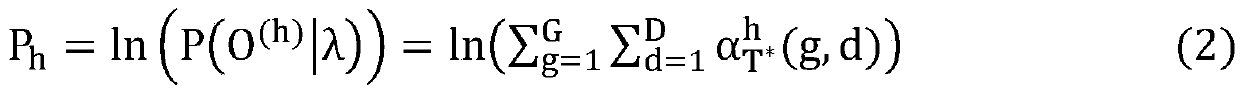Patents
Literature
283results about How to "Does not take up resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
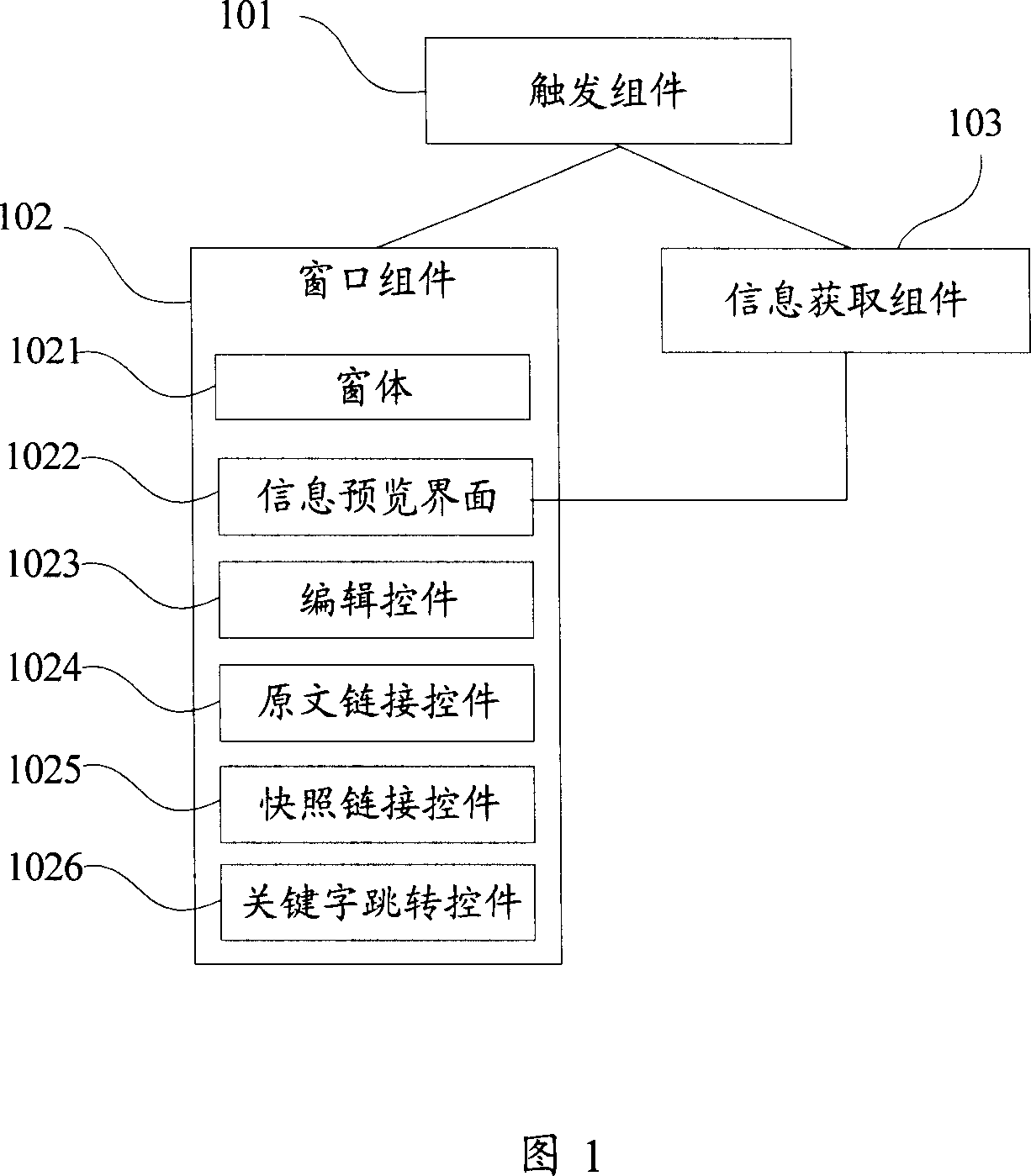
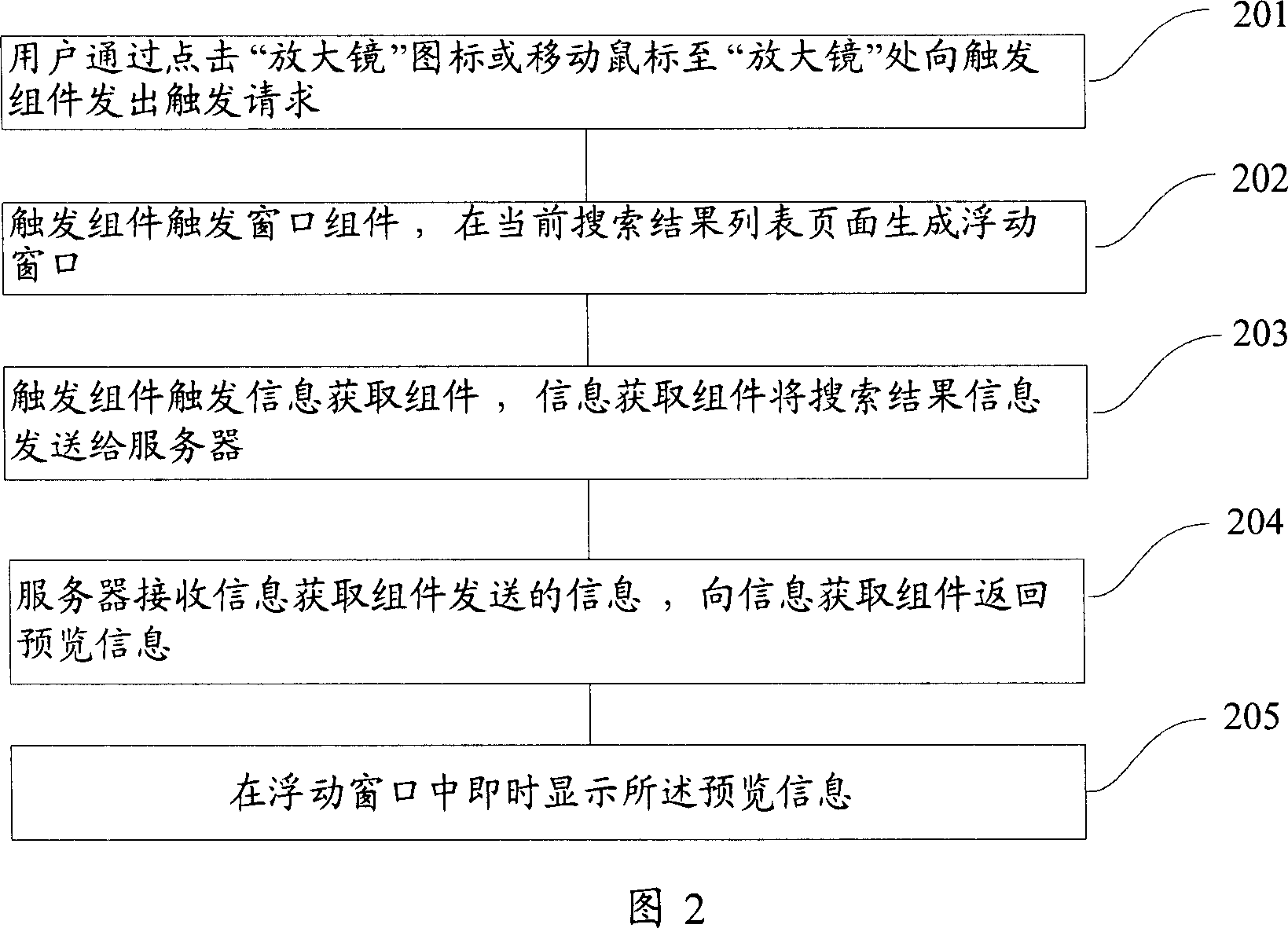
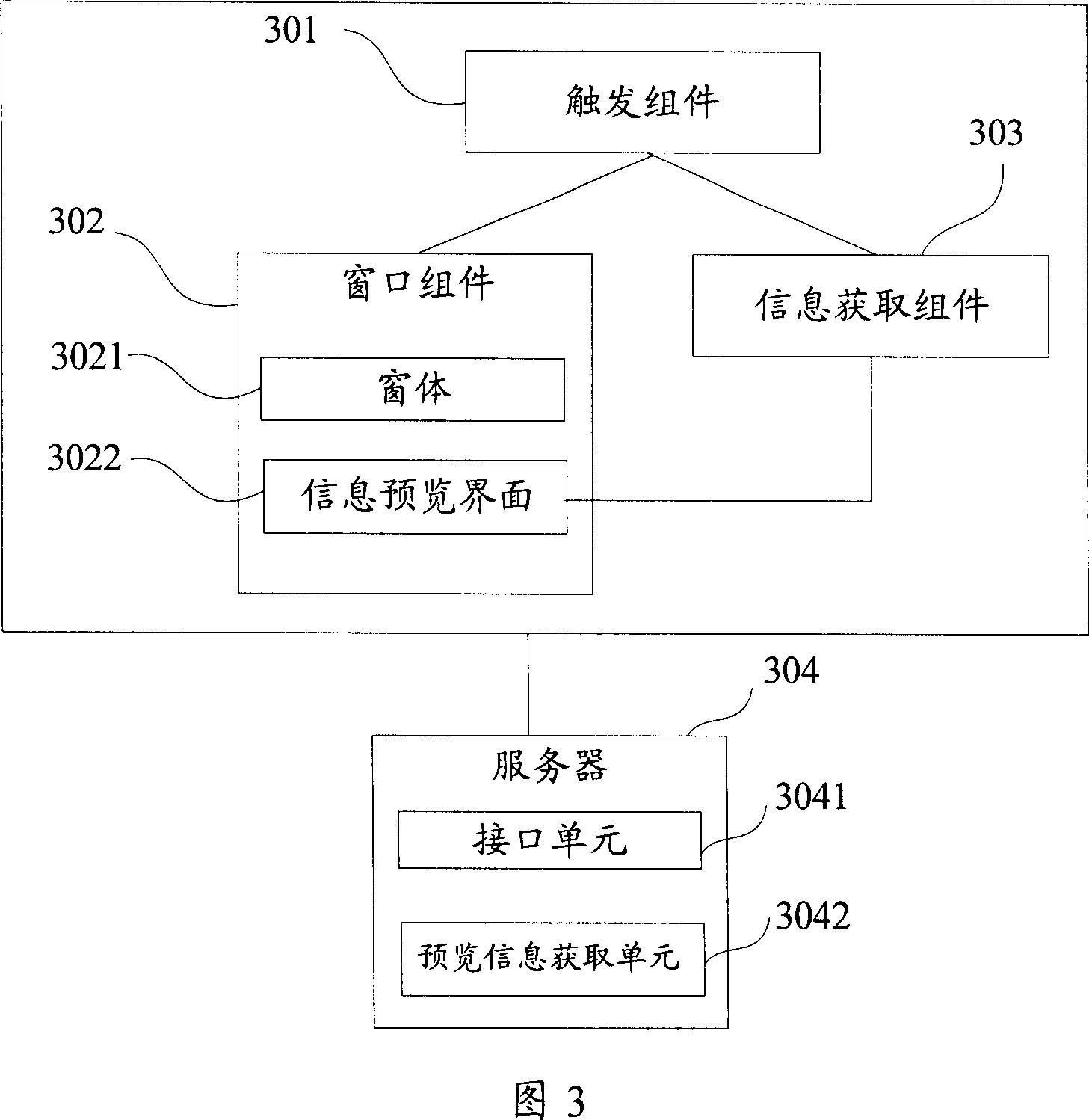
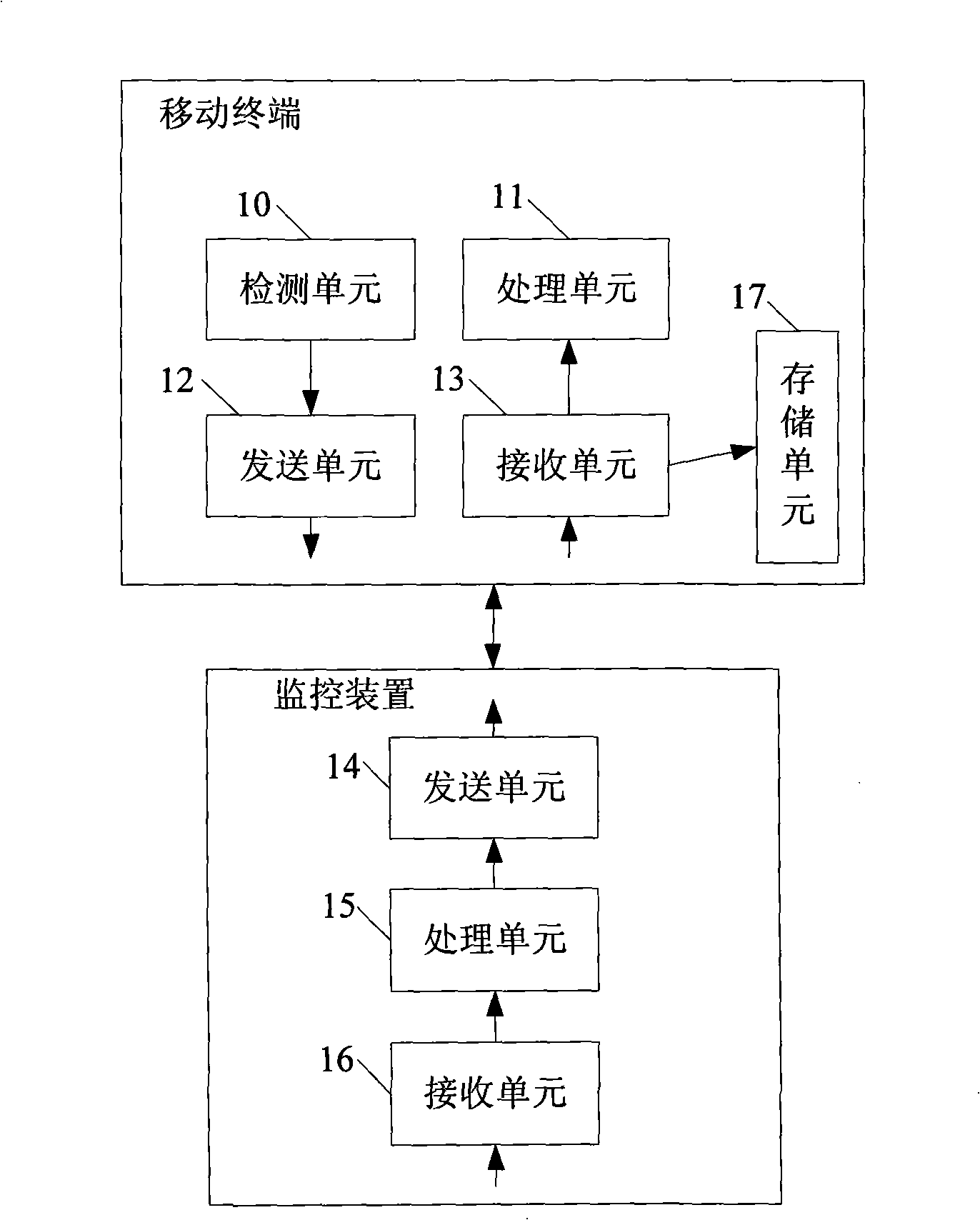
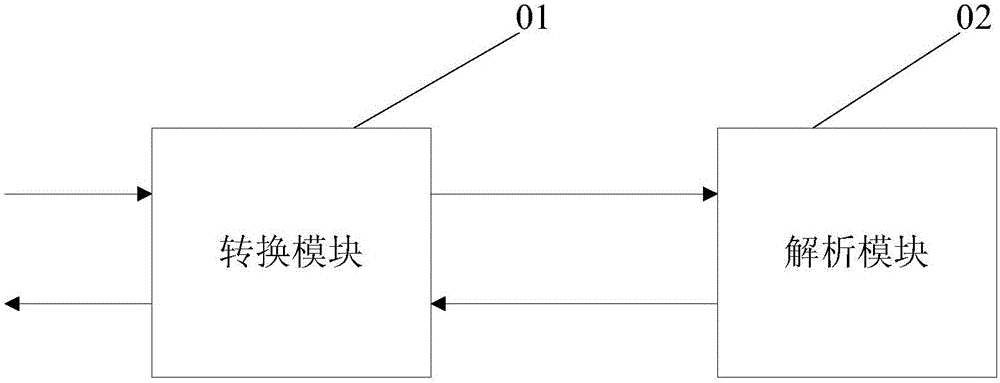
Search engine based search result fast pre-reading device
ActiveCN1924860AMeet the purpose of the queryConvenient text manipulationSpecial data processing applicationsService provisionResult list
This invention relates to search rapid previewing device, which is characterized by the following: trigger set to receive user requirement for window set and information acquirement set; window set to promptly display information on the current result list page to get the preview information including window and information preview page; the said window is to determine window display size, shape and position; the said page is to display preview information of the set; information acquiring set to connect servo research results and to display information to the page.
Owner:网易有道信息技术(北京)有限公司
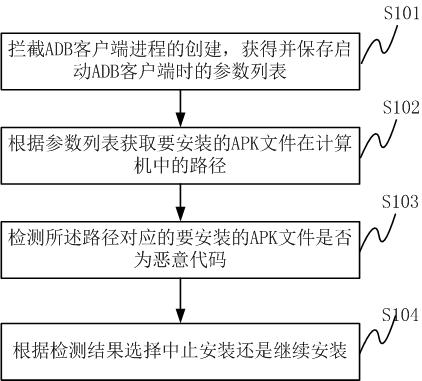
Method and system for detecting and intercepting malicious code of mobile terminal
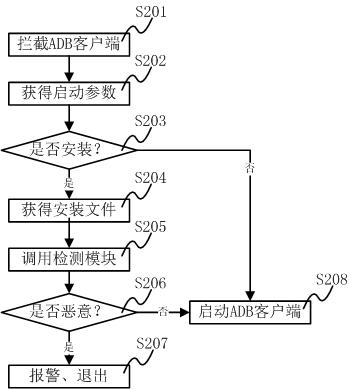
InactiveCN102254113AStrong computing powerDoes not occupy and consume system resourcesPlatform integrity maintainanceTransmissionThird partyComputer terminal
The invention discloses a method for detecting and intercepting a malicious code of a mobile terminal. The method comprises the following steps of: intercepting creating process of an Android debug bridge (ADB) client in a computer, and acquiring and saving a parameter list when the ADB client is started; judging whether an APK file (Android application program) is required to be installed according to the parameter list, if so, acquiring the route of the APK file to be installed in the computer; detecting whether the APK file to be installed corresponding to the route is the malicious code; and selecting stopping installing or continuously installing according to the detection result. The invention further discloses a system for detecting and intercepting a malicious code of a mobile terminal. The method and the system do not consume system resources of the mobile phone; the method and the system are suitable for the existing various installation methods and the third party mobile phone aided software; and the method and the system can effectively prevent the malicious code from spreading to the intelligent mobile phone through the computer.
