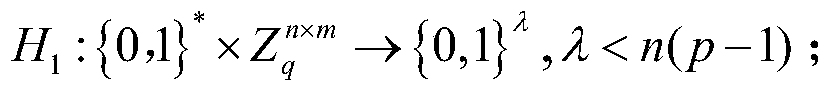Patents
Literature
240results about How to "Improve encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
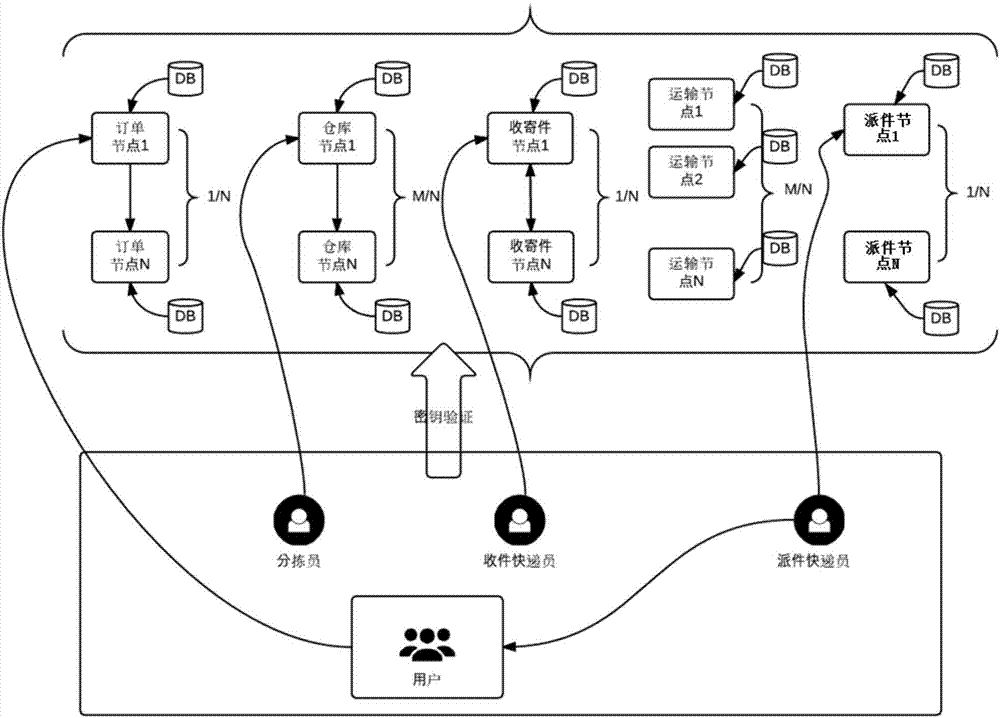
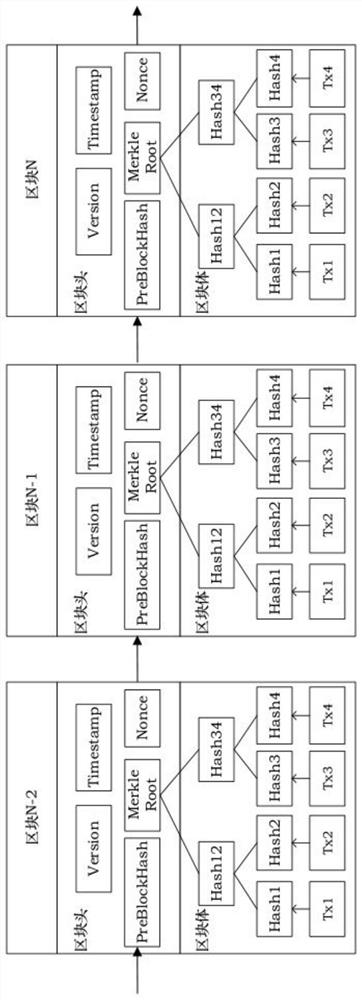
Block chain-based distributed logistic tracking method
InactiveCN106971288AGuaranteed privacyEnsure safetyForecastingDigital data protectionData streamEncryption
A block chain-based distributed logistic tracking method is disclosed and comprises the following steps: an order is placed by a user via a conventional information system, the order is distributed to an order node, and order information is generated; upper node private key decryption verification is adopted for a warehouse node, package information is generated and stored in a block chain after successful verification, and packaging operation is conducted by a sorter; the package is picked up via a package pickup and sending node, the upper node private key decryption verification is adopted, package pickup information is generated and stored in the block chain after successful verification, an optimal transport route is calculated, the upper node private key decryption verification is adopted for a transport node, transport information is generated and stored in the block chain after successful verification, the upper node private key decryption verification is adopted for a package delivery node, package delivery information is generated and stored in the block chain after successful verification, an express delivery worker sends the package to the user who places the order, the upper node private key decryption verification is adopted by the user, and signing information is generated and stored in the block chain after successful verification. Via the block chain-based distributed logistic tracking method, encryption performance and safety of data flows can be greatly improved, the optimal route is provided, and whole course data can be monitored and traced.
Owner:无锡井通网络科技有限公司
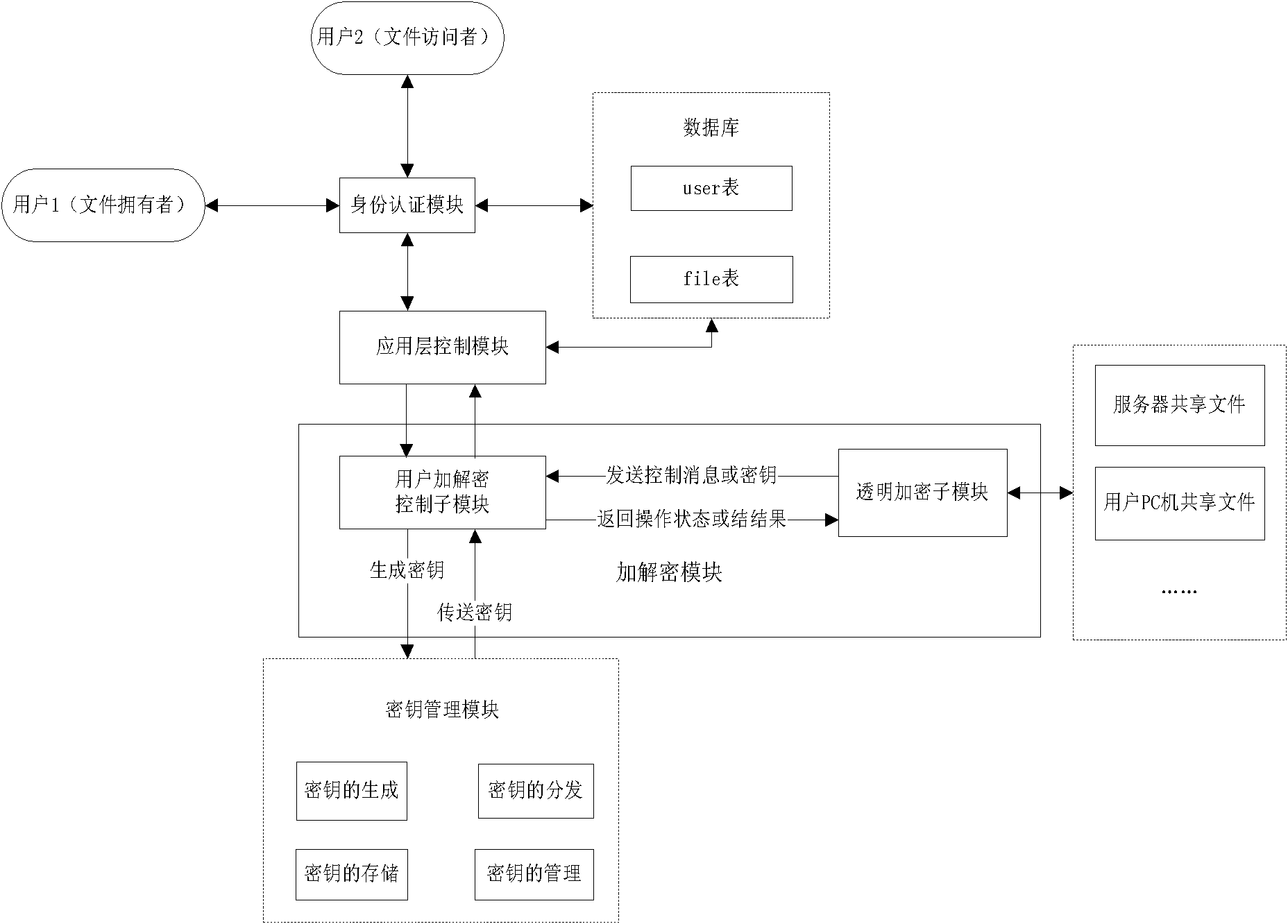
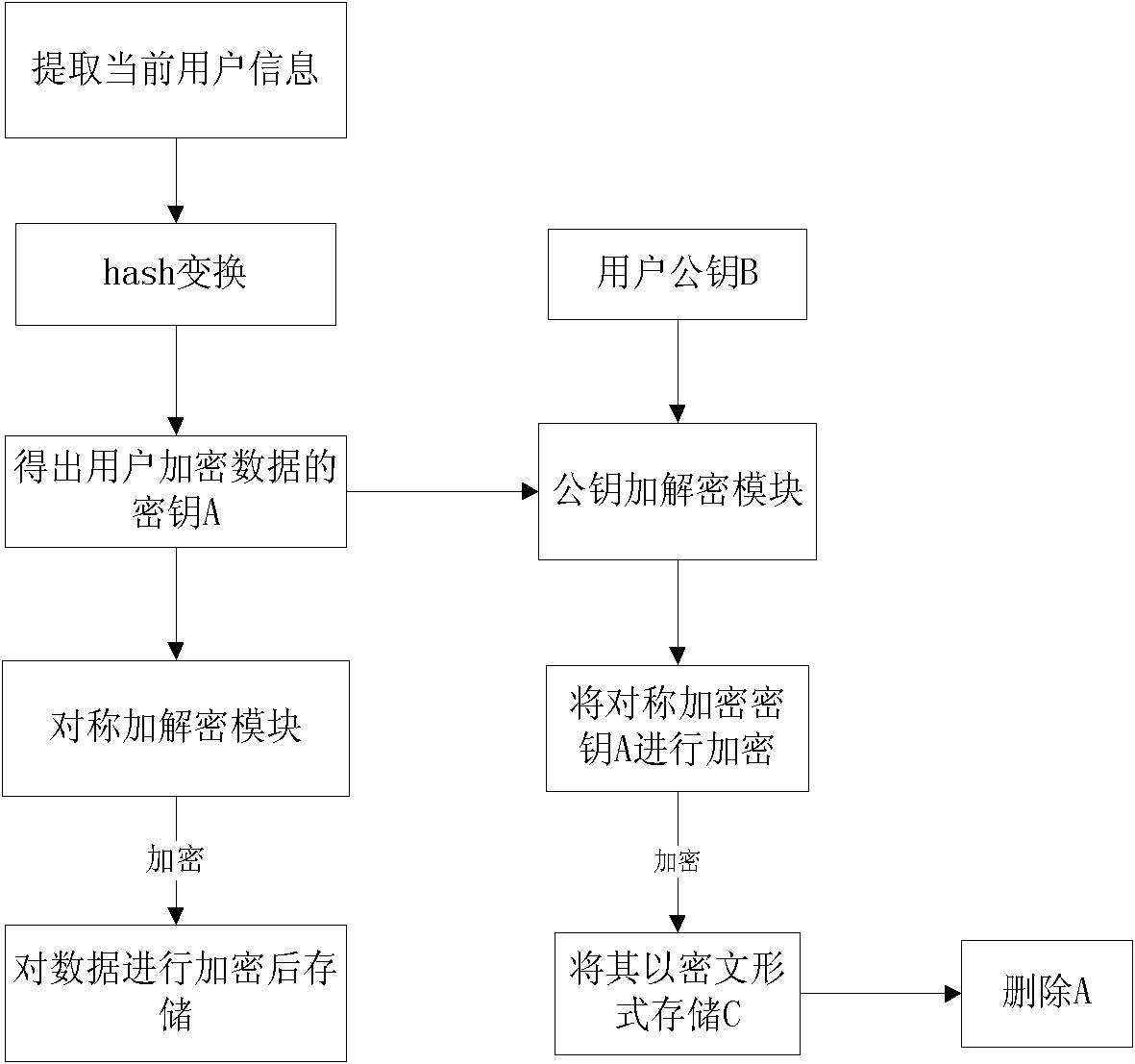
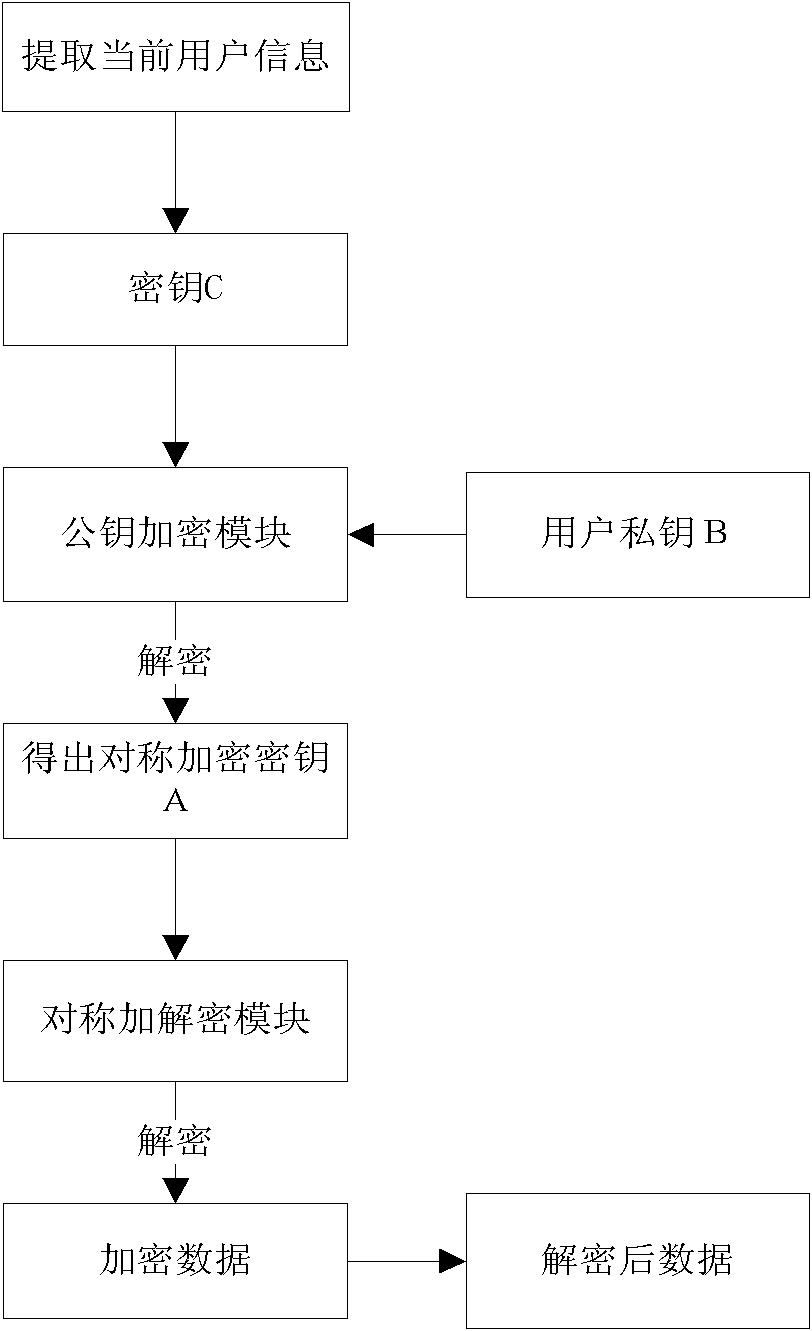
Encryption system, encryption method and decryption method for local area network shared file
InactiveCN102075544AEnsure safetyGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationInformation securityShared resource
The invention discloses an encryption system for a local area network shared file. The system comprises a secret key management module of a secret key to be used by reading, generating and managing an encryption file, and an encryption and decryption module for performing encryption and decryption according to a user command. The encryption system is characterized by also comprising an identity authentication module used for verifying the identity of a user and determining the authority of the user; and after the identity authentication module verifies that the identity of the user is legal, the encryption and decryption module performs encryption and decryption, and then the local area network shared file is accessed. The system limits the authority that different specified users read different files in shared resources, so that the information safety of resources in the local area network can be effectively guaranteed.
Owner:博视联(苏州)信息科技有限公司
Color image encryption method based on SHA-384 function, spatiotemporal chaotic system, quantum chaotic system and neural network
ActiveCN104008520AImprove securityLarge key spaceImage data processing detailsComputer hardwareDiffusion
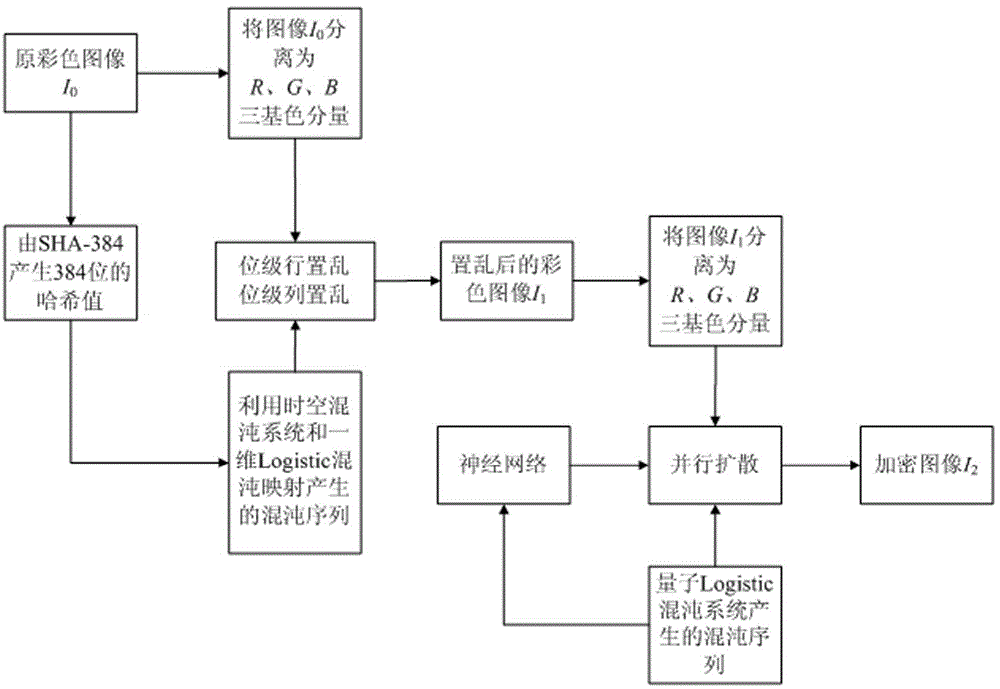
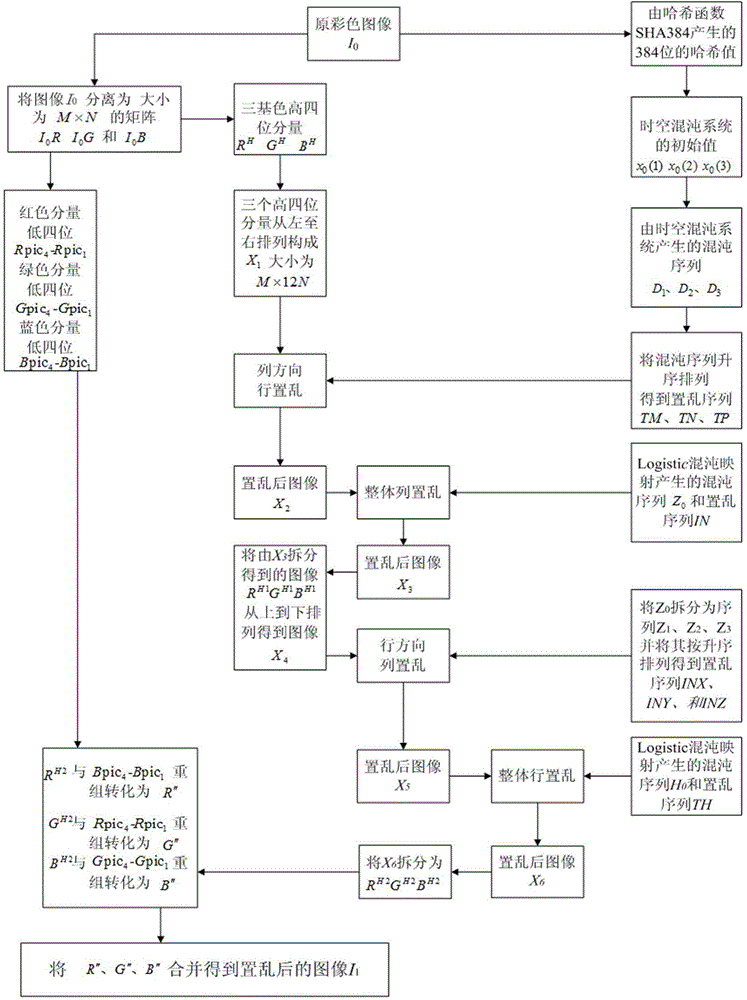
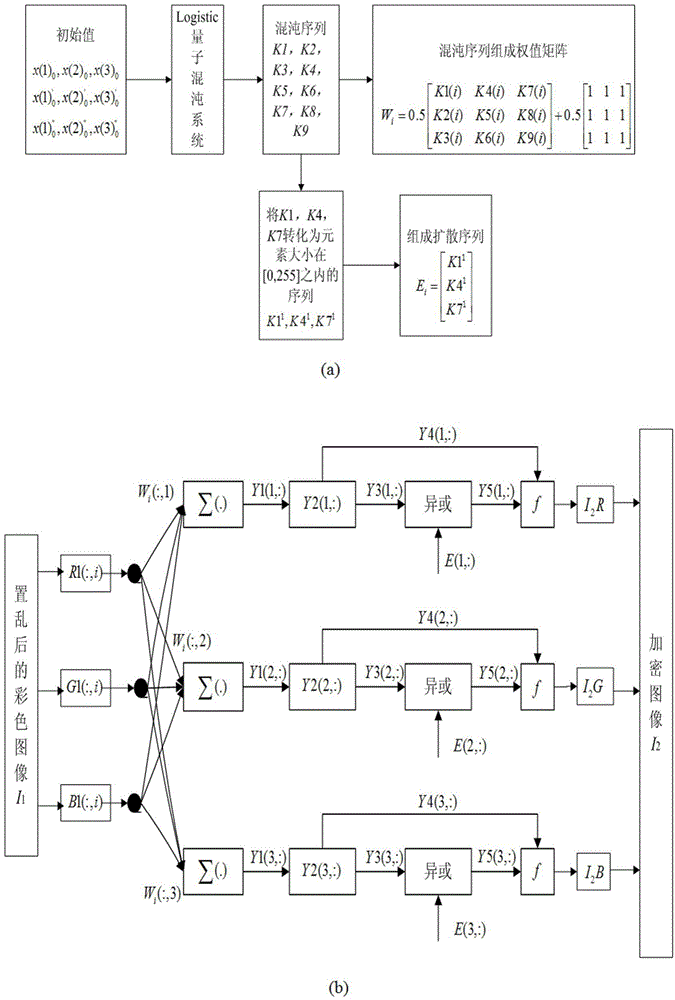
The invention relates to a color image encryption method based on an SHA-384 function, a spatiotemporal chaotic system, a quantum chaotic system and a neural network. The method includes the steps that an original color image I0 is calculated through the SHA-384 function, a Hash value is obtained as a secret key, the Hash value, a CML and one-dimension Logistic chaotic mapping are utilized for generating a chaos sequence, bit-level line-column scrambling is carried out on high four-digit images of components of three primary colors of the I0 through the chaos sequence, and a scrambled image I1 is obtained; the Logistic quantum chaotic system is utilized for generating a chaos sequence for encrypting the scrambled image, and is combined with the neural network to carry out parallel diffusion processing on all pixel values of components of three primary colors of the I1, and a final encrypted image I2 is obtained. By the method, the space of the secret key is greatly enlarged, the safety, encryption effect and secret key sensibility are higher, the attack resistance capacity is higher, the scrambling process and the encryption time are shorter, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
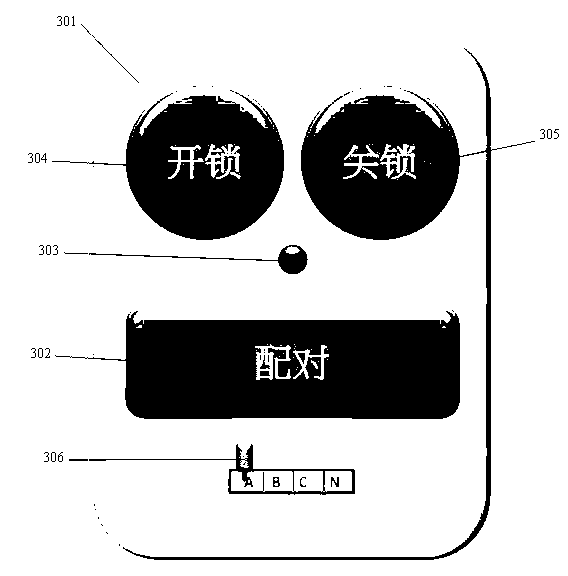
Bluetooth Low Energy (BLE) invisible intelligent lock system controlled by BLE equipment
InactiveCN103174337AMeet the priceFulfil requirementsElectric permutation locksEngineeringData transmission
The invention discloses a Bluetooth Low Energy (BLE) invisible intelligent lock system controlled by BLE equipment. The BLE invisible intelligent lock system controlled by the BLE equipment is based on the BLE wireless communication technology. The BLE invisible intelligent lock system comprises a BLE invisible intelligent lock, the BLE equipment, an application program (APP) capable of running on the BLE equipment, a BLE gateway, and the like. According to the BLE invisible intelligent lock system controlled by the BLE equipment, a key is replaced with the BLE equipment like a daily used smart phone to control the BLE intelligent lock, the BLE technology is adopted to guarantee safety of data transmission and enable the BLE intelligent lock to work over a year normally only by being powered by a battery, requirements of users for safety, convenience and price and the like of a lockset system are met, usage of the key, a lock cylinder and other parts is eliminated by adding only one BLE module, and the lock industry is promoted to step into an energy-saving and environment-friendly lower-carbon time.
