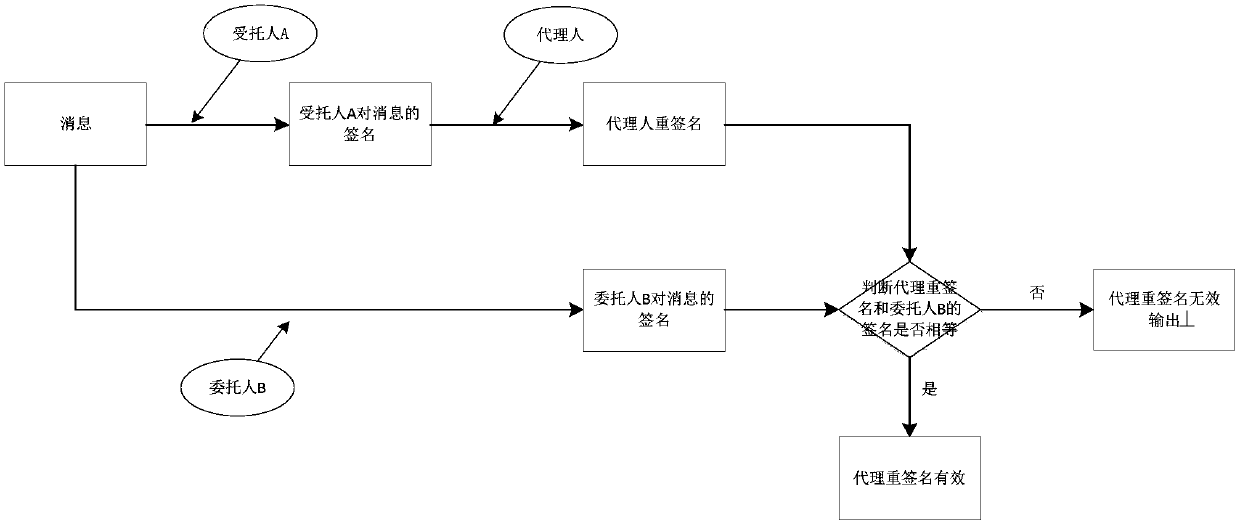
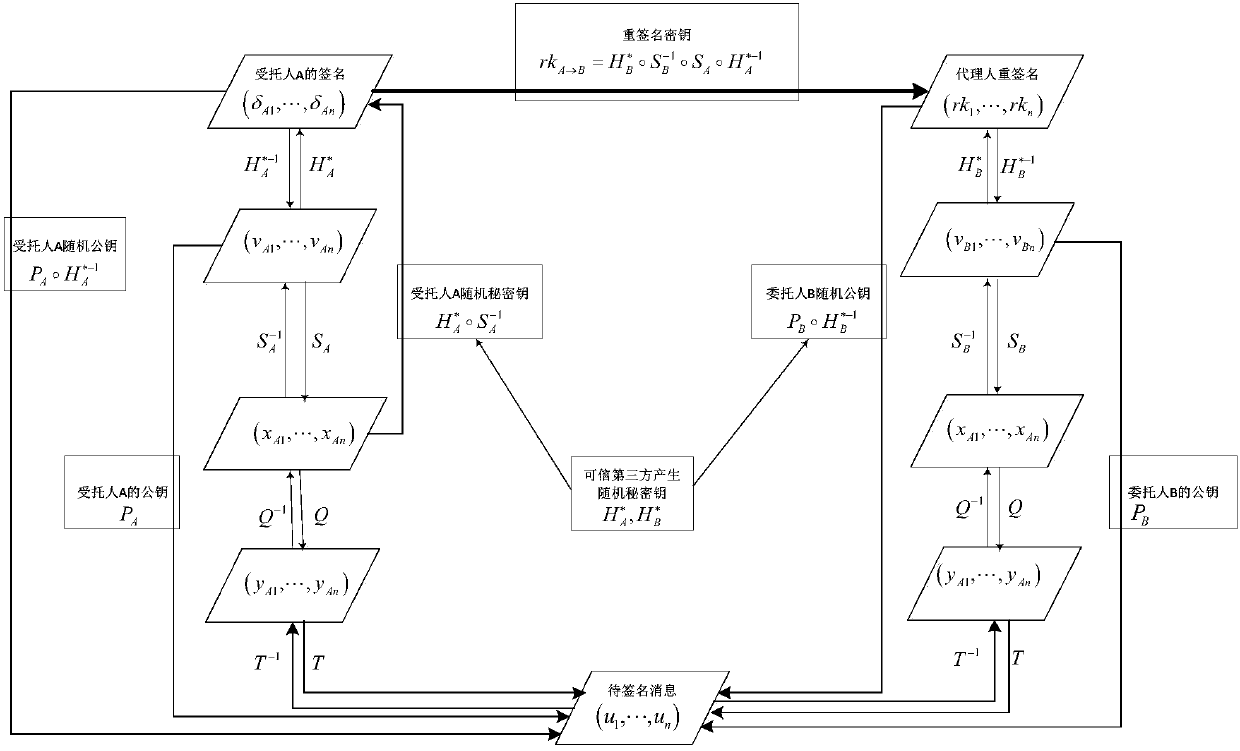
Multivariable-based proxy re-signature method capable of resisting conspiracy attacks
InactiveCN106209377AResistant to Collusion AttacksResistant to Quantum AttacksKey distribution for secure communicationUser identity/authority verificationThird partyConfidentiality
A multivariable-based proxy re-signature method capable of resisting conspiracy attacks comprises the steps of system generation, key generation, re-signature key generation, trustee A signature generation, agent re-signature generation, and re-signature correctness verification. As two random keys (H<*>A and H<*>B) used by a trustee A and a trustee B in proxy re-signature are generated by adopting a trusted third party, and are used for generating new re-signature keys respectively, an agent converts a signature of the trustee A to a certain message into a signature of the trustee B to the same message by using the corresponding new re-signature key, and the confidentiality of the random keys is high, whether the trustee B and the agent or the trustee A and the agent cannot conspire to acquire the private key of the other trustee, that is, the conspiracy attacks can be resisted effectively. The multivariable-based proxy re-signature method is high in efficiency, safe, reliable, and capable of resisting the conspiracy attacks of the trustee A and the agent or the agent and the trustee B, and can be used in proxy re-signature.
