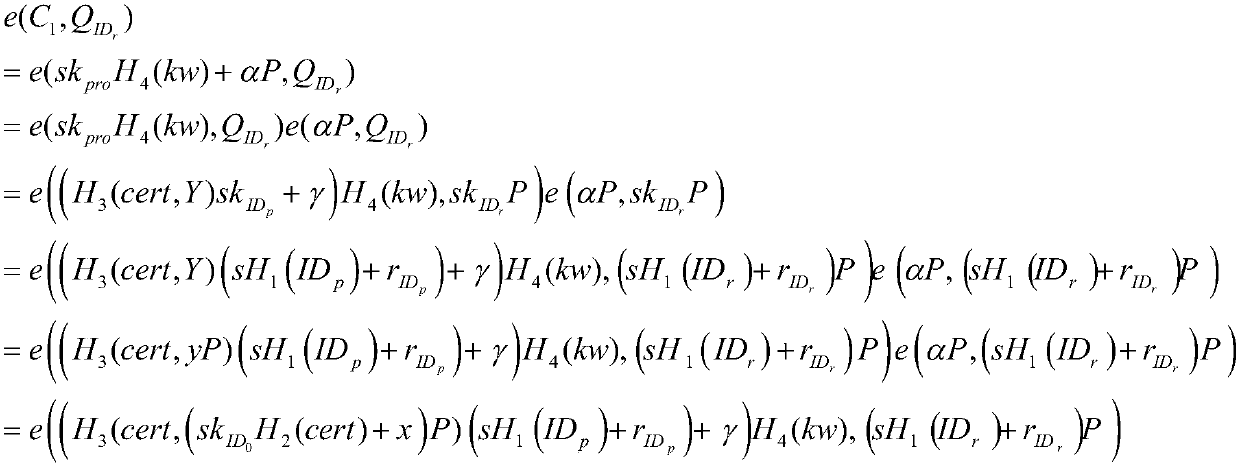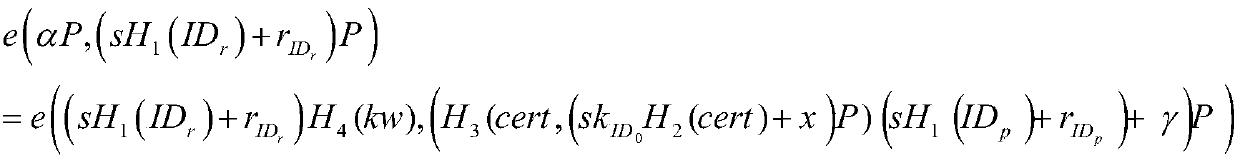Patents
Literature
223results about How to "Guarantee information security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
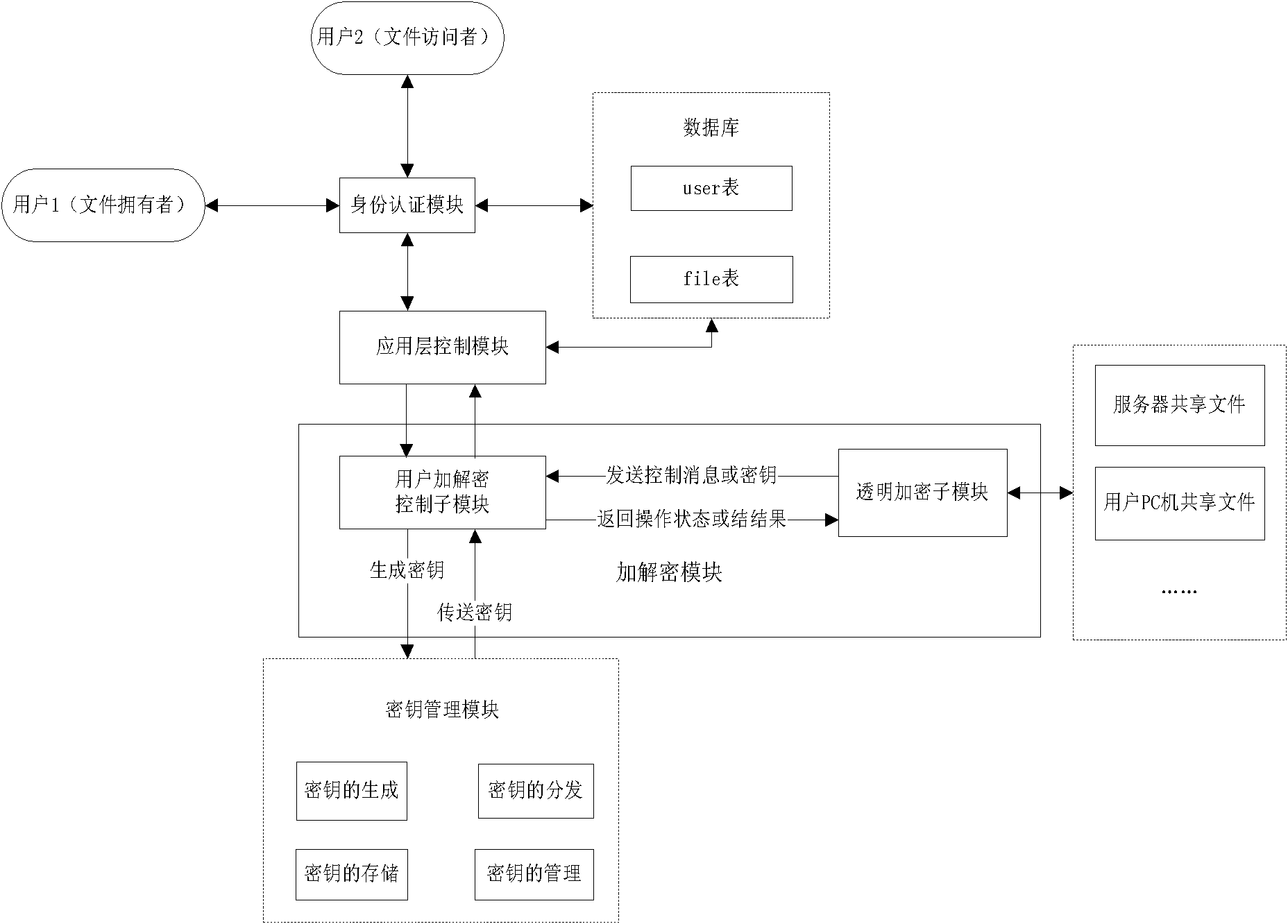
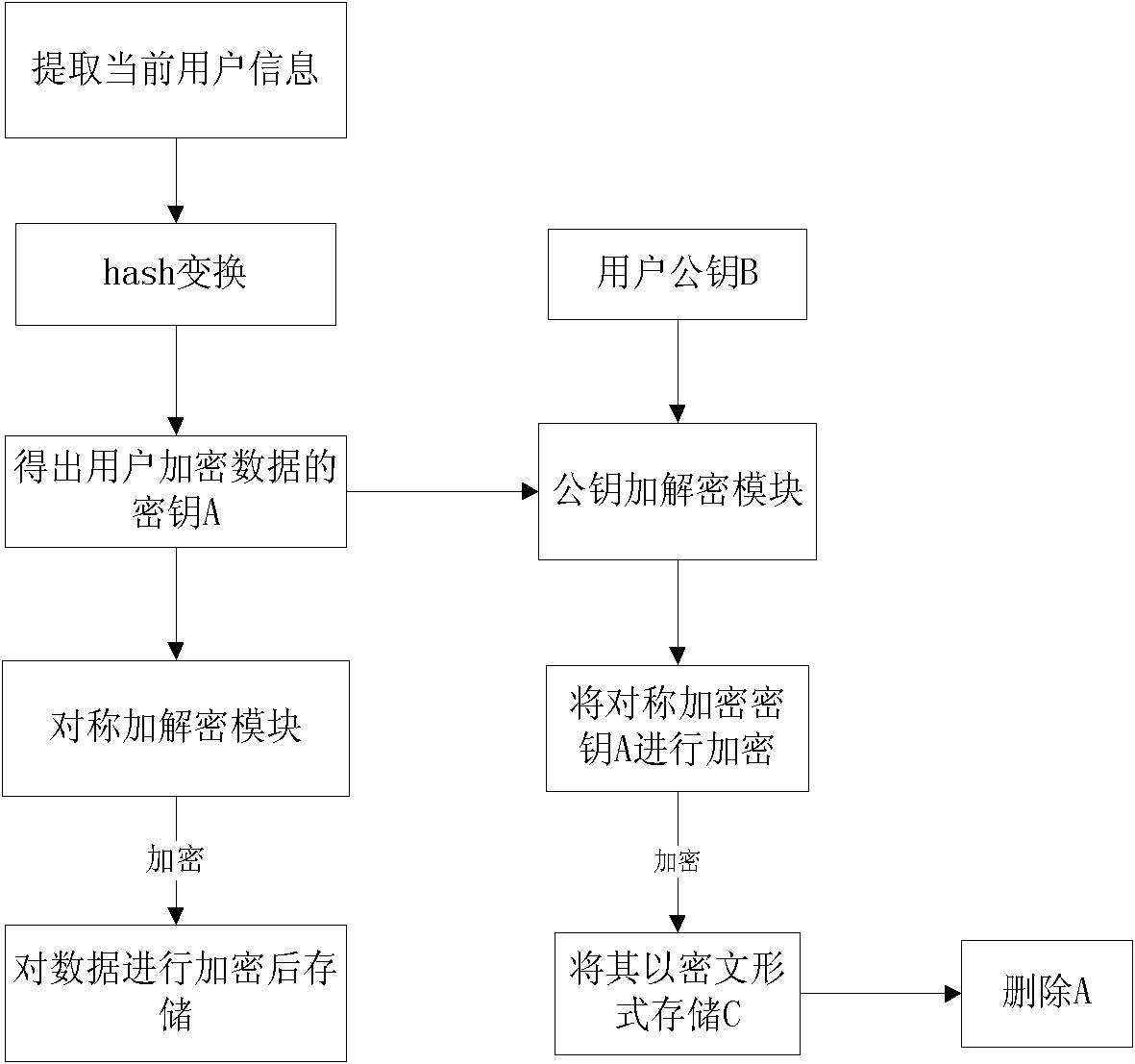
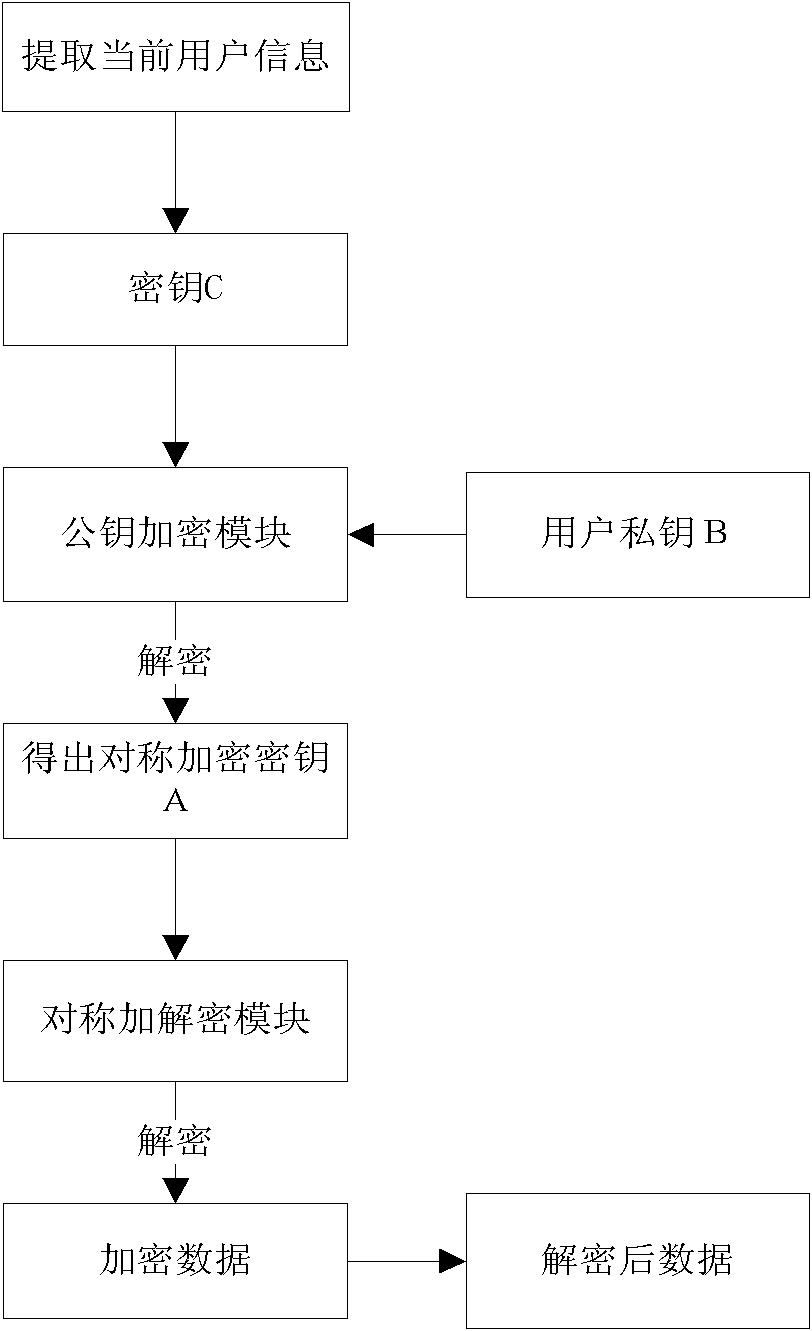
Encryption system, encryption method and decryption method for local area network shared file
InactiveCN102075544AEnsure safetyGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationInformation securityShared resource
The invention discloses an encryption system for a local area network shared file. The system comprises a secret key management module of a secret key to be used by reading, generating and managing an encryption file, and an encryption and decryption module for performing encryption and decryption according to a user command. The encryption system is characterized by also comprising an identity authentication module used for verifying the identity of a user and determining the authority of the user; and after the identity authentication module verifies that the identity of the user is legal, the encryption and decryption module performs encryption and decryption, and then the local area network shared file is accessed. The system limits the authority that different specified users read different files in shared resources, so that the information safety of resources in the local area network can be effectively guaranteed.
Owner:博视联(苏州)信息科技有限公司
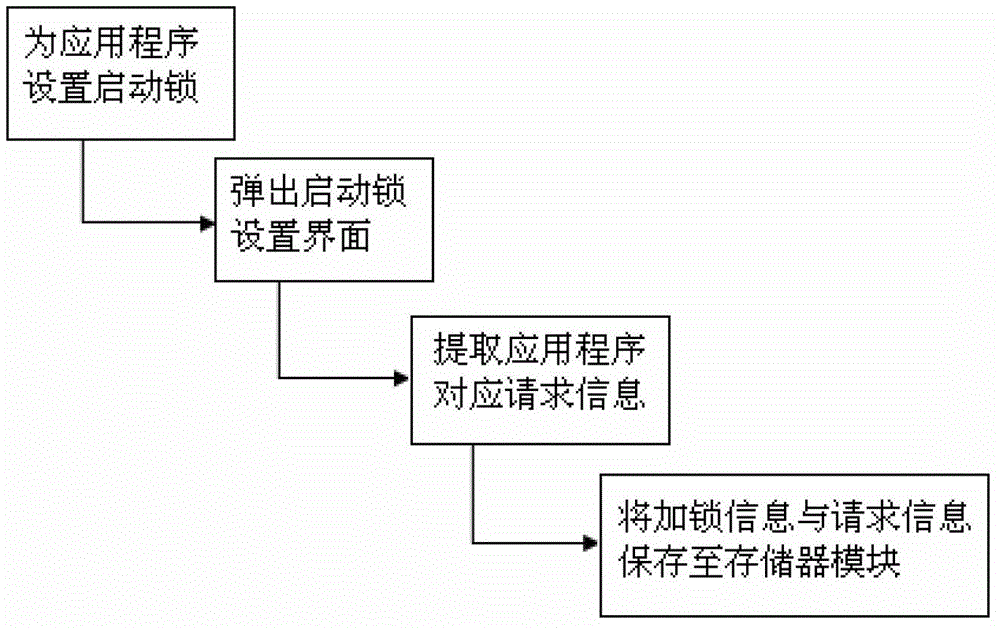
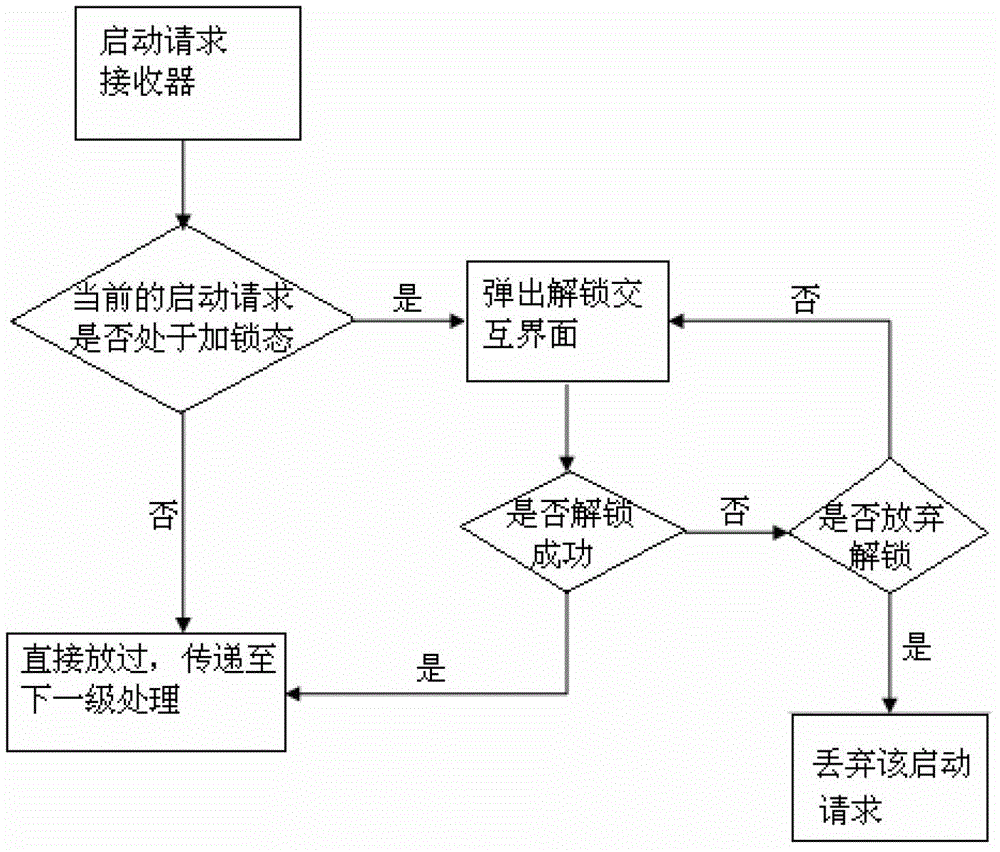
Starting lock for mobile terminal application program
ActiveCN103336924AFix security issuesGuarantee privacy and securityComputer security arrangementsOperational systemApplication software
The invention discloses a starting lock for a mobile terminal application program, and particularly relates to a starting lock of an application program. The starting lock for the mobile terminal application program comprises an operating system platform, the operating system platform is provided with an application program manager which manages at least one application program, and the application program manager comprises a locking module, a storage module and an unlocking module, wherein the storage module stores the locking information of the locking module and relevant starting request information. After the application program manager receives the starting request of an application program, the application program manager analyzes, identifies and judges the starting request, the unlocking module is started for the locked starting request, and the application program manager enables input unlocking information and locking information in the storage module to be matched and judged. According to the starting lock for the mobile terminal application program, the starting request information is extracted and stored during locking, the starting request information is detected, intercepted and captured in use, operation verification is conducted, and therefore individual privacy and information safety are further guaranteed in the using process of the application program.
Owner:宋易霄
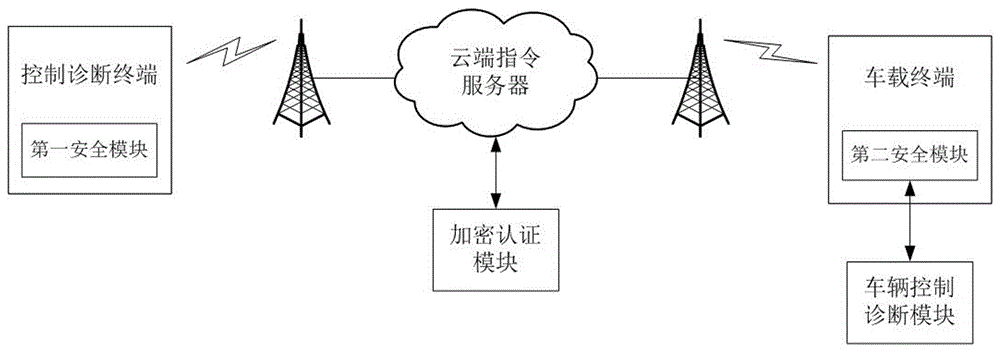
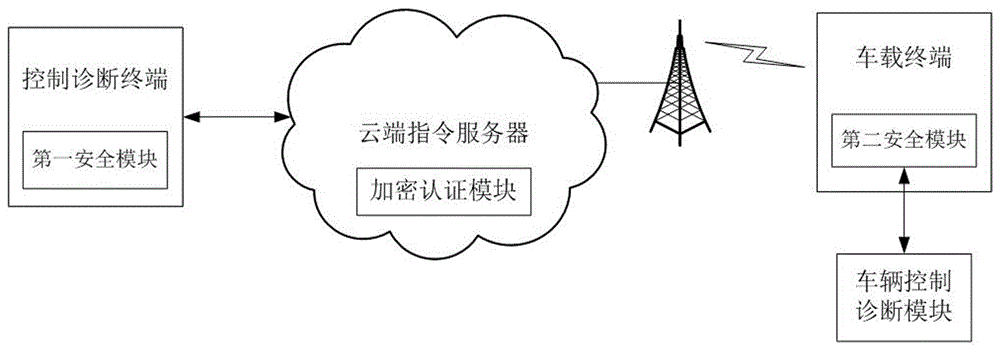
Method for vehicle safety remote control and diagnosis and system thereof
ActiveCN106713264APrevent access to the systemGuarantee information securityKey distribution for secure communicationUser identity/authority verificationRemote controlComputer terminal
The invention provides a method for vehicle safety remote control and diagnosis and a system thereof. A control and diagnosis terminal and a cloud side instruction server perform first identity authentication and key agreement; a vehicle-mounted terminal and the cloud side instruction server perform second identity authentication and key agreement; and the control and diagnosis terminal establishes communication connection with the vehicle-mounted terminal through the cloud side instruction server and performs remote control or remote diagnosis on a vehicle according to the control and diagnosis instruction of a user. Different secret keys are adopted between the control and diagnosis terminal and the cloud side instruction server and between the vehicle-mounted terminal and the cloud side instruction server and so that the information security of remote control and diagnosis information can be guaranteed, and the problem of security insufficiency in the prior art can be effectively solved. The system for vehicle safety remote control and diagnosis has the advantages of being scientific in design, high in practicality, convenient and rapid, high in security and high in reliability.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
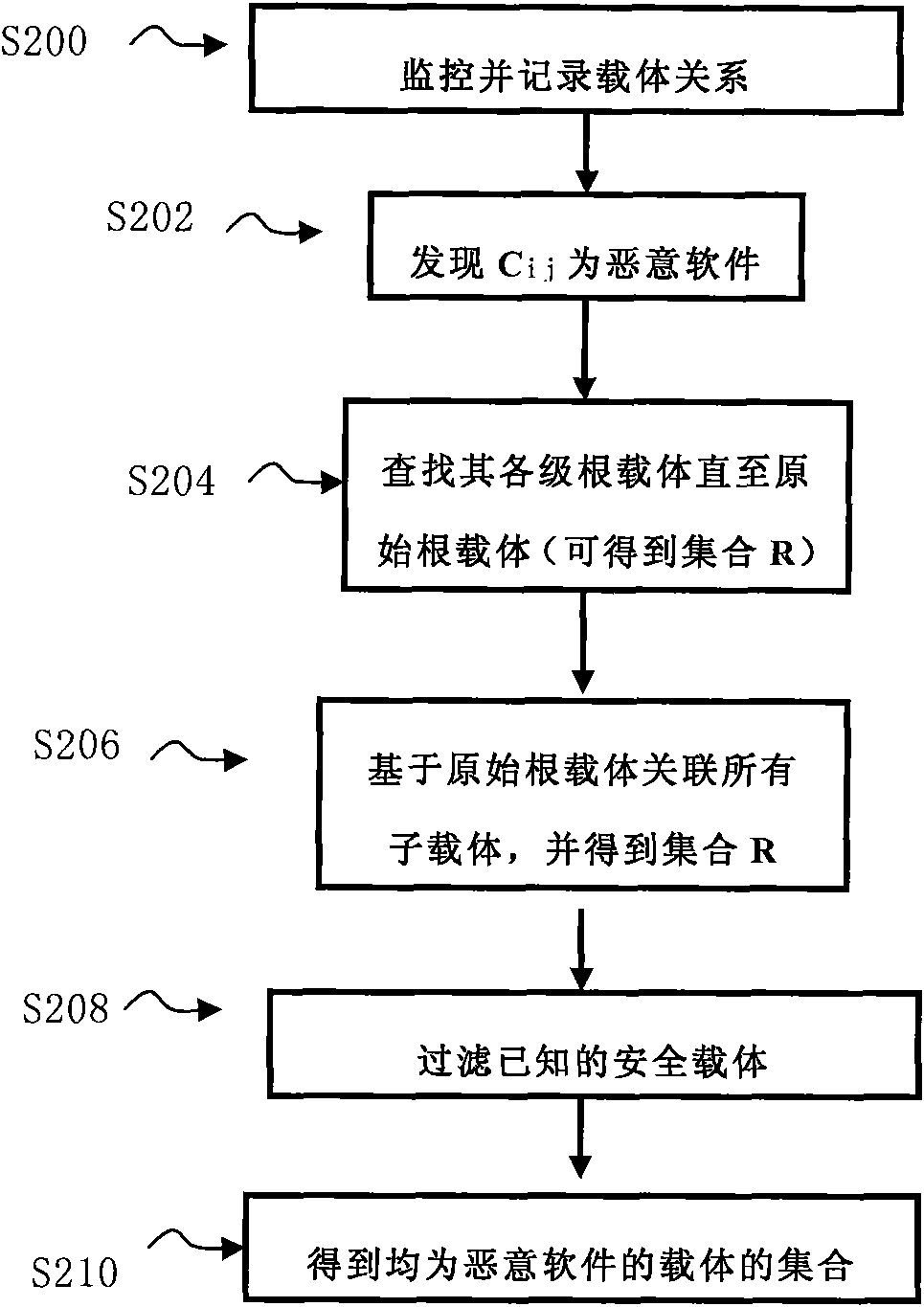
Method and device for detecting malicious software
InactiveCN101604361AUproot in timeCompletely uprootedPlatform integrity maintainanceSoftware engineeringMalware
The invention relates to a method and a device for detecting malicious software, which are used for detecting the malicious software. The invention can monitor and record the development change of the malicious software, can traced back the root of the virus, and can correspondingly detect the distortion relative to the malicious software or all the components when the problem occurs. The invention can emphasize internal change and relation when concerning the fake surface of the malicious software, thereby providing full guarantee for information safety of a user system.