Owner:鲁亚诗 +1
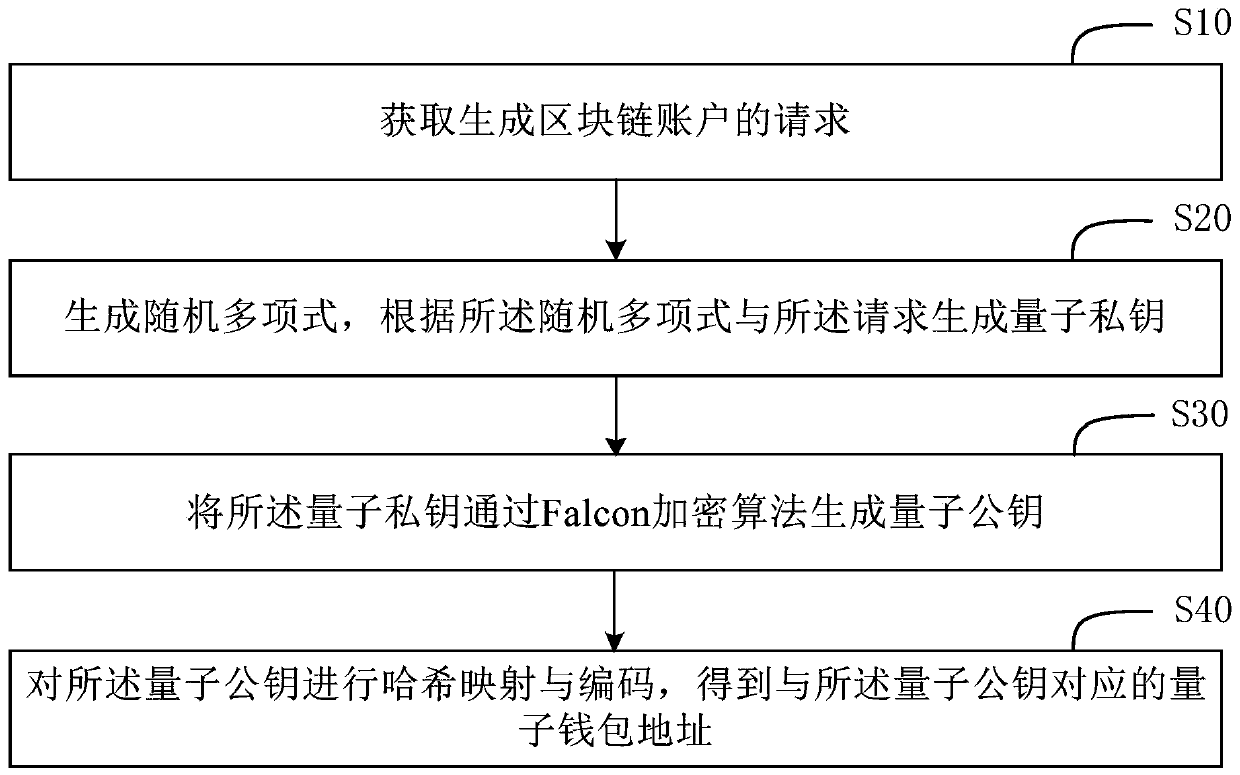
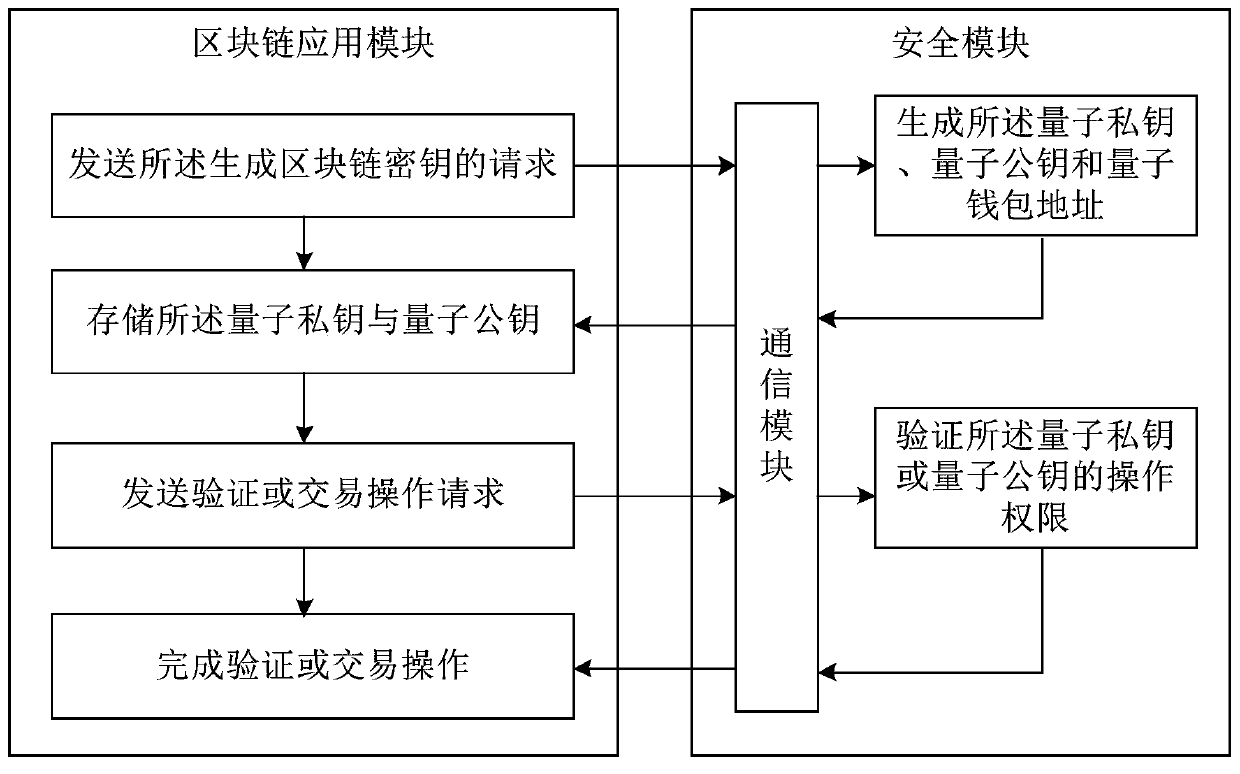
Blockchain account processing method and apparatus, and storage medium
ActiveCN109716375AImprove securityResistance to crackingKey distribution for secure communicationPublic key for secure communicationPasswordSecurity level
The invention provides a blockchain account processing method and apparatus, and a storage medium. The blockchain account processing method comprises the steps of obtaining a request for generating ablockchain account; generating a random polynomial, and generating a quantum private key according to the random polynomial and the request; generating a quantum public key from the quantum private key through a Falcon encryption algorithm; and performing Hash mapping and coding on the quantum public key to obtain a quantum wallet address corresponding to the quantum public key. The quantum publickey is generated through the Falcon encryption algorithm, the security level of the block chain account is improved, and cracking of an existing block chain account system by a quantum computer can be resisted; Compared with an existing secret key formed by a student with a later quantum password, the quantum private key and the quantum public key generated by the method are smaller in storage space and faster in signature and verification speed, and the operation burden caused to the block chain server is also reduced.
Owner:BCM SOCIAL CORP +1
Image encryption method based on hyperchaotic system and multi-level scrambling
ActiveCN108366181AImprove encryptionKey sensitivity is highSecuring communicationPictoral communicationPattern recognitionStatistical analysis
The invention discloses an image encryption method based on a hyperchaotic system and multi-level scrambling. The image encryption method comprises the following steps: firstly, acquiring a hyperchaotic sequence K through the hyperchaotic system; converting an original image into a two-dimensional matrix with the size of L= H x W, wherein H and W are dimensions of rows and columns of a matrix respectively; then converting original image pixel information into a one-dimensional vector sequence P, performing pixel-level, bit-level and DNA-level scrambling on the sequence P through an index sequence generated by the hyperchaotic sequence K, performing an exclusive OR operation on a pixel sequence through a mapping sequence, encrypting the original image to obtain an encrypted DNA sequence through binary bit conversion, DNA coding and DNA base operation, and converting the encrypted DNA sequence into a binary bit sequence B2; and finally, converting the sequence B2 into an encrypted image.According to the image encryption method based on the hyperchaotic system and the multi-level scrambling provided by the invention, the image is scrambled and encrypted at the pixel level, the bit level and the DNA level, the key sensitivity is high, the encryption effect of the image is effectively improved, attack operations such as statistical analysis and exhaustive analysis can be effectively resisted, and the safety is high.
Owner:SOUTHWESTERN UNIV OF FINANCE & ECONOMICS
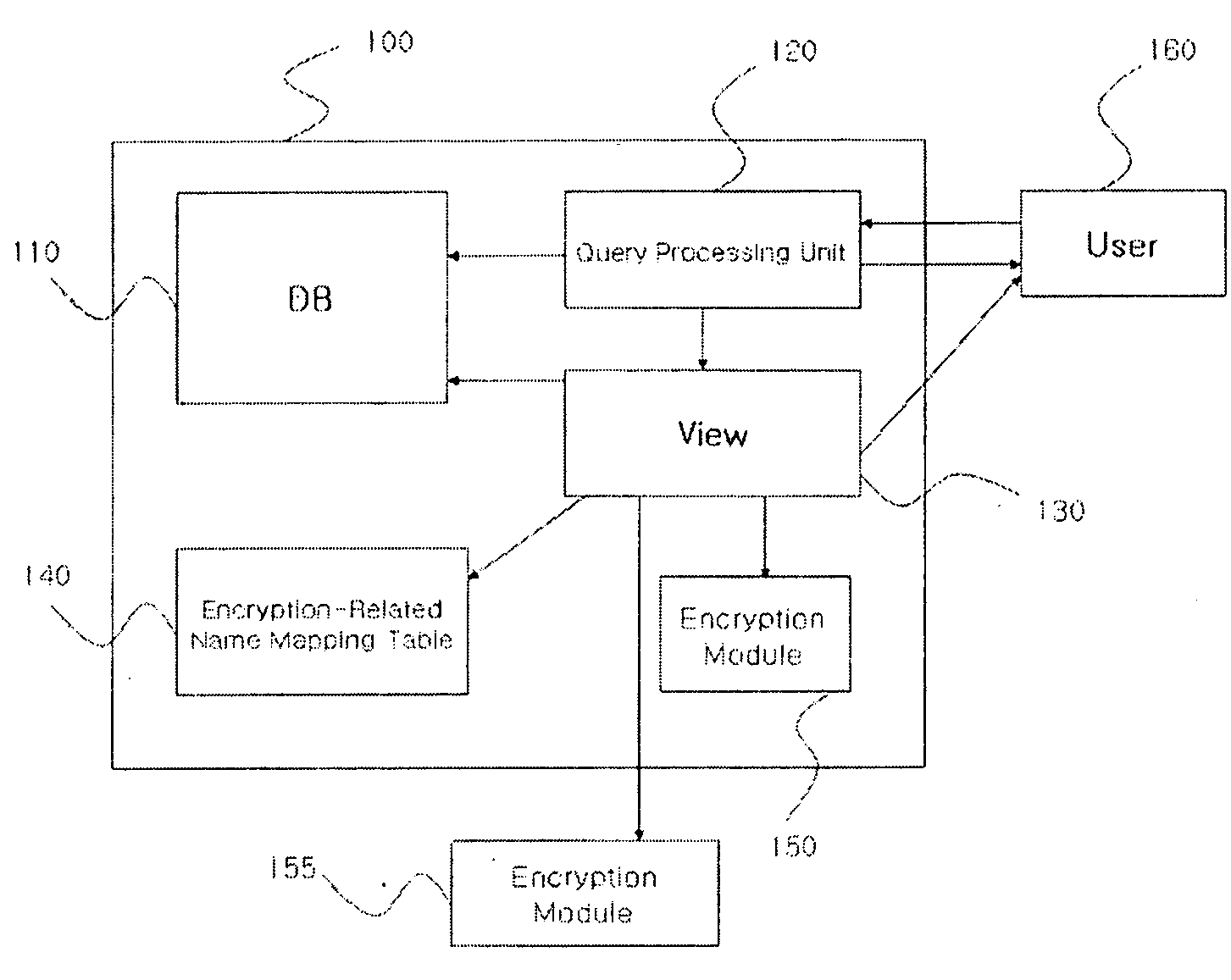
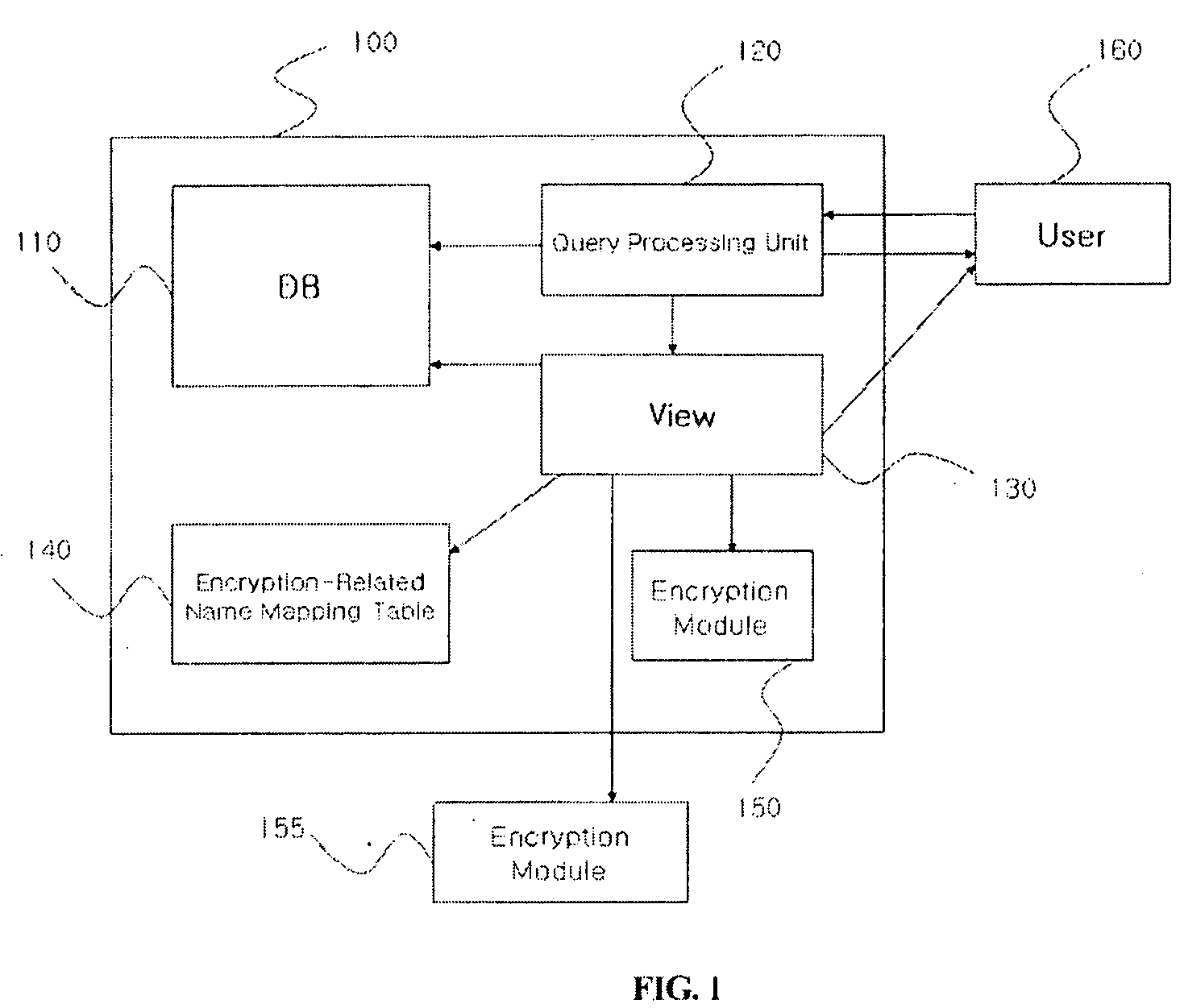
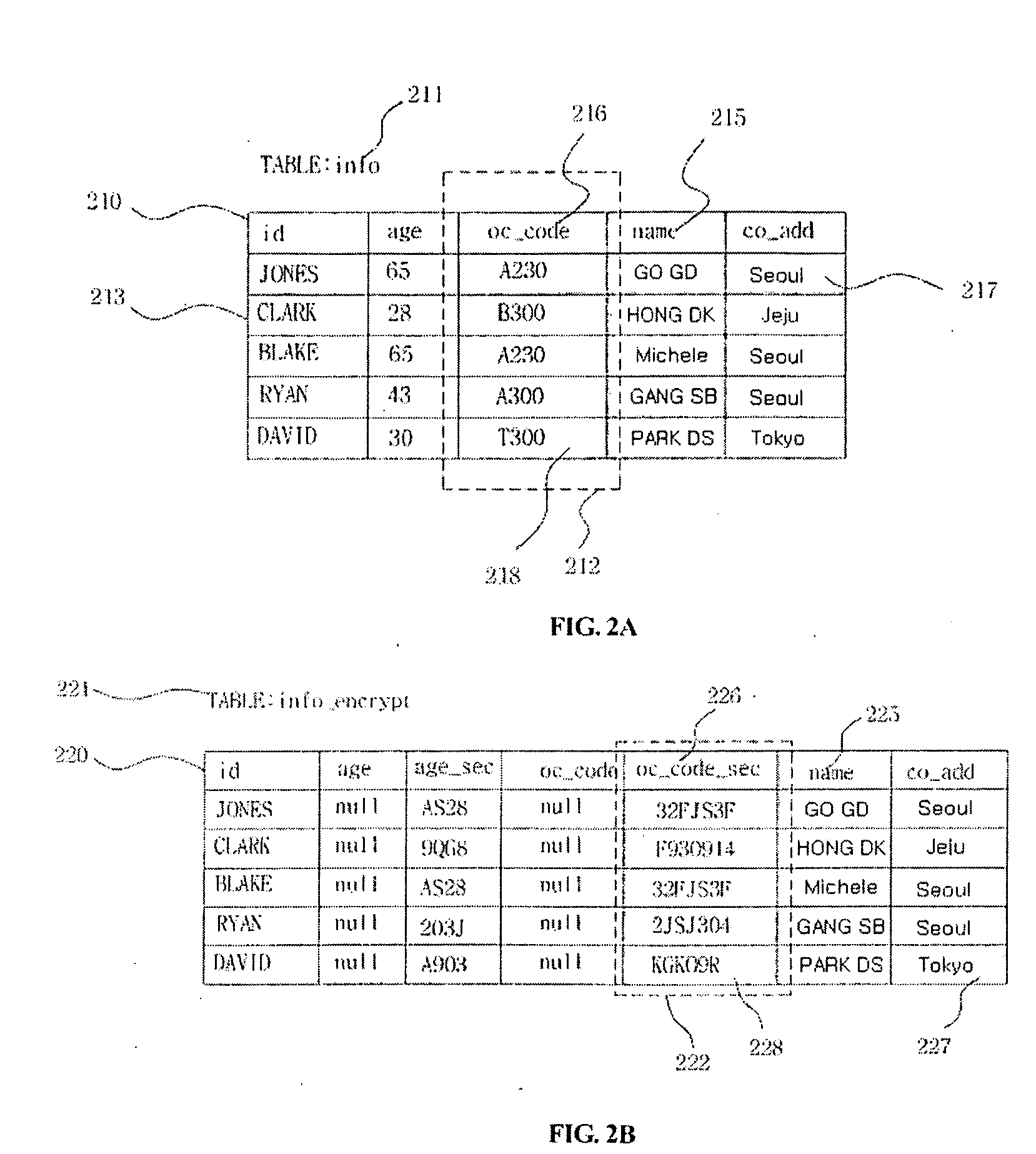
Query processing system and method for database with encrypted column by query encryption transformation
ActiveUS20090100033A1Improve encryptionOvercome slowdownDigital data processing detailsComputer security arrangementsQuery transformationEncryption
Query processing system and method by query transformation transform a user request query based on an original DB structure, destined to a DBMS of a DB with some columns encrypted, into a query based on an encrypted DB structure so that the DBMS processes the query. The query is processed irrespective of whether or not the query includes an encryption-related item, and query-processing performance is remarkably improved.
Owner:PENTA SECURITY SYST
Methods and systems in a computer network for enhanced electronic document security
InactiveUS20050262340A1Improved decryptionImprove encryptionKey distribution for secure communicationSecret communicationComputer hardwareElectronic document
Methods and systems for scanning and encrypting documents are disclosed. A document can be scanned utilizing a scanning device. The document can then be converted into image formatted data representative of the document. The image formatted data can then be encrypted at the scanning device utilizing an encryption key prior to transmitting the image formatted data to its final destination. The image formatted data can be decrypted utilizing an encryption key after the image formatted data is delivered to its final destination, which can be, for example, a rendering device such as a copier or printer linked to a computer network and / or a computer network client and / or a computer network storage device.
