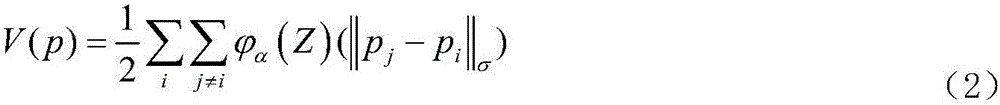Patents
Literature
562results about How to "Avoid insecurity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Dynamic password card and dynamic password generating method
InactiveCN103023643APrevent misuseAvoid insecurityUser identity/authority verificationPayment architectureComputer hardwareHealth information
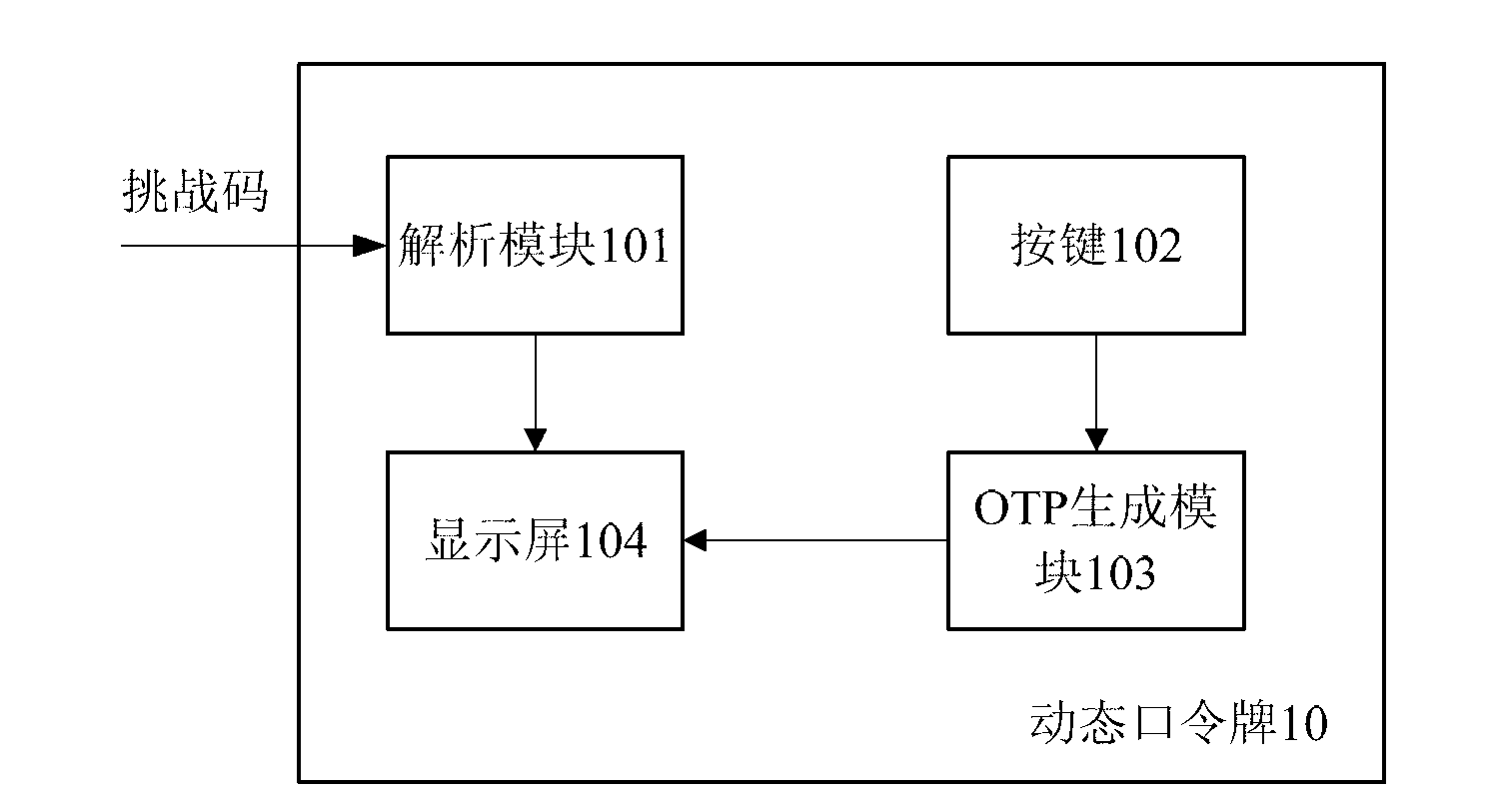
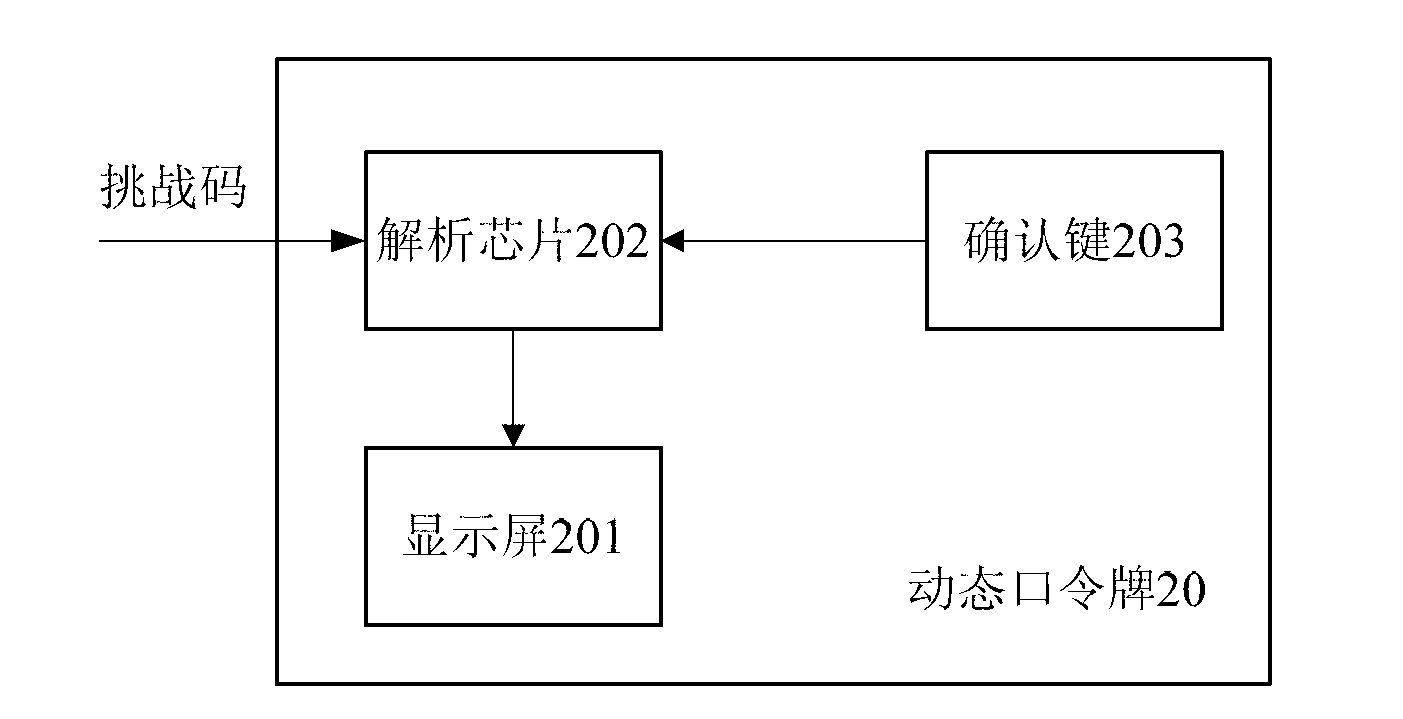
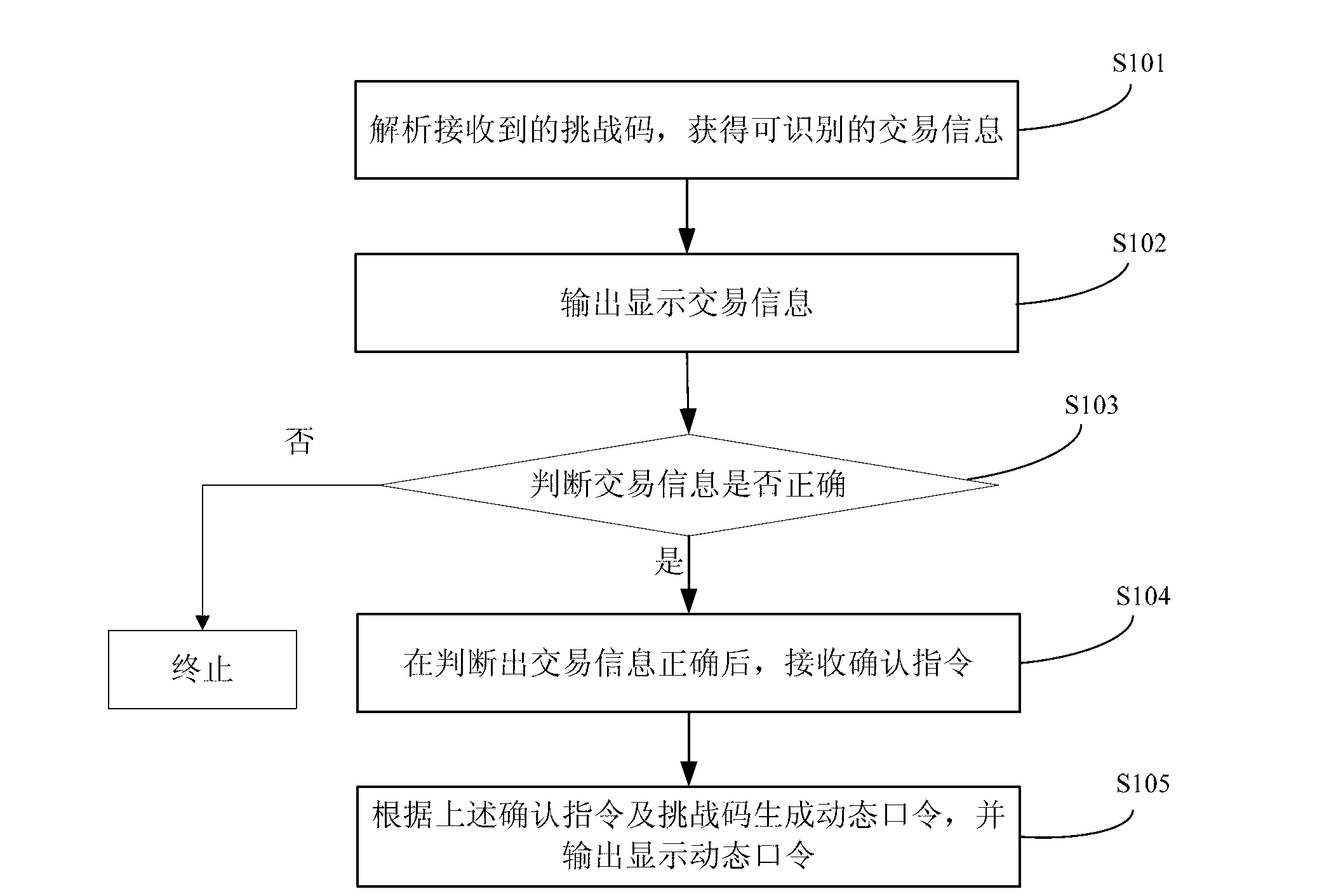
The invention provides a dynamic password card. The dynamic password card comprises a parsing module, a button, an OTP (one time password) generating module and a dispaly screen, wherein the parsing module is used for parsing a received challenge code to obtain recognizable deal information, and outputting the deal information to the display screen; when the deal information displayed by the display screen is correct, the button receives a first confirmation instruction which is then output to the OTP generating module; the OTP generating module generates a dynamic password according to the first confirmation instruction of the button and the challenge code and outputs the dynamic password to the display screen; and the display screen is used for displaying the deal information output from the parsing module and the dynamic password generated by the OTP generating module. The dynamic password card provided by the invention can parse the key deal information (such as an account number and an amount of money) and display the information to users according to the input challenge code when detecting that the challenge code is input, so that the users can master the specific conditions of deal, and the dynamic password is prevented from being misused to cause the insecurity of capital accounts of the users.
Owner:TENDYRON CORP
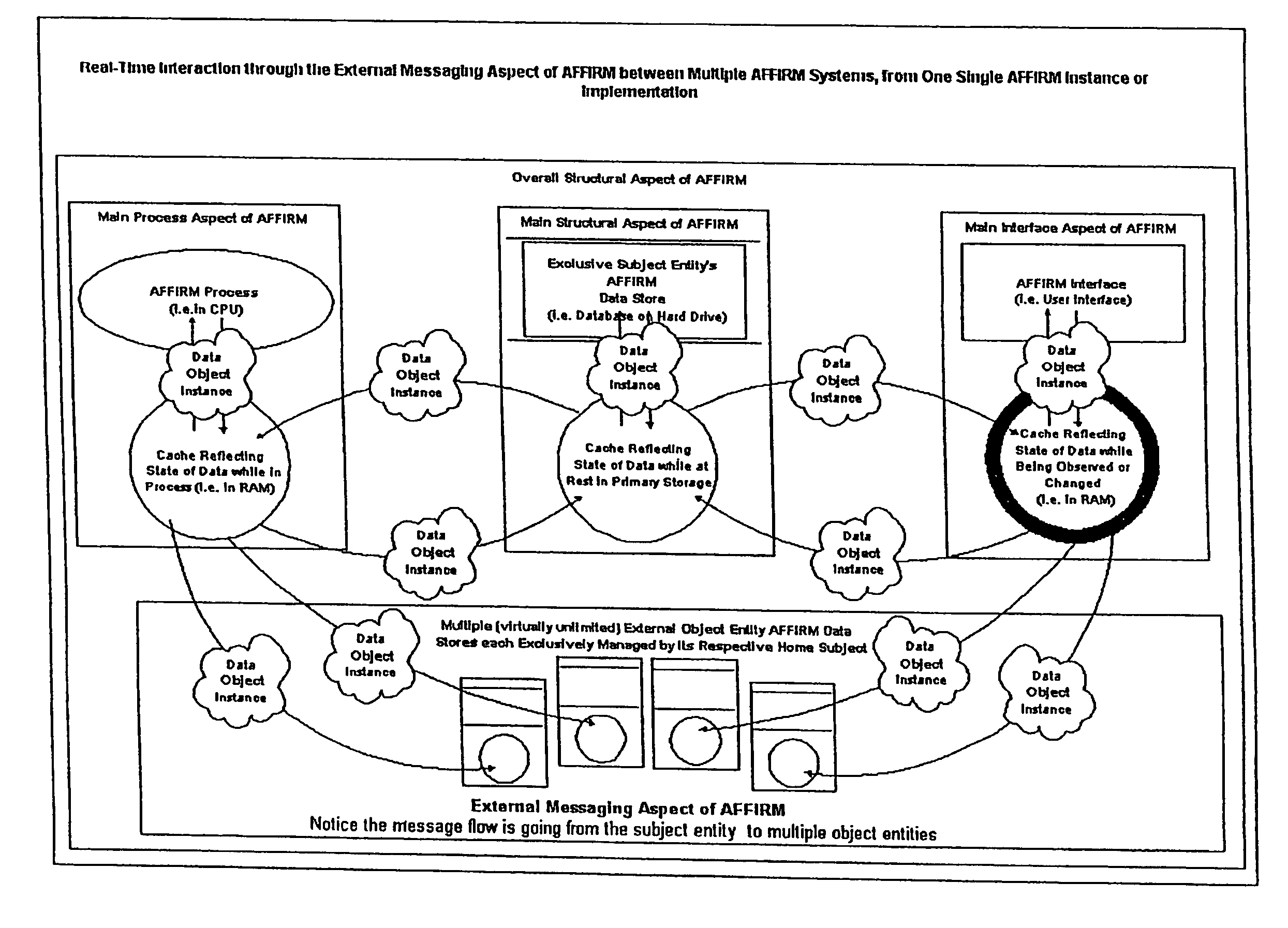
Architectural frameworks, functions and interfaces for relationship management (affirm)
ActiveUS20090006467A1Unique qualityGood tracked and monitoredObject oriented databasesResourcesCustomer relationship managementComputer science
Uniform subject and object oriented data structure adopted in computing device to efficiently store, distribute and process data in a variety of applications. Said data structure comprised of multiple complementary subparts that together and independently facilitate communication (of inputs and outputs) through one or more defined interfaces to facilitate secure access and coordination between given individual subject(s) and other real (physical or metaphysical) entities. Methods are also disclosed that work in tandem with the data structure and interface components to enable and require a single or given human user or other individual personal subject (belonging to a secure AFFIRM network) to maintain exclusive (private) self-control over at least one virtual domain that represents themselves (their actions and their relationships).
Owner:RSVPRO
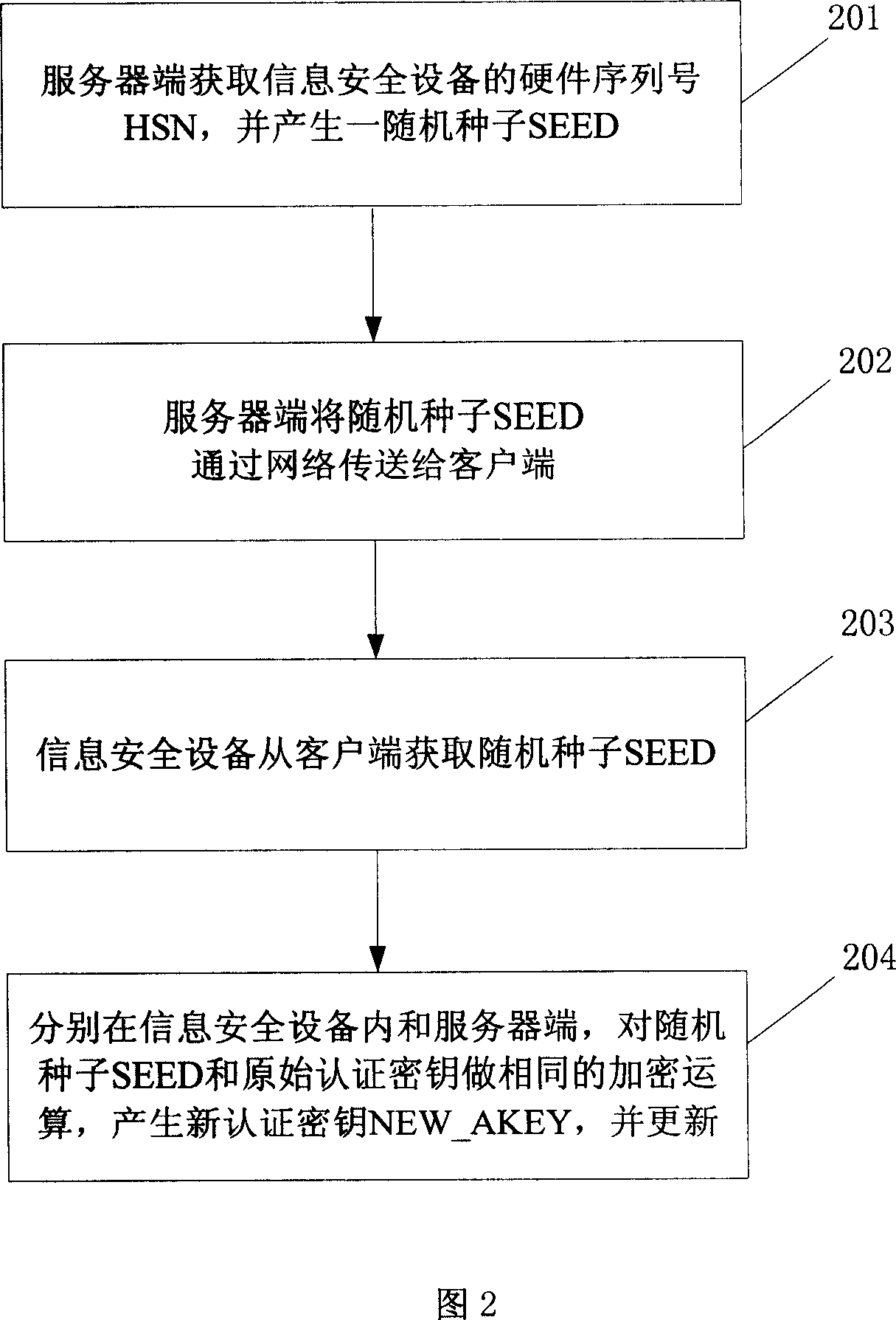
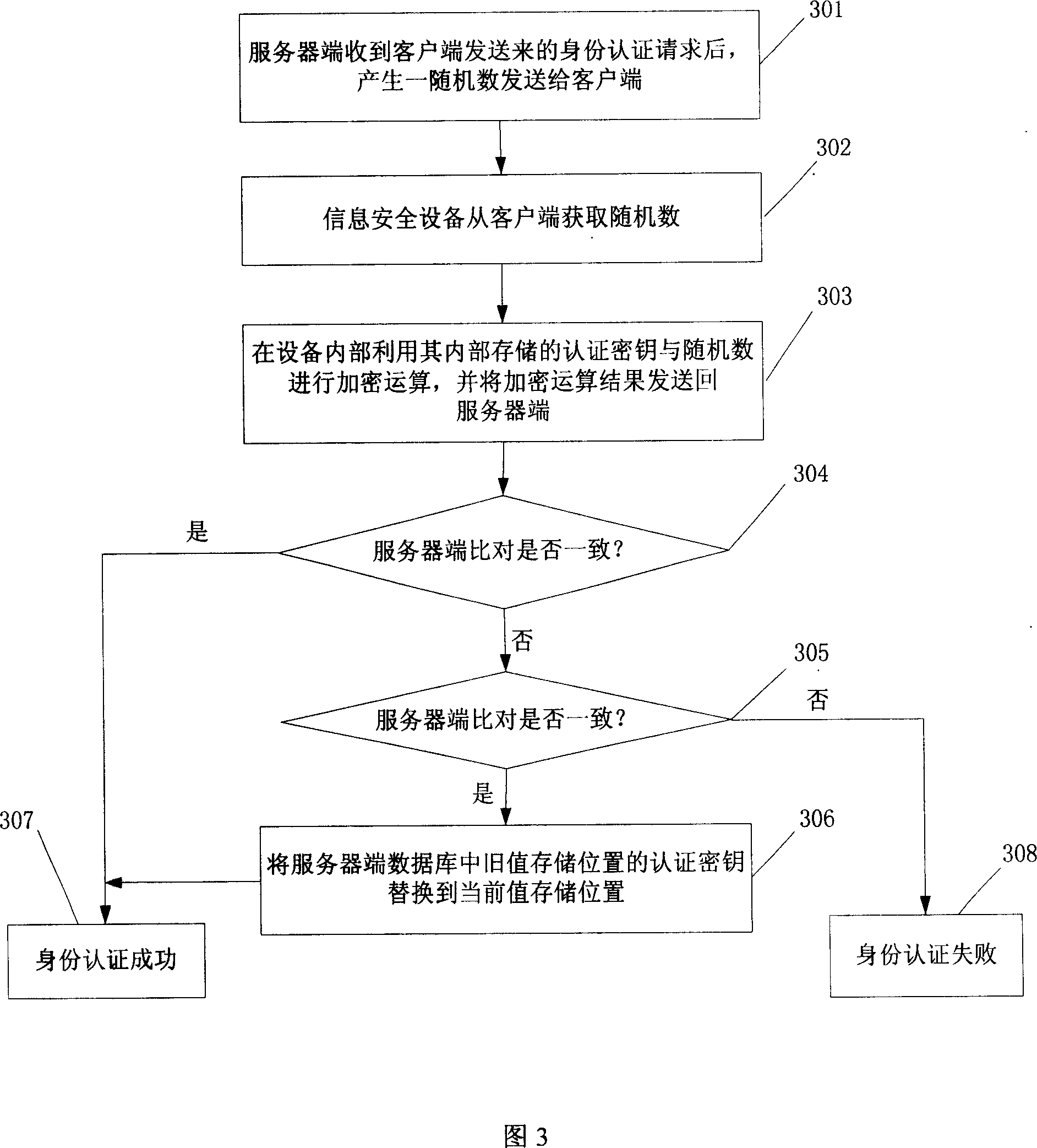
Method and system for updating certification key
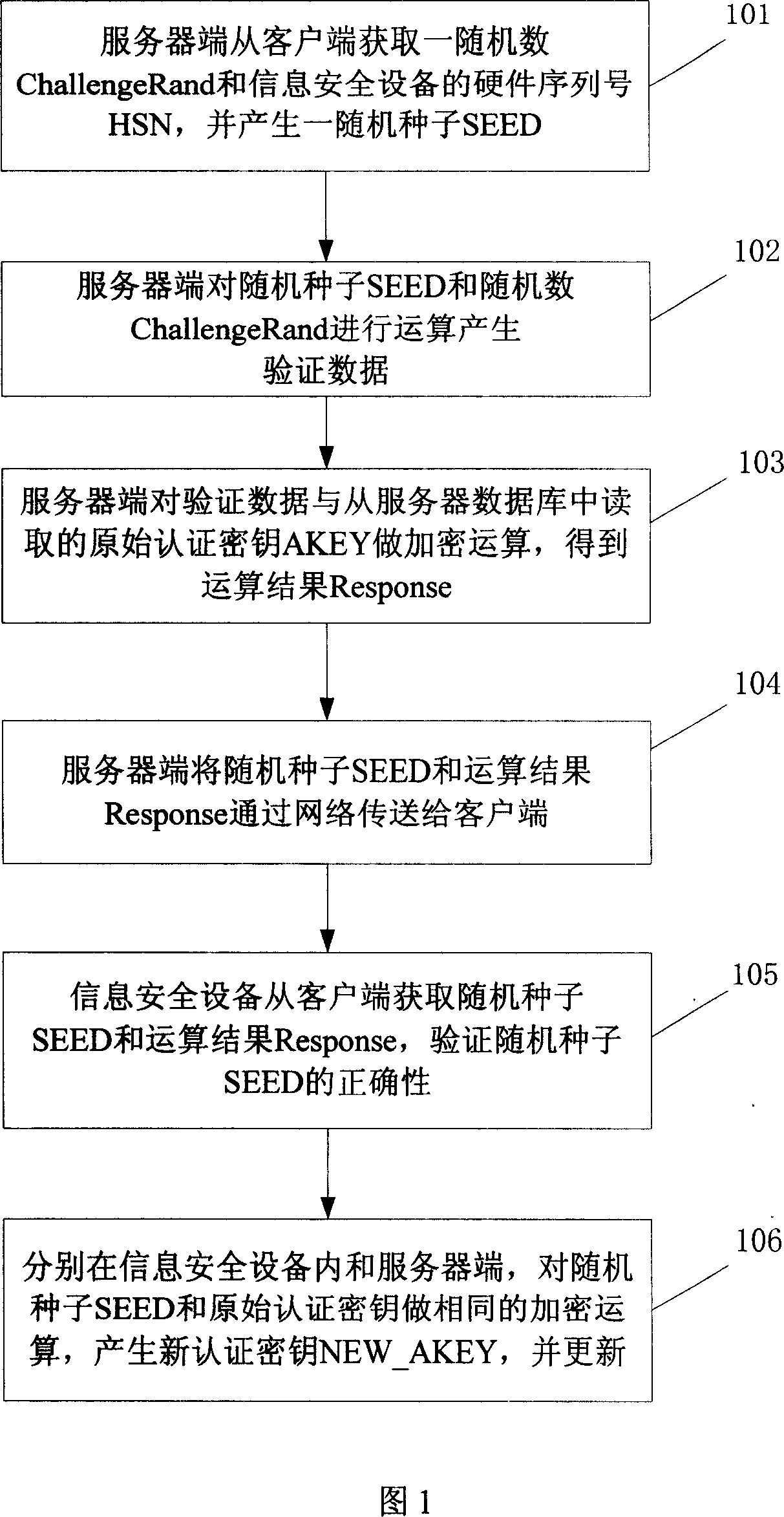
The invention is to solve issues: not security of transferring authentication cipher key through network by using plaintext; and managing bother, and high cost by using cryptograph format to transfer authentication cipher (AC). The disclosed method for updating AC remotely includes steps: server end calculates random seed and random number to generate verification data; server end carries out encryption operation for original AC and verification data, and transfers random seed and result of encryption operation to client end; information security equipment validates correctness of random seed; carrying out same encryption operation for random seed and original AC inside the information security equipment, and at server end so as to generate new AC, which is in use for updating AC inside the information security equipment, and database in server. The invention also discloses system for updating AC.