Owner:BEIJING QIHOO TECH CO LTD
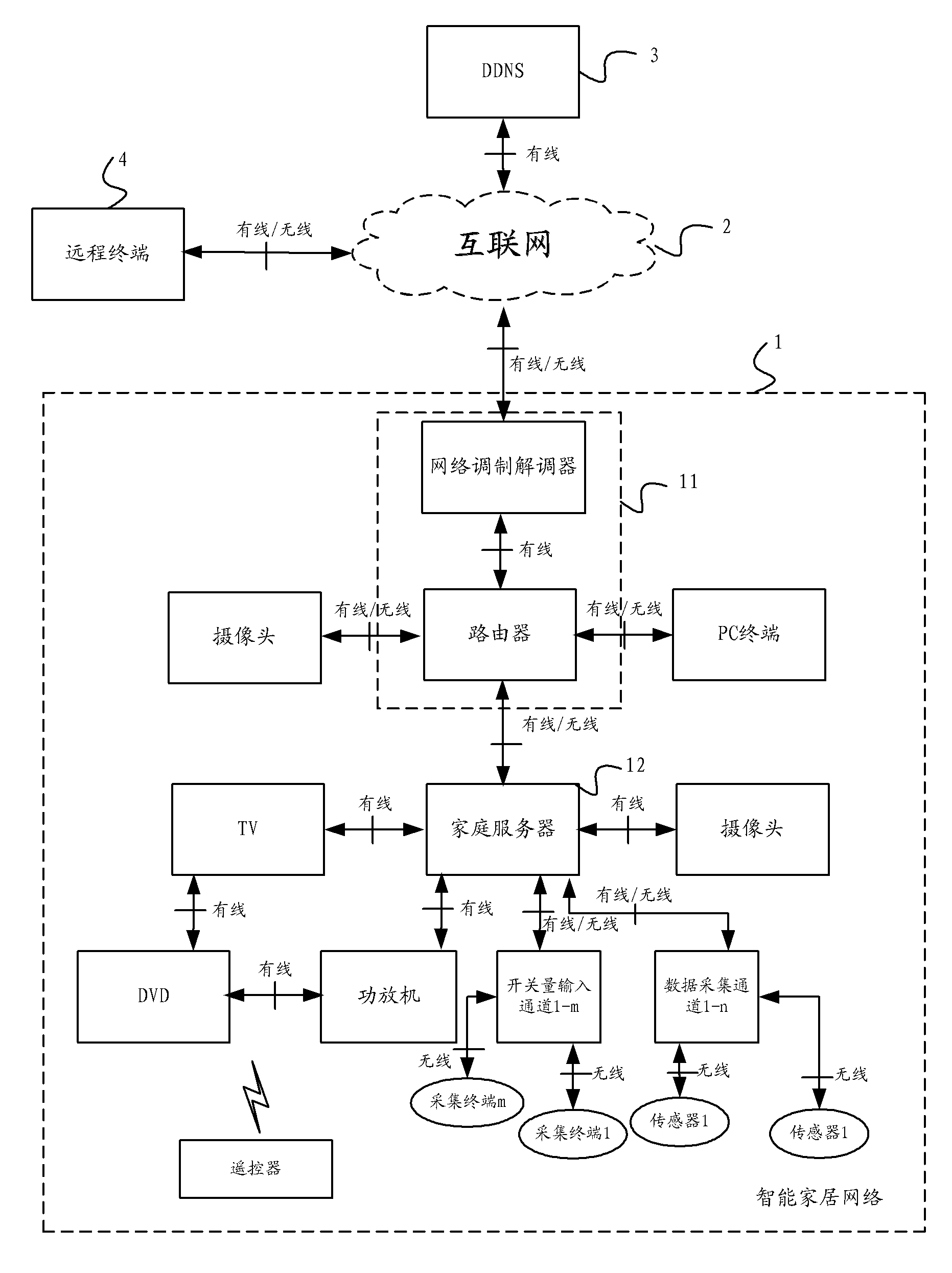
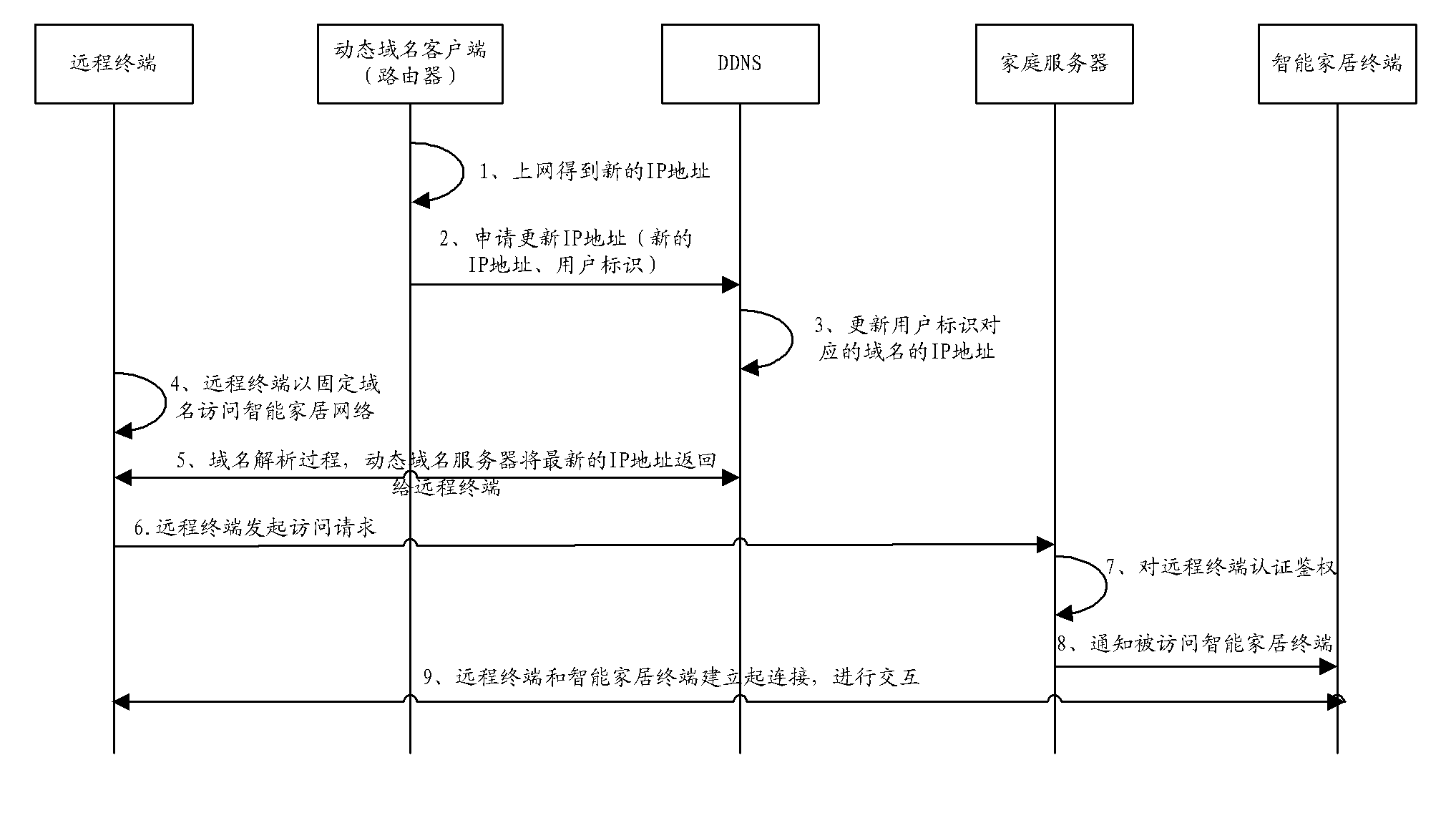
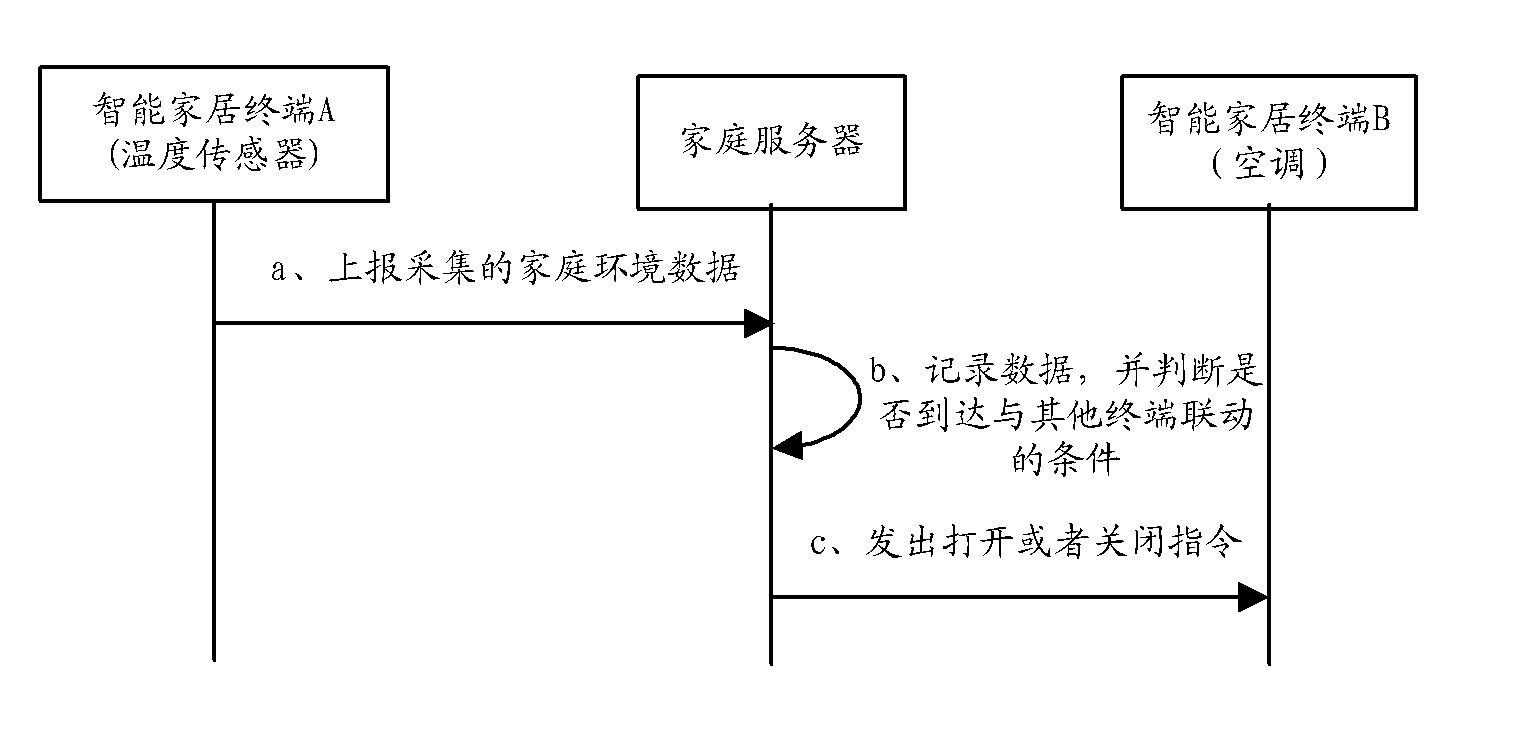
Intelligent home system
InactiveCN102546330AGuarantee privacy and securityGuarantee information securityData switching by path configurationDomain nameInternet communication
The invention provides an intelligent home system. The system comprises an intelligent home network, the Internet and a dynamic domain name server. The intelligent home network comprises network equipment, a home server and a plurality of intelligent home terminals, wherein the network equipment is in communication connection with the Internet, the home server is in communication connection with the network equipment and is used for information interaction with the network equipment, receiving information sent by the intelligent home terminals and sending control signals to the intelligent home terminals so as to control the work of the intelligent home terminals, and the intelligent home terminals are in communication connection with the home server. The dynamic domain name server is in communication connection with the Internet and is used for receiving a dynamic IP (Internet Protocol) address sent by the network equipment through the Internet, binding the dynamic IP address to the fixed domain name of the intelligent home network, and carrying out domain name resolution. With the adoption of the intelligent home system provided by the invention, the functions, such as video surveillance, leisure and entertainment, intelligent control of household appliances and home environment monitoring, can be achieved, and the customized customization, assembly and association can be achieved; and the information security can be guaranteed because no external operation service platform exists.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
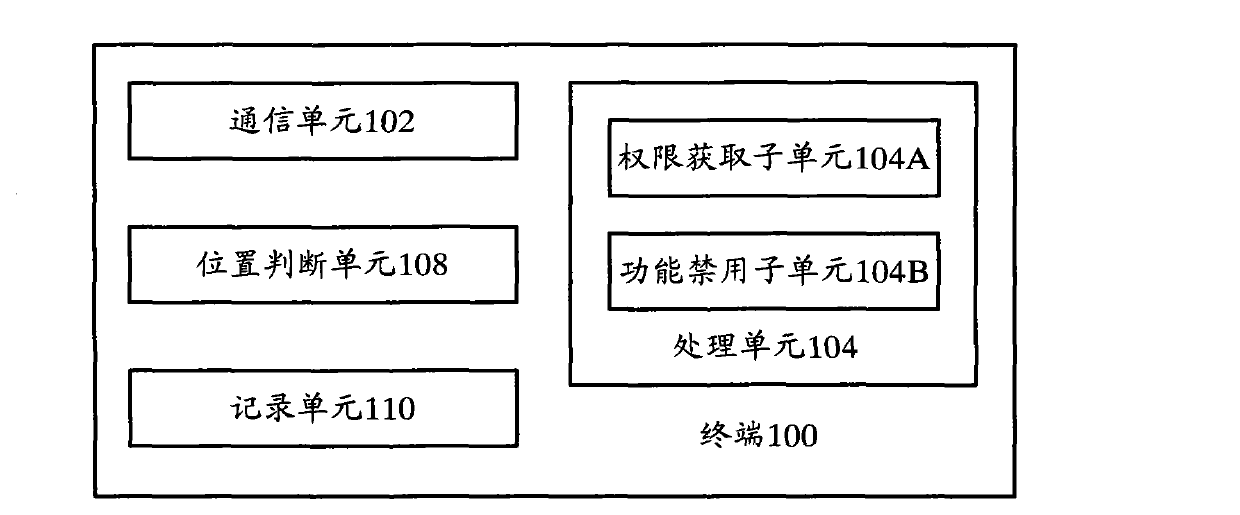
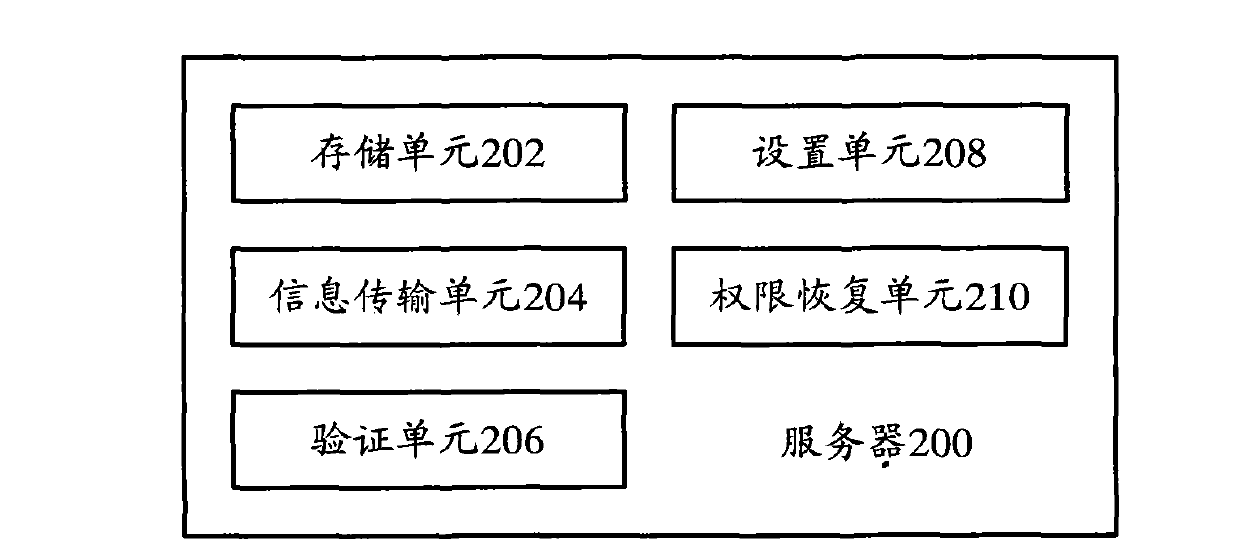
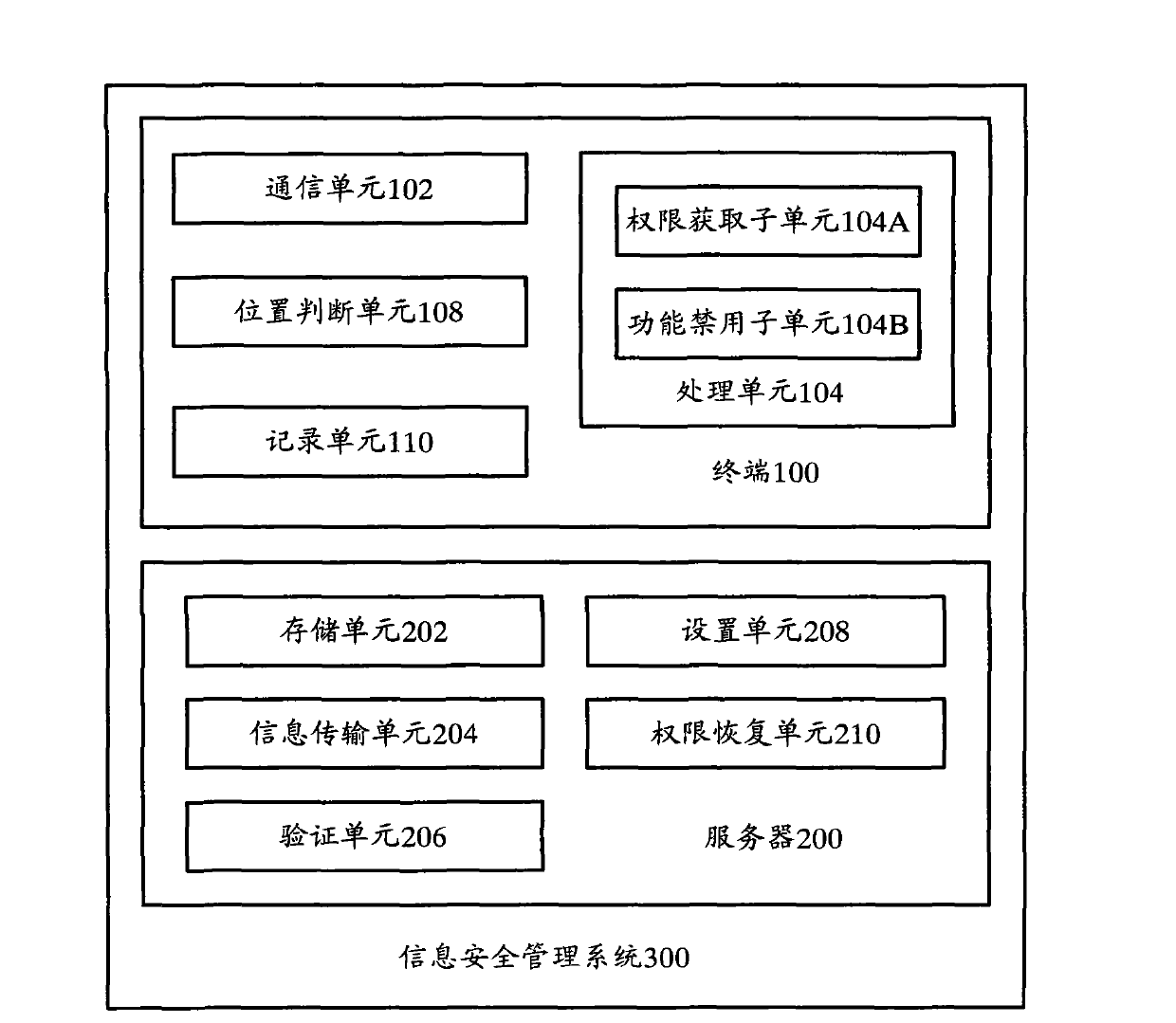
Terminal, server and terminal safety management method
ActiveCN103312676AGuarantee information securityPrevent leakageTransmissionCommunication unitComputer terminal
The invention provides a terminal which comprises a communication unit and a processing unit, wherein the communication unit is used for sending verification request information into a server and receiving permission setting information corresponding to the verification request information from the server; the processing unit is used for configuring the corresponding terminal permission setting according to the permission setting information coming from the communication unit. Correspondingly, the invention also provides the server and a terminal safety management method. After the technical scheme is adopted, the information security problem caused by the mobile terminal can be solved, and information of an area to be protected can be effectively guaranteed to be safe.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method for monitoring high-availability cluster resource
InactiveCN105141456AGuarantee information securityEnsure safetyData switching networksDowntimeInformation security
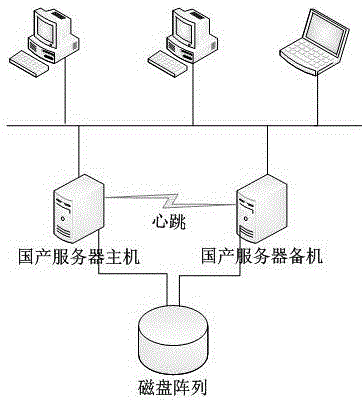
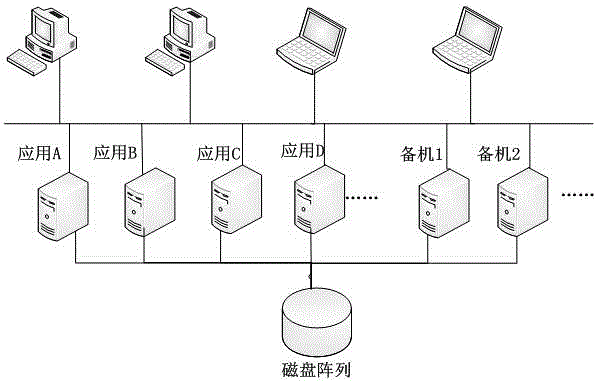
The invention particularly relates to a method for monitoring a high-availability cluster resource. The method for monitoring the high-availability cluster resource comprises the following steps that: heartbeat software, cluster resource layer software and cluster graphical management software are modified, compiled and installed on a cluster node based on a domestic platform; simultaneously, a master node, a backup node, a management node and a monitoring node are arranged in a cluster based on the domestic platform; the backup node and the master node keep information synchronous at any time; and the backup node takes over works of the master node in time when the master node has a downtime fault. According to the method for monitoring the high-availability cluster resource disclosed by the invention, the backup node and the master node keep information synchronous at any time; the backup node takes over works of the master node in time when the master node has the downtime fault; therefore, information safety and uninterrupted continuous operation of various key applications on the domestic platform can be ensured; and virtuous circle of sustainable operation is realized.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Method, system and management center server for providing mobile service
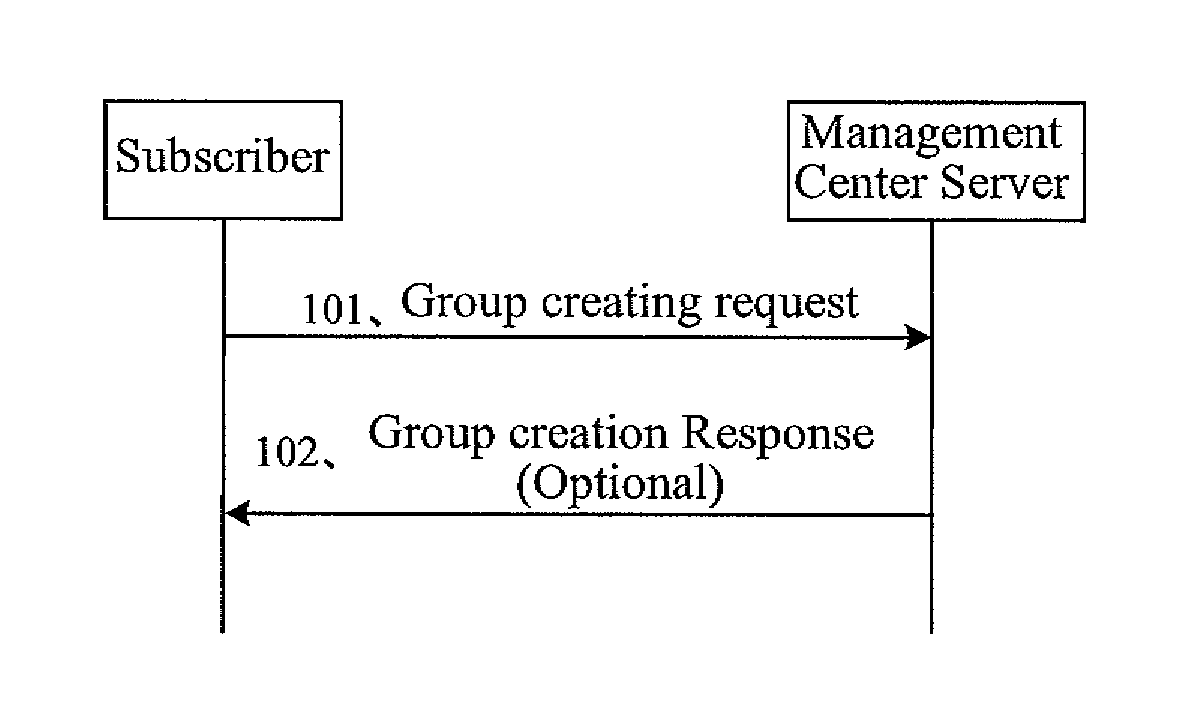
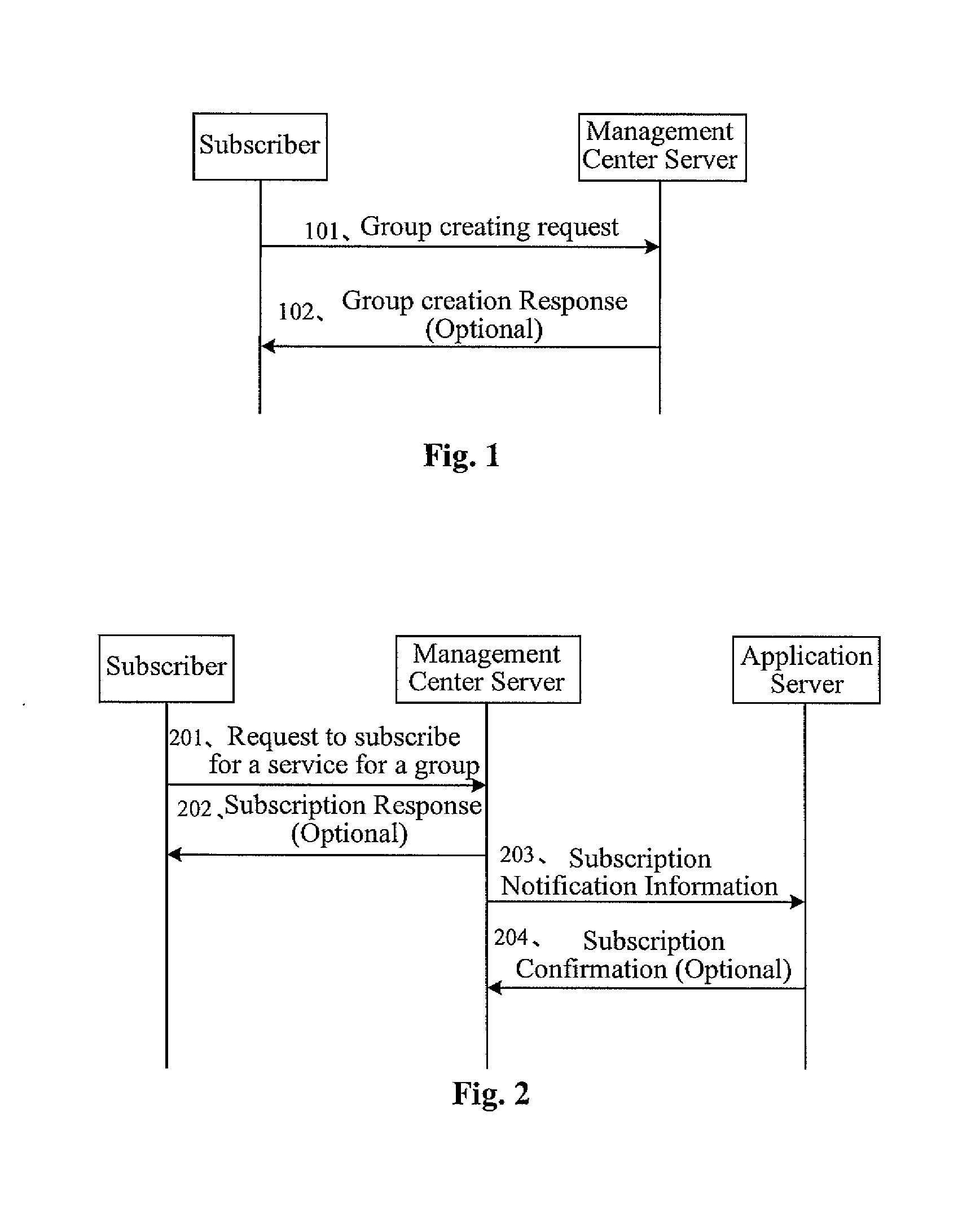
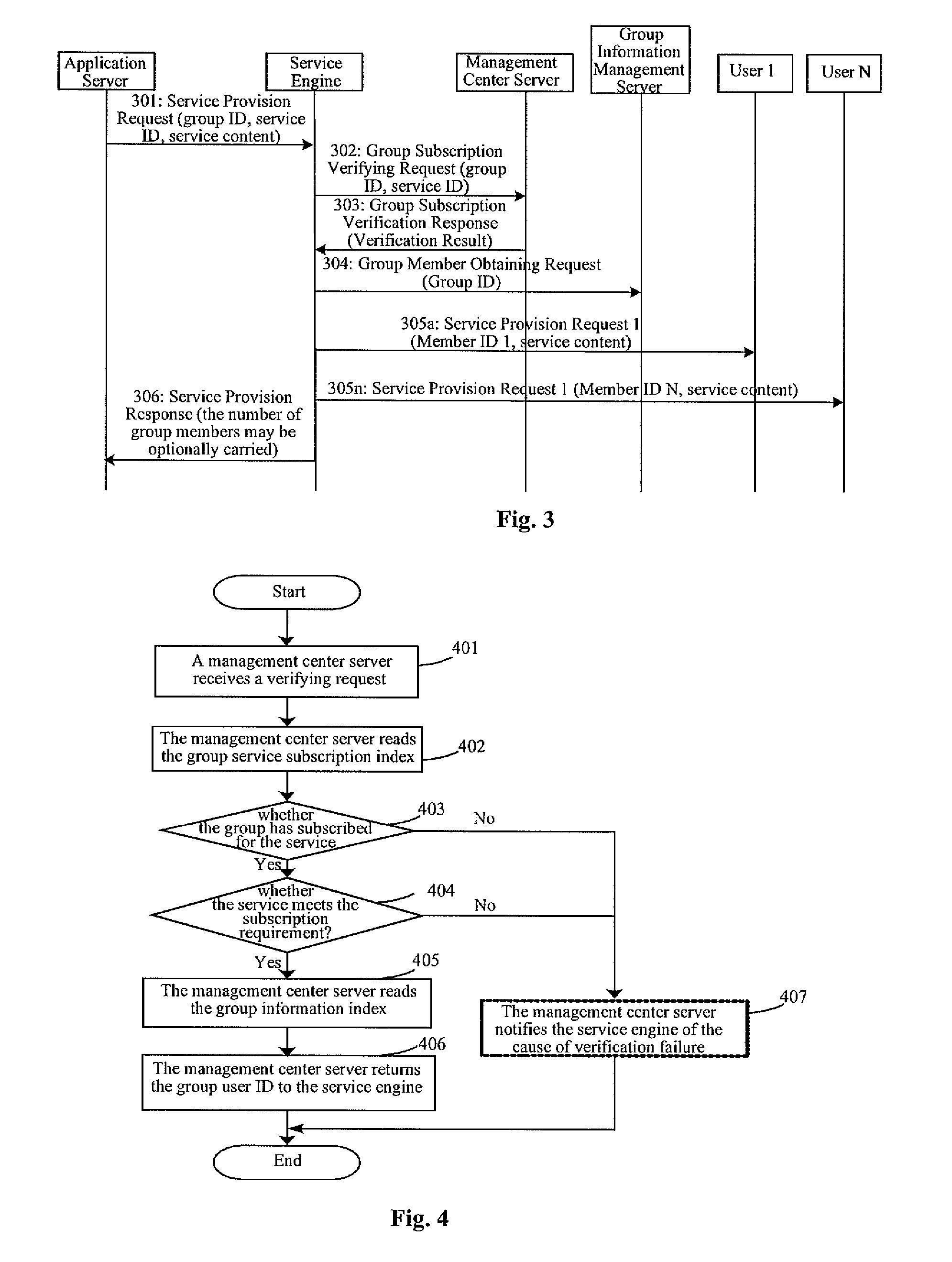
InactiveUS20080045192A1Network flow can be loweredReduce in quantitySpecial service for subscribersTransmissionApplication serverMobile service
A method and a system for providing mobile service are disclosed. In the method, a management center server saves a group service subscription index; a service processing server receives a service message from a service application server, and sends a subscription verifying request containing the service ID and group ID to the management center server when it is resolved that the receiving party of the service message has a group ID; the management center server verifies whether the group has subscribed for the service according to the group service subscription index that is stored; and when the verification is passed, a service engine obtains the group user ID that pertains to the group ID and sends a service message to a user terminal. The invention further provides a management center server.
