Network safe content processing card based on FPGA
A network security and content technology, applied in electrical components, transmission systems, etc., can solve the contradiction between network security and network speed, network management and network cost contradiction, etc., to achieve high-performance results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The function implementation of the board card of the present invention will be described in detail below in conjunction with the accompanying drawings.
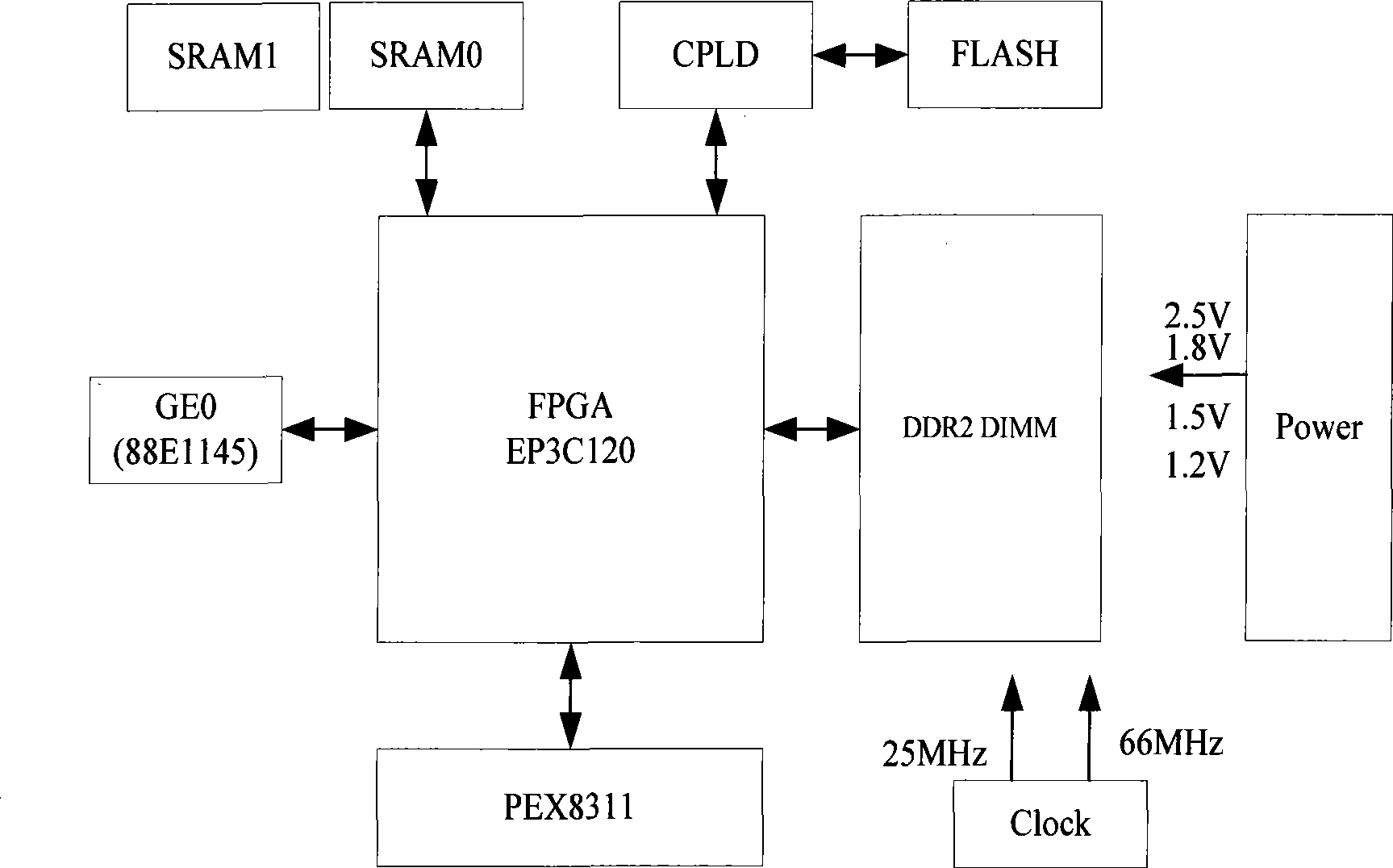
[0018] Such as figure 1 As shown, the present invention is composed of a dedicated FPGA security chip, a Gigabit Ethernet port module (88E1145), a PCI interface (PEX8311), a power supply module, and an SRAM. Main module function of the present invention is as follows:
