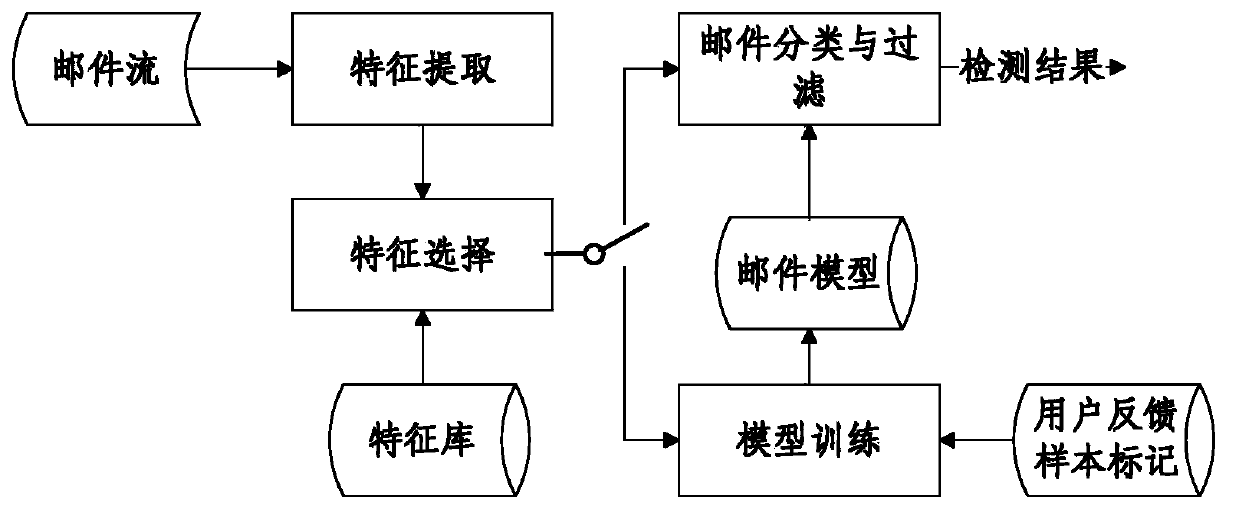
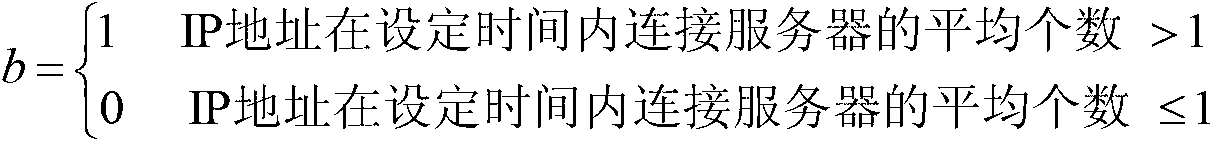Patents
Literature
95 results about "Zombie" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, a zombie is a computer connected to the Internet that has been compromised by a hacker, computer virus or trojan horse program and can be used to perform malicious tasks of one sort or another under remote direction. Botnets of zombie computers are often used to spread e-mail spam and launch denial-of-service attacks (DOS attacks). Most owners of "zombie" computers are unaware that their system is being used in this way. Because the owner tends to be unaware, these computers are metaphorically compared to fictional zombies. A coordinated DDoS attack by multiple botnet machines also resembles a "zombie horde attack", as depicted in fictional zombie films.
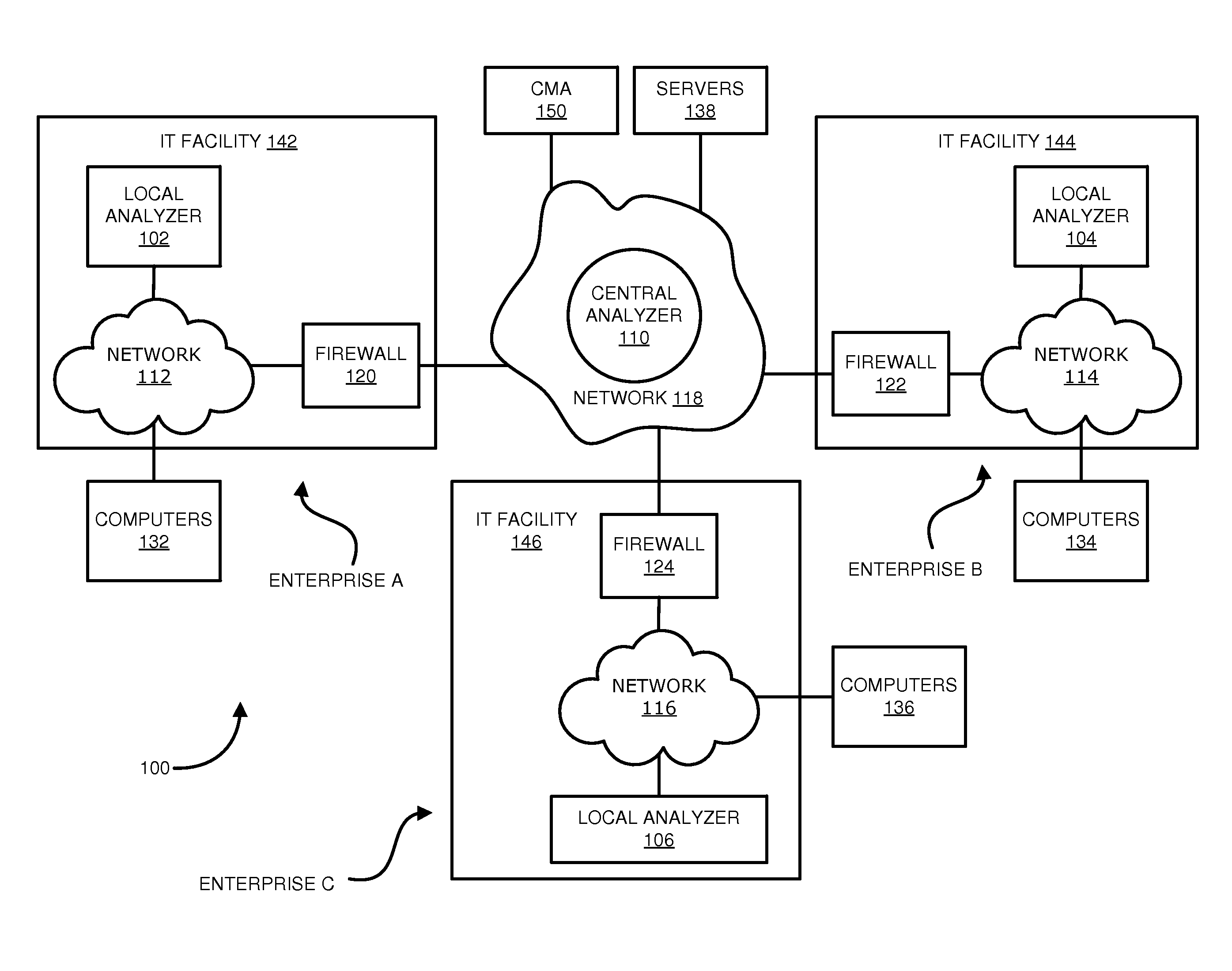
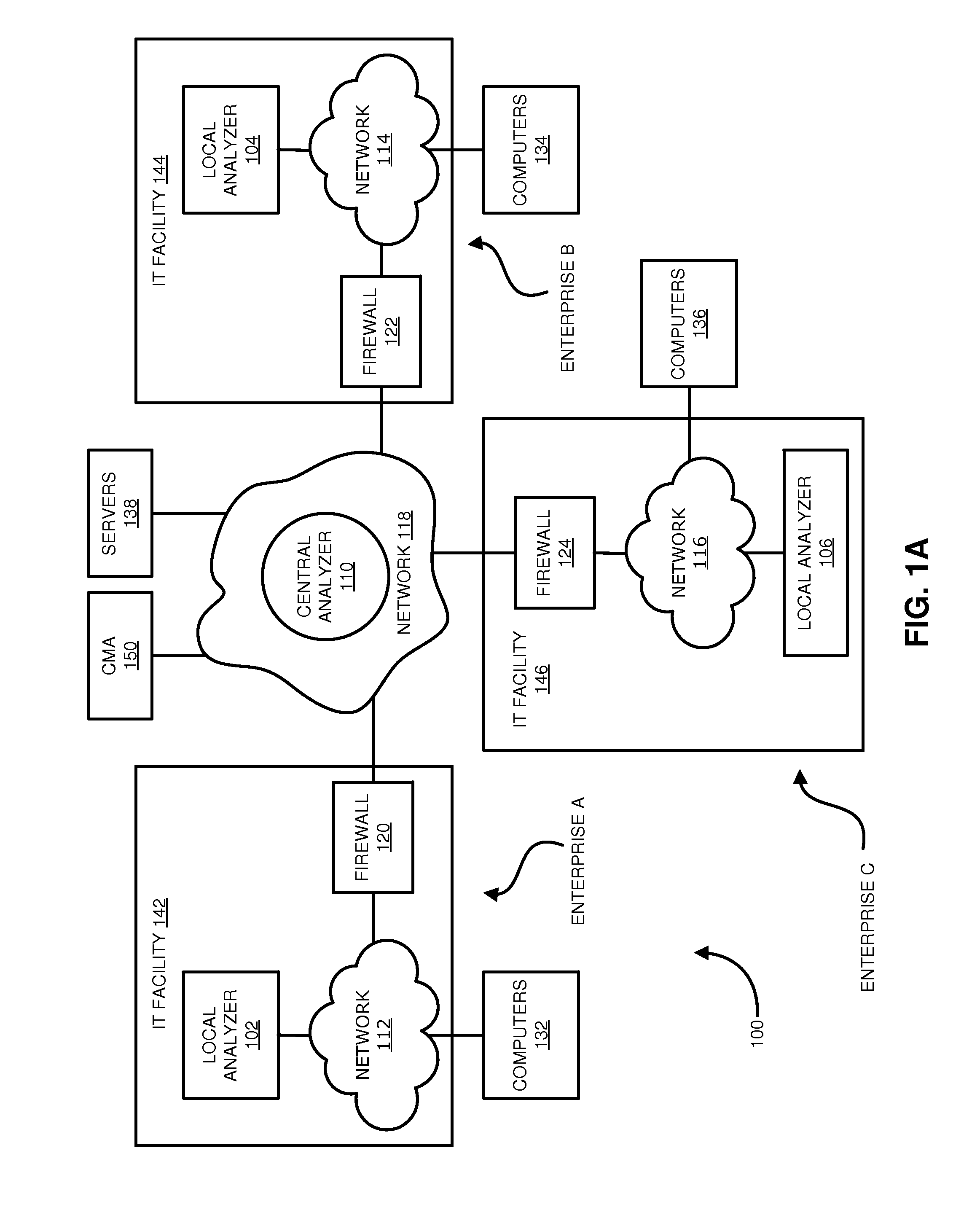
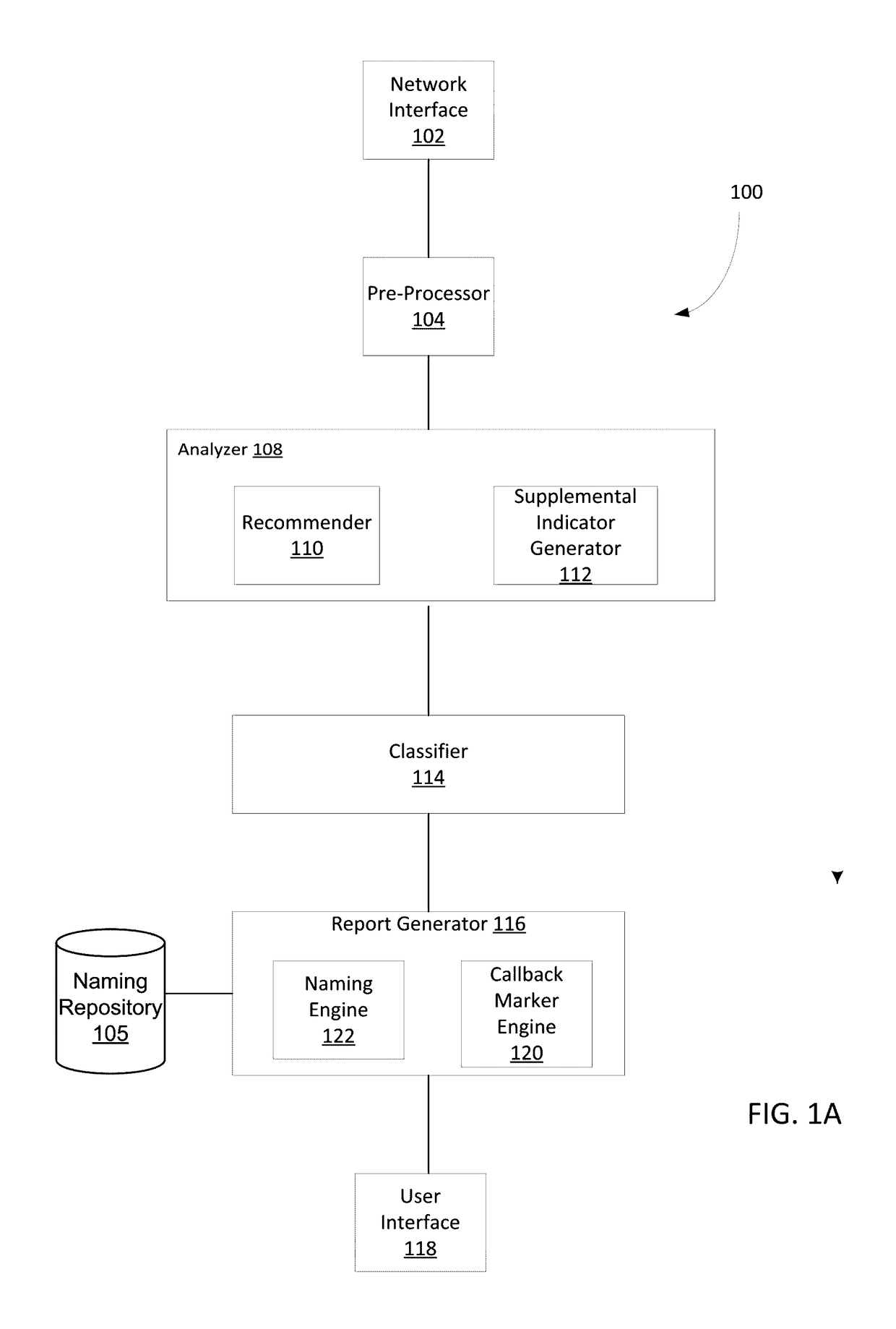
Distributed systems and methods for automatically detecting unknown bots and botnets
ActiveUS9430646B1Error detection/correctionPlatform integrity maintainanceOutbound communicationCommand and control
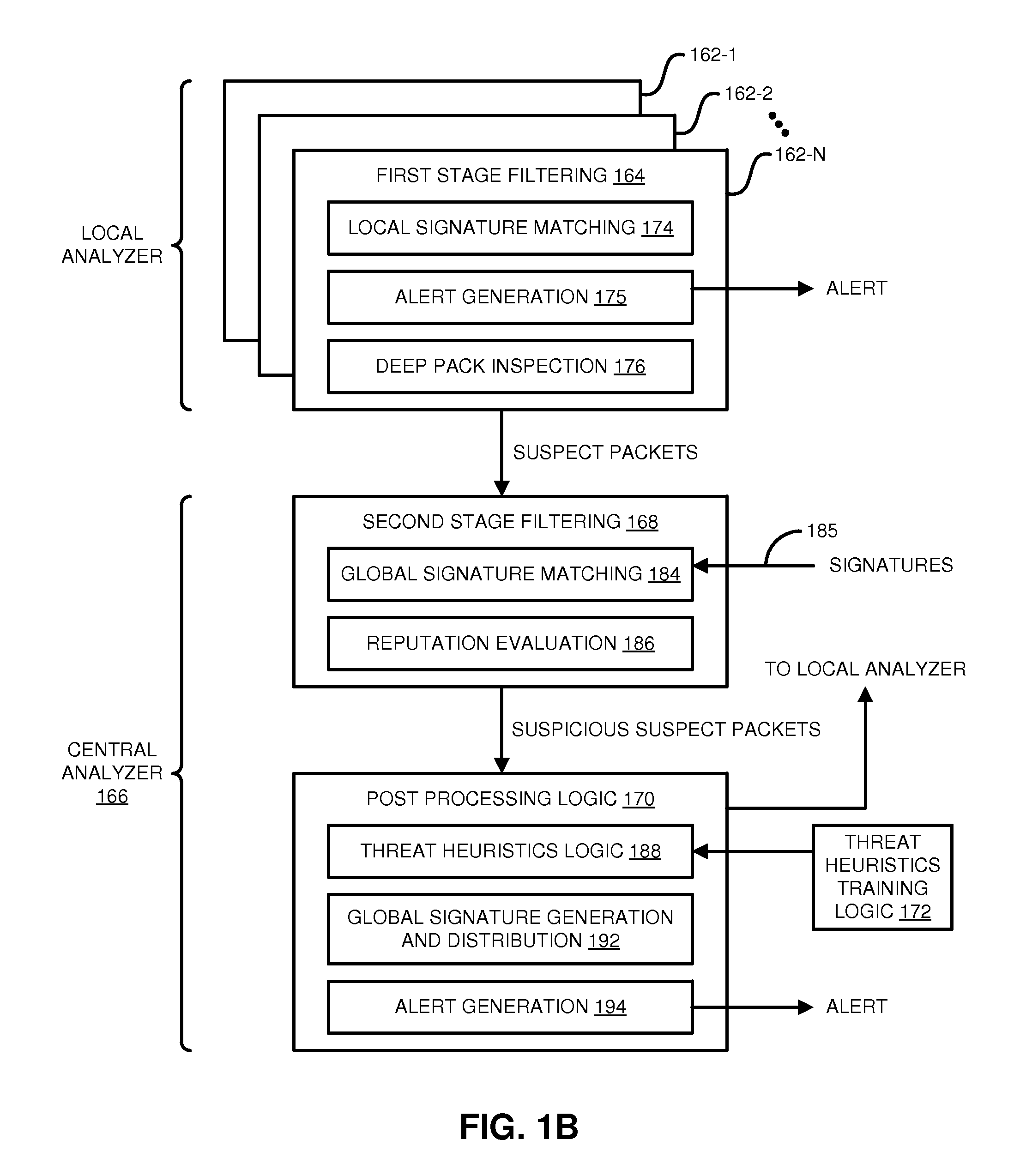
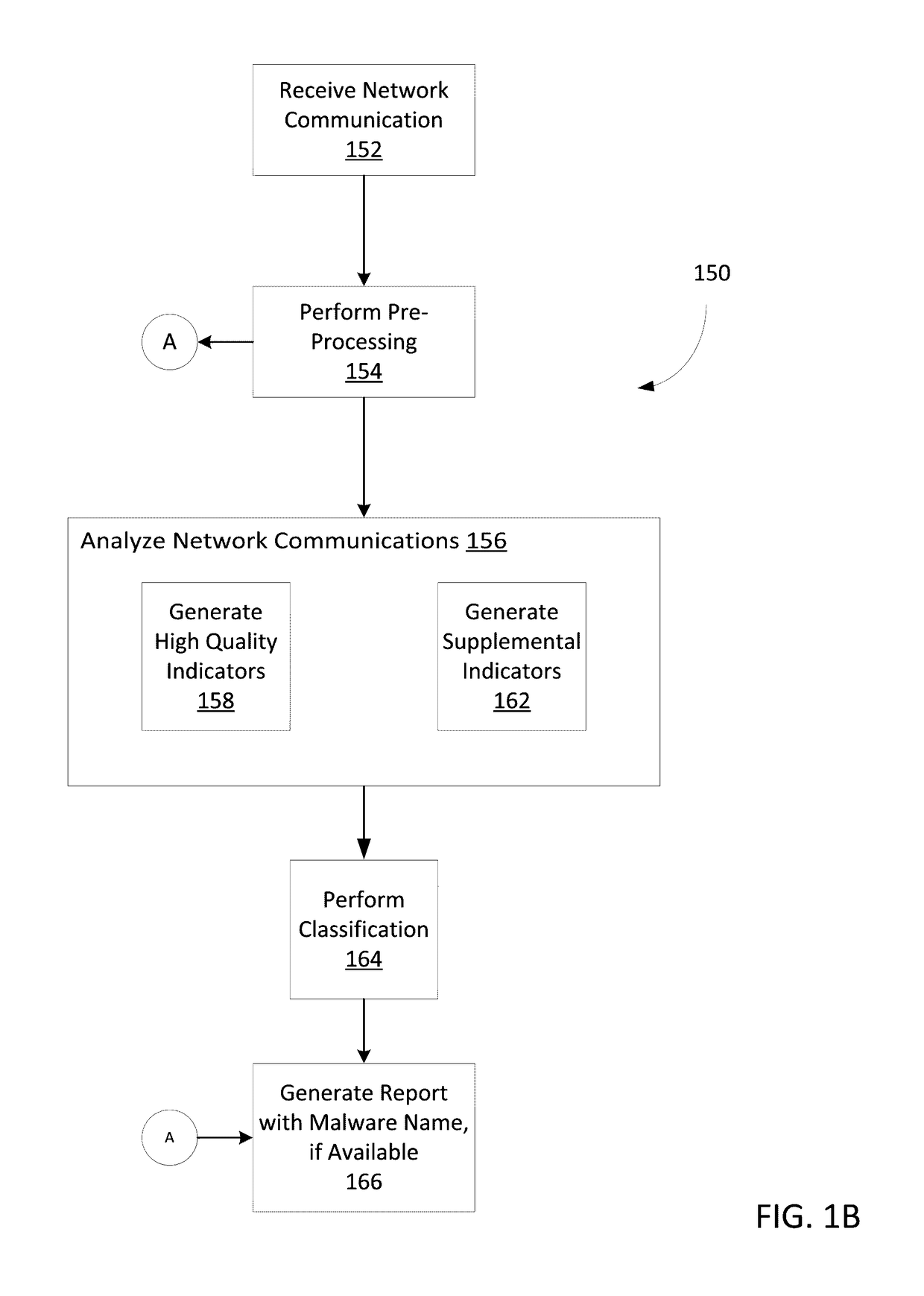
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using a distributed approach employing one or more local analyzers and a central analyzer. The local analyzers capture packets of outbound communications, generate header signatures, and analyze the captured packets using various techniques. The techniques may include packet header signature matching against verified callback signatures, deep packet inspection. The central analyzer receives the header signatures and related header information from the local analyzers, may perform further analysis (for example, on-line host reputation analysis); determines using a heuristics analysis whether the signatures correspond to callbacks; and generally coordinates among the local analyzers.