Owner:XEROX CORP
Data transmission method, apparatus and system
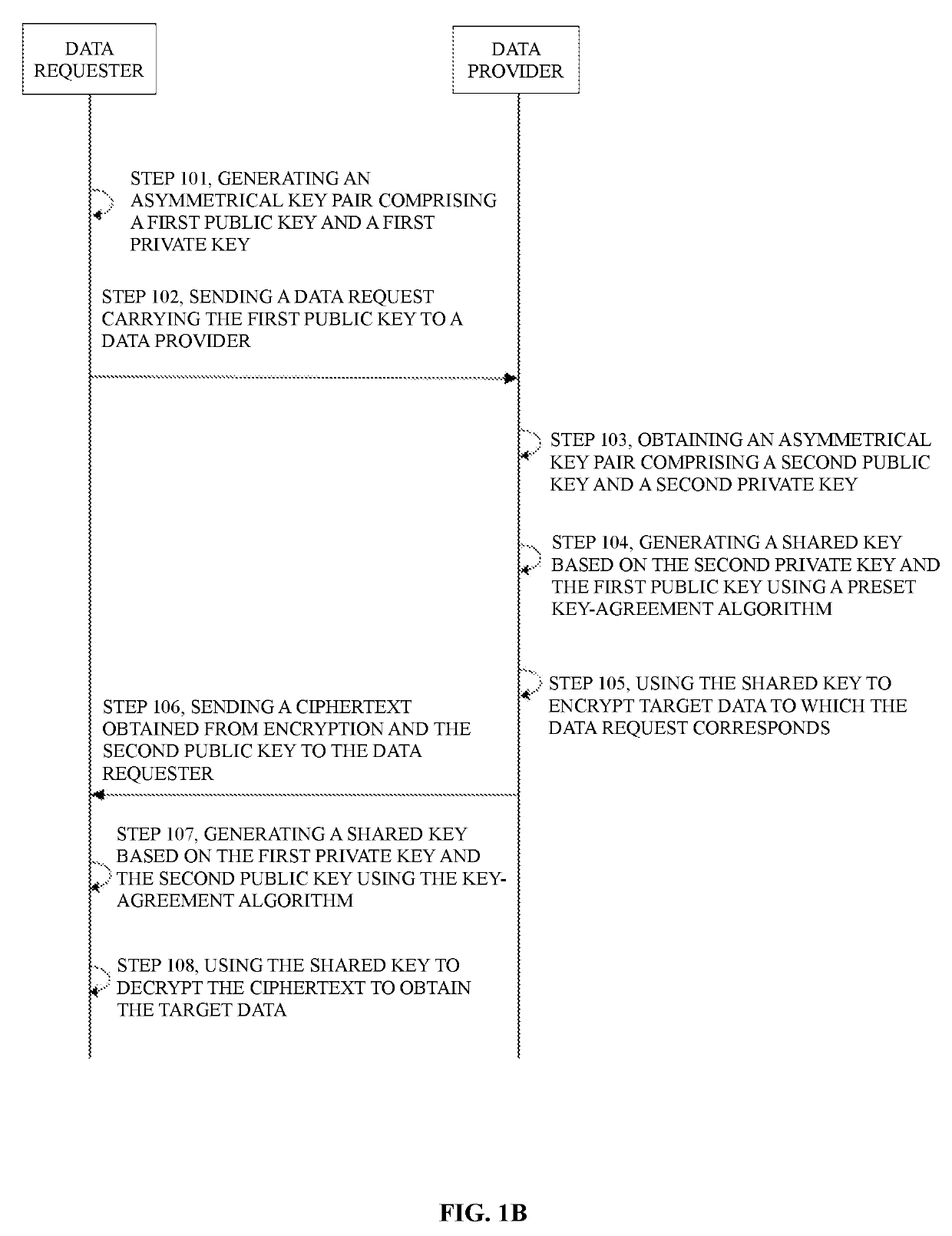
InactiveUS20190253249A1Improve decryptionImprove encryptionKey distribution for secure communicationMultiple keys/algorithms usageCiphertextEngineering
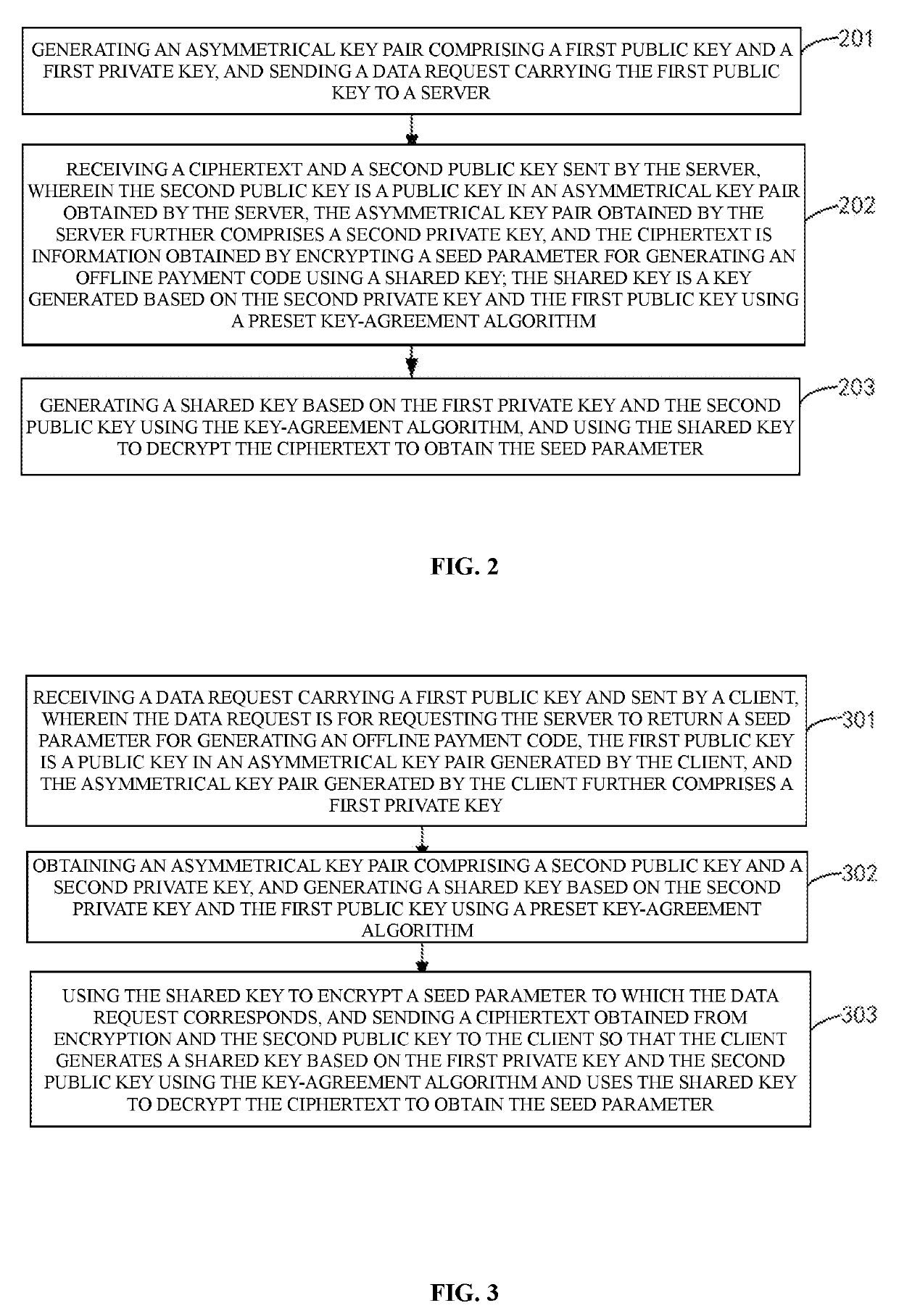
Methods, systems, and apparatus, including computer programs encoded on computer storage media, for data transmission are provided. One of the methods includes: generating, by a computing device, a first asymmetrical key pair comprising a first public key and a first private key, sending, by the computing device, a data request comprising the first public key to a server, and receiving, by the computing device from the server, a ciphertext comprising encrypted data and a second public key. The second public key is associated with a second asymmetrical key pair that further comprises a second private key. The method also includes generating, by the computing device, a shared key based on the first private key and the second public key using a key-agreement algorithm and decrypting, by the computing device, the ciphertext using the shared key.
Owner:ADVANCED NEW TECH CO LTD
Encryption method and system
ActiveCN101631305AImprove encryptionHigh-level encryption effectPublic key for secure communicationUser identity/authority verificationComputer hardwareClient-side
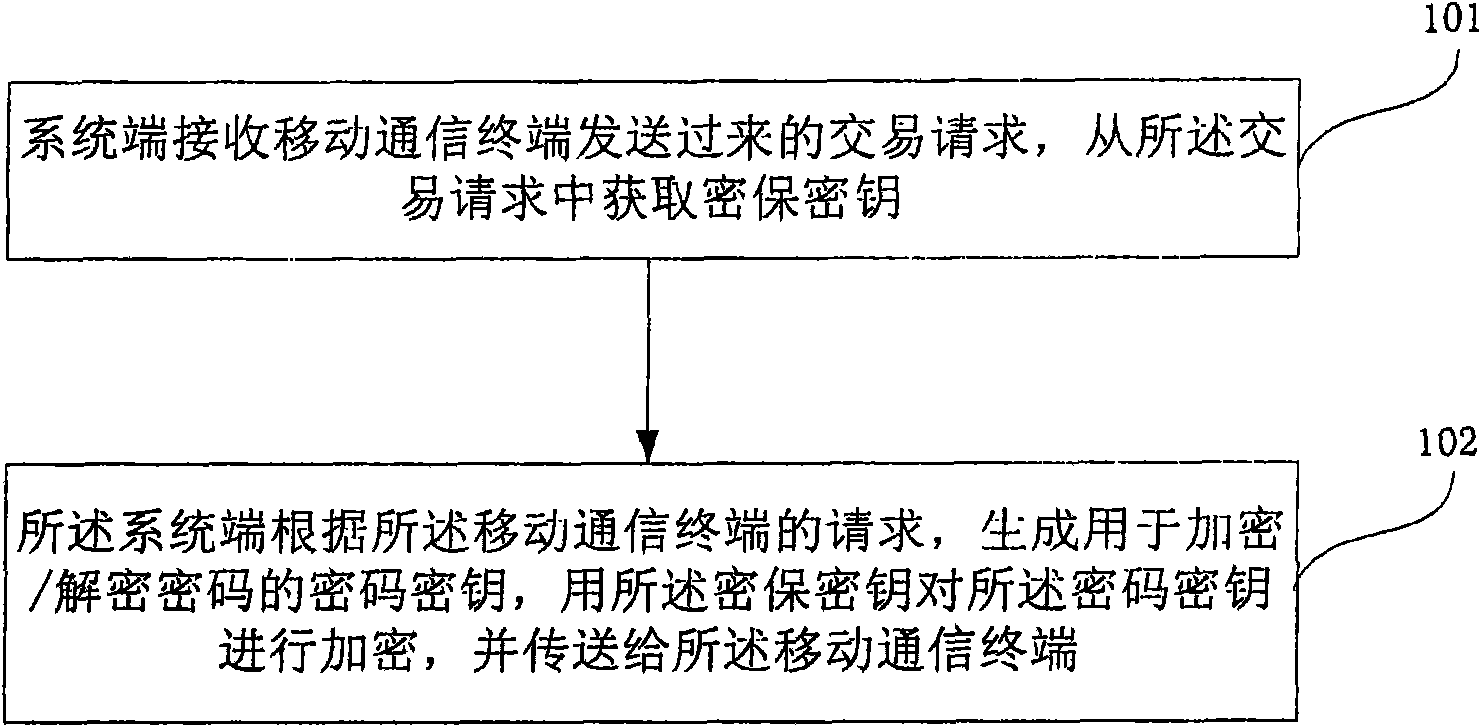
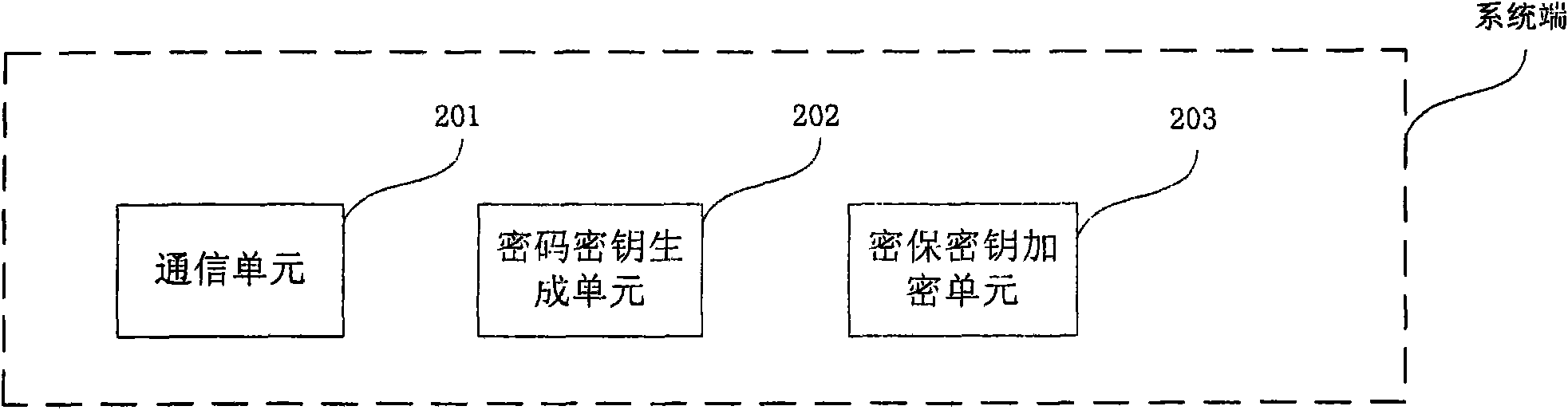
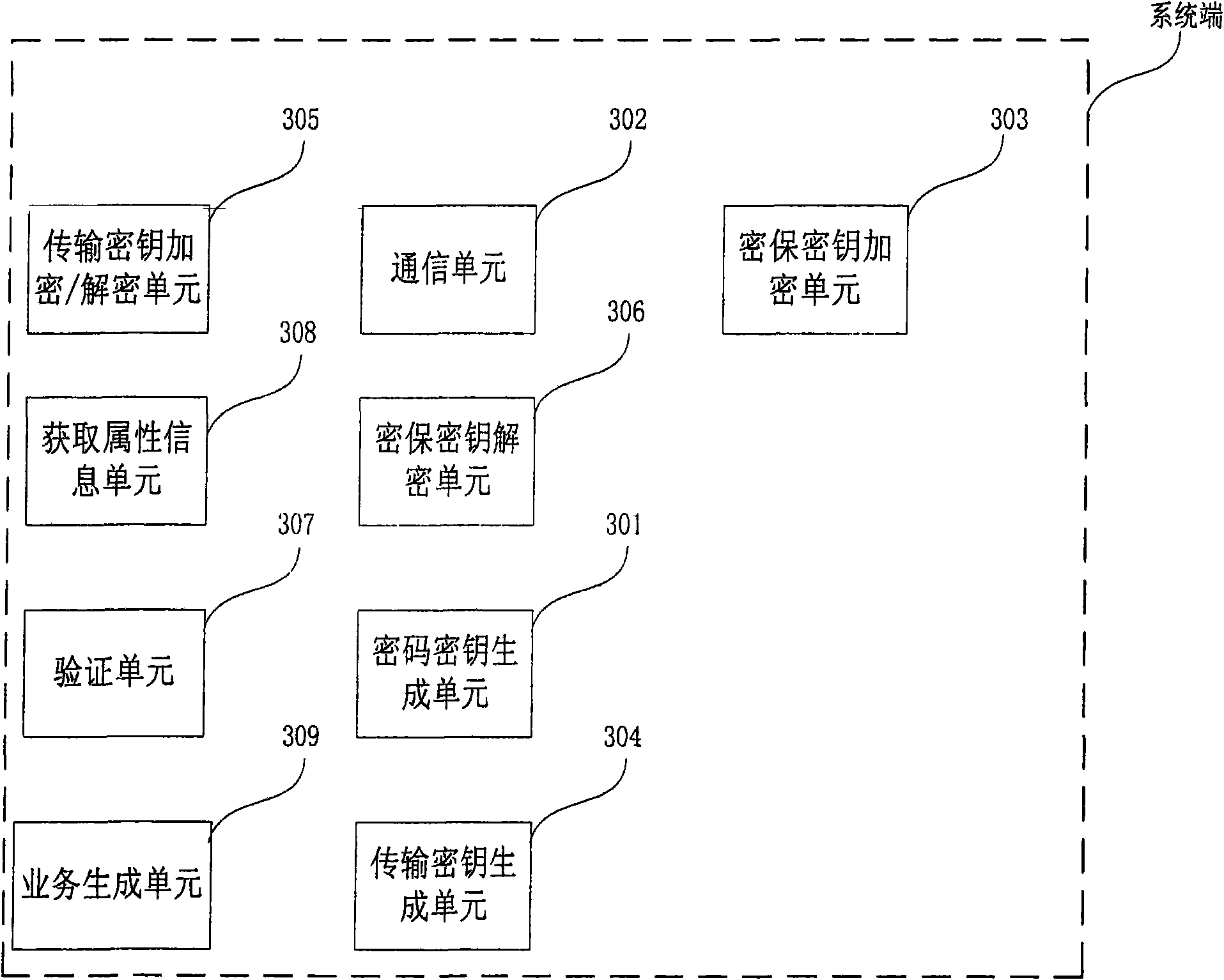
The invention relates to the technical field of encryption, in particular to an encryption method and a system, wherein, the method comprises the following steps that a system end receives a transaction request sent by a mobile communication terminal, and an encryption protection secret key is obtained from the transaction request; and the system end forms an encrypt / decrypt code secret key according to the transaction request of the mobile communication terminal, and the encryption protection secret key is used for encrypting and transmitting the code secret key into the mobile communication terminal. The invention has the advantages that when the client end of the mobile communication terminal starts transaction, a new code secret key is obtained from the system end each time and is used as a code for the encryption client starting the business request, thereby realizing the high grade encryption effect with one-time code.
Owner:BANK OF COMMUNICATIONS
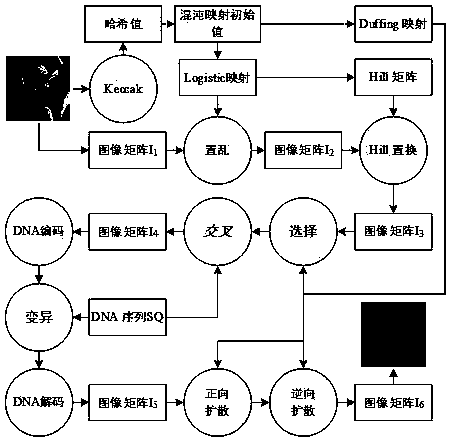
An image encryption method based on Duffing mapping and genetic operation
ActiveCN109376540AIncreased sensitivityIncrease the difficulty of decipheringDigital data protectionPlaintextExclusive or
The invention provides an image encryption method based on Duffing mapping and genetic operation. The hash value of a plaintext image is calculated by using a Keccak algorithm as an initial value input key of a chaotic system; the sensitivity and pseudo-randomness of the chaotic map to the initial conditions are used, the pseudo-random sequence is obtained by iterating the Logistic map and the Hill encryption matrix is generated to scramble and replace the image matrix. Combined with Duffing map and DNA coding technology, pixel selection, crossover and mutation are realized by genetic operation to achieve pixel diffusion and scrambling, and bidirectional exclusive OR operation with chaotic sequence to enhance its confusion and diffusion characteristics. The invention utilizes the pseudo-randomness of Duffing mapping and Logistic mapping, ergodicity and the crossover mutation operation of genetic algorithm, has strong sensitivity to key, can effectively resist statistical attack and differential attack, etc., has good security and application potential, and the image encryption effect and performance are remarkably improved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
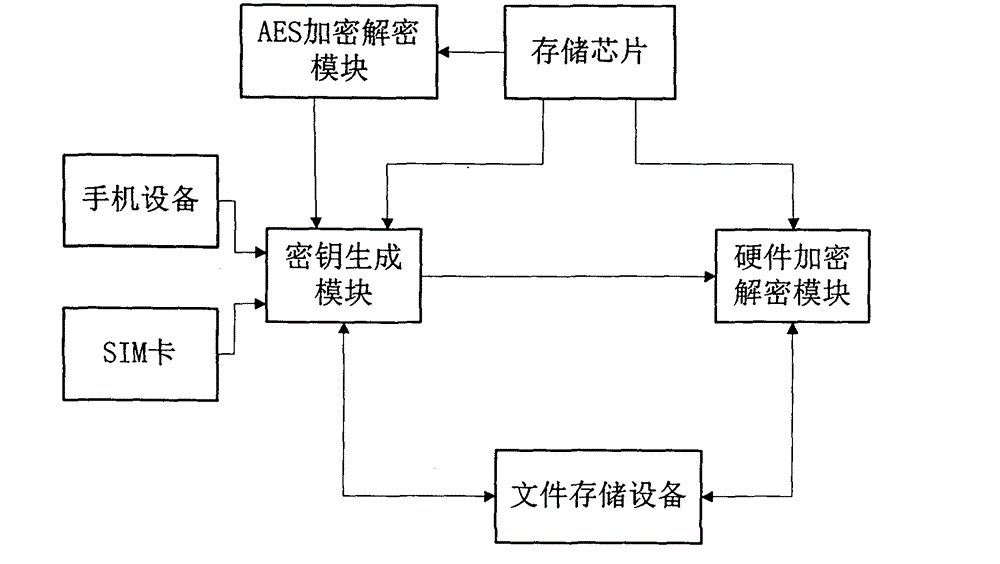
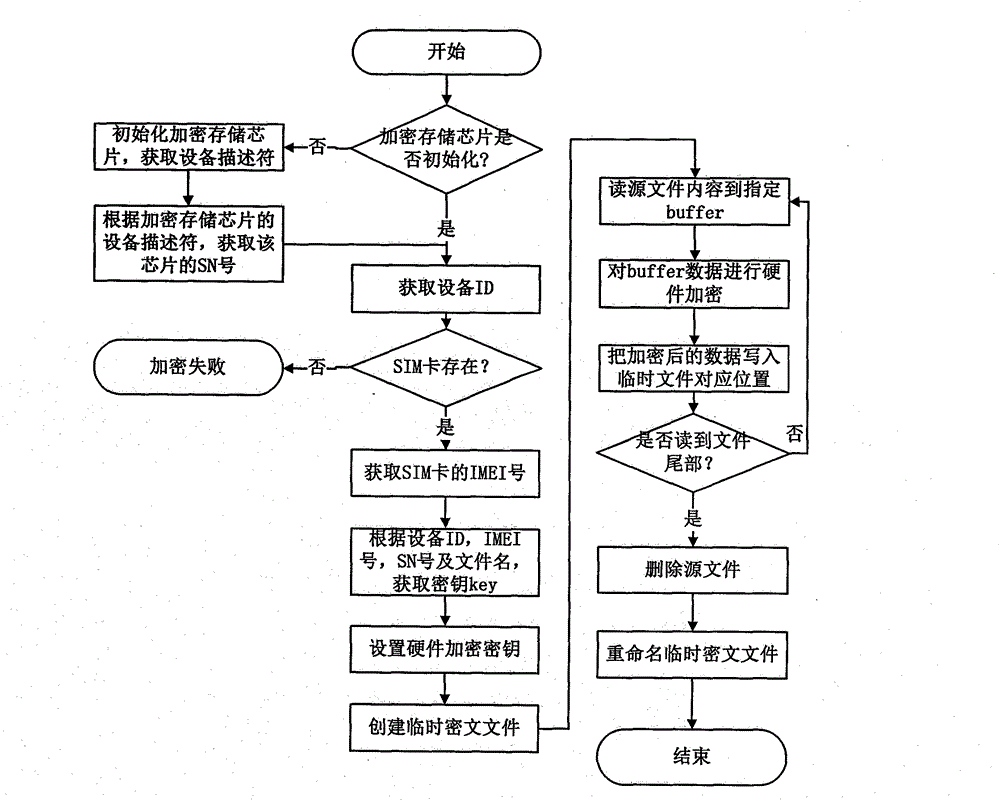
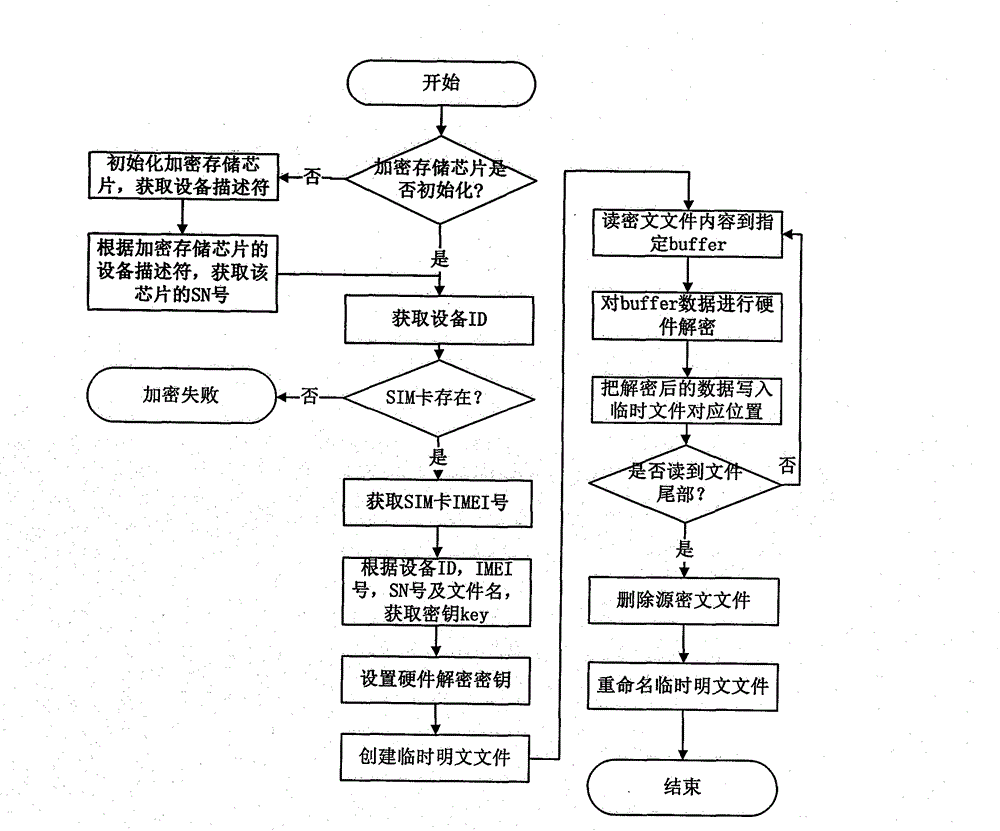
Hardware encryption protection method and system for cellphone data
ActiveCN103559453AMeet encryption protection needsDoes not take up resourcesDigital data protectionComputer moduleEncryption decryption
The invention discloses a hardware encryption protection method and system for cellphone data. The hardware encryption protection method includes utilizing ID (identity) of a cellphone, IMEI (international mobile equipment identity) numbers of an SIM (subscriber identity module), SNs (serial numbers) of a storage chip and name of a source file as dynamic parameters, calling a key generating module and an AES (advanced encryption standard) encrypting and decrypting module to generate Keys for encryption and decryption by being matched with logic calculation; calling a hardware encrypting module to encrypt the file or data for the source file. The key generating module, the AES encryption and decryption module and the encryption and decryption module operate file storage equipment through the storage chip, data encryption and decryption are completed, and the storage chip is welded on a circuit board of the cellphone and provided with an independent core processor. The hardware encryption protection technology for the cellphone data overcomes the defects of the prior art, is free of system resource occupation, has high performance, safety and reliability, and can effectively meet the encryption protection requirements on important files of people.
