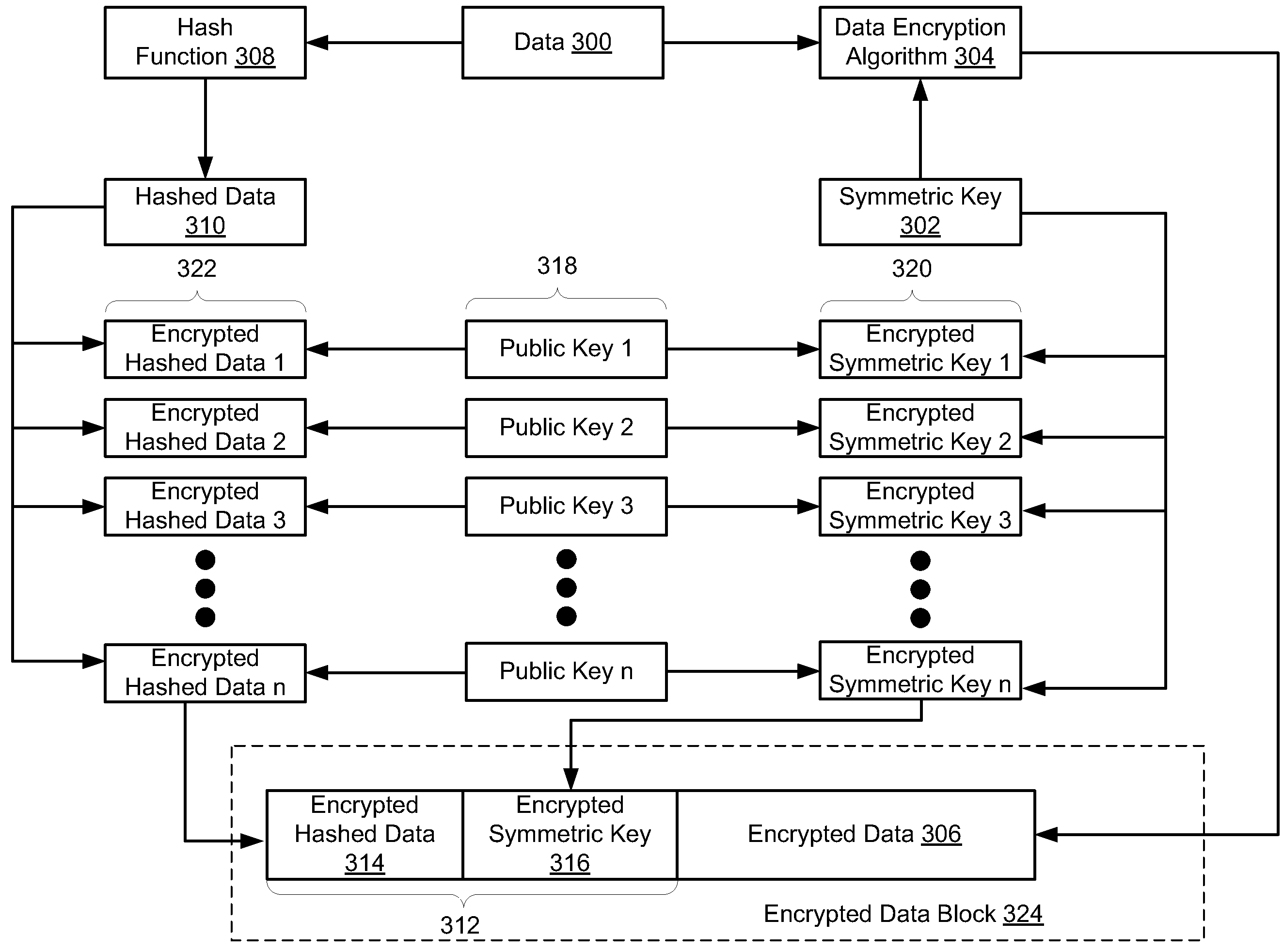
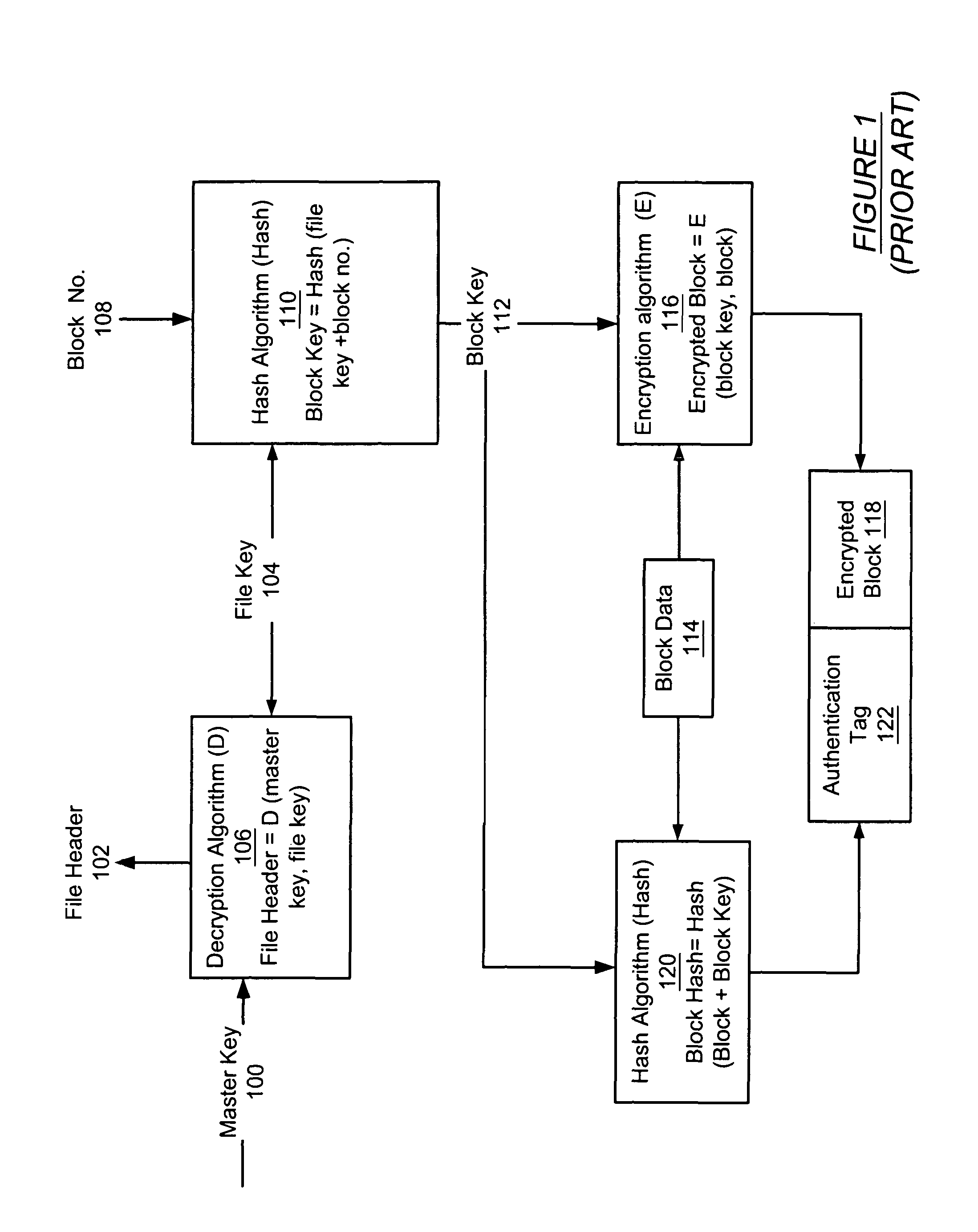
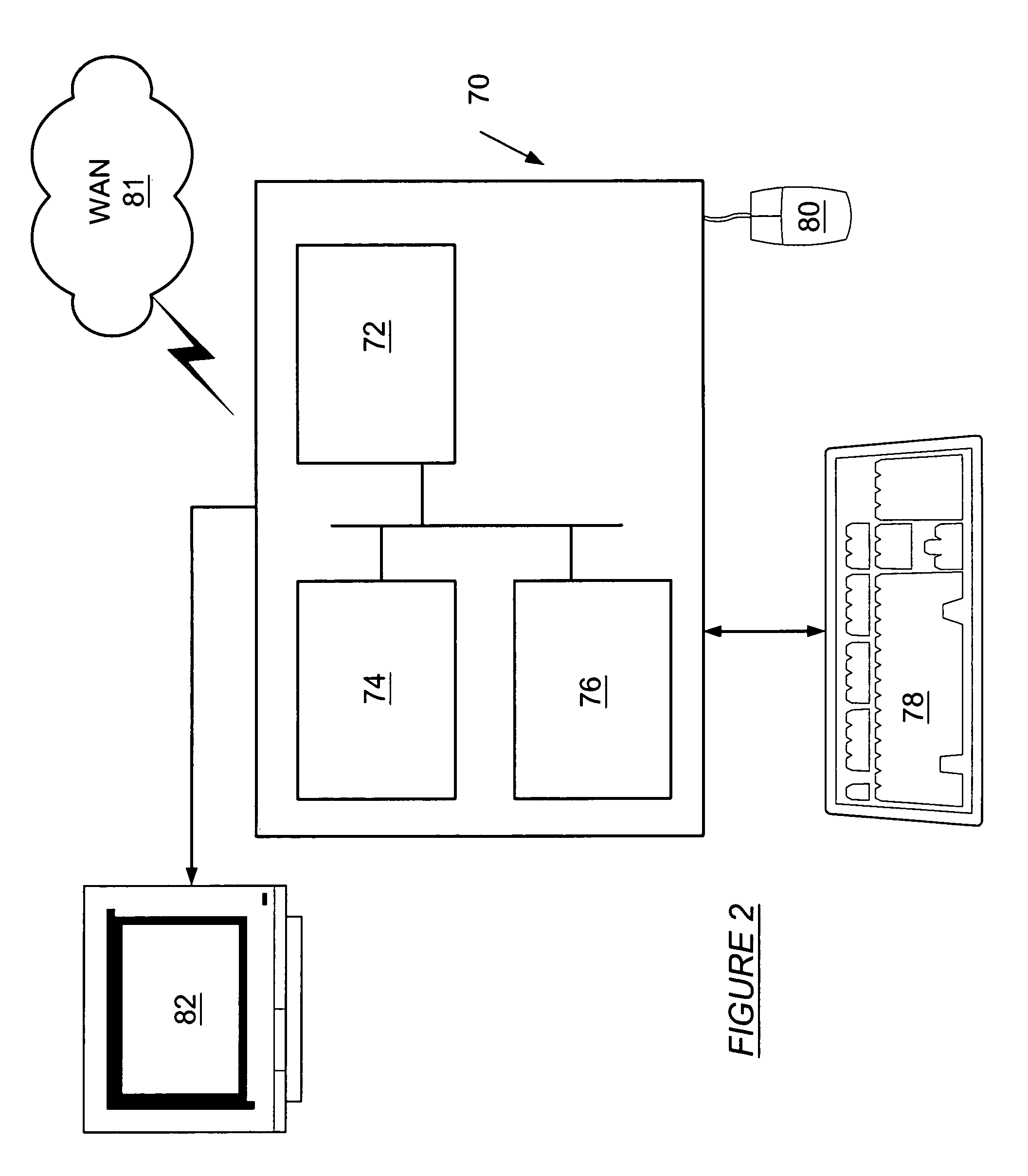
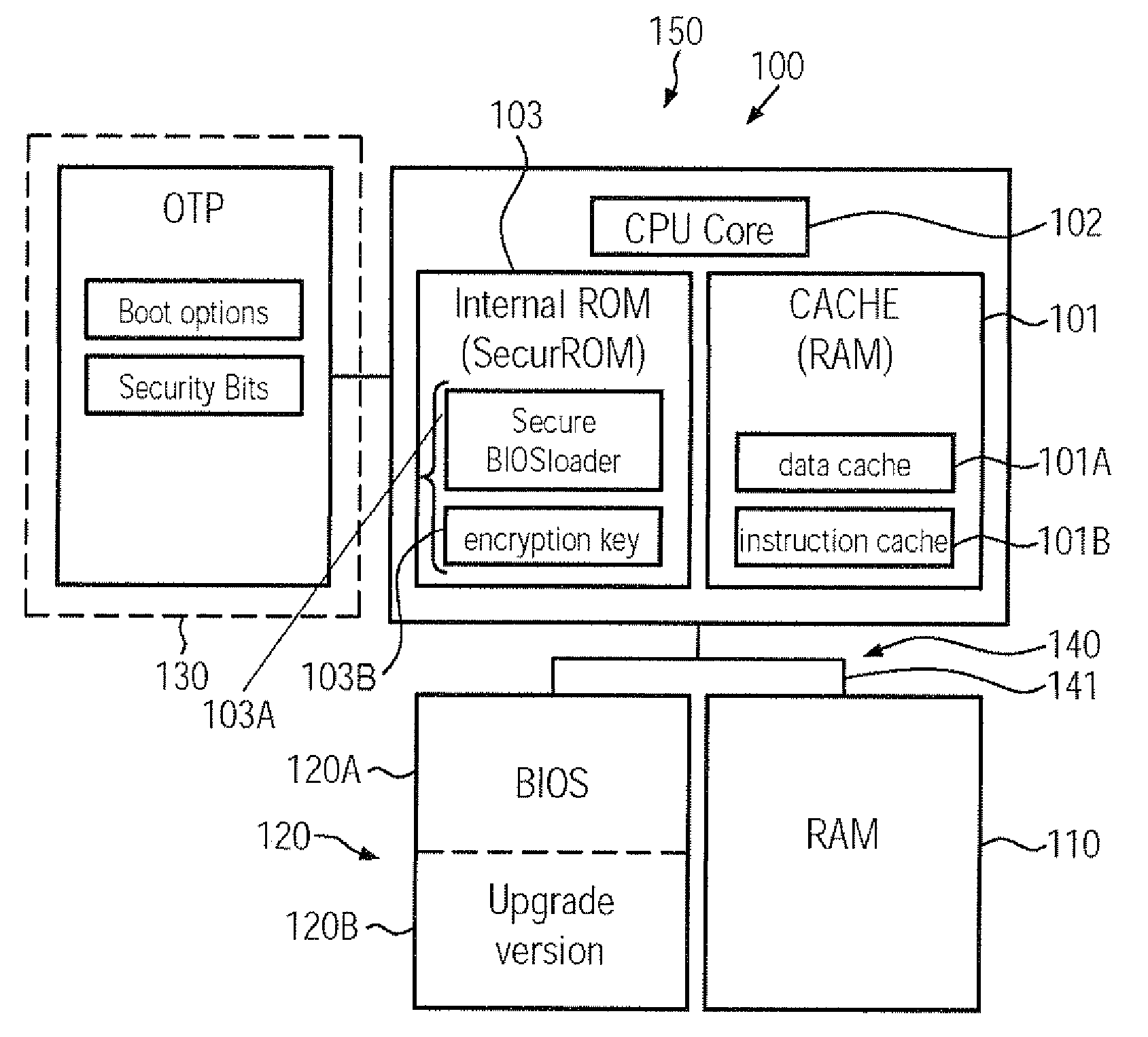
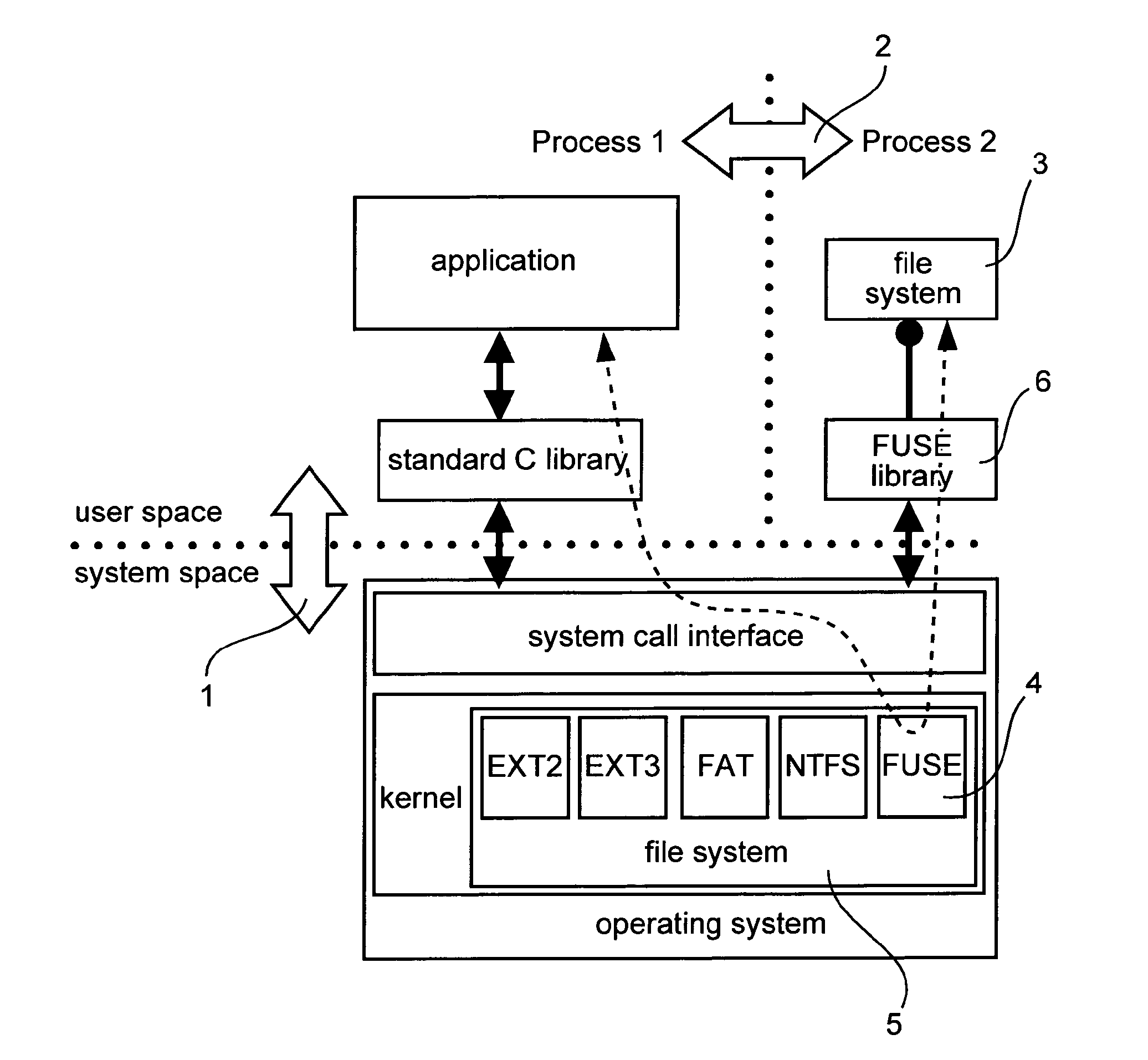
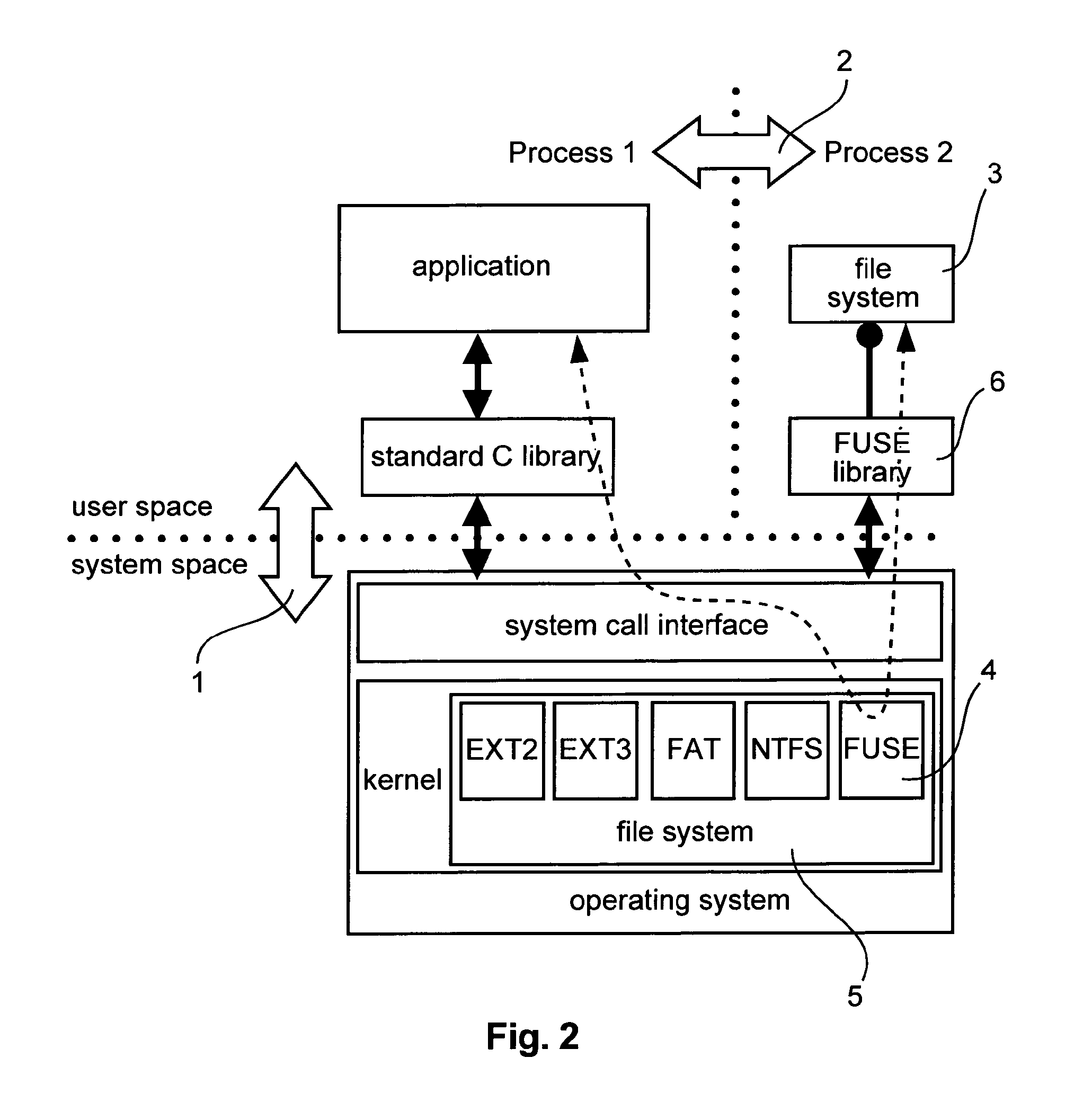
Patents
Literature
238 results about "Symmetric-key algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. This requirement that both parties have access to the secret key is one of the main drawbacks of symmetric key encryption, in comparison to public-key encryption (also known as asymmetric key encryption).
