Patents
Literature
50 results about "Sensor network security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
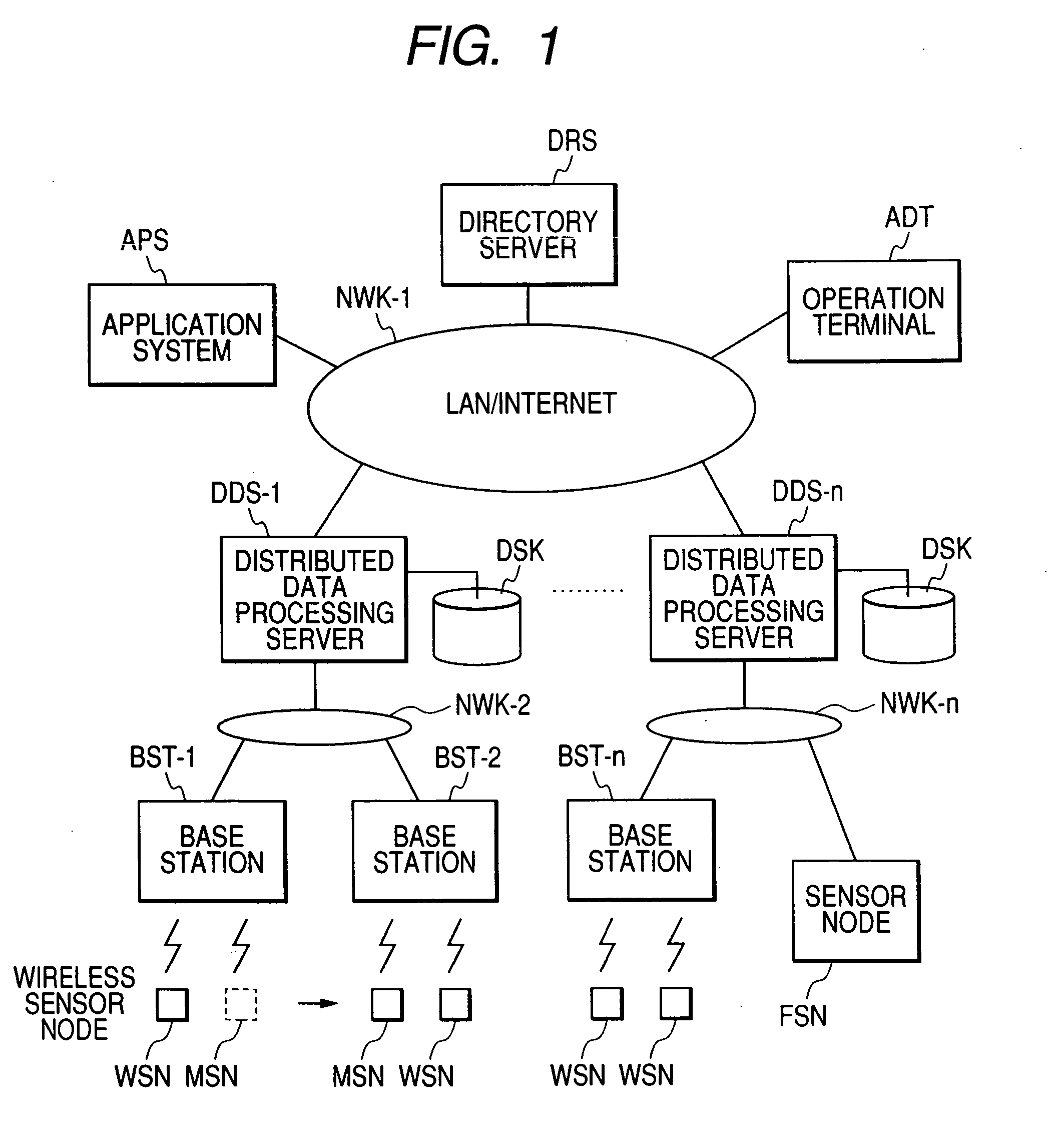
Wireless Sensor Networks Security means secure the data from any kind of attack from outside or inside of the network. This network is always exchange small foot print data in like Sensor reading, Configuration details,Operational data.. and so on.
Protocol for secure and energy-efficient reprogramming of wireless multi-hop sensor networks
ActiveUS8107397B1Energy efficient ICTKey distribution for secure communicationTopology informationReprogramming
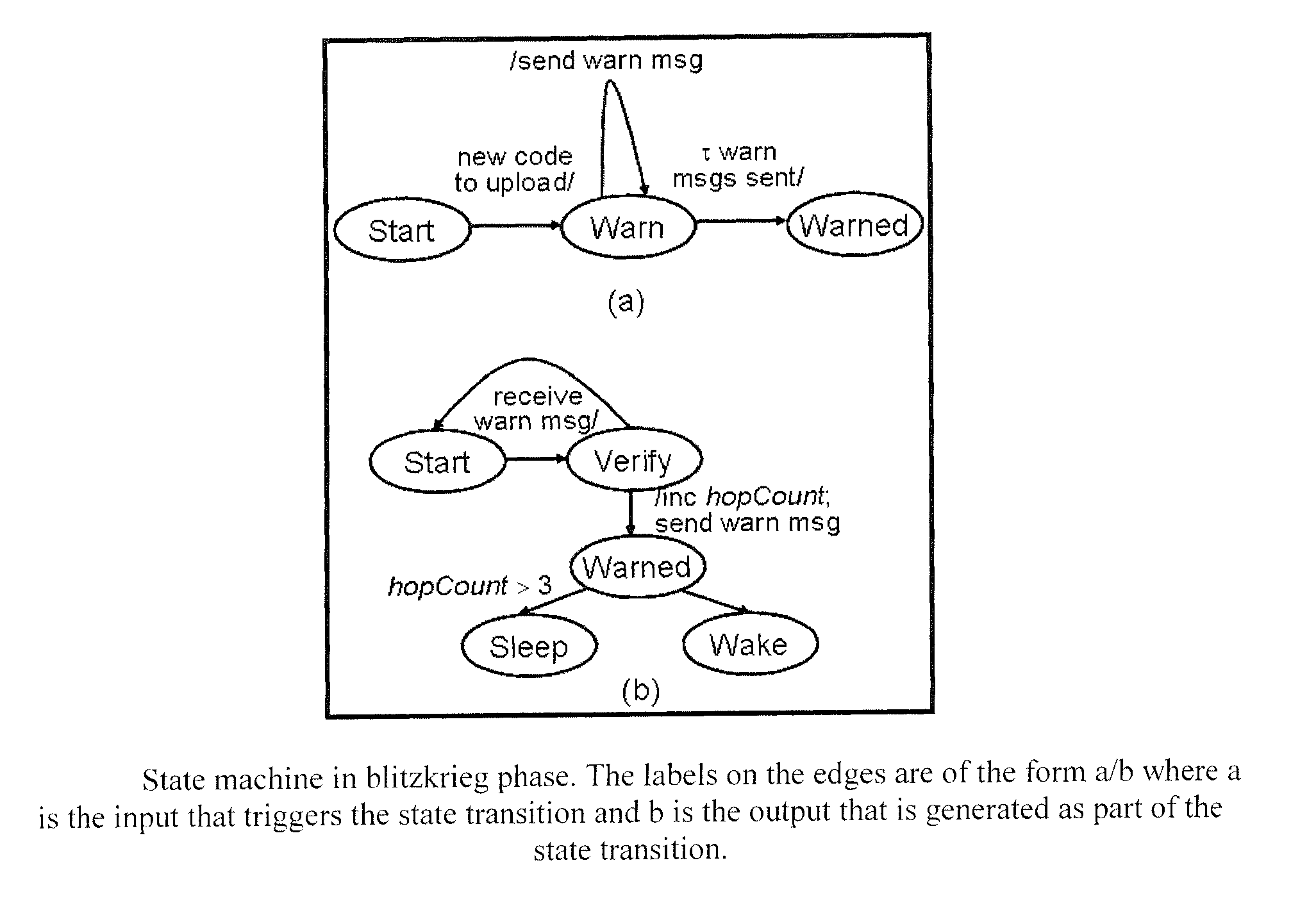
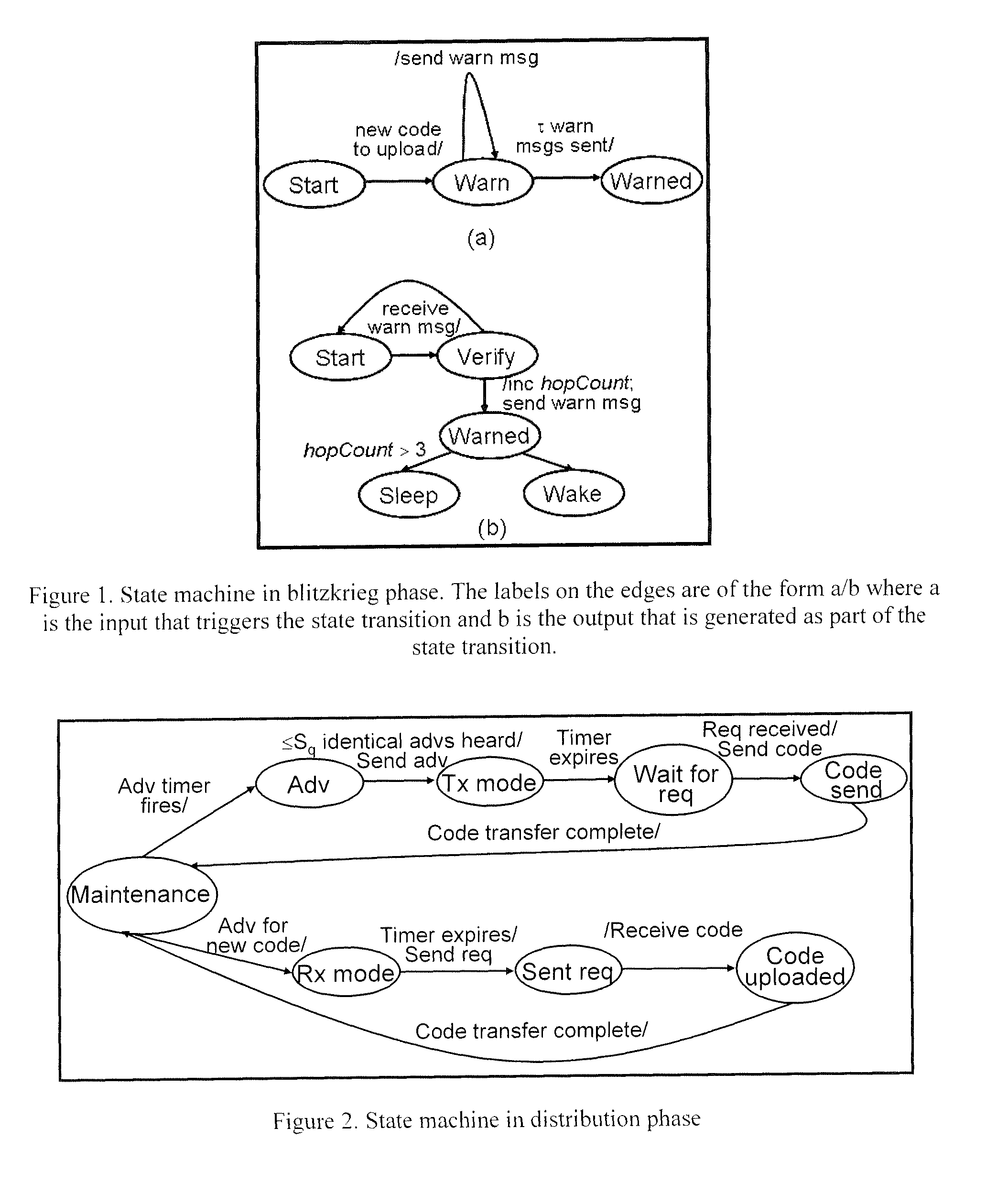
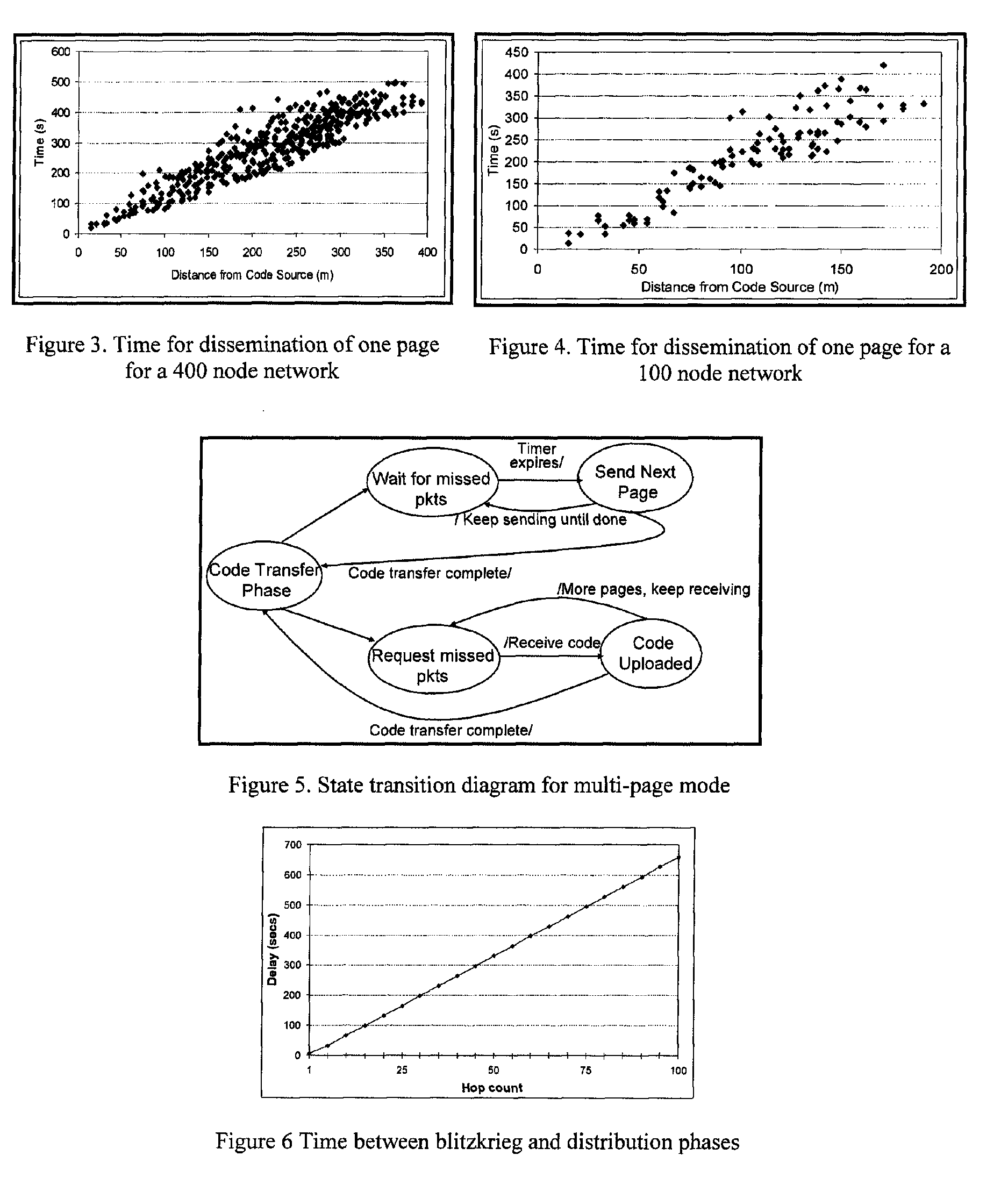
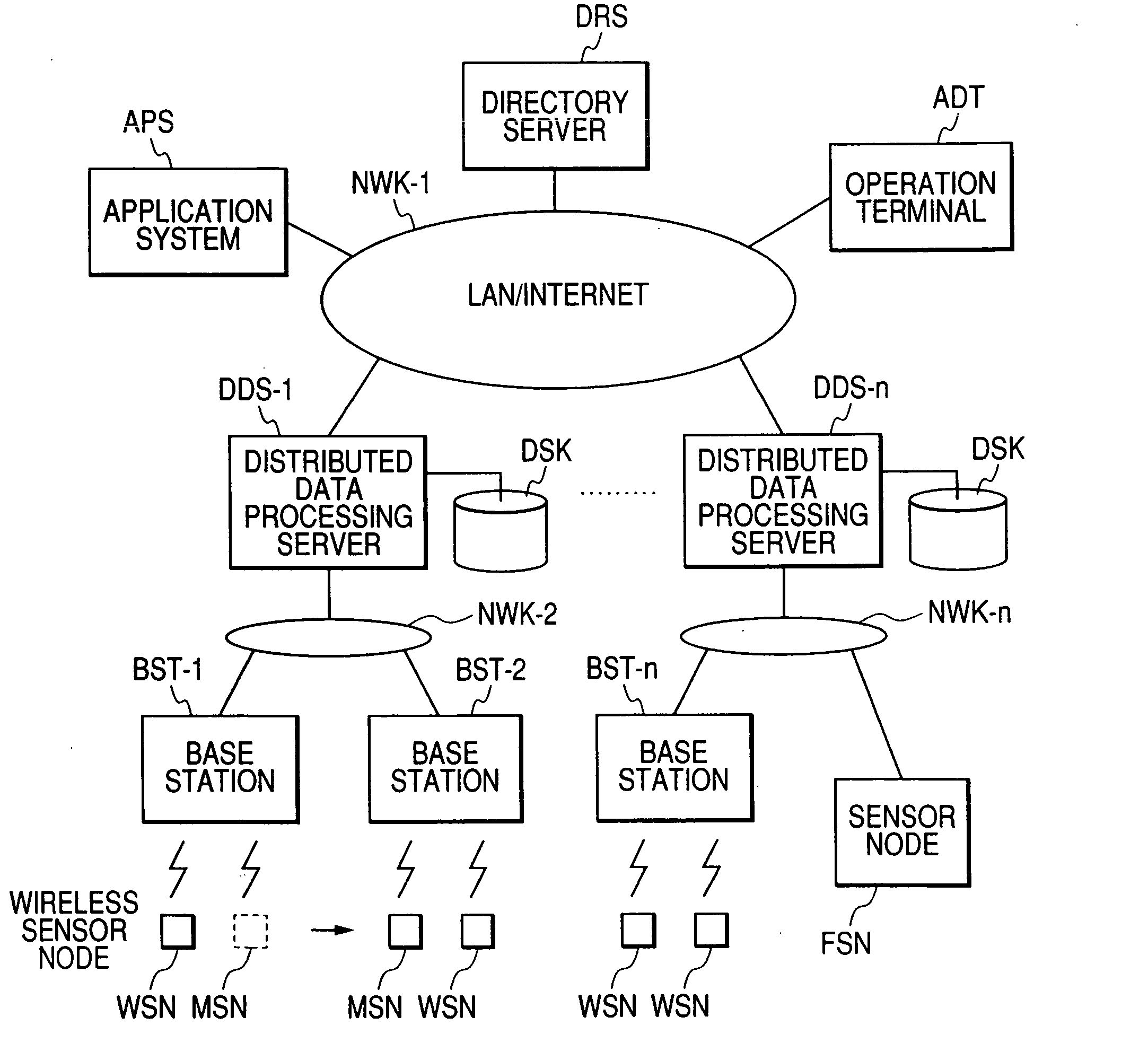
A protocol for optimizing the energy for code upload to sensors in a wireless sensor network and speeding up the dissemination if multiple sources of code are available. Energy optimization is achieved by equipping each node with limited non-local topology information, which it uses to determine the time when it can go to sleep since code is not being distributed in its vicinity. Another aspect of the invention is a protocol that facilitates secure upload of code in the wireless sensor network. The secure communication protocol divides the sensor field into control groups each with a control node, and manages data exchange between nodes within a control group through the mediation of a control head which provides the common key. The keys are refreshed periodically and the control nodes are changed periodically to enhance security. The protocol facilitates secure communication between sensor nodes despite the compromise of any number of other nodes in the network.
Owner:PURDUE RES FOUND INC
Security system
ActiveUS20060212570A1Strong expandabilityEasy to controlElectric signal transmission systemsMultiple keys/algorithms usageAnomalous behaviorComputer science
A security system with processing optimized for monitoring the actions of a surveillance subject and detecting abnormal actions. The action record of an individual is monitored using a sensor network security system SNS, and the development of an action event is reported as an action, and the corresponding processing of the security system SCS is determined based on this action.
Owner:HITACHI INFORMATION & CONTROL SOLUTIONS LTD
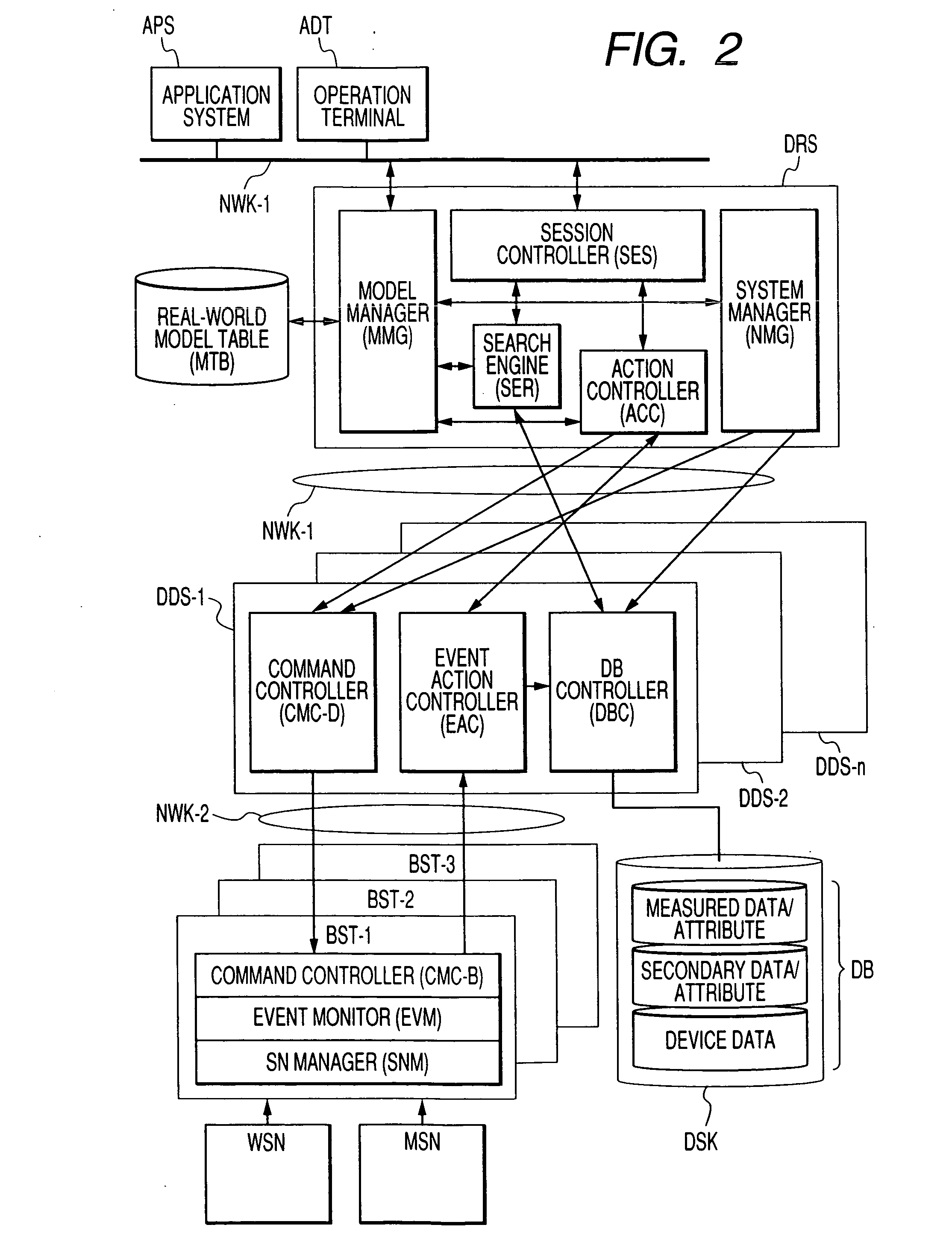
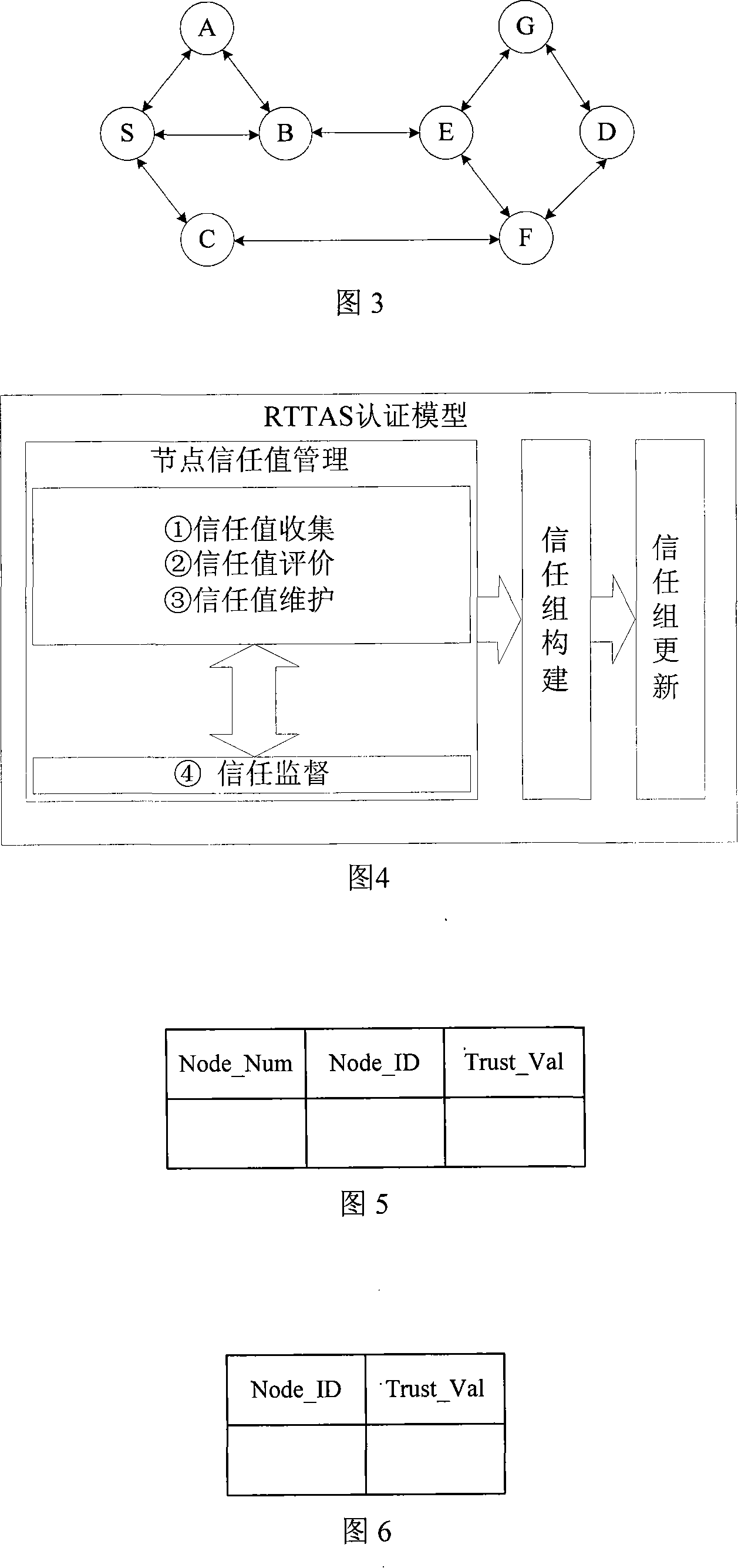
Entity authentication method in wireless sensor network
InactiveCN101159748AEffective Security Authentication PolicyProlong lifePublic key for secure communicationUser identity/authority verificationInformation transmissionDigital signature
The invention provides an entity authentication method in a wireless sensor network, relating to the application field related to sensor network security in information security technology. The invention can ensure the safe communication among nodes by authenticating the identity of nodes in the wireless sensor network. The authentication for determining whether a node is legal and trustable comprises node trust value management, trust group construction, and trust group updating so as to store corresponding trust value in the node. In the information transmission process, the node can determine the information transmission manner and path according to the magnitude of the trust value. The method can acquire effective security authentication strategy by using the ideal of node reputation and the trust group, and can obviate the problem of large calculation amount of digital signature by using public key algorithm, thereby to effectively reduce the authentication delay and improve the network lifetime.
