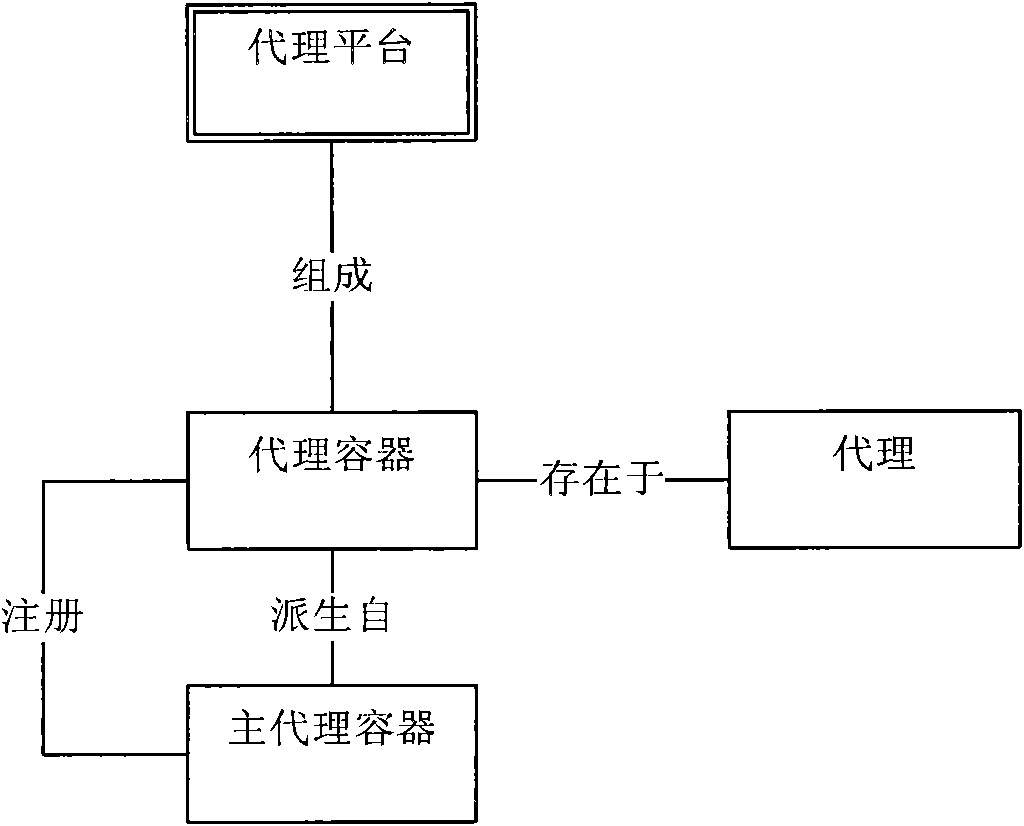
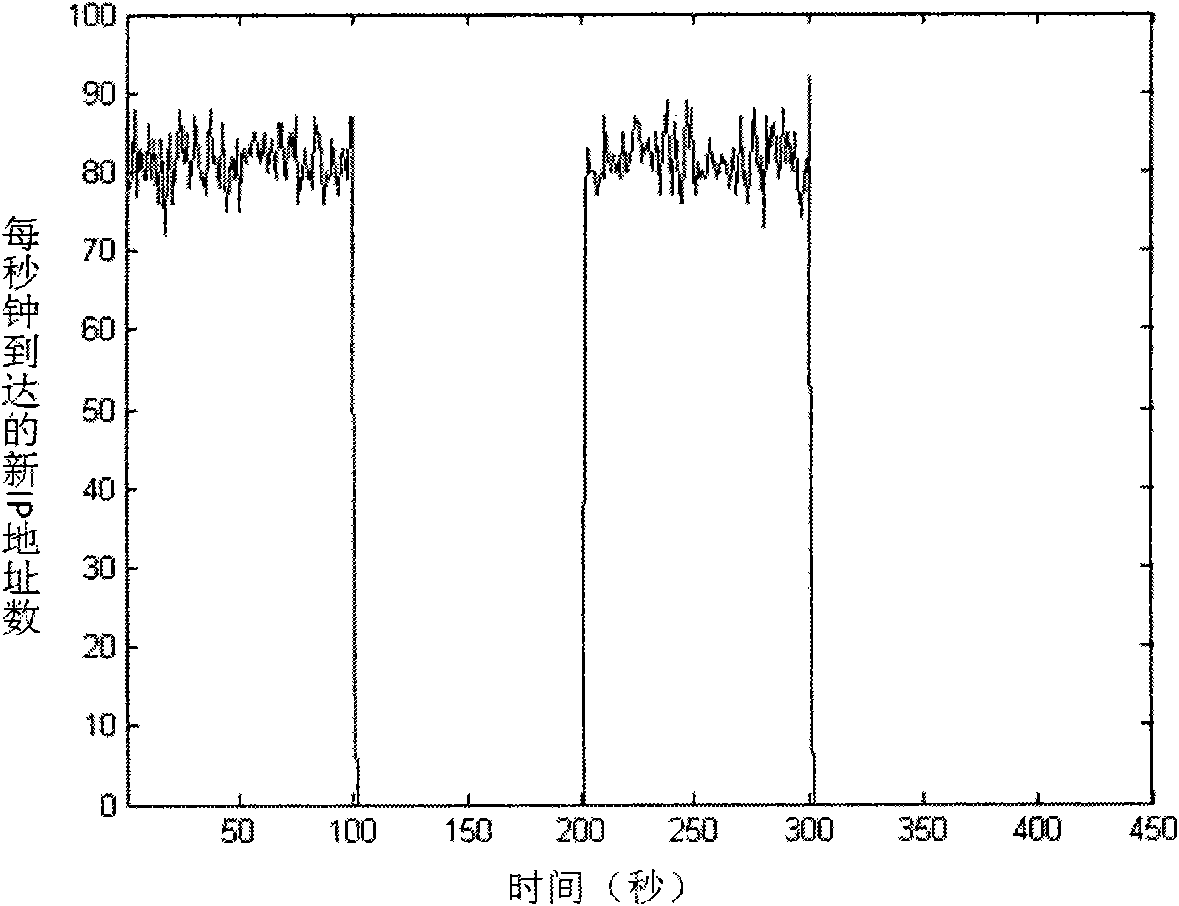
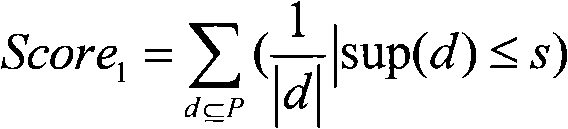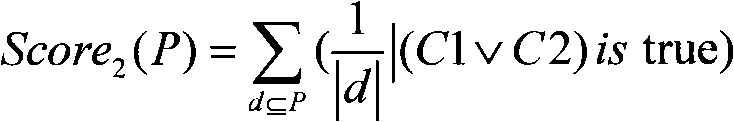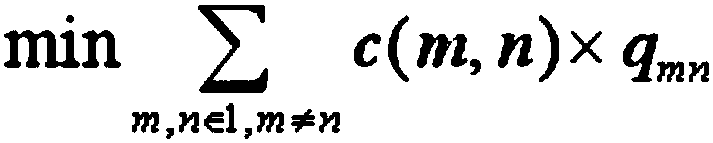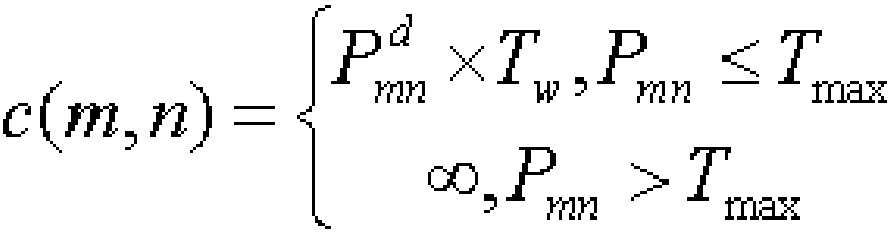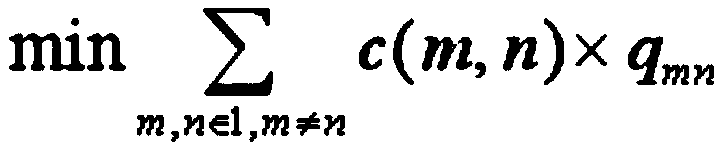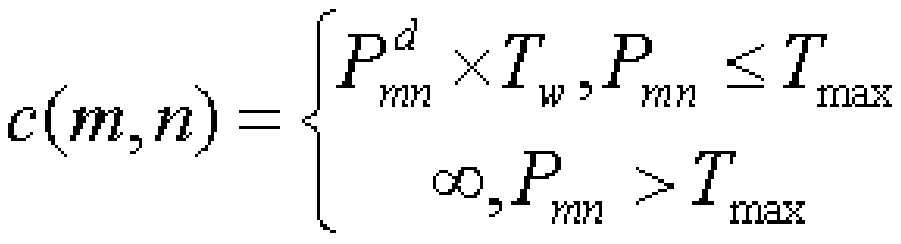Patents
Literature
37 results about "Distributed intrusion detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Distributed intrusion detection method and system for ad hoc network
ActiveCN108306893AAvoid Malicious InterferenceGuarantee authenticityFinanceNetwork topologiesDistributed intrusion detectionFinancial transaction
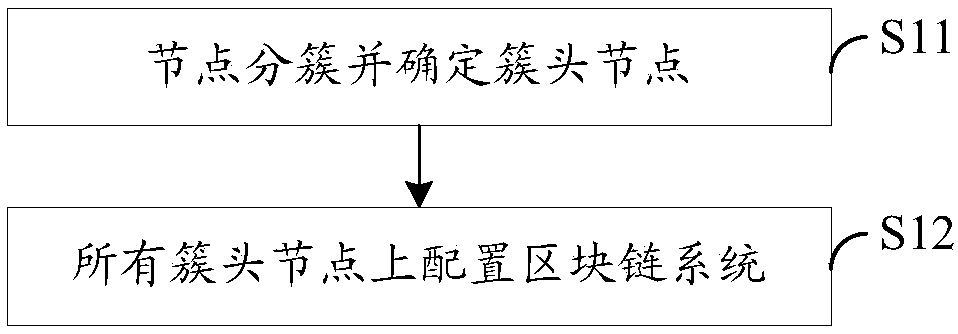
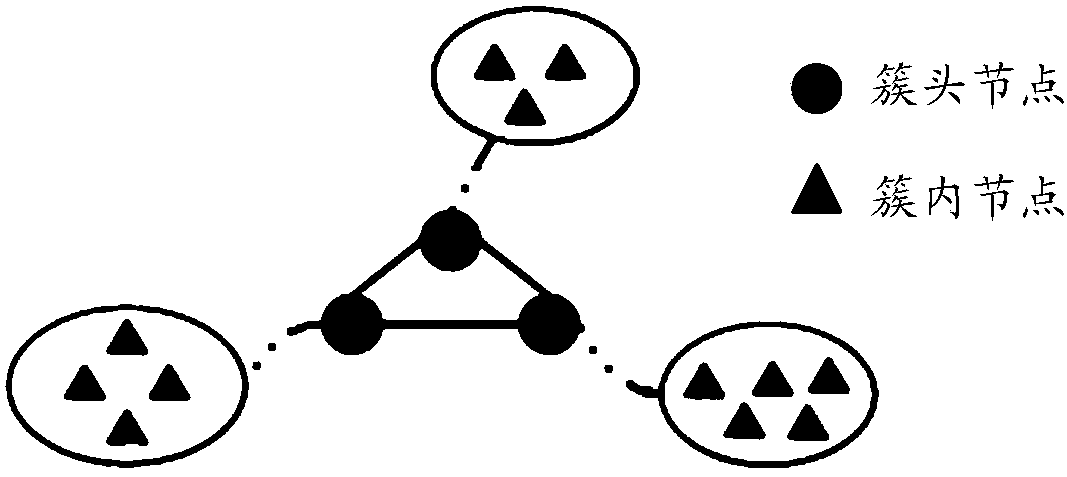
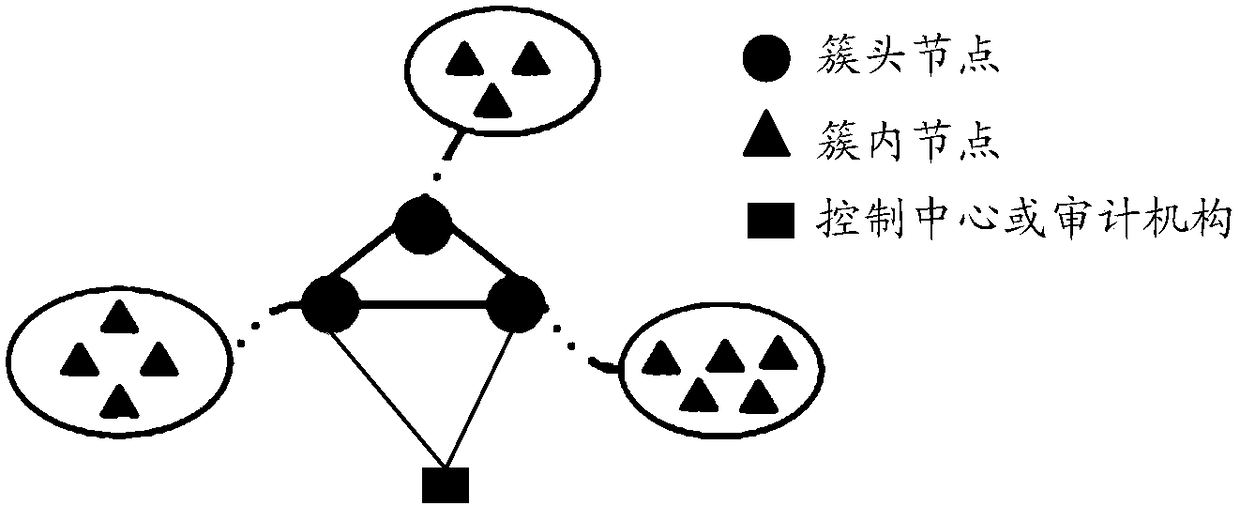
The invention relates to a distributed intrusion detection method and system for an ad hoc network. Nodes in the ad hoc network are clustered and cluster head nodes are selected, block chain systems are configured at all the cluster head node to form a block chain network, and the method includes the following steps: a node where a log is updated sends to the cluster head node thereof a transaction request containing a log information record which is formatted locally at the node; the cluster head node broadcasts the transaction in the block chain network after verifying that the transaction is legal; each cluster head node performs consensus verification of the transaction, after passing the consensus verification, the transaction is packed to be recorded to the block chain to form a shared log data; and each cluster head node executes intrusion detection based on local information and the shared log data. Since consensus verification and recording are performed on the log informationrecord, authenticity and reliability of detection data are ensured, globally reliable shared information records and safety audit data are provided for the centerless weakly-trusted ad hoc network, so as to support global decision making and response, thereby enabling intrusion detection to be more accurate.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
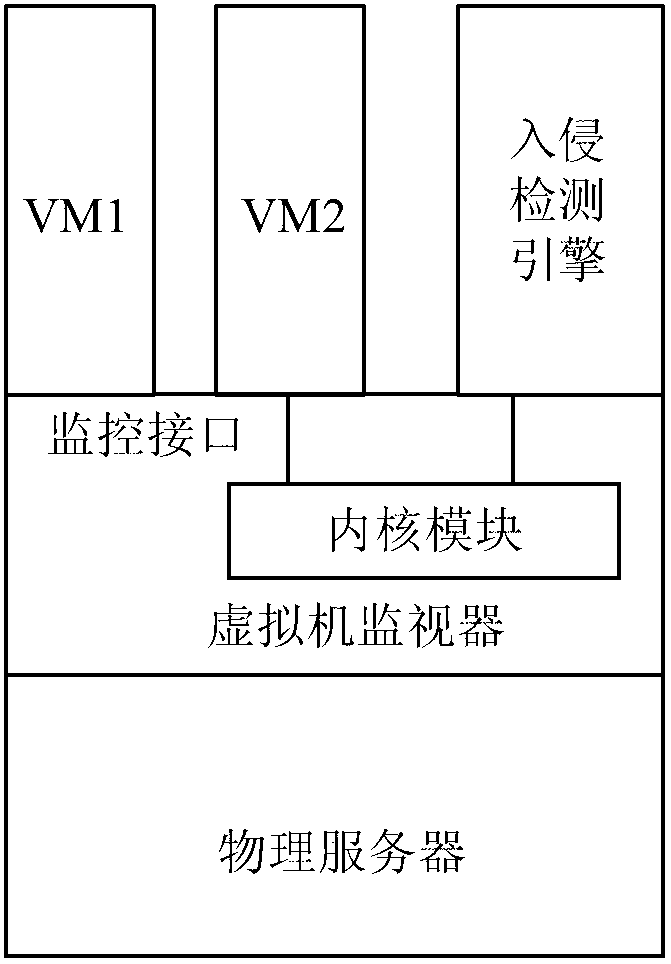
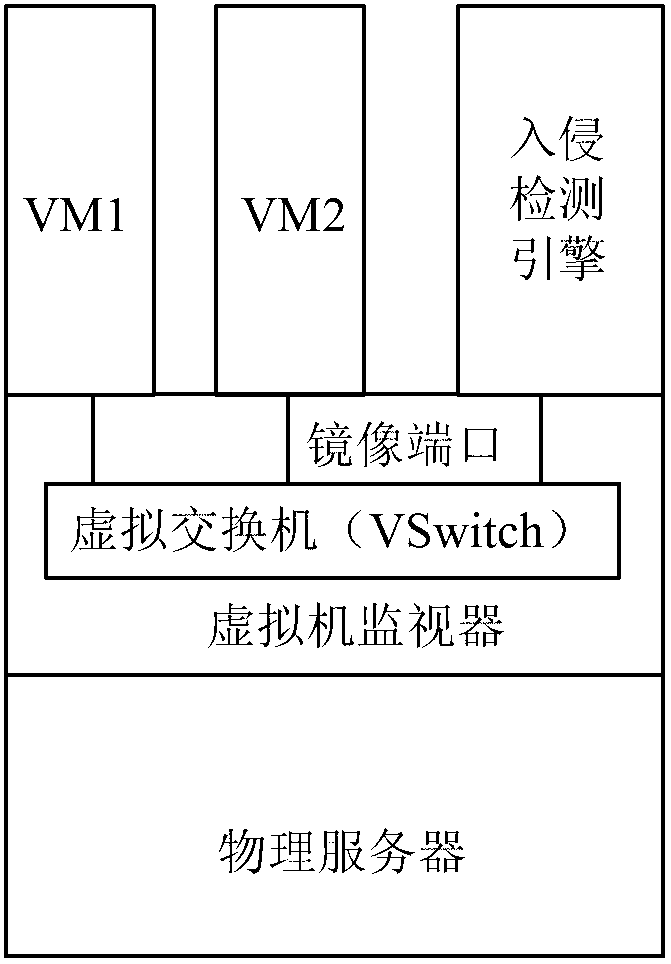
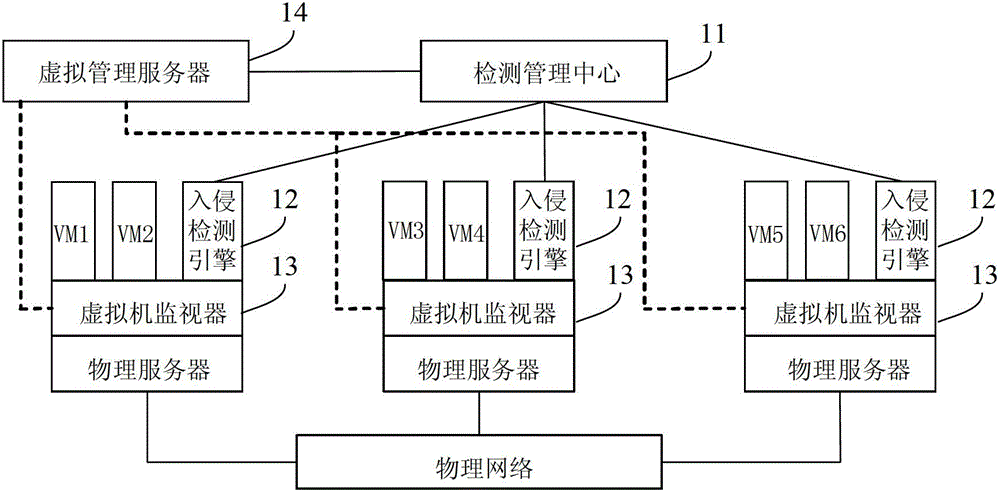
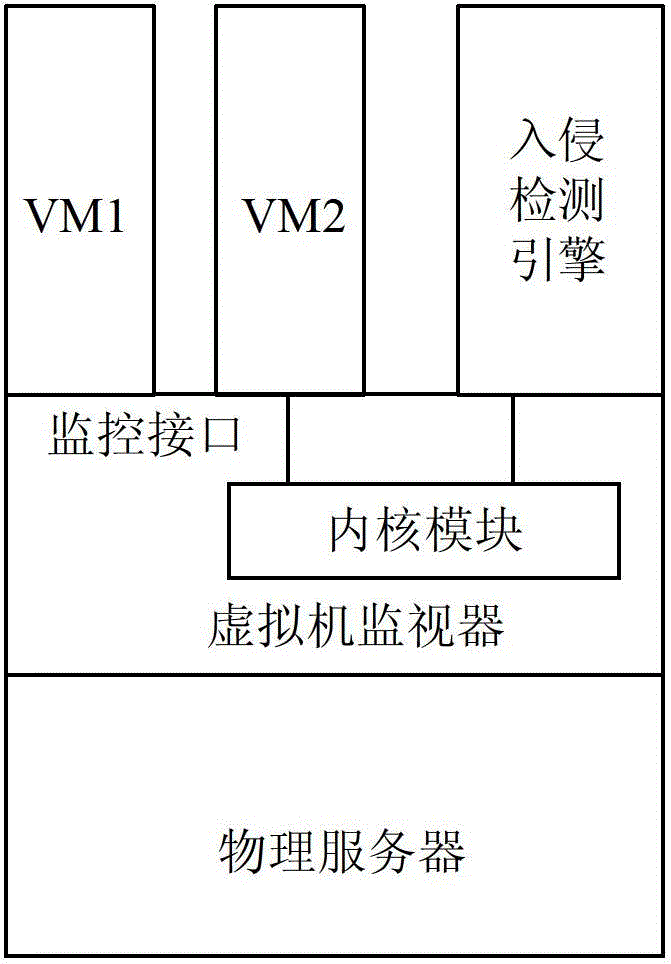
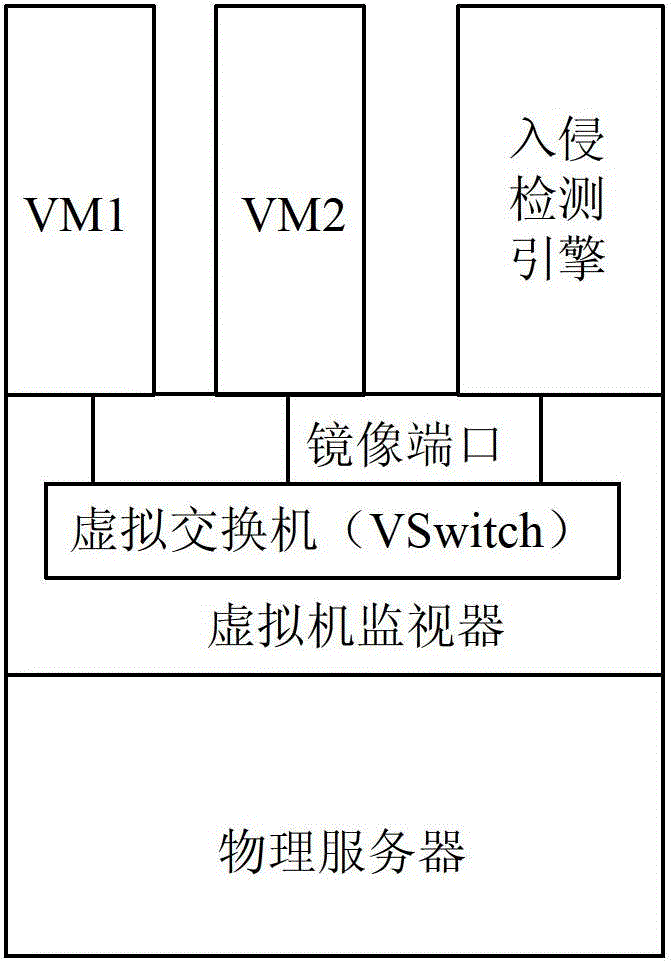
Distributed intrusion detection system and method applied to dynamic virtualization environment
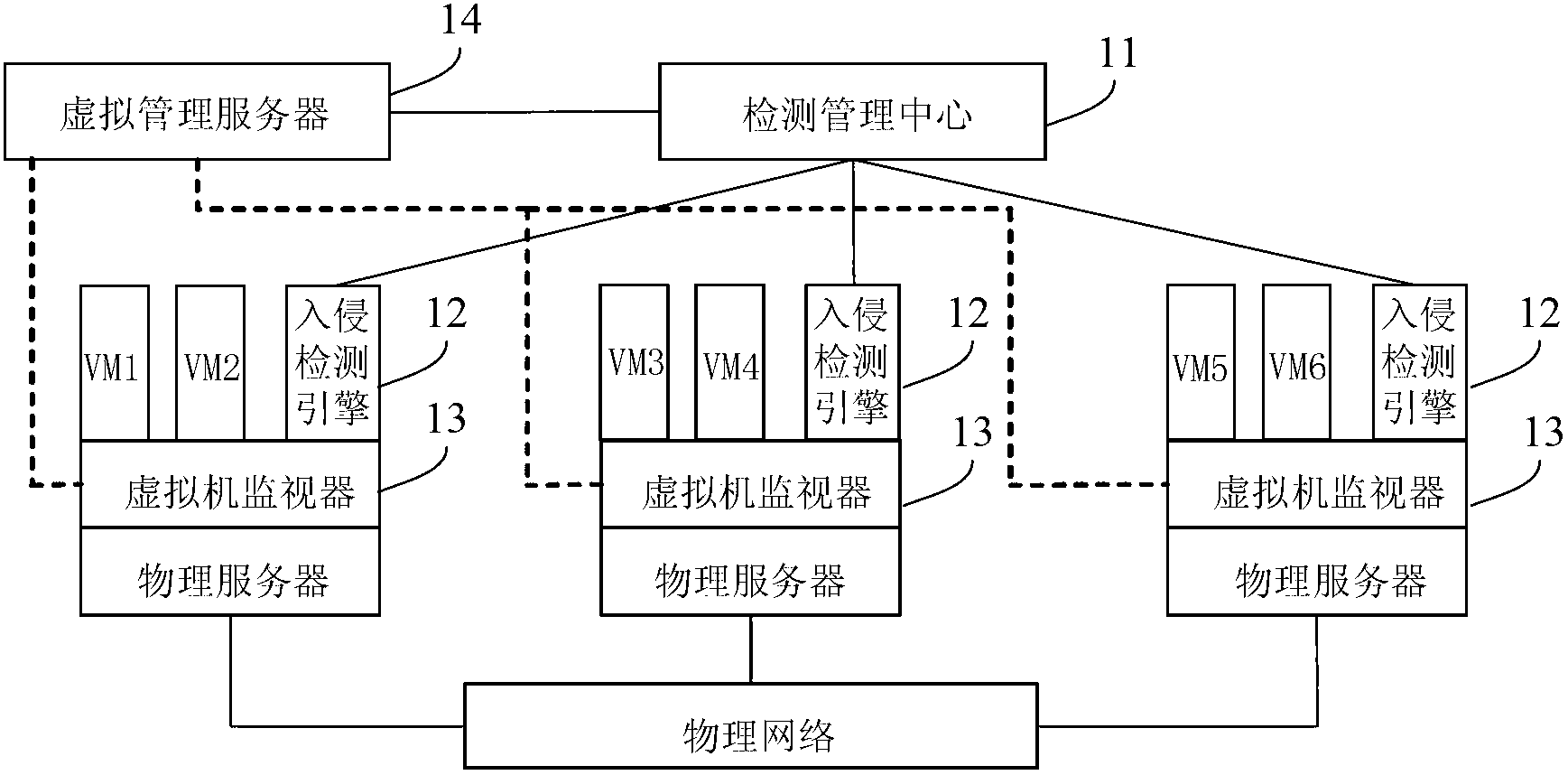
InactiveCN103065086ASolve the problem of continuous monitoringSolve the problem of not being able to continuously monitor virtual machinesPlatform integrity maintainanceTransmissionDistributed intrusion detectionVirtualization
The invention provides a distributed intrusion detection system and a distributed intrusion detection method applied to dynamic virtualization environment. The system comprises a detection management center, and intrusion detection engines positioned on physical servers, wherein the detection management center is used for acquiring information of a source physical server and a target physical server to which the current virtual machine belongs before and after migration; a virtualization management server in a virtualization platform performs intrusion detection stop configuration on the intrusion detection engine on the source physical server and performs intrusion detection start configuration on the intrusion detection engine on the target physical server; and the intrusion detection engines are used for performing intrusion detection on specific virtual machines on the corresponding physical servers after an intrusion detection start safety strategy is configured, and stopping intrusion detection of the specific virtual machines on the corresponding physical servers after an intrusion detection stop safety strategy is configured. By the system and the method, the virtual machines can be continuously monitored.
Owner:BEIJING VENUS INFORMATION TECH +1
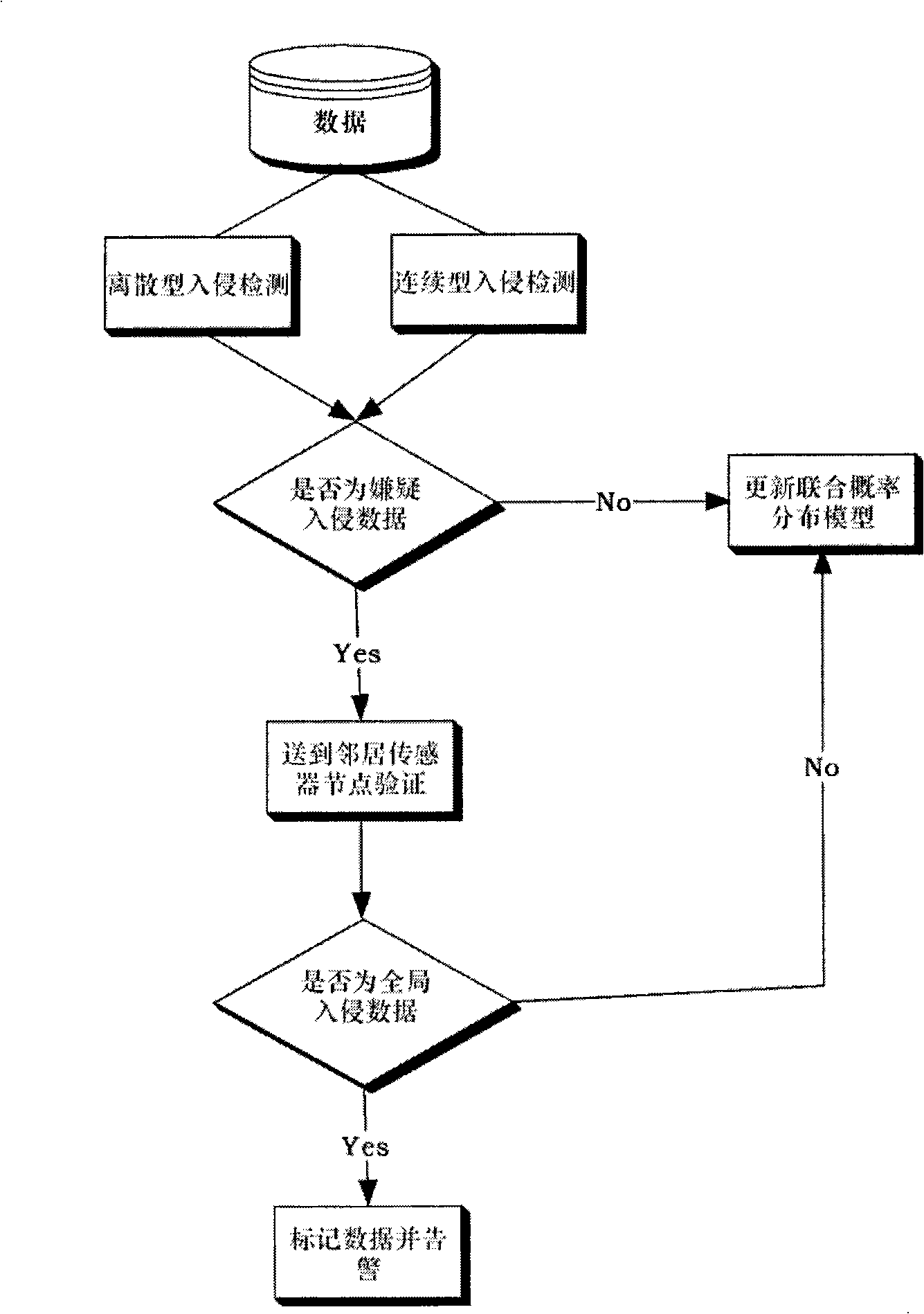
Distributed intrusion detection method in wireless sensor network
InactiveCN101286872AAvoid lossSmall amount of calculationData switching networksLine sensorDistributed intrusion detection
