Encryption system, encryption method and decryption method for local area network shared file
A technology for sharing files and encryption systems, which is applied to transmission systems, electrical components, and key distribution to achieve fast transmission, ensure authenticity, and improve efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
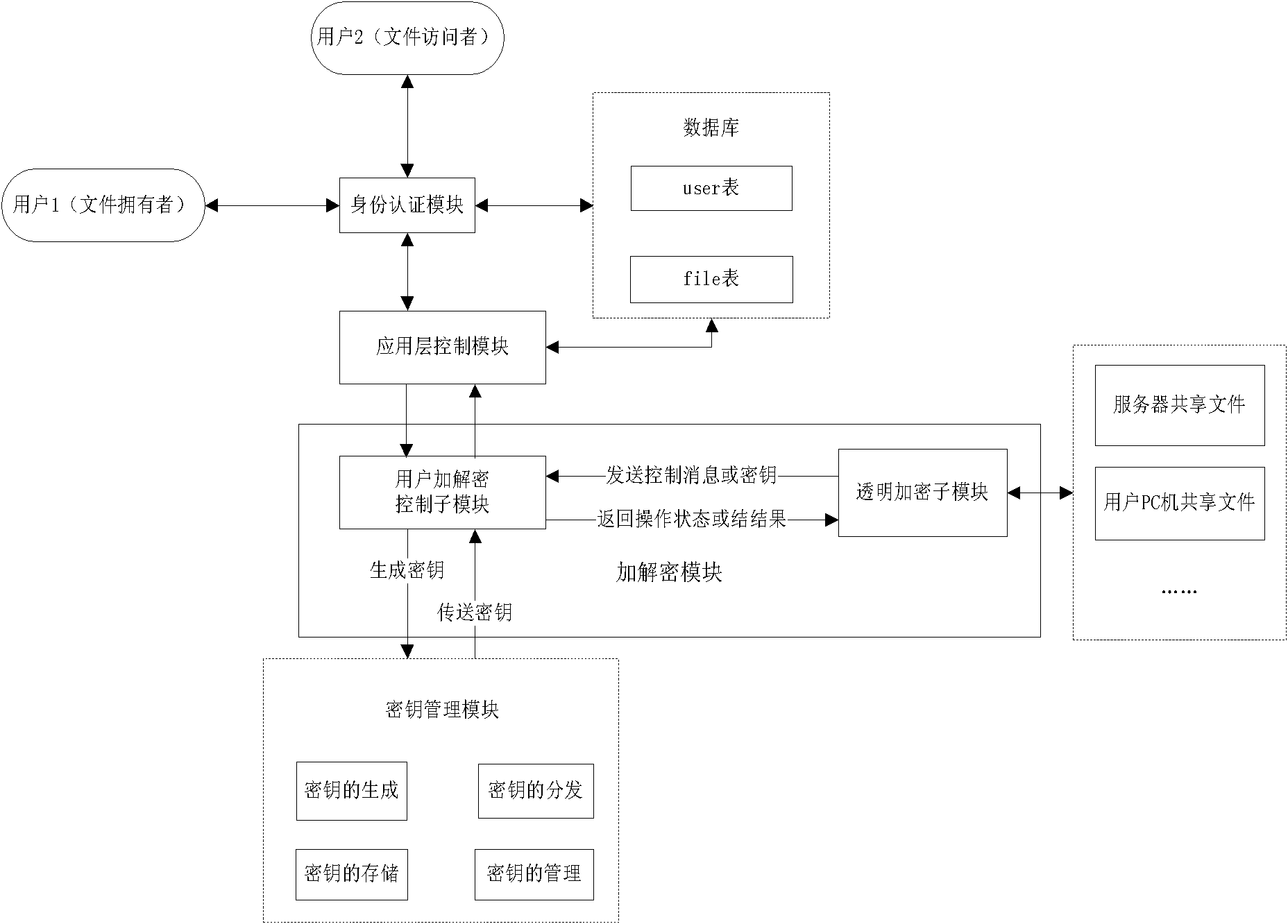
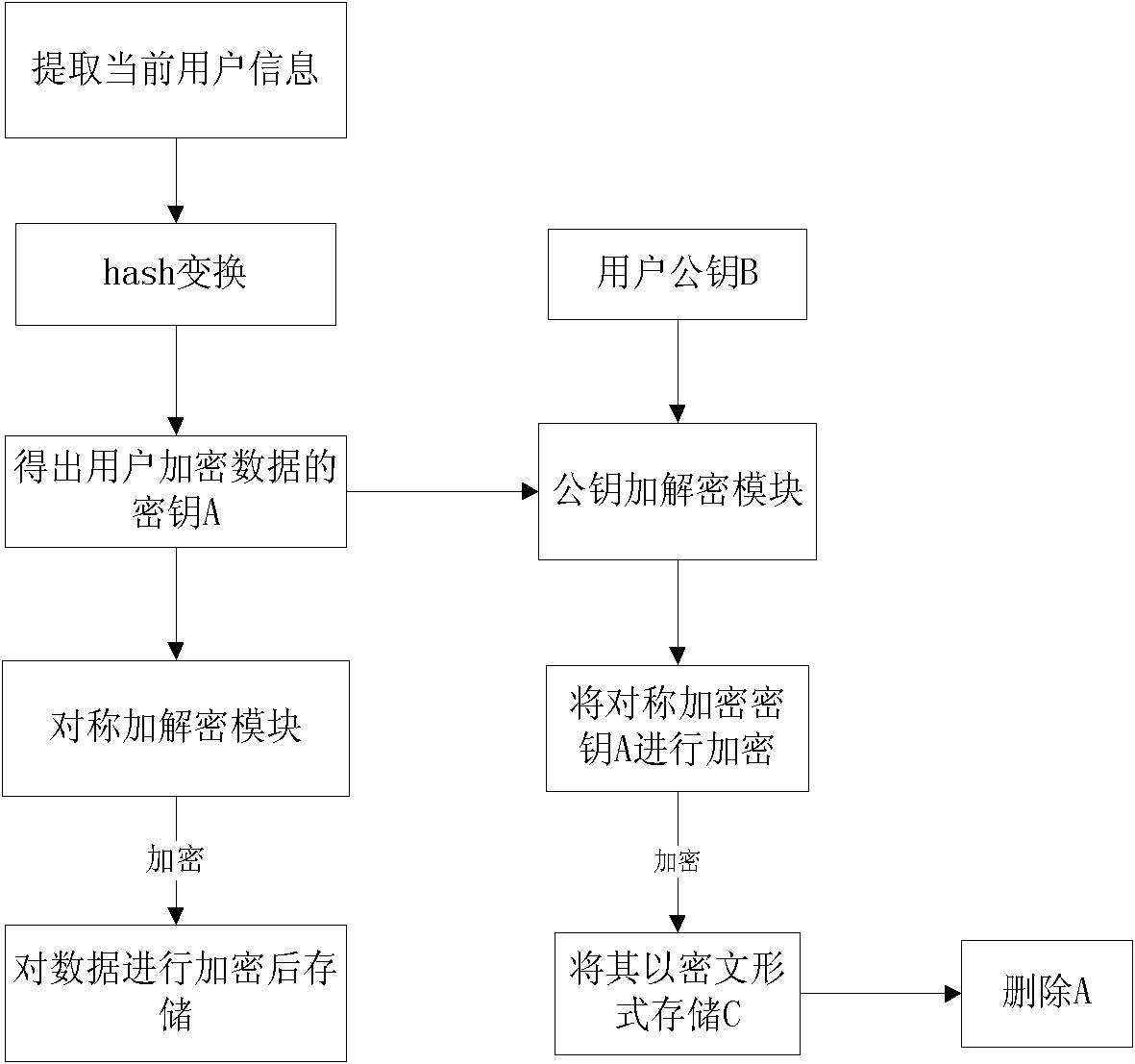
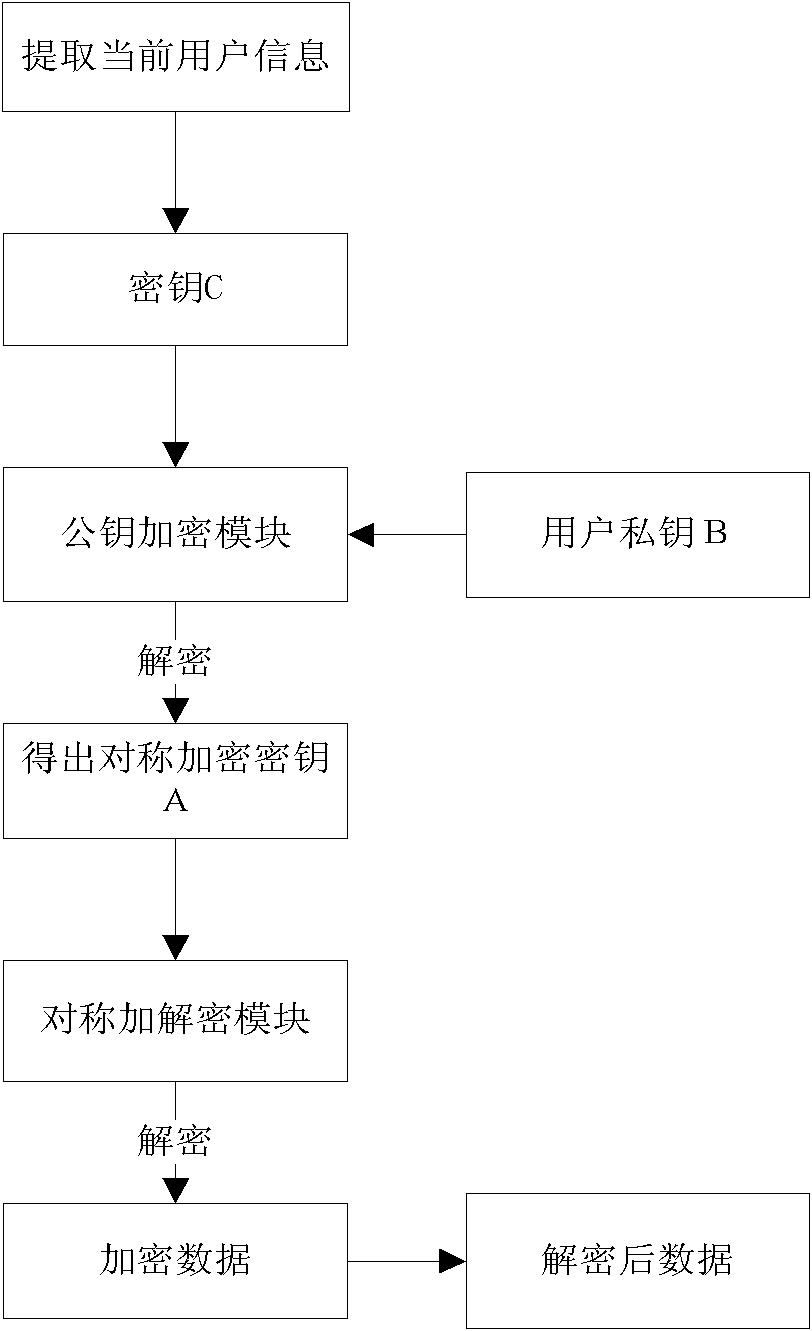
[0042] Such as figure 1 with figure 2 As shown, the local area network shared file encryption system includes a key management module that reads, generates, and manages keys used to encrypt and decrypt files, and an encryption and decryption module that performs encryption and decryption operations according to user instructions. The system also includes identity authentication Module, the identity authentication module verifies the user's identity and determines the user's authority; the user identity authentication module performs encryption and decryption operations through the encryption and decryption module after the identity authentication is legal, and then accesses the shared files in the LAN.
[0043] A database is set in the identity authentication module, including a user table (user table) and a file table (file table). The user table stores all user names and user unique identifiers using the file encryption system, and stores all user names in the file table. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com