Encryption device, system and method for encryption, identification using the encryption device
A technology of identity authentication and computer devices, applied in transmission systems, data processing applications, instruments, etc., can solve problems such as loss of funds, inability to determine whether information has been tampered with, loss of customer funds, etc., to improve security and solve transaction hijacking Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
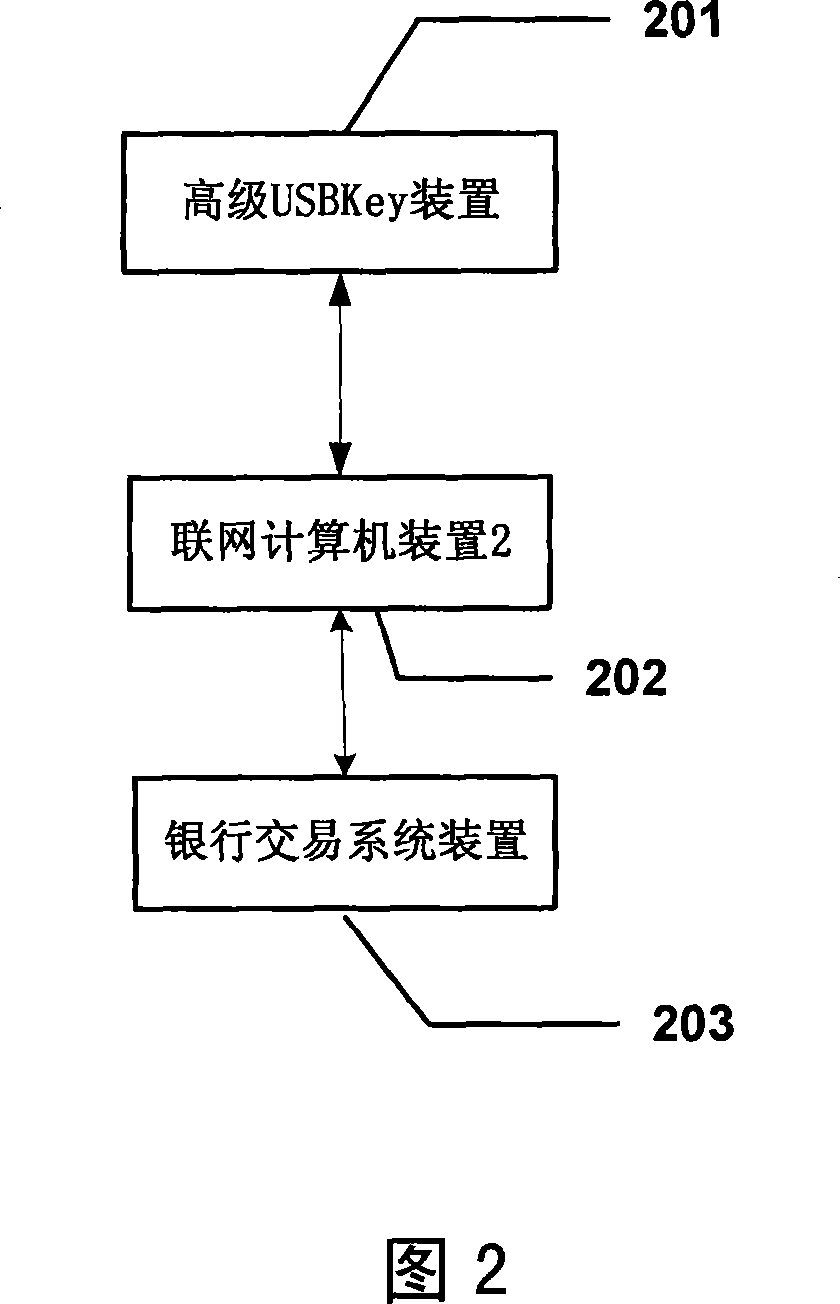