The invention discloses a method for detecting distributed intruding, which is used in a wireless sensor network. A frequent item set detecting method is used in a node of a sensor for detecting abnormality degree of discrete web log data and a method of joint probability distribution calculation is used for detecting the abnormality degree of successional web log data; if the node of the sensor judges that the whole data is abnormal intruding data, the node sends the suspicion data to the neighboring node of the sensor for verification; if the neighboring node also judges that the suspicion data is the intruding data, then the node of the sensor marks the data as the intruding data and starts to detect the next data. The method combines the distributed technology and the intruding detecting technology and reduces the calculation quantity and communication quantity of each node by the cooperation among nodes of the sensor network. An intruding movement is distinguished by analyzing the local web log data and reported to a system as an alarm, so as to realize the security purpose of protecting the wireless sensor network from various new and old attacks.
Owner:SHANGHAI JIAO TONG UNIV
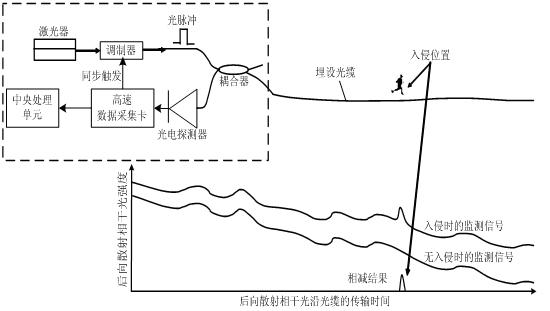
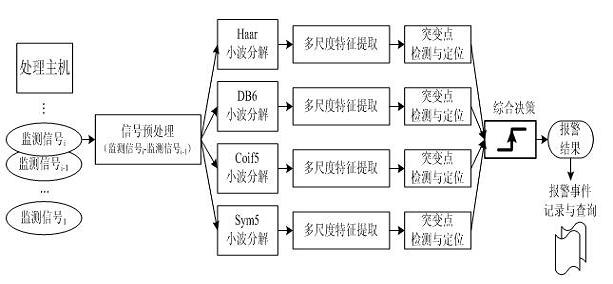
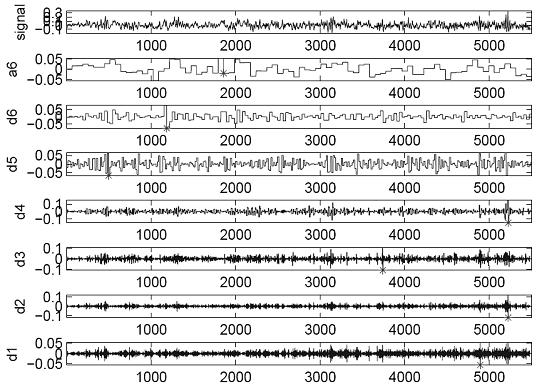
Intrusion detection and location method of distributed fiber optic fence based on φ-otdr
The invention discloses a distributed optical fiber fence intrusion detection and location method based on a phi-OTDR (Optical Time Domain Reflectometer), and the method comprises the following steps of: firstly, subtracting an acquired ith signal by an acquired (i-1)th signal to obtain a preprocessing monitoring signal; secondly, carrying out at least four-layer wavelet decomposition on the preprocessing monitoring signal by adopting a plurality of wavelet functions; thirdly, judging whether actual intrusion exists according to the consistency of distribution positions of maximum-wavelet mode maximums in all scale signals; fourthly, judging that the actual intrusion exists if the distribution positions of the maximum-wavelet mode maximums in at least three scale signals are consistent; fifthly, corresponding multiplying the scale signals in which the intrusion exists and the distribution positions of the maximum-wavelet mode maximums are consistent to obtain a composite signal of which pseudo maximums are inhibited and mode maximums at a catastrophe point are enhanced, using a position corresponding to the maximum-mode maximum in the composite signal as a position of the determined intrusion point, determining the intrusion generation and the intrusion position by combining various composite signal judgment results of wavelet multi-scale analysis according to the majority voting criterion.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Distributed intrusion detection method based on federated learning and trust evaluation and system thereof
ActiveCN112770291AImprove efficiencyImprove abilitiesInternal combustion piston enginesParticular environment based servicesDistributed intrusion detectionIn vehicle
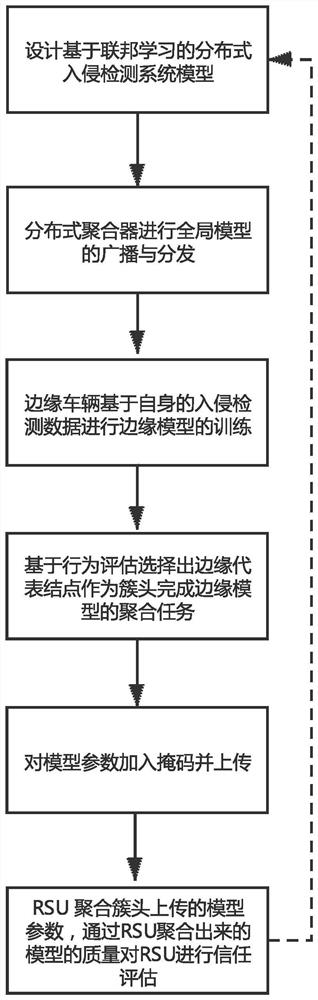
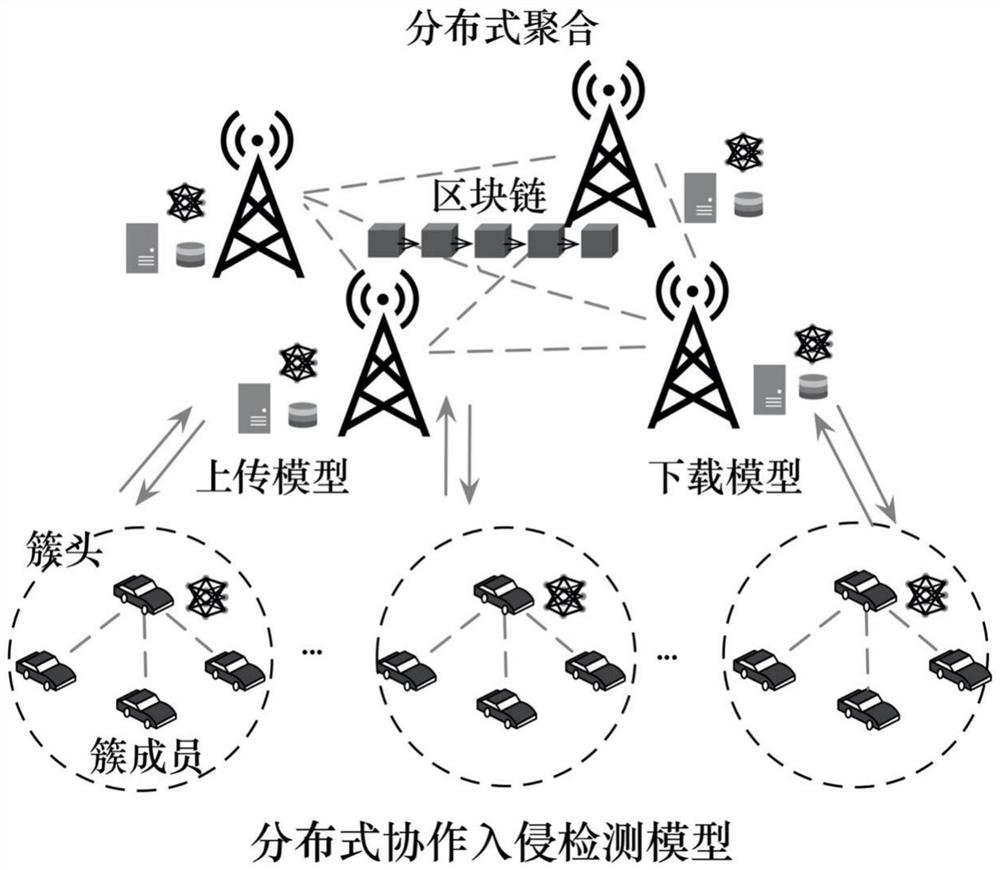
The invention provides a distributed vehicle-mounted intrusion detection system based on federated learning and trust evaluation and a method thereof. The method comprises the following steps: designing a distributed intrusion detection system model based on federated learning; building and pre-training of an intrusion detection model are realized based on federated learning, and broadcasting and distributing a global model by a distributed aggregator; performing edge model training based on intrusion detection data of the edge vehicle by the edge vehicle; selecting an edge representative node as a cluster head based on behavior evaluation to complete an aggregation task of an edge model; adding a mask to the model parameters and then uploading the model parameters to the RSU; performing trust evaluation on the RSU through the quality of a model aggregated by the RSU through the RSU aggregates model parameters uploaded by a cluster head, so that distributed aggregation nodes are stimulated to compete and aggregate a model with higher accuracy, and finally, storing the training model based on a block chain principle to complete model sharing. The invention further creates a defense detection system suitable for automatic driving to resist network intrusion by adopting a safety evaluation mode of information safety.