Owner:FIREEYE SECURITY HLDG US LLC
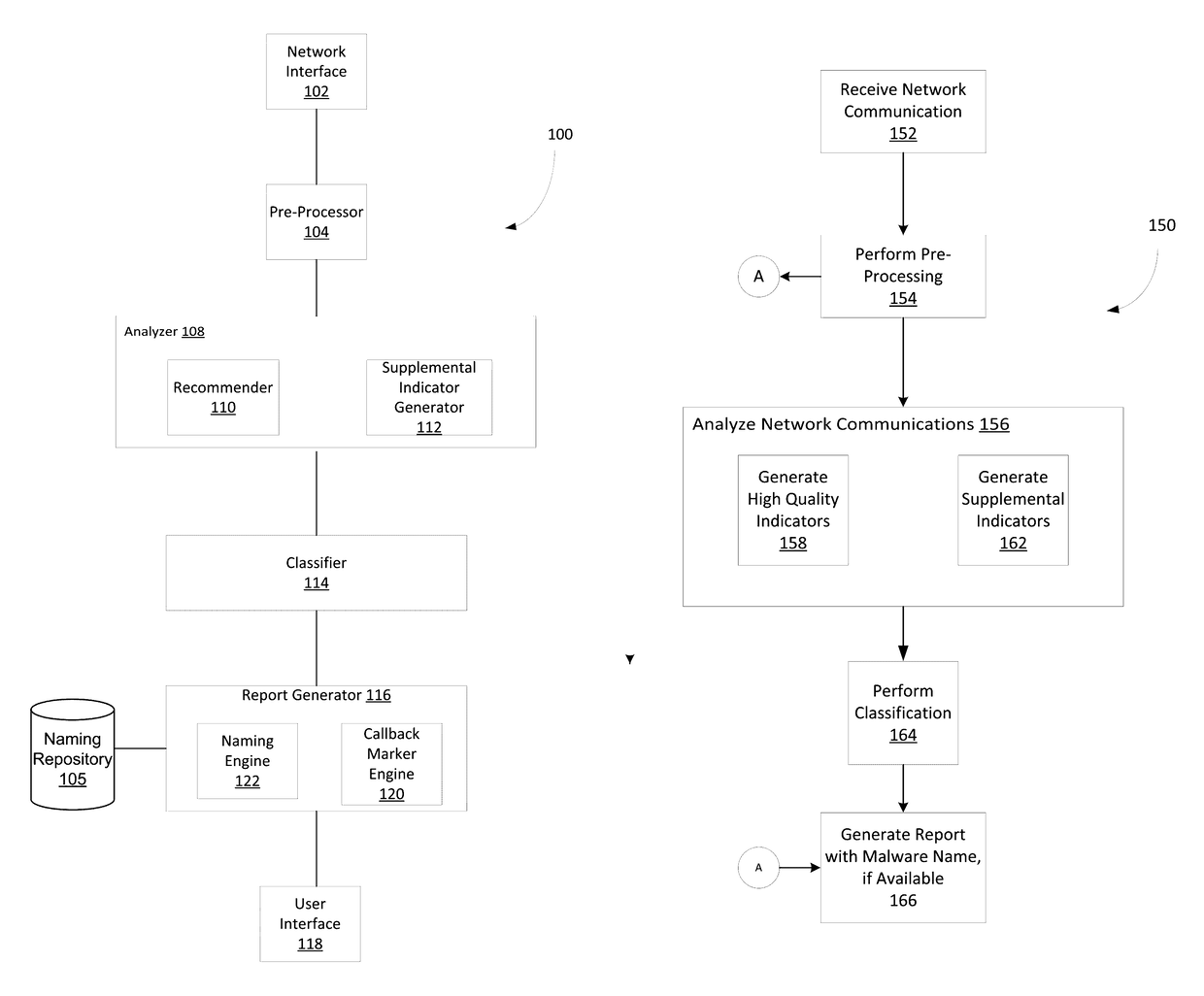
Classifying sets of malicious indicators for detecting command and control communications associated with malware
ActiveUS9635039B1Platform integrity maintainanceTransmissionOutbound communicationCommand and control
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using an approach employing both a set of high quality indicators and a set of supplemental indicators. The high quality indicators are selected since they provide a strong correlation with callbacks, and may be sufficient for the techniques to determine that the network outbound communications actually constitute callbacks. If not, the supplemental indicators may be used in conjunction with the high quality indicators to declare the outbound communications as callbacks.
Owner:FIREEYE SECURITY HLDG US LLC
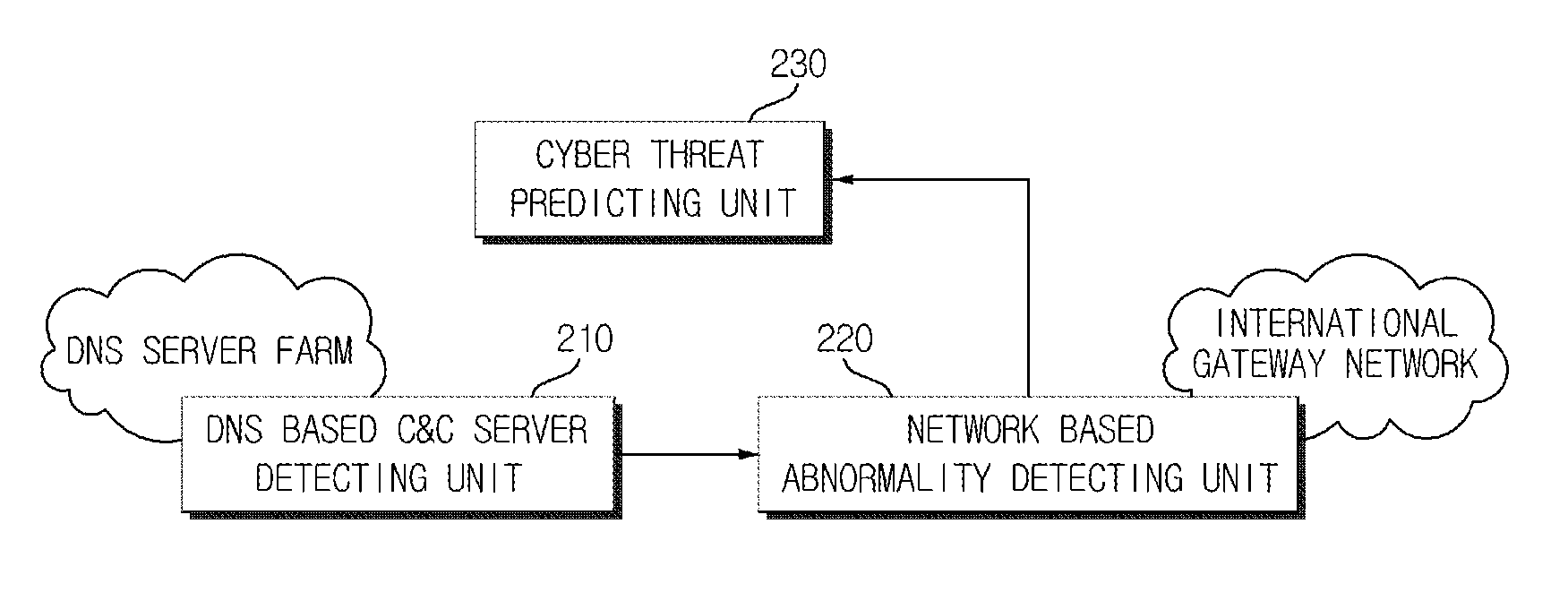
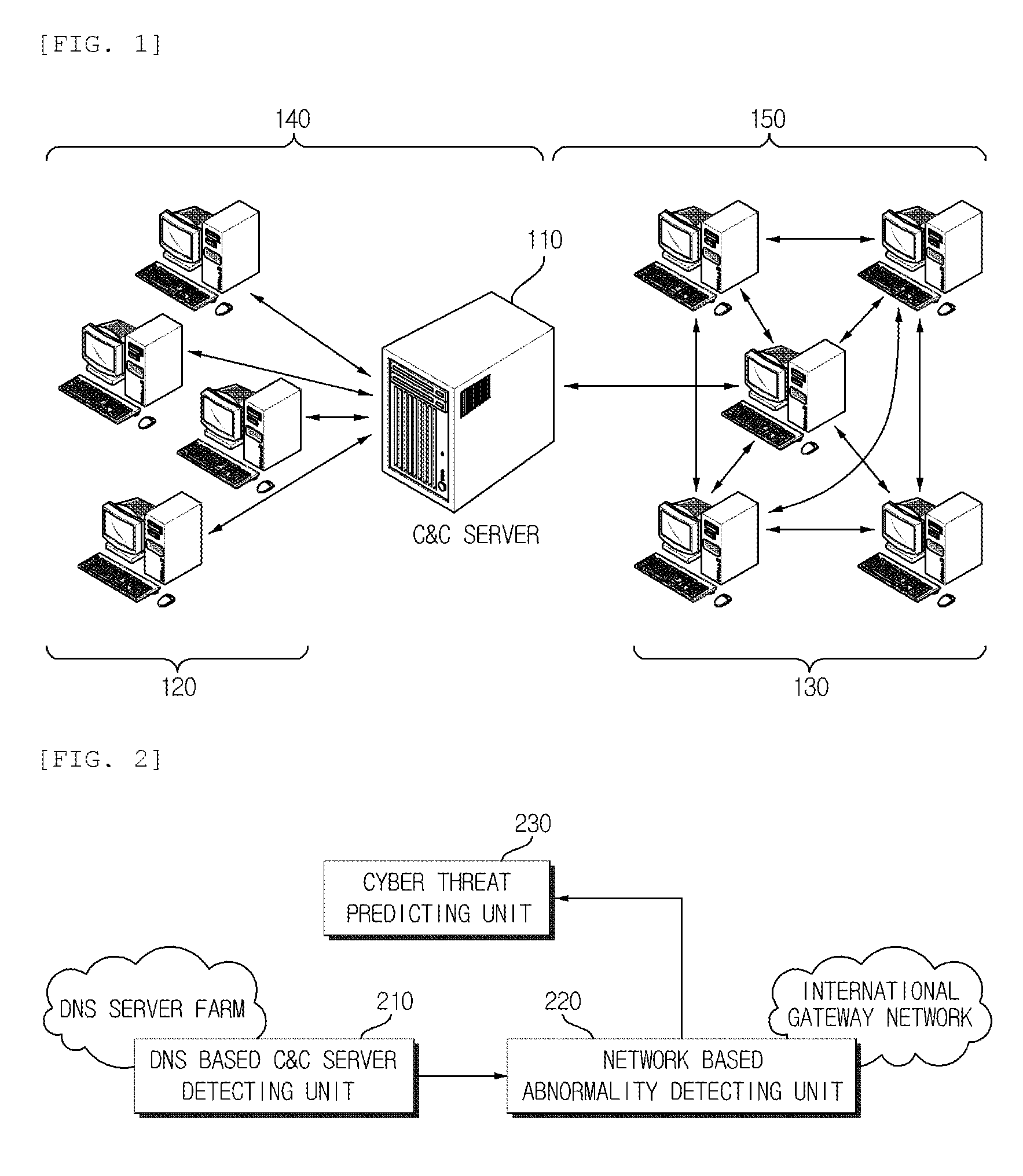
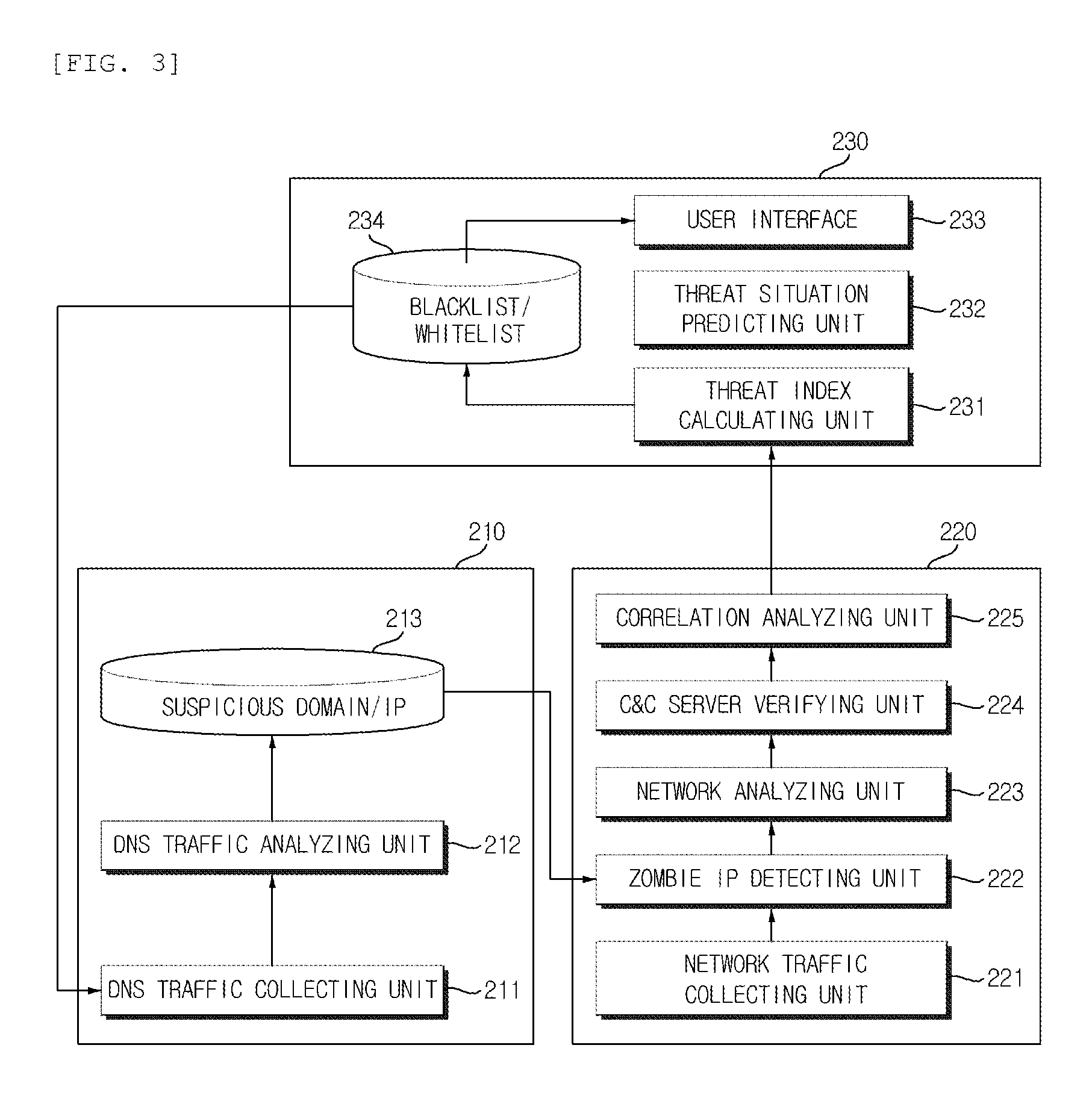
Cyber threat prior prediction apparatus and method
Disclosed are a cyber threat prior prediction apparatus, including a DNS based C&C server detecting unit configured to analyze DNS traffic to extract a domain address which is suspected as a C&C server; a network based abnormality detecting unit configured to analyze the network traffic to detect IP addresses of zombie PCs which access the C&C server and information of the zombie PCs; and a cyber threat predicting unit configured to predict a cyber threat situation based on the information of the zombie PCs.
Owner:ELECTRONICS & TELECOMM RES INST
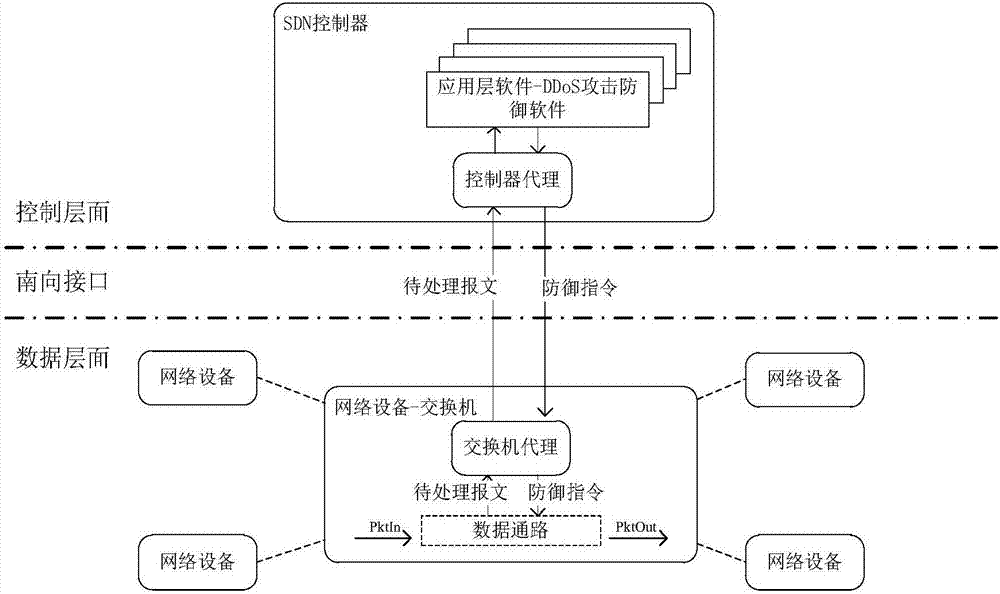
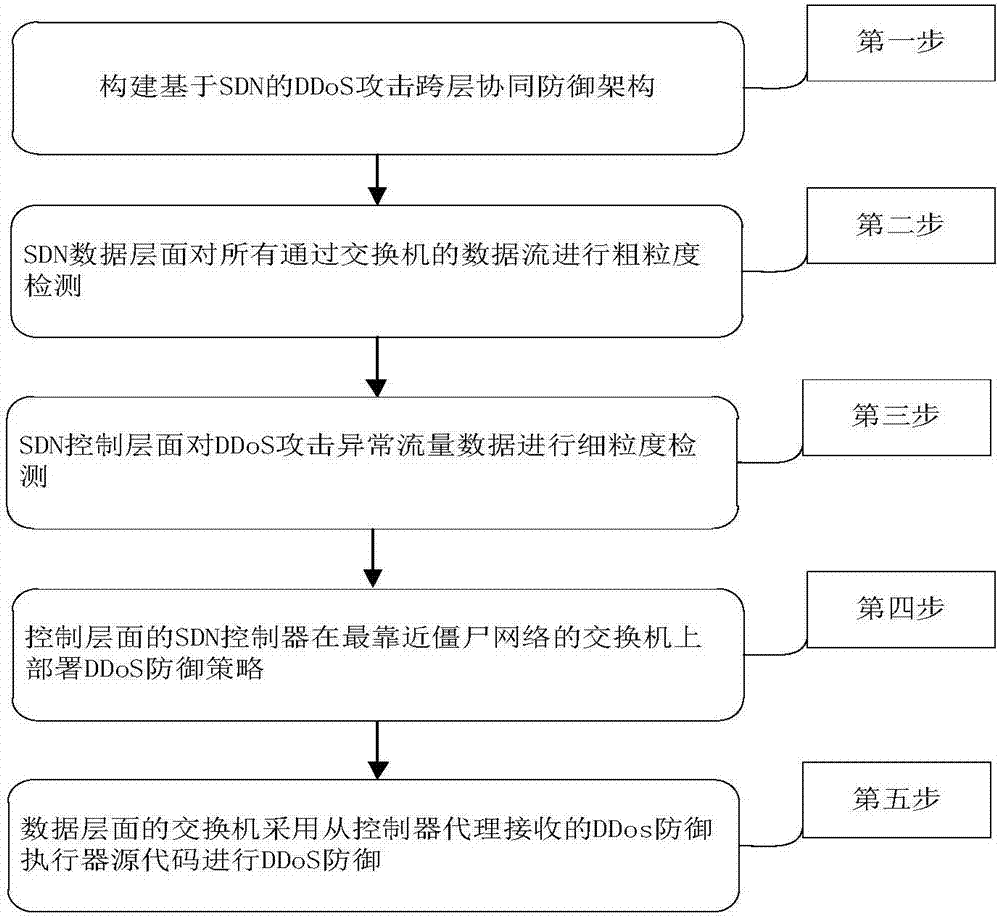
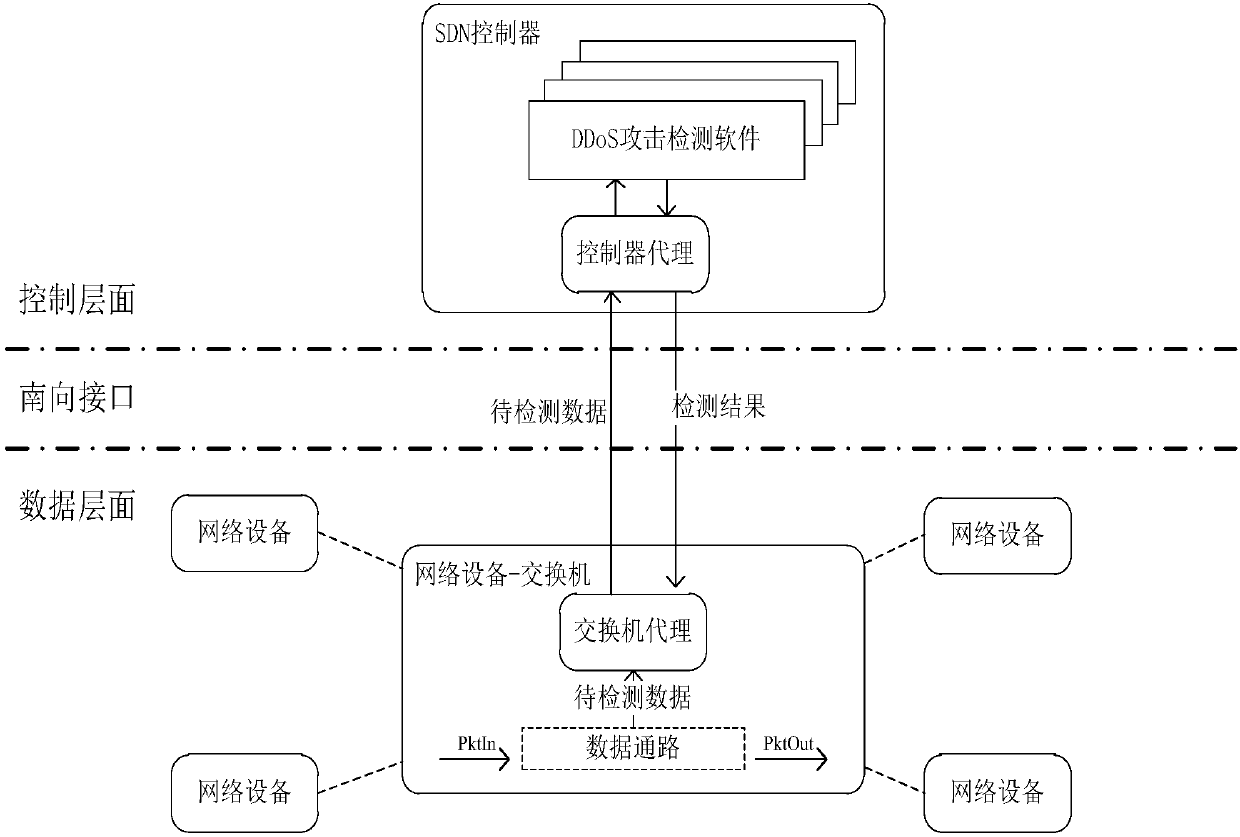
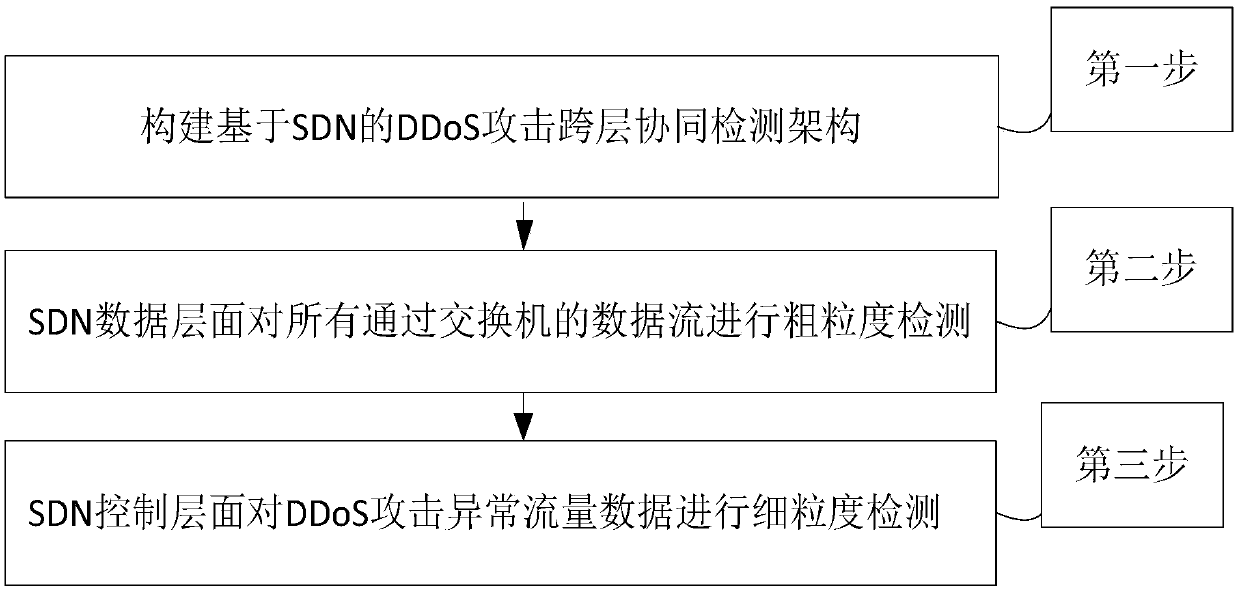
Software defined network-based DDoS attack cross-layer cooperative defense method
The invention discloses a software defined network-based DDoS attack cross-layer cooperative defense method and aims to solve the problems of over high communication pressure of a southbound interfaceand a control plane as well as over high calculation pressure of an SDN controller. According to the technical scheme, the method comprises the following steps: constructing an SDN-based DDoS attackcross-layer cooperative defense framework comprising a data plane and a control plane, performing coarse-grained detection on data flow by the data plane to acquire DDoS attack abnormal flow data, andperforming fine-grained detection on the DDoS attack abnormal flow data by the control plane to acquire an exchanger closest to a bot network; deploying a DDoS defense strategy on the exchanger closest to the bot network by the SDN controller of the control plane, and performing DDoS defense according to the DDoS defense strategy by the SDN exchanger of the data plane. Through cooperation of thedata plane and the control plane, the cooperative defense advantage of the SDN is completely utilized and the problems of high pressure of the SDN southbound interface and too large burden of the SDNcontroller are solved, so that the exchanger can perform automatic defense intelligently.
