Safe network terminal based on single CPU dual bus
A security network, dual bus technology, applied in the field of network terminal devices, can solve problems such as information security problems that cannot be fundamentally solved, and achieve the effects of solving information security problems, having strong expansion functions, and preventing network intrusions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
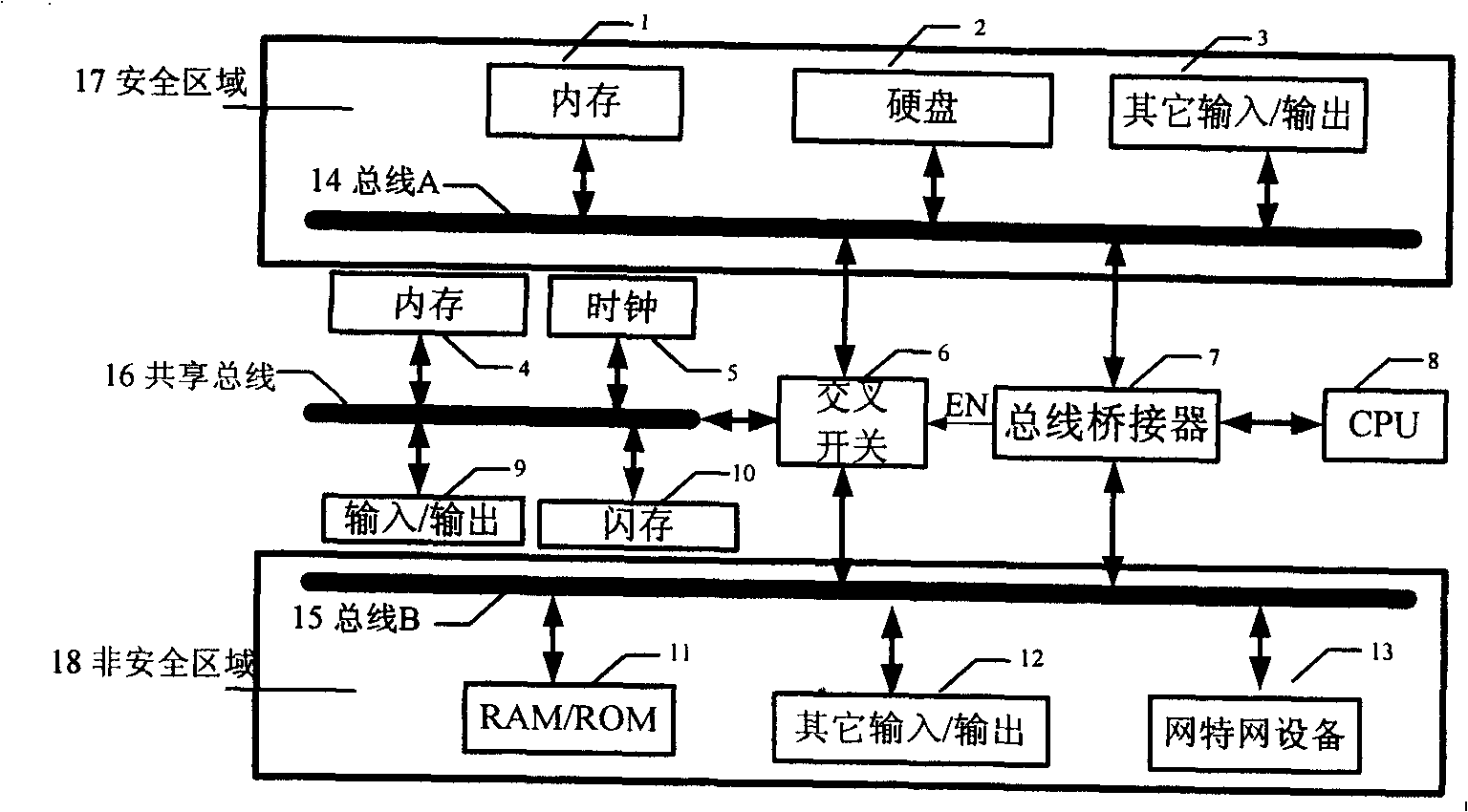
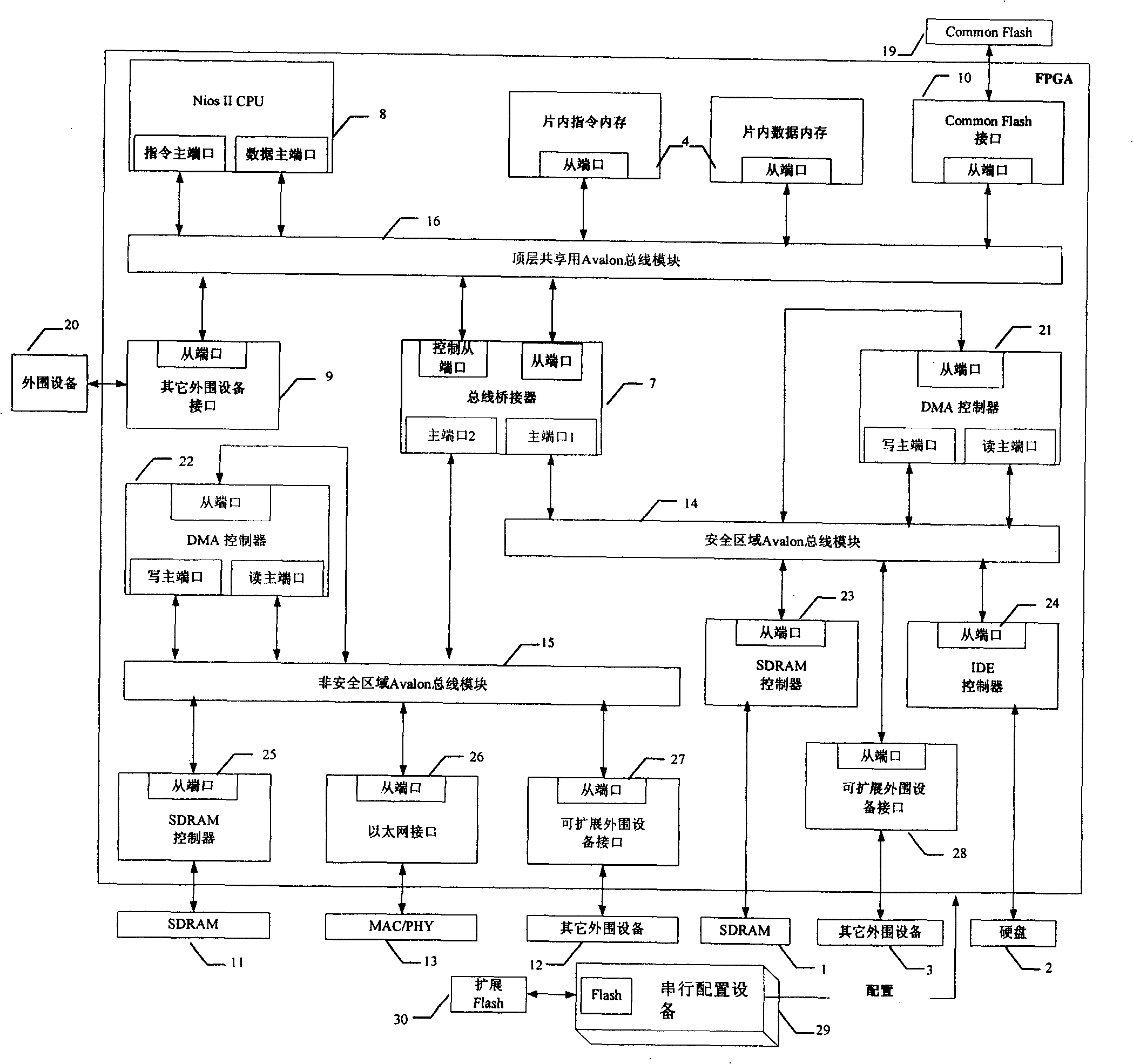
[0012] This embodiment relates to a novel implementation architecture of a single-CPU dual-bus secure network terminal, which is a secure network terminal with intrusion-free, information and data security. The architecture includes: a security area and a non-security area with independent system buses A and B; the Internet interface is only connected to the non-security area bus 15; the bus bridge 7 (BUS Bridge) controls the CPU 8 and the two buses through an agreed mechanism The connection between A and B; the main (protected) memory is only connected to the bus (bus A) in the safe area; the shared device is connected to bus A or bus B through a dual-port circuit for sharing of basic input and output devices and Internal and external communications, etc.
[0013] The unit components that realize the architecture of this embodiment include memory 1, hard disk 2, other input / output devices 3 and 12, clock 5, crossbar switch 6, bus bridge 7, CPU8, input / output 9, flash memory 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com