Owner:UNIV OF SCI & TECH BEIJING
Security system
ActiveUS7755480B2Easily utilize informationIncrease valueElectric signal transmission systemsMultiple keys/algorithms usageSecurity systemSensor network security
Owner:HITACHI INFORMATION & CONTROL SOLUTIONS LTD
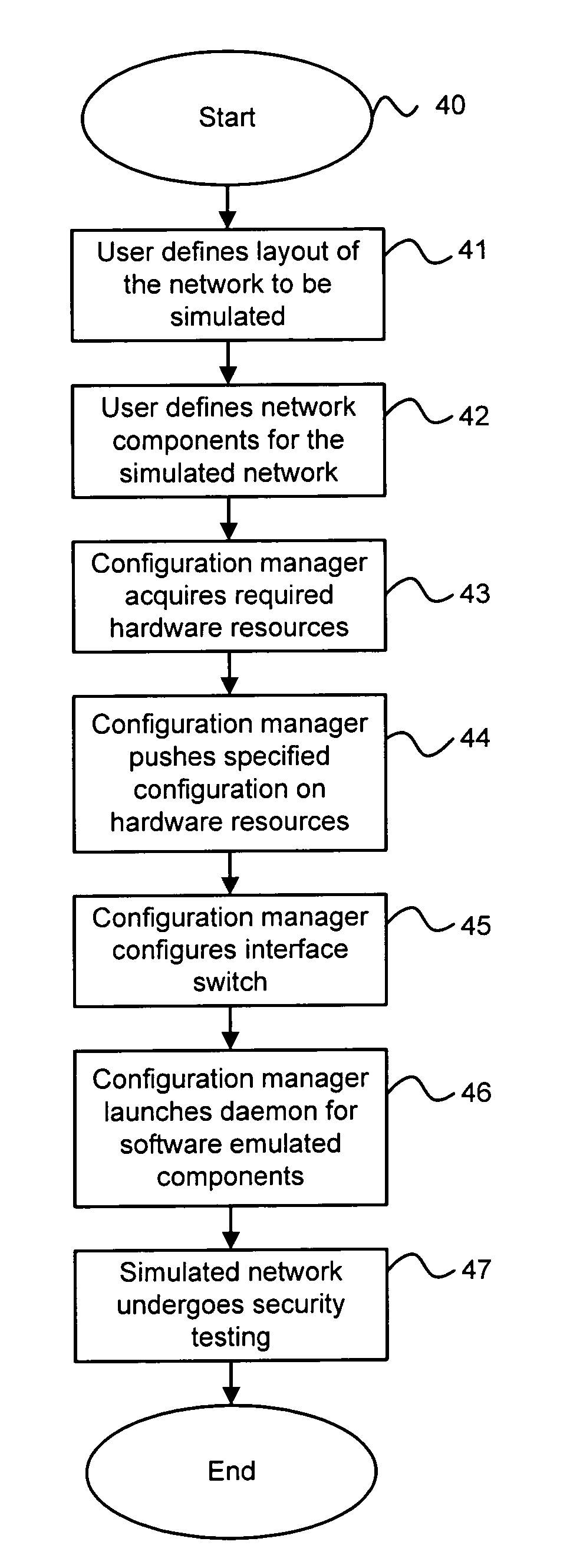
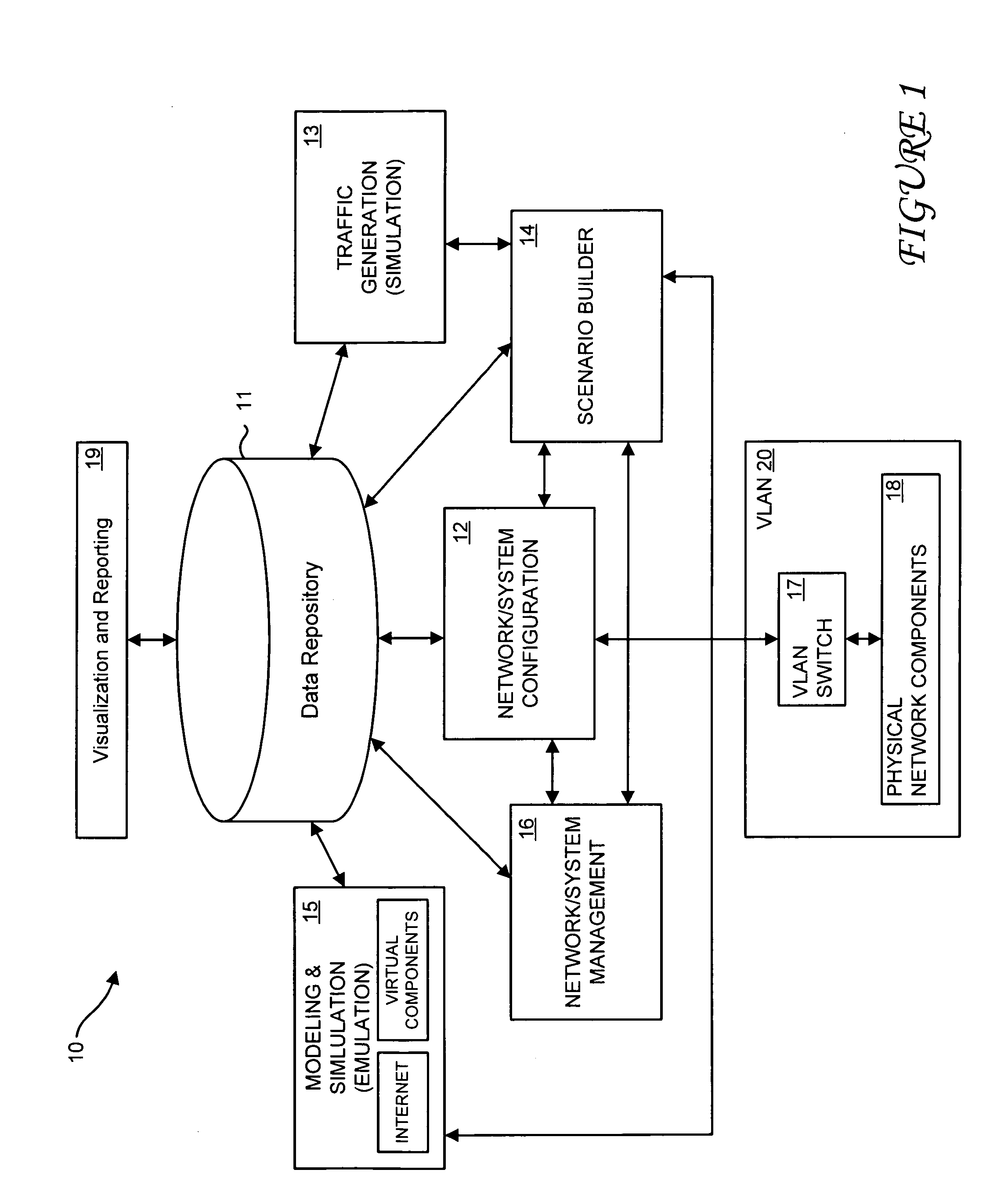
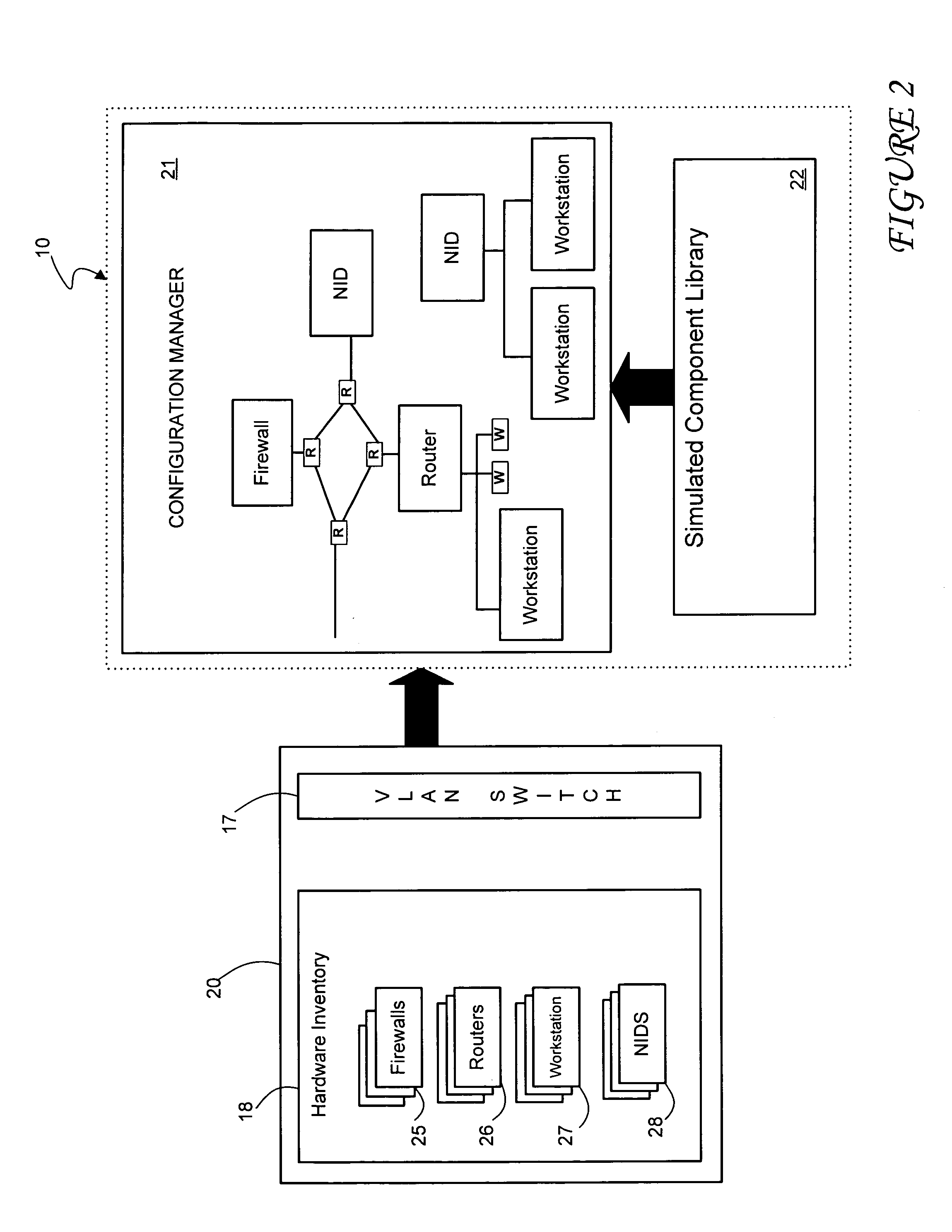
Method and system for simulating computer networks to facilitate testing of computer network security
InactiveUS7379857B2Error preventionFrequency-division multiplex detailsAnalog computerReal-time testing
A method and system for simulating computer networks and computer network components to test computer network security is disclosed. A user specifies a desired configuration of a simulated computer network by using a configuration manager. The user also defines all the network components within the simulated computer network by specifying whether a component should be provided in hardware or should be simulated via software. Upon receiving the above-mentioned information from the user, the configuration manager acquires the required hardware resources from a hardware inventory. The configuration manager utilizes an interface switch that connects the hardware in the hardware inventory to produce the desired network layout. Next, the specified configuration for each of the network components is pushed into the acquired hardware resources. Computer network components to be simulated with software are subsequently initialized by the configuration manager. At this point, the user can use the simulated computer network for real-time testing of network security.
Owner:LOCKHEED MARTIN CORP
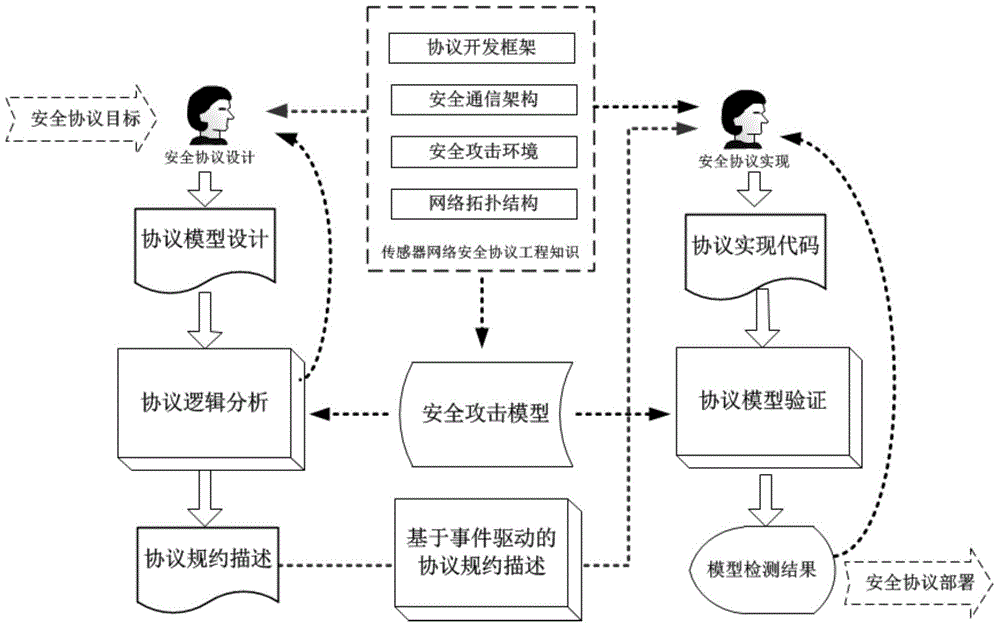
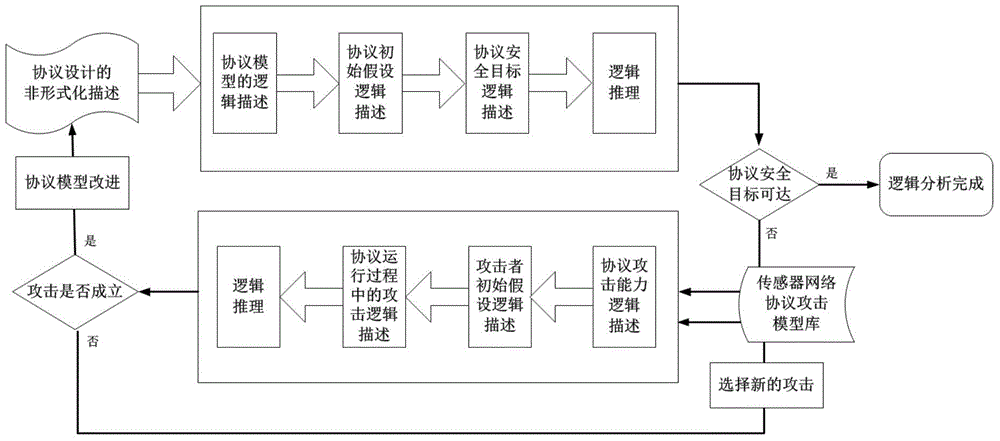
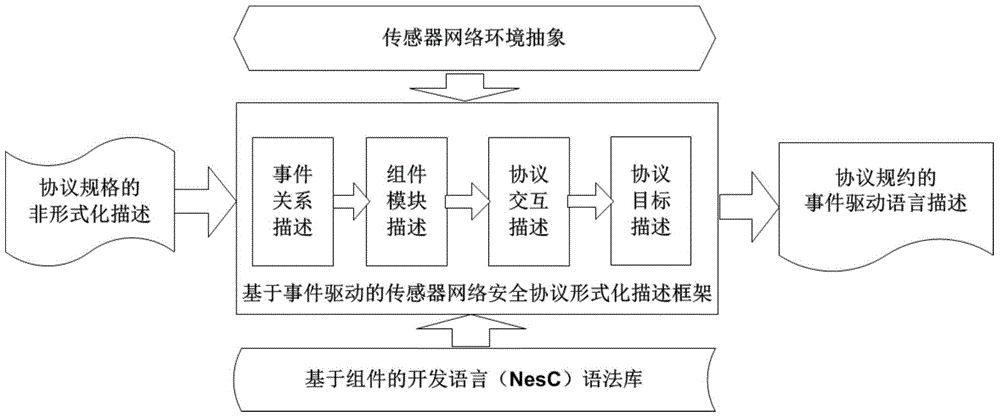
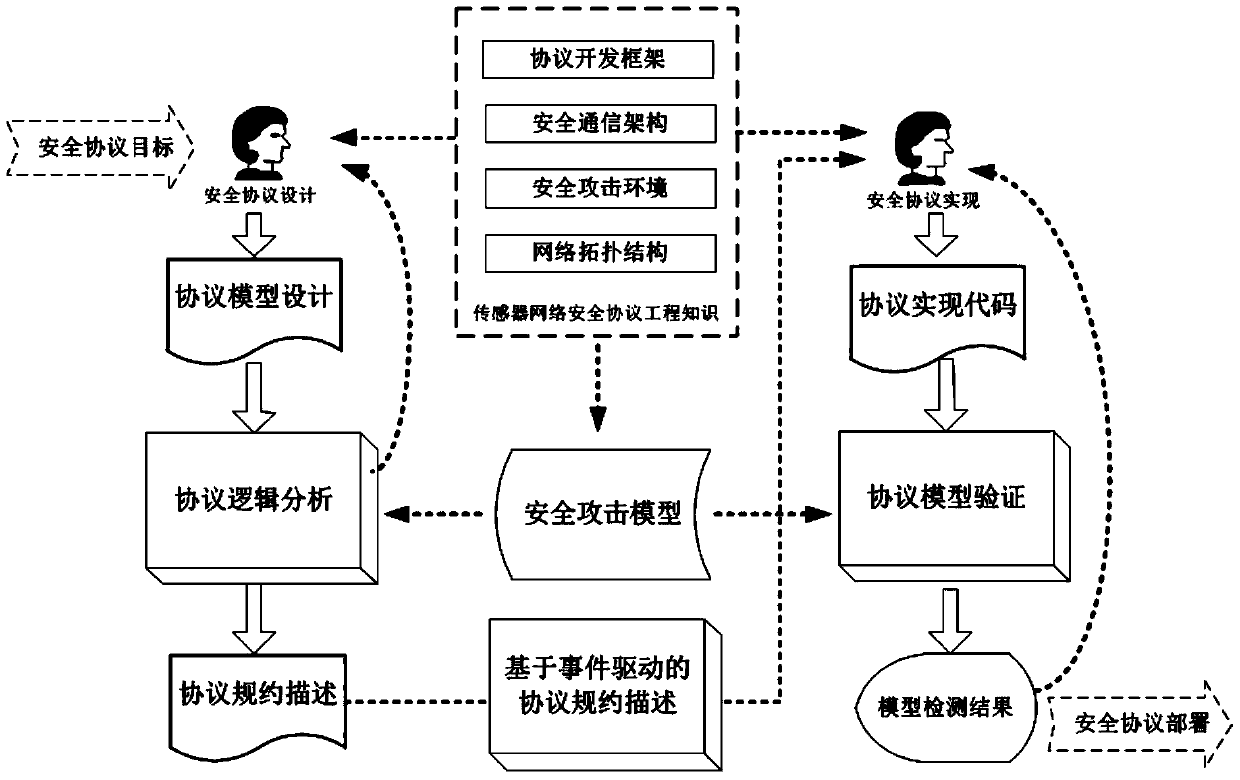
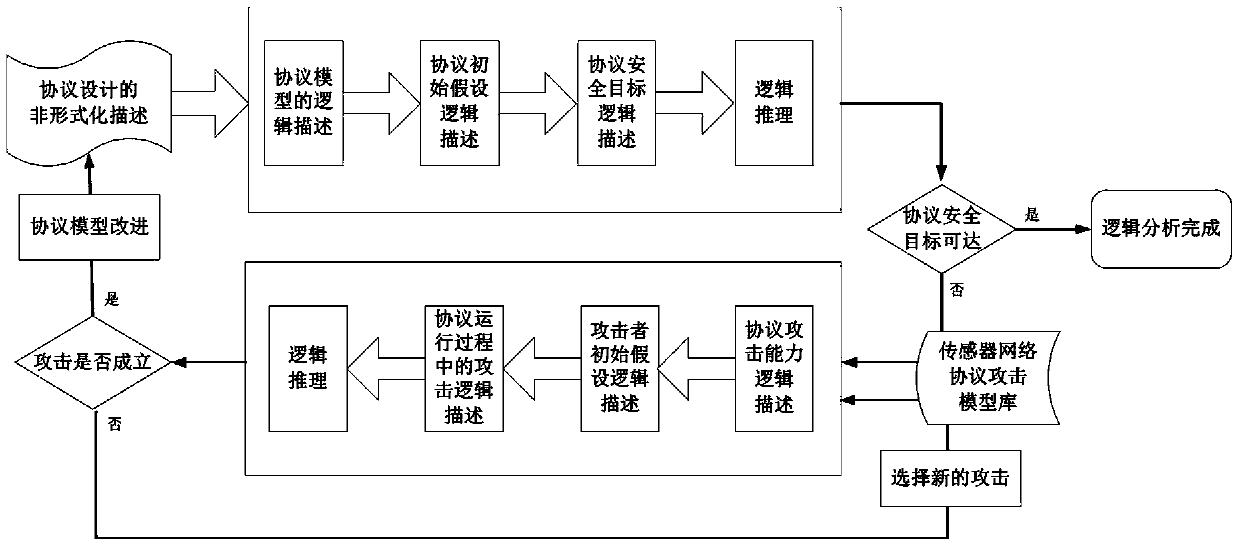
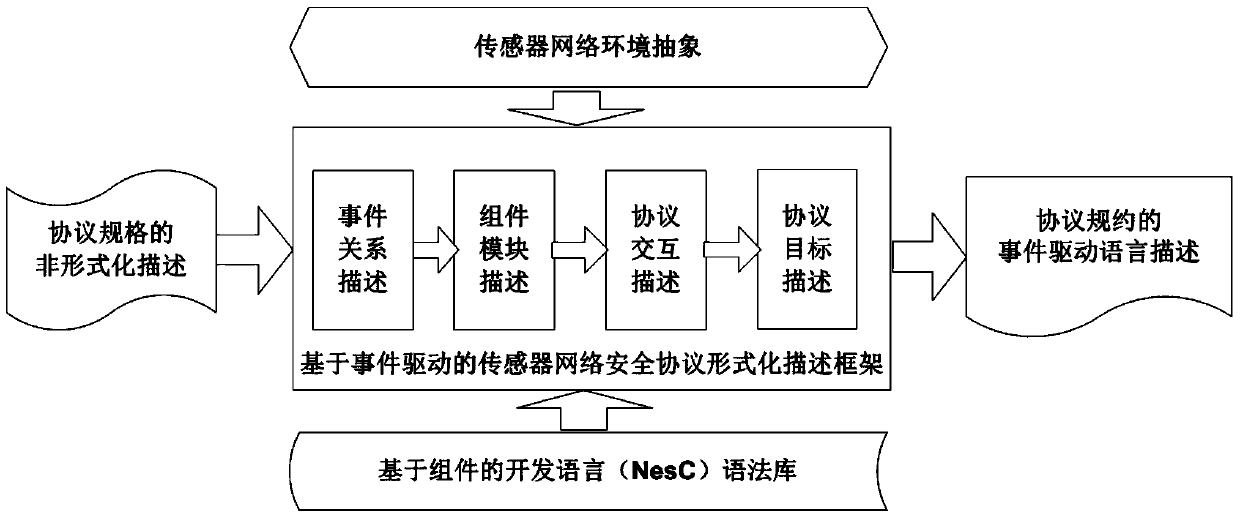
Formal verification method for facing design and accomplishment of wireless sensing network safety protocol
ActiveCN104135397ASimple designImprove development efficiencyData switching networksProtocol designValidation methods
A formal verification method for facing design and accomplishment of a wireless sensing network safety protocol, comprises the following steps: (1) a sensing network safety protocol design method based on logical analysis: a designer of the sensor network safety protocol accepting a protocol design goal, and designing a protocol rudiment based on analysis of sensor network environmental factors; establishing a logical reasoning system to accomplish protocol modeling and logical analysis, amending the protocol design plan according to the analysis result, and repeating logical analysis until the logic of the protocol is correct; and giving description of the protocol specification which is not formalized finally; (2) a safety protocol specification description language facing the sensing network developing environment; and (3) a safety protocol code automatic verification method based on model checking. The present invention effectively ensures safety and efficiency of the design and development and has good expansibility.
