A Byzantine Fault Tolerant Consensus Method Based on Distributed Key
A Byzantine, distributed technology, applied in the field of Byzantine fault-tolerant consensus based on distributed keys, to achieve the effect of improving efficiency, improving consensus efficiency and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In the accompanying drawings of the embodiments of the present invention, the same or similar reference numerals correspond to the same or similar components; in the description of the present invention
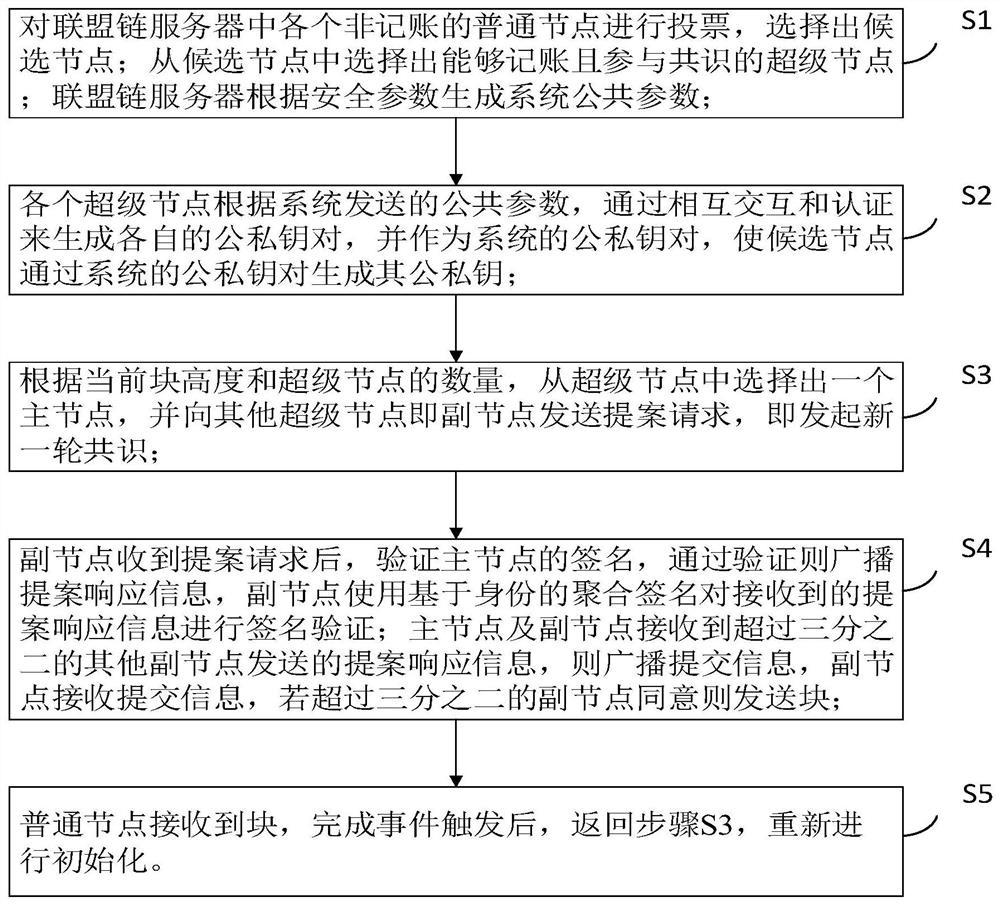
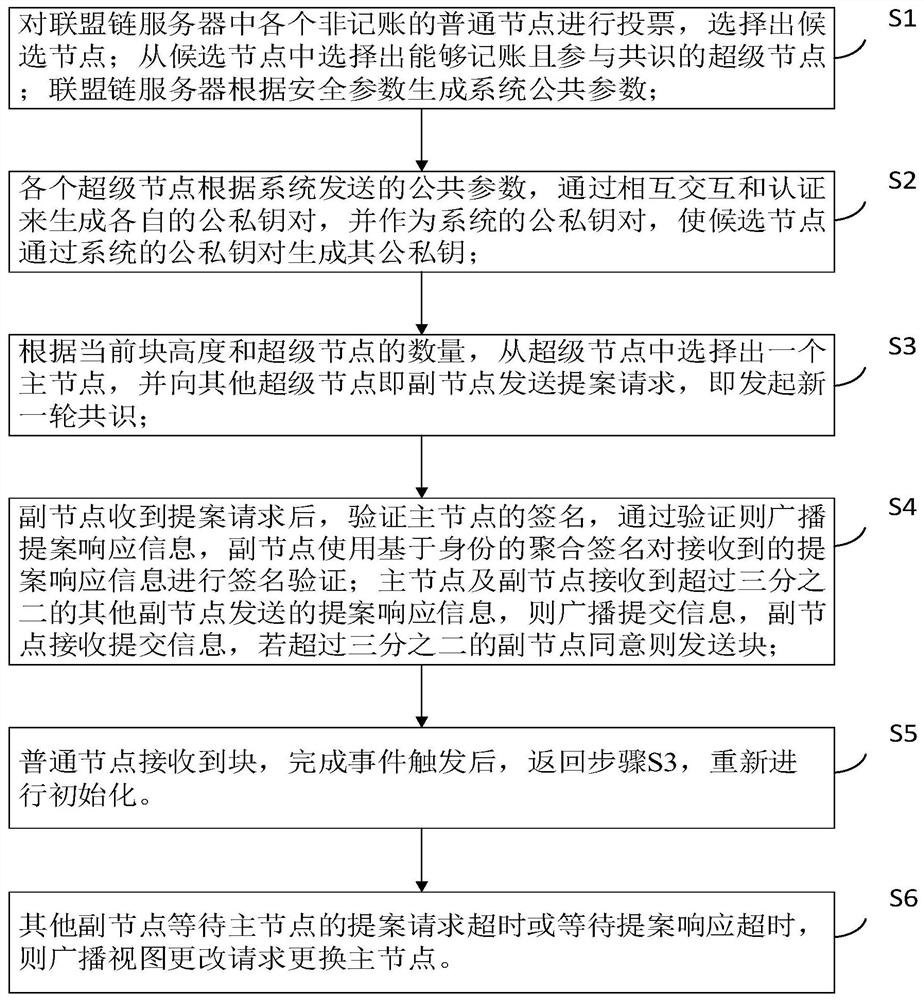
[0042] S4, after receiving the proposal request, the secondary node verifies the signature of the main node, and then broadcasts the proposal response information through the verification,