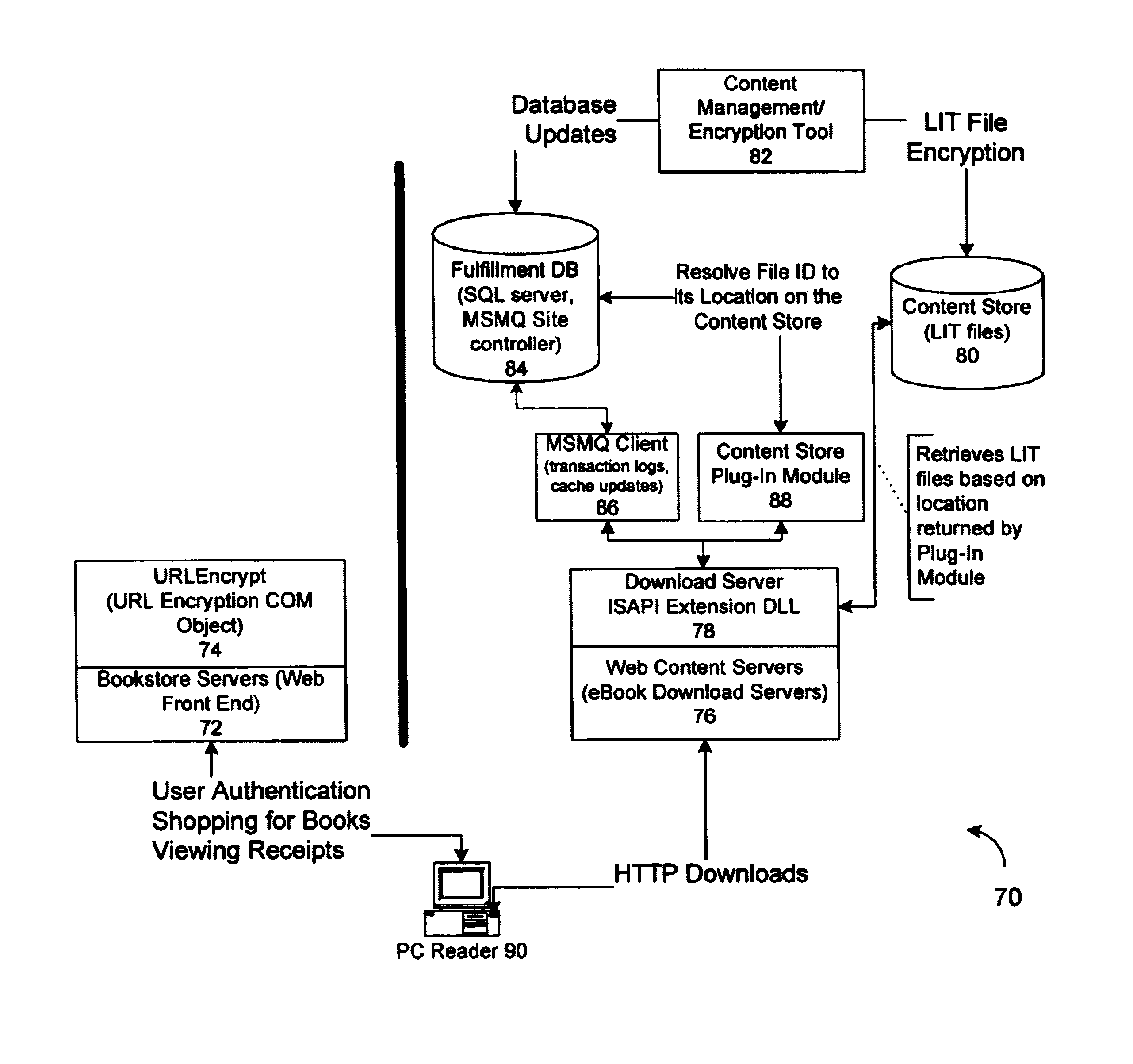
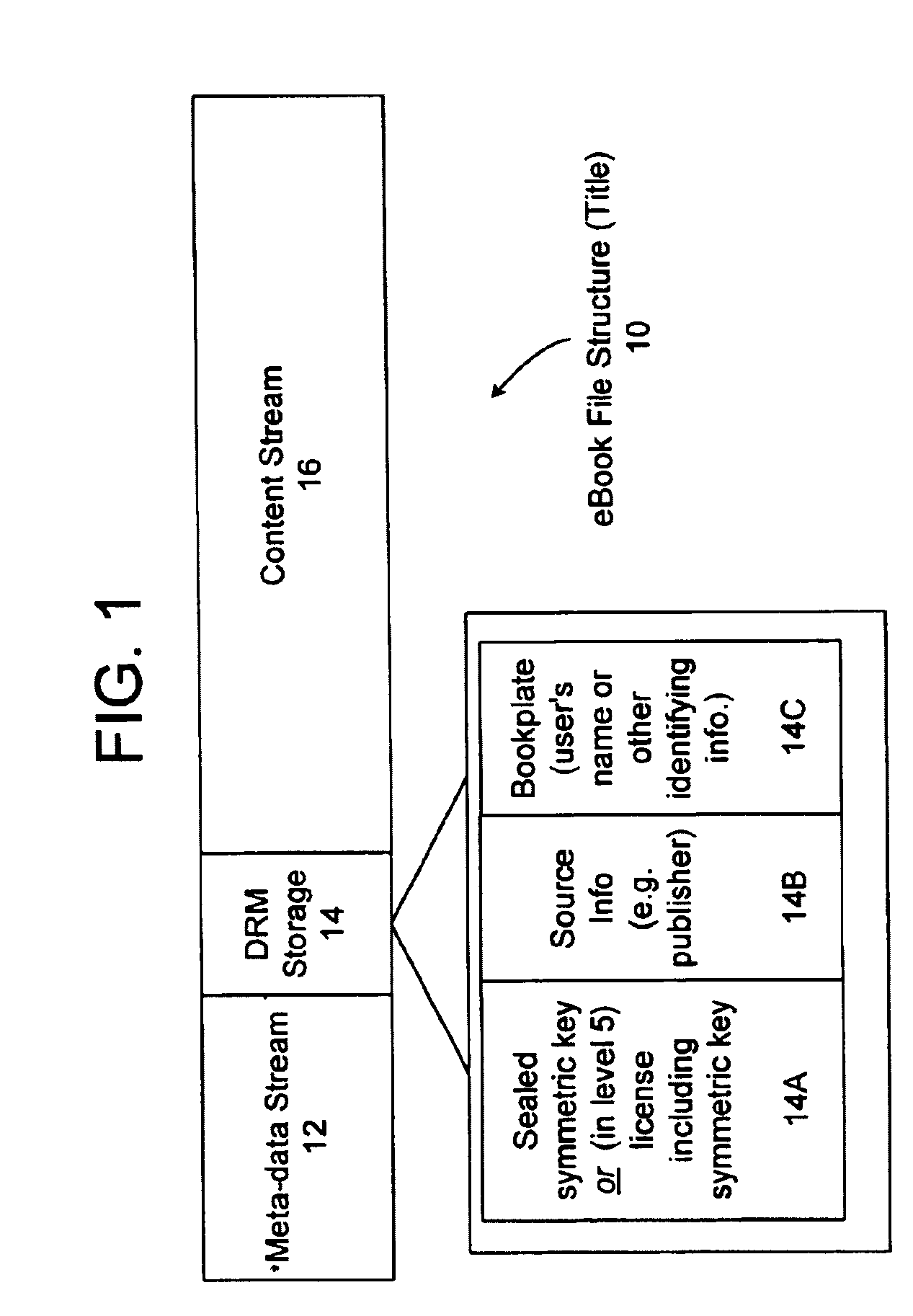
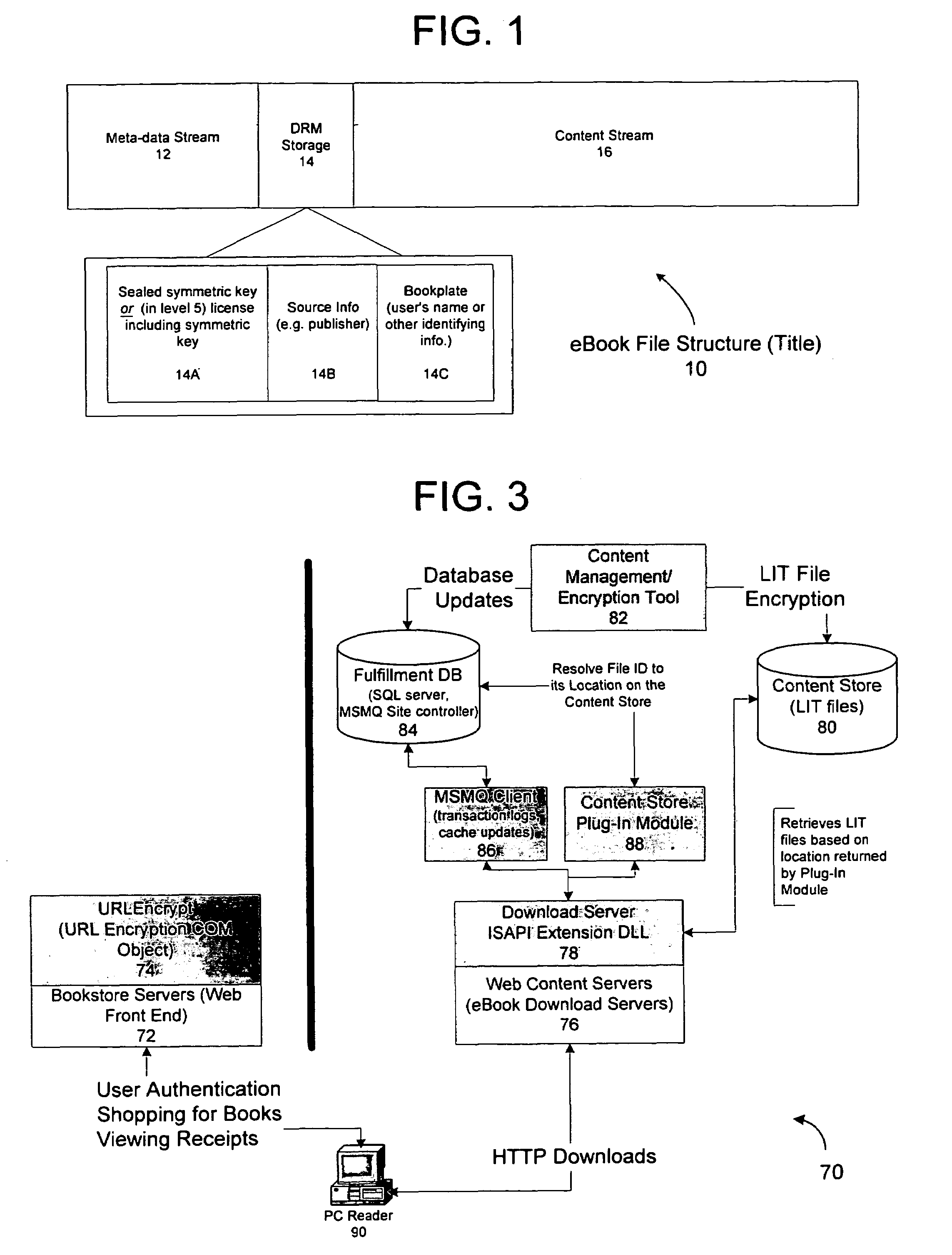
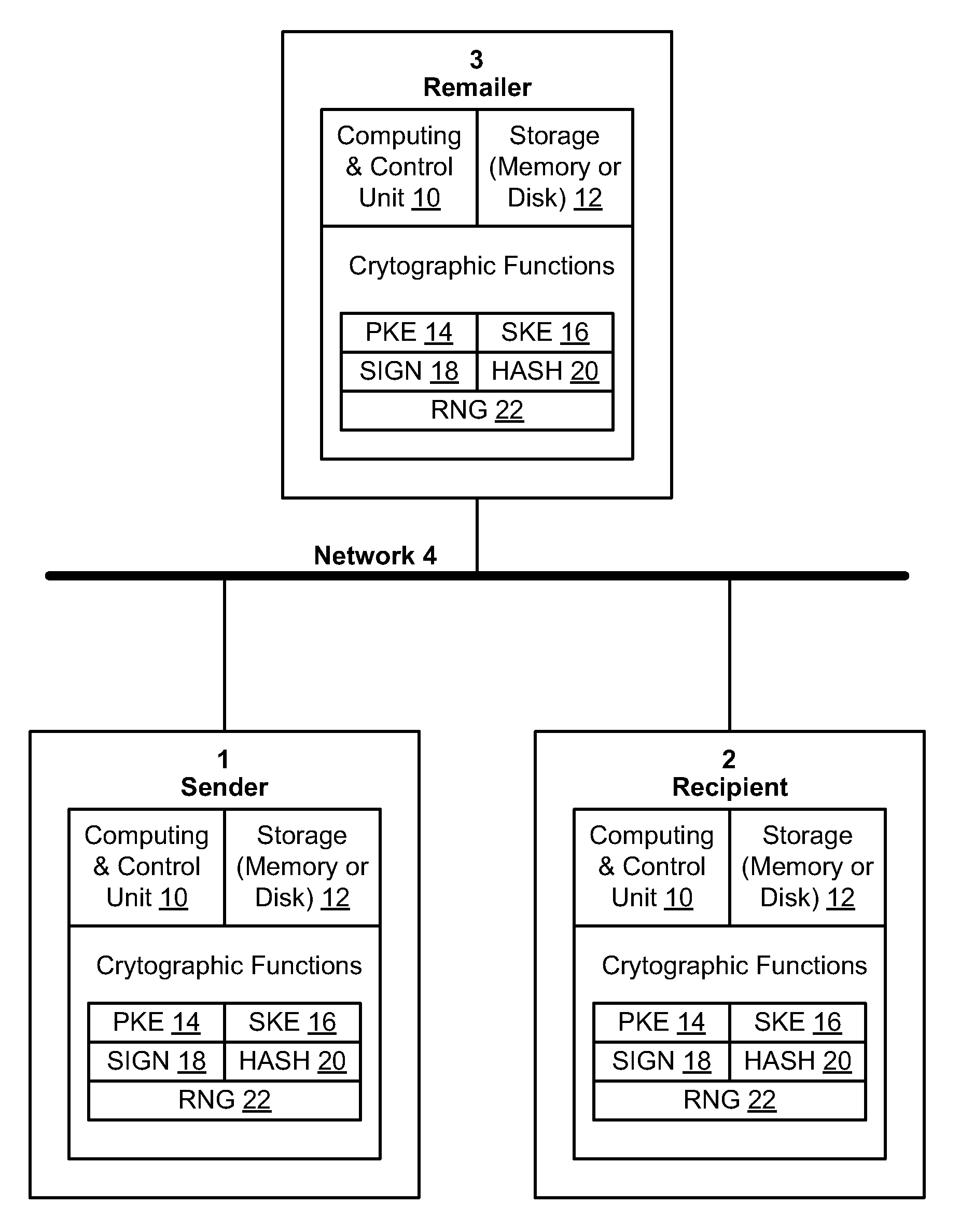
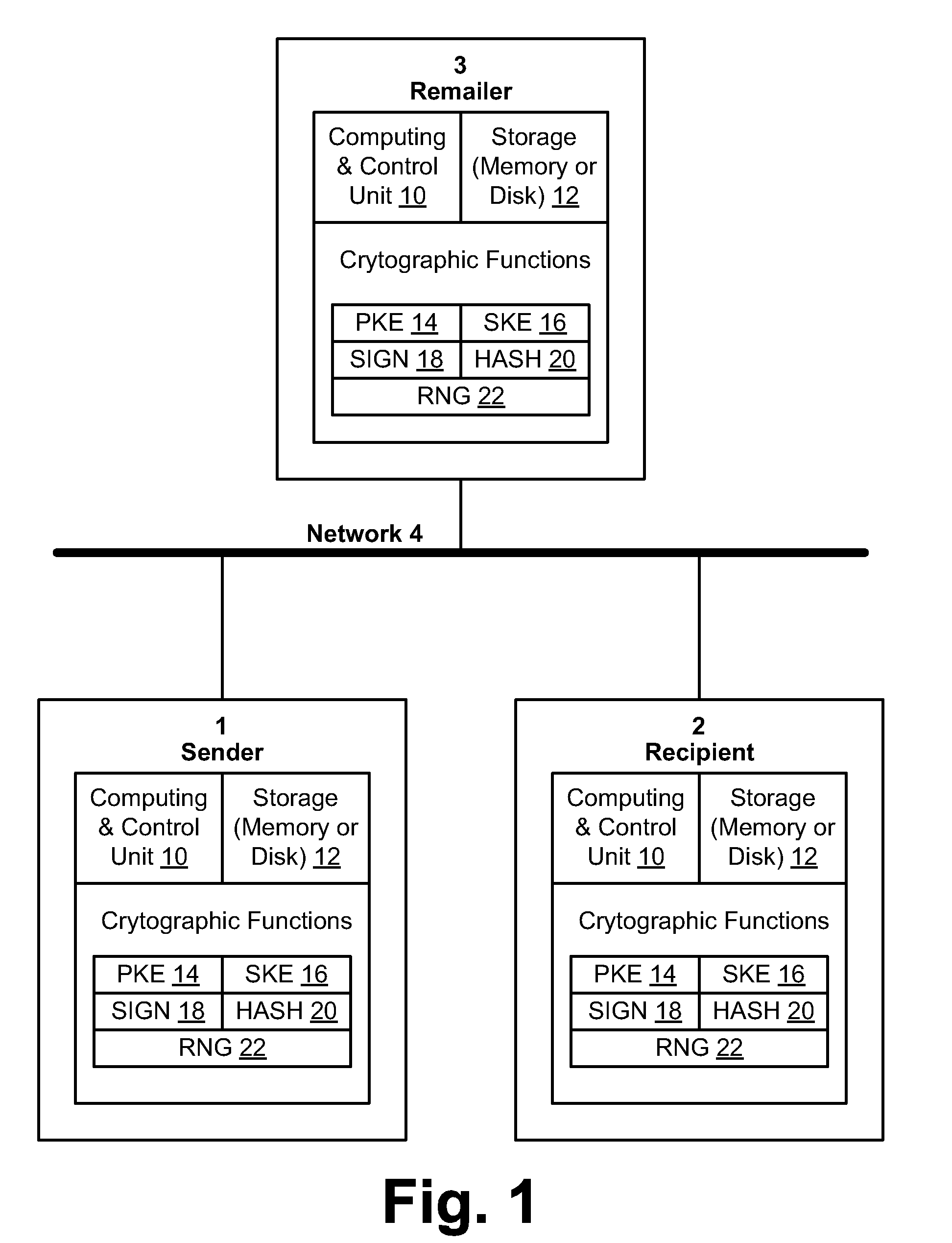
Method and system for binding enhanced software features to a persona
InactiveUS6891953B1Preventing unchecked proliferationKey distribution for secure communicationDigital data processing detailsBiological activationUniform resource locator
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
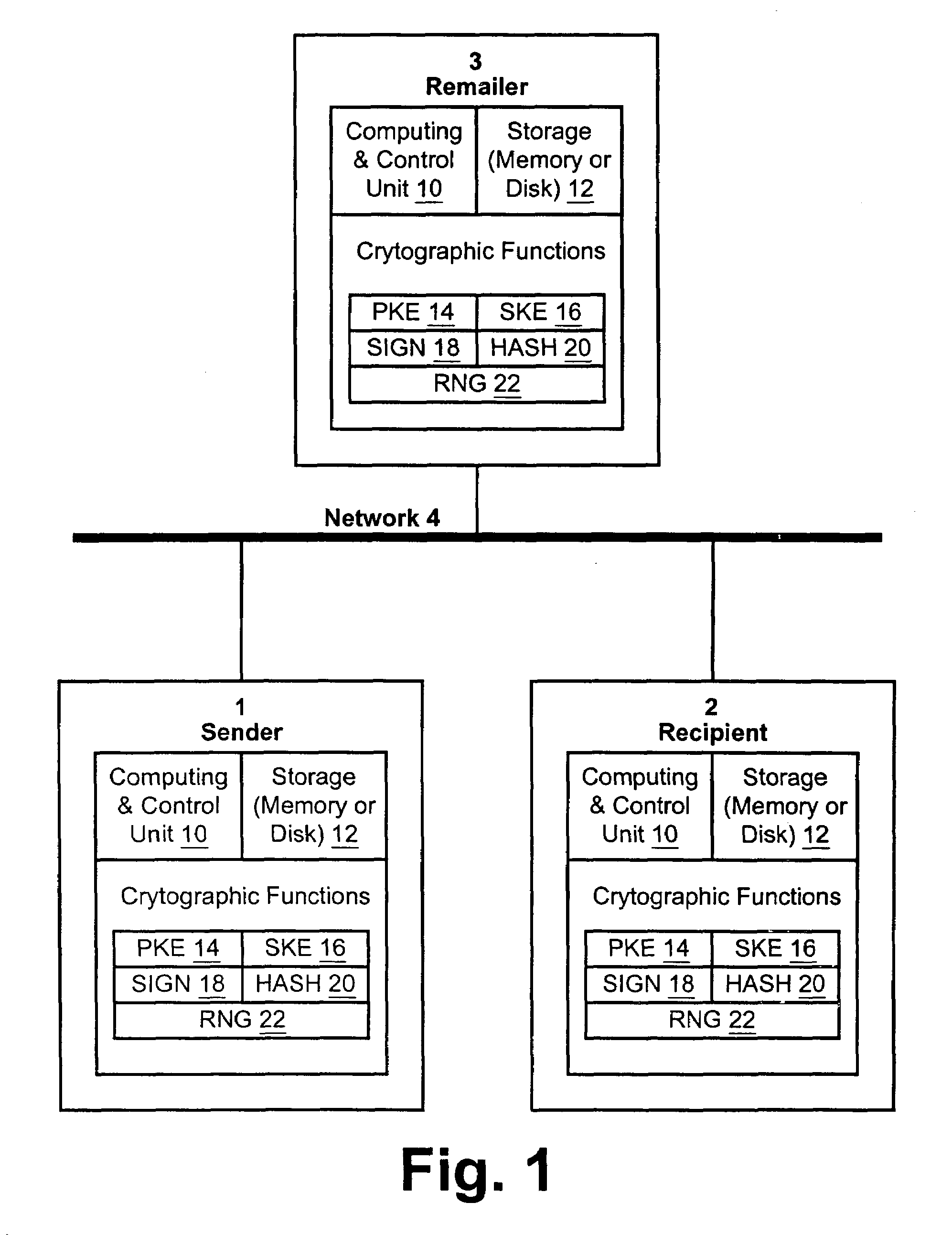
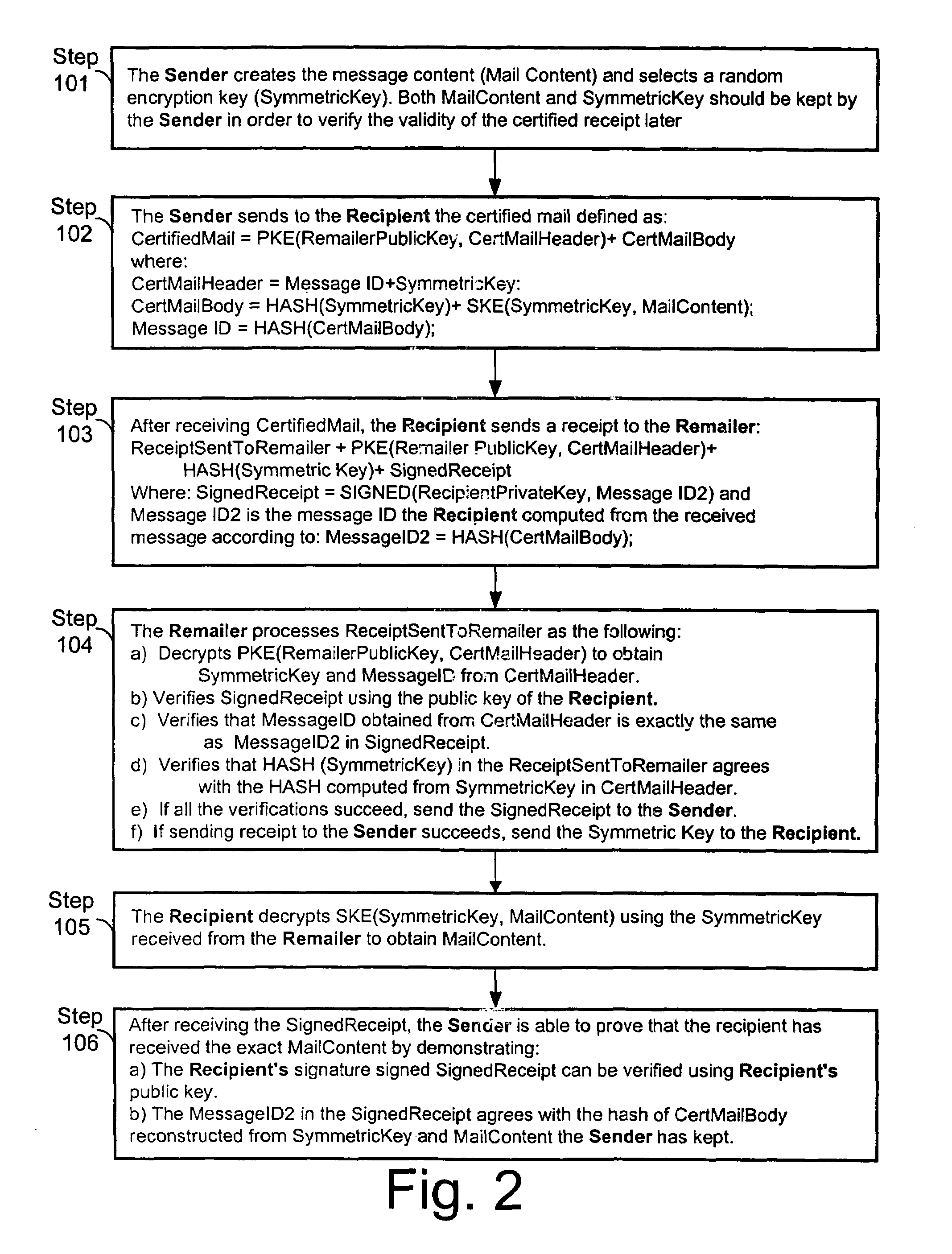
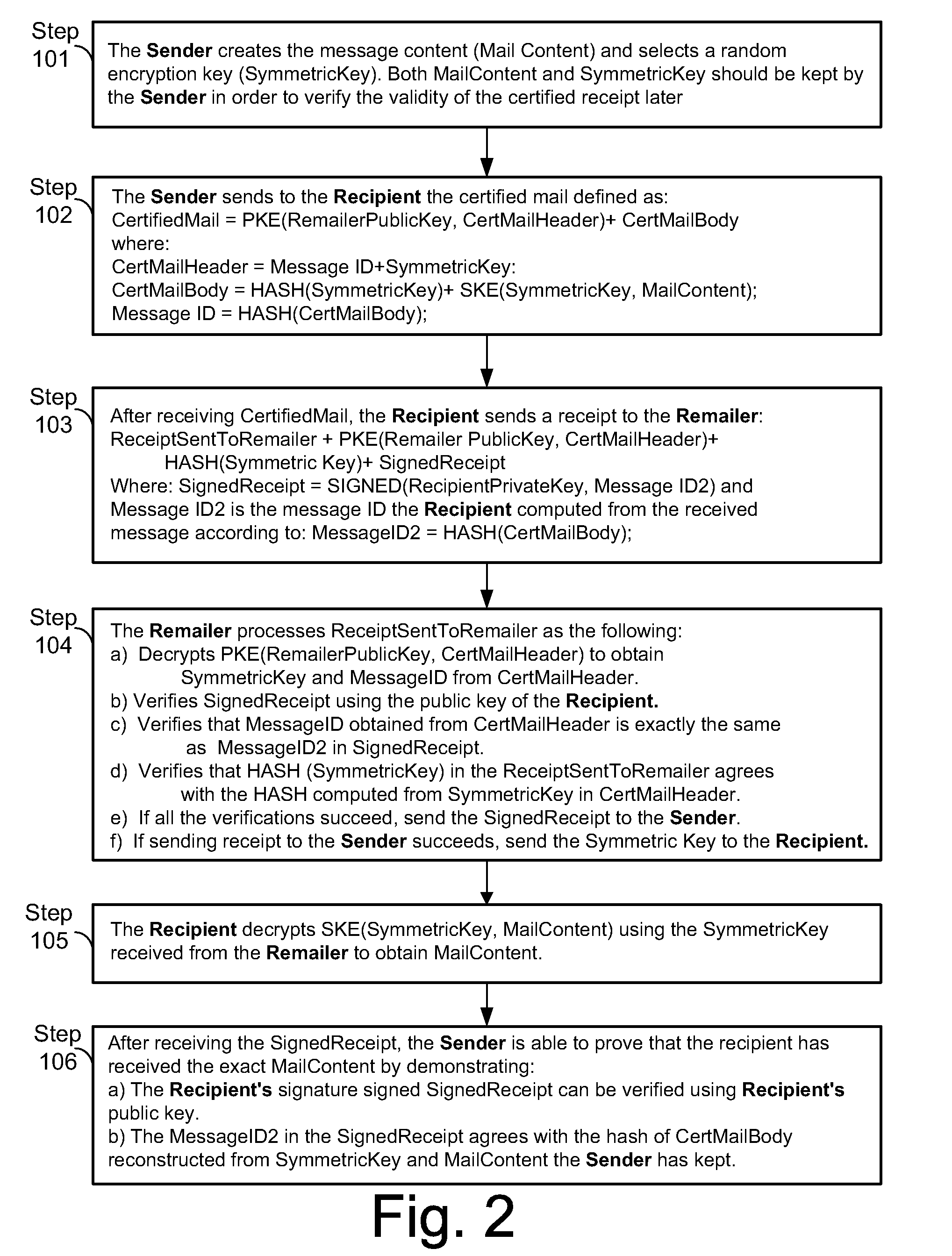
Certified transmission system
InactiveUS7353204B2Improve security featuresKey distribution for secure communicationComputer security arrangementsThird partySymmetric-key algorithm
The invention provides a method and apparatus for transmitting a message from a sender to an intended recipient. The method includes encrypting a message using a symmetric key, sending the encrypted message to an intended recipient without the symmetric key and providing the symmetric key to a third party. If the intended recipient signs and returns to the third party a receipt for the message, the method includes transferring, by the third party, the receipt to the sender and providing the symmetric key to the intended recipient.
Owner:ZIX CORP
Server for an electronic distribution system and method of operating same
ActiveUS7047411B1Preventing unchecked proliferationKey distribution for secure communicationUser identity/authority verificationStore and forwardDigital rights management system
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content items, the retail site transmits to the purchase a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon the following the link, the fulfillment site downloads the ordered content to the consumer preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enable those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
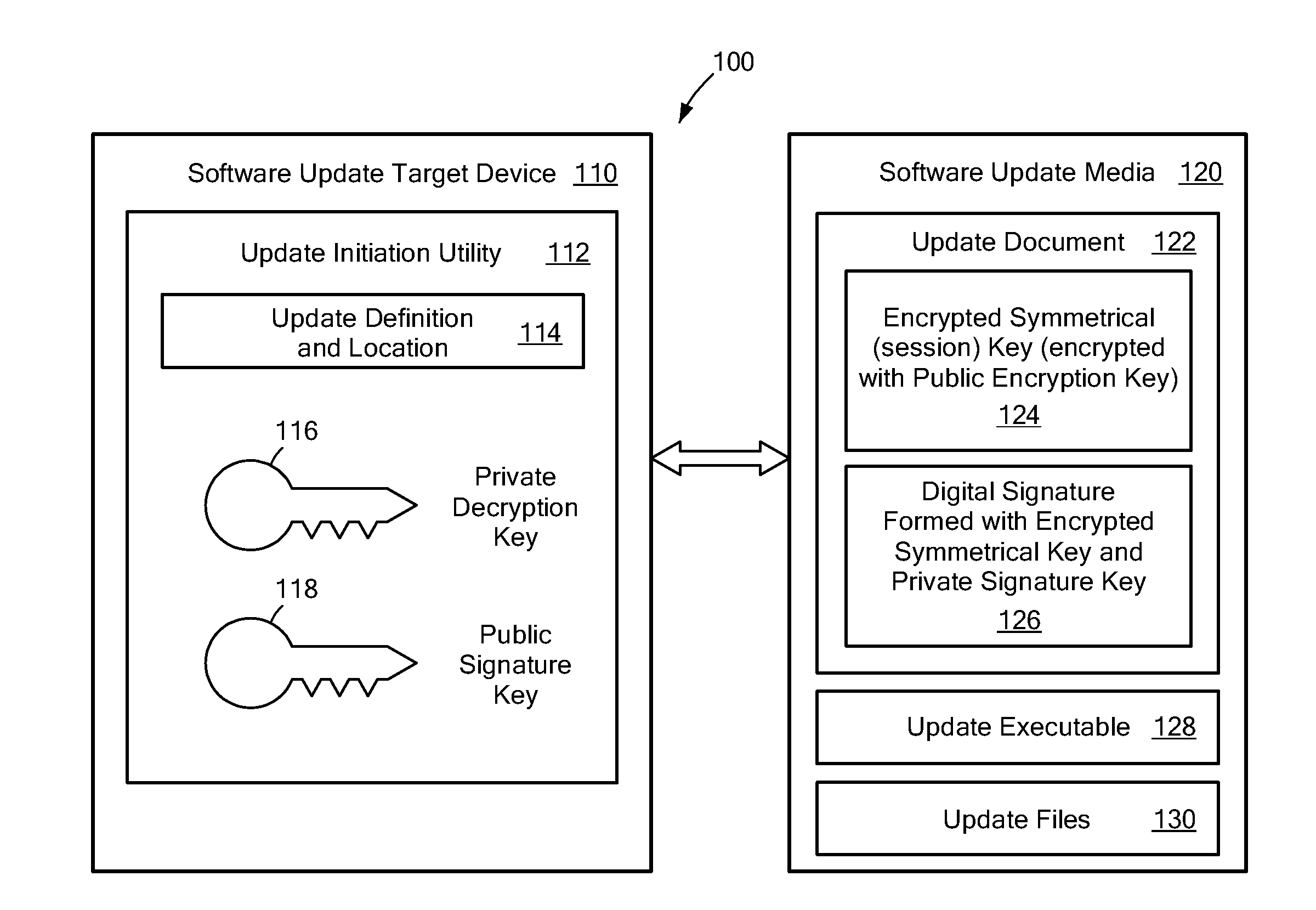
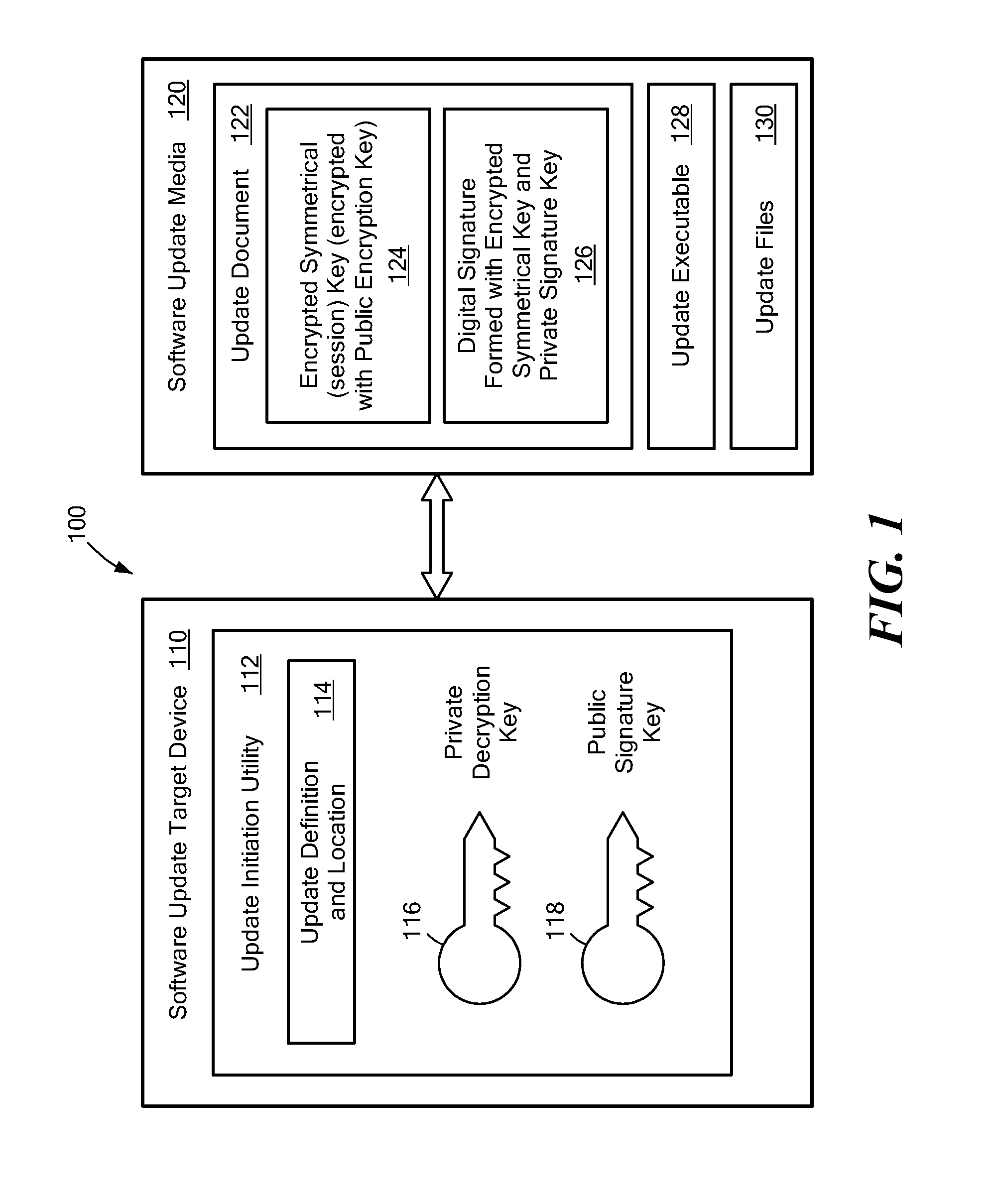
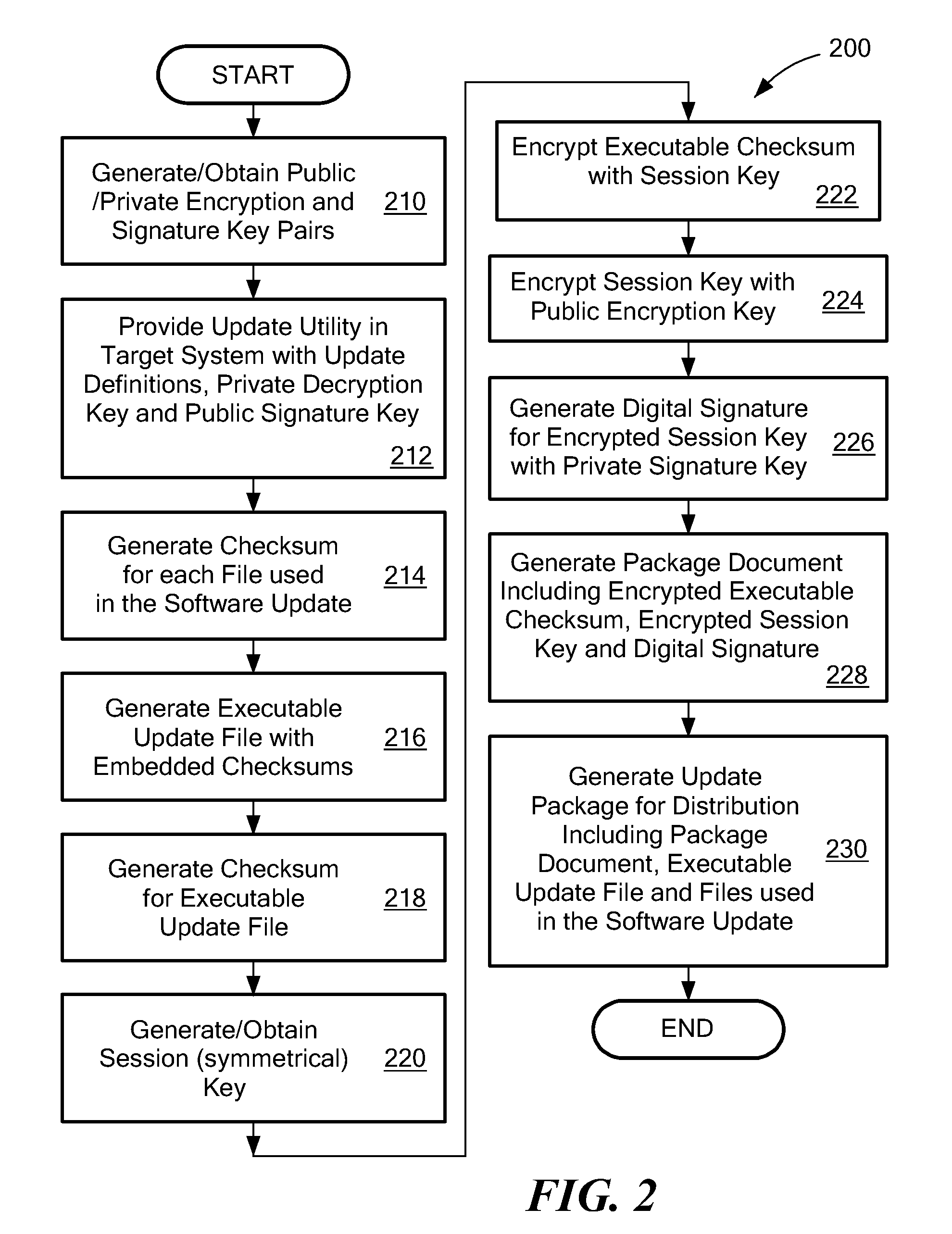
System and Method for Secure Software Update
ActiveUS20130318357A1User identity/authority verificationDigital data protectionThird partySecurity software
A secure software update provides an update utility with an update definition, a private encryption key and a public signature key to a target device. A software update package is prepared on portable media that includes an executable update program, a checksum for the program that is encrypted with a symmetrical key, an encrypted symmetrical key that is encrypted with a public encryption key and a digital signature prepared with a private signature key. The update process authenticates the digital signature, decrypts the symmetrical key using the private encryption key, and decrypts the checksum using the symmetrical key. A new checksum is generated for the executable update program and compared to the decrypted checksum. If inconsistencies are detected during the update process, the process is terminated. Otherwise, the software update can be installed with a relatively high degree of assurance against corruption, viruses and third party interference.