Owner:HUAWEI TECH CO LTD
Authorized identity-based search encryption method with a keyword
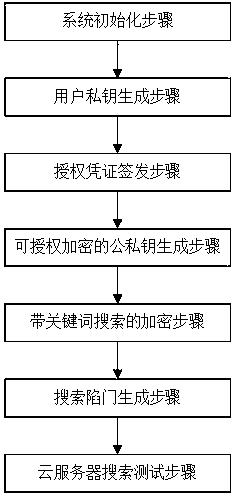
ActiveCN109614818AStrong application flexibilityGuarantee information securityDigital data protectionKey generationAuthorization
The invention discloses an authorized identity-based search encryption method with a keyword. The method comprises the following steps of: initializing a system; a user private key generation step; anauthorization certificate issuing step; generating public and private keys which can be authorized and encrypted; an encryption step with keyword search; a search trap door generation step; cloud server search test step. The method provided by the invention has an authorization function; the application flexibility is relatively high; the proxy uploading problem of searchable encrypted files canbe solved; an original data owner is supported to authorize an agent to help the agent upload a ciphertext of plaintext information and a ciphertext of a keyword to a cloud server, the characteristicof keyword guessing resistance is provided, the server cannot guess the keyword being queried by a user, and the information security of cloud data is effectively guaranteed.
Owner:SOUTHWEST PETROLEUM UNIV
Safety protection architecture for vehicle-mounted Ethernet
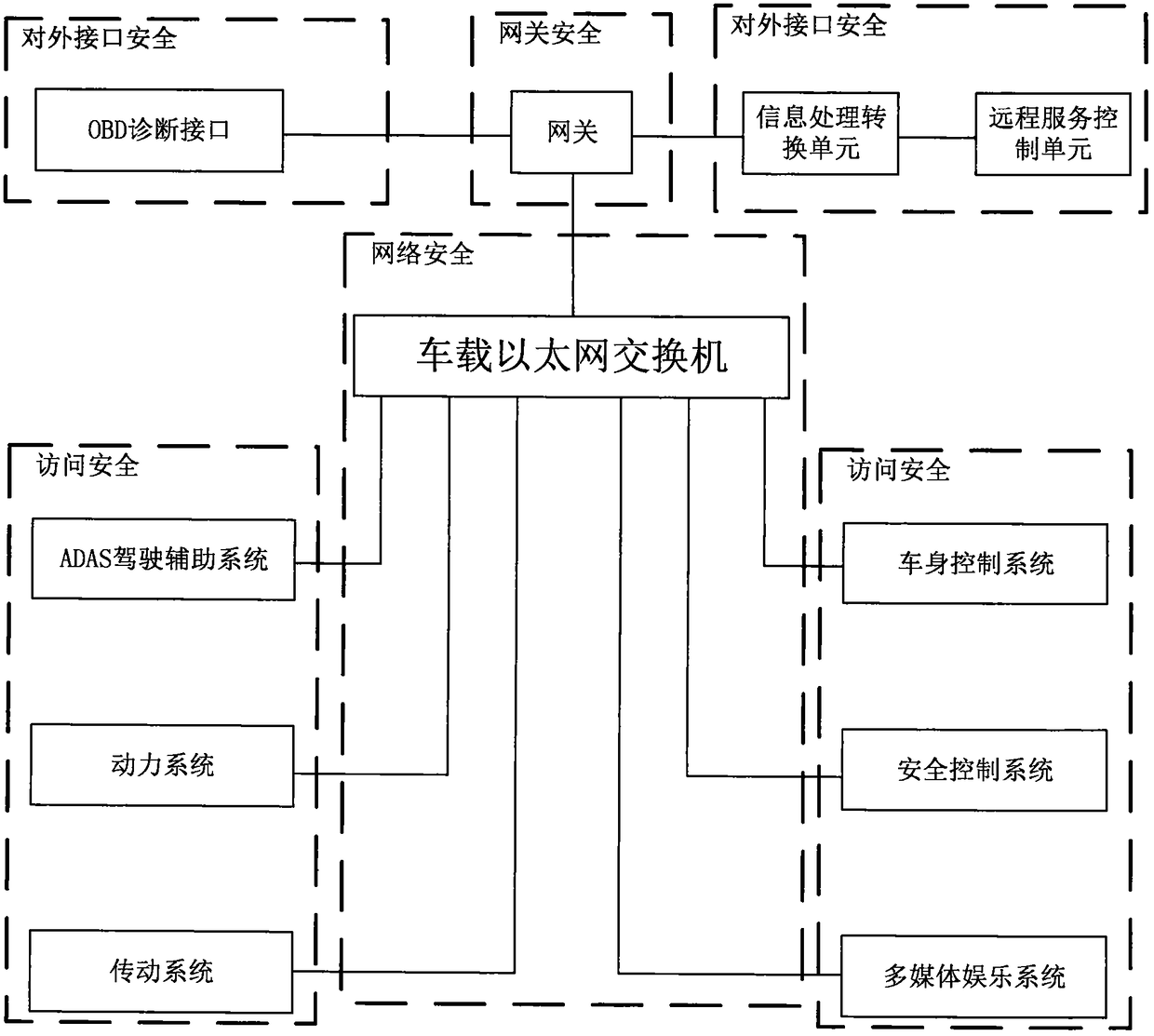
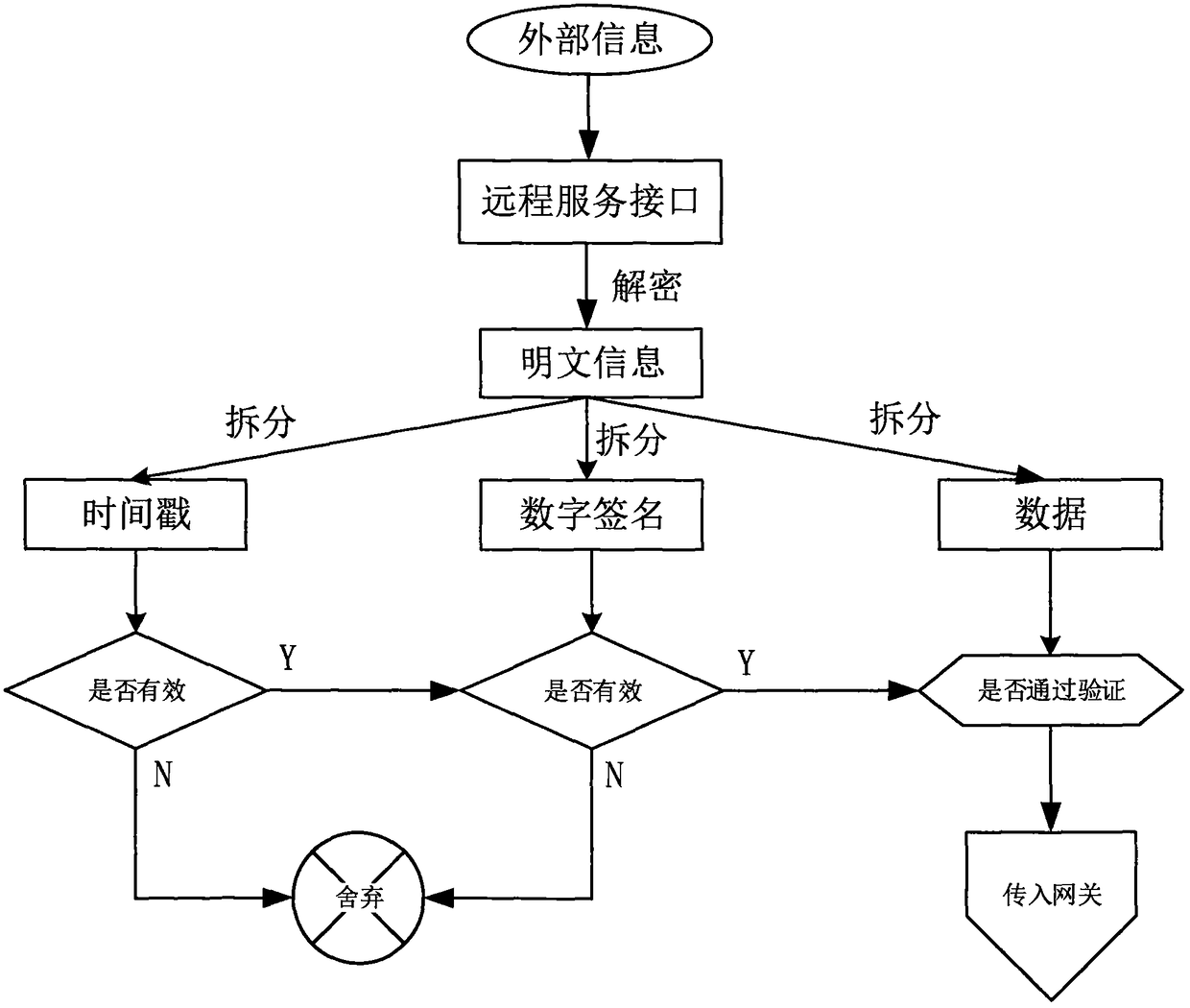
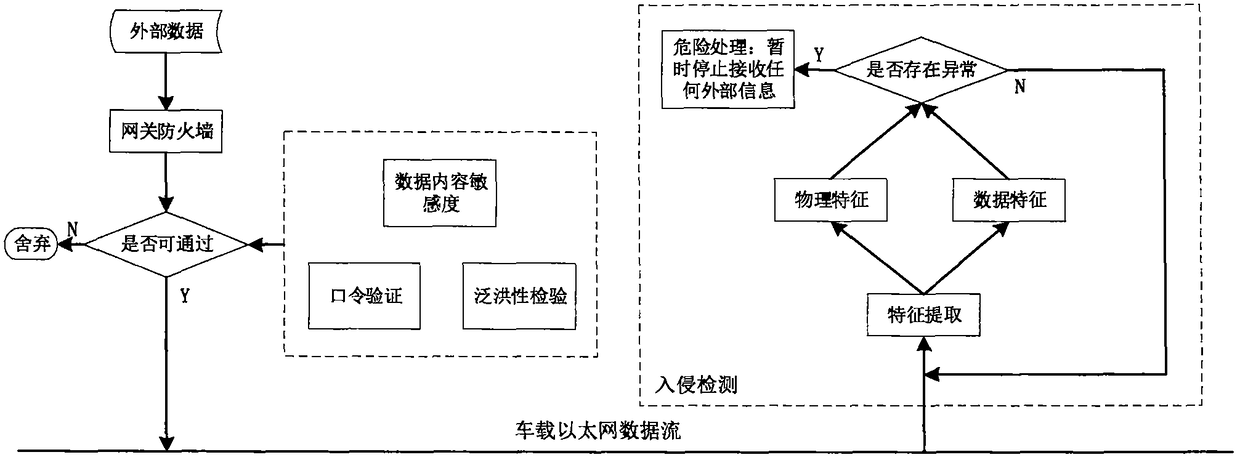
InactiveCN108521410AGuarantee information securityEnsure safetyBus networksCommunications securityIn vehicle
The invention relates to the field of communication safety of an electric vehicle, and particularly relates to a four-layer network safety protection architecture for vehicle-mounted Ethernet, which comprises external interface safety, gateway safety, network safety and access safety. The external interface safety comprises a vehicle-mounted OBD diagnose interface and a remote service informationinterface; the gateway safety comprises safety-authentication gateway safety in a vehicle-mounted Ethernet structure, which takes charge of isolating external data from in-vehicle data; the access safety comprises software safety and data storage safety of a control system connected with the vehicle-mounted Ethernet; the network safety comprises safety of a vehicle-mounted Ethernet link and carries out packaging isolation on a line of the vehicle-mounted Ethernet; and the access safety comprises the software safety and the data storage safety of the control system connected with the vehicle-mounted Ethernet. The four-layer network safety protection architecture is simple in structure, high in implementation, stable, reliable and wide in adaptability.
Owner:BEIHANG UNIV
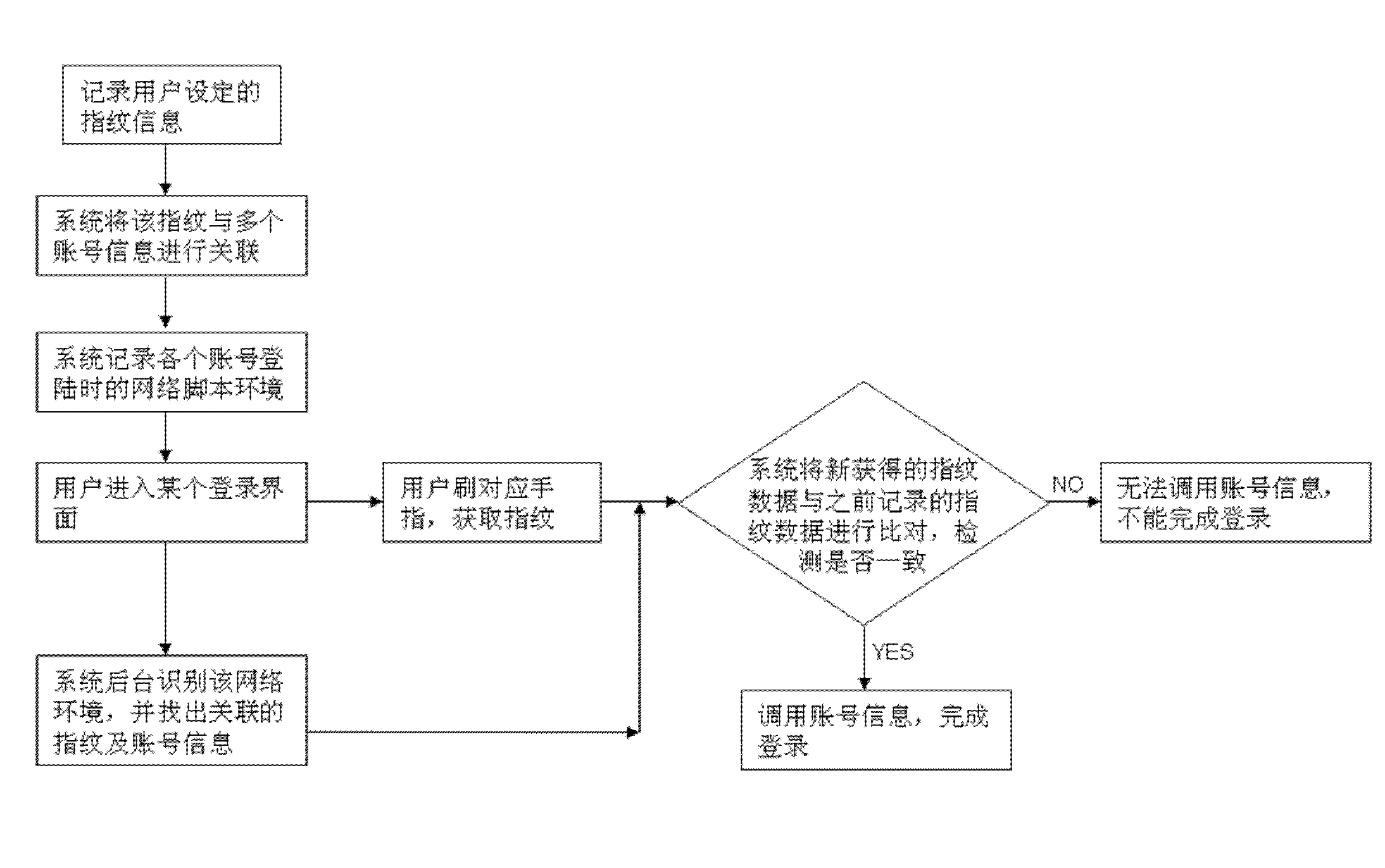
Method for authenticating account by using fingerprint identification
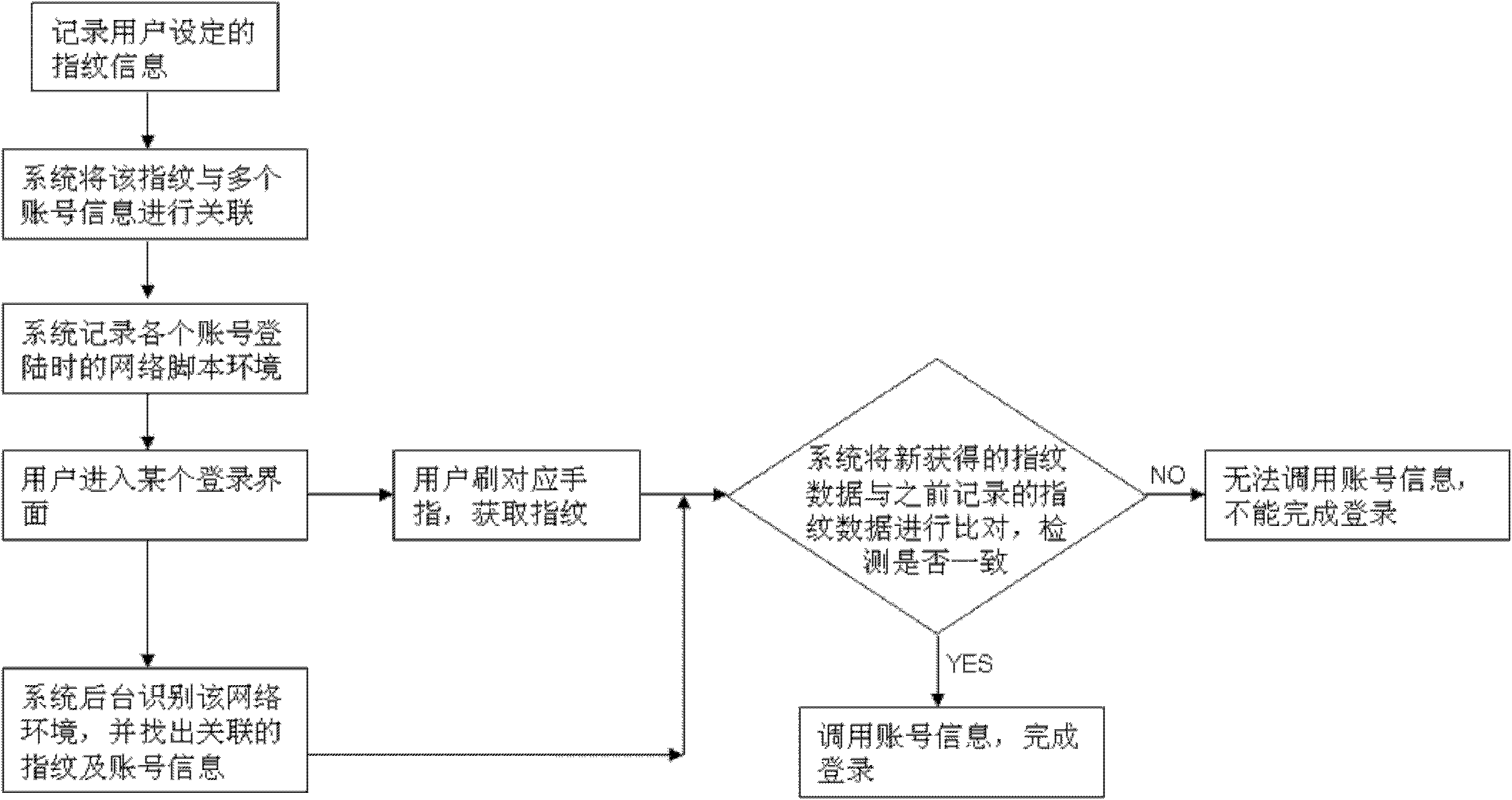
InactiveCN102156857ASave the input processShorten the timeUser identity/authority verificationCharacter and pattern recognitionPasswordAuthentication
The invention relates to a method for authenticating an account by using fingerprint identification. The method comprises the following steps: a system acquires and records fingerprint data of a user and associates the fingerprint information with each account password of the user; the user wipes a corresponding finger when entering a login interface and the system acquires the fingerprint for comparison; the user cannot log in if the fingerprint is not consistent with the fingerprint information; and the user can call account information to finish login if the fingerprint is consistent with the fingerprint information. By implementing the method, the user can finish a network account authentication process by wiping the finger, so that a complex account password input process is saved, time is saved, efficiency is improved, and the information of the user is safer.