Owner:NAT UNIV OF DEFENSE TECH
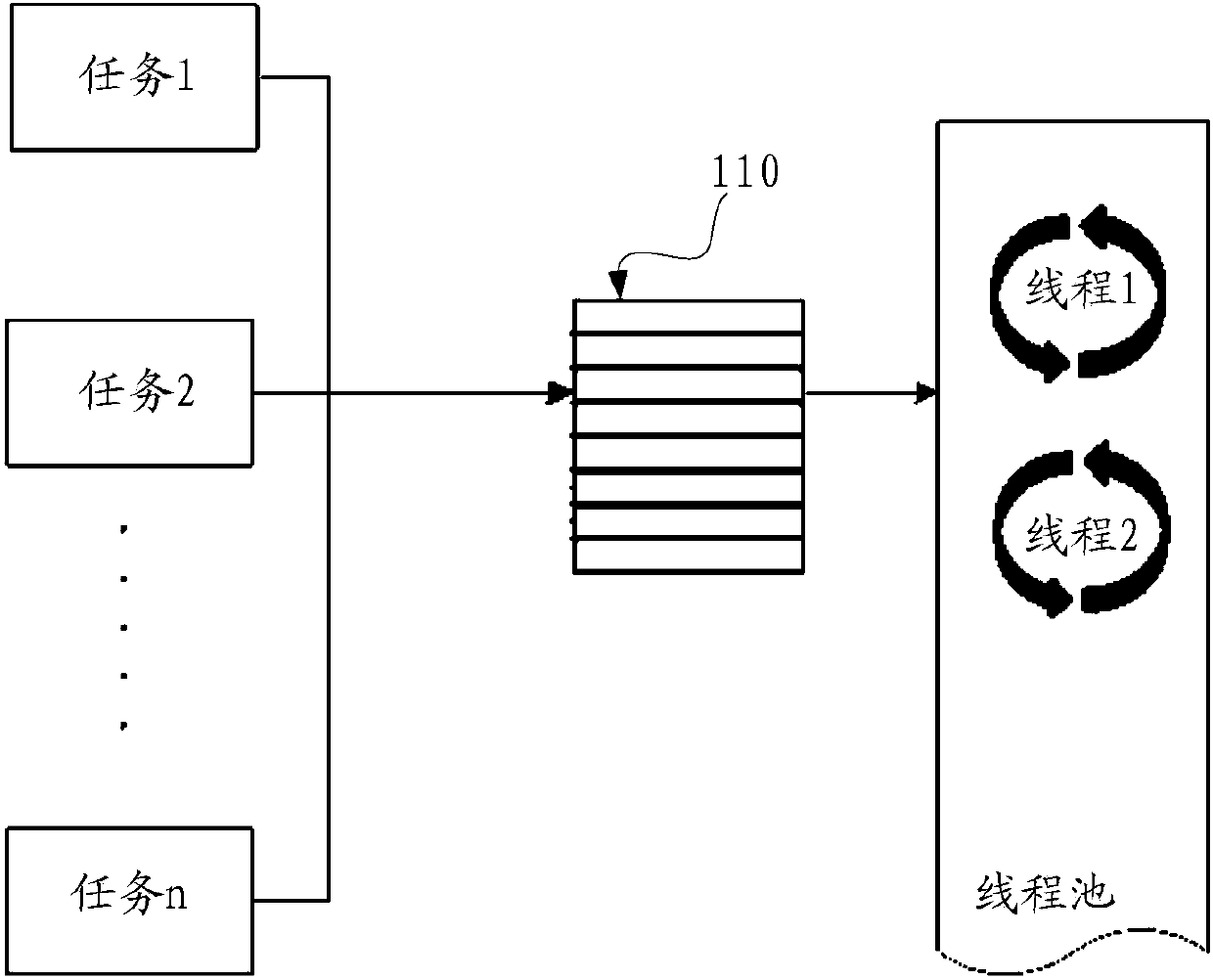
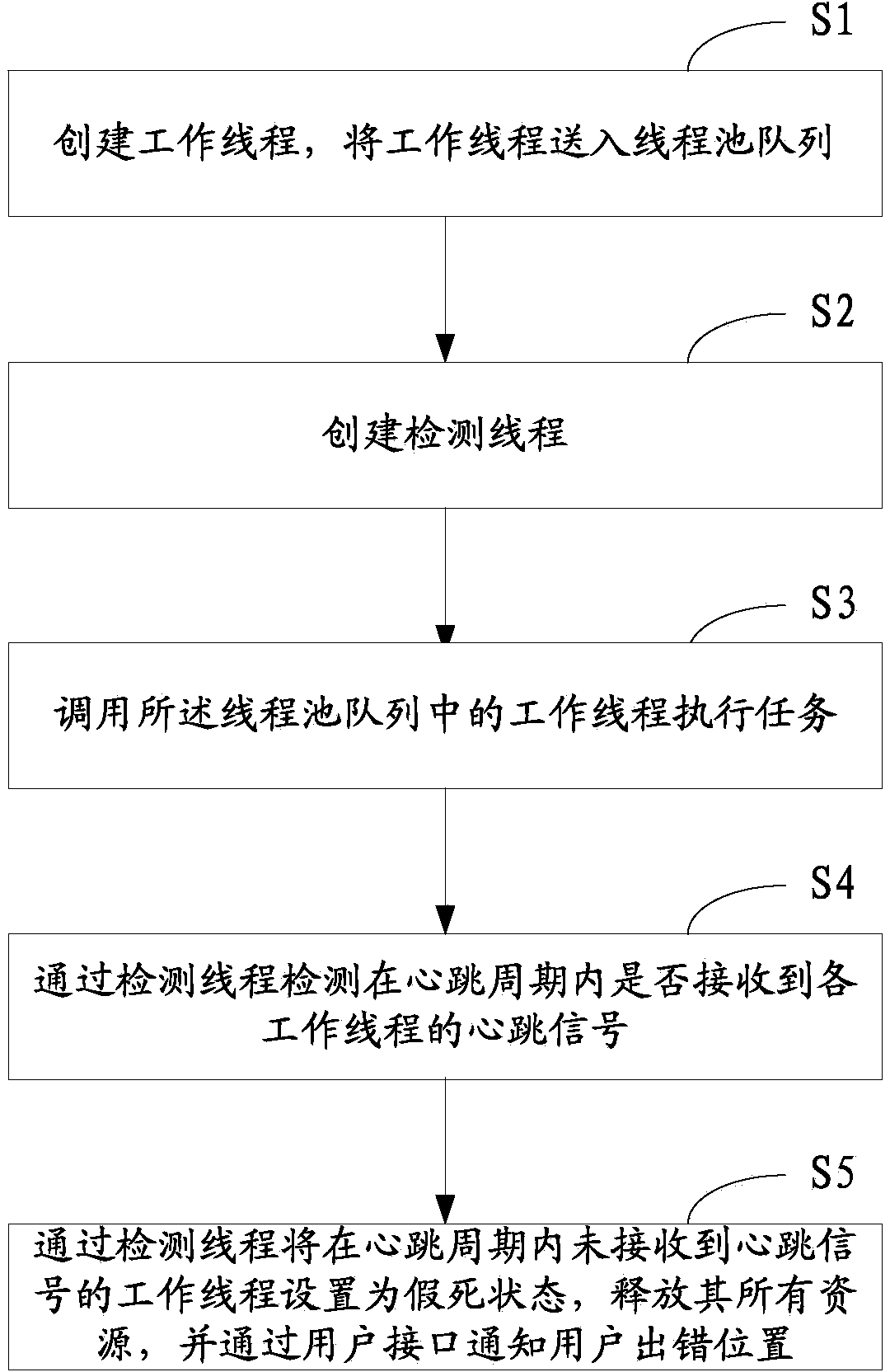
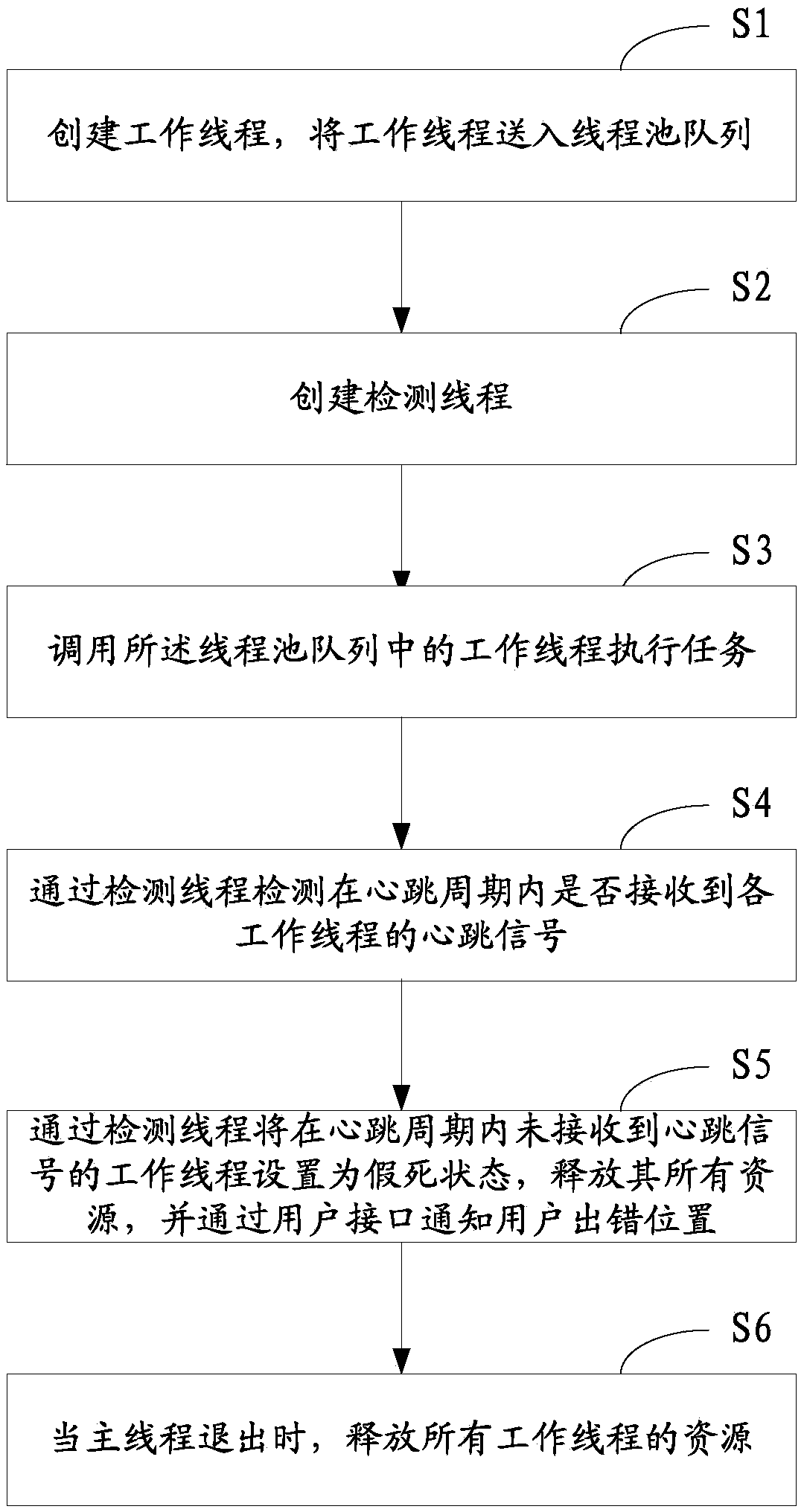
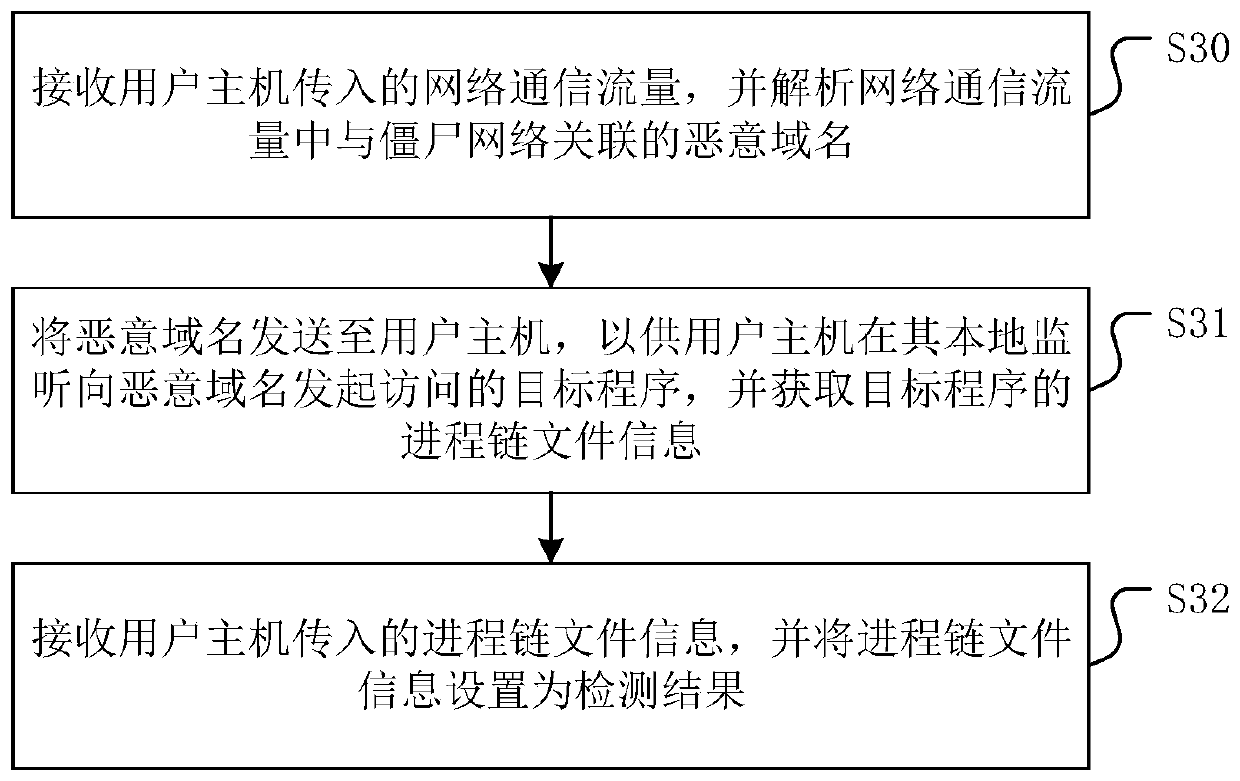
Thread pool managing method and system
ActiveCN103744723AImplement the callKeep abreast ofResource allocationOperational systemSystems management
The invention discloses a thread pool managing method and system. The system comprises a working thread creating unit, a detecting thread creating unit, a working thread calling unit, a heartbeat signal detecting unit and a zombie thread processing unit. The managing method includes: creating a working thread, and delivering the same into a thread pool queue; creating a detecting thread; calling the working thread in the thread pool queue to execute a task; using the detecting thread to detect whether the heartbeat signals of each working thread is received or not in a heartbeat cycle; using the detecting thread to set the working threads whose heartbeat signals are not received in the heartbeat cycle as zombie threads, releasing all the resources of the zombie threads, and notifying a user of the fault positions through a user interface. The method and system has the advantages that the working threads in the thread pool are managed through the thread pool, dependence on operating system management is avoided, zombie threads can be detected timely and accurately, and the fault positions in programs using the zombie threads to execute tasks can be found and notified to the user.
Owner:SHENZHEN LAN YOU TECH
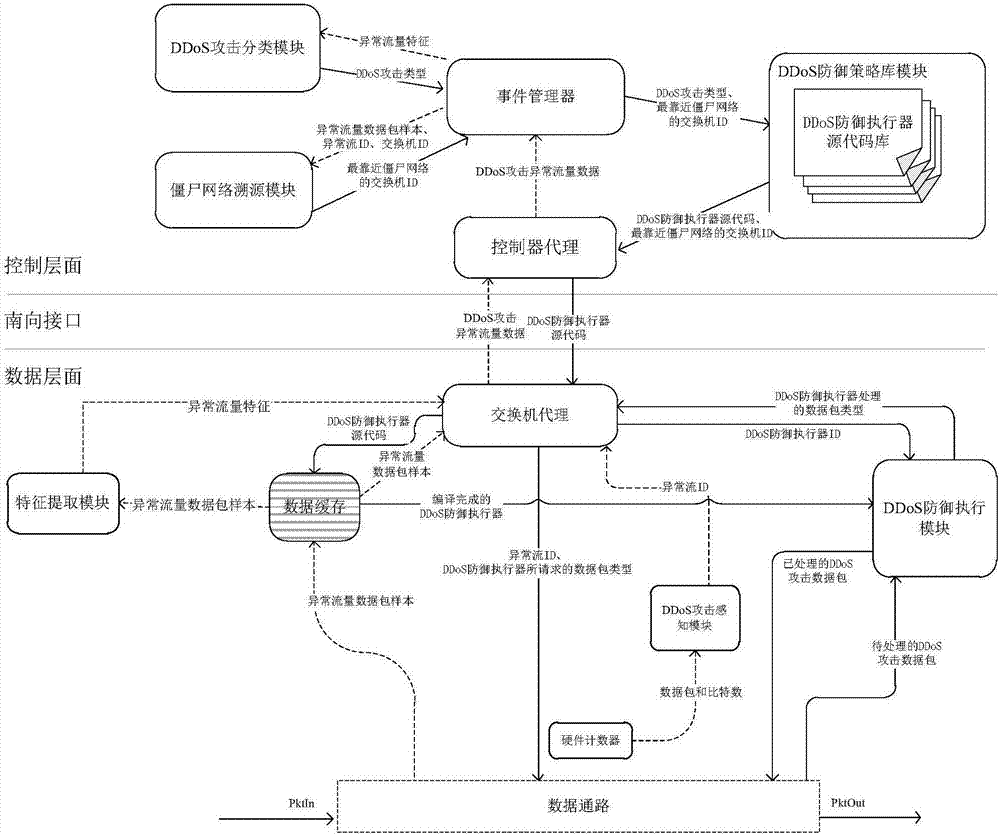
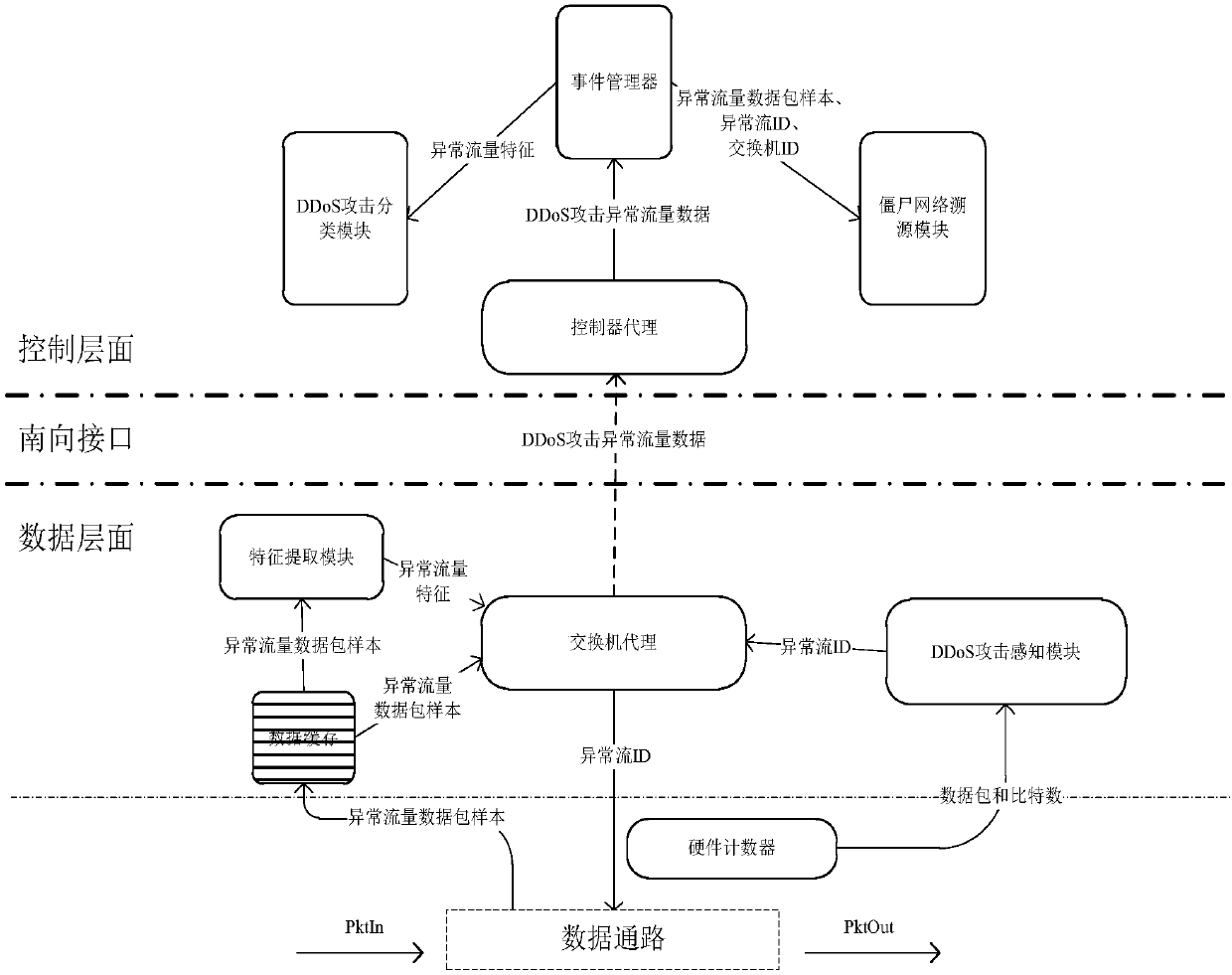
Cross-layer cooperative detection method of DDoS attack based on software defined network
The invention discloses a cross-layer cooperative detection method of a DDoS attack based on an SDN for improving the detection efficiency of the DDoS attack. The technical scheme is as follows: constructing cross-layer collaborative detection architecture based on the SDN composed of a data layer and a control layer, wherein a data path, a switch proxy, a DDoS attack sensing module and a featureextraction module are arranged on an SDN switch of the data layer; and a controller proxy, an event manager, a DDoS attack classification module and a botnet tracing module are arranged on an SND controller of the control layer. The data layer performs coarse granularity detection on the data traffic to obtain DDoS attack abnormal traffic data, and the control layer performs fine-grained detectionon the abnormal traffic data of the DDoS attack. According to the cross-layer cooperative detection method disclosed by the invention, by means of the cooperation of the data layer and the control layer, the problems of large southbound interface pressure of the SDN and overlarge pressure of the SND controller are solved, the type of DDoS attack can be detected, and a switch set close to a botnetcan also be detected, so that the speed and accuracy of detecting the DDoS attack are improved.