Owner:深圳市中易通安全芯科技有限公司
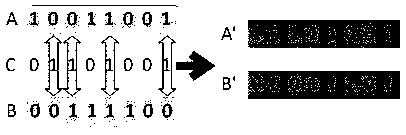
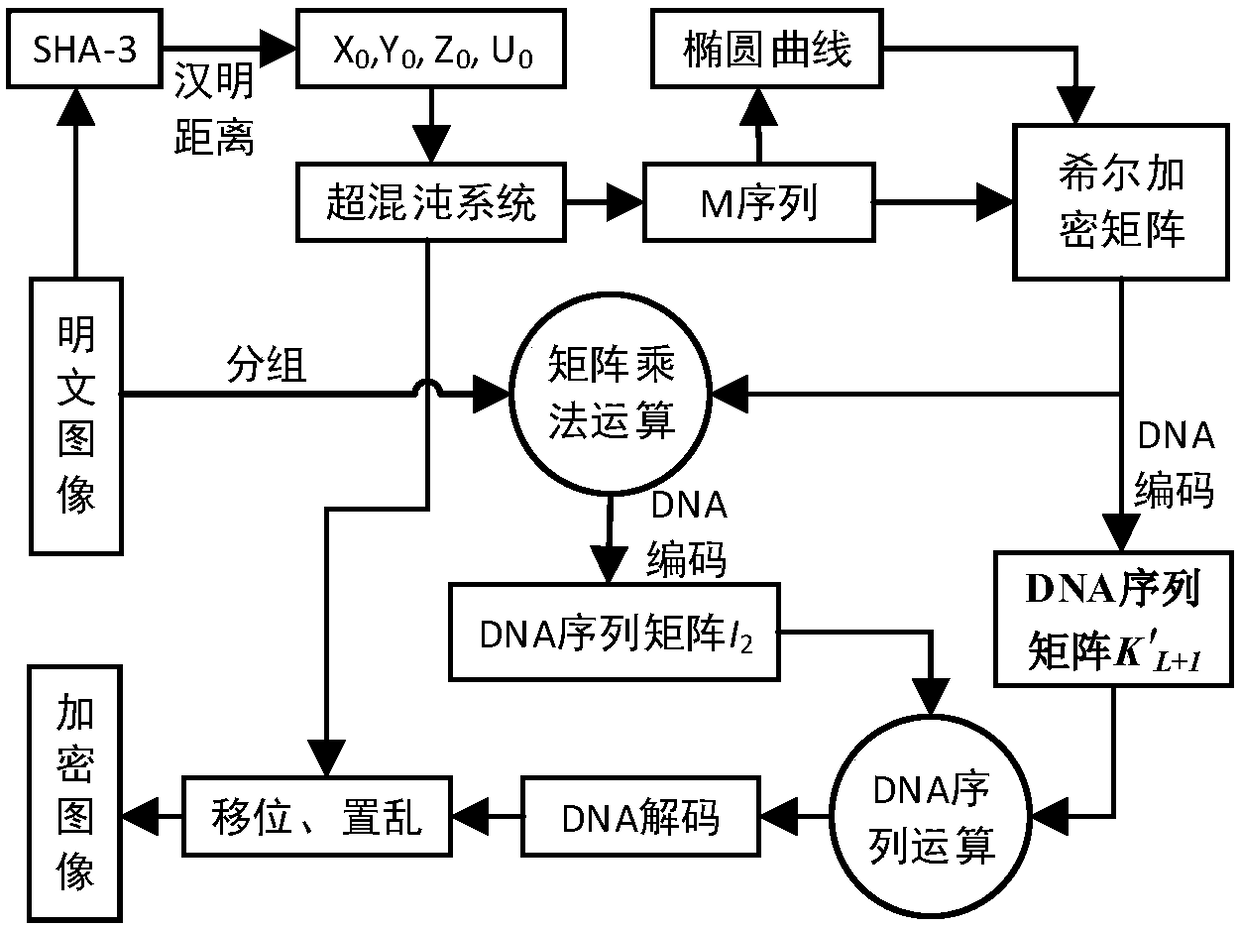
Hill encryption and dynamic DNA coding based image encryption method
ActiveCN108388808AAvoid complexityAvoid impossibilityPublic key for secure communicationDigital data protectionChosen-plaintext attackDna encoding
The invention discloses a hill encryption and dynamic DNA coding based image encryption method which is used for solving the problem that an existing image encryption algorithm is too complex and is liable to crack. The hill encryption and dynamic DNA coding based image encryption method is characterized in that a hill encryption matrix is constructed to perform replacement encryption on an imageby adopting a method combining a hyperchaotic system with an elliptic curve, so that strong dependency among elements is avoided, and complexity and difficulty in realizing of elliptic curve encryption are avoided, and therefore, the encryption algorithm is simple; a dynamic DNA coding rule is combined, and the coding rule is randomly selected according to different positions of pixels for performing DNA coding on the pixels, so that safety of the encryption algorithm is improved, and dependency among secret keys is reduced, therefore, a ciphertext is difficult to crack; and finally, a hyperchaotic sequence is used for scrambling the image. The hill encryption and dynamic DNA coding based image encryption method improves secret key sensibility, safety of transmitted data, further can effectively resist known plaintext and selected plaintext attack, has relatively good ability of resisting exhaustive attack, statistical attacks and differential attacks.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Electronic equipment, and identification system and decryption method thereof
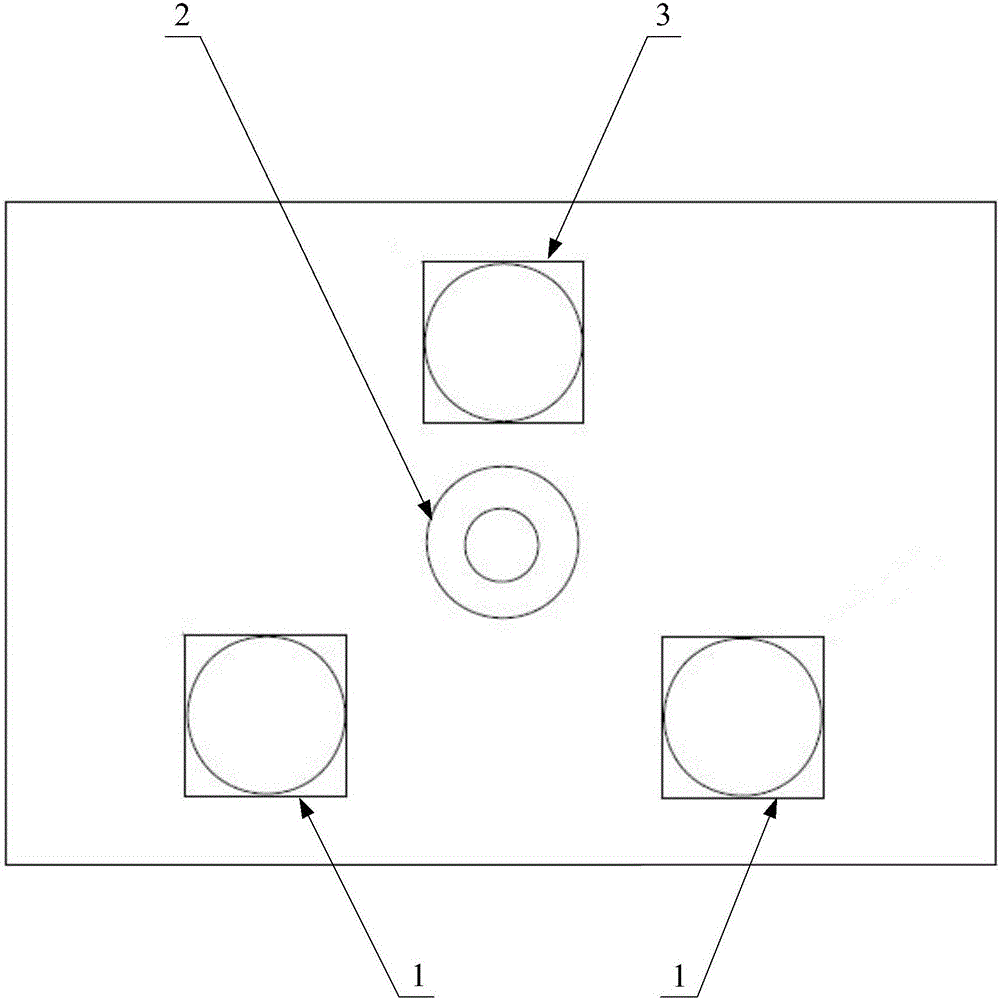
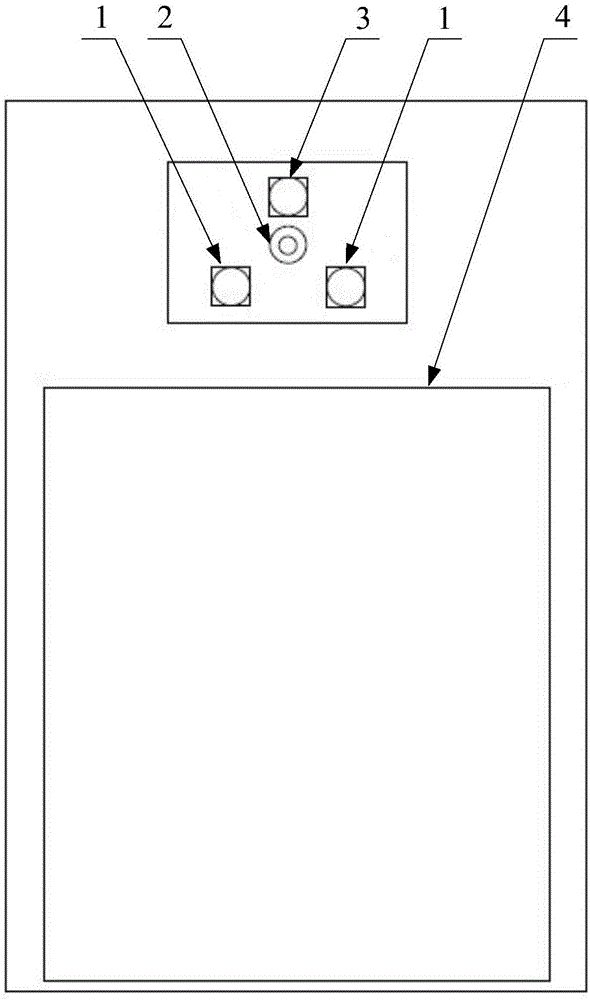
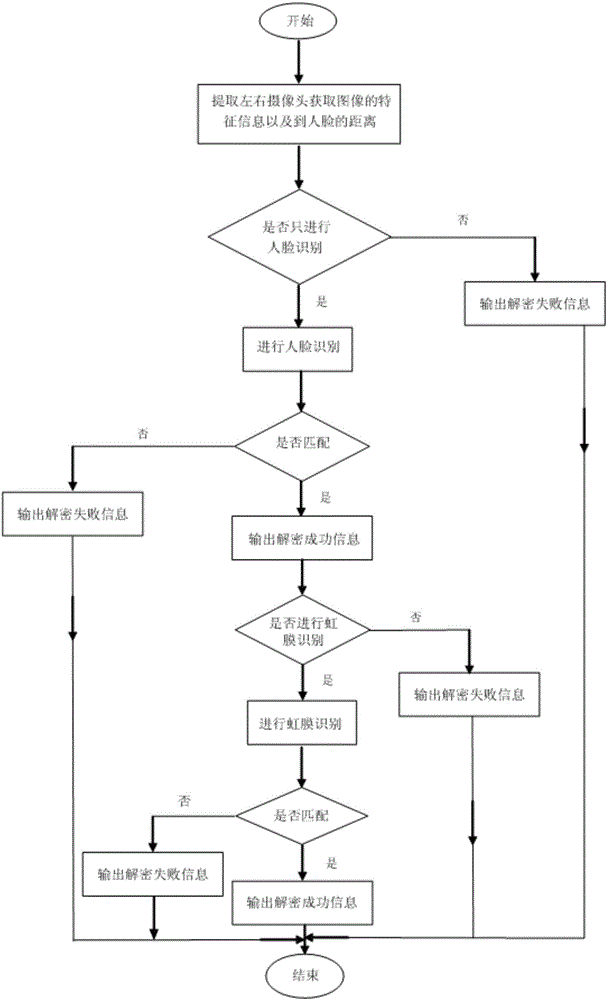
InactiveCN106485118ARealize 3D modelingImplement encryptionCharacter and pattern recognitionDigital data authenticationInfraredIris recognition
The invention discloses an identification system, which is used for being matched with a central processing unit of electronic equipment, so that three-dimensional modelling of a human face is realized. The identification system comprises multiple face shooting modules, an infrared light emitting device and an eye shooting module; the multiple face shooting modules are in signal connection with the central processing unit, and used for respectively shooting different parts of the human face, so that different facial information is obtained; the infrared light emitting device can emit infrared ray; and the eye shooting module is matched with the infrared light emitting device, and used for shooting eyes of a human, so that iris information is obtained. By means of the identification system provided by the invention, acquisition of three-dimensional information of a face can be realized through the multiple face shooting modules 1; furthermore, an iris identification manner is combined; compared with the manner of only acquiring two-dimensional information of the face by using a single camera, the security reliability and the robustness of the electronic equipment are relatively high; and the privacy of users can be protected more safely. The invention further relates to the electronic equipment having the identification system, and a decryption method for decrypting the electronic equipment.
Owner:TRULY OPTO ELECTRONICS
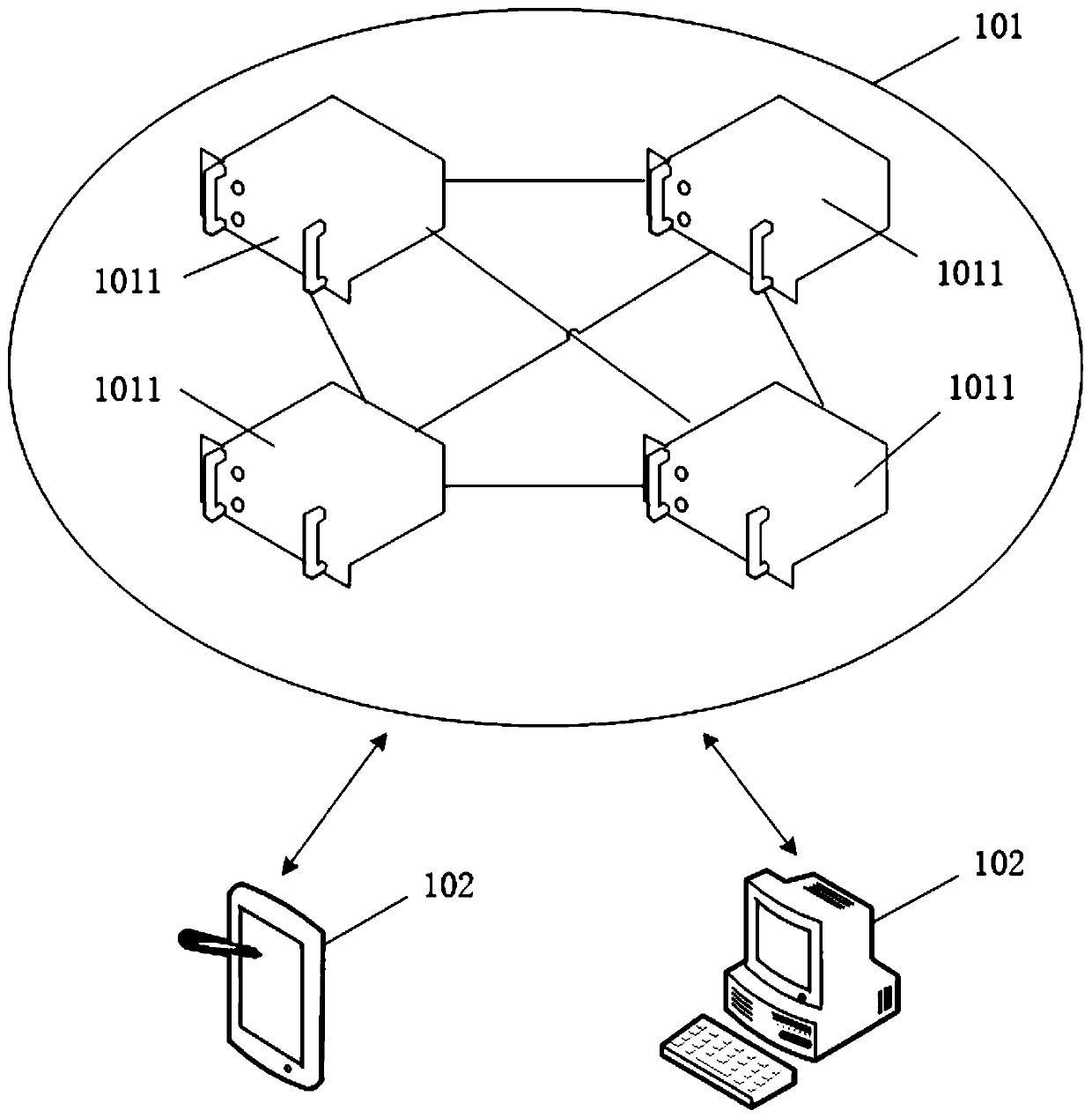
Method for achieving data security communication by applying blockchain encryption technology
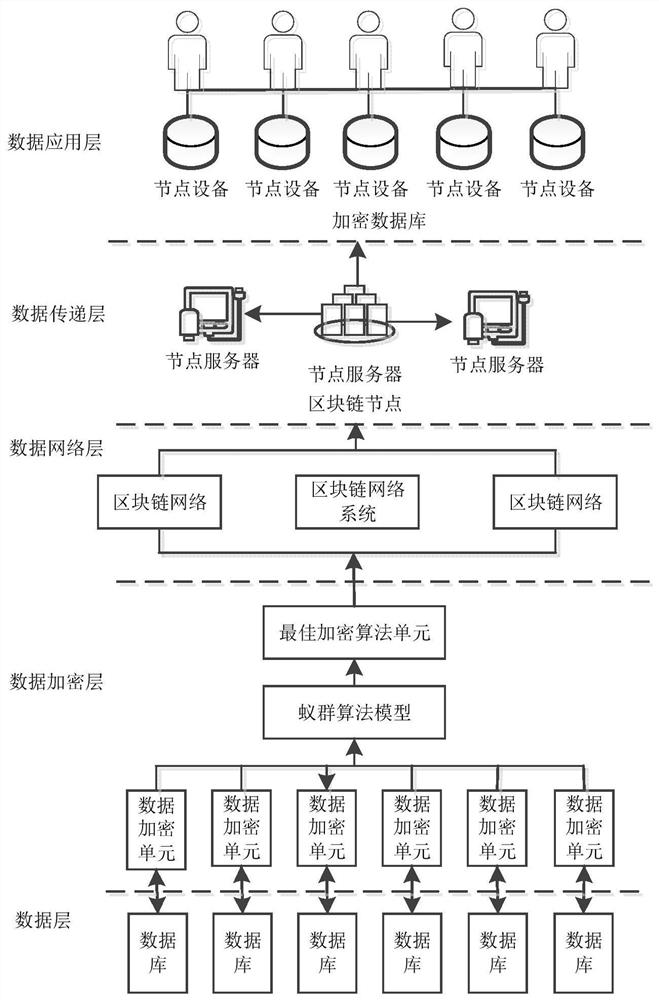
PendingCN111654364AAchieve deliveryAchieve sharingDatabase management systemsData stream serial/continuous modificationData transmissionInteraction device
The invention discloses a method for achieving data security communication by applying a blockchain encryption technology, and relates to the technical field of data encryption. According to the invention, a secure communication system comprising a data layer, a data encryption layer, a data network layer, a data transmission layer and a data application layer is constructed; a block chain technology is integrated into data communication, safe transmission of data is realized, the transmitted data can be shared and cannot be tampered, the encryption performance of the data is improved, remote,online and real-time acquisition and application of the data can be achieved through systematic construction, and a user can achieve application, management and monitoring of database data without going to the site personally. According to the invention, the ant colony algorithm is adopted; according to the characteristics of data communication and the requirements of interaction equipment, the optimization search of the encryption algorithm is carried out among the plurality of encryption units, so that a user can quickly find out the optimal value of the target data suitable for applicationfrom the plurality of encryption algorithms, and the efficiency and the data management capability of the encryption unit application algorithm are greatly improved.
Owner:重庆知翔科技有限公司
Image encryption method based on three-dimensional composite scrambling model and chaos
ActiveCN111031193AImprove encryptionImprove securitySecuring communication by chaotic signalsPictoral communicationAlgorithmTheoretical computer science
The invention discloses an image encryption method based on a three-dimensional composite scrambling model and chaos, which belongs to the field of information encryption and aims at solving the increasingly severe problem of current network transmission security and protecting network interaction image content. In combination with bit plane decomposition, piecewise linear chaotic mapping, two-dimensional zigzag transformation and other technologies, a three-dimensional composite scrambling model is established on the basis of defining block built-in scrambling and block scrambling. Pixel scrambling is carried out on an original image by using the model, and diffusion operation is carried out on the scrambled image by using a mature hyper-chaotic system and exclusive-OR operation to obtainan encrypted image. Experiments show that the algorithm is good in encryption effect, high in security and efficient.
