Method for realizing network certification
An implementation method, a technology of network authentication, applied in the field of network authentication, can solve the reasons of not providing users with authentication failure or offline, unfavorable 802.1x client usability, operation service provider and user authentication failure or offline Misunderstanding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
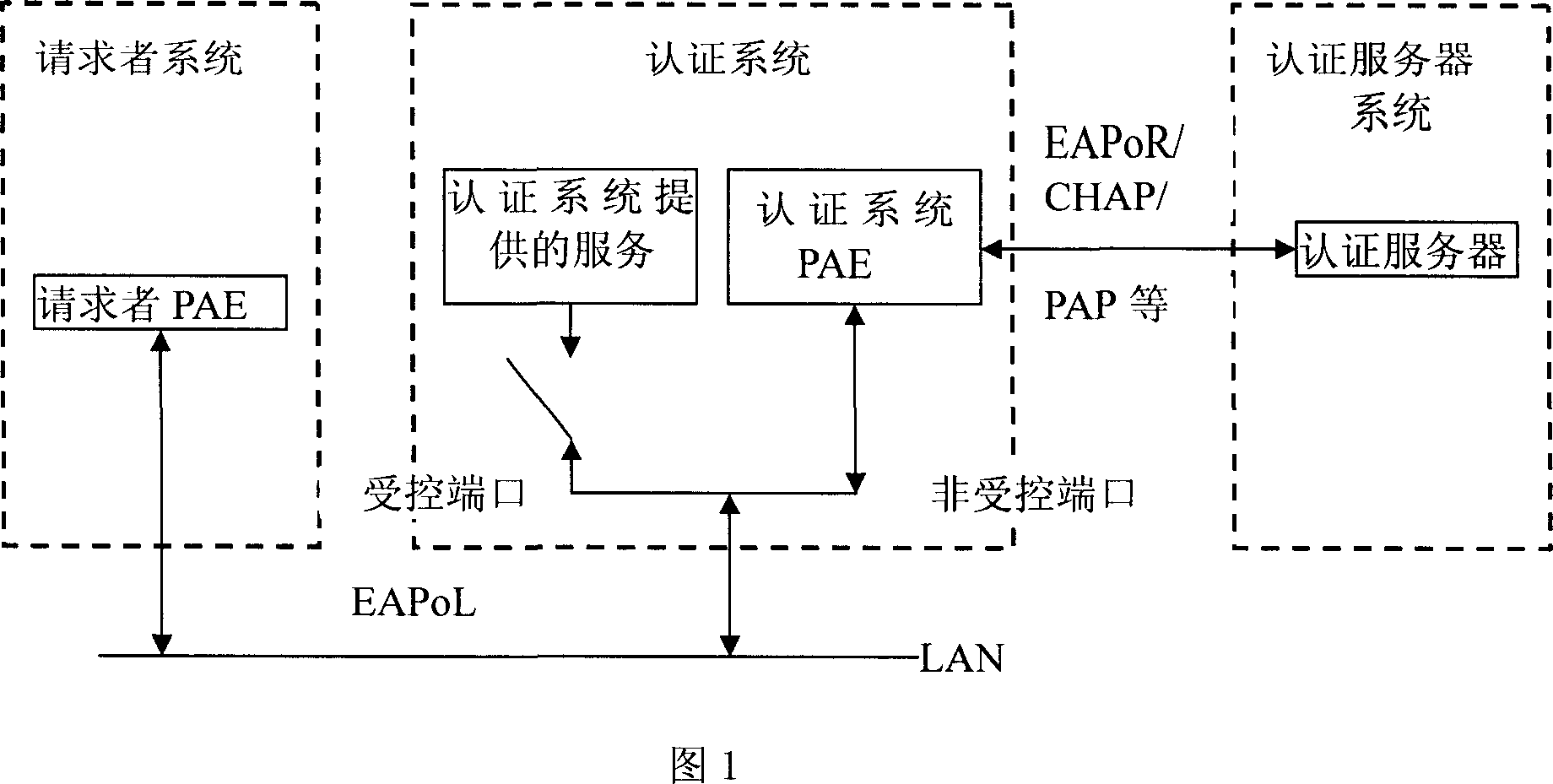
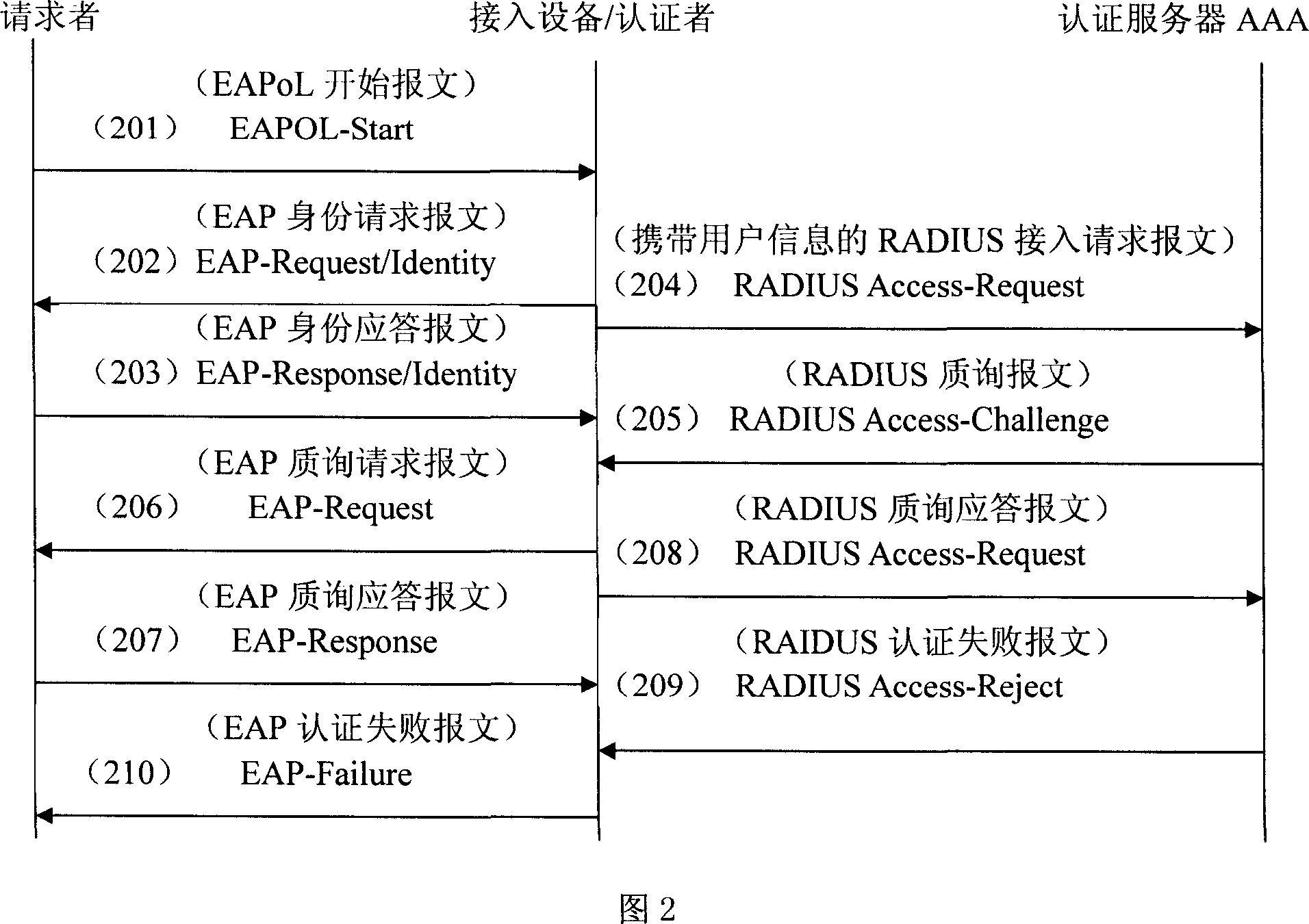
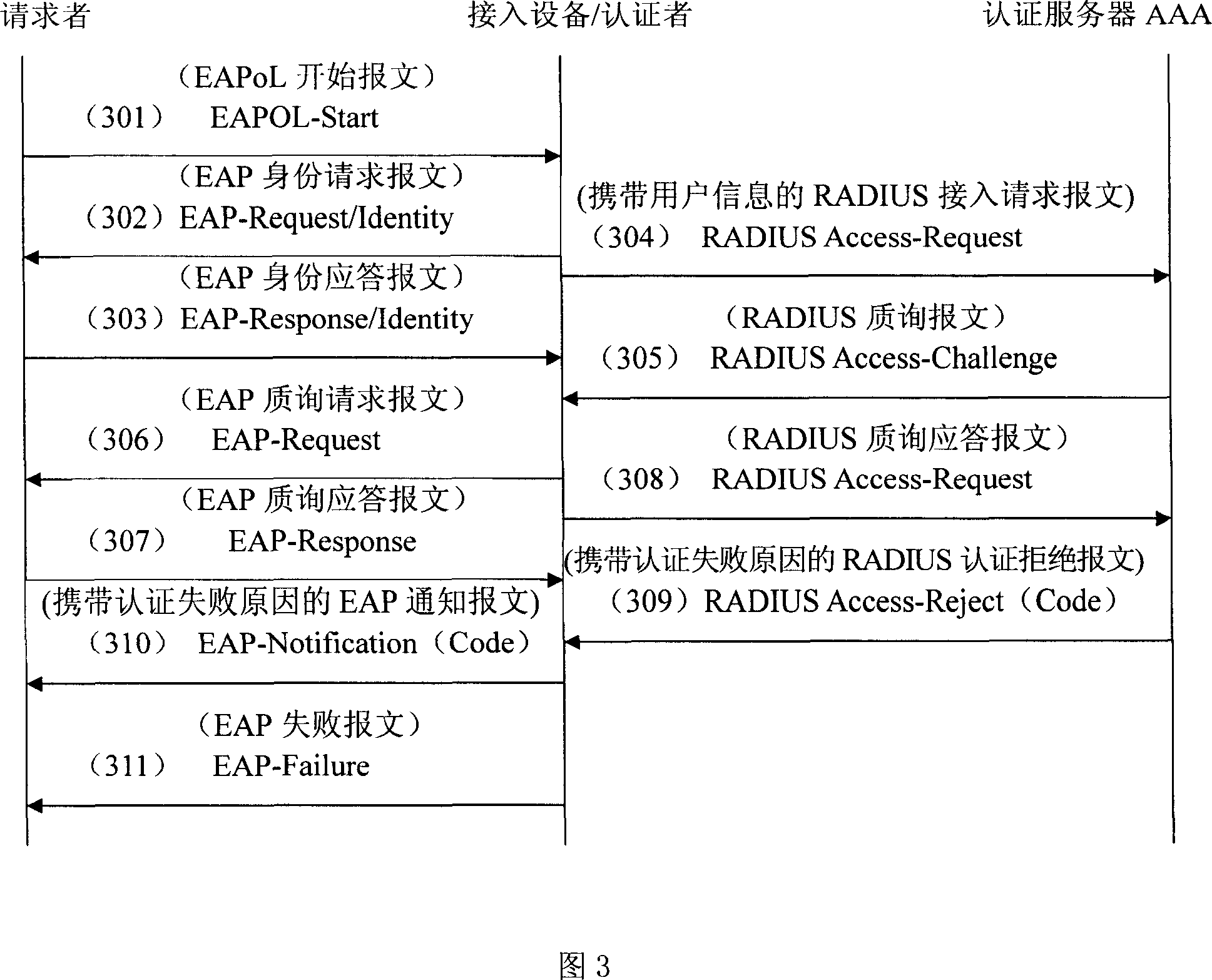
[0039] The present invention will be described in detail below in conjunction with the accompanying drawings.
[0040] The present invention expands the existing EAP Notification message, and transmits the reason of authentication failure or offline to the 802.1x client through the data field in the message. In order to distinguish various authentication failure reasons, set an error code Code value, and define seven types of values for the failure reasons. For example, the Code value is 1, indicating that the user name is incorrect; the Code value is 2, indicating that the user password is incorrect; Code A value of 3 means that the user has violated the security policy of the server and there is an agent on the client side; a value of Code of 4 means that the user has violated the security policy of the server and performed some illegal operations; a value of Code of 5 means that the user has been offline within a time limit; A value of 6 indicates that the traffic limit i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com