Owner:SHAANXI NORMAL UNIV
Cloud storage access control method
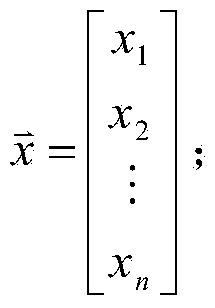
InactiveCN103428299AGuaranteed confidentialityEasy to decryptTransmissionComputation complexityData set
The invention discloses a cloud storage access control method based on a cloud storage access control system which is composed of a cloud storage service provider CSP, a data owner A and a plurality of users. The cloud storage access control method is characterized in that linear transformation is used for realizing encryption of a dataset, a dot product operation is used for realizing decryption of certain private data in the dataset, and therefore a cloud storage access control policy is realized. The cloud storage access control method can effectively solve the problems that in an existing ciphertext access control method based on cloud storage, a decryption process is complex for the users and the ciphertext access control method is difficult to realize, thereby lowering the computation complexity of encryption and particularly decryption, and improving the efficiency of encryption and decryption.
Owner:ANHUI UNIVERSITY
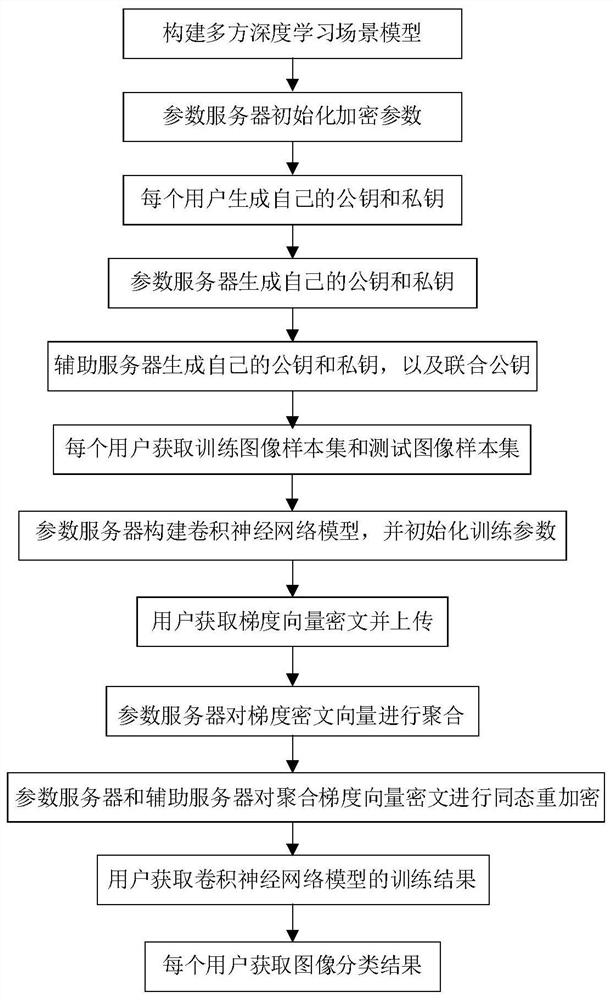
Convolutional neural network image classification method based on homomorphic encryption
ActiveCN112949741AReduce the chance of leaksResistant to Collusion AttacksCharacter and pattern recognitionNeural architecturesAlgorithmCiphertext
The invention provides a convolutional neural network image classification method based on homomorphic encryption, which is used for solving the technical problems that privacy information is easy to leak and collusion attacks cannot be resisted in the prior art, and comprises the following steps: constructing a multi-party deep learning scene model; initializing encryption parameters by the parameter server; enabling each user to generate a public key and a private key of the user; enabling the parameter server to generate a public key and a private key of the parameter server; enabling the auxiliary server to generate a public key and a private key of the auxiliary server and a joint public key; enabling each user to obtain a training image sample set and a test image sample set; enabling the parameter server to construct a convolutional neural network model and initialize training parameters; enabling the user P to obtain and upload a gradient vector ciphertext; enabling the parameter server to aggregate the gradient ciphertext vectors; enabling the parameter server and the auxiliary server to perform homomorphic re-encryption on the aggregation gradient vector ciphertext; enabling the user P to obtain a training result of the convolutional neural network model; and enabling each user to obtain an image classification result.