Owner:CHINA UNIV OF MINING & TECH
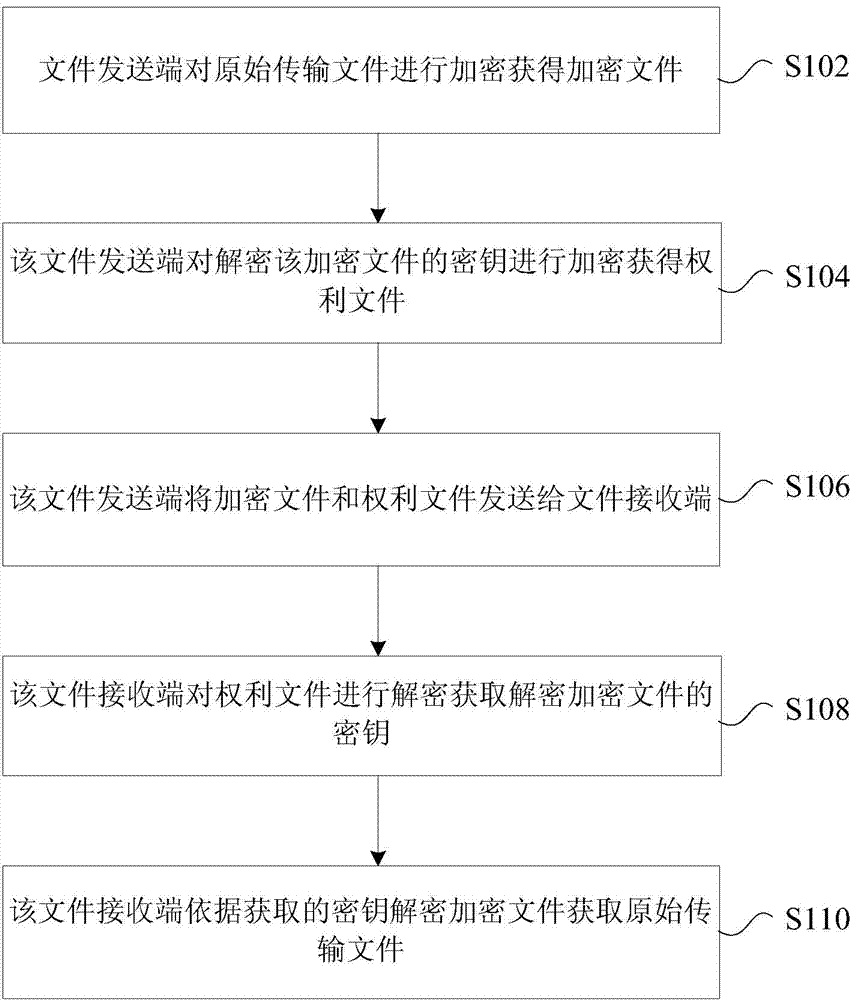
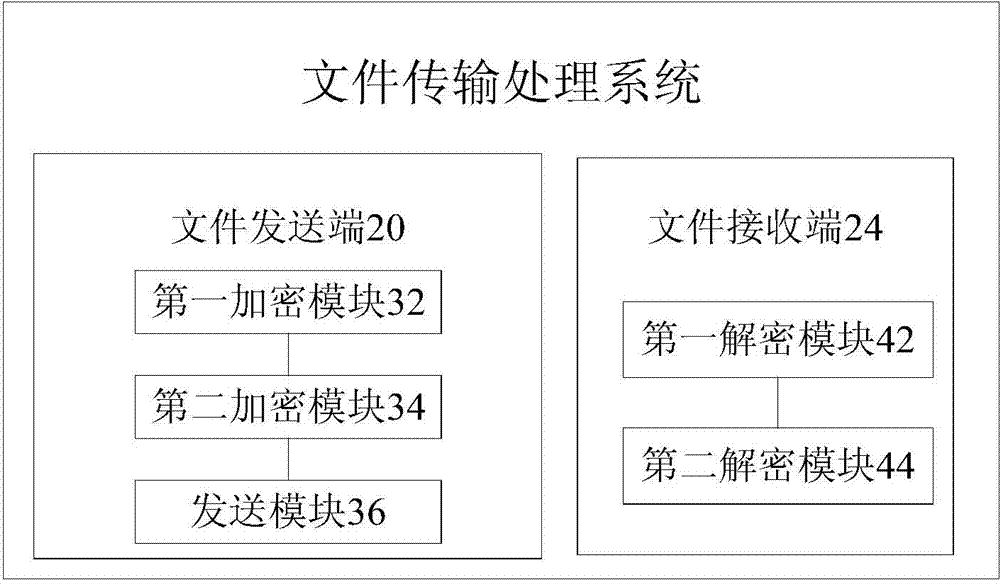
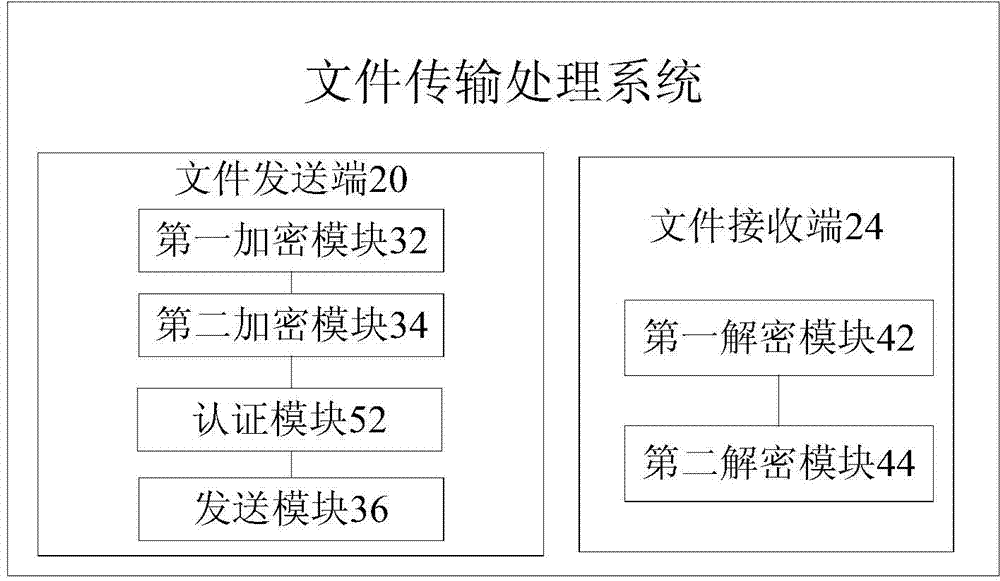
File transfer processing method and system and terminals
ActiveCN104243439AImprove encryptionEasy to useSecuring communicationInternet usersComputer terminal
The invention provides a file transfer processing method and system and terminals. The method includes the steps that the file transmitting terminal encrypts an original transfer file to obtain an encrypted file; the file transmitting terminal encrypts a secret key for decrypting the encrypted file to obtain an entitlement file; the file transmitting terminal transmits the encrypted file and the entitlement file to the file receiving terminal; the file receiving terminal decrypts the entitlement file to obtain the secret key for decrypting the encrypted file; the file receiving terminal obtains the original transfer file by decrypting the encrypted file according to the obtained secret key. Due to the file transfer processing method, the problem that in the related technology, a large safety problem exists when private files of an Internet user are applied is solved, and the effects of high encryption performance, convenient use and low safety cost are achieved.
Owner:DATANG NETWORK CO LTD
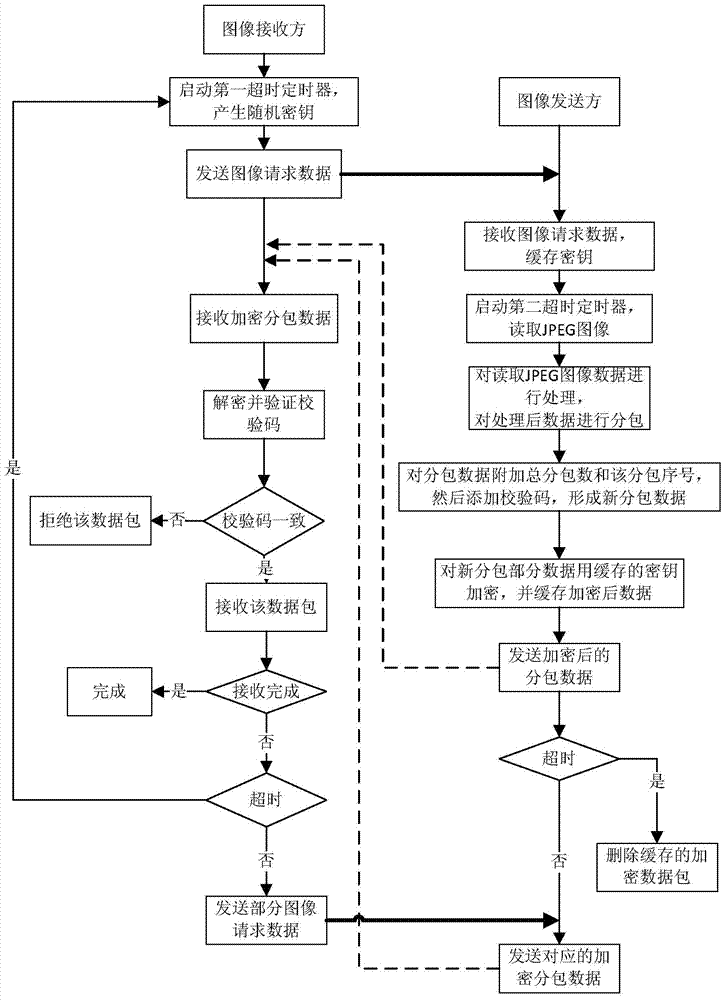
JPEG image encryption transmission method
ActiveCN103581683AImprove encryptionSmall amount of calculationDigital video signal modificationComputer hardwareImage transfer
The invention relates to a JPEG image encryption transmission method. The method is characterized by comprising the steps that an image receiver and an image sender establish a safety channel and an image transmission channel, the image receiver sends image request data to the image sender through the safety channel, after the image sender receives the image request data, a time-out mechanism is started to read corresponding JPEG image data and process the corresponding JPEG image data, after being processed, the JPEG image data are subpackaged, then encrypted and sent to the image receiver, after receiving the data, the image receiver conducts decryption on the data, the image receiver does not receive the complete image data, an image data request of the missing portion is sent in the time-out mechanism, and the image sender transmits some encrypted and subpackaged data before the time-out mechanism. The method has the advantages of being capable of efficiently conducting encryption transmission on JPEG images, and achieving safe and reliable JPEG image transmission through the smaller amount of calculation and smaller amount of network data transmission.
Owner:NINGBO HAIBO GRP CO LTD
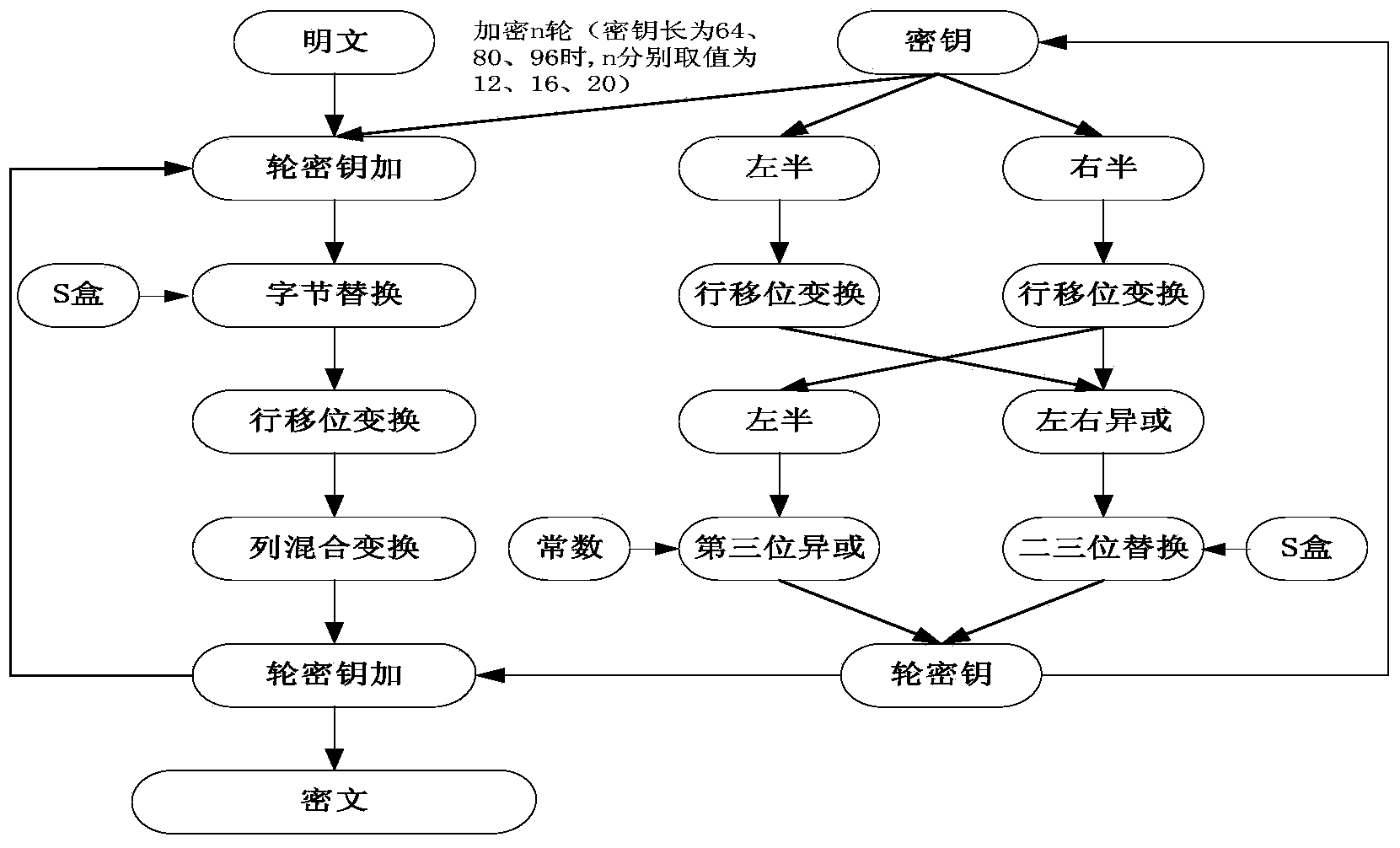
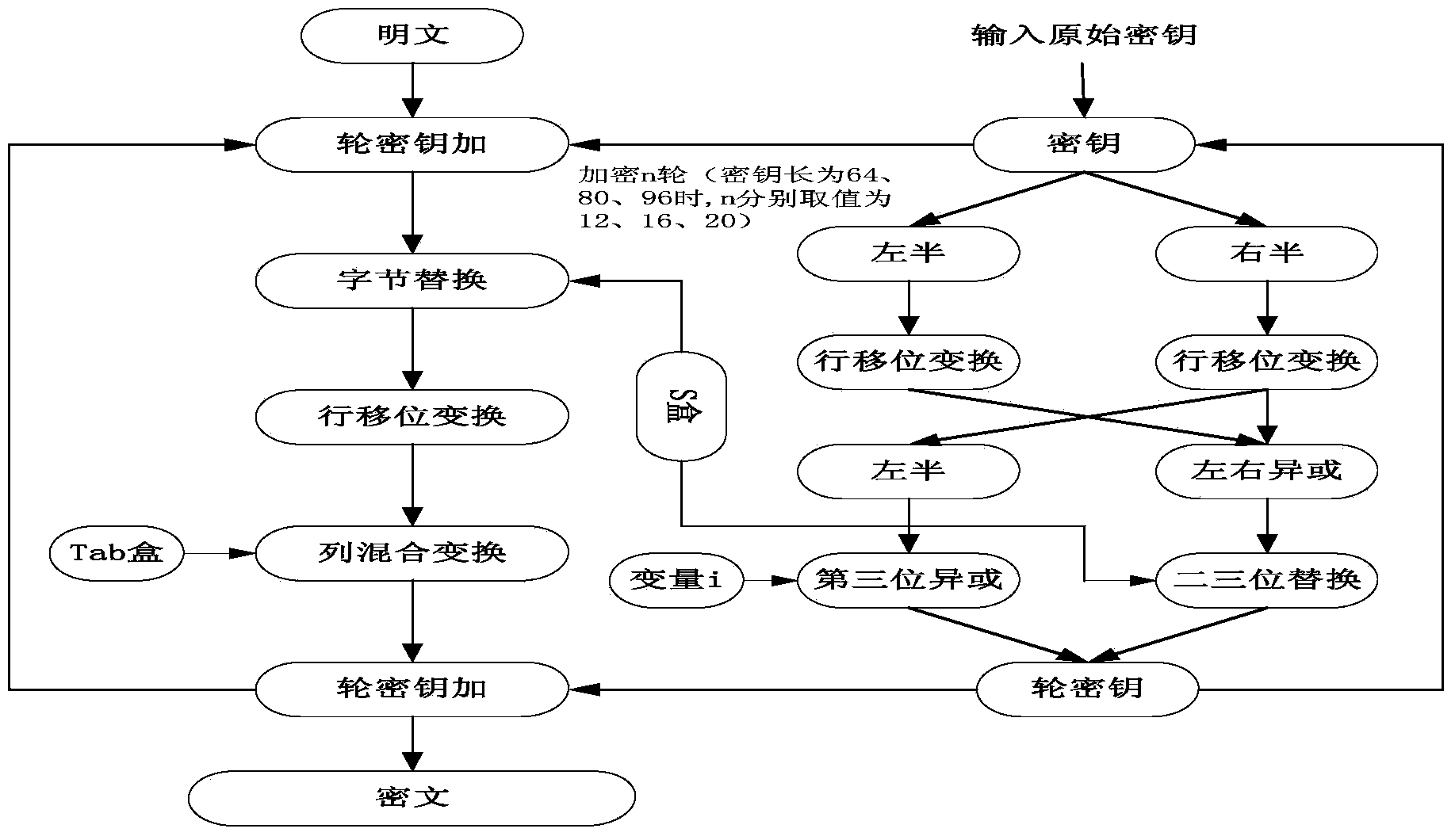
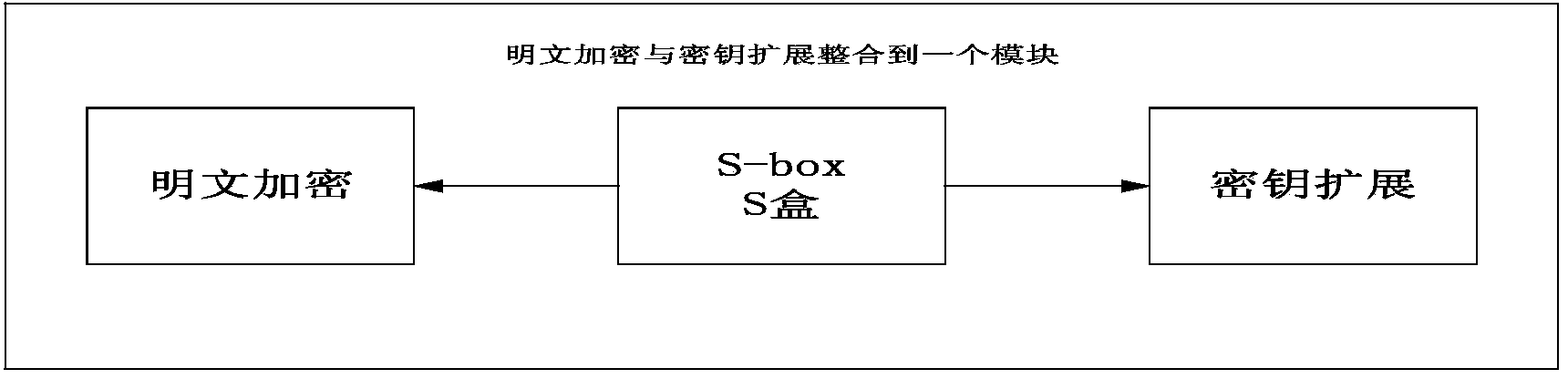
KLEIN encryption implementation method based on area and performance balanced optimization
ActiveCN103684749AImprove parallelismFast encryptionEncryption apparatus with shift registers/memoriesS-boxByte
The invention discloses a KLEIN encryption implementation method based on area and performance balanced optimization. The method includes: optimizing an S box, allowing two modules to share the S box, building a Tab box for fast table look-up, allowing key expansion round constant i to be in a self-adding manner, encapsulating and integrating round key adding, byte substitution, row shifting, line mixing, and key expansion sub-modules into one module, using continuous assignment statement to realize algorithm assignment, updating a clock signal control counter, using Verilog HDL (hardware description language) parallel execution features and the manner integrating the sub-modules into one module, using global synchronization clock pulse triggering, and fully utilizing the device trigger and wiring resources. By the method, the area resource occupation required by implementing the KLEIN encryption algorithm can be saved effectively, encryption speed is increased, and the KLEIN encryption algorithm can be implemented with low hardware area and keep high performance.