Owner:ZHEJIANG UNIV OF TECH
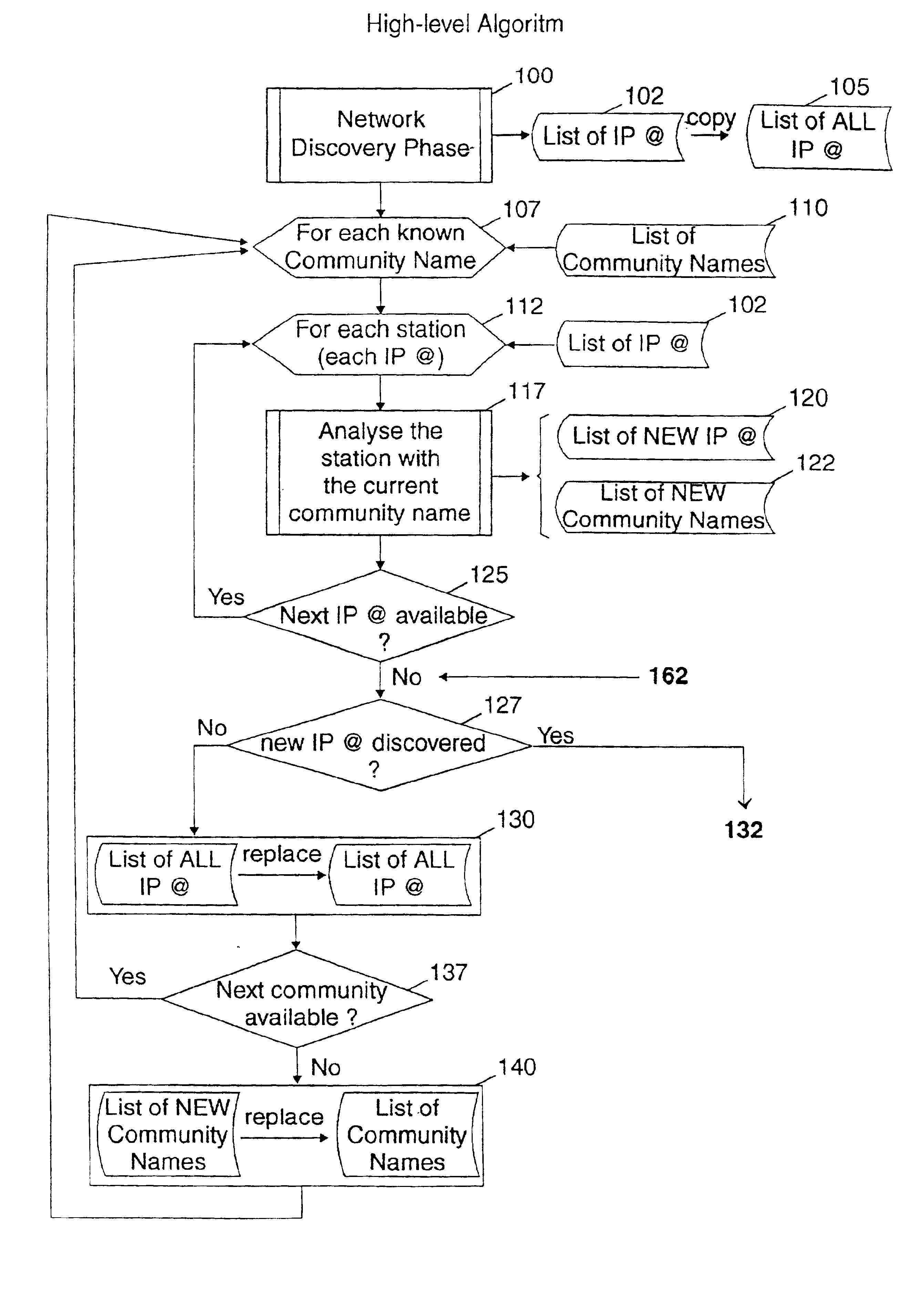
Method and system for evaluating network security
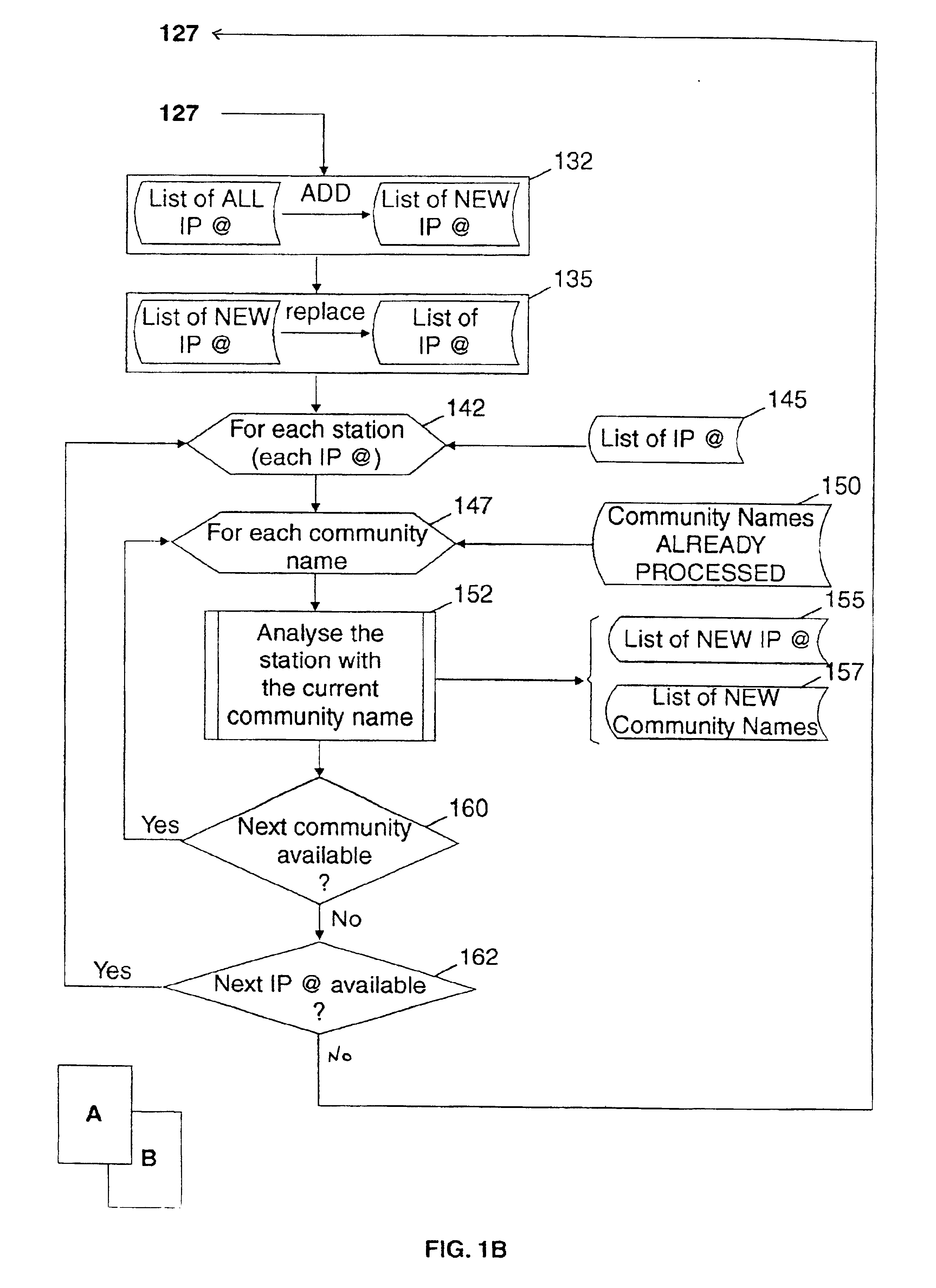
InactiveUS6895436B1Multiple digital computer combinationsData switching networksIp addressNetwork security policy
A method for automatically identifying from an ordinary station connected to a TCP / IP network, the network components managed by a network management station for which it is possible to read or write over the confidential network data they store. Starting from the list of the default passwords protecting the network data and the IP addresses of the network components communicating with the ordinary station, the method allows by repeating the IP address discovery process, to discover step by step the passwords used in all the network components managed by the network management station and try to use them in reading or writing network information.The method allows detecting the lack of protection by password which usually occurs in campus networks and thus auditing such networks against intrusion from one of the stations of the network.
Owner:IBM CORP
Apparatus, method and system for improving network security
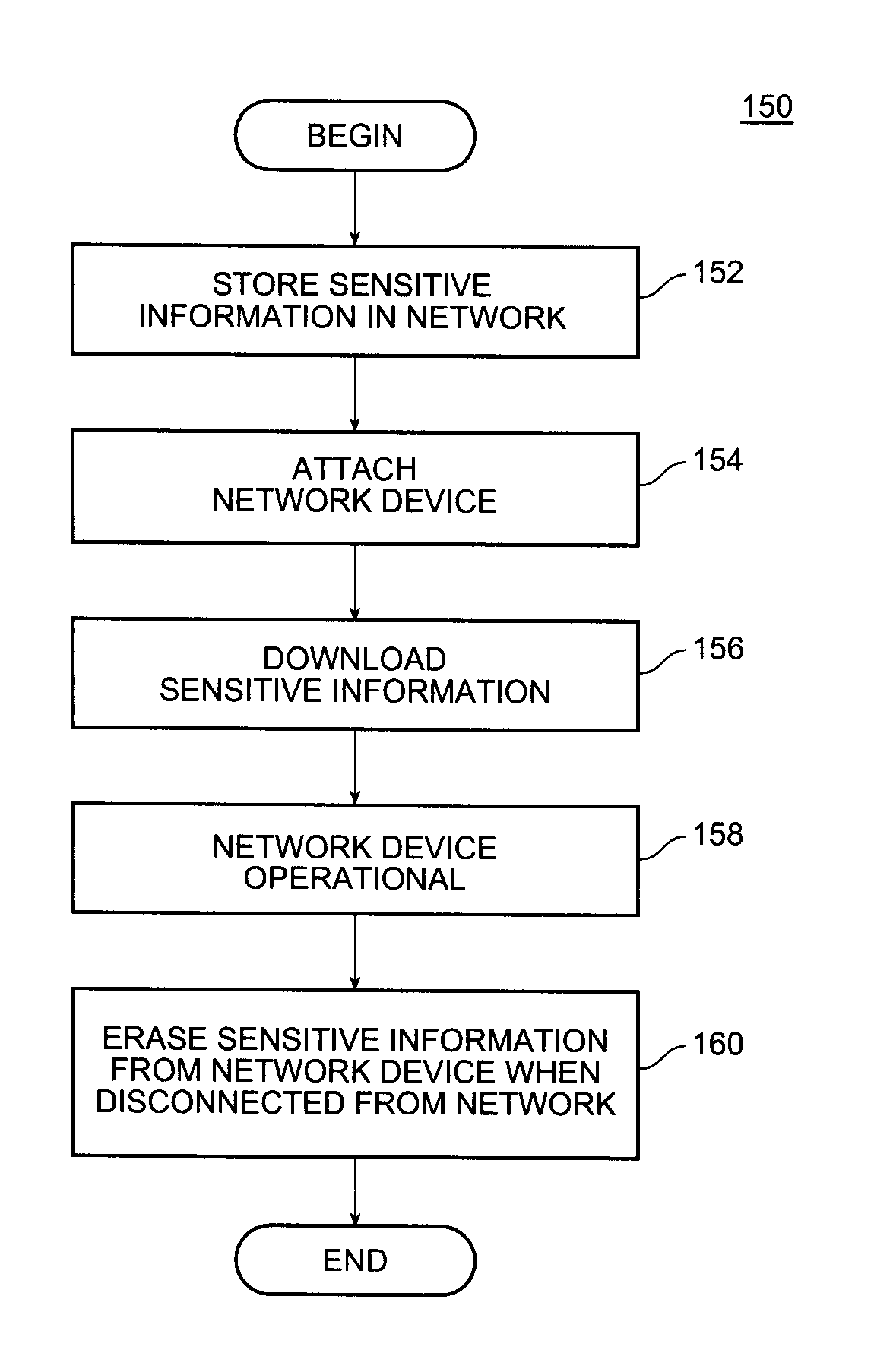
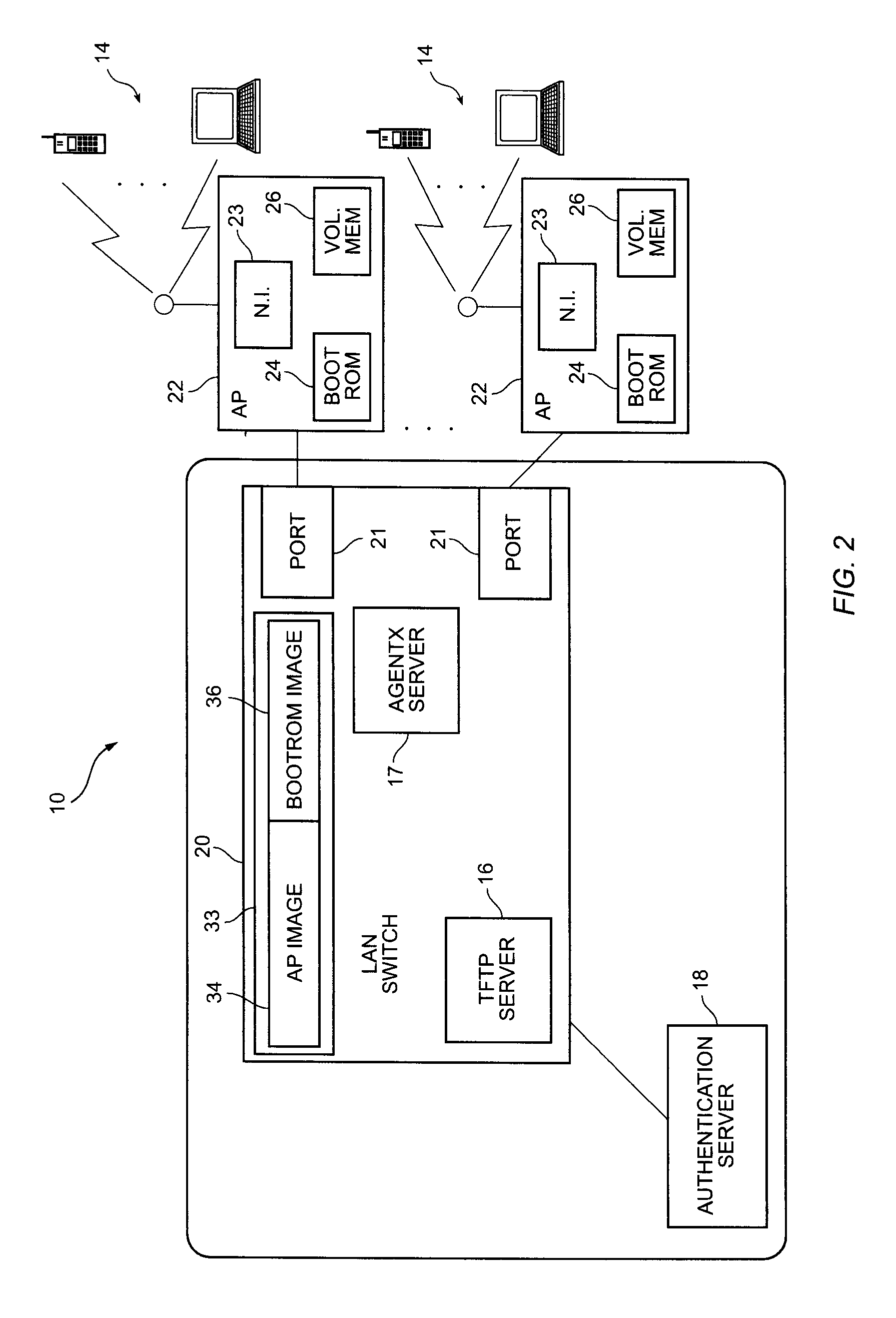
ActiveUS7577996B1Improve network securityStop theftUnauthorised/fraudulent call preventionDigital data processing detailsPasswordNetwork security policy
Devices, systems and related methods are disclosed for improving operational security of a network and / or network devices, such as wireless access points (APs). In the disclosed systems, a network device is not fully operational until it is attached to a network and downloads sensitive information. The information is stored in the network device so that when the device is disconnected from the network, the sensitive information is erased from the device, making the device inoperative and removing sensitive information, such as passwords, network security keys, or the like. Disabling the network device in this manner not only prevents the theft of sensitive network access information, by also discourages theft of the device itself because it cannot be used on another network without the configuration information. In addition to downloading configuration information, the network device can also download an executable image that is likewise not permanently resident on the device.
Owner:EXTREME NETWORKS INC
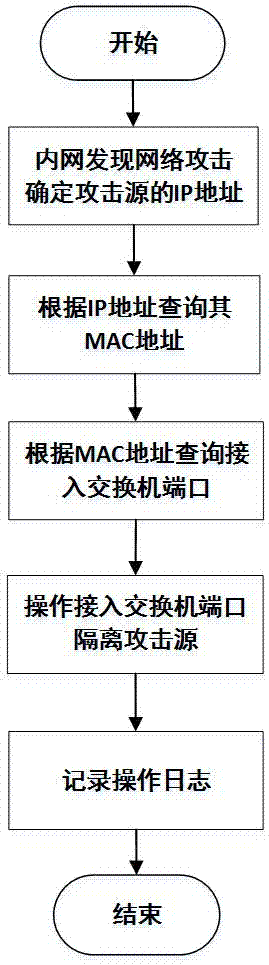
Automatic locating and isolating method of internal attack source of local area network
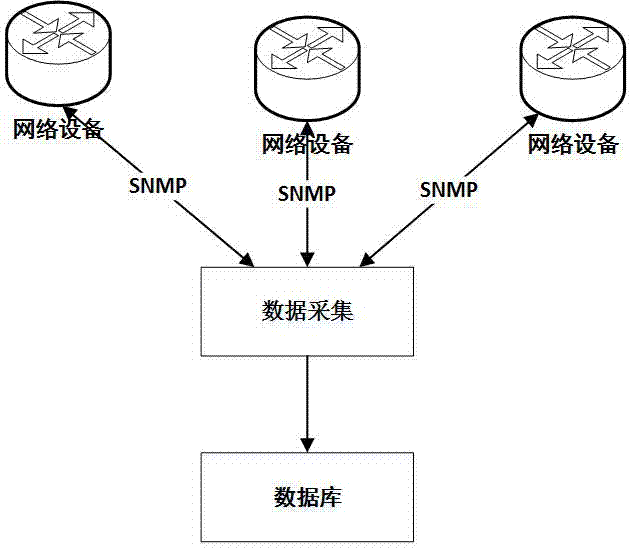
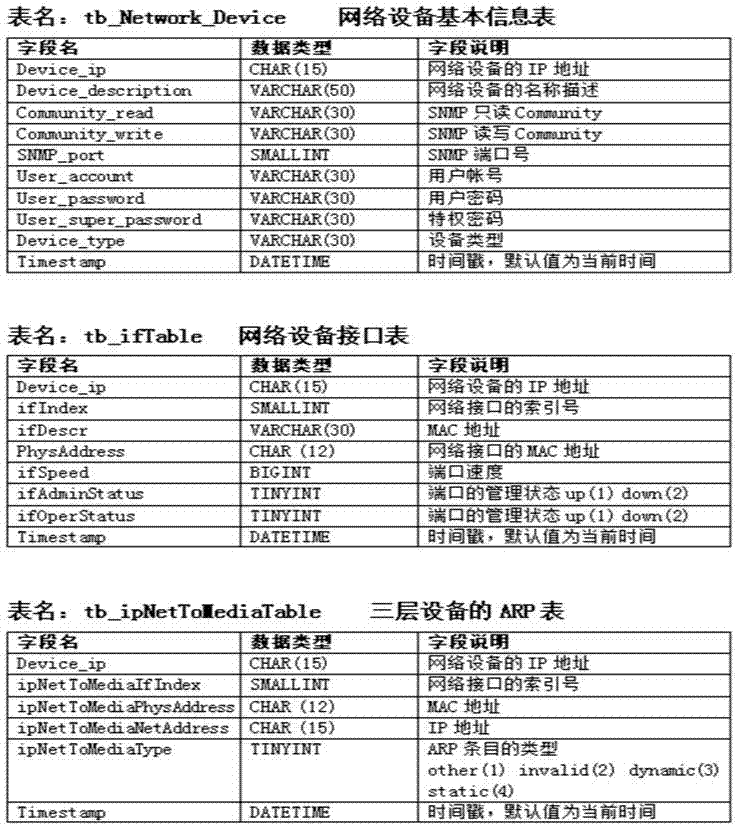
The embodiment of the invention discloses an automatic locating and isolating method of an internal attack source of a local area network. The method comprises the following steps: automatically collecting data of a network device, and storing the data in a database, inquiring an MAC address of the network device according to an IP address of the attack source, detecting ARP fraud counterfeiting the host and matching the timestamps of different IP-MAC items to automatically process the situation that one IP address corresponds to a plurality of MAC addresses, locating a switch port according to the MAC address, and filtering a cascade port of the switch and matching the timestamps of different MAC-switch port items to automatically process the situation that one MAC address corresponds to a plurality of switch ports, and operating the switch to isolate the attack source. The automatic locating and isolating method can be applicable to all kinds of network environments without any manual operation, the larger the network scale is, the more obvious the effect of the automatic locating and isolating method is, by adoption of the automatic locating and isolating method, the processing time of a network security event can be shortened, the working efficiency of a network administrator is improved, and the network security of the local area network is ensured.