Owner:FEITIAN TECHNOLOGIES
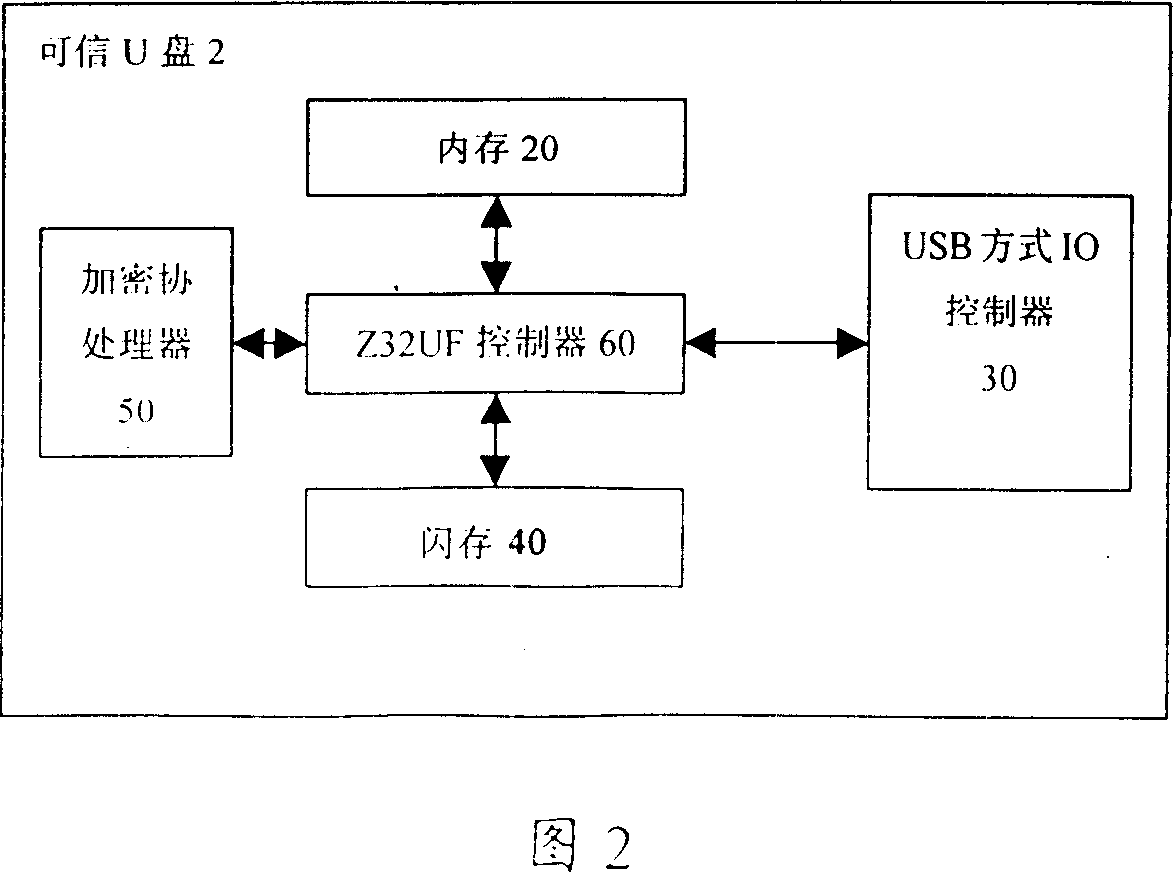
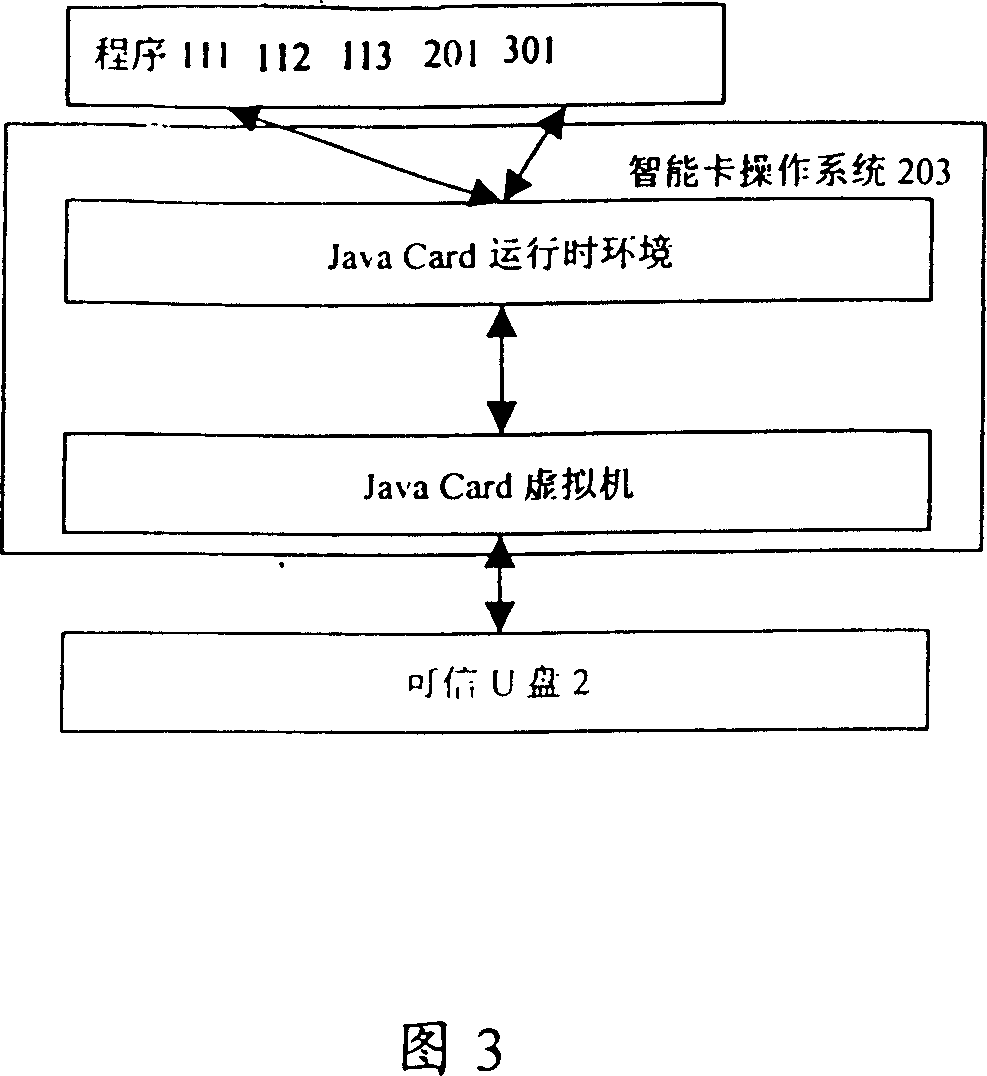
Reliable U disc, method for realizing reliable U disc safety and its data communication with computer
InactiveCN101051292AAvoid insecurityComprehensive consideration of safetyUnauthorized memory use protectionDigital data protectionOperational systemSCSI
A credible U disc is featured as properly solving safety problem of credible U Disc and data communication problem between computer and U disc by utilizing self-destroyed program, certificate certifying program, Applet certification program and SCSI command operated on operation system of intelligent card to carry command of intelligent card.
Owner:中国信息安全产品测评认证中心 +1
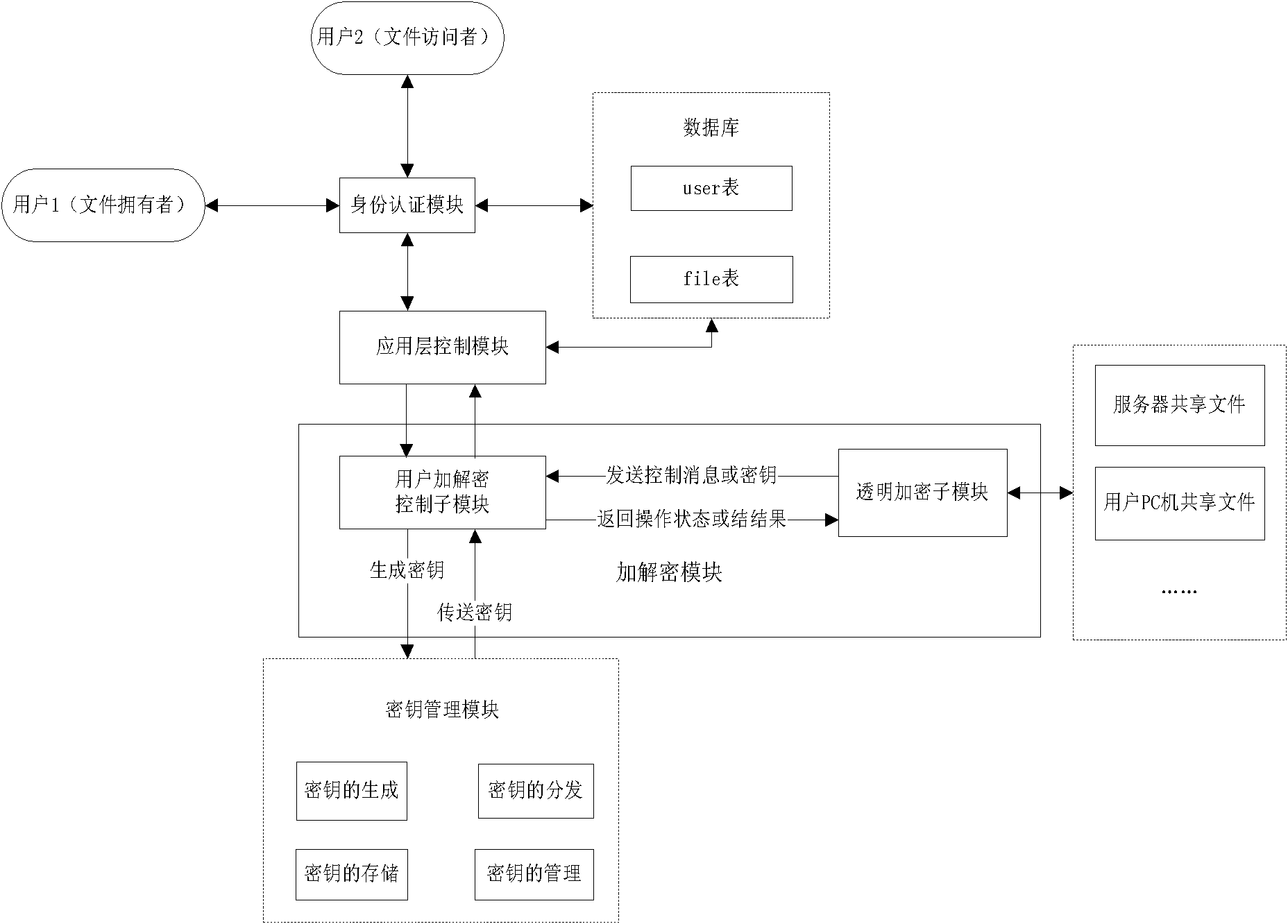
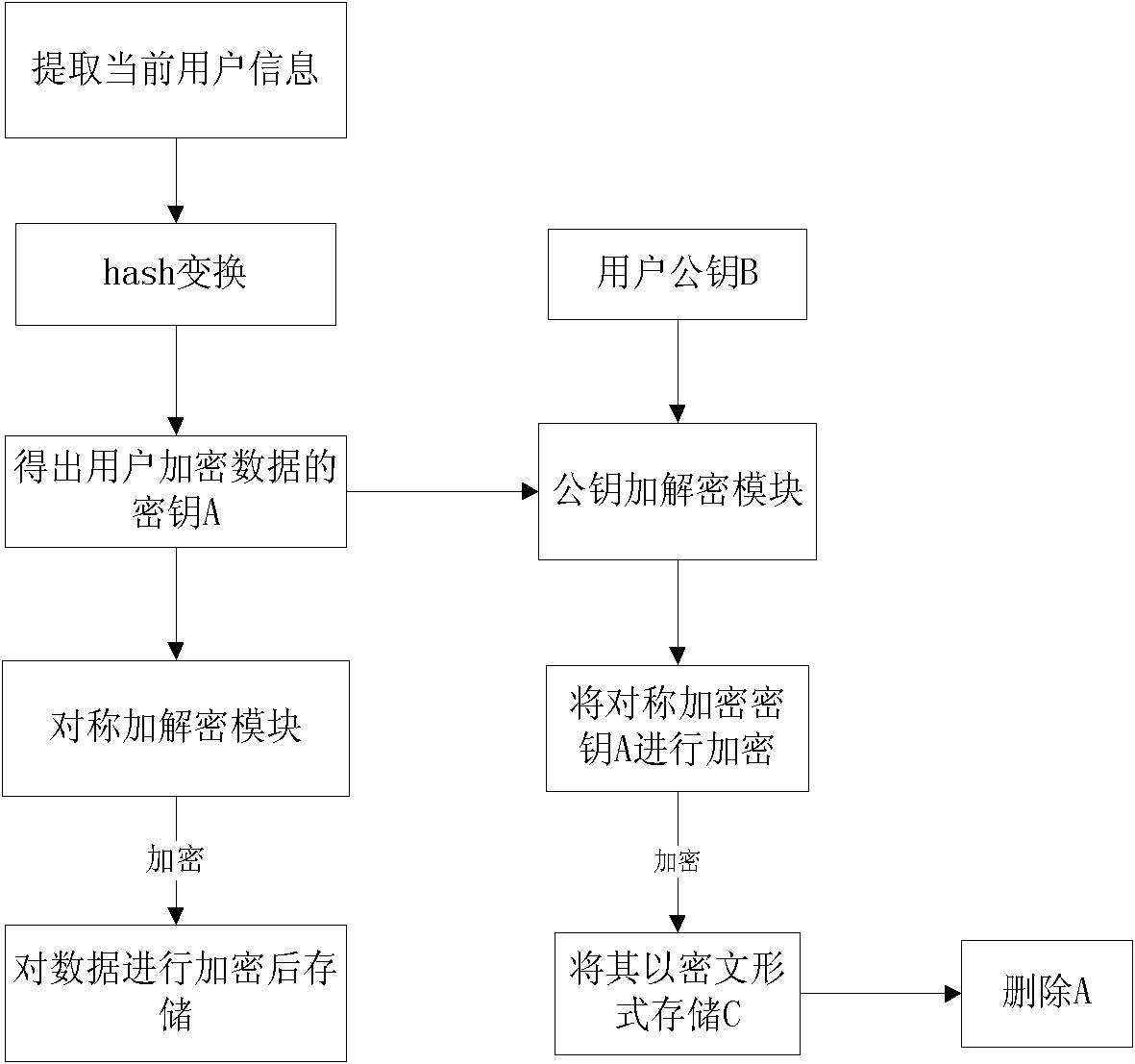
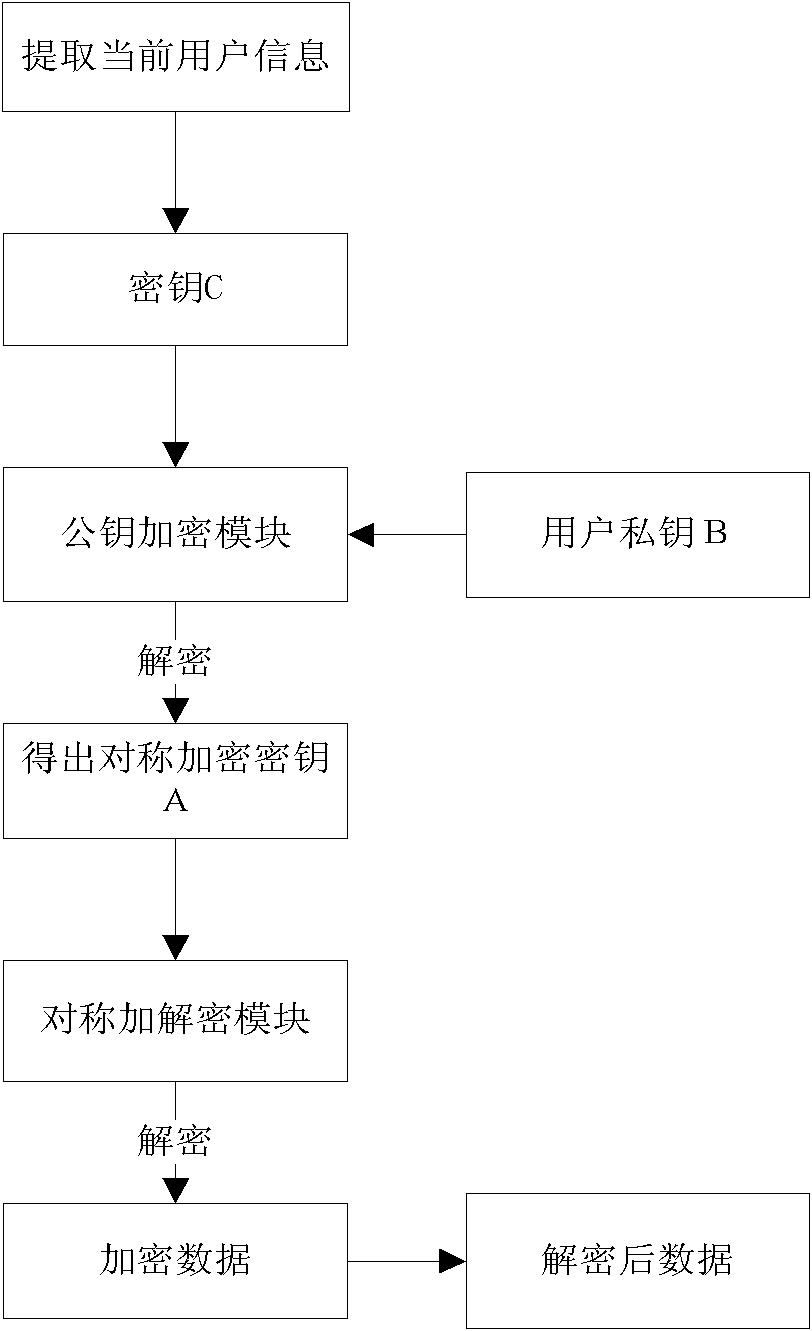
Encryption system, encryption method and decryption method for local area network shared file
InactiveCN102075544AEnsure safetyGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationInformation securityShared resource
The invention discloses an encryption system for a local area network shared file. The system comprises a secret key management module of a secret key to be used by reading, generating and managing an encryption file, and an encryption and decryption module for performing encryption and decryption according to a user command. The encryption system is characterized by also comprising an identity authentication module used for verifying the identity of a user and determining the authority of the user; and after the identity authentication module verifies that the identity of the user is legal, the encryption and decryption module performs encryption and decryption, and then the local area network shared file is accessed. The system limits the authority that different specified users read different files in shared resources, so that the information safety of resources in the local area network can be effectively guaranteed.