Owner:EAST CHINA NORMAL UNIV +2
Task assigning mechanism for large-scale distributive invasion detecting system
InactiveCN1469243ACut off the connection in timeRealize TrackingSpecific program execution arrangementsSpecial data processing applicationsDistributed intrusion detectionComputer architecture
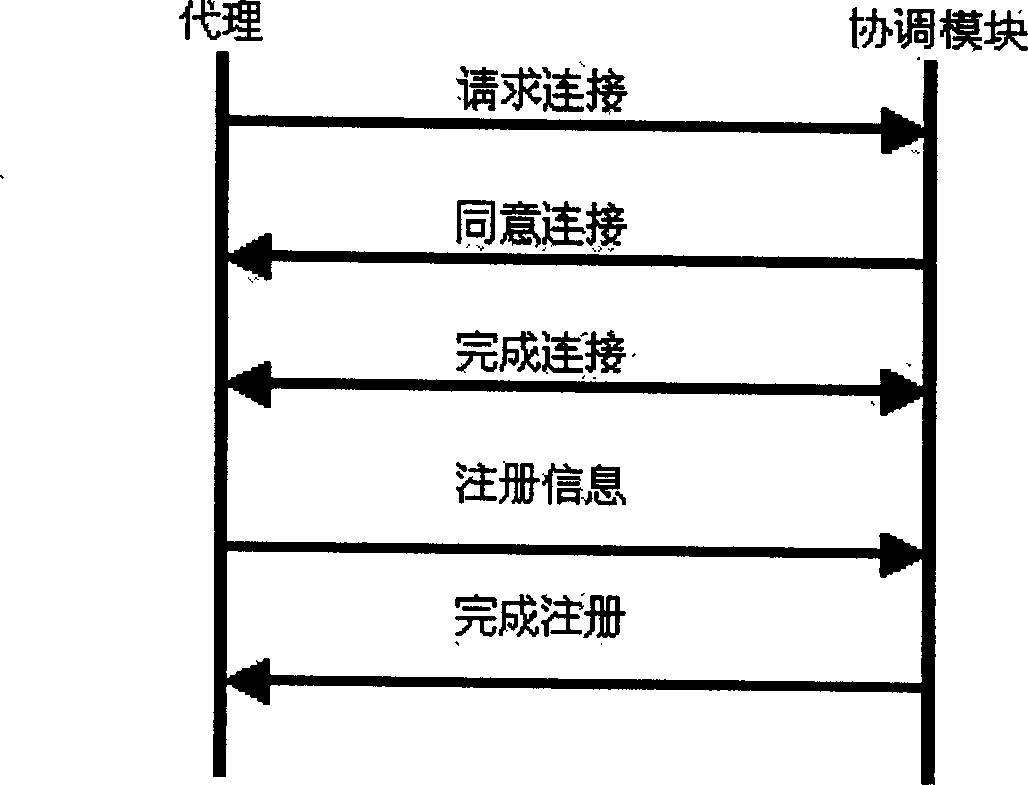
In large-scale high speed network, the invasion detecting system adopts always hierarchical distributive structure including dispersive acquisition, distributive processing and concentrated management. In the hierarchical modular structure, deputy technology is always adopted and the coordinating module in the coordinating management layer assigns and controls the deputies. In abnormal case that the static deputy in the lower layer can not settle, some request is sent to the coordinating module, and the coordinating module assigns movable deputy with specific function to the static deputy for complete the task before the cancel request is sent and the cancel command is sent separately to finish the assignment mechanism. The mechanism can balance the system load, respond timely, complete specific data processing function and make the movable deputy controllable.
Owner:BEIJING UNIV OF POSTS & TELECOMM
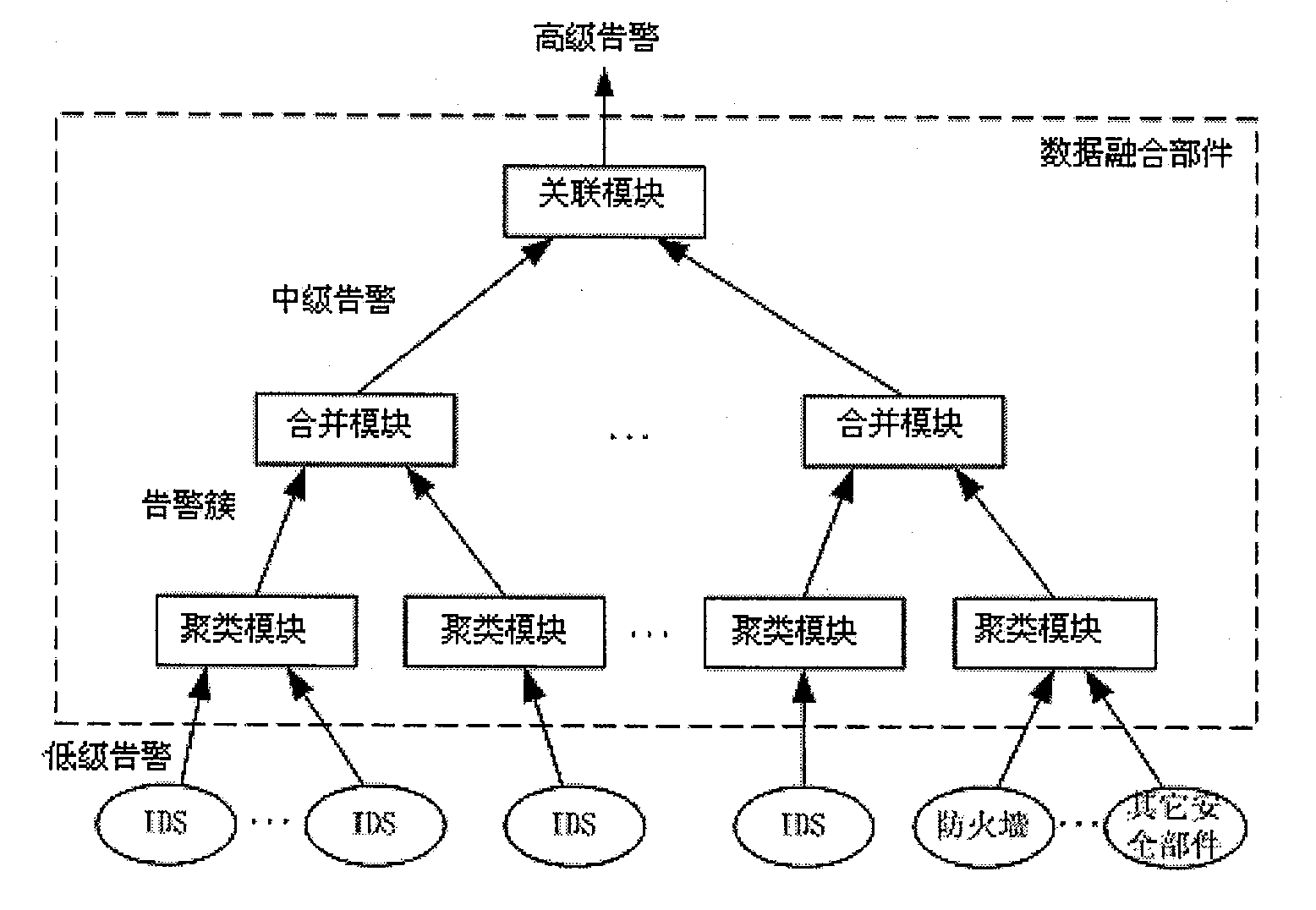
Distributed intrusion detection method, device and system
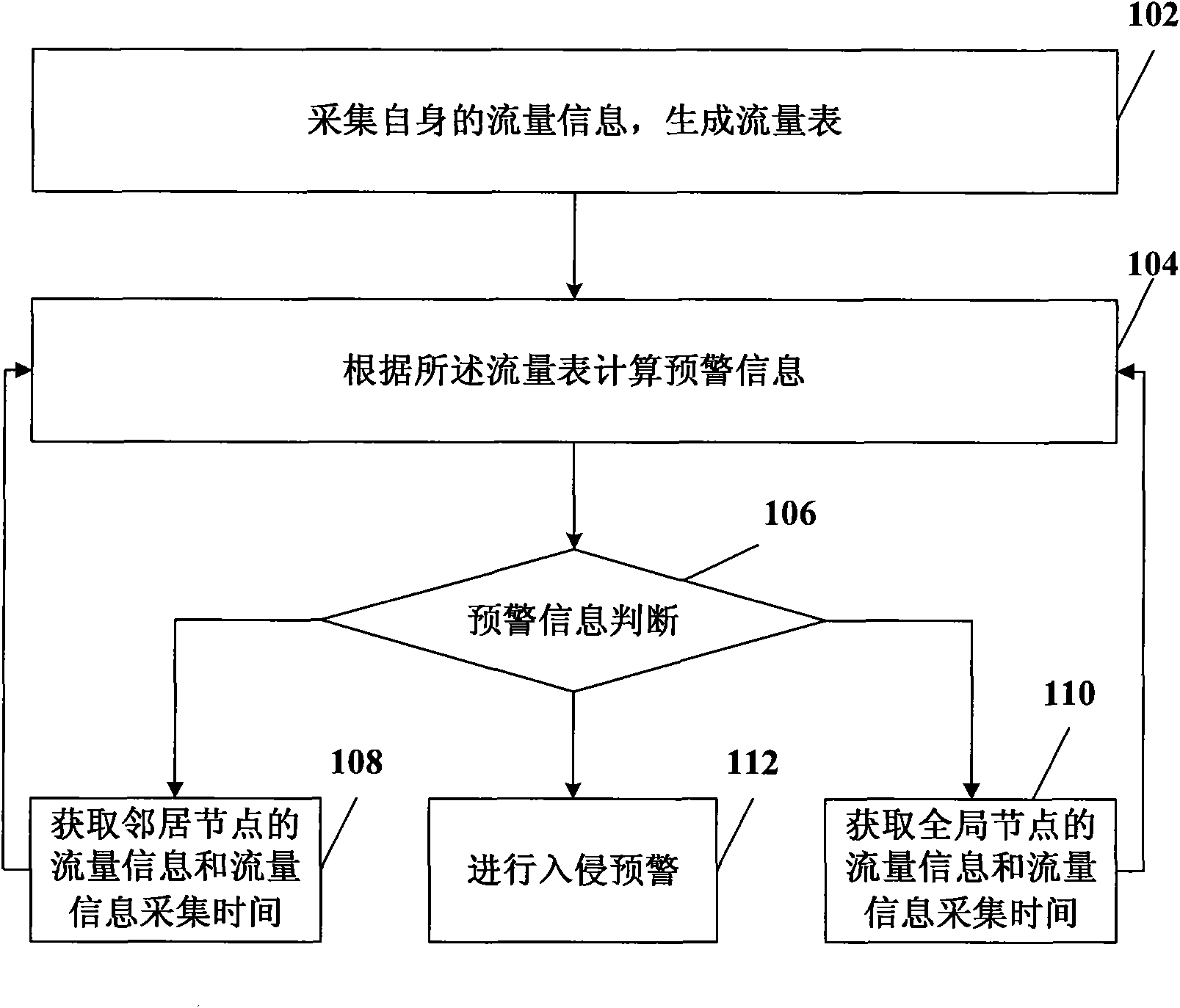
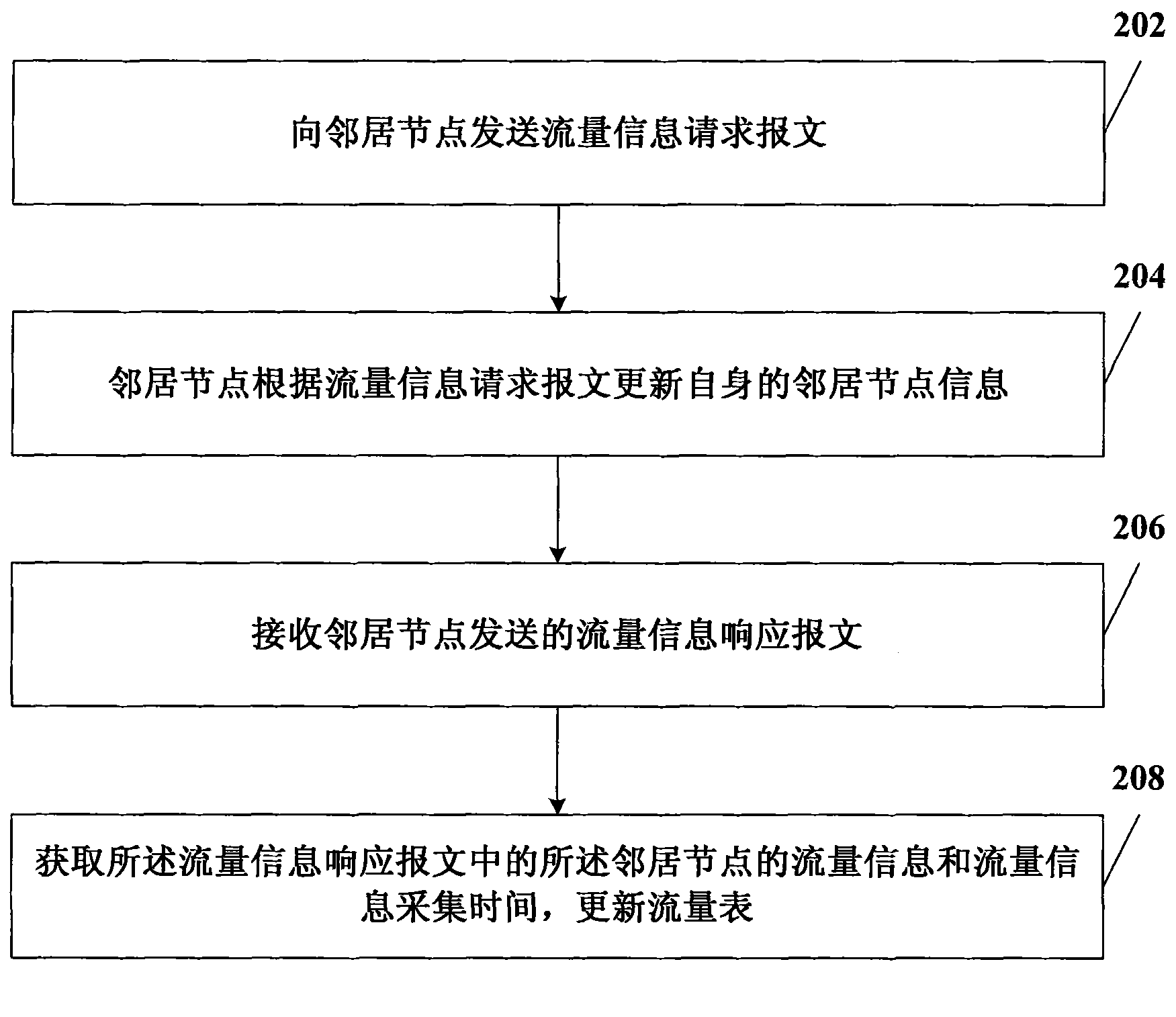
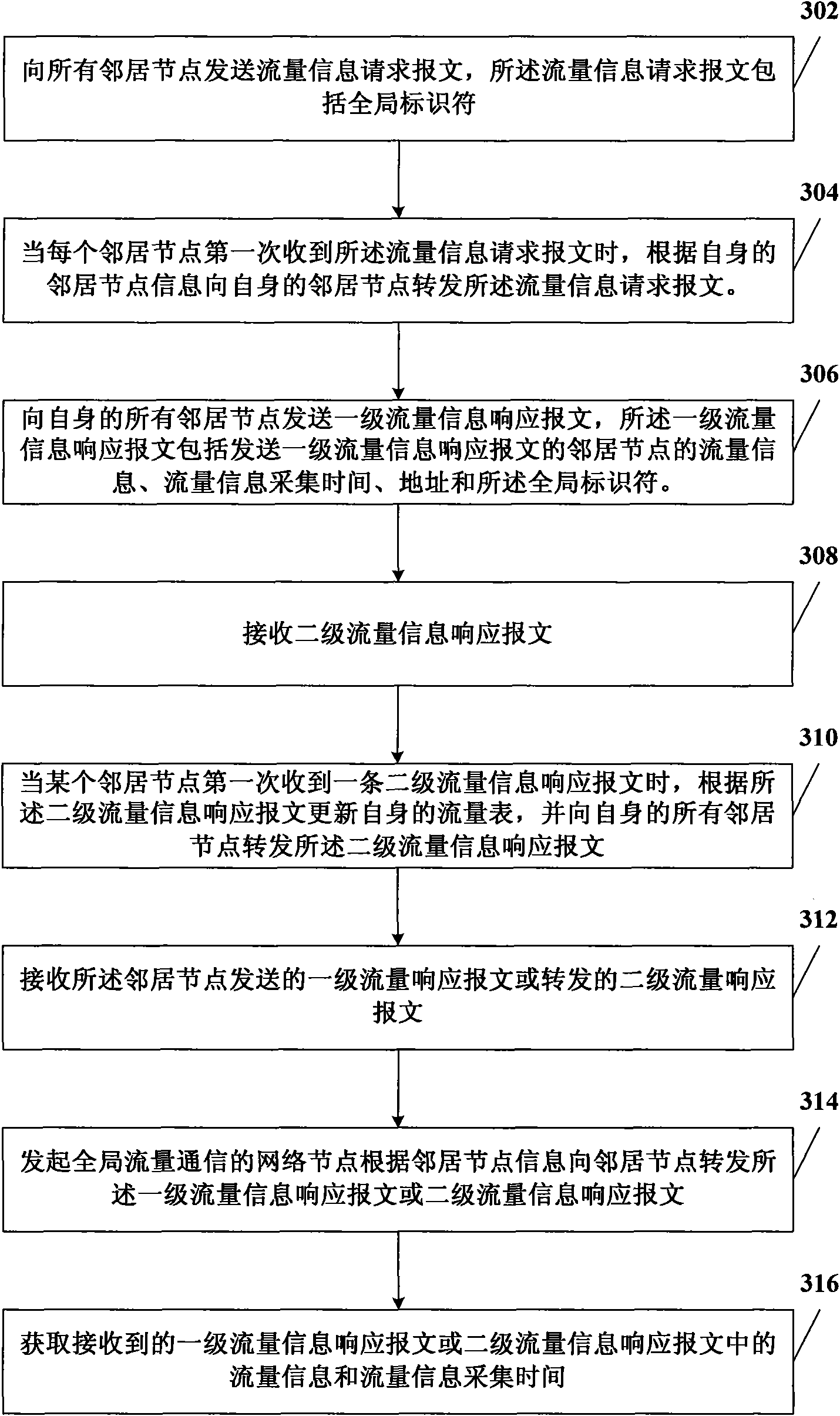
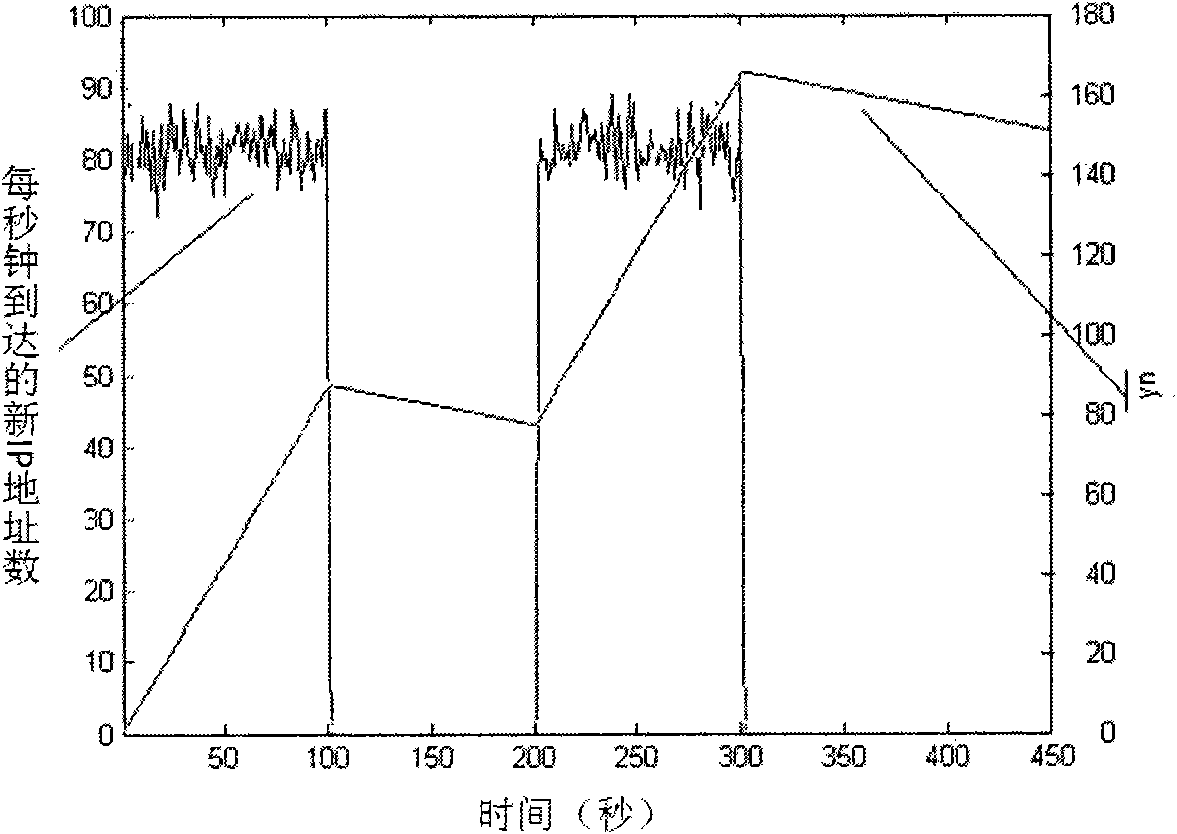
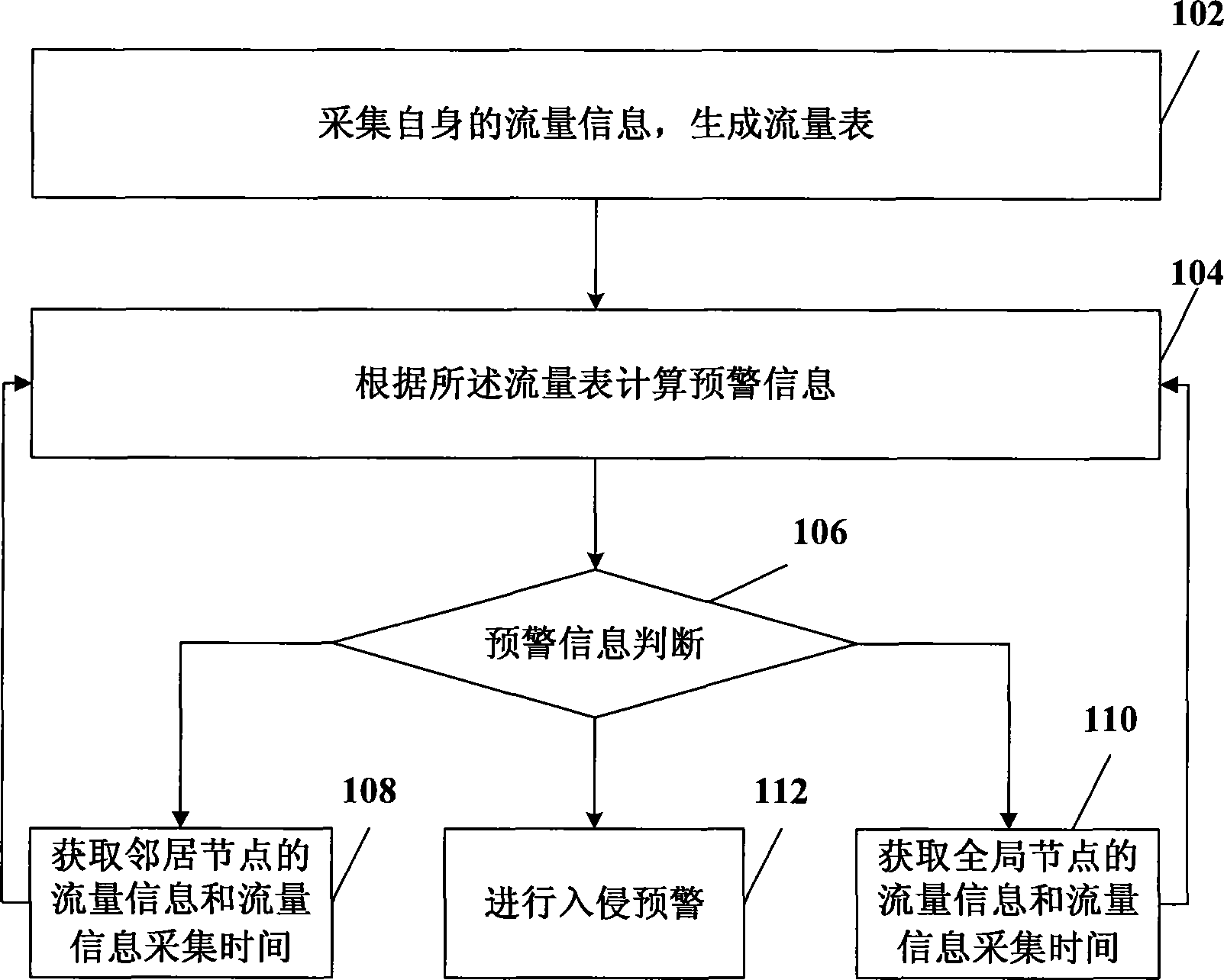
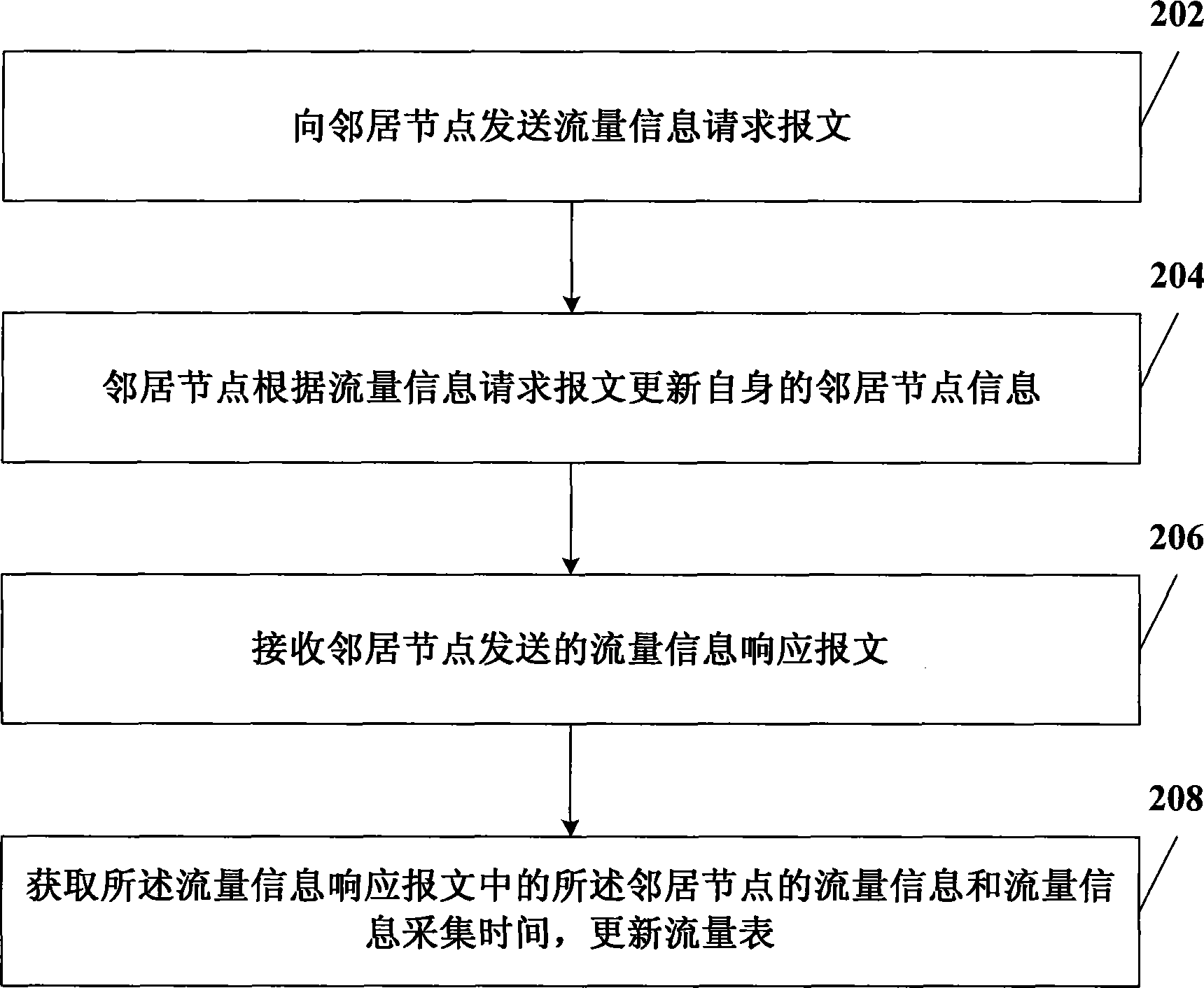
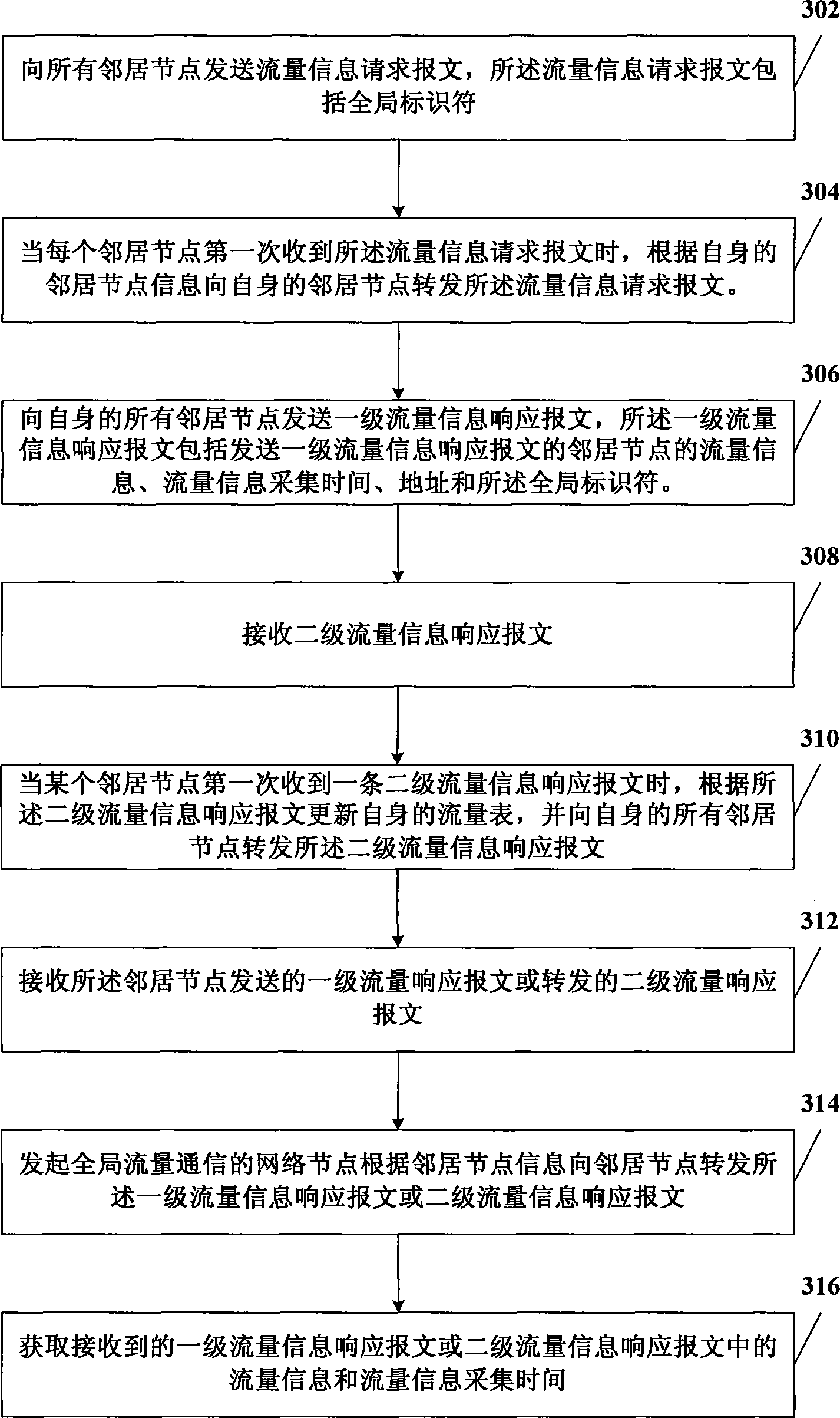
InactiveCN101997830AReduce frequencyReduce the impactSecuring communicationDistributed intrusion detectionNetwork communication
The invention relates to the field of network communication, in particular to a distributed intrusion detection method, a distributed intrusion detection device and a distributed intrusion detection system. The method comprises the following steps of: acquiring own flow information and generating a flow table; calculating early warning information according to the flow table; when the flow table only comprises own flow information or when the early warning information meets neighbor communication conditions, acquiring the flow information of a neighbor node and flow information acquisition time, and updating the flow table and the early warning information; when the early warning information meets global communication conditions, acquiring the flow information of a global node and the flow information acquisition time, and updating the flow table and the early warning information; and when the early warning information meets early warning conditions, performing intrusion early-warning. In the technical scheme provided by the embodiment of the invention, only the flow information of the neighbor node needs acquiring when the early warning information meets the neighbor communication conditions, so the data traffic in distributed intrusion detection is reduced and the influence of the distributed intrusion detection on network performance is reduced.
Owner:HUAWEI TECH CO LTD +1
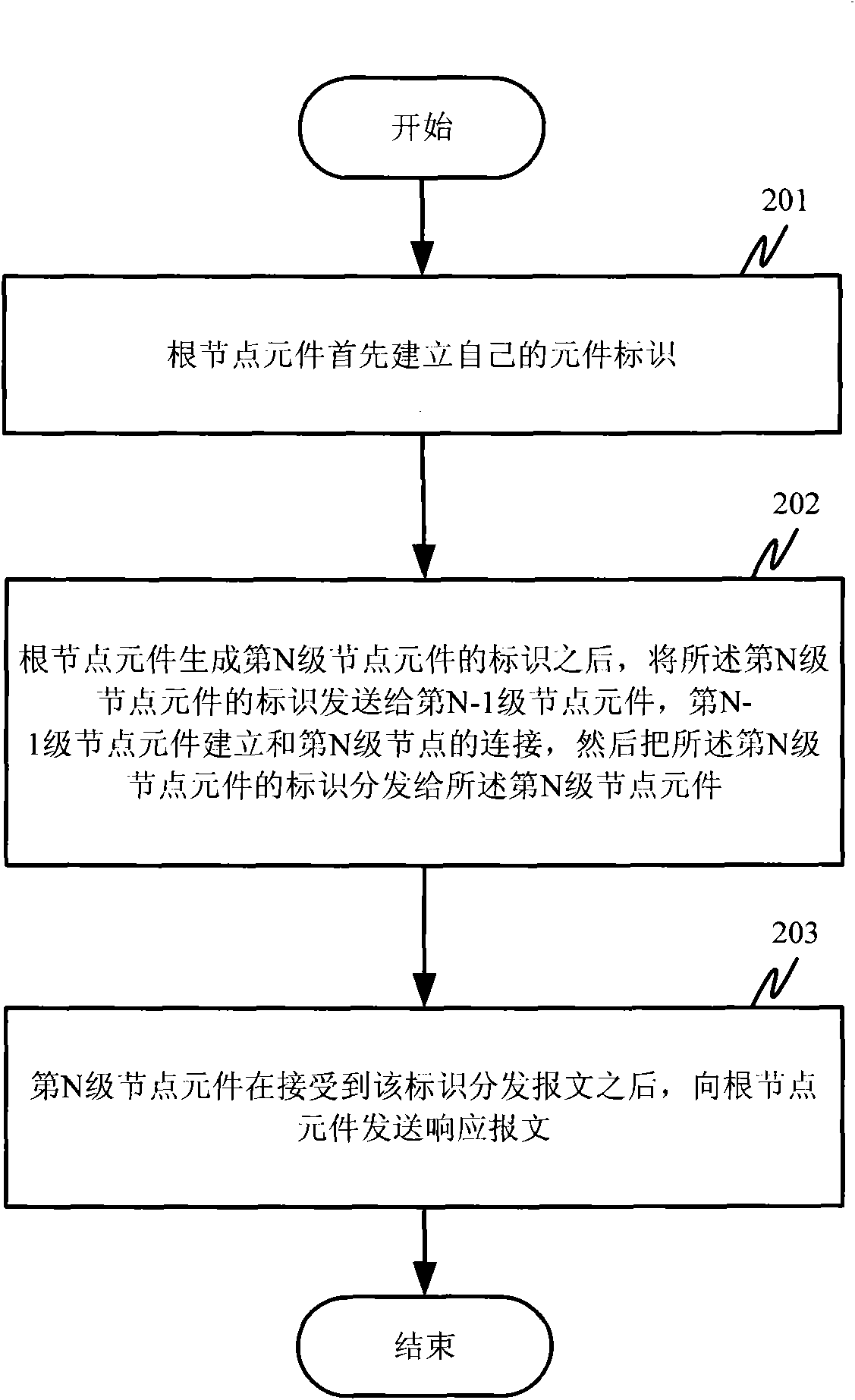
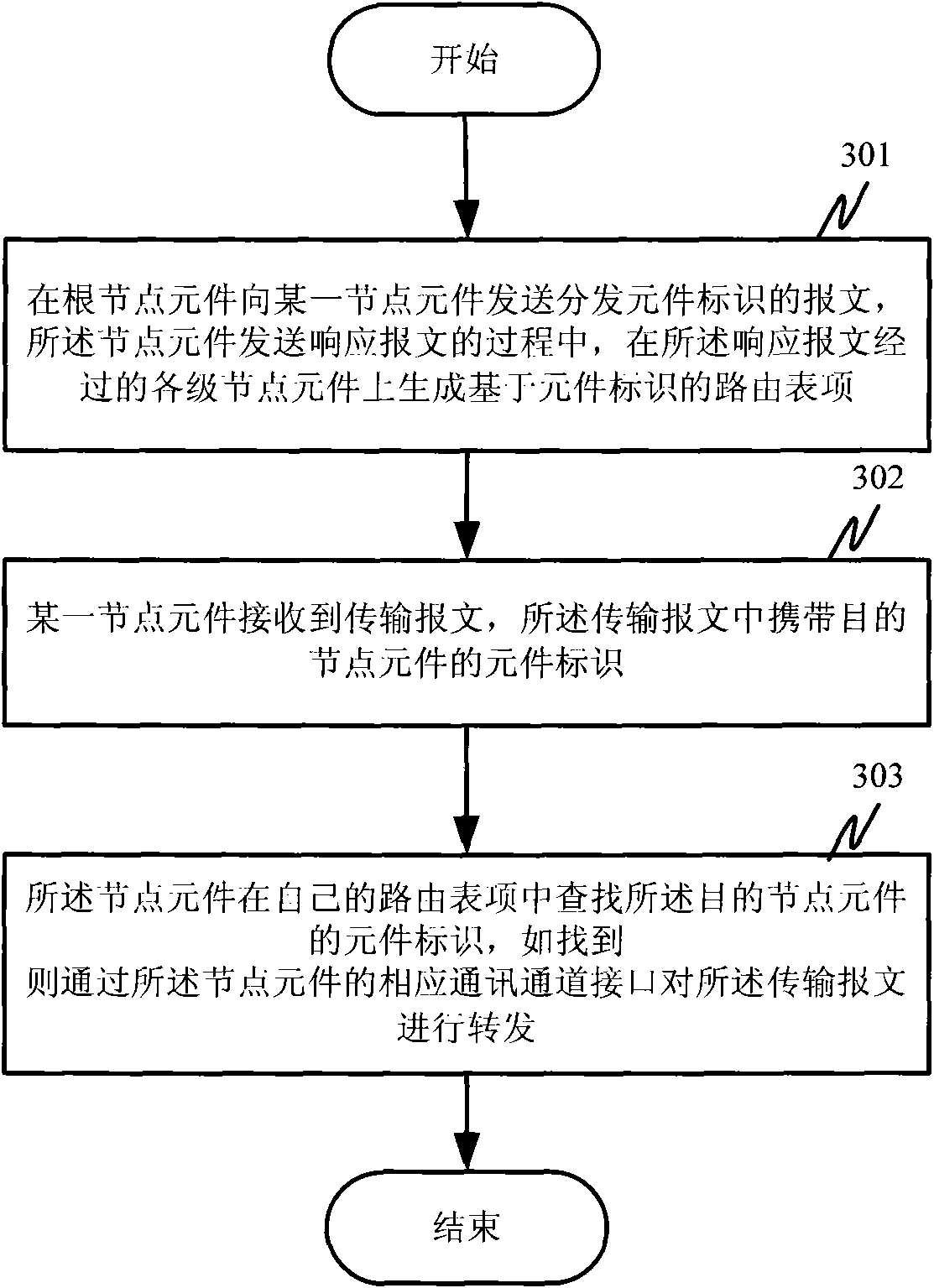
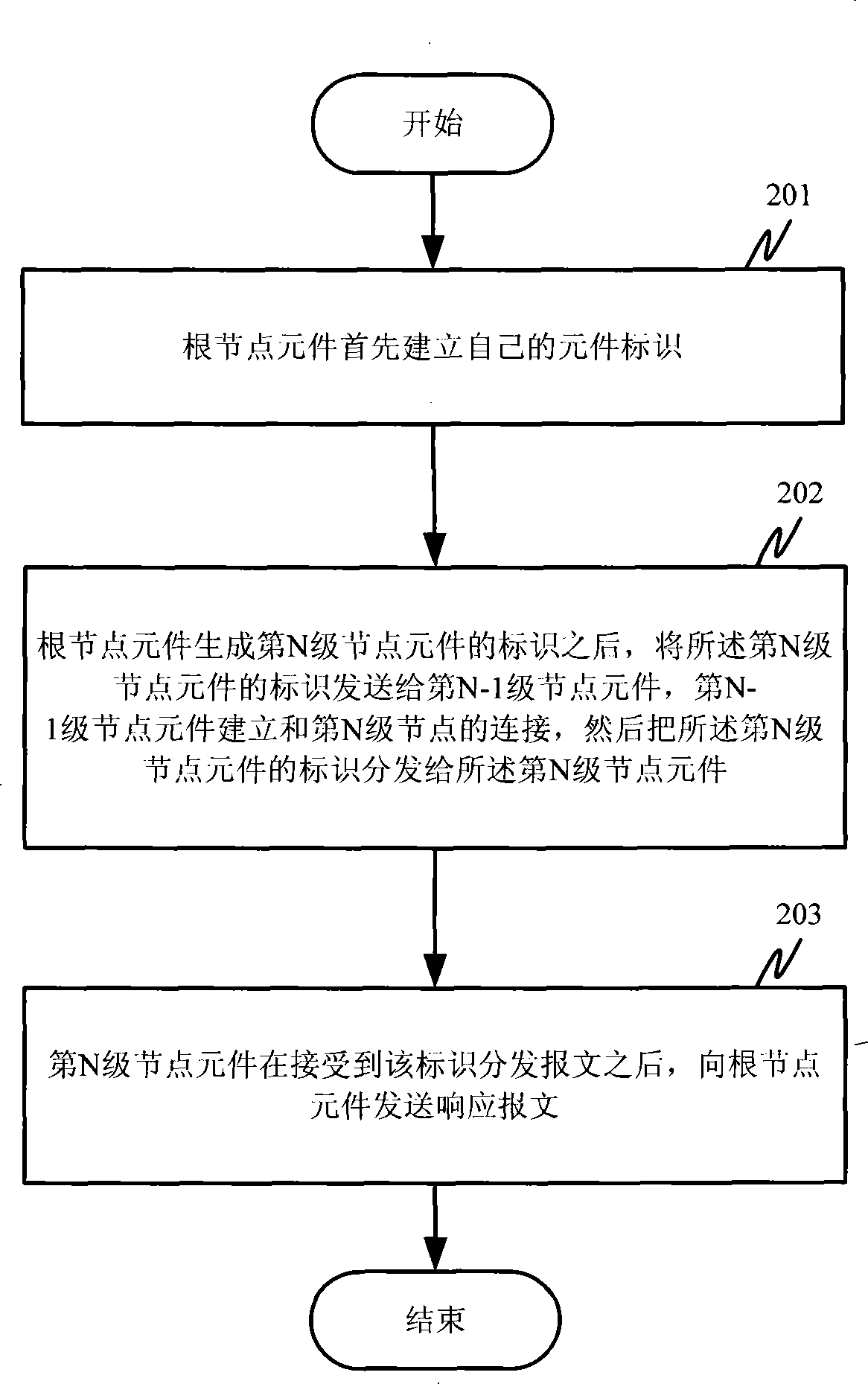
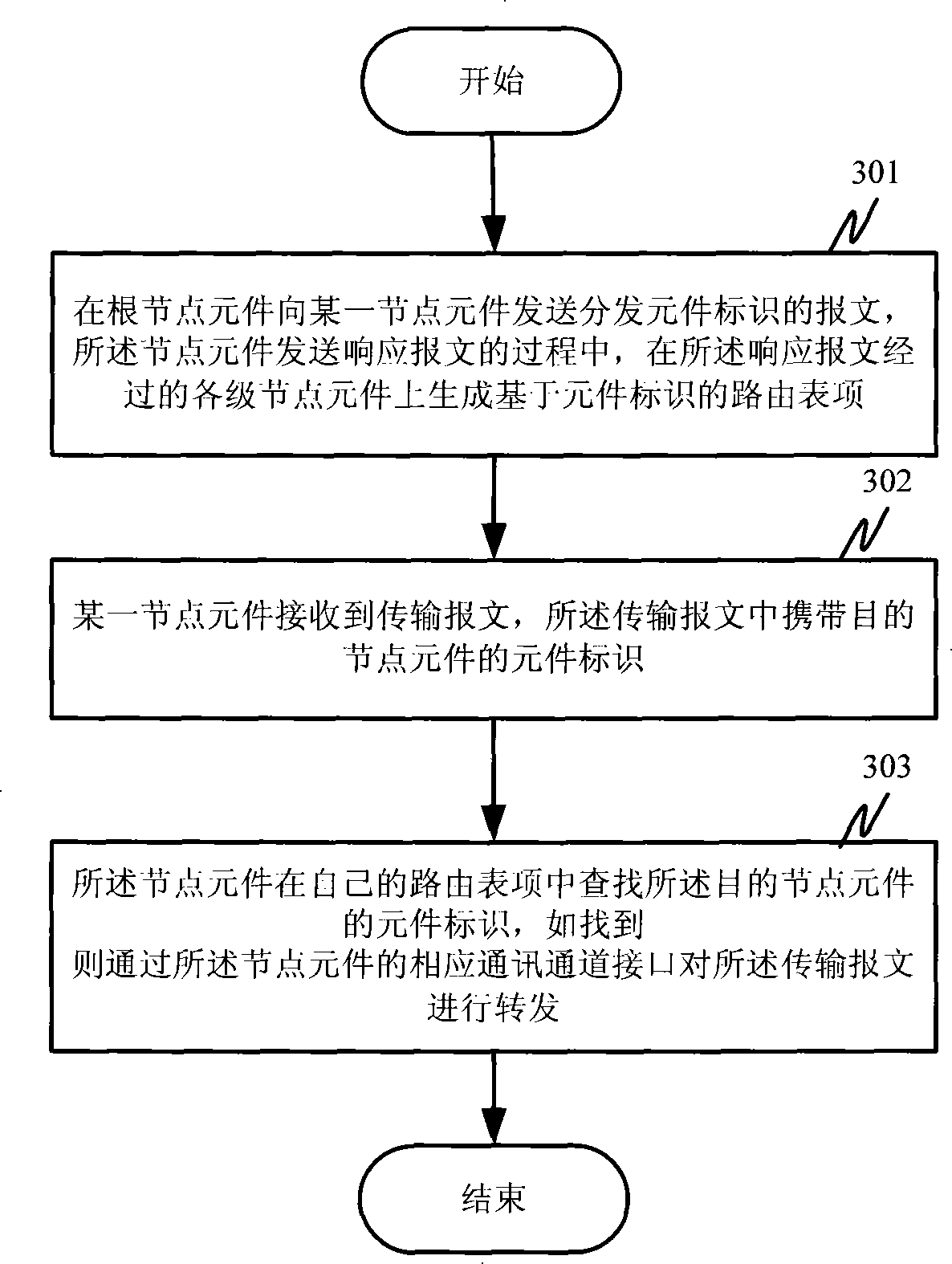
Element identifier distribution method and application layer routing method based on element identifier