Owner:SIEMENS HEALTHCARE DIAGNOSTICS INC
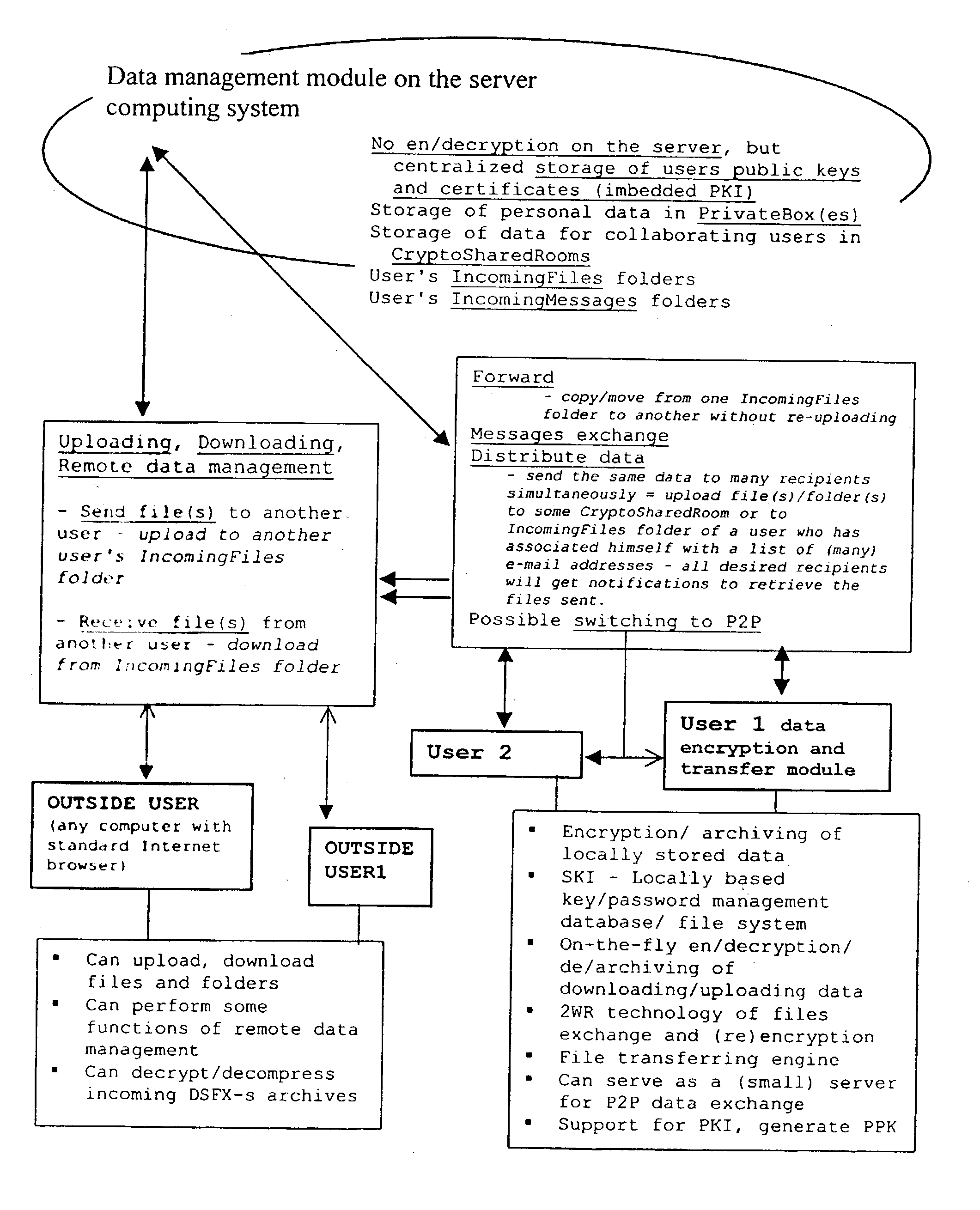
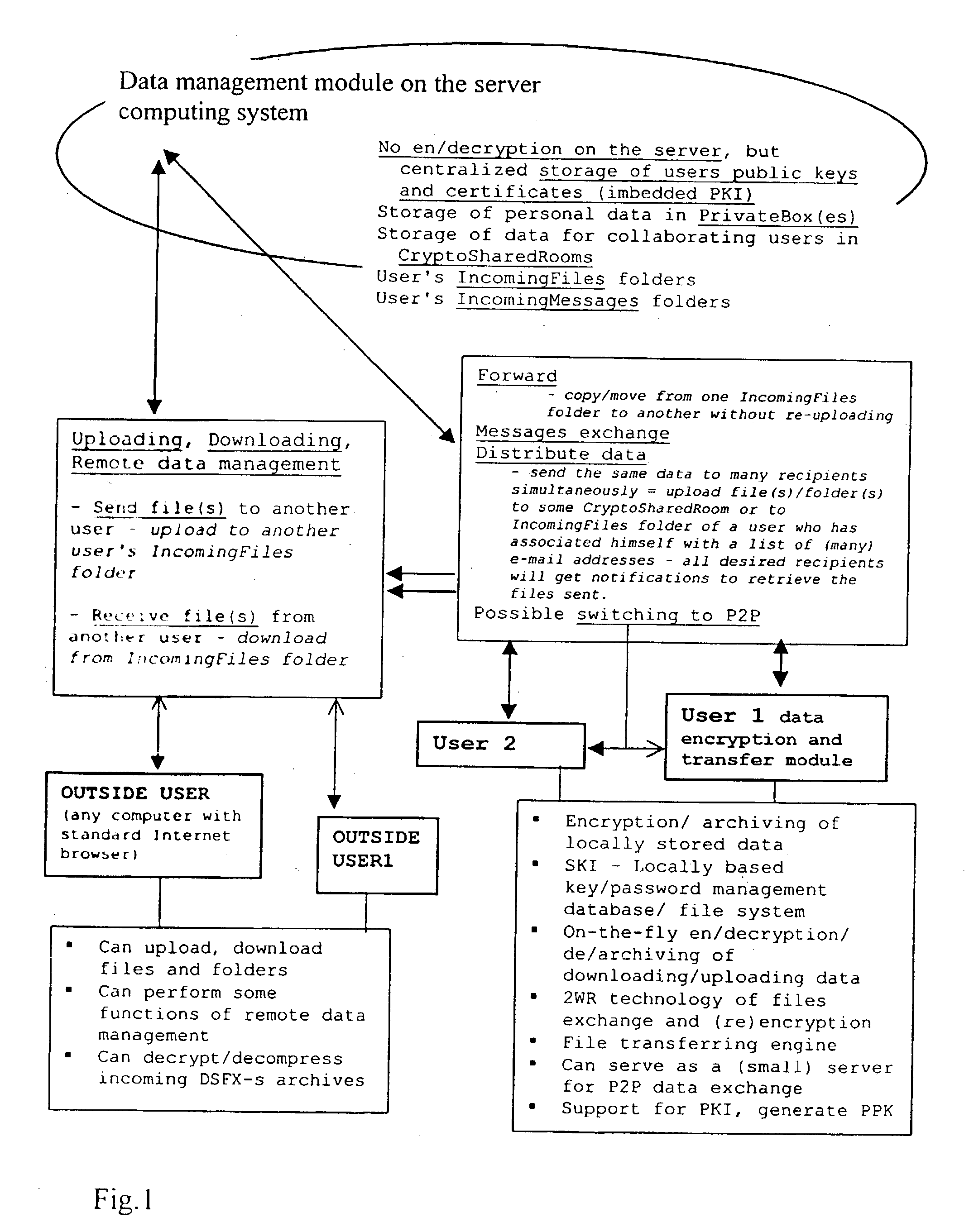
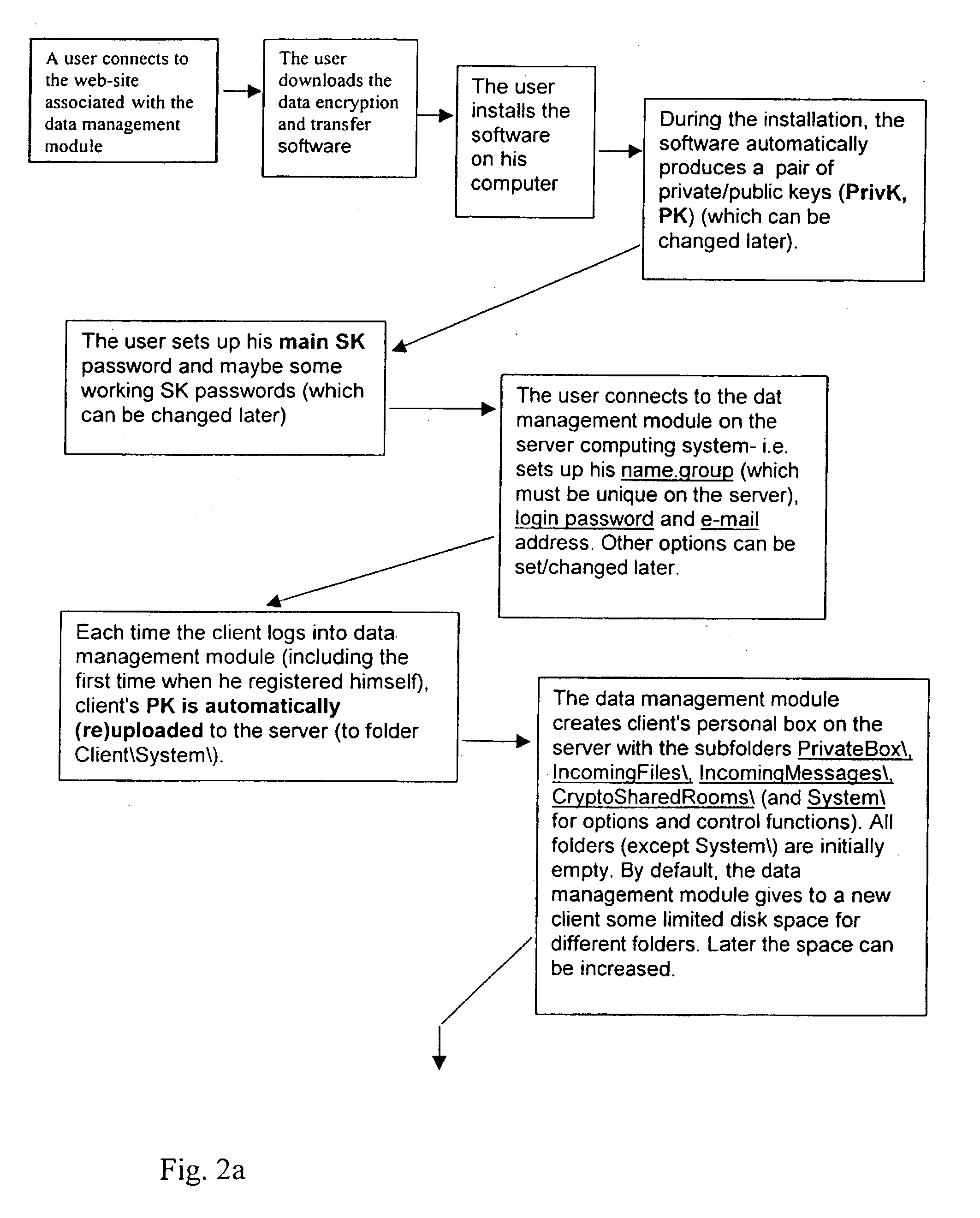
Data transfer and management system
InactiveUS20030177422A1Easily and securely managedEasily downloadableReliability increasing modificationsError preventionMegabyteData file
A system for the secure transfer of data and data management on the Internet has a data encryption and transfer module operable in a user computing system, a data management module operable in a server computing system, the transfer of data between the user and server computing systems being effected on the user computing system through use of the data encryption and transfer module, by moving the data to or from a first desktop window, associated with the user computing system, from or to a second desktop window, associated with the server computing system, each window being associated with a password, such that the step of moving the data from one window to the other causes the data to be encrypted / re-encrypted from one associated password to the other. The system also includes a password management module operable in the user computing system for managing the passwords, which are required to be used by a user of the system. The system uses symmetric key encryption coupled with file transfer protocol (FTP) data transfer and allows for the secure transfer of large data files of 100 megabytes or more.
Owner:HERBERT STREET TECH
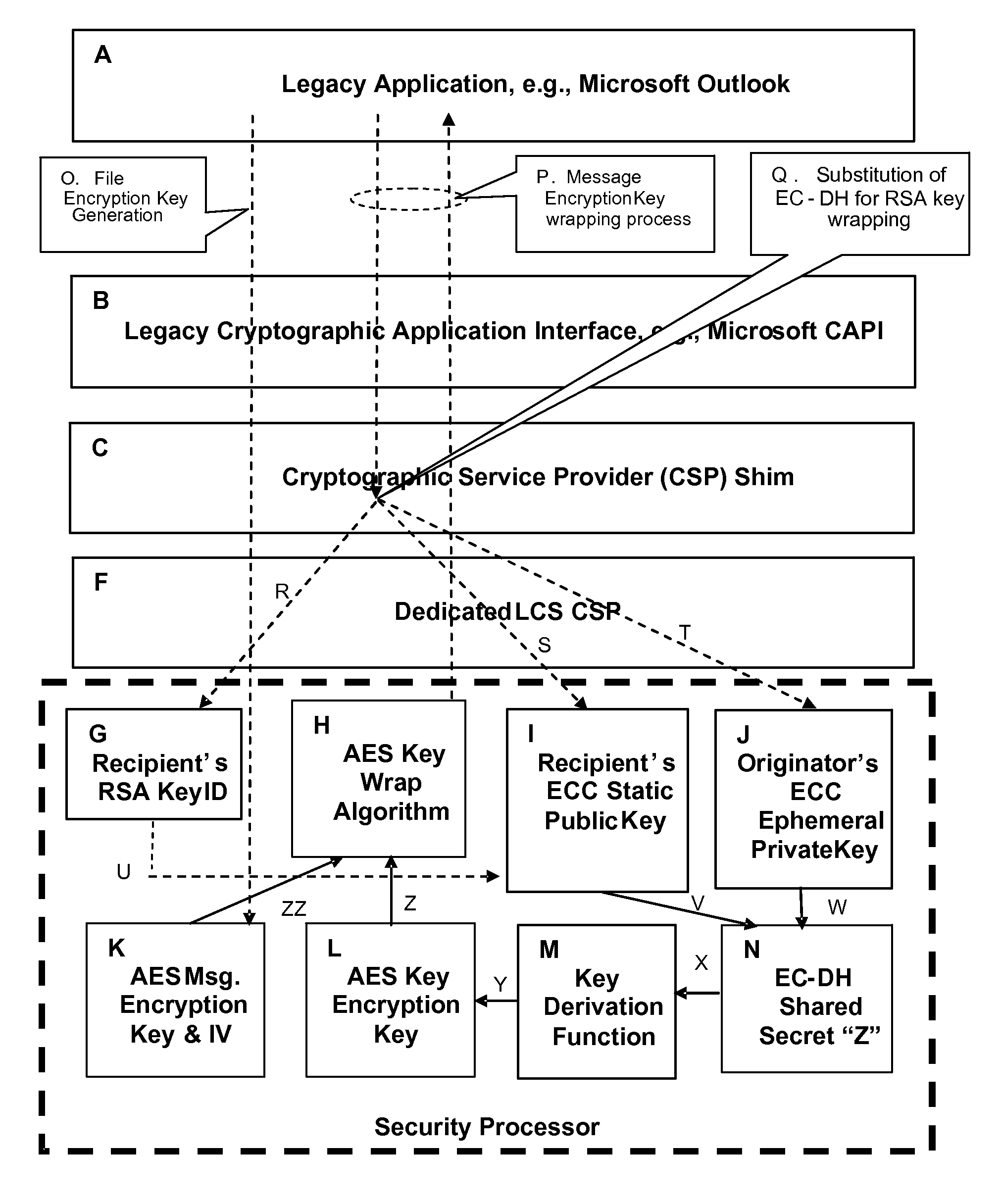
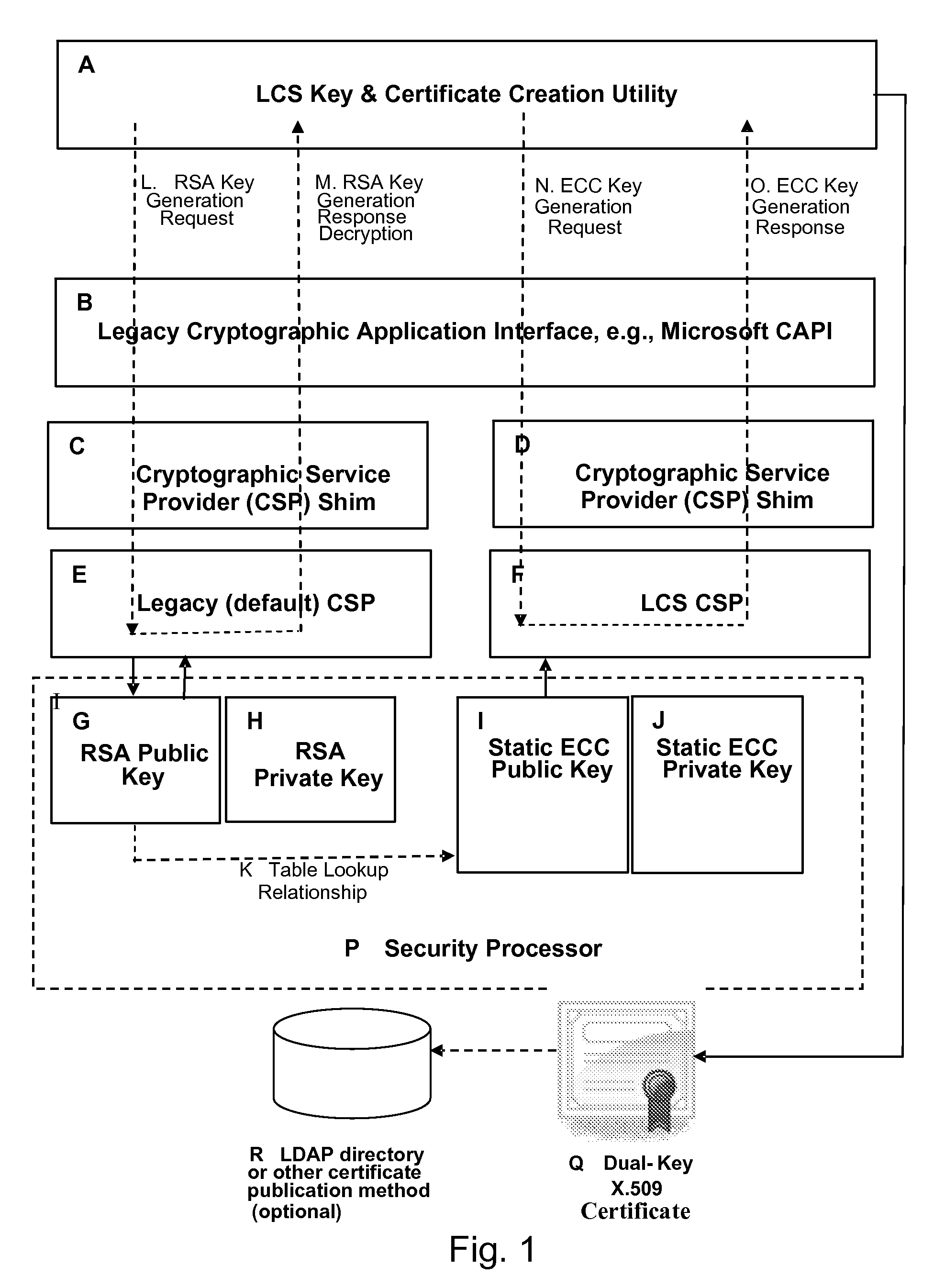
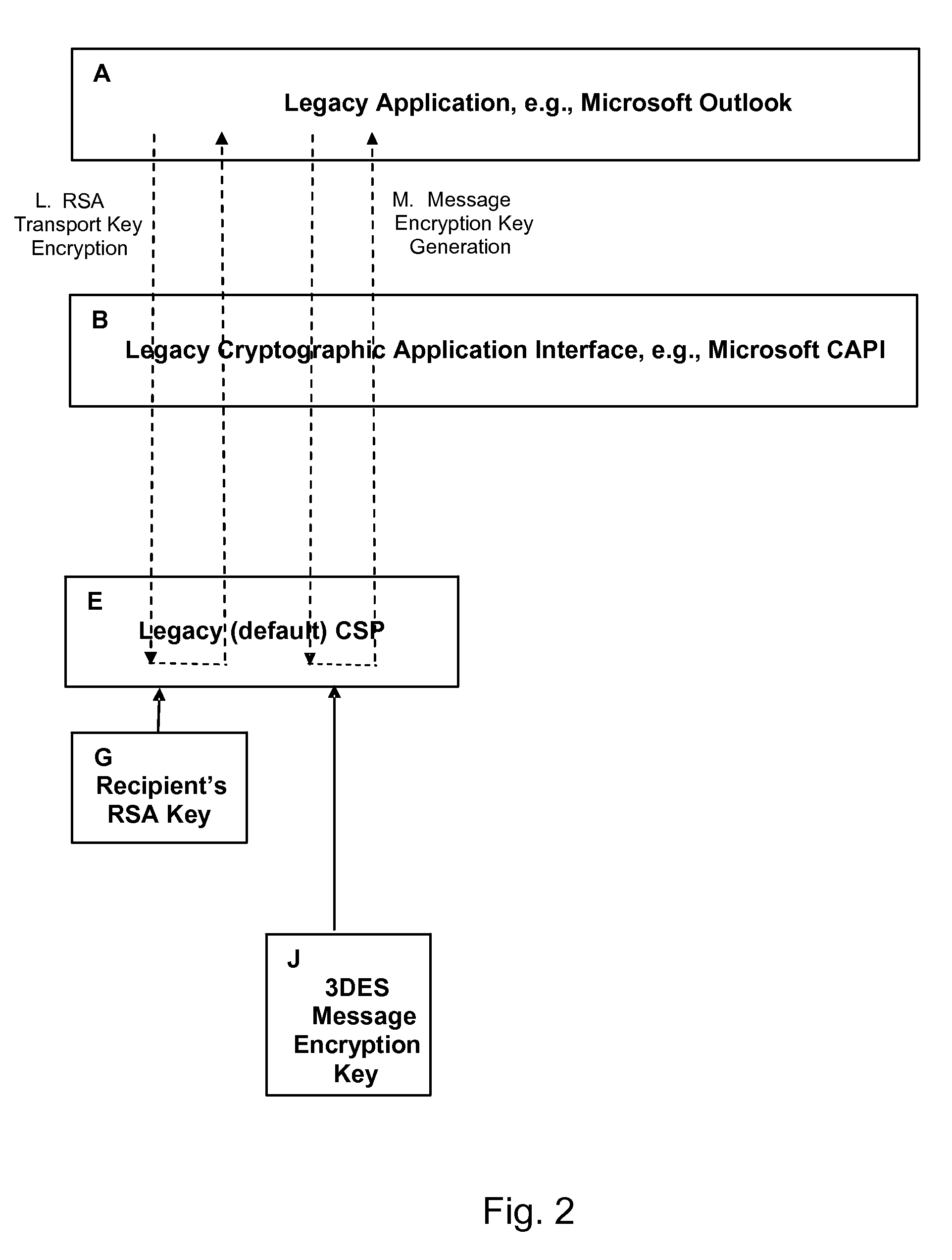
Method and System for Deploying Advanced Cryptographic Algorithms
InactiveUS20080130895A1Key distribution for secure communicationMultiple keys/algorithms usageOperational systemHash function
A method and system for deploying a suite of advanced cryptographic algorithms that includes: providing a legacy cryptographic interface that is associated with a legacy operating system and a legacy application, and supports a suite of legacy cryptographic algorithms; providing a suite of advanced cryptographic algorithms that includes one or more of an advanced asymmetric key algorithm, an advanced symmetric key algorithm, and / or an advanced hash function; providing an advanced cryptographic interface that is independent of the legacy operating system and the legacy application, backwards compatible with the legacy cryptographic interface, and capable of supporting the suite of advanced cryptographic algorithms; and transparently and automatically substituting the suite of advanced cryptographic algorithms for the legacy cryptographic algorithms through the invocation of the advanced cryptographic interface at the time of an initial performance of encrypting, hashing, digitally signing the hash of, decrypting, re-hashing, and / or validating the digital signature of an item.