Owner:博视联(苏州)信息科技有限公司
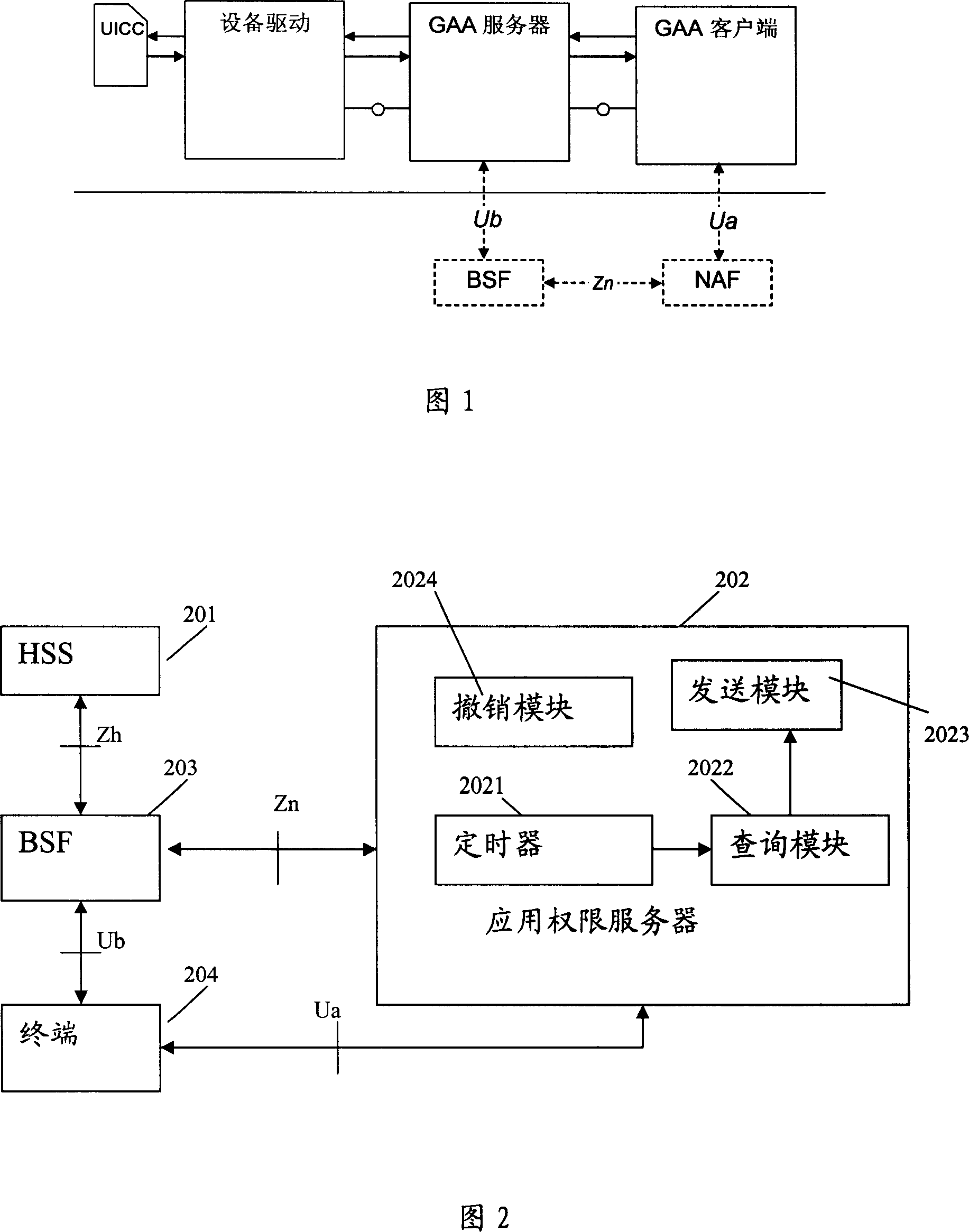
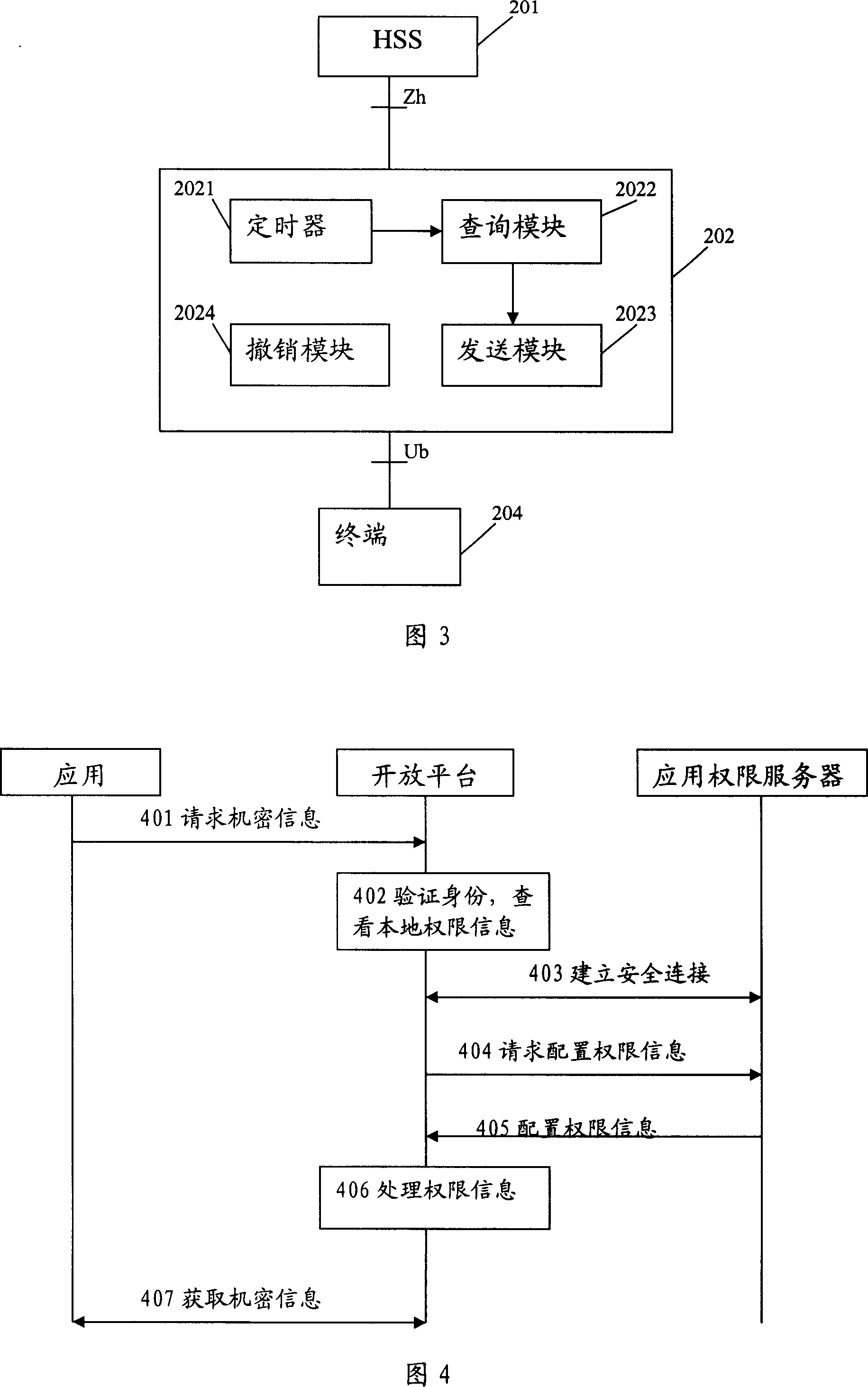
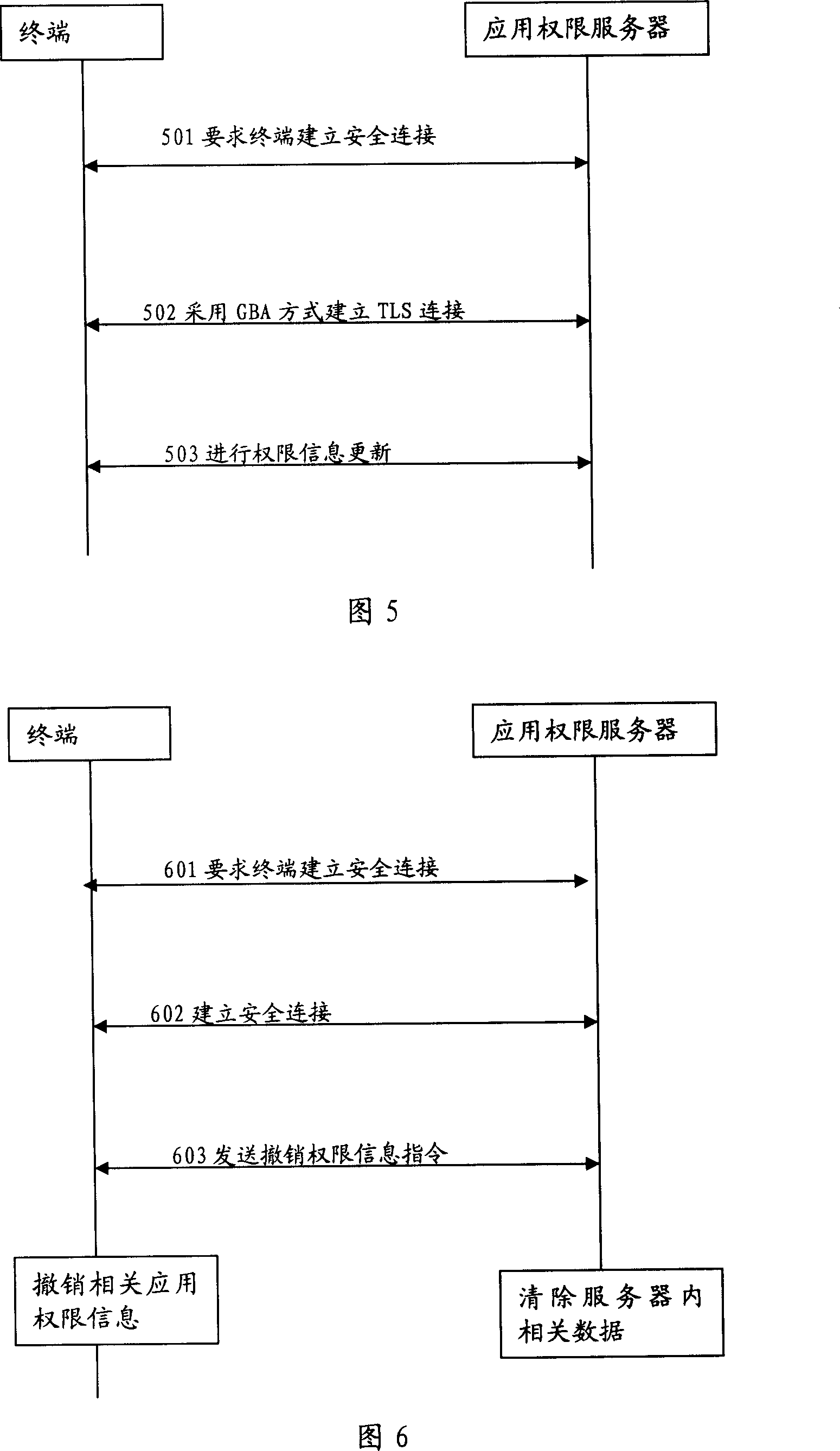
Method and system for managing terminal open platform power information
InactiveCN101005699AEnsure safetyAvoid insecurityRadio/inductive link selection arrangementsSecurity arrangementOpen platformDatabase
The method comprises: the network side has an application authority server saving all application rights information; the application authority server sends the application right information to terminals; the terminals save the application rights information. The invention also reveals a system thereof, which comprises an application authority server used for saving all application right information, and configuring, updating and canceling the application right information saved in the application authority server.
Owner:HUAWEI TECH CO LTD
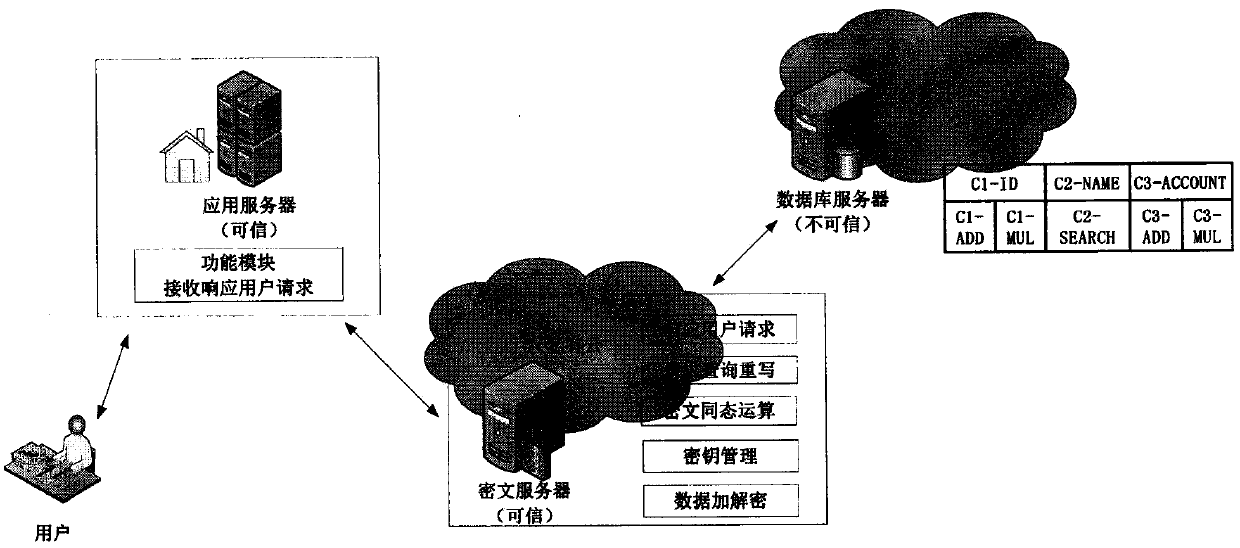
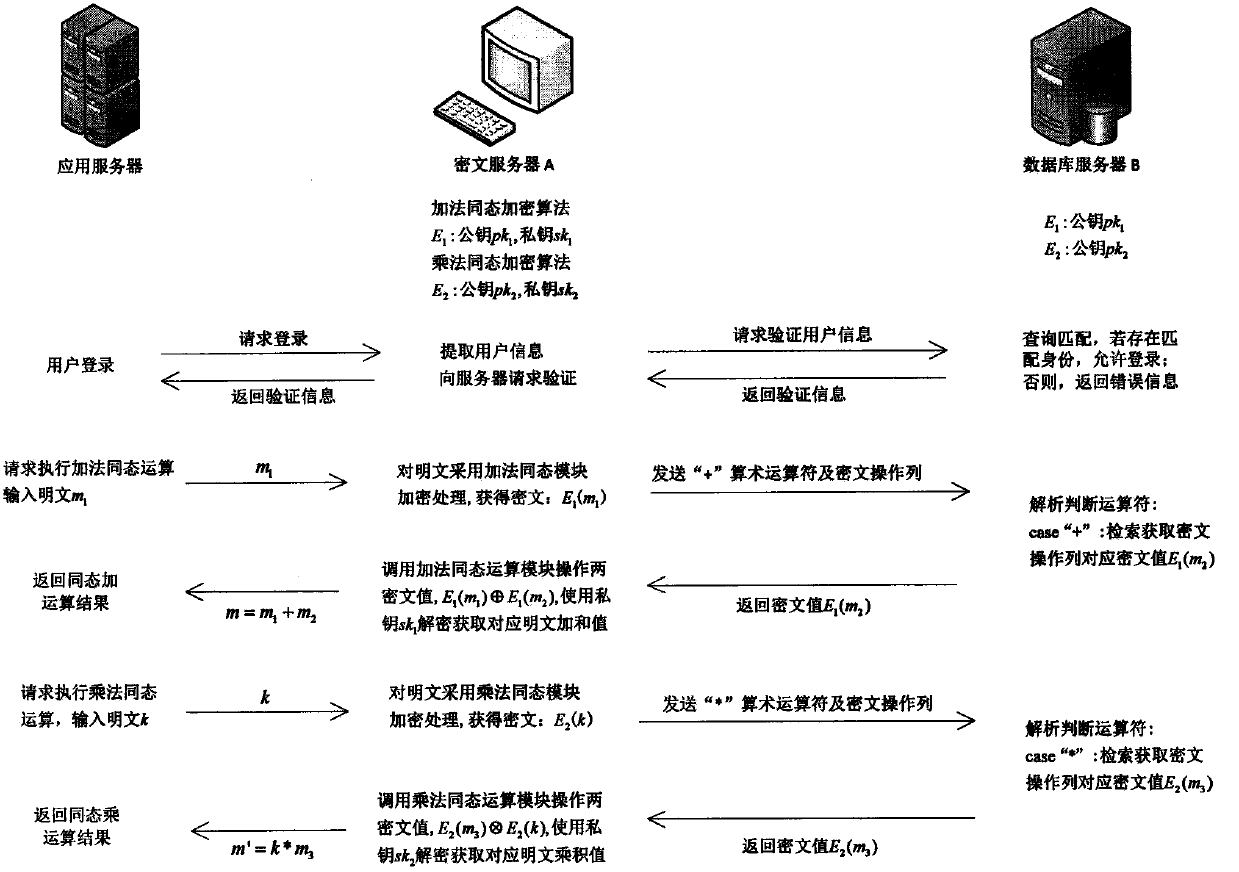
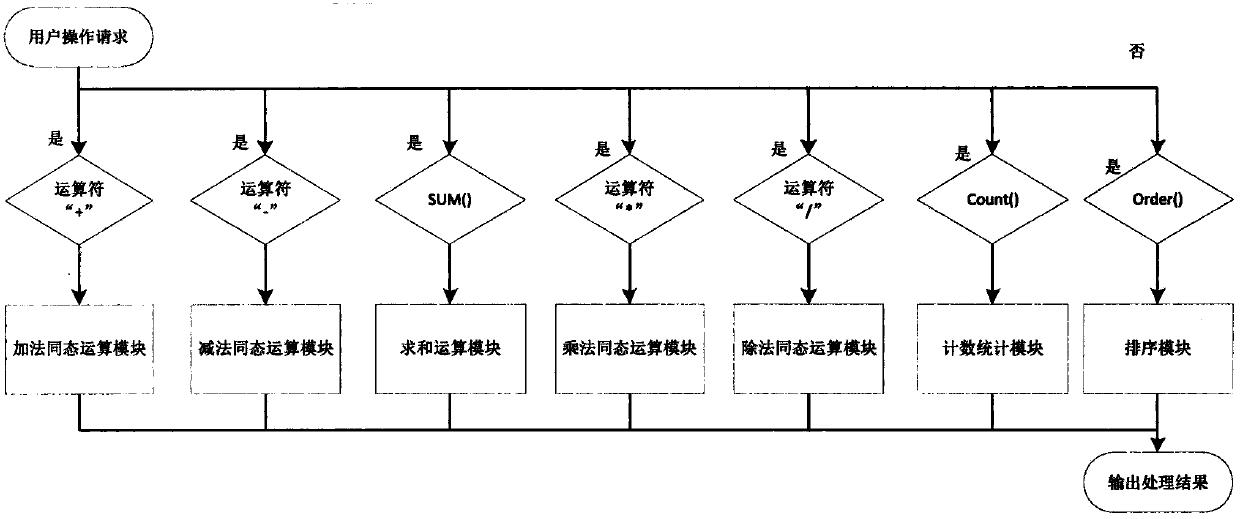
Quasi-fully homomorphic ciphertext data operation method and system
InactiveCN107592195AAvoid insecuritySolving inefficienciesSecuring communicationThird partyCiphertext
The present invention discloses a quasi-fully homomorphic ciphertext data operation method and system and belongs to the ciphertext database and network data privacy protection technical field. The fully homomorphic cipher operation-based hybrid cloud platform architecture is provided, existing database configurations are not needed to be drastically modified, and therefore, a construction mode issimple; a ciphertext server is defined to support homomorphic calculation, query interception rewriting, data encryption and decryption, key management and other functions, is deployed at the privatecloud platform of a local data center and can establish a connection between the local data center and a third-party public cloud platform; a classified field extension mode is adopted, field extension is performed on numerical value data and character type data; by means of mode innovation, quasi-fully homomorphic ciphertext conventional arithmetic calculation is performed on the numerical valuedata through a functional demand-based cipher service strategy; query / operation is directly performed on ciphertext data; and therefore, the processing efficiency of the data and the security of thestorage and retrieval of the data can be improved.
Owner:BEIJING ELECTRONICS SCI & TECH INST
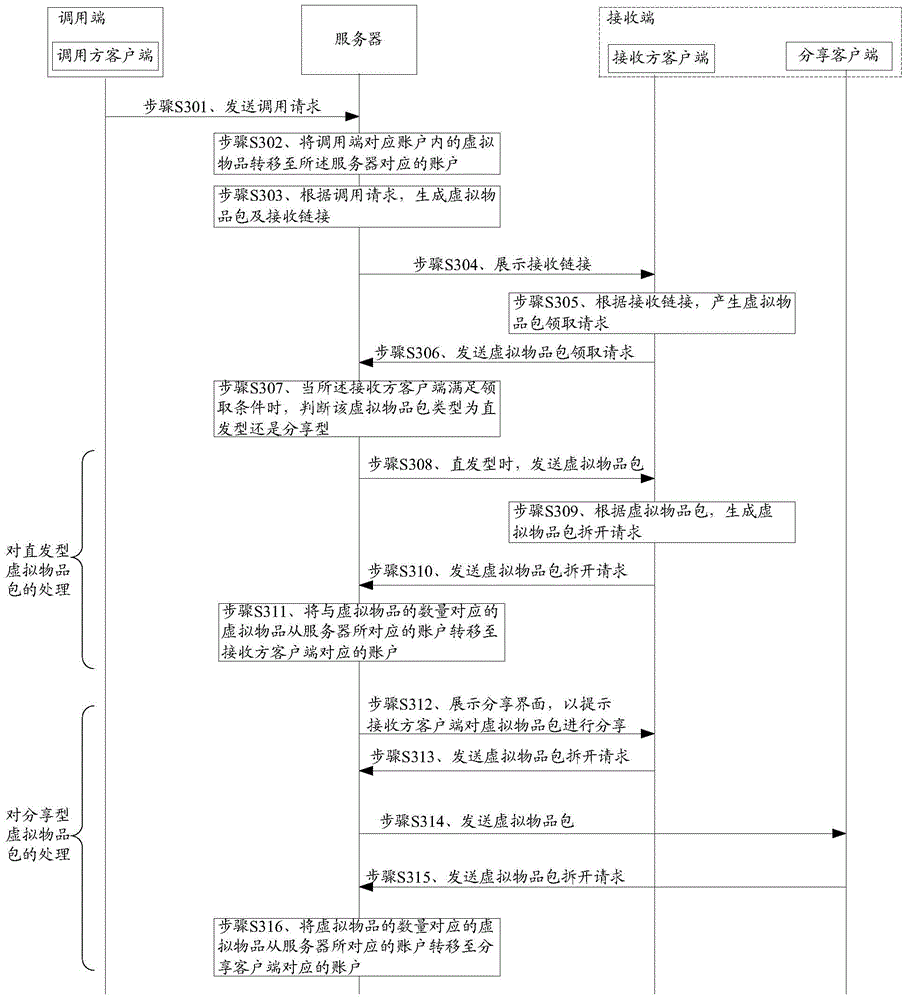
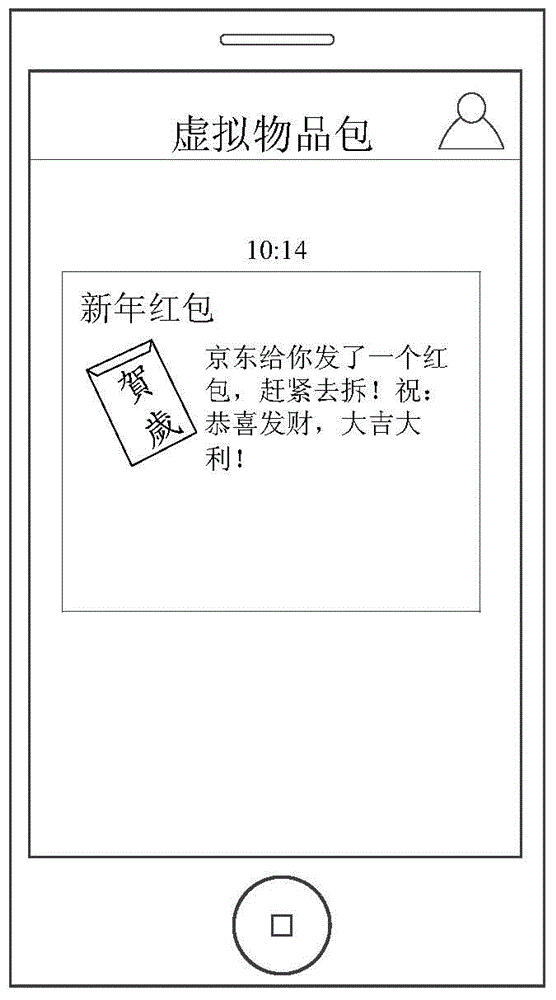
Virtual good sending method and device, receiving method and device, and system
ActiveCN105100162AEasy to operateShort timePayment architectureApparatus for meter-controlled dispensingClient-sideVirtual goods
A method and device for sending and receiving virtual goods are provided. On detecting an invocation request from a virtual goods package generation interface, a server obtains the virtual goods package generation parameters included in the invocation request. The server transfers the virtual goods corresponding to the total amount of virtual goods in the account corresponding to the invoker client to the account corresponding to the server. Upon success of virtual goods transfer, the server generates a virtual goods package and a link for receiving the virtual goods package based on the virtual goods package generation parameters. The server sends the receiving link to the recipient client so that the recipient client interacts with the server to receive the virtual goods package by using the receiving link.