Owner:SHENZHEN ANZHITIAN INFORMATION TECH
Method and system for avoiding overlapped display of bullet screen
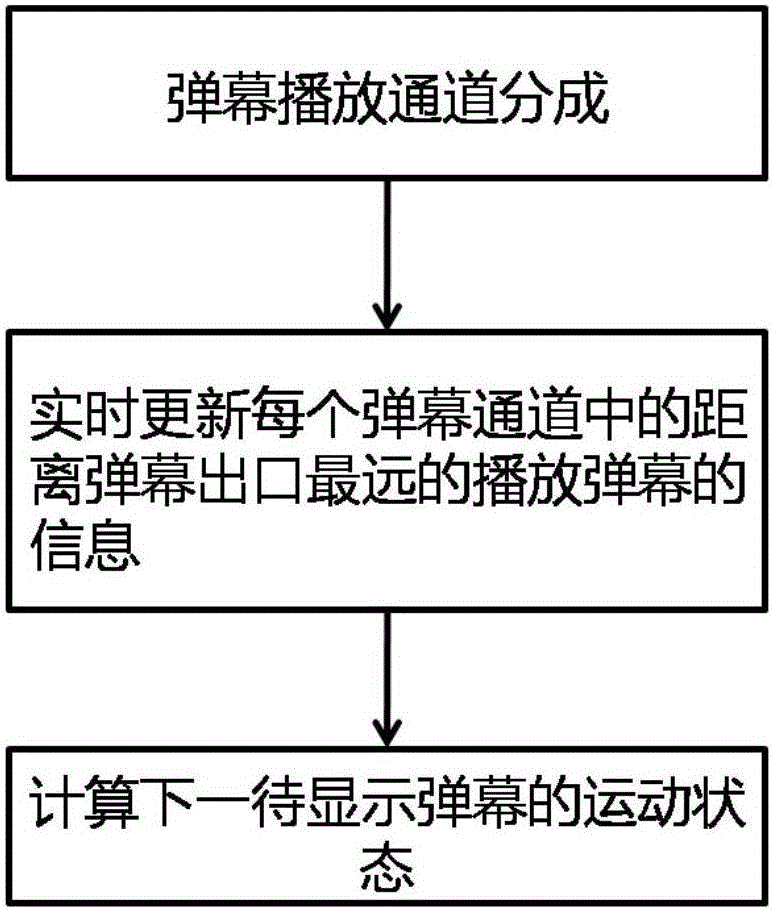
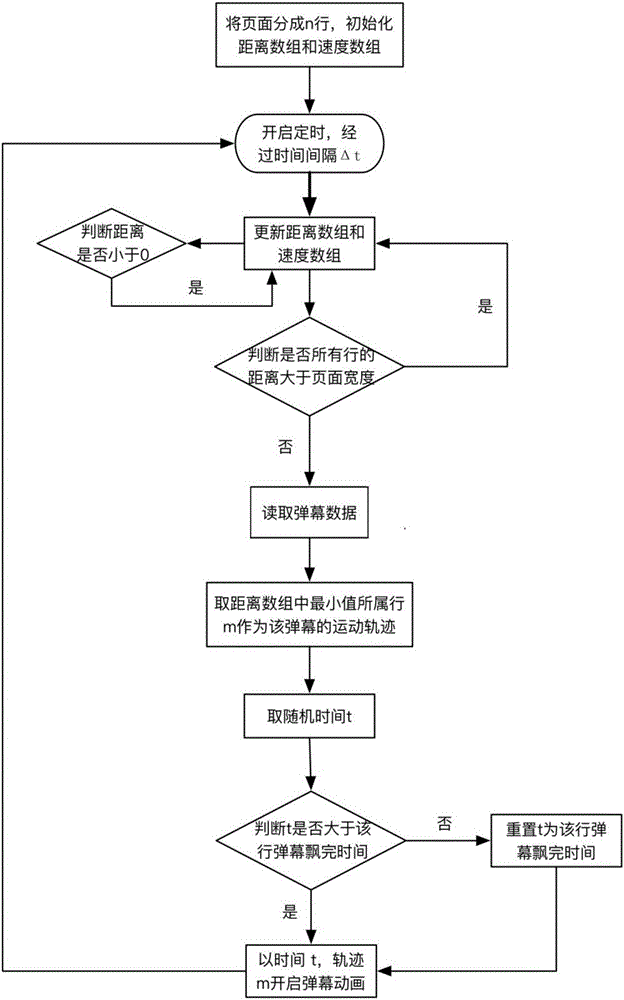
ActiveCN105828164AAvoid overlappingEfficient managementSelective content distributionComputer scienceScreen space
The invention discloses a method and a system for avoiding overlapped display of a bullet screen. The method comprises the following steps: dividing a live streaming display page into n bullet screen playing channels; wherein n meets the following conditions: n X a bullet screen height + (n-1) X a bullet screen spacing <= a live streaming display page; real-time updating information which plays a bullet screen and is the utmost distal from an exit of the bullet screens in each bullet screen playing channel; analyzing the information so as to calculate the motion state of the bullet screen to be displayed next, playing the bullet screen based on the motion state. The method and the system of the invention can explicitly increase efficiency of bullet screen display resources, and explicitly increase interaction experience of bullet screen users.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
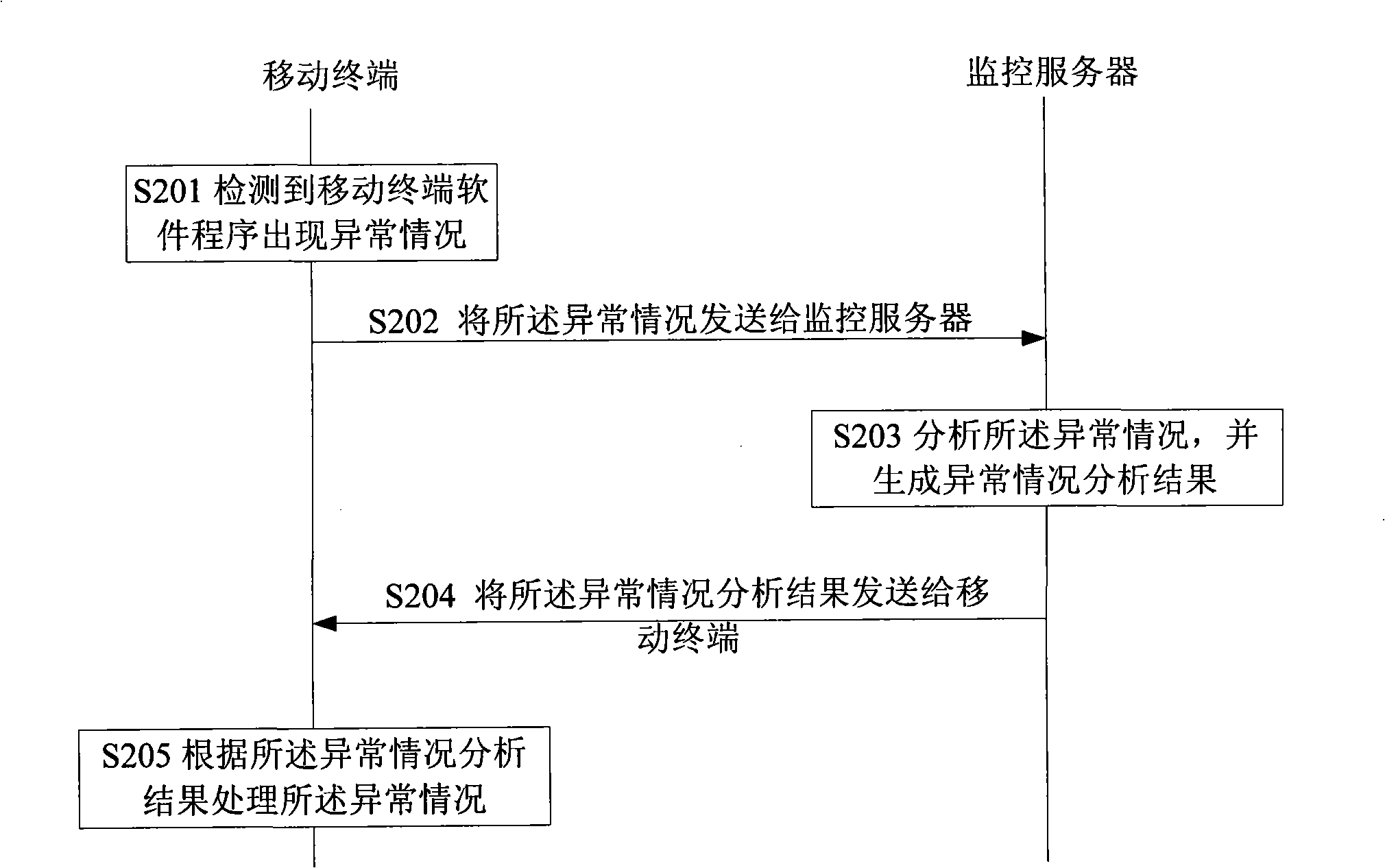
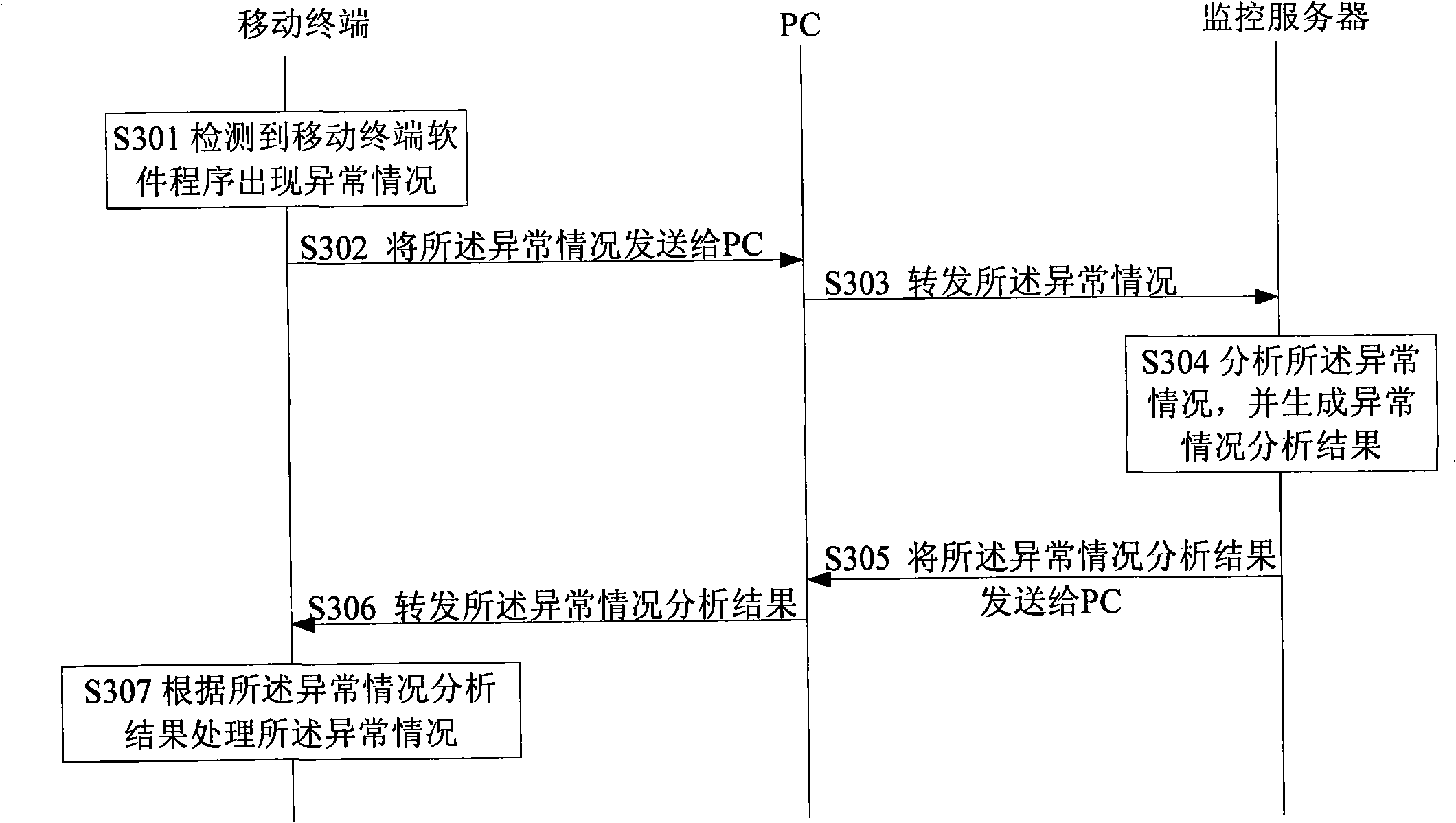
Method, terminal and system for realizing mobile terminal software safe detection
InactiveCN101257678ADoes not take up resourcesMeet openness needsRadio/inductive link selection arrangementsPlatform integrity maintainanceComputer terminalSoftware
The invention discloses a method for realizing the safety detection of mobile terminal software, including: detecting whether the abnormal condition appear in the software program produce; sending the abnormal condition to a monitoring device outside of the mobile terminal if the abnormal condition is detected in the software program produce of mobile terminal; analyzing for the abnormal condition and returning the analyzed result of the abnormal condition by the monitoring device; the mobile terminal recieving the analyzed result of the abnormal condition returned by the monitoring device, and treating the abnormal condition according to the analyzed result of the abnormal condition. The invention also discloses a mobile terminal and a system for realizing the the safety detection of mobile terminal, using the project provided by the invention, the virus can be eliminated or the operation of illegal software program can be forbidden in time before the virus inbreaks, the resourses of mobile terminal are not occupied, the services of mobile terminal can be better enlarged, the open requirement of mobile terminal can be satisfied.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Browser-based suspensible novel network instant chat method
InactiveCN102045269ADoes not take up resourcesImprove experienceData switching networksInternal memoryComputer network
The invention relates to a browser-based suspensible novel network instant chat method. A chat interface can suspend on a browser page, and during instant chat, the popped two-person or multi-person instant chat window can suspend on the browser page. The method has the advantages that: personal computer resources of the user is not occupied, the internal memory and a hard disk are not occupied, the speed is high, and the method is convenient to use; due to the browser-based mode, the security of personal account number, data and chat contents are well ensured and the personal account number, data and chat contents are hardly stolen; besides, the chat interface and the chat window suspend on the page functionally, the chat interface and the chat window can be randomly dragged, and the method meets humanization requirement, and has good user experience.
Owner:于琨洪
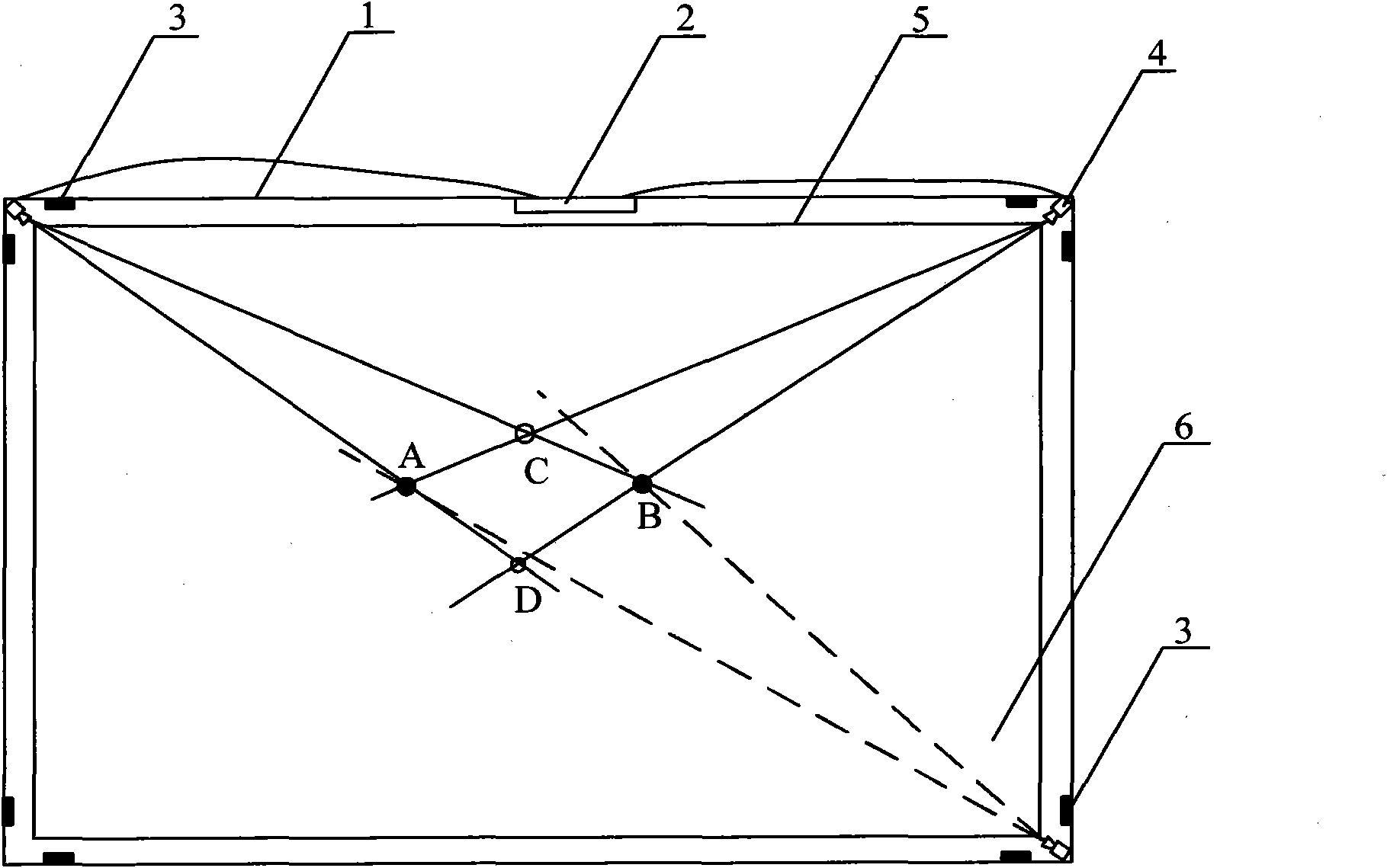
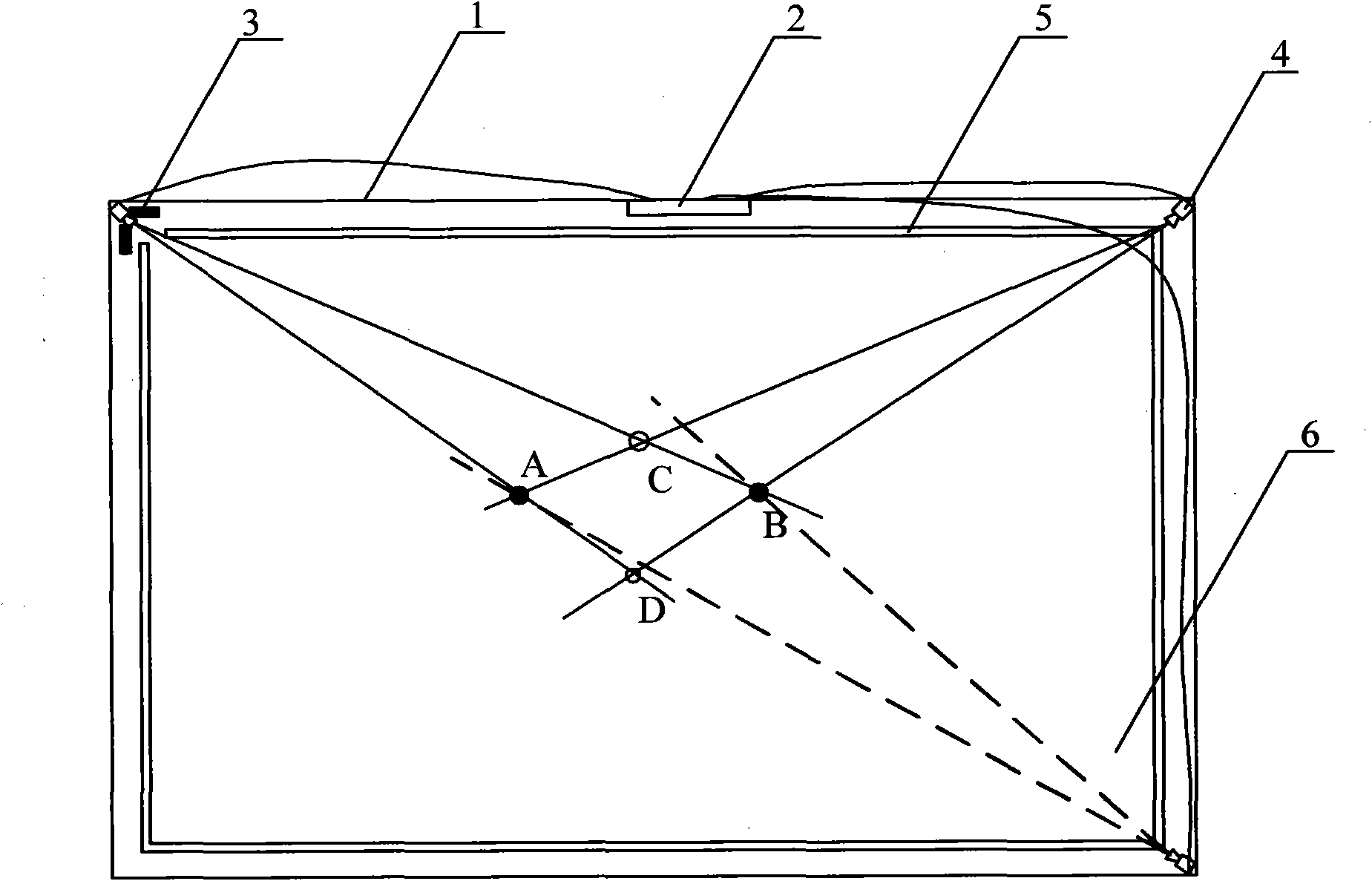
Optical multipoint touch screen and implementation method thereof
InactiveCN102023762ASimple compositionOptimize layoutInput/output processes for data processingLight guideTouchscreen
The invention discloses an optical multipoint touch screen which comprises a frame (1), a main controller (2), infrared monitoring units (4), and light-emitting elements (3), wherein the infrared monitoring units (4) are arranged at the inner sides of corners of the frame (1) and are connected with the main controller (2), and the light-emitting elements (4) are arranged at any position in the frame (1). The invention is characterized in that all the inner walls of the frame (1) are also provided with light guide elements (5); the number of the infrared monitoring units (4) is more than three; and the light-emitting elements (3) are positioned between the frame (1) and the light guide elements (5). In the invention, ghost points formed in a touch area can be removed effectively, the position of a practical touch point is obtained correctly, and the defects of the multipoint touch which can not be realized by the traditional optical touch screen are overcome.
Owner:CHENGDU JIZHOU TECH
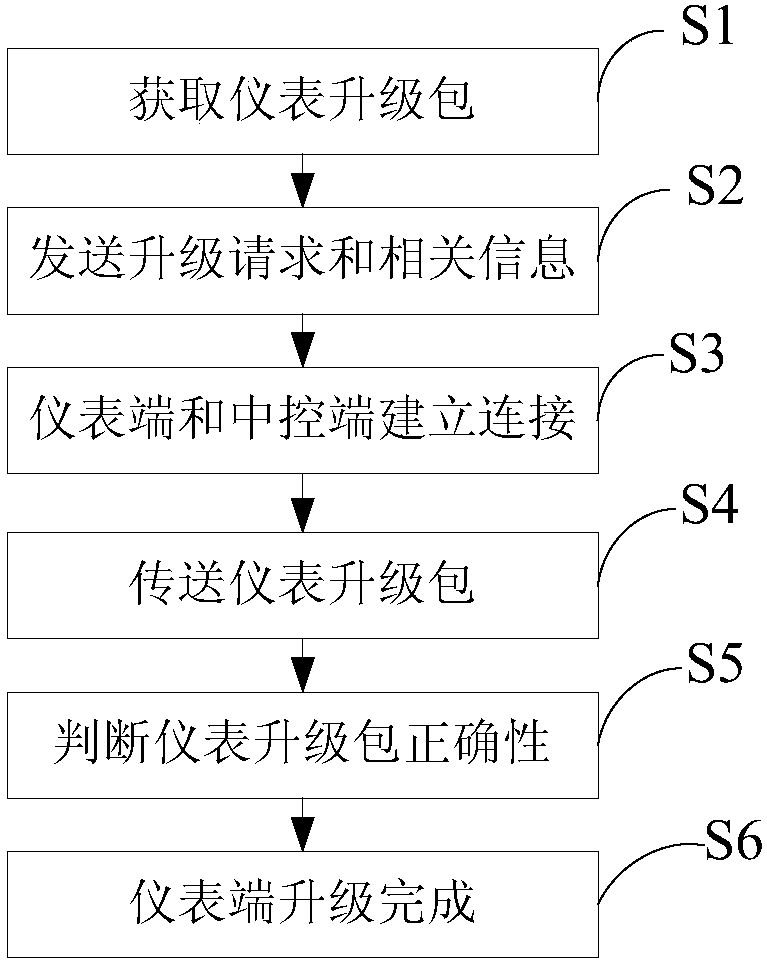
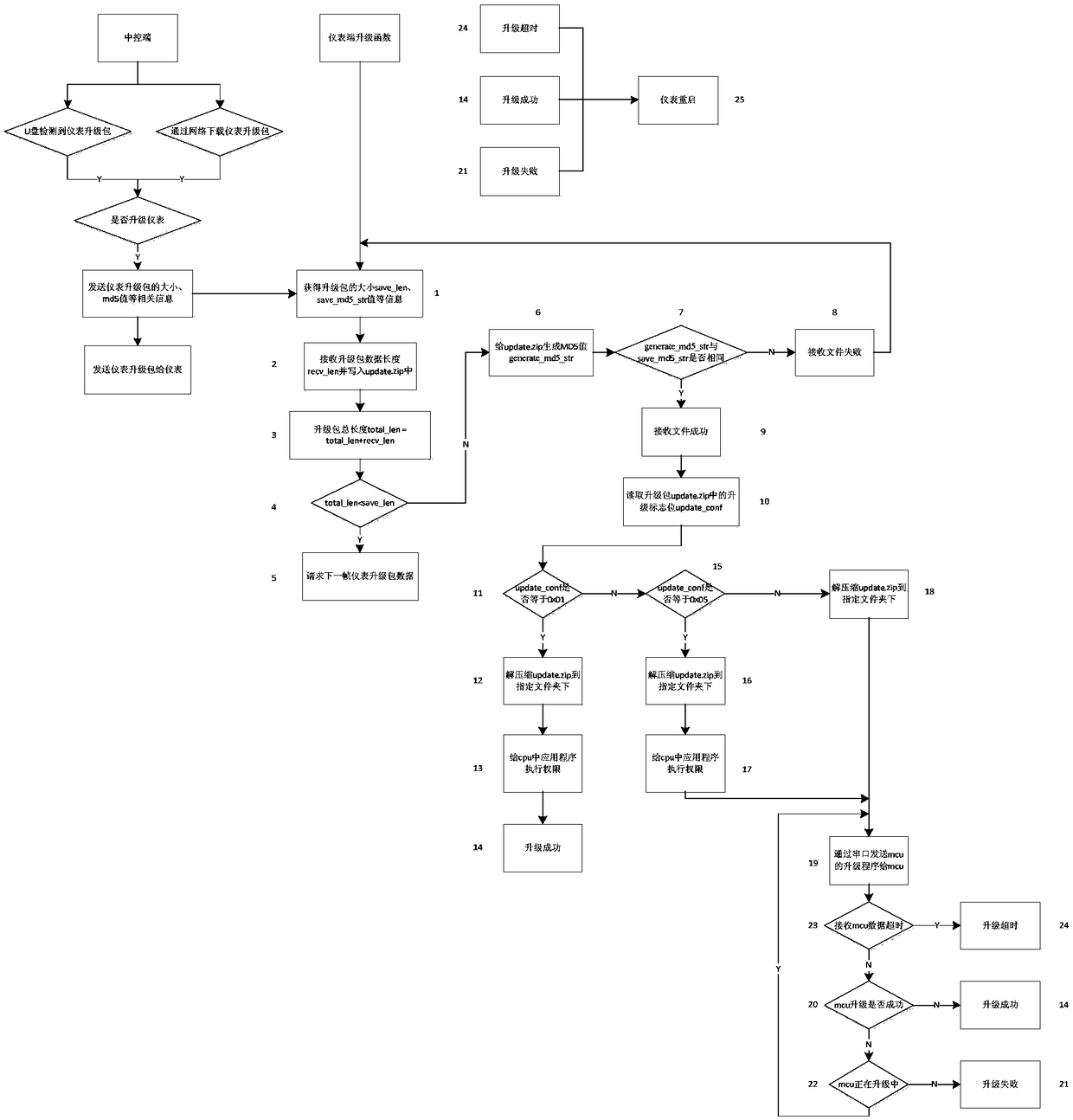
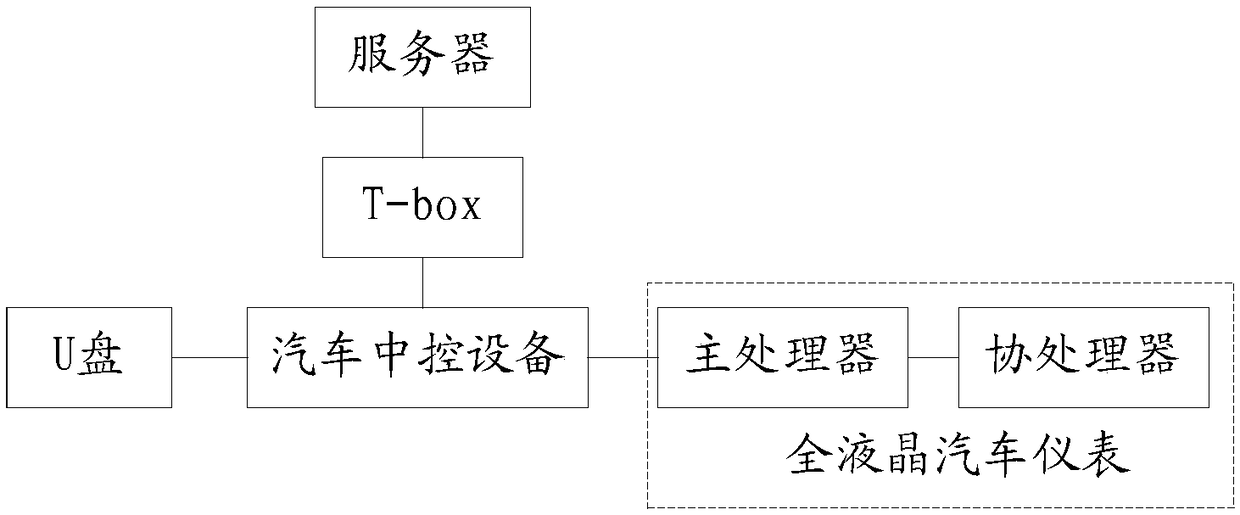
Upgrading method for motormeter software
The invention discloses an upgrading method for a motormeter software. The upgrading method comprises the steps that a central control end acquires a motormeter upgrading package from an external memory device or an Internet, the motormeter end judges validity of a received motormeter upgrading package through length and ciphertext detection, and an upgrading zone bit value is set corresponding toa host processor and / or a co-processor in the motormeter upgrading package. The upgrading method achieves that the motormeter upgrade are independent of professional equipment and staffs, and a USB flash disk, a telephone and other external storage devices or the Internet can be used to upgrade the motormeter, thereby greatly improving the upgrading efficiency of the motormeter and reducing the upgrading requirements of the motormeter. The upgrading method has the advantages that the validity of the motormeter end acquiring the upgrading package is ensured, it is avoided that a failed upgradecaused by a transmission error leads to operation troubles of a motormeter end software, and the safety, reliability and stability of the software upgrading are improved.