Owner:XIDIAN UNIV
Data clustering method for enhancing data privacy in Internet of Things medical system
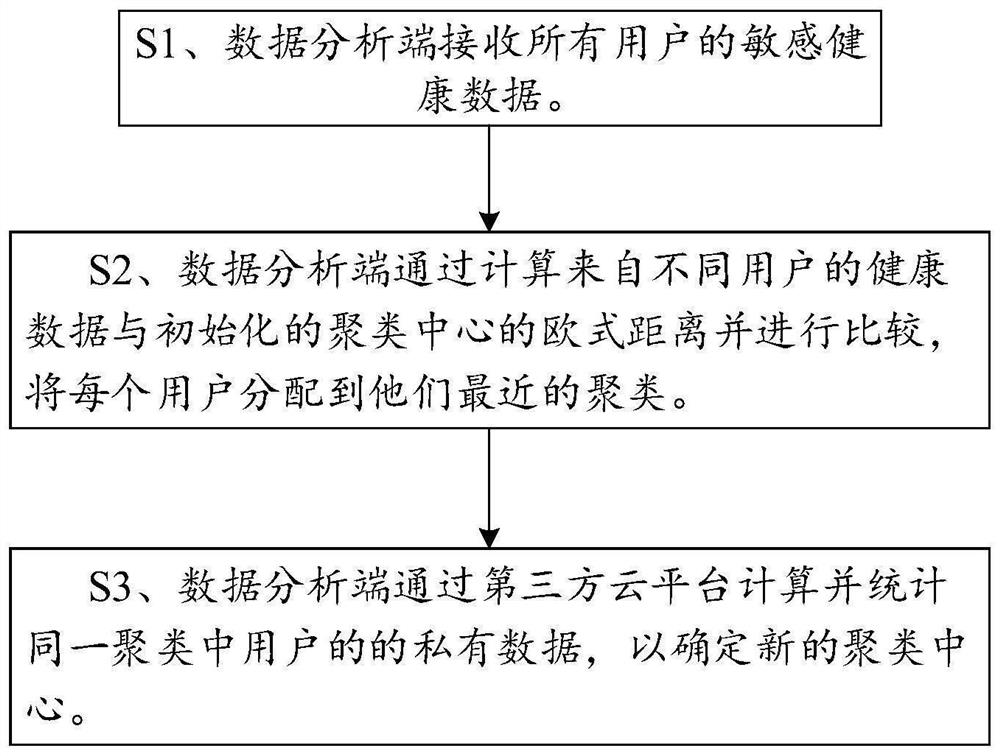
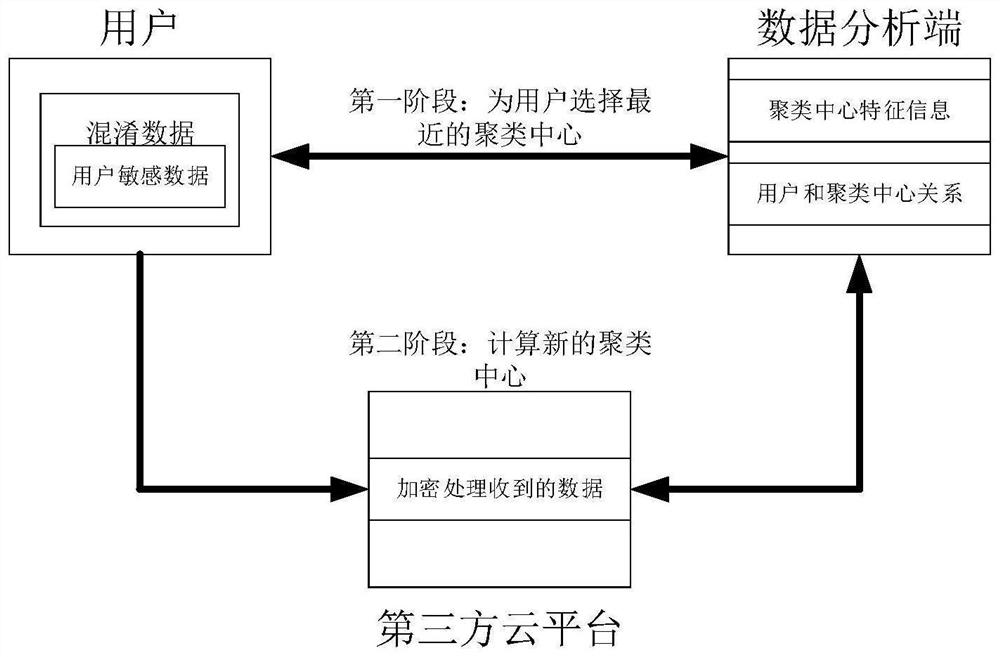
ActiveCN111951918AReduce time complexityResistant to Collusion AttacksMedical data miningCharacter and pattern recognitionClustered dataThird party
The invention discloses a data clustering method for enhancing data privacy in an Internet of Things medical system. The method comprises the following steps: S1: a user initializes and processes ownhealth data, and a data analysis end receives processed data submitted by all users; S2, the data analysis end calculates and compares the Euclidean distance between the health data from different users and the initialized clustering center, and allocates each user to the nearest cluster; and S3, the data analysis end calculates and counts private data of the users in the same cluster through thethird-party cloud platform so as to determine a new clustering center. In the Internet of Things medical system, a third-party cloud platform is comprehensively introduced, homomorphic encryption is carried out, and clustering for protecting user data privacy is realized.
Owner:FUJIAN NORMAL UNIV
A cross-trust domain authentication method for distributed network system
InactiveCN103973451BAvoid creatingReduce maintenance costsUser identity/authority verificationCryptosystemThe Internet
The invention discloses a cross-trust domain authentication method for a distributed network system. The method adopts a distributed key generation based on an elliptic curve cryptosystem and a threshold signature mechanism to construct a virtual bridge authentication center VBCA, and uses the virtual bridge authentication center to VBCA completes the cross-domain interactive authentication between different trust domain entities in the distributed network system. The inventive method is universal to various organizational structures, agile and dynamic, low cost, short authentication path, high bit security, high efficiency and easy hardware It is beneficial to solve the problem of cross-domain interactive authentication between entities in different trust domains in a dynamic distributed network system with limited terminal resources or communication bandwidth. In cloud computing and cloud storage networks, Internet of Things, wireless sensor networks, It has broad application prospects in agile manufacturing systems and virtual organizations.