Owner:SHENZHEN SANG FEI CONSUMER COMM CO LTD
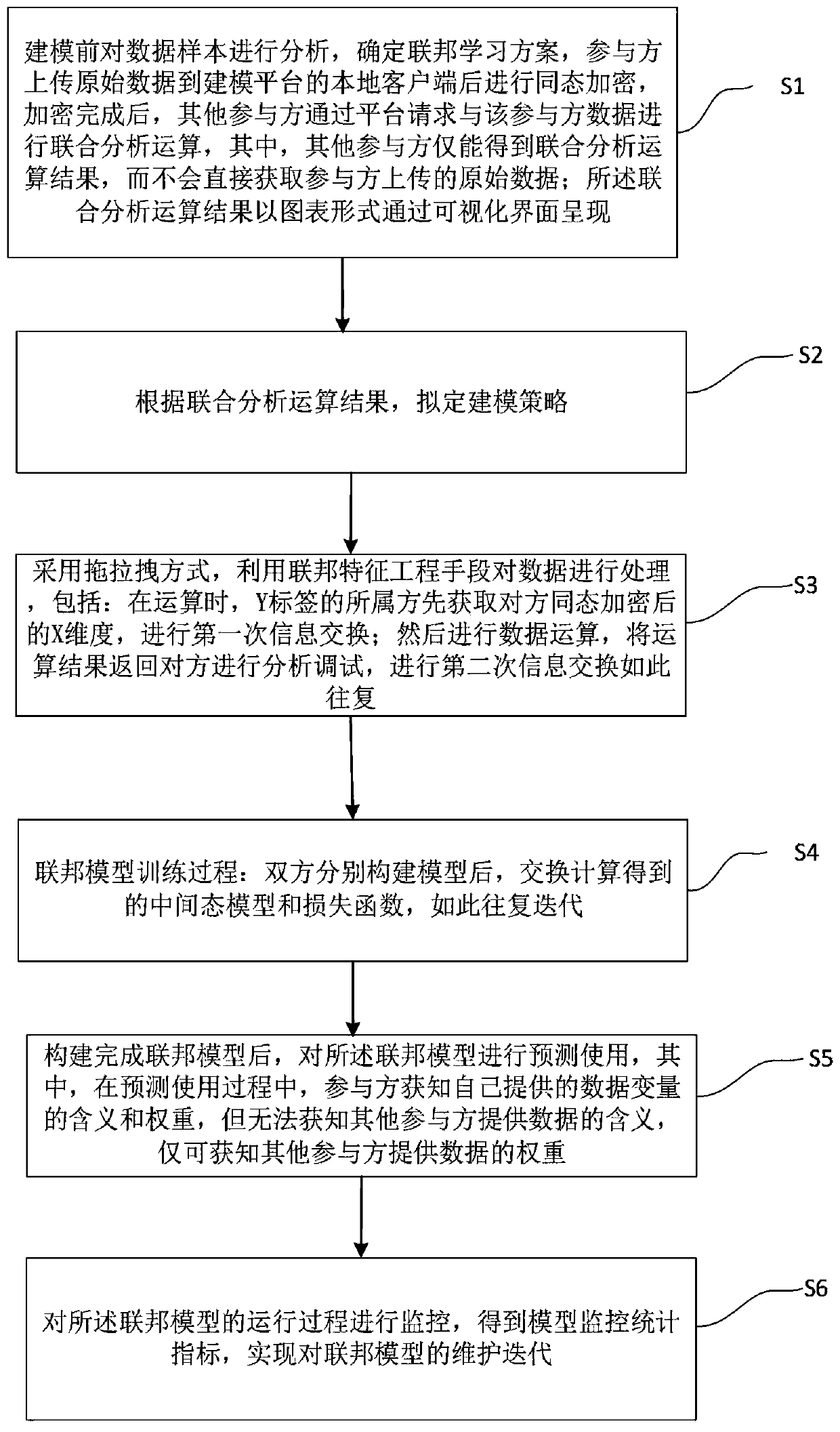
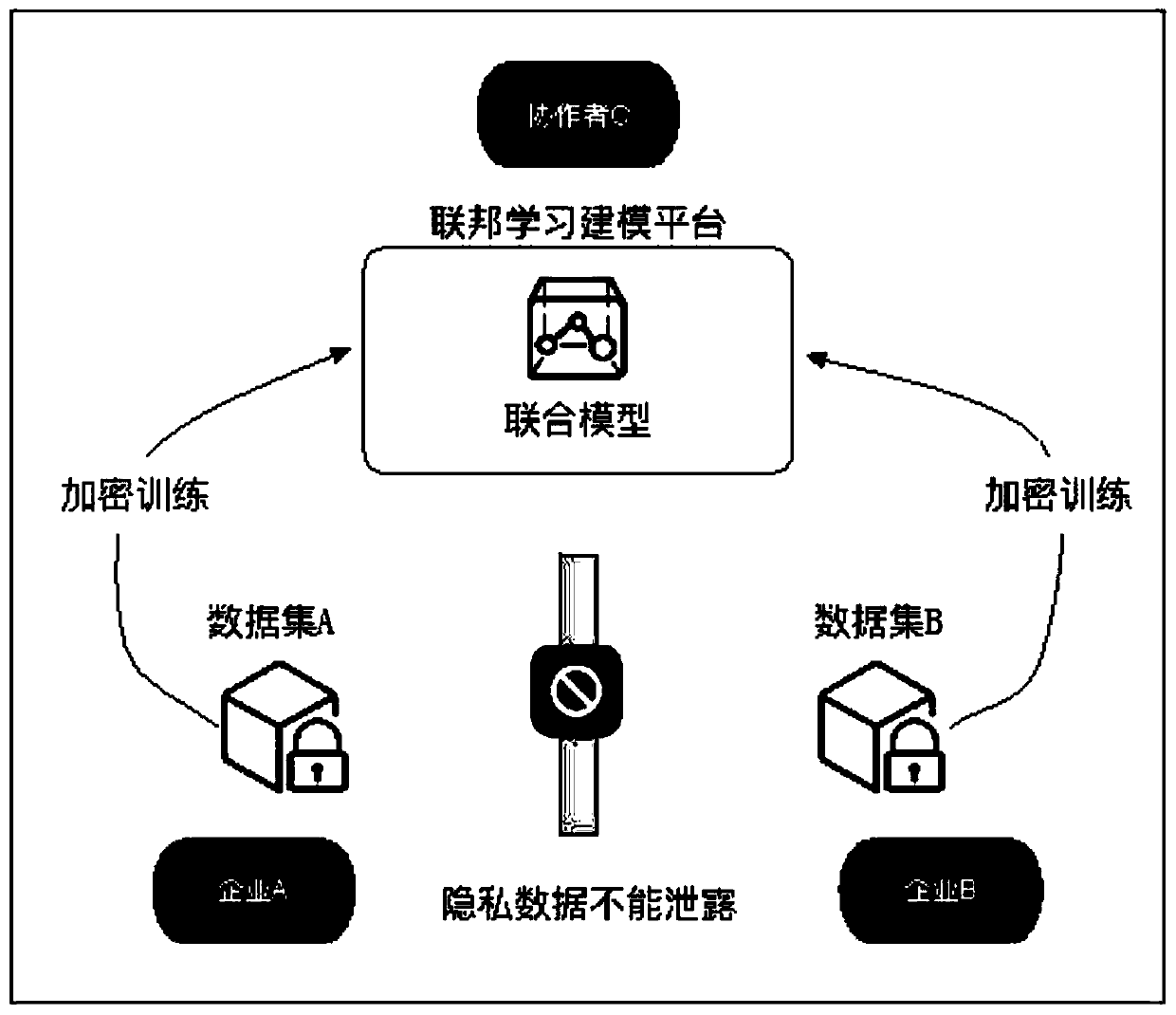
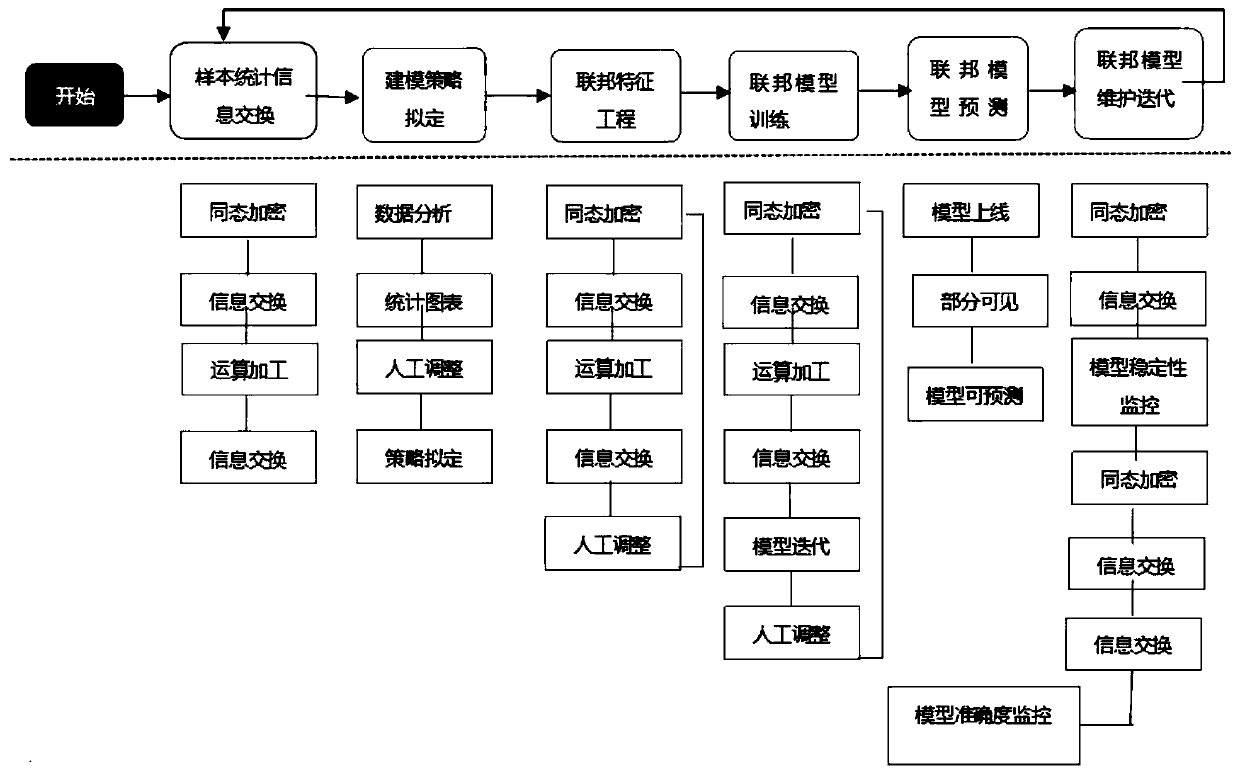
Graphical model full-life-cycle modeling method for federated learning
ActiveCN111104731AReduce the difficulty of participating in optimizationBroaden application scenariosDesign optimisation/simulationResourcesModelSimEngineering
The invention provides a graphical model full-life-cycle modeling method for federated learning, which comprises the following steps: analyzing a data sample before modeling, and determining a federated learning scheme; drawing up a modeling strategy according to a joint analysis operation result; adopting a dragging mode and using a federation feature engineering means to process the data; in thefederated model training process, after the two parties construct models respectively, exchanging an intermediate state model and a loss function which are obtained through calculation ; predicting and using the federated model; and monitoring the operation process of the federated model to obtain a model monitoring statistical index so as to realize maintenance iteration of the federated model.Personnel in each step of federated learning modeling can participate in optimization points through imaging, the personnel participation optimization difficulty is reduced, a later model applicationmaintenance way is provided, and the application scene and usability of the federated learning technology are improved.
Owner:BEIJING GEO POLYMERIZATION TECH
End index block chain-based distributed energy source system
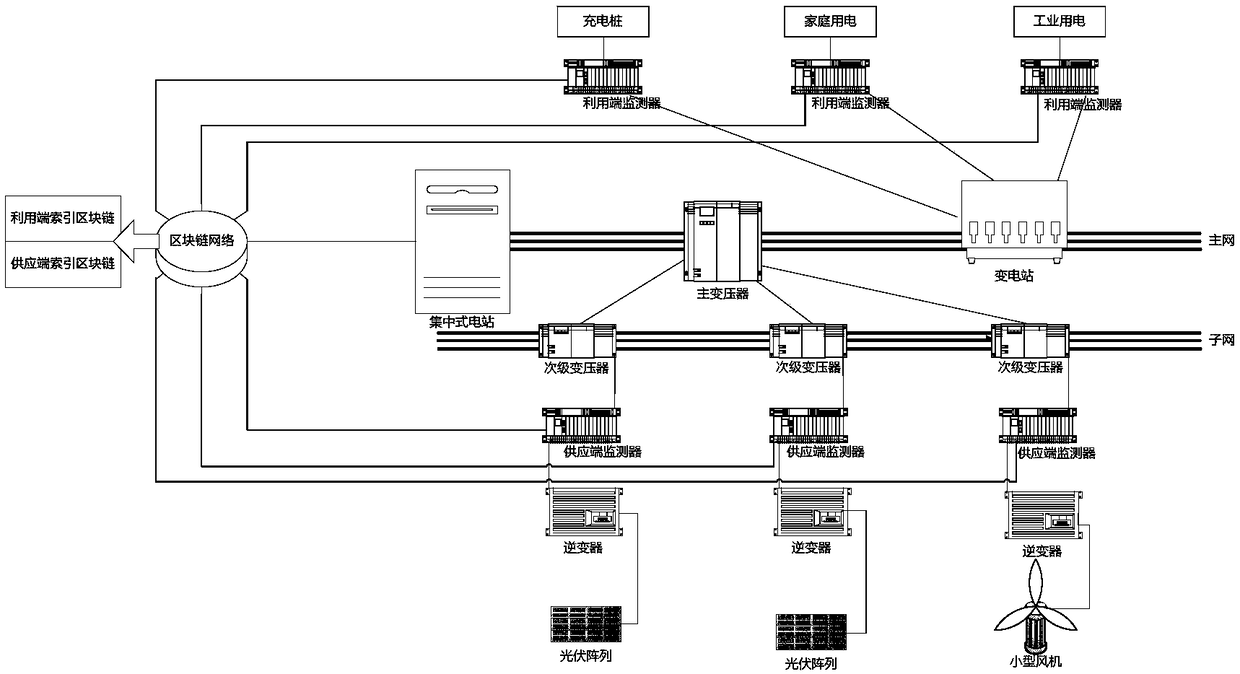
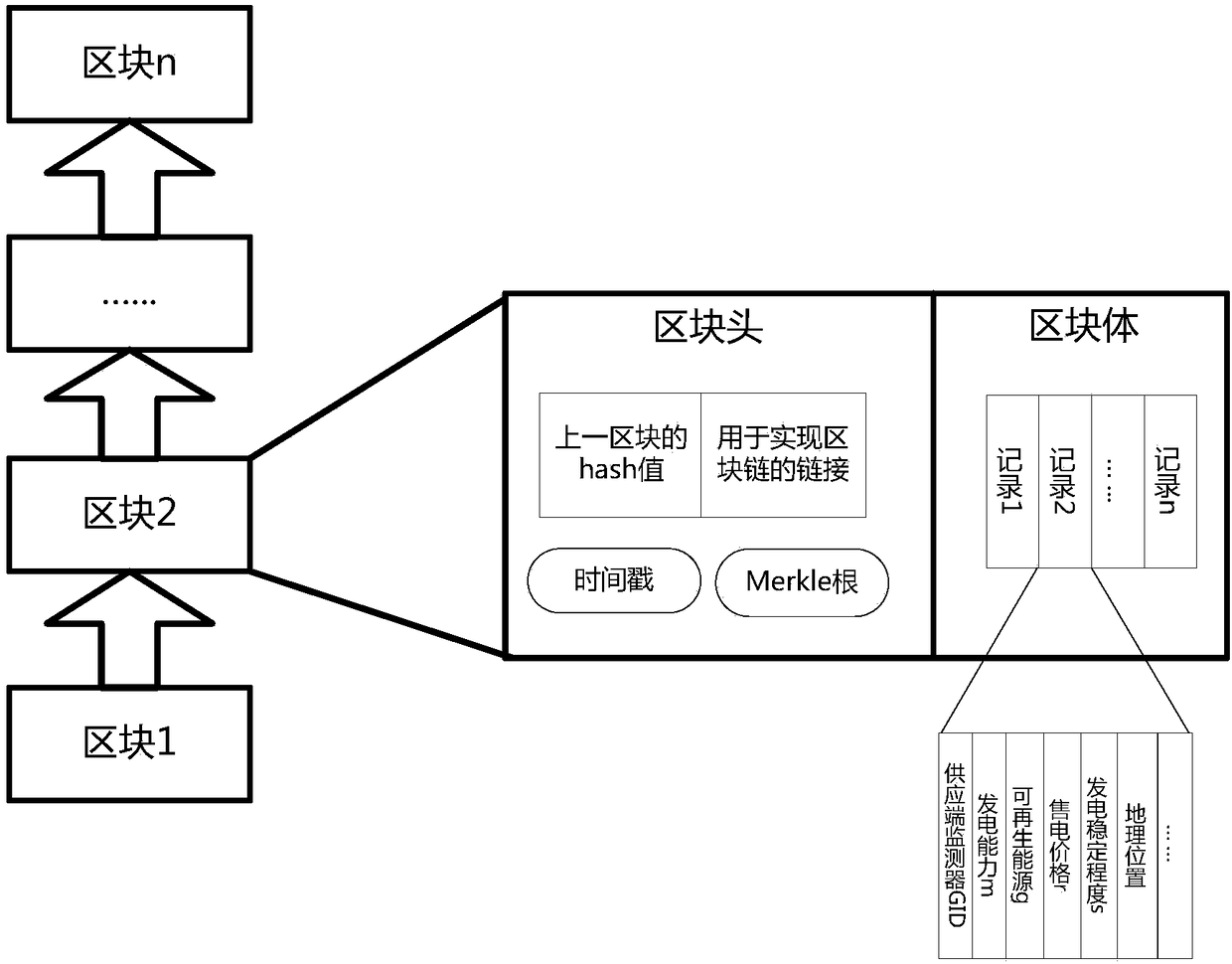
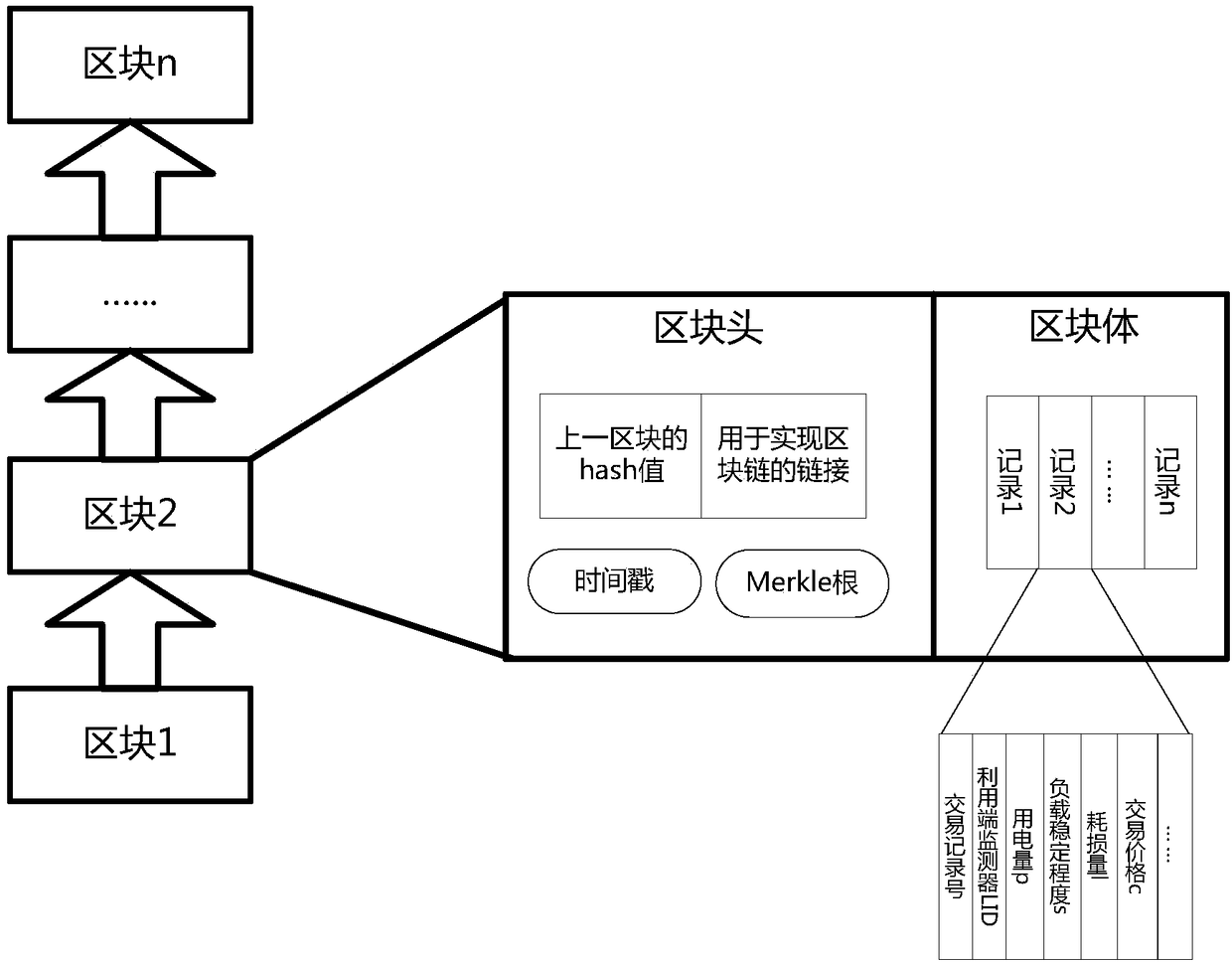
PendingCN108306292AWill not affect normal operationImprove robustnessFinanceInformation technology support systemTransformerEngineering
Disclosed is an end index block chain-based distributed energy source system. The distributed energy source system consists of a supply part, a utilization part, a power transmission part and a blockchain part, wherein the supply part comprises a centralized power station, a distributed power generation unit, an inverter and a supply end monitor; the utilization part comprises industrial power utilization equipment, a distributed power utilization unit and a utilization end monitor; the power transmission part comprises a sub network, a main network, a secondary transformer, a main transformer and a transformer substation; the block chain part comprises a block chain network; the block chain network is connected with the supply end monitor and the utilization end monitor to perform data exchange to form an electric power trade block chain; the electric power trade block chain comprises a utilization end formed block chain; and reasonable configuration of the distributed electric powerresource is realized based on the electric power trade block chain.