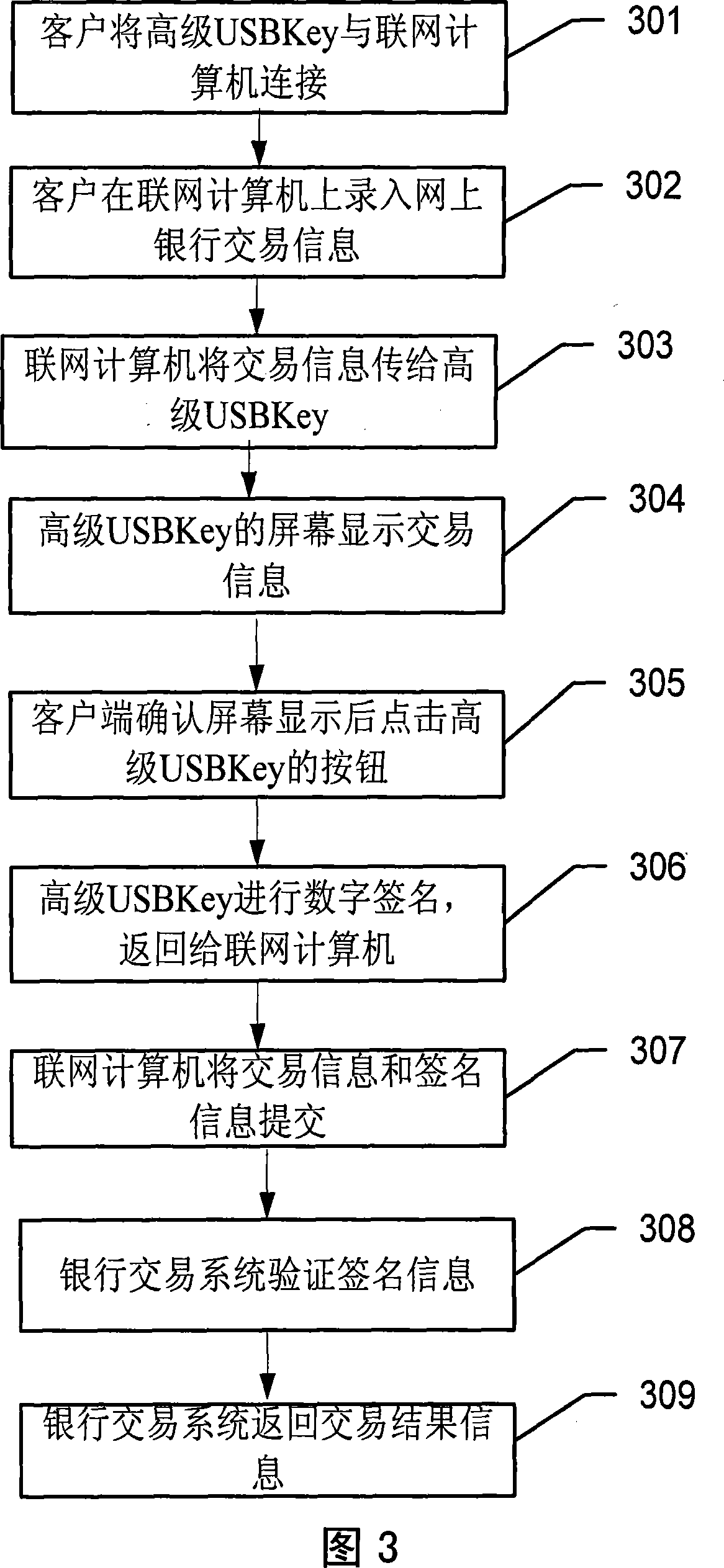
[0050] The invention discloses a USBKey device, and a system and method for encrypting and authenticating online bank data by using the USBKey device. On the basis of the prior art USBKey device, the USBKey device is modified, and buttons and a visual screen are added. It is applied to online banking transactions to prevent criminals from remotely controlling and tampering with signature data during online transactions, further improving the security of online banking and reducing the risk of fund theft.