Owner:TENCENT TECH (SHENZHEN) CO LTD
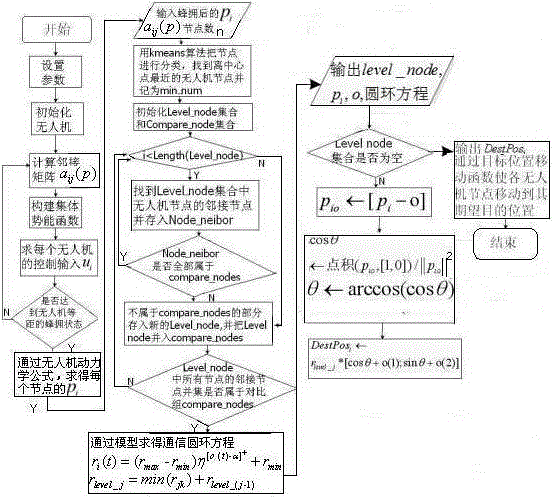
Cooperative control policy based on secure communication of multiple unmanned aerial vehicles
InactiveCN105867415ATo achieve the purpose of secure communicationIncrease autonomyPosition/course control in three dimensionsVehicle dynamicsSecure communication
The invention discloses a cooperative control policy based on secure communication of multiple unmanned aerial vehicles. The cooperative control policy comprises a first step of applying an Olfati-saber flocking control algorithm of a variable speed virtual leader to perform preliminary cooperative control over an unmanned aerial vehicle group; a second step of introducing a virtual communication circle to perform on-line communication power setting on each unmanned aerial vehicle, and calculating an expected position of each unmanned aerial vehicle node meeting the secure communication requirements; and a third step of applying an optimized position movement function to make each unmanned aerial vehicle node move to the expected position obtained in the second step securely without collision. According to the cooperative control policy, how communication affects unmanned aerial vehicle group dynamics and communication topology is studied more; through the newly provided virtual communication circle and by combination of an improved target movement function and an existing classic dynamics flocking algorithm, the problem of insecurity of information leakage possibly occurring to a multi-unmanned aerial vehicle system is effectively solved, and the cooperative control policy is a new idea for describing relations of unmanned aerial vehicle dynamics and wireless ad hoc networks.
Owner:SHENYANG AEROSPACE UNIVERSITY
Login method and device, terminal and network server
ActiveCN103297408AAvoid insecurityEasy loginDigital data authenticationTransmissionPasswordComputer terminal
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Electric vehicle power battery pack temperature control system based on heat pipes
ActiveCN103928729AAvoid heatingAvoid coolingSecondary cellsCell component detailsTemperature controlPower battery
The invention discloses an electric vehicle power battery pack temperature control system based on heat pipes. The electric vehicle power battery pack temperature control system is characterized in that a battery pack temperature control box body is a sealed box body, a sealed battery grouping bin is contained in the sealed box body, the length and the height of the battery grouping bin are smaller than those of the battery pack temperature control box body, but the widths of the two components are equal; an annular heat exchange bin is formed between the battery grouping bin and the battery pack temperature control box body; the heat pipes are arranged in the battery grouping bin along the length direction in a penetration manner, the heat pipes penetrate through insulating heat sinks arranged in parallel, and the ends of the heat pipes are located in the annular heat exchange bin; single batteries are arranged between the insulating heat sinks, the radiating surfaces of the single batteries are fitted with the insulating heat sinks; a heater and an evaporator are respectively arranged in the annular heat exchange bin. The electric vehicle power battery pack temperature control system disclosed by the invention can be used for solving the problem that effective heat treatment cannot be performed on each single battery due to overlarge flow resistance and achieving sealed design of the battery box body, the safety is high, the temperature of the power battery is regulated quickly, and the temperature field distribution is uniform.
Owner:芜湖汇展新能源科技有限公司
Architectural frameworks, functions and interfaces for relationship management (AFFIRM)
ActiveUS8849862B2Good tracked and monitoredAvoid insecurityDigital data processing detailsObject oriented databasesCustomer relationship managementComputer science
Uniform subject and object oriented data structure adopted in computing device to efficiently store, distribute and process data in a variety of applications. Said data structure comprised of multiple complementary subparts that together and independently facilitate communication (of inputs and outputs) through one or more defined interfaces to facilitate secure access and coordination between given individual subject(s) and other real (physical or metaphysical) entities. Methods are also disclosed that work in tandem with the data structure and interface components to enable and require a single or given human user or other individual personal subject (belonging to a secure AFFIRM network) to maintain exclusive (private) self-control over at least one virtual domain that represents themselves (their actions and their relationships).
Owner:RSVPRO
Remote control based network-distribution conduction device for live working
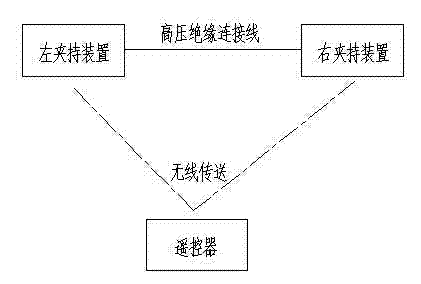
ActiveCN102832569ASimplify operating proceduresAvoid inconvenienceApparatus for overhead lines/cablesRemote controlPositive pressure
The invention relates to a mounting device for an overhead line or a cable, in particular to a remote control based network-distribution conduction device for live working. The structural feature of the network-distribution conduction device comprises a pair of clamping devices, a high-voltage insulation connection wire and a remote control unit. The clamping devices in the conduction device is remotely controlled by a remote control unit so as to clamp and loosen, the operation program of an operator is simplified, a series of inconvenient and unsafe problems brought due to the local operation of the operator are avoided, and meanwhile, the operation reliability problem brought by remote distance manual operation is avoided; the work pressure of the operator is reduced, and the safe production is guaranteed; and moreover, as a speed-down motor is adopted, a balanced clamping action force is exerted to a guide line, so that the problems that the guide line is damaged due to the facts that the force exerted by manual work is uneven, and the direction is deviated, are avoided; and the radian symmetry structure of a movable jaw and a bridge-shaped fixed jaw can adapt to the surface radian of the guide line, and a good surface contact is provided, so that a positive pressure is exerted to the guide line, and the damage problem of the guide line is further solved.
Owner:STATE GRID CORP OF CHINA +2
Waste glass crushing device
ActiveCN106694096AOvercome the problem of low crushing efficiencyCompletely brokenGrain treatmentsDrive wheelEngineering
The invention belongs to the technical field of glass processing, and particularly discloses a waste glass crushing mechanism. The waste glass crushing mechanism comprises a control mechanism and further comprises a rack, a rotation feeding barrel and a pair of crushing rollers arranged in the rotation feeding barrel. Drive wheels driving the rotation feeding barrel are arranged on the outer wall of the rotation feeding barrel in the circumferential direction. The rotation feeding barrel, the drive wheels and the crushing rollers are all connected to the rack. A spiral groove is formed in the inner wall of the rotation feeding barrel. The crushing rollers are conical rollers. The diameter of the parts, at the feeding end position of the rotation feeding barrel, of the crushing rollers is smaller than the diameter of the parts, at the discharging end position of the rotation feeding barrel, of the crushing rollers. The rotation feeding barrel, the drive wheels and the crushing rollers are all electrically connected with the control mechanism. Through the arrangement of the device, the problem that in the prior art, the glass crushing efficiency is low is solved, and crushing is more thorough; and meanwhile the quality of regenerated glass manufactured through recycled glass fragments is improved.
Owner:CHONGQING CONGBO ENERGY SAVING GLASS CO LTD
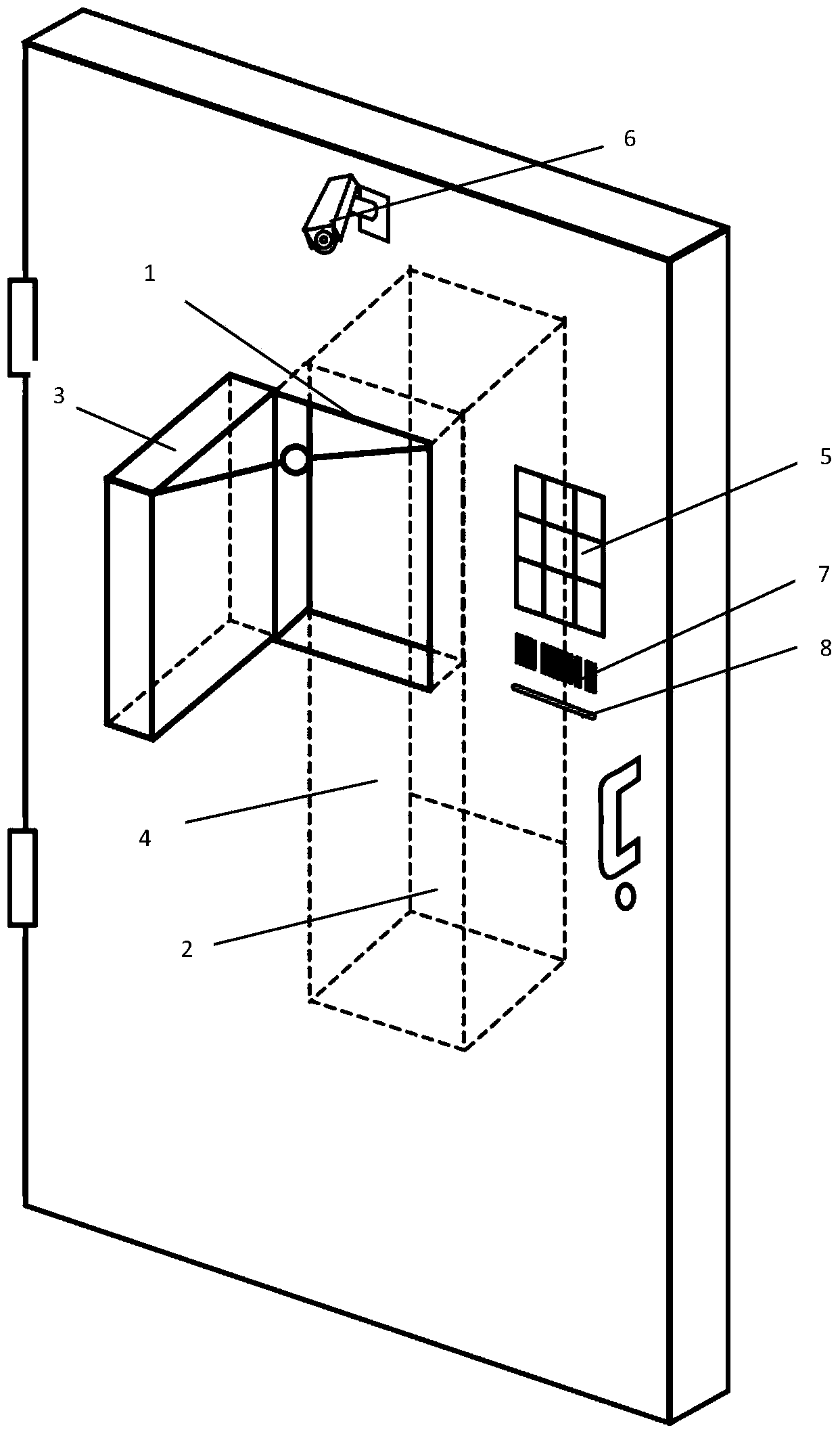
Entrance door provided with intelligent IOT (Internet of Things) terminal
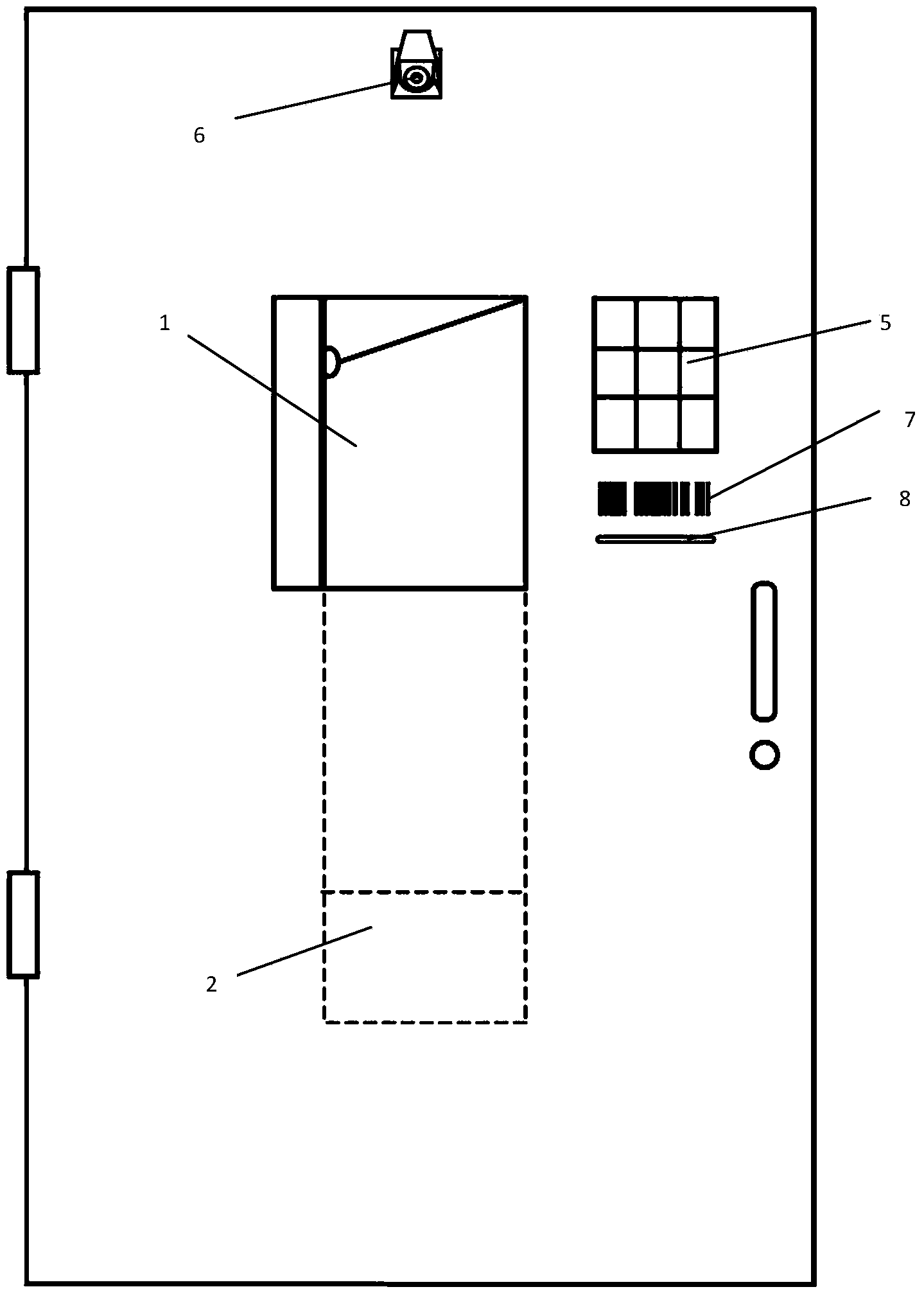
ActiveCN103647851ARealize identificationAchieve receptionTransmission systemsTransmissionAutomatic controlEngineering
The invention discloses an entrance door provided with an intelligent IOT (Internet of Things) terminal, wherein a window is formed in the front side of the entrance door, an article taking opening is formed in the back side of the entrance door, door covers are arranged on the window and the article taking opening, a channel is arranged between the window and the article taking opening, and articles can be put into the window and fall into the article taking opening along with the channel. A control device on the entrance door can be networked with a user so as to automatically control the opening or closing of the door covers so as to monitor the condition before the door. Compared with the prior art, according to the entrance door, the purposes of automatically and intelligently receiving and taking and sending articles can be achieved through the acquaintance of things, so that the entrance door is equivalent to an electronic babysitter; the entrance door fully monitors the receiving and sending processes and the conditions before the door, and generates and retains video evidence, thus being equivalent to an electronic security; the user can be networked with the entrance door at any time, so that the usage efficiency of the user on the IOT is improved, the good use experience of the user on the IOT is increased, and the entrance door has the effect of an intelligent robot and is brought to the field of smart home.
Owner:王恒
System, apparatus, and method for automatically configuring application terminals in home network
InactiveUS20090292794A1Without increase complexityAvoids insecurityHybrid switching systemsDigital computer detailsAuto-configurationComputer hardware
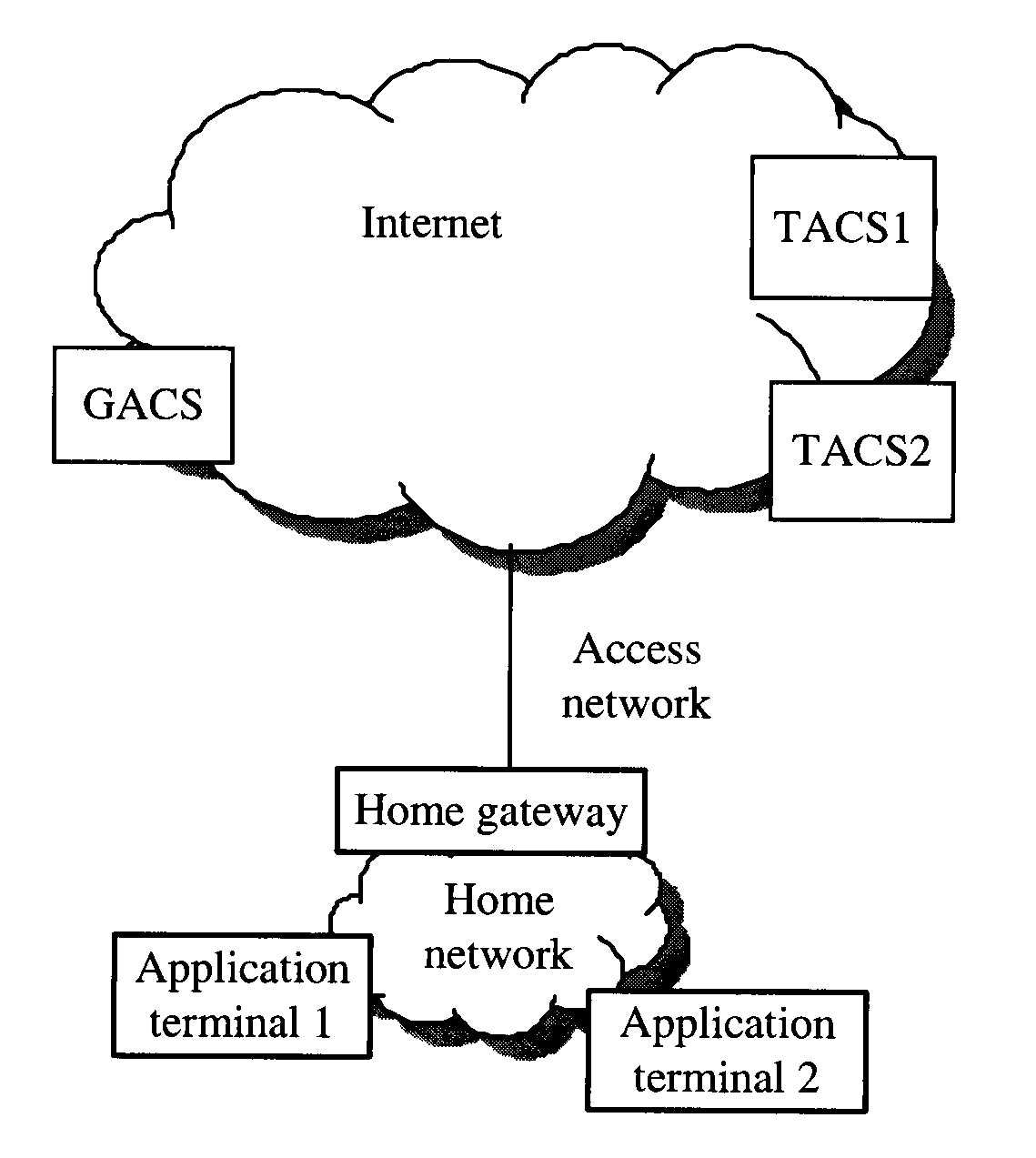
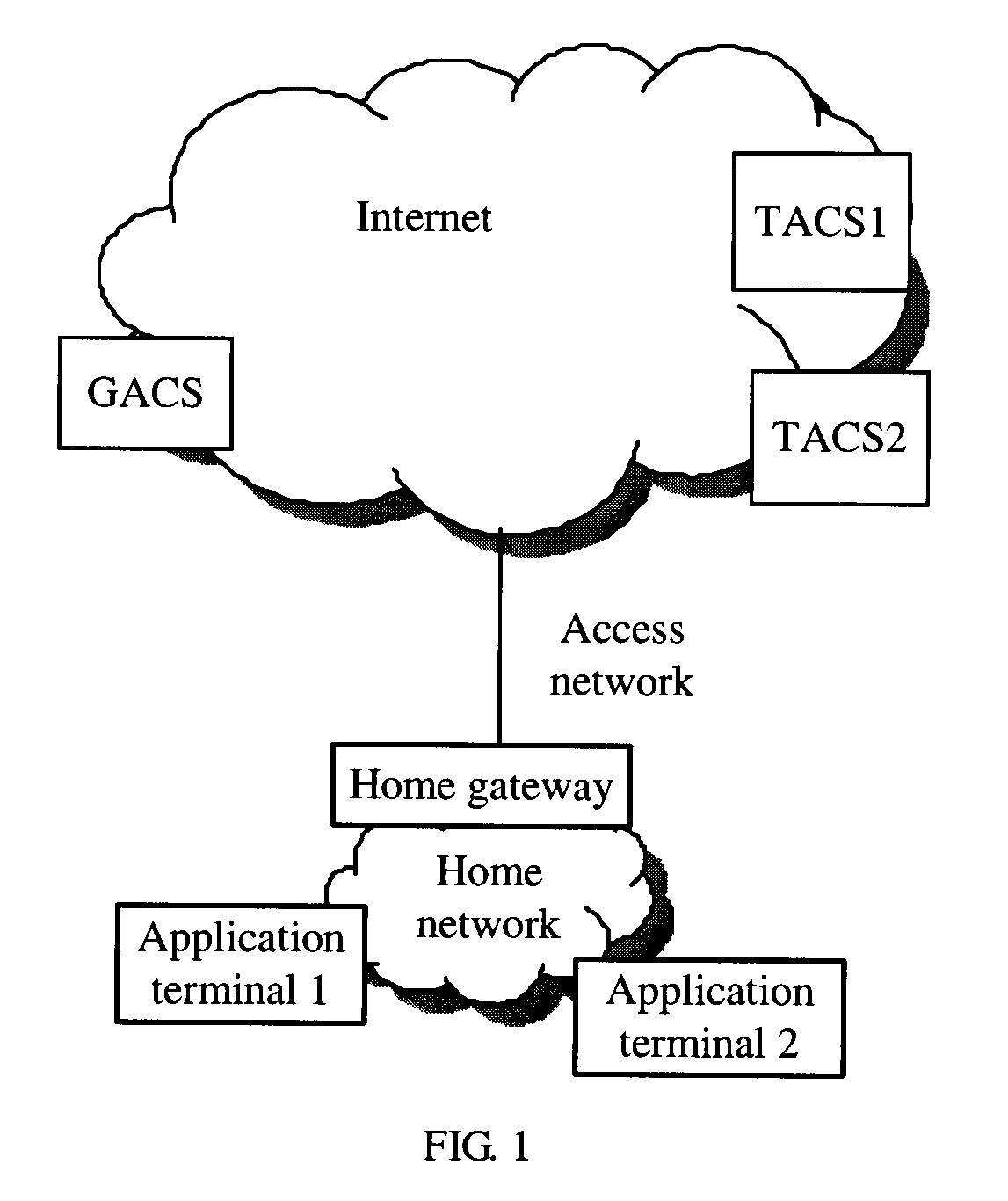
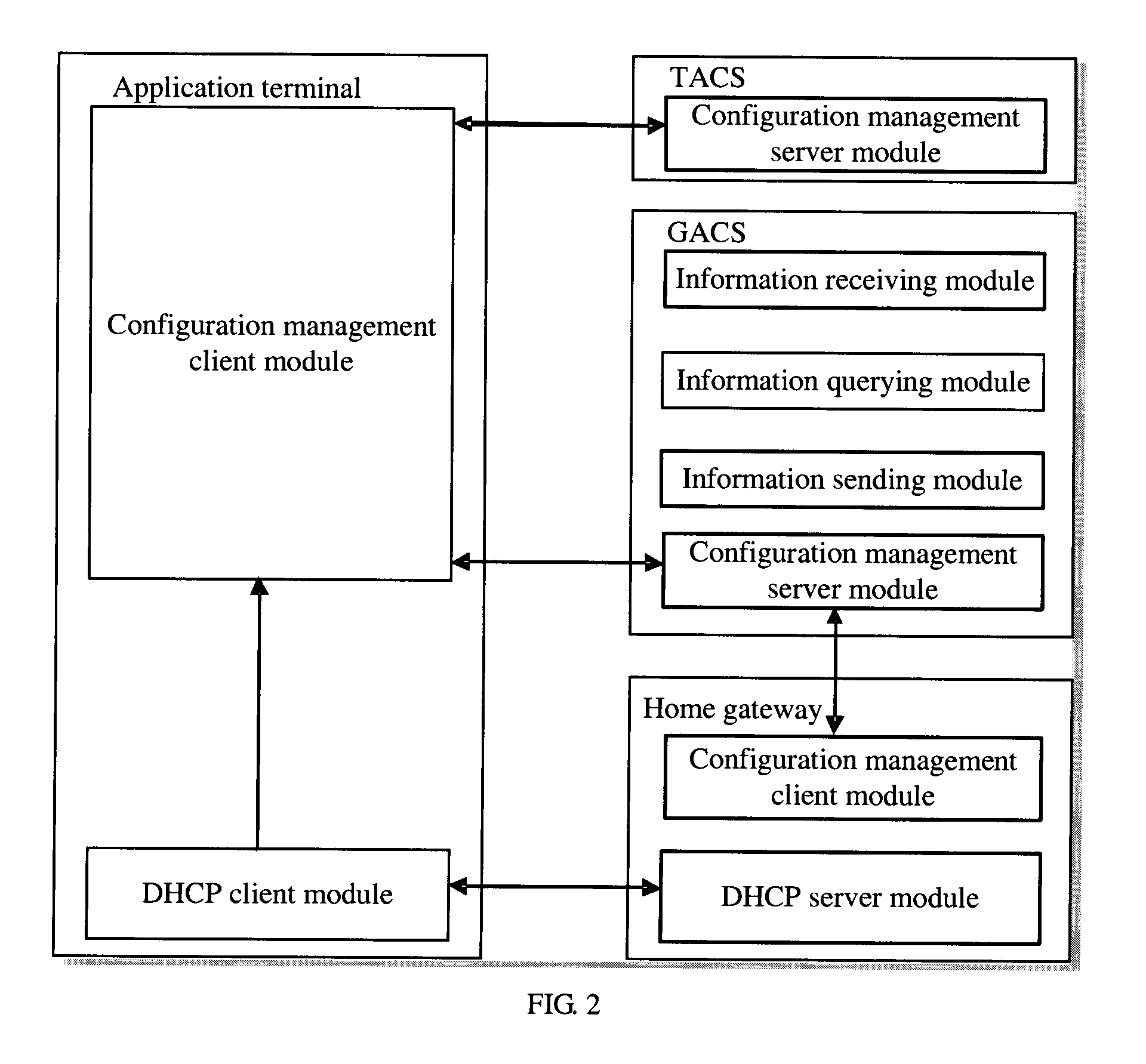
A system, apparatus, and method for automatically configuring application terminals in a home network are provided. The method includes the following steps: the application terminal obtains address information of the GACS from the home gateway and sends a configuration request message to the GACS, the GACS obtains address information of a terminal automatic configuration server (TACS) through query after receiving the configuration request message and sends the address information of the TACS to the application terminal through a configuration response message, and the application terminal sends the configuration request message to the TACS according to the returned address information of the TACS from the GACS to obtain configuration information from the TACS for automatic configuration. The provided system, apparatus, and method may ensure that the application terminal securely obtains the address information of the TACS and thus obtains the configuration, without increasing the complexity of the application terminal.
