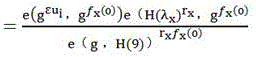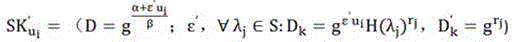Safe data sharing method in cloud environment
A data sharing, cloud environment technology, applied in the field of data security, can solve problems such as increasing the complexity of key revocation, and achieve the effect of resisting collusion attacks and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
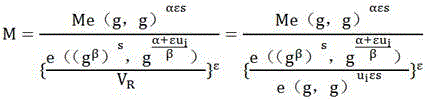
[0010] The user is the data owner, who uploads the data that needs to be shared to the cloud space through a proxy service provider; the proxy service provider, called an agency, rents the cloud space to distribute to his users; the cloud space owner is Cloud service providers, organizations that manage cloud space are called cloud centers; legal visitors are those authorized by users, who obtain encrypted shared data from the cloud storage center and use their own keys to decrypt the data.
[0011] In the present invention, firstly, the authorization agency and the cloud storage center combine the user's unique identifier to jointly generate the user key; secondly, the user mixes the asymmetric key generated by the authorization organization and the symmetric key generated by the cloud service provider to complete the encryption and decryption of data; Finally, when the user logs out, the related key and ciphertext are updated to protect the backward security of the shared dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com