InactiveCN101577707AMeet application needsAchieve distinctionData switching networksDistributed intrusion detectionRouting table
The invention discloses an element identifier distribution method and an application layer routing method based on element identifier, which is applied in centralized-management multilayer distributedsystems. In the method, node elements and element identifier of each level of a distributed system are established layer by layer; a routing table item based on the element identifier is generated inthe process of generating and distributing the element identifier; and addressing is performed through the element identifier during communication so as to realize application layer routing based onthe element identifier, which is needed by the communication of the centralized-management distributed system. The invention also provides a plurality of default routing rules of the routing method. The application layer routing method which is generated in the invention and based on element identifier is unrelated to TCP / IP (Transmission Control Protocol / Internet Protocol) routing methods, has the characteristics of simplicity, practicability, stability, reliability and resource conservation, and can meet special needs of distributed intrusion detection systems, distributed network auditing systems and various centralized-management multilayer distributed systems.
Owner:BEIJING VENUS INFORMATION TECH
Method for balancing low load and packet loss rate in DIDS based on reinforcement learning
ActiveCN111694662ASolve the problem of rising packet loss rateResource allocationCharacter and pattern recognitionDistributed intrusion detectionPacket arrival
The invention discloses a method for balancing a low load and a packet loss rate in DIDS based on reinforcement learning. The method comprises the following steps: calculating the immediate detectionrate, calculating the theoretical packet loss rats, calculating an average data packet arrival number; calculating the average waiting number of the data packets; calculating the packet latency probability, calculating the number of tasks allocated to the detection engine, calculating the probability that the detection engine is allocated to the tasks, calculating the working efficiency of the detection engine, calculating the overall working efficiency of the distributed intrusion detection system, and adjusting the balance of two contradictory indexes of low load and packet loss rate by detecting the probability that the detection engine is allocated to the detection tasks. The problem that in a task scheduling algorithm of a distributed intrusion detection system with a low load as a target disclosed in the prior art, the packet loss rate is possibly increased due to the fact that the low load is purely emphasized is solved.
Owner:陕西森印多西网络科技有限责任公司
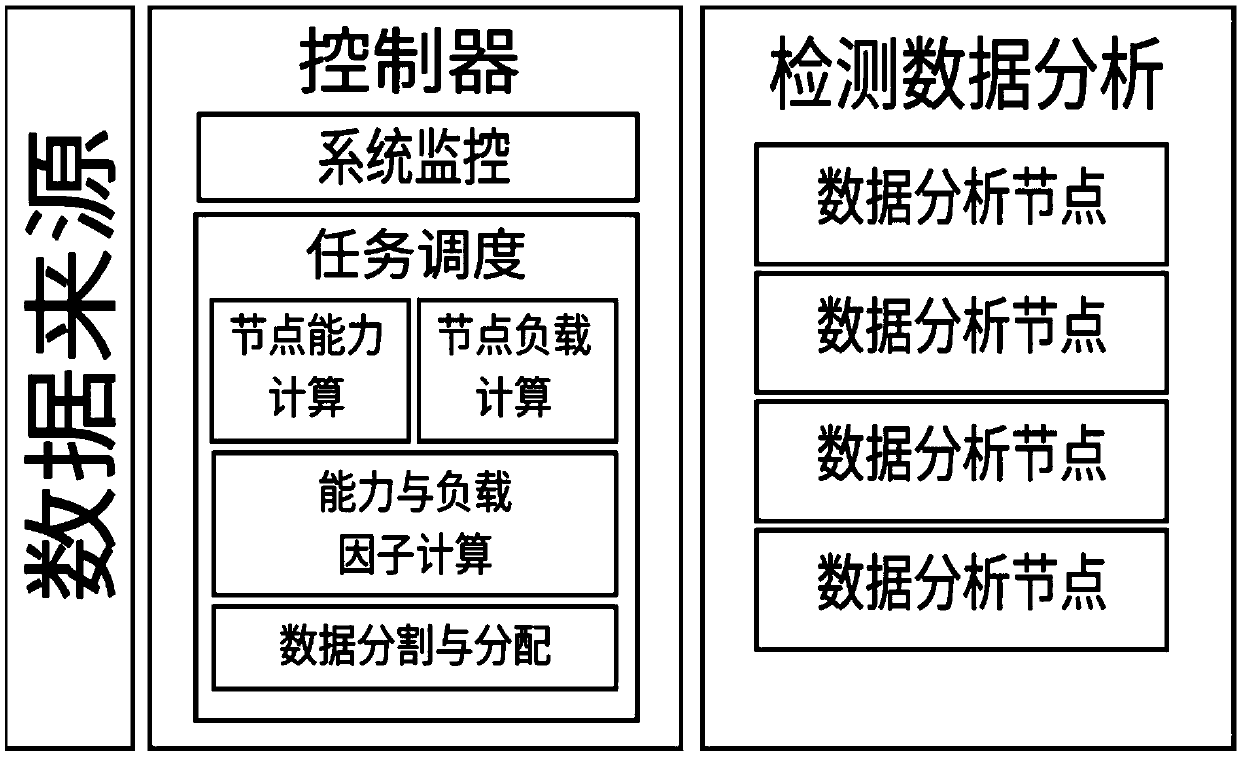
Data distribution method based on node data processing capability and node operation load
InactiveCN109600359AReduce parallel processing overheadImprove response efficiencyTransmissionClustered dataDistributed intrusion detection