Owner:HENGYANG NORMAL UNIV
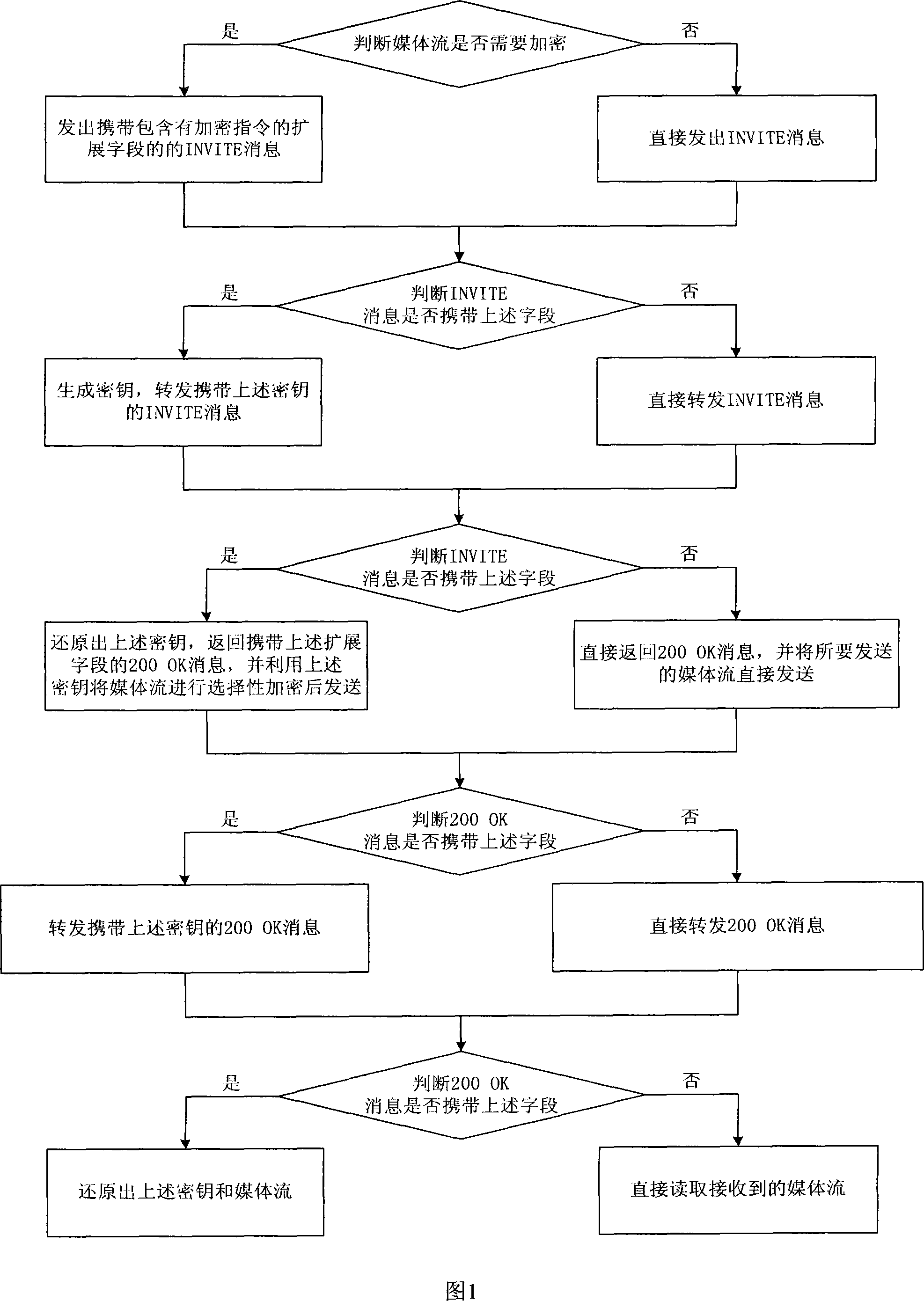
Media stream transmission method
ActiveCN101102463ASecure encrypted transmissionImprove data securityAnalogue secracy/subscription systemsEncryption
The method comprises: the first terminal decides if the media stream needs to be encrypted, and sends a session starting request carrying an expanded field, or directly sends out the session starting request; the control platform decides if the session starting request carries the expanded field, and generates a key, and relays the session starting request with the key, or directly relays the session starting request; the second terminal decides if the session starting request carries the expanded field, and restores the key, and returns the response carrying the expanded field, and uses the key to make a selectable encryption for the media stream, or directly returns the response and directly sends out the media stream; the control platform decides if the response message carries the expanded filed, and relays the response message carrying the key, or directly relays the response message; the first terminal decides if the response message carries the expanded field, and restores the key and media stream, or directly reads the media stream.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
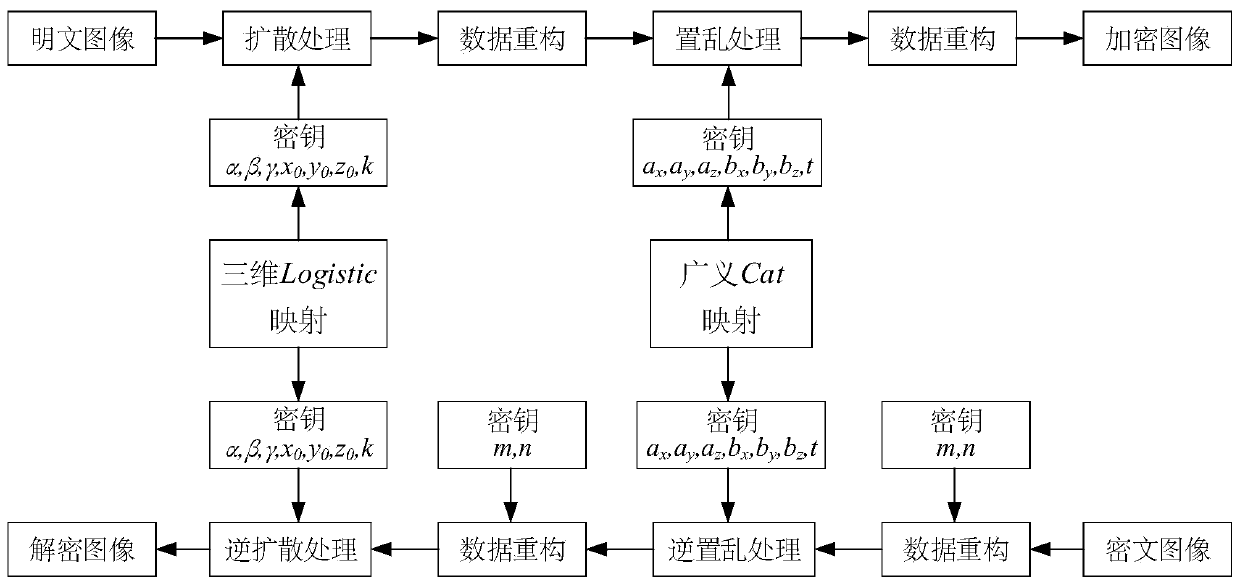
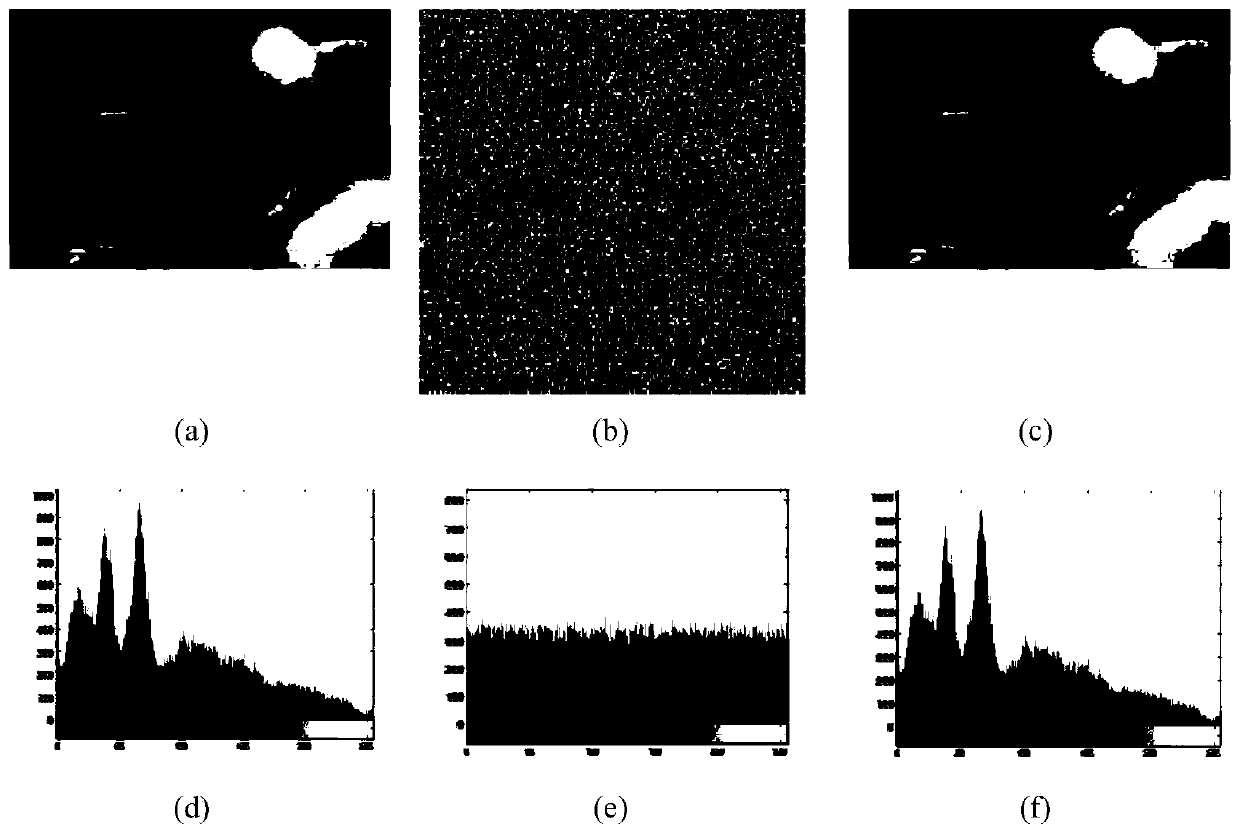
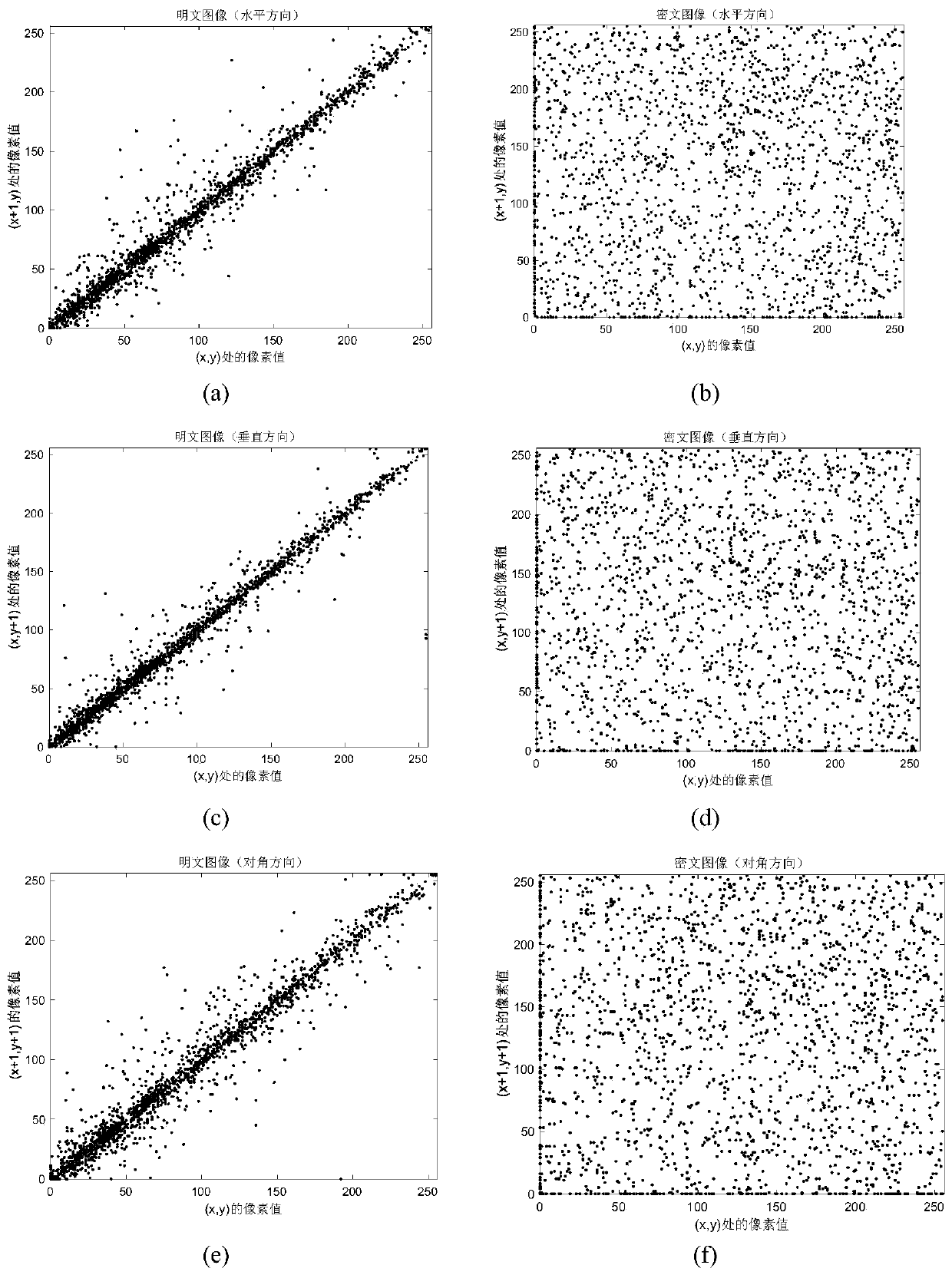
Color image encryption method based on three-dimensional Logistic mapping and generalized Cat mapping
The invention provides a color image encryption method based on three-dimensional Logistic mapping and generalized Cat mapping, which comprises the following steps: reading an original color image toobtain two-dimensional pixel matrixes corresponding to R, G and B components, and straightening the two-dimensional pixel matrixes to obtain three pixel sequences; three groups of chaotic sequences are generated through three-dimensional Logistic mapping iteration, and subjecting the three groups of chaotic sequences and the three pixel sequences to XOR operation to realize diffusion processing; carrying out data reconstruction on the chaotic sequence obtained after diffusion processing and expanding the chaotic sequence into a three-dimensional cube; performing position scrambling processingon the three-dimensional cube through generalized Cat mapping; and converting the three-dimensional cube with the scrambled position into a cuboid which is a ciphertext image. According to the method,parameters and initial values of three-dimensional Logistic mapping and generalized Cat mapping and the plaintext image size are used as keys, the key space is increased. Encryption safety is improved, and the method has the advantages of being high in key sensitivity, high in anti-attack capability and the like.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
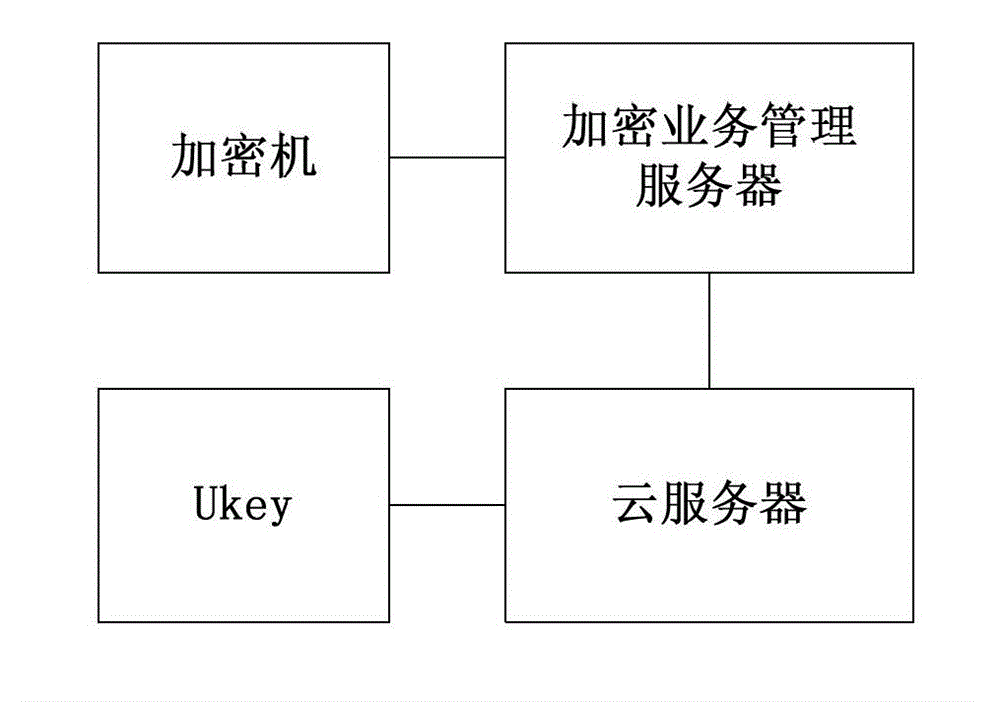
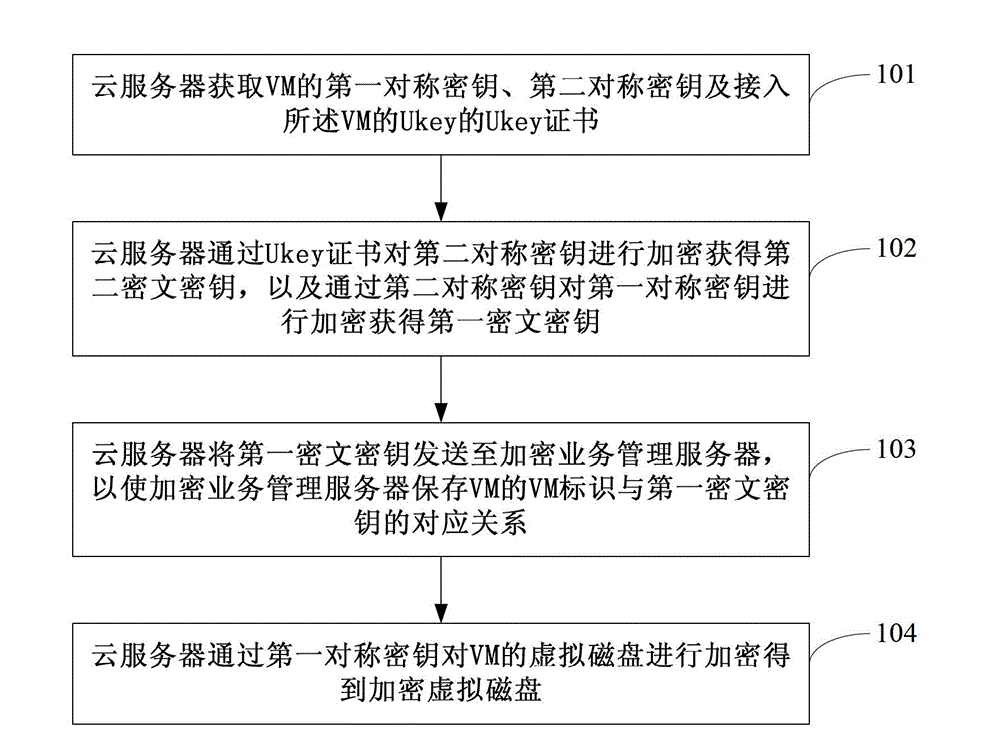
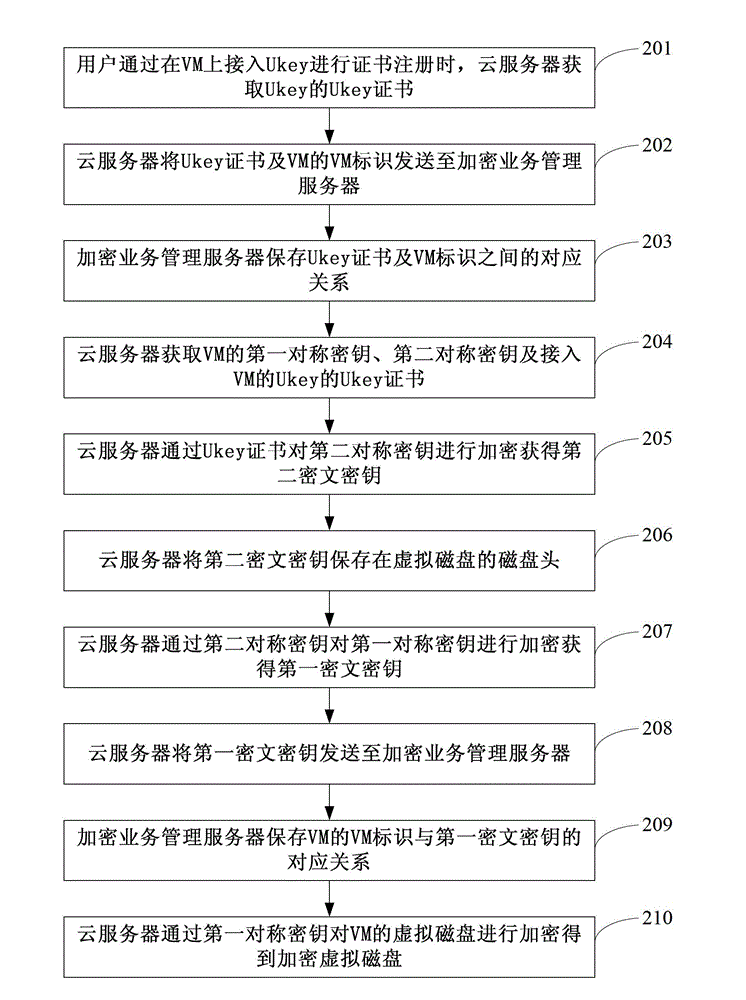
Encryption method, decryption method, encryption device and decryption device of virtual disk and cloud server
ActiveCN102984273AIncrease flexibilityImprove encryptionKey distribution for secure communicationUser identity/authority verificationDisk encryptionVirtual machine
The invention discloses an encryption method, a decryption method, an encryption device and a decryption device of a virtual disk and a cloud server. The encryption method comprises the steps that the cloud server acquires a first symmetric key and a second symmetric key of a VM (virtual machine) and a Ukey (user key) certificate of a Ukey accessed to the VM; the cloud server acquires a second ciphertext key by encrypting the second symmetric key through the Ukey certificate and acquires a first ciphertext key by encrypting the first symmetric key through the second symmetric key; the cloud server sends the first ciphertext key to an encryption service management server; and the cloud server encrypts the virtual disk of the VM through the first symmetric key to obtain an encrypted virtual disk. Encryption of the virtual disk of the VM is realized by interaction among the cloud server, the encryption service management server and the Ukey; and as different keys are separately managed by the cloud server, the encryption service management server and the Ukey, the encryption performance and encryption safety are improved.
Owner:HUAWEI TECH CO LTD
Method for generating two-dimensional code with online bank information based on current system time
ActiveCN104636783AWith encryptionImprove encryptionRecord carriers used with machinesOperational systemEncrypted function
The invention provides a method for generating a two-dimensional code with online bank information based on current system time. The method comprises the following steps of inputting the online bank information in an information input interface of a two-dimensional code generating interface, and converting the inputted online bank information, so as to obtain a corresponding first serial number; according to the current display time of an operation system implanted with the two-dimensional code generating interface, calling an algorithm to perform at least one encrypting operation on the serial number, so as to generate a second serial number; sequencing the first serial number and the second serial number, so as to form a serial number group; inputting the serial number group into the two-dimensional code generating interface, so as to generate the two-dimensional code corresponding to the serial number group. The method has the advantages that the corresponding encrypting method is called through the current system time, so the two-dimensional code with the encrypting function is generated according to the inputted online bank information in the two-dimensional code generating interface.
Owner:苏州智高嘉华科技有限公司
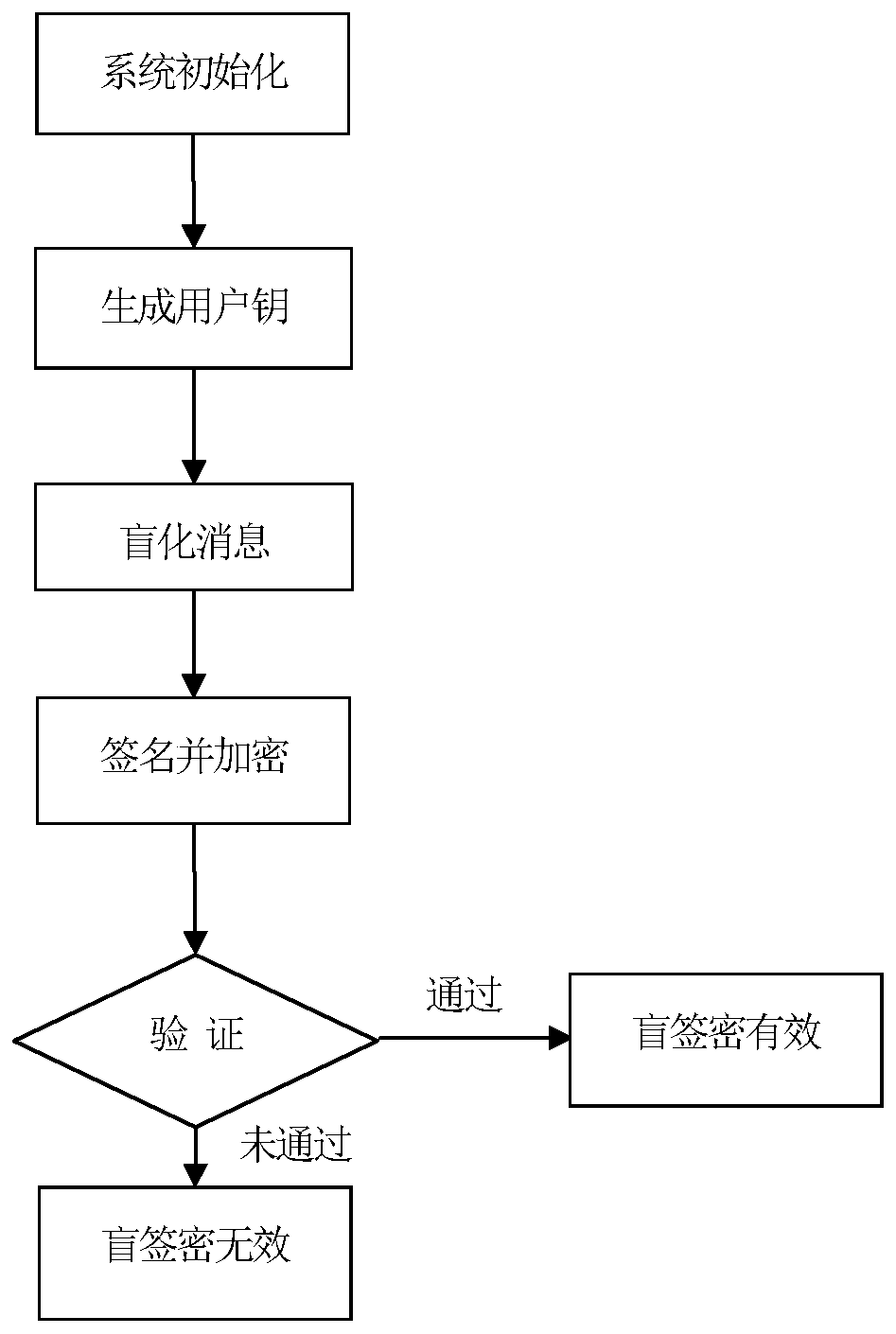
Blind signcryption method under lattice public key cryptosystem
ActiveCN110138543AHigh efficiency of blind signcryptionImprove encryptionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordEncrypted function
The invention discloses a blind signcryption method under a lattice public key cryptosystem. The blind signcryption method is characterized by comprising the steps of system initialization, user key generation, message owner blinding message, user signature, encryption and verification. According to the invention, by referencing a blind signcryption and lattice password method under a traditionalpassword system, a lattice-based post-quantum blind signcryption method is constructed, so that the blind signcryption efficiency is higher than the efficiency of blind signature before encryption, compared with a lattice-based blind signature method, an encryption function is added, and relative to a blind signcryption method under the assumption of finite field discrete logarithm and elliptic curve discrete logarithm, due to the fact that the blind determination message Mu is added in the signcryption scheme, the blind function is added, the signcryption has anonymity, the privacy of a message owner is effectively protected, the quantum attack can be resisted, the calculation efficiency is higher, and the method can be used for the technical field of electronic signcryption.
