A method and system for hardware encrypted transmission and storage of mobile phone private text messages
A technology for hardware encryption and private contacts, applied in the field of hardware encrypted transmission and storage of mobile phone private short messages, can solve the problems of poor security, inability to unlock, and low security, and achieve high reliability, high security, and simple operation. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
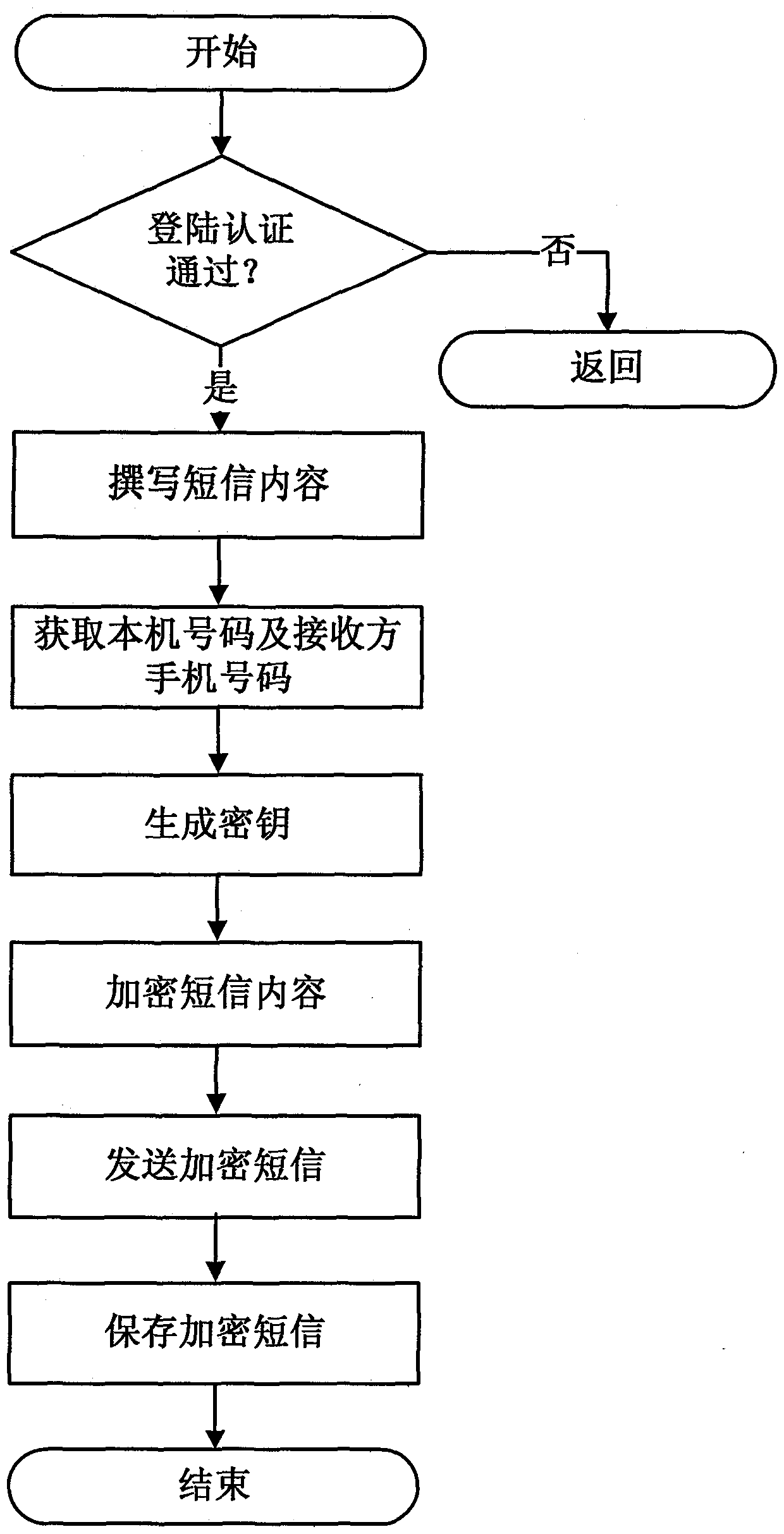
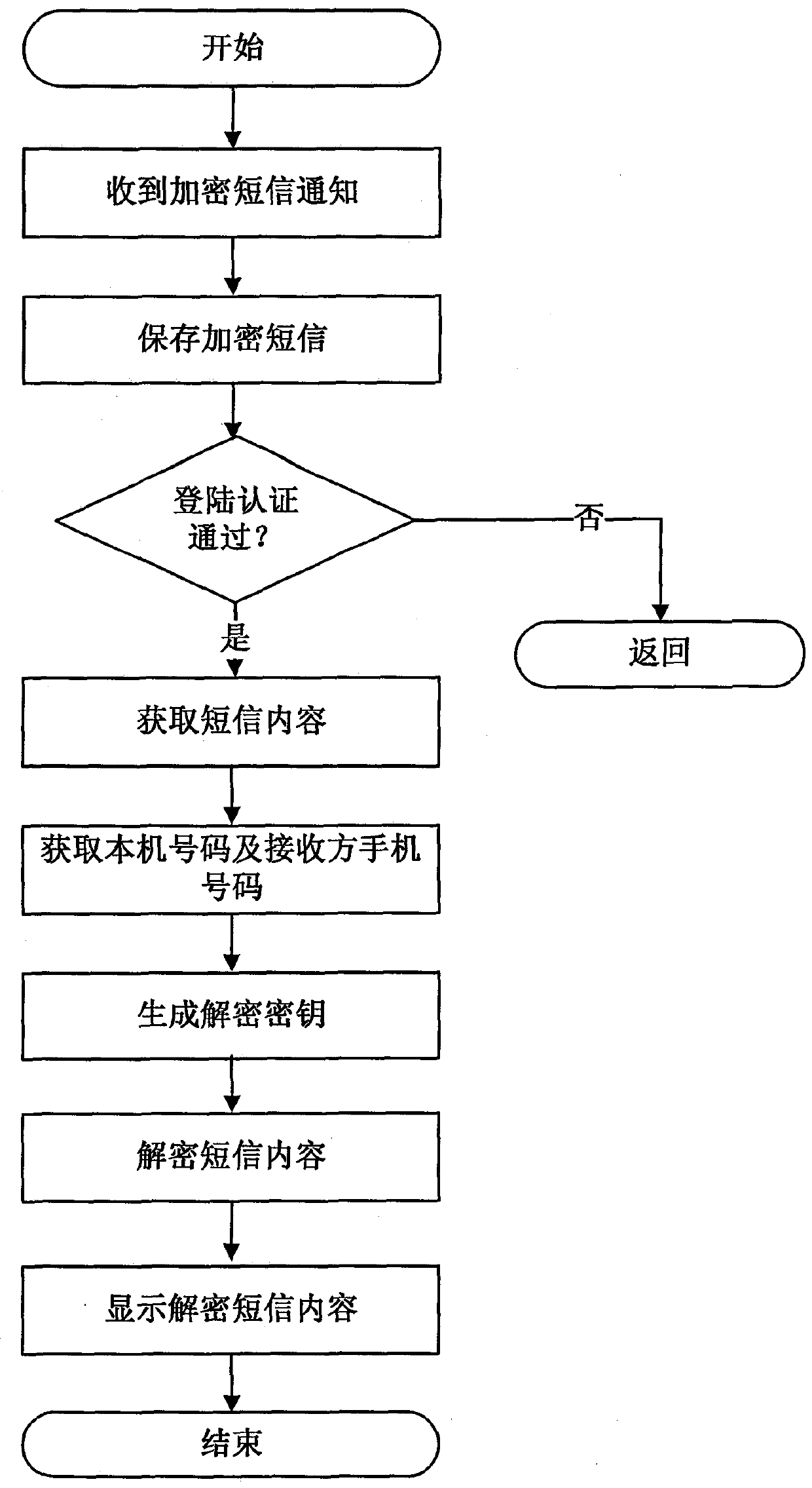
[0032] In order to better understand the technical solutions of the present invention, the embodiments provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
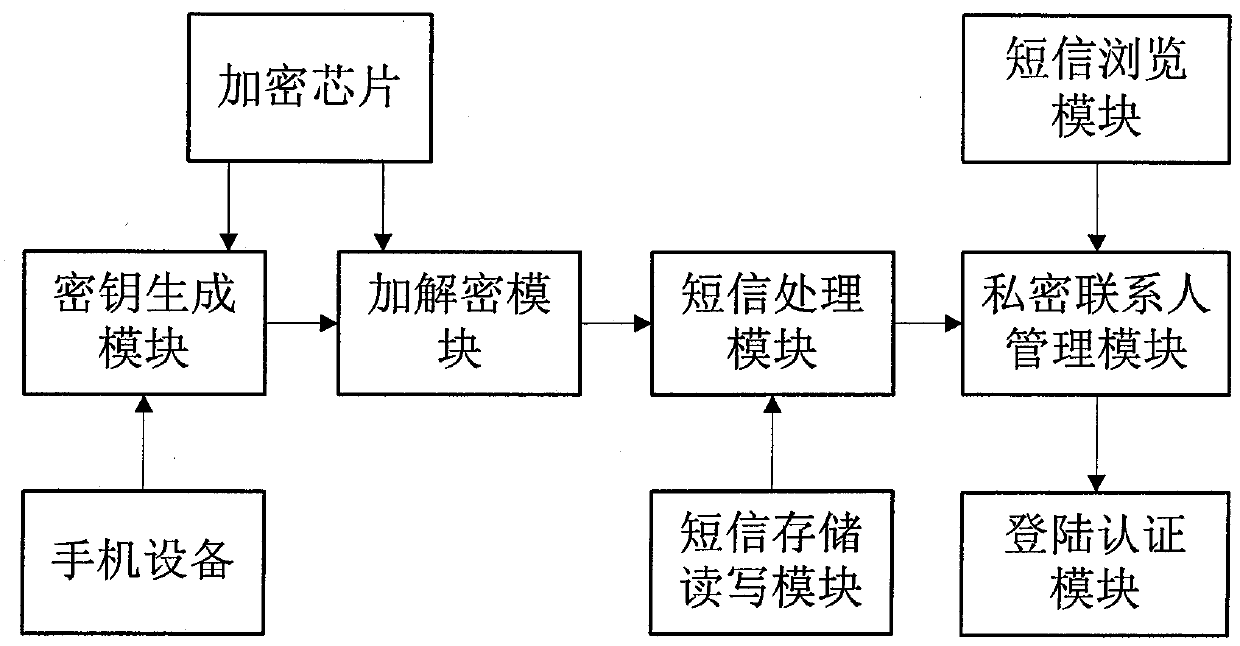
[0033] Such as figure 1 As shown, a hardware encrypted storage system for mobile phone private contacts is proposed, including mobile phone equipment, encryption chip, key generation module, encryption and decryption module, private contact management module, login authentication module, SMS storage read-write module, SMS processing module, SMS browsing module;
[0034] The encryption chip has an independent core processor and does not occupy the CPU resources of the system, so the performance is more efficient than the encryption and decryption process of pure software;
[0035] The key generation module is used to read the information of the sender and receiver of the mobile phone and generate the key used for encryption and decryption;
[0036] The encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com