Owner:SPEX TECH
Inter-server communication using request with encrypted parameter
InactiveUS6970849B1Preventing unchecked proliferationDigital data processing detailsUser identity/authority verificationUniform resource locatorBiological activation
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
Password triggered trusted encrytpion key deletion
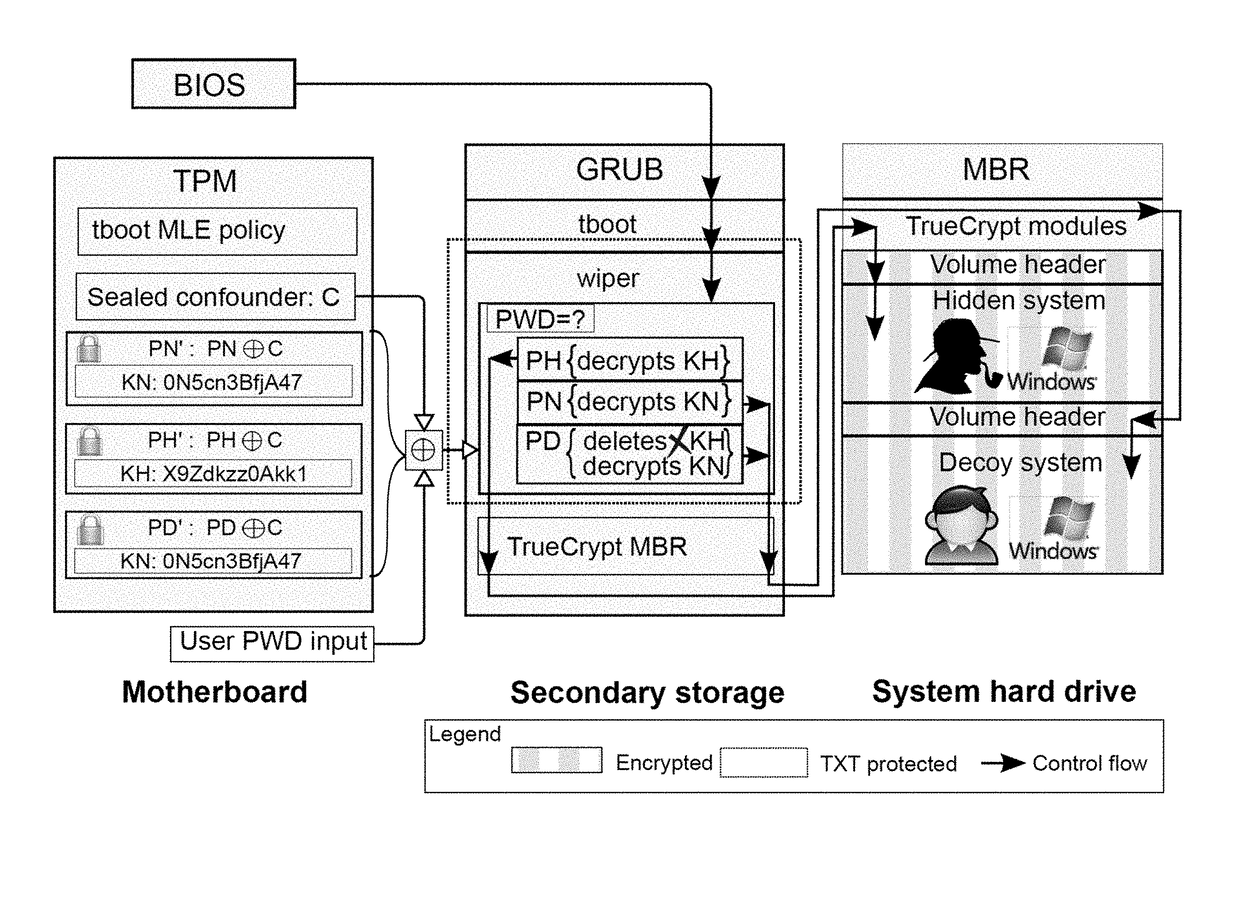
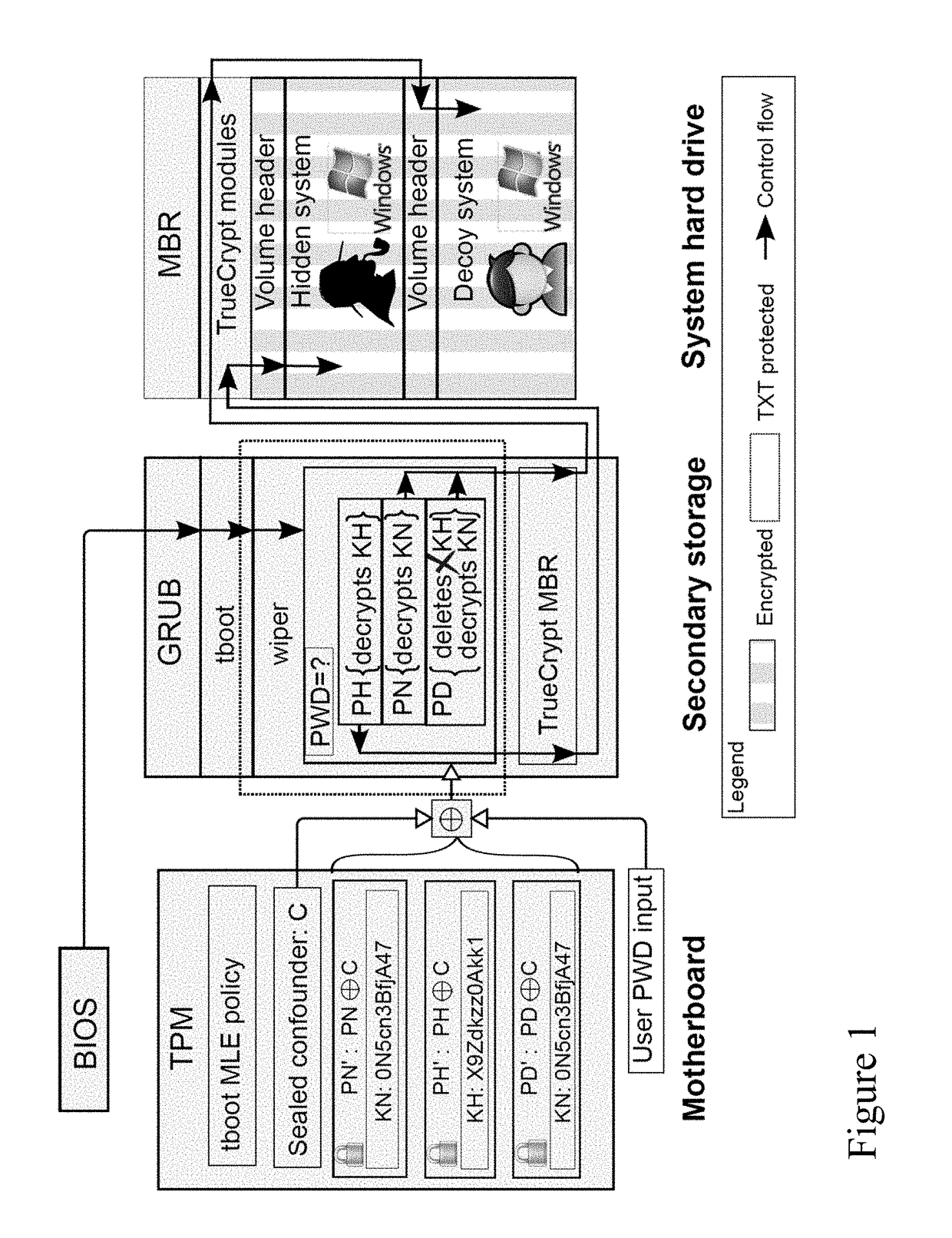
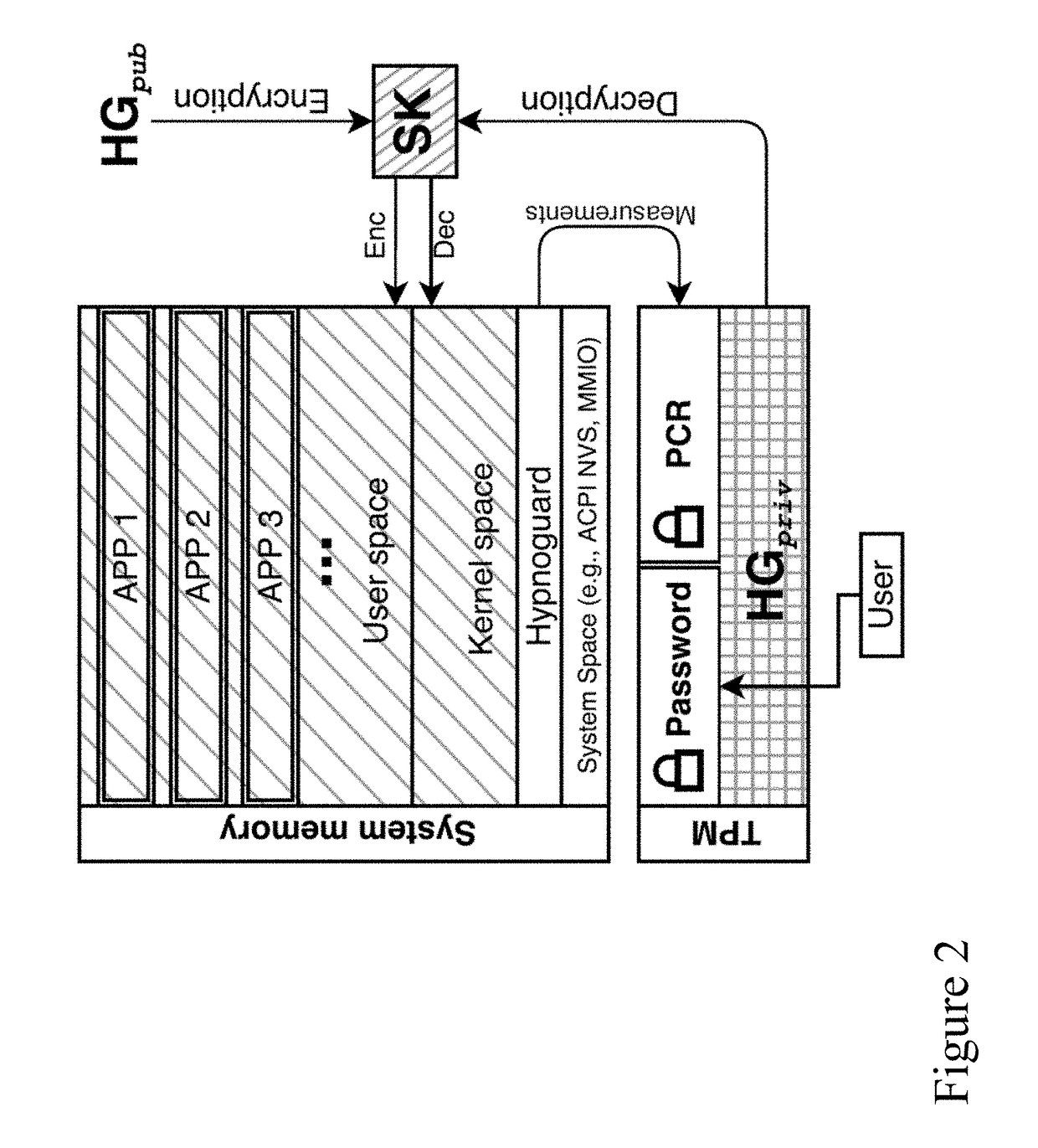
ActiveUS20170230179A1Reduce restrictionsGood plausibilityKey distribution for secure communicationDigital data protectionGraphicsPassword
Owner:MANNAN MOHAMMAD
Method and apparatus for re-encrypting data in a transaction-based secure storage system
ActiveUS7792300B1Digital data processing detailsUser identity/authority verificationFile systemData access
A method for re-encrypting encrypted data in a secure storage file system, including obtaining selected data to re-encrypt from the secure storage file system using a user data access record and the encrypted data, decrypting the selected data using a symmetric key, re-encrypting the selected data using a new symmetric key to obtain new encrypted data, encrypting the new symmetric key using a public key to obtain a new encrypted symmetric key, storing the new encrypted data and the new encrypted symmetric key if the public key is associated with a file system user having read permission, and storing an encrypted hash data if the file system user has write permission.
Owner:ORACLE INT CORP
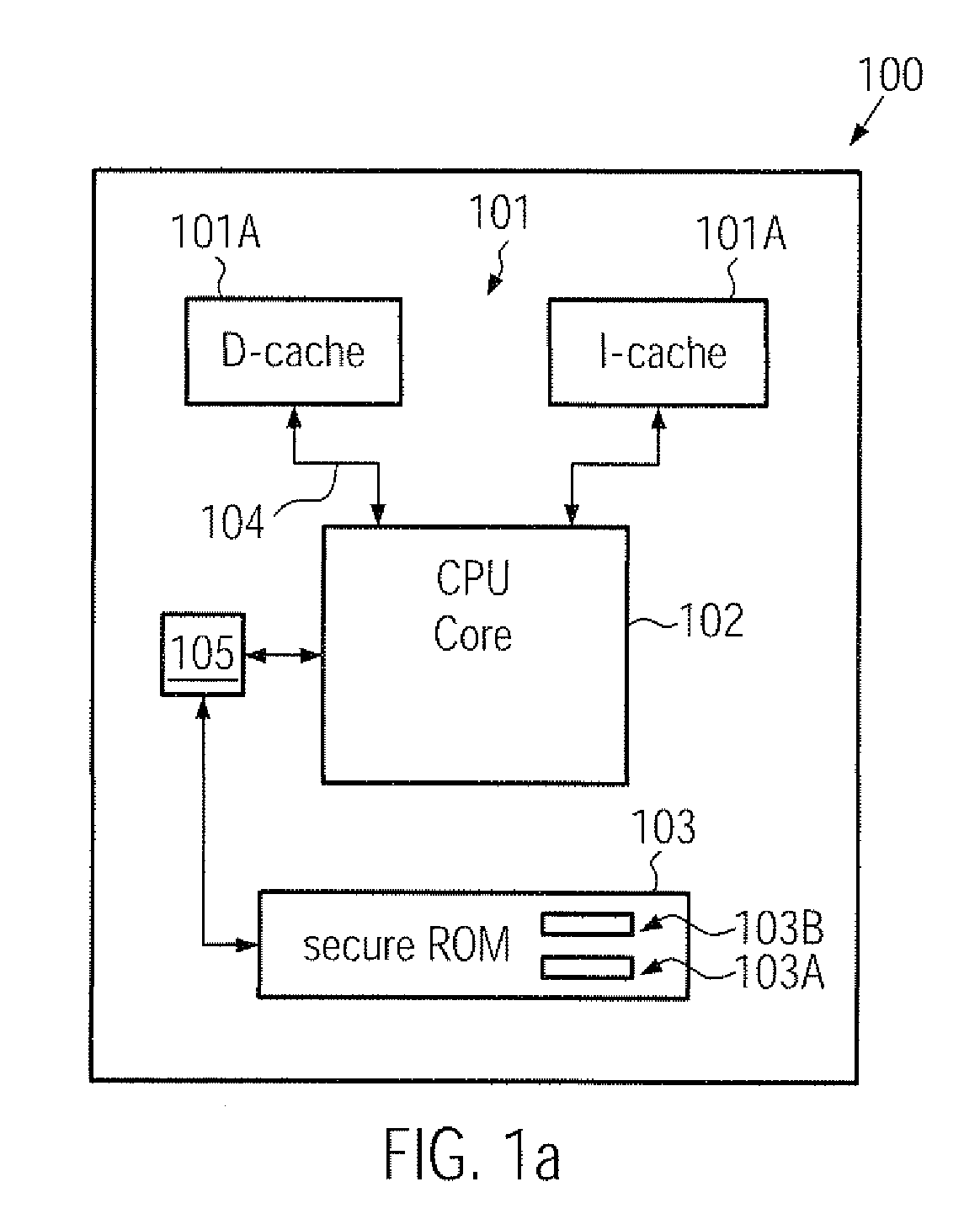
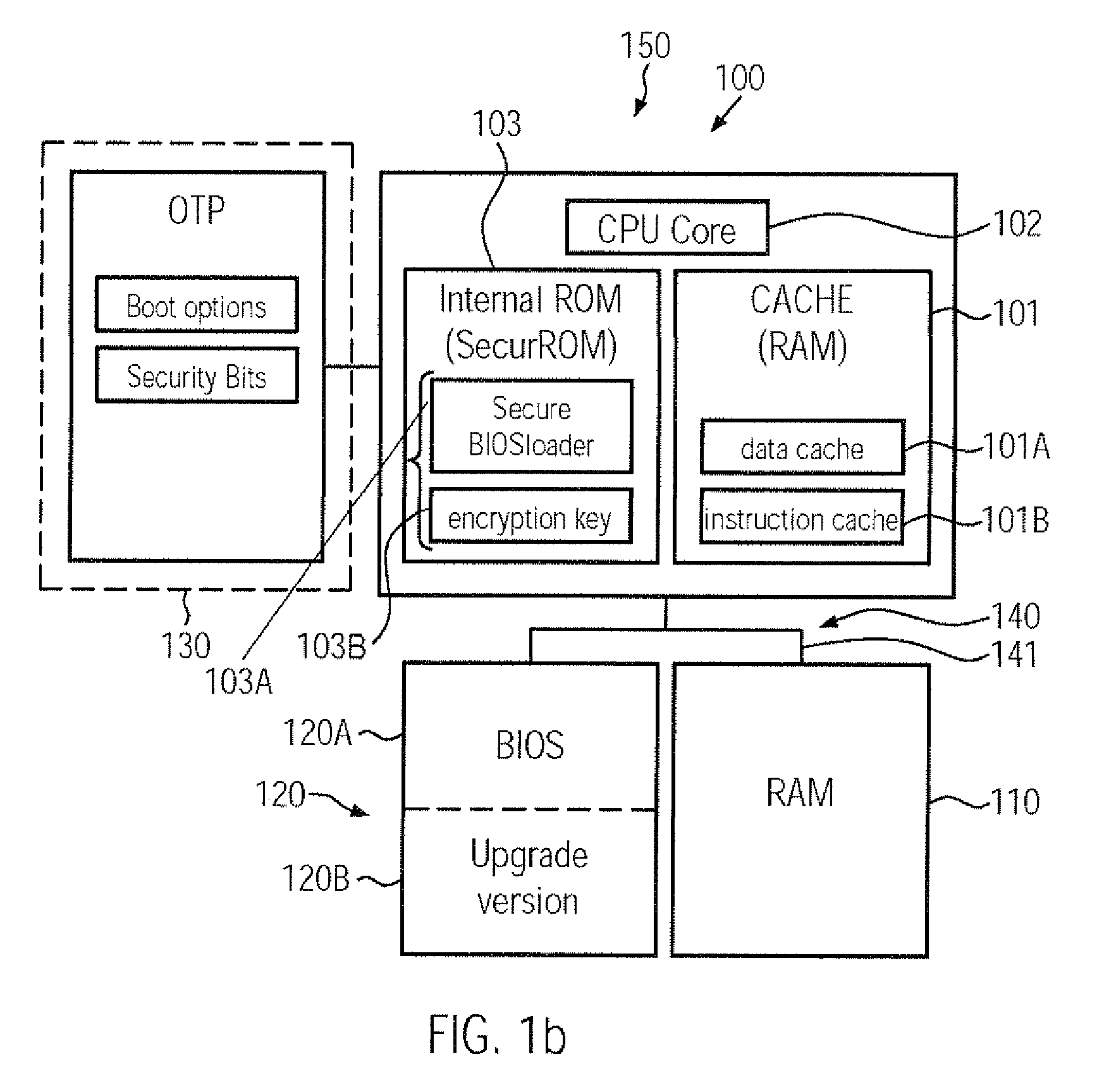
Computer system comprising a secure boot mechanism on the basis of symmetric key encryption
ActiveUS20090276617A1Improve integrityHigh protection levelUser identity/authority verificationDigital computer detailsCryptographic key generationComputerized system
A CPU, a computer system and a secure boot mechanism are provided in which a symmetric encryption key may be incorporated into a non-volatile memory area of the CPU core, thereby substantially avoiding any tampering of the encryption key by external sources. Moreover, pre-boot information may be internally stored in the CPU and may be retrieved upon a reset or power-on event in order to verify a signed boot information on the basis of the internal symmetric encryption key. Furthermore, the BIOS information may be efficiently updated by generating a signature using the internal encryption key.
Owner:MEDIATEK INC
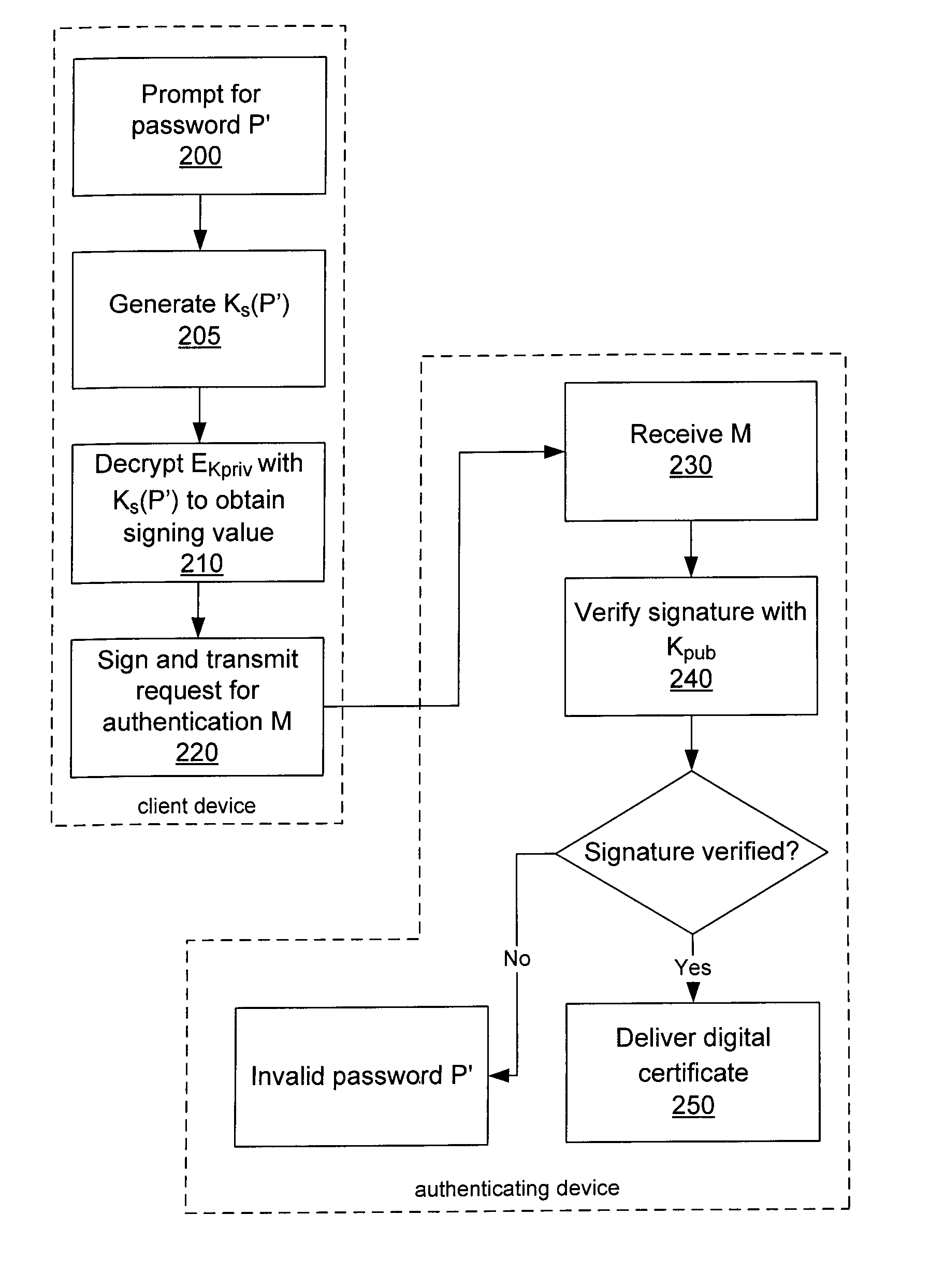
System and method for protecting a password against brute force attacks
ActiveUS20080120504A1User identity/authority verificationCryptographic attack countermeasuresBrute forcePassword
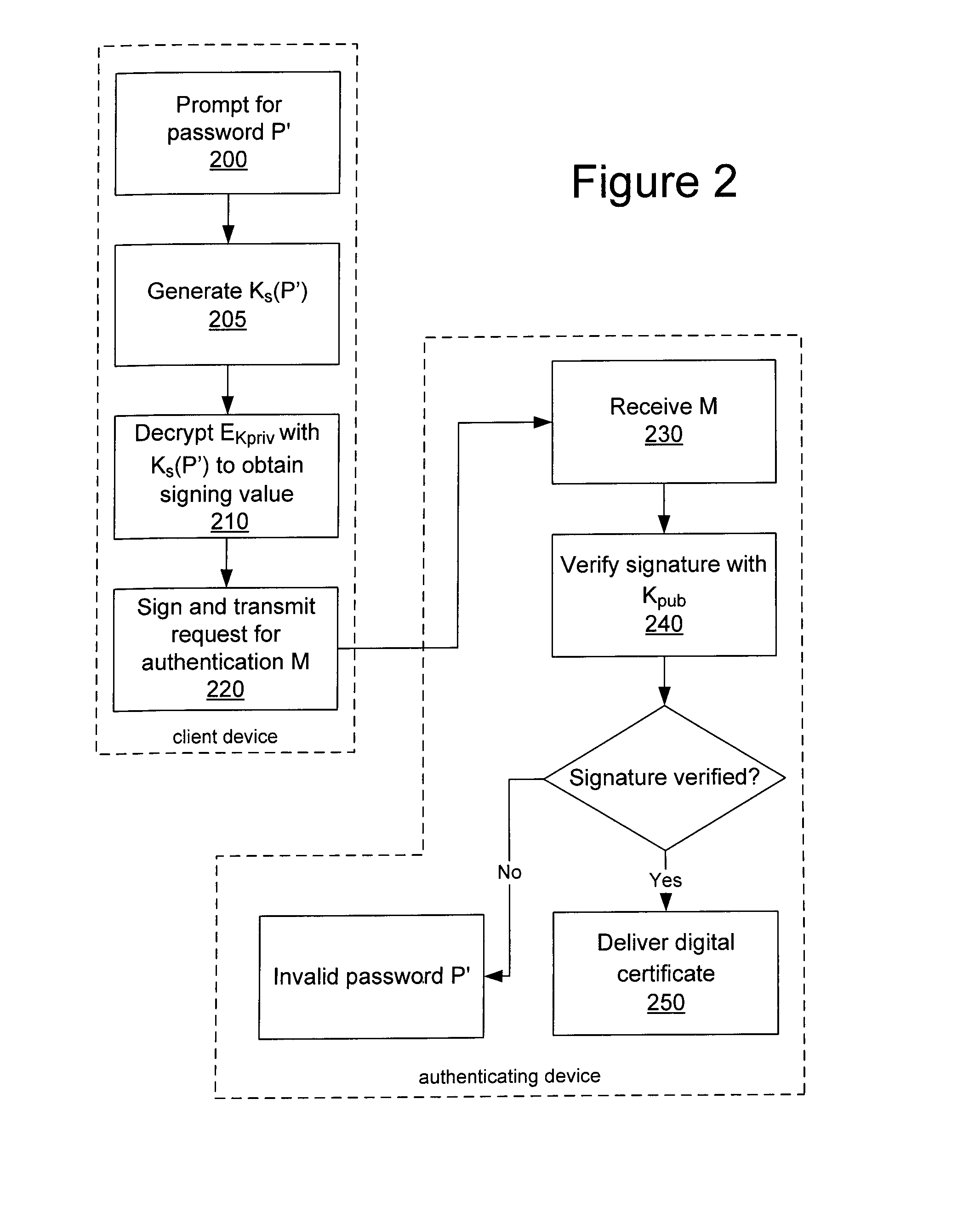
In a system and method for authenticating a client device by an authentication device, the client device user is assigned a PIN generated by the authentication device. The user provides the PIN and a password to the client device, from which the client device generates a symmetric key and further generates a public / private key pair. The private key is encrypted using the symmetric key and stored in encrypted form only. The public key and a message authentication code generated from the PIN are provided to the authentication device, which stores the public key. Subsequently, when the user seeks to be authenticated, the user enters a password at the client device, which is used to generate a symmetric key to decrypt the encrypted private key. A message to the authentication device is signed using the resultant value. The authentication device uses the public key to verify the signature of the message.