Owner:XIAN UNIV OF POSTS & TELECOMM
Encryption apparatus, decryption apparatus, and authentication information assignment apparatus, and encryption method, decryption method, and authentication information assignment method
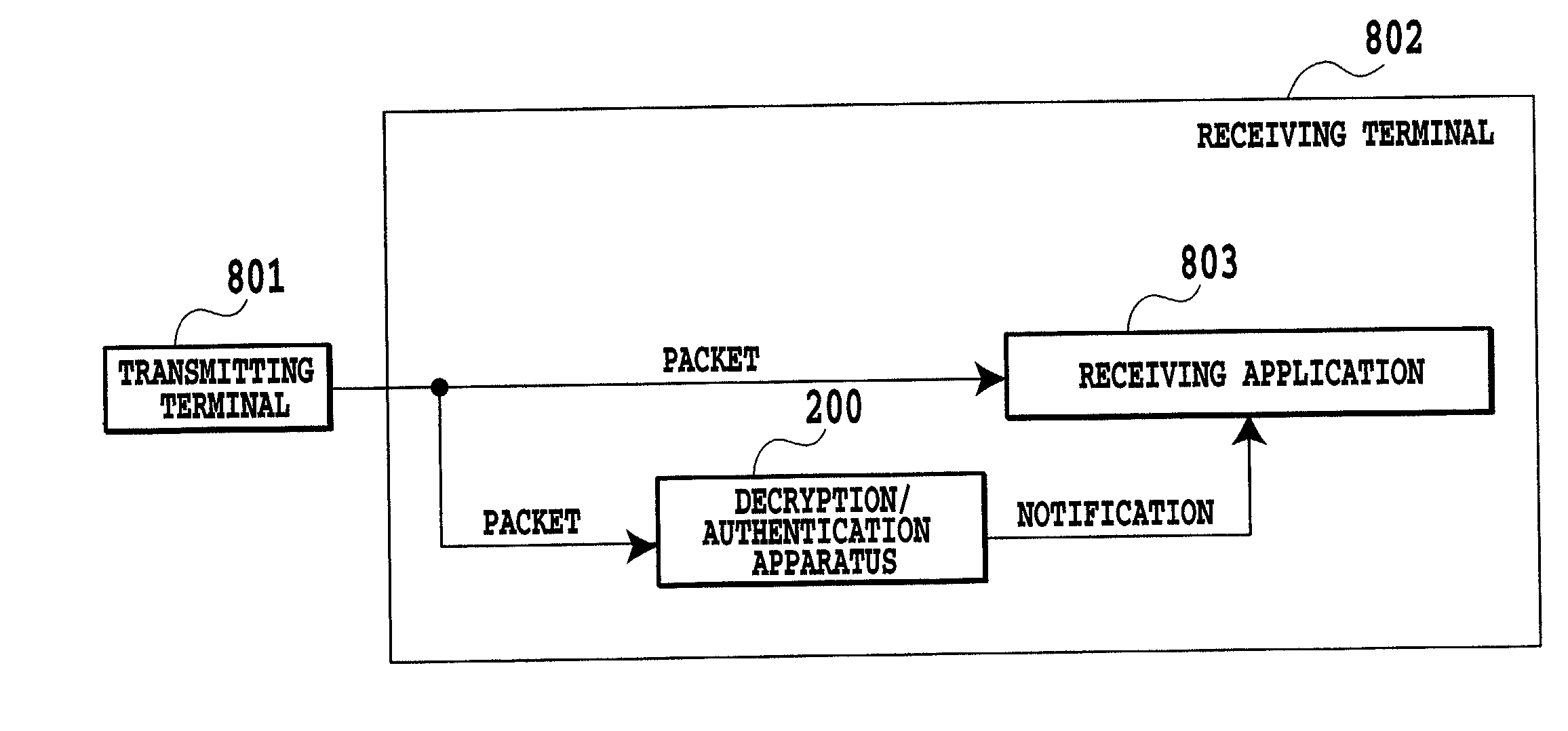
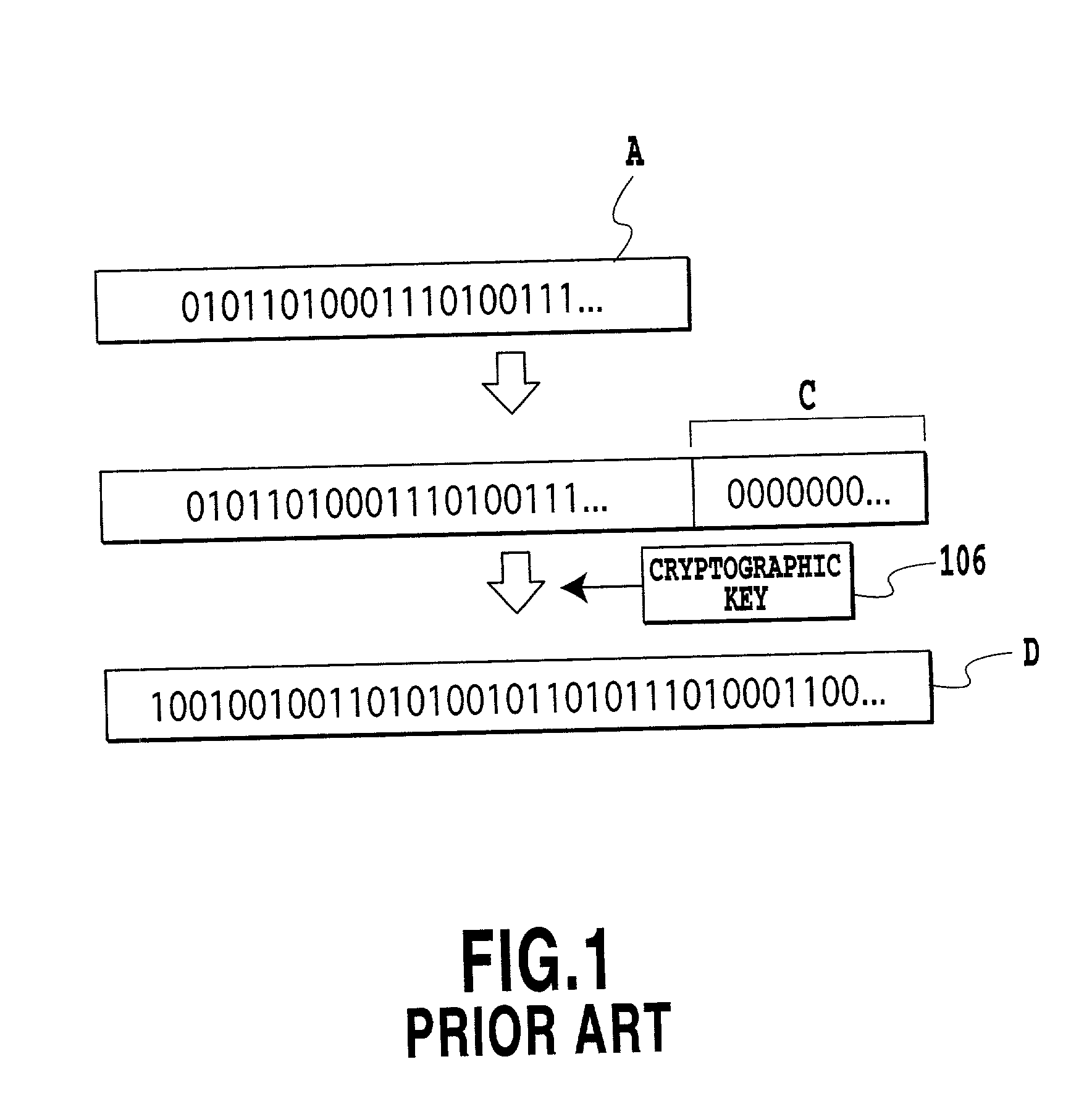
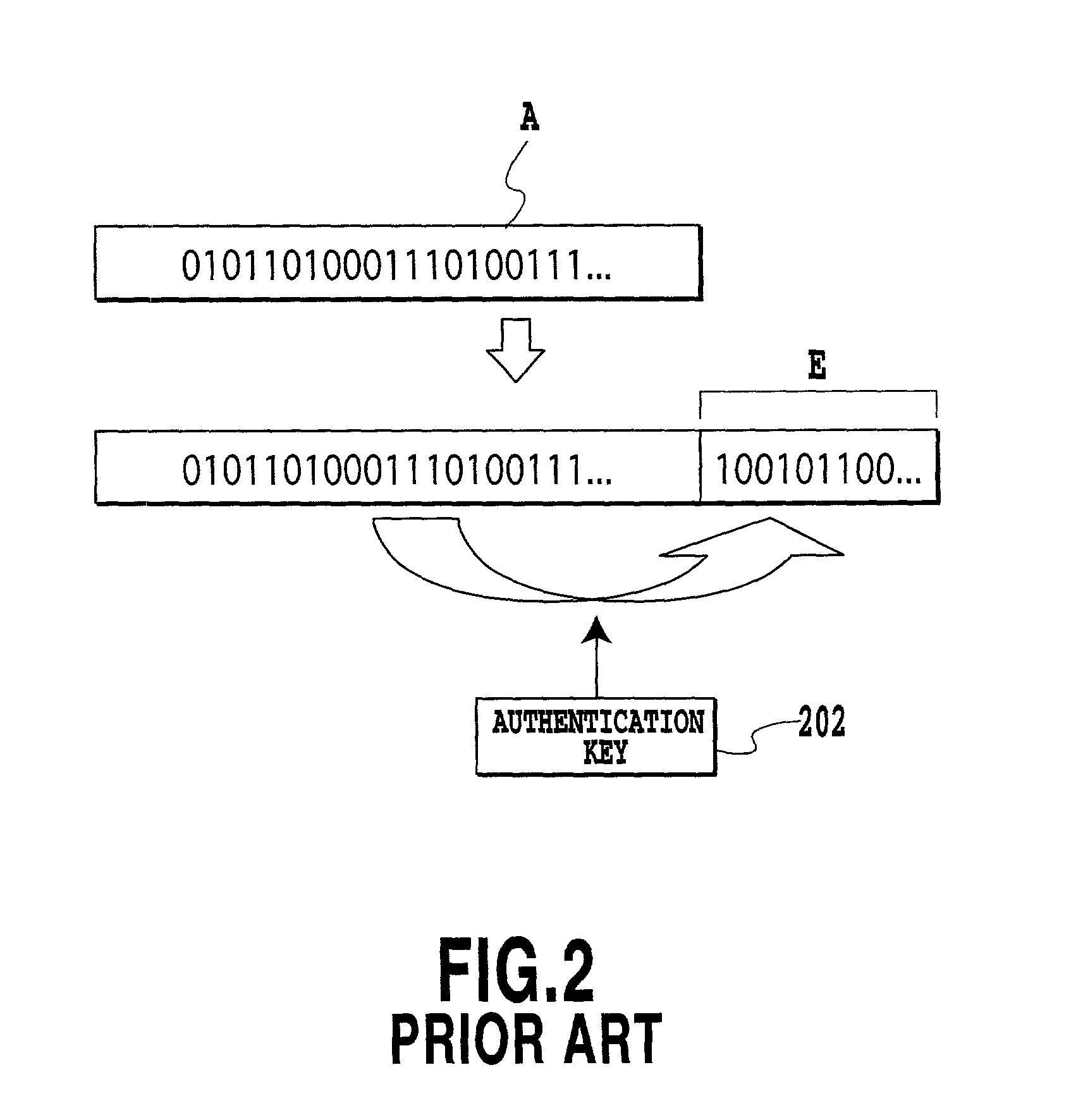
InactiveUS20020118828A1Reduce overheadImprove encryptionData stream serial/continuous modificationMultiple keys/algorithms usageAssignment methodsComputer hardware
An encryption apparatus and an encryption method are provided which can prevent a cryptographic key or authentication key from being broken. A voice stream is transmitted from a transmitting terminal to a receiving terminal. A bit stream of the voice stream includes speech bursts and speech pauses. Although the speech bursts are encrypted or provided with authentication information, the speech pauses are not encrypted or provided with authentication information, and are transmitted without change. Thus carrying out the encryption or the assignment of the authentication information selectively in accordance with the type of the bit stream makes it possible to prevent the cryptographic key or authentication key from being broken. Besides, it can reduce the processing amount of the encryption or authentication process, thereby being able to limit an increase in the information amount.
Owner:NTT DOCOMO INC
Memory chip with encryption function and anti-piracy method
InactiveCN102289625ALow costReduce workloadInternal/peripheral component protectionComputer hardwareMemory chip
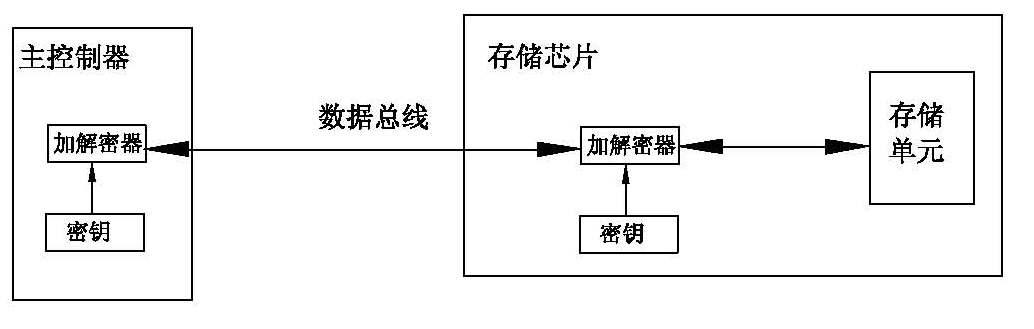
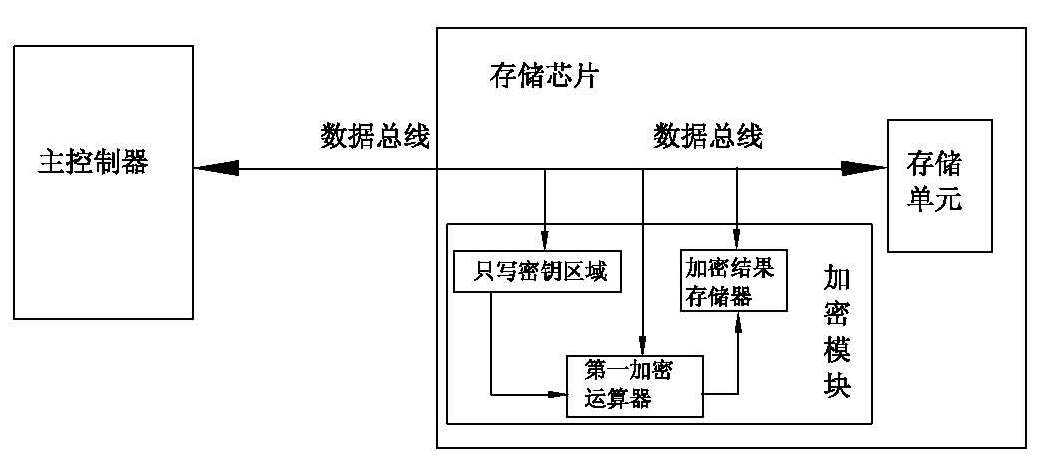
The invention discloses a storage chip with encryption function and an anti-piracy method. The storage chip includes a data bus and a storage unit, and also includes an encryption module connected in parallel with the storage unit on the data bus; the encryption module includes a write-only key area , a first encryption operator and an encryption result memory; the write-only key area is preset with a first key; the first encryption operator is used to calculate the first encryption by encryption operation according to the first key and the encrypted original text Ciphertext; the encryption result memory is used to store the first encrypted ciphertext; the storage unit includes a second key and a second encryption operator. The storage chip of the present invention does not require special design on the hardware, and does not require additional hardware drivers on the software, which reduces the cost and the workload of development, and does not change the hardware circuit board and underlying hardware drivers for existing systems without encryption functions. The only way to increase the encryption function under the premise of the program.
Owner:方波
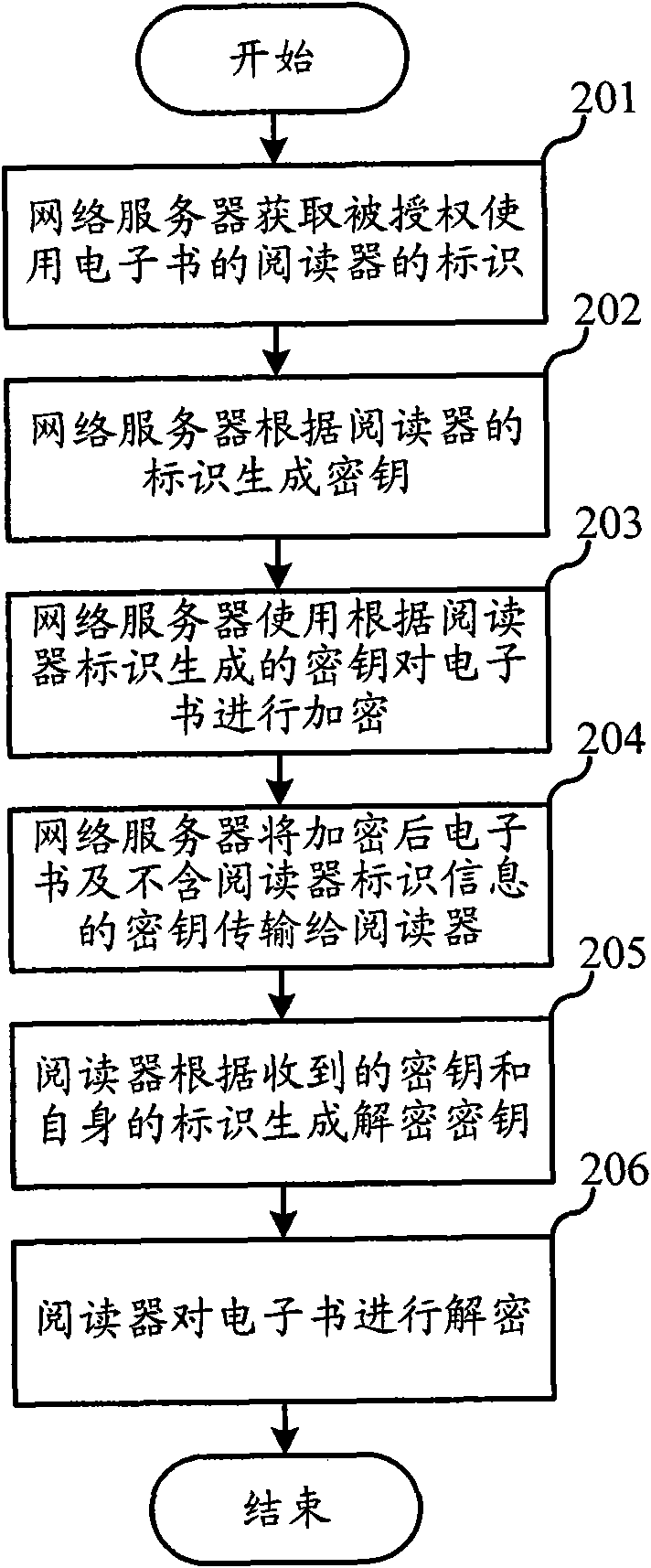
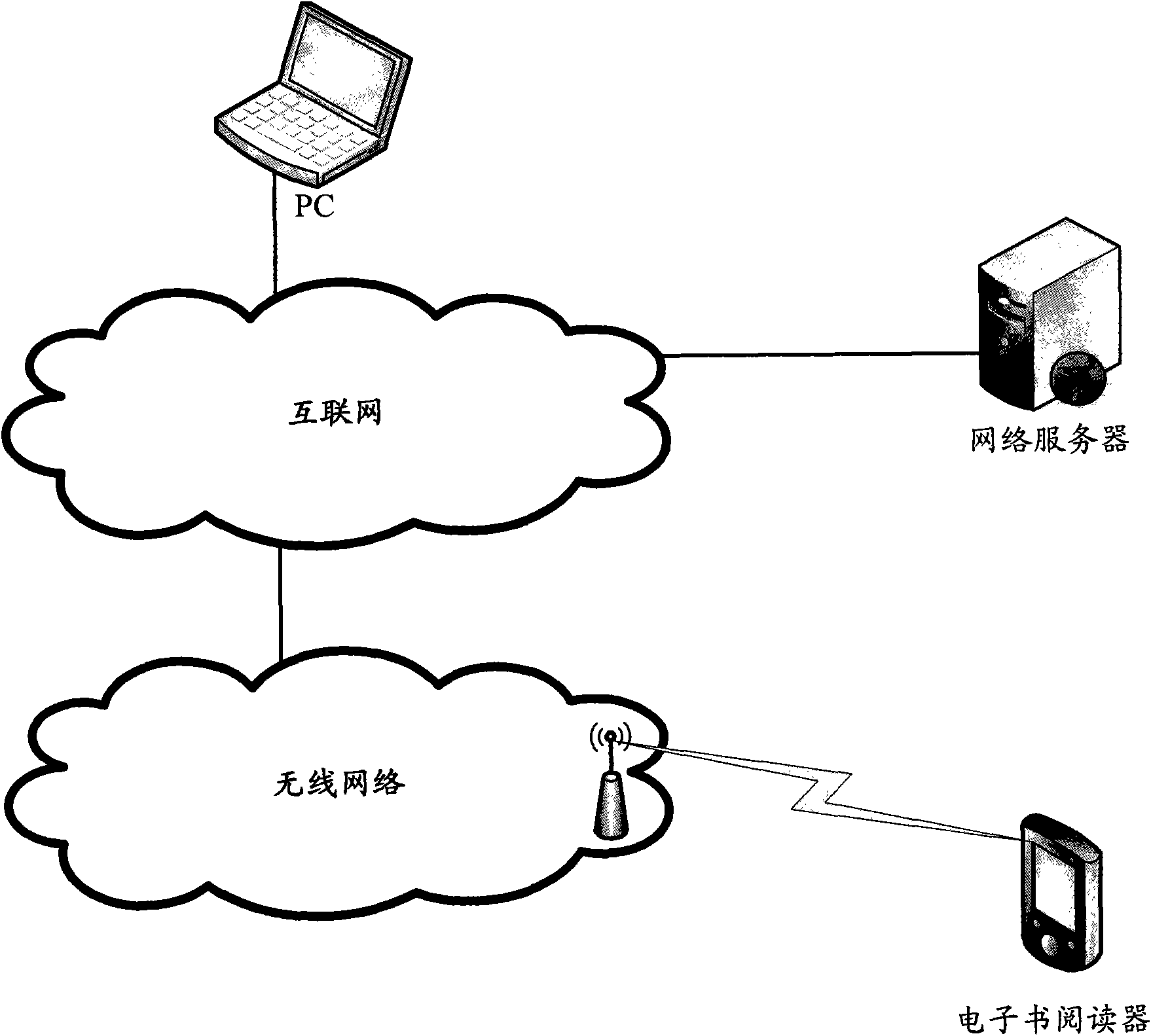
Electronic book downloading method and purchasing system
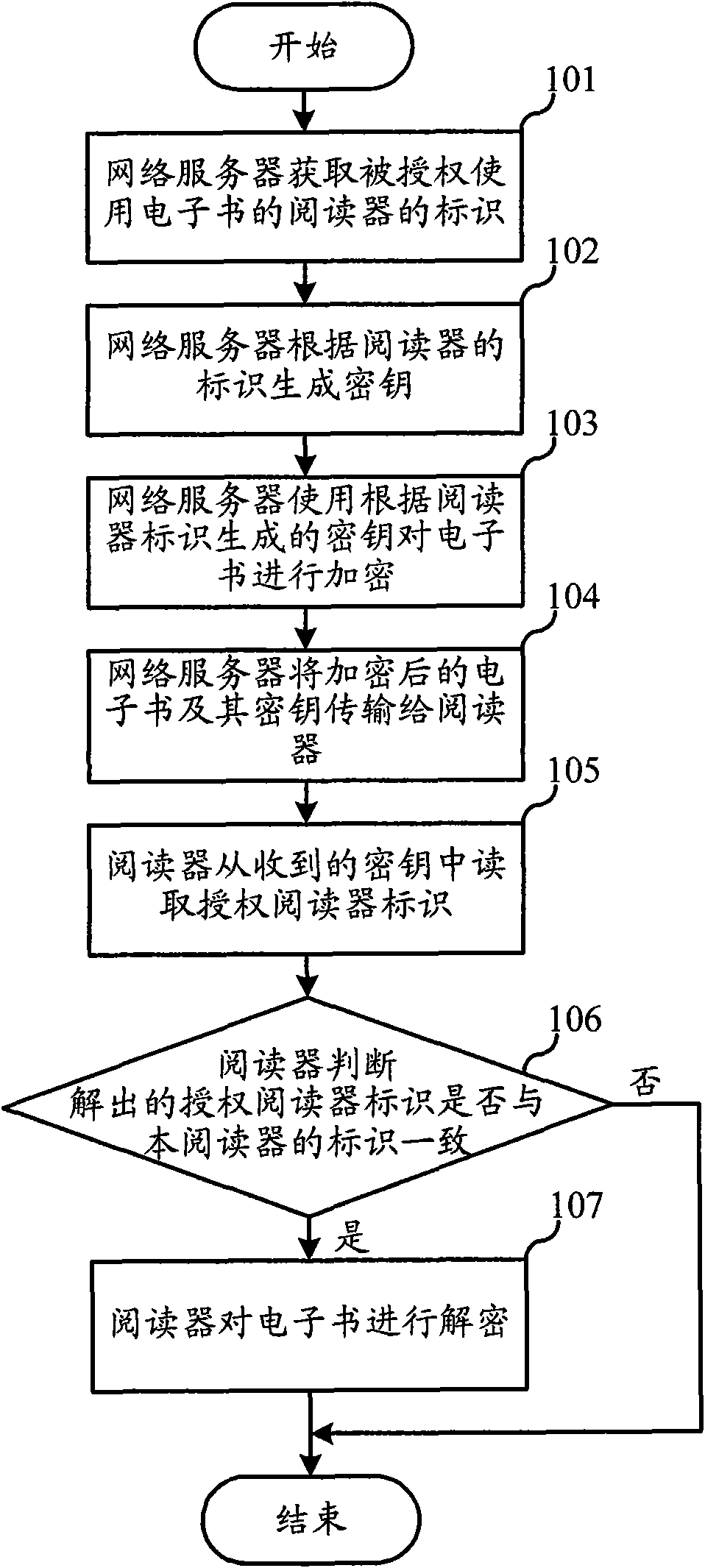
InactiveCN101894222AWill not copyNo piracyEncryption apparatus with shift registers/memoriesProgram/content distribution protectionElectronic bookPurchasing
The invention relates to the field of electronic book distribution and discloses an electronic book downloading method and a purchasing system. In the invention, a key is generated according to the mark of a reader, thus, an encrypted electronic book can only be decrypted by the appointed reader, thereby protecting the downloaded electronic book from being copied and pirated. Before the decryption of the reader, the mark of the authorized reader is read from the key and compared with the mark per se, and the electronic book is decrypted when both the marks are consistent, thereby preventing the electronic book from being decrypted by the unauthorized reader.
