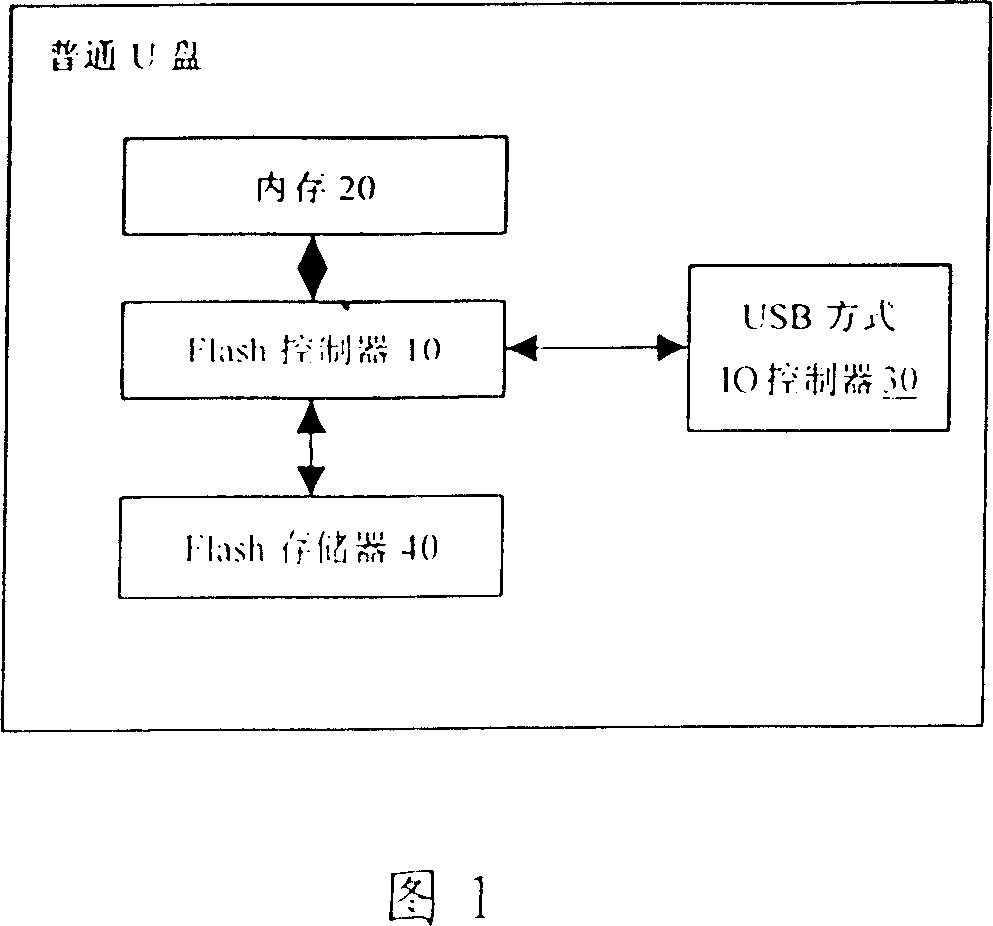
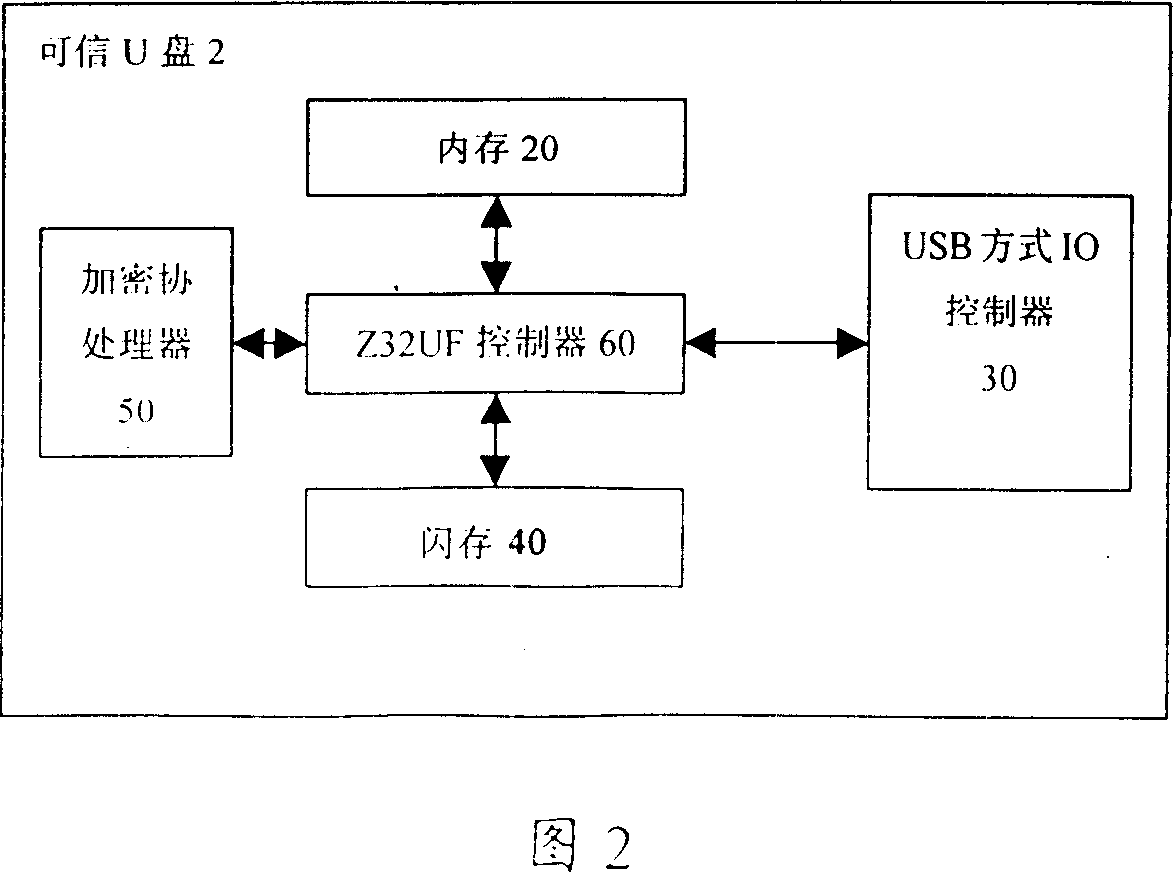
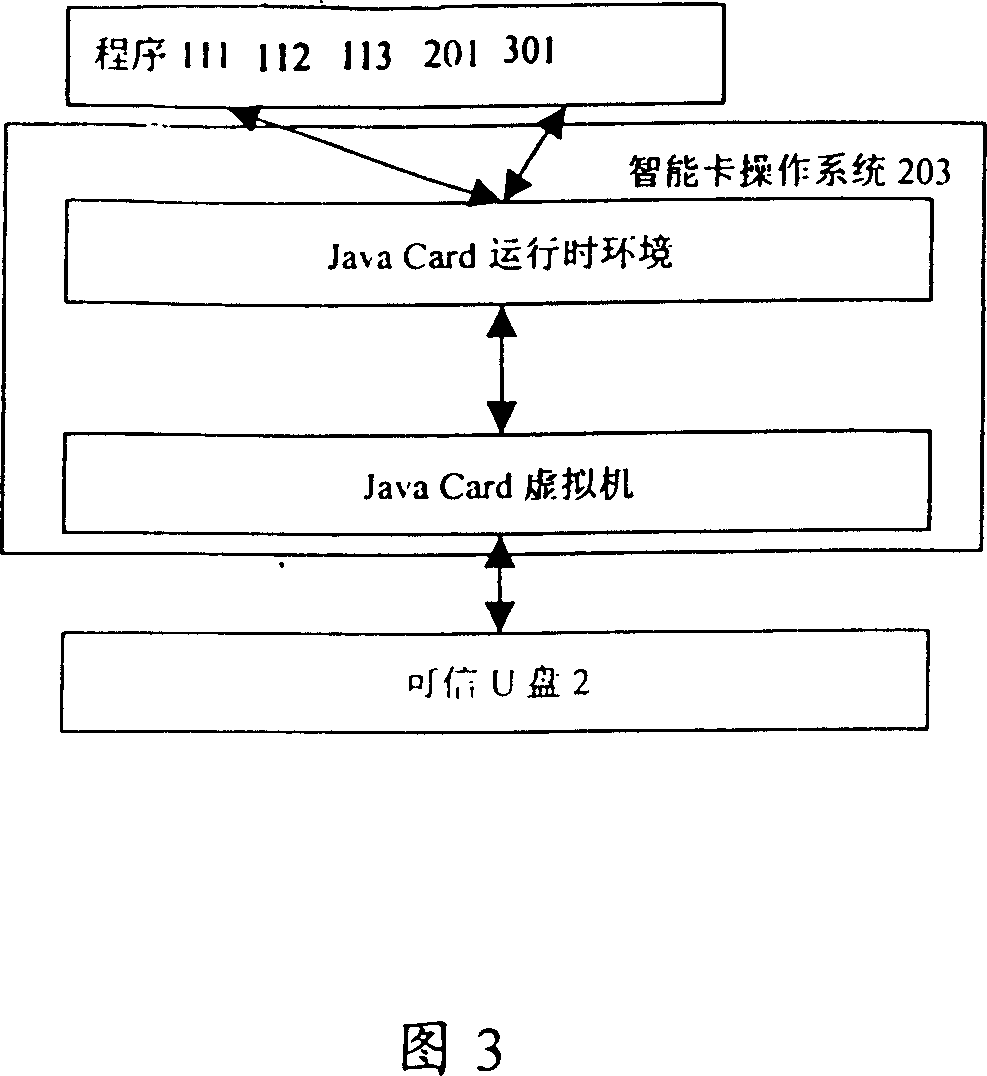
Reliable U disc, method for realizing reliable U disc safety and its data communication with computer
A data communication and security technology, applied in computer components, computer security devices, computing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0136] The Trusted Computing Organization proposes the necessary attributes, functions and characteristics of trusted devices:
[0137] 1. The Trusted Computing Group (TCG, Trusted Computing Group) defines "trusted" as: trustworthiness is an expectation under which a device operates in a specific way according to a specific purpose.
[0138] According to the Trusted Computing Organization's Trusted Computing Platform Standard Implementation Specification, trusted computing should include the following three attributes and functions:
[0139] ①. Ensure the uniqueness of the user's identity, the integrity and privacy of the user's work space.
[0140] ②. Ensure the integrity of hardware environment configuration, OS kernel, services and applications.
[0141] ③. Ensure the confidentiality / integrity of information stored, processed, and transmitted.
[0142] 2. The Trusted Computing Organization has formulated a series of complete specifications for different terminal types and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com