Owner:NAT UNIV OF DEFENSE TECH
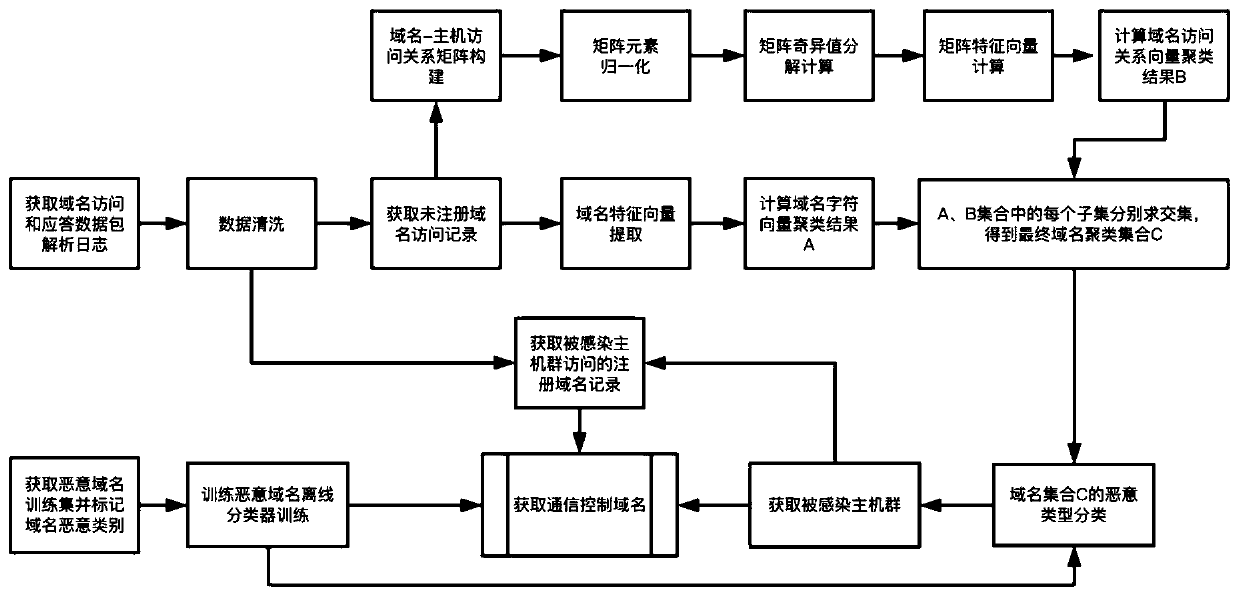
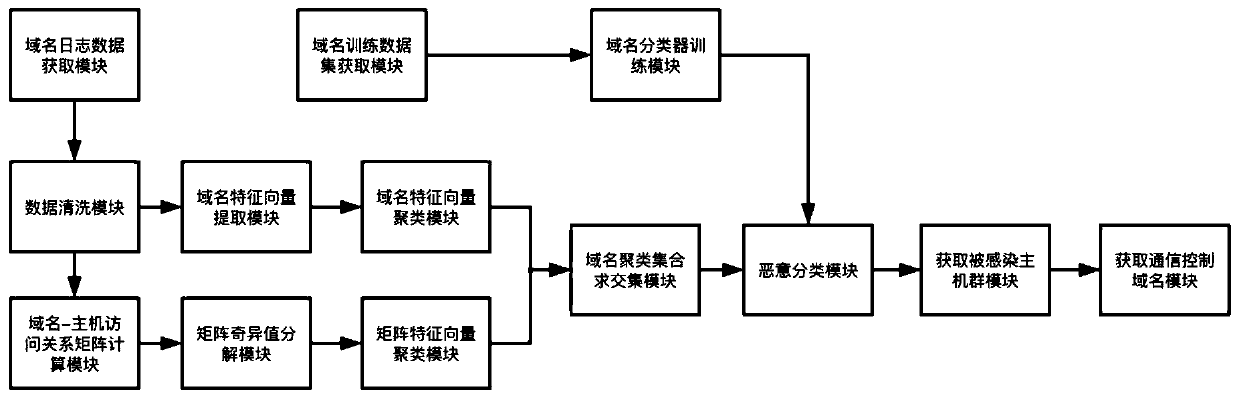
Massive network malicious domain name identification and classification method and system
ActiveCN111131260AEfficient and accurate identificationReduce data volumeCharacter and pattern recognitionTransmissionDomain nameData pack
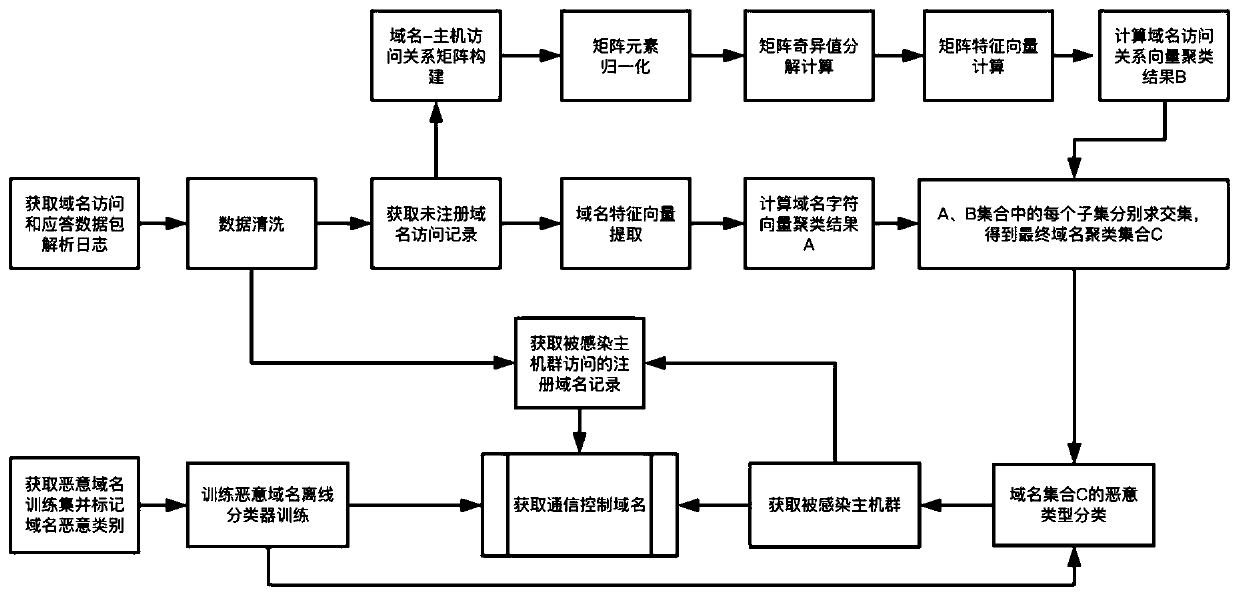
The invention discloses a malicious domain name recognition and classification method and system based on massive domain name access logs, and the method comprises the steps: obtaining an unregistereddomain name by analyzing a domain name server response data packet in a domain name access log, detecting a malicious domain name, and recognizing an infected zombie host; and detecting viruses infected by the zombie host and communication control malicious domain names used for communication of the control end from the domain name set accessed by the zombie host. By adopting the technical schemeof the invention, the calculation complexity is relatively low, the data calculation amount is greatly reduced, and the method is suitable for efficiently identifying malicious domain names in massive domain name access logs.
Owner:邑客得(上海)信息技术有限公司
Botnet detection and mitigation
ActiveUS20200366689A1Substantial beneficial technical effectTransmissionInternet privacyInternet traffic
Method and systems for detecting and mitigating a malicious bot. Threat information is obtained, the threat information identifying one or more indicators of compromise (IOC) corresponding to suspected or known malicious network traffic. A control list (CL) corresponding to the threat information is generated, the CL describing rules for identifying network flows to be logged in a network log. The network log identifying the network flows is obtained and a suspect network flow identified by both the threat information and the network log is identified. An address corresponding to the suspect network flow is identified and the address is correlated with a user identifier. A notification is issued to a user associated with the user identifier, the notification indicating a suspected existence of a malicious bot.
Owner:CHARTER COMM OPERATING LLC
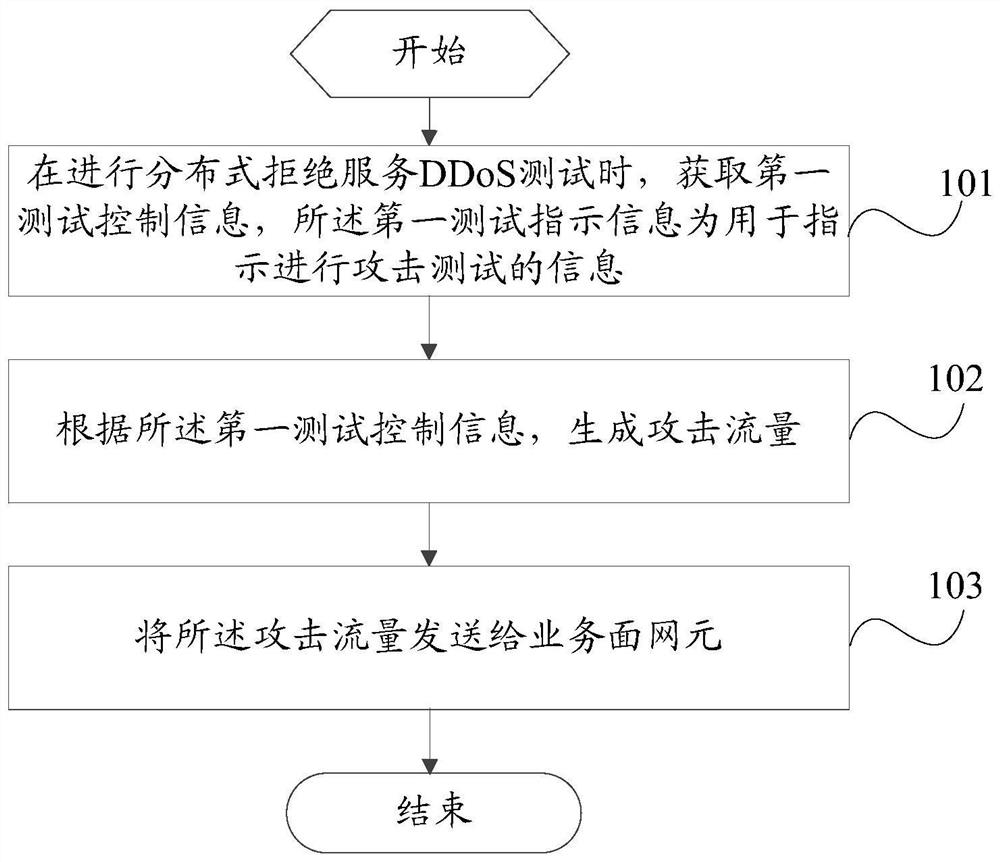
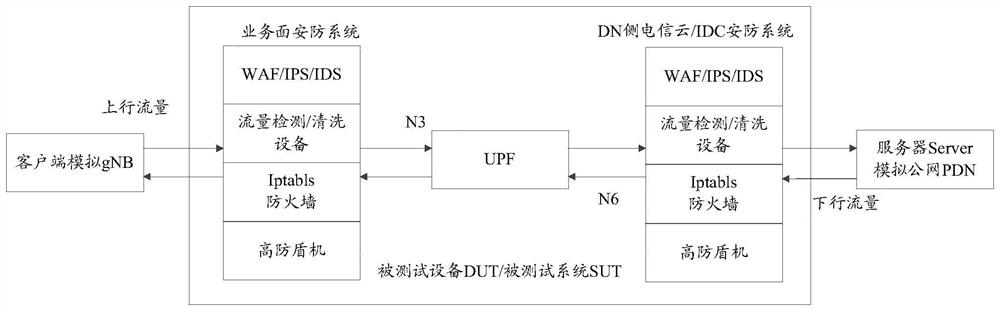
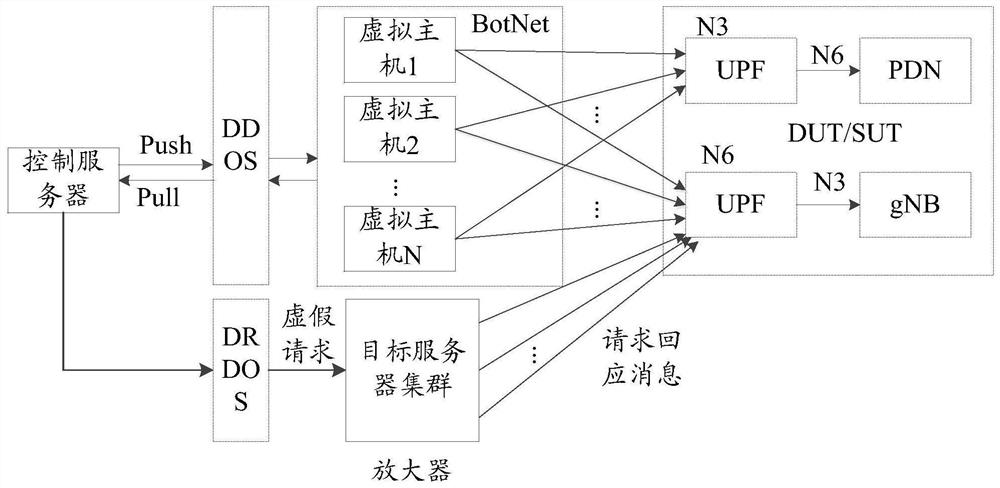
Attack testing method, host server and control server
The invention provides an attack test method, a host server and a control server, and solves a problem of how to carry out an attack test on a core network service surface. The method comprises stepsthat when a distributed denial of service DDoS test is carried out, the first test control information is acquired, and the first test indication information is used for indicating to carry out an attack test; attack traffic is generated according to the first test control information; and the attack traffic is sent to a service plane network element. The method is advantaged in that the virtual host is controlled by the control server, so large-scale DDoS attacks can be safely and effectively simulated, and diffusion threats of backdoor programs and harm caused by botnets do not need to be considered.
Owner:DATANG MOBILE COMM EQUIP CO LTD
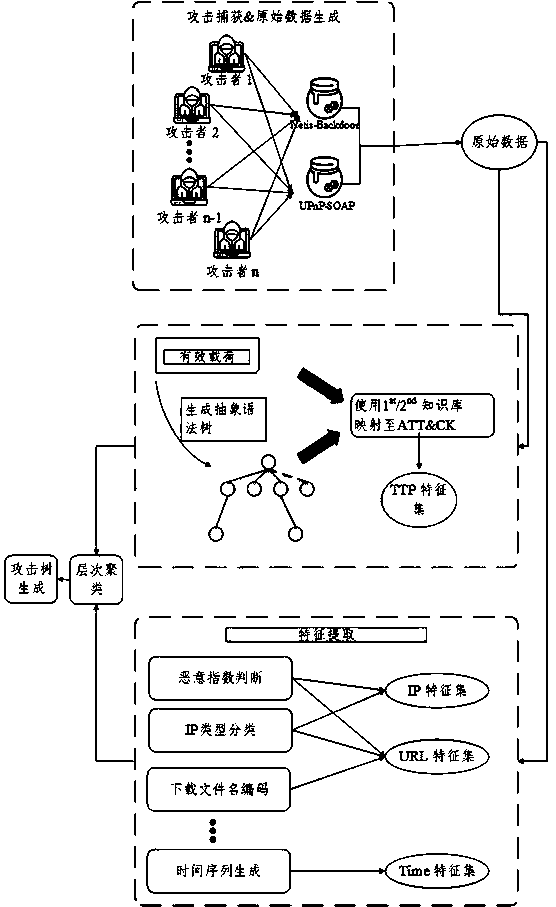
TTP automatic extraction and attack team clustering method
The invention relates to a TTP automatic extraction and attack team clustering method. Along with increasingly popularization of advanced persistent threats in the global range, the Internet of Thingsis directly exposed to the Internet due to poor security, so that the Internet of Things becomes an excellent weapon for a hacker organization to initiate APT attacks. Therefore, an attacker can establish a botnet by using the attacked Internet of Things device and initiate an APT attack by using the botnet. The invention provides a framework for observing and predicting attacks of the Internet of Things. The framework aims at automatically extracting technologies, tactics and processes of attackers and mining potential attacker teams behind a large number of attacks. Firstly, related fieldsare extracted from captured Internet of Things honeypot logs; and then, the attack behavior is mapped to an ATT & CK framework to realize TTP automatic extraction. Furthermore, the method generates four feature groups including 18 features including TTP, time, IP and URL, potential attack groups are mined through specific hierarchical clustering, and finally, an attack tree is generated for each attacker cluster so as to better describe team attack behaviors.