Owner:HUAWEI TECH CO LTD
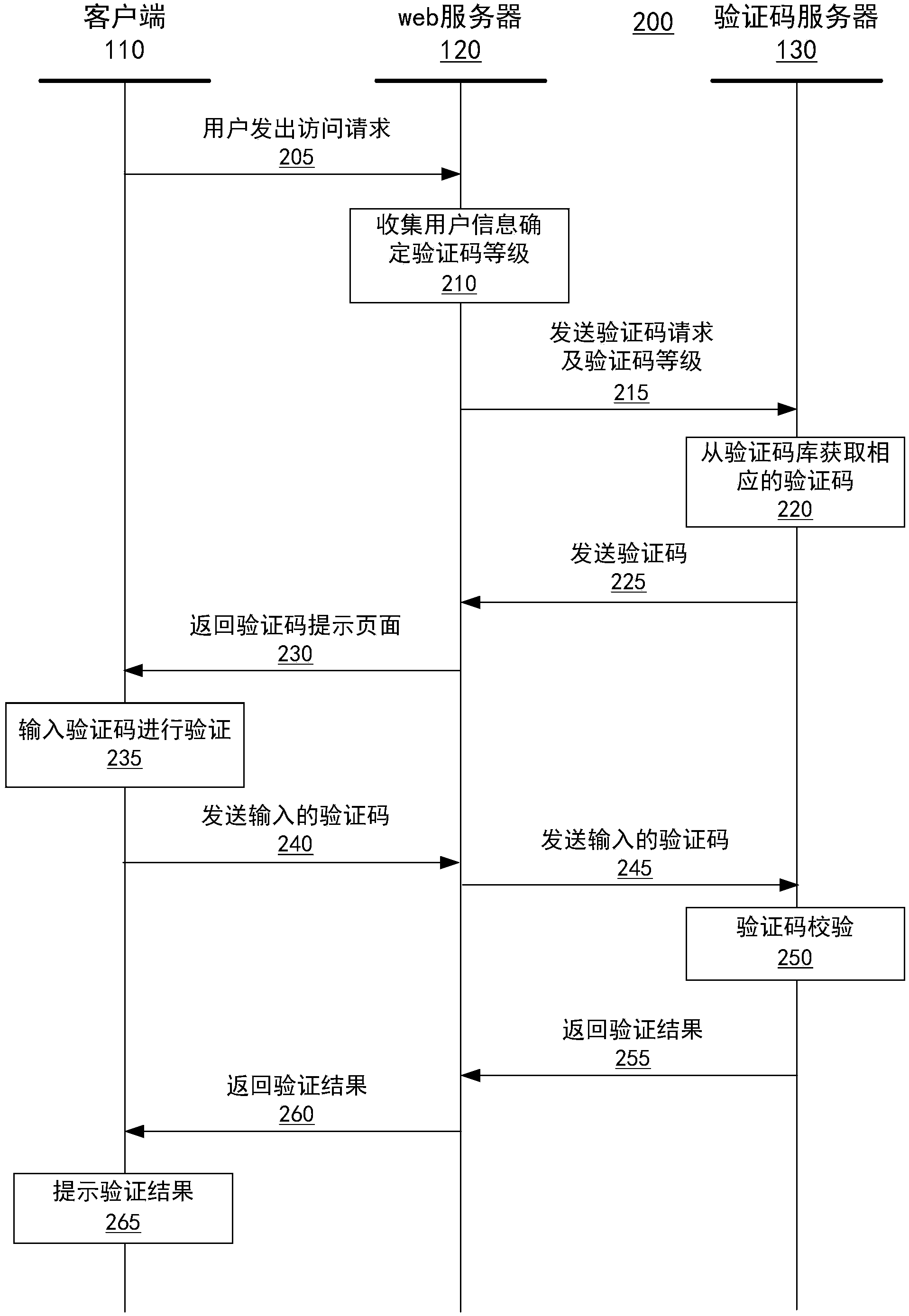
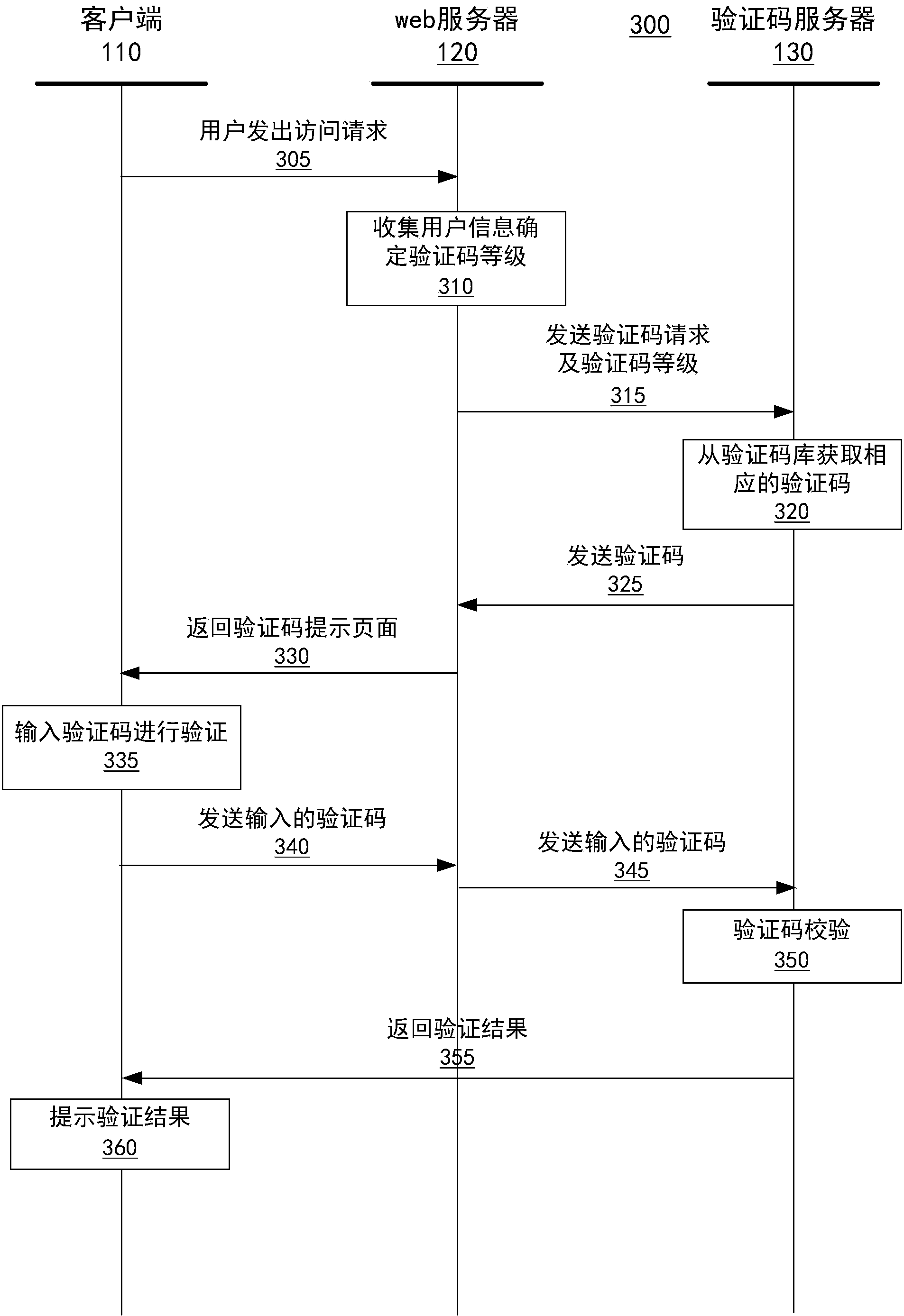
Verification method and system
ActiveCN104038346AAvoid insecurityPrevent unfair behaviorUser identity/authority verificationValidation methodsPassword
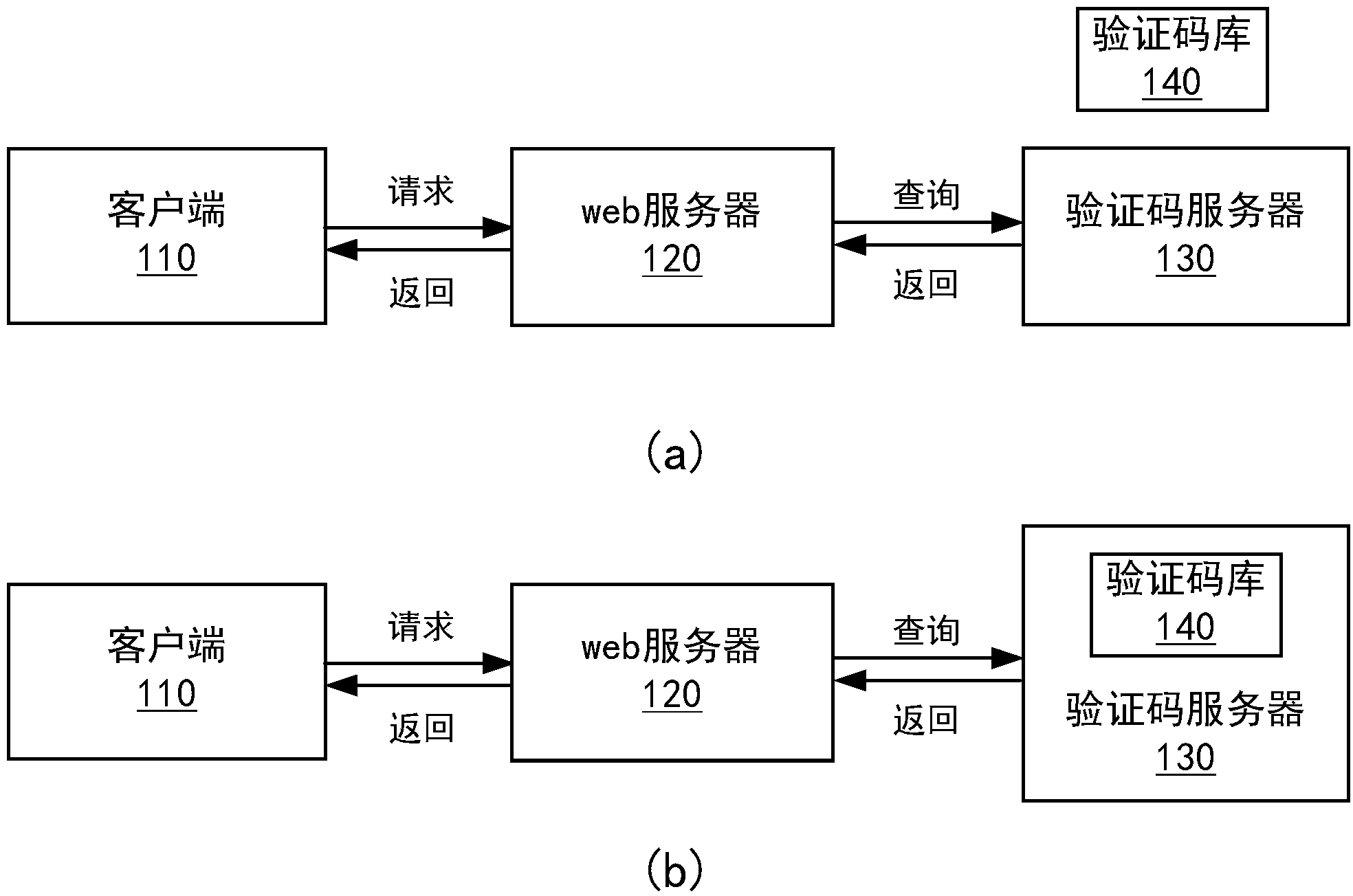
The invention provides a verification method and a verification system. The verification method includes following steps: a) receiving a web access request and accessory user information, sent by a user; b) confirming a verification code grade provided for the user according to the received user information, wherein the verification code grade is confirmed according to a user experience degree grade and the fact that whether a machine cracking difficulty grade is added; c) obtaining a verification code corresponding to the verification code grade according to the confirmed verification code grade, and sending the verification code to the user; d) receiving a verification code input by the user according to the verification code corresponding to the verification code grade and performing verification; e) returning a verification result to the user. According to the verification method and the verification system, the verification code grade is confirmed based on friendliness of the user and cracking difficulty of a machine, and therefore not only are network insecurity and inequity behaviors such as malicious password cracking, ticket brushing and forum irrigation, but also the common user can obtain good user experience.
Owner:BEIJING 58 INFORMATION TECH
Power tool
InactiveCN101623834AAvoid shockAvoid insecurityMetal sawing devicesProfiling/shaping machinesPower toolOperation safety
The invention discloses a power tool comprising a casing, a motor and an output shaft, wherein the motor is contained in the casing, and the output shaft is matched and connected with a working head and is provided with a locking device capable of rotating between a locking position prohibiting the rotation of the output shaft and a release position permitting the rotation of the output shaft. When the motor is started, an electromagnet component drives the locking device to move from the locking position to the release position. In the invention, the locking device of the output shaft of the power tool automatically moves from the locking position to the release position when the motor is started, and the power tool is safe and convenient to operate.
Owner:POSITEC POWER TOOLS (SUZHOU) CO LTD
Vehicle stability control system based on active intervention steering system
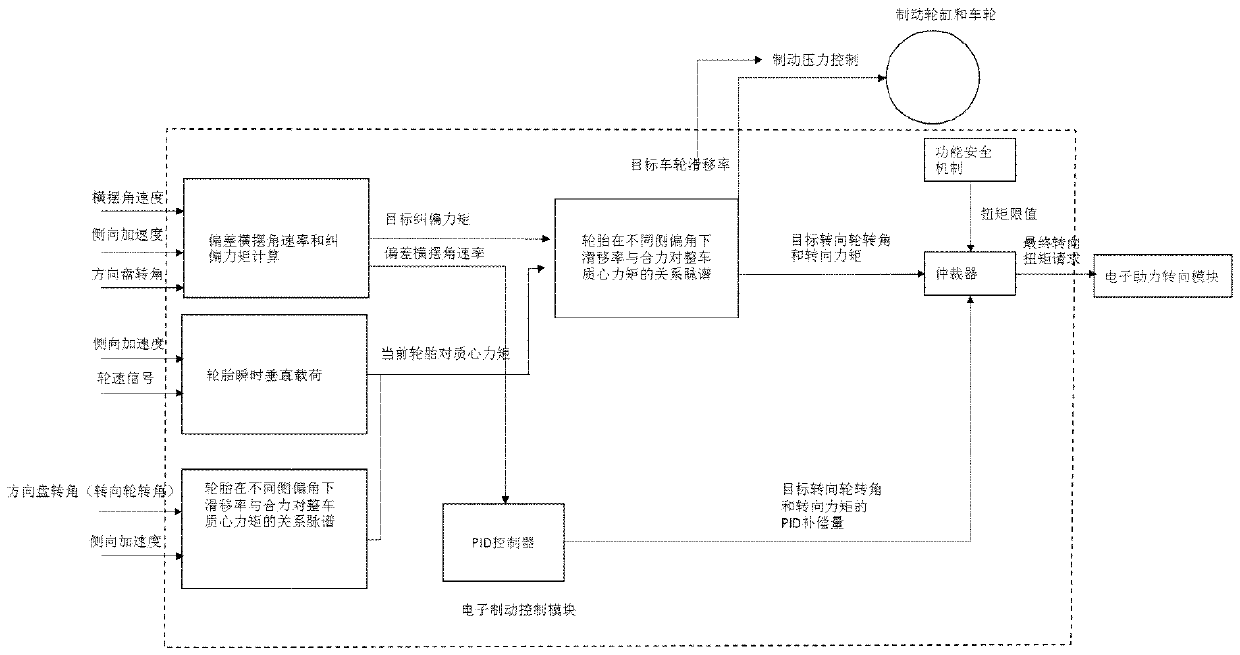
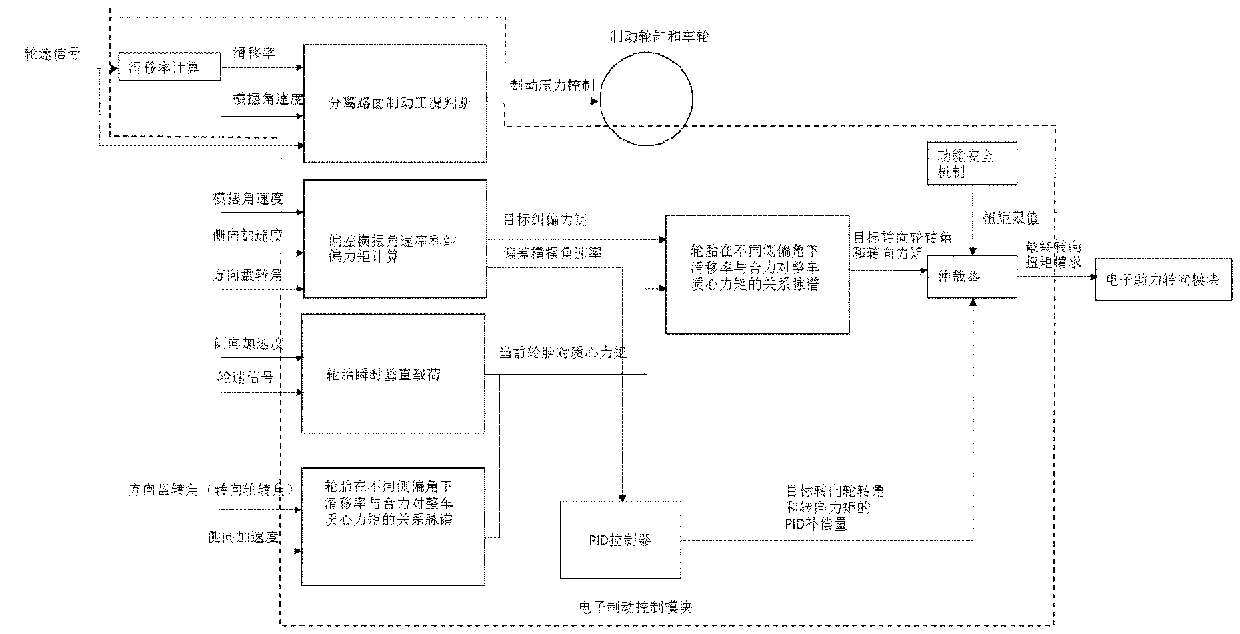
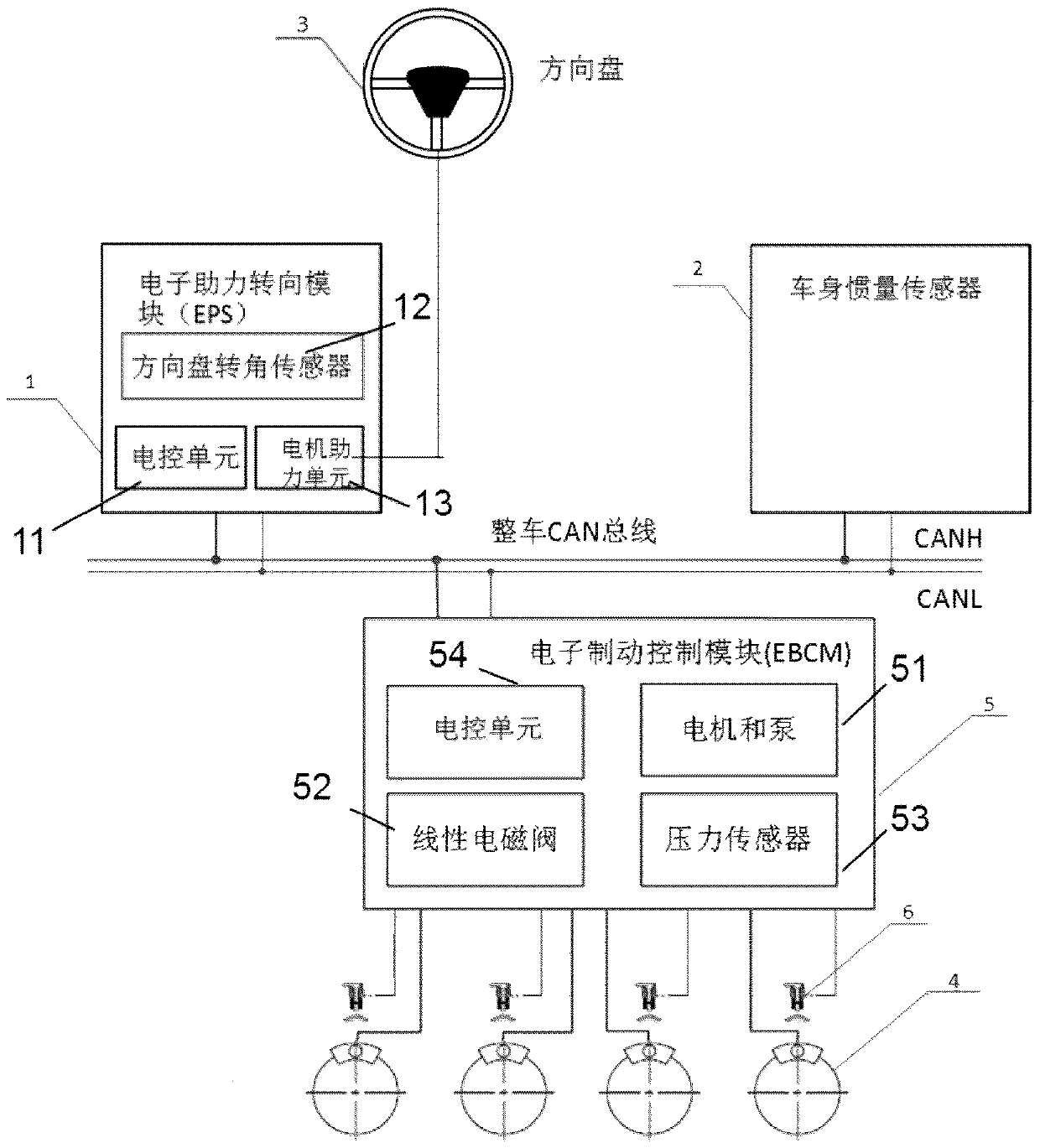
ActiveCN109693663AAdd corner controlImproved stability controlDriver input parametersWheel speed sensorControl system
The invention relates to a vehicle stability control system based on an active intervention steering system, which is characterized by at least comprising: an electronic assistance steering module used for receiving a torque request instruction from an electronic brake control module and outputting torque for intervening with the positions of a turning wheel and a steering wheel by torque; the electronic brake control module configured to determine the running state of a vehicle according to the hydraulic pressure applied by the driver through the brake pedal, the wheel working state input through wheel speed sensors, and the vehicle actual acceleration and yaw rate signals input by vehicle inertia sensors and calculate the stability deviation of the current vehicle control state from theideal control state and the turning wheel rotating angle required to compensate for the stability deviation according to the brake back pressure applied by the driver, and obtain the assist torque value to be provided for achieving the target turning wheel rotating angle and send the same to the electronic assistance steering module.