Owner:陈惠萍
Method and device for file safety control
ActiveCN103268456AImprove communication efficiencyGuarantee information securityDigital data protectionPlaintextCiphertext
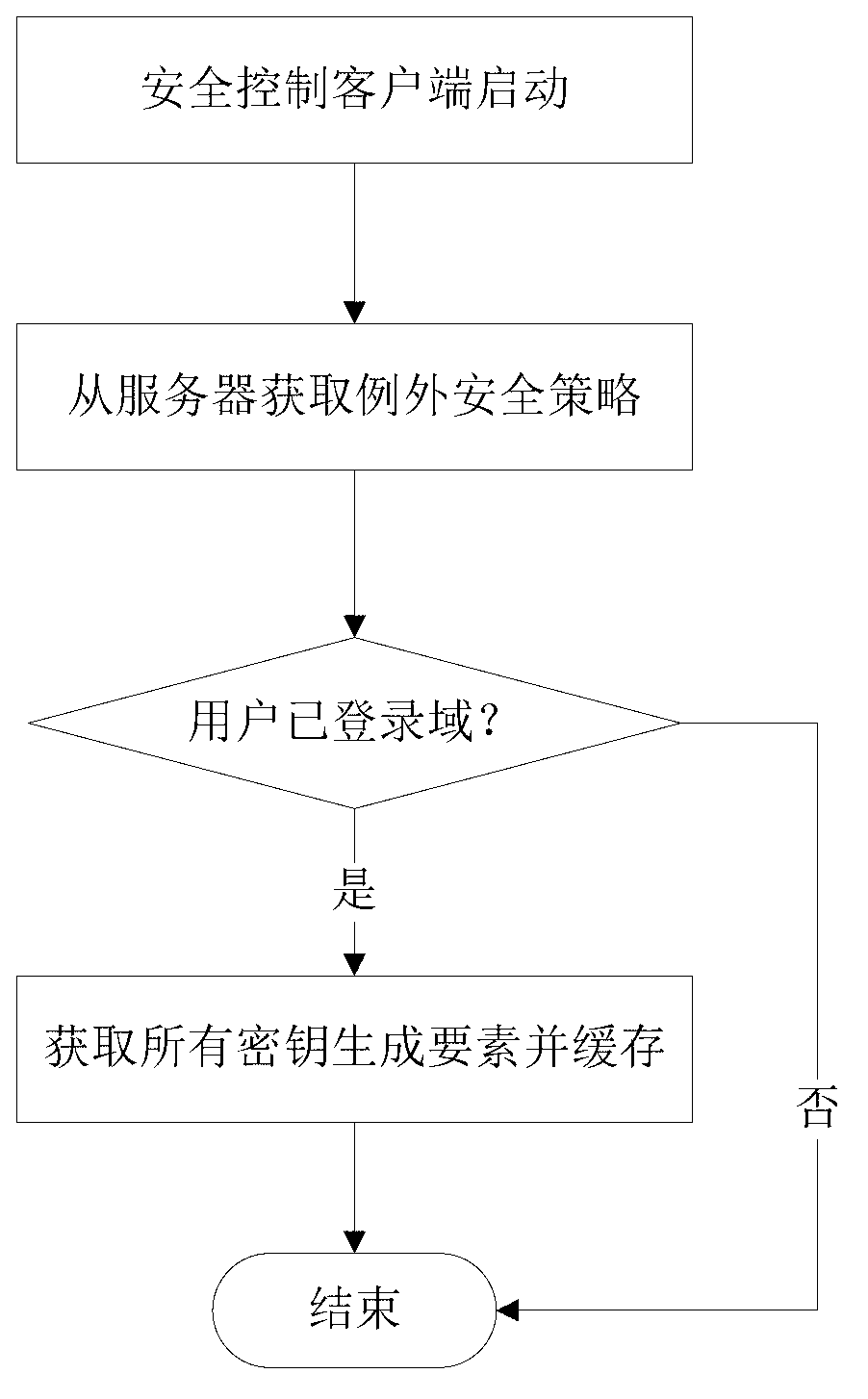
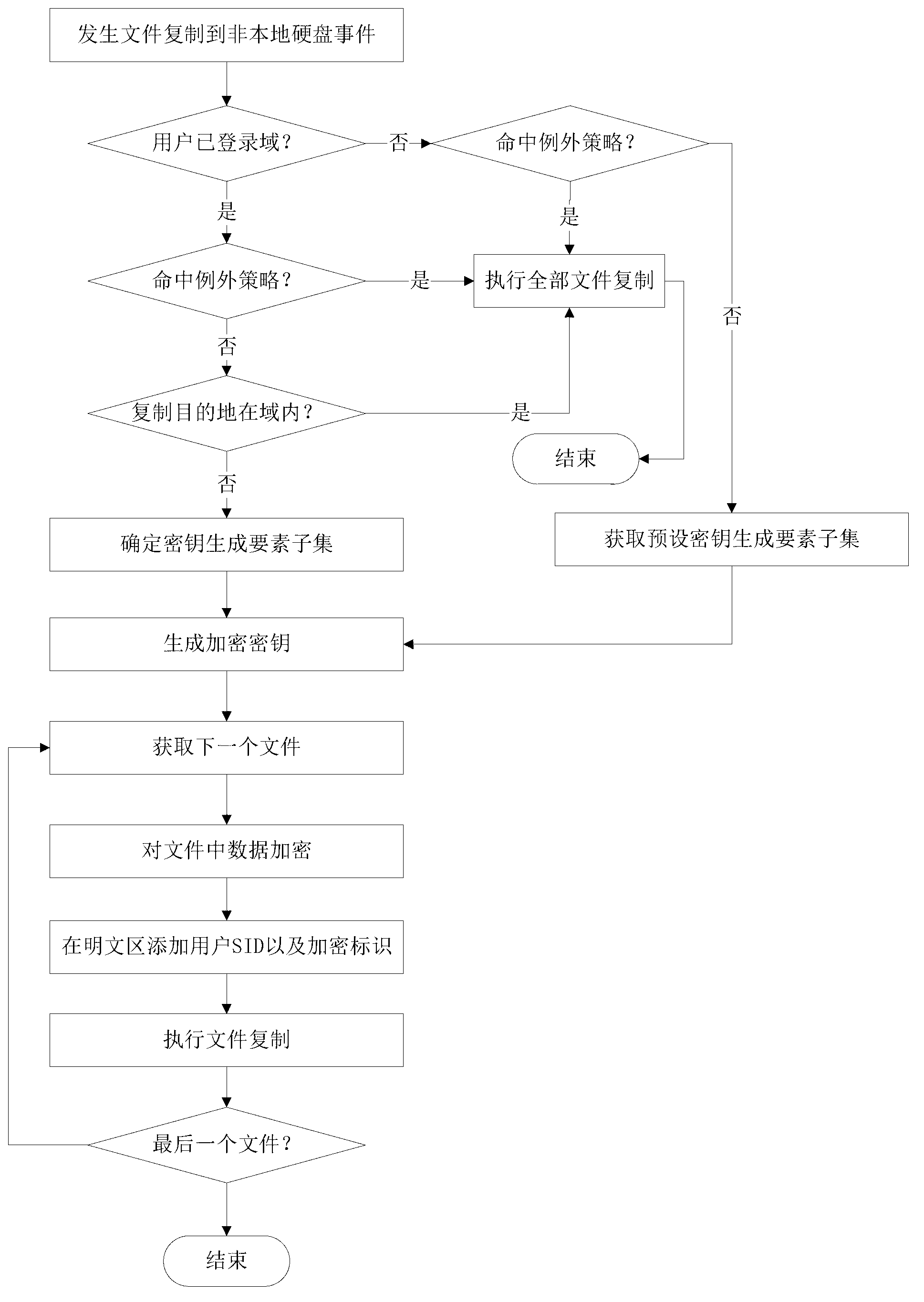
The invention provides a method for file safety control and a corresponding device. The method and device is mainly applied to a host computer. The method includes the steps that step A, when a logged-in domain user copies files in a local disk of the current host computer to the outside, corresponding encryption keys of the current files needing to be copied are obtained, and step B, the encryption keys are used for encrypting plaintext data in the current files to form ciphertext data, and encryption identifications corresponding to the encryption keys are stored in a plaintext region of the encrypted files. Compared with the prior art, the method and device improve efficiency of file interchange among users in the organization on the premise of guaranteeing file information safety.
Owner:NEW H3C TECH CO LTD
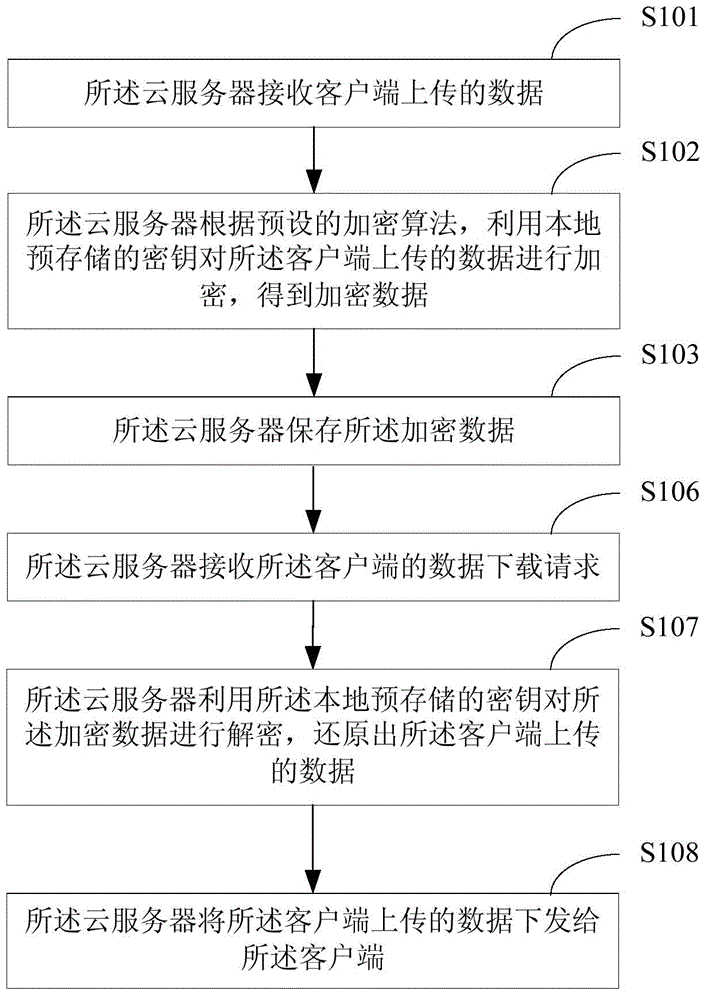
Method for protecting cloud storage data and cloud server
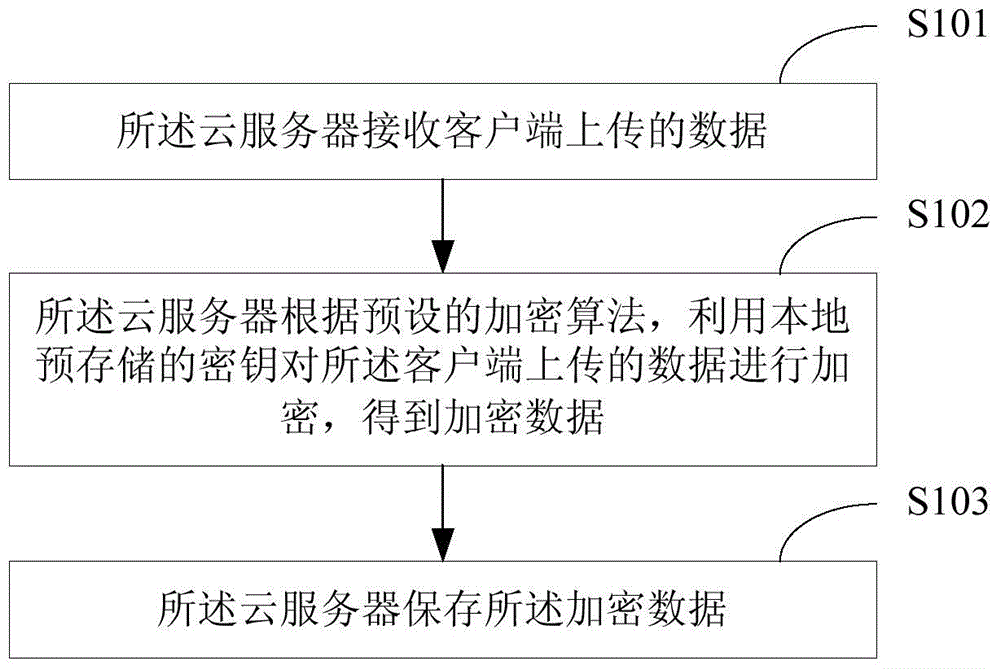
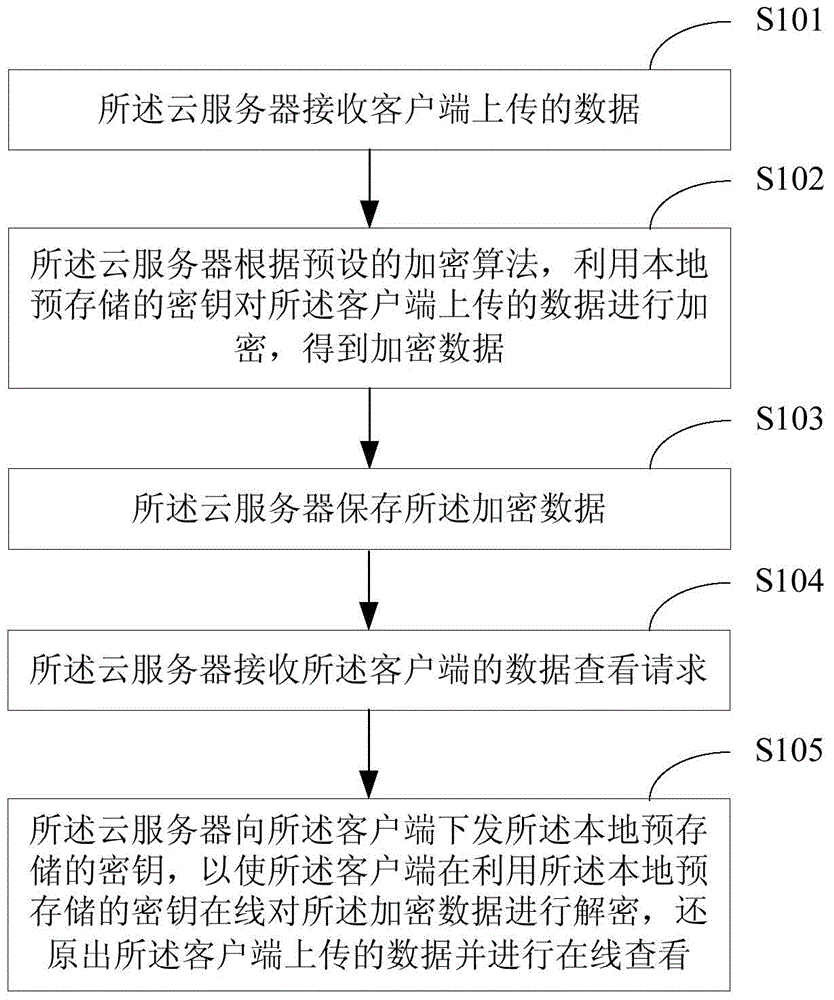
The invention relates to the technical field of information security and provides a method for protecting cloud storage data and a cloud server. The method comprises the steps that data uploaded by a client side are received by the cloud server; the data uploaded by the client side are encrypted by the cloud server through a locally-stored key according to a preset encryption algorithm, so that encrypted data are obtained; the encrypted data are stored by the cloud server. According to the method, in terms of the cloud storage data, the data are converted into a ciphertext from a plaintext by the cloud server and stored by the cloud server, so that even though the cloud storage data are leaked, the real data are difficult to obtain for a third party, the safety of the cloud storage data is guaranteed, and therefore the information safety of a cloud server user is guaranteed.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Multi-enterprise cloud folder deployment and information interaction method facing common client
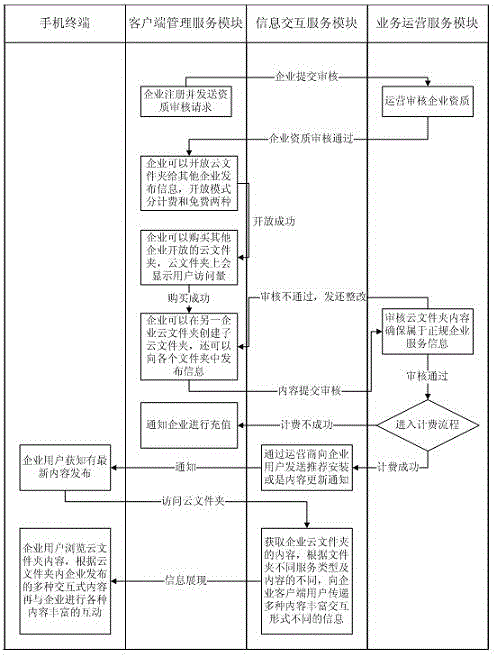
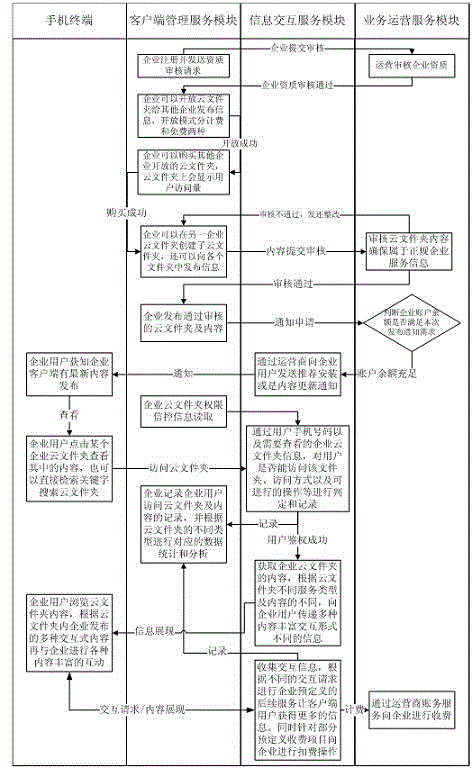
ActiveCN103152417ALower the thresholdAvoid the Burden of FeesData switching networksClient-sideData harvesting
The invention relates to a multi-enterprise cloud folder deployment and information interaction method facing a common client. The method specifically comprises the following steps: a plurality of enterprises deploy client content of the enterprises in a cloud folder manner; when the content is approved by verification, a service operation module carries out billing operation on the enterprises; when the billing is successful, a result is expressed in an enterprise user client to carry out information interaction between the enterprise user client and the enterprises; the enterprises can publish information and services in the same sharing cloud folder or one enterprise can publish own information and services in the cloud folder of the other enterprise under the precondition that one enterprise can obtain the allowance of the other enterprise; and the enterprise user can obtain the information and services of a plurality of enterprises at the same time. According to the multi-enterprise cloud folder deployment and information interaction method facing the common client disclosed by the invention, the convenient publishing and management of a plurality of enterprises on the same enterprise user client can be realized, and the efficiency of carrying out the information interaction on the enterprise user and the enterprises is improved; and the multi-enterprise cloud folder deployment and information interaction method is mainly used for fields of propaganda of the enterprises, data collection, membership service, depth and precision marketing, and establishment, duplication and management of a client relation and the like.
Owner:SHANGHAI FLAGINFO INFORMATION TECH
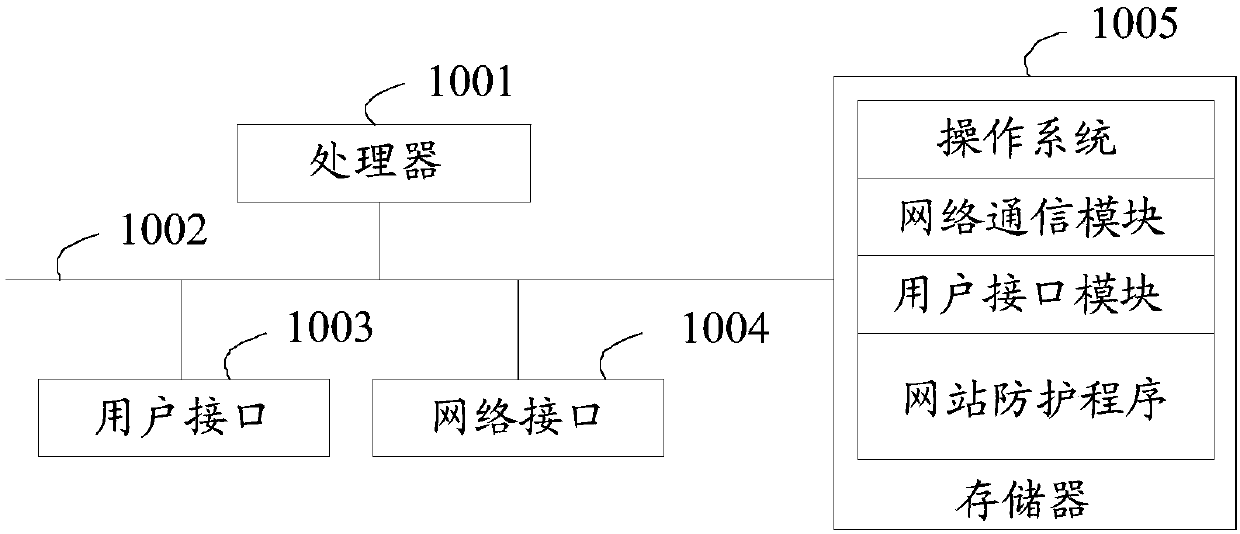
Website protection method, website protection device, website protection equipment and storage medium
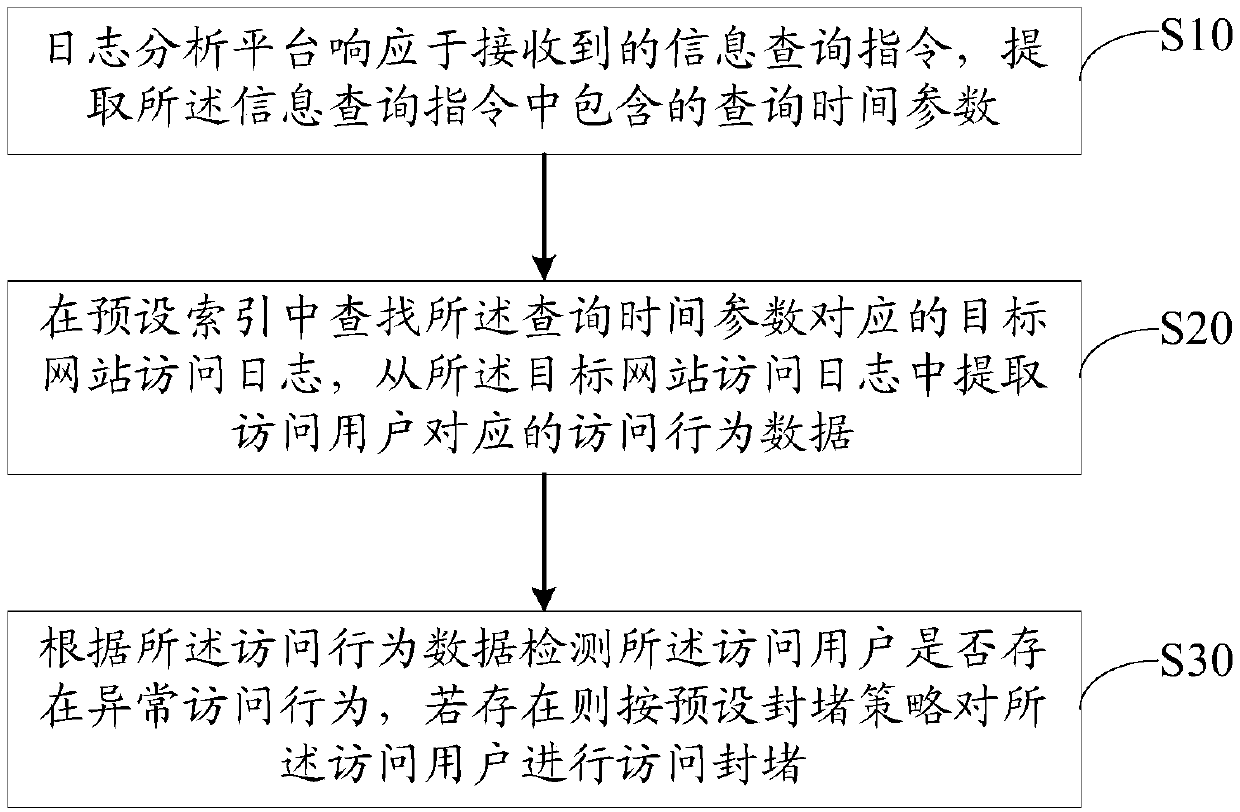
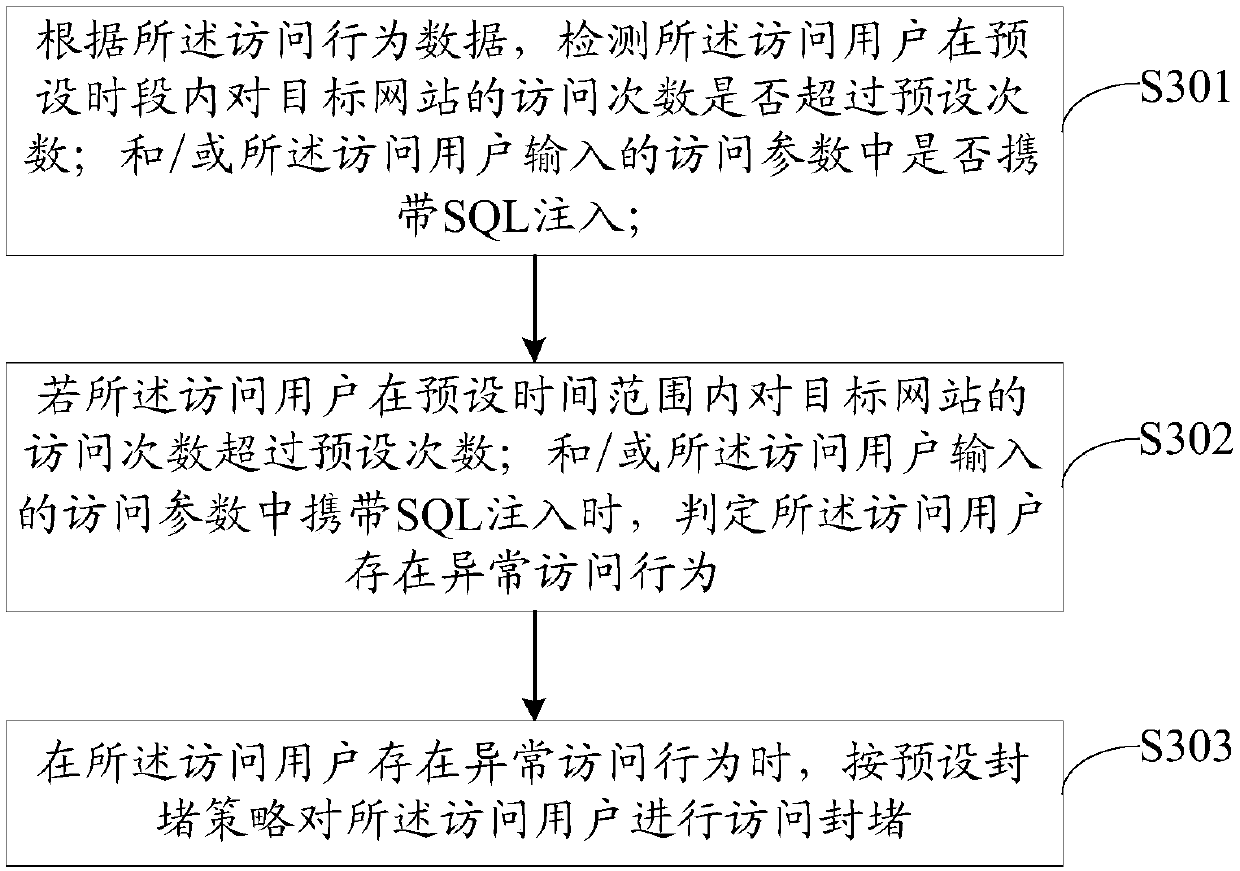
ActiveCN109688097AIncrease flexibilityImprove adaptabilityTransmissionInternet privacyInformation security
The invention discloses a website protection method, a website protection device, website protection equipment and a storage medium. The method comprises the following steps: responding to a receivedinformation query instruction by a log analysis platform, and extracting a query time parameter contained in the information query instruction; in preset indexes, looking for a target website access log corresponding to the query time parameter, and extracting access behavior data corresponding to an access user from the target website access log; and according to the access behavior data, detecting whether the access user has abnormal access behaviors, and if yes, performing access blocking on the access user according to a preset blocking strategy. The log analysis platform judges whether auser access is an abnormal access or not according to the access behavior data of the user, so that the situations that a normal access request is mistakenly reported as access rules or firewall strategies are made and an abnormal access request is fail to report are avoided, website protection flexibility and anti-intrusion capability are improved, and information security of a website as well asstructural safety are guaranteed.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method and terminal for checking screen lock notification information
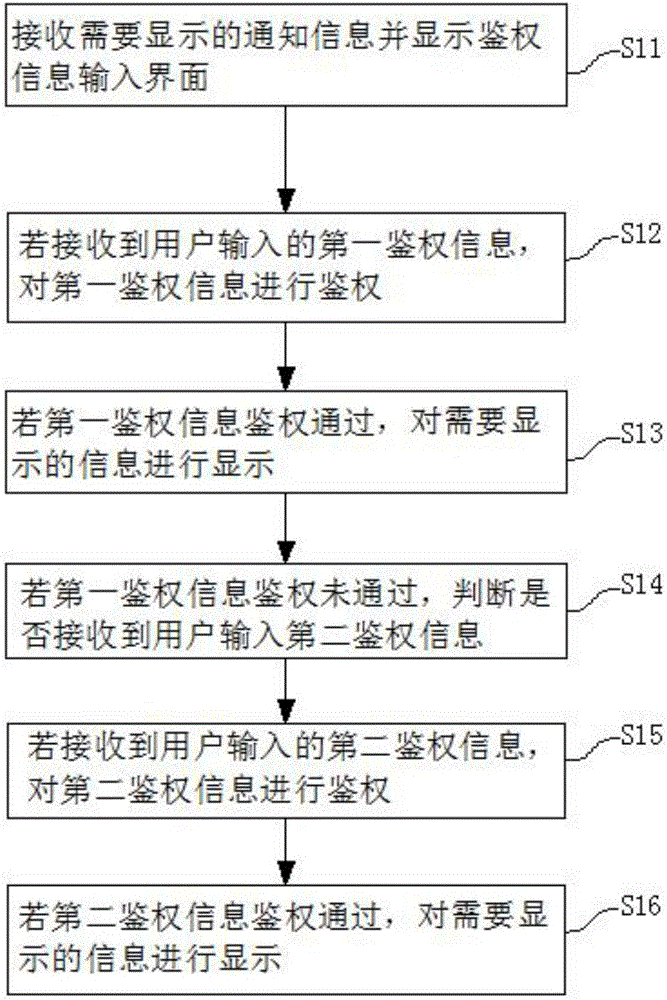
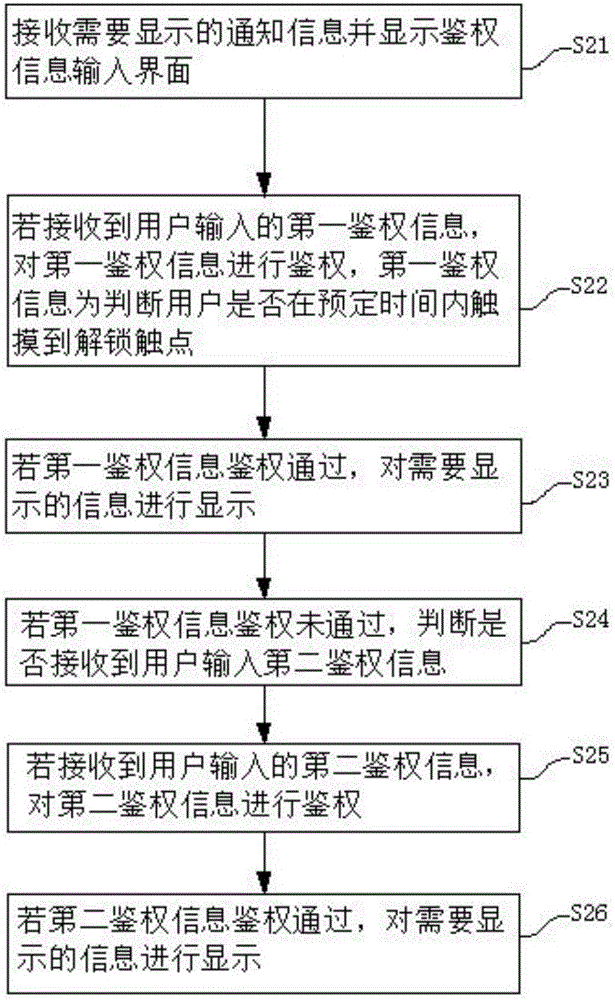
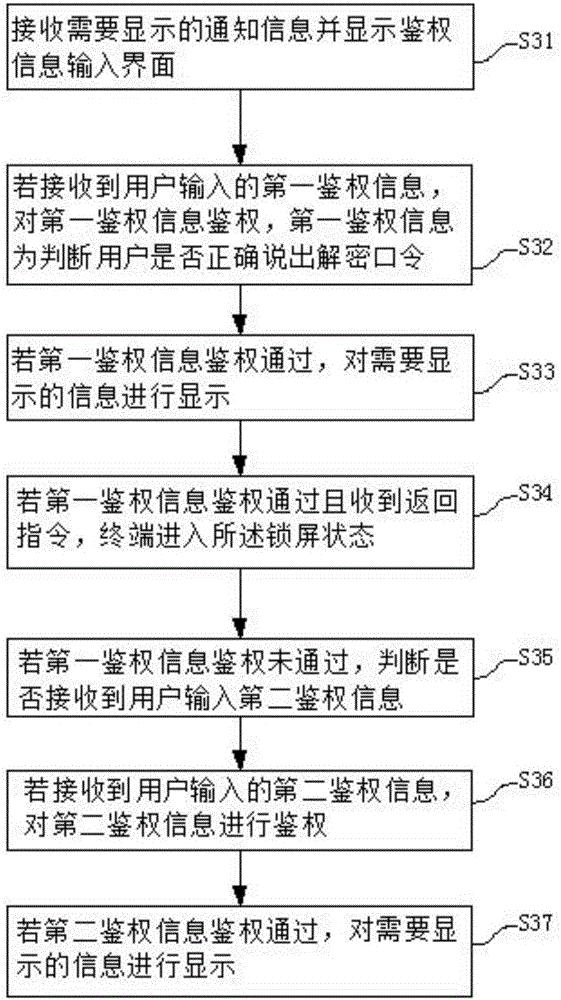
InactiveCN106446631AGuarantee information securityEasy to viewDigital data authenticationComputer hardwareAuthentication information
The embodiment of the invention provides a method and terminal for checking screen lock notification information. The method comprises the steps that the notification information needing to be displayed is received, and an authentication information input interface is displayed; first authentication information input by a user is obtained and authenticated; if the first authentication information passes the authentication, the information needing to be displayed can be displayed; if the first authentication information does not pass the authentication, whether second authentication information is received is judged; if the second authentication information is received, authentication will be conducted; and when the information passes the authentication, the information can be displayed. The method and terminal for checking the screen lock notification information provided by the embodiment of the invention are characterized in that graded identity judgment is conducted to the user; if the user passes judgment of a first authentication information verification mechanism, the information can be displayed; and if the first authentication information does not pass the judgment, a second authentication information verification mechanism will be started, and the information can be displayed only when the information passes second authentication information verification. In this way, the user can guarantee safety of the information in the terminal; and the user can more easily and conveniently check the current screen lock notification information.