Owner:SHANTOU UNIV
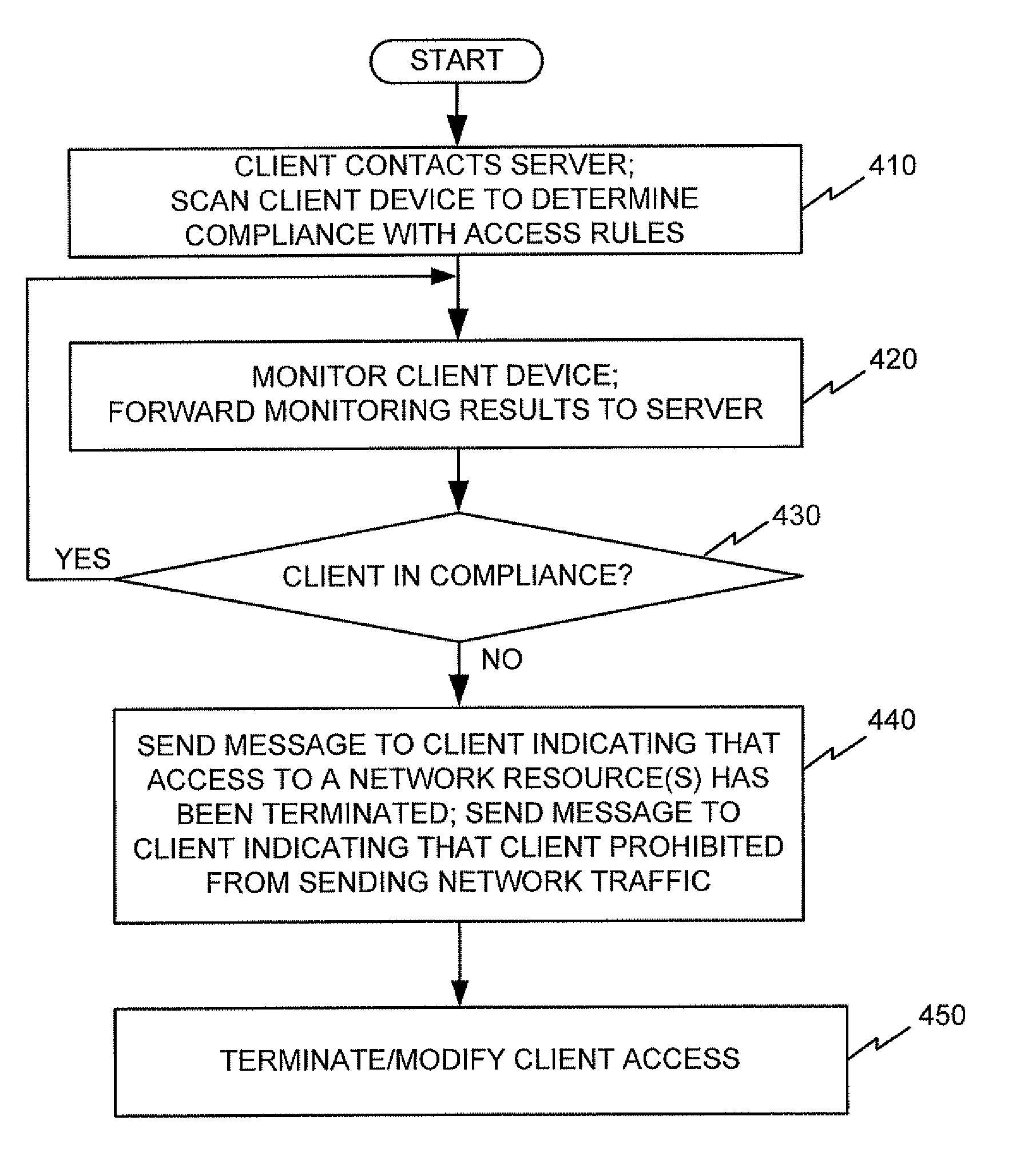
Dynamic access management for network security
Owner:PULSE SECURE
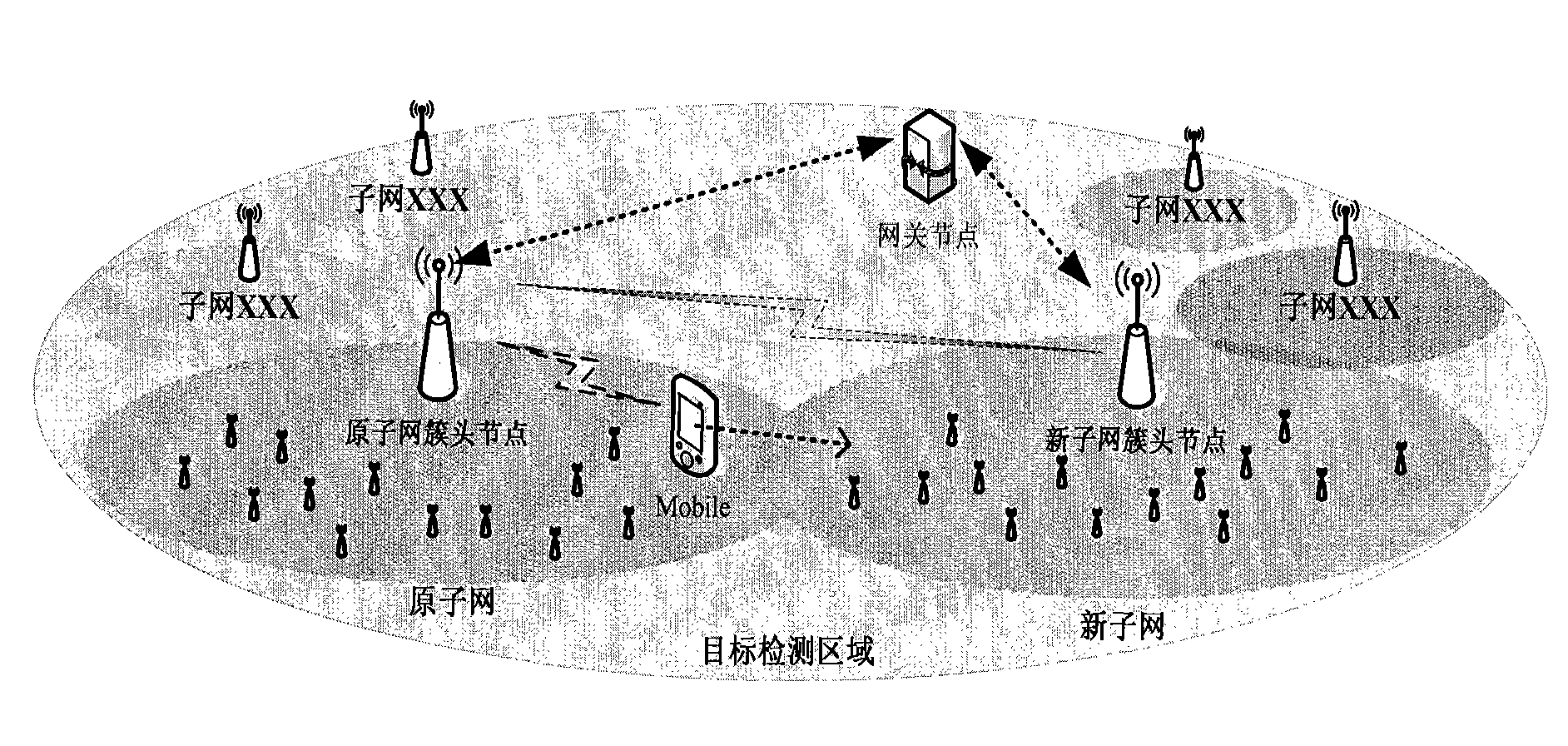
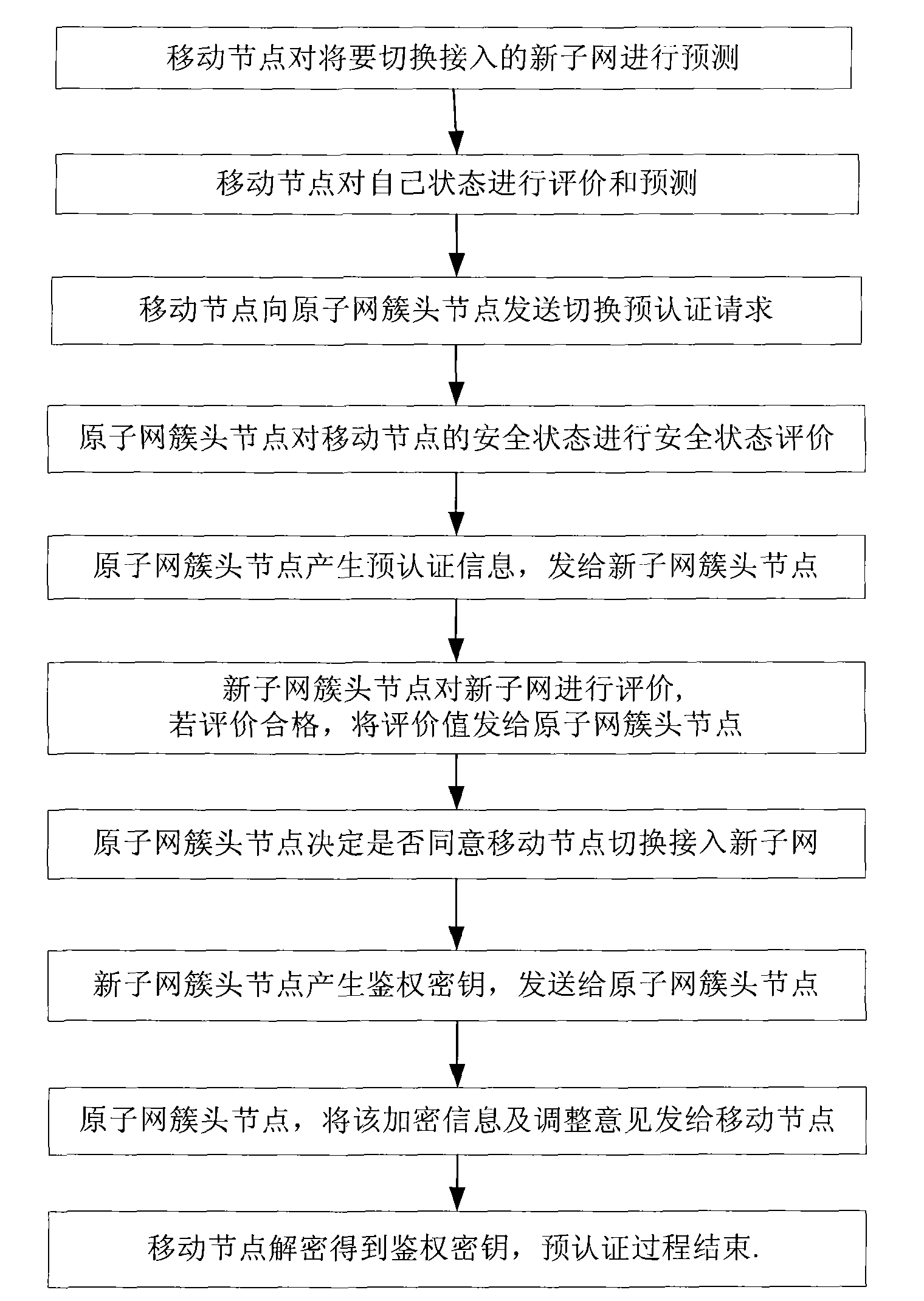
Wireless sensor network switching and pre-authenticating method based on evaluation
InactiveCN101873591AAuthentication supportSolve the delay problemNetwork topologiesSecurity arrangementWireless sensor networkingAuthentication information
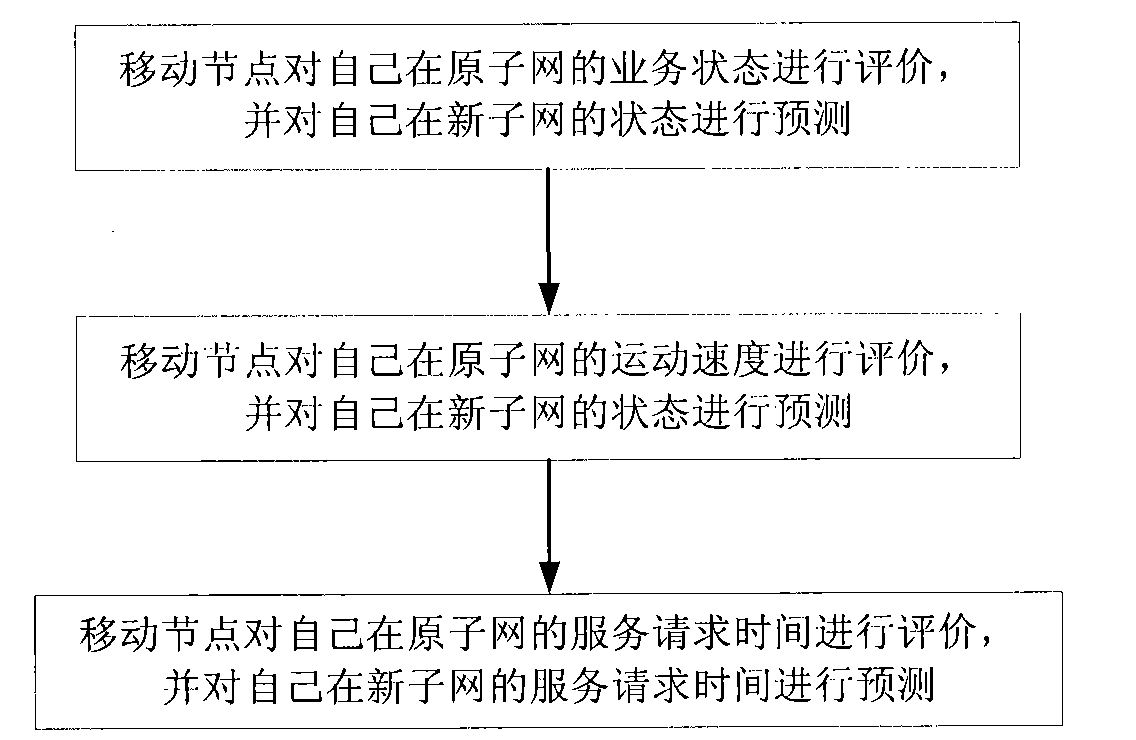
The invention discloses a wireless sensor network switching and pre-authenticating method based on evaluation, comprising the steps of: 1, predicting a new subnet to be switched by a mobile node, evaluating and predicting the mobile node, and making a pre-authenticating request; 2, evaluating the mobile node by the original subnet cluster head node, if the evaluation is safe, sending pre-authenticating information to a new subnet cluster head node; 3, evaluating the new subnet by the new subnet cluster head node, and authenticating the identity of the mobile node, if the evaluation is qualified, passing the authentication, agreeing to access, and sending evaluation information to the original subnet cluster head node; 4, deciding whether agreeing to access or not by the original subnet cluster head node according to the request of the mobile node and the evaluation on the new subnet, giving an adjustment suggest; and 5, if agreeing to access, negotiating a private key between the mobile node and the new subnet cluster head node. The invention has the advantages of short time delay, high safety and long service life of a sensor network, and can be applied to the field of sensor networks with high requirements for time delay and safety.
Owner:XIDIAN UNIV +2
Portable security device and method for providing network security
ActiveCN103051601AUser identity/authority verificationSecurity arrangementUser deviceNetwork connection
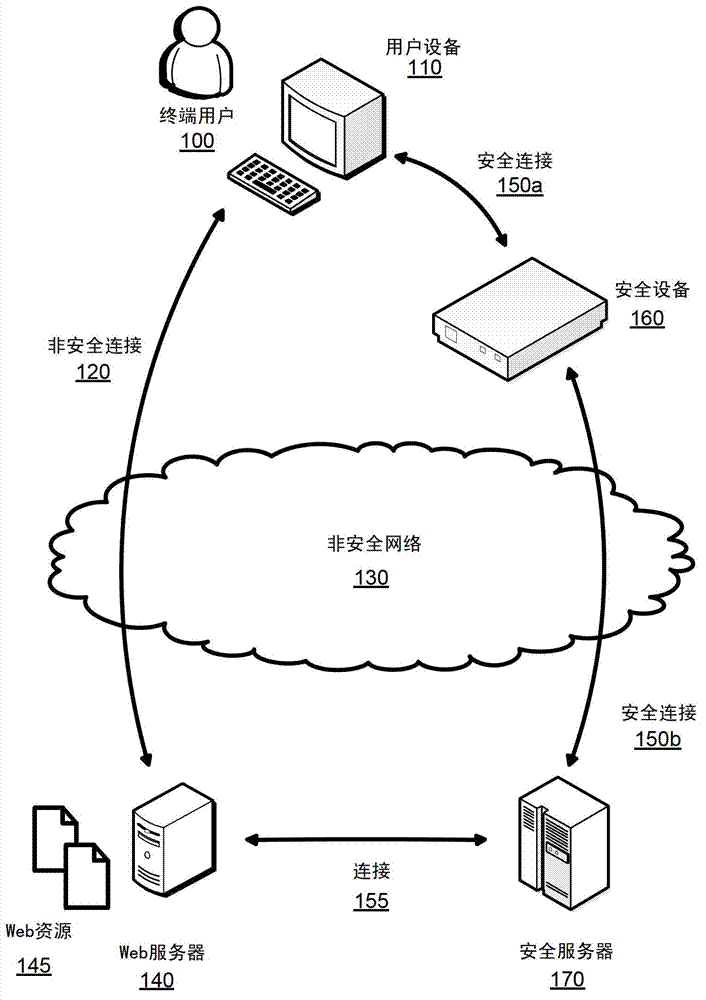
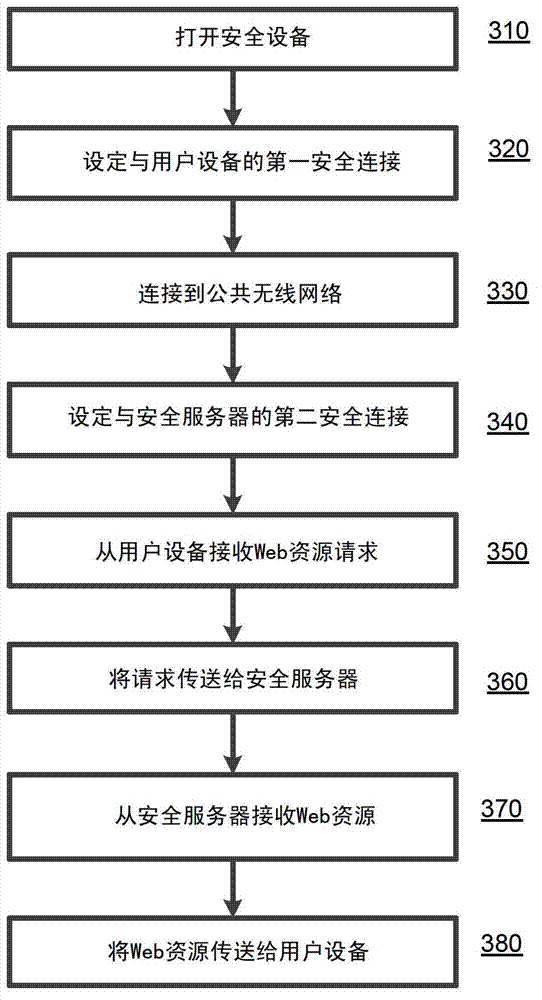
Disclosed herein are systems, methods and computer program products for providing secure Internet access to a user device in an unsecure network environment, such as a public wireless network. The system includes a portable security device configured to establishing a first secure direct wireless connection with the user device and a second secure network connection through the public wireless network to a security server, which provides Internet access. The security device provides Internet browser and e-mail application, which can be used instead of unsecure applications of the user device to access Web resources through the first and second secure network connections. In addition, the security device includes a secure keyboard, which can be used by the device user instead of the unsecure keyboard of the user device to enter user authentication data for accessing the desired Web resources.
Owner:AO KASPERSKY LAB
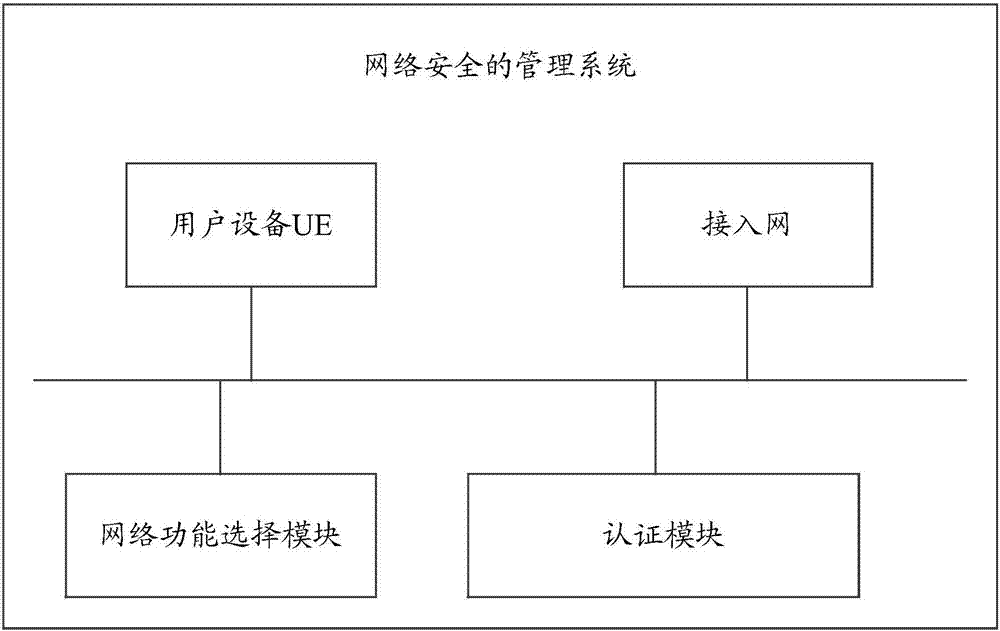
A management system, method and apparatus for network security
ActiveCN107579948AImprove securityMeet security needsSecurity arrangementSecuring communicationNetwork security policyProtocol for Carrying Authentication for Network Access
The embodiment of the invention discloses a management system, method and apparatus for network security. The system includes UE, an AN, a network function selection module and at least two authentication modules. The UE is used to send a first service request to the network function selection module, wherein the first service request carries authentication protocol information. The network function selection module is used to select a target authentication module according to the authentication protocol information and send a second service request to the target authentication module; and thetarget authentication module is used to perform mutual authentication with the UE; and the target authentication module is further used to determine first security configuration according to a specified security policy and send the first security configuration to the AN. The AN is used to determine second security configuration according to the first security configuration or the specified security policy and send the second security configuration to the UE. The technical solution provided by the invention can meet the security requirements of differentiated authentication protocols and security policies of the network so as to improve network security.
Owner:HUAWEI TECH CO LTD
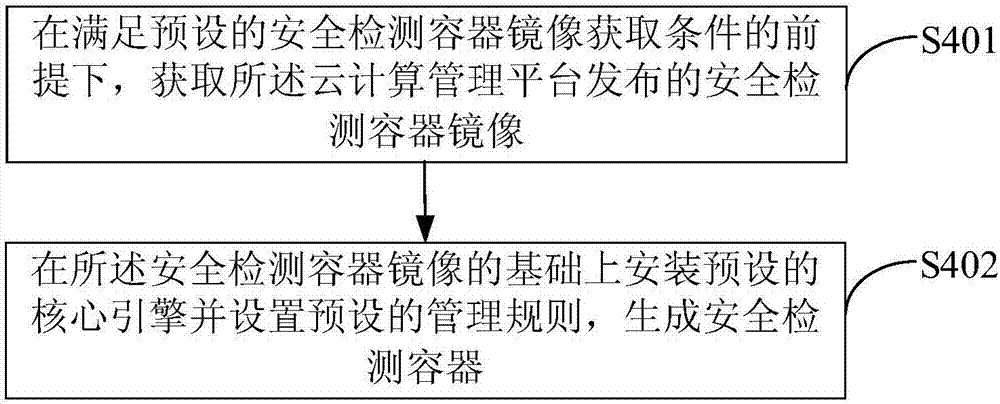
System for providing network security as a service in cloud computing environment
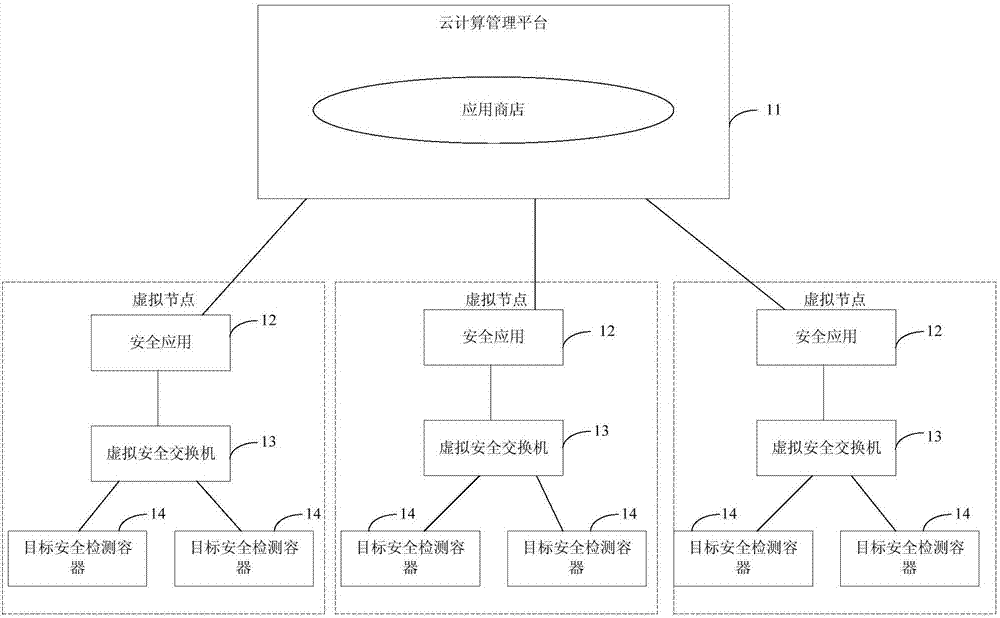
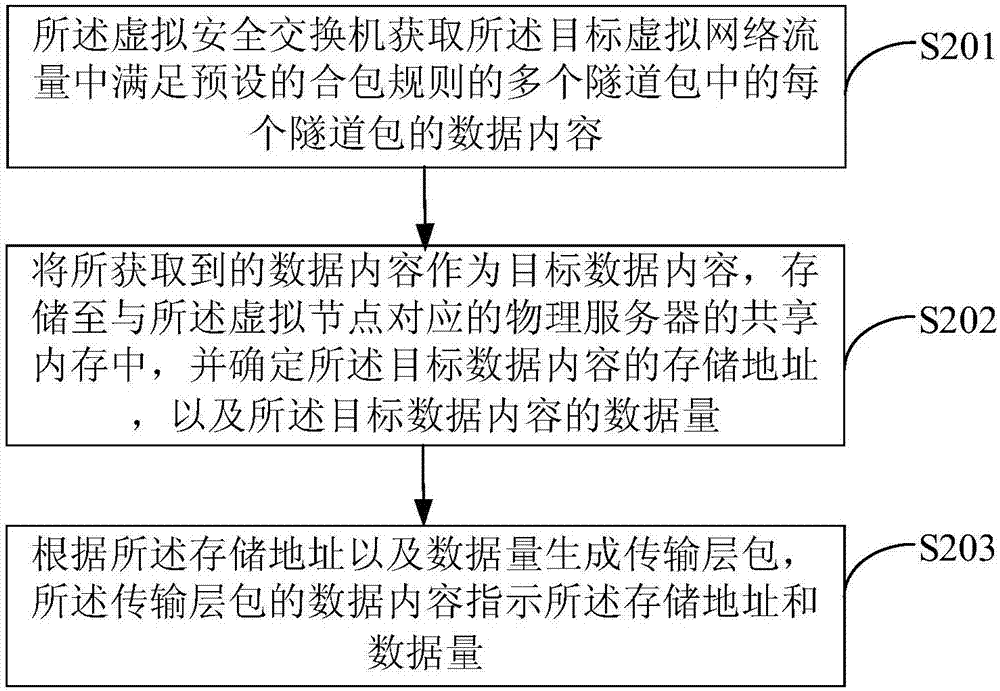
The embodiment of the invention provides a system for providing network security as a service in a cloud computing environment. The system comprises a cloud computing management platform, security applications corresponding to virtual nodes in a virtual network, virtual security switches and a target security detection containers. The virtual security switches process a plurality of tunnel packets in target virtual network traffic corresponding to the virtual nodes, thereby obtaining a transmission layer packet, and transmits the transmission layer packet to each target security detection container for security detection. After the security detection of the transmission layer packet is successful, the transmission layer packet is processed and transmitted, so security service is provided for the virtual network, and the security of the virtual network is improved. In a mode that the plurality of tunnel packets are combined into one transmission layer packet and the transmission layer packet is transmitted to each target security detection container for security detection, the transmission speed is improved, the number of the data packets on the target security detection containers is reduced, the data packet processing performance of the target security detection containers is improved, and the energy consumption of the whole system is reduced.
