Login method and device, terminal and network server
A technology of network server and login method, applied in the fields of instruments, digital data authentication, electronic digital data processing, etc., can solve the problems of easy privacy leakage, affecting the willingness to use, and degrading user experience, and achieve the effect of ensuring security and login security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
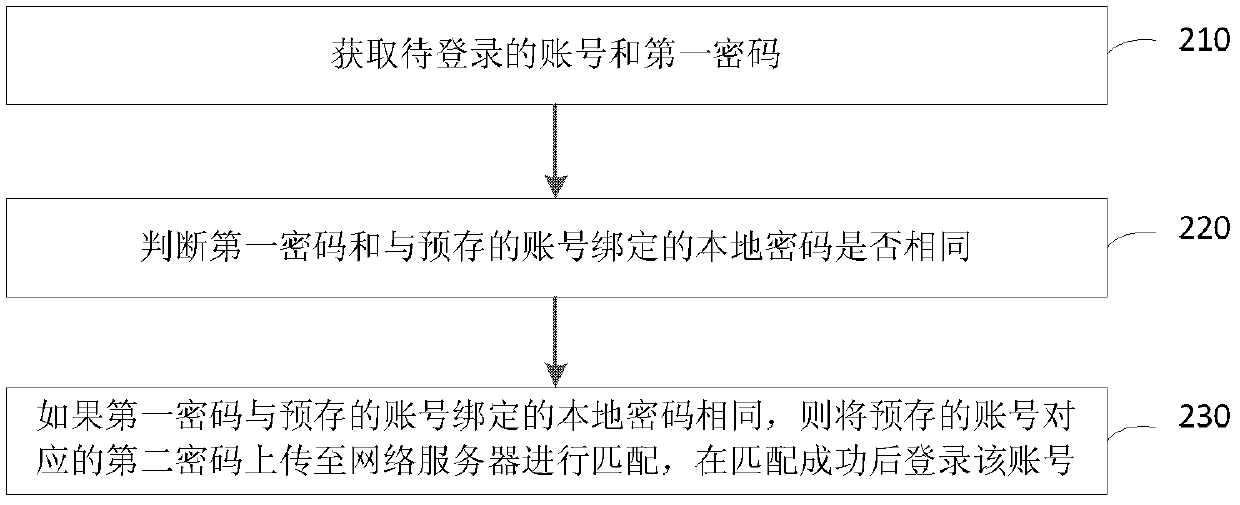
[0066] figure 2 is a schematic flow chart of the login method provided by Embodiment 1 of the present invention, which can be applied to figure 1 In the terminal 110 in. Login methods include:
[0067] Step 210, acquiring the account to be logged in and the first password.
[0068] The first password can be the input password input for the current account to be logged in, and the first password can also be the input password input for the current account to be logged in and the machine code of the terminal (i.e. terminal 110) used to receive the input password combination.
[0069] Wherein, the machine code is used to uniquely identify a terminal, and the machine code of the terminal 110 is the unique identification code of the terminal 110 .
[0070] Step 220, judging whether the first password is the same as the local password bound to the pre-stored account.
[0071] In this embodiment, the local password can be a custom password that has been stored in the terminal a...