Owner:SOUTHWEST JIAOTONG UNIV
A Distributed Attribute-Based Encryption Method Supporting Fine-grained Attribute Revocation on Lattice
ActiveCN108880801BSolve the leakage problemImprove securityKey distribution for secure communicationSecret shareTheoretical computer science
Owner:芽米科技(广州)有限公司
Method and system for information processing of medical health monitoring network model based on signature aggregation
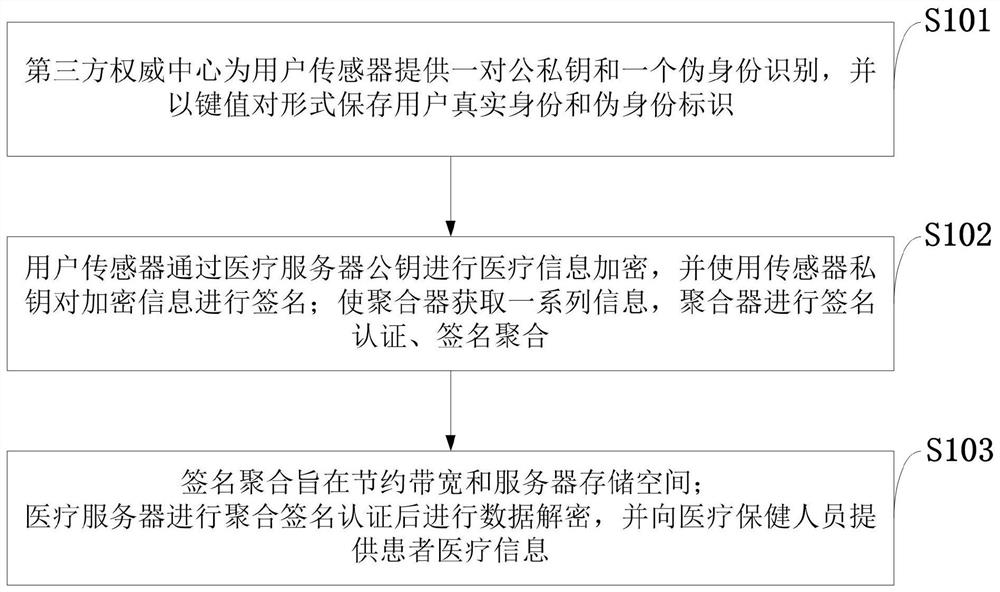
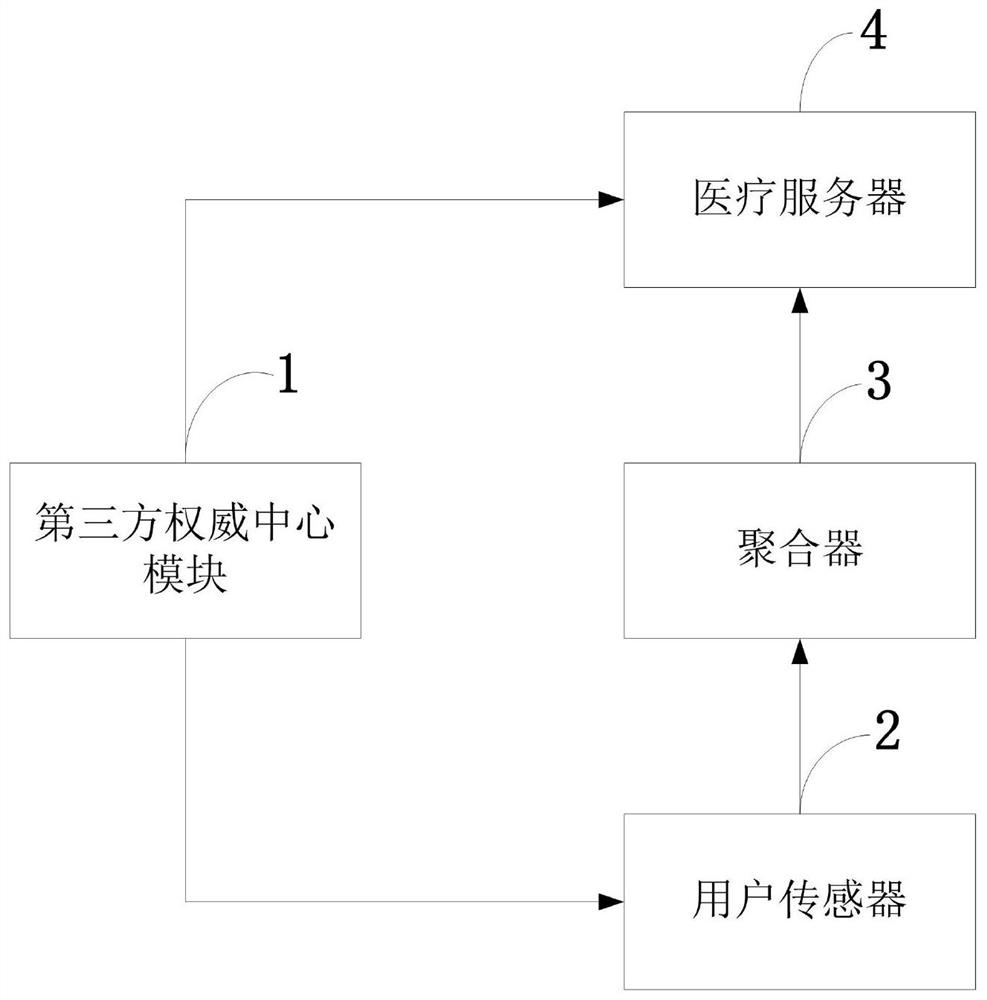
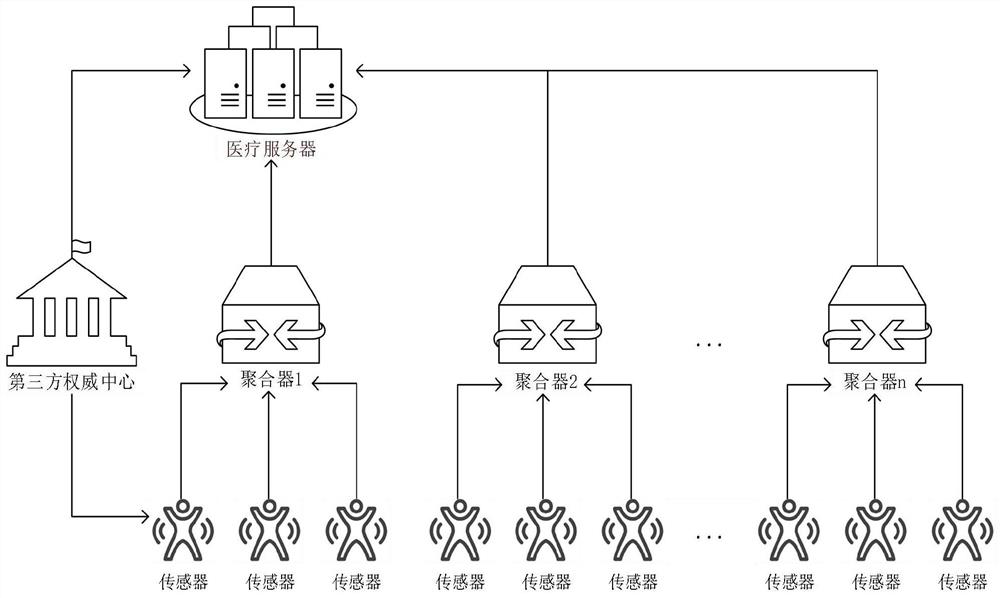
ActiveCN109584978BIntegrity guaranteedGuarantee authenticityDigital data protectionMedical equipmentInformation processingIdentity recognition
The invention belongs to the technical field of information security, and discloses a method and system for processing medical and health monitoring network model information based on signature aggregation; a third-party authoritative center provides a pair of public and private keys and a pseudo-identity identification for user sensors, and uses the key-value pair form Save the user's real identity and pseudo identity; the user sensor encrypts medical information through the medical server public key, and uses the sensor private key to sign the encrypted information; makes the aggregator obtain a series of information, and the aggregator performs signature authentication and signature aggregation; Aggregation is designed to save bandwidth and server storage space; the medical server performs data decryption after aggregate signature authentication, and provides patient medical information to healthcare personnel. The invention transmits the judgment information of medical care professionals to real patients through the third-party authoritative center and aggregator; multiple signatures can be combined into a single aggregate signature through the aggregate signature, thereby greatly reducing network bandwidth and storage costs.