Owner:SICHUAN UNIV
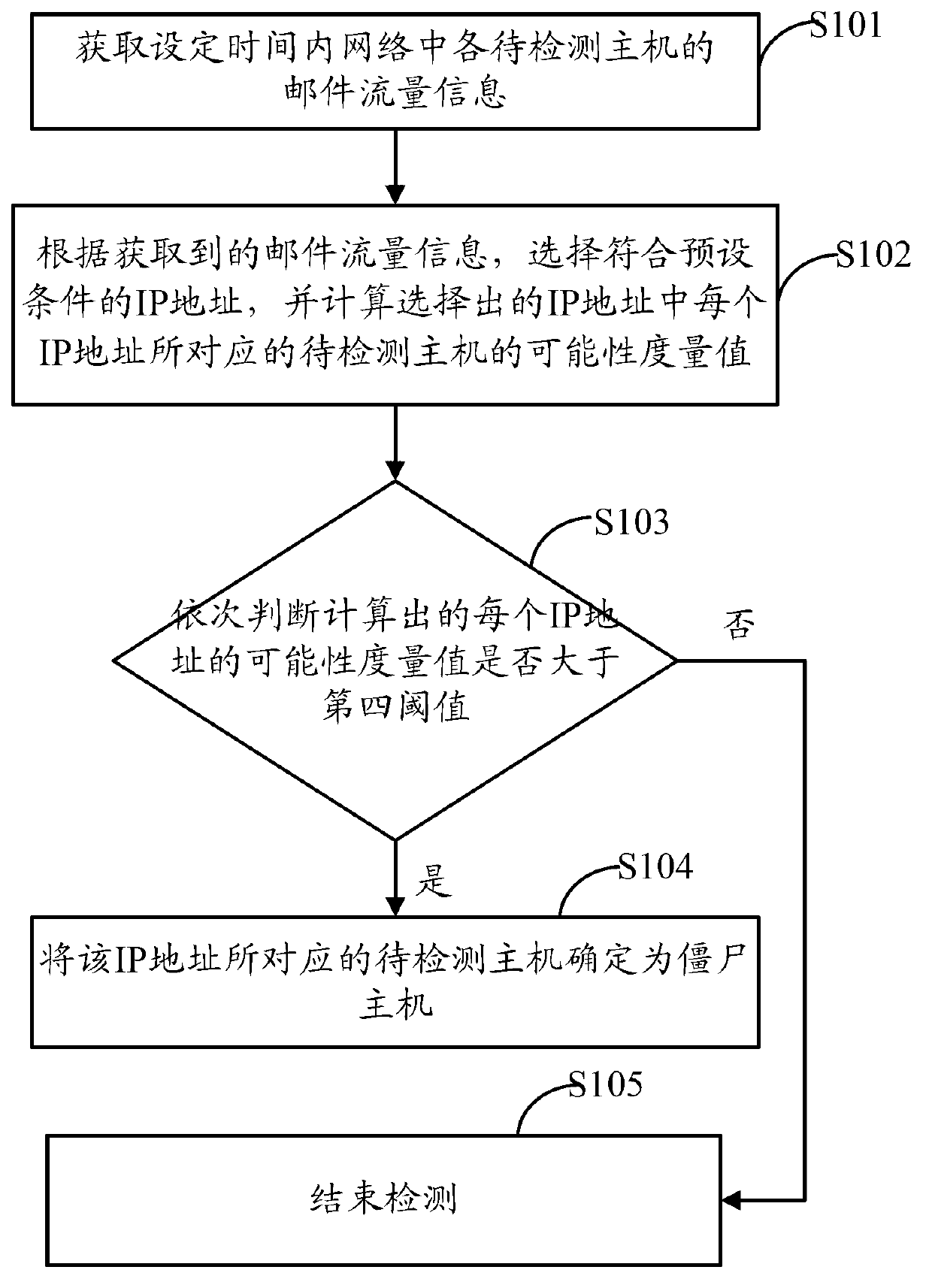
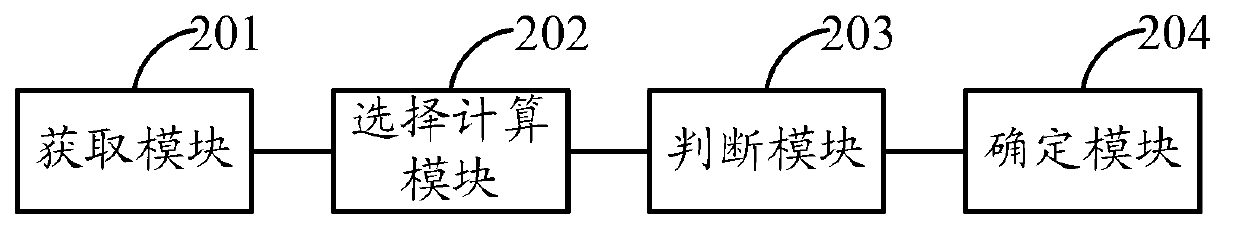
Detection method and detection device of zombie host computers
ActiveCN103139206AImprove detection efficiencyImprove detection accuracyTransmissionIp addressComputer engineering
The invention provides a detection method and a detection device of zombie host computers. The detection method of the zombie host computers includes the following steps: email flow information of each to-be-detected host computer in the network is obtained within set time; according to the obtained email flow information, internet protocol (IP) addresses according with preset conditions are selected, and a possibility measuring value of each to-be-detected host computer corresponding to each of the selected IP addresses is calculated out; and the calculated out possibility measuring value of each IP addresses is judged whether to be lager than a fourth threshold in sequence, and under the condition of 'yes', the to-be-detected host computers corresponding to the IP addresses are determined as the zombie host computers. According to the detection method and the detection device of the zombie host computers, the email flow information of the to-be-detected host computers can be periodically obtained, and the detection method is relatively timely. Besides, after the email flow information is processed according to the preset conditions, the high-possibility IP addresses of the zombie host computers can be obtained, the zombie host computers in the network can be obtained after processed with a certain algorithm, and the detection efficiency and the accuracy are improved.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Botnet program domain name identification method and device, equipment and storage medium
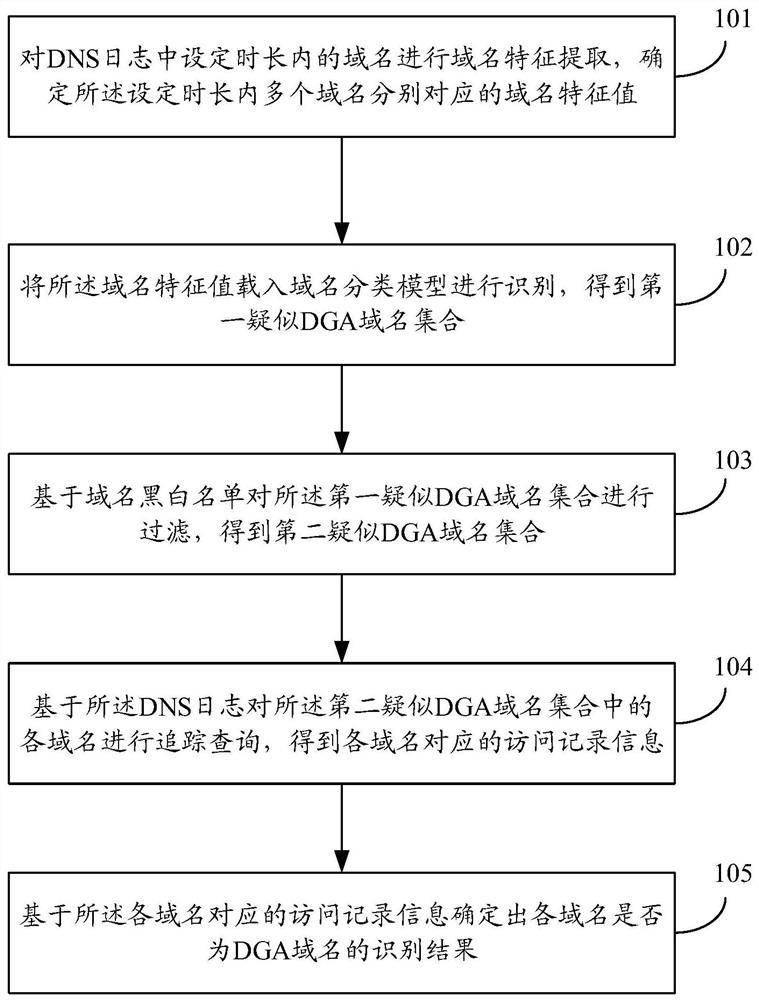
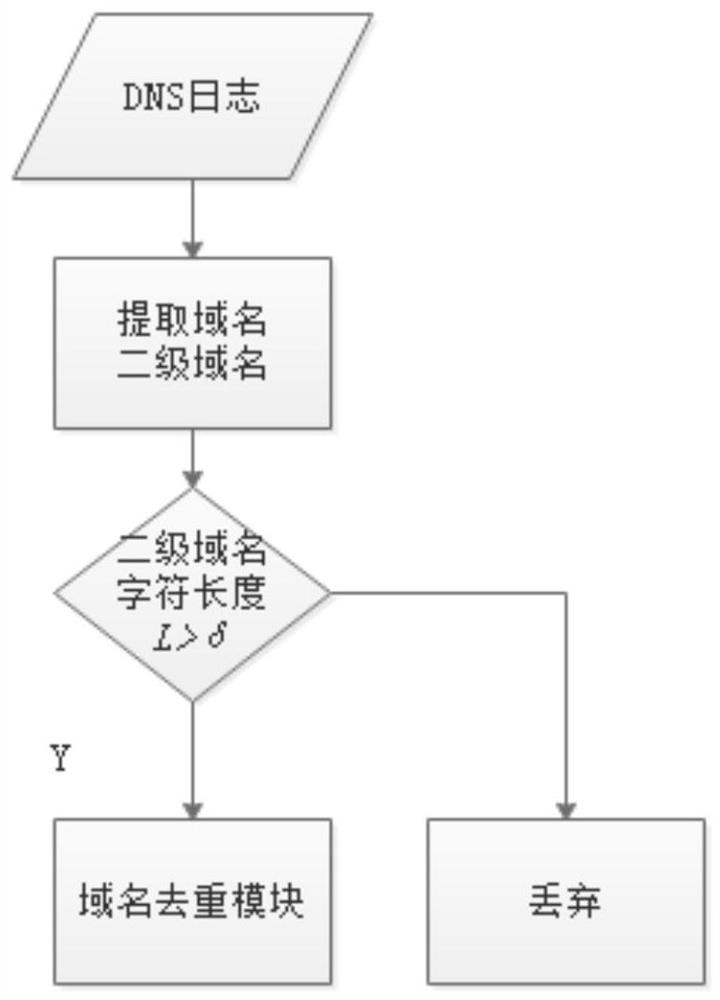
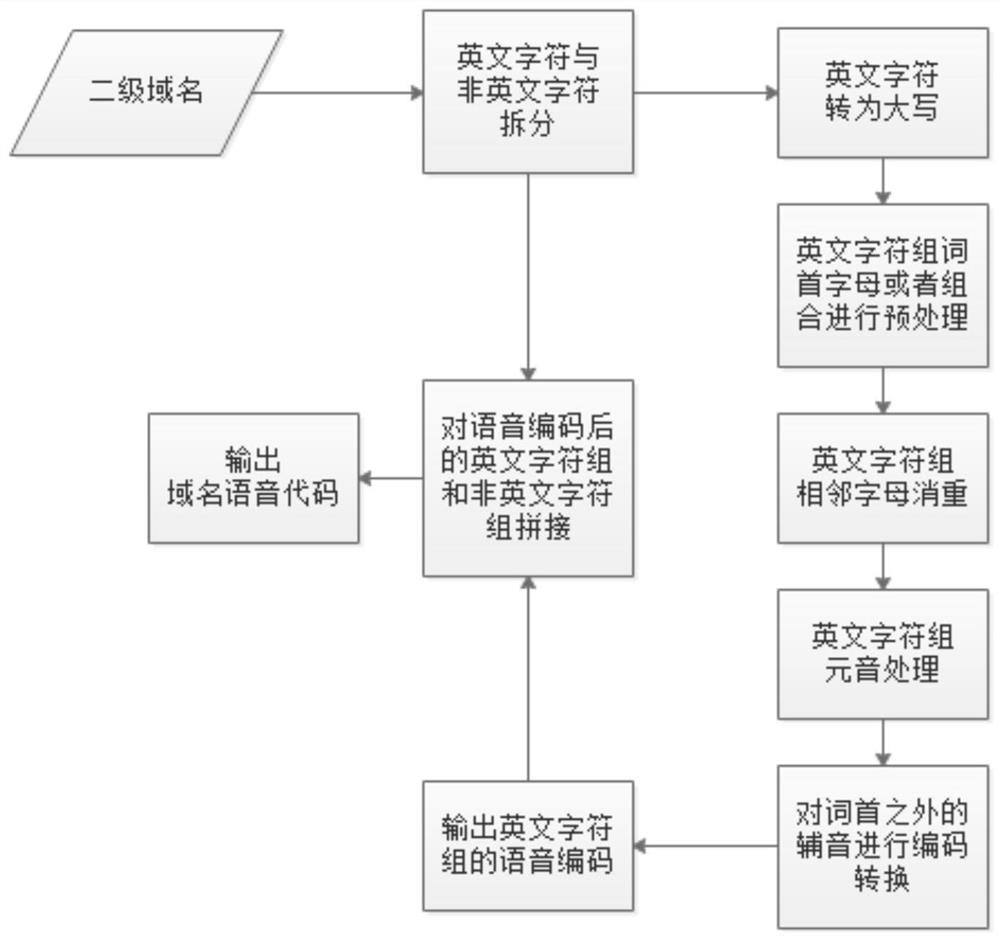
ActiveCN112839012AReduce false alarm rateImprove accuracyCharacter and pattern recognitionTransmissionFeature extractionTheoretical computer science
The invention discloses a zombie program domain name identification method and device, equipment and a storage medium. The method comprises the following steps: carrying out domain name feature extraction on domain names in a set time length in a domain name system (DNS) log, and determining domain name feature values respectively corresponding to a plurality of domain names in the set time length; loading the domain name feature value into a domain name classification model for identification to obtain a first suspected domain name generation algorithm (DGA) domain name set; filtering the first suspected DGA domain name set based on a domain name blacklist and a domain name whitelist to obtain a second suspected DGA domain name set; performing tracking query on each domain name in the second suspected DGA domain name set based on the DNS log to obtain access record information corresponding to each domain name; and determining an identification result of whether each domain name is a DGA domain name based on the access record information corresponding to each domain name.
Owner:CHINA MOBILE COMM LTD RES INST +1
http flow defense method and system for resisting DDoS attack
ActiveCN112003873AGuaranteed recognition functionSolve traffic problemsTransmissionInternet privacyAttack
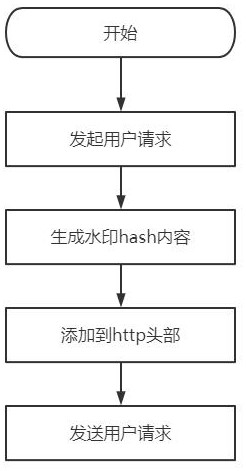
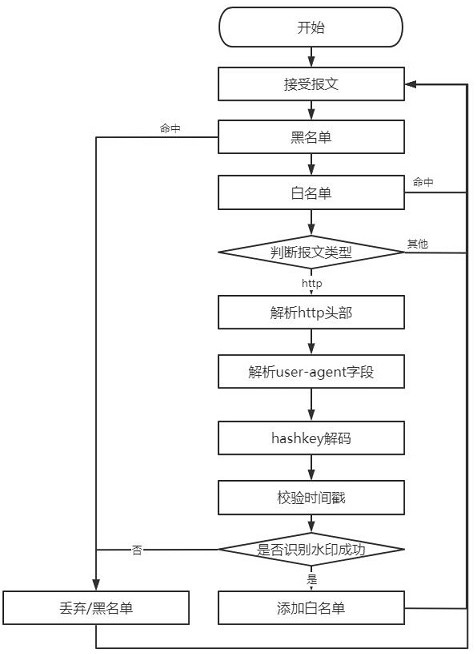
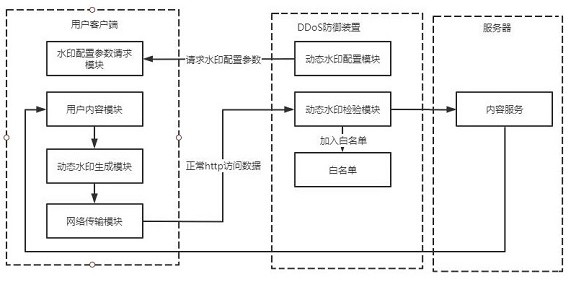
The invention provides an http flow defense method and system for resisting DDoS attack. A dynamic watermark generation module is arranged in a mobile client, a dynamic watermark is generated when anHTTP request is initiated to a server, when the message passes through a DDoS defense device, the correctness and integrity of the watermark in the HTTP protocol header are quickly checked to identifywhether the message belongs to the flow of a normal client or the attack flow initiated by a zombie host controlled by an attacker, and a cleaning action is performed through the defense device. Through the arrangement, the identification function of the mobile client is ensured, and the flow problem that a normal client and an illegal attacker cannot be distinguished is effectively solved; and the HTTP attack identification and performance processing capabilities of the DDoS defense device are improved.
Owner:CHENGDU DBAPP SECURITY
Cellular WIFI - cellular data handoffs
InactiveUS20210392551A1Save considerable moneyReduce minute usageNetwork topologiesCommmunication supplementary servicesComputer networkWifi network
Enabling handoffs between WiFi networks and cellular data networks for mobile devices. Utilizing a WiFi Fixer or Zombie Fixer to interact with a special platform to enable handoffs of calls between cellular data and WiFi.
Owner:MOVIUS INTERACTIVE CORP
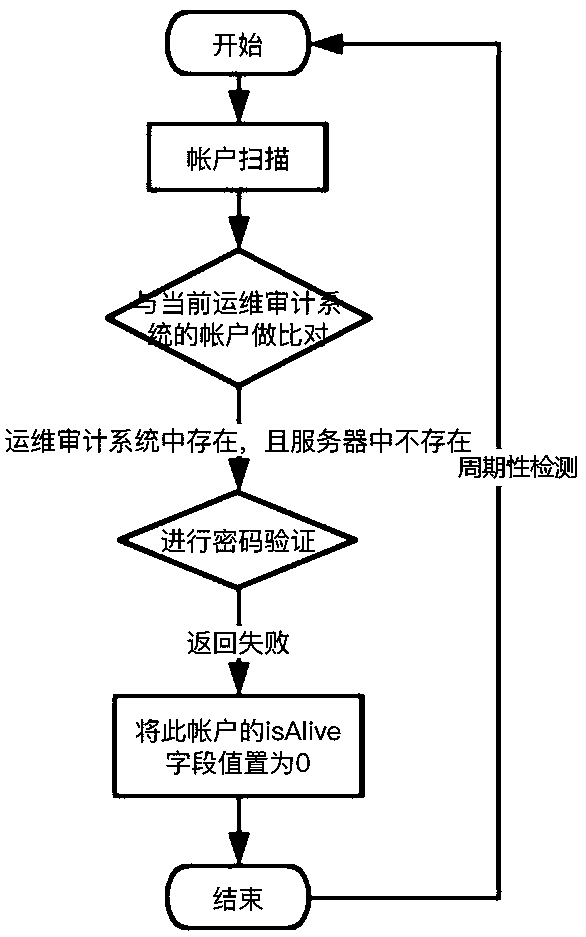
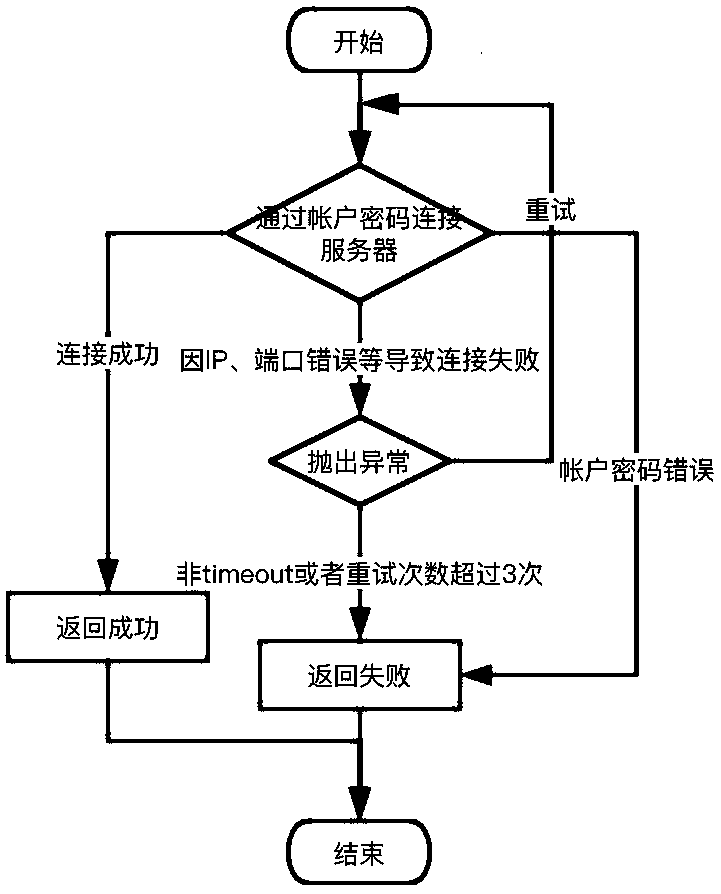
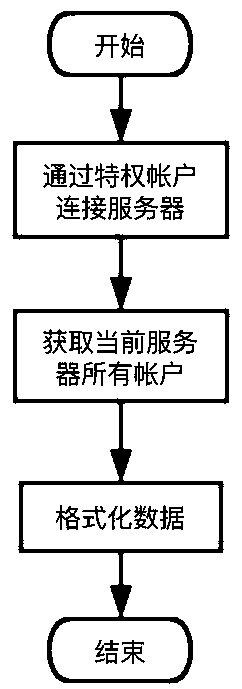
Zombie account management method based on operation and maintenance auditing system
The invention discloses a zombie account management method based on an operation and maintenance auditing system. The zombie account management method comprises the following steps of screening out anon-scanning account which is not stored in a to-be-detected server but is stored in the operation and maintenance auditing system by scanning the to-be-detected server; further determining that the non-scanning account indeed does not exist in the server through the password login verification, and defining the determined non-scanning account that indeed does not exist the server as a non-real account; judging the longest non-login time limit of the non-real account; and identifying the non-real account of which the interval between the final login time and the current time is greater than the longest non-login time limit as a zombie account. Through the zombie account management method, managers can screen and sort out the zombie accounts which are distributed in a scattered mode and clean or modify the zombie accounts in a unified mode, and meanwhile the potential safety hazards caused by account logout and reconstruction in the server are avoided through the periodical cleaning.
Owner:CHENGDU DBAPP SECURITY
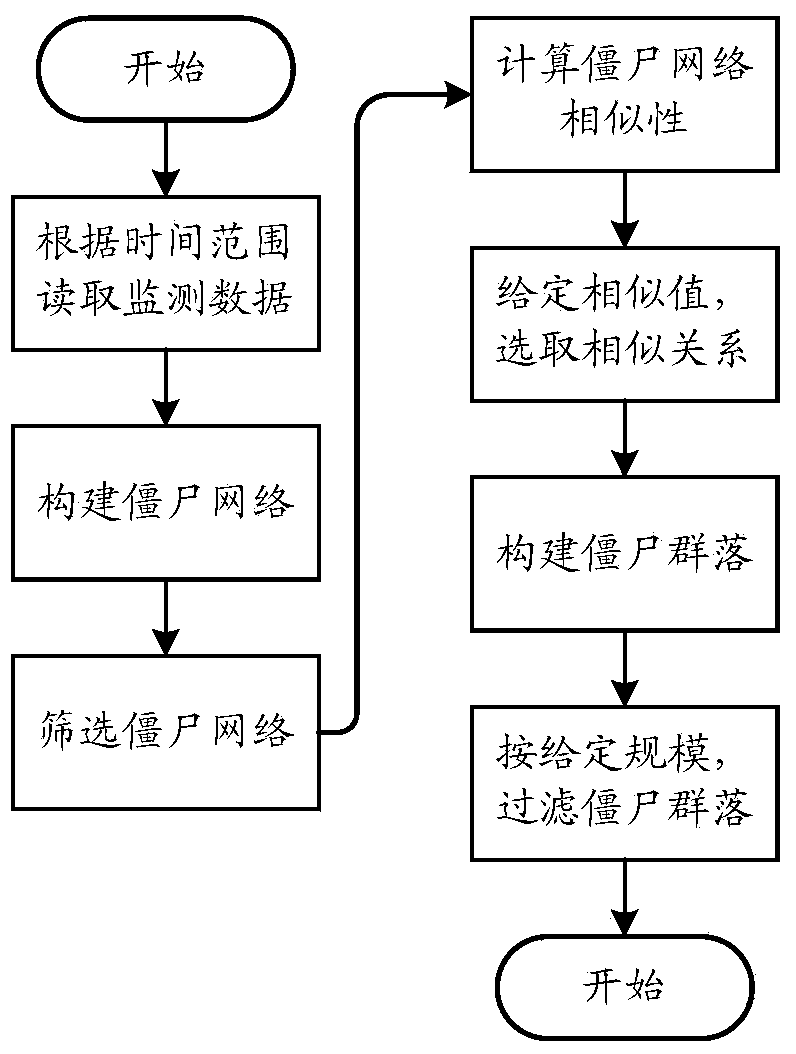
Method and device for analyzing zombie community
ActiveCN103795591ADiscover inner relationshipsEffective trackingData switching networksEngineeringData mining
The invention discloses a method and device for analyzing a zombie community. The method comprises the steps of acquiring monitored data generated within a set time range by a zombie network monitoring system, establishing zombie networks according to the monitored data, computing the similarity factor of any two zombie networks, selecting similarity relations with the similarity factors larger than a preset similarity factor threshold value, establishing the zombie community according to the similarity relations, and making analysis. According to the method for analyzing the zombie community, the internal relations among the zombie networks can be found out, the behavior modes of hacker groups behind the zombie networks can be tracked and researched more effectively, support and help are provided for network safety and network defense, and national macroscopic hierarchical internet safety research and control are promoted.
Owner:BEIJING TOPSEC SOFTWARE +3
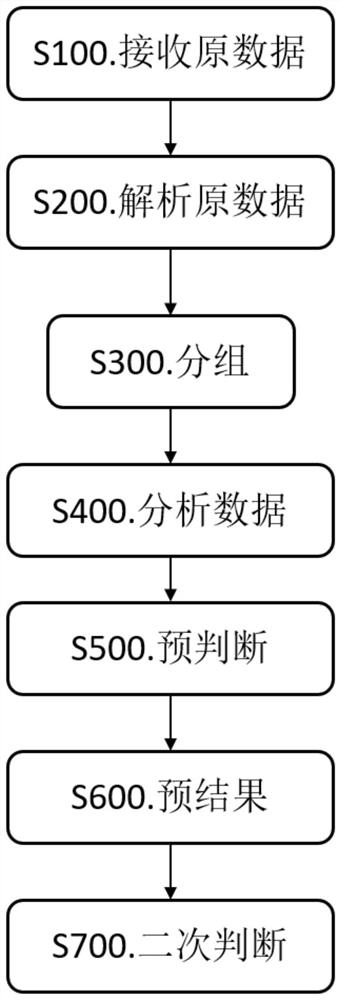
DDoS attack identification method and device and storage medium
ActiveCN112788039AImprove accuracyMeet high performance requirementsTransmissionHigh level techniquesComputer networkOriginal data
The invention provides a DDoS attack identification method and device with higher accuracy and a storage medium. The DDoS attack identification method comprises the following steps: receiving original data; analyzing the original data to obtain first processing data; grouping: grouping and converging the received data according to the first processing data; analyzing the data to obtain second processing data; pre-judgment: judging whether an attack occurs or not according to the second processing data; pre-result: generating the pre-result according to the pre-judgment result; and secondary judgment: judging whether the attack occurs or not according to the zombie, trojan and worm module and the pre-result. According to the invention, the accuracy of DDoS attack detection is improved, the false alarm rate is reduced, the performance requirement of a detection system is reduced, the problem that in a traditional detection method based on original flow, the performance requirement for hardware is too high is effectively solved, and therefore, the DDoS detection system is suitable for being deployed on various backbone large-bandwidth networks.