Embodiment 2
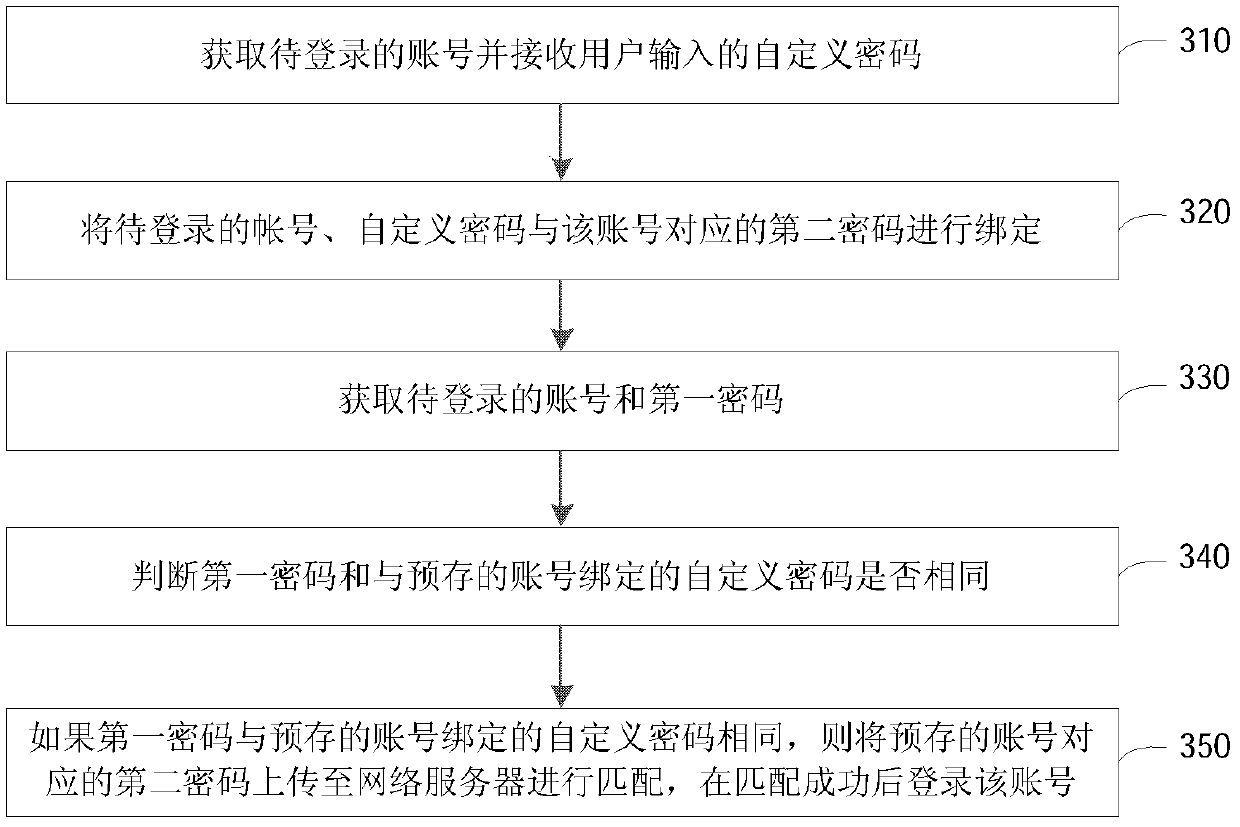
[0079] image 3 is a schematic flow chart of the login method provided in Embodiment 2 of the present invention, which can be applied to figure 1 In the terminal 110 in. Login methods include:
[0080] Step 310, obtaining an account to be logged in and receiving a user-defined password input by the user.
[0081] A custom password is a password that the user presets for the account to be logged in. Usually, in order to avoid the complexity of the custom password and make it easier for the user to remember or input, the custom password can be set relatively simply. Generally, the custom password can be set by A combination of letters, numbers, or punctuation symbols. For example, a custom password can be set to 123 or abc. In practical applications, on a fixed terminal 110, generally only one custom password is set for the same account, that is, on the same terminal 110, the same account corresponds to only one custom password.
[0082] In specific implementation, you can s...
Embodiment 3
[0098] Figure 5 is a schematic flowchart of the login method provided by Embodiment 3 of the present invention, which can be applied to figure 1 In the terminal 110 in. Login methods include:
[0099] Step 510, obtain the account to be logged in, receive the user-defined password input by the user, and obtain the local machine code.
[0100] A custom password is a password preset by the user for the account to be logged in. Usually, in order to avoid the complexity of the custom password and make it easier for the user to remember or input, the custom password can be set relatively simple. Generally, the custom password can be It is composed of letters, numbers, or punctuation symbols. For example, a custom password can be set to 123, or abc, etc. In practical applications, on a fixed terminal, generally only one custom password is set for the same account, that is, on the same terminal 110, the same account corresponds to only one custom password.
[0101] In specific im...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com