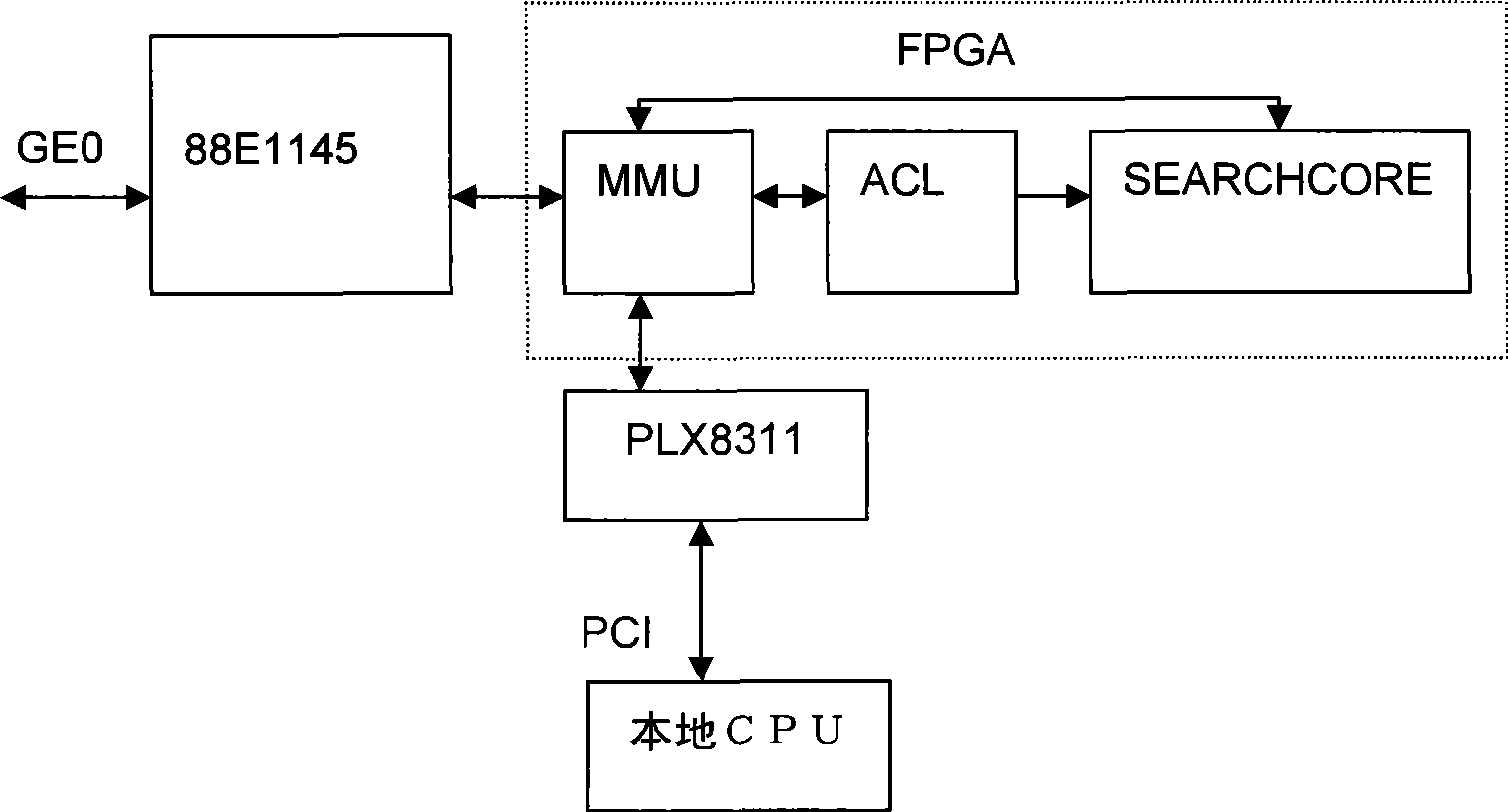
[0019] FPGA chip: It mainly implements logical functions such as intrusion prevention, content filtering, traffic monitoring, security audit, and security policy scheduling.
[0020] Gigabit Ethernet port module (88E1145): Complete the receiving and sending of Ethernet data packets by means of 1000baseT interface. At the same time, it can communicate with a remote computer through an Ethernet network connection, receive security policy management commands, and complete remote management.
[0021] PCI interface (PEX8311): Complete the data communicati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com