Botnet program domain name identification method and device, equipment and storage medium
A technology of bots and domain names, applied in the field of network security, can solve the problems of consuming computing resources, low detection accuracy, poor real-time performance of DGA domain names, etc., and achieve the effect of reducing false alarm rate and improving accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0034] Unless otherwise defined, all technical and scientific terms used herein have the same meaning as commonly understood by one of ordinary skill in the technical field of the invention. The terms used herein in the description of the present invention are for the purpose of describing specific embodiments only, and are not intended to limit the present invention.
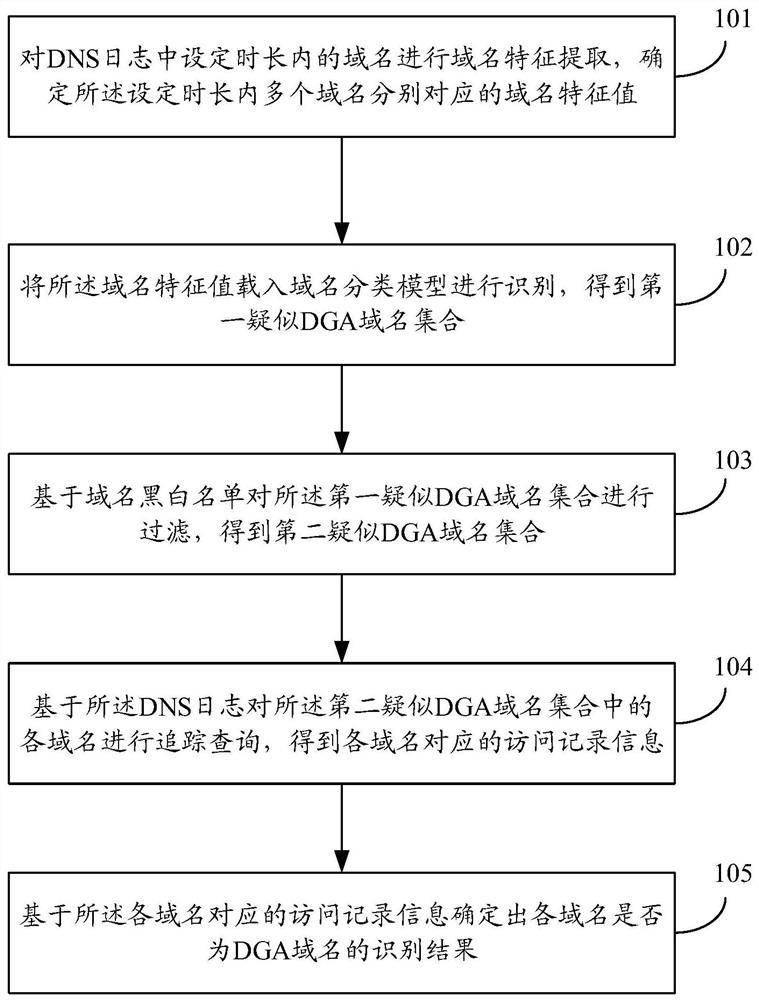
[0035] The embodiment of the present invention provides a method for identifying a bot domain name, such as figure 1 As shown, the method includes:
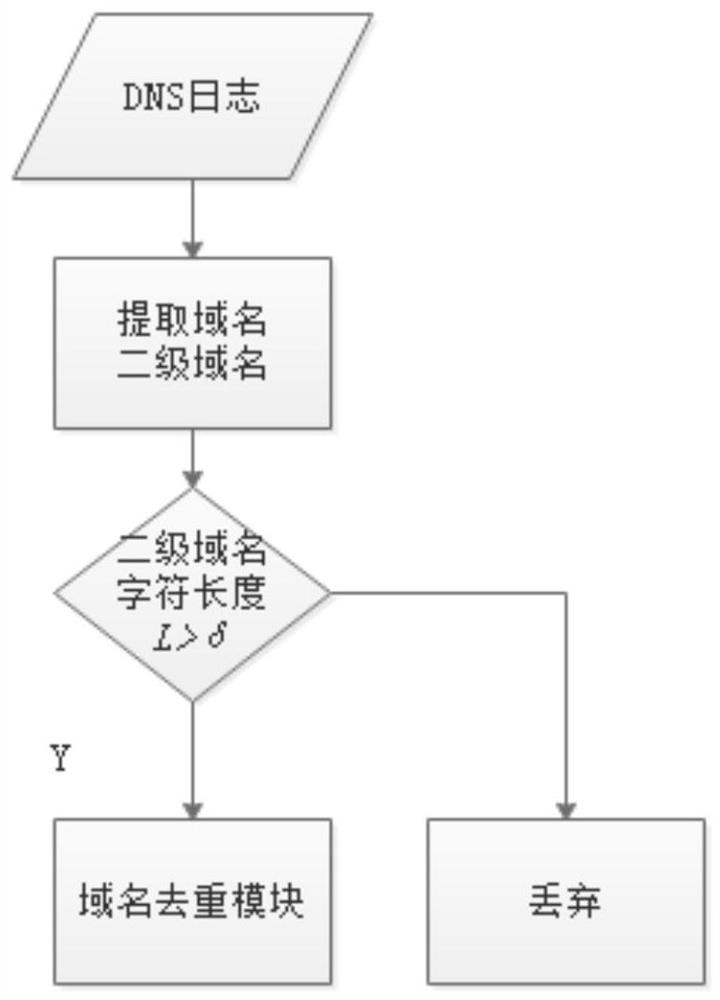
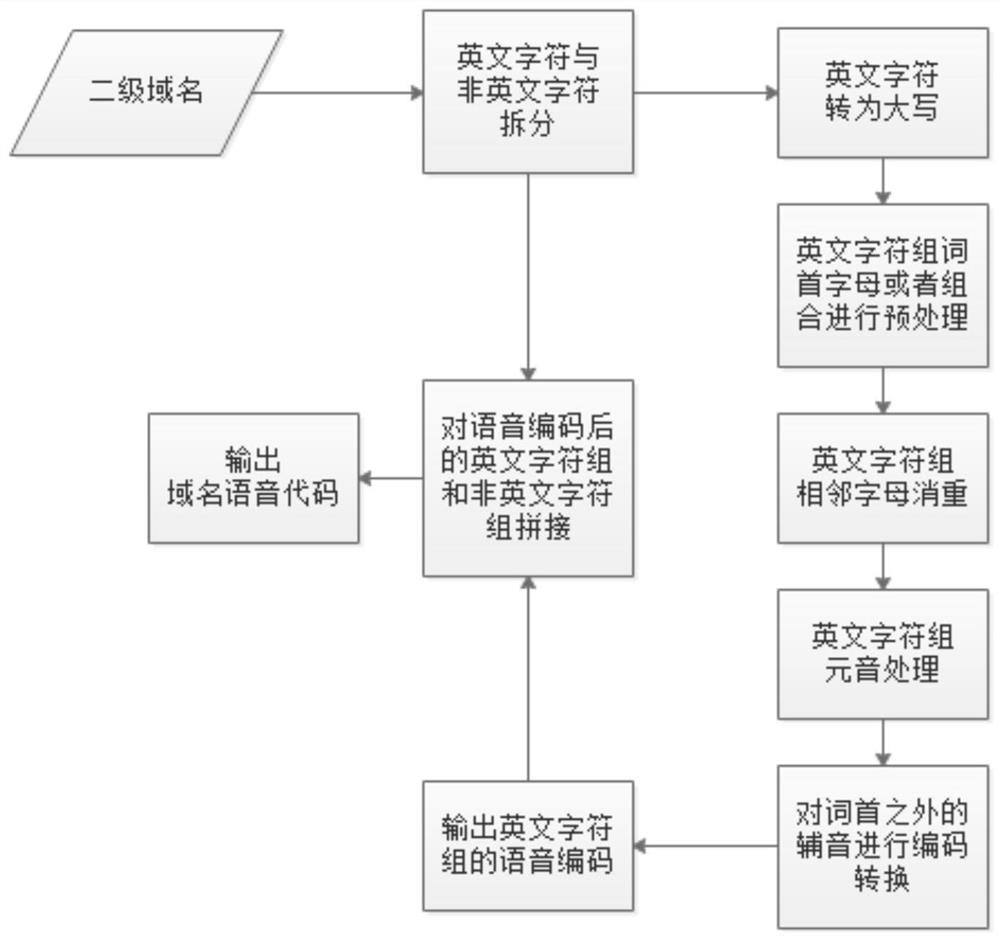
[0036] Step 101, performing domain name feature extraction on domain names within a set time period in the DNS log, and determining domain name feature values corresponding to multiple domain names within the set time period;
[0037] Step 102, loading the feature value of the domain name into the domain name classification mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com