Owner:BEIJING BAIWU TECH CO LTD
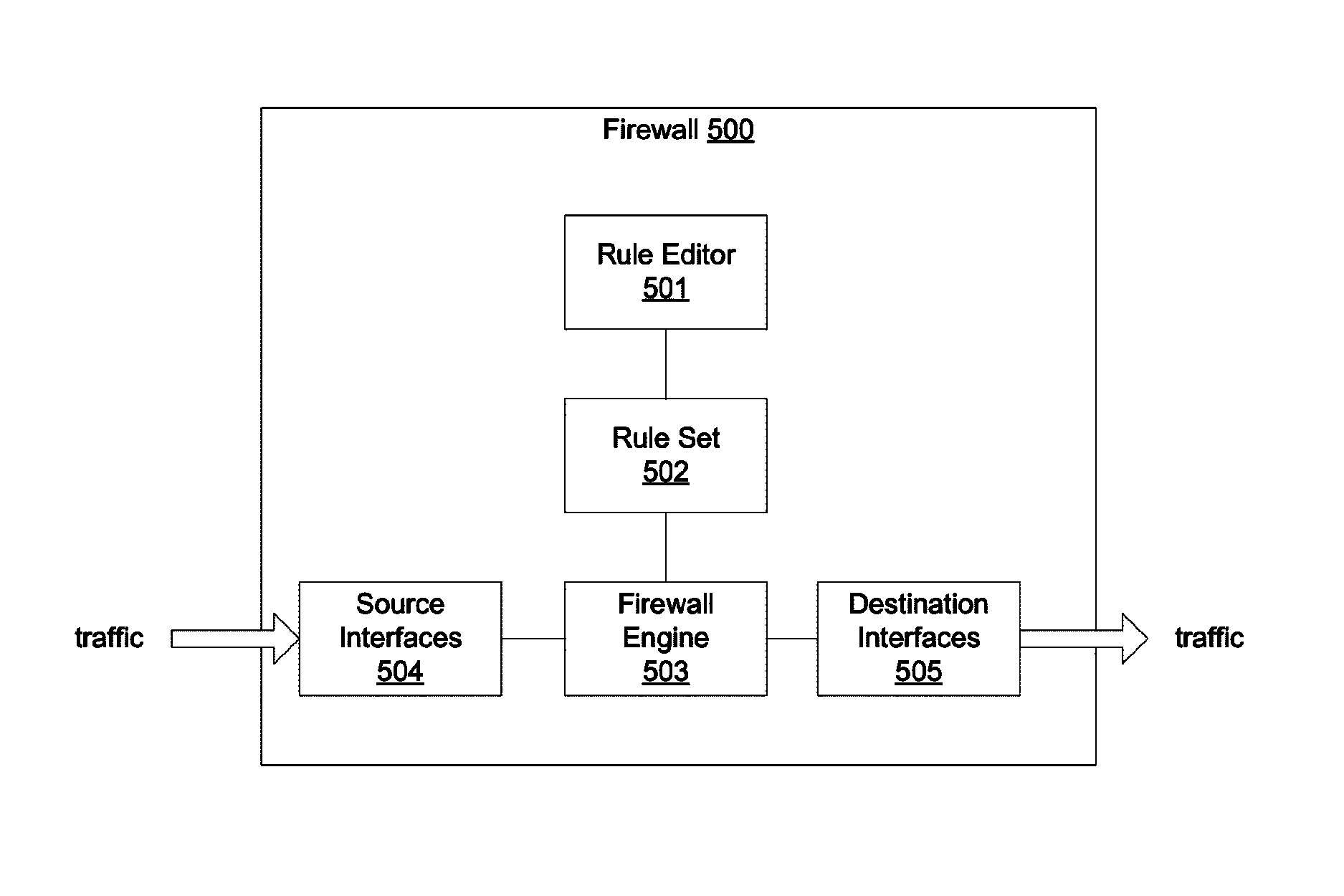
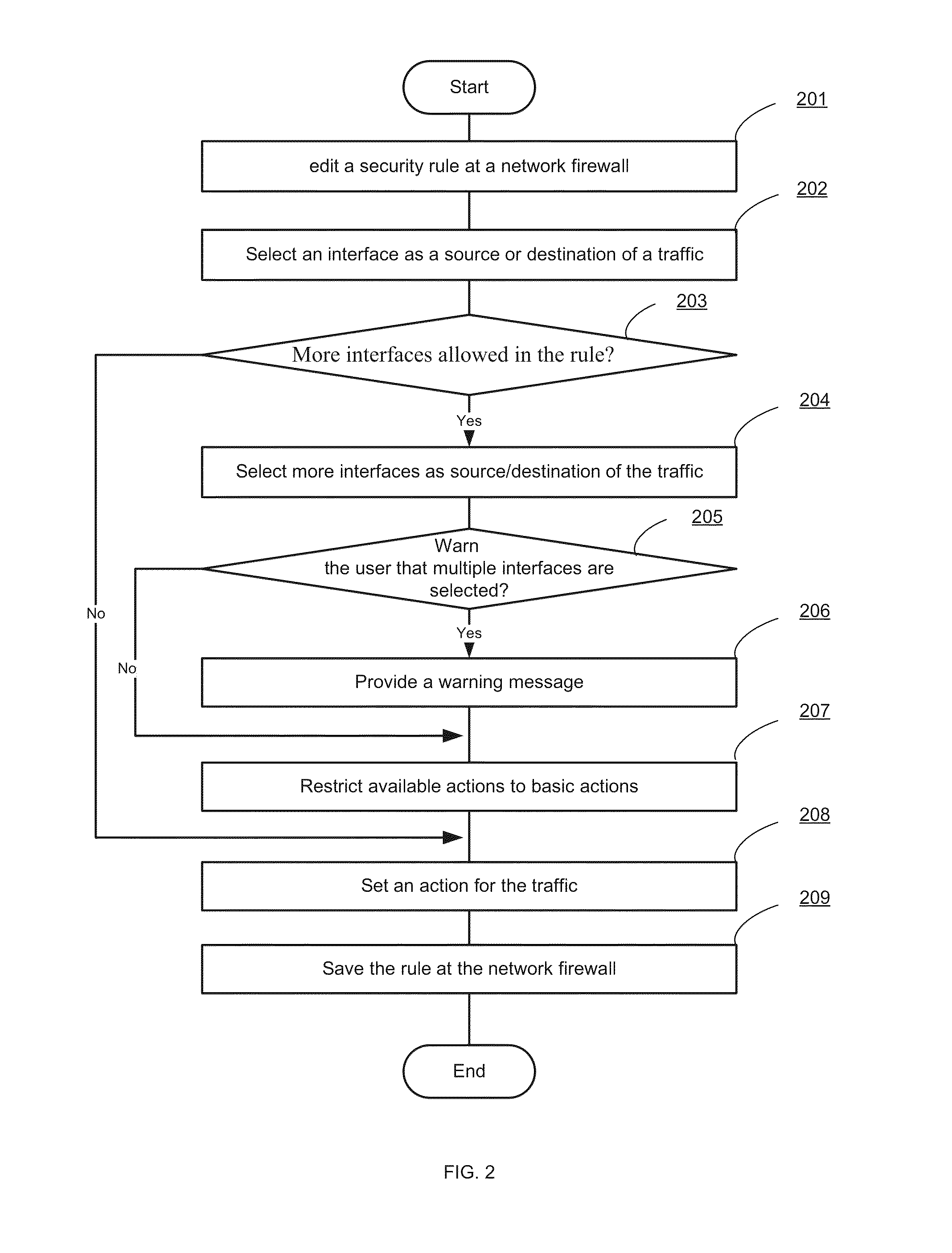
Interface groups for rule-based network security
Systems and methods for designating a proper subset of interfaces of a network security appliance as source / destination interfaces in connection with defining a security rule pertaining to a traffic flow are provided. According to one embodiment, a security rule configuration interface is provided through which a network administrator can specify parameters of security rules to be applied to traffic attempting to traverse the network security appliance. Interface information, defining a traffic flow to be controlled by a security rule, is received via the configuration interface. The interface information specifies multiple interfaces, representing a proper subset of the interfaces of the network security appliance, as source / destination interfaces of the traffic flow. Information regarding an action to be performed on the traffic when the security rule is matched is received via the configuration interface. The security rule is stored as part of a rule set to be applied to the traffic.
Owner:FORTINET
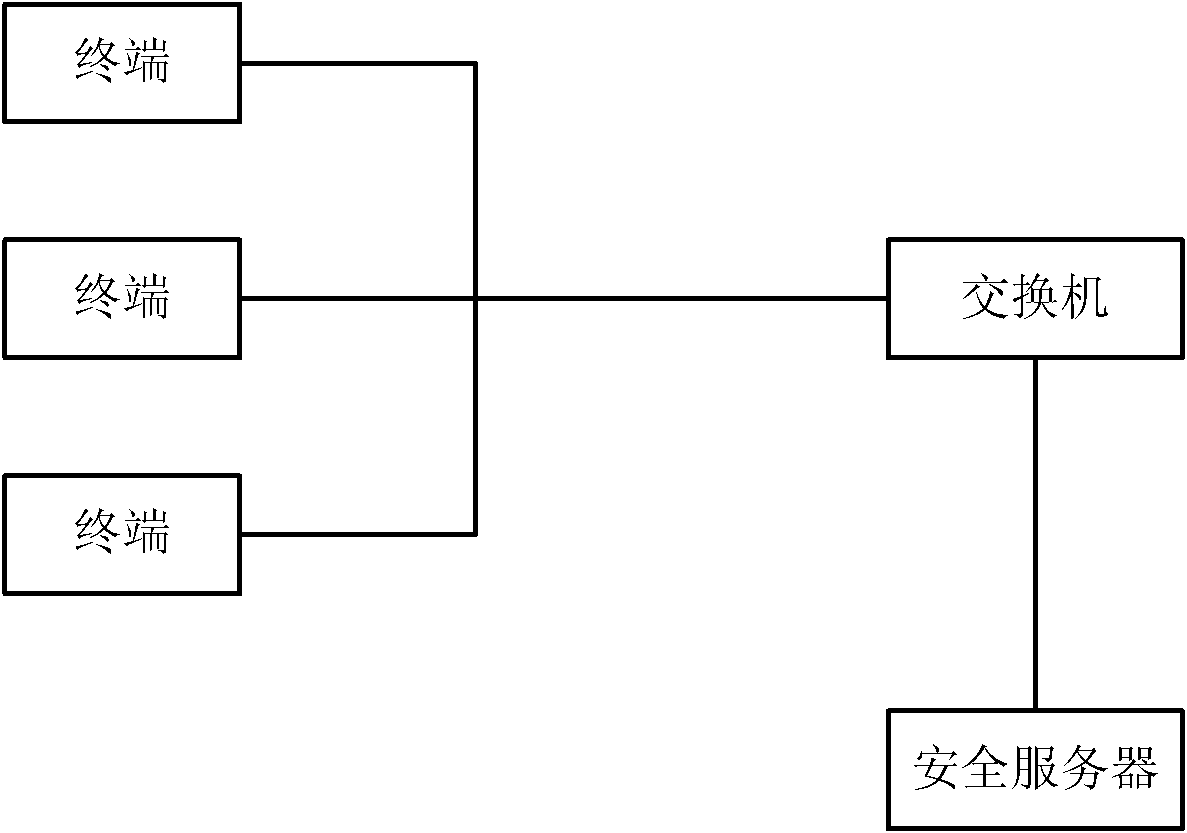
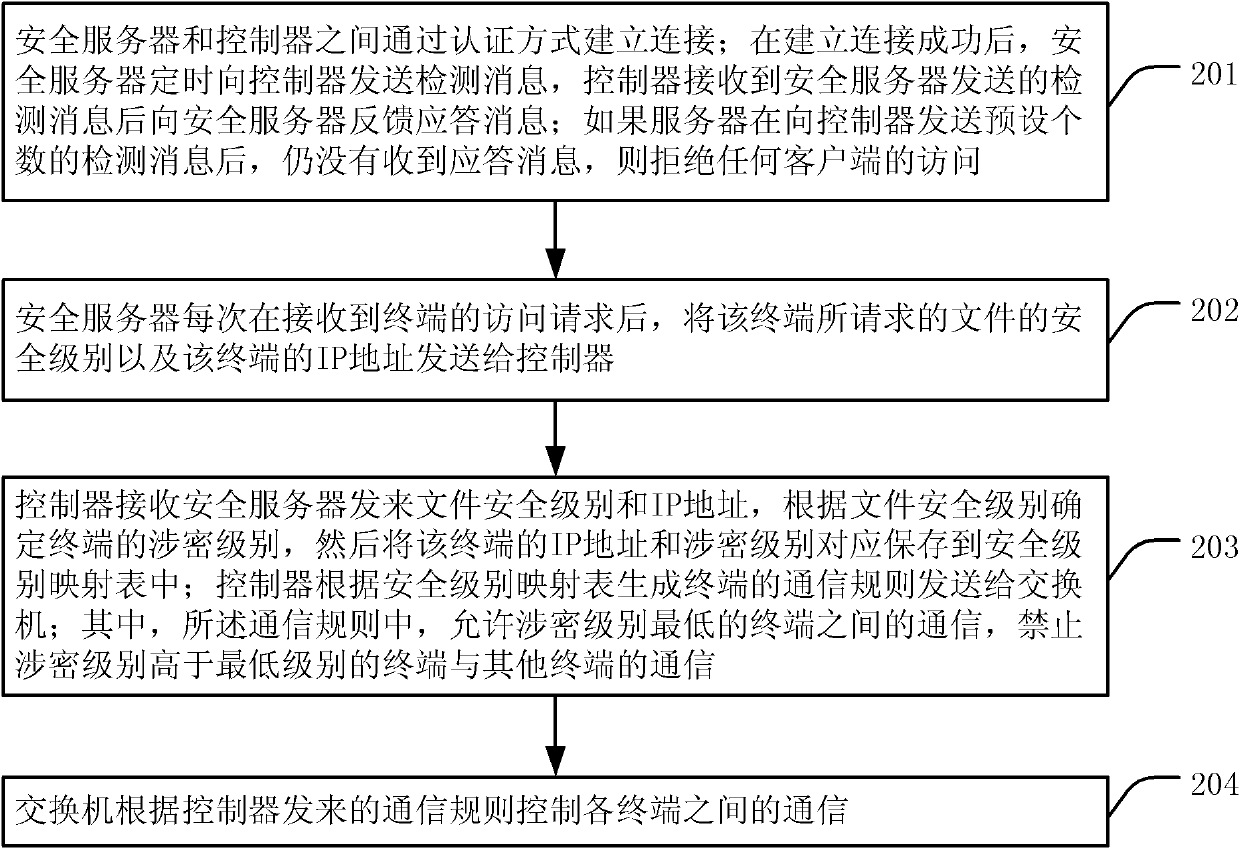
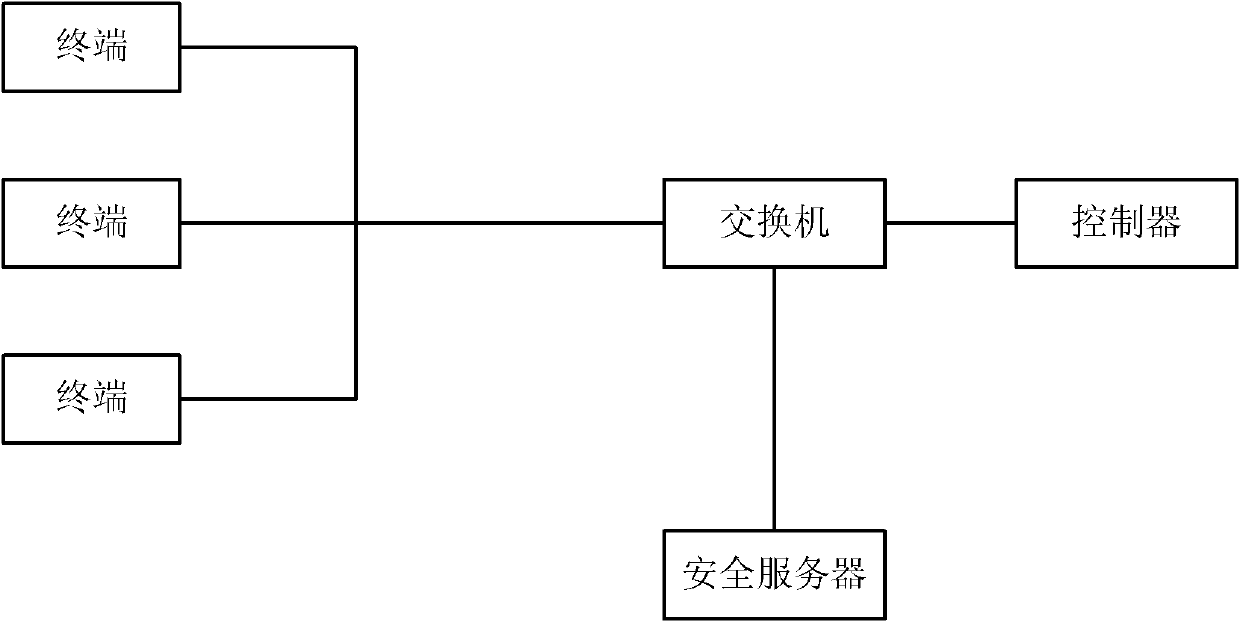
Method for realizing network security and star network
The invention discloses a method for realizing network security and a star network. In the scheme of the invention, a controller is added to the start network; the controller and a security server are connected in an authentication manner; the security server confirms the communication security between the security server and the controller by periodically sending a detection message; every time after receiving an access request from a server, the security server sends the security level of the file requested by the terminal and the IP (Internet protocol) address of the terminal to the controller; and the controller determines the confidential level of the terminal according to the security level of the file, stores the IP address and confidential level of the terminal in a security level mapping table, generates a communication rule of the terminal according to the security level and sends the communication rule to a switch so as to control communication between terminals. Through the technical scheme of the invention, the security of the star network is greatly improved.
Owner:苏州九州安华信息安全技术有限公司
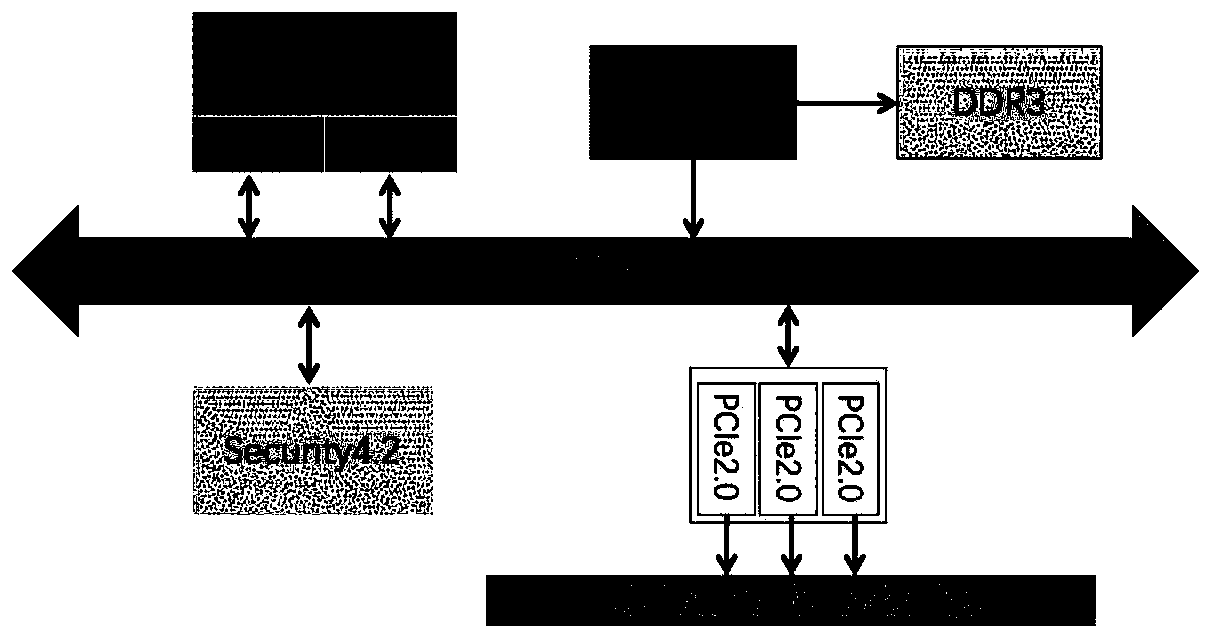
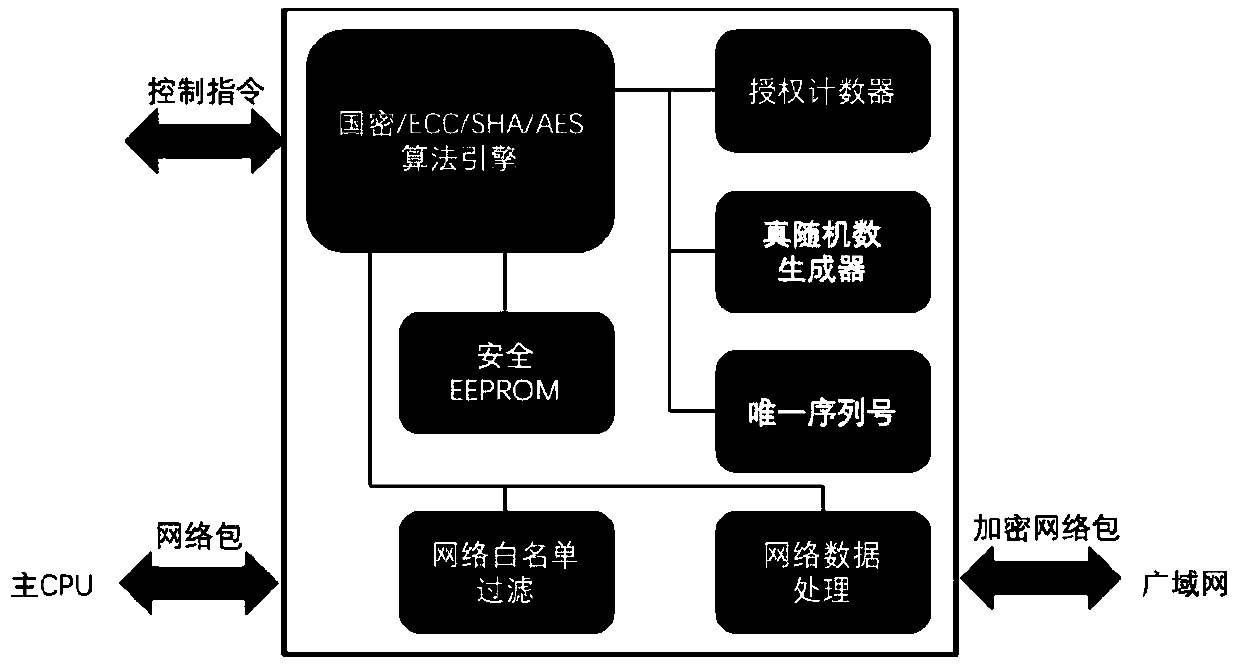
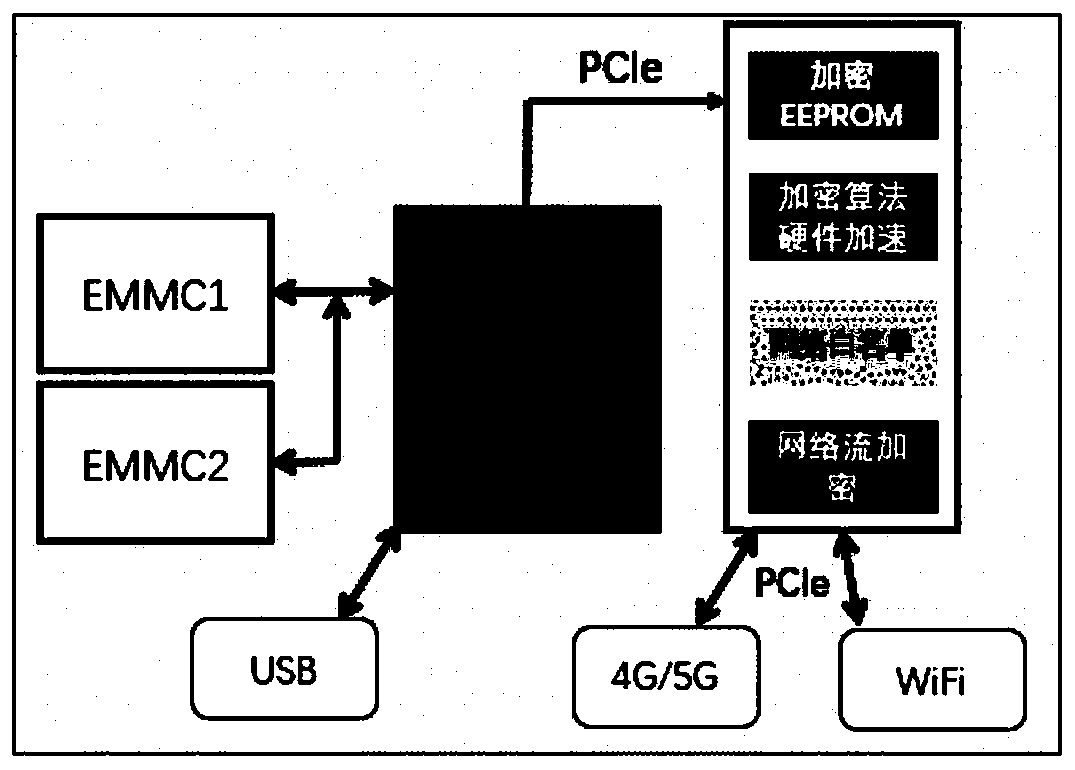
Security chip for protecting network security system and network security system using same
InactiveCN110430178AHigh speed encryptionHigh speed recoveryKey distribution for secure communicationUser identity/authority verificationCommunications securityData stream
A security chip for protecting a network security system comprises a data security part for providing a secure encryption and decryption algorithm and an interaction protocol, wherein the data security part mainly comprises an encryption and decryption algorithm control engine, an authorization counter, a true random number generator, a unique serial number and a secure EEPROM; and a network security part composed of a network white list filtering module and a network data processing module. The encryption and decryption algorithm control engine comprises private key security storage for supporting private key ECDH operation and ECDSA signature authentication. The mainstream national password and commercial password encryption and decryption algorithms perform high-speed encryption and reduction on the data stream so as to adapt to the security requirements of different scenes. The chip safety management supplies power, manages the read-write ROM on the chip, allows special equipment to write, and allows remote erasure but does not allow reading. The invention also provides a network security system using the security chip. The sensitive data communication security can be protectedfrom the hardware level, and the efficiency can be greatly improved while the system security is improved.