Owner:SHENZHEN GIONEE COMM EQUIP
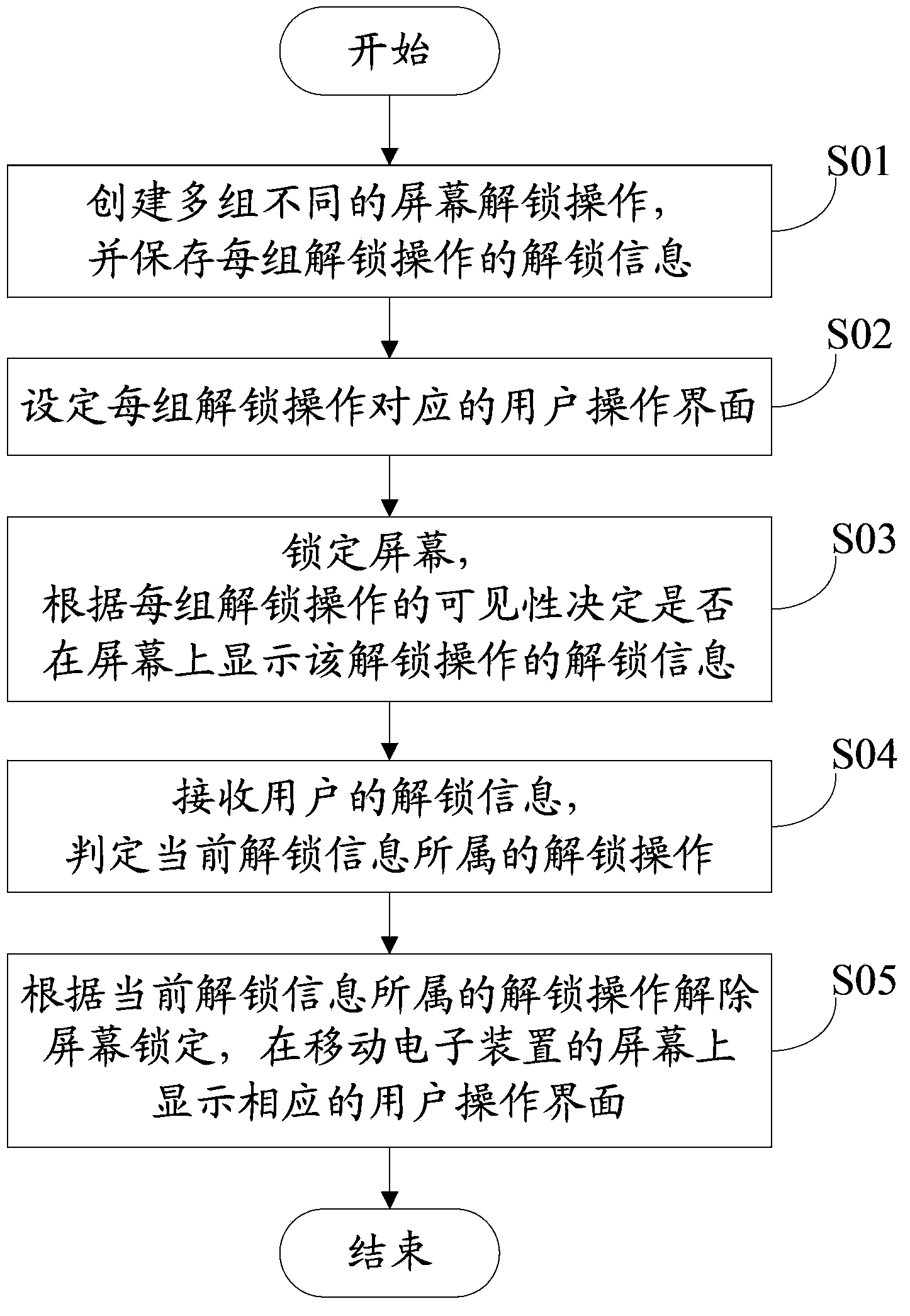
Multiple-screen unlocking system and method
The invention provides a multiple-screen unlocking method. The method comprises the following steps of a creating step, namely, creating a plurality of groups of different unlocking operations, and storing the unlocking information of each group of unlocking operation into a memory; a setting step, namely, setting a user operation interface corresponding to each group of unlocking operation; a locking step, namely, locking a screen, and determining if the unlocking information of the unlocking operations is displayed on the screen or not according to the visibility of each group of unlocking operation; a judging step, namely, receiving the unlocking information of the user, and judging the unlocking operation of the current unlocking information; an unlocking step, namely, according to the unlocking operation of the current unlocking information, unlocking the screen, and displaying the corresponding user operation interface on the screen of a mobile electronic device. The invention further provides a multiple-screen unlocking system.
Owner:SHENZHEN FUTAIHONG PRECISION IND CO LTD
System and method for preventing unauthorized use of IC card
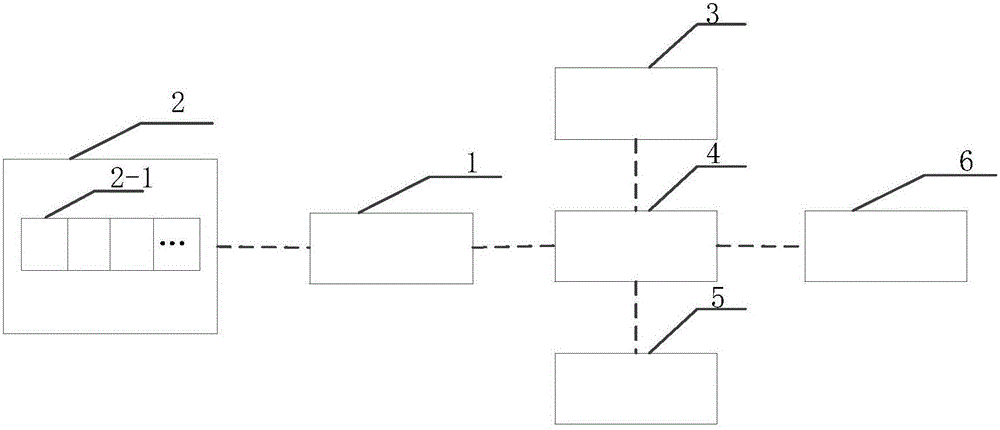
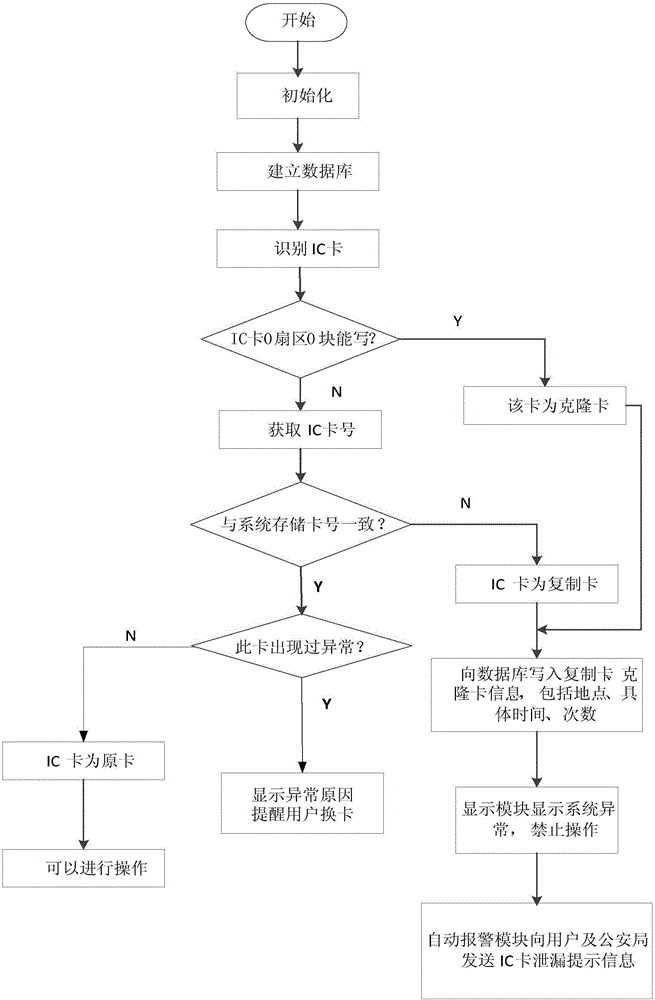
ActiveCN106022181AEasy to investigateReduce the risk of useTesting sensing arrangementsInternal/peripheral component protectionConfidentialityCard reader
The invention discloses a system for preventing unauthorized use of an IC card. The system comprises an IC card reader-writer, a microprocessor, a testing UID card, a power supply module, a display module, and an automatic alarming device. The device is capable of preventing the unauthorized use of the IC card mainly by determining whether the data writing-in state of the 0 block data of the 0 sector of the IC card, the number of the IC card, and information stored in the IC card are consistent with related information of a system database. The UID card is tested to determined whether the working of the system is normal. When the working of the system is normal, user IC card operation is carried out. When the IC card is not the original card, the system is capable of forbidding the writing and reading operation of the card, and is used to transmit IC card leakage prompting information to a cell phone of a user and a public security organ by short messages. The principle and the operation of the device for preventing the unauthorized use of the IC card are simple and clear, and therefore whether the IC card information is leaked can be determined accurately, and the safety and the confidentiality of the IC card are greatly improved.
Owner:SHAANXI UNIV OF SCI & TECH
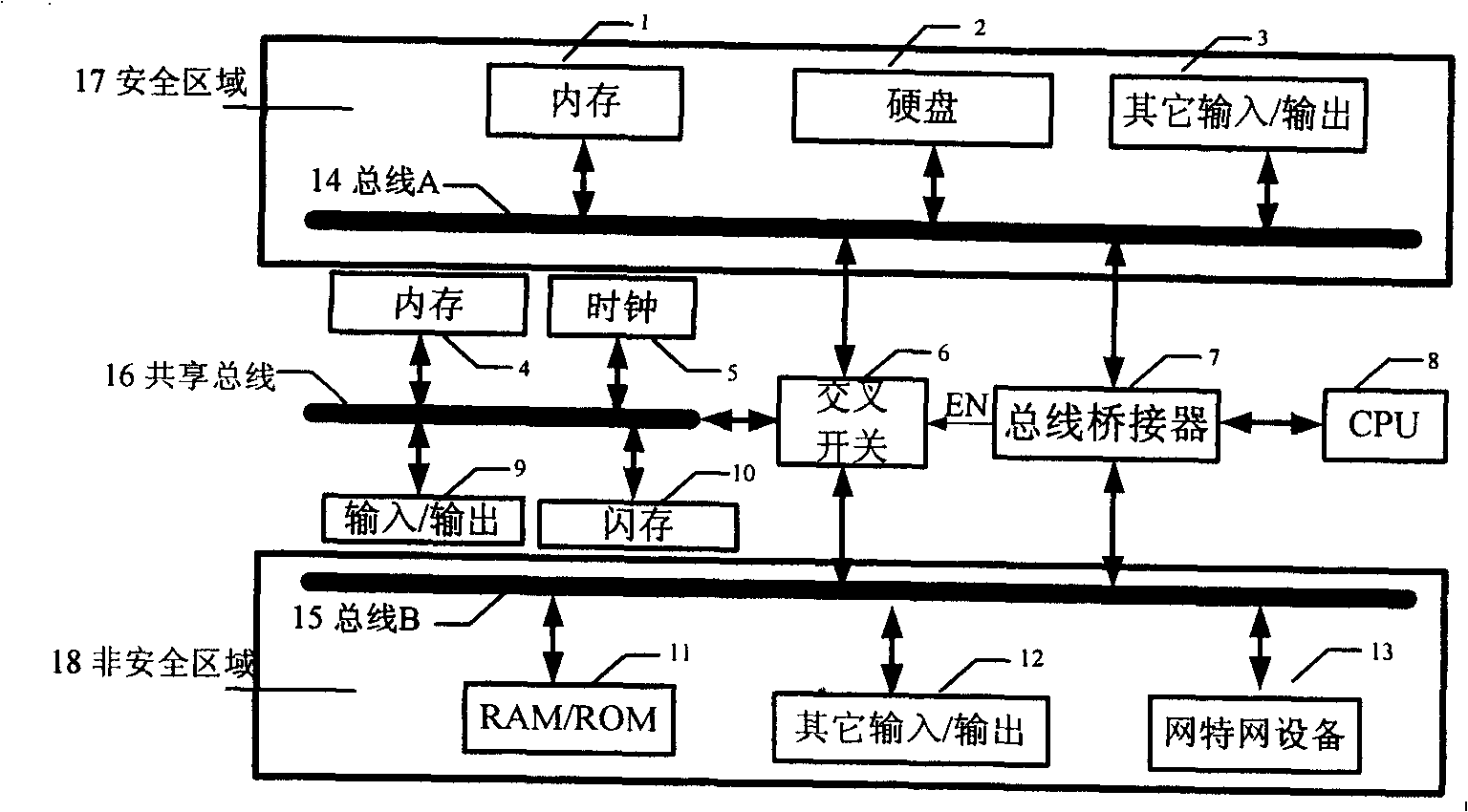
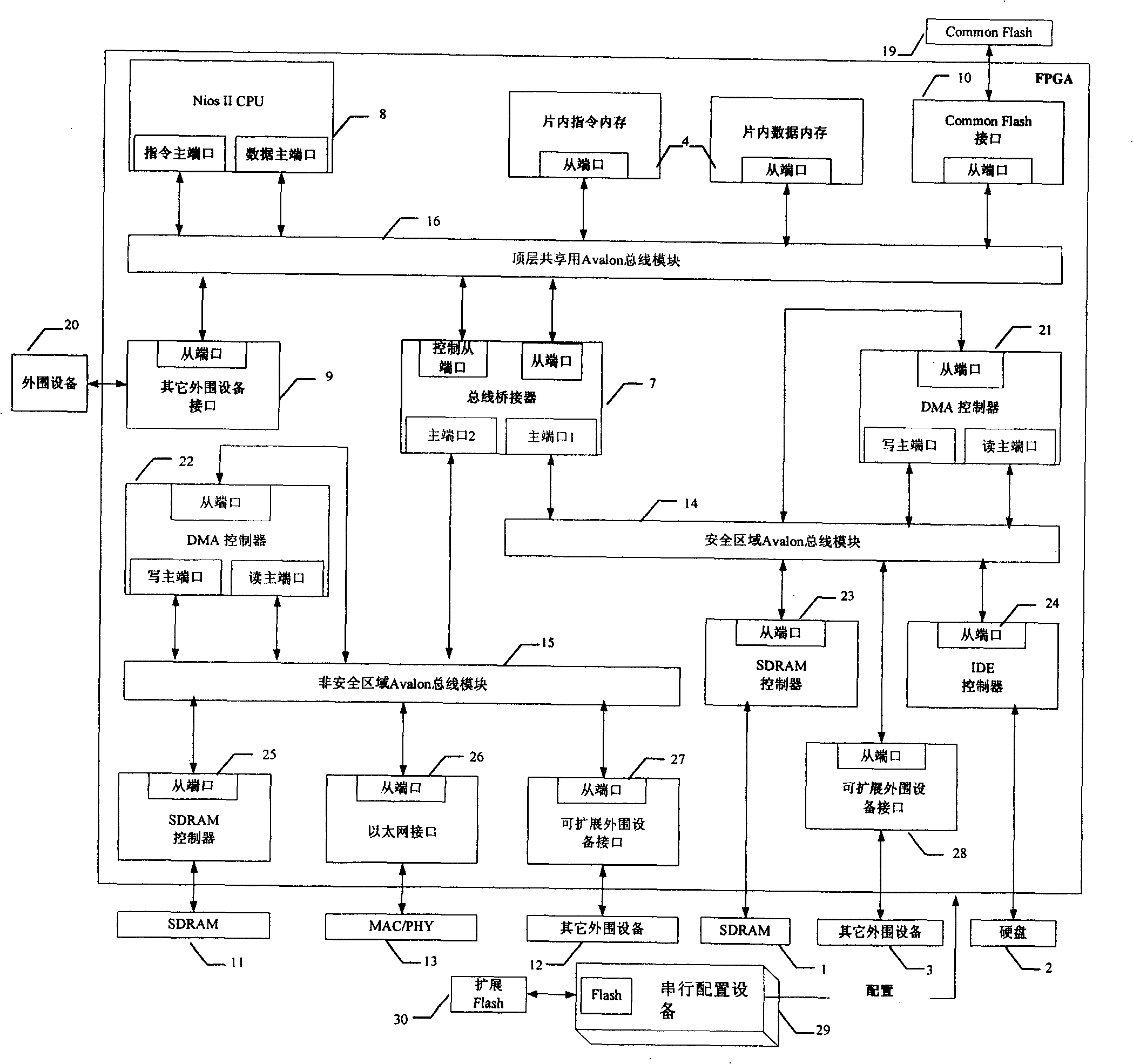
Safe network terminal based on single CPU dual bus
InactiveCN101299228APrevent network intrusionGuarantee information securityPlatform integrity maintainanceTransmissionEmbedded systemInternet communication
The invention relates to a novel safe network terminal based on single CPU double-bus. The novel safe network terminal provides resistance function to the known or unknown network instruction by physical insulation and access control, adopts a single CPU and a safe area system bus and a non-safe area system bus isolated physically, the bus bridge controls the dynamic connection of the CPU and the system bus, and realizes the physical insulation of the two system buses; the related internet communication apparatus is only connected to one bus, while the related safe data memory apparatus is connected to the other system bus; one sharing bus is used to share the bus communication between the keyboard, mouse and the other input / output equipment, and the inside and outside system. The invention can effectively prevent the network instruction, guarantee information safety, and have advantages of low cost, strong spreading functional, safety and reliability, and the like.
Owner:QINGDAO UNIV
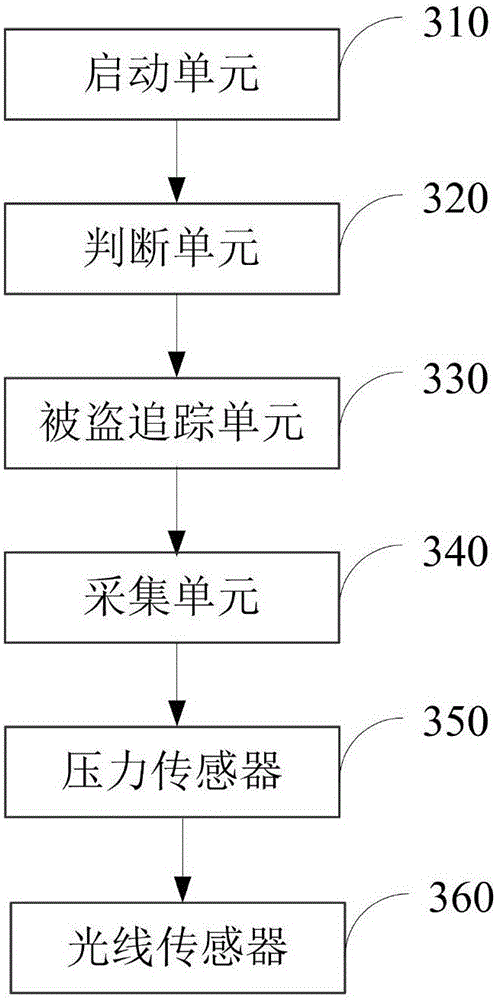
Mobile terminal theft prevention method and device
InactiveCN105118201AProtect property and information securityImprove user experienceBurglar alarmAlarm signalComputer science
The invention discloses a mobile terminal theft prevention method and a device, which belongs to the technical field of communication. The device comprises a starting unit, a judging unit and a stolen tracking unit, wherein the starting unit is used for starting the theft prevention mode of the mobile terminal; the judging unit is used for judging whether an illegal user operates on the mobile terminal; the stolen tracking unit is used for enabling the mobile terminal to enter a stolen mode and sending an alarming signal when an illegal user operates on the mobile terminal. Thus, operation on the mobile terminal by an illegal user can be found out at the first time, property security and information security of the user can be ensured forcefully, and user experience can be improved greatly.