The invention discloses a data distribution method based on node data processing capability and node operation load. The data distribution method comprises the following steps: step 1, measuring the processing capability of cluster data processing nodes; step 2, measuring the load of the cluster data processing nodes; step 3, calculating the load capacity weight of the cluster data processing nodes; and step 4, segmenting and distributing data. Under a high-speed distributed network environment, the parallel detection and processing efficiency of mass data is improved, the system detection time is shortened, the response efficiency of an intrusion detection system is improved, and the distributed intrusion detection capability is improved. According to the method, data segmentation and distribution can be matched with the working conditions of the nodes in the cluster in real time, and good load balance of the system is guaranteed. The parallel processing overhead of a distributed intrusion detection system is effectively reduced, the response efficiency of the intrusion detection system is improved, and the distributed intrusion detection capability is improved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
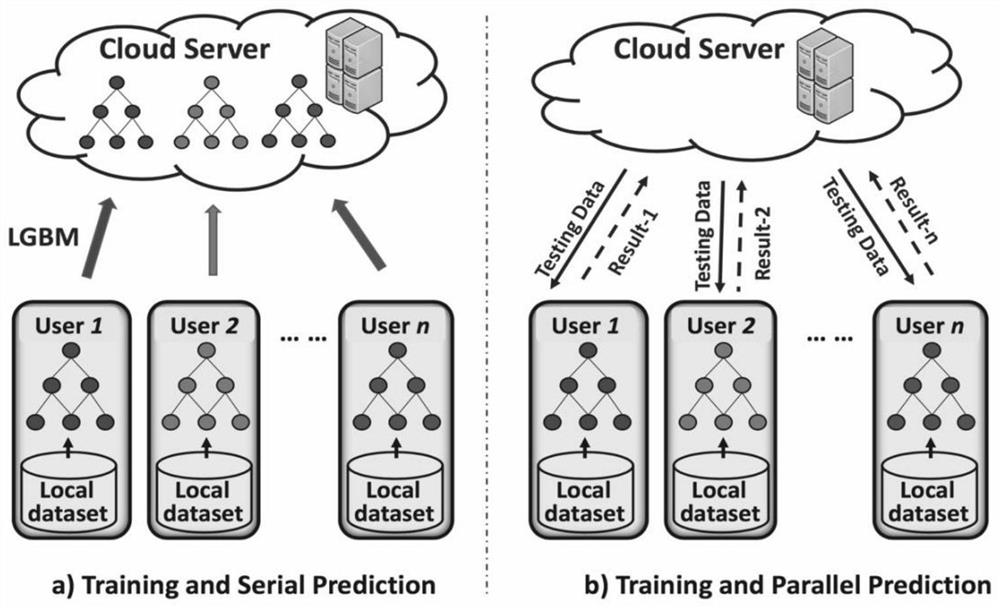
Lightweight distributed intrusion detection method
ActiveCN113688385AFast constructionFast predictionCharacter and pattern recognitionPlatform integrity maintainanceDistributed intrusion detectionGradient boosting
The invention proposes a lightweight distributed intrusion detection method, and the method comprises the steps of preparing local data for each client, wherein the local data is non-independent identically distributed non-IID flow data and corresponding intrusion detection classification labels; in the training stage, enabling each client to use local data to train a local lightweight gradient boosting machine LGBM, in the prediction stage, inputting test data to each trained LGBM, and obtaining an intrusion detection prediction result output by each LGBM; and after the server collects intrusion detection prediction results output by each LGBM, obtaining a final intrusion detection result aiming at the test data in a voting mode. According to the invention, a lightweight gradient lifting algorithm is introduced on the basis of a traditional decision tree method, and a large number of samples can be effectively processed on non-independent identically-distributed data by combining a decision tree trained by a user. Compared with an existing method based on federated learning, the framework achieves higher accuracy and lower overhead on independent identically distributed data and non-independent identically distributed data.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
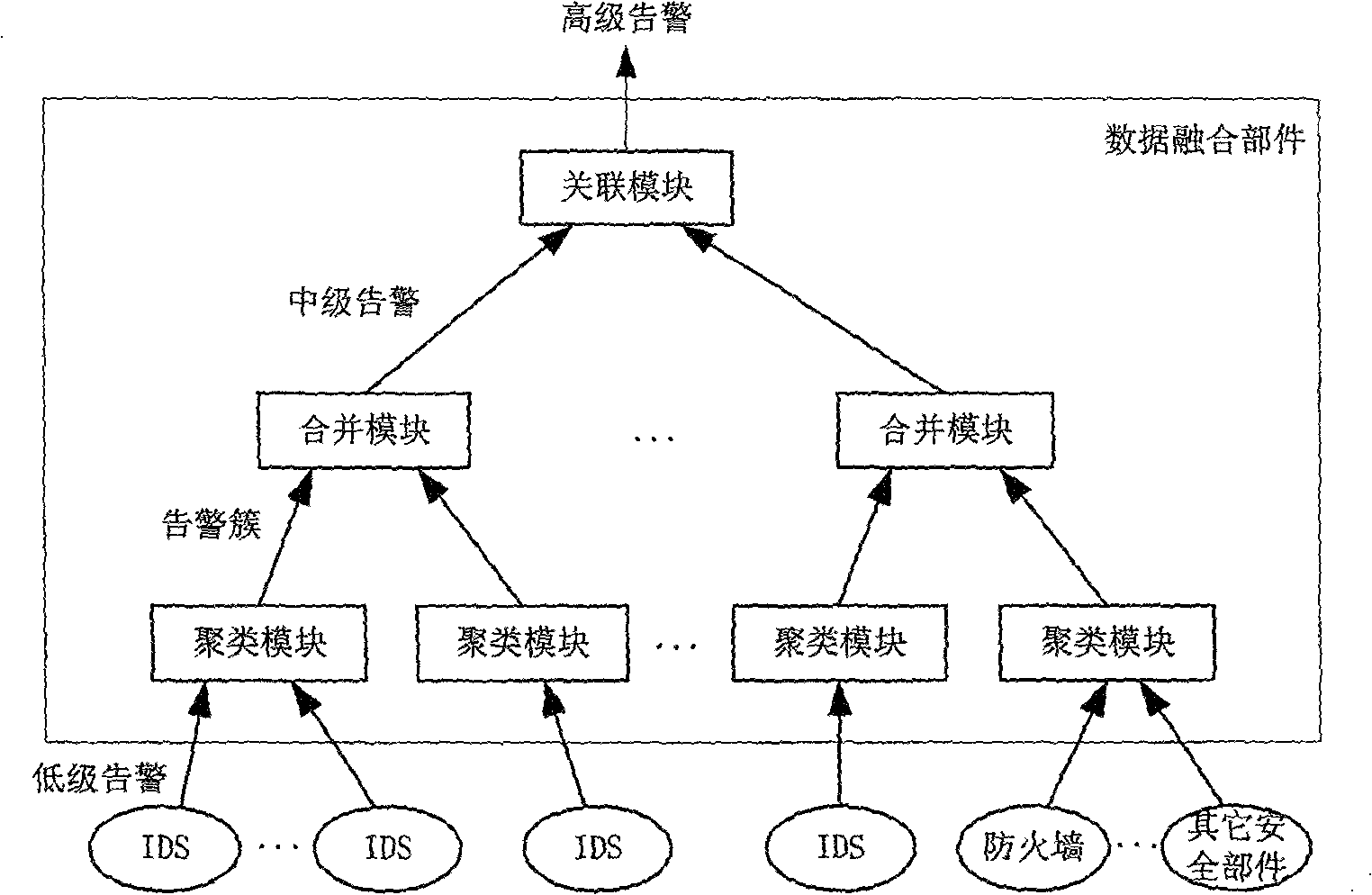
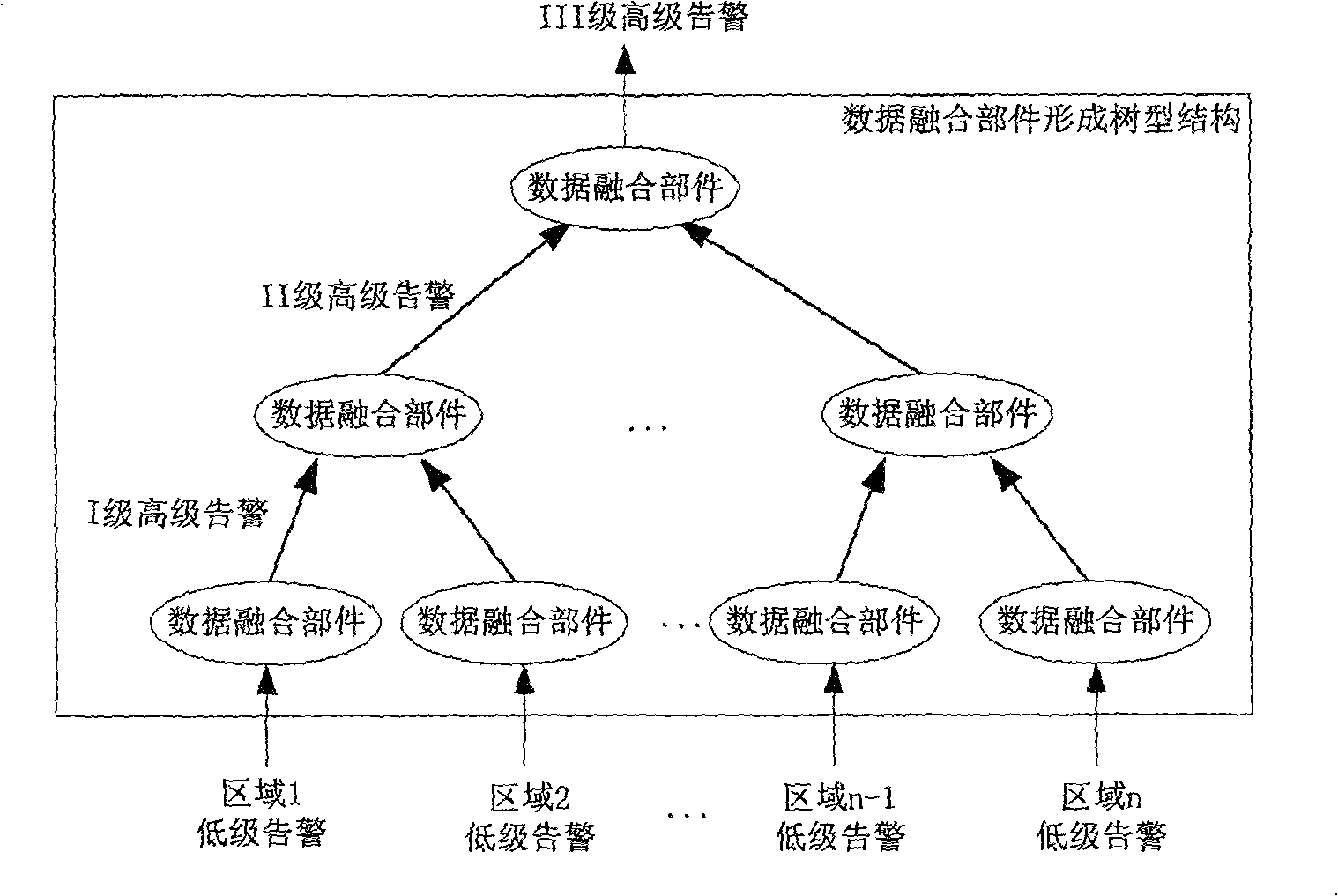
Data merging mechanism for large distributive intrusion inspecting system
InactiveCN100414868CUser identity/authority verificationData switching networksDistributed intrusion detectionReal-time data
The present invention is a real time warning merging system for a large scale distributive type of invasion detecting system. In a large scale high speed network, the invasion detecting system generally adopts the stratified distributive type of structure, which can meet the requirements of a large scale high speed network through the dispersive collection, the distributive process and the concentrative administration. In a large scale network there can be disposed a plurality of invasion detecting systems, each of which covers a part of the network, and other safety members such as fire wall and like. In order to obtain a global aeroview of invasion, all of these safety members must operate in coordination with each other.