Owner:SAIC GENERAL MOTORS +1
Method of controlling coordinate network and its node
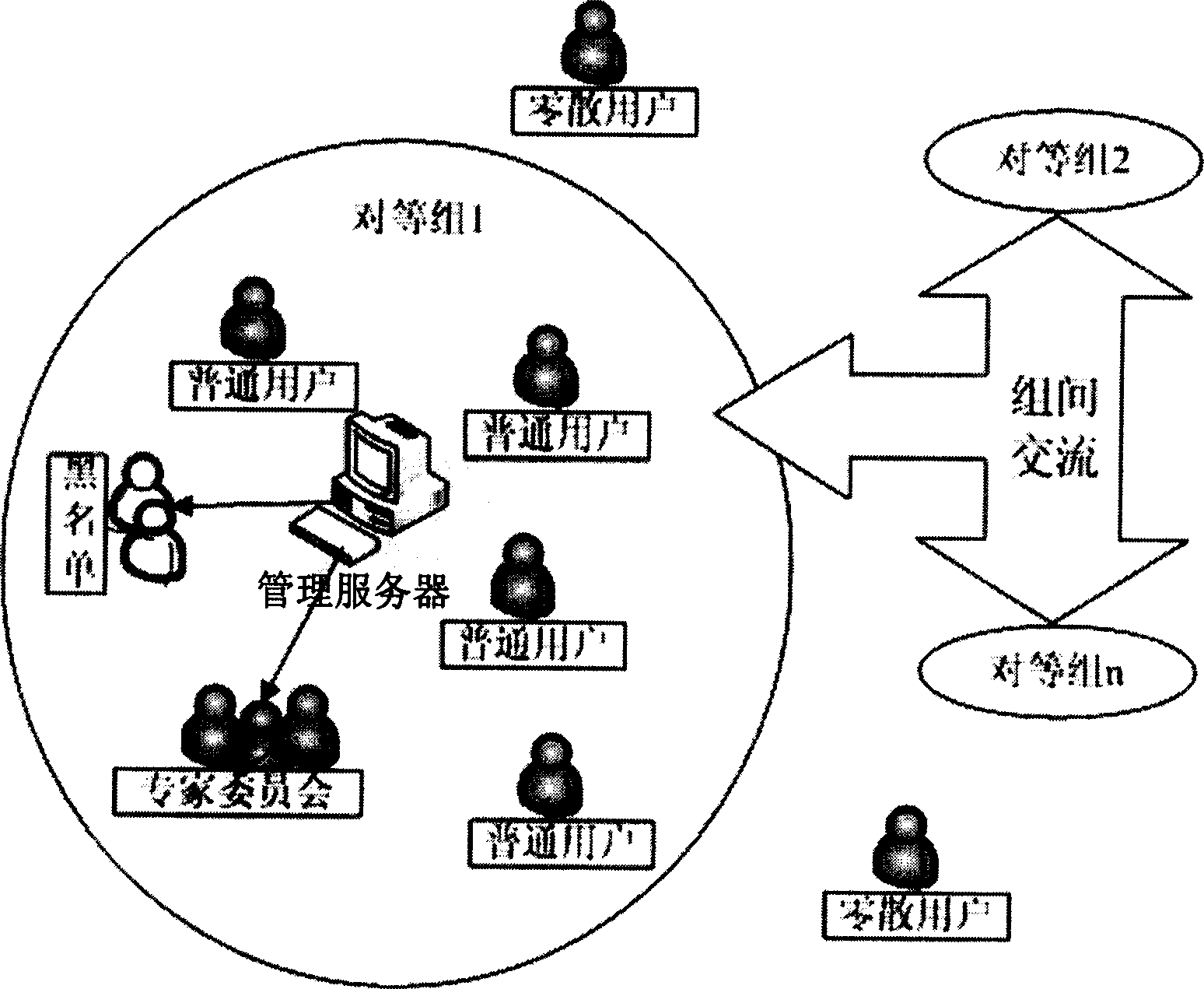
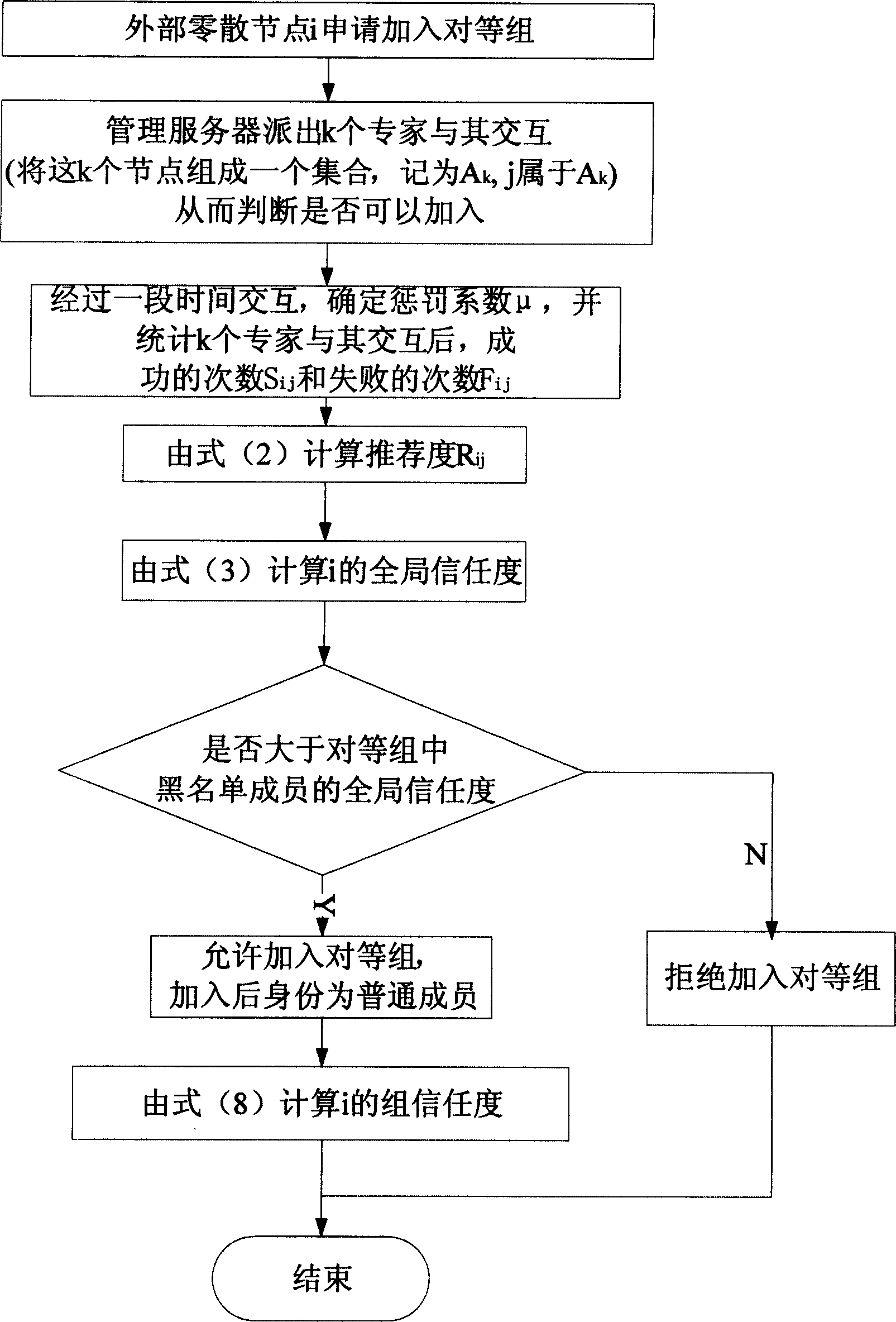
ActiveCN1863090AImprove securityEasy to manageData switching networksSecuring communicationDependabilityDistributed computing
The invention relates to an equity network and the node control method that includes the following steps: sets different equity group in network that contains several nodes; selecting the node in the equity network to take intercommunication and take manage whether adding the external nodes or the node in the equity group to ensure the reliability in equity group. Each equity group at least set one manage server to record the belief degree of the node in group. The invention improves the safety of the equity network.
Owner:HUAWEI TECH CO LTD
Counter weight method for hydro-generator rotor dynamic balancing test
InactiveCN105675213AReduce downtimeAvoid insecurityStatic/dynamic balance measurementPower flowExcitation current
The invention discloses a counterweight method for a hydroelectric generator rotor dynamic balance test, which includes: separately testing the vibration parameters of the hydroelectric generator set under different rotational speeds and different excitation current conditions, analyzing the vibration characteristics, and estimating the initial weight and position of the test weight ;According to the estimated weight and position of the trial weight, a number of magnetic bases are adsorbed to a certain position of the generator rotor; start the machine again for variable speed and variable excitation tests, and analyze whether the trial weight and position are appropriate; process and manufacture according to the calculation results Permanent counterweight, remove the magnetic base, weld and fix the counterweight at the final counterweight position; turn on the machine again to test the vibration data under rated speed and rated voltage, and analyze and evaluate the counterweight effect; the biggest feature of this method is The counterweight of the magnetic base does not need to be welded, and it is convenient to install, move and change the weight, and the magnetic base can be reused, so it has a good application prospect.
Owner:STATE GRID GASU ELECTRIC POWER RES INST +2
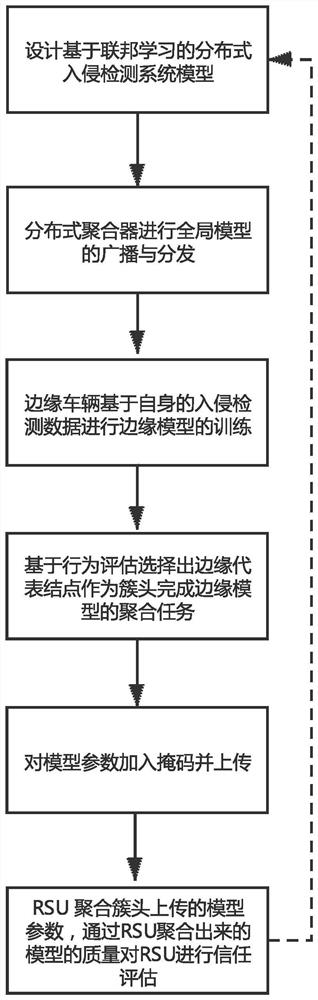
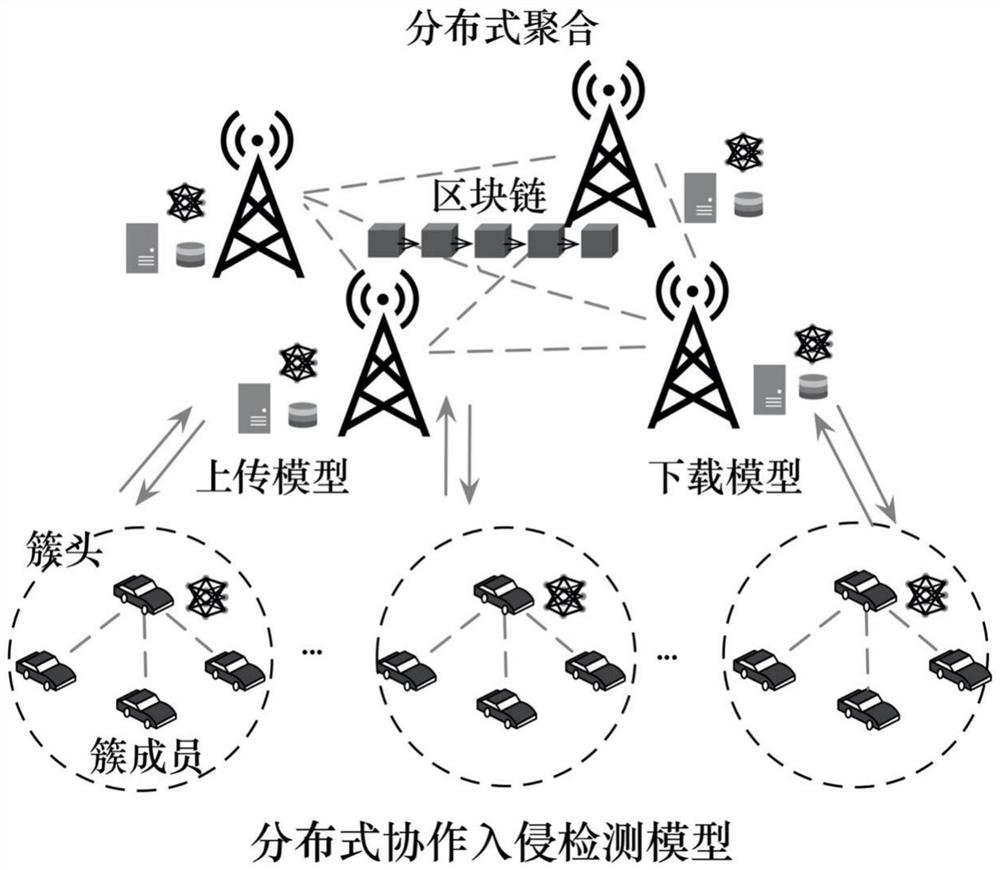
Distributed intrusion detection method based on federated learning and trust evaluation and system thereof
ActiveCN112770291AImprove efficiencyImprove abilitiesInternal combustion piston enginesParticular environment based servicesDistributed intrusion detectionIn vehicle
The invention provides a distributed vehicle-mounted intrusion detection system based on federated learning and trust evaluation and a method thereof. The method comprises the following steps: designing a distributed intrusion detection system model based on federated learning; building and pre-training of an intrusion detection model are realized based on federated learning, and broadcasting and distributing a global model by a distributed aggregator; performing edge model training based on intrusion detection data of the edge vehicle by the edge vehicle; selecting an edge representative node as a cluster head based on behavior evaluation to complete an aggregation task of an edge model; adding a mask to the model parameters and then uploading the model parameters to the RSU; performing trust evaluation on the RSU through the quality of a model aggregated by the RSU through the RSU aggregates model parameters uploaded by a cluster head, so that distributed aggregation nodes are stimulated to compete and aggregate a model with higher accuracy, and finally, storing the training model based on a block chain principle to complete model sharing. The invention further creates a defense detection system suitable for automatic driving to resist network intrusion by adopting a safety evaluation mode of information safety.
Owner:EAST CHINA NORMAL UNIV +2
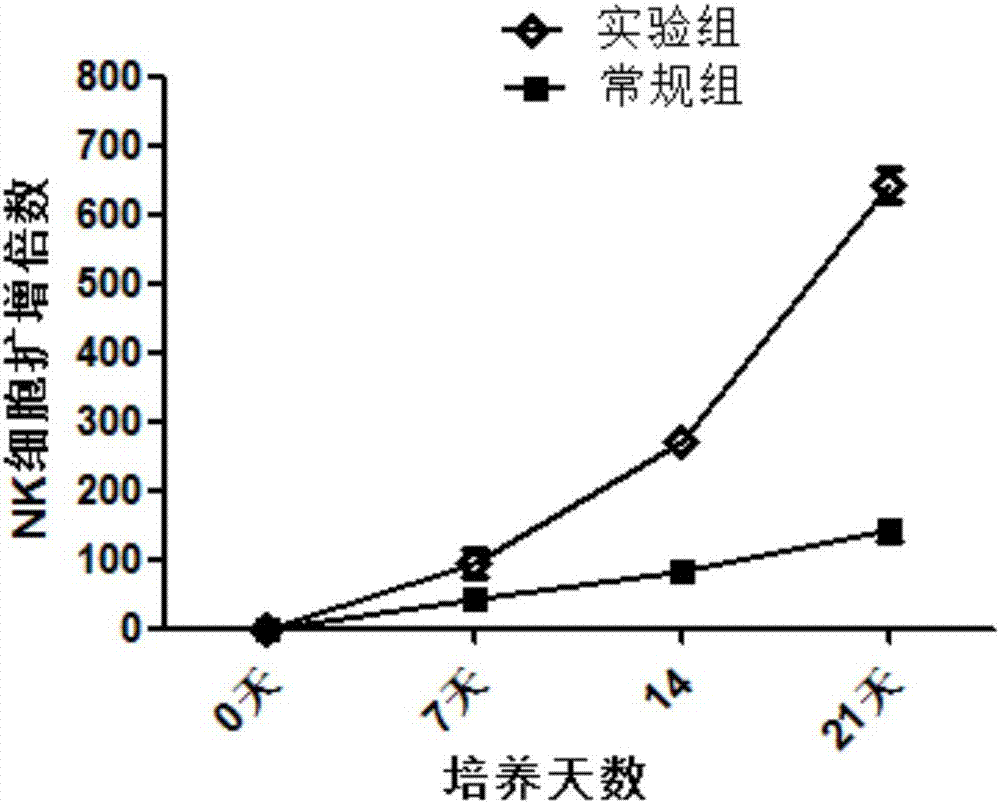
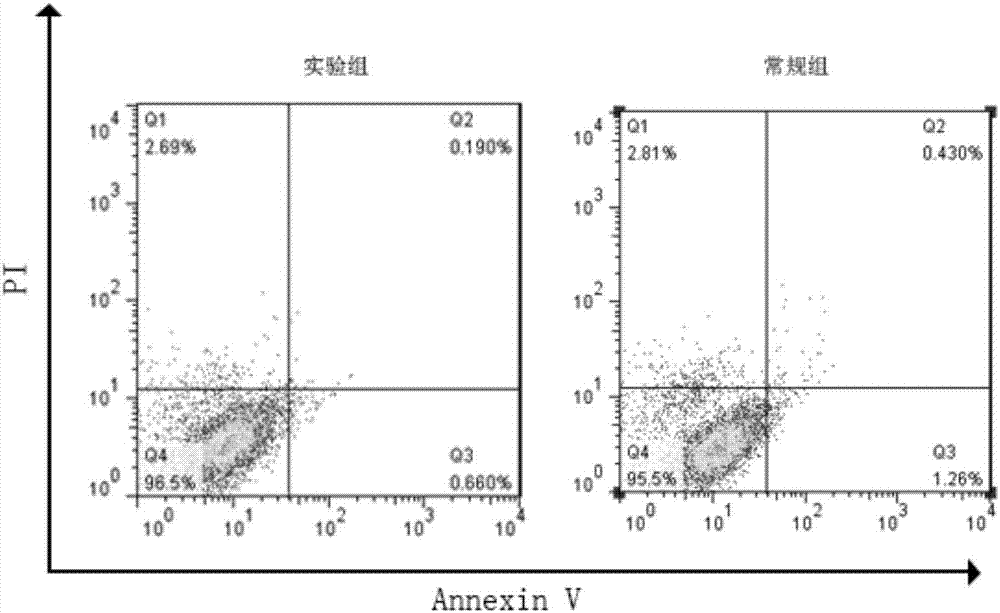
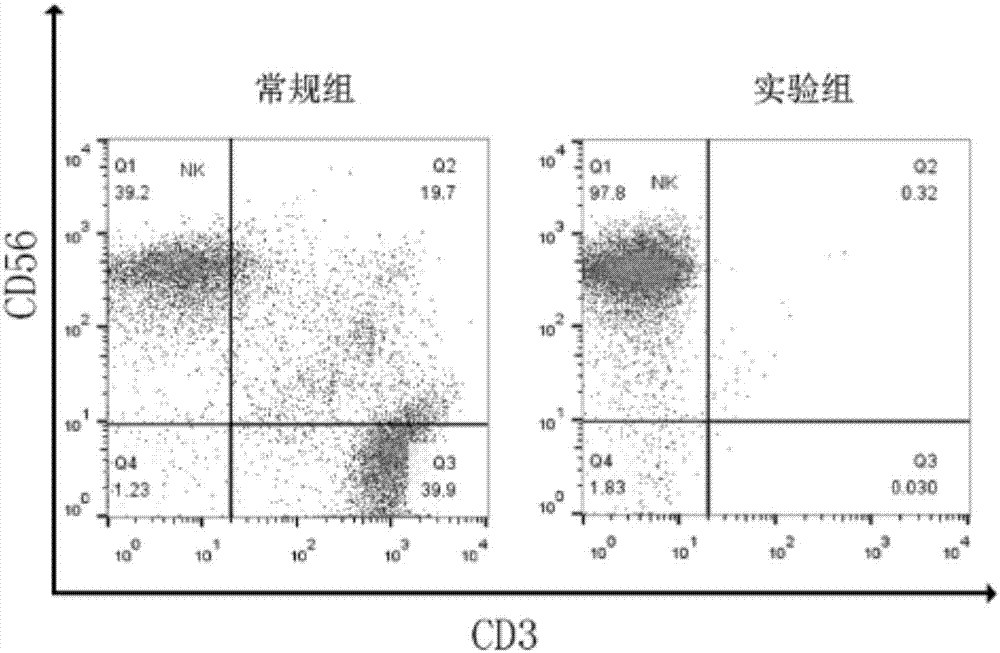
Method for efficiently amplifying natural killer cells from peripheral blood in high purity manner
ActiveCN107326008AAvoid insecurityHigh purityBlood/immune system cellsCD16Natural Killer Cell Inhibitory Receptors
The invention relates to a method for efficiently amplifying natural killer cells from peripheral blood in a high purity manner. The method comprises the following steps: collecting 100ml-200ml of peripheral blood, separating mononuclear cell, putting the mononuclear cell into a culture bottle coated with CD16 monoclonal antibody and CD226 monoclonal antibody for culturing, and activating the cell by virtue of IFN-gamma; after the activation is carried out for 24 hours, adding IL-2, IL-15, IL-21, OK432, CD2 monoclonal antibody and inactivated autoserum into a culture medium; transferring the cell into a culture bottle which is not coated with CD16 monoclonal antibody and CD226 monoclonal antibody for culturing, and supplementing liquid to the cell once in each 2-3 days; and finally transferring the cell into a culture bag for culturing, and collecting NK cell in the 21th day. According to the method, no any heterologous serum component or trophoblast cell is used, so that the safety and reliability of the prepared NK cell are guaranteed; and the method has good clinical application values.