Owner:CHONGQING DELCO ELECTRONICS INSTR
Method and system for integrally acquiring webpage information
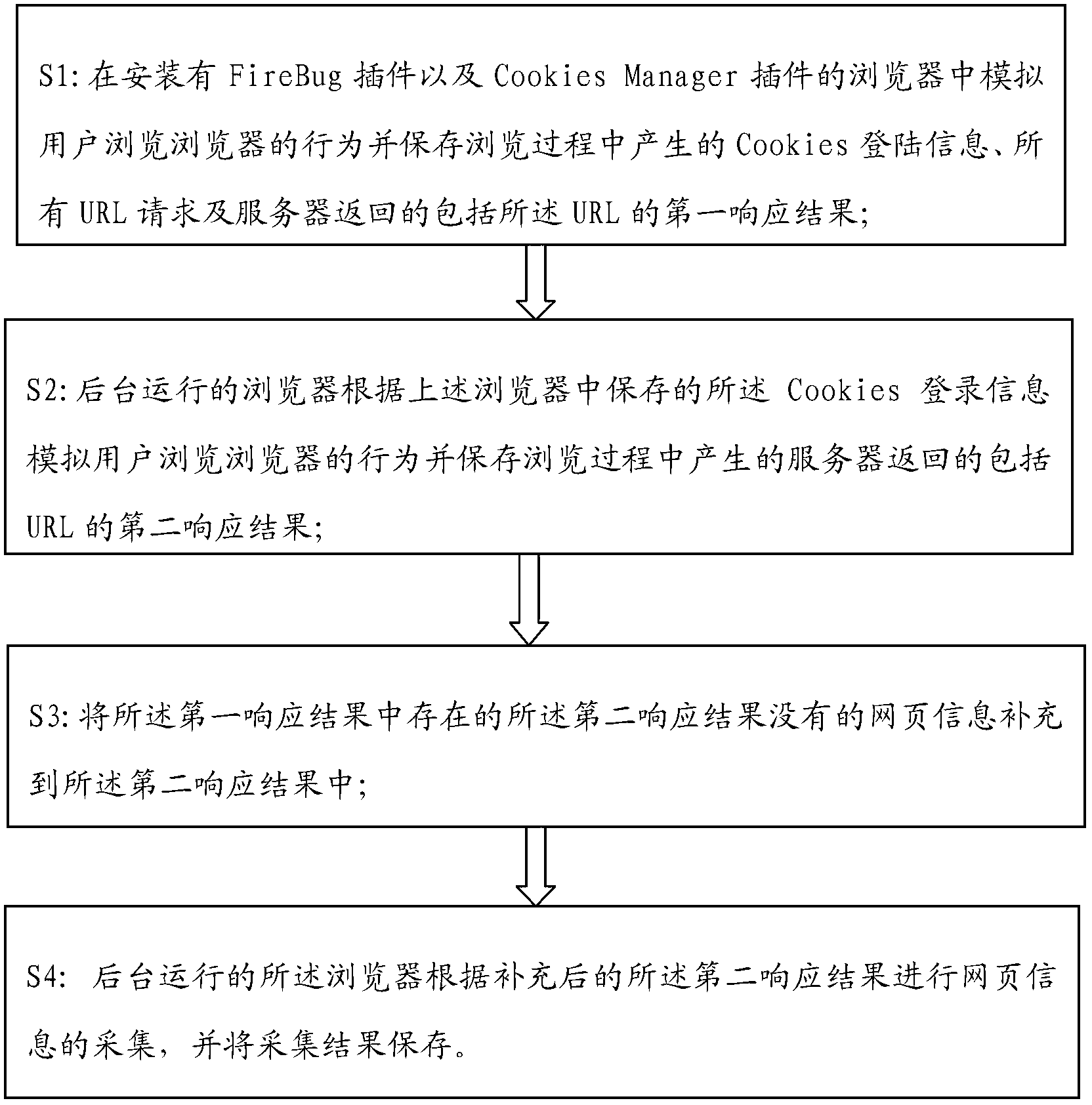
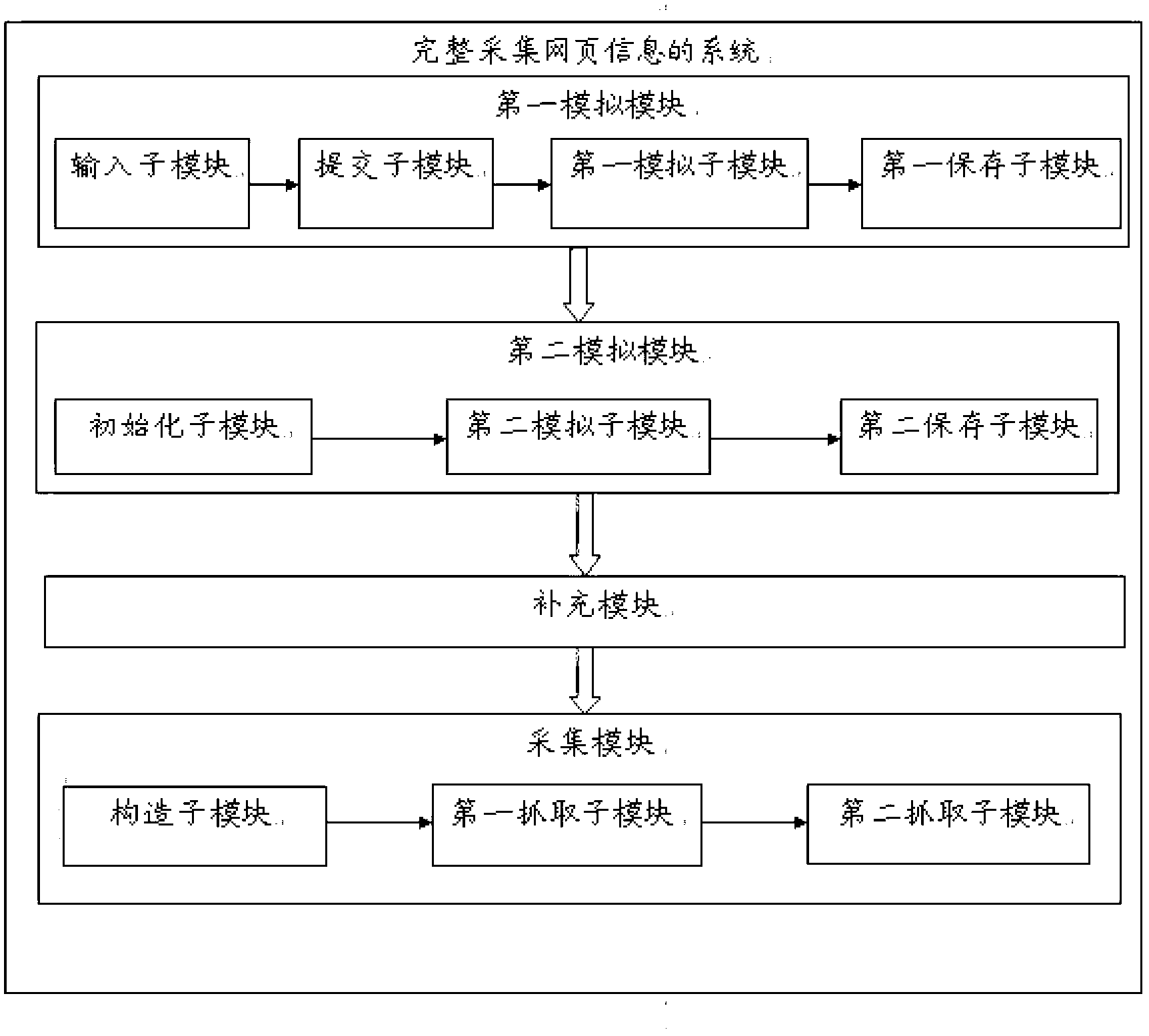
ActiveCN103186670ADoes not take up resourcesSolve the problem that the link page dynamically generated by AJAX cannot be obtainedSpecial data processing applicationsDynamic web pageUniform resource locator
The invention relates to a method and a system for integrally acquiring webpage information. The method comprises the following steps of: (1) simulating the behavior that a user browses a browser in the browser provided with FireBug and Cookies Manager, and storing a first response result returned by Cookies information, all URL (uniform resource locator) requests and a server; (2) simulating the behavior that the user browses the browser and storing a second response result by the browser which is in background operation; (3) compensating the webpage information which is available in the first response result and unavailable in the second response result into the second response result; and (4) acquiring and storing the webpage information according to the compensated second response result by the browser which is in background operation. After the method and the system for integrally acquiring the webpage information provided by the invention are used, the browser which is in background operation can acquire all the webpage information according to the compensated second response result without occupying the resource of the browser, so that the problem that a link page dynamically generated by AJAX (asynchronous java and xml) can not be obtained by a dynamical webpage acquisition method in the prior art can be solved.
Owner:北京中金云网科技有限公司
Print monitoring system and method for universal printer
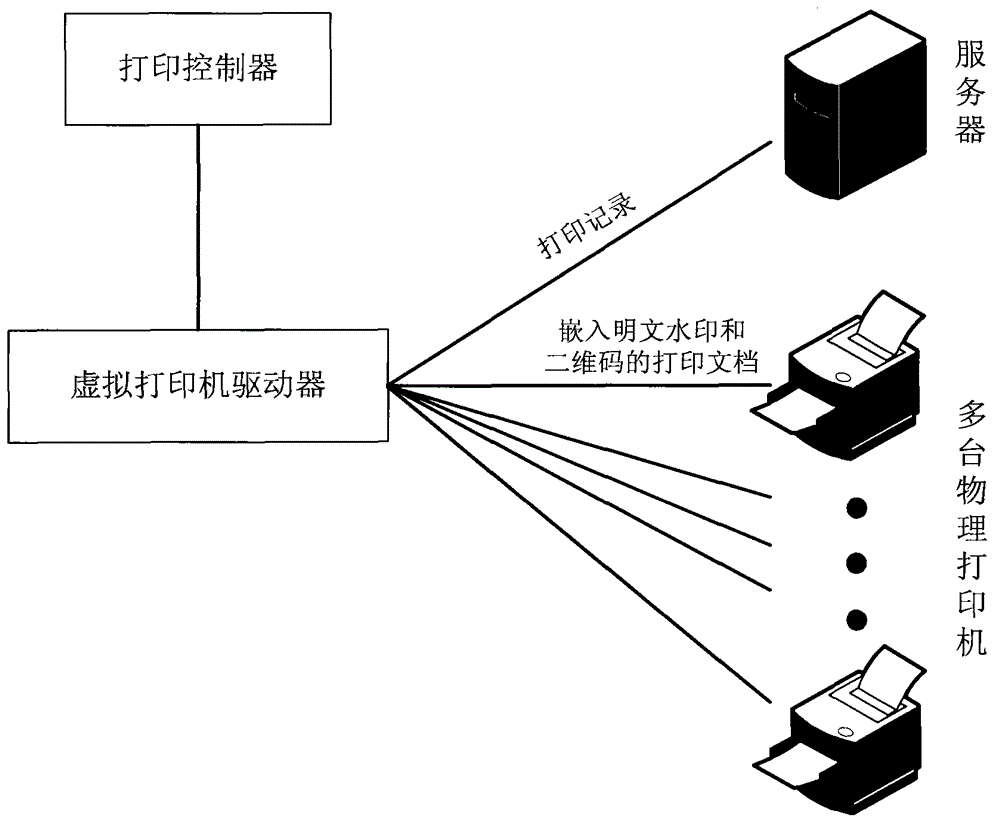
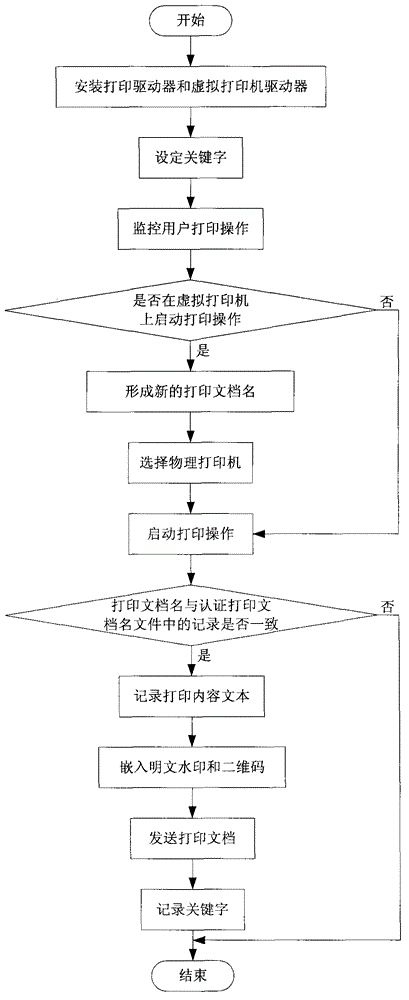
ActiveCN103336923AOvercome the deficiency of manslaughterPracticalPlatform integrity maintainanceVirtual printerMonitoring system
The invention discloses a print monitoring system and a method for a universal printer. The print monitoring system comprises a print control unit, a virtual printer driver, a server and a plurality of physical printers. The print monitoring method comprises the specific steps of: 1, mounting the print control unit and the virtual printer driver, 2, setting a key word, 3, monitoring print operation of a user, 4, forming a new print document name, 5, selecting the physical printer, 6, starting the print operation, 7, recording a print content text, 8, embedding a plaintext watermark and a two-dimensional code, 9, sending the print document, and 10, recording the key word. According to the system and the method, the physical printers are controlled on the premise of not changing allocation of the client printers, and a method effectively auditing the print content and tracing a document source is provided by checking and processing the print content.
Owner:XIDIAN UNIV
Anomaly detection method of internal virtual machine of cloud system
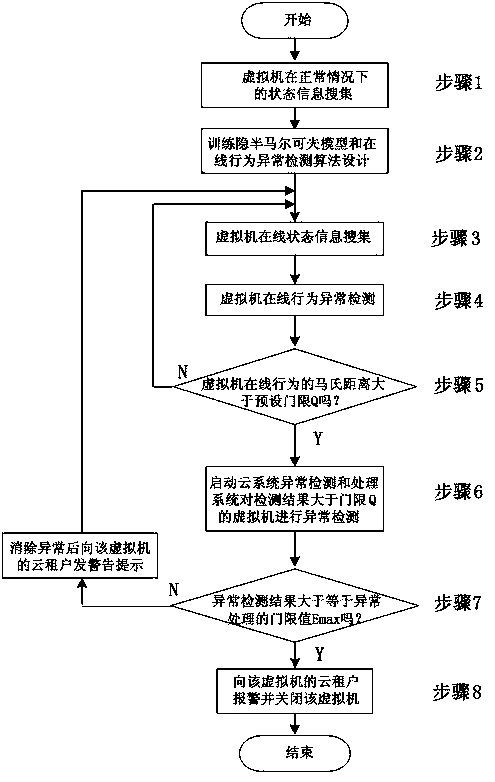
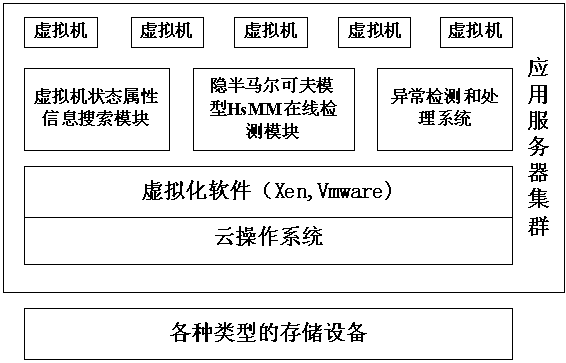
ActiveCN105511944AGuaranteed availabilityGuaranteed real-timeHardware monitoringChaos modelsHidden semi-Markov modelAnomaly detection
The invention relates to an anomaly detection method of an internal virtual machine of a cloud system, which comprises the following steps: state information of a normal virtual machine of the cloud system is collected to train Hidden Semi-Markov Model (HsMM), and a corresponding algorithm is designed for detecting and computing probabilities and mahalanobis distances of resource dynamic change behaviors when various virtual machines in the cloud system are on line; if the mahalanobis distance in the online detection result of some virtual machine is more than a preset threshold value, the activities of the virtual machine are abnormal, so an anomaly detection and processing system in the cloud system is started for anomaly detection and processing of the virtual machine; if the anomaly rate of some virtual machine is detected to be less than the maximum threshold value of the anomaly detection and processing, after the anomaly is eliminated, a warning prompt is sent to a cloud tenant; otherwise, an alarm is given for the cloud tenant of the virtual machine, and the virtual machine is closed. According to the anomaly detection method, abnormal behaviors of the internal virtual machine of the cloud system can be detected in real time, the occupied system resources are less, and the high availability and high safety of the internal virtual machine of the cloud system can be fully ensured.
Owner:SHANGHAI MARITIME UNIVERSITY
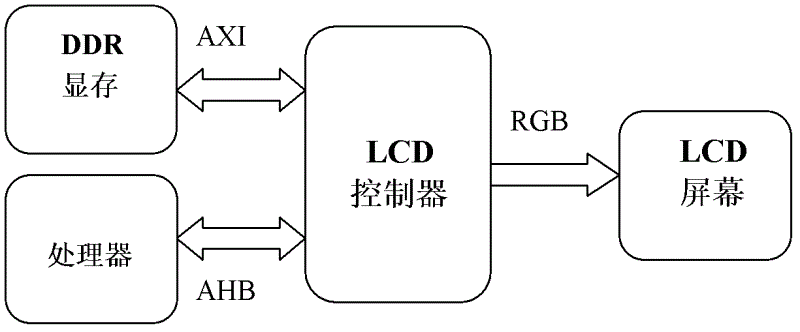
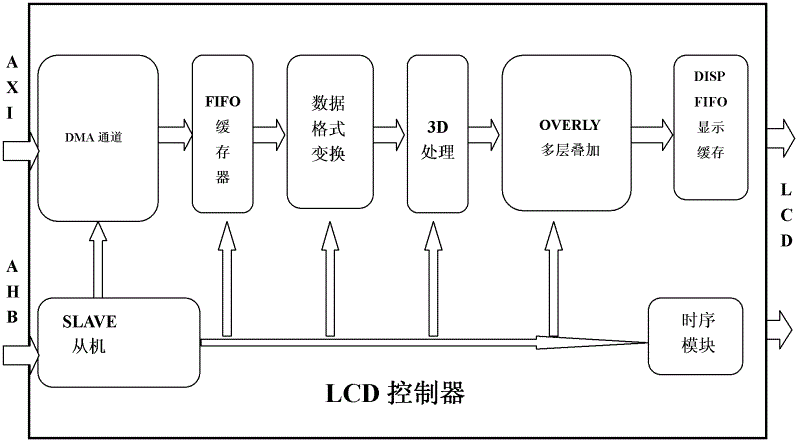
LCD (Liquid Crystal Display) controller and display control method thereof
InactiveCN102622979AMeet needsDoes not take up resourcesStatic indicating devicesDirect memory accessLiquid-crystal display
The invention relates to an LCD (Liquid Crystal Display) controller and a display control method thereof. The LCD controller comprises a slave module, a DMA (Direct Memory Access) channel module, an FIFO (First-In First-Out) buffer, a data format converting module, a 3D (3-Dimensional) processing module, an overly multi-layer overlay module, a DISP (Display) FIFO display cache module and a time sequence module, and supports the functions, such as naked-eye 3D visualization, multi-layer display and automatic restoration. The multi-layer display function is achieved by the LCD controller and isnot subjected to the operation processing of a processor any more, so that the operating speed is increased, and the load of the processor is reduced; the automatic restoration function means that the LCD controller can temporarily stop outputting image data if the condition that bandwidth is insufficient in a short term occurs when the LCD controller plays a high-definition video, and outputs the image data again until the bandwidth is enough, and the image data are sufficient; and as the condition that the bandwidth is insufficient is an occasional and short-term case, the display control method can solve the problems of screen cracking and screen blurring arising from short-term insufficient bandwidth on the basis of not affecting a watching effect.
Owner:SOUTHEAST UNIV
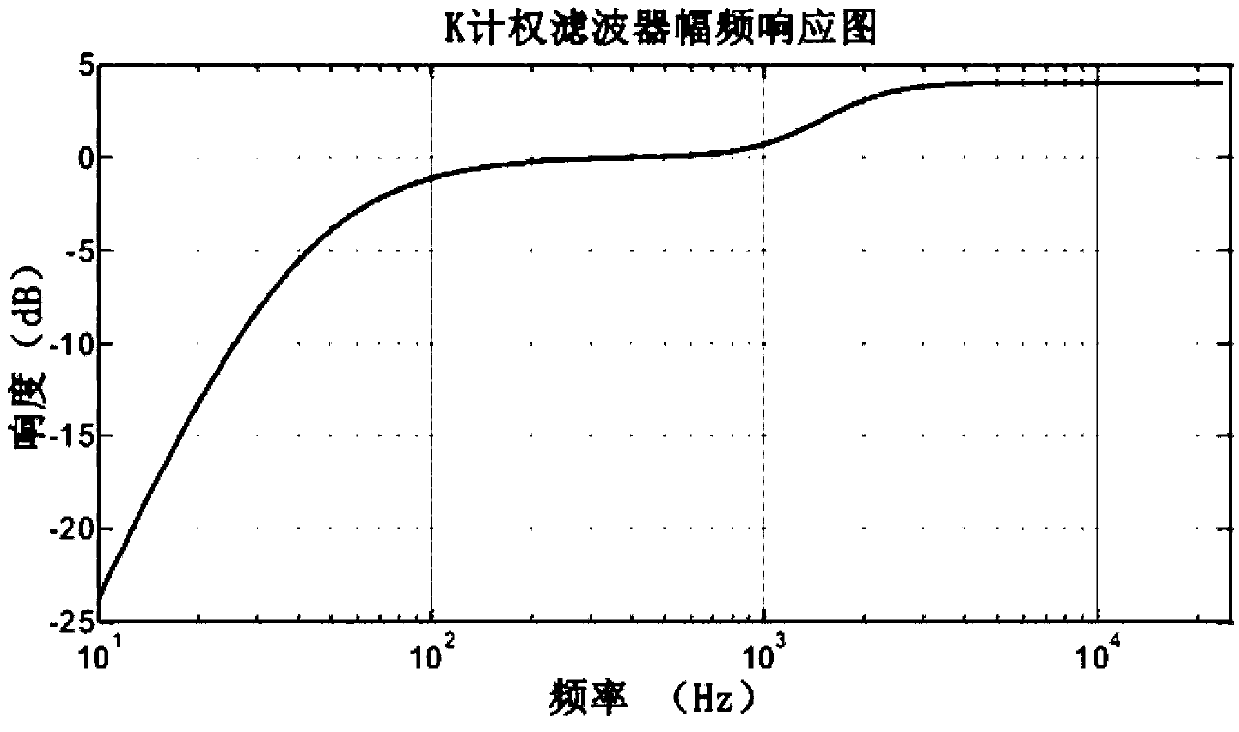
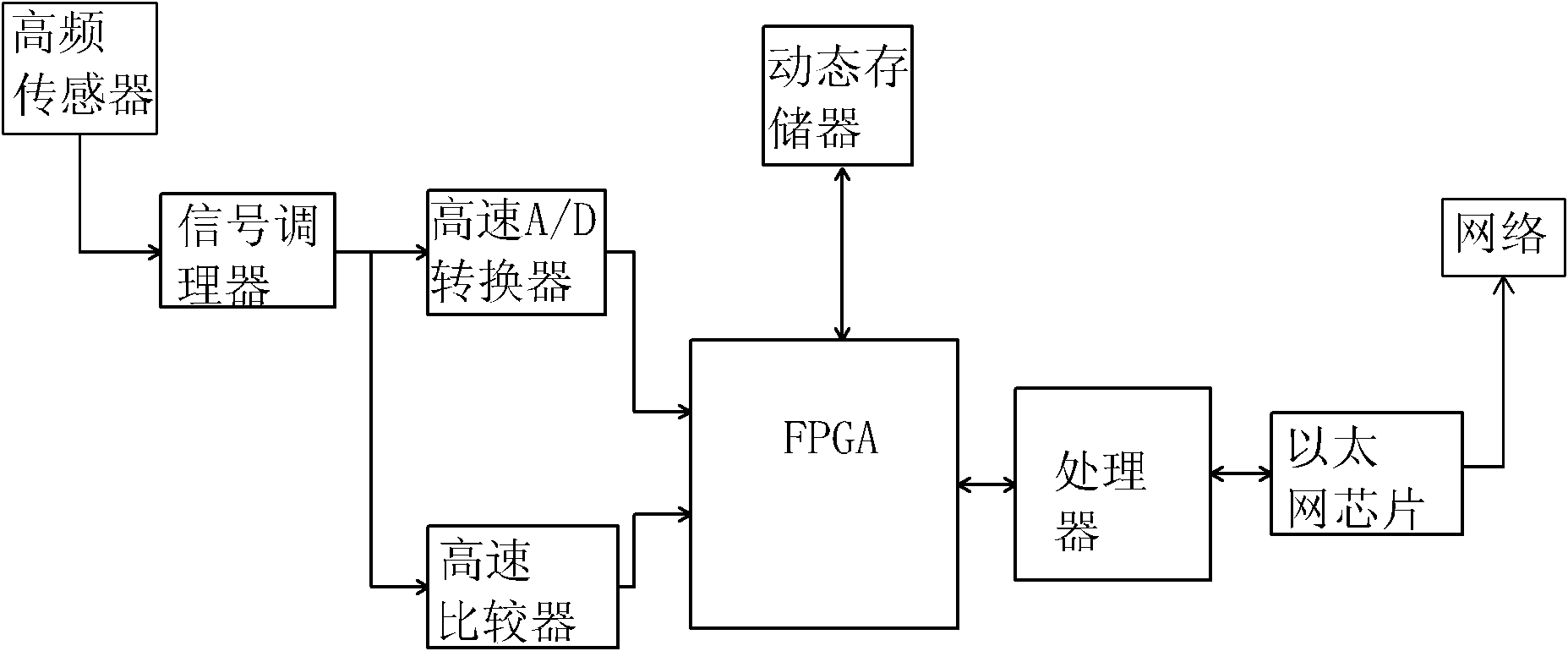
Method for monitoring digital audio signal volume
The invention provides a method for monitoring digital audio signal volume. The method is achieved by combined action of hardware and programs. A digital audio signal volume monitoring card which comprises a digital audio acquisition unit, a decoding unit, a volume computing unit and a communication unit is adopted for the hardware. A computer accesses the volume monitoring card through the programs, and under the condition of not affecting other producing and playing normal operation, the volume of input audio signals and the dynamic range of the volume are recorded, displayed, stored and analyzed; the digital audio volume monitoring card acquires the digital audio signals and computes the corresponding volume of the audio signals; the digital audio acquisition unit is provided with three sets of input interfaces, and each set of the interface is provided with three input interface circuits suitable for digital audios with AES / EBU signals or S / PDIF signals, the input interface circuits are used for receiving the AES / EBU signals or the S / PDIF signals input in a balanced mode and imbalanced mode respectively; the volume computing unit computes the volume data result.