Owner:BEIJING UNIV OF POSTS & TELECOMM
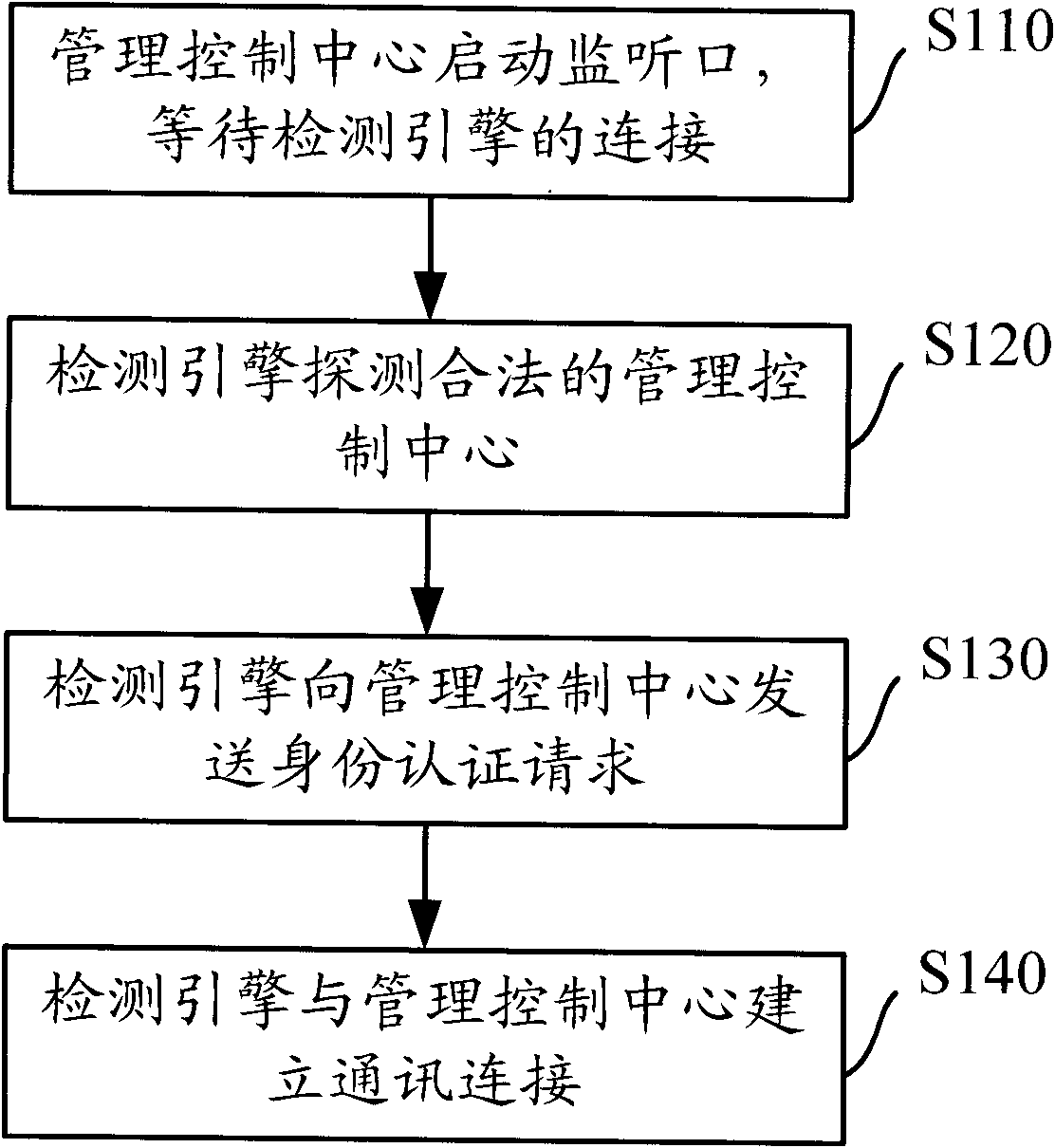
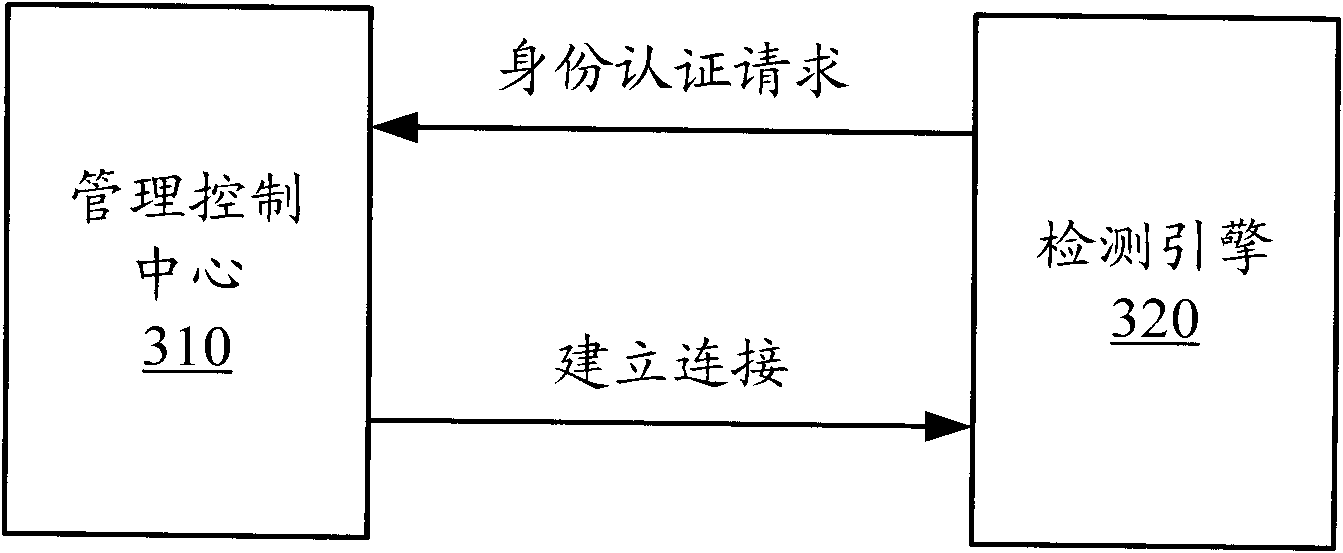
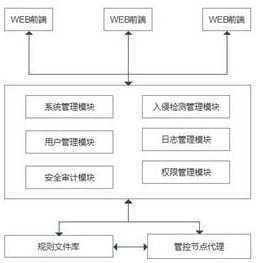
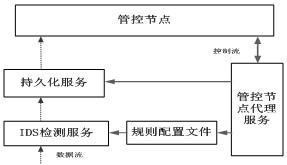
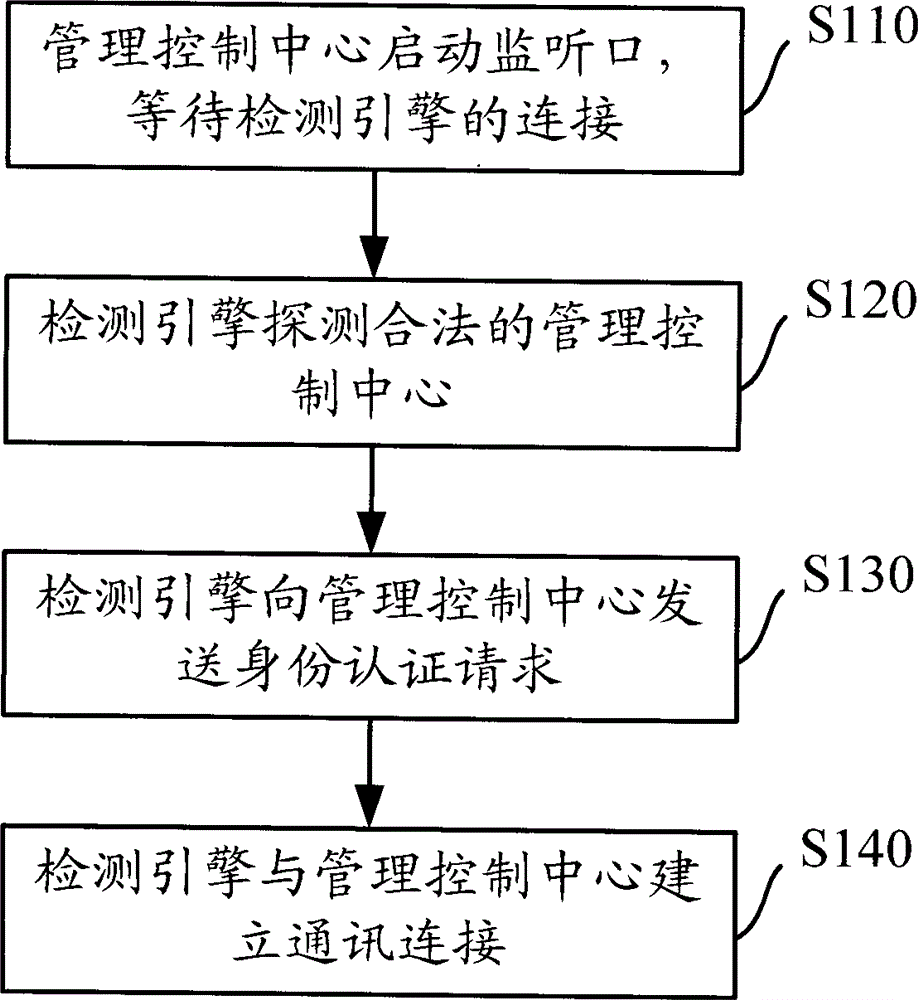
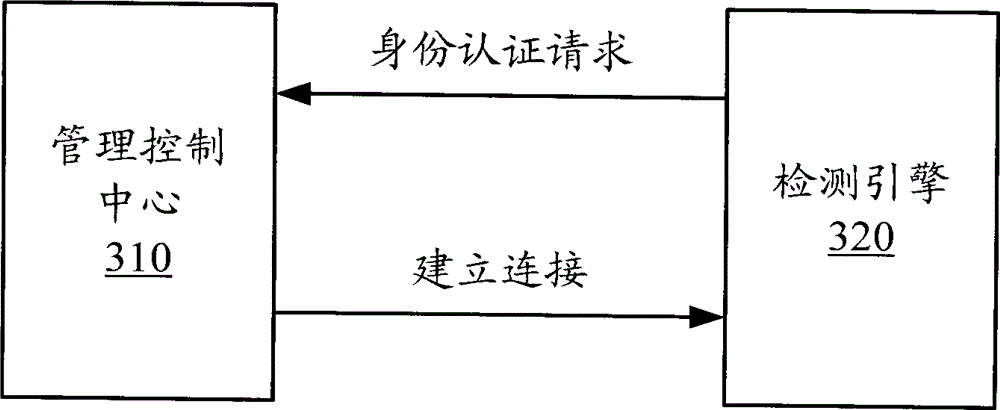
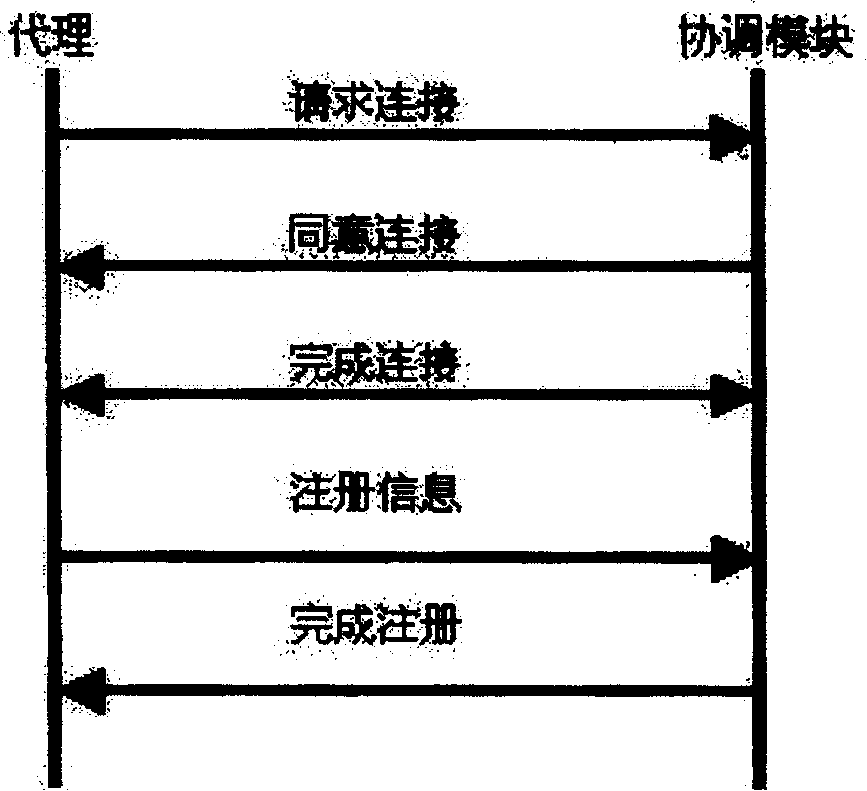
Distributed intrusion detection system and connecting method of centralized management in same
InactiveCN102148691AReduce complexityImprove securityData switching networksDistributed intrusion detectionWorkload
The invention discloses a distributed intrusion detection system and a connecting method of centralized management in the same, improving the security of a detection engine in the distributed intrusion detection system. The method mainly comprises the following steps of: starting a monitoring opening by a management control center; detecting the management control center by the detection engine; sending an identity authentication request to the management control center by the detection engine for identity authentication; and establishing communication connection between the detection engine and the management control center after the management control center is authenticated. Compared with the prior art, the technical scheme provided by the invention greatly lowers the communication management complexity of the distributed intrusion detection system, improves the security of the detection engine and reduces the workload of a system administrator.
Owner:BEIJING VENUS INFORMATION TECH +1
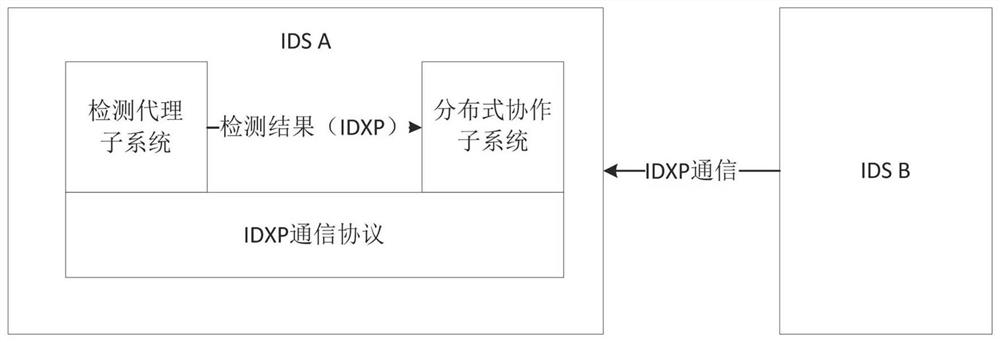
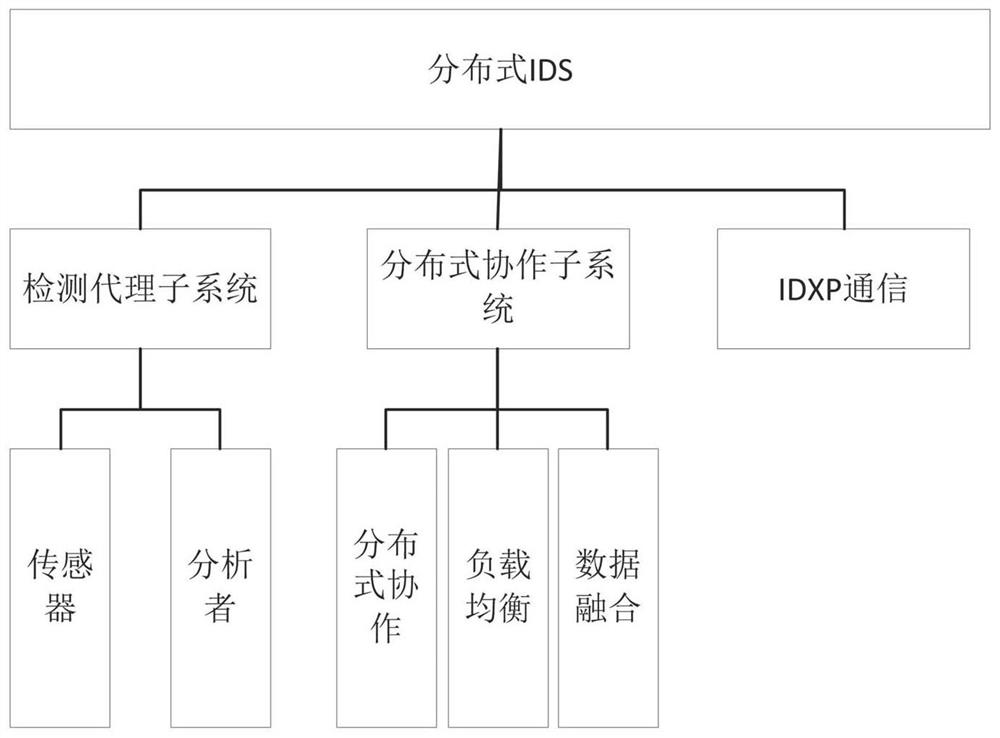
Correlation-based hierarchical distributed intrusion detection system
ActiveCN113965339AGuaranteed detection accuracyReduce the cost of distributed collaborationSecuring communicationDistributed intrusion detectionEngineering
The invention relates to a correlation-based hierarchical distributed intrusion detection system, which is technically characterized by comprising a plurality of intrusion detection systems; each intrusion detection system consists of a detection agent subsystem, a distributed cooperation subsystem and an IDXP communication protocol module; intrusion detection information interaction is carried out between the detection agent subsystem and the distributed cooperation subsystem and between the intrusion detection systems through the IDXP communication protocol modules; and the distributed cooperation subsystem is provided therein with a correlation-based distributed cooperation model. The system is reasonable in design, constructs a cooperation model based on the correlation between agents, uses an IDXP communication protocol in intrusion detection standardization, can effectively resist more and more complex attack means, effectively reduces the distributed cooperation cost of the system while guaranteeing the system detection accuracy, and has the characteristics of strong fault-tolerant capability, easy system expansion, wide detection range and the like.