[0043] S5, the ordinary node receives the block, and after completing the event trigger, returns to step S3, and re-initializes.
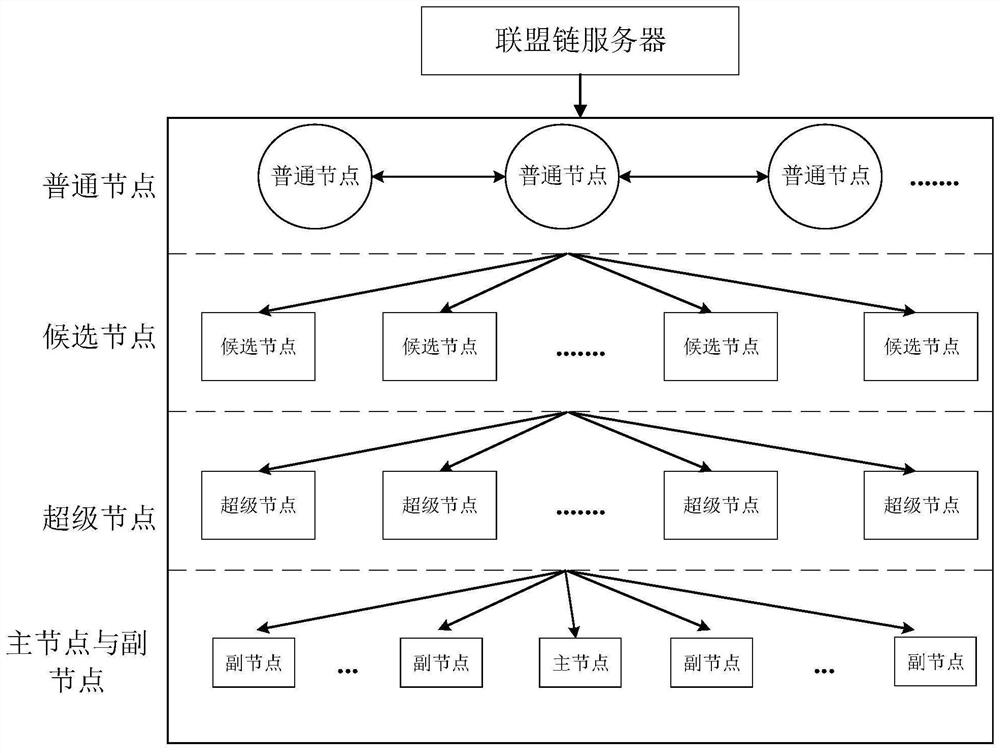
[0044] It can be understood that the present invention needs to determine the role of each node in the system. Divide it into non-bookkeeping and bookkeeping
[0049] S4, after the secondary node receives the proposal request, verify the signature of the main node, and then broadcast the proposal response information through the verification,
[0050] S5, the ordinary node receives the block, and after completing the event trigger, returns to step S3, and r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com