Hardware encryption protection method and system for cellphone data
A technology of hardware encryption and protection system, applied in the field of mobile communication and information security, it can solve problems such as inability to meet requirements and performance problems, and achieve the effects of high security, high performance and high reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
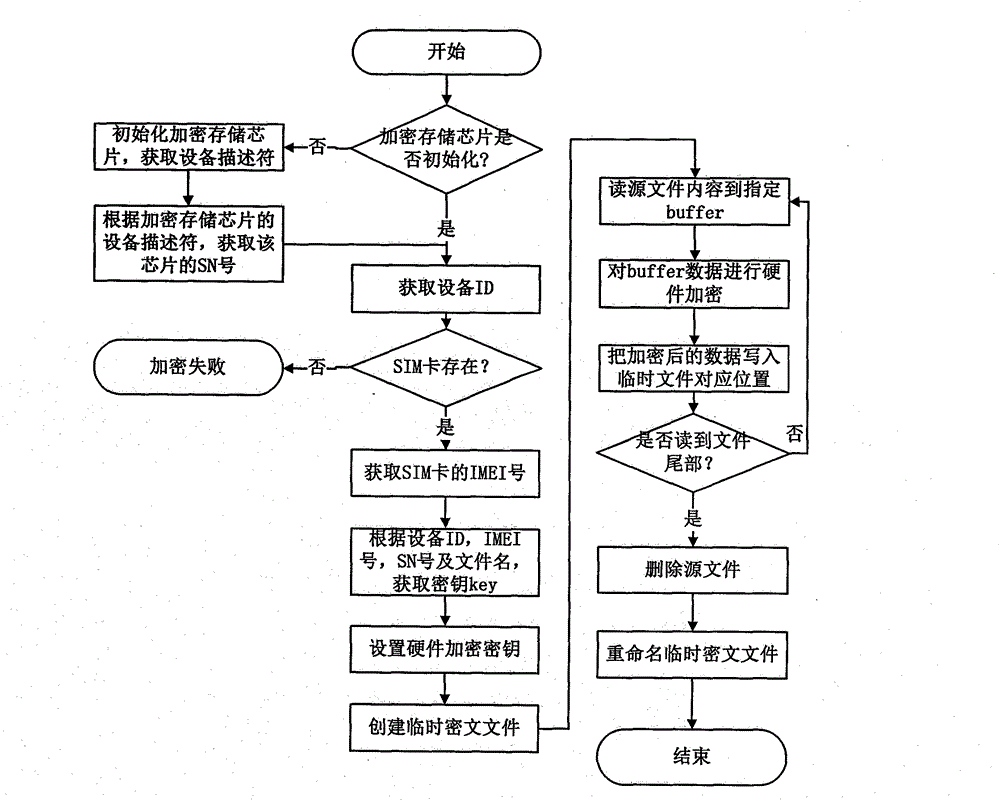
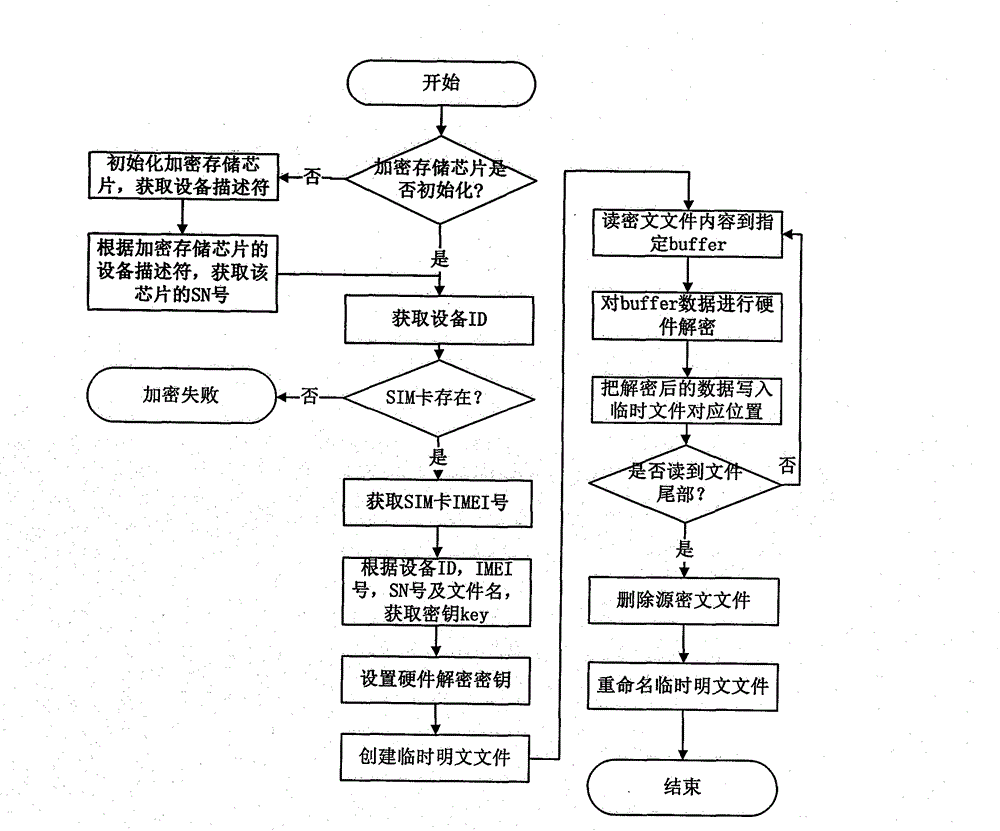
[0029] In order to better understand the technical solutions of the present invention, the embodiments provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
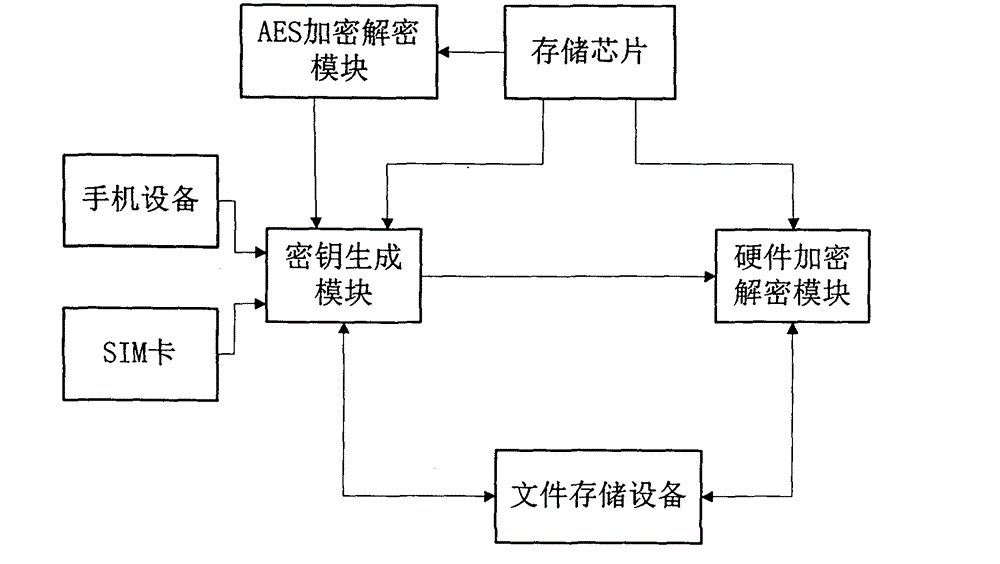
[0030] like figure 1 As shown, a hardware encryption protection system for mobile phone data is proposed, including a mobile phone device, a memory chip, a key generation module, an AES encryption and decryption module, a hardware encryption and decryption module, and a file storage module.
[0031] The memory chip includes a core processor and a built-in memory, and is fixed on the circuit board of the mobile phone by welding. The chip not only provides encryption and decryption functions; but also has a built-in small storage space, which can only be accessed through the SDK provided by the manufacturer. It can be used to save private data, or establish a data binding relationship, and is used for data recovery in special cases. The main function of the chi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com