Owner:XIAN UNIV OF POSTS & TELECOMM
Efficient ciphertext retrieval method and cloud computing service system based on cp-abe automatic correction
ActiveCN110138561BAvoid Frequency Guessing AttacksReduce complexityKey distribution for secure communicationPublic key for secure communicationCiphertextTheoretical computer science
The invention belongs to the technical field of cloud computing privacy protection, and discloses a high-efficiency ciphertext retrieval method based on CP‑ABE automatic correction and a cloud computing service system; combining an R tree and a Bloom filter as an index structure, an encrypted Bloom filter The device and the corresponding ciphertext file ID set are stored in the leaf nodes of the R tree; the cloud server performs matrix positioning on the R tree according to the search trapdoor, and then matches the encrypted Bloom filter in the leaf node; according to the Bloom filter The inner product result sorts the files; the trapdoor generation process introduces random numbers, even if the same keyword will generate different trapdoors; it is encrypted by using the access structure and the owner's secret attribute. The invention uses a symmetric key with a small CP-ABE encryption volume to realize fine-grained access control; introduces multiple proxy servers to realize decentralization; and prevents collusion between proxy servers.
Owner:XIDIAN UNIV
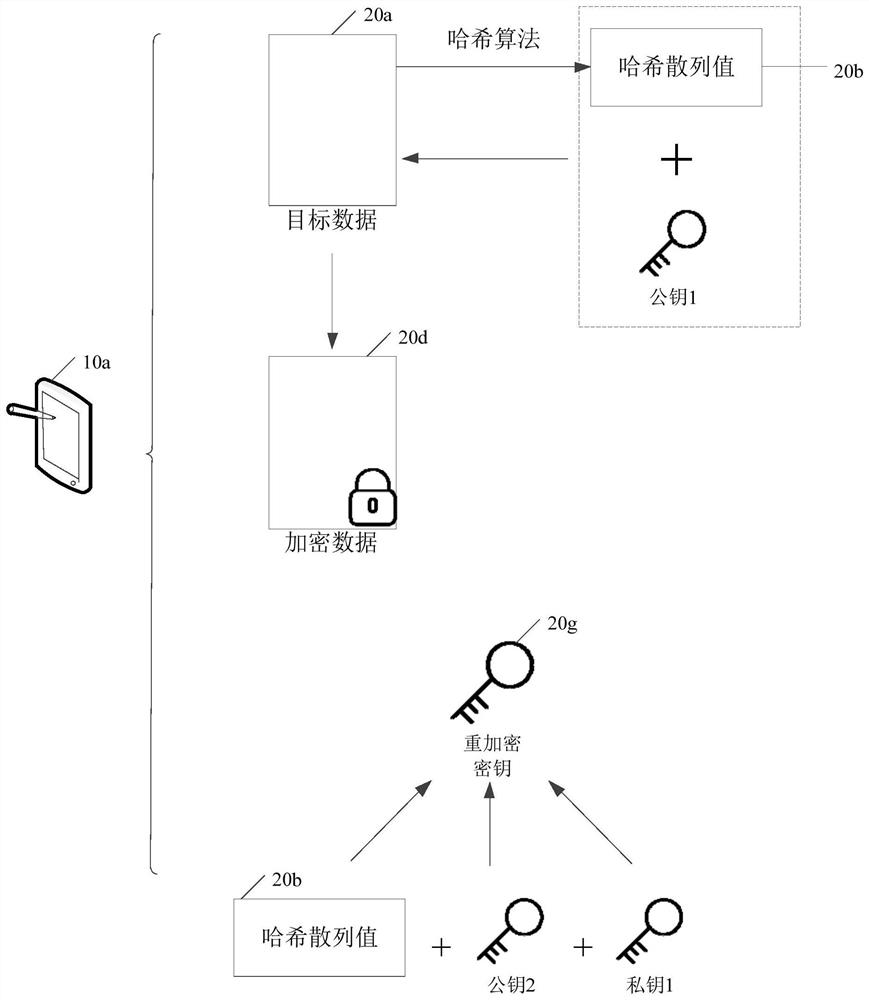
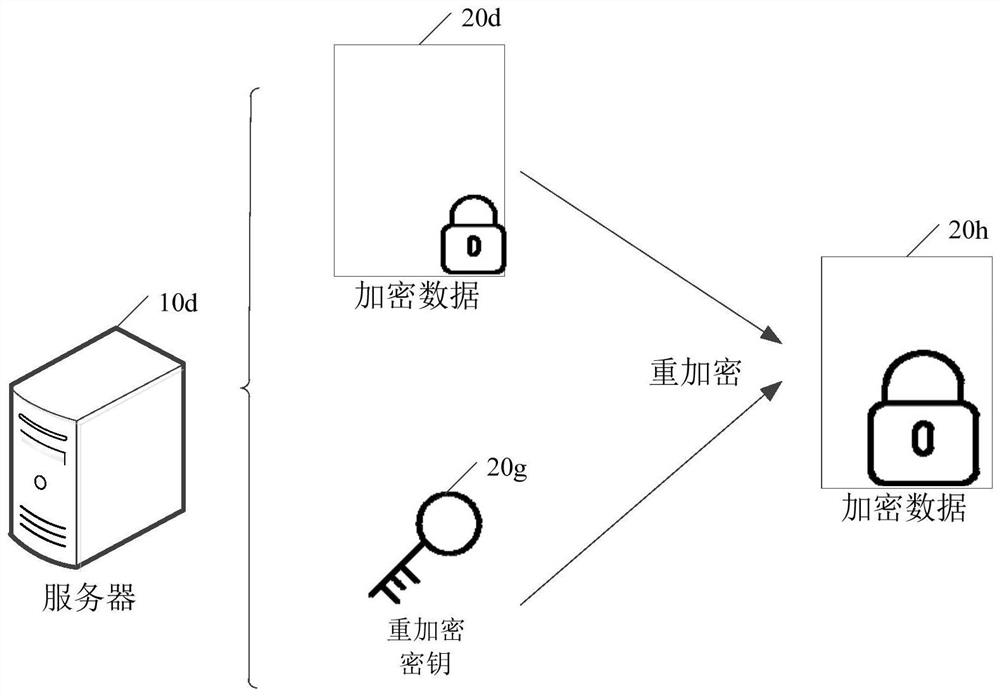
Data sharing method, device, computer equipment and storage medium
The embodiment of the present application discloses a data sharing method, device, computer equipment, and storage medium. The data sharing method includes: the sending node obtains the target data, and determines the data fingerprint of the target data; the sending node uses the sending node's sending public key and data fingerprint Encrypt the target data to obtain the first encrypted data; the