Owner:MALIKIE INNOVATIONS LTD
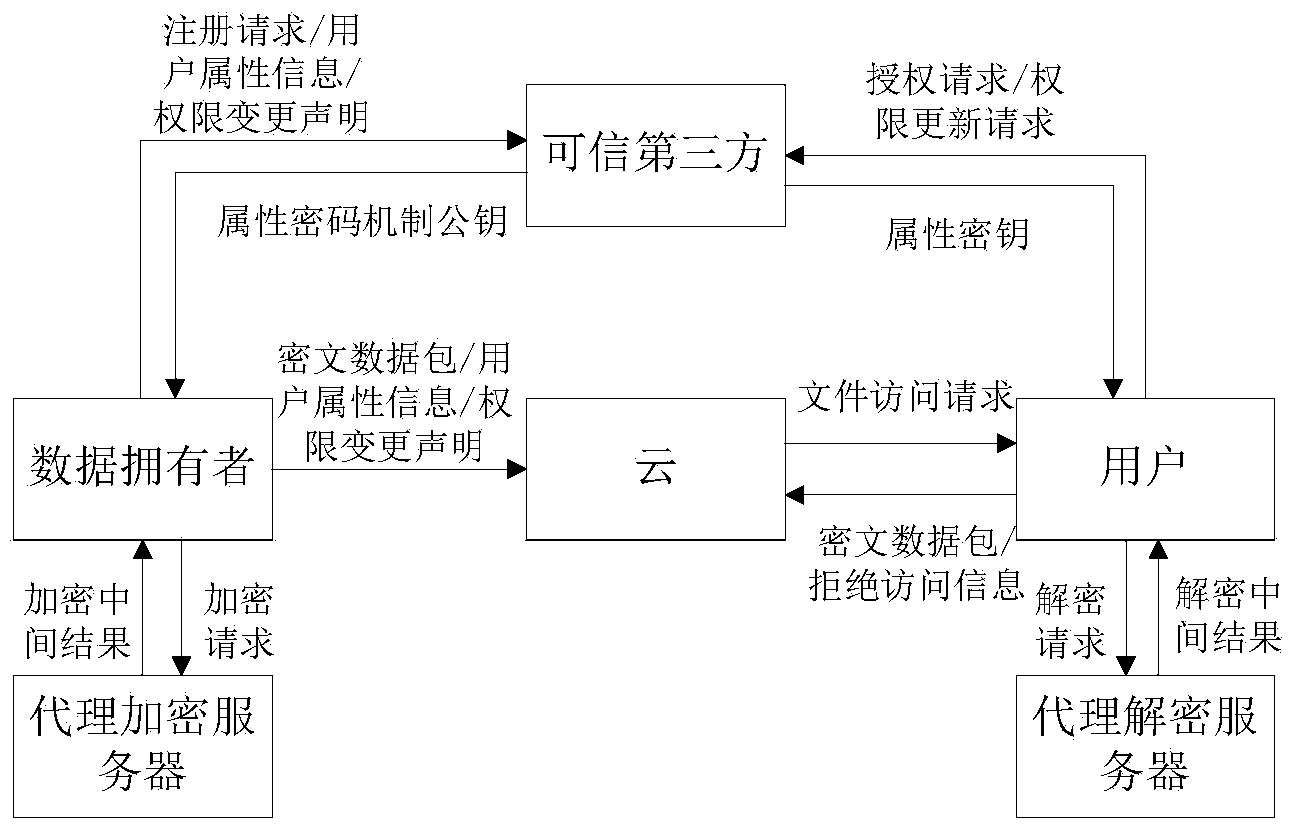
Blockchain-based data cloud storage encryption method and system
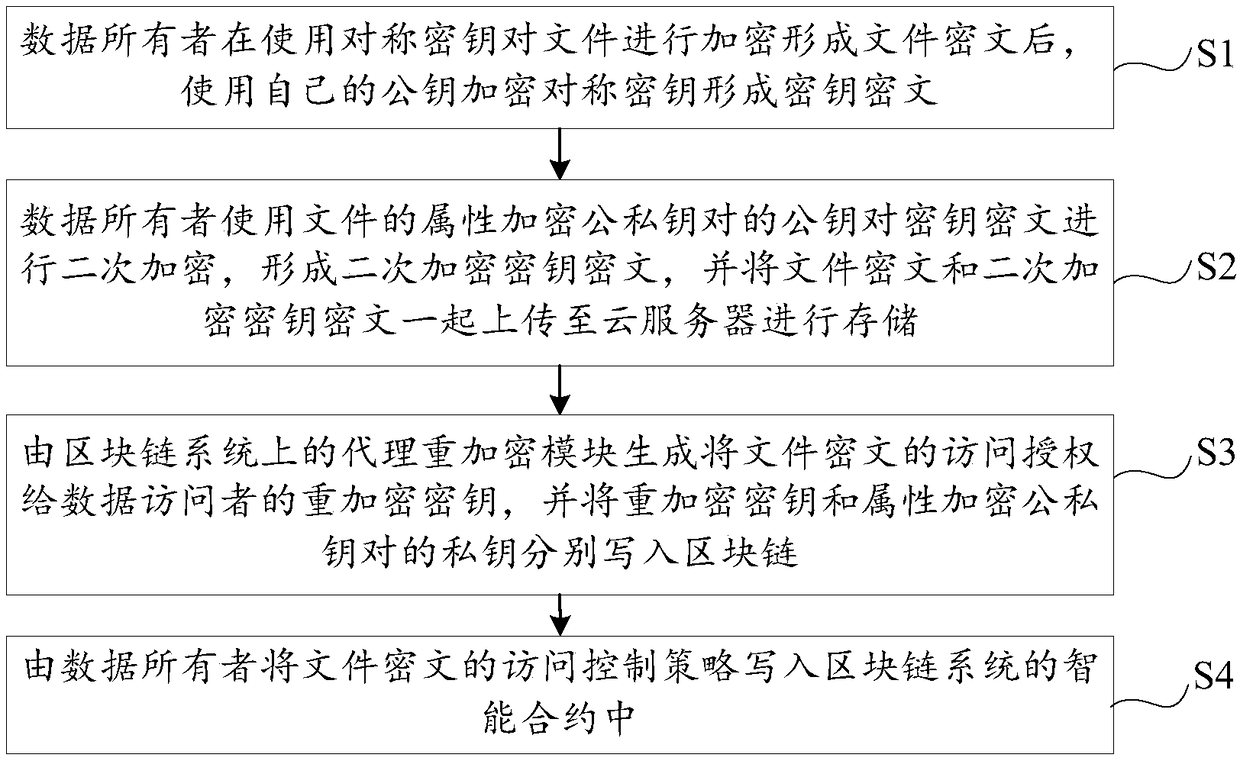
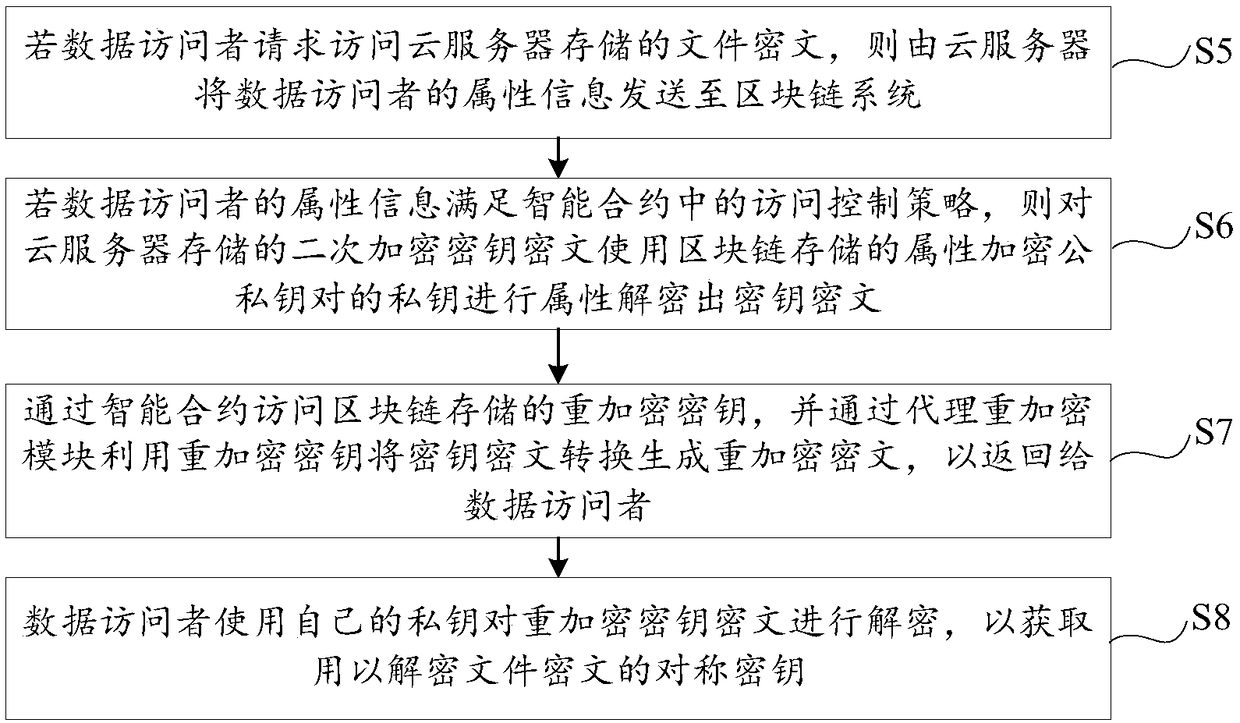
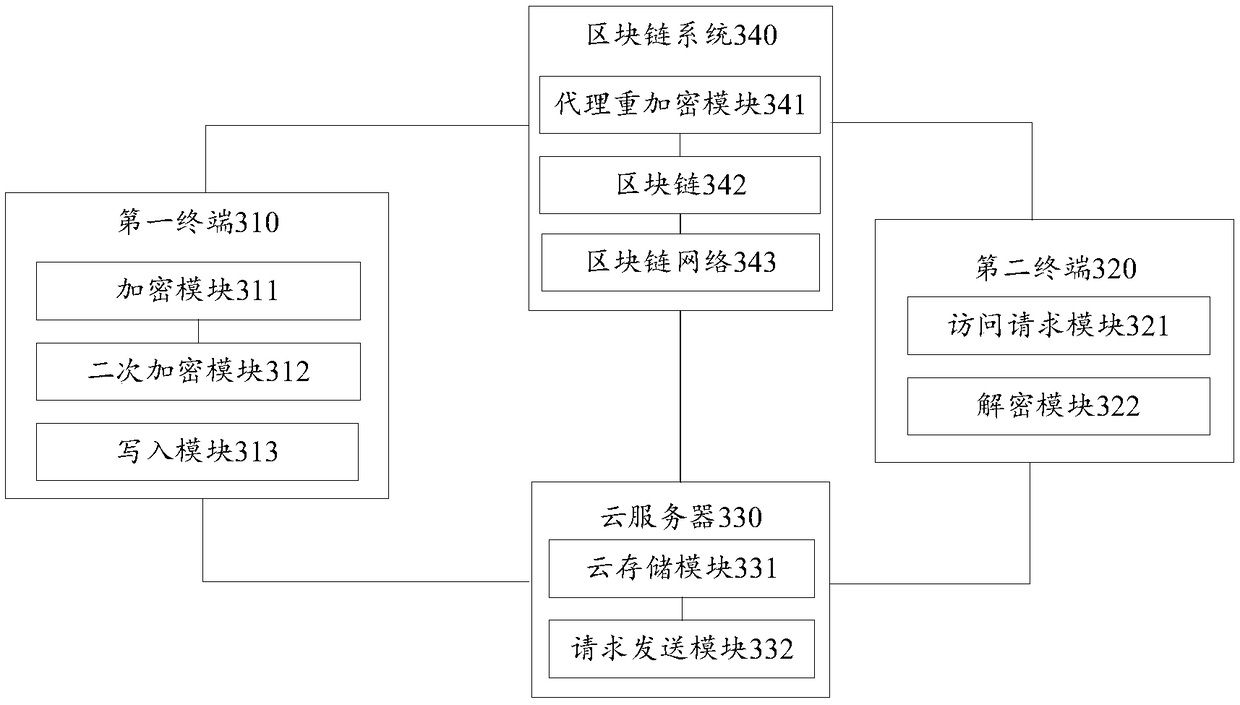
The invention discloses a blockchain-based data cloud storage encryption method and system. The method includes the following steps that: a data owner uses a symmetric key to encrypt a file so as to obtain a file ciphertext, and then, encrypts the symmetric key by using the public key of the data owner so as to obtain a key ciphertext, and the data owner uses the public key of an attribute key pair to perform secondary encryption on the key ciphertext, and stores the file ciphertext and the key ciphertext which has been subjected to secondary encryption to could, wherein the attribute encryption public and private key pair is generated by a proxy re-encryption module; the proxy re-encryption module generates a re-encryption key that authorizes access to the file ciphertext to a data visitor, and writes the re-encryption key and the private key of the attribute encryption public and private key pair into a blockchain; and the data owner writs the access control policy of the file ciphertext into a smart contract. According to the blockchain-based data cloud storage encryption method and system of the embodiments of the invention, the re-encryption technology and the attribute encryption technology are combined, so that the encrypted storage of data files on the cloud can be realized; and the smart contract technology is used to realize the access control of the data on the cloud, and therefore, the privacy and security of the data can be fully guaranteed.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
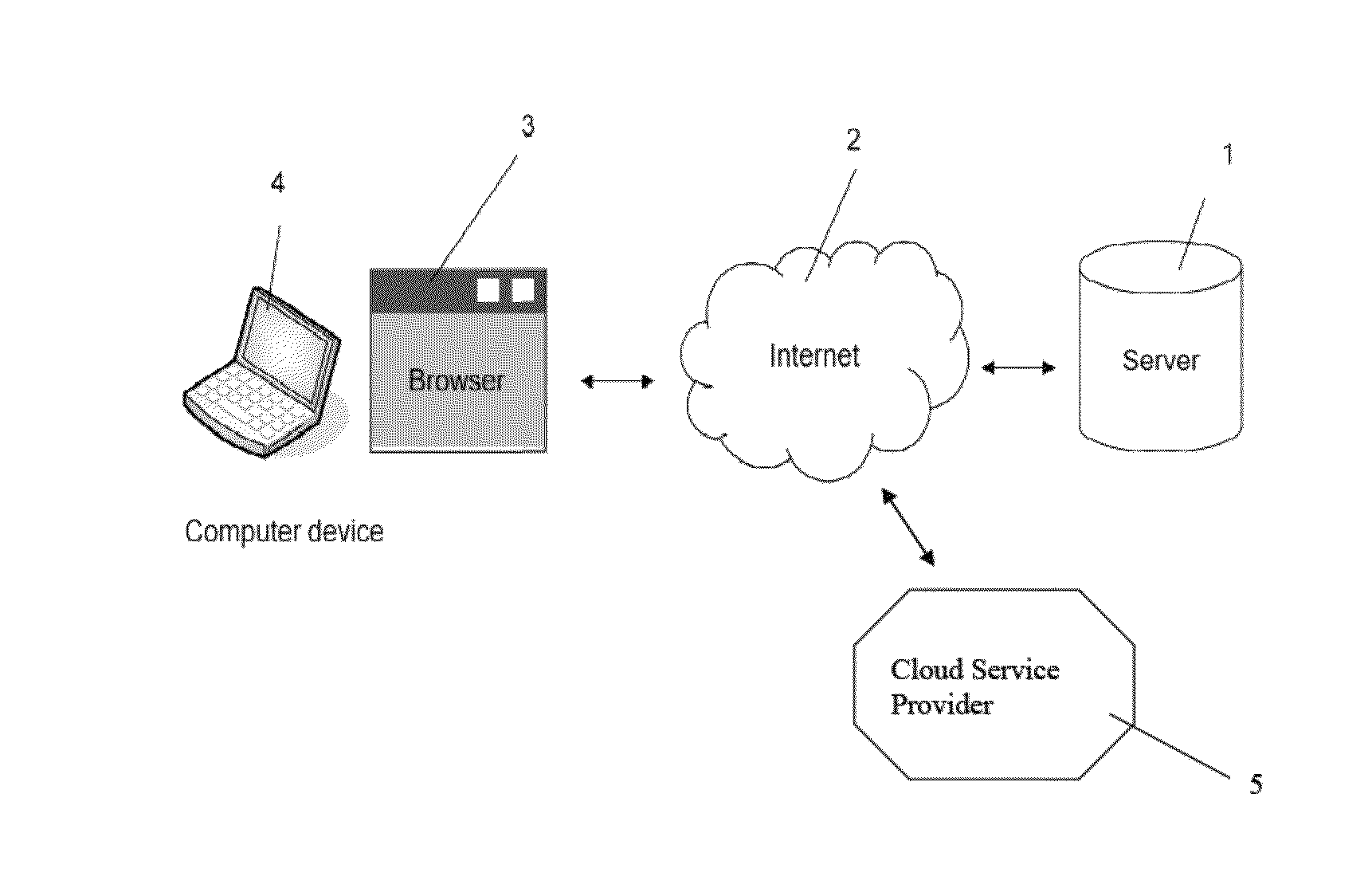
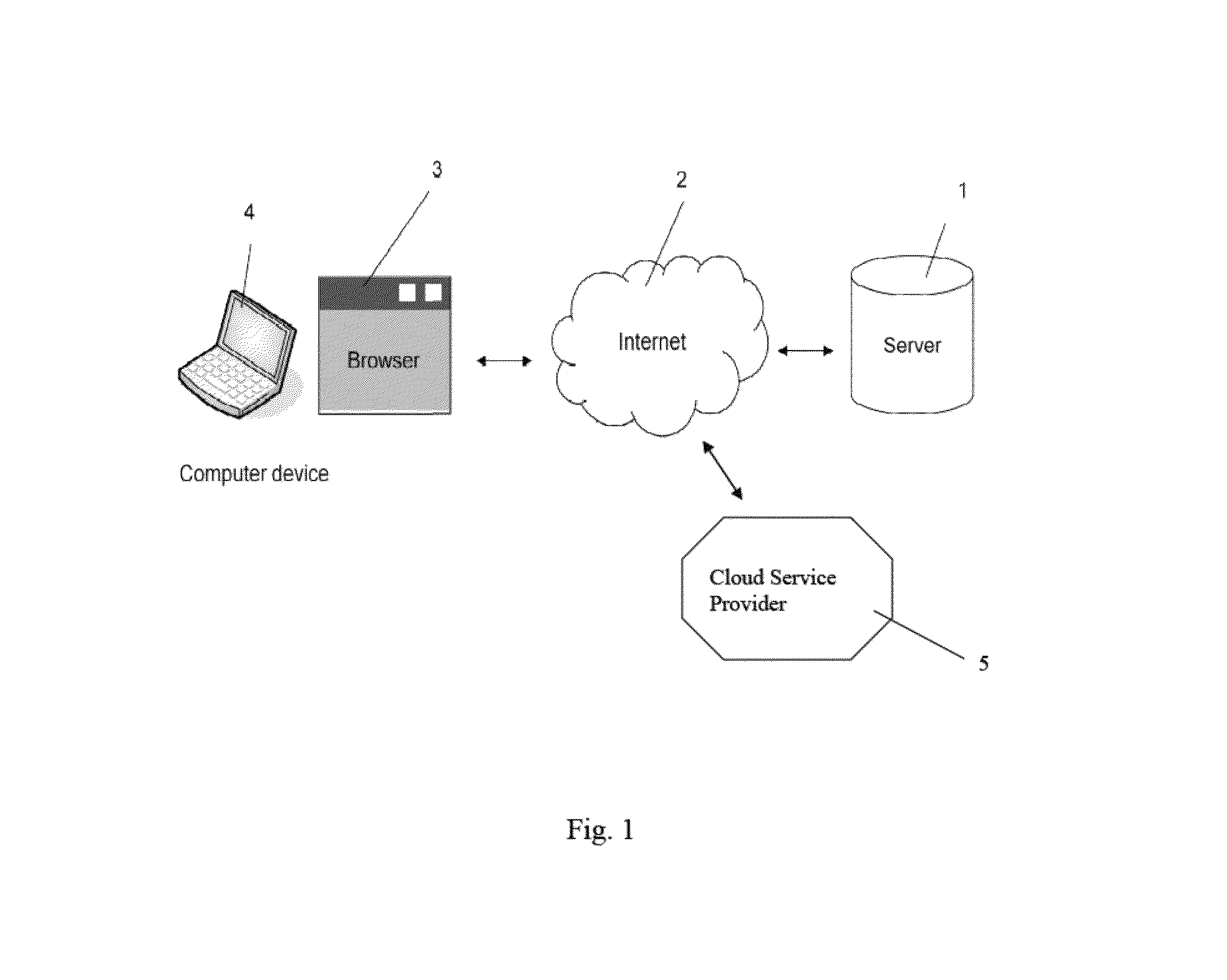
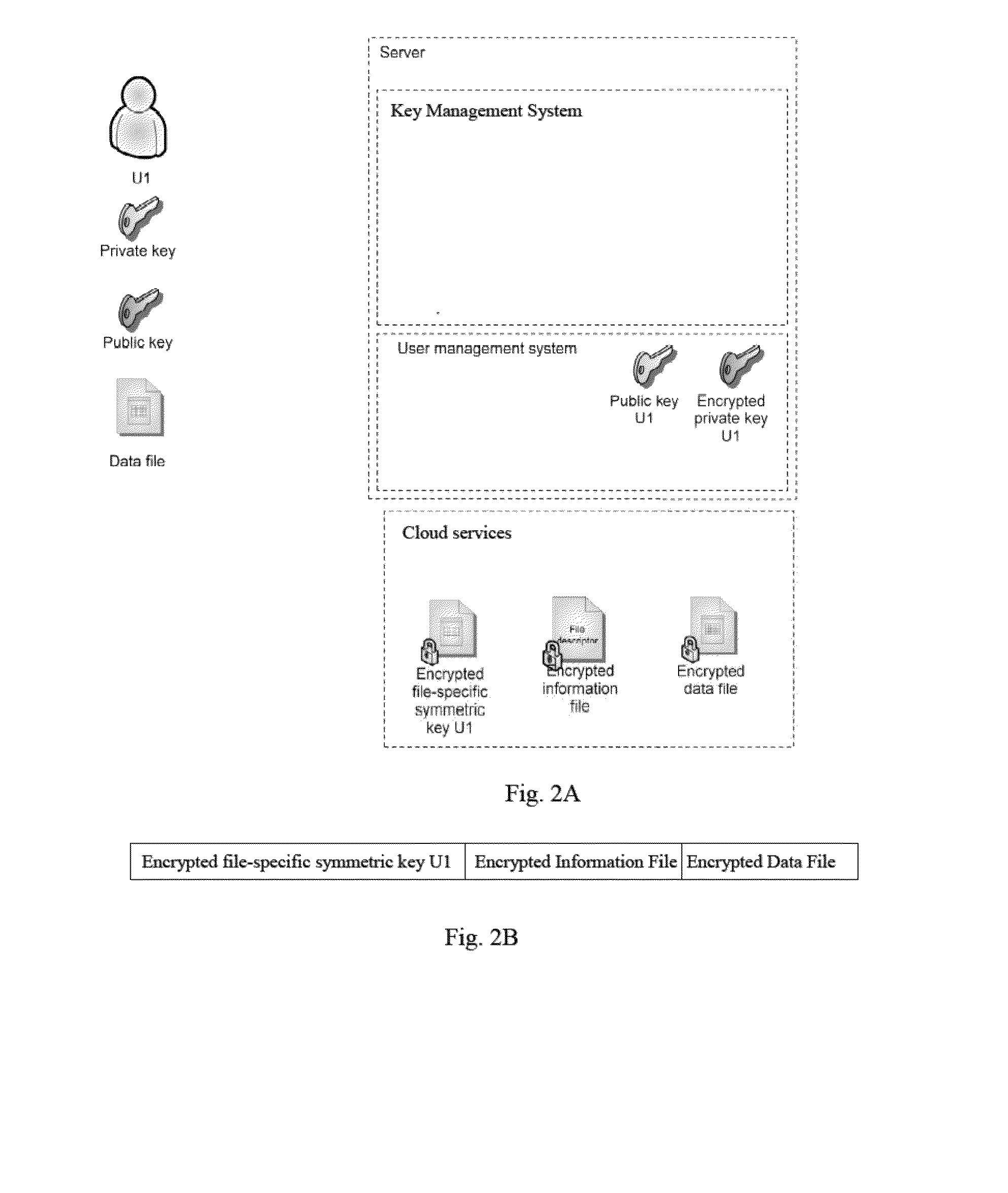
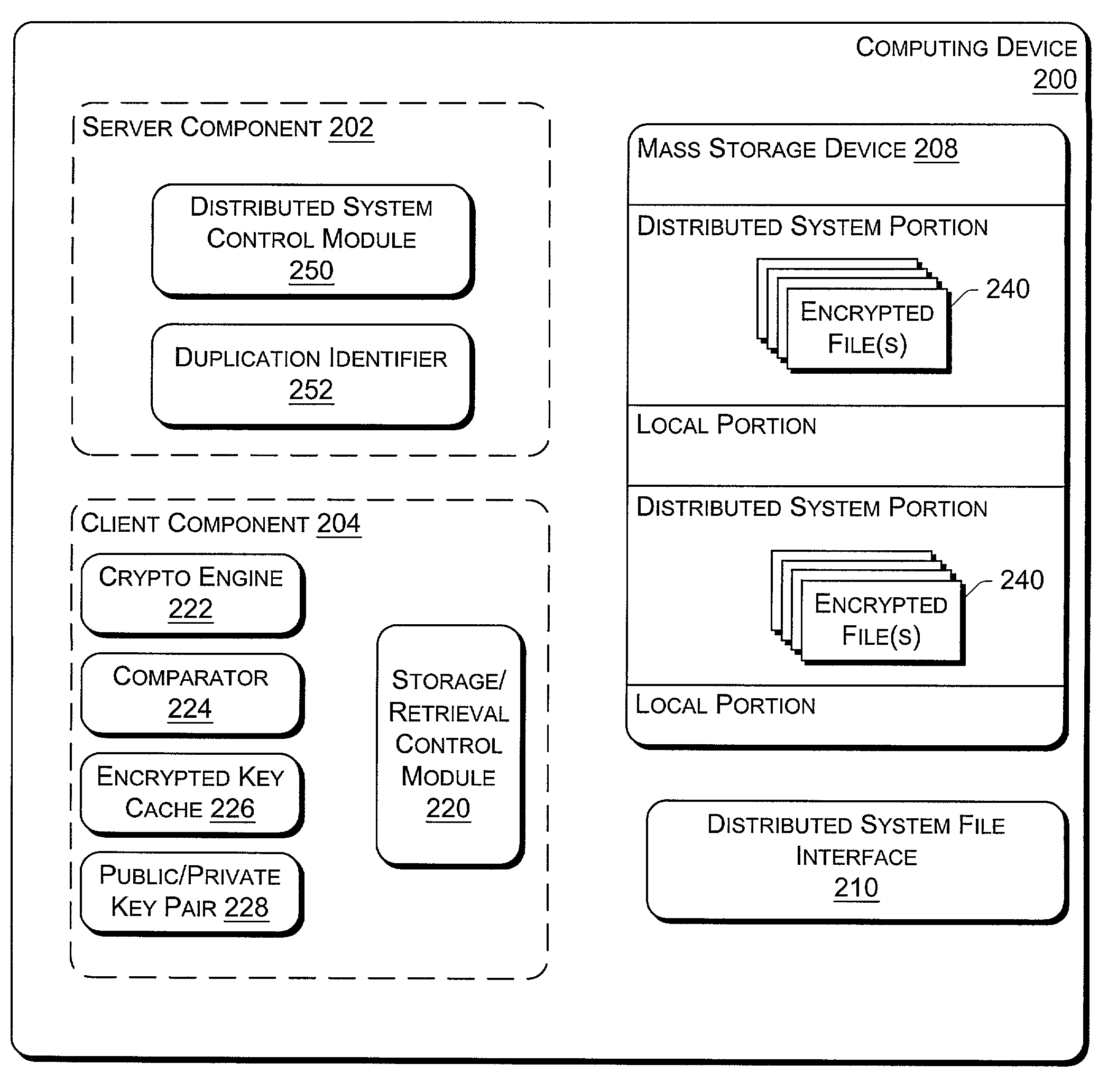
Method for secure storing and sharing of a data file via a computer communication network and open cloud services
ActiveUS20150113279A1User identity/authority verificationComputer security arrangementsWeb browserPassword
A computer implemented method, server computer and computer program for securely storing a data file via a computer communication network and open cloud services. The method includes: providing a user's computer with code for providing a unique user name; asking the user for a password; generating an asymmetric key pair having one public key and one private key; encrypting the private key via a hash of the password; generating a file-specific symmetric key specific for the data file; encrypting the data file via the file-specific symmetric key; encrypting the file-specific symmetric key via the public key; where the code is executed by a web browser on the computer; storing the encrypted file-specific symmetric key as a header part of the encrypted data file, and interacting with the file exchange interface of a cloud service which receives the encrypted data file, and storing the encrypted data file and header part.
Owner:INVENIA
Encrypted key cache
InactiveUS6981138B2Key distribution for secure communicationPublic key for secure communicationSymmetric-key algorithmAccess control
A file that has been encrypted using a symmetric key and that has a corresponding access control entry with the symmetric key encrypted using the public key of a public / private key pair can be accessed. An encrypted key cache is also accessed to determine whether an access control entry to symmetric key mapping exists in the cache for the access control entry corresponding to the file. If such a mapping exists in the cache, then the mapped-to symmetric key is obtained form the cache, otherwise the encrypted symmetric key is decrypted using the private key of the public / private key pair. The encrypted key cache itself can also be encrypted and stored as an encrypted file.
Owner:MICROSOFT TECH LICENSING LLC
Key encryption method based on file attribution
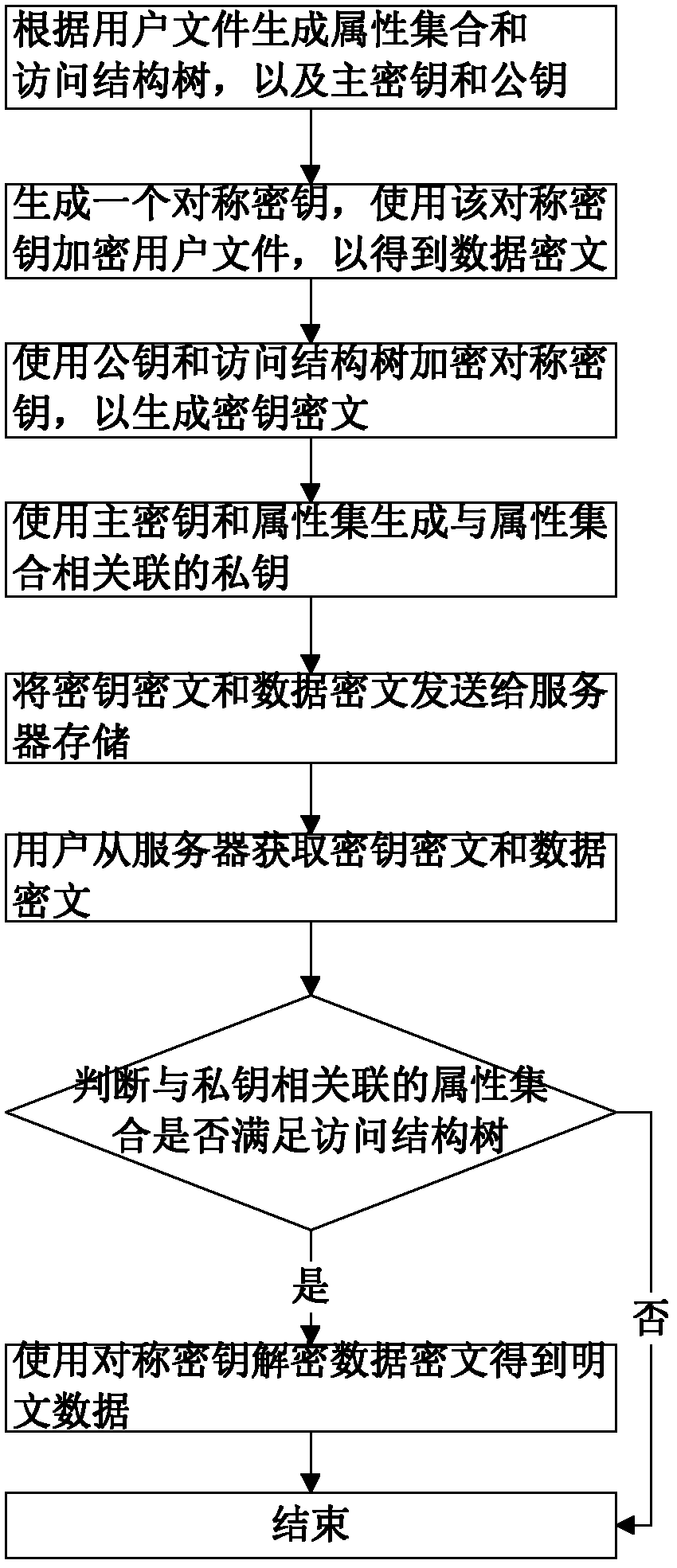
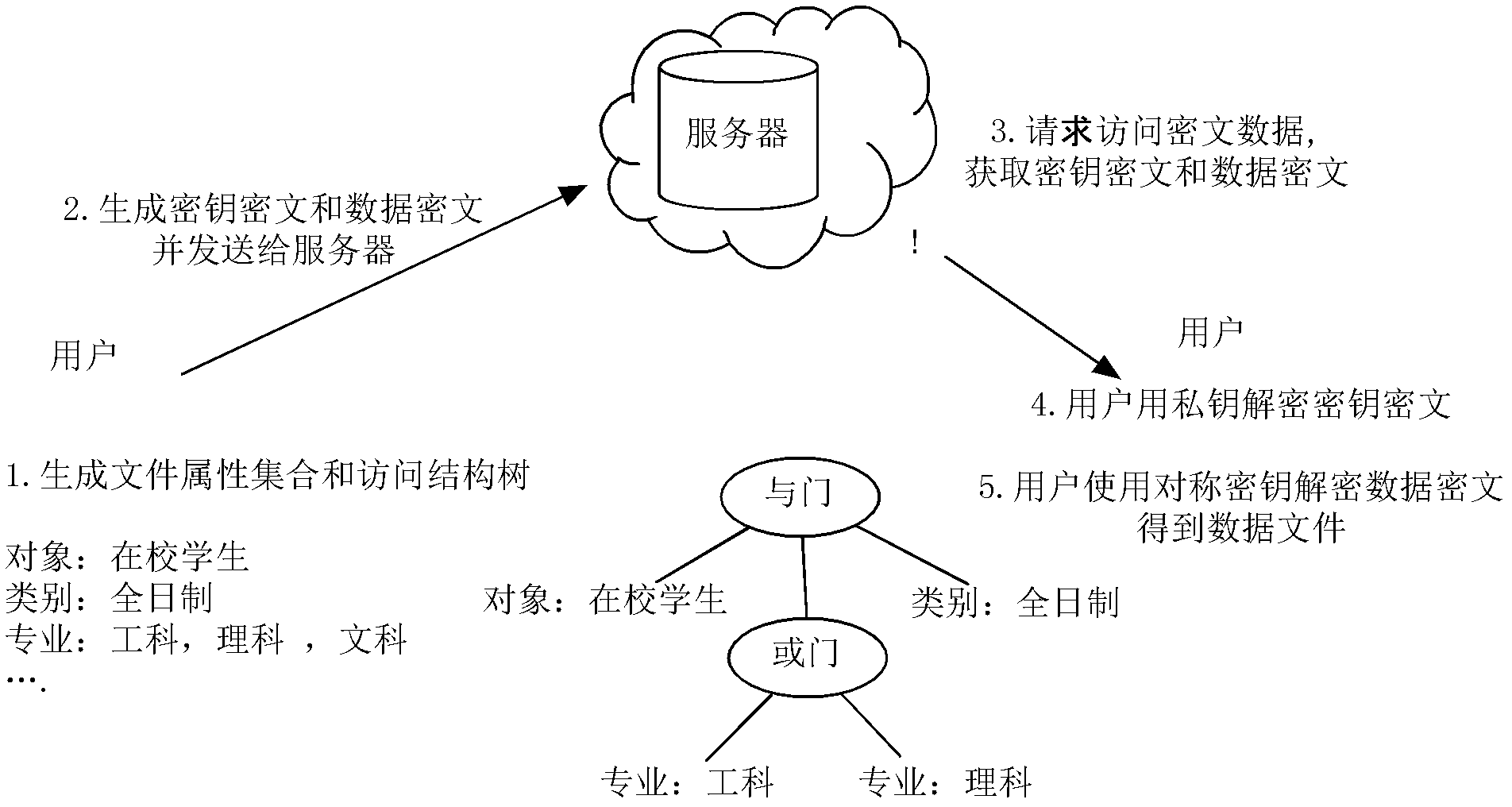
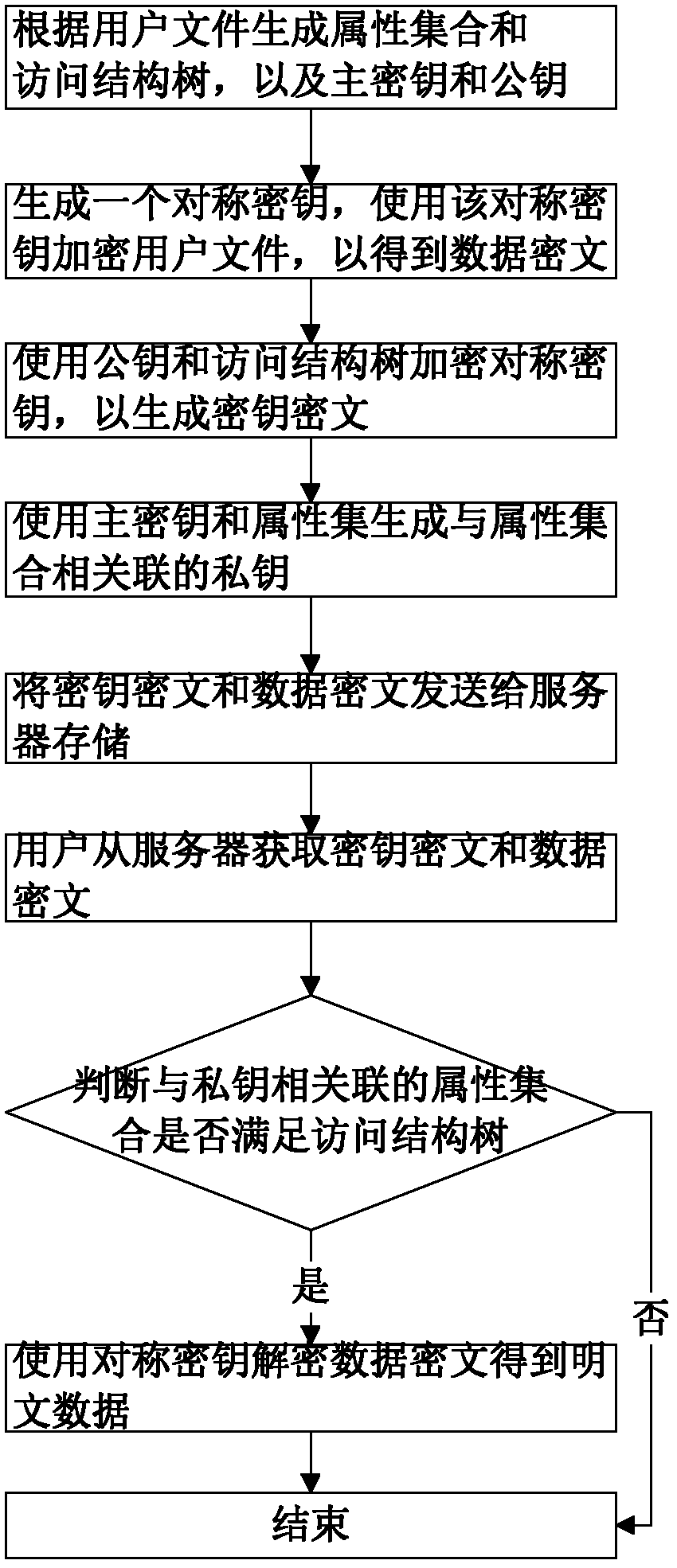
InactiveCN102624522AEfficient encryptionReduce multiplication (exclusiveSecuring communicationPlaintextAccess structure
The invention discloses a key encryption method based on file attribution. The key encryption method comprises the following steps of: receiving a user file, generating an attribution aggregate, an access structure tree, a main key and a public key according to the user file, randomly generating symmetric keys, encrypting the user file by using the symmetric keys and a symmetric encryption algorithm to obtain data cipher text, encrypting the symmetric keys by utilizing the public key and the access structure tree to generate a key cipher text, generating a private key associated with the attribution aggregate by utilizing the main key and the attribution aggregate, transmitting the key cipher text and the data cipher text to a server to store, obtaining the key cipher text and the data cipher text from the server by a user, decrypting the key cipher text by using the private key by the user to judge whether the attribution aggregate associated with the private key meets the access structure tree or not, and if meeting the access structure tree, decrypting the symmetric key and decrypting the data cipher text by utilizing the symmetric key through the user to obtain plaintext data. According to the key encryption method based on the file attribution, disclosed by the invention, data is encrypted by the symmetric encryption algorithm, the safety of the symmetric key is protected based on attribution encryption, and the high-efficiency safe access of encrypted data is realized.
