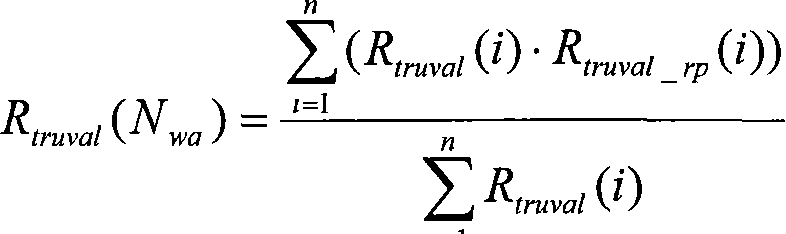Entity authentication method in wireless sensor network
A technology of wireless sensor and authentication method, applied in the field of entity authentication scheme, can solve the problems of large energy consumption of nodes, need of public key infrastructure, hidden dangers of wireless link security, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0092] Below in conjunction with example the present invention will be further described:
[0093] When the network is newly established, the trust value of the nodes in the network is initially 4, and the trust value of the nodes newly added to the network is 4 for its neighbor nodes.
[0094] 1 node trust value obtained
[0095] 1) Trust value collection
[0096] When node A authenticates another node B, node A first checks its own trust list. If node B is in its list, and the trust value is "yes", then B is trustworthy; if the trust value is "no", then B is not trustworthy. If B is not in A's trust list, A sends a request for B's trust value to all trusted nodes in its trust list:
[0097] rreq={request, id A , ID B , time‖K(MAC)}
[0098] Among them, time represents the serial number of the time stamp of sending the packet, which is used to prevent replay. If a trusted node in the list does not know node B, the node forwards A's request to a node in its own trust li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com