sending node obtains the receiving public key of the receiving node, and generates a re-encryption key for the first encrypted data according to the sending private key, receiving public key and data fingerprint of the sending node; sending The node sends the re-encryption key and the first encrypted data to the proxy server. By adopting the application, the security of user data can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
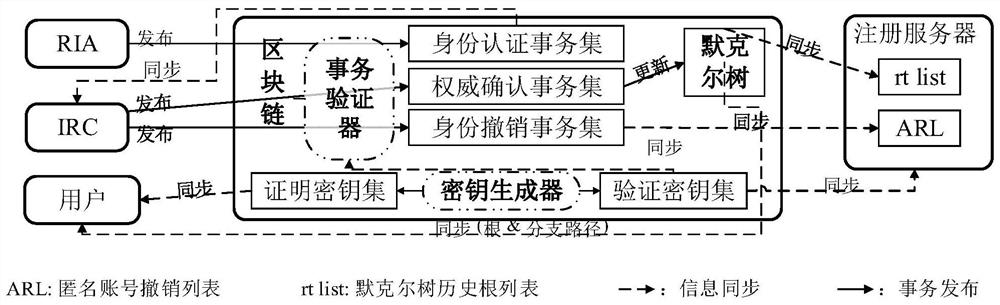
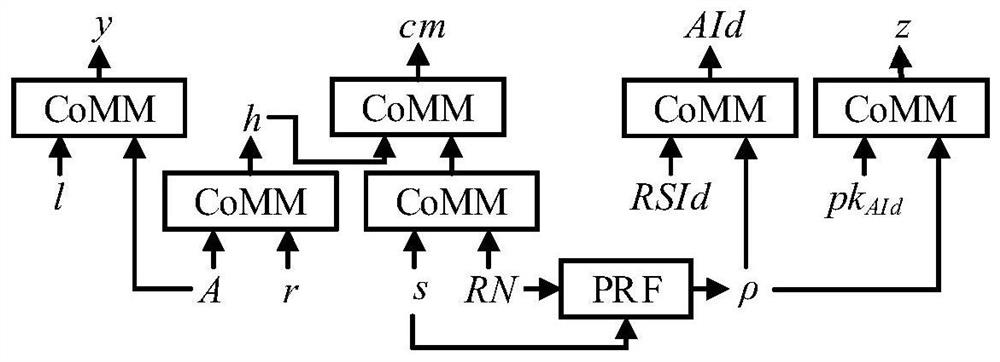
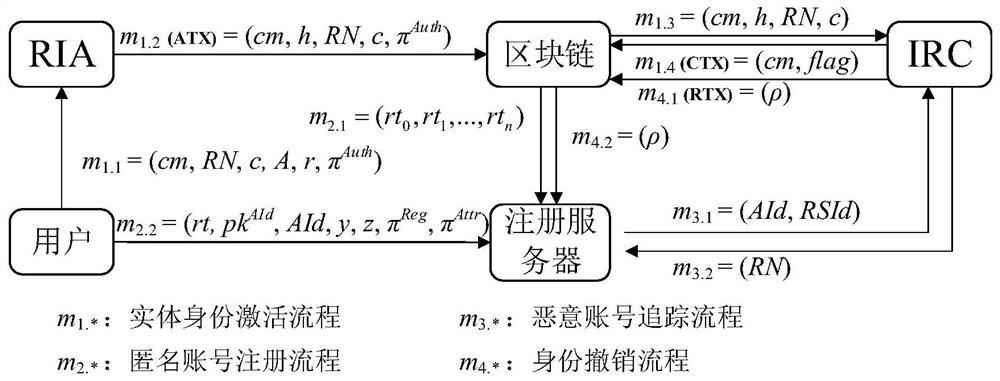
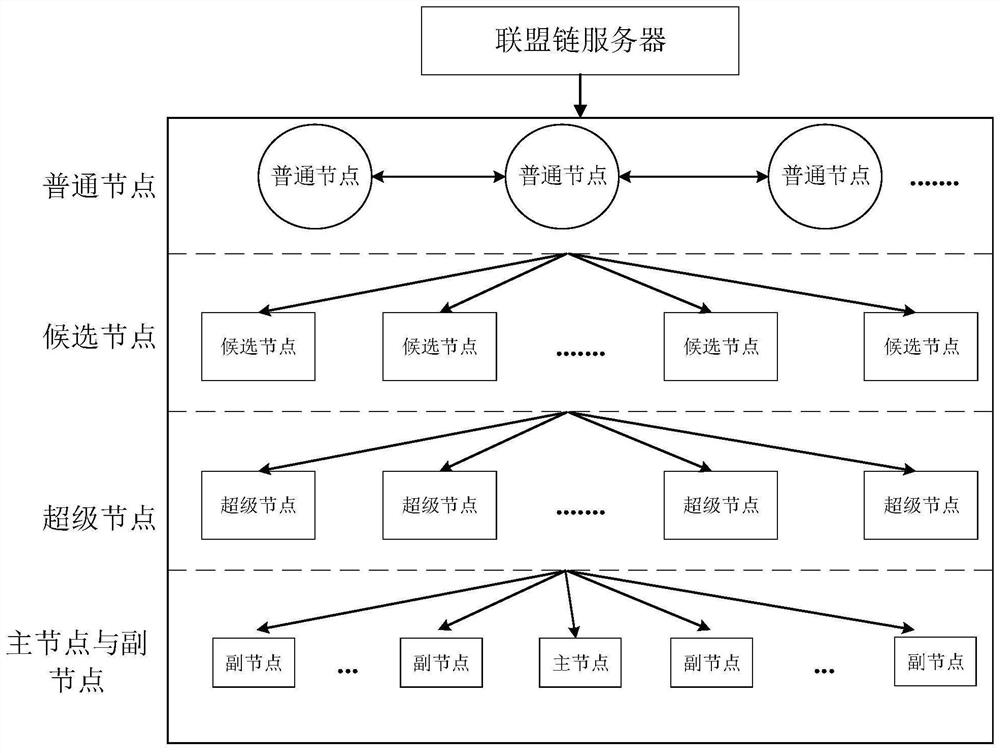
An anonymous registration method and system for protecting user privacy based on blockchain
ActiveCN111428249BPrevent leakageResistant to Collusion AttacksDatabase distribution/replicationDigital data protectionWeb siteInternet privacy
The invention relates to an anonymous registration method and system for protecting user privacy based on blockchain. This method involves the entity identity activation process and the anonymous account registration process: after the user's entity identity certificate is verified by an entity identity authentication agency, the commitment of the identity certificate information can be released to the block chain; after the user completes the entity identity activation , when registering anonymously on a website, zero-knowledge proof technology can be used to prove the legitimacy of one's own entity identity and the compliance of attributes. The invention can avoid leaking unnecessary private information of the user's identity certificate to the registration server during the registration process, and can make the registration server unable to obtain redundant identity private information while confirming that the user's identity attributes meet the requirements.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI +1
A Byzantine Fault Tolerant Consensus Method Based on Distributed Key