Owner:NUBIA TECHNOLOGY CO LTD
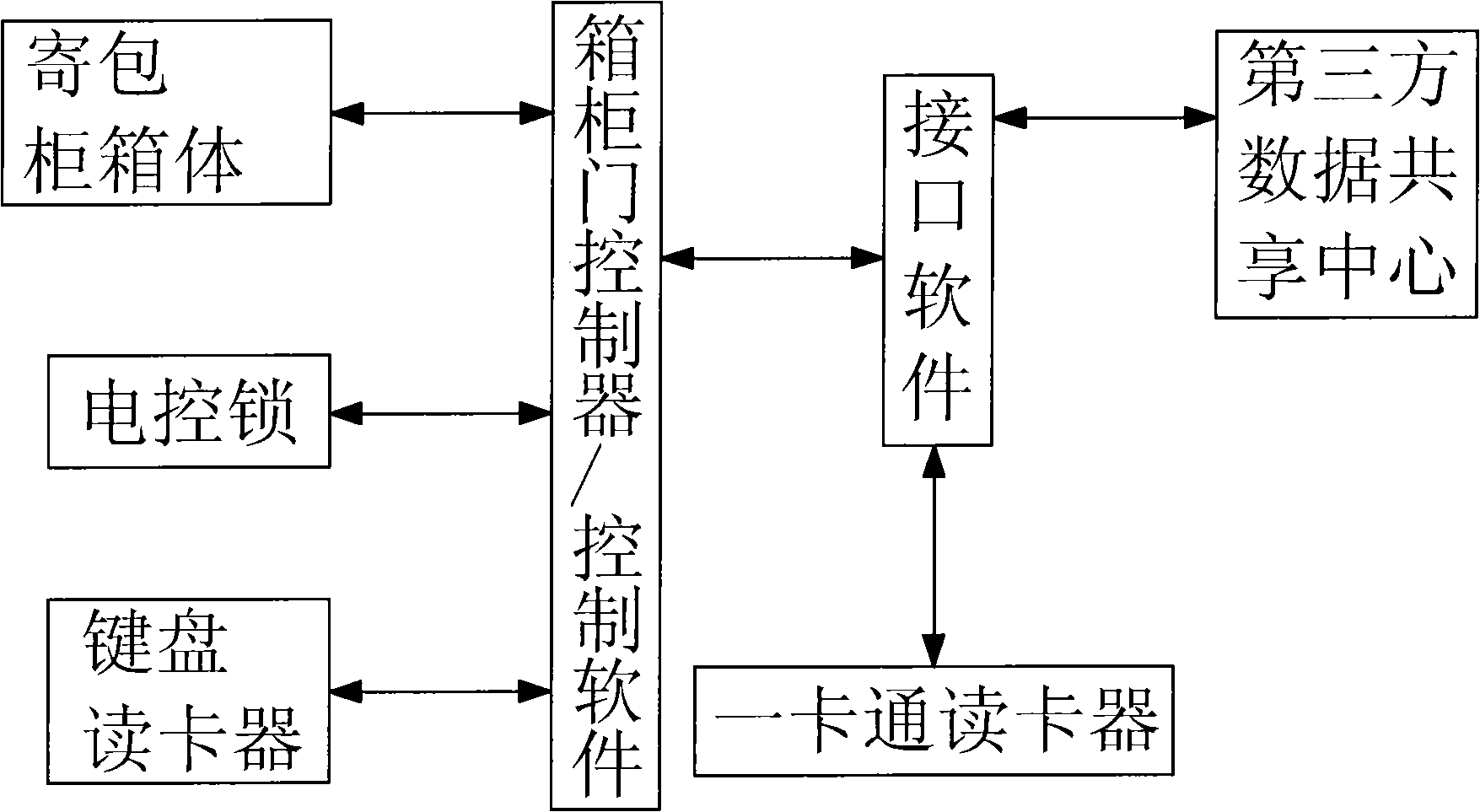
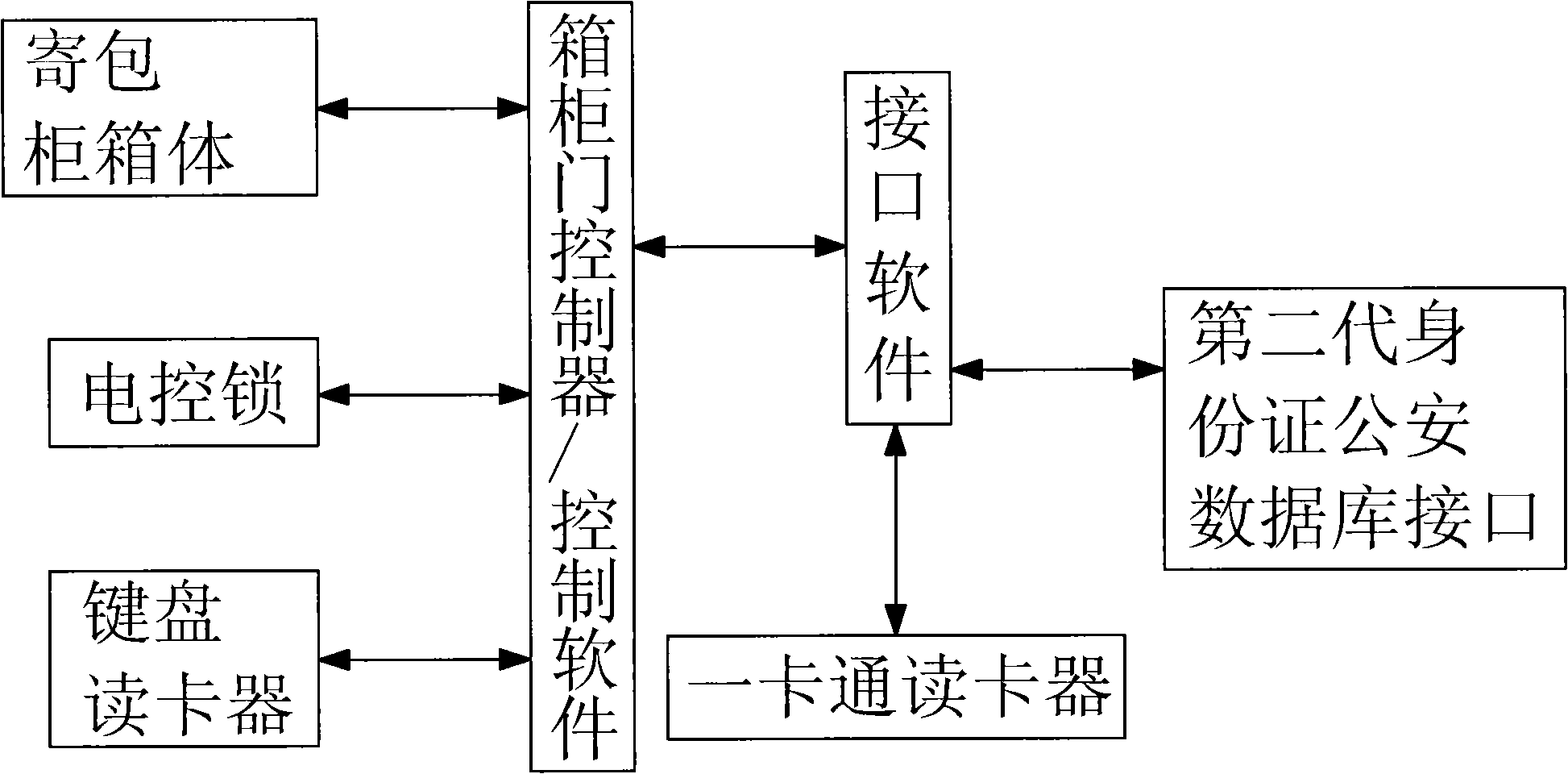
Bag cabinet control method and system based on data sharing center
InactiveCN101339683AGuarantee information securityEasy to carryApparatus for meter-controlled dispensingThird partyCard reader
The invention discloses a storage cabinet control method based on a data sharing center; the method is characterized in that a third-party data sharing center and an interface software are provided; an all-in-one card reader carries out a card authentication, reads the all-in-one card information and sends the corresponding request information to the interface software; the request information comprises an unlocking request message, a position message and user information obtained from the all-in-one card; the interface software put forward an identity verification request to the third-party data sharing center and checks whether the read card has the unlocking authority according to the request information; the third-party data sharing center feeds back the verification information to the interface software; if the verification information proves that the card has the unlocking authority, the interface software sends the unlocking information to the storage cabinet system and a controller drives the unlocking. For the storage cabinet control method, the data sharing center is established by a user party, the all-in-one card reader, the storage cabinet system and the data sharing center are connected by the interface software, thus leading the storage cabinet system to be more conveniently and the safety of the storage cabinet system is greatly improved.
Owner:SUZHOU INST OF TRADE & COMMERCE
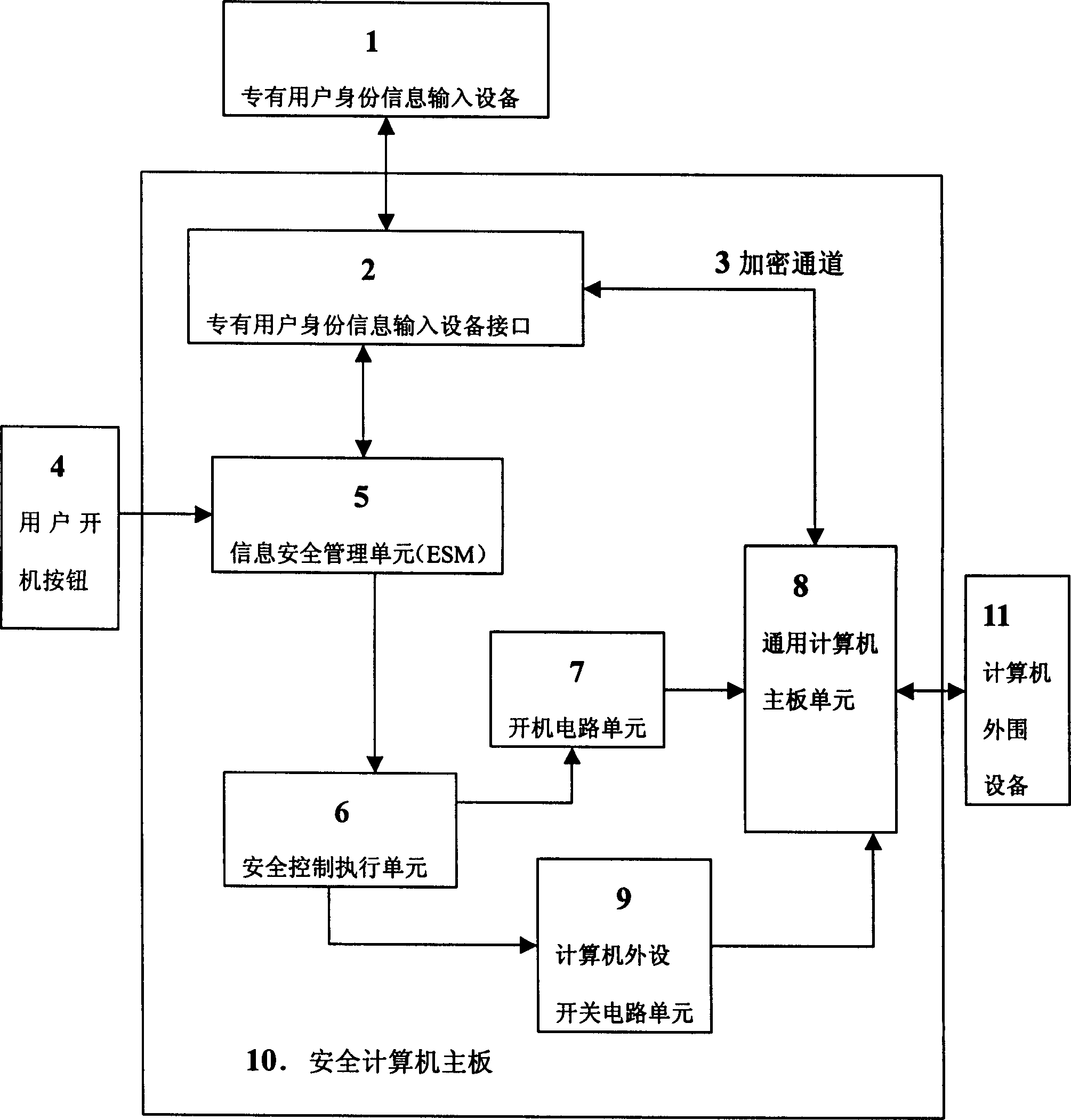
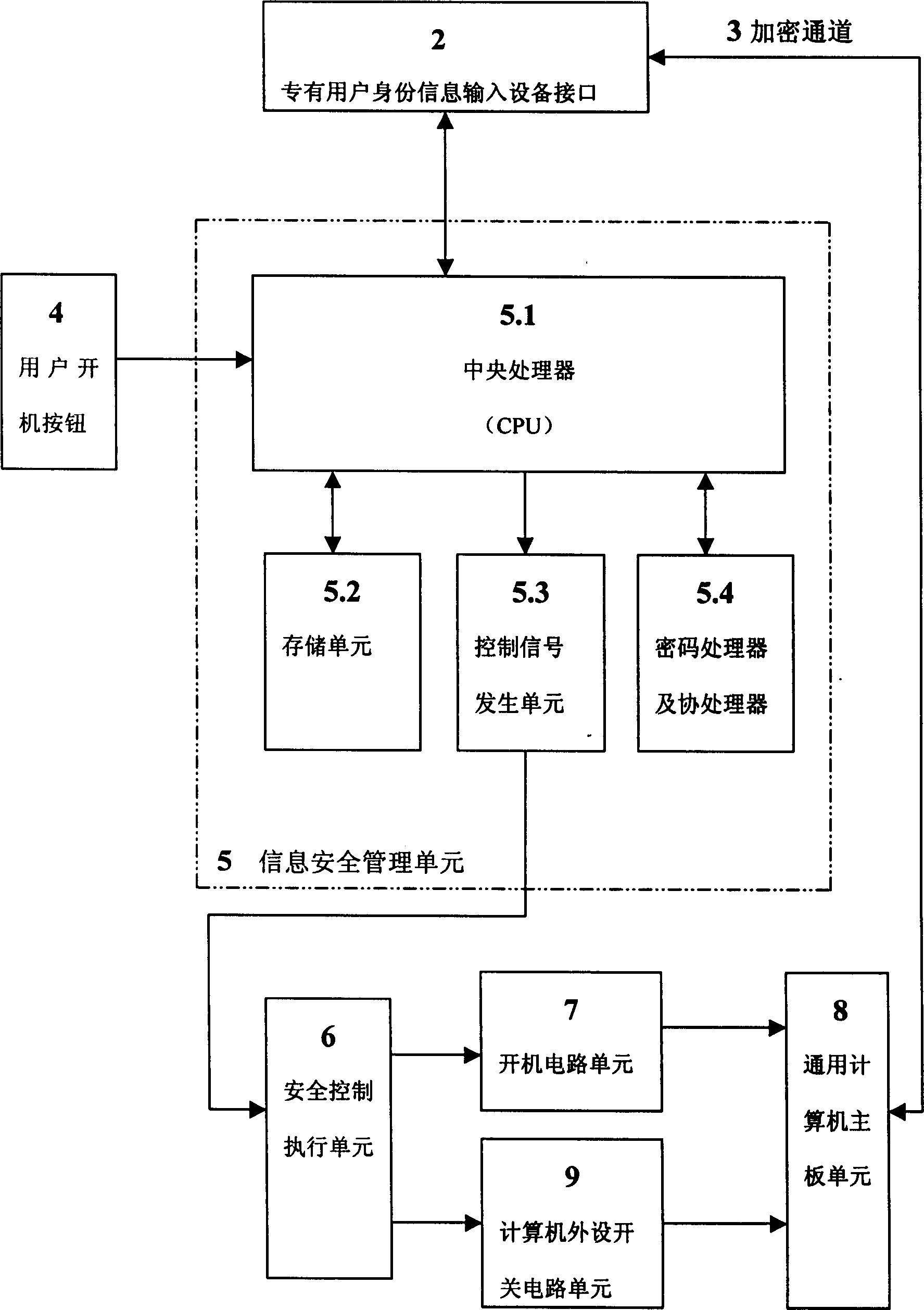
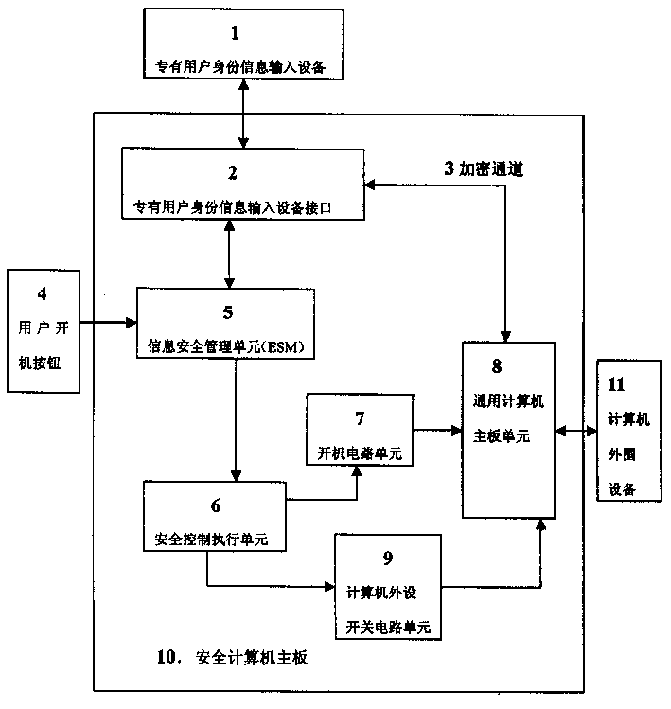
Safety computer with information safety management unit
InactiveCN1423203ASolving Information Security IssuesGuarantee information securityMemory loss protectionUnauthorized memory use protectionManagement unitInformation security
The safety computer comprises the device interface for inputting the identification information, the information safety management unit, the safety control execution element, the starting up circuit unit, the circuit unit for switching computer peripherals and the computer main board unit. The safety management unit in the safety computer can be prepared as the element of the safety module. The invention possesses the advantages of providing the functions of the self-checking and the validation. The management information is controlled from the botton layer of the hardware so as to solve the improve the issue of the safety and the protection of the computer information.
Owner:瑞达信息安全产业股份有限公司
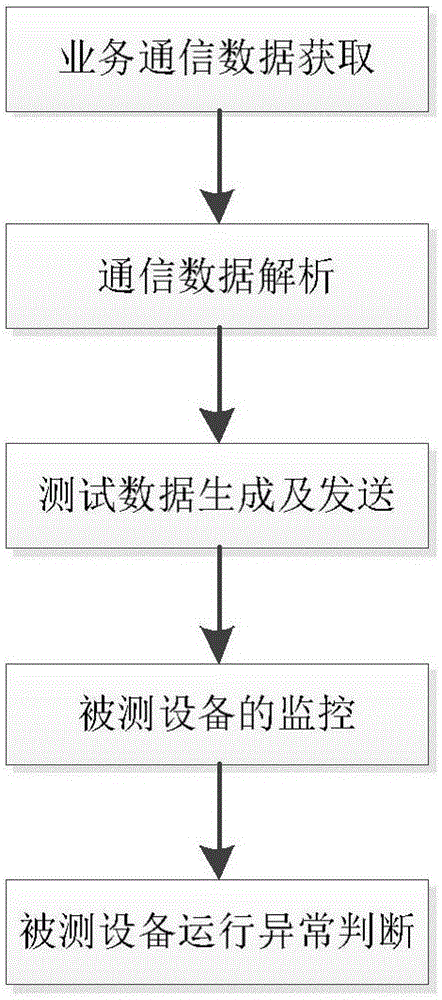
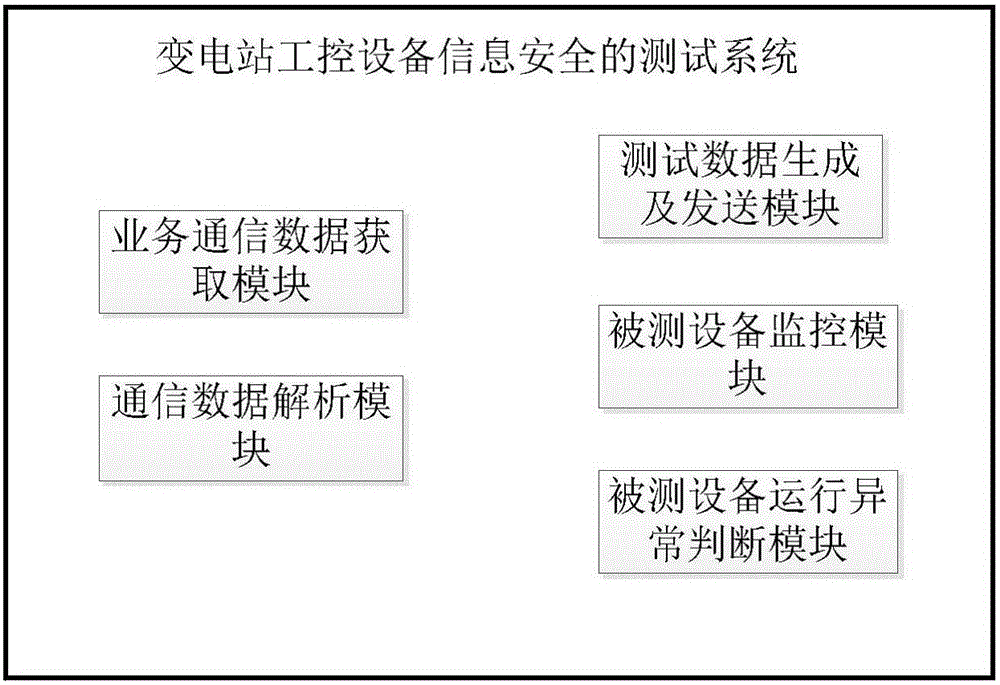
Test method and system for information security of transformer substation industrial control equipment
ActiveCN105827613AGuarantee information securityReduce Information Security RisksPlatform integrity maintainanceData switching networksTest data generationData analysis
The invention relates to a test method for information security of transformer substation industrial control equipment. The test method includes the steps of: 1. service communication data acquisition; 2. service communication data analysis; 3. test data generation and sending; 4. tested equipment monitoring; and 5.tested equipment operation abnormality judgment. The invention also relates to a system specialized for the abovementioned method. The system includes the following modules connected in sequence: a service communication data acquisition module, a communication data analysis module, a test data generation and sending module, a tested equipment monitoring module and a tested equipment operation abnormality judgment module. By adoption of the system and method provided by the invention, information security vulnerabilities of transformer substation embedded equipment can be effectively mined, system operation and maintenance are assisted and the current information security status of transformer substation industrial control equipment is grasped, information security loopholes of the system are repaired in advance, information security f an industrial control system is guaranteed, and information security risks of national infrastructures are reduced.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
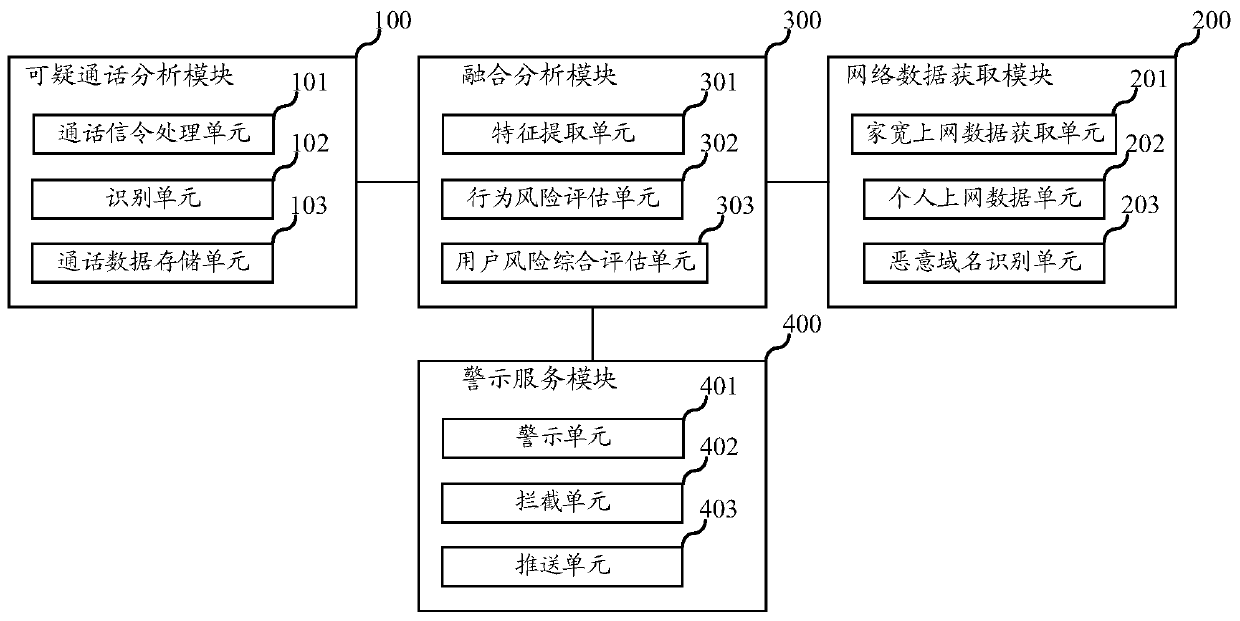
Anti-fraud system and method, server and storage medium
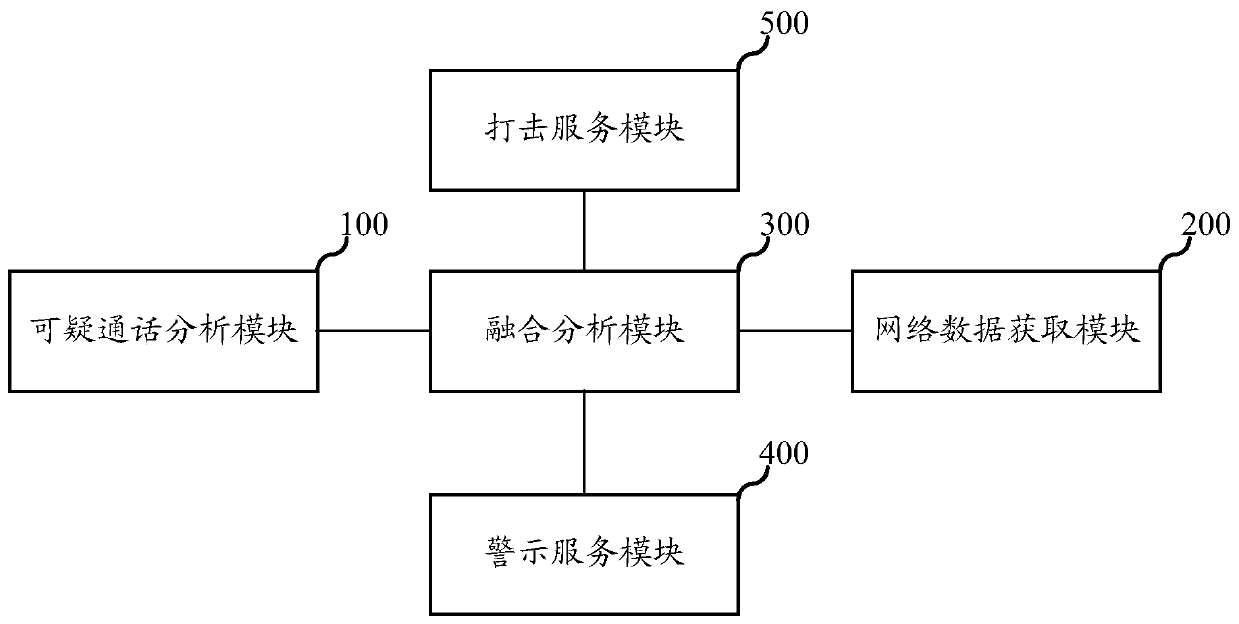
PendingCN111278014AReduce the risk of miscalculationGuarantee information securityTransmissionSecurity arrangementComputer securityEngineering
The embodiment of the invention relates to the technical field of communication, and discloses an anti-fraud system and method, a server and a storage medium, and the anti-fraud system comprises a suspicious call analysis module, a network data obtaining module, a fusion analysis module and a warning service module. The suspicious call analysis module is used for identifying the call signaling corresponding to the personal account according to a first preset model and recording suspicious call data; the network data acquisition module is used for discriminating the personal internet surfing data according to a second preset model and acquiring network data for accessing a malicious website; the fusion analysis module is used for performing fraud identification on the suspicious call data and the network data according to a third preset model; and the warning service module is used for intercepting and sending out early warning after judging that the personal account is suspected to becheated. By aggregating the call data and the internet surfing data, the fraud event is more accurately and comprehensively recognized, comprehensive reminding and interception are achieved, and the fraud event prevention and control capacity of family users is effectively improved.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
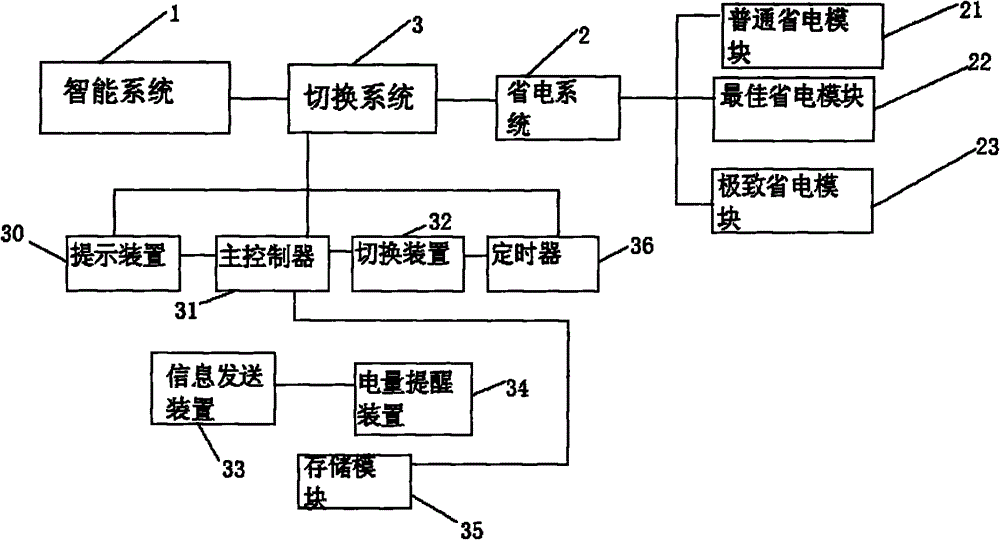
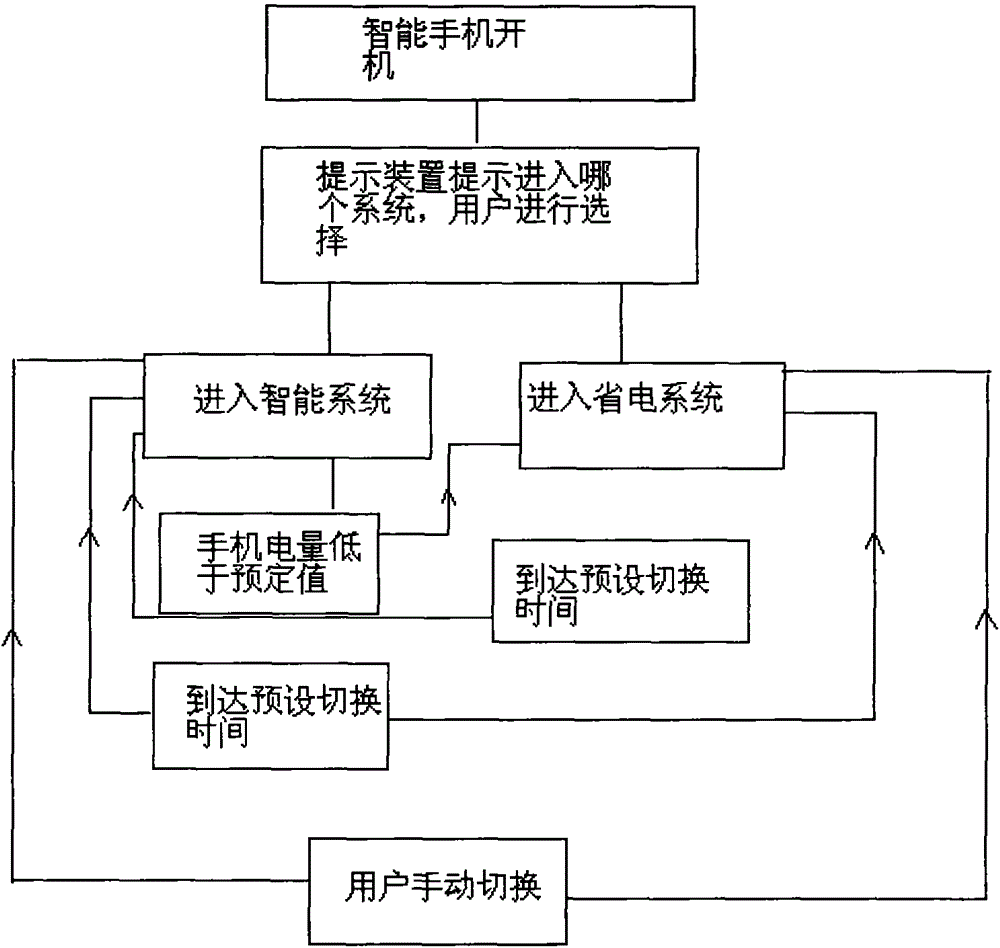
Smart phone provided with smart system and power saving system, and switching method
InactiveCN104158950AMeet needsMeet the needs of useCurrent supply arrangementsSubstation equipmentComputer moduleInformation security
Disclosed is a smart phone provided with a smart system and a power saving system. The smart phone comprises a smart system and a power saving system which are disposed in a memory of a smart phone. The power supply system is provided with a general power module, an optimal power saving module and an extreme power saving module, and a user can choose any one mode. Switching buttons are disposed on main interfaces of the smart system and the power saving system. The smart phone further comprises a switching system. The switching system comprises a prompt device, a main controller, a switching device, an information transmitting device and a power amount reminding device. The invention is advantageous in that an extreme power saving dual system can be quickly switched to meet the needs of different users; the power saving system has the characteristics of large icon, large font and contact shortcut, the use for middle-aged and senior people is satisfied, meanwhile the system setting items such as networking are closed, and information security of users is ensured; and two power saving modes of the power saving system are automatically timed to open flexibly at each time period, requirements for daily power saving and nighttime power saving of users are met, smart power saving for users is facilitated, and the effective amount of power saving is up to 40-50%.