Owner:扬州易狄欧电子科技有限公司
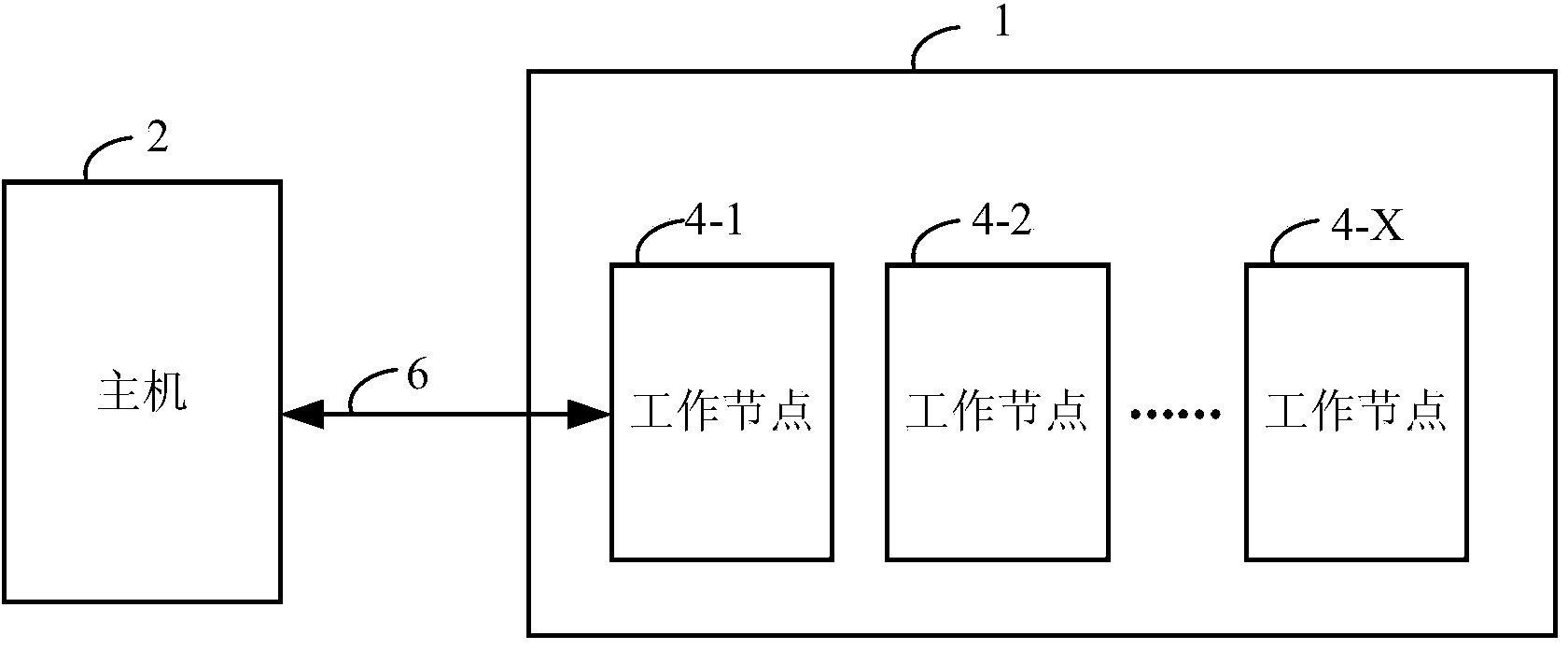
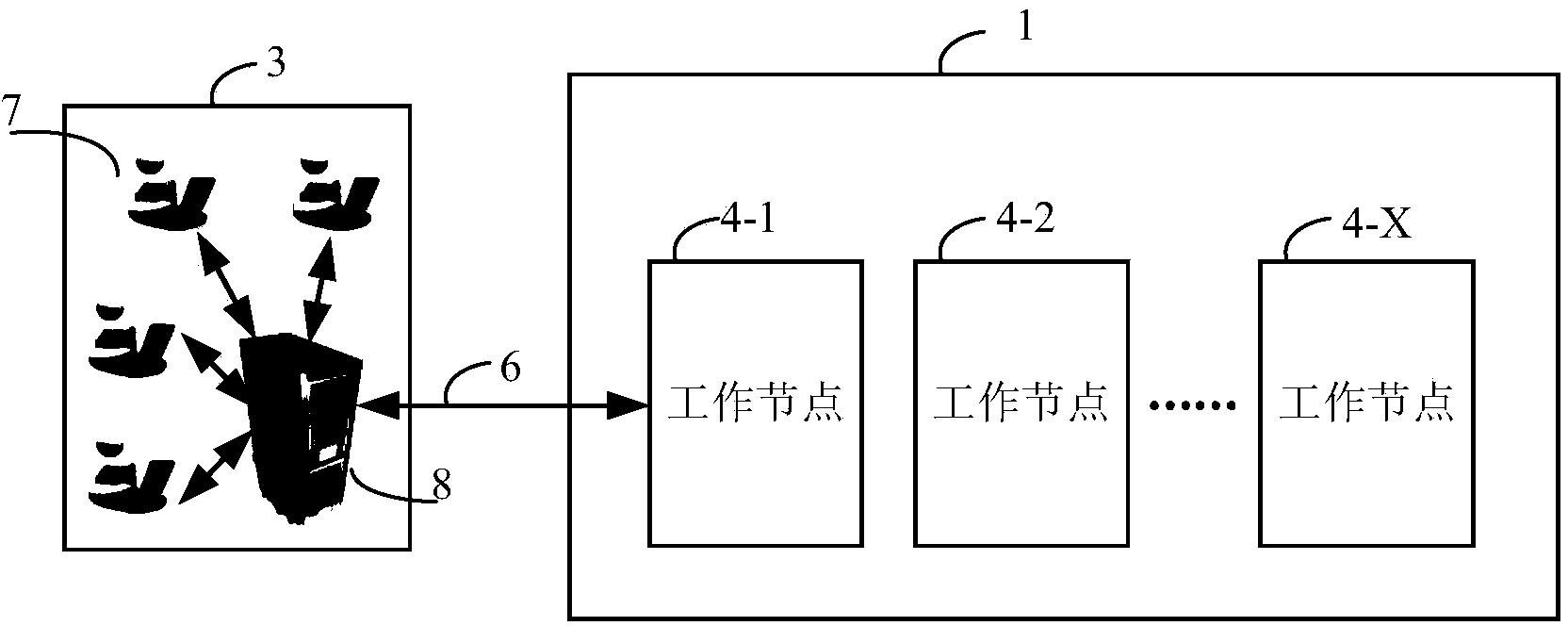
Distributed encryption system
ActiveCN103942107AOptimize allocationFast encryptionResource allocationDigital data authenticationComputer hardwareDelayed time
The invention provides a distributed encryption system. The distributed encryption system comprises a plurality of work nodes which are used for executing encryption tasks and are connected with one another in a cascading mode; at least one work node is connected with a host and is used for receiving encryption tasks allocated by the host; each work node can execute at least one encryption task and send the other encryption tasks to be executed to other work nodes connected with the work node. By the adoption of the technical scheme, the encryption tasks can be rapidly allocated to all the work nodes, the encryption tasks can be executed at nearly the same time in all the work nodes, so that the encryption speed is greatly increased, the delay time is shortened and the encryption performance is greatly improved.
Owner:SAGE MICROELECTRONICS CORP
Selective Data Encryption and Decryption Method and Apparatus
InactiveUS20120134490A1Increase speedLower performance requirementsSecret communicationSecuring communicationComputer hardwarePlaintext
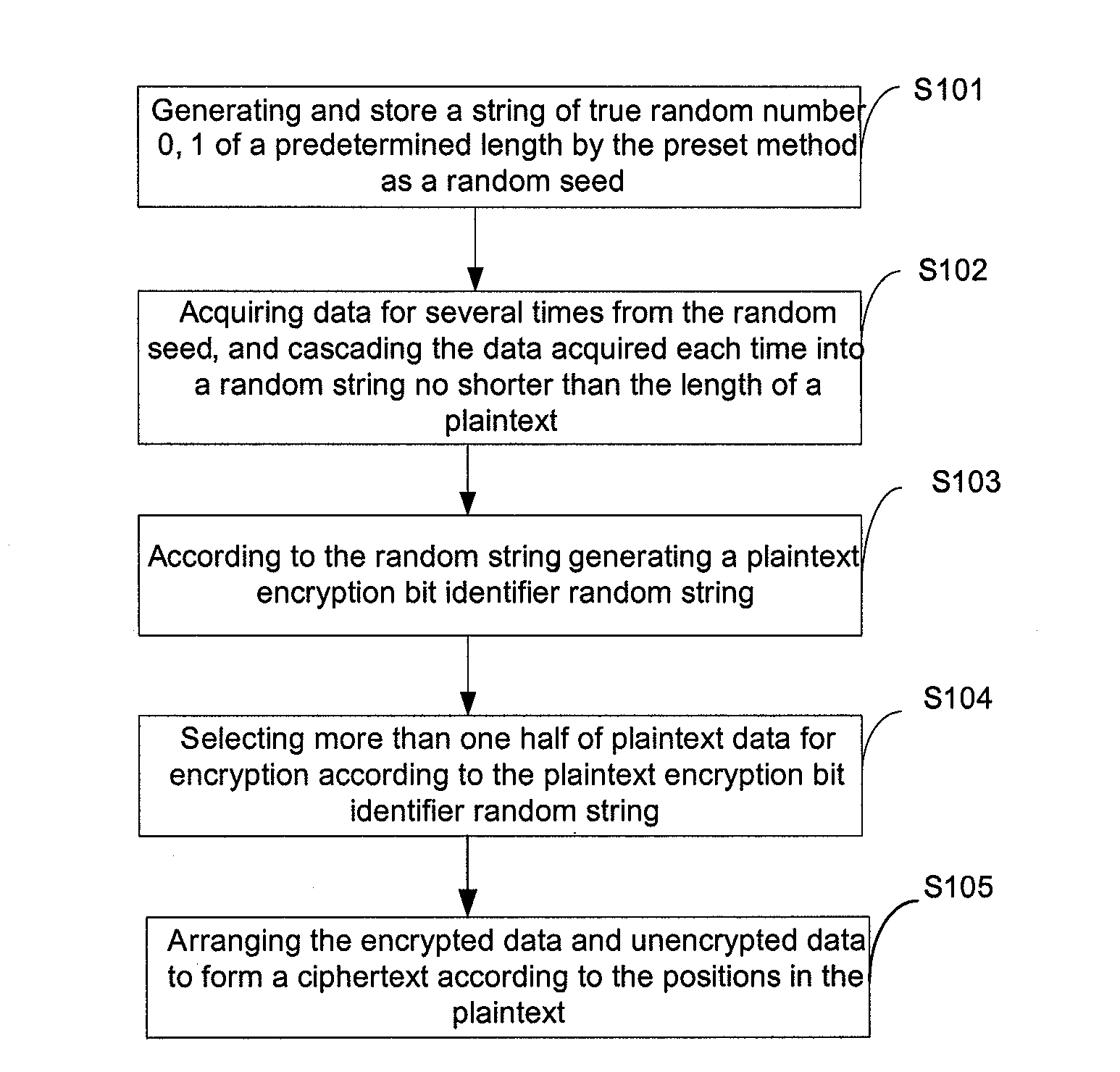
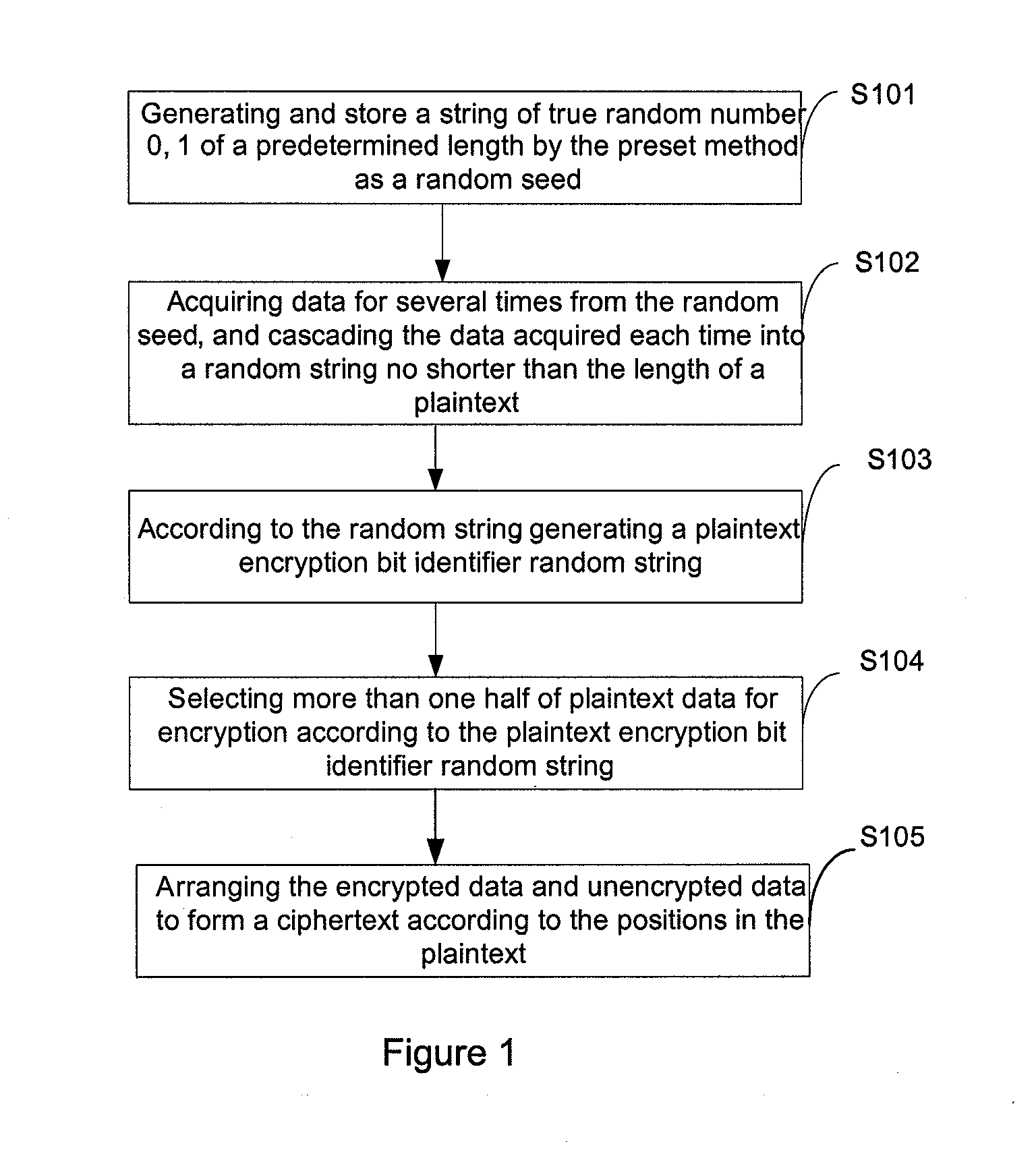
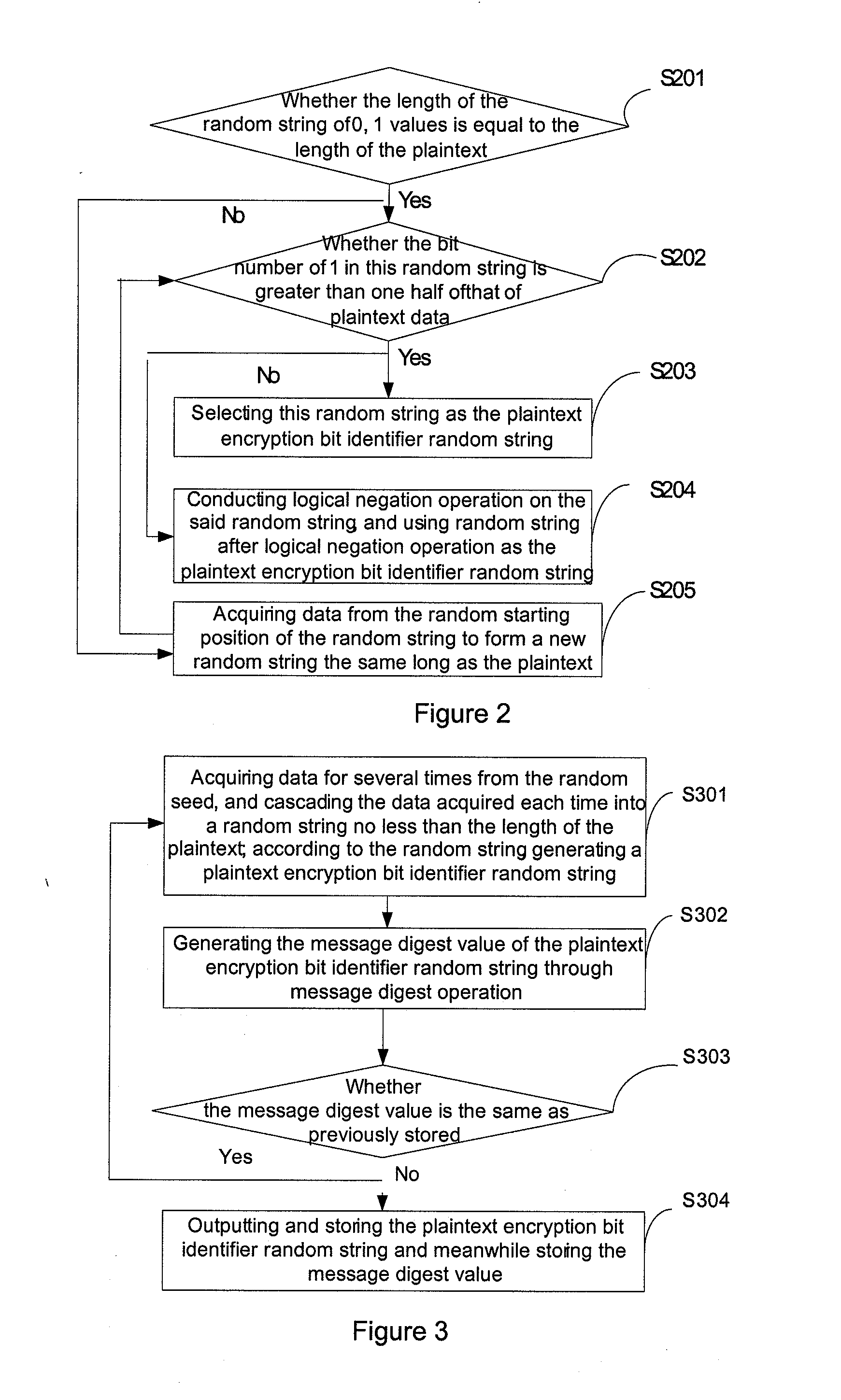
This present application relates to the field of data encryption and decryption technology, and in particular, relates to a selective data encryption and decryption method and apparatus. The encryption method includes: generating a string of true random numbers 0, 1 of a predetermined length via the preset method as a random seed; acquiring data for several times from the random seed, and cascading the data acquired each time into a random string no shorter than the length of a plaintext; according to the random string, generating a plaintext encryption bit identifier random string; randomly selecting more than one half of plaintext data for encryption according to the plaintext encryption bit identifier random string; arranging the encrypted data and unencrypted data to form a ciphertext according to their positions of the plaintext. The encryption apparatus includes: true random number generation module, encryption bit identifier random string generation module, plaintext selectivity encryption module and ciphertext formation module. This application also provides a selective data decryption method and apparatus. This invention reduces the amount of data to be encrypted or decrypted, thus improves the data encryption and decryption performance.
Owner:BEIJING Z & W TECH CONSULTING
Image encryption method based on composite chaotic system and image processing device
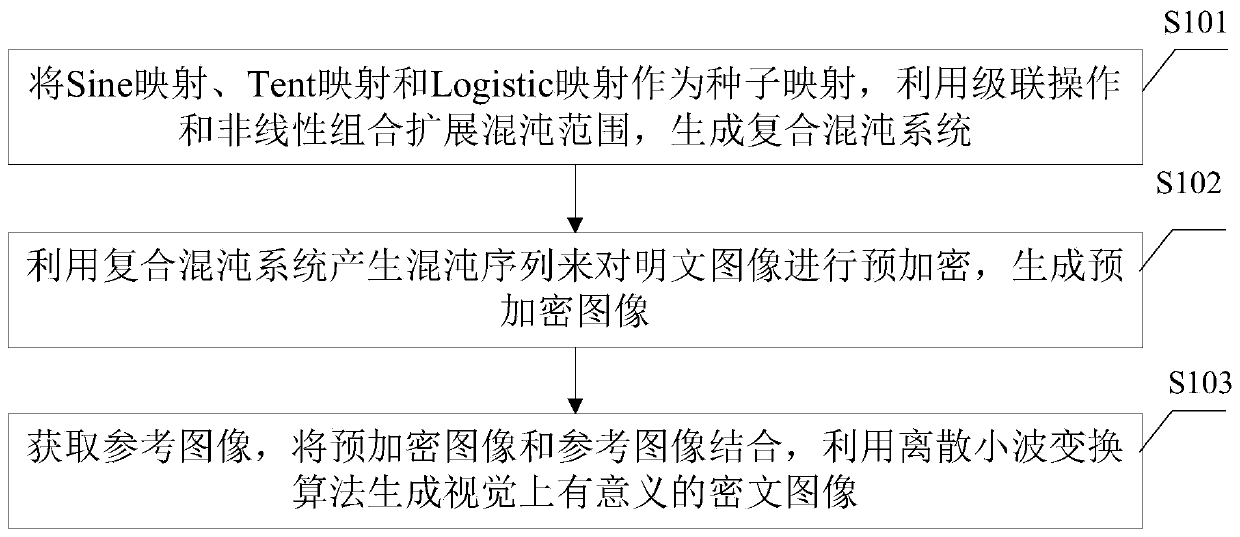
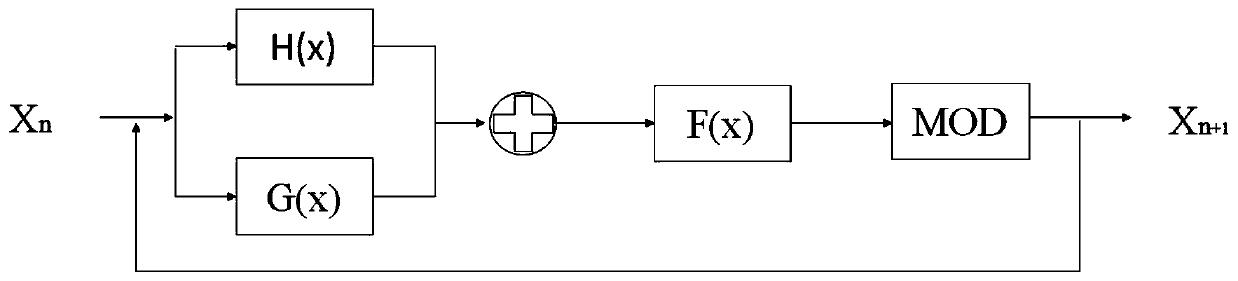
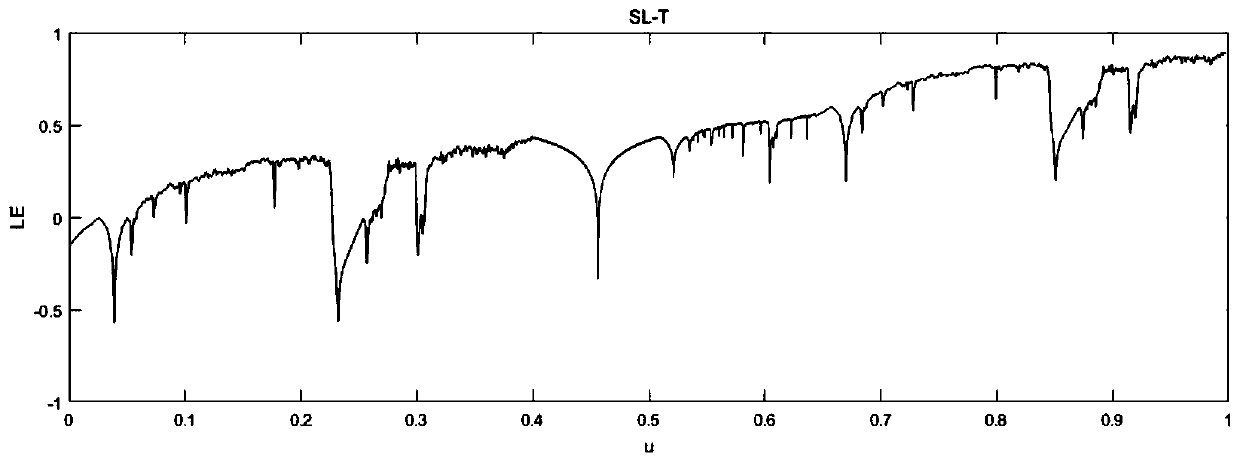
ActiveCN109977686AWide range of chaosComplex chaotic behaviorDigital data protectionImage data processing detailsChosen-plaintext attackImaging processing
The invention is applicable to the field of image encryption, and provides an image encryption method based on a composite chaotic system and an image processing device. The method comprises the following steps of taking Sine mapping, Tent mapping and Logistic mapping as seed mapping, and generating a composite chaotic system by utilizing a cascade operation and a nonlinear combination expansion chaotic range; generating a chaotic sequence by using a composite chaotic system to pre-encrypt the plaintext image, and generating a pre-encrypted image; and obtaining a reference image, combining thepre-encrypted image with the reference image, and generating a visually meaningful ciphertext image by using a discrete wavelet transform (DWT) algorithm. The method provided by the invention has a wider chaotic range and the more complex chaotic behaviors, and the encryption performance is improved. In addition, due to the fact that the visually significant ciphertext image is generated, the attack probability is reduced, the selected plaintext attack and the exhaustion attack can be resisted, and the encryption performance is better.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com