Owner:SHANGHAI LIFE SCI & TECH CO LTD
System and method for integrated surgical table
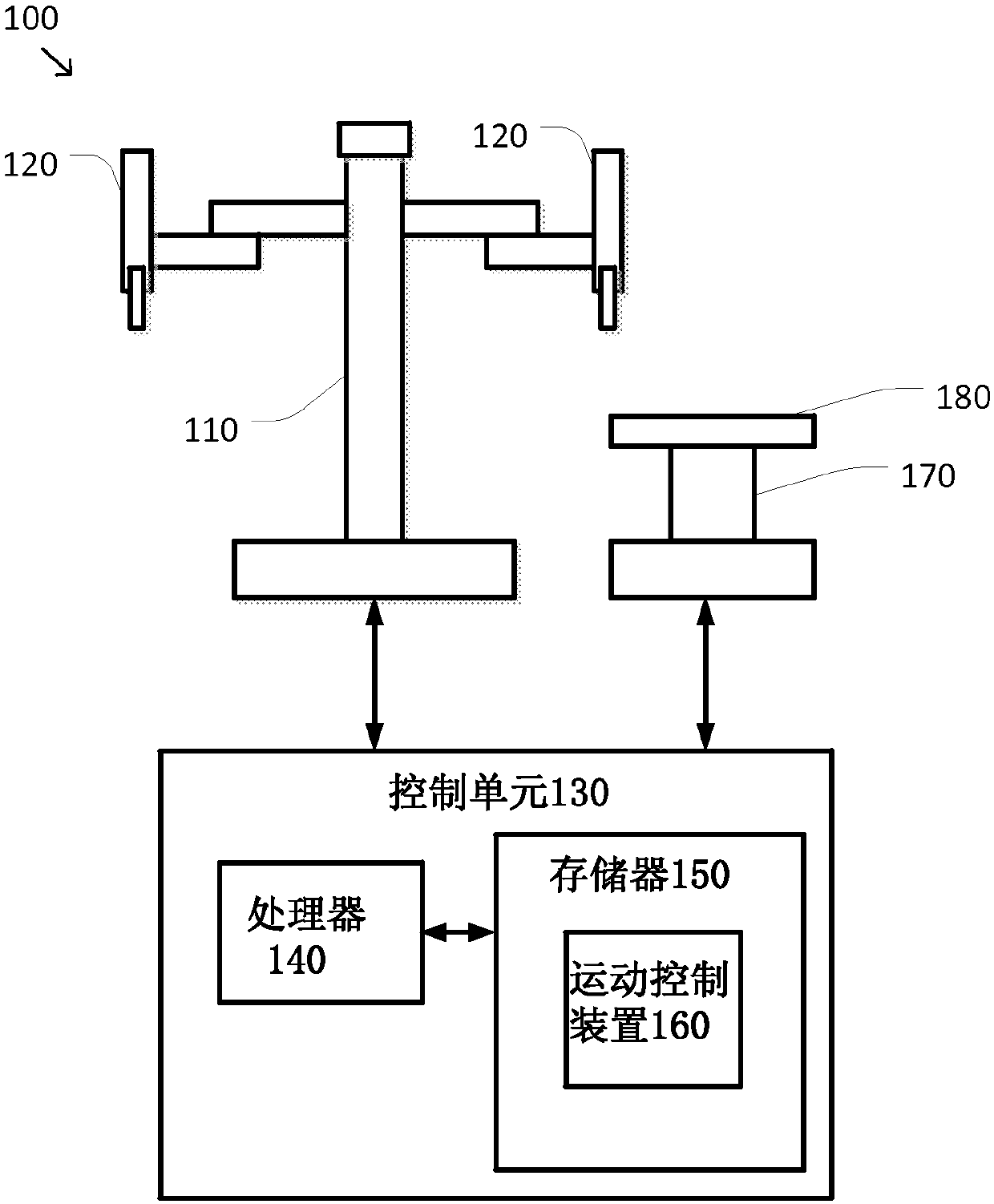
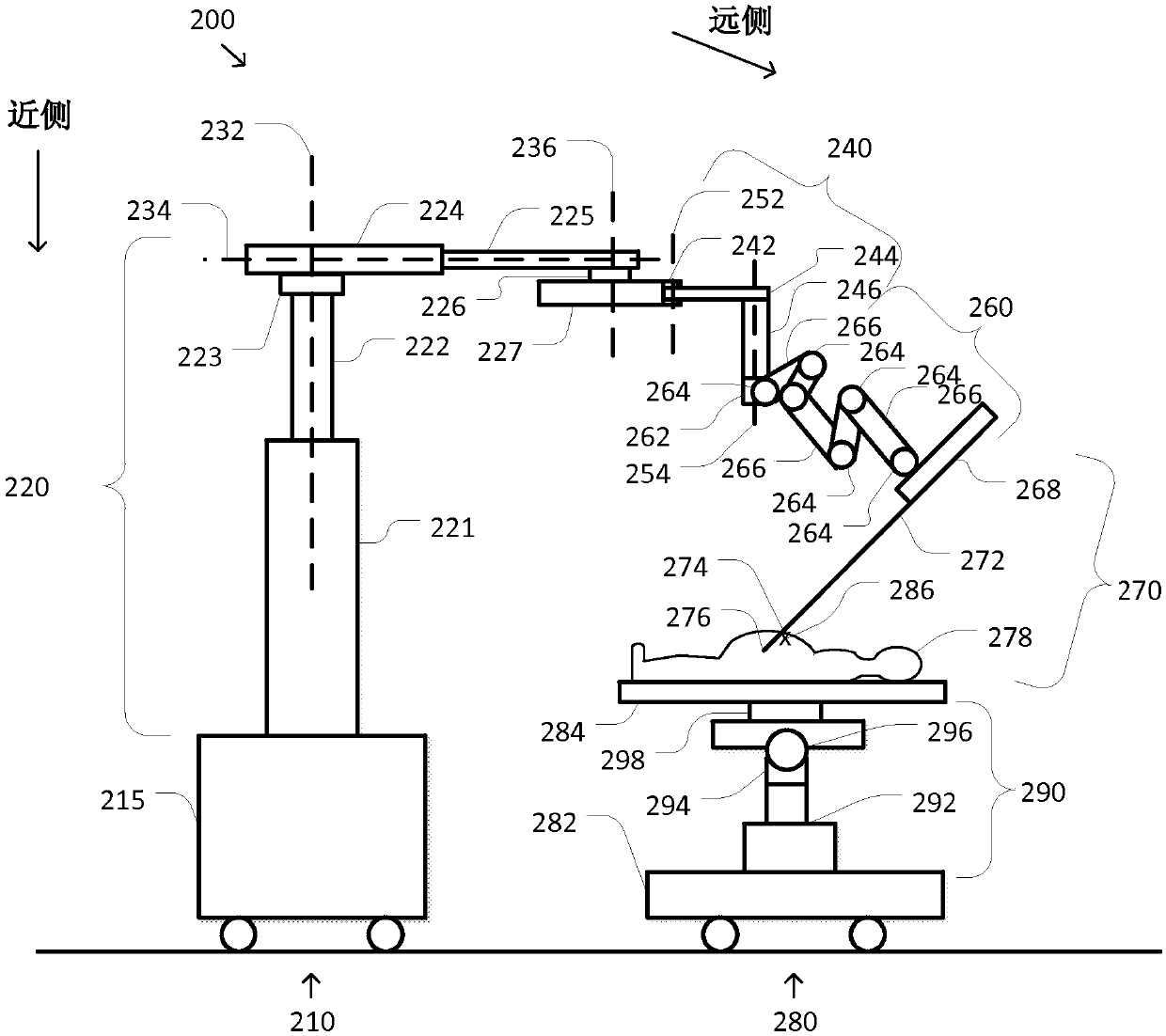
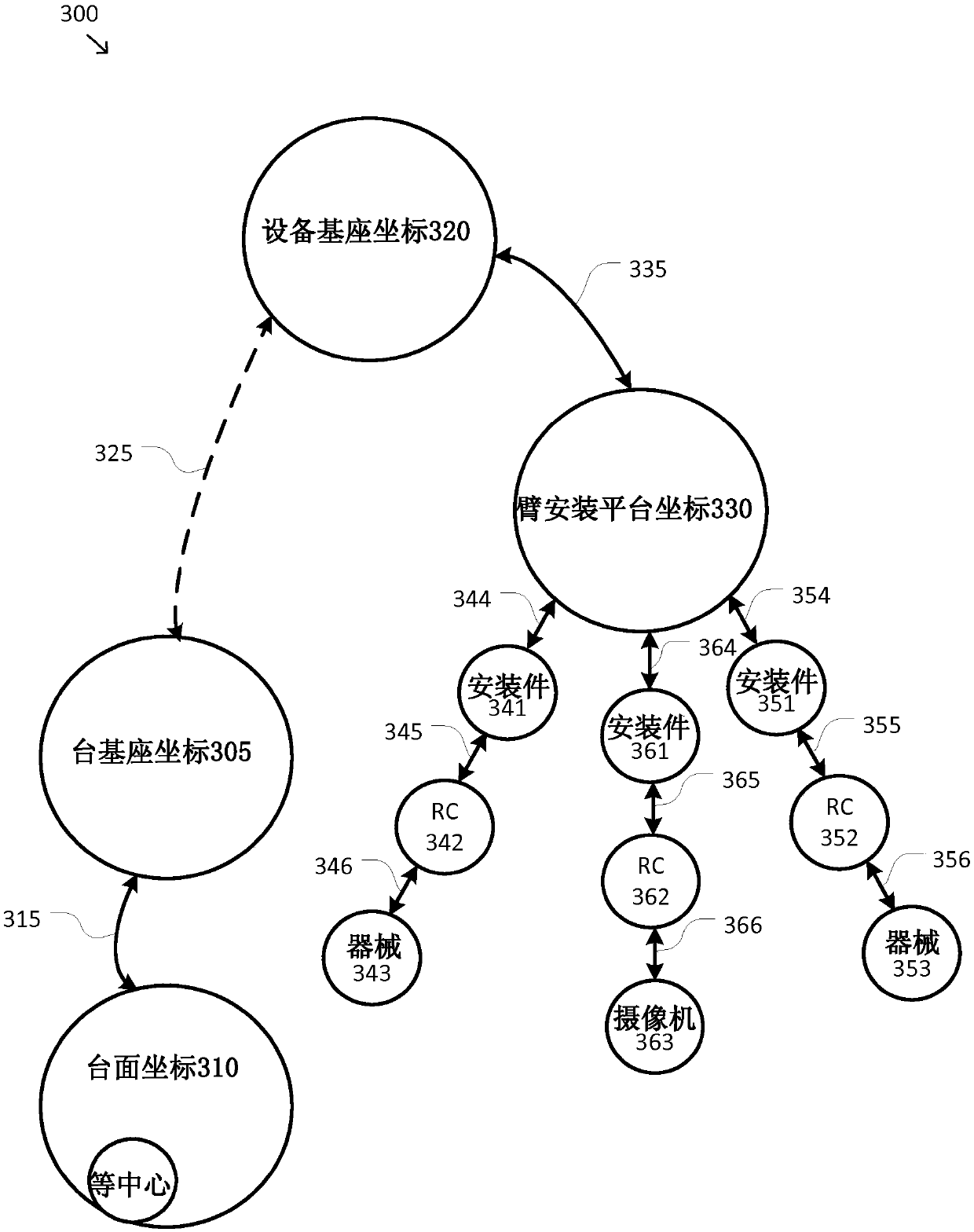
ActiveCN107072725AControl not allowedSports are not allowedOperating tablesSurgical systems user interfaceEngineeringSacroiliac joint
A system and method for an integrated surgical table includes a medical device including an articulated arm having one or more first and second joints and a control unit. The articulated arm has at least a cannula, an endoscope, or an instrument mounted distal to the first and second joints, which is inserted into a patient at a body opening. The control unit unlocks the first joints, receives a surgical table movement request, determines whether the surgical table movement request should be granted, allows the surgical table to perform the requested movement based on the determining, uses the first joints to allow the articulated arm to track movement of the body opening based on forces applied by a body wall at the body opening, and compensates for changes in a pose of the cannula, endoscope, or instrument due to the tracked movement by performing compensating motions in the second joints.
Owner:INTUITIVE SURGICAL OPERATIONS INC
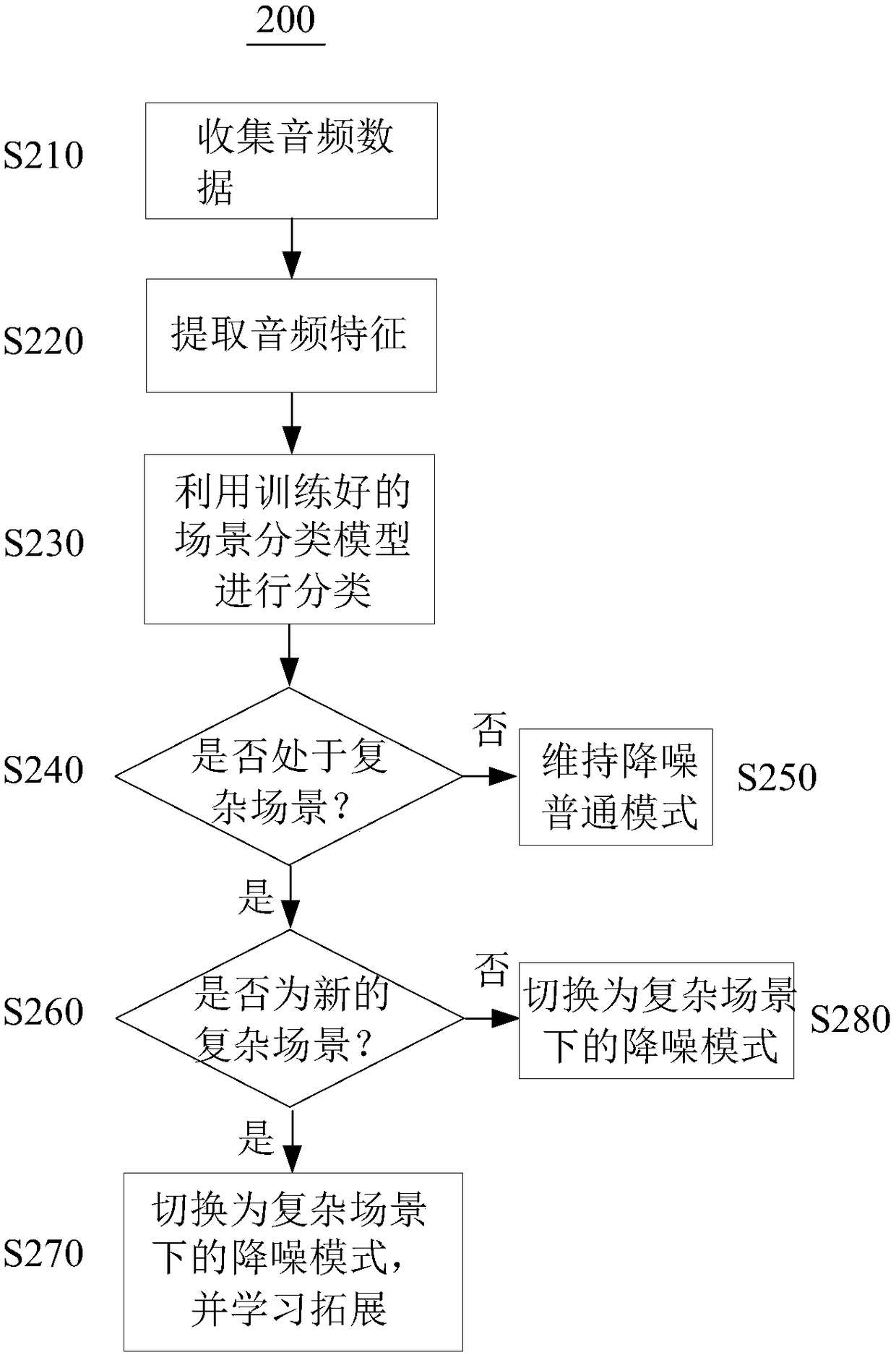
Active noise reduction method and device, headset and computer storage medium
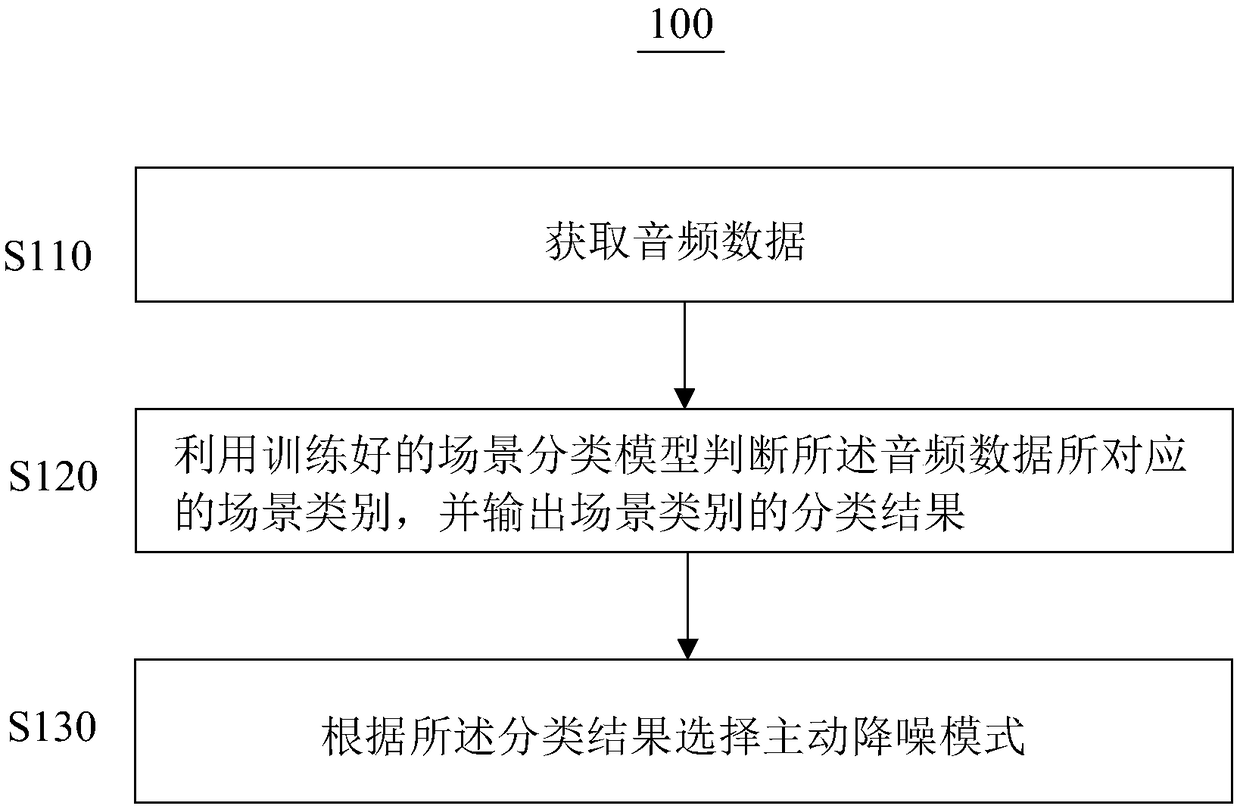
PendingCN109346055AAvoid insecurityAvoid cumbersomenessMicrophonesLoudspeakersNoise reductionClassification result
The invention provides an active noise reduction method and device, a headset and a computer storage medium. The method includes the following steps: acquiring audio data; judging the scene category corresponding to the audio data by using a trained scene classification model, and outputting the classification result of the scene category; and selecting an active noise reduction mode according tothe classification result. The noise reduction mode is selected according to the scene category in the invention, so that insecurity caused by noise reduction is avoided, and the tediousness of manualswitching between noise reduction modes is avoided.
Owner:ANKER INNOVATIONS TECH CO LTD
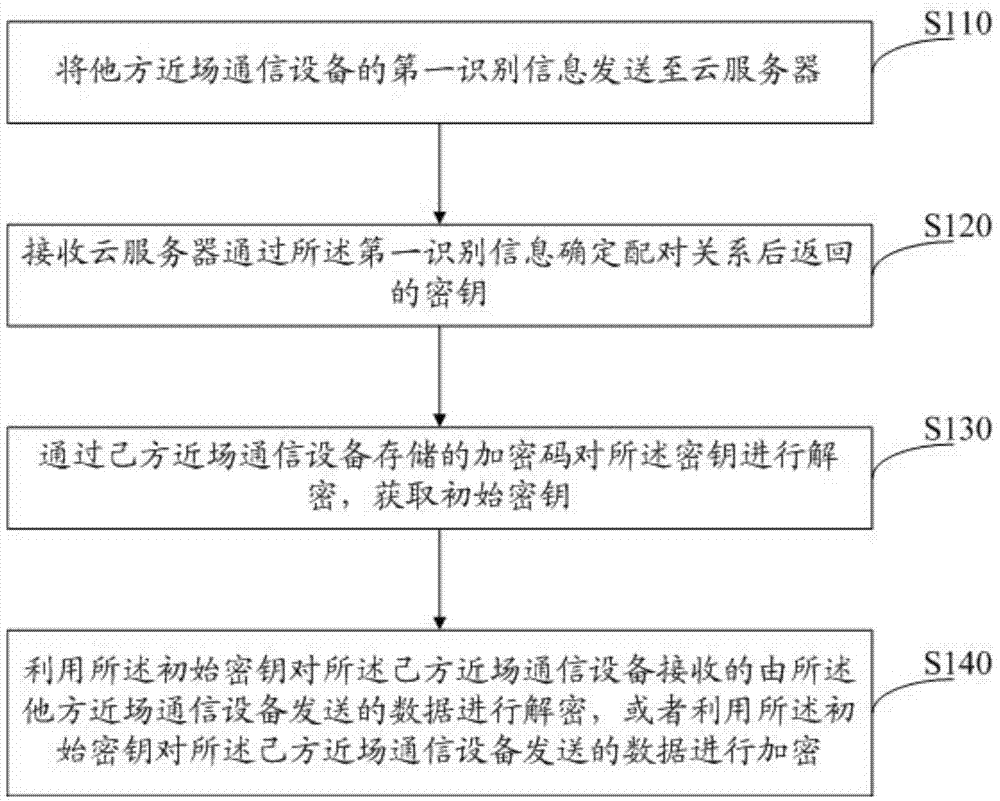
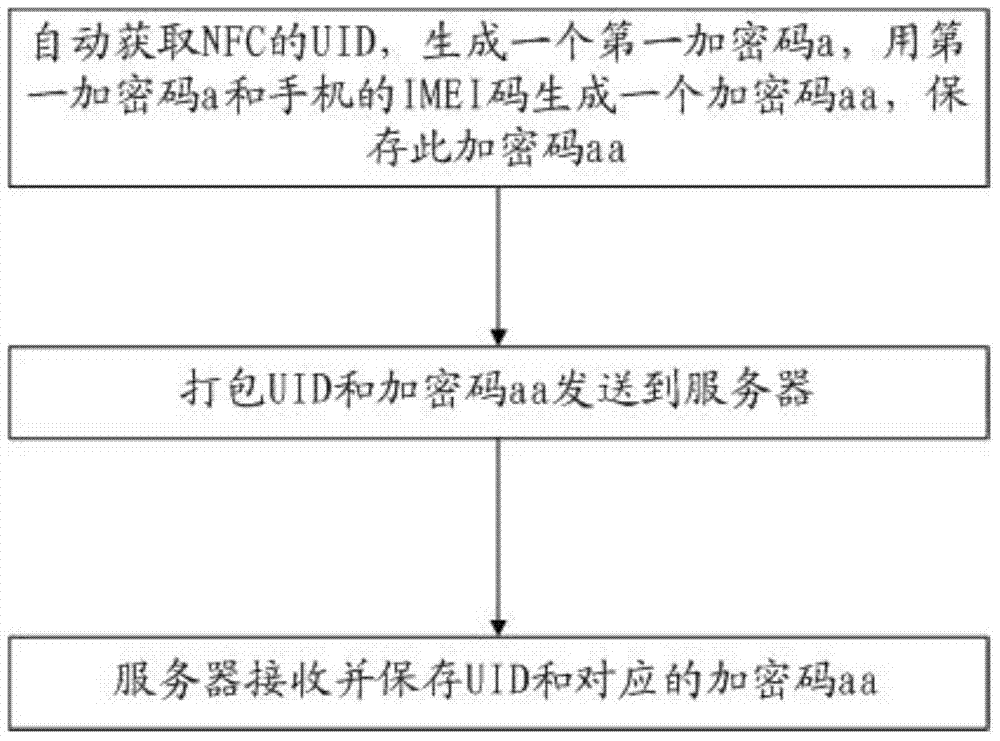
NFC encryption method and system
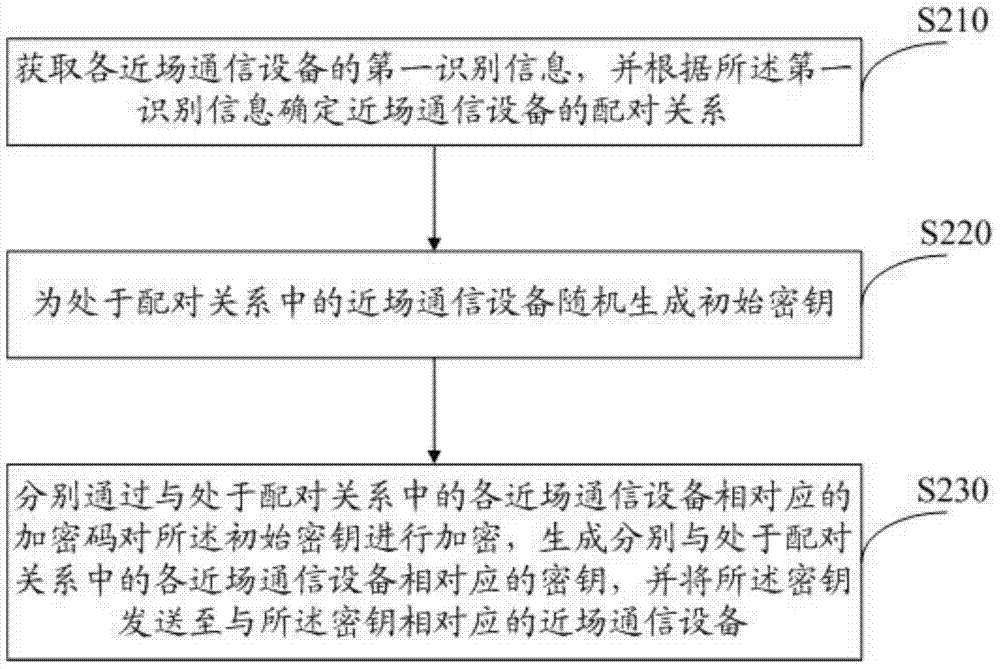
ActiveCN104270244AAvoid insecurityIncreased complexityKey distribution for secure communicationNear-field transmissionComputer hardwareSecurity question
The invention provides an NFC encryption method. The method comprises the following steps that first identifying information of an NFC device of the other party is sent to a server; a secret key returned by the server after the matching relation is determined according to the first identifying information is received; the secret key is decrypted through encrypted codes stored in an NFC device of this party to obtain an initial secret key; the initial secret key is used for decrypting data which are sent by the NFC device of the other party and received by the NFC device of this party, or the initial secret key is used for encrypting data sent by the NFC device of this party. According to the NFC encryption method, the whole NFC process is subjected to two-way encryption through the server in combination with the identifying information of the NFC devices, and therefore the problem of insecurity of NFC is effectively solved; the complexity of encryption is improved in a secondary encryption mode, so that NFC is more reliable.