Owner:合肥浩瀚深度信息技术有限公司
Zombie network control node detection method and device
ActiveCN109962898AEnable Threat Intelligence Situational AwarenessImprove detection efficiencyTransmissionNetwork controlBotnet
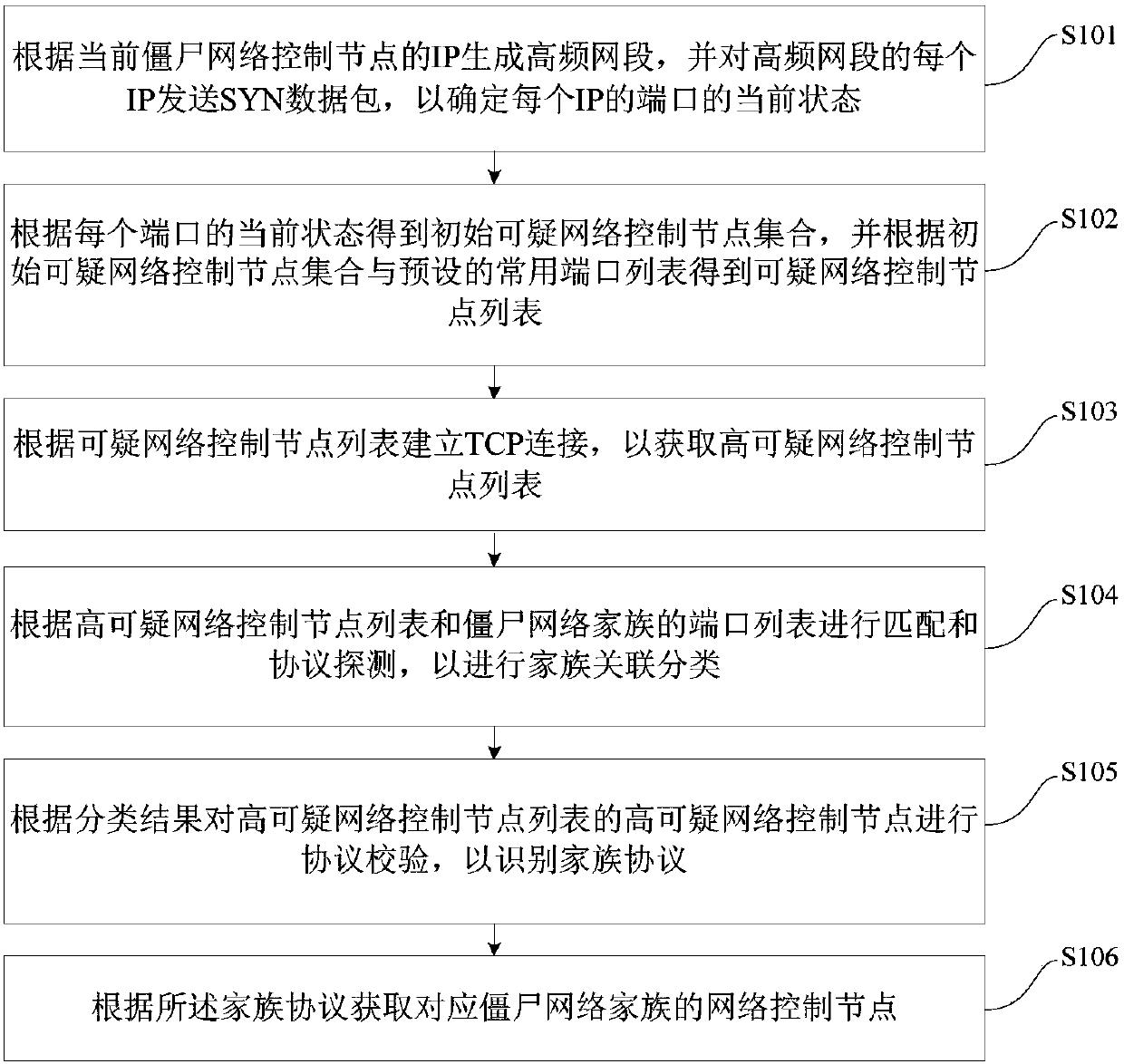
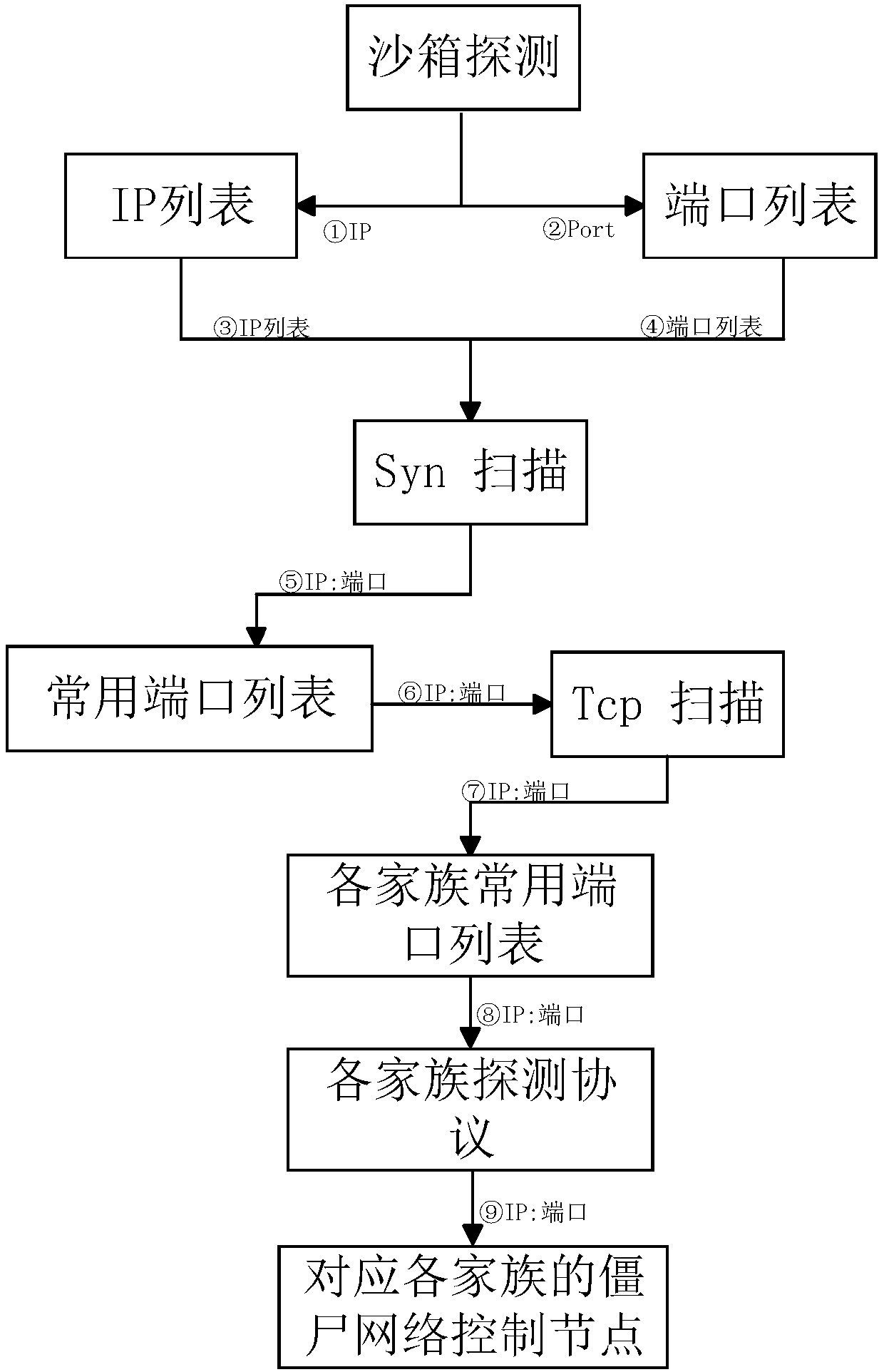
The invention discloses a zombie network control node detection method and device, and the method comprises the steps: generating a high-frequency network segment according to the IP of a current zombie network control node, so as to rapidly locate the position of a suspicious network control node; obtaining an initial suspicious network control node set according to the current state of the portof the high-frequency network segment IP, and obtaining a suspicious network control node list with a preset common port list; filtering according to the suspicious network control node list to obtaina high suspicious network control node list; performing matching and protocol detection according to the highly suspicious network control node list and the port list of the zombie network family; performing protocol verification on the highly suspicious network control nodes in the highly suspicious network control node list according to the classification result; and obtaining the network control node of the corresponding zombie network family according to the family protocol. The method accelerates automatic active analysis and detection of zombie network control nodes, detects more unknown zombie network control nodes, improves the detection efficiency, and improves the scanning efficiency.
Owner:HARBIN ANTIY TECH
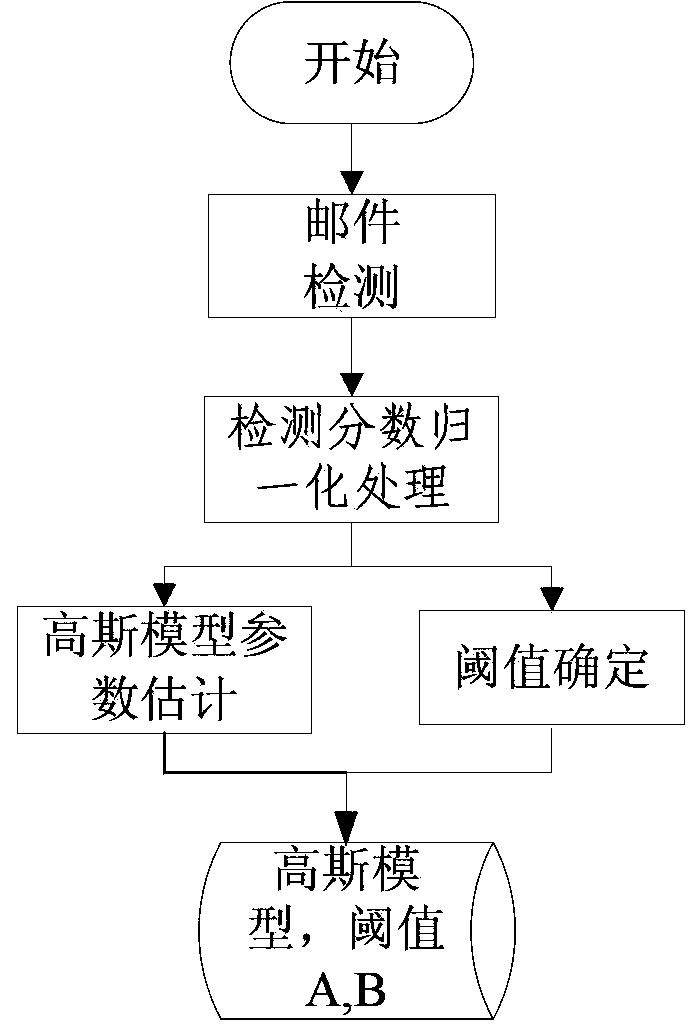
Spam botnet host detection method and device
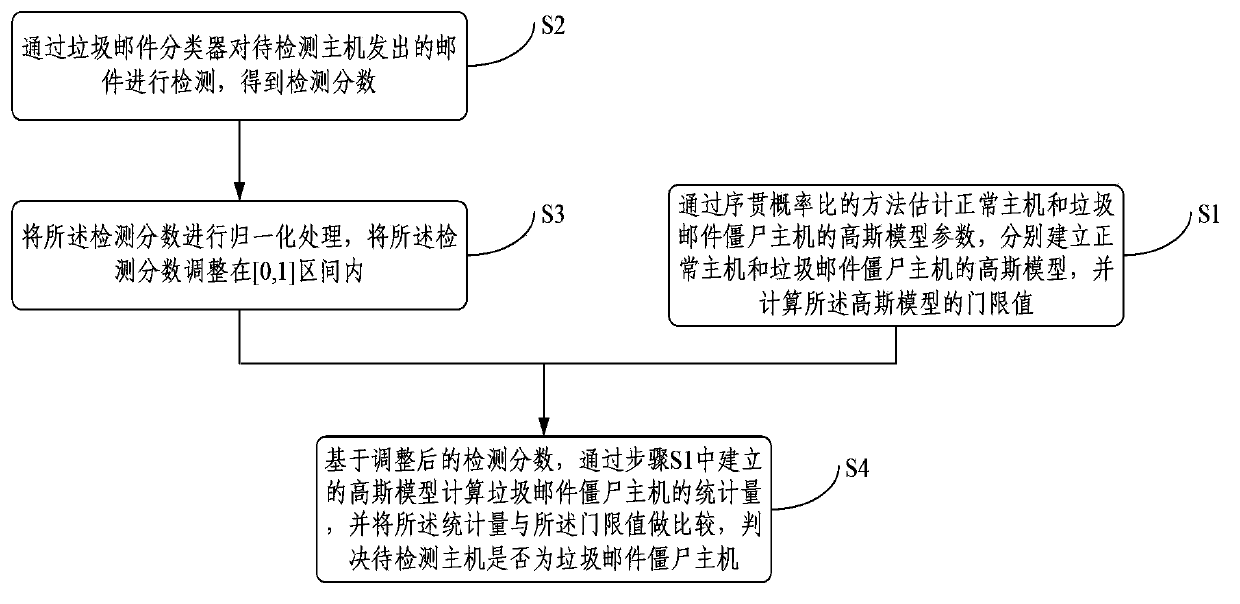
The invention provides a spam botnet host detection method and device and relates to the field of computer network security. The method includes a training phase and a detecting phase: S1, estimating Gaussian model parameters of a normal host and a spam botnet host by means of a sequential probability ratio method, establishing Gaussian models, and calculating thresholds of the Gaussian models; S2, detecting mails that a host to be detected send out, by a spam sorter so as to obtain detection scores; S3, normalizing the detection scores and adjusting the detection scores in a (0, 1) range; S4, on the basis of the adjusted detection scores, calculating a statistic of the spam botnet host by the Gaussian models established in the step S1, comparing the statistic with the thresholds, and judging whether or not the host to be detected is the spam botnet host or not. The botnet host which transmits spams is detected, an origin of transmitting the spams can be cut off, and substantially, fewer spams are transmitted.
Owner:HARBIN UNIV OF SCI & TECH
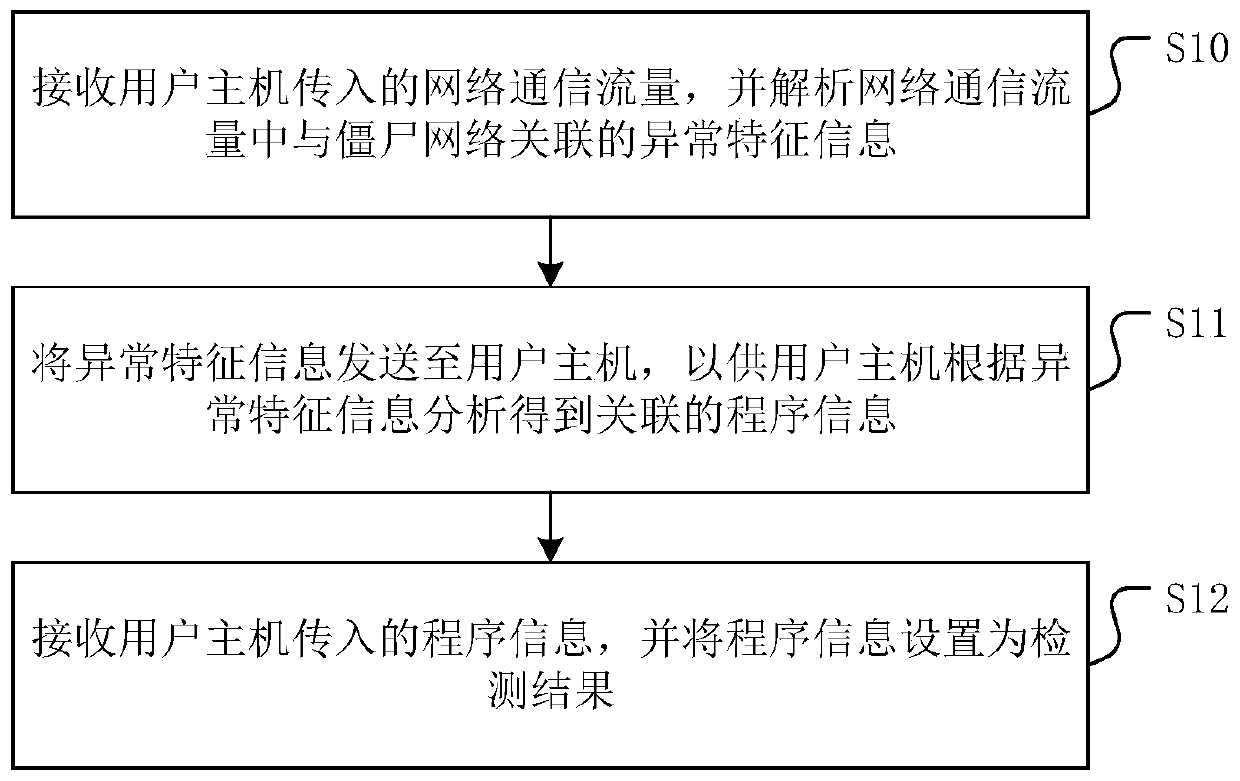
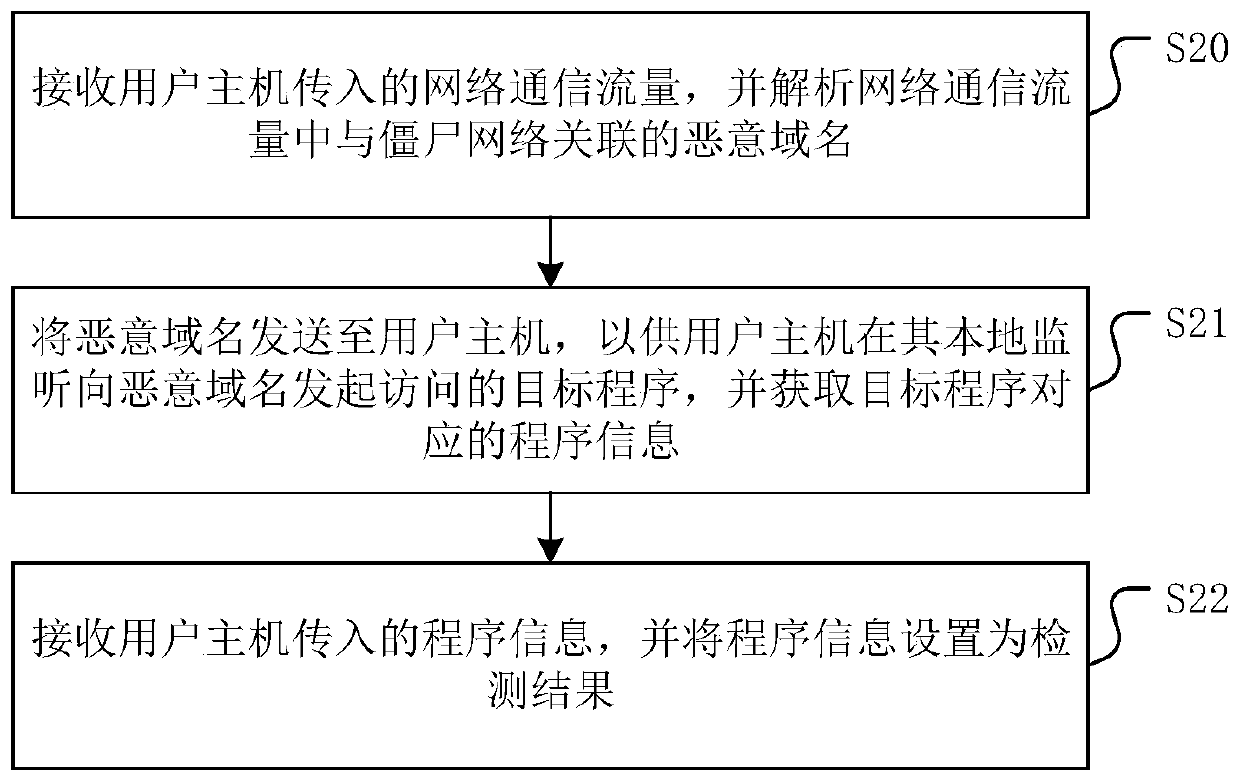
Botnet host detection method, system and device and storage medium
The invention discloses a zombie host detection method, system and device and a storage medium. According to the method, the linkage relationship between the firewall device and the user host is detected; after the firewall equipment detects that the user host has a zombie host behavior; furthermore, the information of the related programs causing the user host to have zombie host behaviors is obtained through the user host, so that the user can learn the abnormal programs causing the user host to have zombie host behaviors through the firewall, and the user is ensured to be capable of clearing the abnormal programs in the zombie host in a targeted manner. In addition, the invention further provides a zombie host detection system, zombie host detection equipment and a storage medium, whichhave the same beneficial effects.
Owner:SANGFOR TECH INC
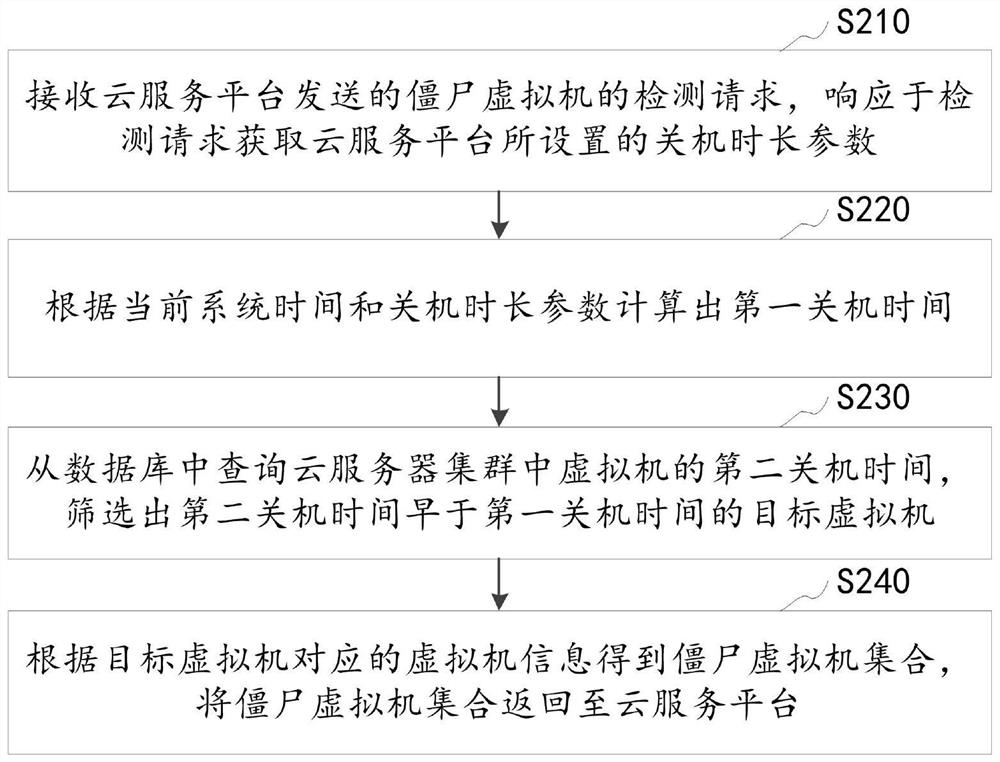
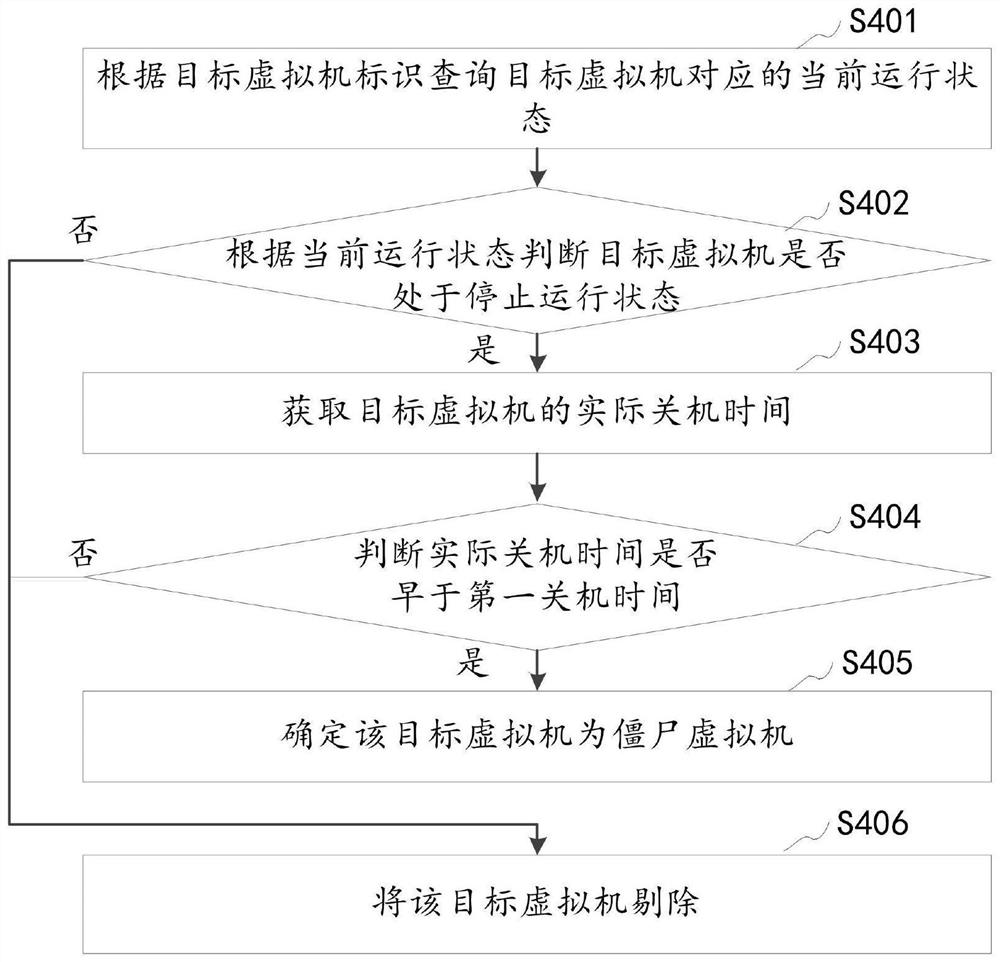
Zombie virtual machine detection method and device, computer device and storage medium
PendingCN114003339AImprove detection efficiencyDatabase management systemsSoftware simulation/interpretation/emulationShut downData bank
The invention relates to a zombie virtual machine detection method and device, a computer device and a storage medium, and relates to the technical field of virtual machines. The method comprises the steps of obtaining a shutdown duration parameter configured by a cloud service platform, calculating the first shutdown time according to the current system time and the shutdown duration parameter, and querying a target virtual machine of which the second shutdown time is earlier than the first shutdown time from a database, obtaining a zombie virtual machine set according to the virtual machine information corresponding to the target virtual machine, and returning the zombie virtual machine set to the cloud service platform. According to the above technical scheme, the detection efficiency of the zombie virtual machine can be improved.