ActiveCN111371744BResistant to Collusion AttacksImprove consensus efficiencyKey distribution for secure communicationUser identity/authority verificationByzantine fault toleranceCompletion time
The invention belongs to the field of security authentication in the discipline of cyberspace security, and relates to a distributed key-based Byzantine fault-tolerant consensus method; the method includes selecting super nodes participating in the consensus, and generating system public parameters; according to the public Parameters, generate system public-private key pairs and public-private keys of candidate nodes through mutual interactive authentication; select the master node from the super nodes to initiate a proposal request, and start a new round of consensus; the sub-nodes perform individual verification and aggregation on the proposal request Verification, to finally determine whether to agree to send the block; after the ordinary node receives the block, the completion time triggers the next round of consensus. In this process, if the secondary node waits for the master node’s proposal request or proposal response to Broadcast the view change request and replace the master node; the invention can greatly improve the efficiency in the consensus process.
Owner:芽米科技(广州)有限公司
A Quantum Secret Sharing Method Based on Bell State
InactiveCN106712945BRealize secret sharingReduce complexityKey distribution for secure communicationQuantum efficiencyBell state
The invention discloses a quantum secret sharing method based on a Bell state. The quantum secret sharing method is characterized by comprising a secret distributor and n participants, the secret distributor distributes a random secret to the n participants, wherein each participant obtains a sub-secret, when the n participants accumulate all sub-secrets, the originally shared secret can be restored, and any information of the shared secret cannot be obtained less than n participants. By