Owner:NANJING LANGSHENG ACOUSTIC TECH
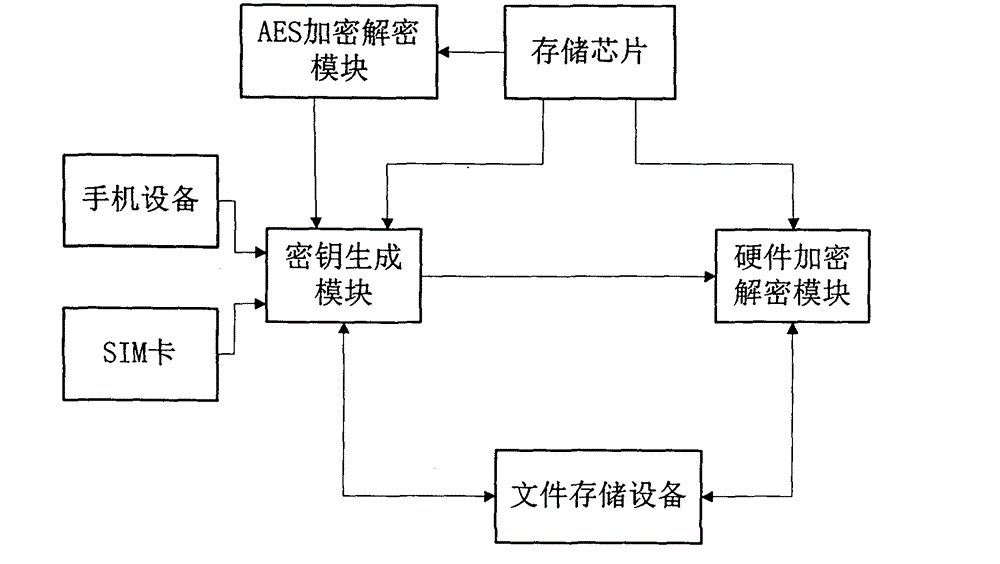
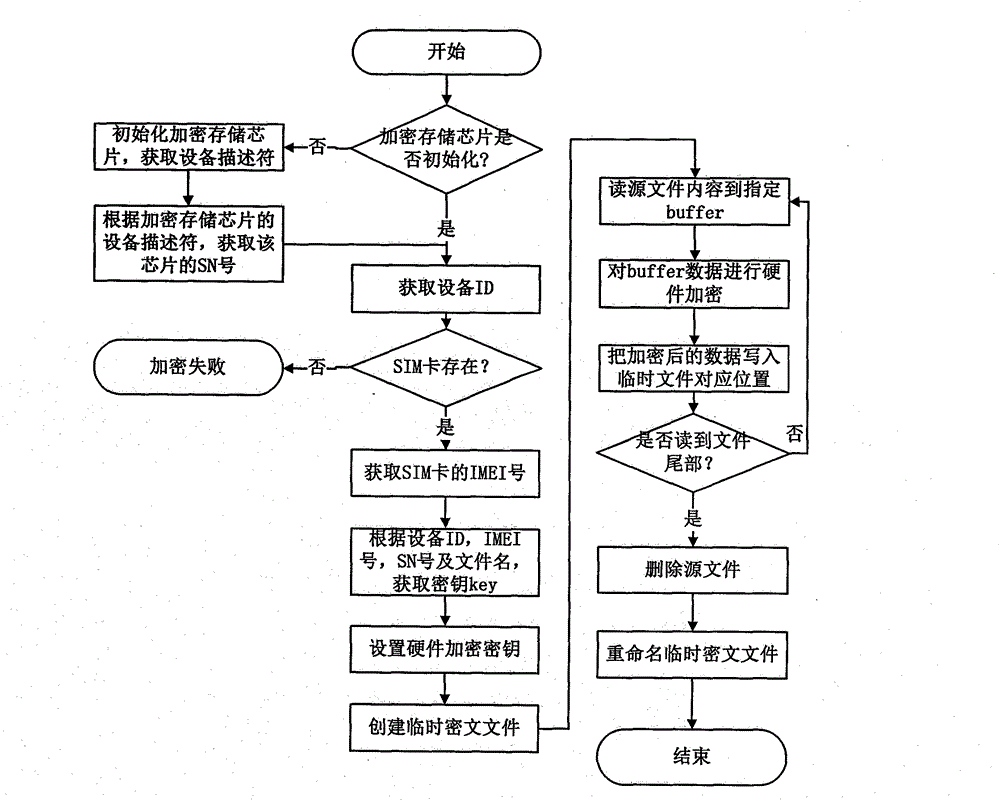
Hardware encryption protection method and system for cellphone data
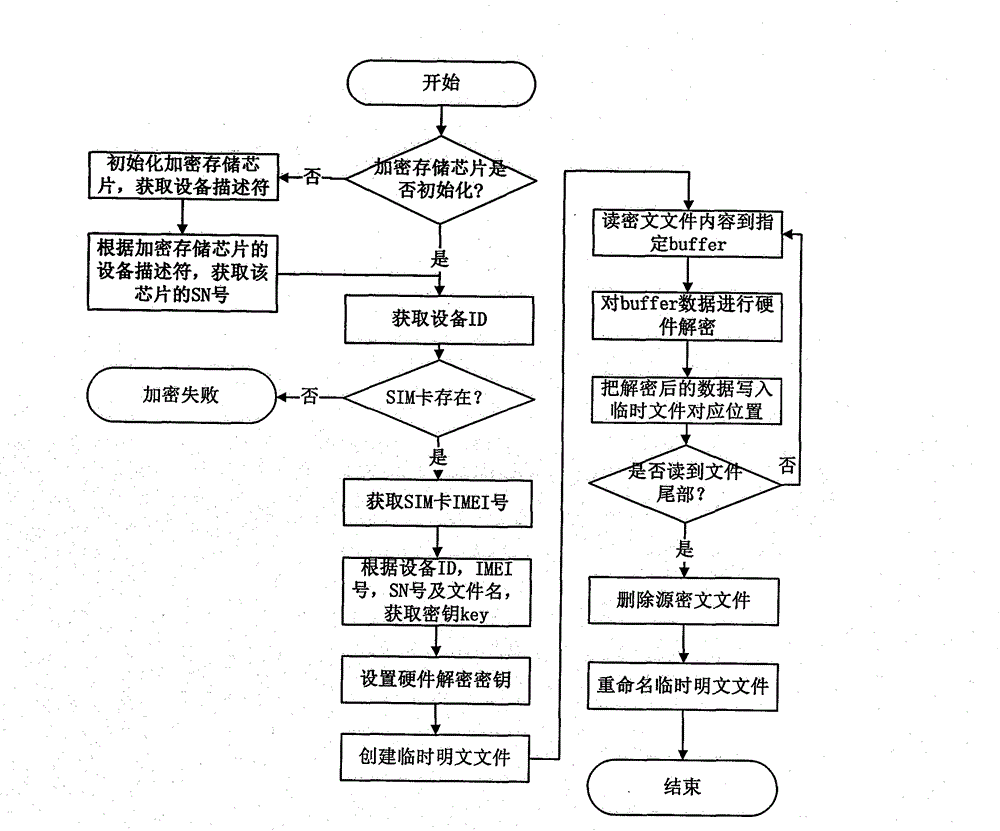
ActiveCN103559453AMeet encryption protection needsDoes not take up resourcesDigital data protectionComputer moduleEncryption decryption
The invention discloses a hardware encryption protection method and system for cellphone data. The hardware encryption protection method includes utilizing ID (identity) of a cellphone, IMEI (international mobile equipment identity) numbers of an SIM (subscriber identity module), SNs (serial numbers) of a storage chip and name of a source file as dynamic parameters, calling a key generating module and an AES (advanced encryption standard) encrypting and decrypting module to generate Keys for encryption and decryption by being matched with logic calculation; calling a hardware encrypting module to encrypt the file or data for the source file. The key generating module, the AES encryption and decryption module and the encryption and decryption module operate file storage equipment through the storage chip, data encryption and decryption are completed, and the storage chip is welded on a circuit board of the cellphone and provided with an independent core processor. The hardware encryption protection technology for the cellphone data overcomes the defects of the prior art, is free of system resource occupation, has high performance, safety and reliability, and can effectively meet the encryption protection requirements on important files of people.
Owner:深圳市中易通安全芯科技有限公司
On-orbit noise autonomous restraint method for APS star sensor
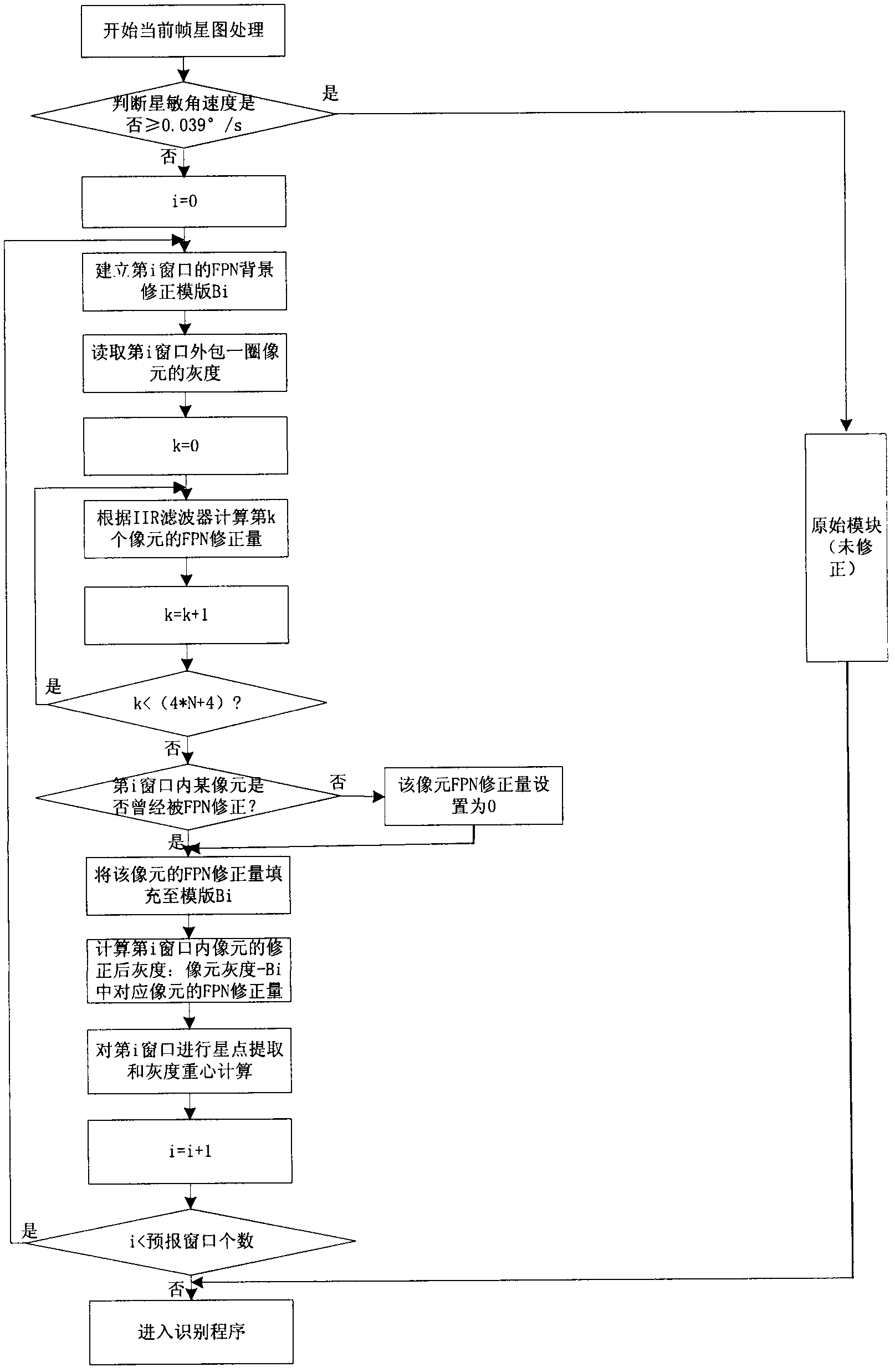
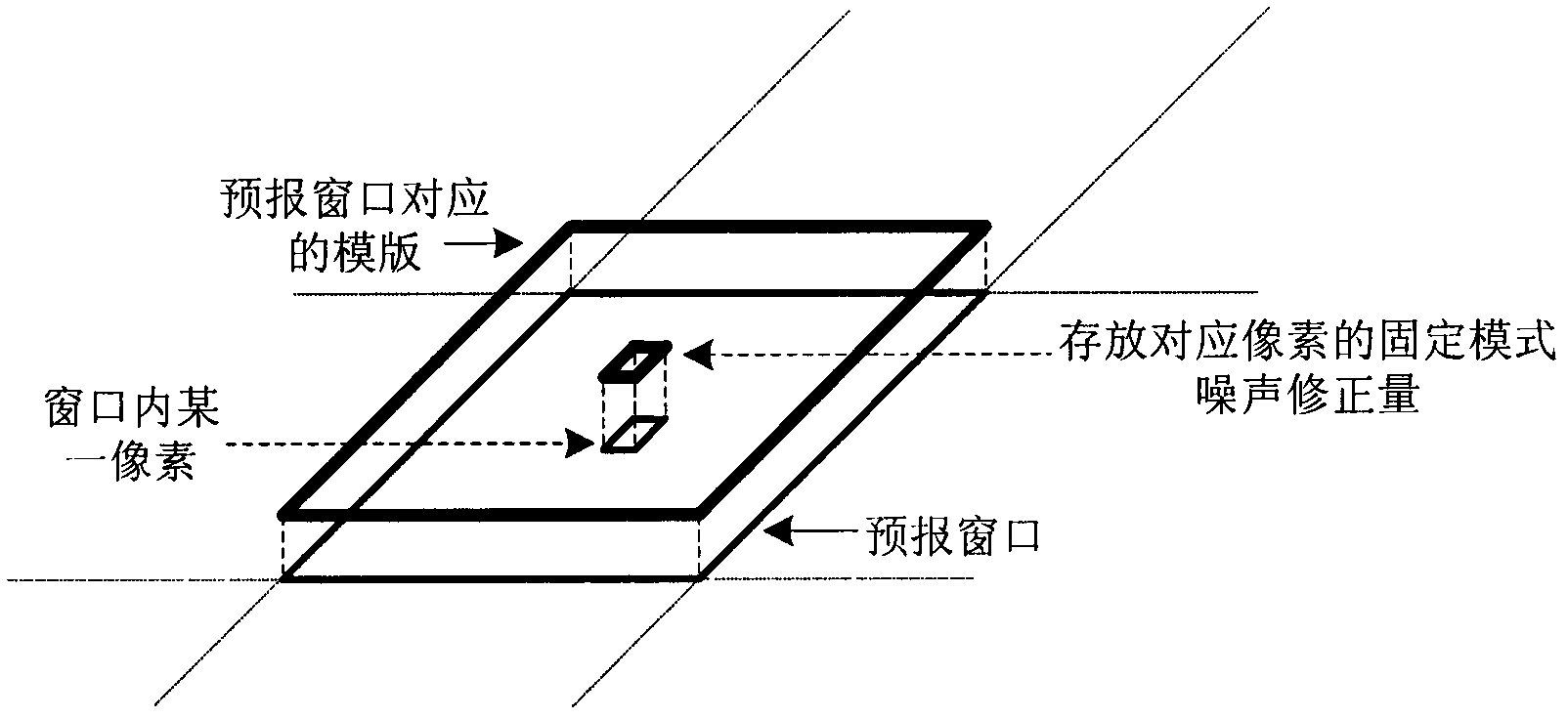
ActiveCN102564457ASuppresses and eliminates spatial noiseFull of noiseNavigation by astronomical meansStar sensorSelf adaptive
The invention discloses an on-orbit noise autonomous restraint method for an APS star sensor, and is applied before pixel traverse and star point extraction are conducted on a forecast window. Firstly, IIR self-adapting filter processing is conducted on the externally coated circle of pixel of the forecast window; the fixed mode noise correction of pixel gray level is calculated for later use; then whether the pixel in the precast window is corrected or not is defined; when the pixel in the precast window is corrected, the correction of the pixel is written into a corresponding position of a mold plate; when the pixel in the precast window is not corrected, the original gray level of the pixel in the precast window is compared with corresponding correction to obtain a corrected gray level; and then the pixel traverse and the star point extraction are conducted on the window according to the corrected pixel. The method has the advantages that no hardware resource is occupied; the method is realized by software; no ground calibration is required; and the real-time performance and the autonomy are high.
