Distributed intrusion detection method based on multilayer extreme learning machine in Internet of Things environment
An extreme learning machine and intrusion detection technology, applied in the field of intrusion detection and deep learning, can solve problems such as inability to process training data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] The present invention will be further described below in conjunction with embodiment, detailed description is as follows:
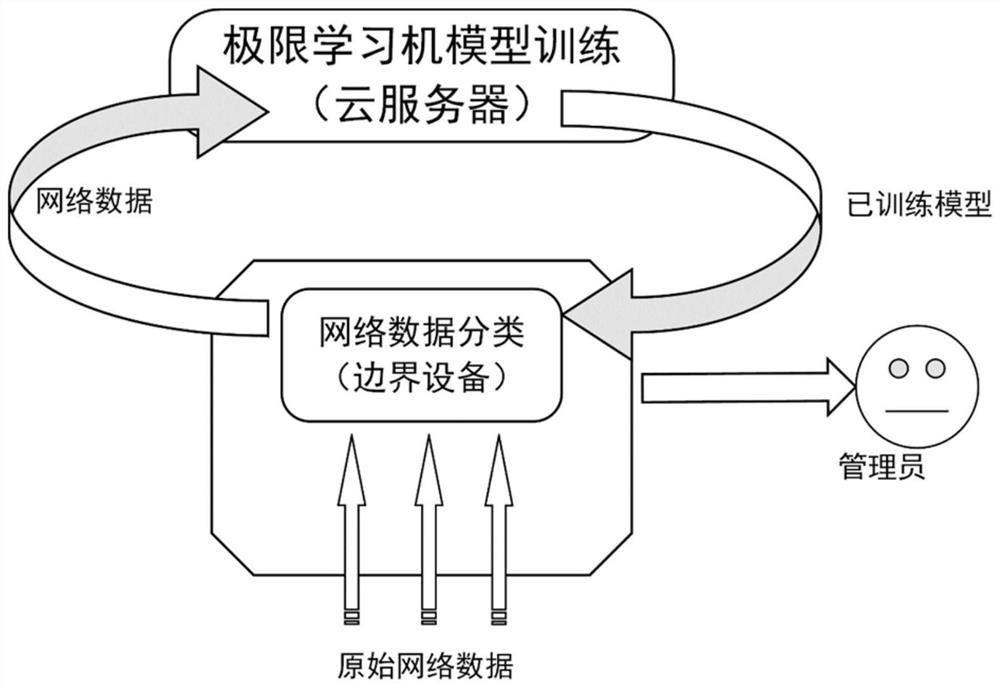
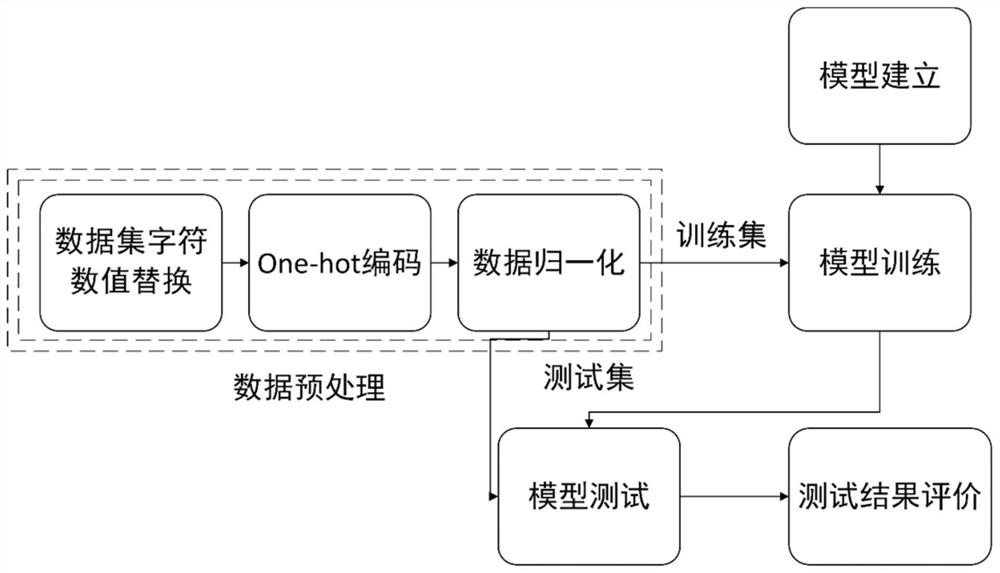
[0073] The overall structure of the intrusion detection of the present invention is shown in the accompanying drawings figure 1 As shown, the architecture is divided into two parts, the edge device and the cloud server. The border device is preset with a model trained by the cloud server. Its function is to preprocess and classify the original network data. If the classification result is abnormal, the administrator will be notified; the cloud server accepts the network data transmitted by the border device and uses the data to perform Model training, and then distribute the newly trained model to the border devices to update the model. The following is a detailed description of the experimental part, and the experimental flow chart can refer to the attached figure figure 2 .
[0074] Step 1, preprocessing the network traffic data.
[0075] St...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com