Owner:济南浪潮数据技术有限公司
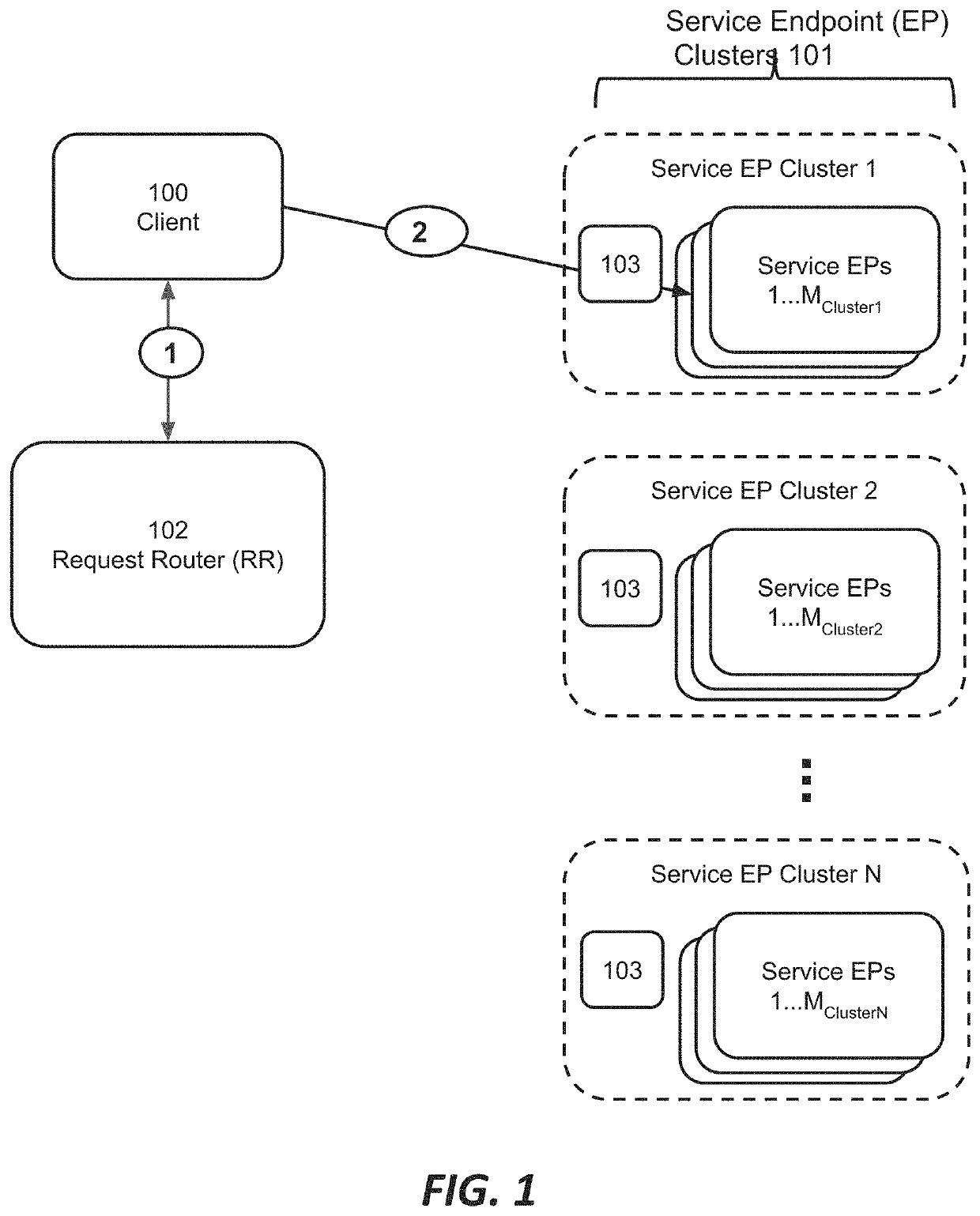
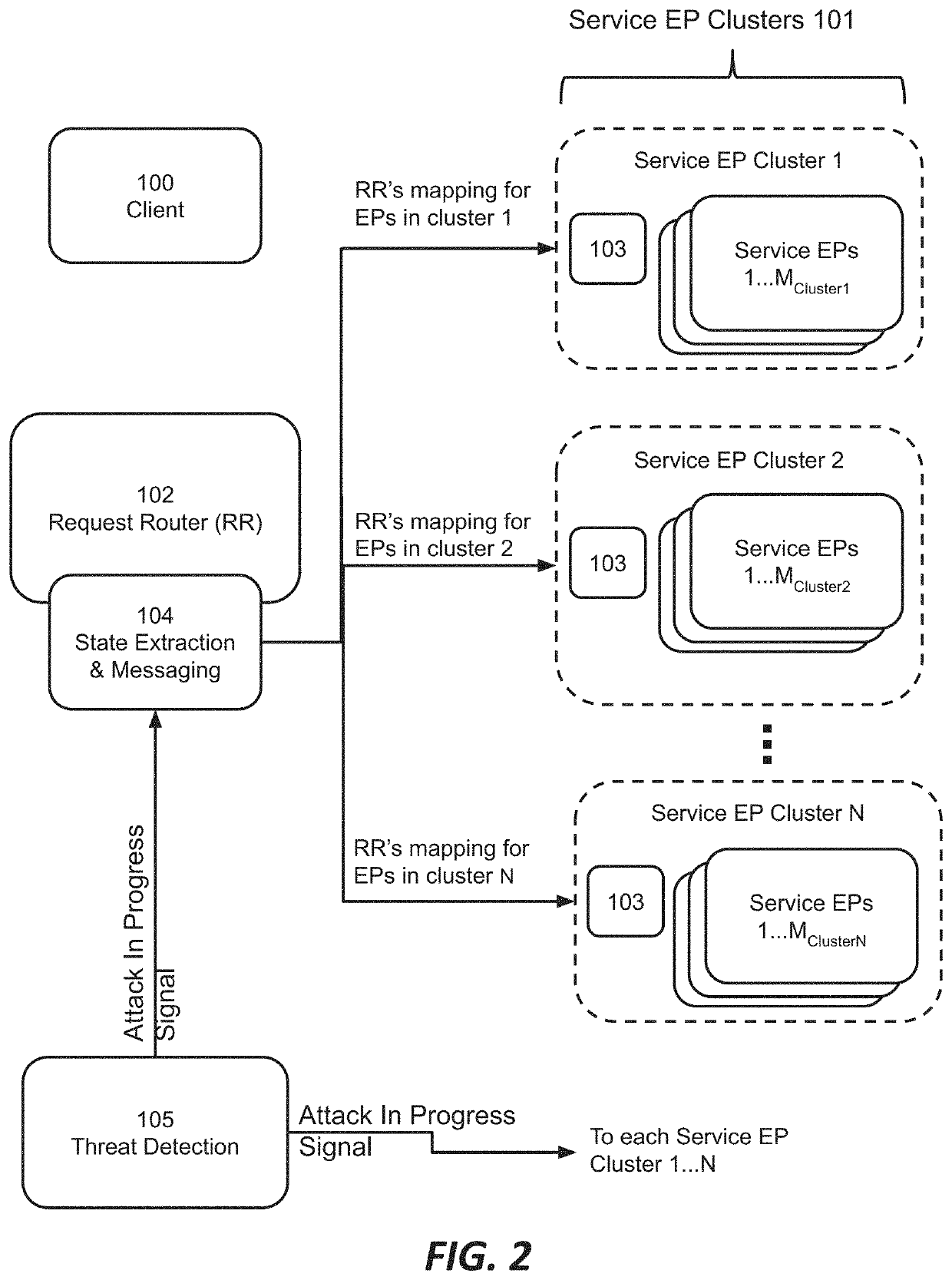
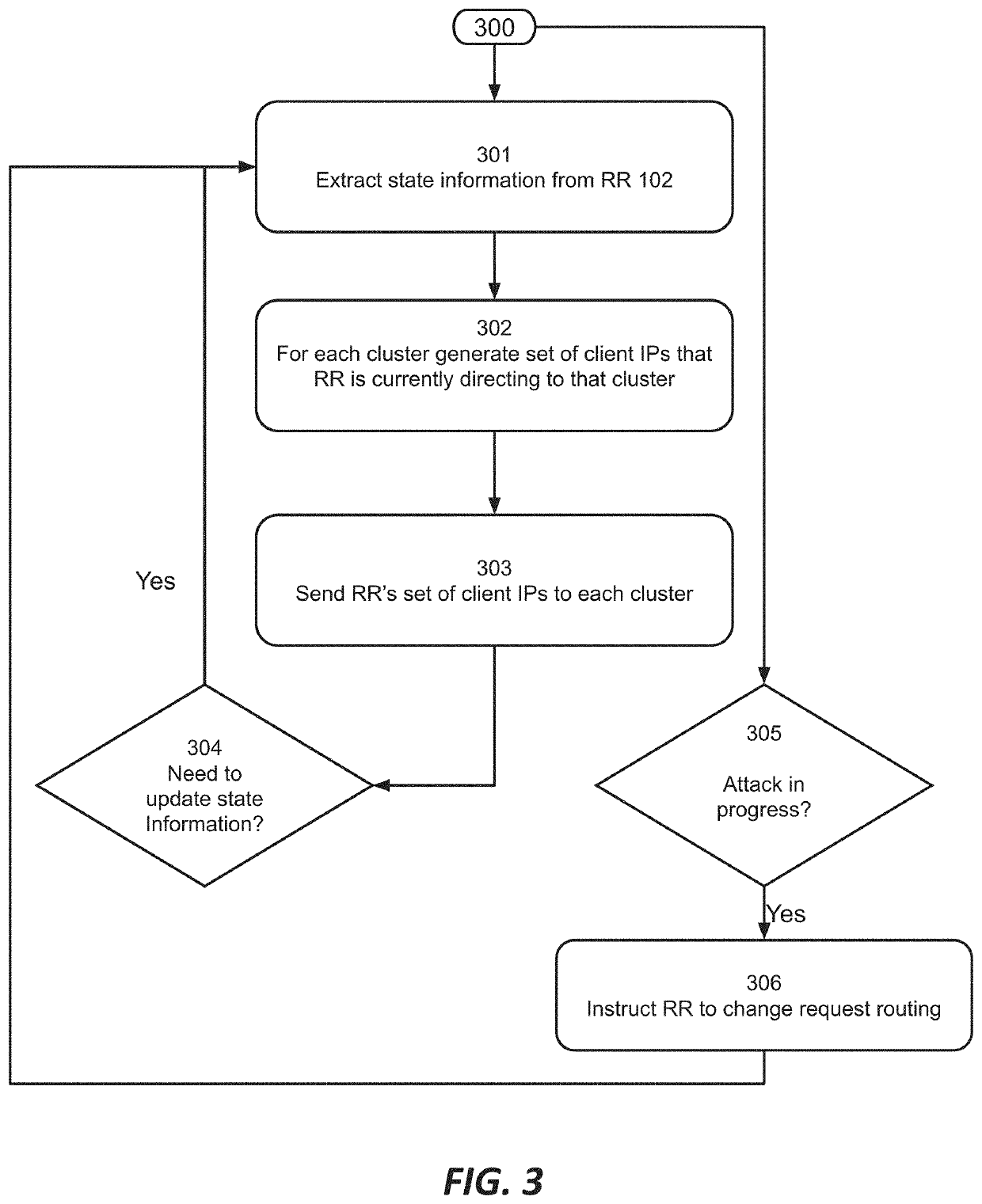
Using the state of a request routing mechanism to inform attack detection and mitigation
Among other things, this document describes systems, methods and apparatus for identifying and mitigating network attacks, particularly botnet attacks and other volumetric attacks. In some embodiments, a distributed computing platform provides client-facing service endpoints and a request routing mechanism (request router or RR) directing clients to a particular service endpoint or cluster thereof to obtain a service. The state of the RR at a given time is communicated to enforcement points in the system, which may be cluster equipment, service endpoints, or other components. When client traffic arrives at a particular enforcement point it is checked for consistency with the RR's directions, referred to as ‘mapping consistency’. This information is incorporated into decisions about how to handle the packets from the client.
Owner:AKAMAI TECH INC
Identification and removal of zombie virtual machines
Owner:LENOVO INT LTD
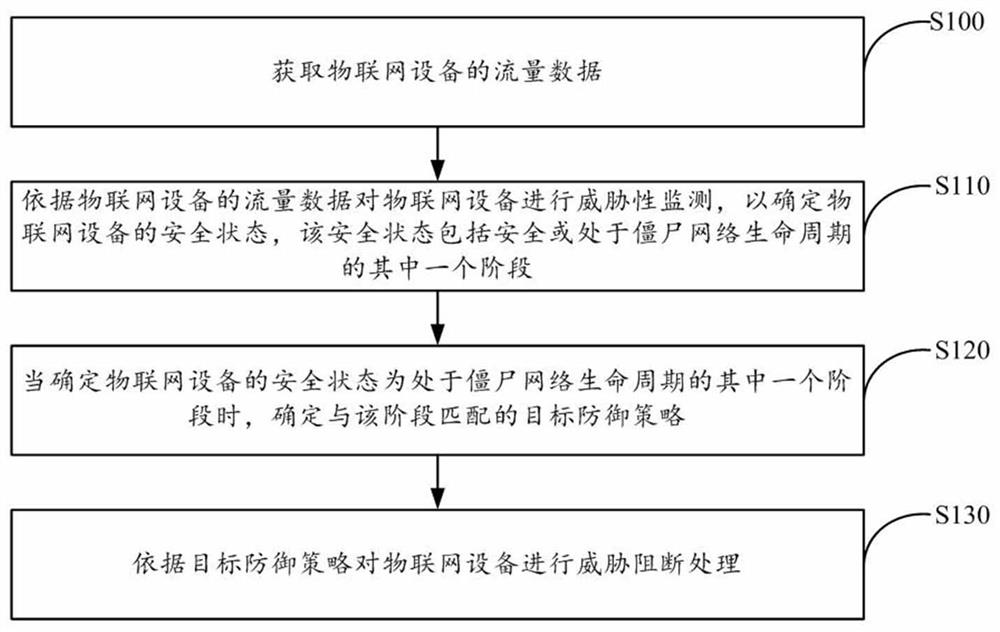
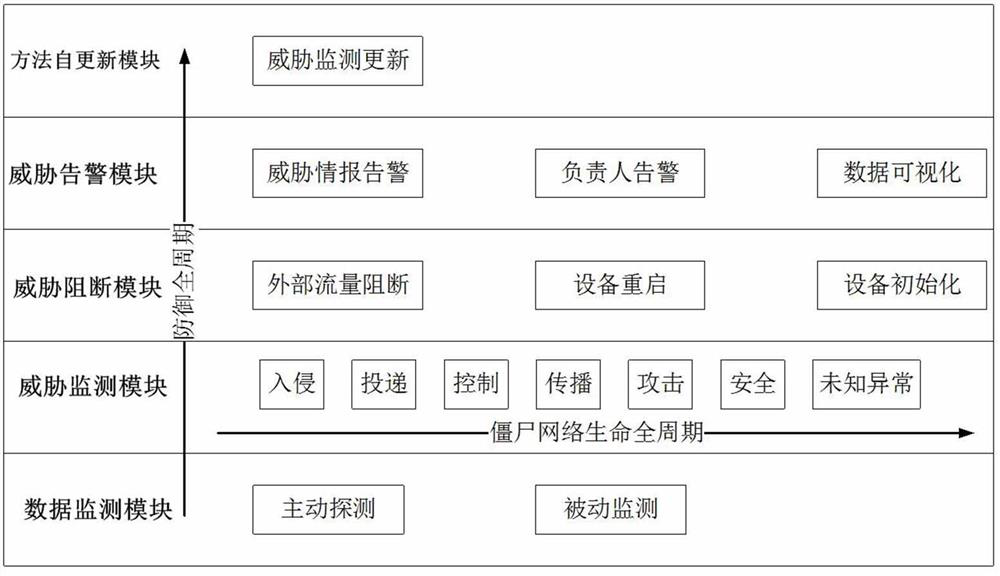
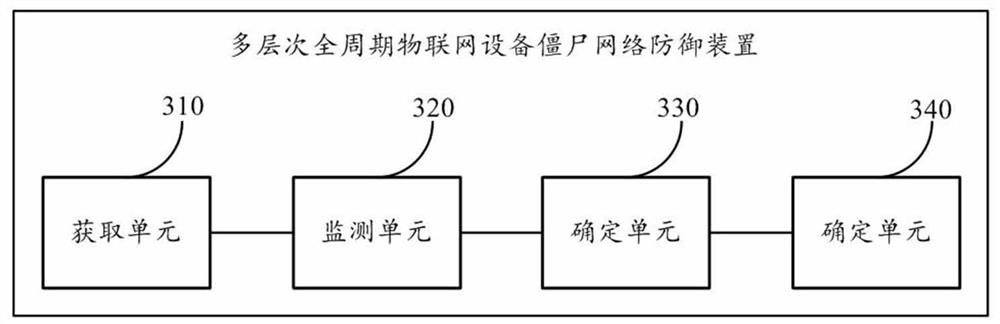
Botnet defense method, device and equipment for multi-level full-period Internet of Things equipment
The invention provides a multilevel full-period botnet defense method, device and equipment for Internet of Things equipment. The method comprises the following steps: acquiring flow data of the Internet of Things equipment; performing threat monitoring on the Internet of Things equipment according to the flow data of the Internet of Things equipment to determine the security state of the Internet of Things equipment, wherein the security state comprises a security state or a stage in a botnet life cycle; when it is determined that the security state of the Internet of Things equipment is in one stage of a botnet life cycle, determining a target defense strategy matched with the stage; and performing threat blocking processing on the Internet of Things equipment according to the target defense strategy. According to the method, the botnet defense effect of the Internet of Things equipment can be optimized.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Rdma transport with hardware integration and out of order placement
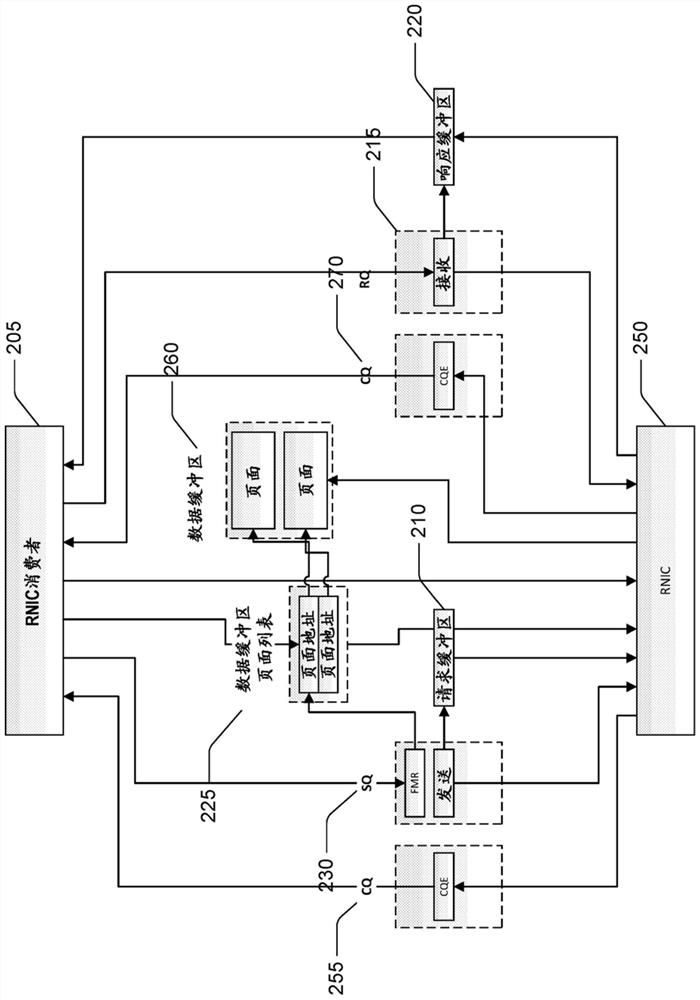
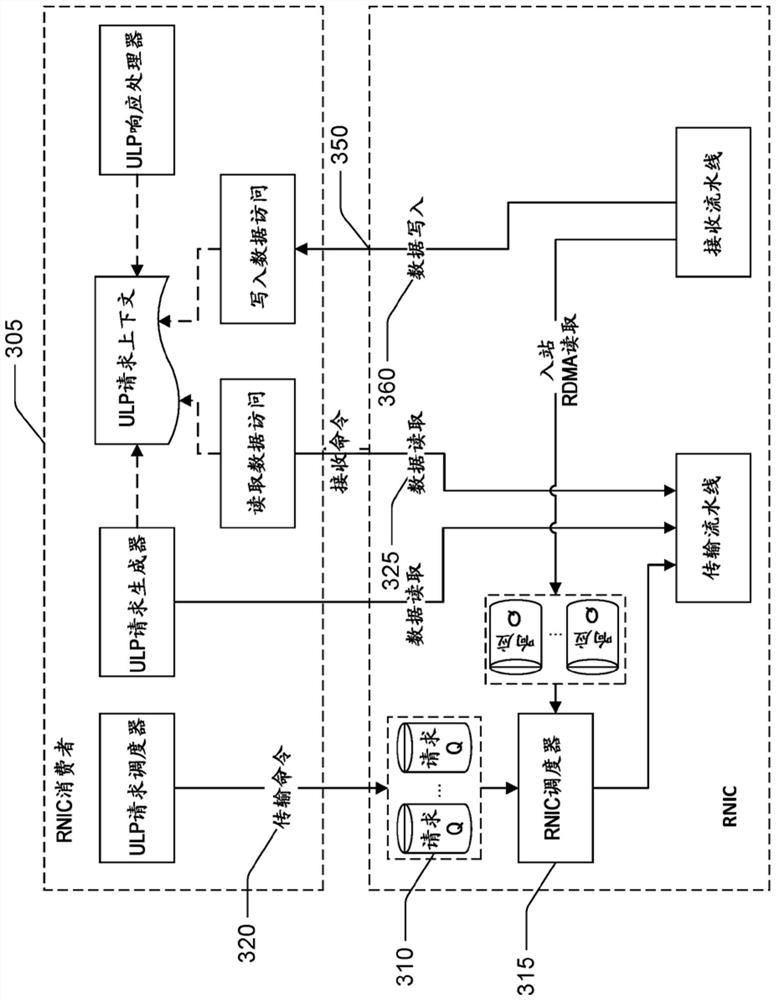
PendingCN113490927AIncrease workloadReduce latency jitterError preventionInterprogram communicationVirtualizationDirect memory access
Techniques are disclosed for implementing direct memory access in a virtualized computing environment. A new mapping of interfaces between RNIC consumer and RDMA transport is defined, which enables the efficient retry, a zombie detection mechanism, and identification and handling of invalid requests without bringing down the RDMA connection. Techniques are disclosed for out of order placement and delivery of ULP Requests without constraining the RNIC consumer to the ordered networking behavior, if it is not required for the ULP (e.g., storage). This allows the efficient deployment of an RDMA accelerated storage workload in a lossy network configuration, and reduction in latency jitter.
