Detector for binary-code buffer-zone overflow bugs, and detection method thereof
A binary code, buffer overflow technology, applied in instruments, software testing/debugging, multi-programming devices, etc., can solve problems such as affecting accuracy, inability to determine whether memory operands point to the same memory address, incomplete analysis, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
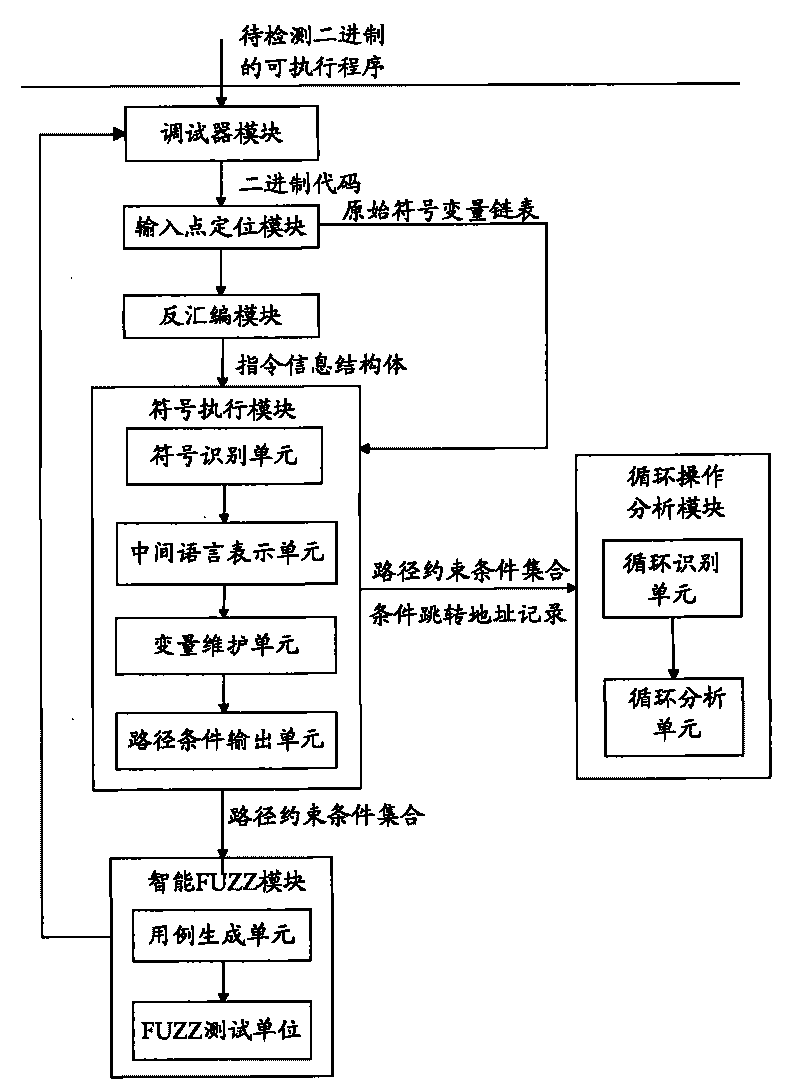
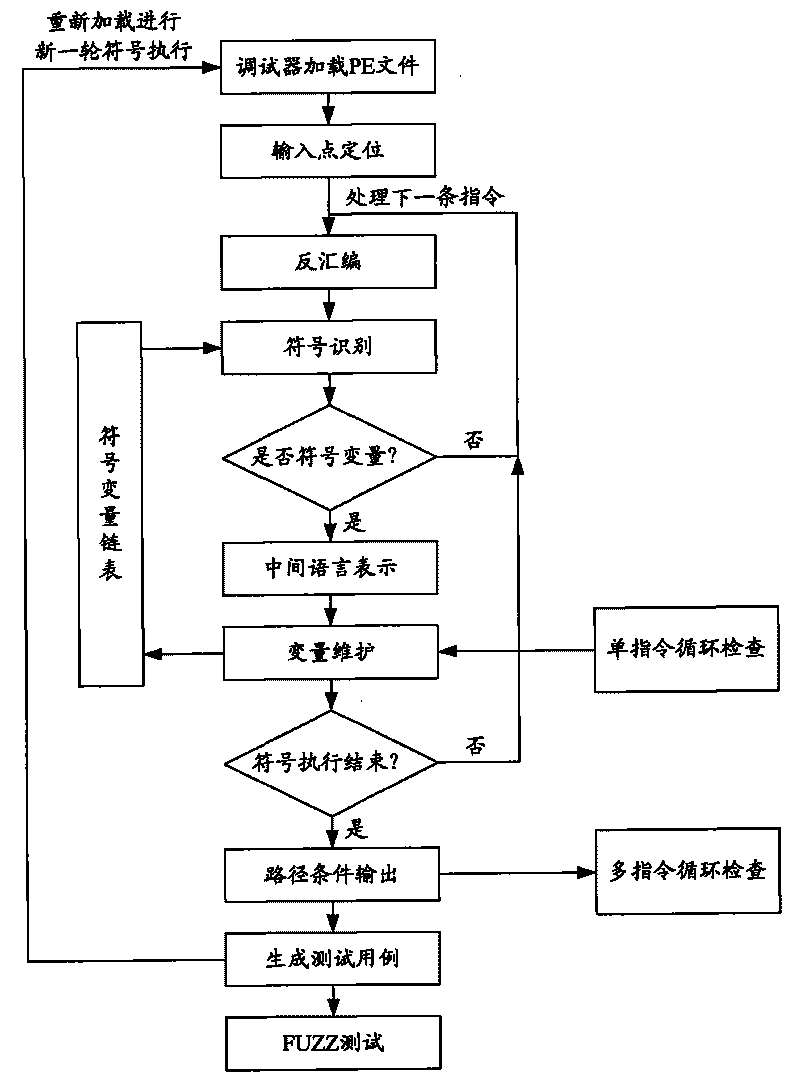
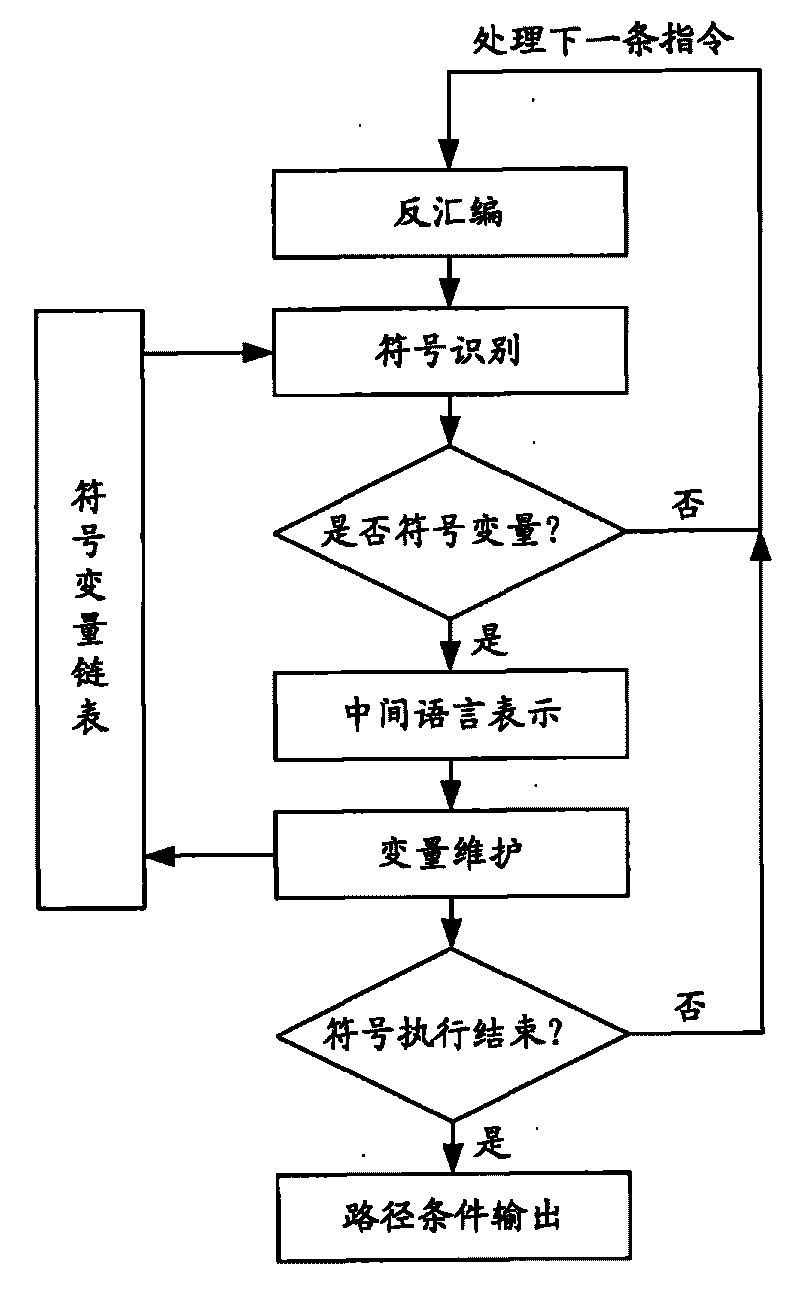
[0065] The present invention is an overflow vulnerability detector based on symbolic execution and combined with the actually executed binary code buffer, which can monitor all executable EXE programs in PE format and related The code in the DLL file of the dynamic link library performs path coverage testing and overflow vulnerability detection on all executable programs in PE format; in order to detect buffer overflow vulnerabilities of various executable programs under the Windows platform, and discover overflow vulnerabilities at the same time , giving information about the cause of the vulnerability.
[0066] see figure 1 , introduce the structural composition of overflow loophole detector of the present invention, it is provided with six software function modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com