Owner:XI AN JIAOTONG UNIV
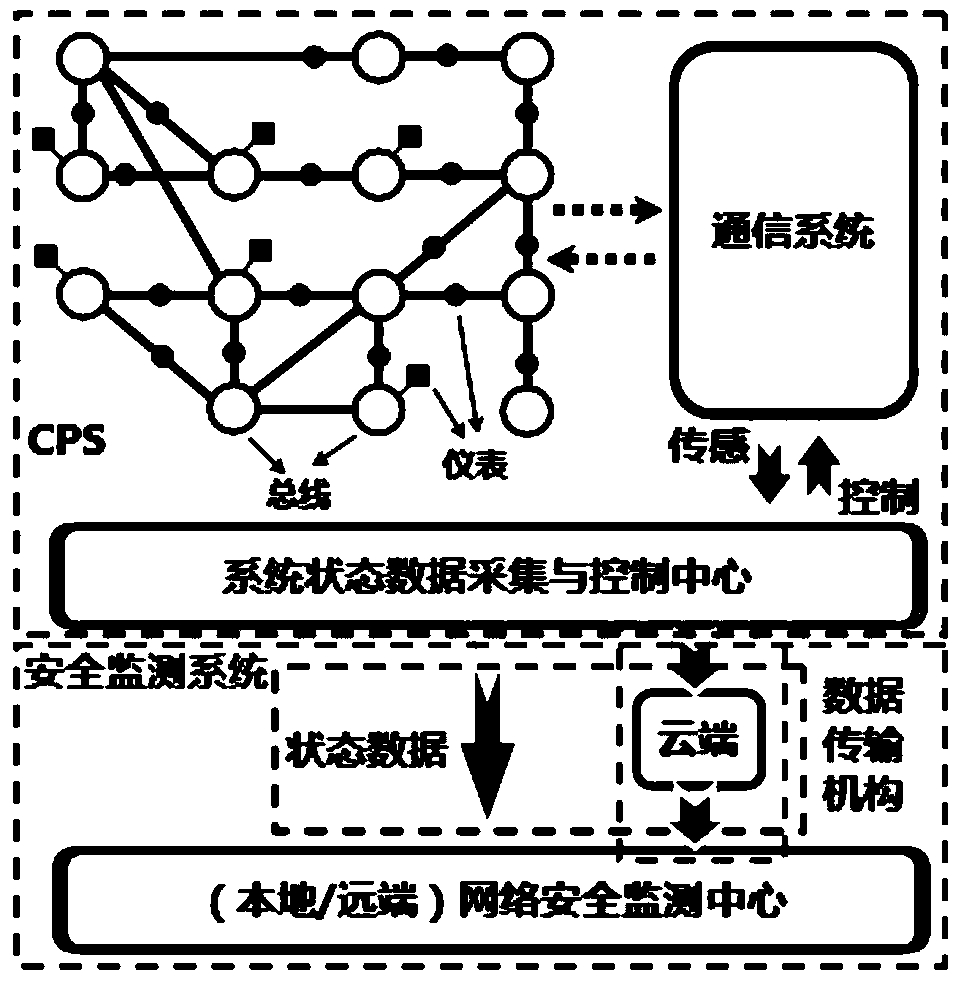
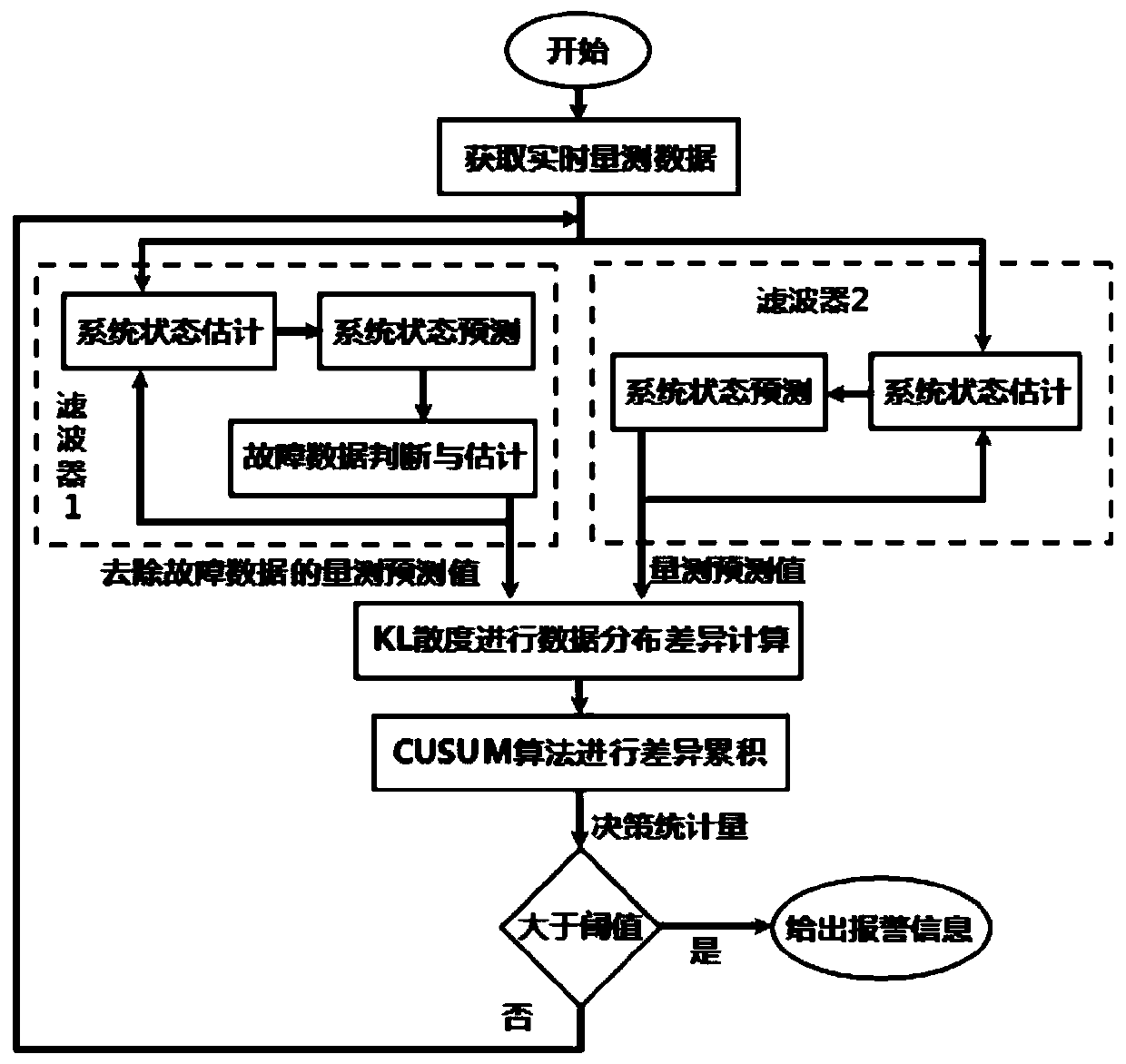
Sensor network security real-time online monitoring system based on parallel filtering
ActiveCN110011879AEmbedded strongImprove developmentData switching networksElectric power systemPhysical system
The invention discloses a sensor network security real-time online monitoring system based on parallel filtering. According to the invention, real-time estimation is carried out on true values of power values measured by all instruments by using a parallel unscented Kalman filter; when the network has a fault, namely, when a system operation failure, an instrument and meter failure or a network attack occurs, deviation is generated between two filters, the deviation is accumulated by using a generalized CUSUM detection method taking KL divergence as an index to obtain decision statistics of fault detection of the whole system and each instrument and meter, and when the decision statistics exceeds a predefined threshold, alarm information is given to indicate that the fault occurs. According to the monitoring system provided by the invention, the abnormal condition of the electric power information physical system is effectively monitored from the perspective of sensor data, and the system has relatively high embedding property, real-time property and stability, is convenient to develop on an original system, and ensures the safe and economic operation of the electric power system.
Owner:YANSHAN UNIV
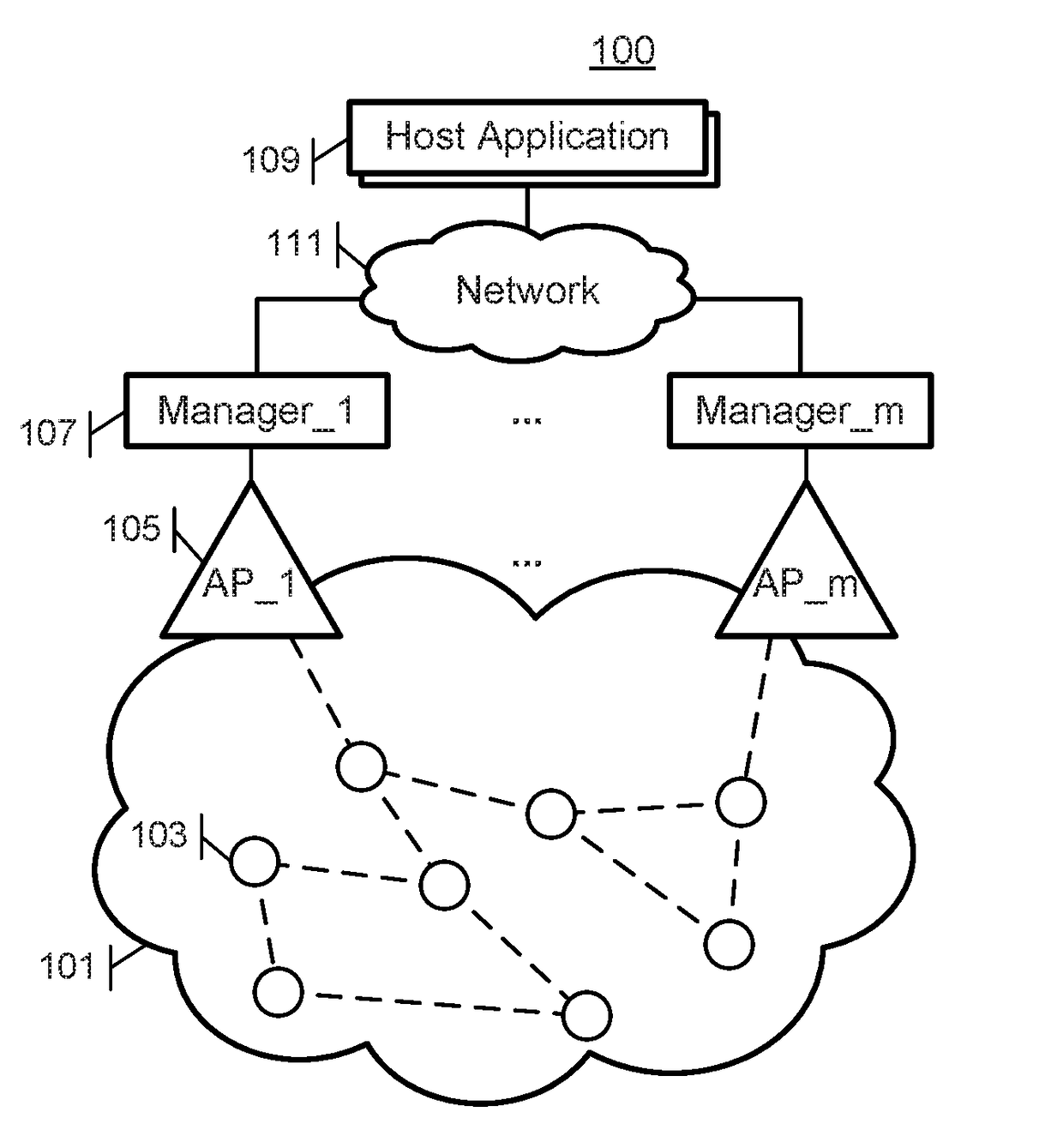
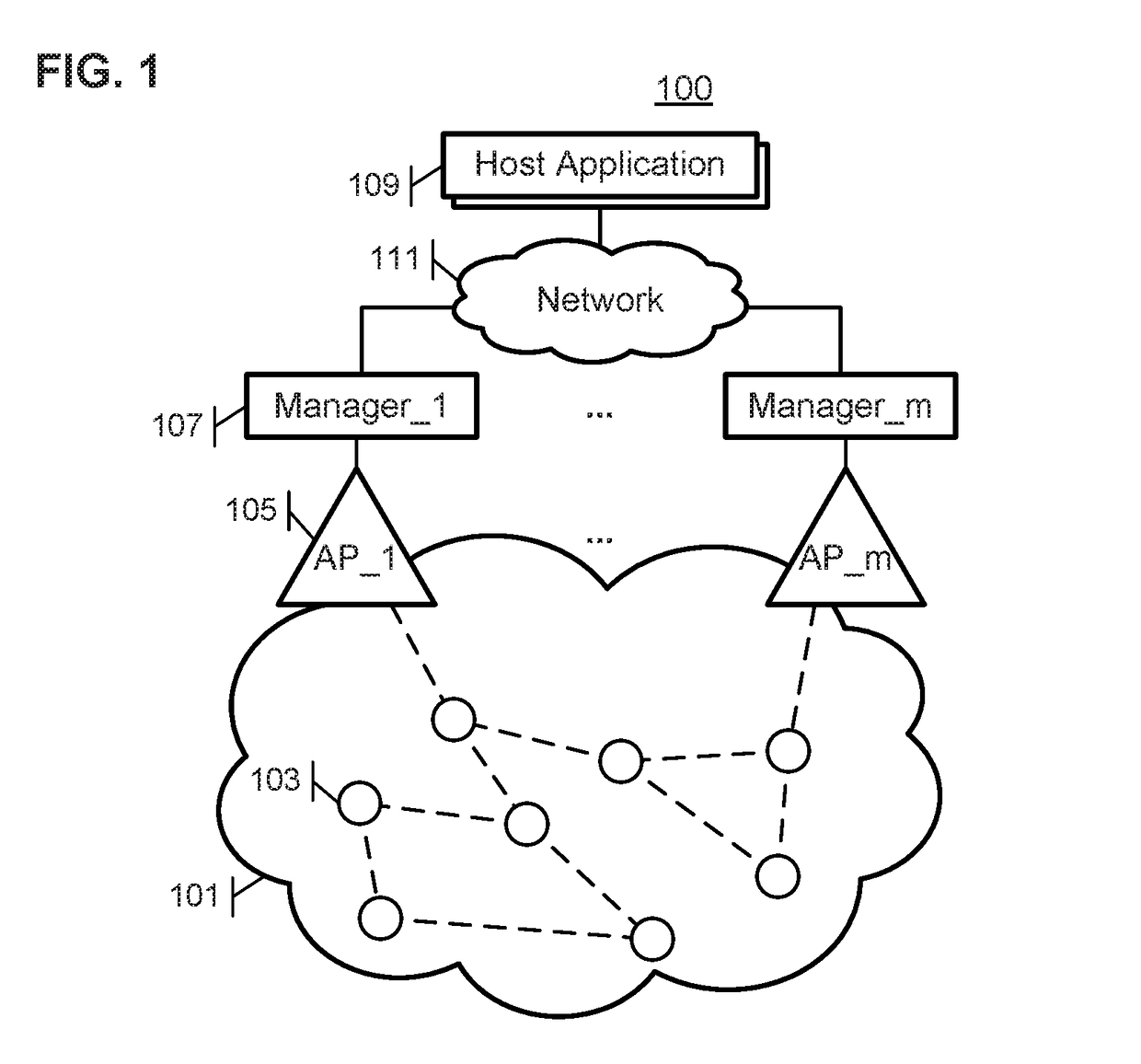
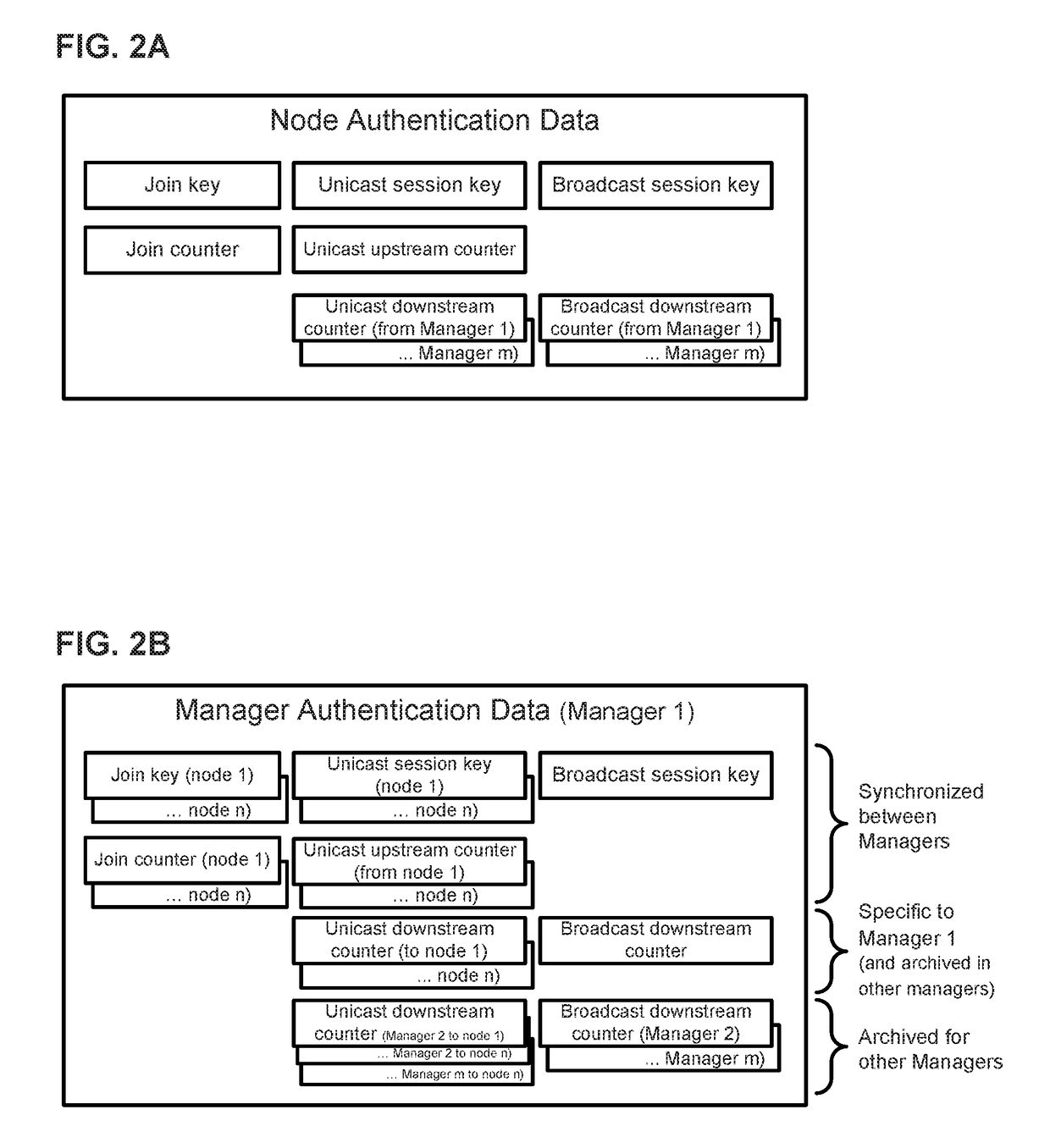
Disjoint security in wireless networks with multiple managers or access points
ActiveUS20180317089A1Improve throughputImprove reliabilityKey distribution for secure communicationNetwork topologiesWireless mesh networkWireless network coding
In a wireless mesh network having multiple network managers, the network managers maintain network security through the use of encryption keys and packet counters. To ensure that each network manager can authenticate communications with any node of the network, the authentication data is replicated in a disjoint manner in all network managers. Advantageously, network reliability is assured by providing redundant managers that can seamlessly maintain network operation even if multiple network managers fail; newly joining managers can obtain full authentication data for the network upon joining; and network throughput is increased by ensuring that any of the multiple managers can authenticate the communications of any network node. The disjoint replication of the authentication data across all network managers is performed with low data-rate manager-to-manager packets propagated through the network. The disjoint security methods and systems can advantageously be used in wireless battery monitoring systems, for example.
Owner:ANALOG DEVICES INT UNLTD
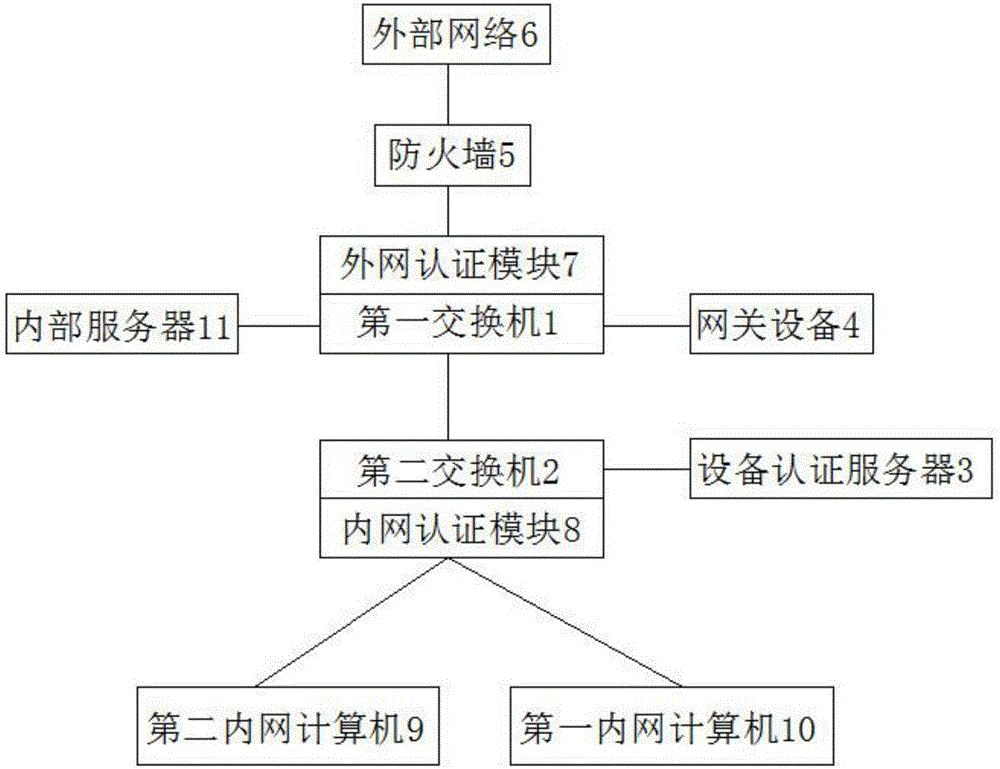
Double authenticated network security system
The invention discloses a network security system of a double authenticated mechanism. The network security system comprises an outer network authentication module positioned between an outer network firewall and a first switch, an inner network authentication module positioned between an inner network computer and a second switch, a device authentication server connected with the second switch, and a network management device connected with the first switch. The network management device manages an outer network access permission of a user, a device authentication server stores device information allowed to access an inner network. The firewall is used for preventing Trojan and virus attacks, the outer network authentication module is used for controlling a permission of an inner network user accessing an outer network, and the inner network authentication module is used for controlling the permission of a device applying for the access to the inner network. The double authenticated network security system is rigorous in prevention, convenient to manage and capable of improving the security performance.
