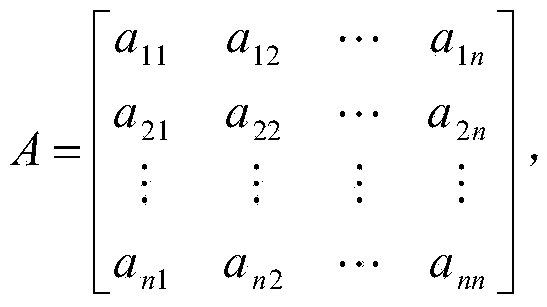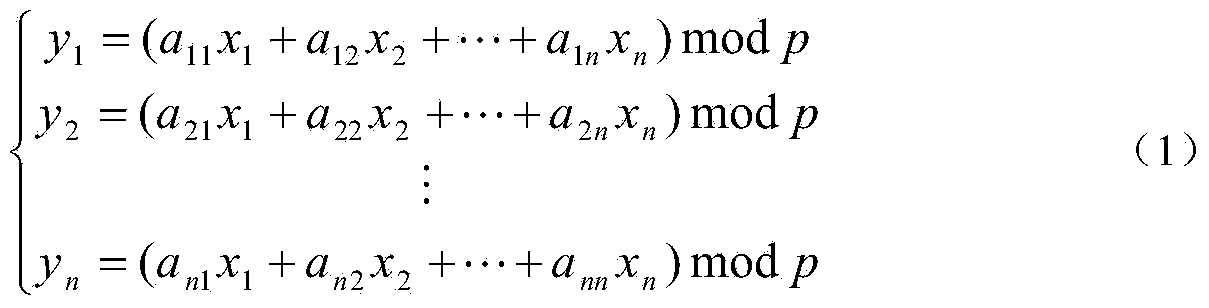Cloud storage access control method
An access control and cloud storage technology, applied in electrical components, transmission systems, etc., to solve problems such as difficulty in implementation and complex decryption process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
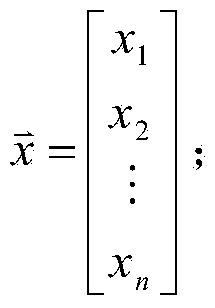
[0034] In this embodiment, a cloud storage access control method is based on a cloud storage access control system composed of a cloud storage service provider CSP, a data owner A and several users. First, the system needs to establish a finite field GF(p) , where p is a large prime number, and the large prime number p is open to all users; finite fields and large prime numbers are well-known concepts in the field of information security;
[0035] The large prime number p is generated according to the following steps:
[0036] a) Determine the bit length d of the large prime number p; for example, according to specific security requirements, the bit length d can be set to 256, 512 or 1024, etc.;
[0037] b) Randomly generate an odd number q whose bit length is d bits and whose first and last bits are 1;
[0038] c) Use the prime number detection method to judge whether q is a prime number, if so, set p=q, otherwise, re-execute step b.
[0039] The cloud storage access contro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com