Multi-mechanism attribute-based encryption method supporting strategy dynamic updating
An attribute-based encryption and dynamic update technology, which is applied in the cloud environment and cryptography, can solve the problems of not meeting the actual application requirements, low security, low efficiency, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
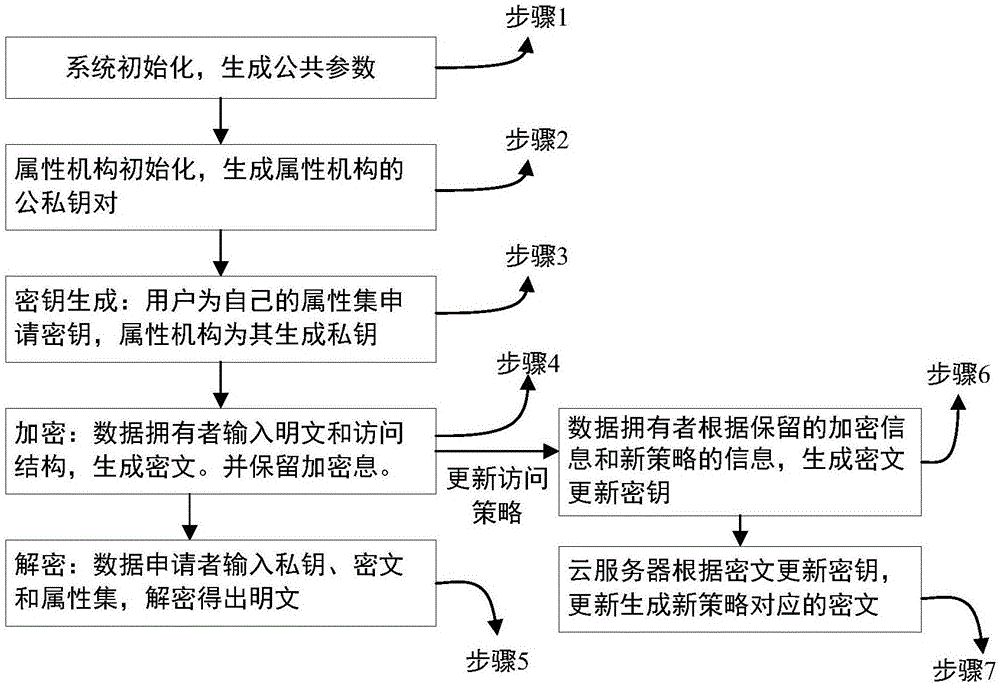
[0065] The present invention will be further described below in conjunction with embodiment and accompanying drawing.
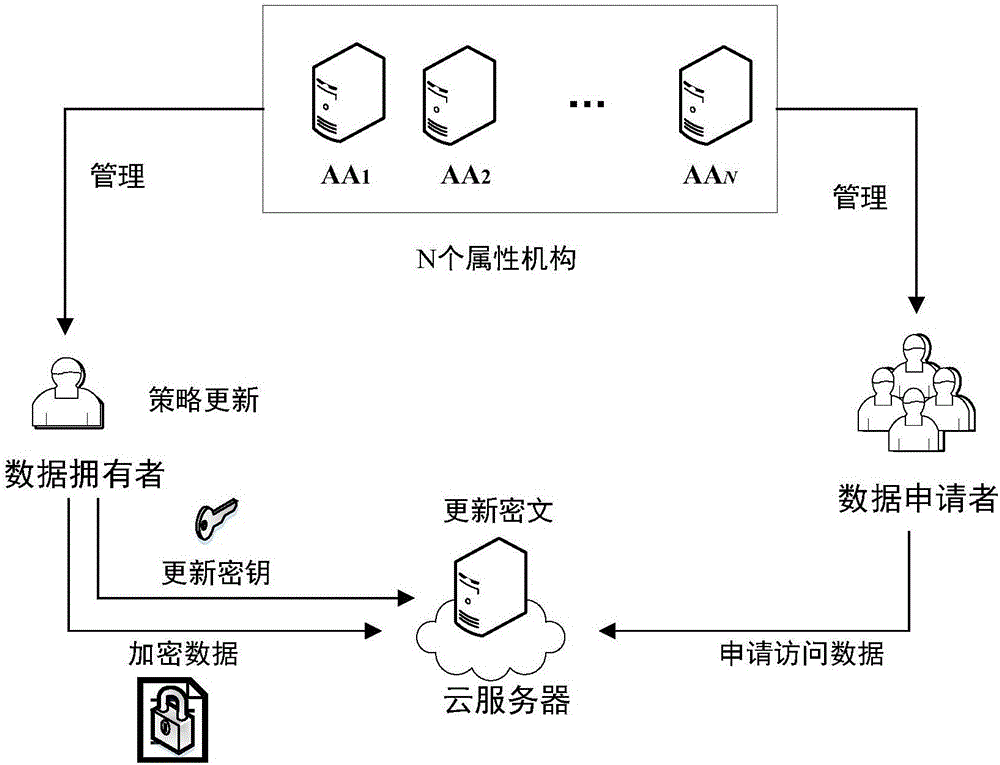
[0066] Assuming that the present invention has a total of N attribute institutions AA 1 ,AA 2 ,...,AA N , each attribute body AA i control set of properties And each user has a unique identity GID;
[0067] The algorithm flow designed by the present invention is specifically as follows:
[0068] Step 1: System initialization, executed by the system, input security parameters 1 λ , output the system public parameter PP. The specific steps of system initialization are:
[0069] Step 1.1: Input security parameter λ, output PP=(e,p,g,h,h 1 ,G,G T ), where G,G T is the multiplicative cyclic group of two order prime numbers p, g, h, h 1 is the generator of the group G, e:G×G→G T ;
[0070] Step 1.2: Choose a hash function: H:{0,1} * → Z p , calculate u=H(GID).
[0071] Step 2: The attribute organization is initialized, executed by the attribute org...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com