Owner:安徽天达网络科技有限公司
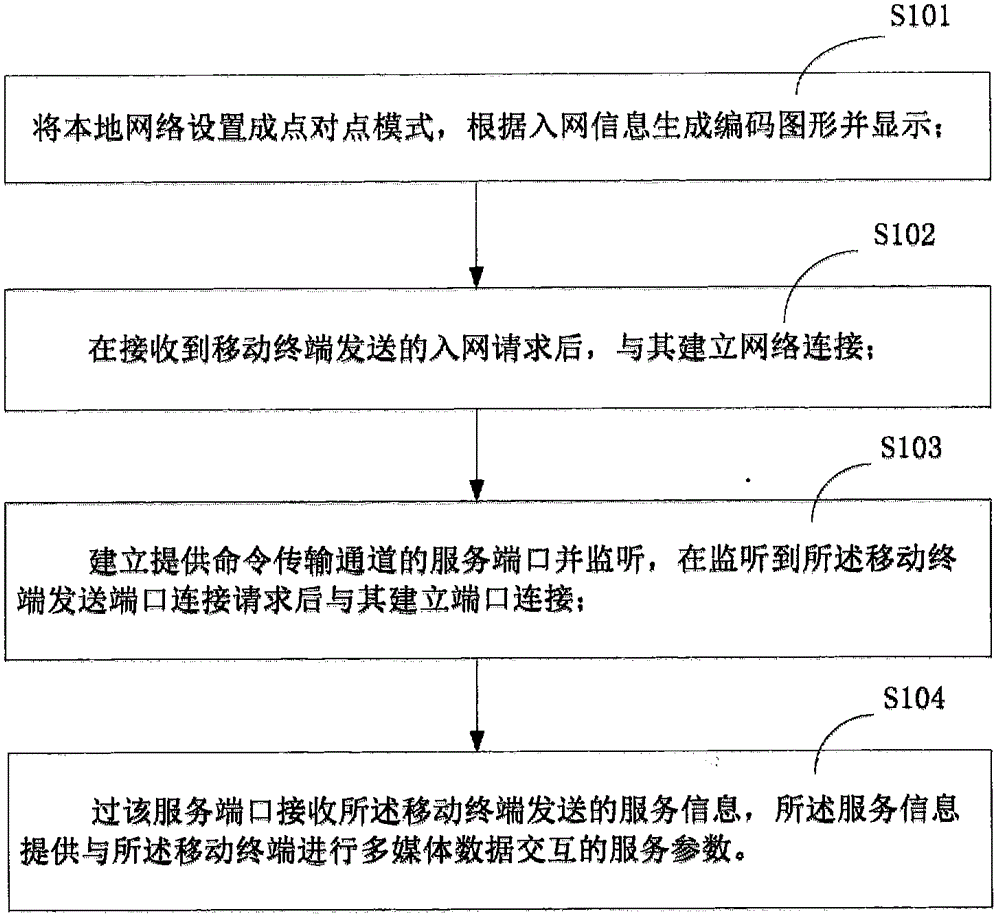
Method for terminal interaction based on network security and relevant device thereof
A network security-based terminal interaction method and related equipment, wherein the method includes: setting the local network to a point-to-point mode, generating and displaying coded graphics according to network access information; after receiving a network access request sent by a mobile terminal, and Establish a network connection; establish and monitor a service port that provides a command transmission channel, and establish a port connection with the mobile terminal after listening to the port connection request sent by the mobile terminal; receive the service information sent by the mobile terminal through the service port, and the service information Provide service parameters for multimedia data interaction with the mobile terminal. By adopting the above-mentioned method and related equipment, it has the characteristics of high network security and strong privacy when resource sharing and exchange control are performed, and the resource transmission speed is fast.
Owner:袁斌
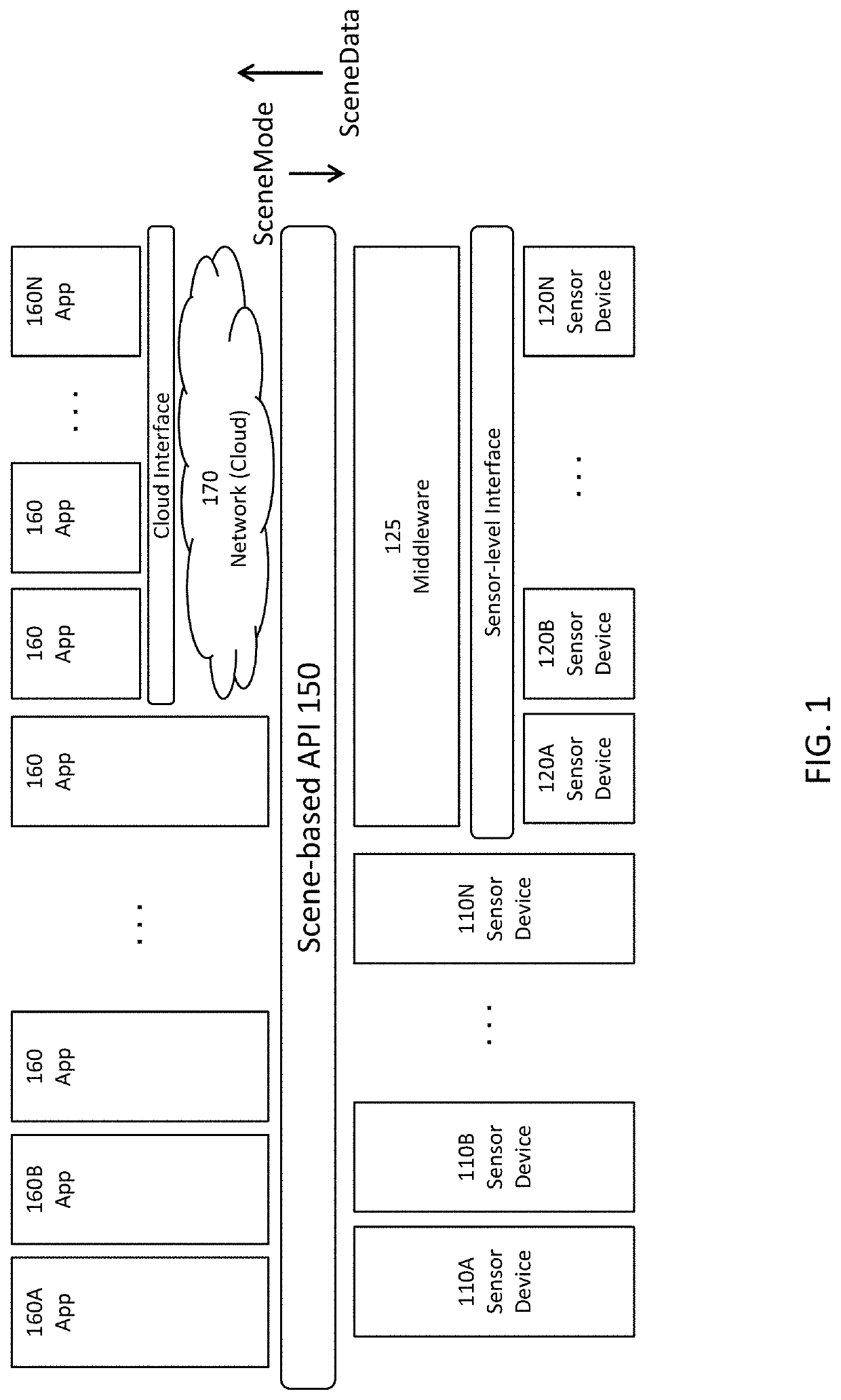
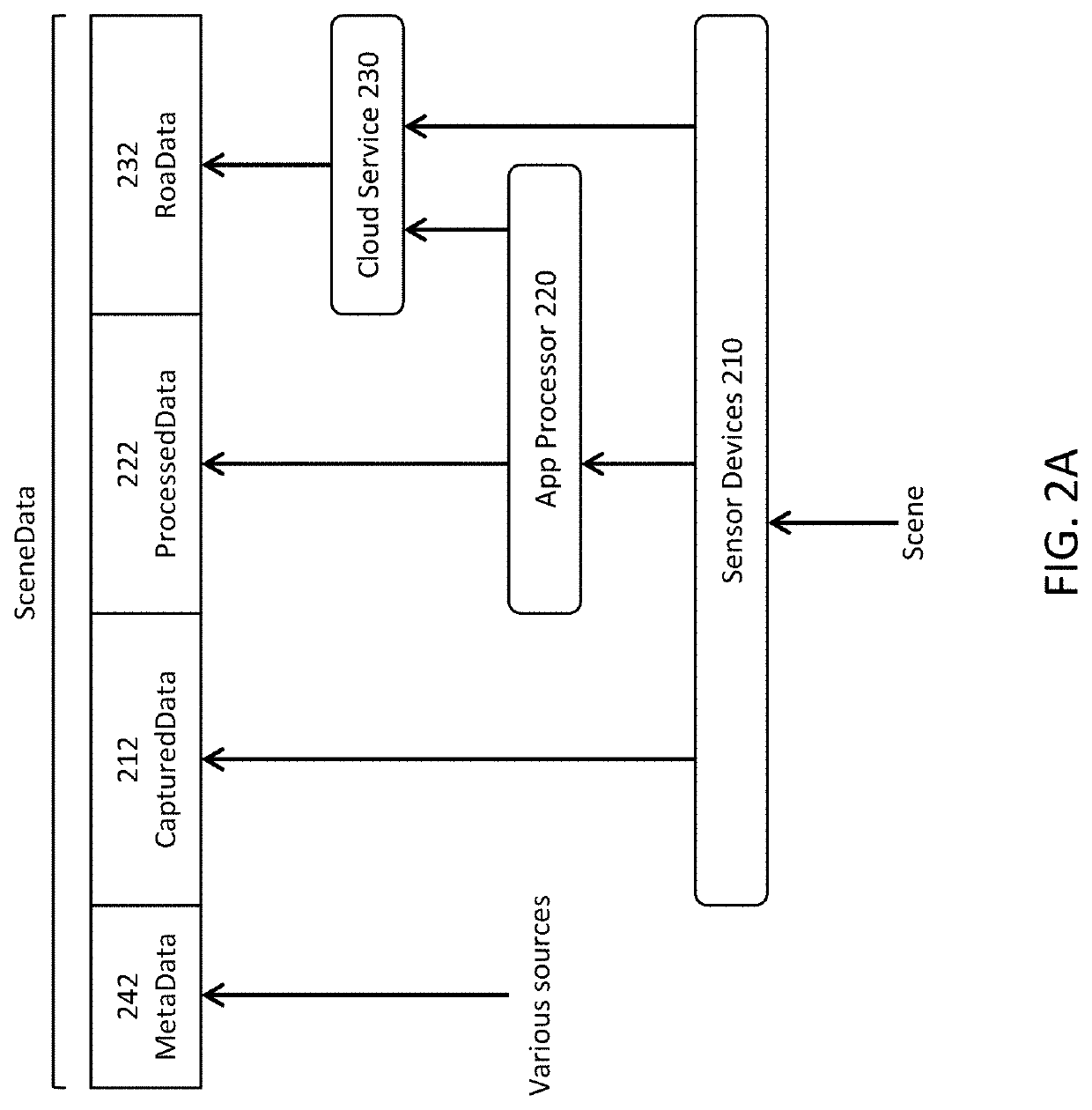
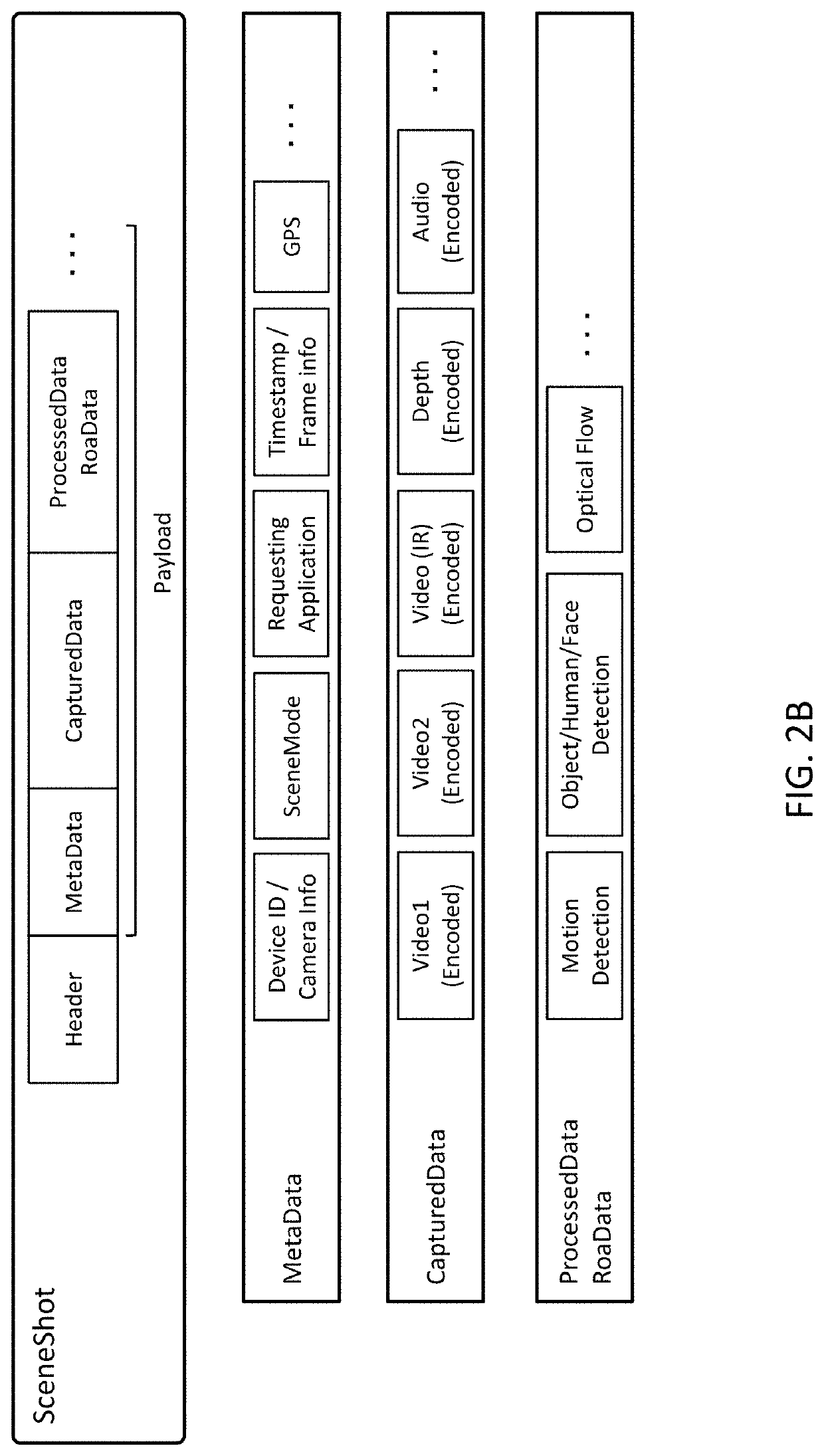
Security for scene-based sensor networks
ActiveUS10693843B2Overcome limitationsUser identity/authority verificationCharacter and pattern recognitionNetwork managementReliability engineering
Security and access control is provided for sensor devices, the data captured by sensor devices, and the results of processing and analyzing that data. In one aspect, SceneData related to a Scene is requested from a sensor-side technology stack and at least some of the SceneData is secured, for example by encryption. Different SceneData can be secured separately and at different levels of security, thus providing fine-grained security of the SceneData. In yet another aspect, data security is implemented by a separate privacy management system. In yet another aspect, sensor devices themselves are secured against external network threats. The sensor device includes an execution environment and a separate network management layer that secures the execution environment against threats from the external network. In one implementation, the sensor device is partitioned into a trusted region and a non-trusted region, and the network security stack is implemented in the trusted region.
Owner:SCENERA INC
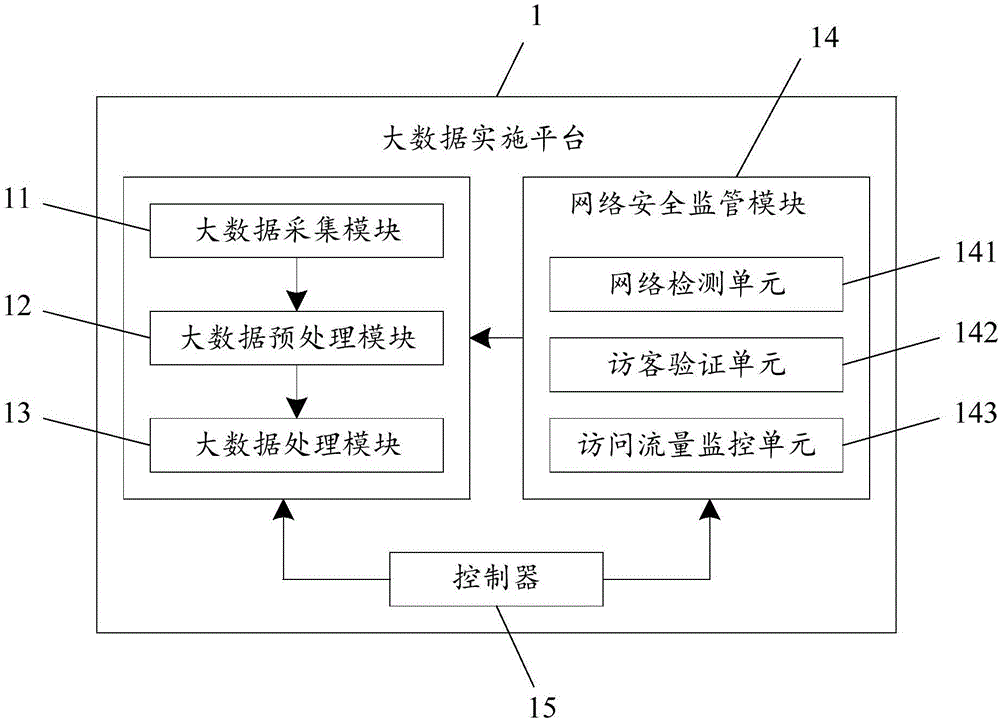
Big data implementation system and method based on network security
InactiveCN107528852AReduce processing efficiencyNot easy to cause blockageDigital data protectionData switching networksResource utilizationData loss
The invention discloses a big data implementation system and method based on network security. The big data implementation platform of the system comprises: a big data acquisition module, a big data preprocessing module, a big data processing module, a network security monitoring module and a controller; the network security monitoring module comprises a network detection unit, a visitor verification unit and an access flow monitoring unit. The big data implementation system collects multiple paths of data in parallel via a data receiver with multiple data interfaces, a priority number and a frame number are added to the frame packaging data, the collected data are stored in a hierarchical manner, so that the stored data are analyzed and screened according to the priority number and the frame number and are output; that is, in a big data implementation process, the data are collected via multiple channels, so that the collection efficiency is high, and the collection data is large; and the data stored in the hierarchical manner are output according to the priority number and the frame number, so that the data transmission is sequential, network blockage and data loss are unlikely to generate, the data processing efficiency is low, and the resource utilization rate is low.
Owner:SHENGDA ECONOMICS TRADE & MANAGEMENT COLLEGE OF ZZ
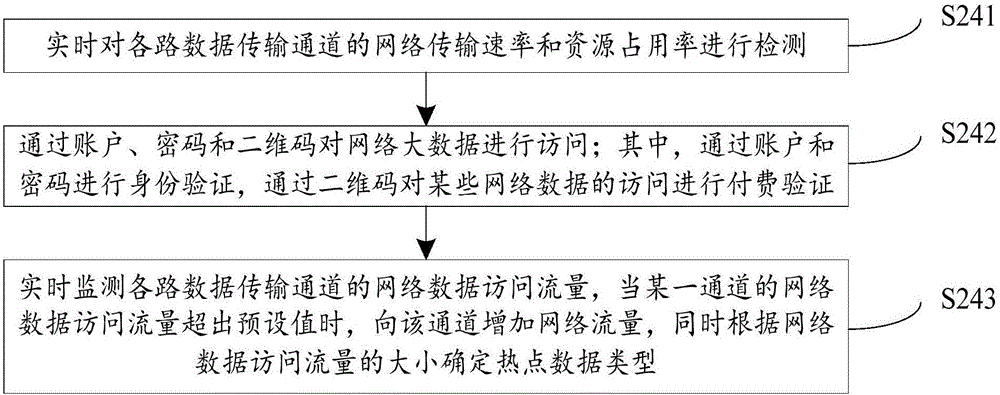
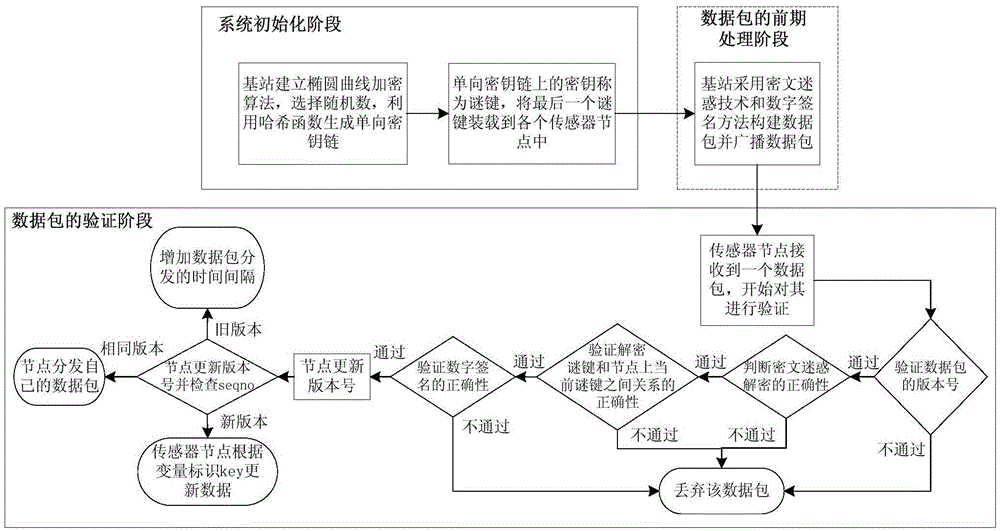
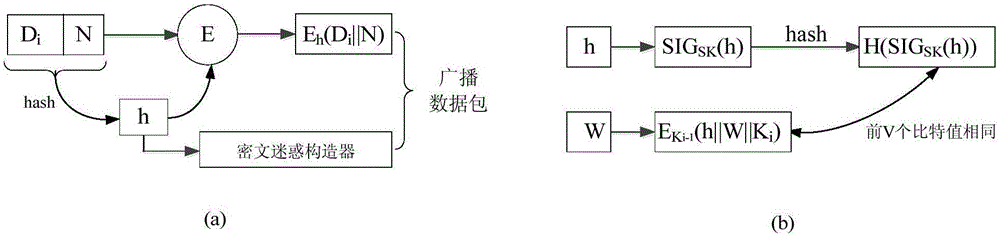
Small data distribution method enabling wireless sensor network security and denial of service attack defense
InactiveCN105141620AIntegrity guaranteedEnsure safetyNetwork topologiesTransmissionPacket lossDistribution method
The invention discloses a small data distribution method enabling wireless sensor network security and denial of service attack defense. The method includes the following steps that: a system initialization phase: a base station generates a key material and loads a public parameter into each sensor node before sensor network deployment; a data packet earlier-stage processing phase: the base station generates data packets through adopting a cipher confusing technology and a digital signature method before data item distribution; and a data packet authentication phase: after receiving the data packets, the sensor nodes judge the validity of the data packets, if the data packets are valid data packets, the sensor nodes receive and update the data packets, otherwise, the sensor nodes discard the data packets. With the mall data distribution method of the invention, under the condition that sensor node resources are limited, resistance to compromise of the sensor nodes can be realized, the integrity and security of information can be ensured, and no time synchronization is required between the base station and the sensor nodes, and defense for denial of service attack can be effectively realized. The small data distribution method has high robustness in packet loss and data packet transmission out-of-sequence.