Owner:MICROSOFT TECH LICENSING LLC
Method for identifying and processing private zombie virtual machine
PendingCN112214278AImprove resource utilization efficiencyWide range of applicationsSoftware simulation/interpretation/emulationSoftware engineeringCloud management
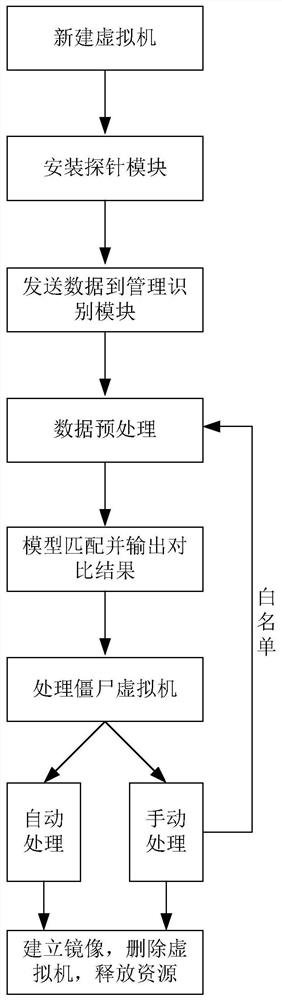
The invention discloses a private zombie virtual machine identification and processing method, which comprises the following steps of S1, newly establishing a virtual machine through a cloud management platform; S2, installing a probe module in the virtual machine; s3, sending data to a cloud platform management identification module; S4, preprocessing the data and identifying zombie virtual machines; and S5, processing the zombie virtual machine. The invention provides the identification and processing method of the private zombie virtual machine, which solves the problems of identification and processing of the private zombie virtual machine, reduces computing resources occupied by the zombie virtual machine, reduces system entropy increase and improves the availability of a private cloud platform.
Owner:ZHEJIANG WINDEY
DDoS malicious code detection and traceability method based on breeding
ActiveCN112261029AAccurate analysisImprove farming efficiencyPlatform integrity maintainanceTransmissionAttackEngineering
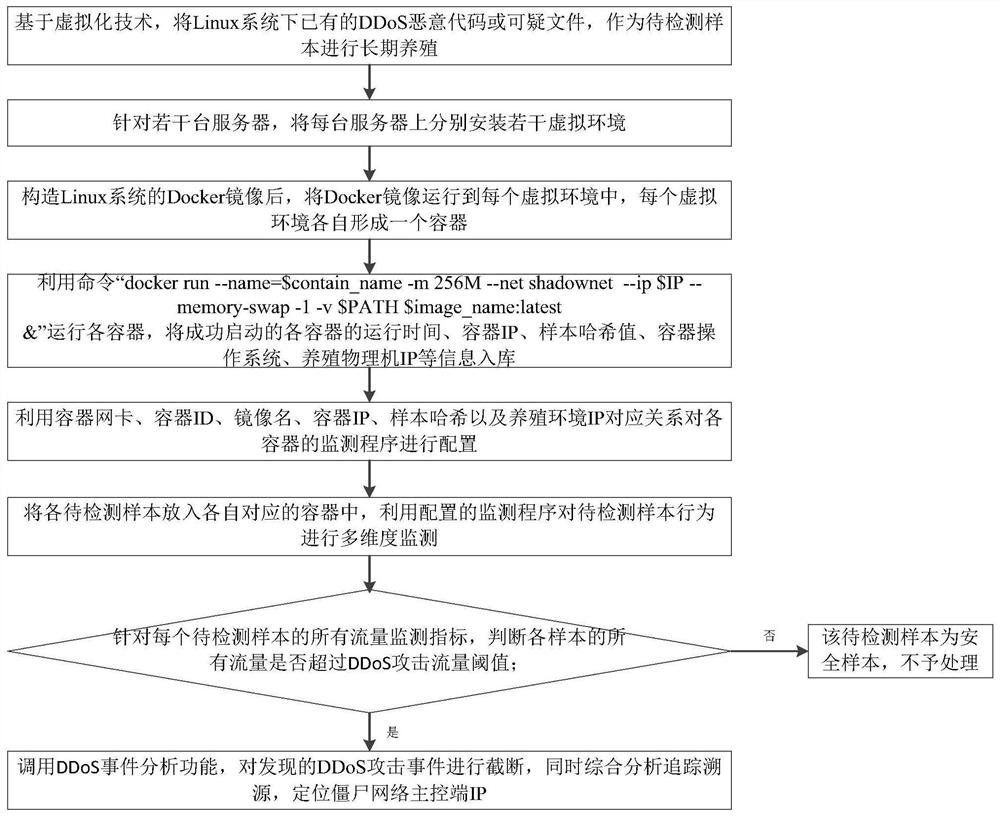
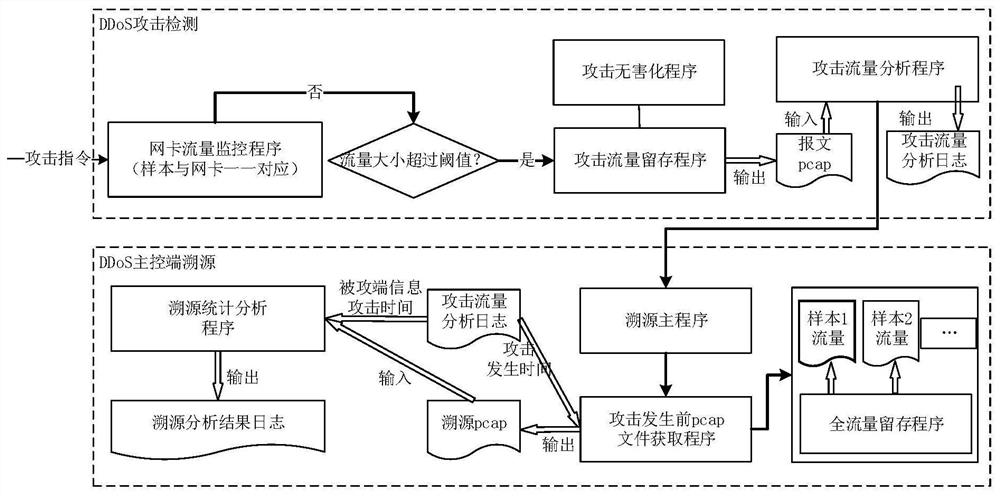
The invention discloses a breeding-based DDoS malicious code detection and tracing method, and relates to the technical field of network security. The method specifically comprises the steps that firstly, existing DDoS malicious codes or suspicious files under a Linux system serve as samples to be detected to be bred for a long time; constructing a Docker mirror image of the Linux system, runningthe Docker mirror image into each virtual environment of each server to form a container, successfully starting each container, storing running information into a database, and configuring a monitoring program of each container; then, putting each to-be-detected sample into a respective corresponding container, and carrying out multi-dimensional monitoring on the behavior of the to-be-detected sample by utilizing a monitoring program; and judging whether all traffic of each sample exceeds a DDoS attack traffic threshold, and if so, calling a DDoS event analysis function to cut off a discoveredDDoS attack event, comprehensively analyzing, tracking and tracing, and positioning an IP of a botnet main control end. Otherwise, the to-be-detected sample is a safe sample and is not processed. Themaster control end of the puppet machine can be effectively tracked.
Owner:BEIJING RUICHI XINAN TECH
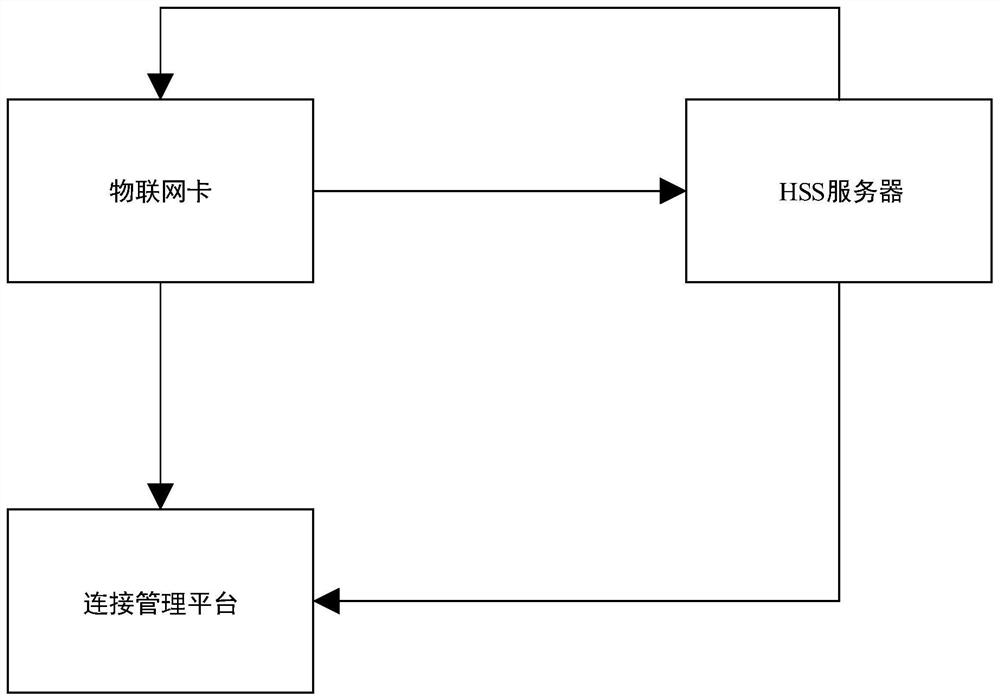
Method and system for preventing DDOS (Distributed Denial of Service) attack of zombie terminal
ActiveCN114268509ADDOS attack solutionImprove communication success rateSecurity arrangementSecuring communicationThe InternetConnection management
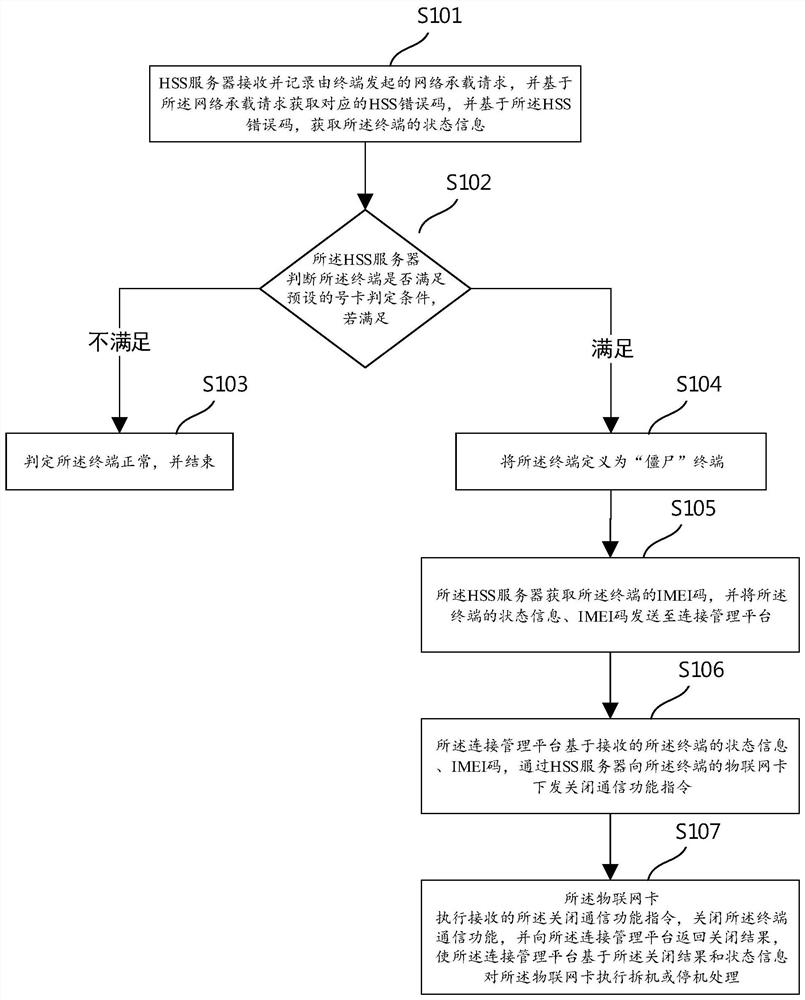
The invention discloses a method and a system for preventing DDOS (Distributed Denial of Service) attack of a zombie terminal. The method comprises the steps that an HSS server receives and records a network bearing request initiated by a terminal, obtains a corresponding HSS error code and state information of the terminal, judges whether the terminal meets a preset number card judgment condition or not, and defines the terminal as a zombie terminal if the terminal meets the preset number card judgment condition; after the terminal is judged to be a zombie terminal, the HSS server obtains an IMEI code of the terminal and sends the IMEI code to the connection management platform; the connection management platform issues a communication function closing instruction to the Internet of Things card of the terminal; and the Internet of Things card executes the received communication function closing instruction, closes the communication function of the terminal, and returns a closing result, so that the connection management platform executes disassembly or shutdown processing on the Internet of Things card. According to the method, the zombie terminal is automatically found fundamentally, the operation of closing the communication function module is carried out on the zombie terminal, the problem that the zombie terminal initiates the DDOS attack is thoroughly solved, and the communication success rate of the area is remarkably improved.
Owner:E SURFING IOT CO LTD
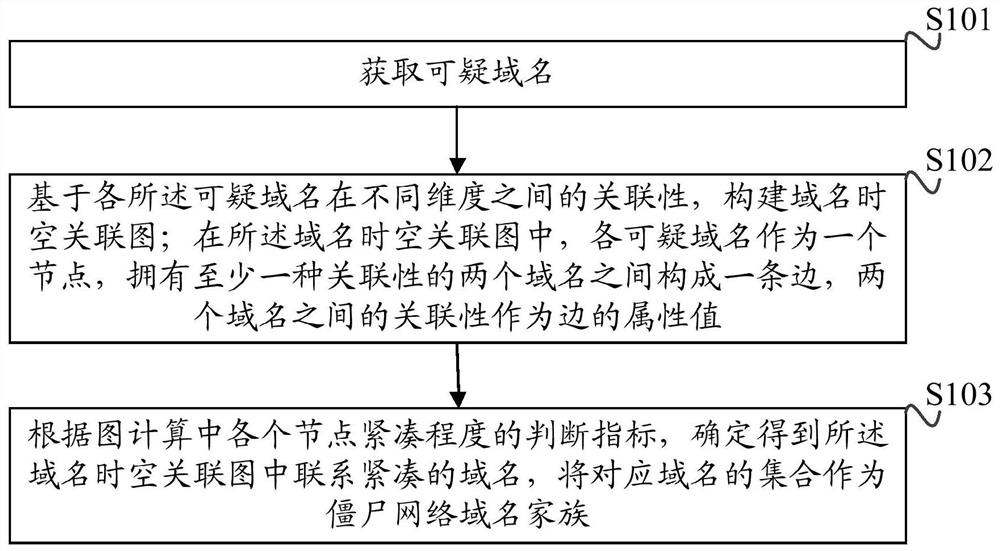
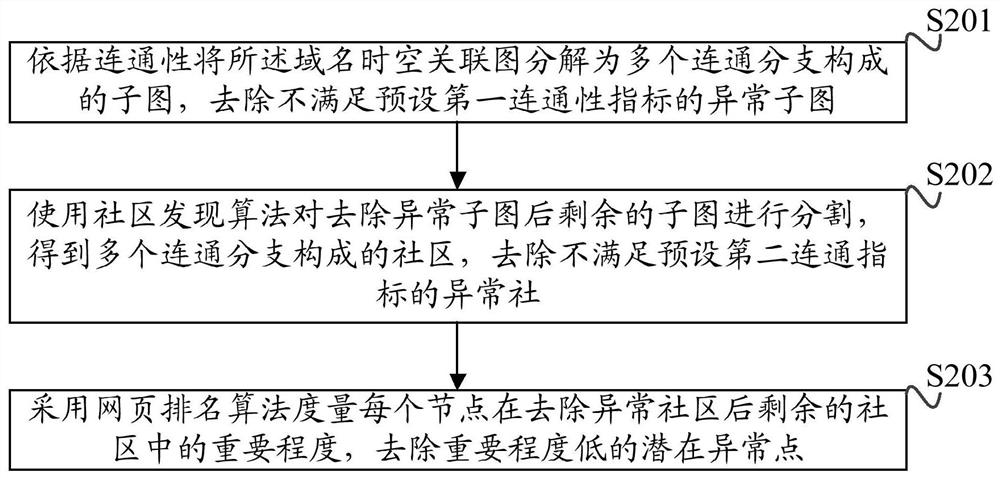
Detection method, device, equipment and storage medium of botnet domain name family
The invention discloses a detection method of a botnet domain name family. By obtaining suspicious domain names; based on the relevance of each suspicious domain name in different dimensions, a domain name space-time correlation graph is constructed; in the domain name spatio-temporal correlation graph, each suspicious domain name is used as a Nodes, two domain names with at least one kind of correlation form an edge, and the correlation between the two domain names is used as the attribute value of the edge; according to the judgment index of the compactness of each node in the graph calculation, it is determined to obtain the domain name space-time correlation graph The closely related domain names in the domain name are used as the set of corresponding domain names as the botnet domain name family. In this application, the correlation between different dimensions between domain names is uniformly expressed in the form of a correlation graph, which has stronger detection capabilities. At the same time, it can detect zombie domain name families more quickly and has wider applicability. In addition, the present application also provides a detection device, device and computer-readable storage medium of a botnet domain name family having the above-mentioned technical advantages.
Owner:SANGFOR TECH INC
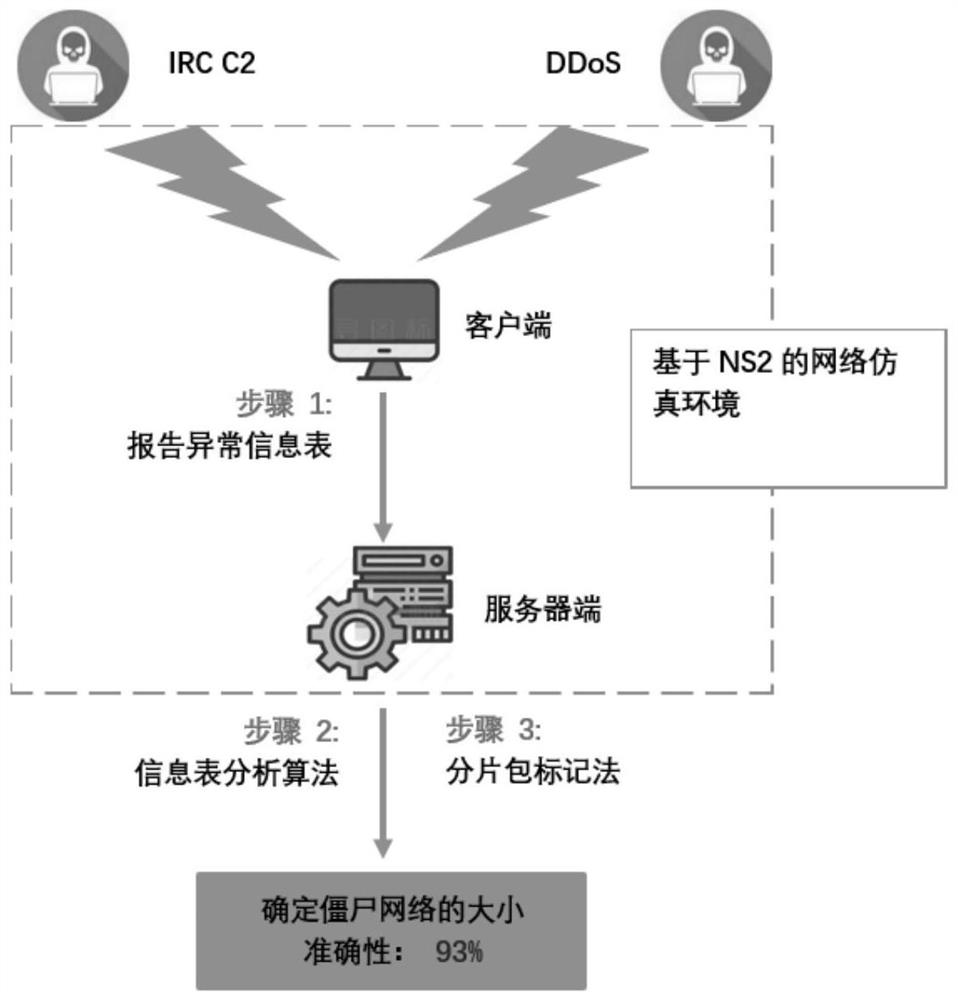
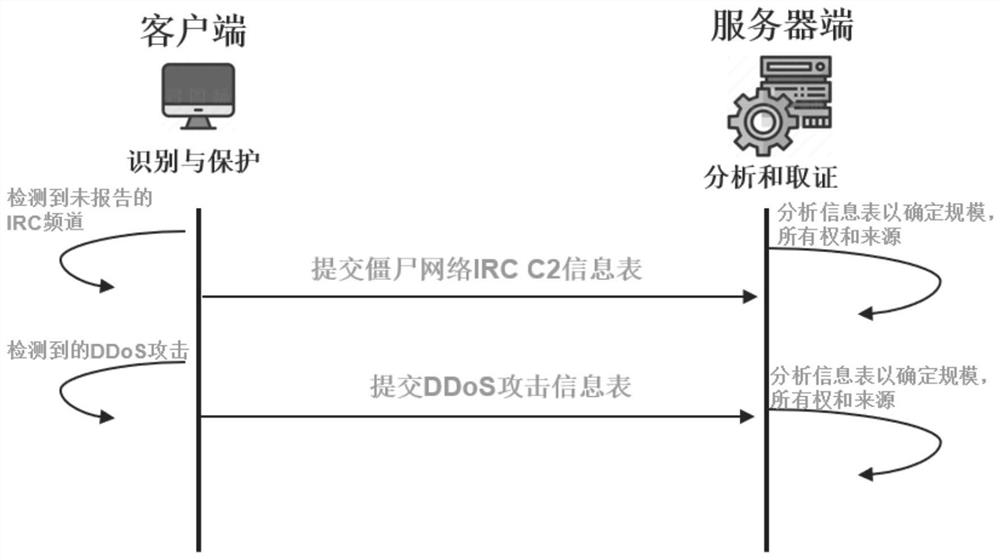
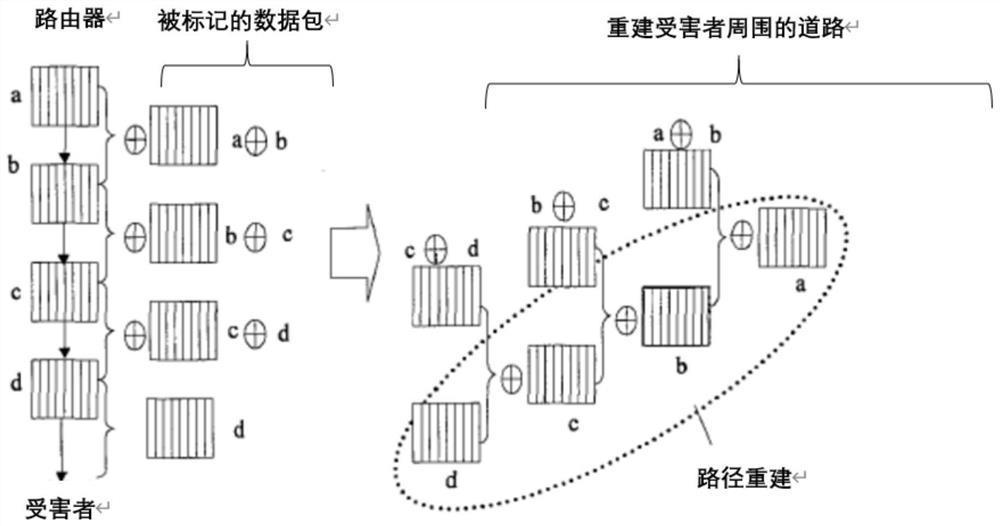
Evidence obtaining method and system for DDoS attack
The invention discloses an evidence obtaining method and system for a DDOS attack. The method comprises the following steps: reporting an abnormal information table; analyzing the information table; and representing a FMS data packet. The system comprises an NS2 simulation module, an anomaly reporting module, an analysis algorithm module and a fragment packet marking method module. According to the system, the network environment and the network nodes are simulated by using the NS2, so that not only can the real network environment be simulated, but also network paralysis caused by actual attacks can be prevented. All analysis algorithms can be realized in NS2 simply and efficiently without complex tools. According to the method, a botnet and DDoS attack electronic evidence analysis methodis used, fragment data packet marks are used when a server analyzes the electronic evidences so as to track the source and path reconstruction of a router, and therefore the scale recognition rate isincreased to 93%.
Owner:NANJING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com