Blockchain account processing method and apparatus, and storage medium
A processing method, blockchain technology, applied in the computer field, can solve the problems of slow signature and verification, large storage space occupied by keys, lack of provable security, etc., and achieve fast verification speed, small storage space, effective Good for backward compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 3 example
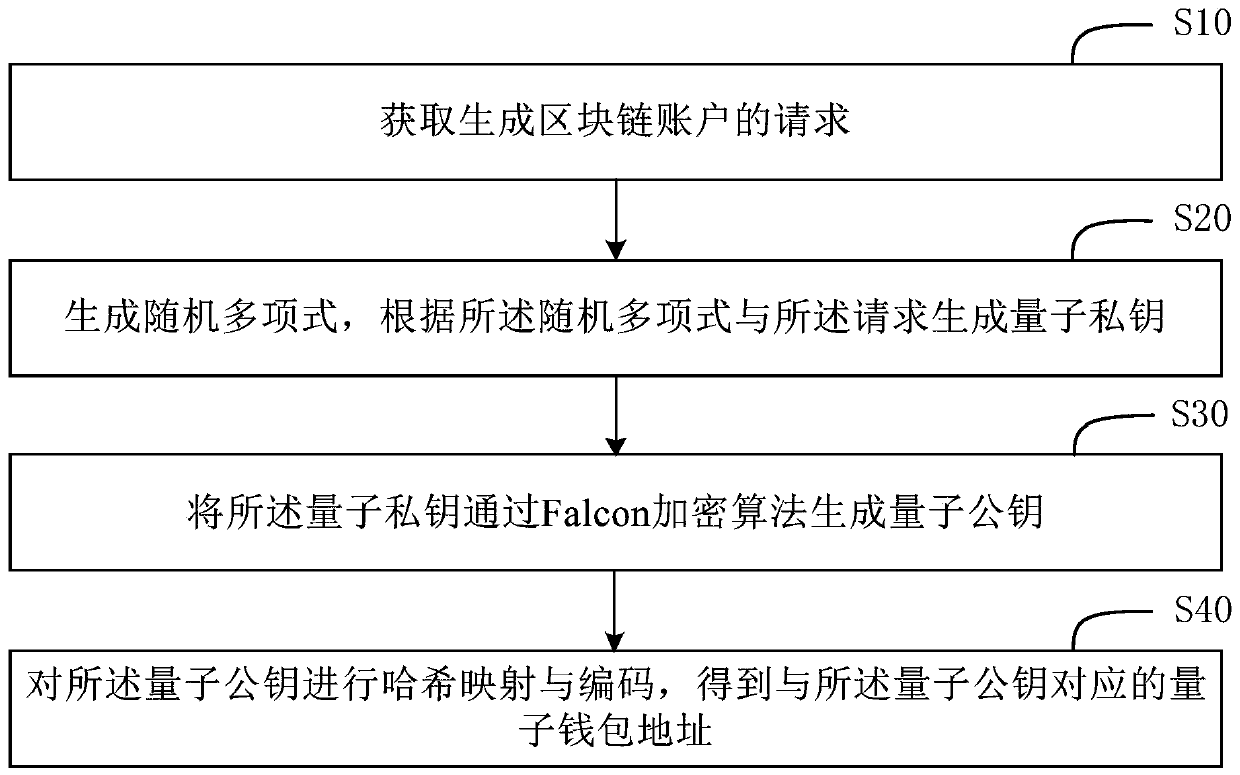
[0099] In order to further improve the scope of application of the present invention, the present invention also proposes a third embodiment: after obtaining the request to generate a blockchain account, it also includes:
[0100] randomly generating a second random number or a second random polynomial according to the request;
[0101] generating a second private key according to the second random number or the second random polynomial;
[0102] Using the second private key to generate a second public key through a second encryption algorithm different from the Falcon encryption algorithm;
[0103] Perform hash mapping and encoding on the second public key to obtain a second wallet address corresponding to the second public key.
