Calibration method and device
A verification method and message technology, applied in the field of communication, can solve problems such as ease of use and business security, failure, undiscovered solutions, etc., to improve practicability and user experience, reduce difficulty, and reduce engineering failures The effect of the probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
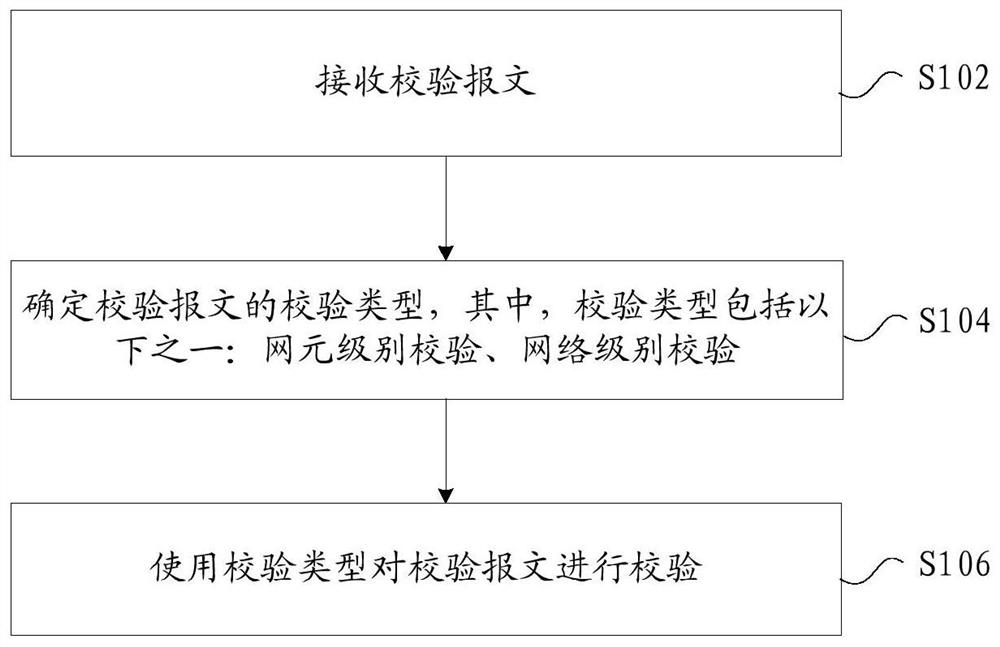
[0028] In this embodiment, a verification method is provided, figure 1 is a flow chart of a verification method according to an embodiment of the present invention, such as figure 1 As shown, the process includes the following steps:
[0029] Step S102, receiving a verification message;
[0030] Step S104, determine the verification type of the verification message, wherein the verification type includes one of the following: network element level verification, network level verification;
[0031] Step S106, verifying the verification message by using the verification type.
[0032] Through the above steps, by selecting two levels of service security verification at the network element level and the network level, the technical problem of low usability and service security in related technologies that can only be verified by the client is solved, and the improvement is improved. It not only improves the practicability and user experience, but also greatly reduces the probab...
Embodiment 2
[0050] In this embodiment, a verification device is also provided, which is used to implement the above embodiments and preferred implementation modes, and those that have been explained will not be repeated here. As used below, the term "module" may be a combination of software and / or hardware that realizes a predetermined function. Although the devices described in the following embodiments are preferably implemented in software, implementations in hardware, or a combination of software and hardware are also possible and contemplated.
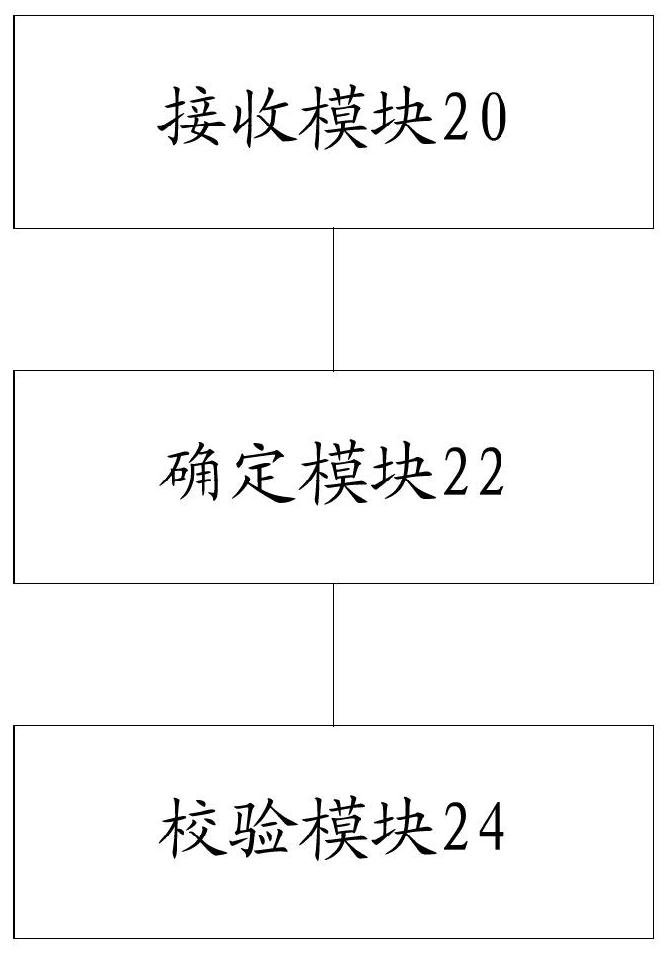
[0051] figure 2 is a structural block diagram of a verification device according to an embodiment of the present invention, such as figure 2 As shown, the device includes:
[0052] The receiving module 20 is used to receive the verification message;
[0053] The determination module 22 is used to determine the verification type of the verification message, wherein the verification type includes one of the following: network element level v...
Embodiment 3
[0058] This embodiment is an optional embodiment according to the present invention, and is used to describe the application in detail and supplementary in conjunction with specific examples:
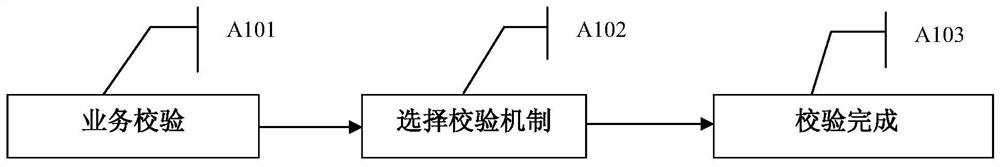
[0059] This embodiment provides a service security verification mechanism and method. It is divided into single network element setting command verification and network level function verification. The client check sink adapter is only applicable to single-point setting commands. For client verification of network-level functions, it will sink to the server for verification.
[0060] The method of this embodiment includes:
[0061] Method 1: NE-level function verification (NE-level verification)
[0062] Many single-point configuration checks in related technologies are deployed on network management clients. This mode is not a big problem in normal single-point configuration scenarios, but in northbound access or end-to-end management scenarios, these The verification rules will fa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com