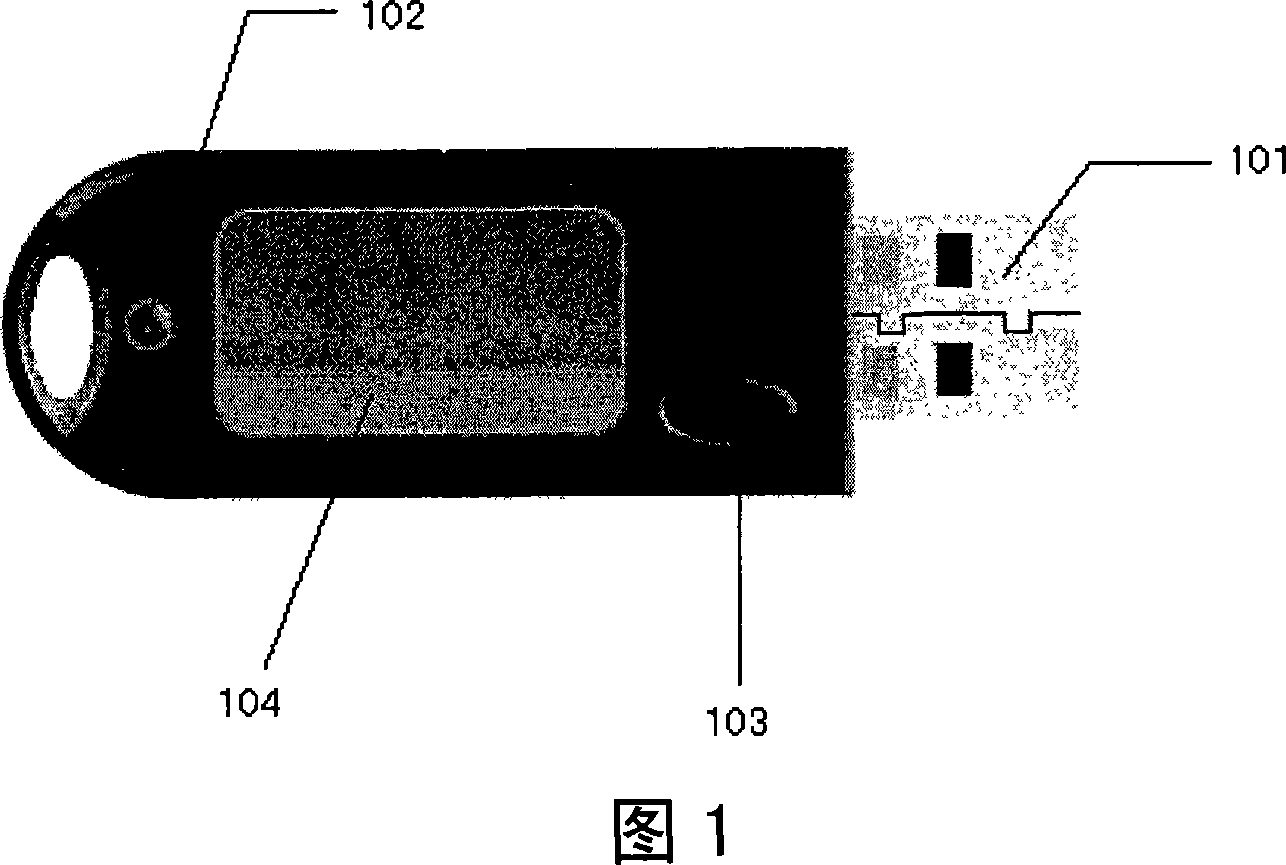
[0051] FIG. 1 depicts a schematic diagram of a USBKey device involved in the present invention.
[0052] The shape and size of the USBKey device involved in the present invention are similar to those of common keys, and are easy to carry and use. Through the USB interface 101, insert the USB socket on the computer to connect with the computer; the indicator light 102 indicates its working status; the button 103 is used for: when the client confirms that the USBKey device is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com