Hierarchical classification access authorization management method based on roles
A technology of authorization management and roles, applied in the field of data communication, which can solve problems such as unauthorized access, sensitive information leakage, and easy leakage of data transmission.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
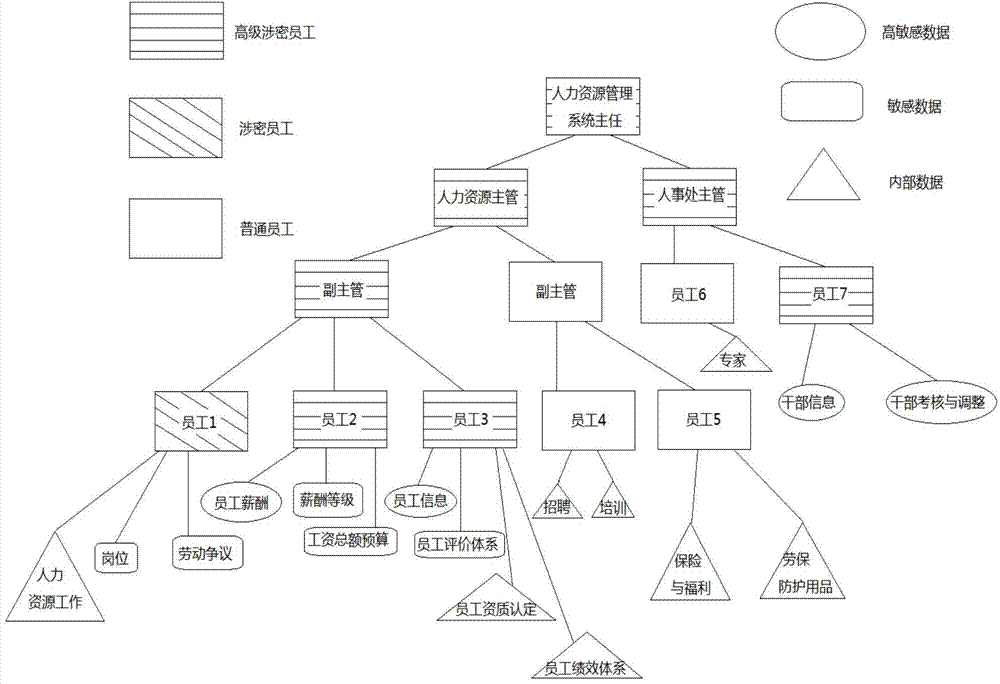
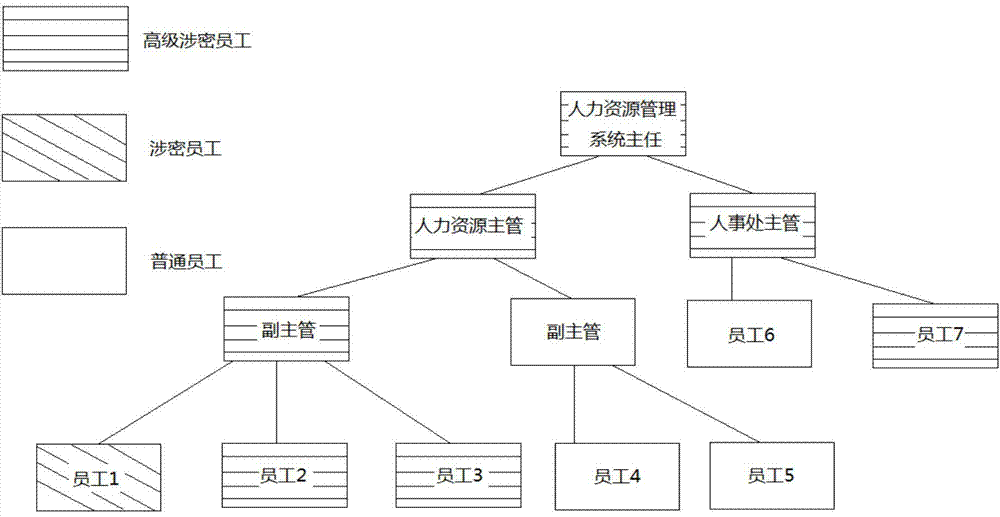
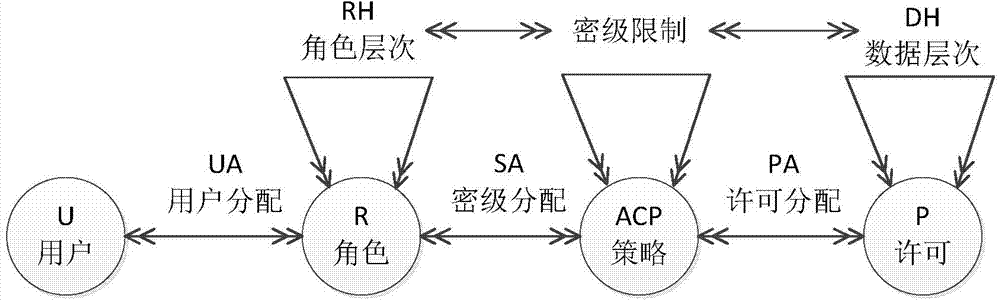
[0074] Embodiment of the present invention: a method for authorization management of role-based hierarchical classification access, such as Figure 8 shown, including the following steps:
[0075] S1. Initialization: Assuming that there are n+1 data types and m users in the information system, an encryption key hierarchy tree is established, and the index master key K is calculated j and class key K x , where 1≤j≤t, t+1≤x≤n, t and j are the main index nodes, and t+1, x and n are the leaf nodes under the main index node;
[0076] Specifically, the index master key K is calculated by the following method j and class key K x :
[0077] (1) The encryptor randomly selects an integer IV, two HMACHs with keys k (·)and Run the polynomial-time group generation algorithm g(1 n′ ) to generate a group G, and choose a collision-resistant hash function H′: {0, 1}*→G, where K is the system access master key, and K x for safety class C x the class key;
[0078] (2) Calculate the in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com