Owner:TIANJIN QISUO PRECISION ELECTROMECHANICAL TECH
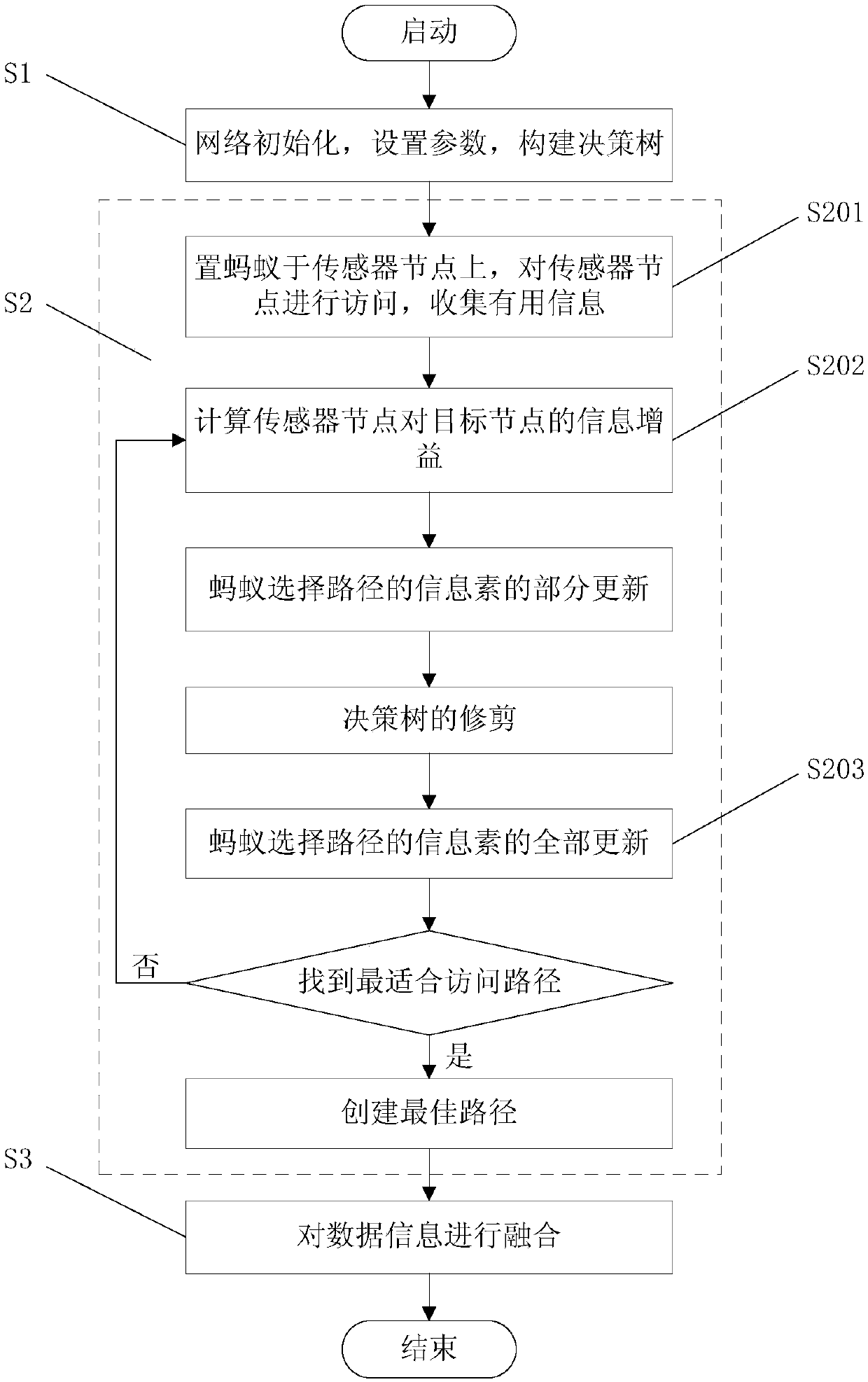
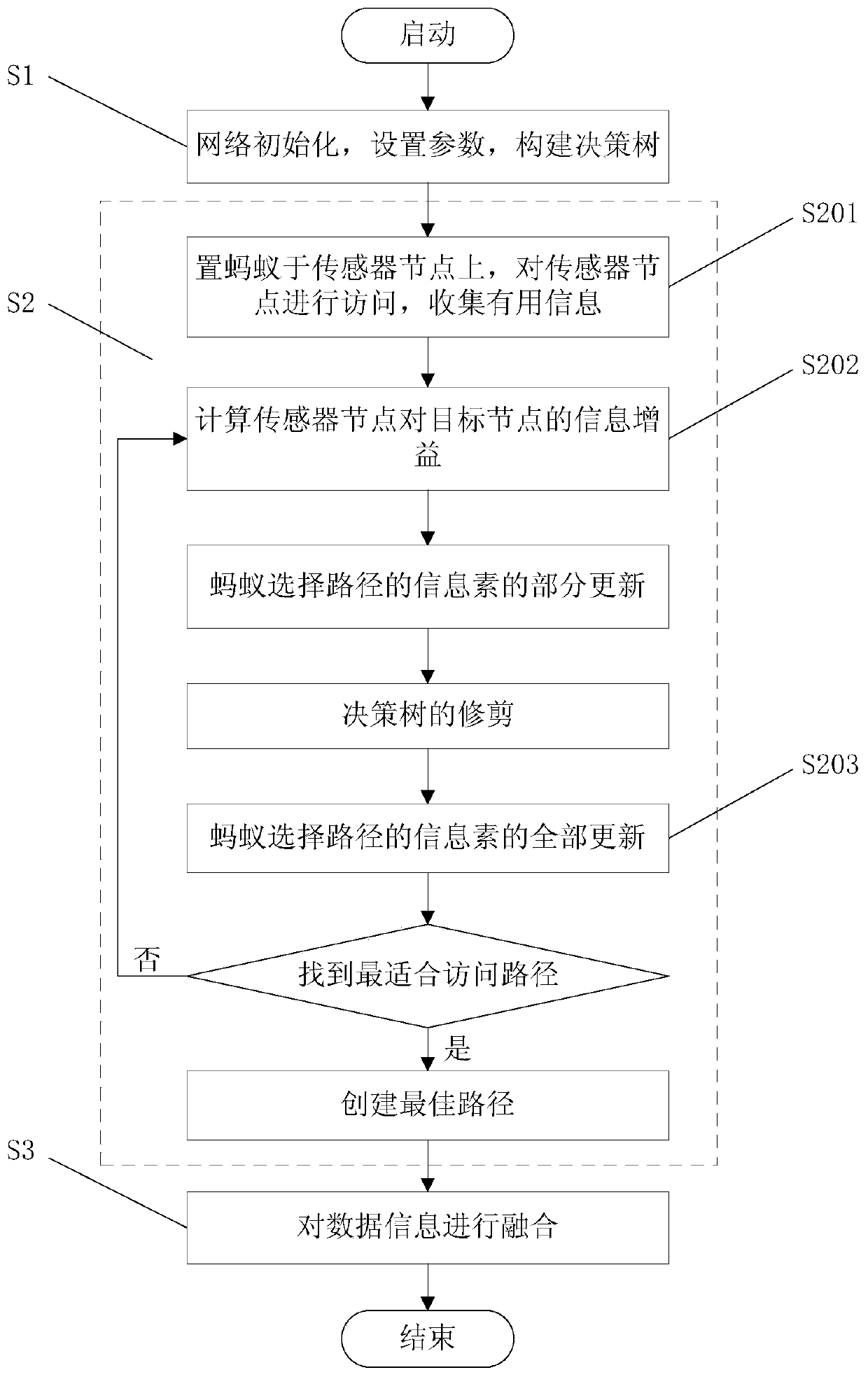
Distributed intrusion detection method based on ant colony algorithm
ActiveCN107612916AEnsure safetyImprove detection efficiencyForecastingTransmissionDistributed intrusion detectionData information
The invention discloses a distributed intrusion detection method based on an ant colony algorithm. The distributed intrusion detection method comprises the following processes: starting, initializinga distributed sensor, setting parameters of the ant colony algorithm based on attribute decision making, constructing a decision tree structure definition rule, setting ants on sensor nodes, determining a next node of data fusion, partially updating the information factors of an ant selection path, trimming the decision tree, and updating all information factors of the ant selection path, if an optimal path is not discovered, returning to the step of partially updating the information factors of the ant selection path; and finding the optimal path, creating the optimal path, and fusing data information. Compared with the prior art, the distributed intrusion detection method has the advantages of improving the detection efficiency of data intrusion in a network system, reducing the energy consumption and effectively guaranteeing the security of the distributed network system.
Owner:潘晓君
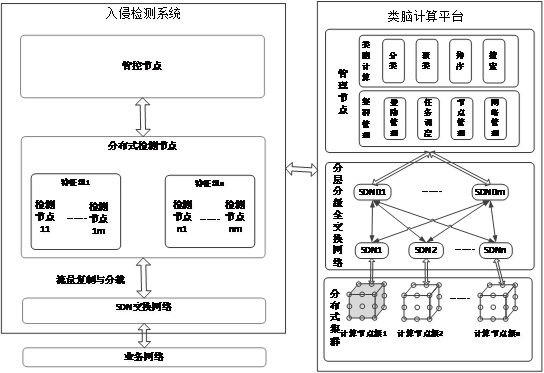
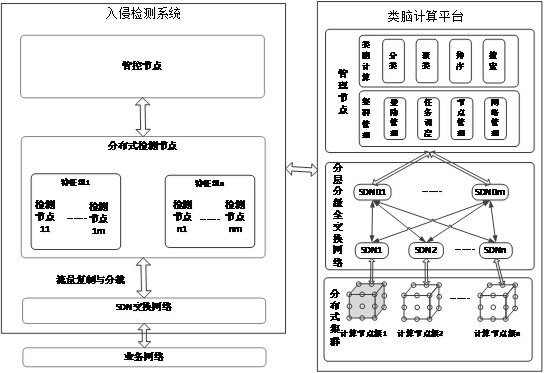
Intrusion detection system based on brain-like calculation
ActiveCN113283594AStrong computing powerQuick checkResource allocationNatural language data processingDistributed intrusion detectionExchange network
The invention discloses an intrusion detection system based on brain-like computing. The intrusion detection system comprises management and control nodes, distributed detection nodes, an SDN switching network and a brain-like computing platform; the management and control node is used for managing and controlling the distributed intrusion detection node; the distributed detection nodes are used for detecting the distributed network flow and judging whether an intrusion behavior occurs in real time in combination with the support of the brain-like computing platform; the SDN switching network is used for copying and / or distributing network traffic in a distributed manner; and the brain-like computing platform is used for providing computing power support for the management and control node, the distributed detection node and the SDN switching network. According to the invention, intelligent detection strategy management and control are realized, intelligent detection flow management and control are realized, and rapid real-time detection is realized.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Distributed Intrusion Detection System and Method Applied to Dynamic Virtualization Environment
InactiveCN103065086BSolve the problem of continuous monitoringSolve the problem of not being able to continuously monitor virtual machinesPlatform integrity maintainanceTransmissionDistributed intrusion detectionVirtualization
The invention provides a distributed intrusion detection system and a distributed intrusion detection method applied to dynamic virtualization environment. The system comprises a detection management center, and intrusion detection engines positioned on physical servers, wherein the detection management center is used for acquiring information of a source physical server and a target physical server to which the current virtual machine belongs before and after migration; a virtualization management server in a virtualization platform performs intrusion detection stop configuration on the intrusion detection engine on the source physical server and performs intrusion detection start configuration on the intrusion detection engine on the target physical server; and the intrusion detection engines are used for performing intrusion detection on specific virtual machines on the corresponding physical servers after an intrusion detection start safety strategy is configured, and stopping intrusion detection of the specific virtual machines on the corresponding physical servers after an intrusion detection stop safety strategy is configured. By the system and the method, the virtual machines can be continuously monitored.
Owner:BEIJING VENUS INFORMATION TECH +1
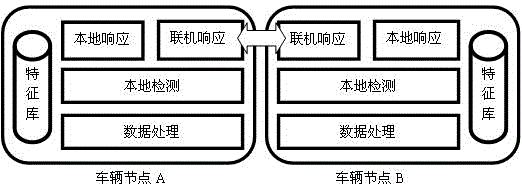
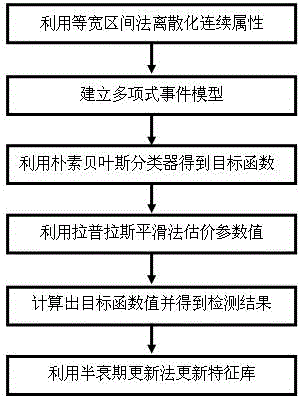
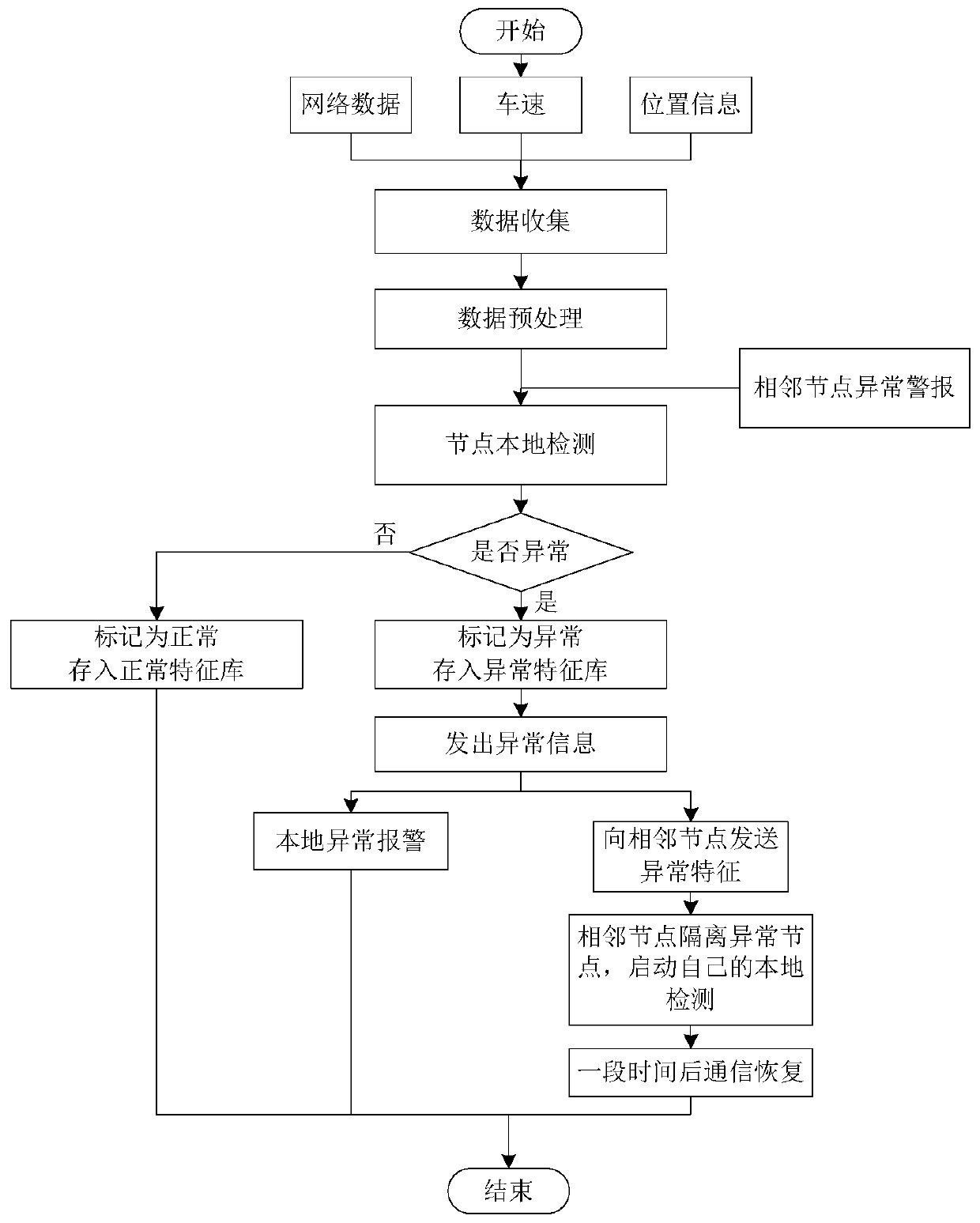
Distributed intrusion detection method of vehicle ad hoc network
InactiveCN103237308BImprove analysis and detection capabilitiesAdd network transfer functionData switching networksSecurity arrangementDistributed intrusion detectionSystem structure
The invention provides a distributed intrusion detection method of a vehicle ad hoc network. Local detection is started by adopting a Naive Bayesian classification algorithm by vehicle nodes; when an abnormal condition is detected, data are marked to be abnormal and are stored into a local feature library; response measures are immediately adopted by a local response module; meanwhile, abnormal warning is sent out to adjacent nodes and abnormal features are transmitted to the adjacent nodes through an on-line response module, if the adjacent nodes are also abnormal, the abnormal features are transmitted to the local feature library, and response measures are immediately adopted by the local response module; and meanwhile, the abnormal warning is sent to other adjacent nodes and the abnormal features are transmitted to the other adjacent nodes except source nodes of abnormal warning through the on-line response module; and abnormal warning and abnormal feature transmission are continuously passed through the manner, so that distributed intrusion detection of the whole vehicle ad hoc network is realized. With the adoption of the distributed intrusion detection method of the vehicle ad hoc network, analysis and detection ability of the whole vehicle ad hoc network is improved; and the distributed intrusion detection method has the characteristic of being simple in system structure, low in complexity, strong in learning and high in intelligentization degree.
Owner:XIHUA UNIV
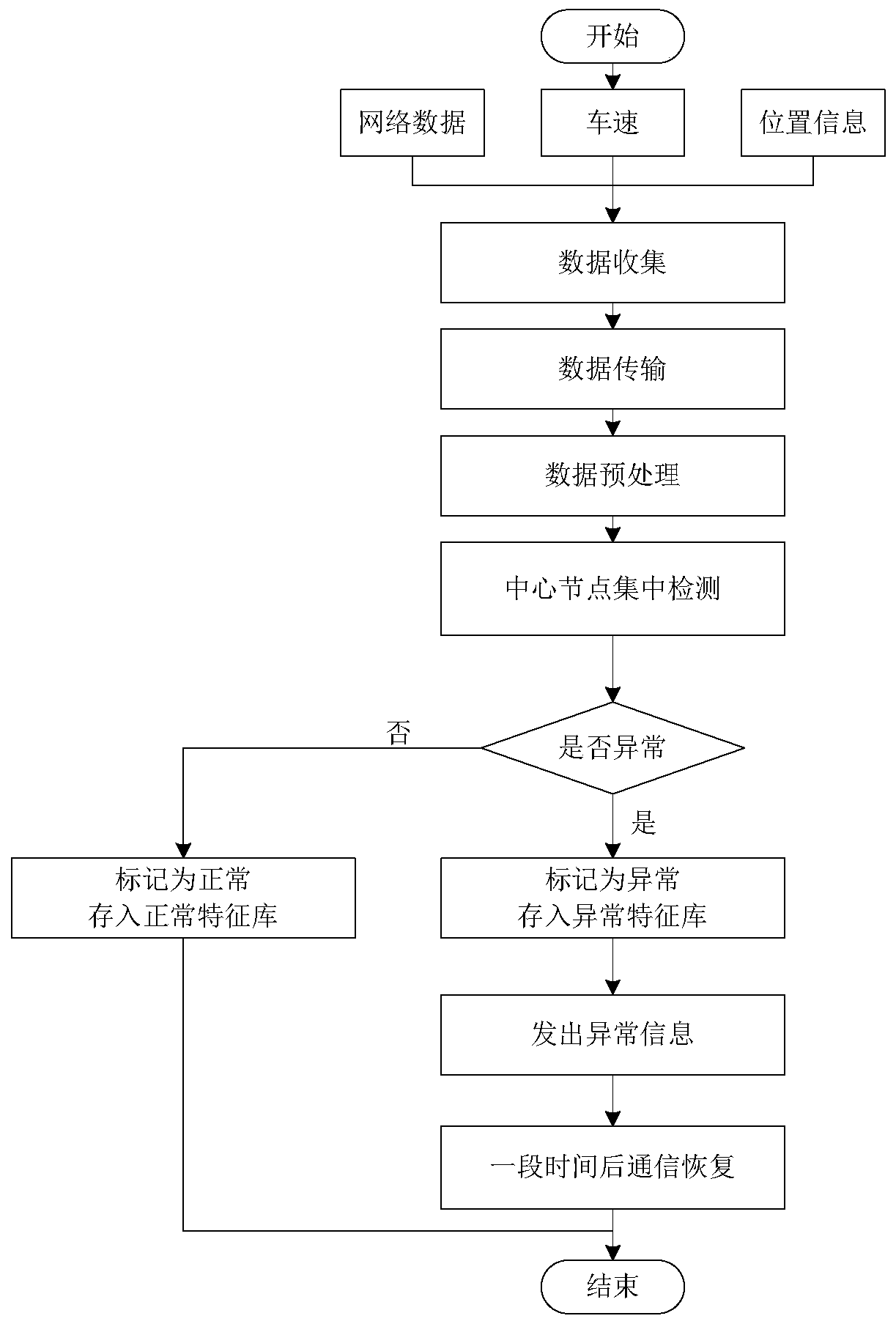
An abnormal intrusion detection method for Internet of Vehicles based on the difference of traffic flow density
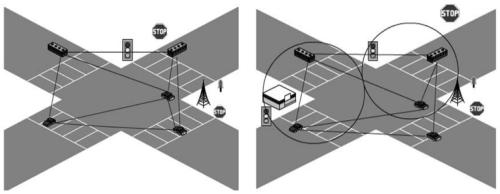
ActiveCN109005173BIntegrity guaranteedImprove efficiencyTransmissionDistributed intrusion detectionIn vehicle
The invention discloses a vehicle networking abnormal intrusion detection method based on traffic flow density difference, belonging to the field of vehicle networking and network intrusion detection.The invention is provided with an event analysis module in a vehicle-mounted unit and a roadside base station. Firstly, a distributed intrusion detection mechanism or a centralized intrusion detection mechanism is selected according to the difference of the actual traffic flow density in the road network. Then, the network information and traffic information in the vehicle node are obtained by the vehicle unit, and the anomaly intrusion detection in the vehicle network environment is realized by using the event analysis module of the vehicle computer or the roadbed computer and the weighted improved naive Bayesian algorithm to classify the information. The two detection mechanisms of the invention cooperate with each other so that the vehicle node can be detected under any moving speed, thus ensuring the integrity and high efficiency of the intrusion detection, and solving the problem that the traditional intrusion detection system is not adapted to the dynamic change of the vehicle networking communication and the network node moves quickly.
