System and method for preventing unauthorized use of IC card
A testing system and card number technology, applied in the direction of instruments, inductive record carriers, internal/peripheral computer component protection, etc., can solve problems such as hidden dangers of life and property safety, falsified data, user losses, etc., so as to reduce the use risk and improve the safety. The effect of security and confidentiality, principle and operation is simple and clear
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples.
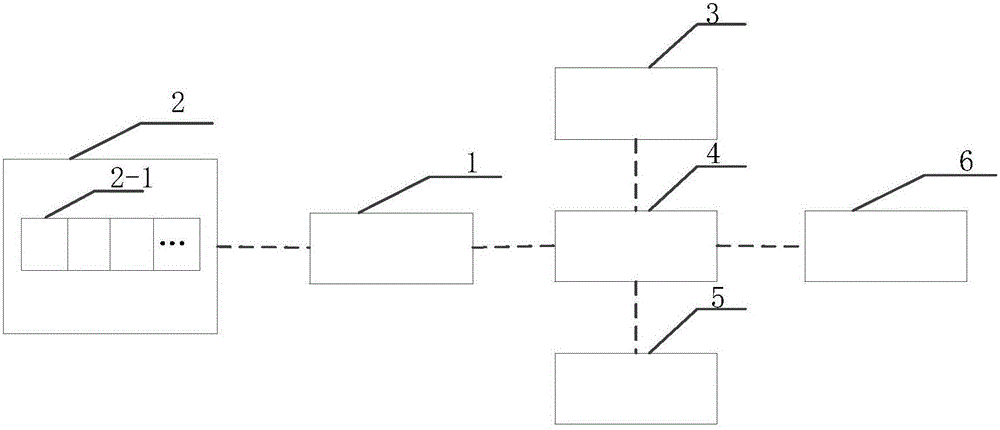
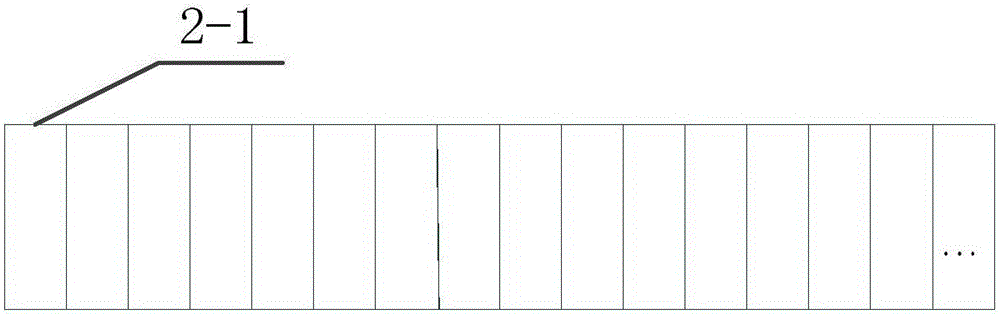
[0032] see figure 1 , a device and method for preventing IC card theft, including IC card reader 1, test UID card 2, power supply module 3, microprocessor 4, automatic alarm device 5, display module 6, etc., microprocessor 4 and The card reader 1, the power module 3, the automatic alarm device 5, and the display module 6 are connected, and the IC card reader 1 communicates wirelessly with the test UID card 2 through magnetic field energy. The test UID card 2 is divided into 16 sectors, each sector has 4 blocks, a total of 64 blocks; among them, sector 0 and block 0 can perform data writing operations.
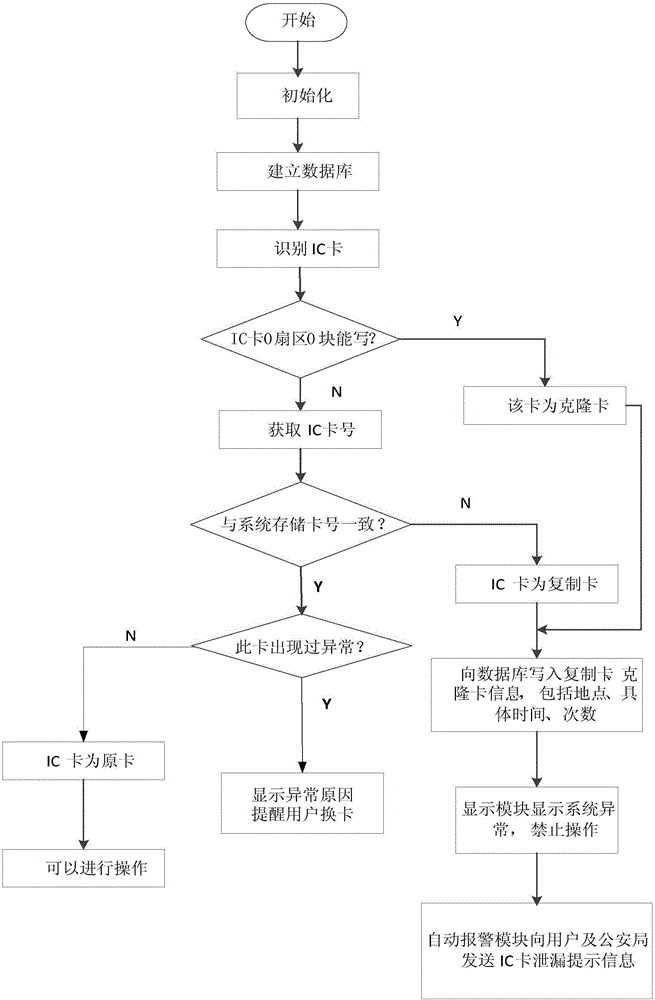
[0033] After the system was normally opened, the microprocessor 4 set up a database for storing the user's mobile phone number and its IC card number and all information in the card. First use the test UID card to test whether the system is norm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com