Owner:HUAZHONG UNIV OF SCI & TECH
Electronically verified digital signature and document delivery system and method
InactiveUS7082538B2Low costReduce complexityPublic key for secure communicationUser identity/authority verificationWeb serviceNetwork service
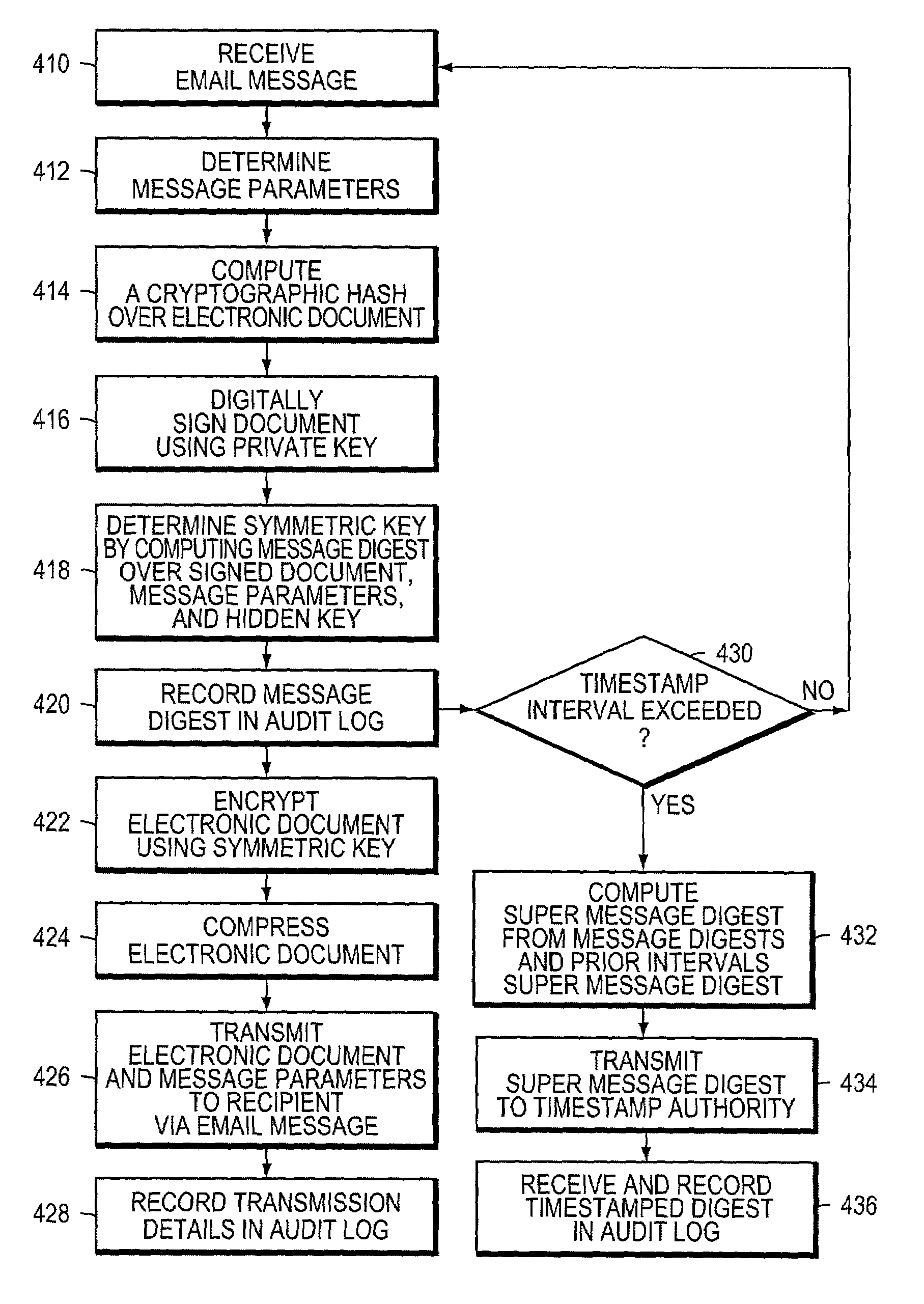
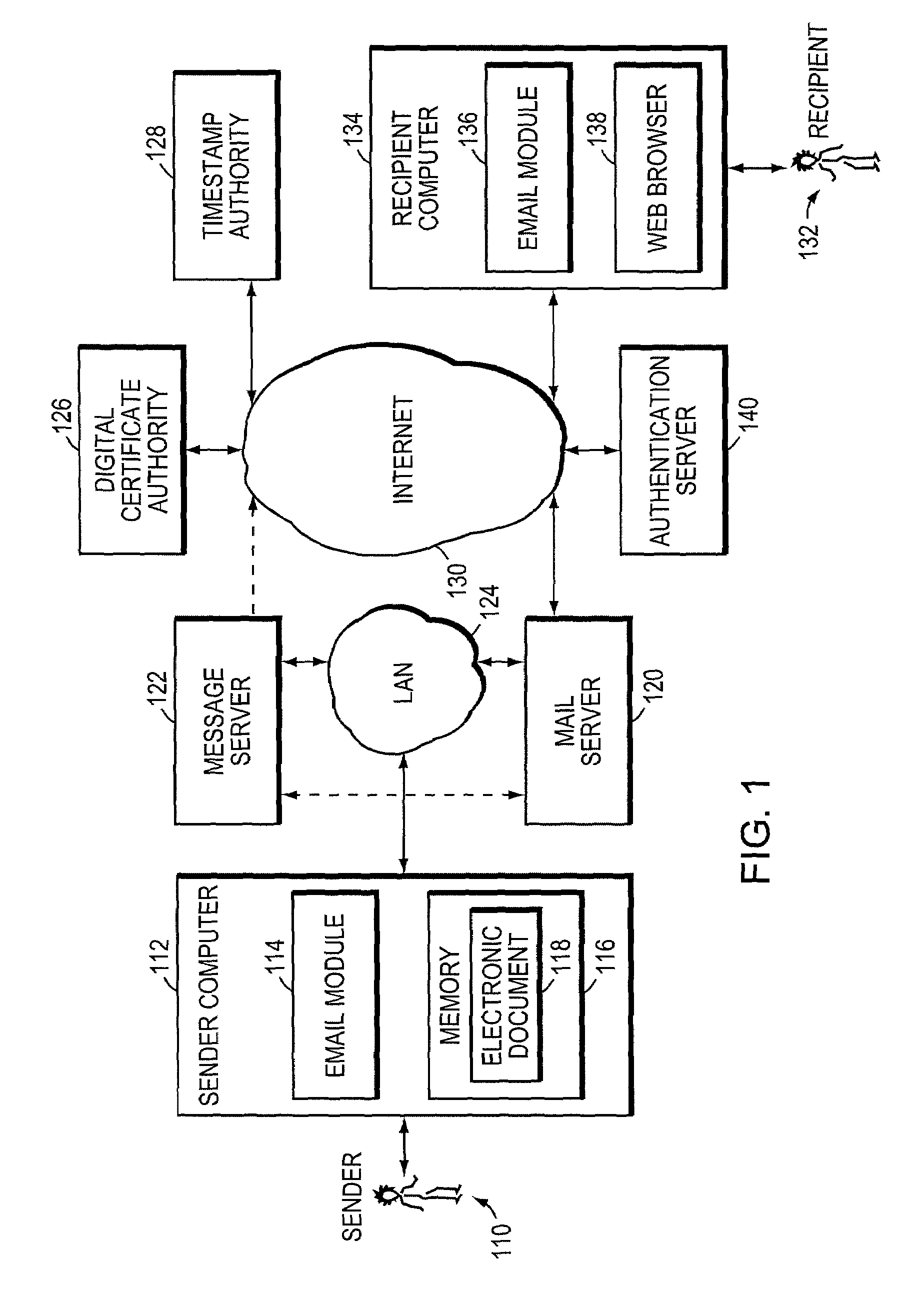
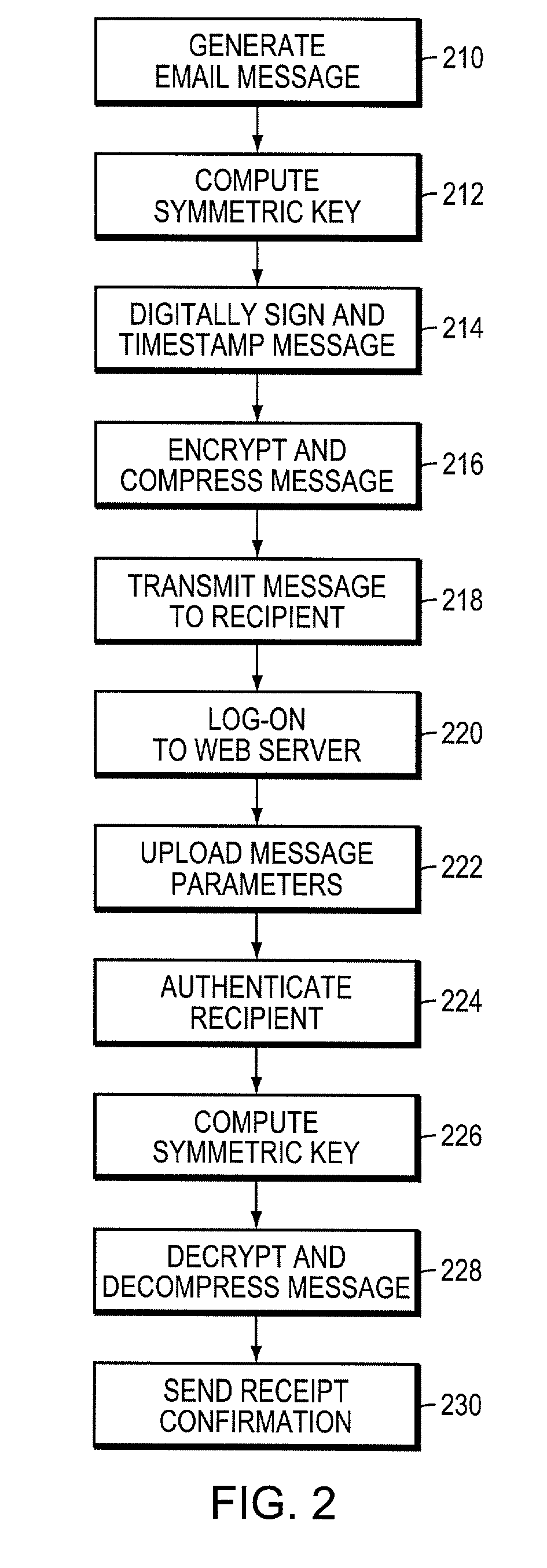
The secure messaging system of the invention encrypts an electronic document using a symmetric key and transmits the encrypted document and related message parameters to a recipient whose identity is then authenticated by a web server. The web server dynamically regenerates the symmetric key from a hidden key and from the message parameters accompanying the encrypted document, and thus avoids having to maintain a central repository of encrypted documents as required by typical “post and pick-up” encrypted messaging systems. Further, an audit trail produced while practicing the invention provides timestamped message digest data for a plurality of time intervals, where the message digests for adjacent time intervals are computationally linked together. The audit trail effectively enables timestamped message digest data to verify not only the existence of a document during a first time interval, but also to verify the existence of documents encountered in a prior time interval.
Owner:UPLAND SOFTWARE INC
Method and system for authenticating entity based on symmetric encryption algorithm
ActiveUS20130212390A1Low implementation costImprove authentication efficiencyUser identity/authority verificationSecurity arrangementSymmetric-key algorithmEncryption
A method and a system for authenticating an entity based on a symmetric encryption algorithm are provided. The method includes the following steps: 1) an entity A sends an authentication request message to an entity B; 2) after receiving the authentication request message, the entity B sends an authentication response message to the entity A; 3) the entity A determines the validity of the entity B according to the received authentication response message. The implementation cost of the system can be reduced by using the authentication according to the invention.
Owner:CHINA IWNCOMM
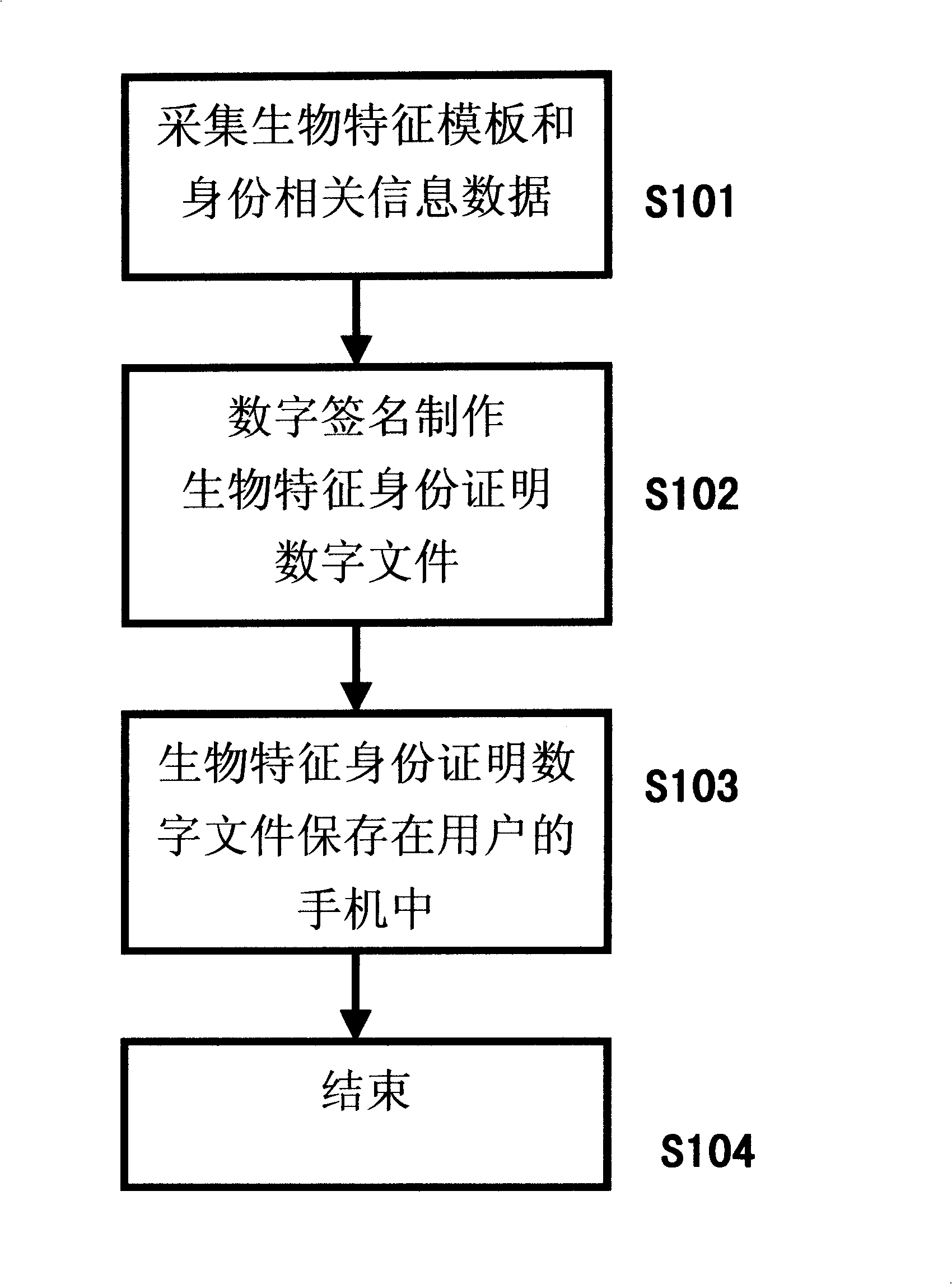
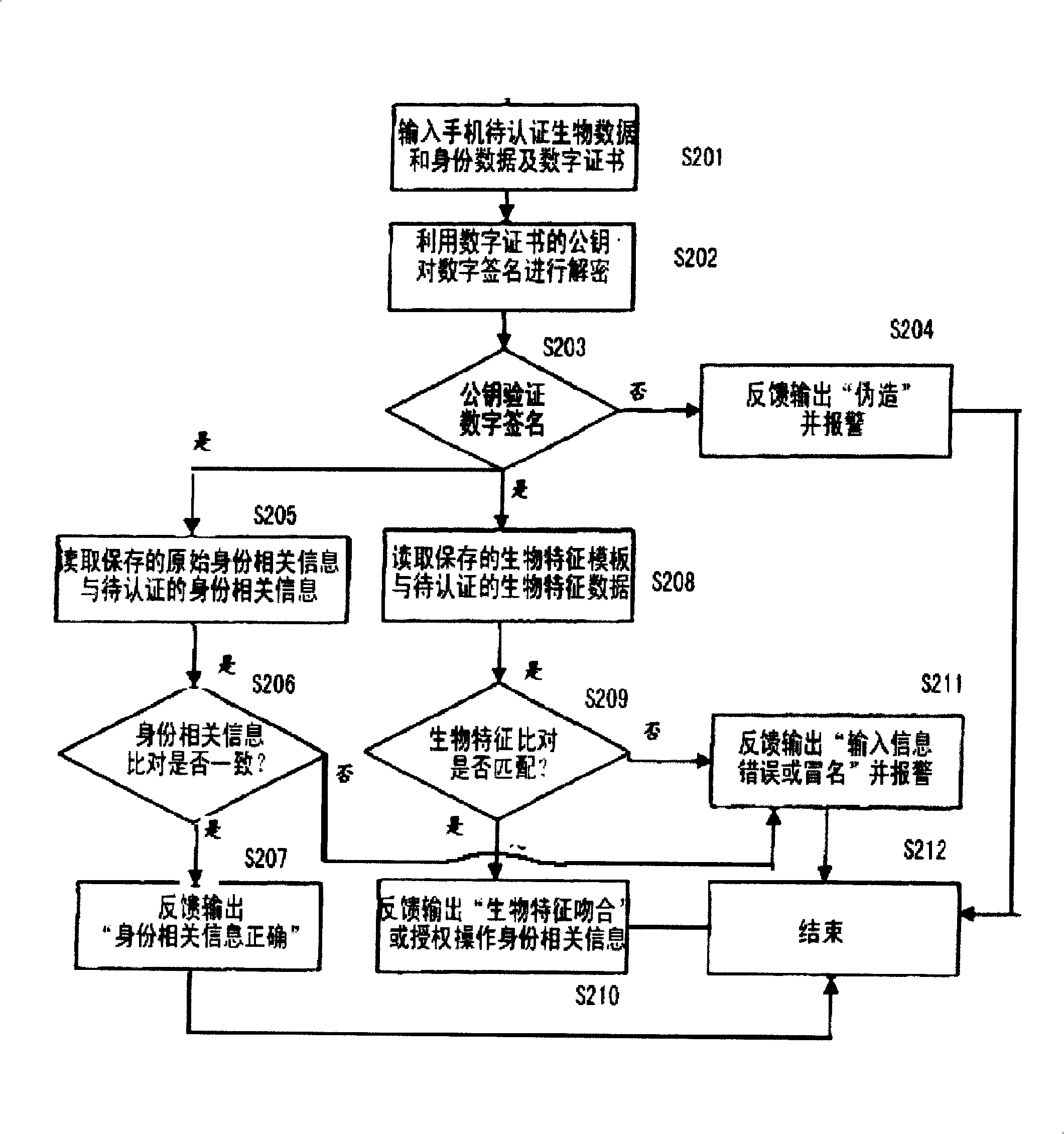
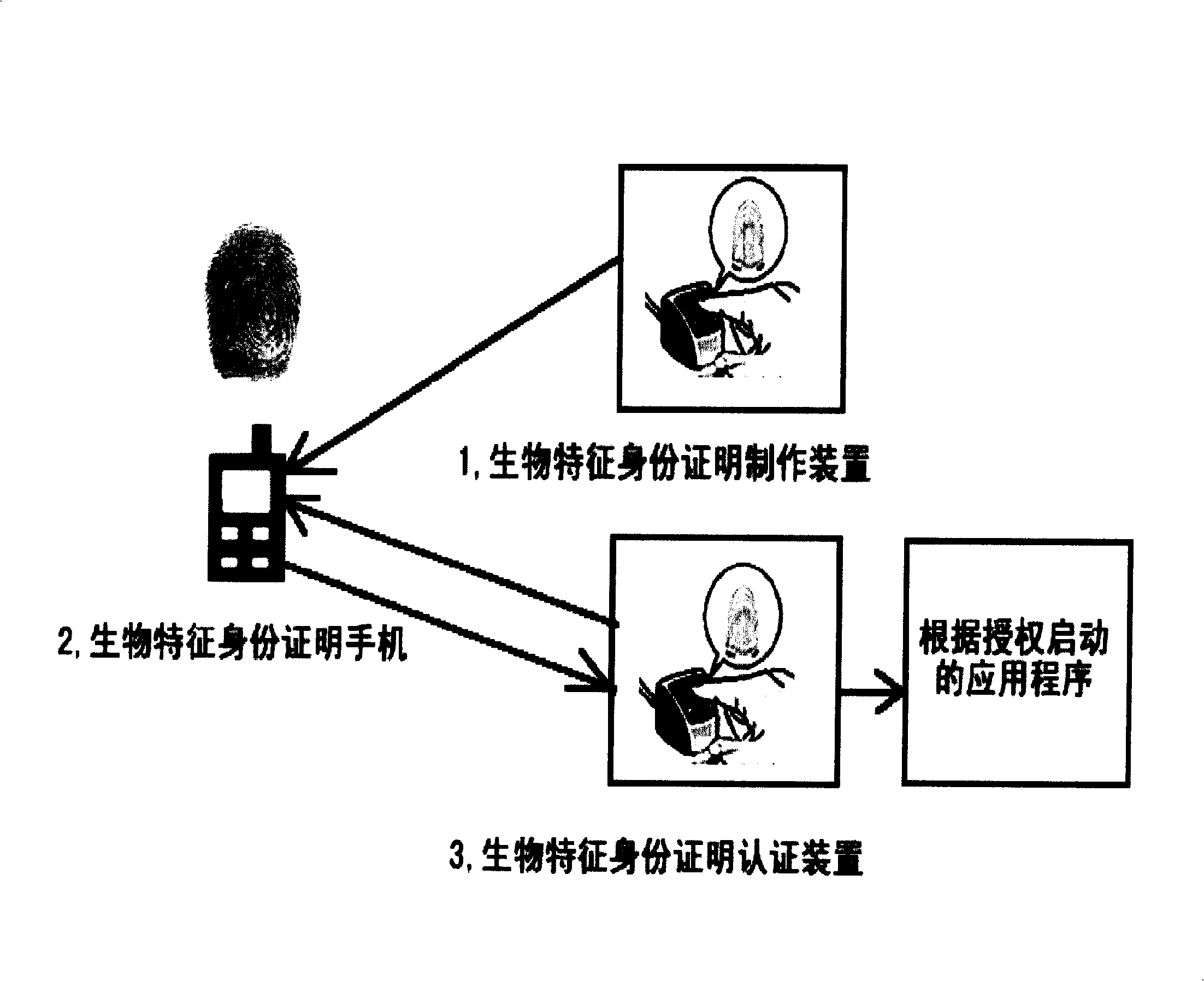
Mobile phone biological identity certification production and authentication method, and its authentication system
InactiveCN101321069AOvercoming technical biasPrivacy protectionUser identity/authority verificationRadio/inductive link selection arrangementsBiometric dataDigital signature
A biologic character template of a user and the related information of the user's identity constitute a whole data block, comprising: selecting an asymmetric key algorithm, using the private key to perform the digital signature or the digital seal, manufacturing the biologic character ID digital file of the digital signature, which is stored in the mobile phone of the user. The biologic character data of the user to be validated is collected on the site, and the digital certiuficate including the public key is sent to the user; mobile phone for storing the biologic character ID digital file in advance for verification; the mobile phone of the user uses the public key in the digital certificate to validate the digital signature of the biologic character ID digital file; the biologic character data to be certificated are inputted, to compare with the corresponding biologic character template in the biologic character ID digital file; the mobile phone of the user outputs the result data of the comparing and the validate, to display the result or output the authorization data of the further operation.
Owner:刘洪利
Encrypting operating system
InactiveUS7810133B2Effective meanEncryption apparatus with shift registers/memoriesDigital data processing detailsOperational systemFile system
A method of and system for encrypting and decrypting data on a computer system is disclosed. In one embodiment, the system comprises an encrypting operating system (EOS), which is a modified UNIX operating system. The EOS is configured to use a symmetric encryption algorithm and an encryption key to encrypt data transferred from physical memory to secondary devices, such as disks, swap devices, network file systems, network buffers, pseudo file systems, or any other structures external to the physical memory and on which can data can be stored. The EOS further uses the symmetric encryption algorithm and the encryption key to decrypt data transferred from the secondary devices back to physical memory. In other embodiments, the EOS adds an extra layer of security by also encrypting the directory structure used to locate the encrypted data. In a further embodiment a user or process is authenticated and its credentials checked before a file can be accessed, using a key management facility that controls access to one or more keys for encrypting and decrypting data.
