Data transmission encryption and decryption method
A data transmission, encryption and decryption technology, applied in the transmission system, electrical components, etc., can solve problems affecting the company's profitability, achieve the effect of not occupying resources, convenient modification, and preventing data from being stolen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
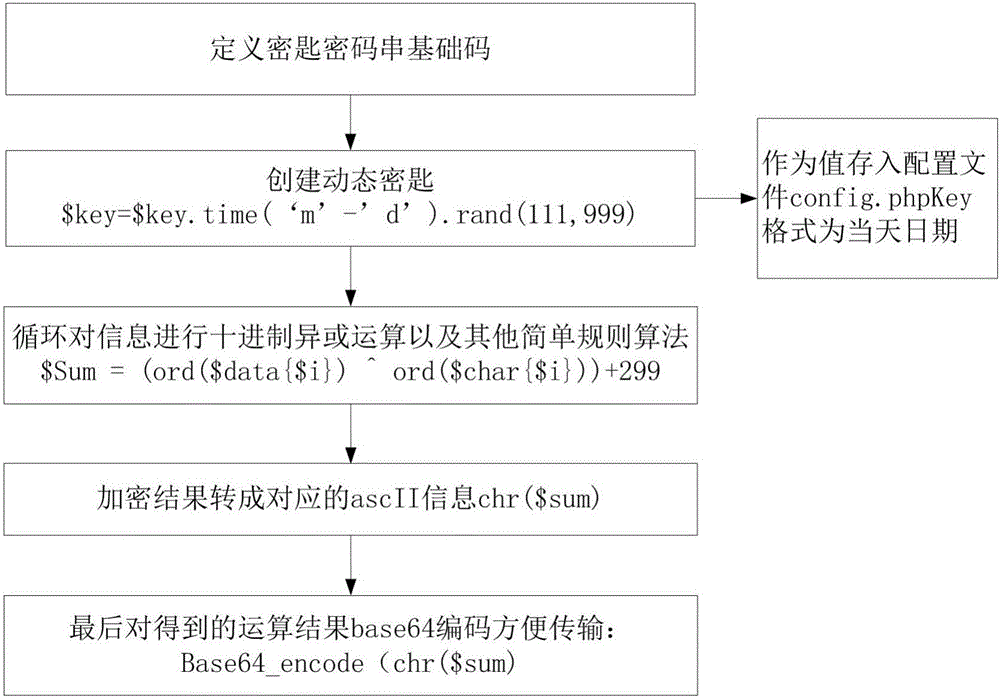
[0017] see figure 1 and figure 2 As shown, a method for data transmission encryption and decryption of the present invention, the method defines a key chain in the code, and the key chain is used as the center to encrypt and decrypt data;
[0018] The encryption operation: carry out the carry number encoding of the key string and the character string to be encrypted, then perform logical operations, and finally perform base64 encoding to obtain the encrypted character string;
[0019] The decryption operation: carry out carry encoding on the key chain and the character string to be decrypted, then perform logical operations, and finally perform base64 decoding to obtain the decrypted data.
[0020] Wherein, the encryption operation is specifically:
[0021] First define the key chain, splicing the date format of the timestamp and the random number to get the dynamic key, so that the results of the data encryption are different every day, which increases the difficulty of de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com