Owner:CHONGQING GUOHONG TECH DEV
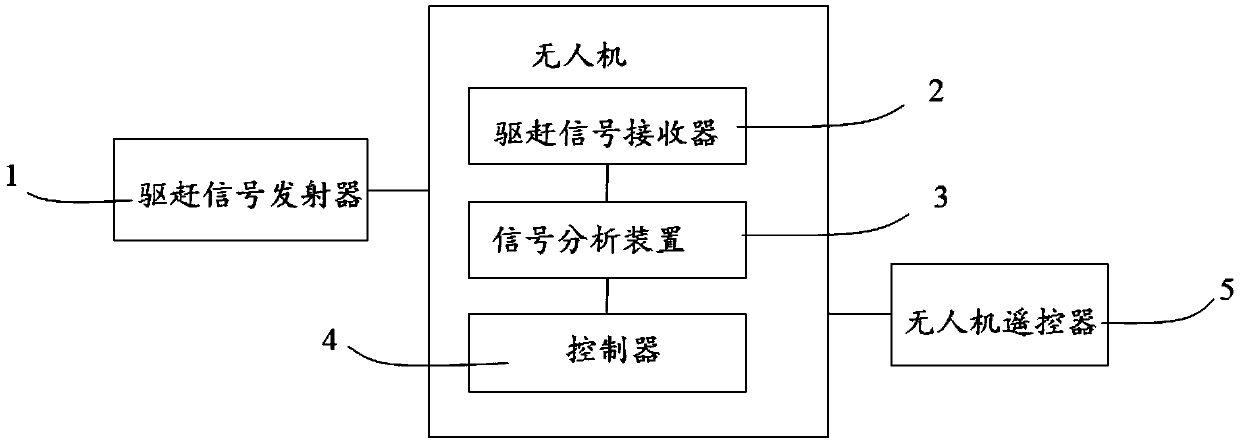
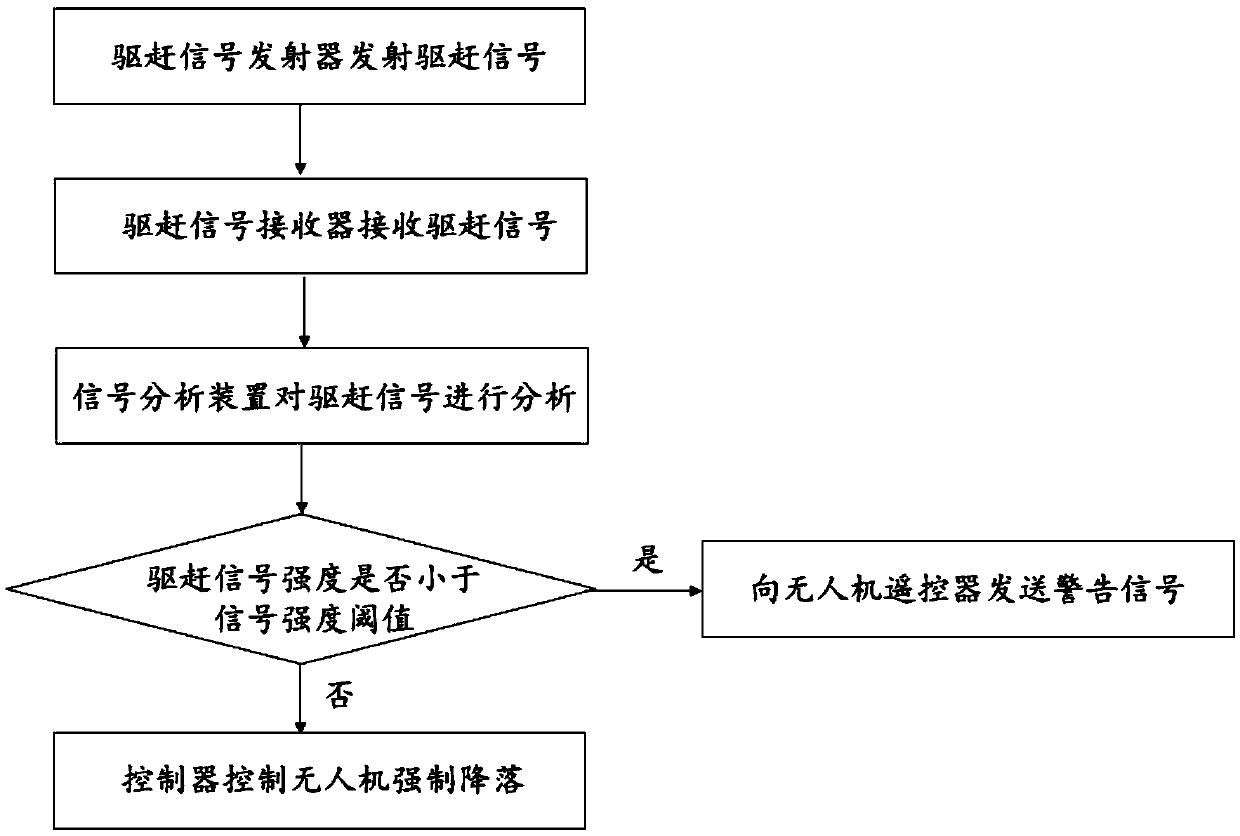
Unmanned aerial vehicle driving device and method
ActiveCN105511491AReduce the rate of false entryGuarantee information securityPosition/course control in three dimensionsRemote controlEngineering
The invention discloses an unmanned aerial vehicle (UAV) driving device comprising a driving signal emitter, a driving signal receiver, a signal analysis device and a controller. The driving signal emitter is arranged on the ground, and the signal analysis device, the controller and the driving signal receiver are mounted on a UAV. The driving signal emitter emits a driving signal, the driving signal receiver receives the driving signal and sends the driving signal to the signal analysis device, and the signal analysis device analyzes the driving signal. When the strength of the driving signal is smaller than a preset signal strength threshold, the UAV sends a warning signal to a UAV remote control; and when the strength of the driving signal is greater than or equal to the preset signal strength threshold, the controller forces the UAV to land. Accordingly, the invention provides a UAV driving method. The intrusion rate is reduced, and the information security in the control area is ensured.
Owner:南京石知韵智能科技有限公司
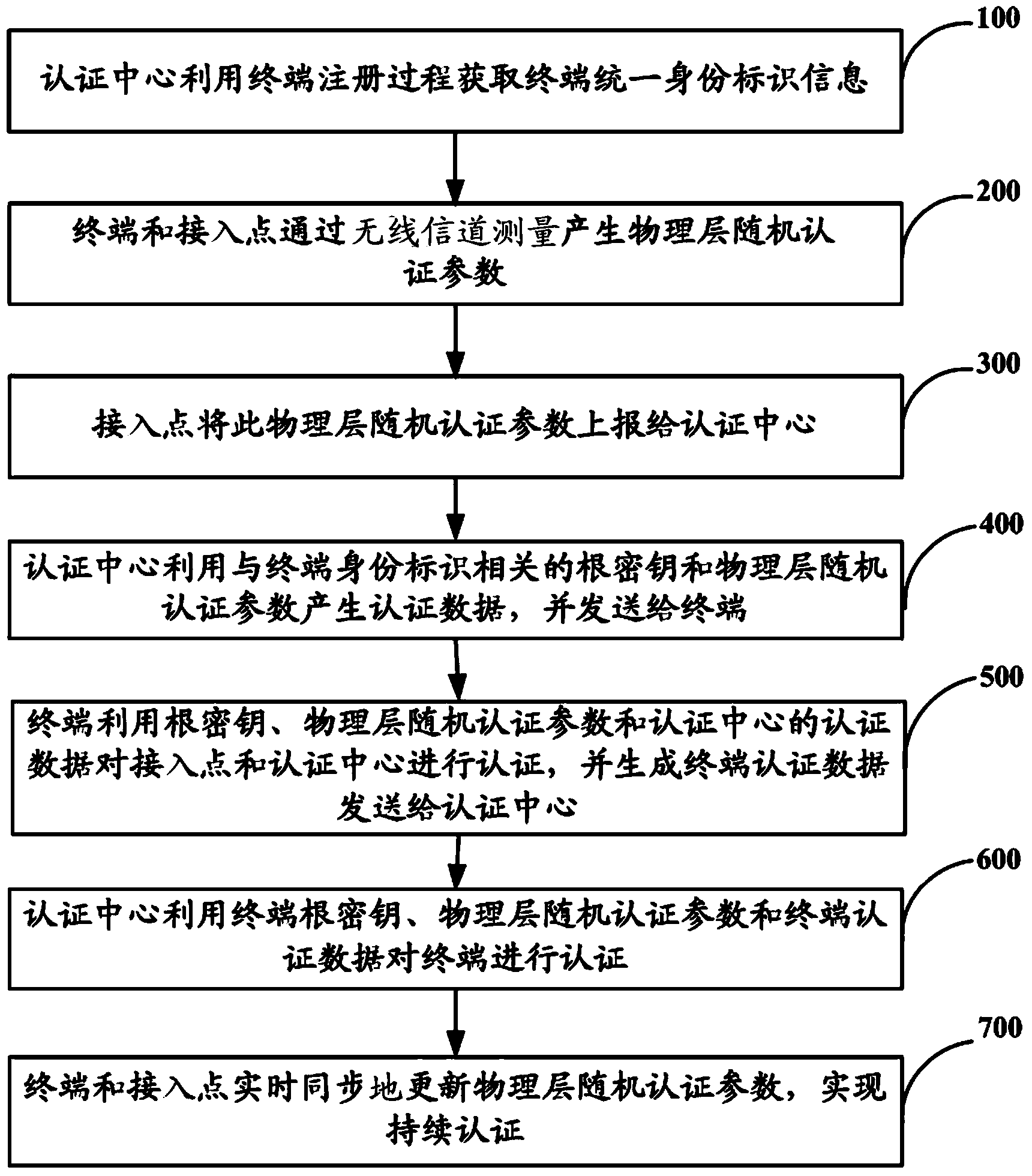
Heterogeneous network unified authentication method based on physical layer safety
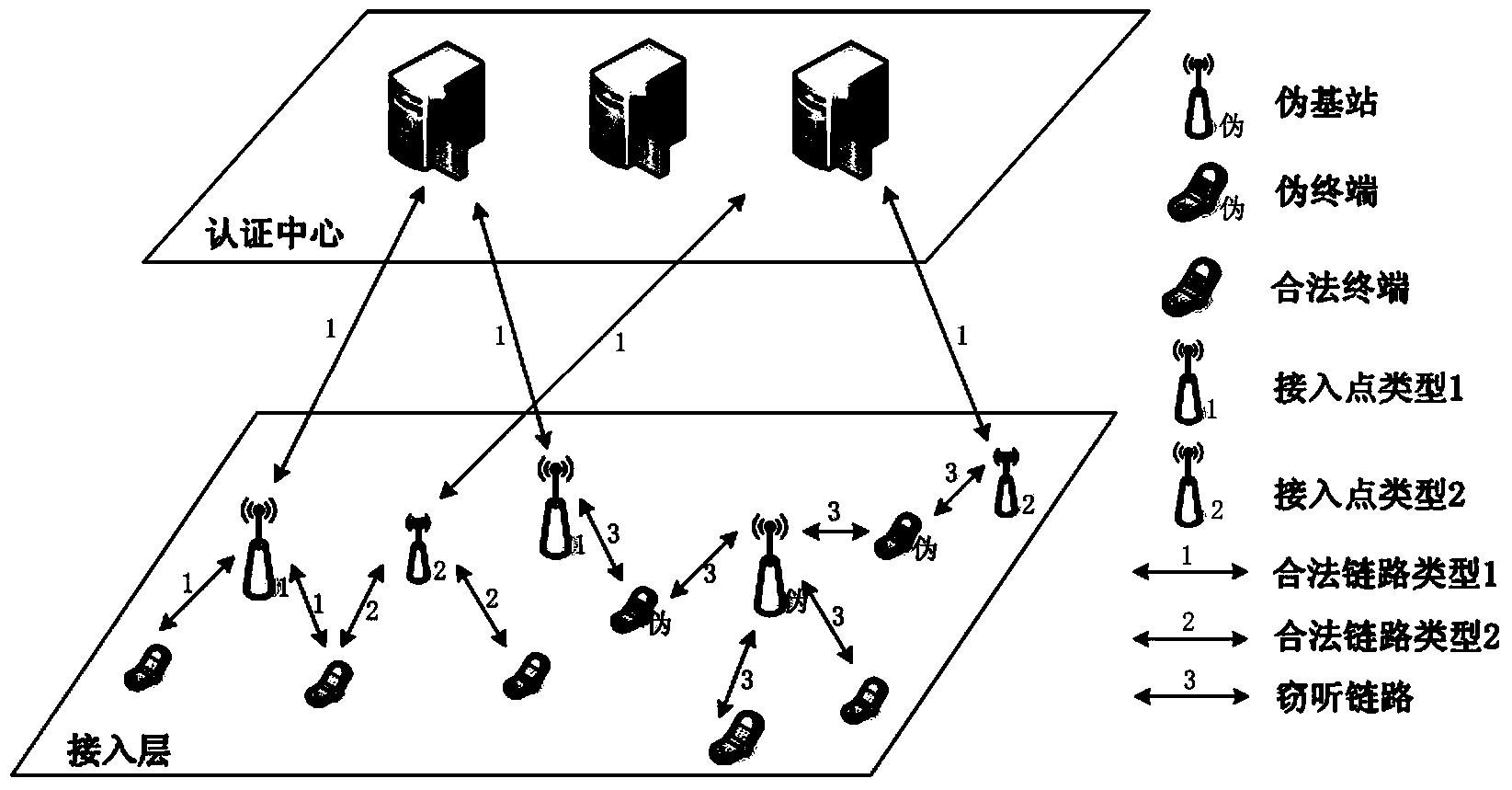
ActiveCN104010310AImprove unityEnsure communication securitySecurity arrangementPhysical layerHeterogeneous network
The invention relates to a heterogeneous network unified authentication method based on physical layer safety. The heterogeneous network unified authentication method based on the physical layer safety comprises the steps that the unified identity information of a terminal is obtained by an authentication center; physical layer random authentication parameters are generated by the terminal and an access point; the physical layer random authentication parameters are reported to the authentication center by the access point; authentication data are generated by the authentication center through a root key of the terminal and the physical layer random authentication parameters, and the authentication data are transmitted to the terminal; the access point and the authentication center are authenticated by the terminal through the root key, the physical layer random authentication parameters and the authentication data of the authentication center, and terminal authentication data are generated and transmitted to the authentication center; the terminal is authenticated by the authentication center through the root key of the terminal, the physical layer random authentication parameters and the terminal authentication data; the physical layer random authentication parameters are simultaneously updated by the terminal and the access point, and continuous authentication is achieved. By means of the method, multi-party bidirectional identity authentication between various terminals and a heterogeneous network is achieved, and transparent transfer attacks of pseudo-base-stations and pseudo-terminals can be recognized and restrained.
Owner:THE PLA INFORMATION ENG UNIV
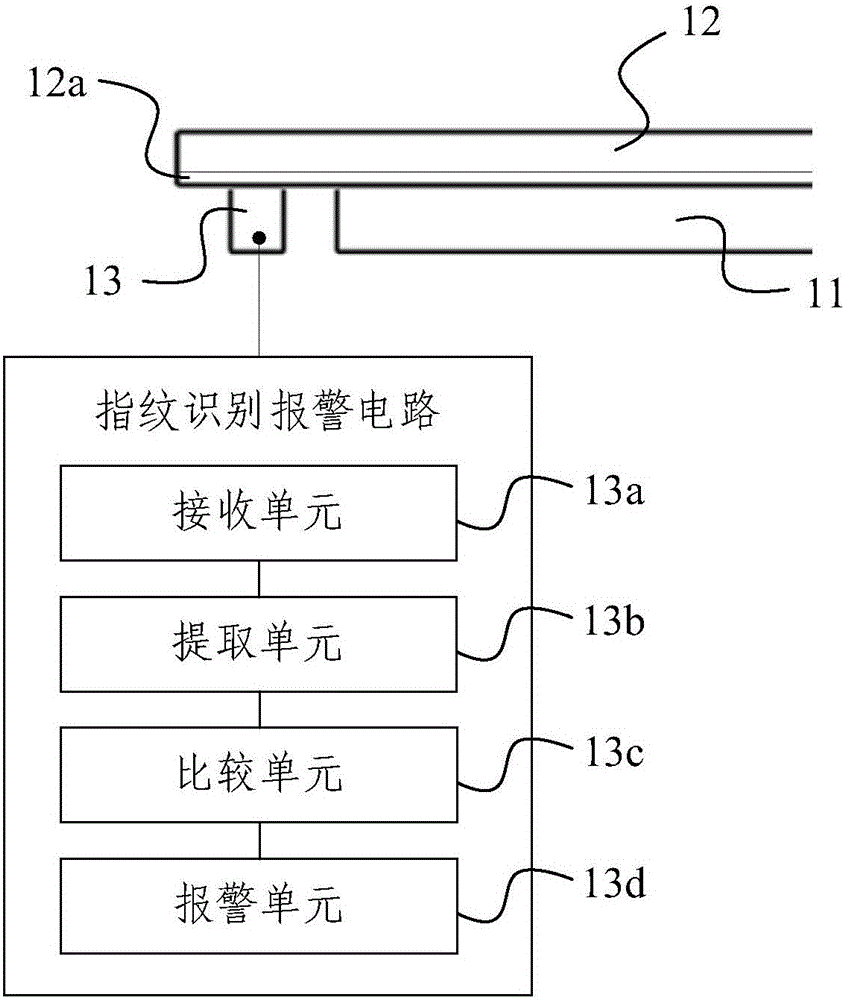
Display apparatus
ActiveCN105160230AGuarantee information securityGuaranteed privacyInternal/peripheral component protectionDigital data authenticationEngineeringAuthentication
The invention provides a display apparatus which comprises a display panel, a transparent cover plate and a fingerprint identification alarm circuit, wherein the transparent cover plate is arranged on the display panel; a full-screen fingerprint sensor is arranged on a first side, close to the display panel, of the transparent cover plate and is used for acquiring fingerprint information on the surface of a second side of the transparent cover plate; and the fingerprint identification alarm circuit is arranged on a first side of the transparent cover plate and comprises a receiving unit connected with the full-screen fingerprint sensor and used for receiving fingerprint information of the full-screen fingerprint sensor, an extraction unit connected with the receiving unit and used for extracting a fingerprint feature of fingerprint information obtained by the receiving unit, a comparison unit connected with the extraction unit and used for comparing the fingerprint feature obtained by the extraction unit with a pre-stored fingerprint feature, and an alarm unit connected with the comparison unit and used for performing alarm operation when the fingerprint feature obtained by the extraction unit is not matched with the pre-stored fingerprint feature. The display apparatus can realize automatic identity authentication of users in a normal use state.
Owner:BOE TECH GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com