Owner:BEIJING INST OF CONTROL ENG
Network safe content processing card based on FPGA
InactiveCN101483649AHigh Content Processing CapabilityEfficiency is not affectedTransmissionWire speedNetwork packet
The invention relates to a network safety content processing card based on FPGA (field programmable gate array). The invention provides a method for solving the problem that contradiction between network safety and network speed and contradiction between network management and network cost are becoming serious. The method comprises giving first place to an FPGA safety chip, adopting a PCI card inserted into a PCI slot of a server, performing data communication with the server by using a PCI express interface protocol, connecting with an outer network through kilomega network ports for completing data receiving and sending, realizing byte-by-byte content detection, content labeling, and flow recombination of the server data under a kilomega line speed, and at the same time, realizing functions of network flow real-time controlling, blocking, inbreak detecting and log auditing. By adopting the invention, networking cost can be reduced, CPU resources of servers can be saved, a CPU can focus on completing other functions, and therefore, the integral performance of the system is improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
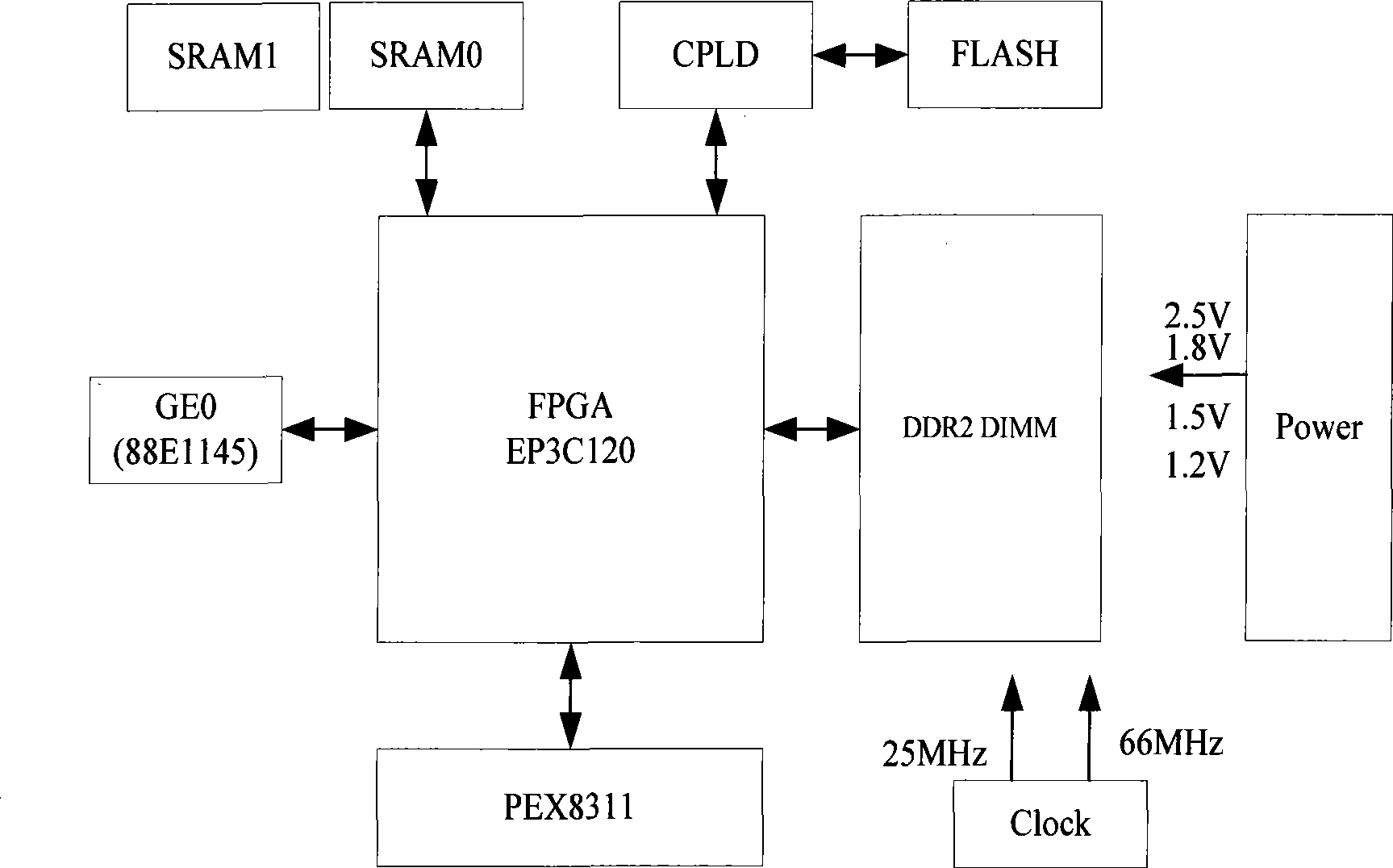
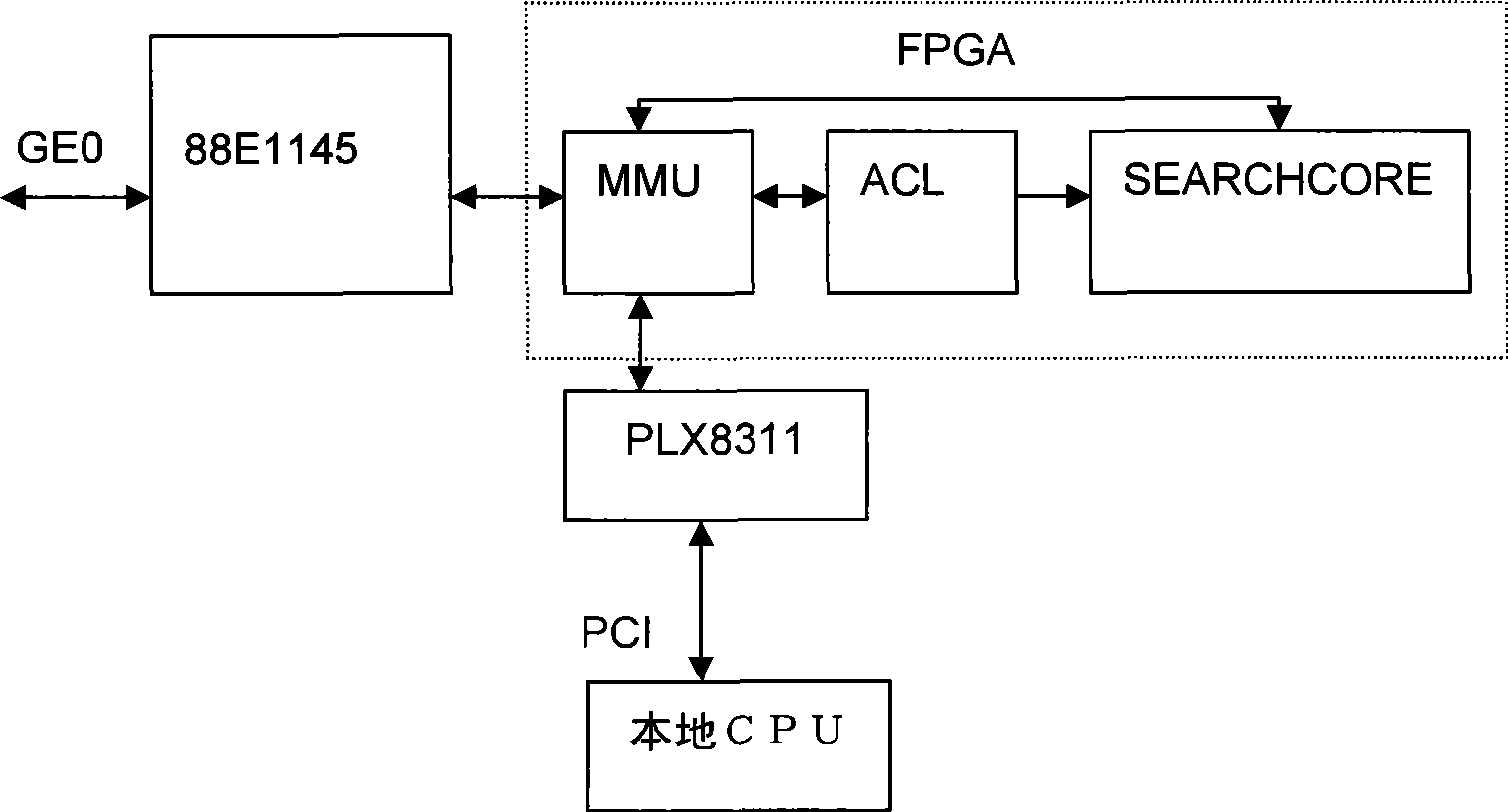
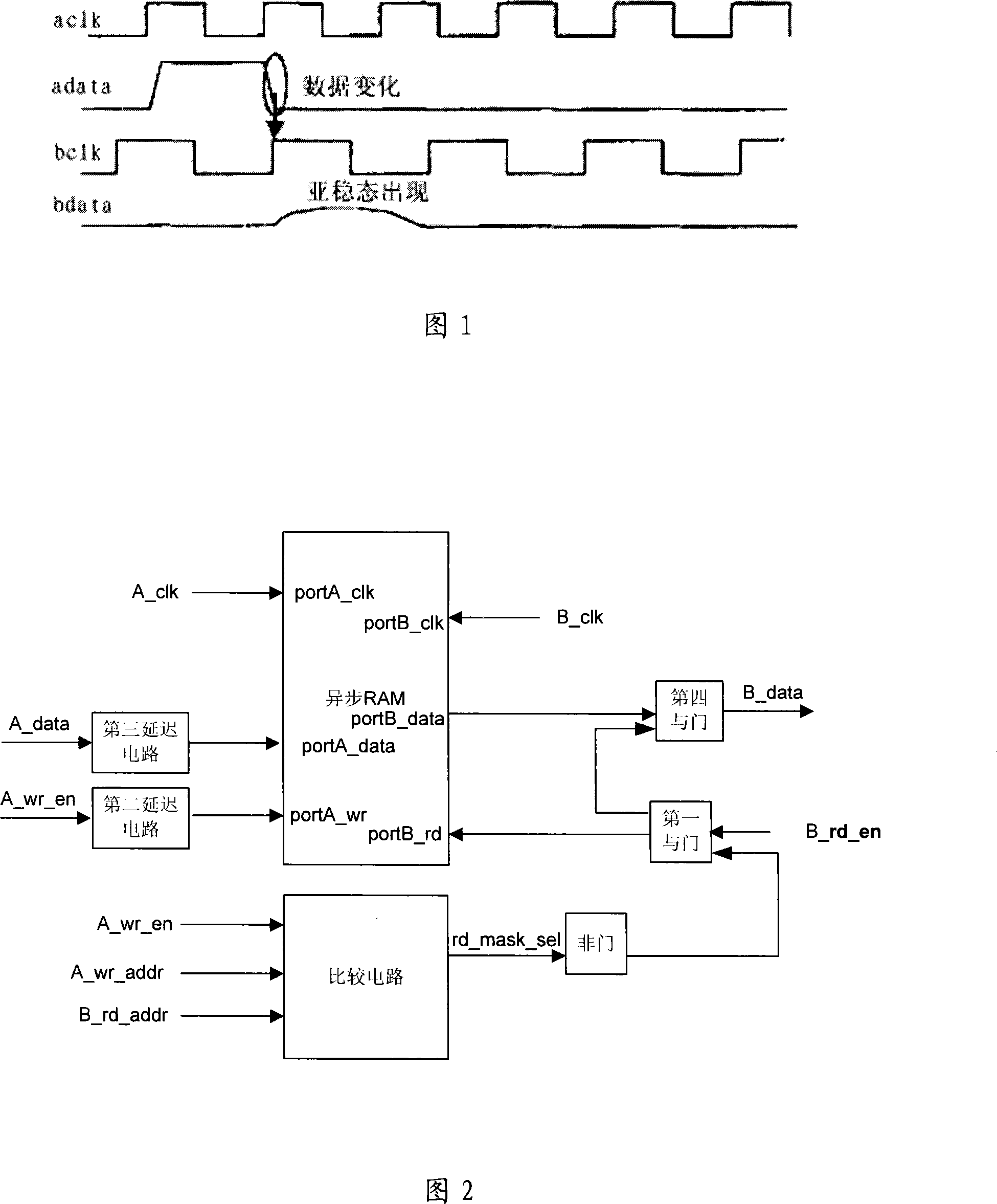
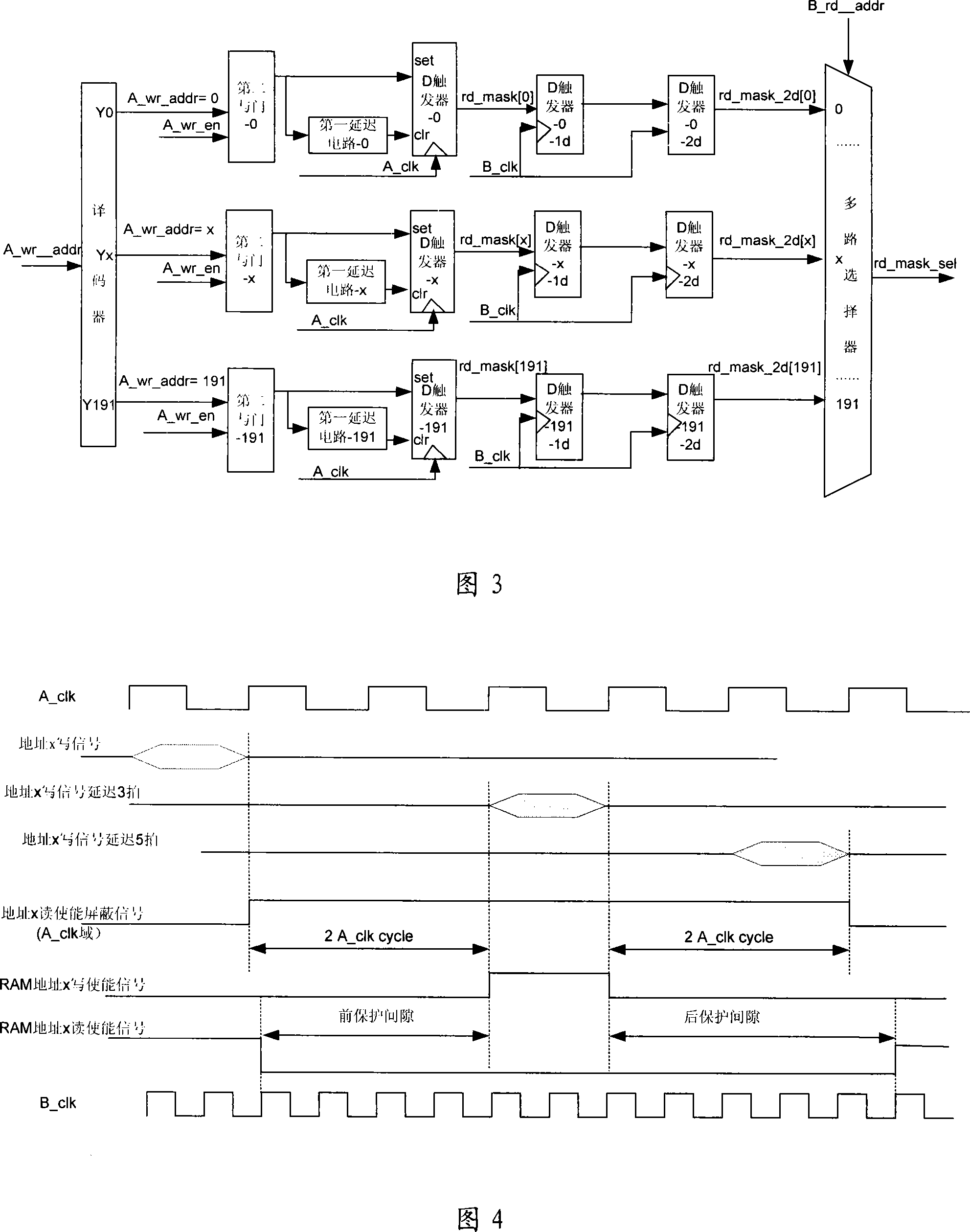
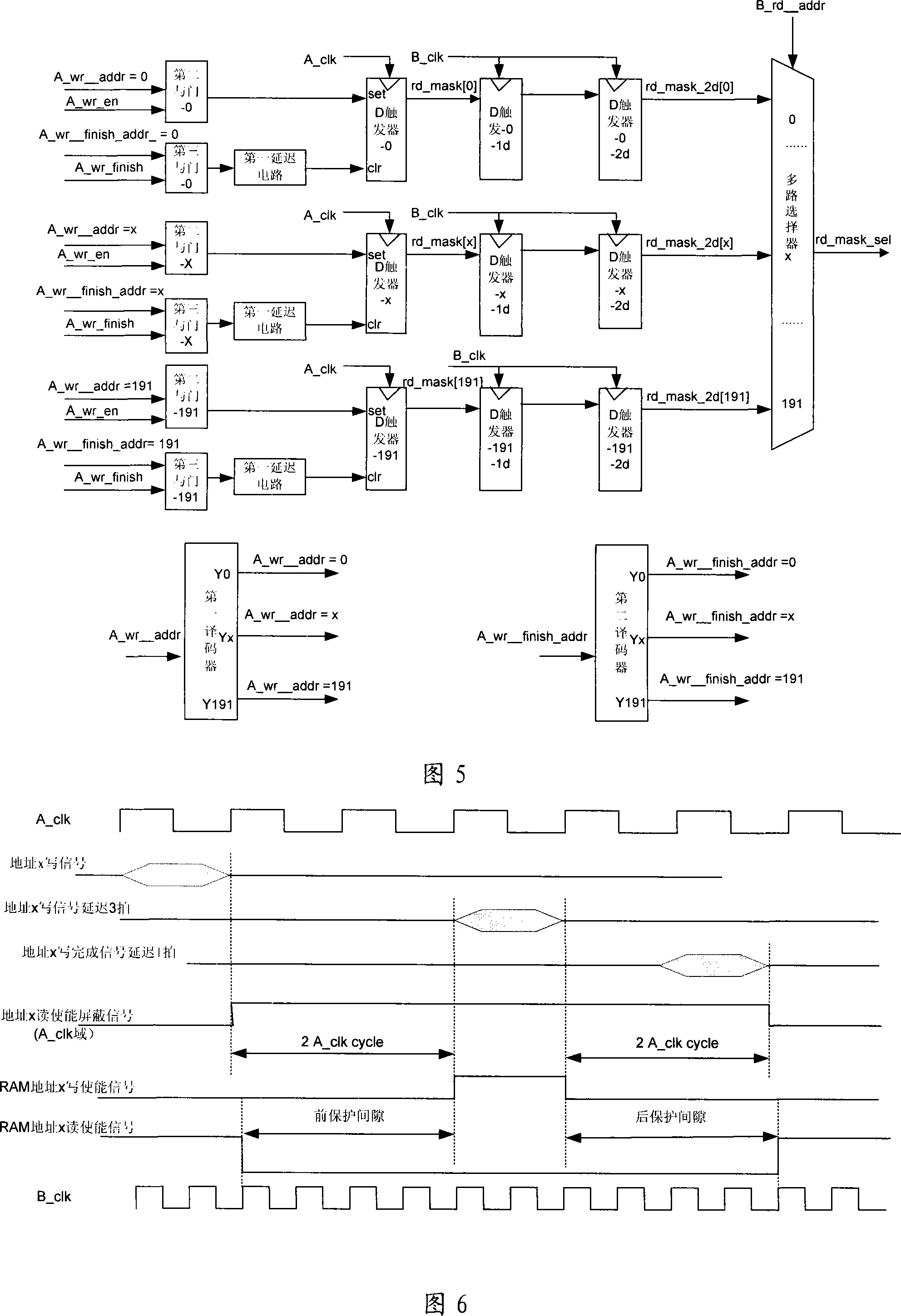
Read-write control circuit, method and apparatus for two-port RAM
ActiveCN101226767AAvoid reading and writing conflictsDoes not take up resourcesDigital storageControl circuitDual-ported RAM
The practical example of the invention discloses a read write control circuit with a dual-port RAM, a device and a method thereof, relating to the technical field of storage, and the invention is invented for evading read write conflict problem of the dual-port RAM. The circuit comprises a comparison circuit, a negation gate and a first coincidence gate, wherein the comparison circuit is used to output read screen signals of a storage unit corresponding with bus signals of a second port address, the negation gate is used to inverse the read screen signals of the storage unit which are corresponding with the bus signals of the second port address, one input end of the first coincidence gate receives the read screen signals of the storage unit which are corresponding with the bus signals of the second port address after being inversed, the other input end of the first coincidence gate receives the read enable signals of a second port, and the output end of the first coincidence gate is connected with the read enable end of the second port. The practical example of the invention can be used in chip circuit designing.
Owner:HONOR DEVICE CO LTD
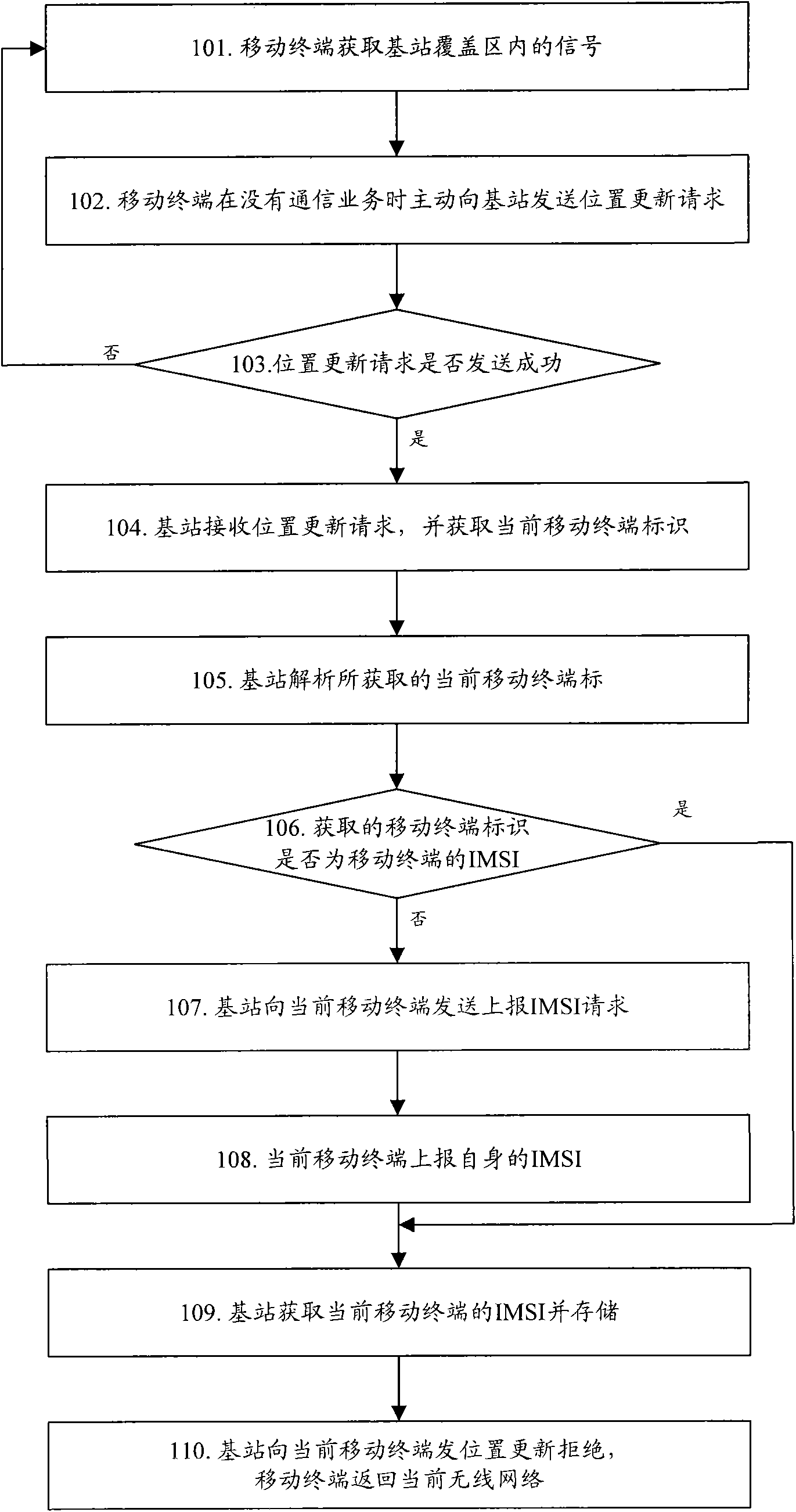
Method and device for acquiring international mobile subscriber identity of mobile communication terminal by base station
InactiveCN101631302AWill not affect normal operationDoes not take up network resourcesAssess restrictionNetwork data managementInternational mobile subscriber identityWireless network
The invention discloses a method for acquiring international mobile subscriber identity (IMSI) of a mobile communication terminal by a base station. The base station is integrated with partial functions of a wireless network controller and a core network; and the method also comprises that: when not having communication service, the mobile communication terminal actively initiates a position update request to the base station; and the base station simulates the current wireless network to receive the position update request, and acquires the IMSI of the current mobile communication terminal in the position updating process of the mobile communication terminal. The invention also discloses a device for acquiring the IMSI of the mobile communication terminal by the base station. The method and the device can timely acquire the IMSI of the mobile communication terminal in the coverage area of the base station.
Owner:ZTE CORP
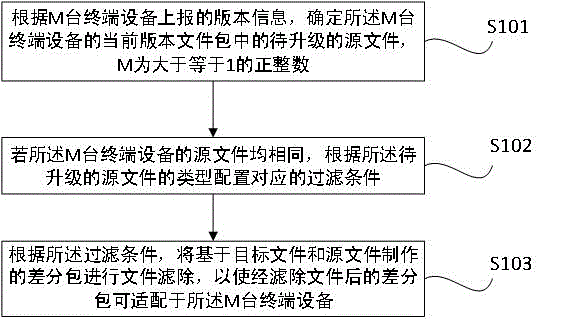
Difference package manufacturing method and device
InactiveCN105487907ADoes not take up resourcesSoftware engineeringProgram loading/initiatingSoftware updateTerminal equipment
The invention discloses a differential package manufacturing method and device. The method comprises: determining the source files to be updated in the current version file packages of M terminal devices according to the version information reported by M terminal devices, wherein M is a positive integer more than or equal to 1; if the source files of the M terminal devices are the same, configuring corresponding filtering conditions according to the types of the source files to be updated; carrying out file filtering to the differential packages manufactured basing on target files and source files so that the differential packages after file filtering are adaptive to the M terminal devices. According to the invention, the problems in the prior art are solved; the problems comprise that under the condition that the software updating contents are the same, the updating packages of multiple versions are needed to be manufactured for the terminals with different hardware information so that the updating packages are adaptive to the terminals, therefore, the development and test cost is wasted, and more system server resources are occupied. The terminal devices of different sizes used in the invention can share the target files of the same version.
Owner:HISENSE VISUAL TECH CO LTD
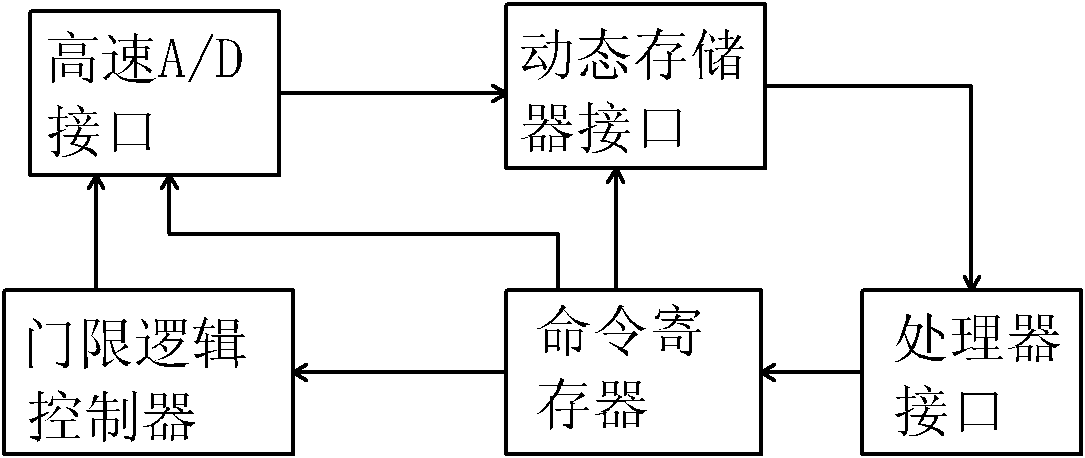
Chip debugging device, debugging method and SOC (System of Chip) chip system
InactiveCN105808396AImprove soundnessDoes not take up resourcesFaulty hardware testing methodsAdvanced Microcontroller Bus ArchitectureEmbedded system
The invention discloses a chip debugging device, a debugging method and an SOC (System of Chip) chip system. The chip debugging device is characterized in that a conversion module carries out serial-parallel conversion on input debugging command data; an analysis module analyzes the debugging command data after serial-parallel conversion into an AMBA (Advanced Microcontroller Bus Architecture) bus command and obtains executive result data obtained by a chip through executing the AMBA bus command, so that a function module in the chip is accessed according to the AMBA bus command, read and write operations are carried out on the function module in the chip and an operation result is returned to the conversion module; and the conversion module outputs the operation result after serial-parallel conversion to complete debugging of the chip. In comparison with the prior art, a chip debugging process of the chip debugging device provided in the embodiments of the invention does not need participation of a CPU (Central Processing Unit), CPU resources are not occupied, and the chip is debugged based on the AMBA bus command, so that the function module in the SOC chip can be debugged, and thus the integrity of chip debugging is improved.
