Agent re-encryption method used for group traffic
A proxy re-encryption and re-encryption technology, which is applied to key distribution, can solve problems such as large-scale dynamic groups that are difficult to apply to membership relationships, bottlenecks in group controllers, and complex calculations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be described in detail below in conjunction with the accompanying drawings.
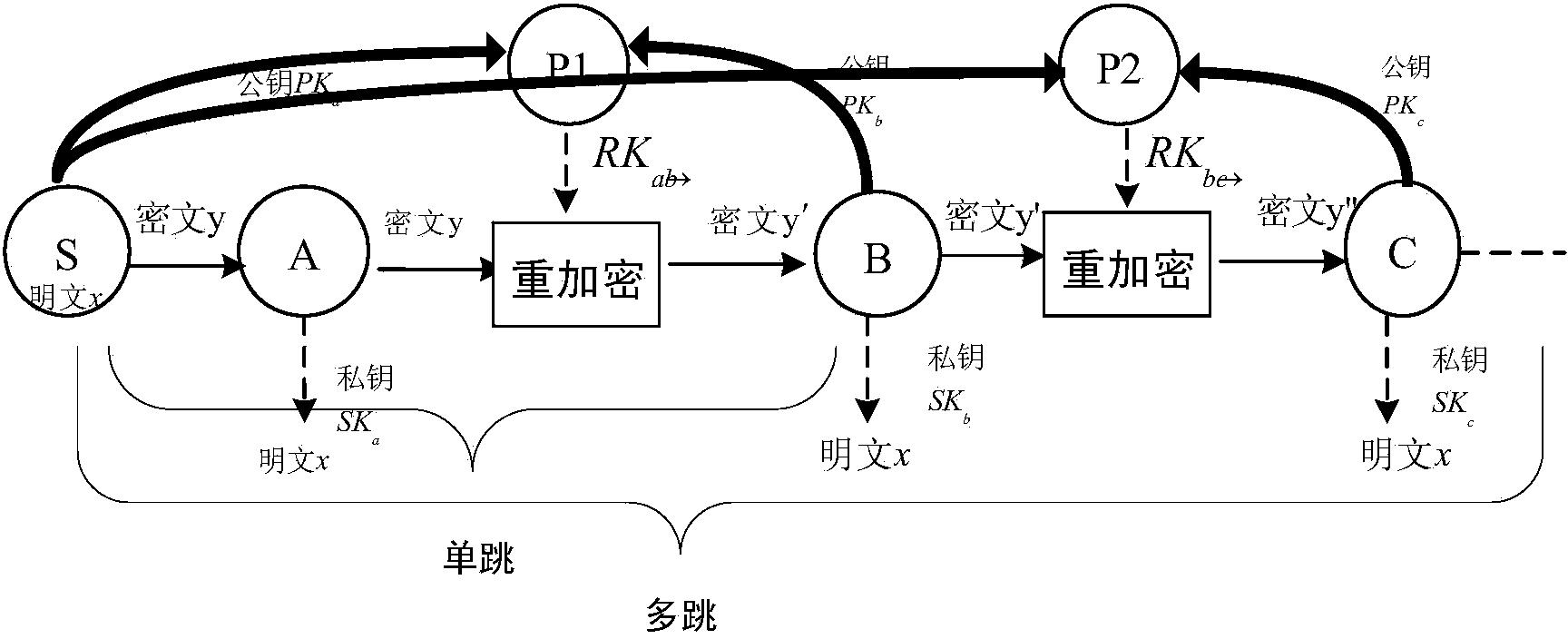
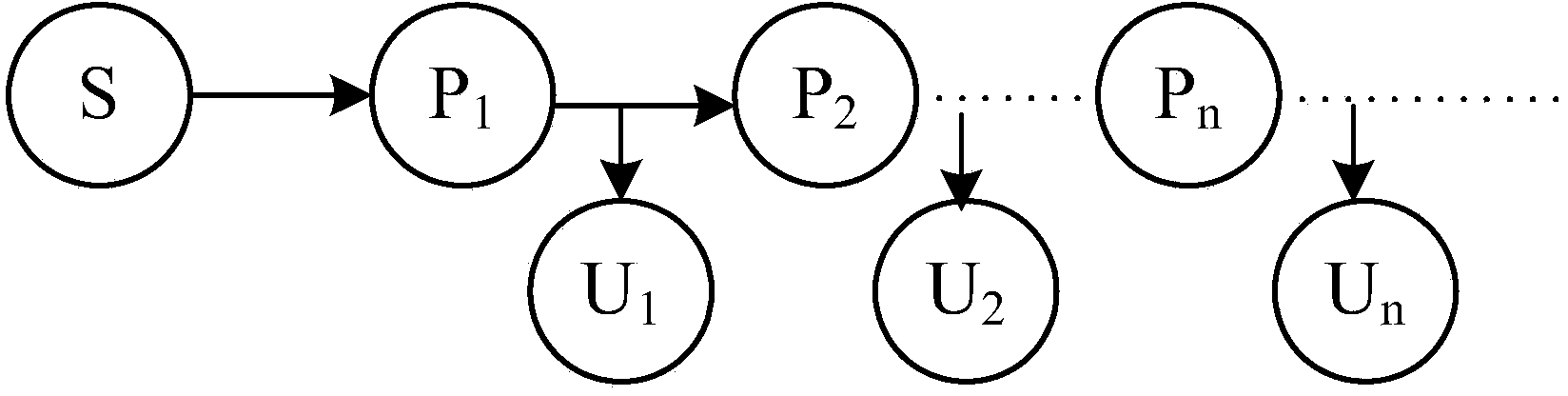
[0040] see figure 1 , 2 , shown in 3, multicast communication of the present invention uses proxy re-encryption method to comprise the following steps: Step 1: system initialization; The sender sets security parameters, and broadcasts the security parameters to all agents and deputies;
[0041] The sender or a unified secure communication platform is responsible for setting the security parameters. Broadcast to all users after parameter setting. The system parameters to be set are as follows: k is a safety parameter, which is a function of p and l, p is a prime number, G and G T are two multiplicative cyclic groups of order p, g and g' are two independent generators of the group G, H 1 ( . ) : { 0,1 } ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com