[0104] In some cases, for example, when the second encryption algorithm is an existing non-quantum computer-resistant algorithm, the request may include the steps of generating a second random number and generating a second private key based on the...
no. 2 example
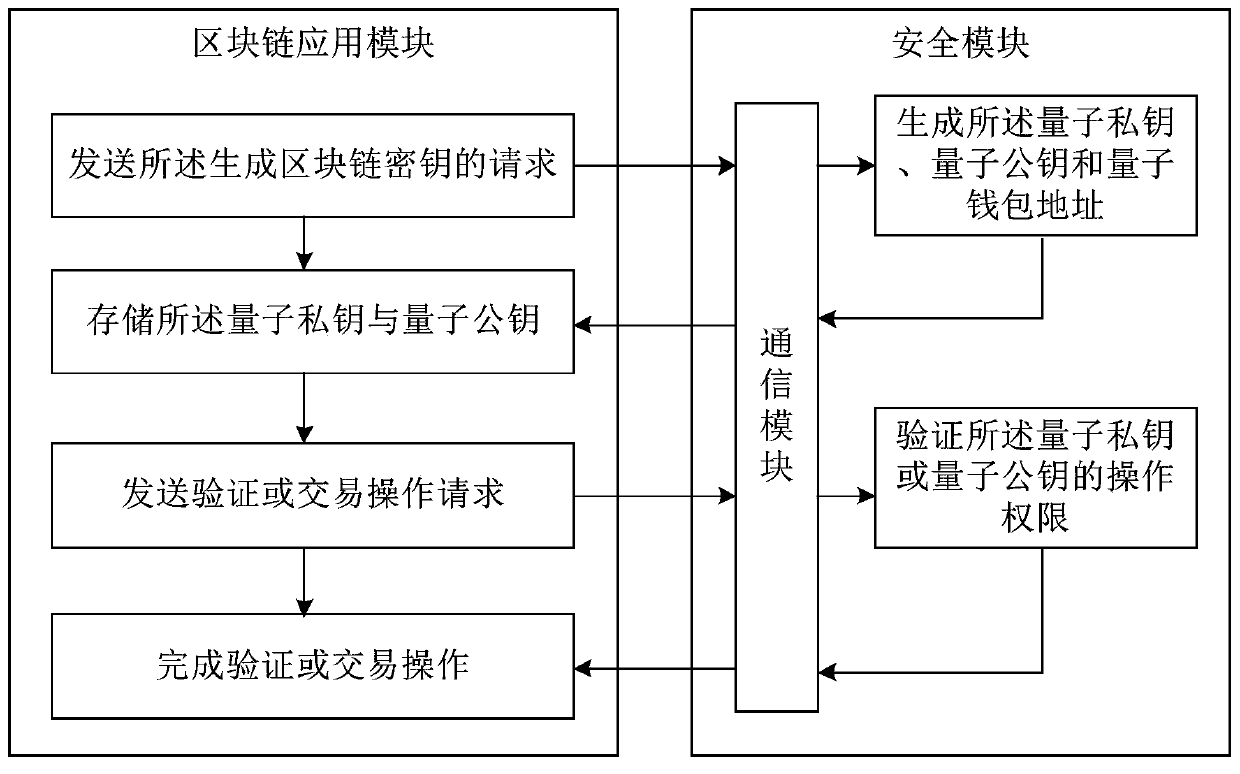
[0106] Based on the second embodiment, the present invention also proposes another embodiment: after obtaining the request to generate a blockchain account, it also includes:
[0107] Confirm that the system uses the Falcon encryption algorithm or the secp256k1 encryption algorithm;
[0108] If the system uses the Falcon encryption algorithm, continue the step of generating a random polynomial, and generate a quantum private key and a quantum private key according to the random polynomial and the request;
[0109] If the system uses the secp256k1 encryption algorithm, continue the step of generating random numbers, and generate an elliptic curve private key according to the random numbers and the request.
[0110] In this embodiment, two encryption algorithms can be preset in the system framework to determine which preferred encryption algorithm is currently used to generate the private key and public key according to the specific situation, which is conducive to the backward ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com