Owner:ZHEJIANG DAHUA TECH CO LTD
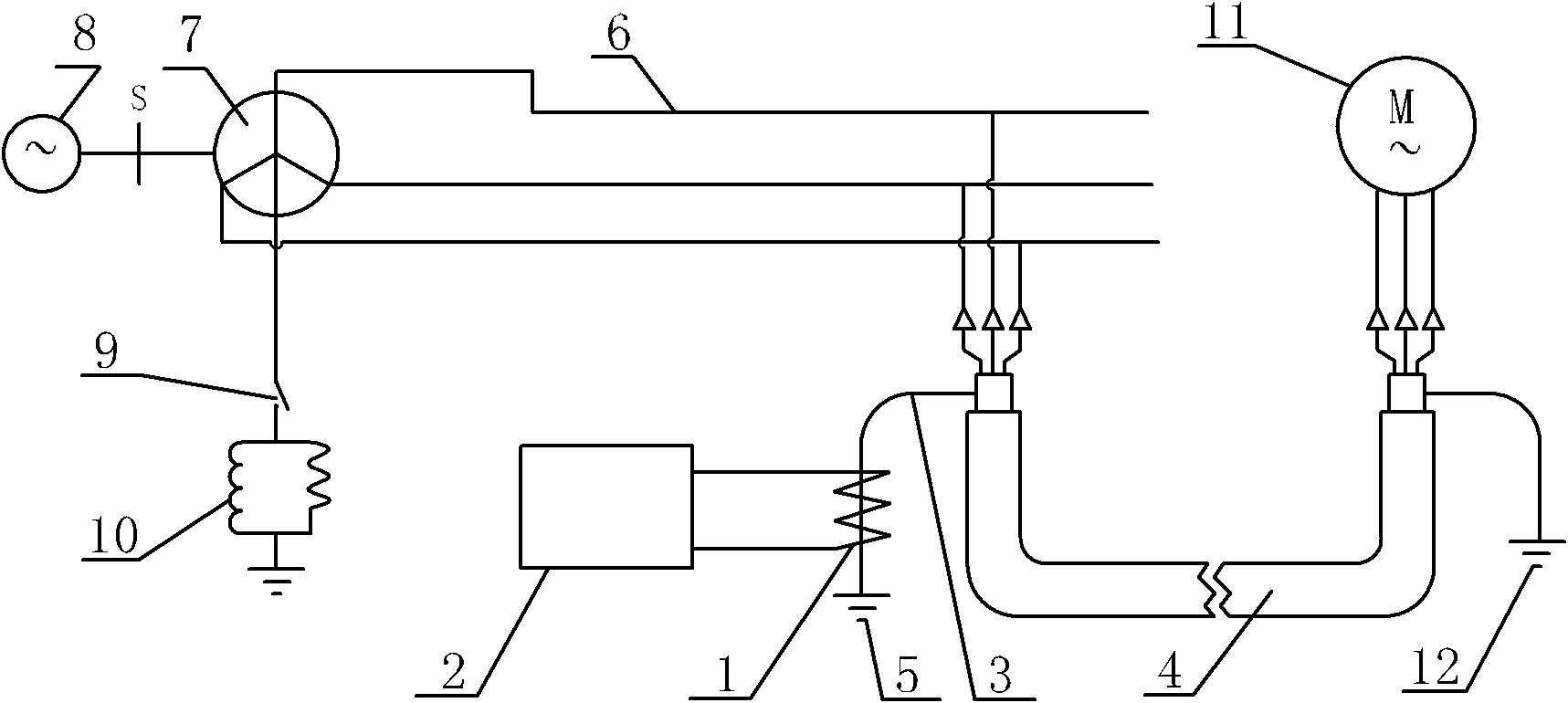
On-line early warning method of failure of cross-linked polyethylene power cable
ActiveCN101819244ARealize online fault warningDoes not take up resourcesFault locationPower cableElectrical conductor
The invention relates to an on-line early warning method for failure of a cross-linked polyethylene power cable, belonging to the field of on-line monitoring of power cables and comprising a cross-linked polyethylene power cable to be detected. The on-line early warning method for failure of the cross-linked polyethylene power cable is characterized in that when restorable failure of a certain cross-linked polyethylene power cable to be detected is detected and recorded on line in real time, an instantaneous electromagnetism transient signal flowing through a metal shielding layer earthing conductor of the power cable to be detected is generated, and the instantaneous electromagnetism transient signal is analyzed by utilizing a specific criterion so as to make an early warning for the power cable to be detected. By adopting the on-line early warning method of the restorable failure of the power cable, on-line early warning is performed on the restorable failure before the cable is damaged, which is beneficial for the power supply departments to overhaul in advance or in a planned way, avoiding sudden failure of the cable to cause power failure, reducing economic loss caused by the power failure and adverse effect brought for enterprise production and people's life, and improving the reliability of the power supply.
Owner:淄博文广电气有限公司 +1
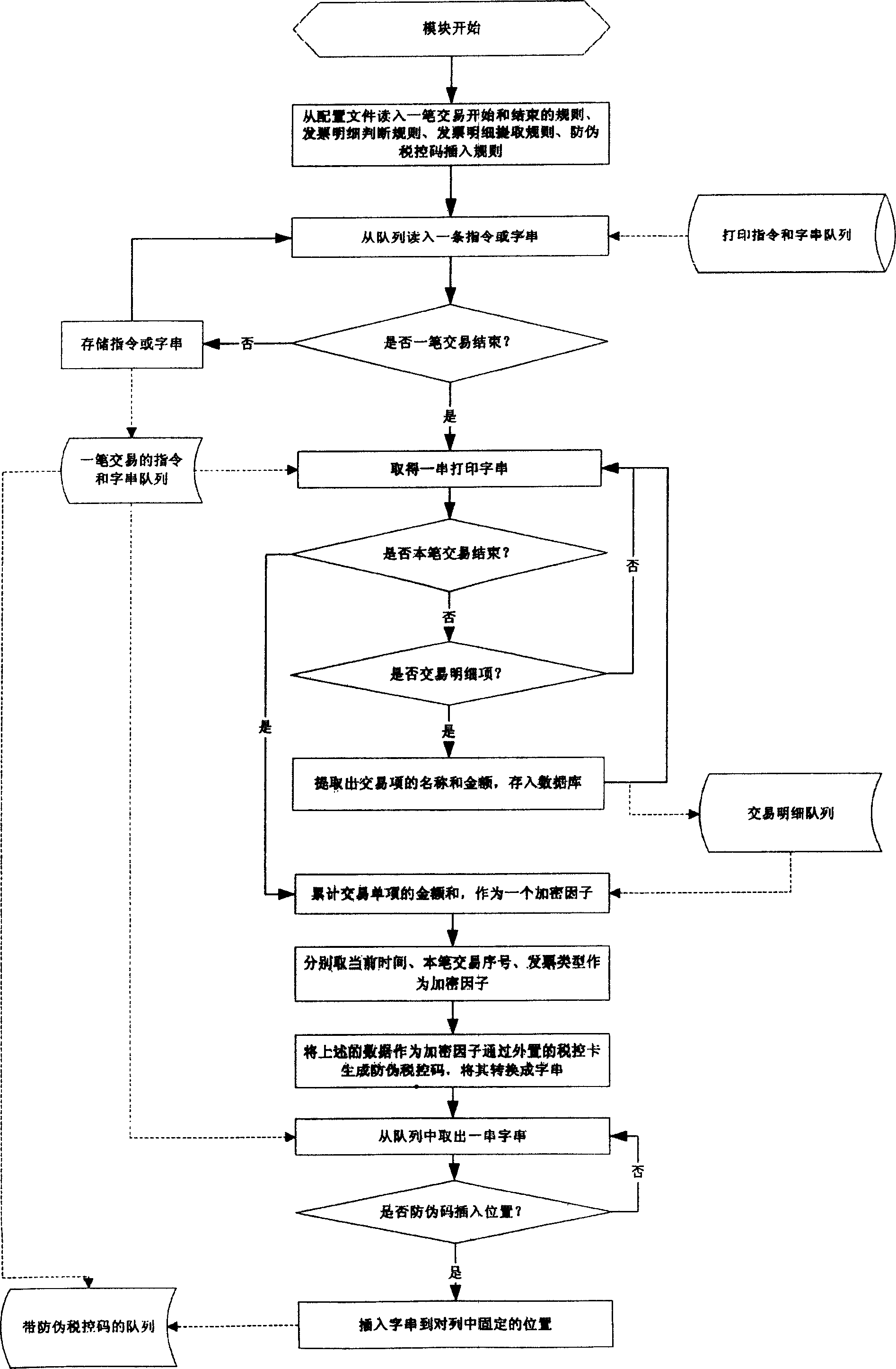
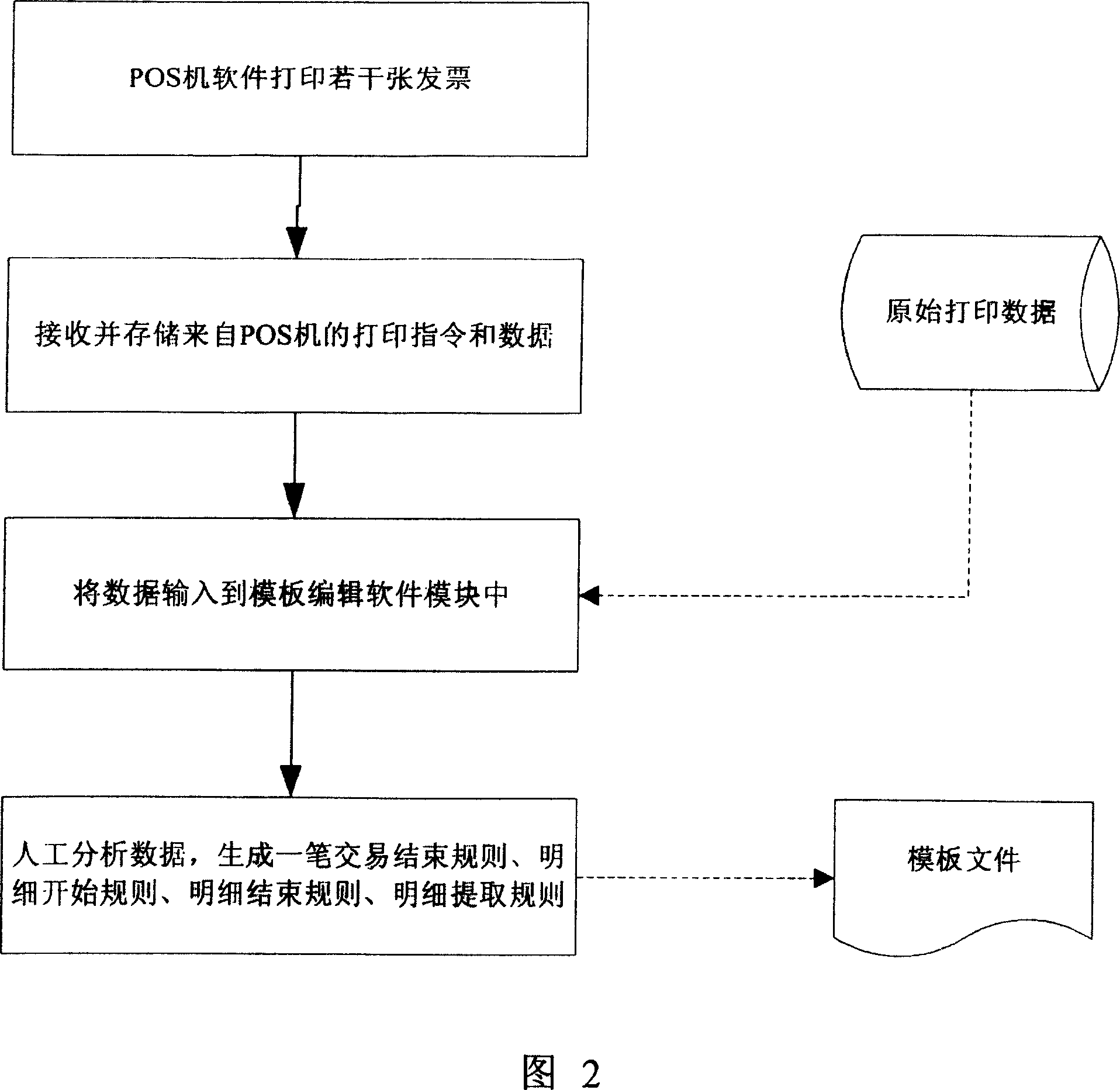
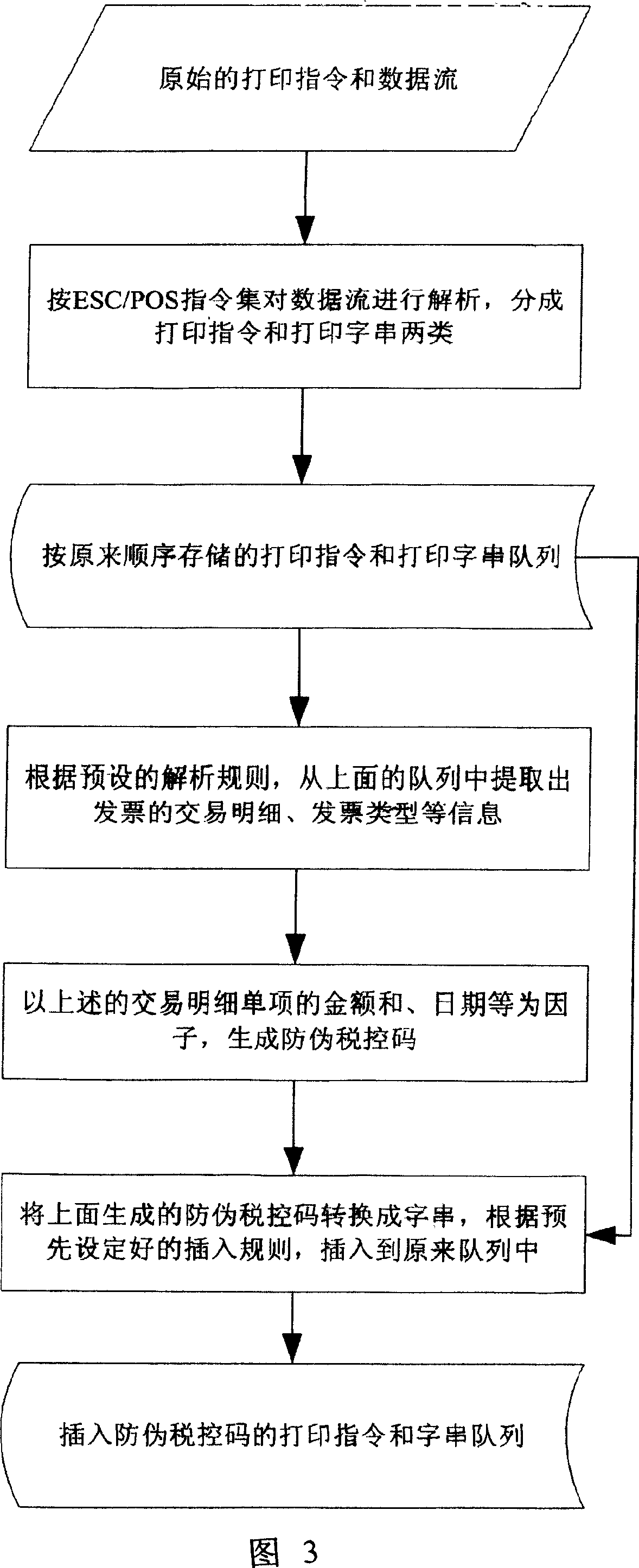
Method for generating fakeproof fiscal code in printing data outputted from POS
InactiveCN1924787AHigh transparencyImprove anti-counterfeiting performanceCash registersSpecial data processing applicationsData streamSoftware system
Owner:HISENSE INTELLIGENT COMML SYST CO LTD
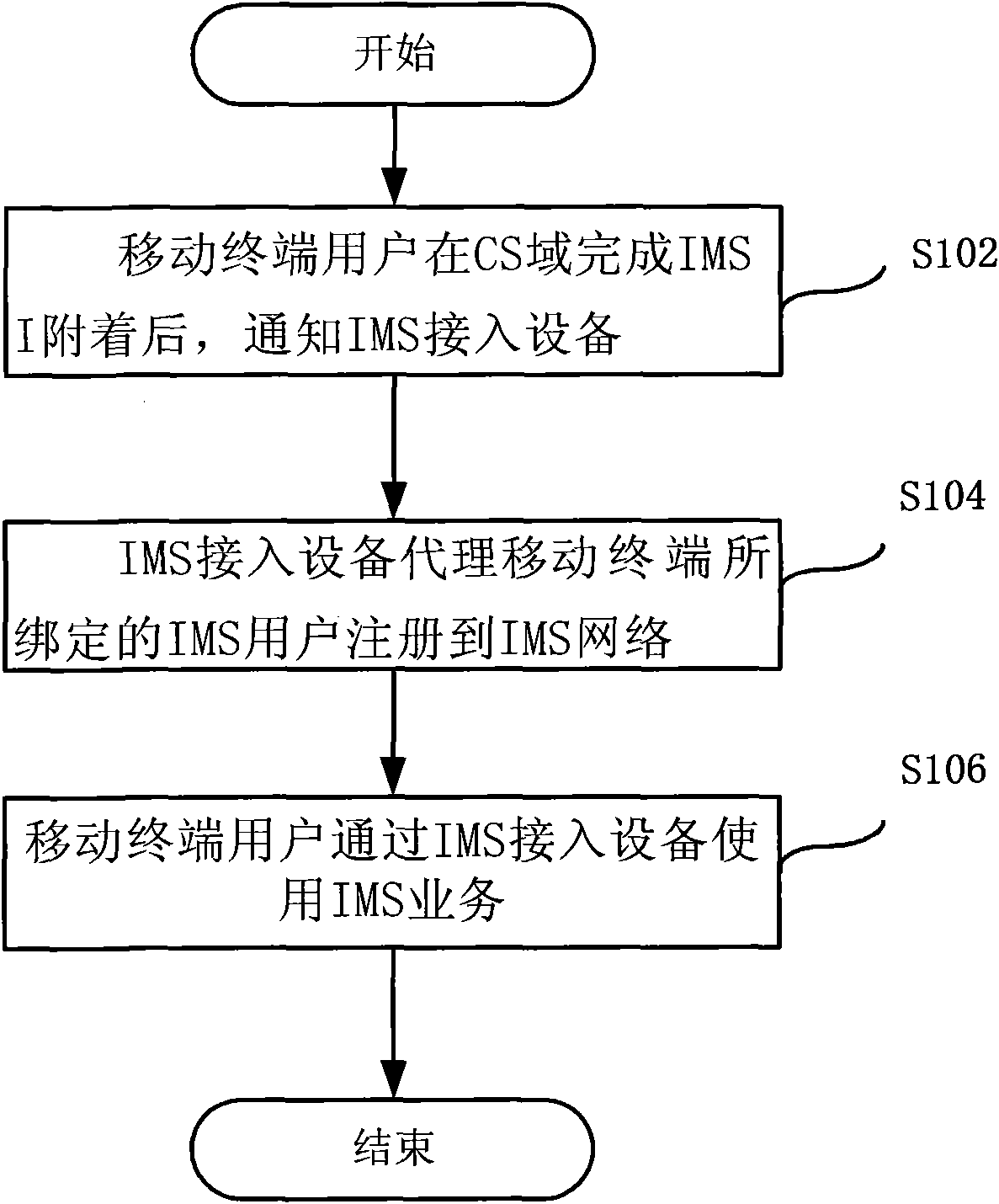
Method for using Internet protocol (IP) multimedia subsystem (IMS), equipment and system
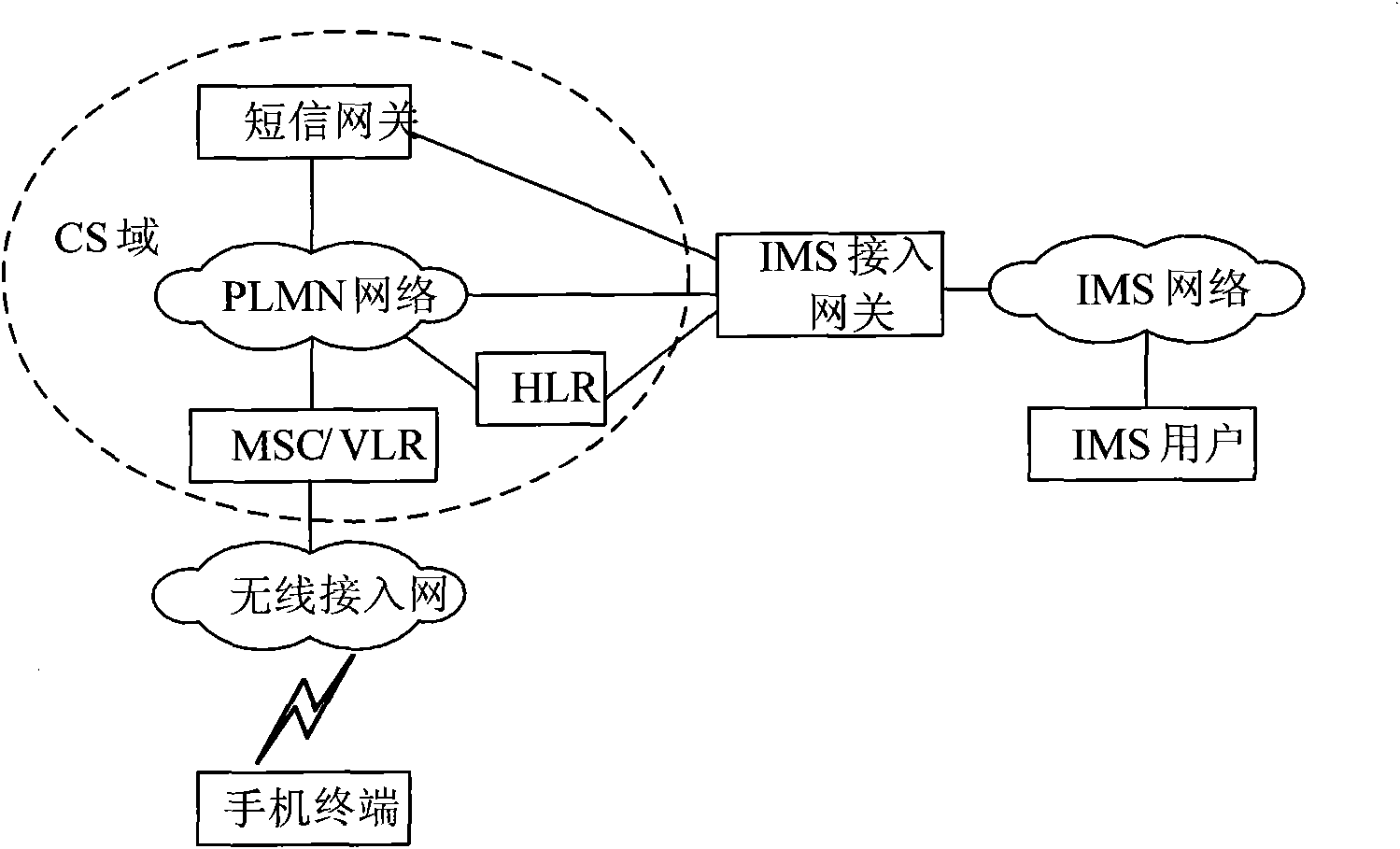
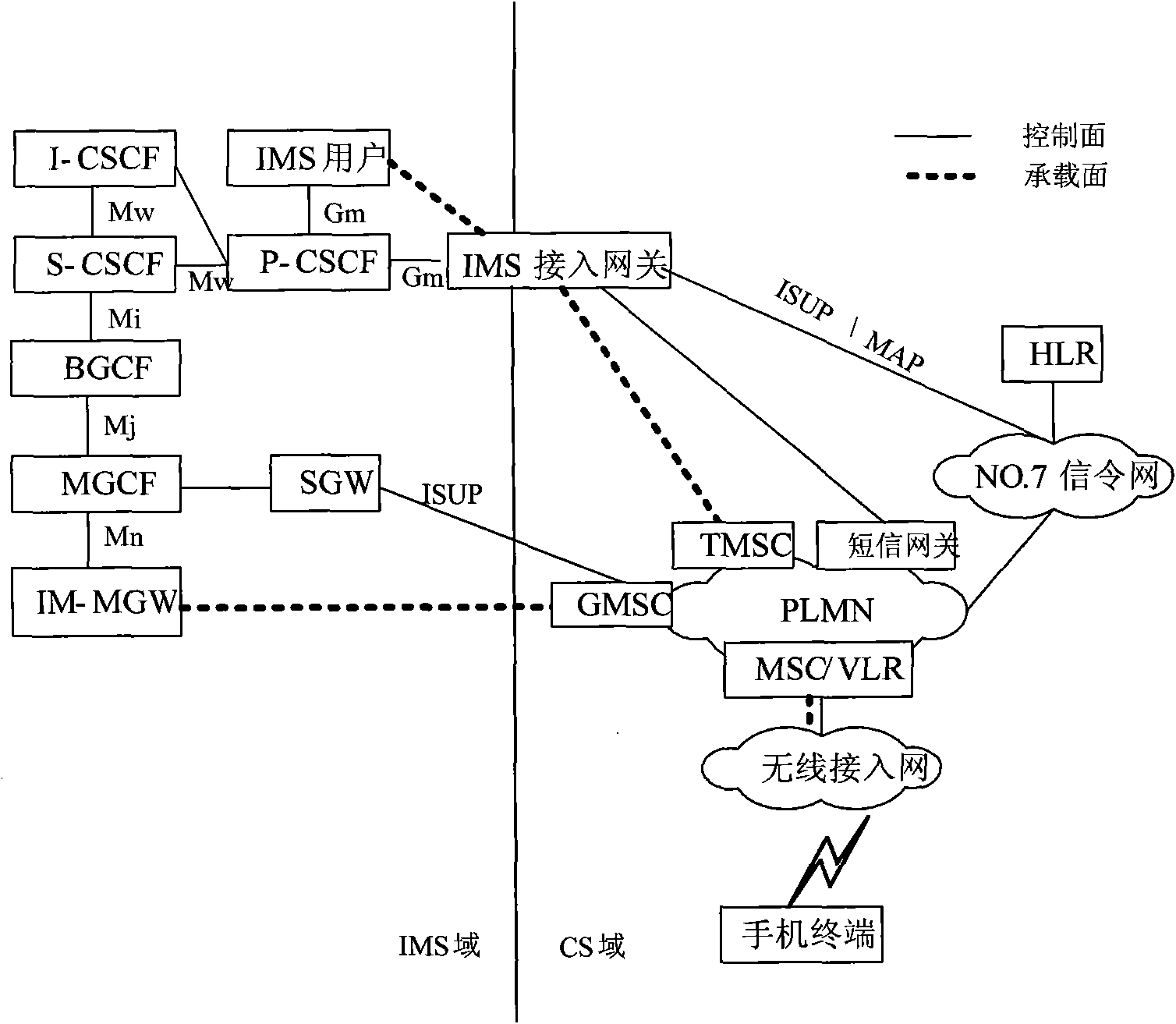
InactiveCN102075501AMeet voiceMeet instant messageTransmissionInternet protocol suiteComputer terminal
The invention discloses a method and a system for using an Internet protocol (IP) multimedia subsystem (IMS), and equipment. The method comprises that: after finishing the attachment of international mobile subscriber identity in a circuit switched (CS) domain, a mobile terminal subscriber informs the IMS access equipment; the IMS access equipment registers an IMS subscriber bound with the mobile terminal subscriber to an IMS network as a proxy; and the mobile terminal subscriber uses an IMS service by the IMS access equipment. In the method, the equipment and the system, the IMS service can be used by the CS domain without installing a client, requiring the subscriber to keep a registration state all the time and occupying a great number of network resources, the IMS subscriber can online use the service in real time, various requirements of the IMS service can be simultaneously met, and the shortcomings of use of the IMS service through IP access in the prior art are overcome.