Owner:EXIT CUBE HONG KONG
Entity authentication method in wireless sensor network
InactiveCN101159748AEffective Security Authentication PolicyProlong lifePublic key for secure communicationUser identity/authority verificationInformation transmissionDigital signature
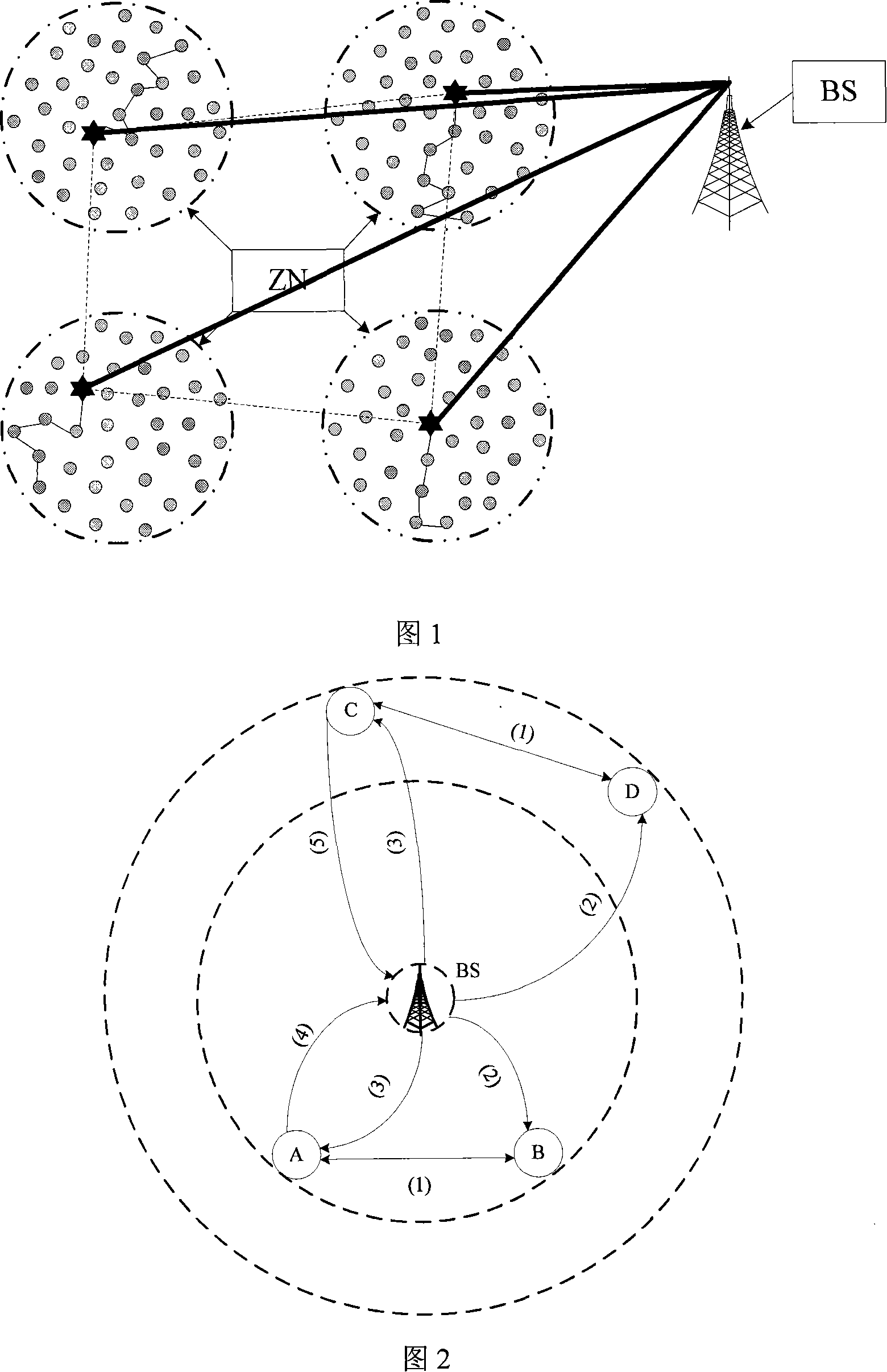
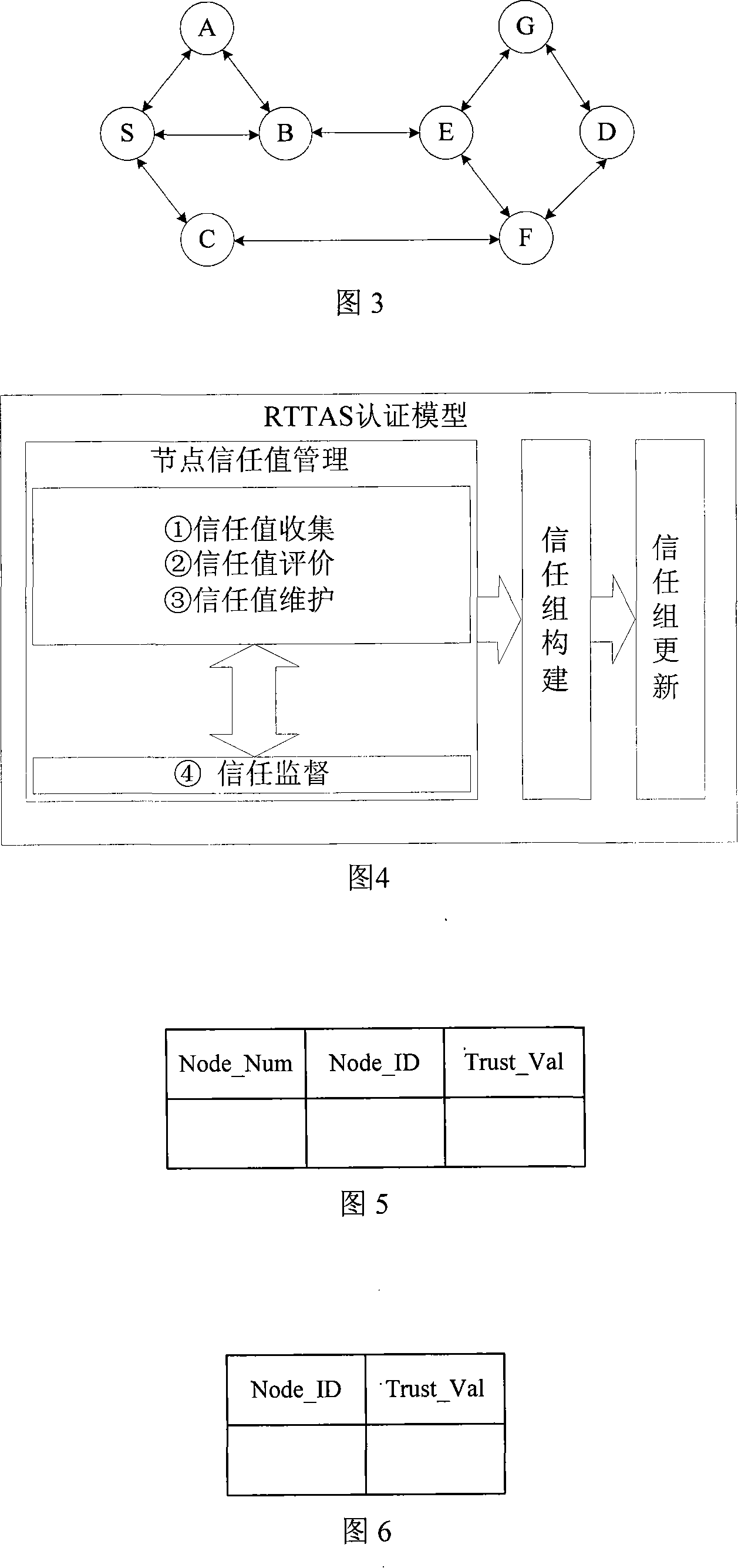
The invention provides an entity authentication method in a wireless sensor network, relating to the application field related to sensor network security in information security technology. The invention can ensure the safe communication among nodes by authenticating the identity of nodes in the wireless sensor network. The authentication for determining whether a node is legal and trustable comprises node trust value management, trust group construction, and trust group updating so as to store corresponding trust value in the node. In the information transmission process, the node can determine the information transmission manner and path according to the magnitude of the trust value. The method can acquire effective security authentication strategy by using the ideal of node reputation and the trust group, and can obviate the problem of large calculation amount of digital signature by using public key algorithm, thereby to effectively reduce the authentication delay and improve the network lifetime.
Owner:UNIV OF SCI & TECH BEIJING
Two-way-security-authentication-based data downloading method and system
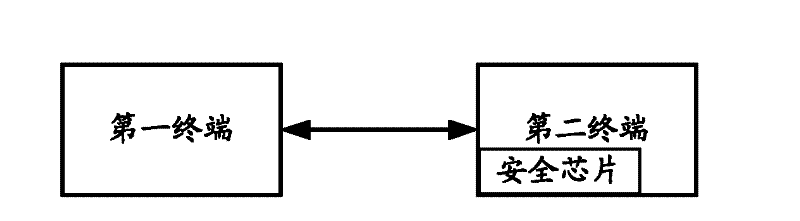
ActiveCN102413132ASolve imperfectionsProtection securityUser identity/authority verificationDigital Signature AlgorithmComputer terminal
The invention discloses a two-way-security-authentication-based data downloading method and a two-way-security-authentication-based data downloading system. The method comprises that: a first terminal verifies a second terminal through a symmetric key algorithm to acquire a first verification result; after the second terminal is determined to be a legal terminal according to the first verification result, the second terminal verifies the first terminal through an asymmetric key algorithm to acquire a second verification result; and after the first terminal is determined to be a legal terminal according to the second verification result, the second terminal downloads data which is encrypted through a digital signature algorithm to the first terminal. By the method and the system, the creation of two-way authentication channels and security downloading among different terminals can be realized, and the security and integrity of interactive data are protected.
Owner:BEIJING SUMAVISION PAYMENT TECH CO LTD
Blockchain encryption retrieval scheme
The invention provides a blockchain encryption retrieval scheme. A user having the right to query sets a retrieval code, a factor needing to be retrieved is connected with the retrieval code in series, and a Hash operation is conducted; the result obtained after the Hash operation serves as a key, a content needing to be queried is stored in a value, and a symmetric key is used for encryption and encrypted with a public key of an authorized user. In query, the user computes the key so that the value can be found. The key and value serve as the transaction content so as to compute a Hash value, namely hash, to be uploaded to a blockchain.
Owner:HANGZHOU FUZAMEI TECH CO LTD
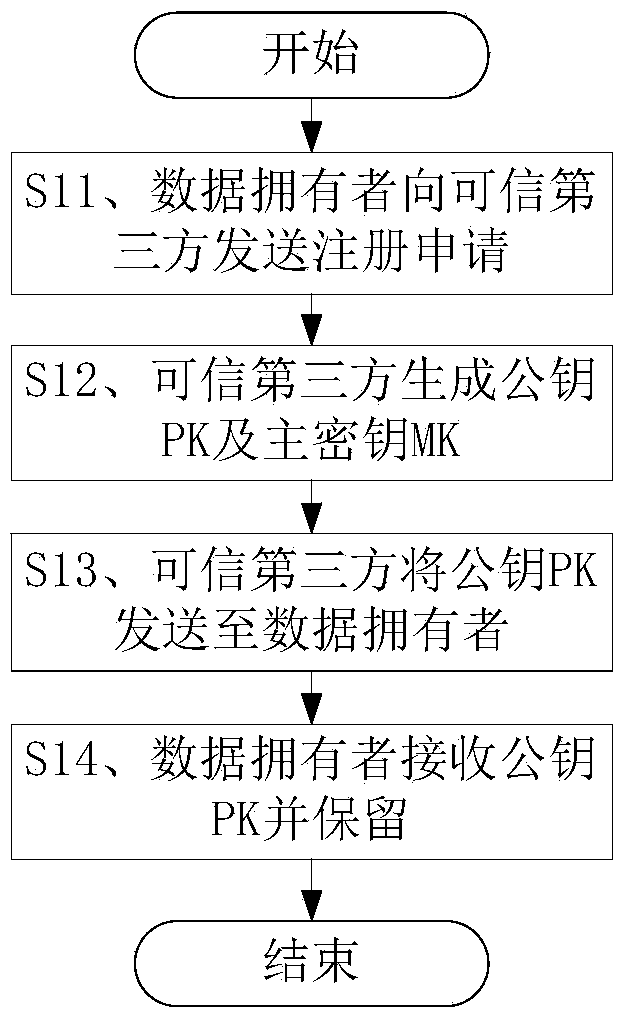
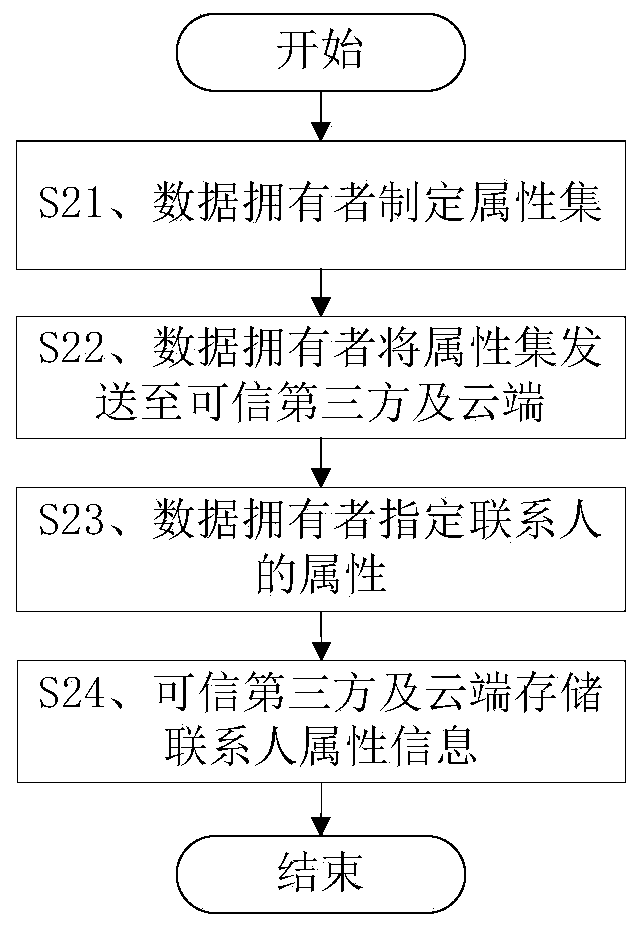
Method for safely sharing mobile cloud storage light-level data
The invention discloses a method for safely sharing mobile cloud storage light-level data. The method comprises the steps that an attribute set is registered in a credible third party by a data owner, the attribute set is assigned to a user by the data owner, the user is authorized by the credible third party through an attribute code mechanism according to the attribute set of the user, so that an attribute key is generated, when the data owner uses a mobile side to share a file, the file is firstly encrypted through a symmetric cryptography mechanism, a symmetric key is encrypted through a proxy encryption server by the utilization of an attribute key mechanism, a file ciphertext and a key ciphertext are sent to a cloud side, after the file ciphertext and the key ciphertext are read from the cloud side by the user, the attribute code mechanism is used by a proxy decryption server to decrypt the file, an authority limit alteration statement is sent to the credible third party and the cloud side by the data owner, and judgments are made by the credible third party and the cloud side, so that authority limits of the user are increased or deleted. According to the method for safely sharing the mobile cloud storage light-level data, the data can be safely shared on the mobile side on the conditions that electric quantity and computing power are limited.
Owner:HUAZHONG UNIV OF SCI & TECH
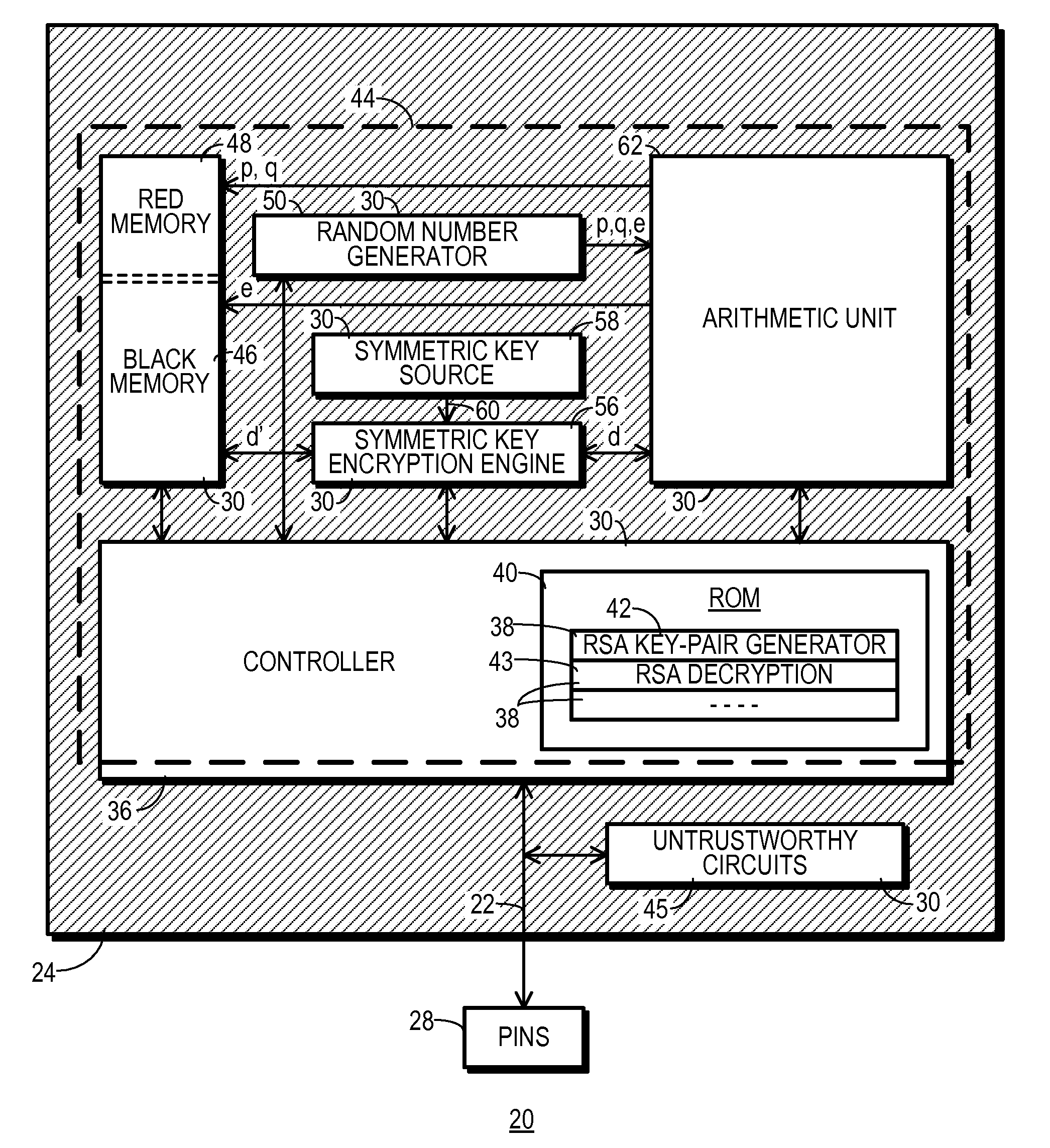
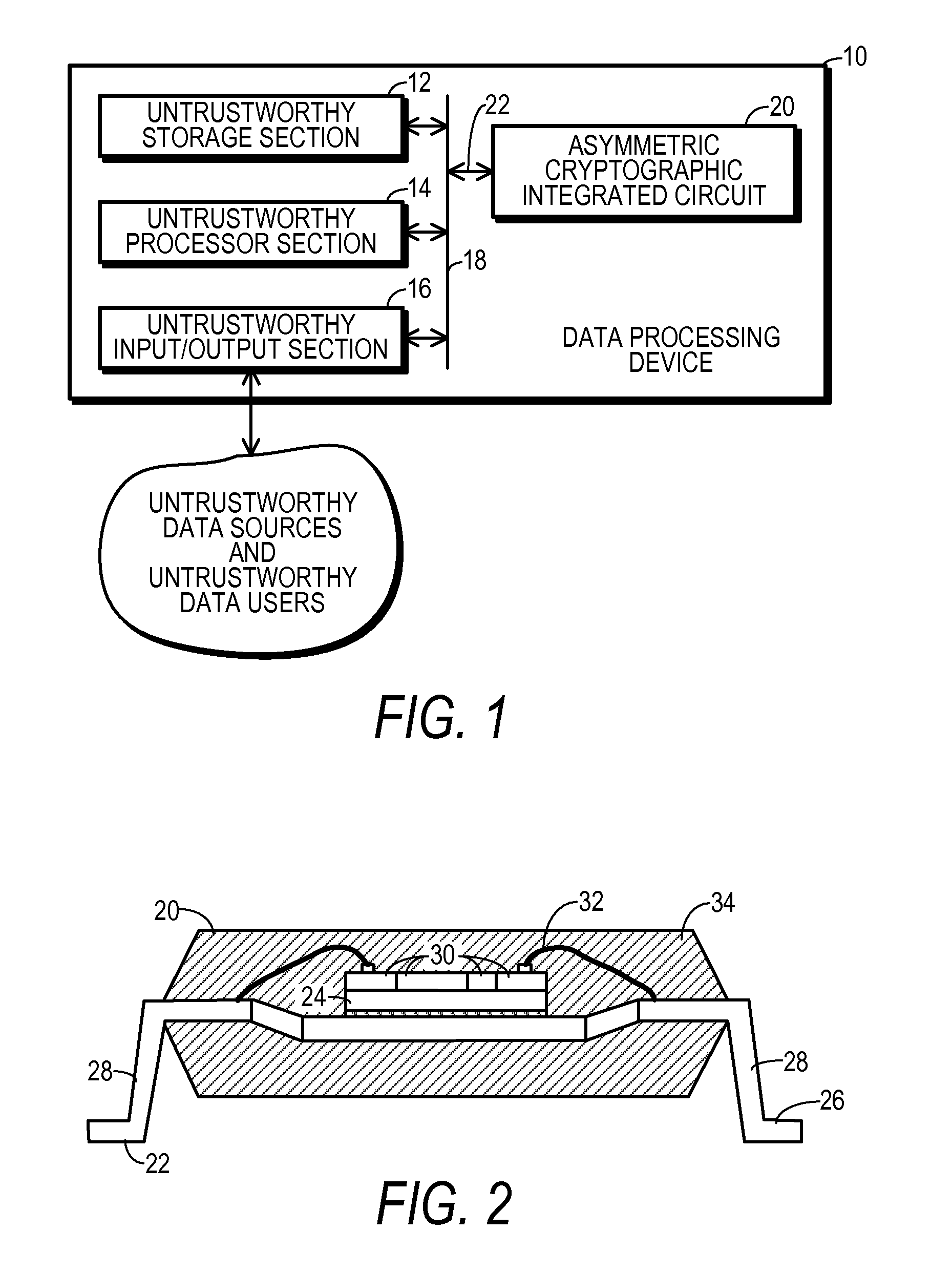
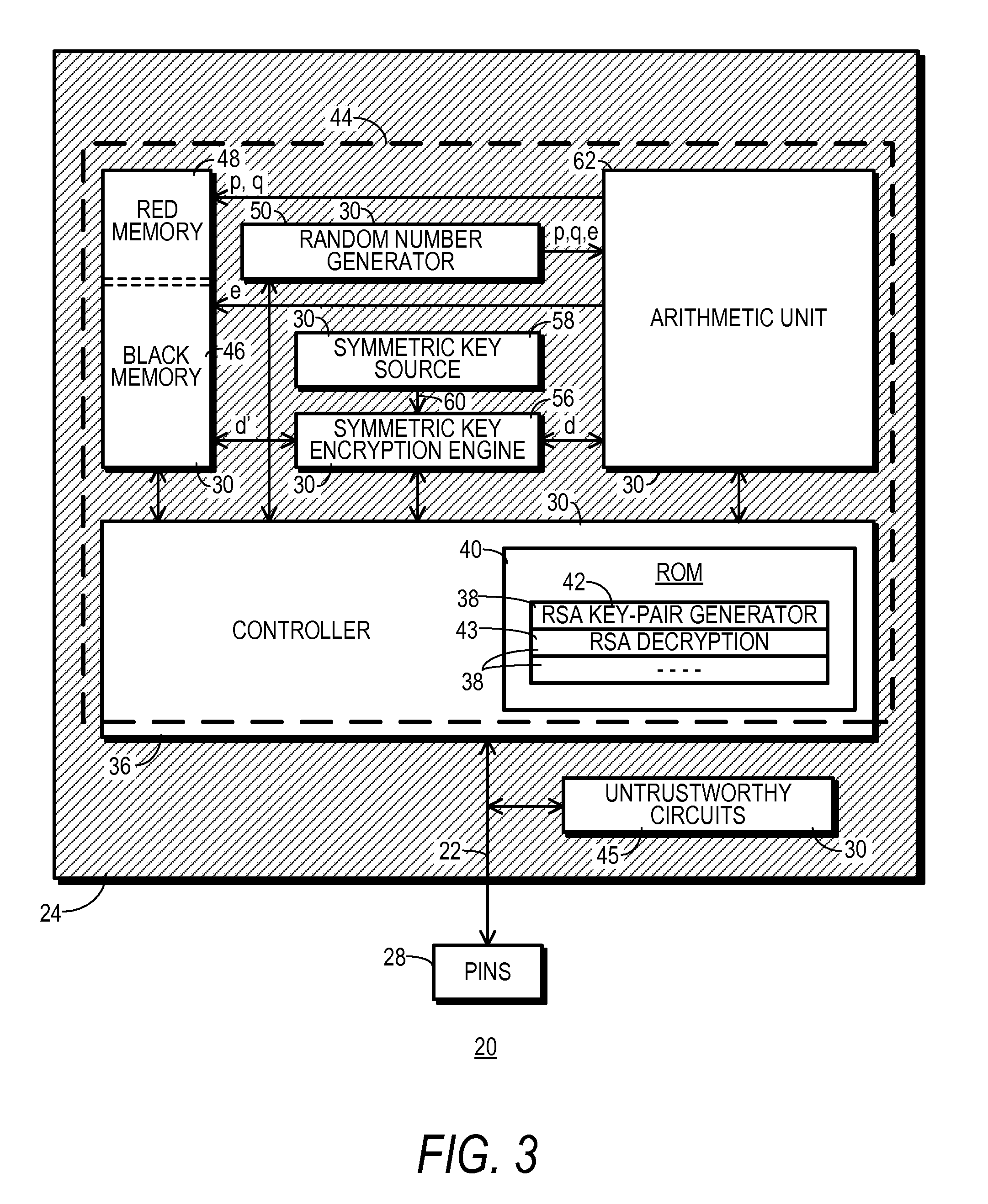
Asymmetric Cryptographic Device With Local Private Key Generation and Method Therefor
ActiveUS20100027788A1Random number generatorsMultiple keys/algorithms usageData treatmentNumber generator
An asymmetric cryptographic integrated circuit 20 and a data processing device 10 in which the integrated circuit 20 is used are disclosed. A security boundary 44 is confined to the interior of integrated circuit 20. A random number generator 50 with a hardware entropy source 54 and an arithmetic unit 62 programmed through microcode 38″ to perform a variety of cryptographically useful functions are included within security boundary 44. One of these functions is a primality tester 72. A controller 36 for integrated circuit 20 may cause cryptographically sensitive data, such as large random prime numbers and a clear private key to be generated within the confines of security boundary 44. A symmetric key encryption engine 56 is included within security boundary 44 and used to encrypt the clear private key so that a resulting encrypted private key may be stored outside security boundary 44 in a non-volatile memory 12.
Owner:NXP USA INC
Data access control method and system in cloud storage environment
ActiveCN104980477AGuaranteed confidentialityIntegrity guaranteedTransmissionSpecial data processing applicationsConfidentialityData access control
Embodiments of the invention provide a data access control method and system in a cloud storage environment. The method mainly comprises the steps that a user registers personal information to a cloud server through a client side; when a data owner determines that the data to be transmitted to the cloud server is shared data, the client side of the data owner uses a symmetric key to encrypt the data, and sends the encrypted data, the symmetrical key, a hash operation result of the data and a shared attribute of the data to the cloud server; when the data is not the shared data, the client side of the data owner uses its own public key to encrypt the data, and sends the encrypted data, the hash operation result of the data and the shared attribute of the data to the cloud server. Through adoption of the method and system, confidentiality and integrity of the user data are guaranteed, and confidentiality of the user files is classified, so that authority control under data sharing is better realized, and security improvement of data access control under cloud storage is effectively provided.