Owner:EAST CHINA NORMAL UNIV +1
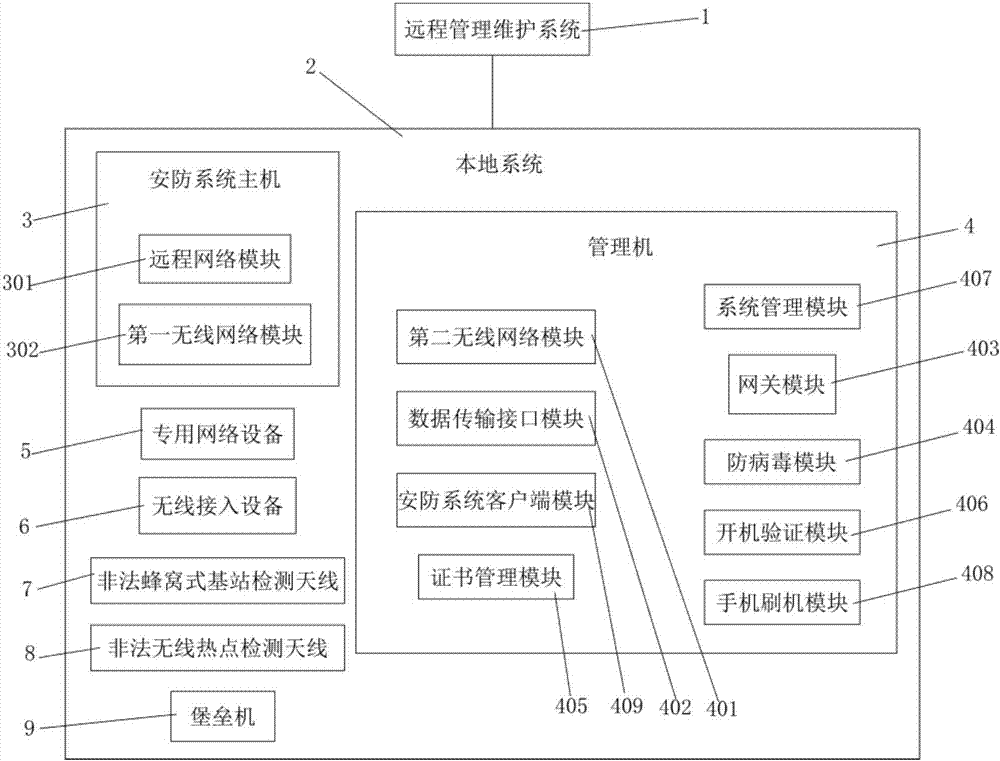
Distributed regional internet security protection system
InactiveCN107889108AEnsure safetyGuarantee information securitySecurity arrangementNetwork data managementPrivate networkInformation security management
The invention discloses a distributed regional internet security protection system, and belongs to the technical field of network security. The distributed regional internet security protection systemcomprises a remote management and maintenance system and a local system; and the local system comprises a security protection system host, a management machine, dedicated network equipment and wireless access equipment. The distributed regional internet security protection system disclosed by the invention can perform security protection and integrated management on internet users, internet access terminals, access networks and flow information in multiple special regions distributed in different geographical positions; the internet users and networks in the regions cannot be maliciously violated; the privacy and information security of network users can be effectively protected; and thus, the distributed regional internet security protection system disclosed by the invention is particularly suitable for departments having relatively high requirements on information security, such as governments, armies and commercial corporations.
Owner:北京军地联合网络技术中心
Packet processing method, fire wall equipment and network security system
ActiveCN101345711BSolve the problem of forwarding confusionLegitimacy testingNetworks interconnectionMessage processingNetwork security policy
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Multi-function, modular system for network security, secure communication, and malware protection
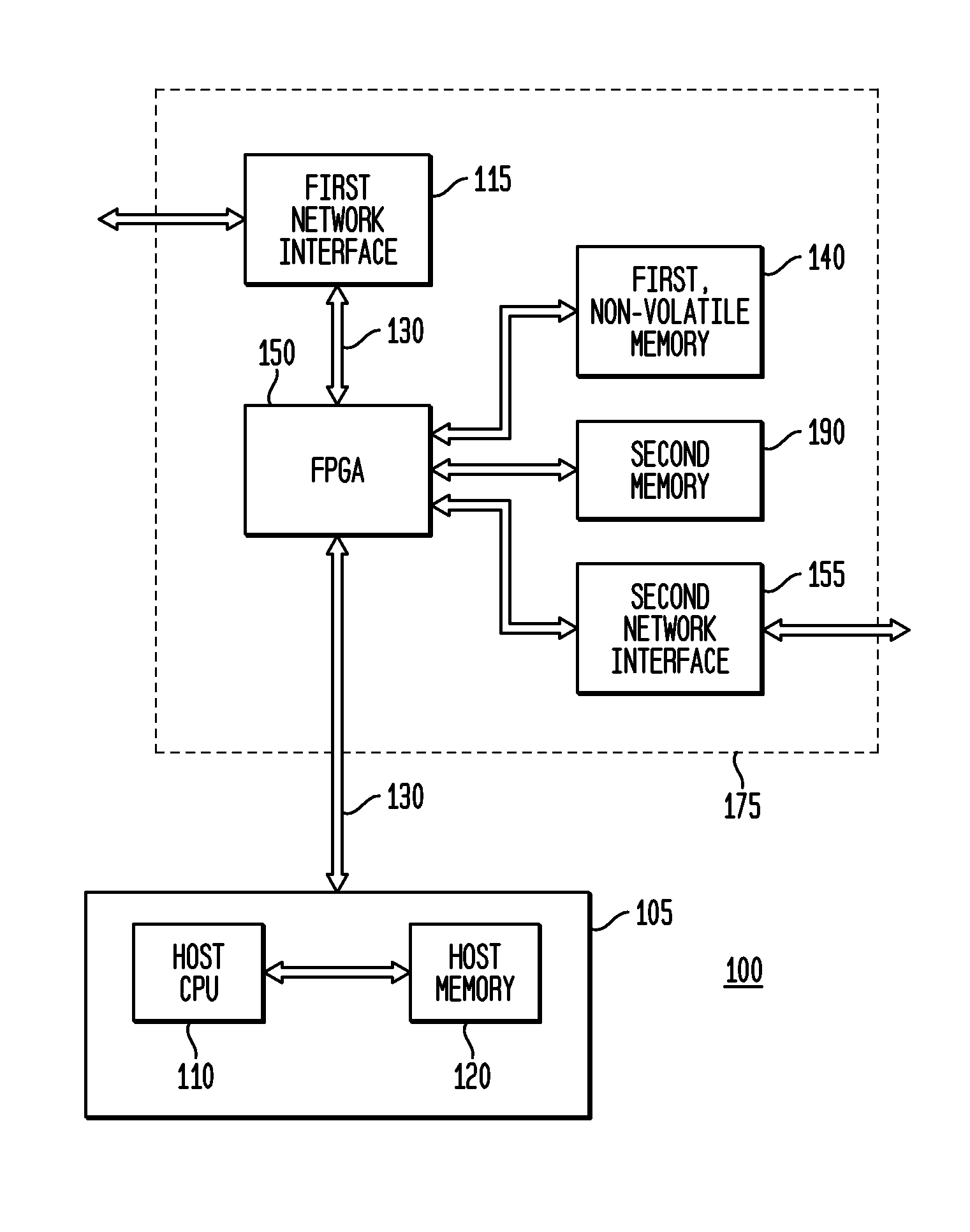
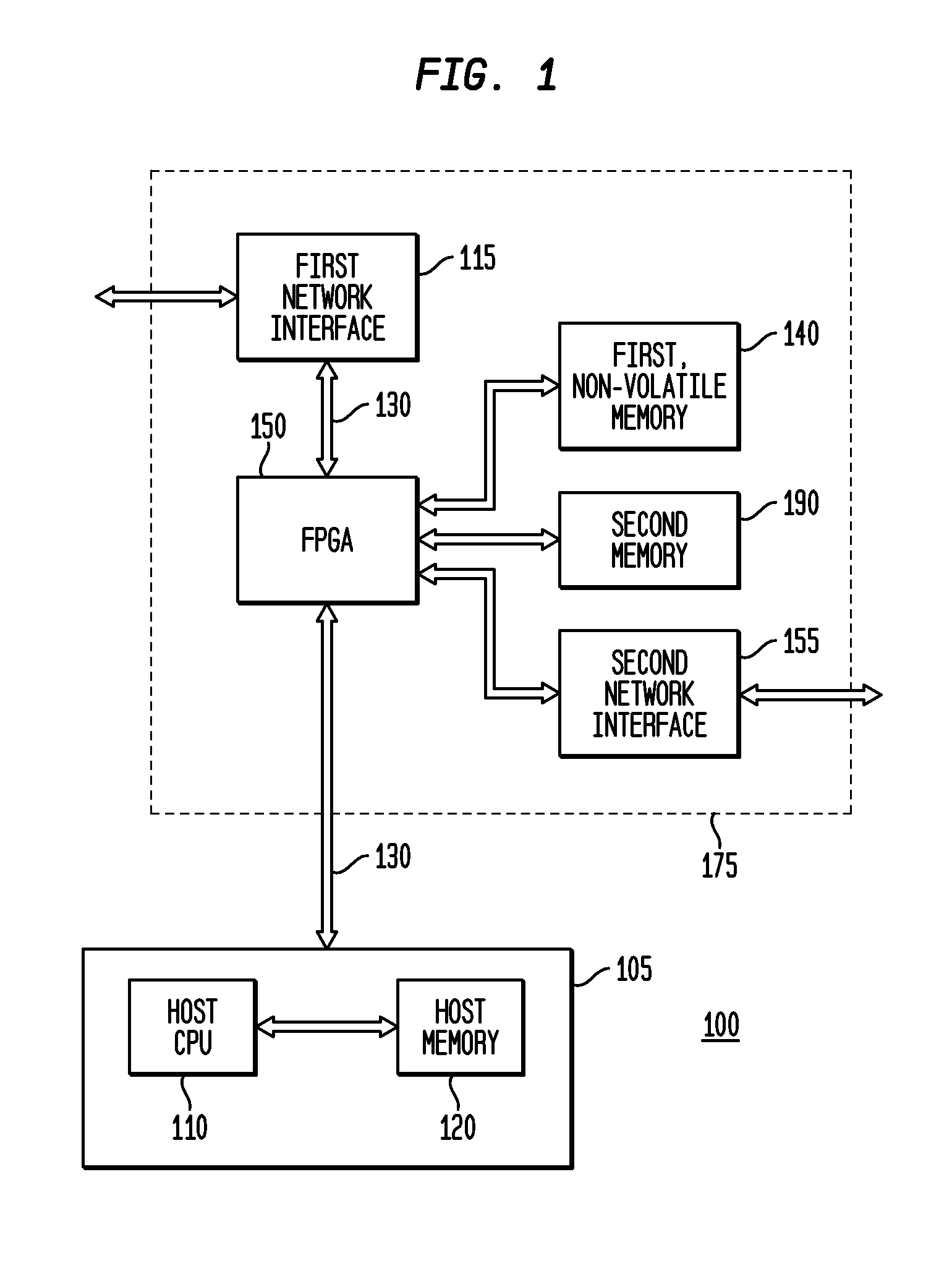
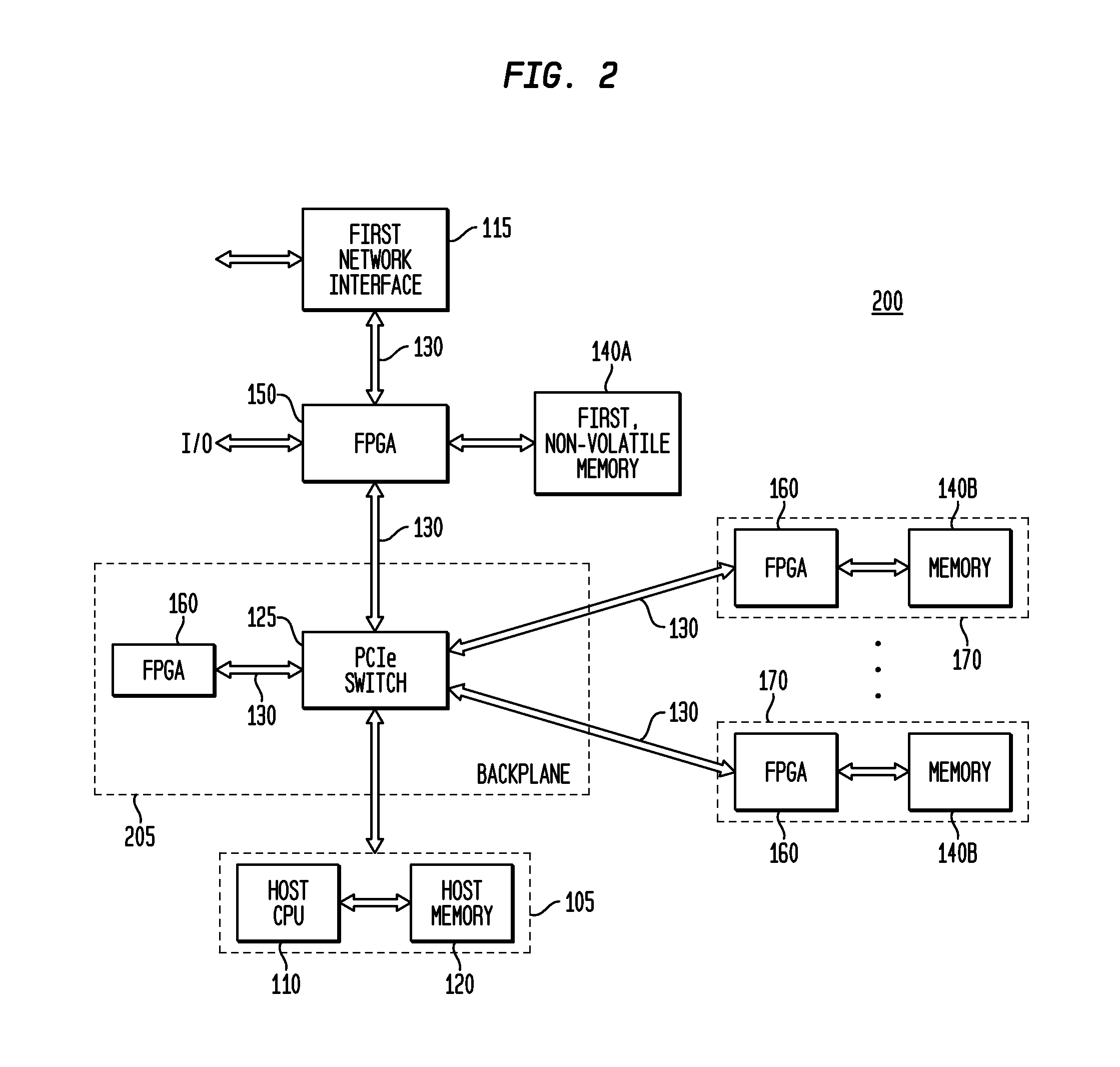
ActiveUS9444827B2Effectively undetectableInternal/peripheral component protectionPlatform integrity maintainanceNetwork Communication ProtocolsHost memory
Representative embodiments are disclosed for providing network and system security. A representative apparatus includes an input-output connector coupleable to a data network; a network interface circuit having a communication port; a nonvolatile memory storing a configuration bit image; and a field programmable gate array (“FPGA”) coupled to the network interface circuit through the communication port, the FPGA configurable to appear solely as a communication device to the first network interface circuit, and to bidirectionally monitor all data packets transferred between the input-output connector and the first network interface circuit and any coupled host computing system. In another embodiment, the FPGA is further configurable for only a partial implementation of a communication protocol, such as a PCIe data link and / or physical layers. The FPGA may also monitor host memory and provide encryption and decryption functionality. The FPGA is not addressable within the computing system and therefore is largely undetectable by malware.
Owner:LODESTAR LICENSING GRP LLC
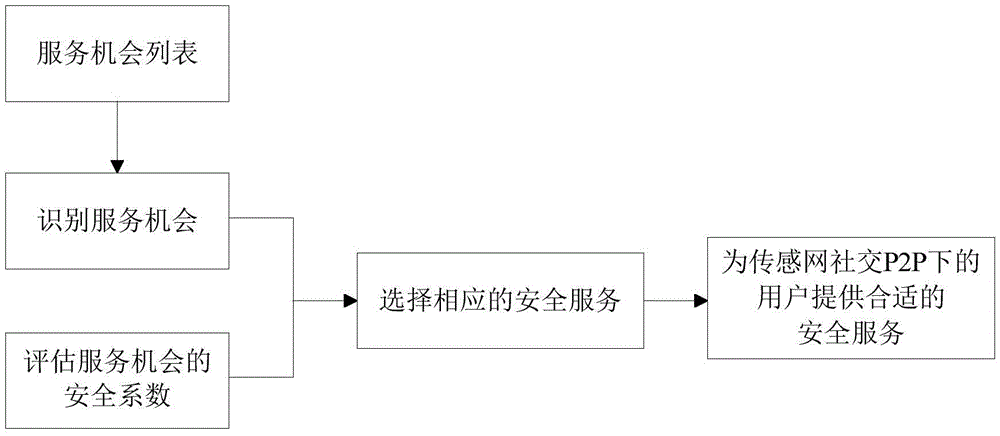
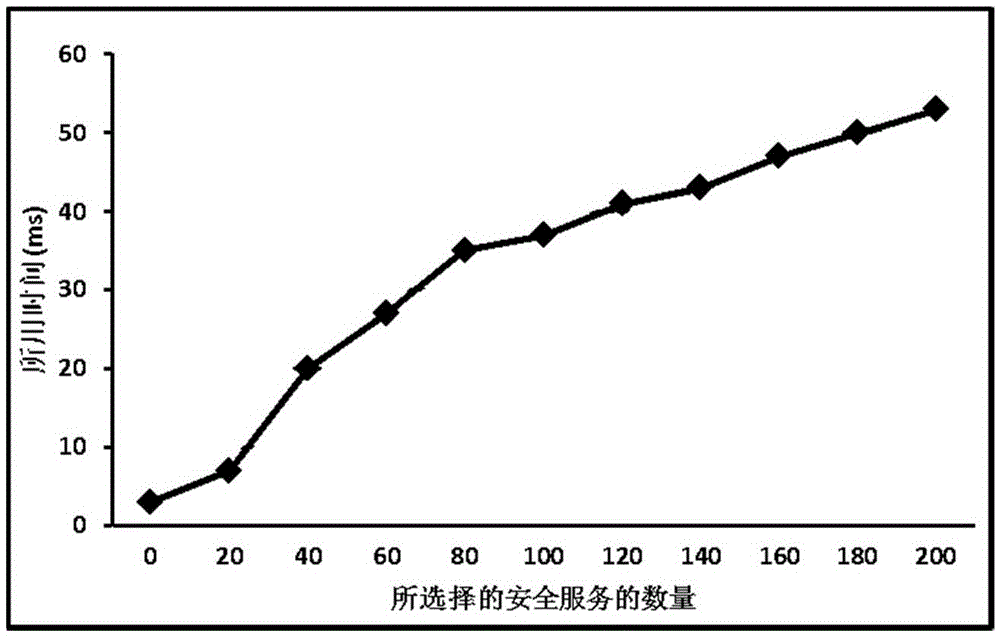
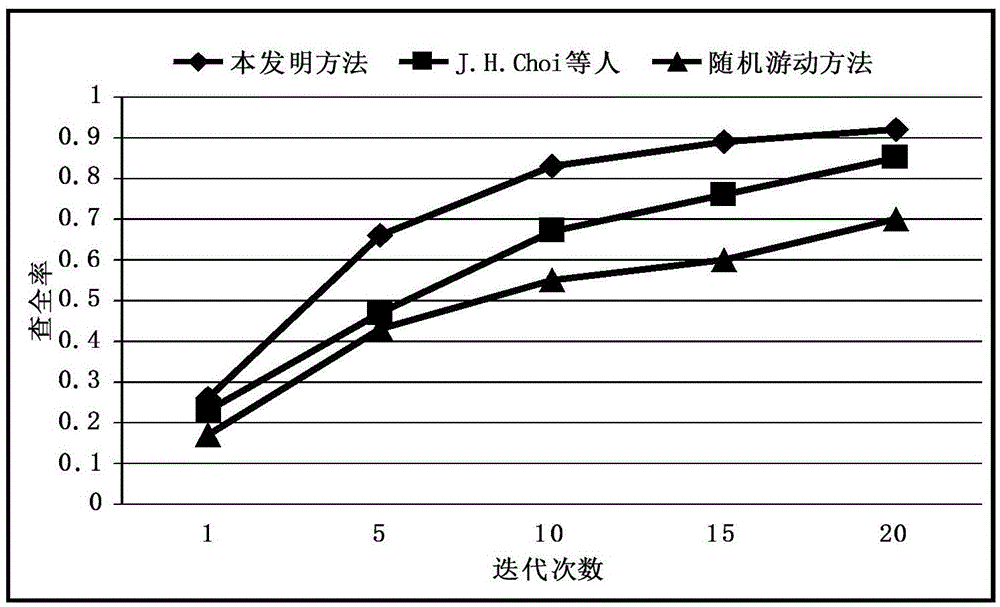
Method for selecting P2P sensor network security service under social network environment
The invention provides a method for selecting a P2P sensor network security service under a social network environment. The method comprises the steps: step 1, building a service opportunity list according to an unexpected event sent by an operator; step 2, identifying a built relative service opportunity from the service opportunity list; step 3, calculating relative security indexes for each service opportunity; step 4, under social P2P of a sensor network, selecting and outputting a proper security service for each user according to the security indexes. The method for selecting the P2P sensor network security service under the social network environment is low in service retransmission probability, thereby reducing loads of a server side; better user applicability and controllability and stronger service discovery and selection capability are achieved.
Owner:SHANGHAI JIAO TONG UNIV +2
Big data implementation control system based on internet network security
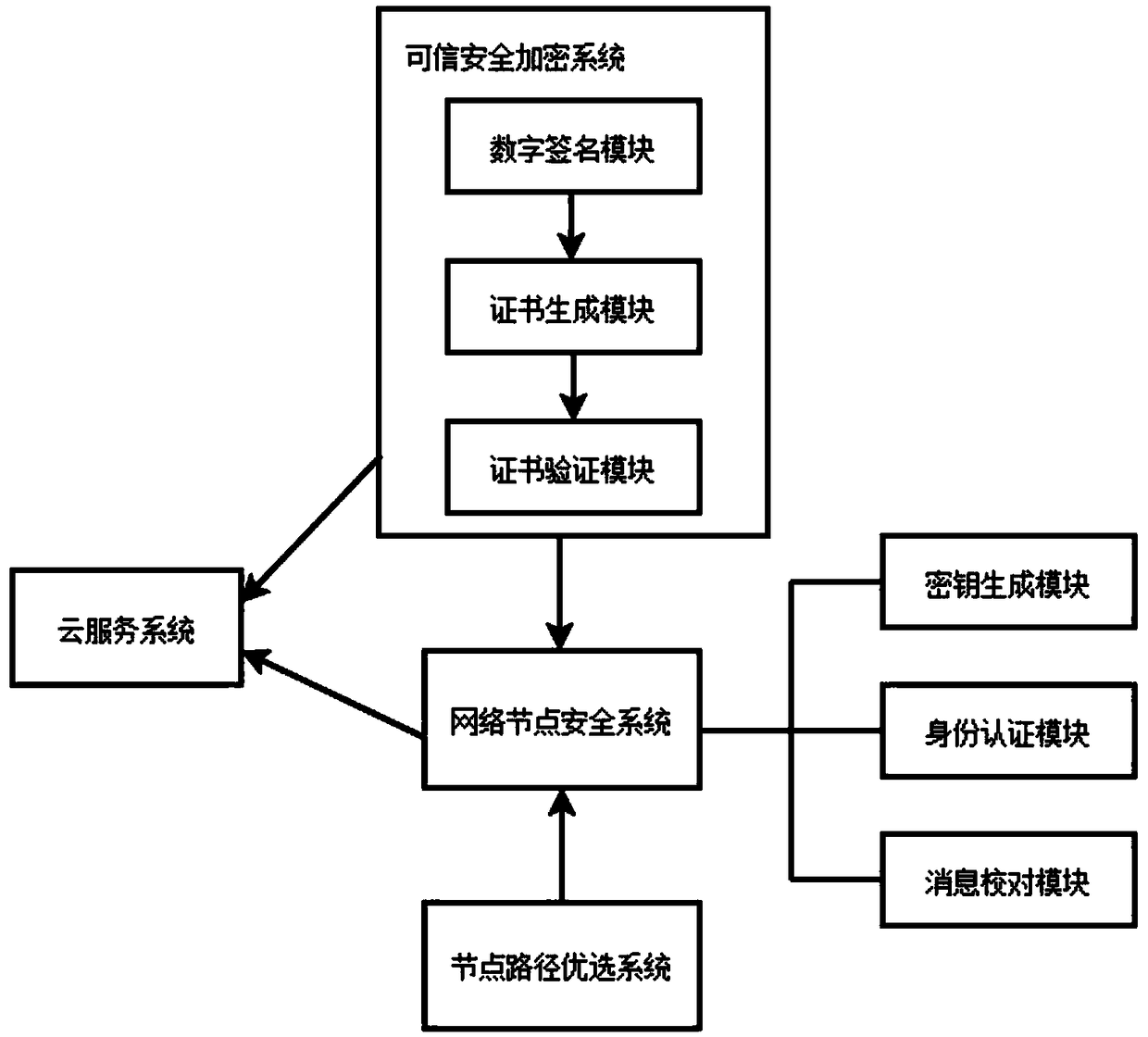
ActiveCN108881285AAdd encryption settingsAvoid attackKey distribution for secure communicationUser identity/authority verificationKey generationSecurity system
The invention relates to the technical fields of big data, network security and the like, and specifically relates to a big data implementation control system based on internet network security. The system comprises a network node security system, a trusted security encryption system, a node path optimization system and a cloud service system; the network node security system establishes a secureroute for determining a secure transmission path of data in the network; the network node security system comprises an identity authentication module, a key generation module and a message check module; the trusted security encryption system is used for performing encryption setting on a network node, and a serial number of the node needs to be verified before the data transmission of the networknode; the node path optimization system is used for selecting an optimal node path during the data transmission of the node; and the cloud service system is used for providing a cloud support for thebig data implementation control system of the entire network security. By adoption of the scheme, the security during the data transmission is enhanced, and the efficiency of the data transmission isimproved.
Owner:HUBEI POLYTECHNIC UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com