Owner:CHINA MOBILE COMM GRP CO LTD
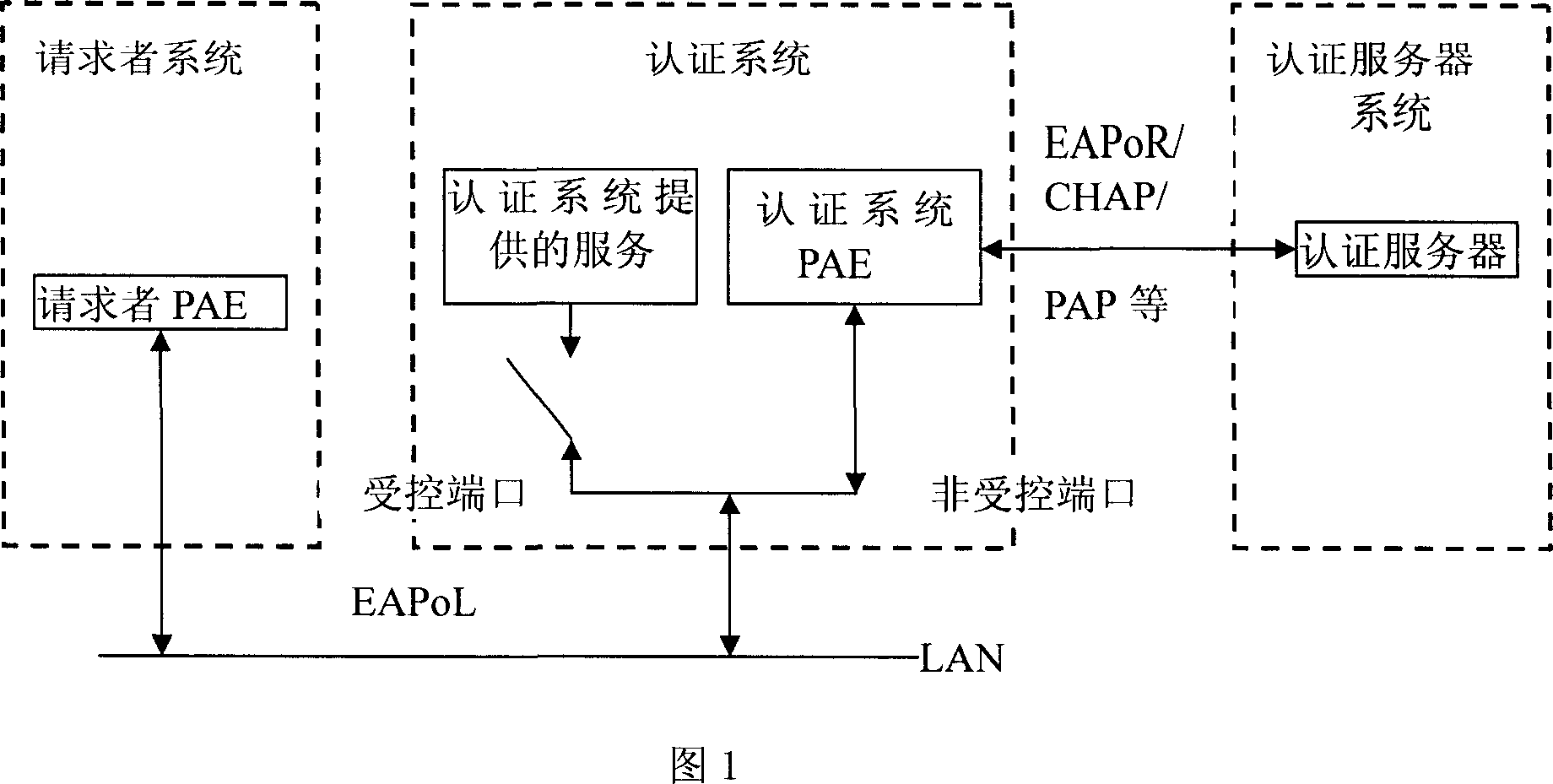
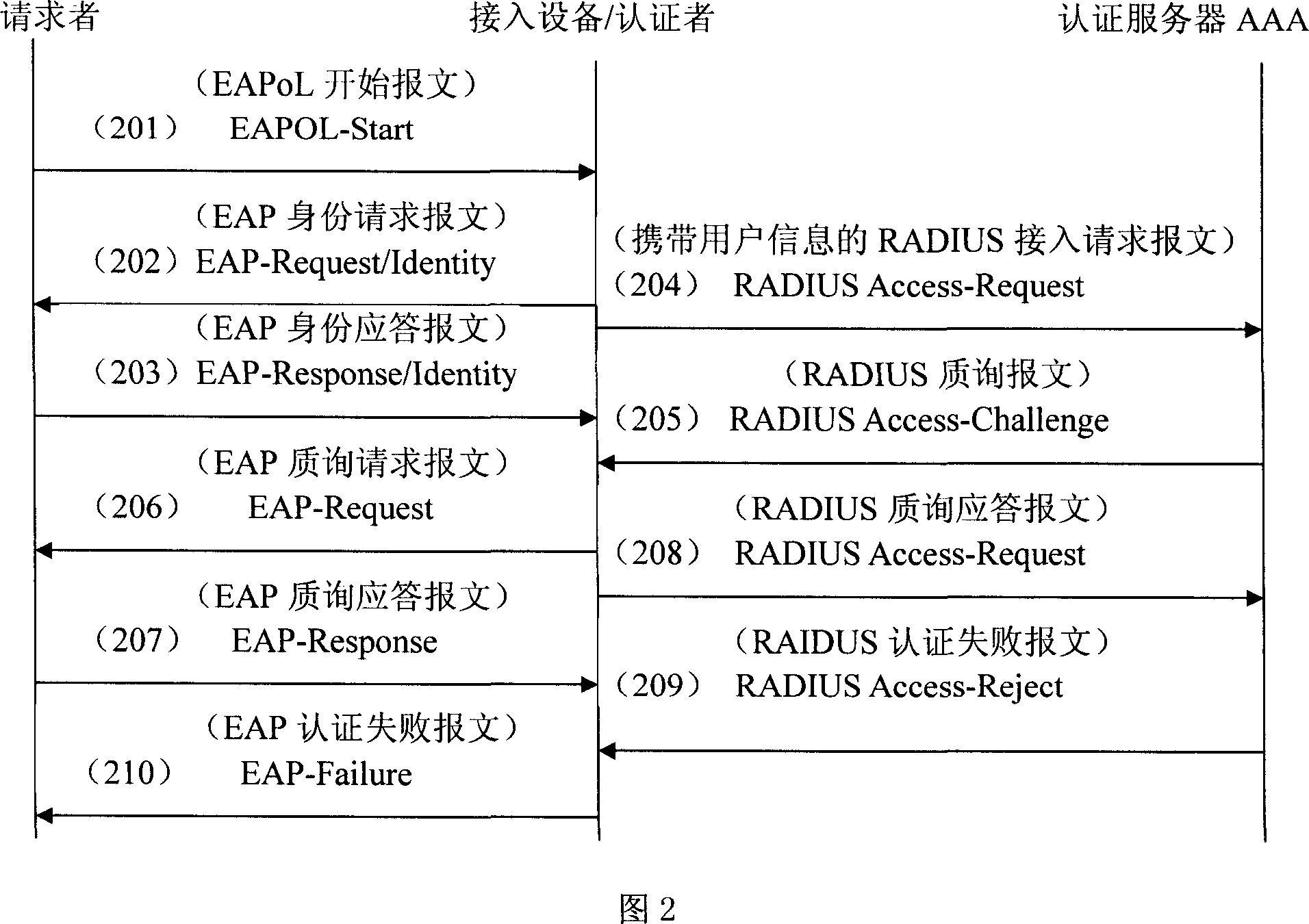
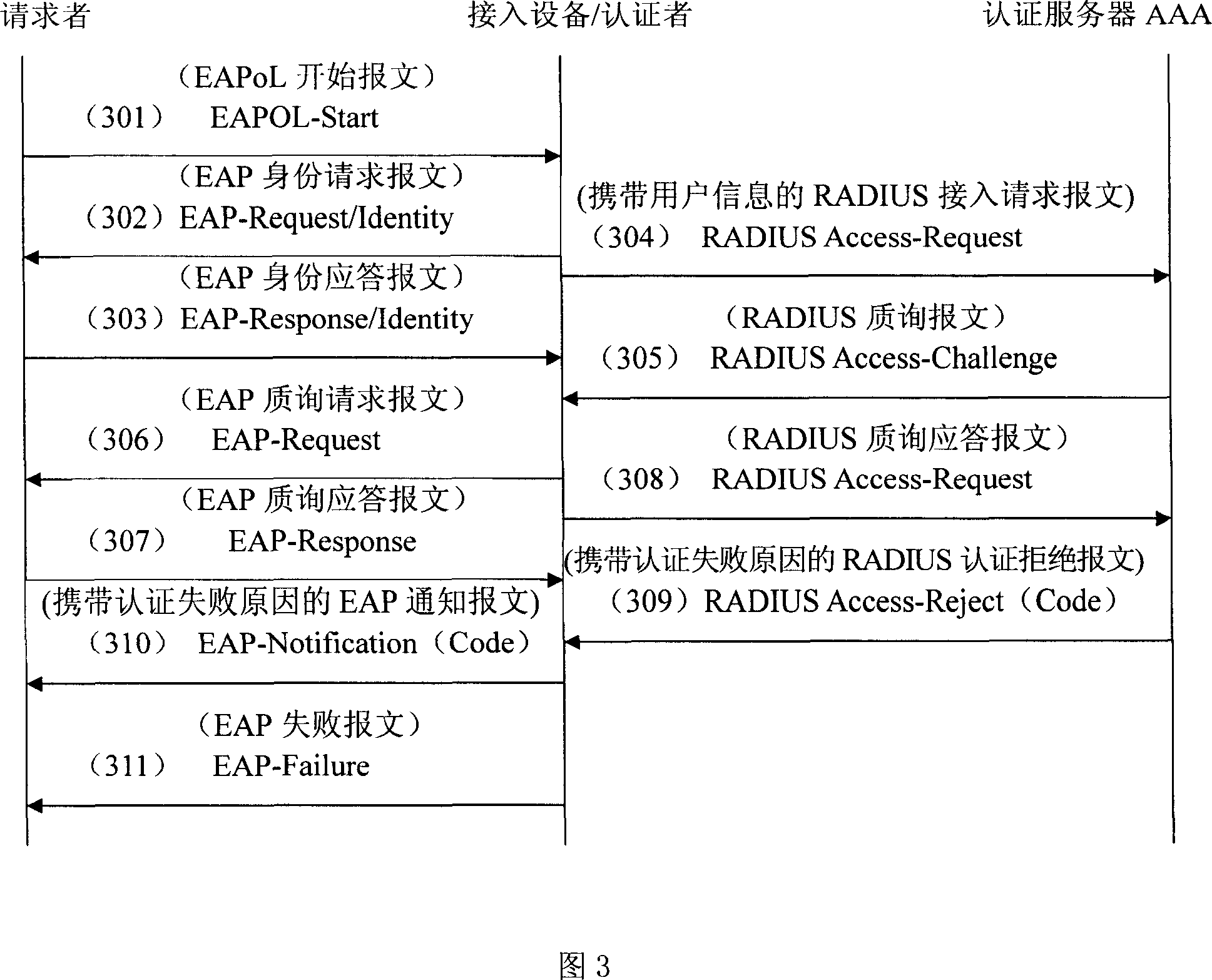
Method for realizing network certification
InactiveCN101075869AAddress usabilityResolve misunderstandingsUser identity/authority verificationWeb authenticationUsability
The invention is used for providing a reason of authentication failure for user when user fails to pass through the authentication and is off-lined. It comprises: before user fails to pass through the authentication and is off-lined, the server sends its reason to the 802.1x apparatus; 802.1x apparatus places the reason code in the expanded identification protocol notice message, and sends the message to the 802.1x client side.
Owner:ZTE CORP
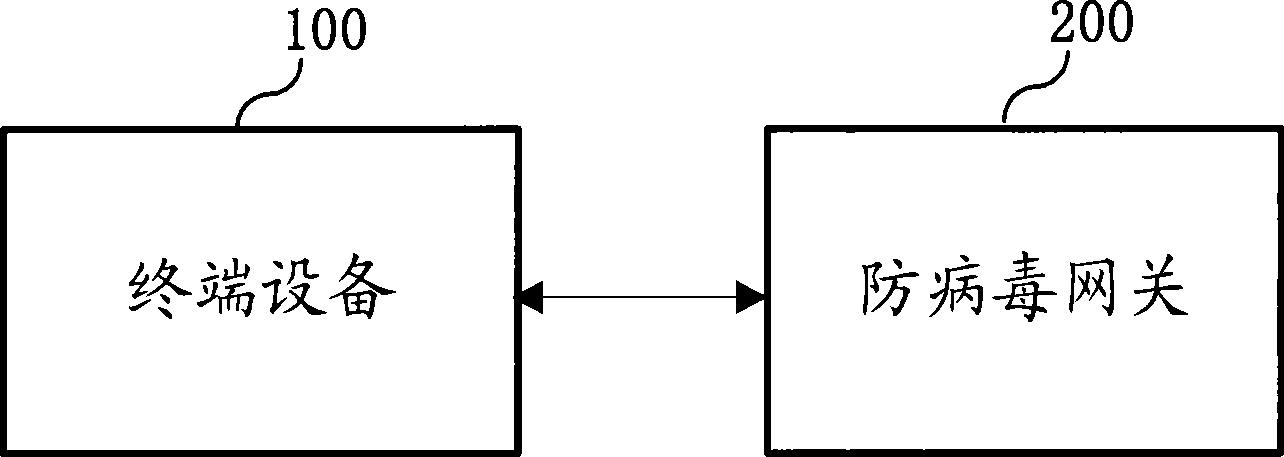
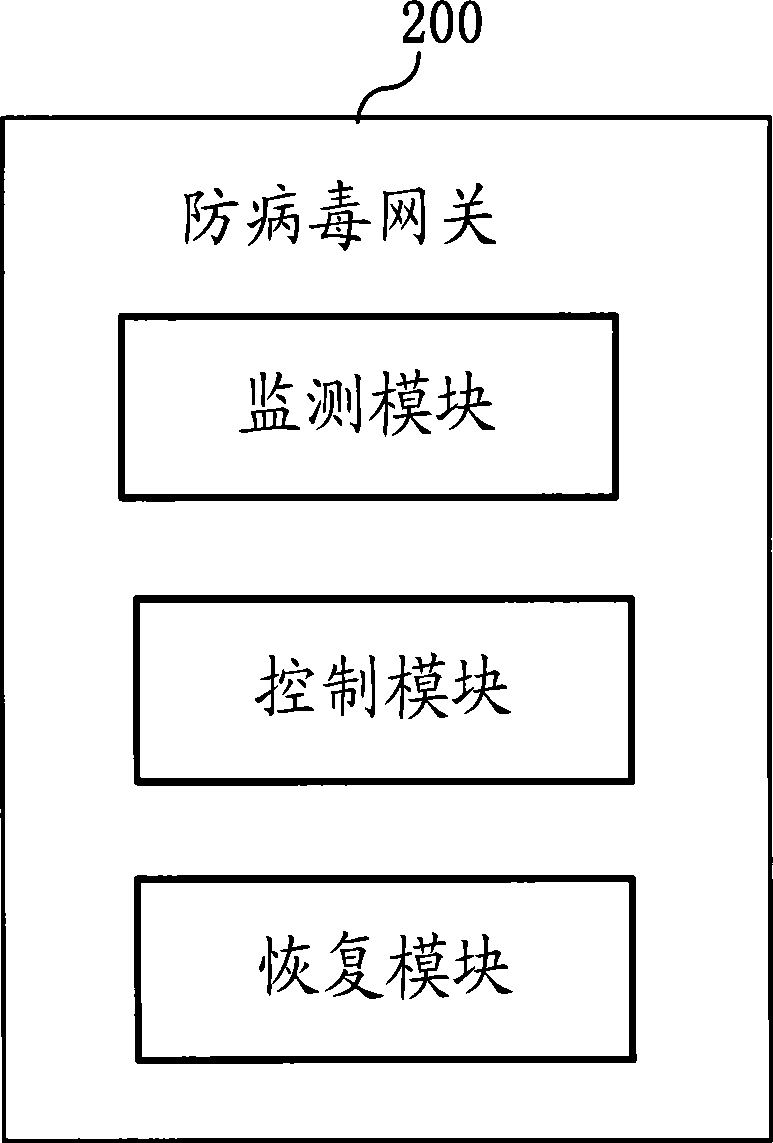
Method, apparatus and system for network safe transmission
InactiveCN101399786ADoes not take up resourcesSolve the problem of intruding into the network and blocking the networkNetwork connectionsAnti virusSecure transmission
The invention provides a network security transmission method, a device and a system thereof. The method of the invention comprises that: an anti-virus gateway is used for monitoring the security state of terminal equipment, so as to judge whether security hidden troubles exit in the terminal equipment; when the security hidden trouble exits in the terminal equipment, the network transmission of the terminal equipment is controlled according to the security control policy and a control command is transmitted to the terminal equipment to cause the terminal equipment to search and kill virus and remove the hidden trouble. The anti-virus gateway equipment comprises a monitoring module, a transmission module and a control module. By adopting the invention, the problem that the network virus utilizes the security hidden trouble of the terminal equipment to invade the network and block the network is solved, and meanwhile, the mutual transmission between terminal equipment can be avoided; therefore, the network security transmission can be realized.
Owner:HUAWEI TECH CO LTD
Intrusion detection system of wireless sensor network based on sniffer
ActiveCN101902744AHigh precisionDoes not take up resourcesNetwork topologiesSecurity arrangementIntrusion detection systemIntelligent algorithms
The present invention discloses an intrusion detection system of a wireless sensor network based on sniffer, comprising the following steps: sample training: 1), training the sample data of each node by using a Co-training algorithm in semi-supervised study and obtaining predictive model of each node; 2), training the sample data covered by each sniffer by using a minimax probability method (MPM)having a confidence value and obtaining the predictive model of each sniffer; 3), training the data monitored by all the sniffer by using a kernel vector machine algorithm in a support vector machinefor solving the big sample training problem, obtaining the predictive model of the entire network; monitoring in real time: 4), adding a plurality of sniffer detecting nodes in the wireless sensor network, detecting all the frame signals in the wireless sensor network by the sniffer detecting node; 5) sending the frame signal to a host by the sniffer detecting node, performing the intrusion detection judgment and alarming to the different grades (node, sniffer covering domain, entire network) via a predictive model obtained by a traditional feature detection and an intelligent algorithm training by the host.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Six-degree-of-freedom equipment for installation and connection of bullet train coupler
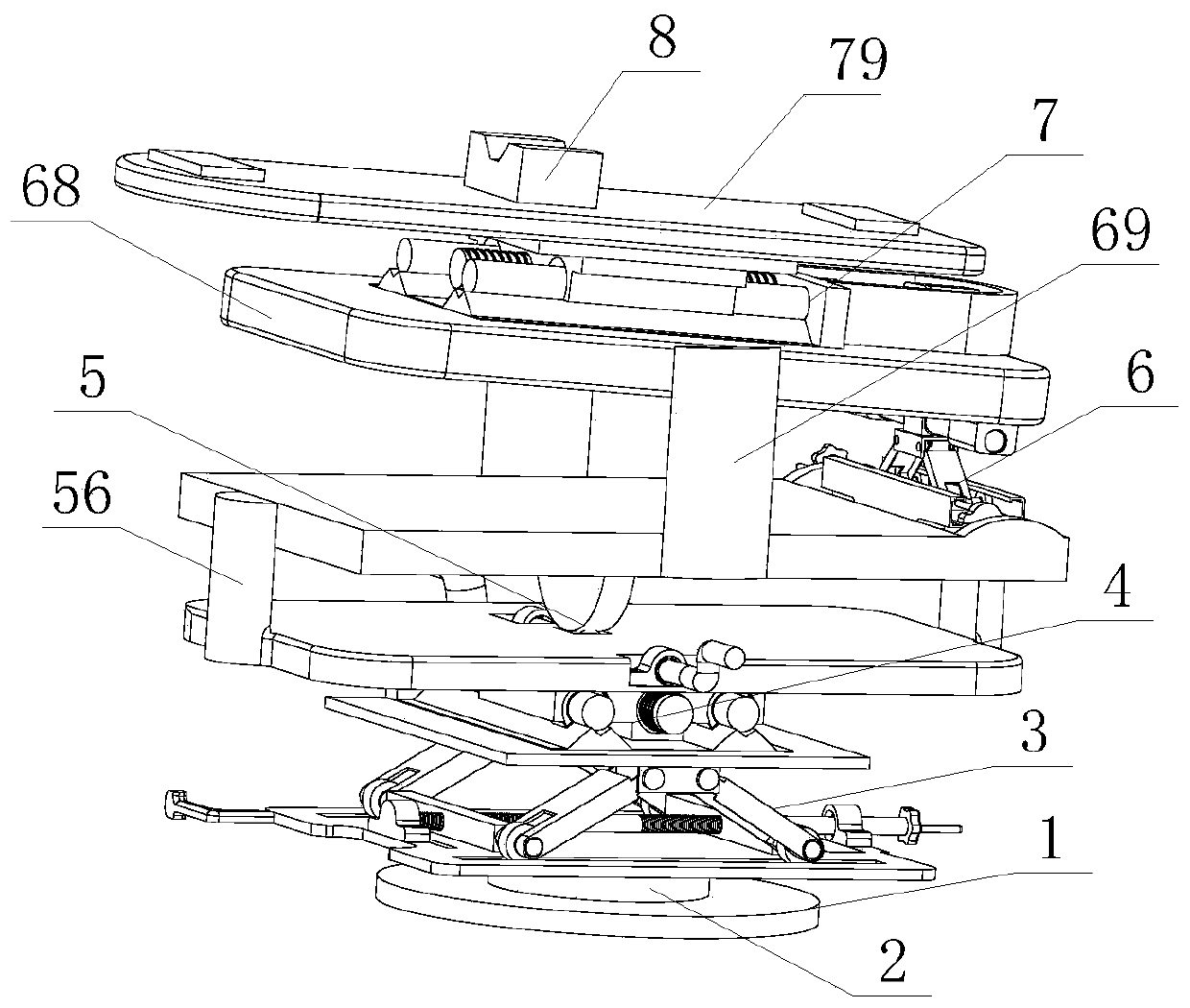
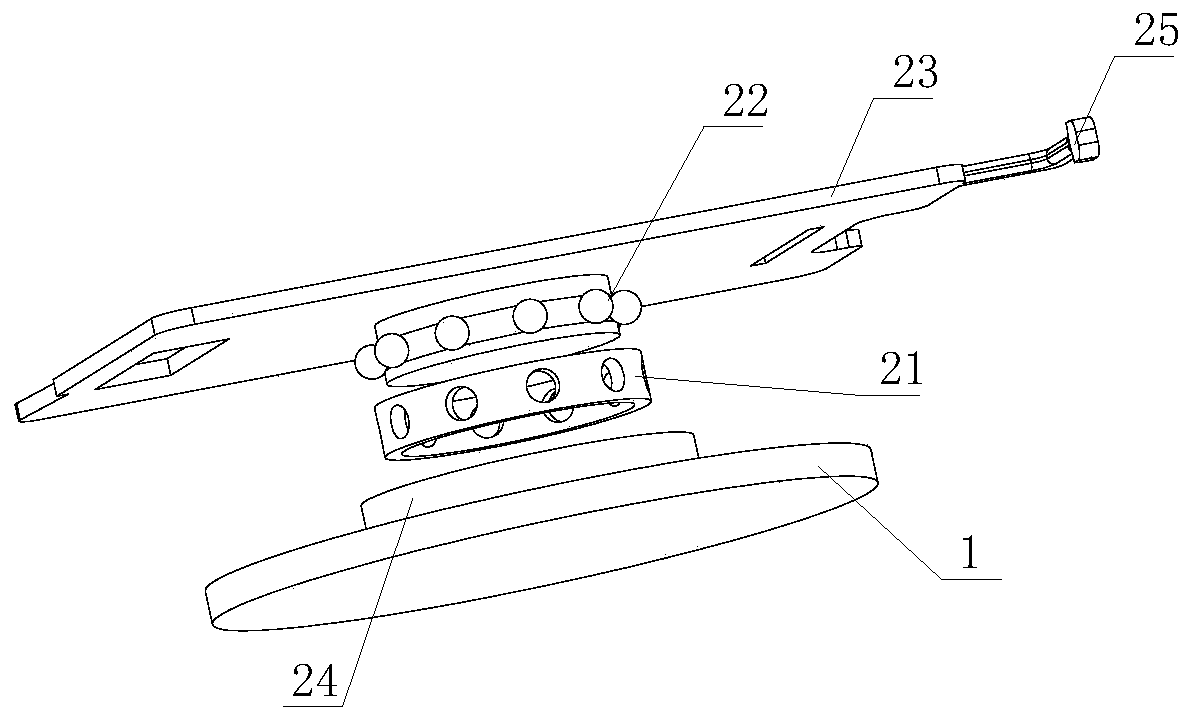
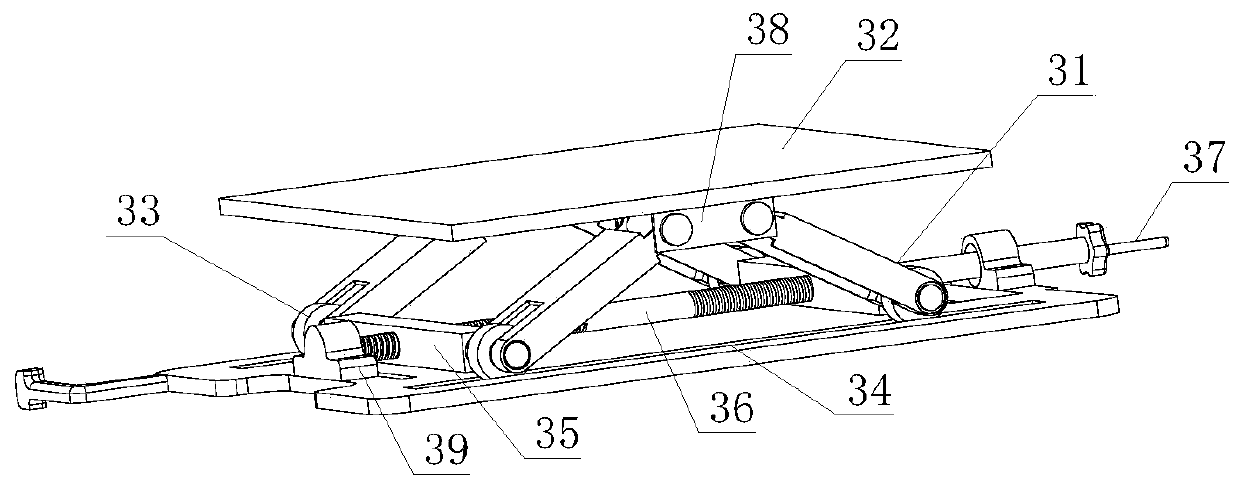
InactiveCN111039222AEasy to shipReduce consumptionLifting framesControl engineeringStructural engineering
The invention discloses six-degree-of-freedom equipment for installation and connection of a bullet train coupler. The six-degree-of-freedom equipment comprises a base, a machine body rotating mechanism, a lifting mechanism, a left-right moving mechanism, a turnover mechanism, a jacking mechanism, a front-back moving mechanism, an objective table and an installation clamp which are sequentially arranged from bottom to top. The machine body rotating mechanism, the lifting mechanism, the left-right moving mechanism, the overturning mechanism, the jacking mechanism and the front-back moving mechanism can complete six-degree-of-freedom movement. All the mechanisms are arranged in a layered mode, rotating, lifting, left-right moving, left-right overturning, front-back overturning and front-backmoving are successively achieved from bottom to top, each action is independently completed, and the bullet train coupler conveying and installing device is convenient to apply widely. The six-degree-of-freedom equipment for installation and connection of the bullet train coupler is low in energy consumption and cost, convenient to move and small in occupied area during usage, and can be idle when actions do not need to be adjusted so that resource waste is reduced.