Owner:黑龙江航天信息有限公司
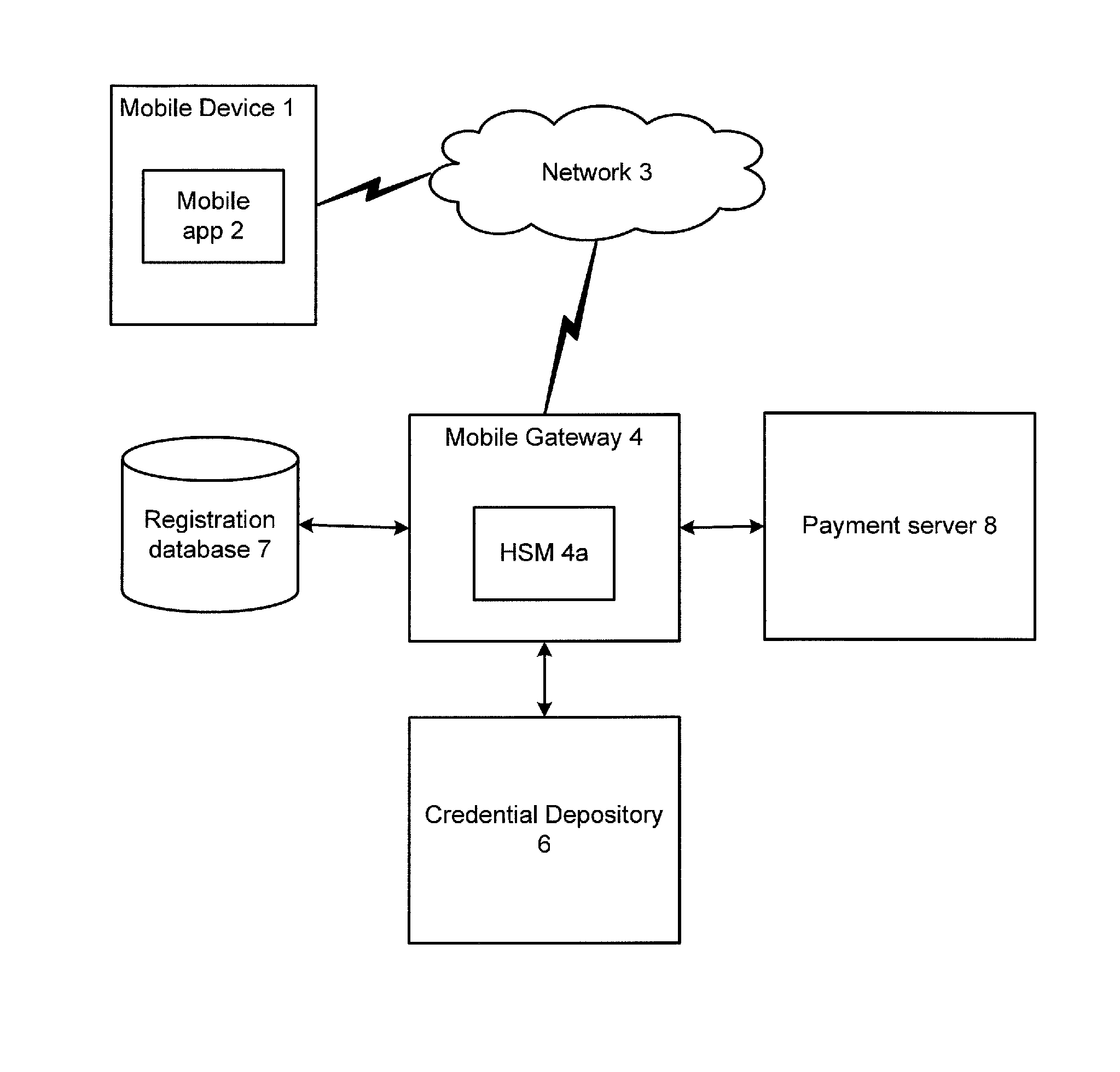
Credential Recovery
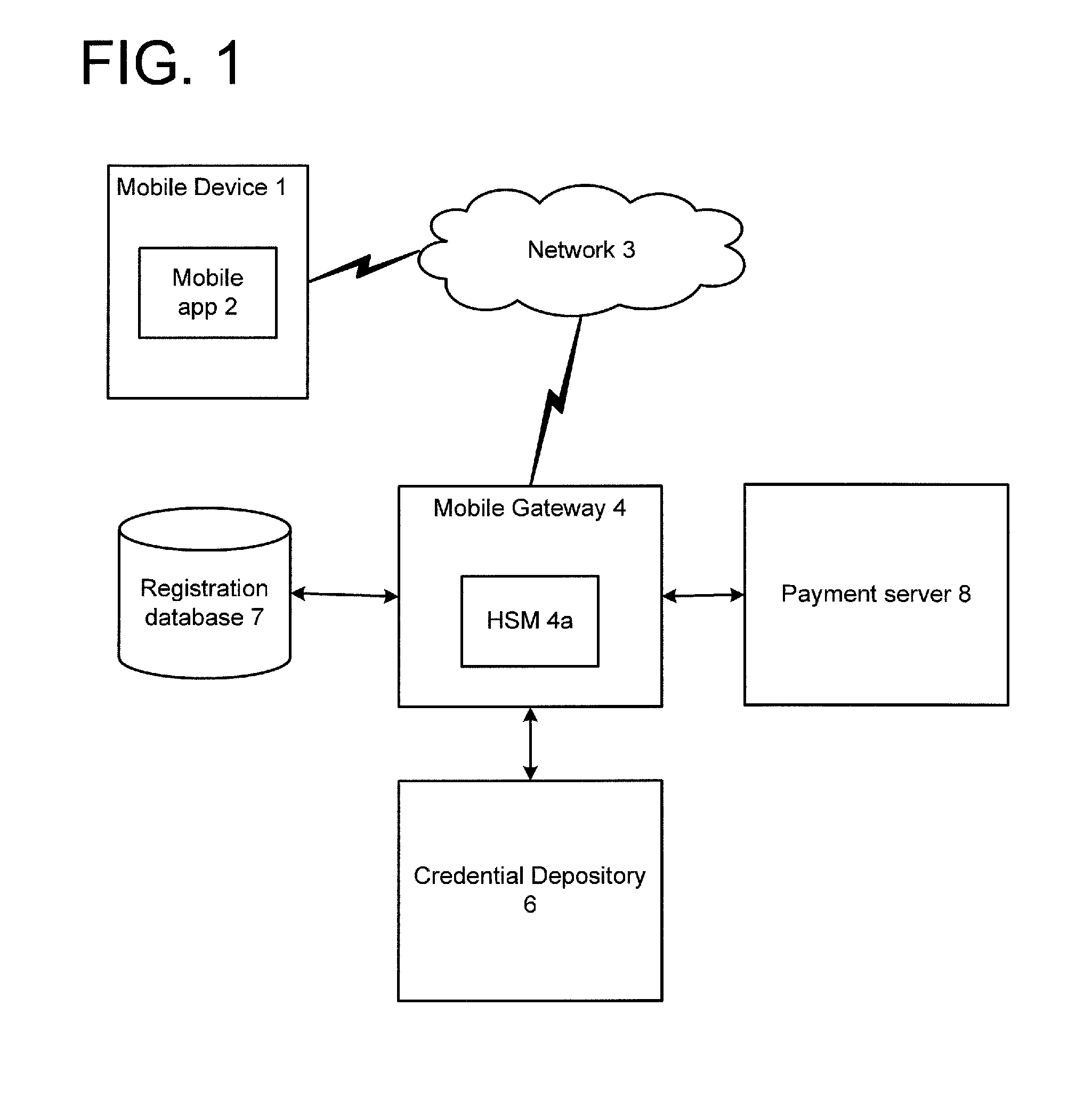
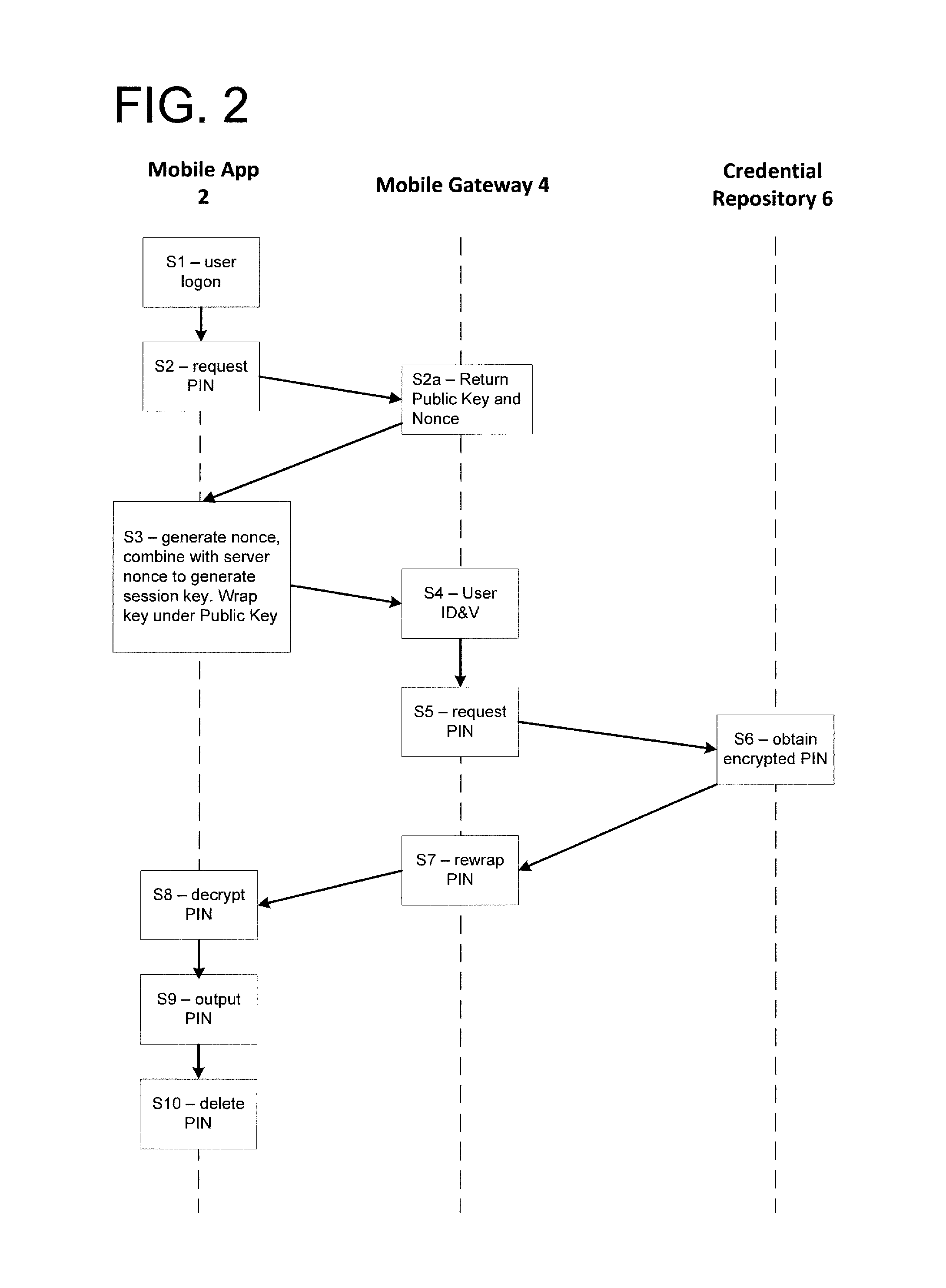
ActiveUS20140156989A1Key distribution for secure communicationDigital data authenticationHardware security moduleCommunication device
In a credential recovery process, a user is authenticated using an application running on a mobile communications device, and requests recovery of a credential. The application generates a session key encrypted with the public key of a gateway, and sends the encrypted key to the gateway. The gateway recovers the credential from a depository, encrypted using a symmetric key shared with the depository. The gateway decrypts the credential and re-encrypts the credential using the session key. Preferably, the decryption and re-encryption is performed within a hardware secure module within the gateway. The re-encrypted credential is sent to the application, which decrypts the credential and outputs it to the user. In this way, the credential is provided securely to the user and may be made available for use immediately, or nearly so.
Owner:BARCLAYS EXECUTION SERVICES LTD
Method for password based authentication and apparatus executing the method
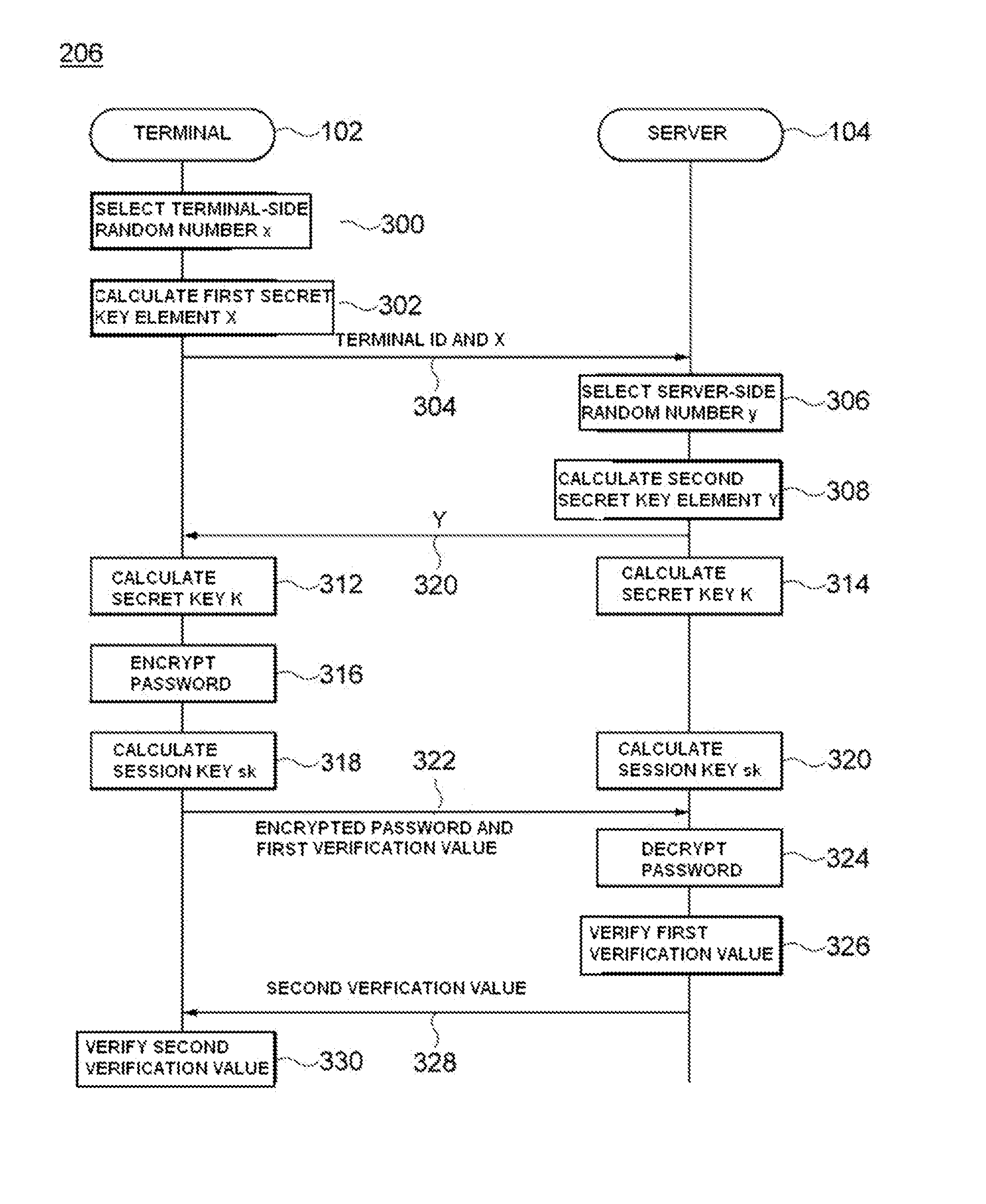
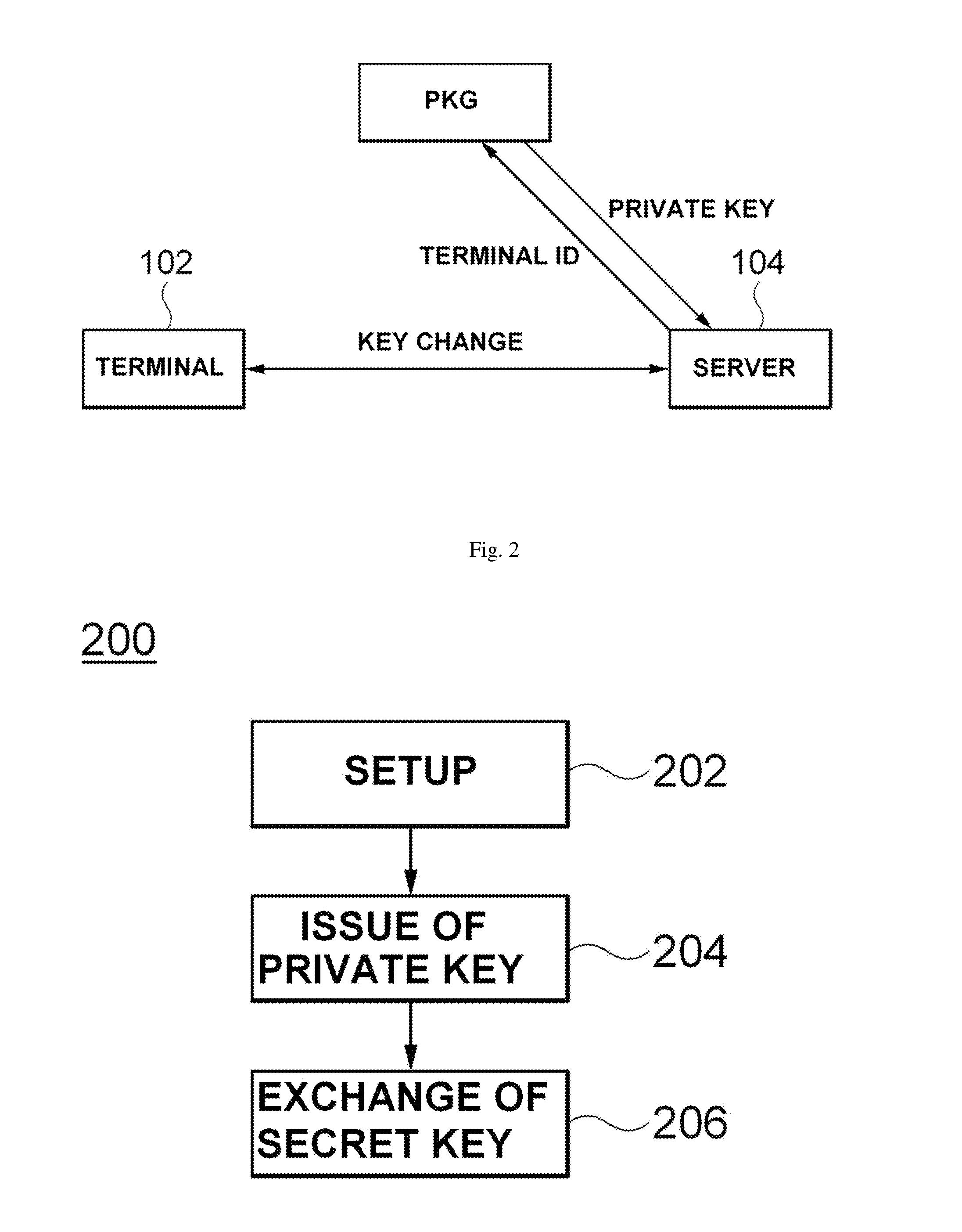
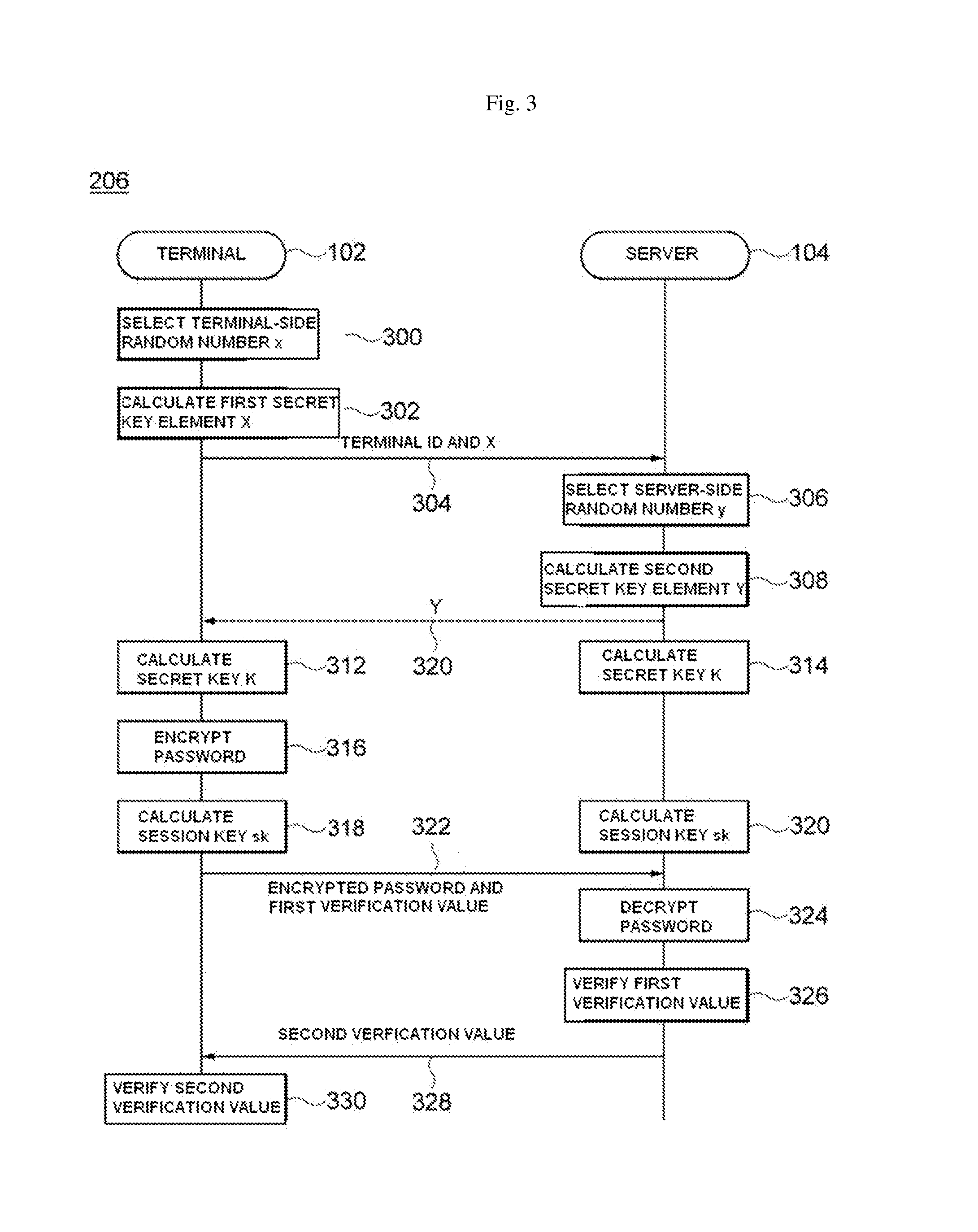
ActiveUS20140122888A1Reduce the amount requiredKey distribution for secure communicationUser identity/authority verificationPasswordKey generation
Provided are an authentication method and an apparatus for the method. An authentication method includes generating, at a terminal, an identifier (ID)-based secret key using an ID of a user of the terminal and key generation factors exchanged with a server, encrypting, at the terminal, a password of the user using a symmetric key encryption algorithm taking the generated secret key as a symmetric key, and requesting authentication for the terminal user by transmitting the encrypted password to the server, and receiving, at the terminal, a response to the authentication request from the server.
Owner:SAMSUNG SDS CO LTD +1
Certified Transmission System
InactiveUS20080155253A1Improve security featuresKey distribution for secure communicationUser identity/authority verificationThird partySymmetric-key algorithm
Owner:ZIX CORP
Method for a secured backup and restore of configuration data of an end-user device, and device using the method
InactiveUS20140189362A1Multiple keys/algorithms usagePublic key for secure communicationService provisionComputer terminal
The method for a backup and restore of configuration data of an end-user device comprises the steps: encrypting the configuration data by using symmetric-key encryption with a symmetrical key, signing the encrypted configuration data with a device private key, and sending the encrypted and signed configuration data to a personal computer of a user of the end-user device, and / or to a storage location of a service provider network, for storage. For restoring of configuration data intended for use within the end-user device, a first or a second public key of an asymmetric key encryption system is used for validating signed configuration data provided by the service provider network or for validating signed configuration data stored on the personal computer of the user.
Owner:MAGNOLIA LICENSING LLC
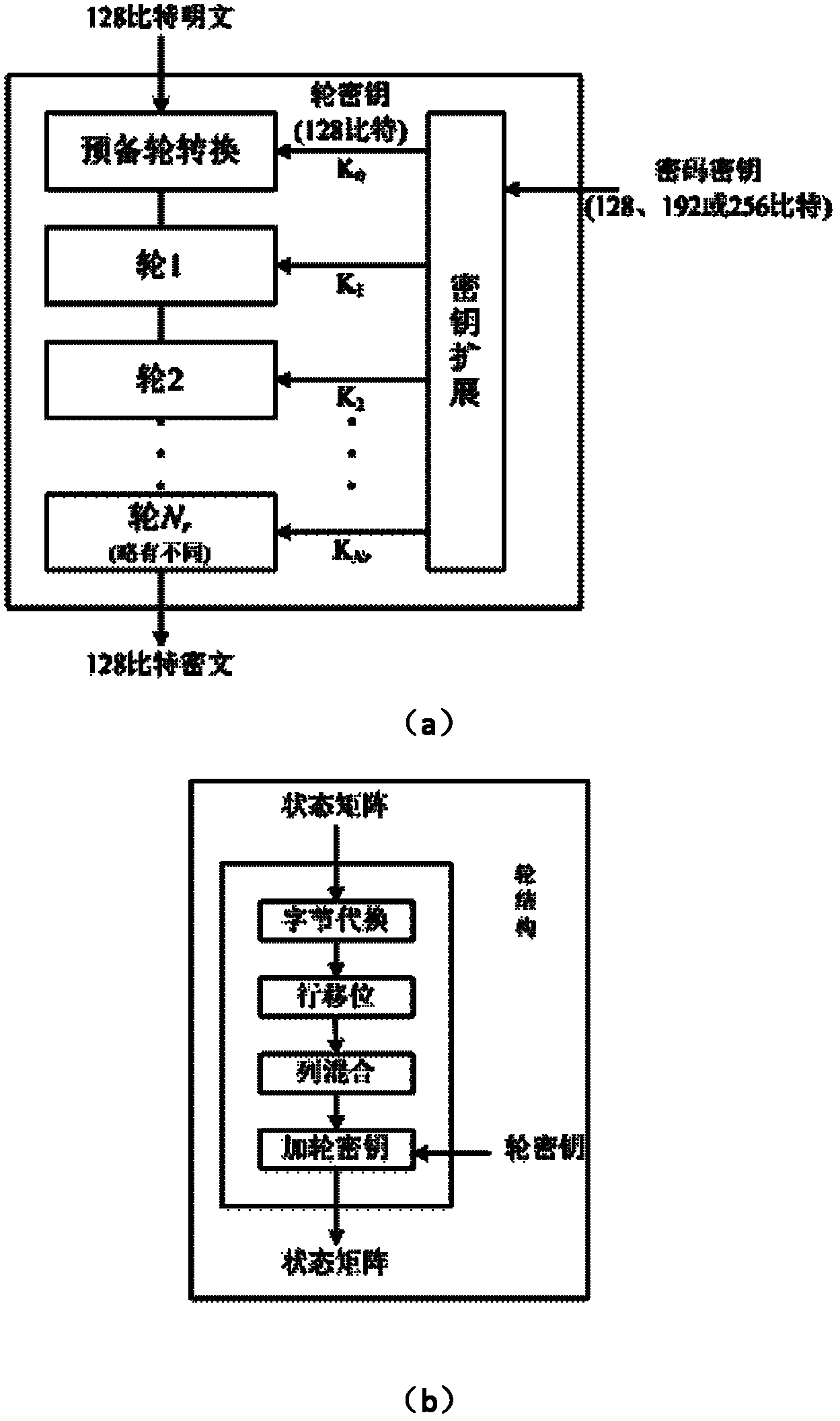
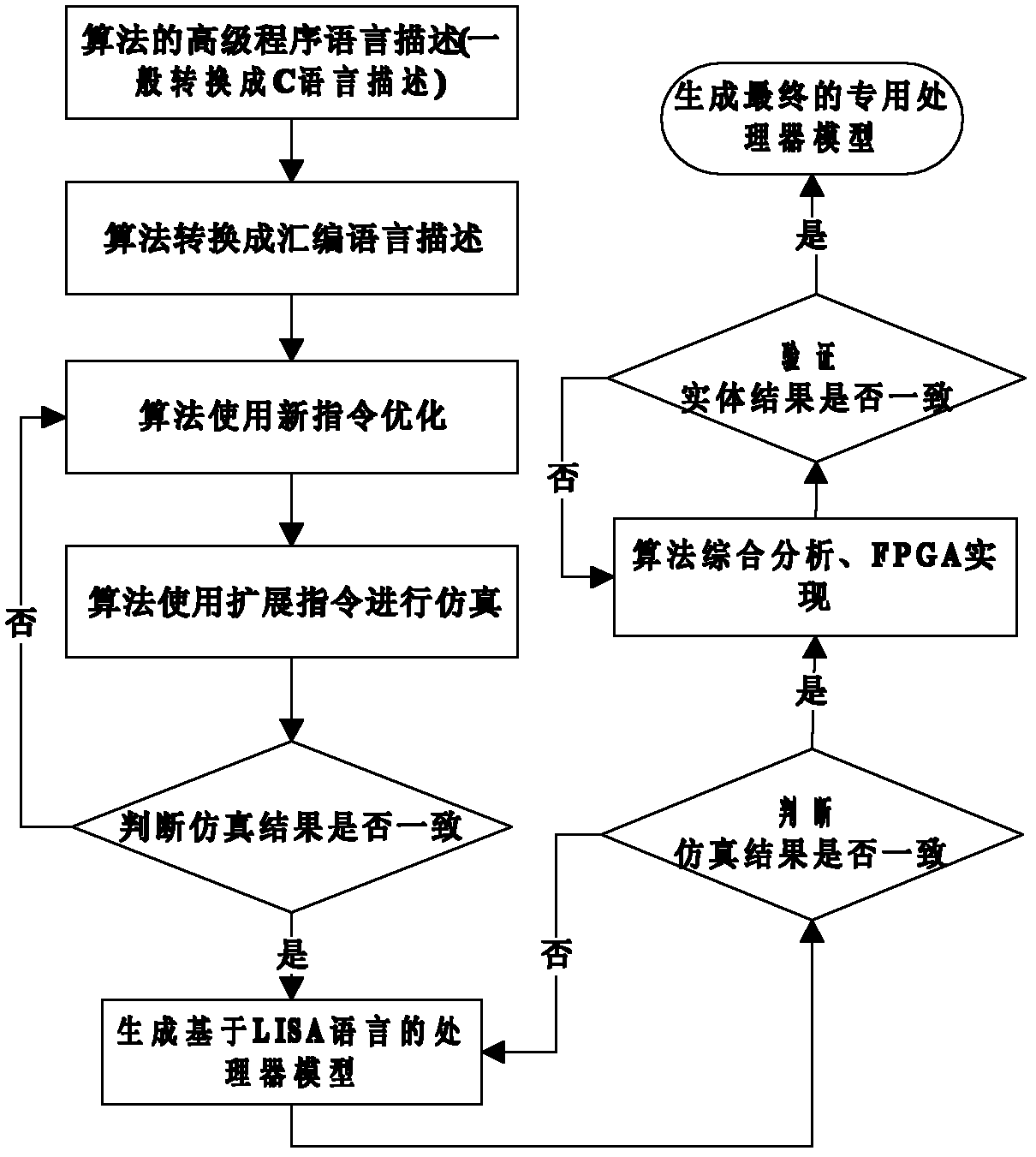
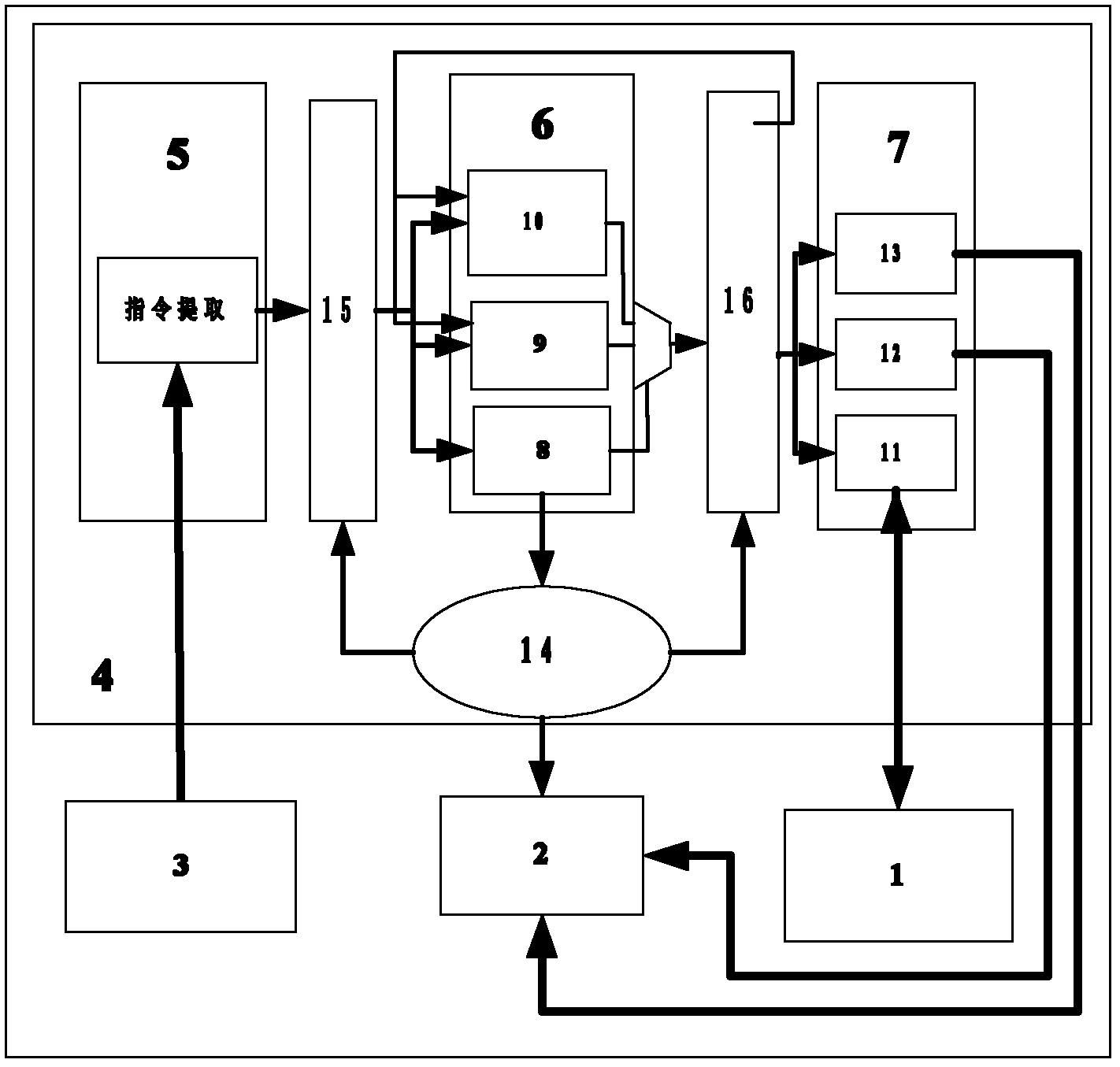
Instruction optimization method and processor for AES (Advanced Encryption Standard) symmetric encryption algorithm
InactiveCN102221990AImprove execution efficiencySave storage spaceMachine execution arrangementsCode spaceAssembly line
The invention discloses an instruction optimization method and an instruction processor for AES (Advanced Encryption Standard) symmetric encryption algorithm, wherein the instruction processor mainly comprises four parts of: a data memory, a code memory, a register file and an assembly line, wherein the assembly line comprises an addressing unit, a decoding unit, an execution unit and an assembly line controller. With the instruction optimization method, in the aspect of execution efficiency is reduced by 57.3x% relative to an ARM (Advanced RISC Machines) processor in a way that the clock periodicity required for AES_ASIP performing AES encryption algorithm is counted through periodic emulation, so that the execution efficiency of the algorithm is greatly improved; and in the aspect of code space, the instruction code occupies 783 bytes of memory space on the ARM processor, while the instruction code on the AES_ASIP just occupies 416 bytes of memory space, so that 46.6x% of code memory space is saved.
Owner:SHANDONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com