Owner:BEIHANG UNIV
Distributed intrusion detection system and connecting method of centralized management in same
InactiveCN102148691BReduce complexityImprove securityData switching networksDistributed intrusion detectionCentralized management
Owner:BEIJING VENUS INFORMATION TECH +1
Element identifier distribution method and application layer routing method based on element identifier
InactiveCN101577707BEasy to implementSave resourcesData switching networksDistributed intrusion detectionRouting table
The invention discloses an element identifier distribution method and an application layer routing method based on element identifier, which is applied in centralized-management multilayer distributed systems. In the method, node elements and element identifier of each level of a distributed system are established layer by layer; a routing table item based on the element identifier is generated in the process of generating and distributing the element identifier; and addressing is performed through the element identifier during communication so as to realize application layer routing based on the element identifier, which is needed by the communication of the centralized-management distributed system. The invention also provides a plurality of default routing rules of the routing method. The application layer routing method which is generated in the invention and based on element identifier is unrelated to TCP / IP (Transmission Control Protocol / Internet Protocol) routing methods, has the characteristics of simplicity, practicability, stability, reliability and resource conservation, and can meet special needs of distributed intrusion detection systems, distributed network auditing systems and various centralized-management multilayer distributed systems.
Owner:BEIJING VENUS INFORMATION TECH
An Intrusion Detection System Based on Brain-like Computing
ActiveCN113283594BStrong computing powerQuick checkResource allocationNatural language data processingDistributed intrusion detectionInternet traffic
The invention discloses an intrusion detection system based on brain-inspired computing, which includes management and control nodes, distributed detection nodes, an SDN switching network, and a brain-inspired computing platform; the management and control nodes are used to manage and control distributed intrusion detection nodes; The distributed detection node is used to detect the allocated network traffic, and combined with the support of the brain-inspired computing platform, judges in real time whether there is an intrusion behavior; the SDN switching network is used to replicate and / or distribute the network traffic distribution; the brain-inspired computing platform is used to provide computing power support for the management and control nodes, the distributed detection nodes, and the SDN switching network. The invention realizes intelligent detection strategy management and control, intelligent detection flow control and rapid real-time detection.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Distributed Intrusion Detection Method Based on Ant Colony Fusion Algorithm
ActiveCN107612916BEnsure safetyImprove detection efficiencyForecastingTransmissionDistributed intrusion detectionData information
The invention discloses a distributed intrusion detection method based on an ant colony algorithm. The distributed intrusion detection method comprises the following processes: starting, initializinga distributed sensor, setting parameters of the ant colony algorithm based on attribute decision making, constructing a decision tree structure definition rule, setting ants on sensor nodes, determining a next node of data fusion, partially updating the information factors of an ant selection path, trimming the decision tree, and updating all information factors of the ant selection path, if an optimal path is not discovered, returning to the step of partially updating the information factors of the ant selection path; and finding the optimal path, creating the optimal path, and fusing data information. Compared with the prior art, the distributed intrusion detection method has the advantages of improving the detection efficiency of data intrusion in a network system, reducing the energy consumption and effectively guaranteeing the security of the distributed network system.
Owner:潘晓君
Flow characteristic analysis-based distributed intrusion detection method
InactiveCN101980506BAccurate detectionAccurate monitoringTransmissionDistributed intrusion detectionRelevant information
The invention discloses a flow characteristic analysis-based distributed intrusion detection method. The method comprises the following steps of: performing intrusion detection based on a JADE platform by using an intelligent decision analysis agent and a data acquisition and independent intrusion condition monitoring agent; detecting a definite network intrusion action for an intrusion characteristic by using the data acquisition and independent intrusion condition monitoring agent; and comprehensively monitoring different statistical characteristic quantities comprising a flow bandwidth, a new source IP (Internet protocol) address and the like in network flow by using the intelligent decision analysis agent through an improved non-parameter cumulative sum (CUSUM) algorithm, namely, a threshold regression algorithm and realizing network abnormity detection in combination with related information transmitted by the data acquisition and independent intrusion condition monitoring agent so as to effectively enhance intrusion detection efficiency and accuracy. In the method, different network flow models can be differentiated effectively by monitoring the new source IP address, so that the misstatement rate of the intrusion detection system is further lowered.
Owner:BEIHANG UNIV
Distributed intrusion detection method, device and system
InactiveCN101997830BReduce frequencyGuaranteed reliabilitySecuring communicationDistributed intrusion detectionNetwork communication
The invention relates to the field of network communication, in particular to a distributed intrusion detection method, a distributed intrusion detection device and a distributed intrusion detection system. The method comprises the following steps of: acquiring own flow information and generating a flow table; calculating early warning information according to the flow table; when the flow table only comprises own flow information or when the early warning information meets neighbor communication conditions, acquiring the flow information of a neighbor node and flow information acquisition time, and updating the flow table and the early warning information; when the early warning information meets global communication conditions, acquiring the flow information of a global node and the flow information acquisition time, and updating the flow table and the early warning information; and when the early warning information meets early warning conditions, performing intrusion early-warning. In the technical scheme provided by the embodiment of the invention, only the flow information of the neighbor node needs acquiring when the early warning information meets the neighbor communication conditions, so the data traffic in distributed intrusion detection is reduced and the influence of the distributed intrusion detection on network performance is reduced.
Owner:HUAWEI TECH CO LTD +1
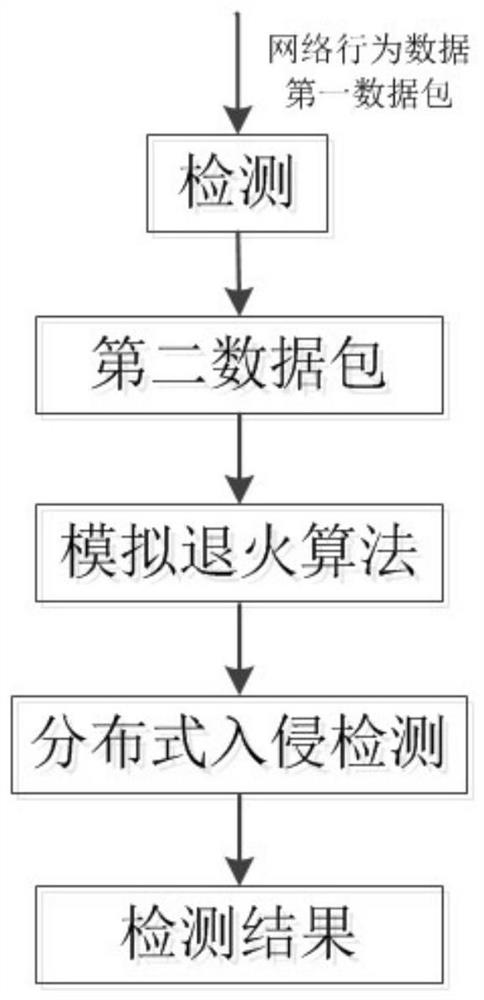
Distributed intrusion detection method and system based on simulated annealing fusion algorithm
InactiveCN111625818AImprove accuracyImprove execution efficiencyCharacter and pattern recognitionPlatform integrity maintainanceDistributed intrusion detectionData pack
The invention provides a distributed intrusion detection method and system based on a simulated annealing fusion algorithm. Specifically, a first data packet of a current network behavior is acquiredin real time and initial detection is performed, whether a second data packet after initial detection is abnormal is judged based on a simulated annealing algorithm, and if the second data packet after initial detection is abnormal, the abnormal data packet is analyzed and network behavior detection result data based on different categories is generated. According to the invention, the final detection result data is obtained through dual detection and correlation analysis processing, the global optimization capability of simulated annealing is fully utilized, and the accuracy and execution efficiency of the intrusion detection model are improved.
Owner:潘晓君
DIDS theoretical modeling method for detecting different engine processing capacities
ActiveCN112291217ASolve the limitations of modeling methods with the same processing powerFacilitate decision-makingPlatform integrity maintainanceData switching networksDistributed intrusion detectionData pack
The invention discloses a DIDS theoretical modeling method for detecting different engine processing capacities. The DIDS theoretical modeling method specifically comprises the following steps: step 1, performing model analysis and parameter setting on a distributed intrusion detection system; 2, performing state space analysis on the distributed intrusion detection system; and 3, calculating theaverage busy detection engine number in the distributed intrusion detection system, the average queue length of the data packets in the waiting queue, the average stay time of the data packets in thesystem and the average queuing waiting time of the data packets in the system. By adopting a method for establishing a model, necessary parameters such as the average busy detection engine number andthe average queue length in the waiting queue in the operation process of DIDS with different detection engine processing capacities can be mastered, and decision making and optimization on the basisare facilitated.
Owner:陕西边云协同网络科技有限责任公司
Task assigning mechanism for large-scale distributive invasion detecting system
InactiveCN100385392CTo achieve load balancingSolve the detection accuracy is not highSpecific program execution arrangementsSpecial data processing applicationsDistributed intrusion detectionComputer architecture
In large-scale high speed network, the invasion detecting system adopts always hierarchical distributive structure including dispersive acquisition, distributive processing and concentrated management. In the hierarchical modular structure, deputy technology is always adopted and the coordinating module in the coordinating management layer assigns and controls the deputies. In abnormal case that the static deputy in the lower layer can not settle, some request is sent to the coordinating module, and the coordinating module assigns movable deputy with specific function to the static deputy for complete the task before the cancel request is sent and the cancel command is sent separately to finish the assignment mechanism. The mechanism can balance the system load, respond timely, complete specific data processing function and make the movable deputy controllable.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Distributed intrusion detection method based on multilayer extreme learning machine in Internet of Things environment
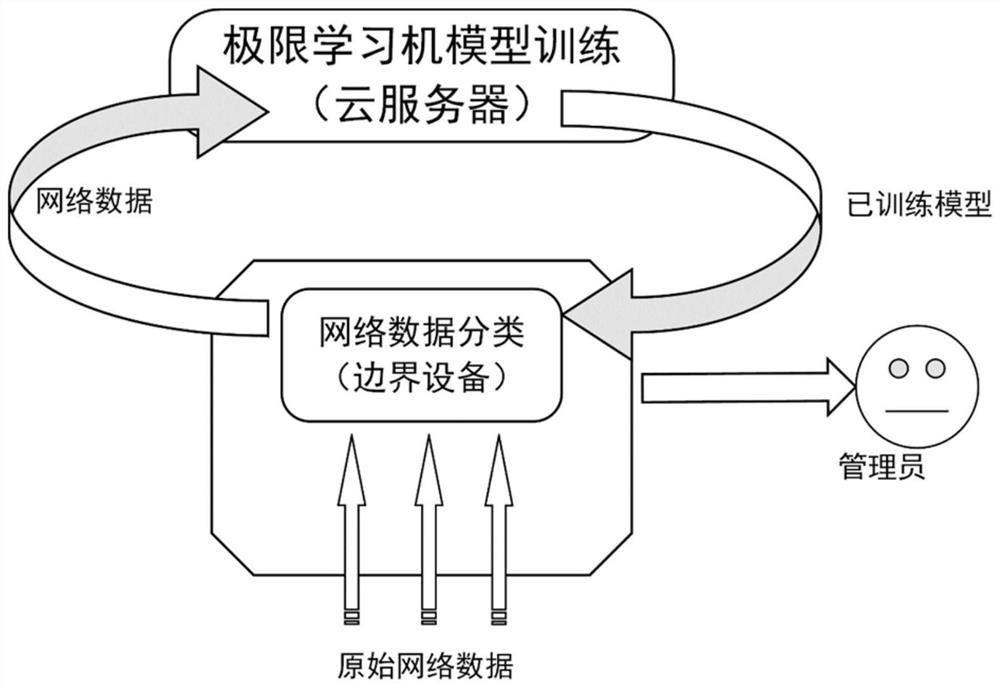
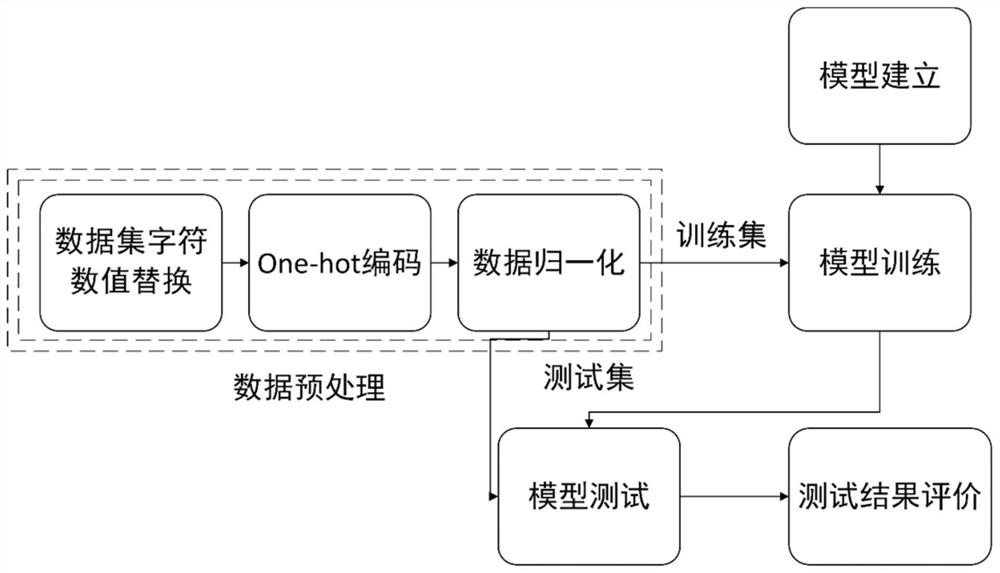
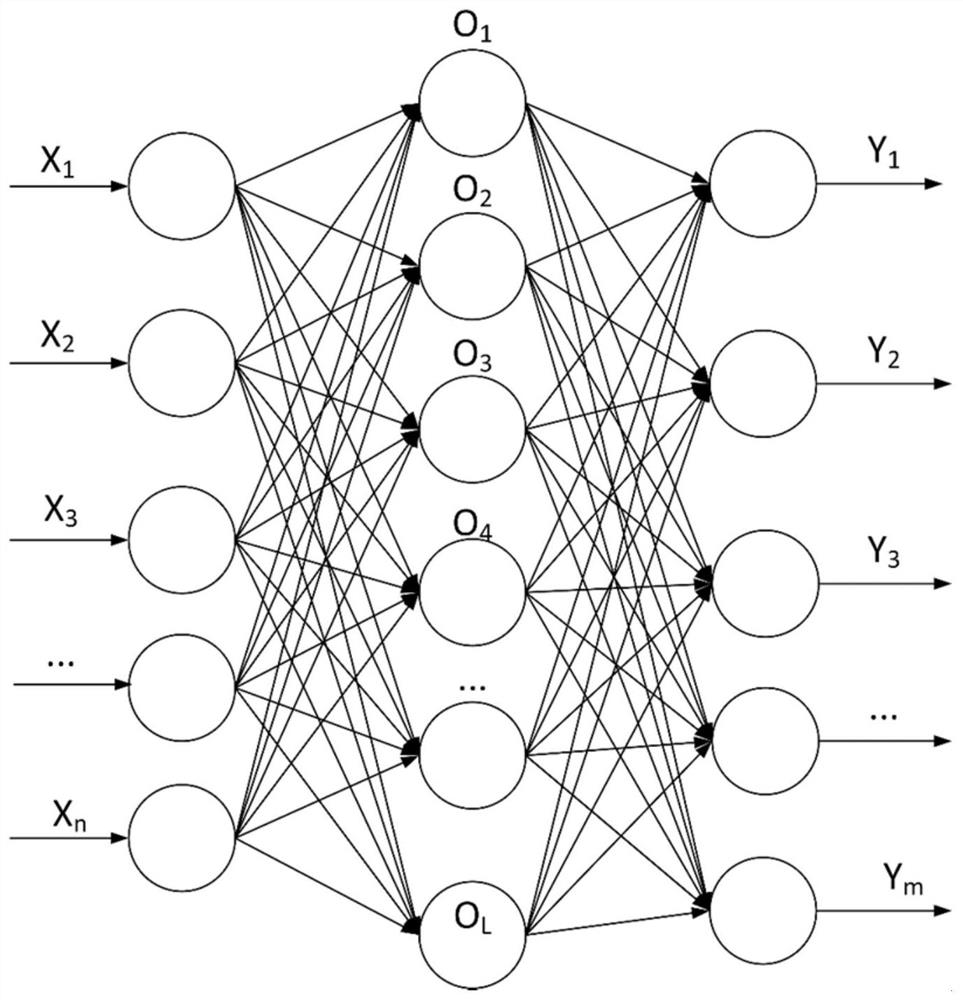
ActiveCN112653751AImprove efficiencyLower performance requirementsNeural architecturesData switching networksLearning machineAttack
The invention discloses a distributed intrusion detection method based on a multi-layer extreme learning machine in an Internet of Things environment, and aims to move tasks with heavier calculation for realizing automatic attack detection to boundary equipment due to the characteristic that resources of related equipment are constrained, so as to enable a processing function to be close to a data source. The boundary devices can operate a preset classification model. However, when facing a large amount of training data, there is no sufficient storage and processing capabilities to construct and upgrade such models. In order to solve the problem, training operation with dense calculation and large storage capacity is moved to a cloud server to be carried out, and a single-hidden-layer extreme learning machine model and a multi-hidden-layer extreme learning machine model are constructed and trained in the cloud server, so that boundary equipment executes flow classification based on a deep learning model preset in the cloud server; therefore, whether the traffic is normal traffic or network attack is classified, and experimental analysis shows that the multi-hidden-layer extreme learning machine has better performance.
Owner:HANGZHOU DIANZI UNIV +1
Zombie machine detection method based on alarm association
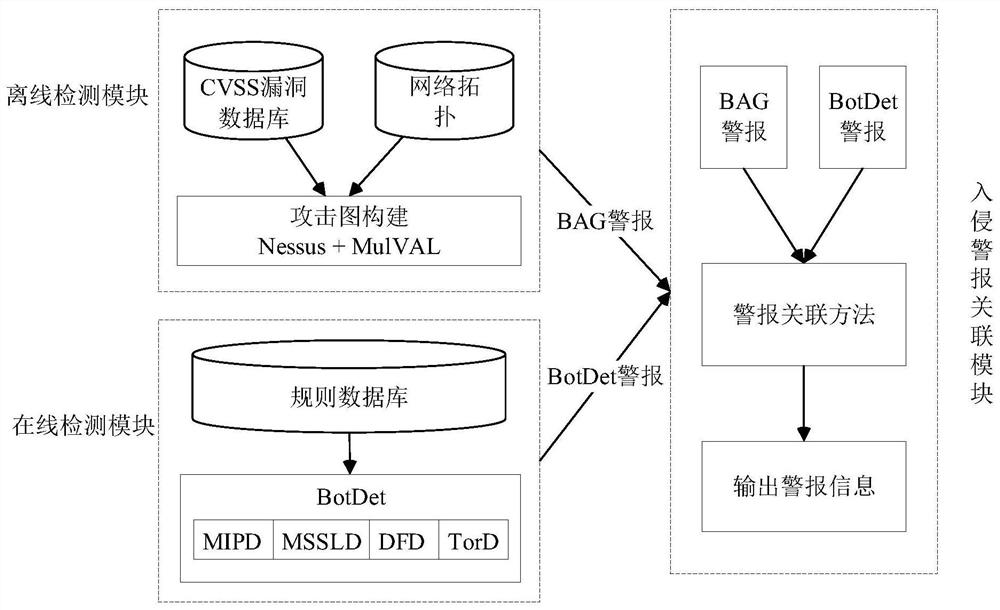
ActiveCN111931168AEfficient detectionReduce false alarm rateCharacter and pattern recognitionPlatform integrity maintainanceDistributed intrusion detectionAnomaly detection
The invention discloses a distributed intrusion detection method based on alarm association in a cloud environment. The method comprises the following steps: collecting intrusion evidences; establishing a distributed behavior diagram template; carrying out anomaly detection; carrying out behavior graph template update. Distributed detection in the cloud environment is achieved in a clustering mode, further intrusion detection judgment is achieved based on the thought of alarm association, and the false alarm rate can be reduced. By means of the method, zombie machines in the cloud environmentcan be effectively detected, and therefore cloud computing resources are protected against malicious utilization.
Owner:HOHAI UNIV CHANGZHOU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com