Owner:YANSHAN UNIV
Industrial personal computer safety protection system and industrial personal computer safety protection method based on security baseline
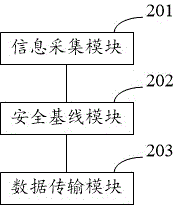
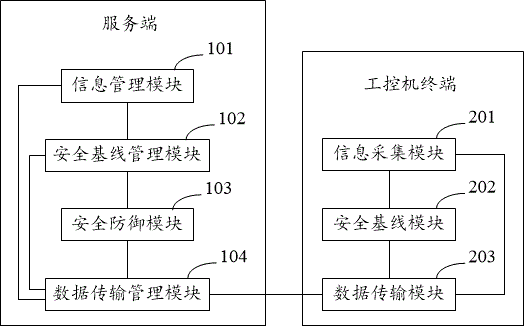
InactiveCN106603551AMaintain securityDoes not take up resourcesTransmissionTerminal equipmentPersonal computer
The invention provides an industrial personal computer safety protection system and an industrial personal computer safety protection method based on a security baseline. The method comprises the steps of establishing the security baseline for an industrial personal computer terminal according to information of each industrial personal computer terminal in an industrial control network; when unknown data enter the industrial control network, detecting security of the unknown data; updating the security baseline according to a security detecting result of the known data; allowing entering of the safe unknown data in the industrial control network, and preventing operation of unsafe unknown data in the industrial control network. According to the industrial personal computer safety protection system and the industrial personal computer safety protection method, security of equipment in the industrial control network is ensured through the closed security baseline; furthermore the security baseline of the equipment can be dynamically updated; and detection of the unknown data and establishment of the security baseline are performed in a service end, thereby preventing resource occupation of the industrial personal computer terminal and realizing no influence on service operation of the industrial personal computer terminal.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
Data transmission encryption and decryption method
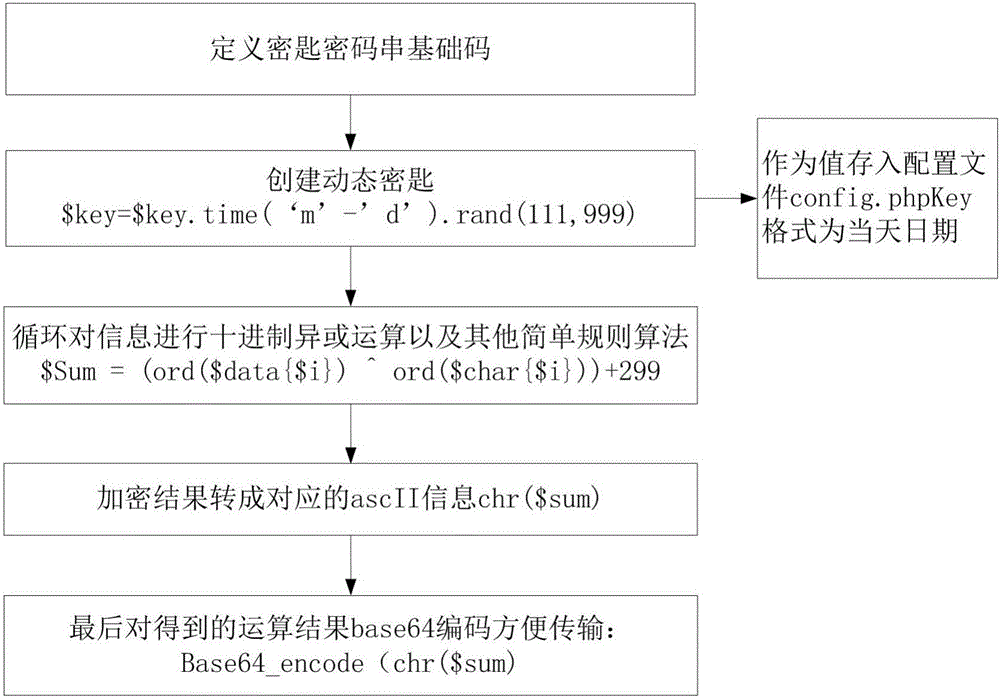
InactiveCN106131049APrevent theftDoes not take up resourcesTransmissionComputer hardwareData transmission
The invention provides a data transmission encryption and decryption method. The method comprises the steps of defining a key string in code; carrying out encryption and decryption operations on data by taking the key string as a center, wherein the encryption operation comprises the steps of carrying out carry number coding on a character string needing to be encrypted, carrying out logic operation, and carrying out base 64 coding to obtain encrypted character string, and the decryption operation comprises the steps of carrying out carry number coding on the key string and the character string needing to be decrypted, carrying out the logic operation, and carrying out base 64 coding to obtain decrypted character string. According to the method, encryption operation logic and decryption operation logic are in mutual symmetry, so that a logic rule can be modified conveniently; and through adoption of a mode of modifying an encryption logic rule and a key, the data can be rapidly and effectively prevented from being stolen.
Owner:福建中金在线信息科技有限公司
Multi-bus communication system of cross modulation instrument
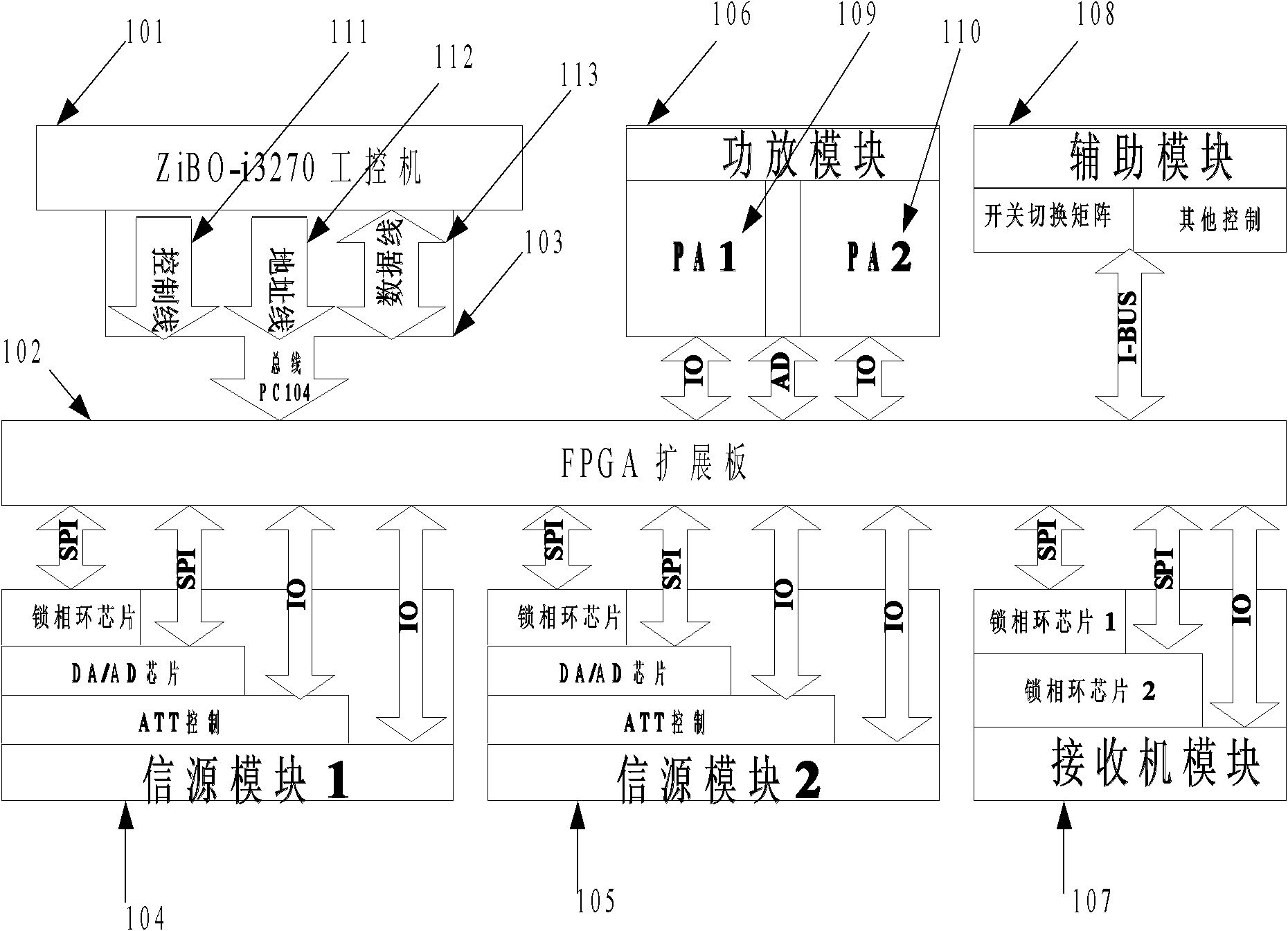
InactiveCN102123068AHigh communication frequencyIncrease speedTotal factory controlProgramme total factory controlCommunications systemComputer module
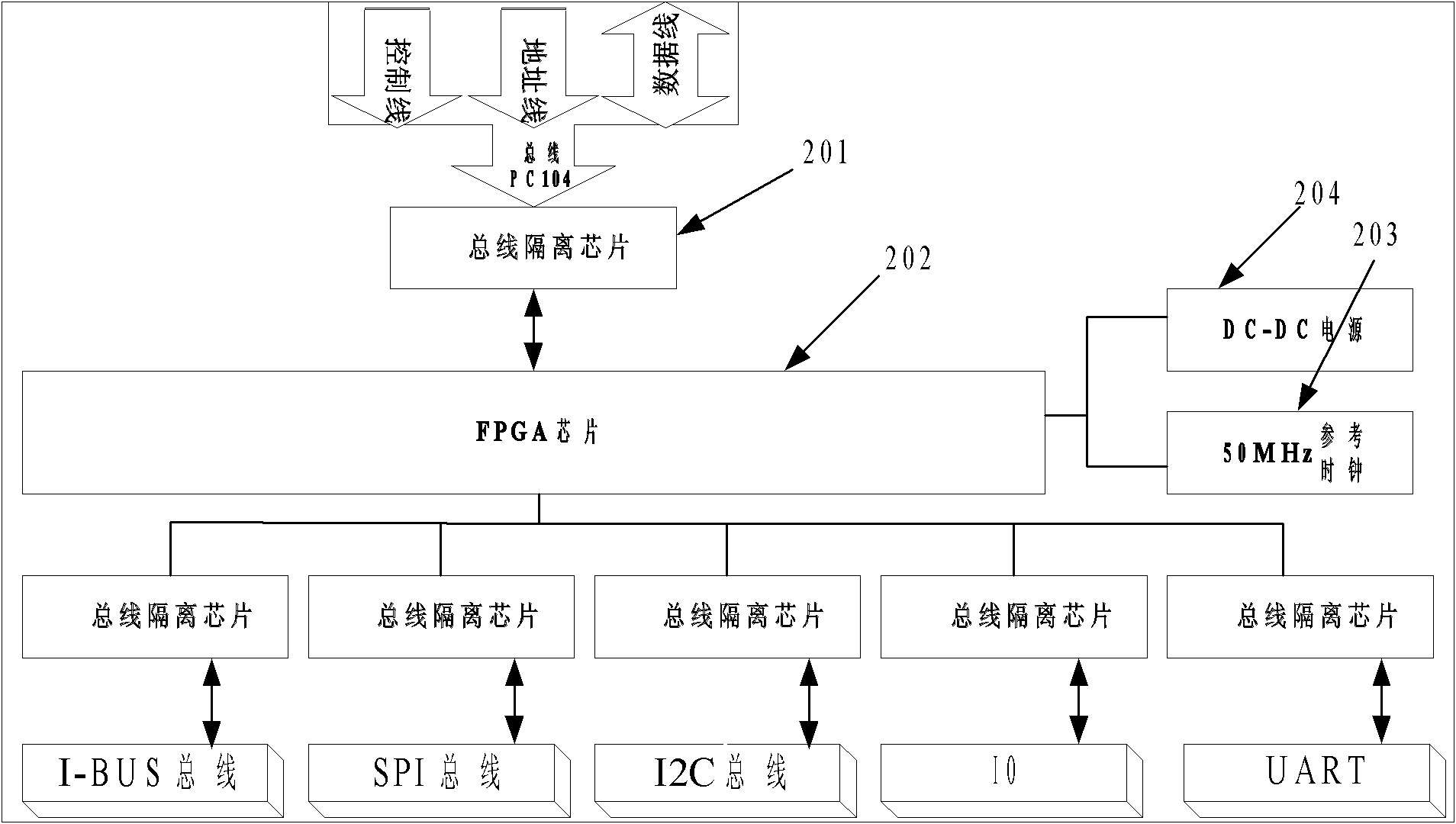
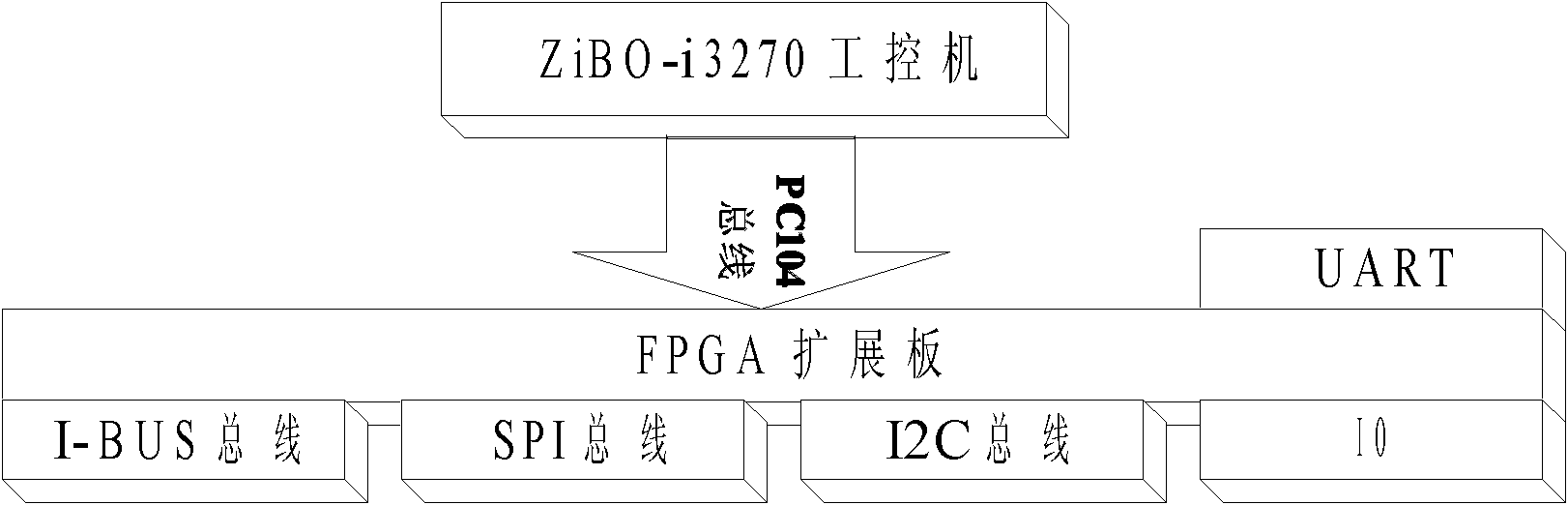
The invention discloses a multi-bus communication system of a cross modulation instrument, which comprises an industrial personal computer, a FPGA (Field Programmable Gate Array) expansion board, a first information source module, a second information source module, a power amplification module and a receiver module, wherein a PC104 bus is expanded by adopting the FPGA, and the conversion of the timing sequences of hardware buses is realized through programming so as to achieve the purposes of multi-bus communication and the communication between an industrial control board and all peripheral modules. In the communication system disclosed by the invention, the communication means of a bus of the industrial control board is expanded; the number of IO (Input / Output) ports of the control board is increased; the speed and the throughput of the bus are improved; and the peripheral equipment of equipment is independently controlled, so that the CPU (Central Processing Unit) resource is not occupied; and moreover, the parallel control of the equipment can be realized.
Owner:ROSENBERGER (SHANGHAI) TECH CO LTD
Peripheral device, conference tool and conference tool system
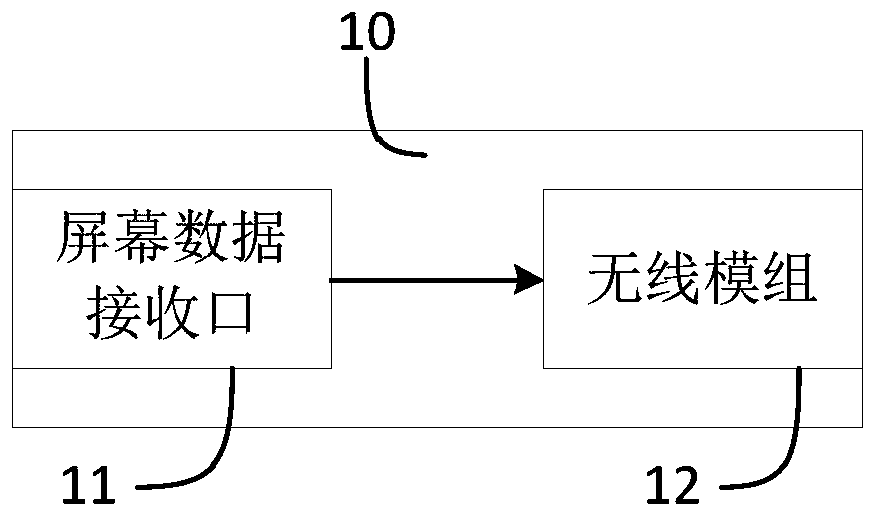
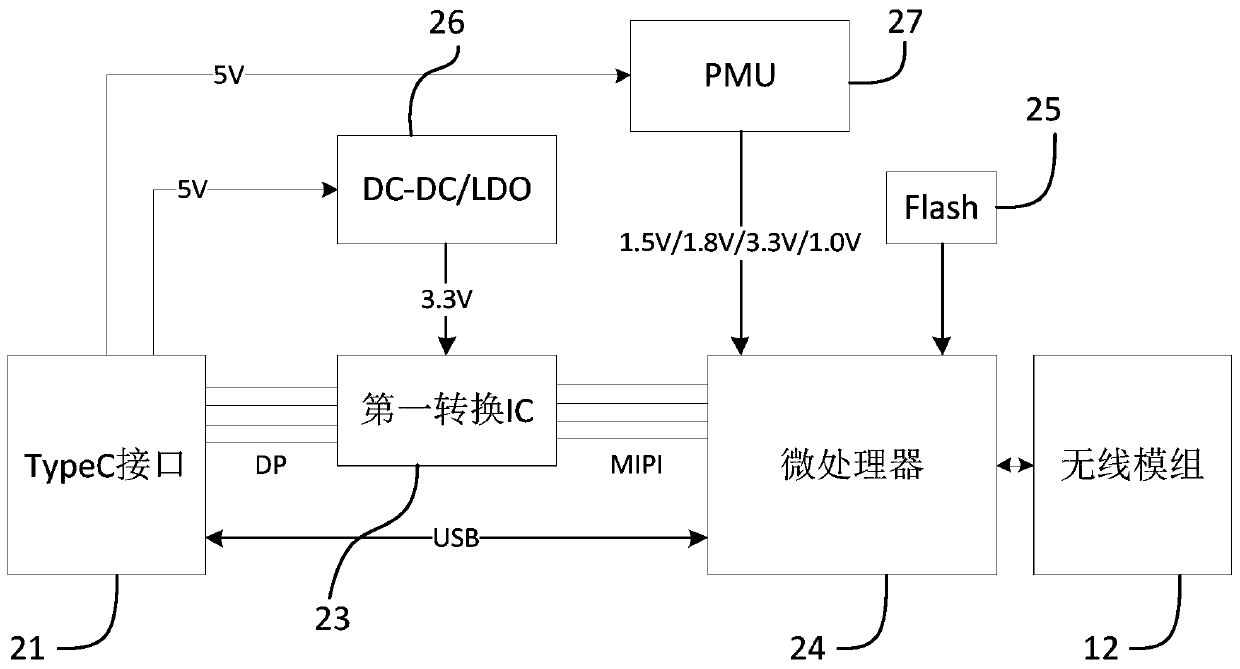
ActiveCN110007883AReduce preparation timeDoes not take up resourcesStatic indicating devicesTelevision conference systemsDisplay deviceData transmission
The invention discloses a peripheral device, a conference tool and a conference tool system. The peripheral device comprises a screen data receiving port, a wireless module and a microprocessor. The screen data receiving port is used for being connected with a video signal interface of a processing device and obtaining uncompressed first audio and video data output by the video signal interface. The media content corresponding to the first audio and video data is the same as the media content displayed on the first display. The microprocessor is connected with the screen data interface and isused for compressing and encoding the first audio and video data. The wireless module is connected with the microprocessor, and the wireless module is used for communicating with a wireless communication network and transmitting the received first audio and video data to a network node matched with the wireless communication network. By implementing the embodiment of the invention, drive-free screen transmission can be realized, the preparation time before screen transmission is shortened, and resources of the processing device are not occupied.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com