adoption of the quantum secret sharing method disclosed by the invention, the problems of participant fraud, low security, complexity and efficiency of channels in the existing quantum secret sharing process are solved, the quantum and classical resources can be saved, the operation complexity is reduced, and higher quantum efficiency is ensured.
Owner:ANHUI UNIVERSITY
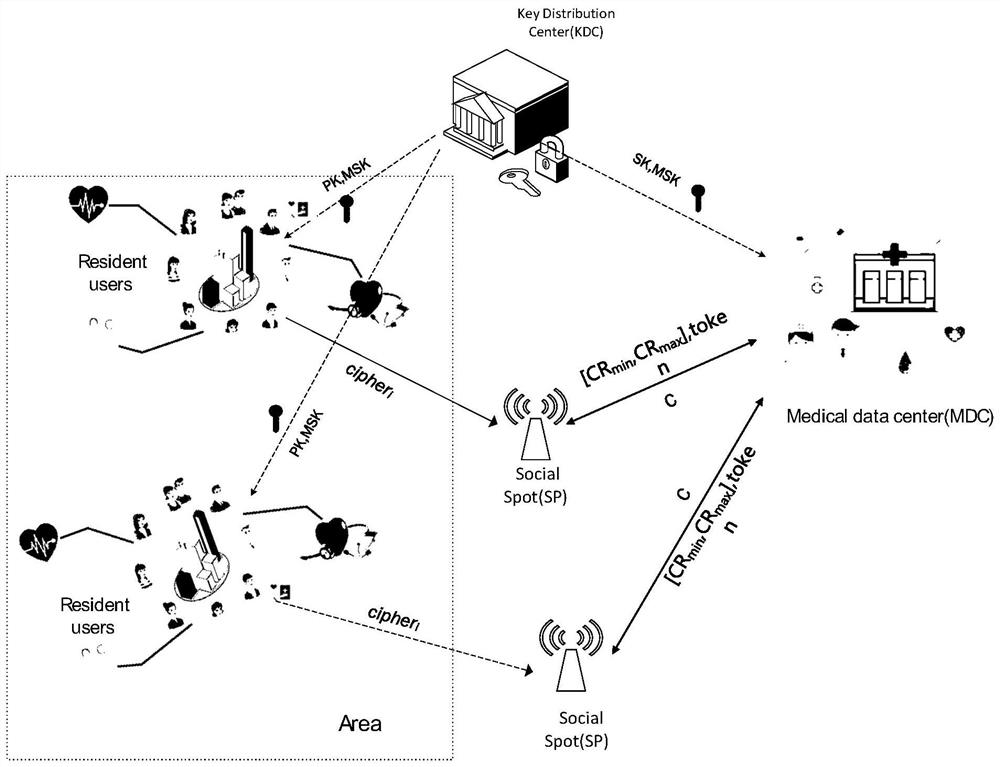
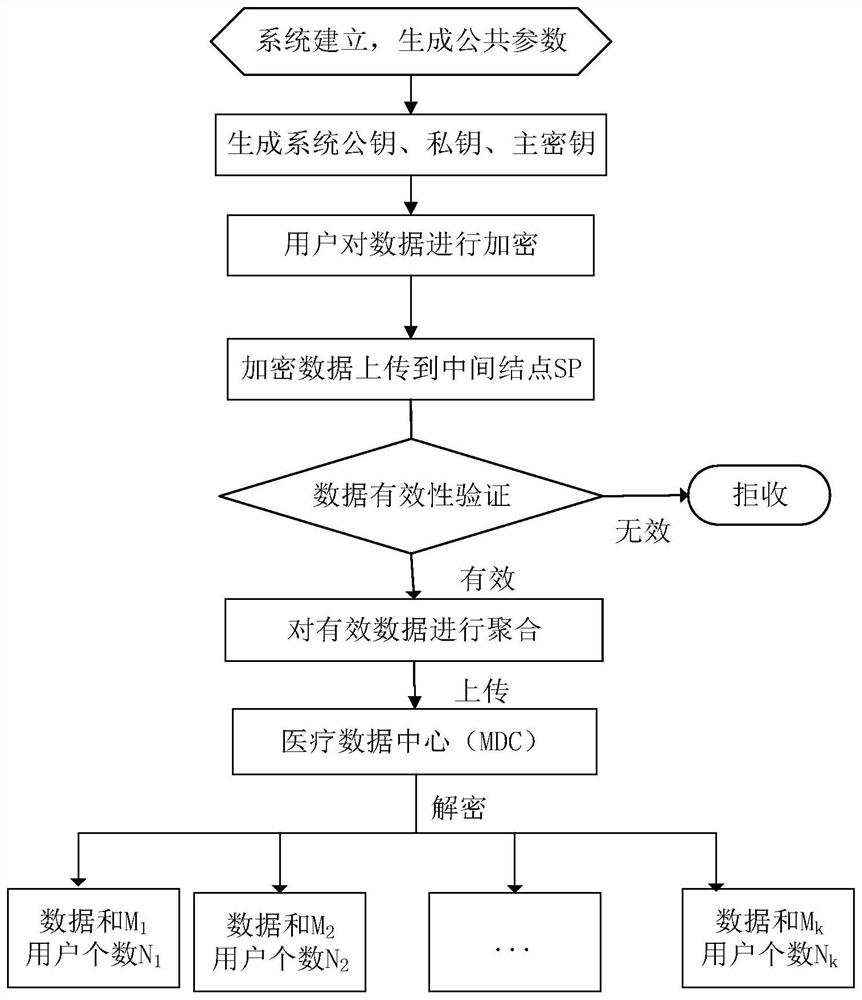
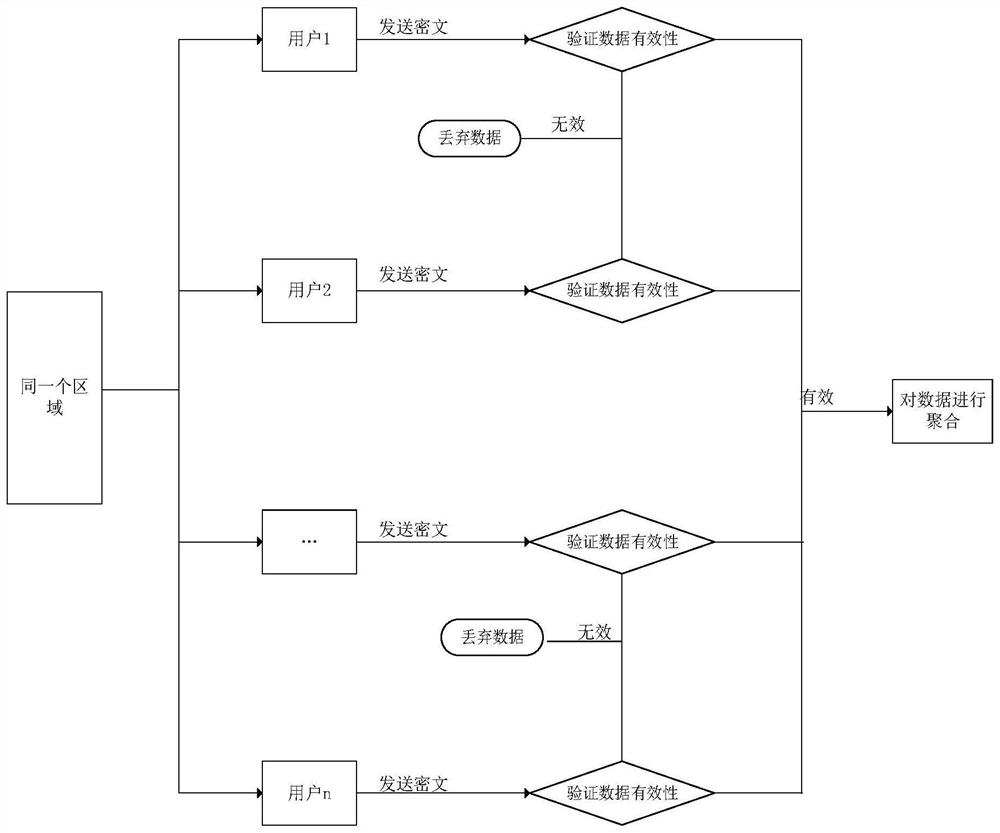
Data Aggregation Method with Validity Verification Function in Internet of Things Environment
ActiveCN109743706BGuaranteed accuracyGuaranteed validityPublic key for secure communicationParticular environment based servicesConfidentialityAttack
The invention discloses a data aggregation method with a validity verification function under the Internet of Things environment, and relates to the technical field of data aggregation under the Internet of Things environment. The correctness and accuracy of the data ensures that the aggregation results received by the medical data center are valid, thereby avoiding large data errors due to illegal data transmission, which is not conducive to data analysis and statistics. At the same time, the present invention is implemented at the medical data center The segmentation statistics of the data are realized, and the statistics of different attributes of each type of data are realized. The security proof shows that this scheme guarantees the confidentiality and privacy of data based on the difficult problem of discrete logarithm, and can also resist collusion attacks, thereby ensuring the security of user data. The performance analysis shows that, compared with the existing solutions, the present invention obviously reduces the calculation cost and saves the transmission bandwidth while ensuring the correct data transmission.
Owner:JINAN UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com