Owner:GUANGDONG ANJUBAO DIGITAL TECH
Sub-depot flow-guiding type solar water heater
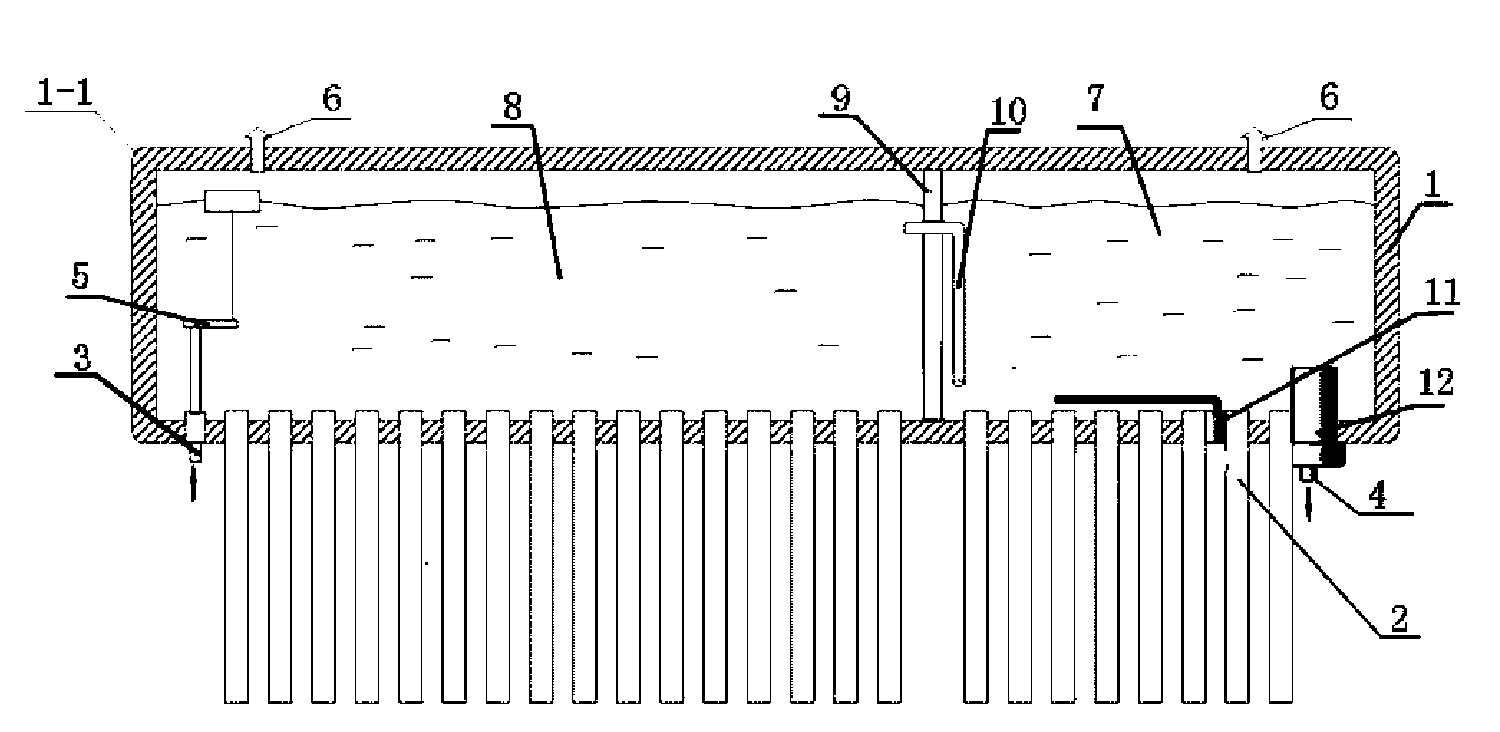
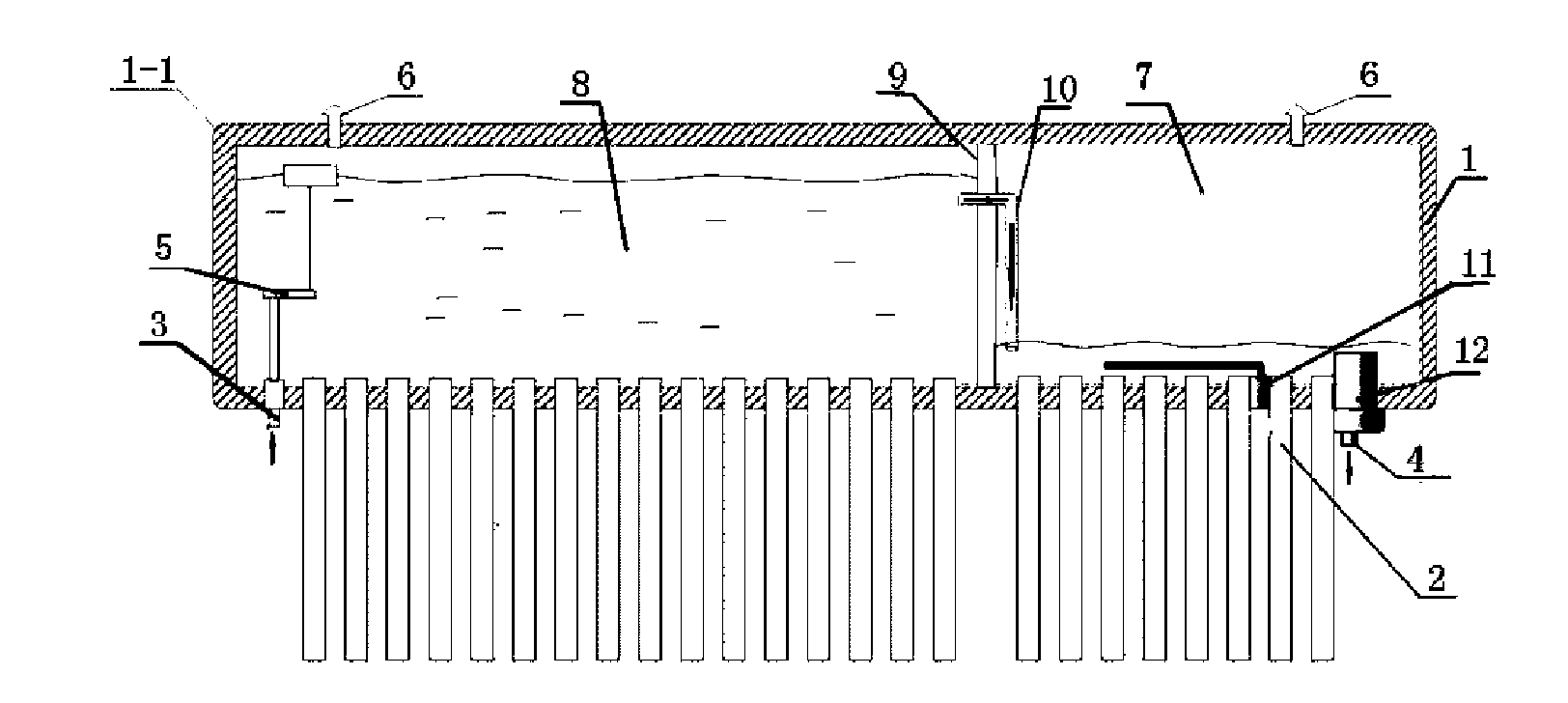
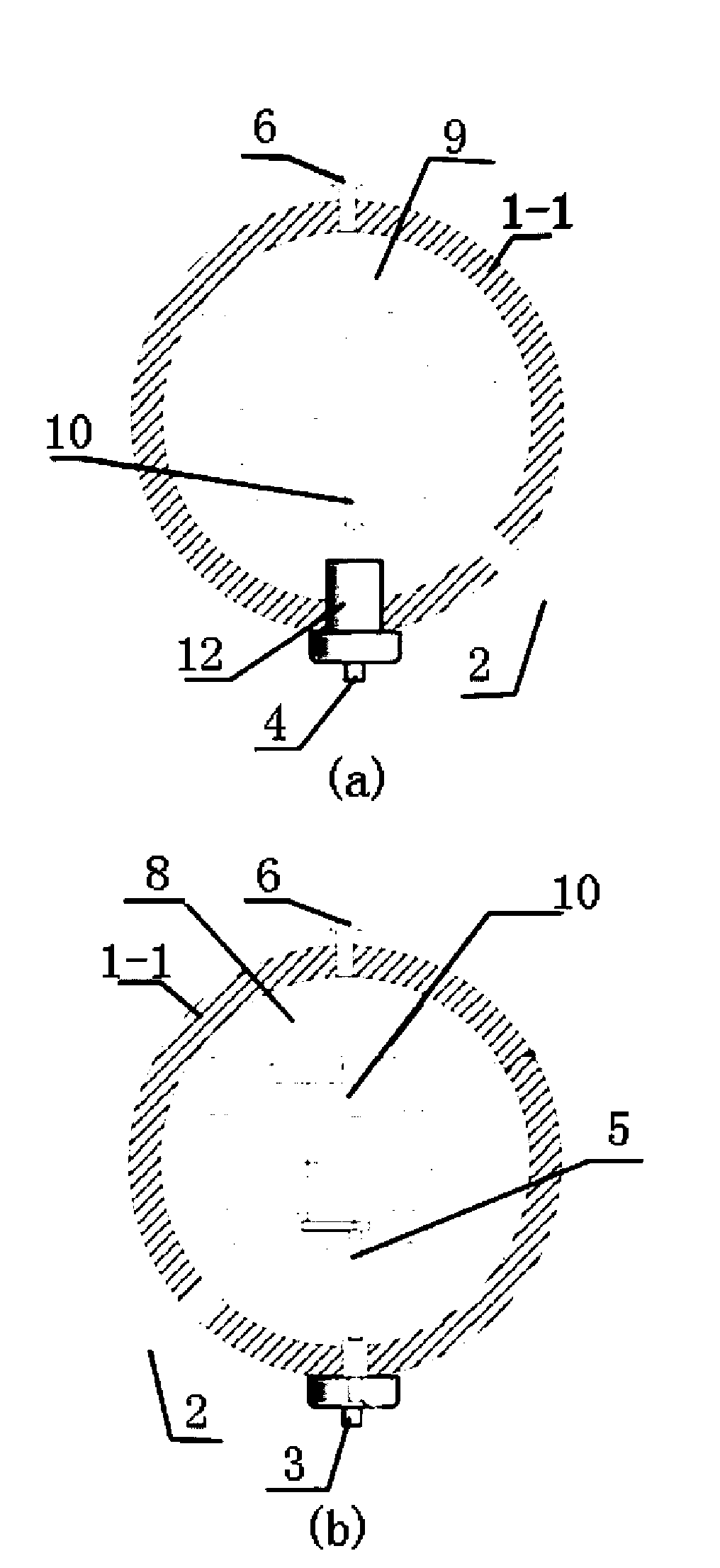
InactiveCN101666553AExtended service lifeSolve the explosion puzzleSolar heating energySolar heat devicesElectricityExhaust valve
The invention relates to a sub-depot flow-guiding type solar water heater water tank with simple structure and good insulating and energy-saving effects, comprising a water tank body and a vacuum pipe, wherein the water tank body is connected with the vacuum pipe; the water tank body is provided with a water inlet and a water outlet; the water inlet is provided with an automatic water supplying device; an exhaust valve is arranged above or on the side wall of the water tank body; the water tank body is internally divided into a heating depot and a water storing depot by a heat insulating device; the water inlet is positioned at the water storing depot and the water outlet is positioned at the heating depot; the heat insulating device is provided with a flow-guiding pipe communicating the heating depot and the water storing depot; the exhaust valve is respectively arranged above or on the side wall of the heating depot and the water storing depot; and the water inlet is provided with the automatic water supplying device. The solar water heater water tank is designed in a sub-depot manner, stores heat and heats in the sub-depot manner, and separates transmission of the water temperature of the two depots by the heat insulating device; an electric heating device heats the heating depot, and play the roles of saving energy and protecting environment, wherein the heated amount is same as the used amount;, thus solving the difficulty that the electricity amount is large when electric heating is started in winter and cloudy and rainy days.
Owner:福建圣元电子科技有限公司
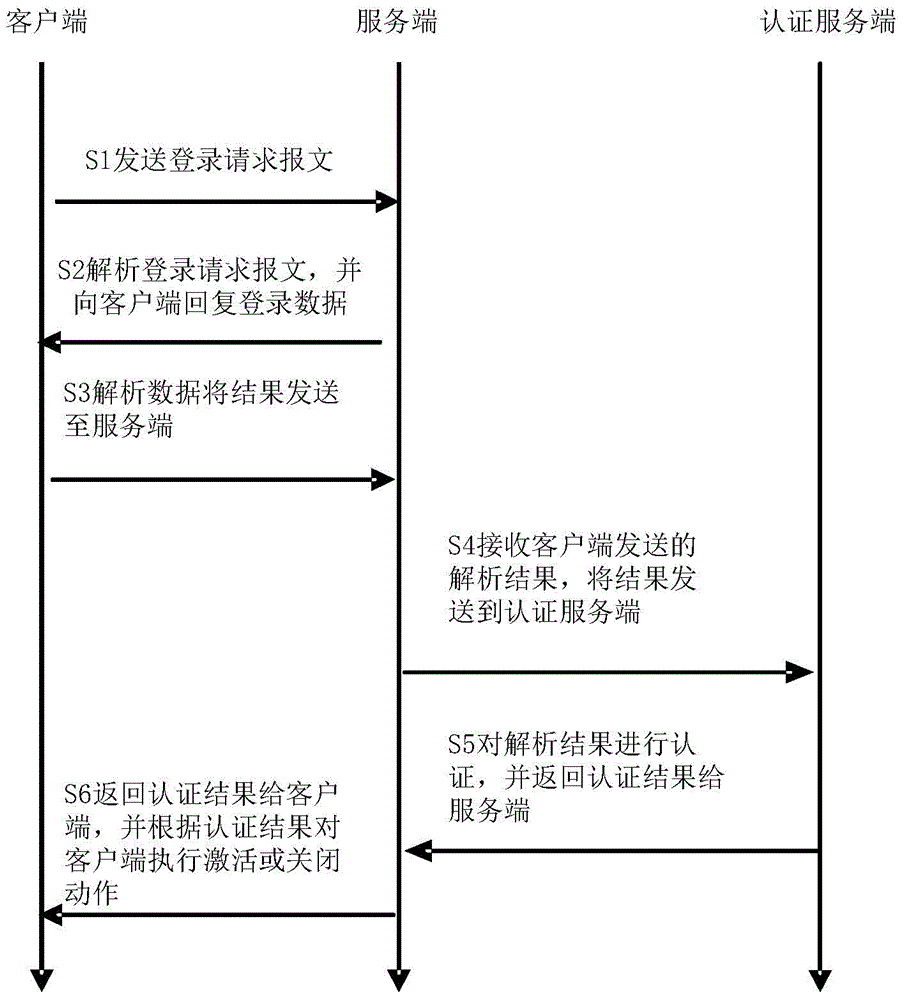
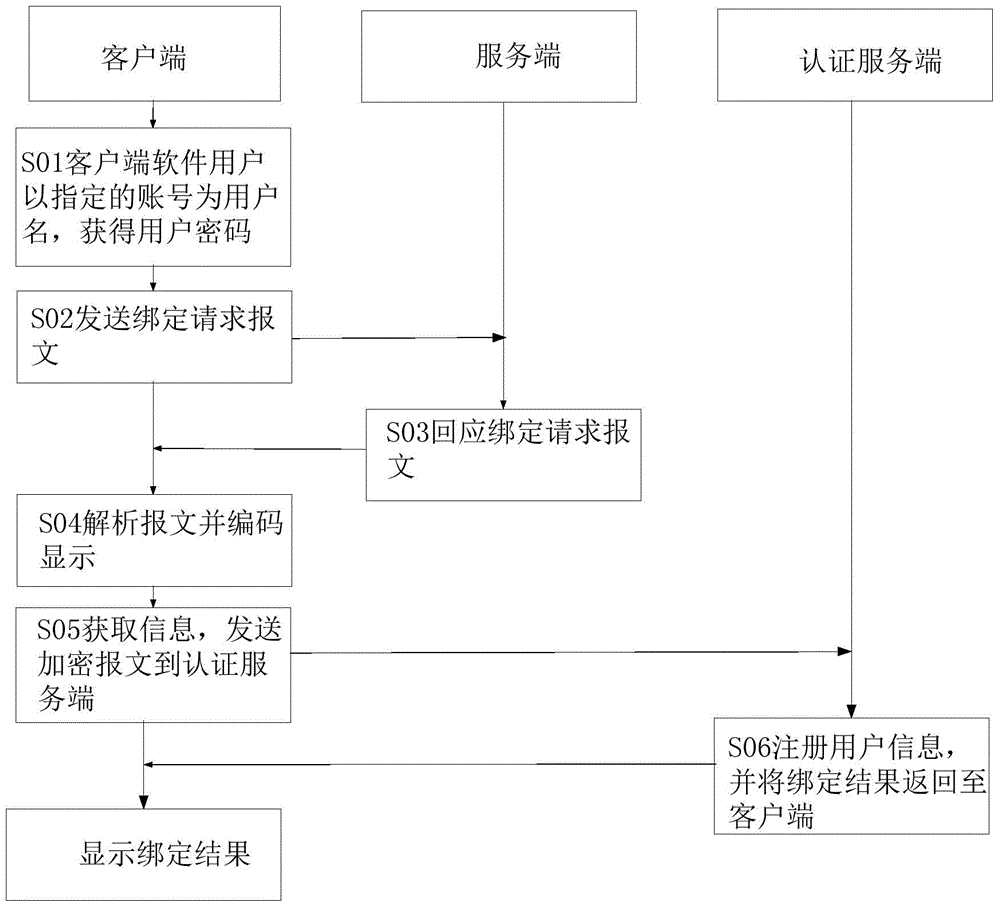
Identity authentication method for client software
The invention discloses an identity authentication method for client software. The method comprises the following steps that: a client sends a login request message to a server side; the server side resolves the login request message sent by the client, and returns login data to the client, wherein the login data is displayed on the client in a code form; the client resolves coded data transmitted by the server side, and transmits a resolution result to the server side; the server side receives the resolution result transmitted by the client and transmits the resolution result to an authentication server side, and the authentication server side verifies the resolution result; the authentication server side authenticates the resolution result, and returns an authentication result to the server side; and the server side receives the authentication result, returns the authentication result to the client, and executes an activation or shutdown action on the client according to the authentication result. The client software is bound with accounts and password information, and an encryption algorithm is adopted, so that the problem of account insecurity caused by means of peeking, cracking, analysis and the like is solved effectively.
Owner:CHENGDU CYBERKEY TECH
Current guiding device for live operation of distribution network with long-distance real-time monitor
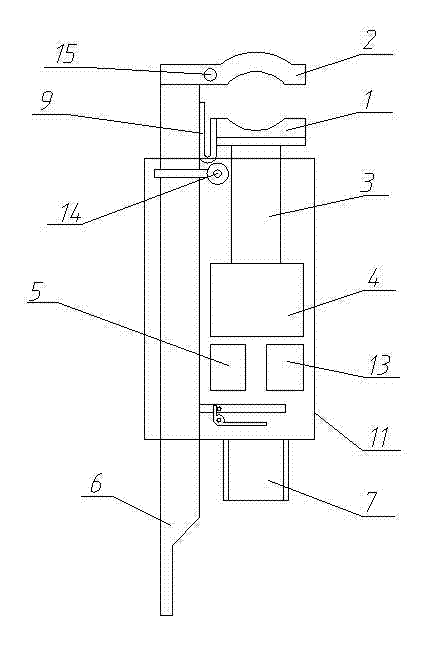
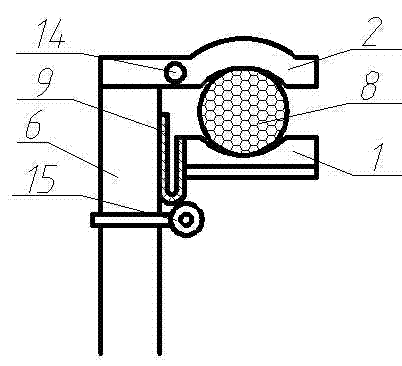
ActiveCN102832568AGuarantee personal safetyMaintain normalClamped/spring connectionsApparatus for overhead lines/cablesWorking pressureCurrent sensor
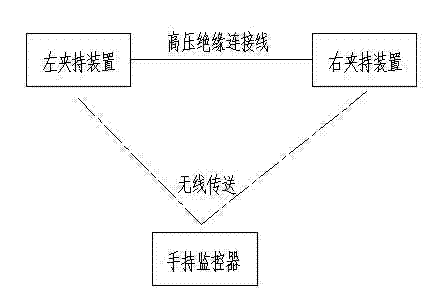
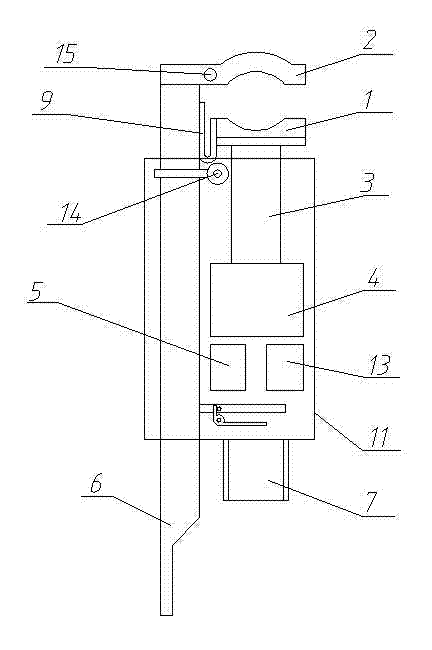
The invention relates to a mounting device for an overhead line or cable, in particular to a current guiding device for live operation of a distribution network with a long-distance real-time monitor, which is structurally characterized by comprising a pair of clamping devices, a high-voltage insulated connecting wire and a handheld monitor, wherein each clamping device comprises a movable jaw, a fixed jaw, a temperature sensor, a current sensor, a master control board and a current guiding connection device, each current guiding device is provided with the effective and reliable temperature sensor and current sensor for real-time collection of monitoring data, and the data are further wirelessly transmitted to the handheld monitor on the ground in a long-distance and real-time way within a controllable range for check of monitoring personnel, so that the monitoring personnel can promptly know the field construction situation, judgment can be made in a real-time way, correct prompts can be uttered in advance, the personal safety of operators can be guaranteed, the labor intensity can be lowered, the working pressure can be reduced, and the field construction safety of the live operation can be facilitated.
Owner:STATE GRID CORP OF CHINA +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com