Data access control method and system in cloud storage environment
A data access control and data access technology, applied in the field of network communication, can solve problems such as illegal use of user data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0059] The following first explains the noun symbols that appear in this article:
[0060] DataOwner: data owner
[0061] DataUser: data user
[0063] UID: User ID
[0064] FID: file identifier
[0065] HashDataUnit: data hash unit
[0066] DataUnit: data storage unit
[0067] KeyUnit: shared key storage unit
[0068] PKDO: data owner public key
[0069] SKDO: data owner private key
[0070] K: shared key
[0071] CertDU: data user certificate
[0072] PKDU: data user public key
[0073] SKDU: data user private key
[0074] Hash(): hash calculation
[0075] E(M)K: Symmetric encryption of plaintext M using symmetric key K
[0076] E(M)PK: use the public key to encrypt the plaintext M
[0077] D(C)PK: use the private key to decrypt the ciphertext C
[0078] S(v)SK: Use the private key to sign the proof v
[0079]V(s)PK: Use the public key to verify the signature s
[0080] Data: processed data
[0081] isShared: shared type
[0...
Embodiment 2
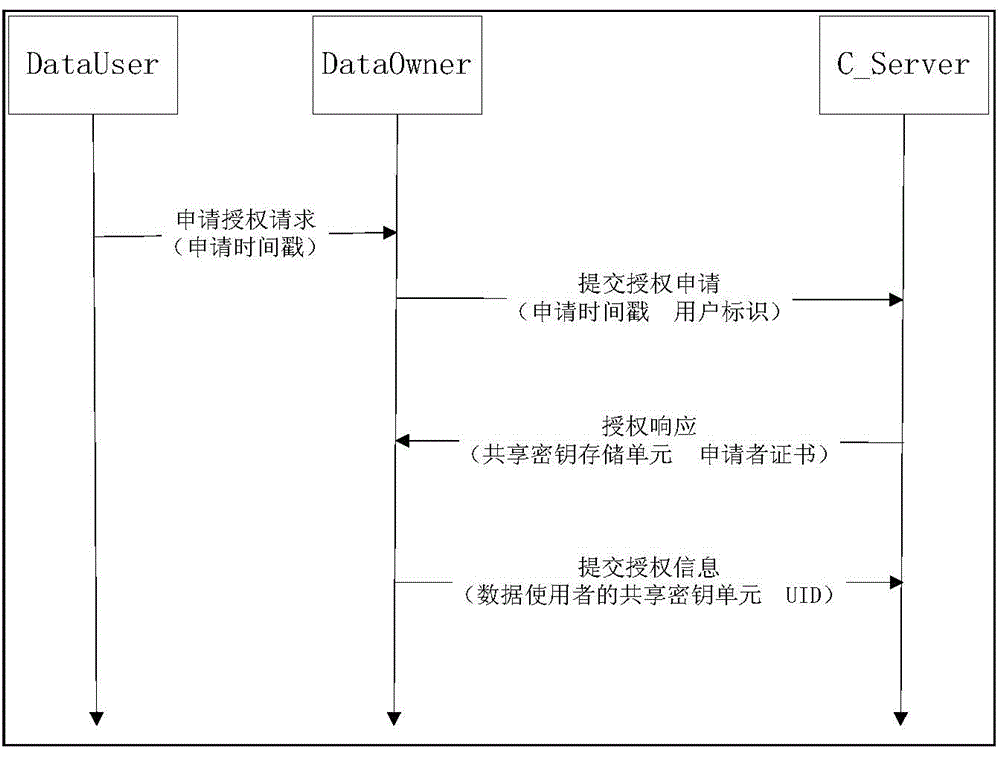
[0115] This embodiment provides a data access control system in a cloud storage environment, and its specific implementation structure is as follows Figure 5 As shown, it may specifically include: the client of the data owner, the client of the data user, and the cloud server.
[0116] The client of the data owner is used to register the personal information of the data owner with the cloud server. When the data owner determines that the data that needs to be uploaded to the cloud server is shared data, the client uses symmetric Encrypting the data with a key, and sending the encrypted data, the symmetric key, the hash operation result of the data, and the shared attribute of the data to the cloud server;
[0117] When the data owner determines that the data that needs to be uploaded to the cloud server is non-shared data, the client uses its own public key to encrypt the data, and the encrypted data, the hash operation result of the data and The sharing attribute of the dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com