Patents
Literature
160 results about "Top level domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
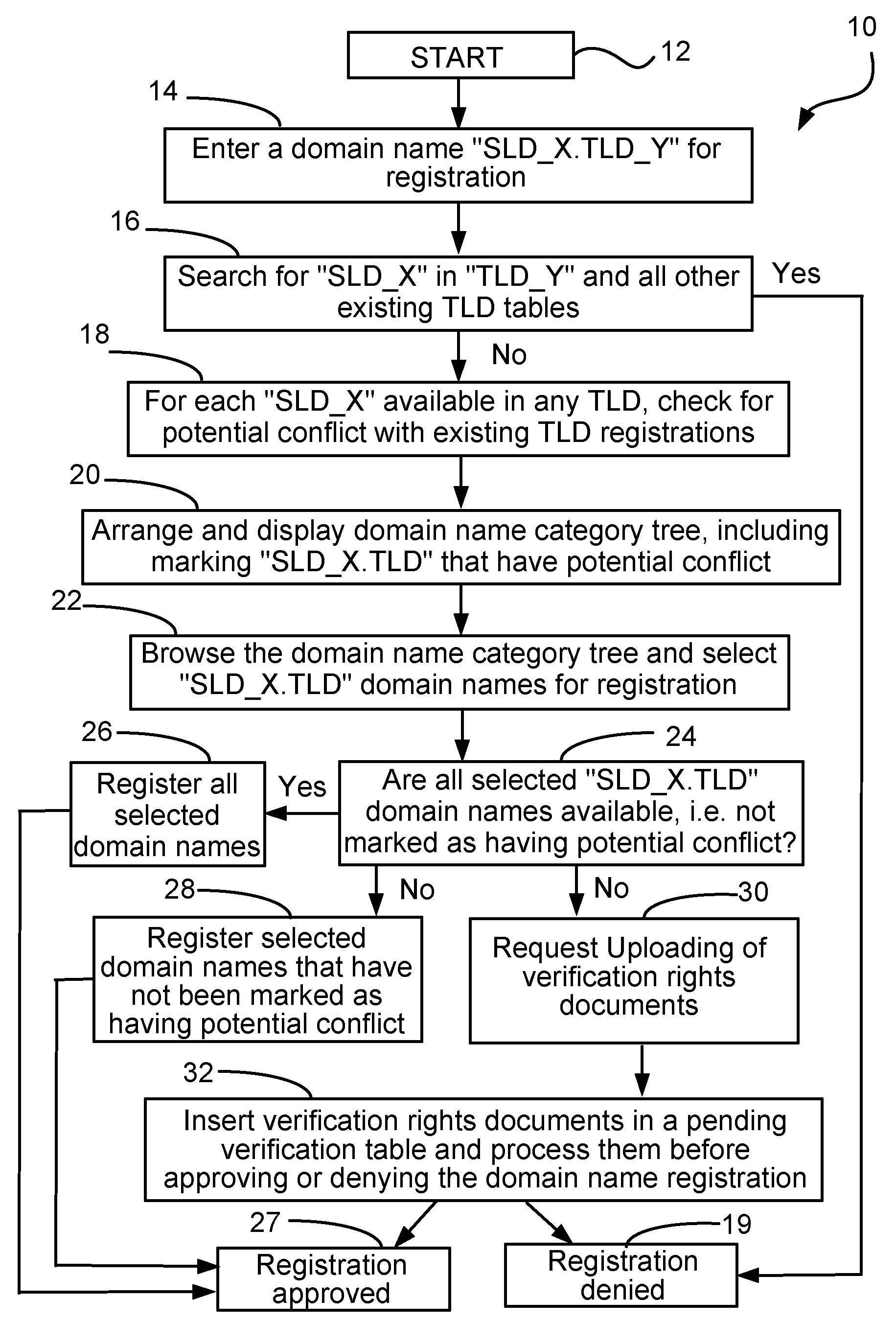
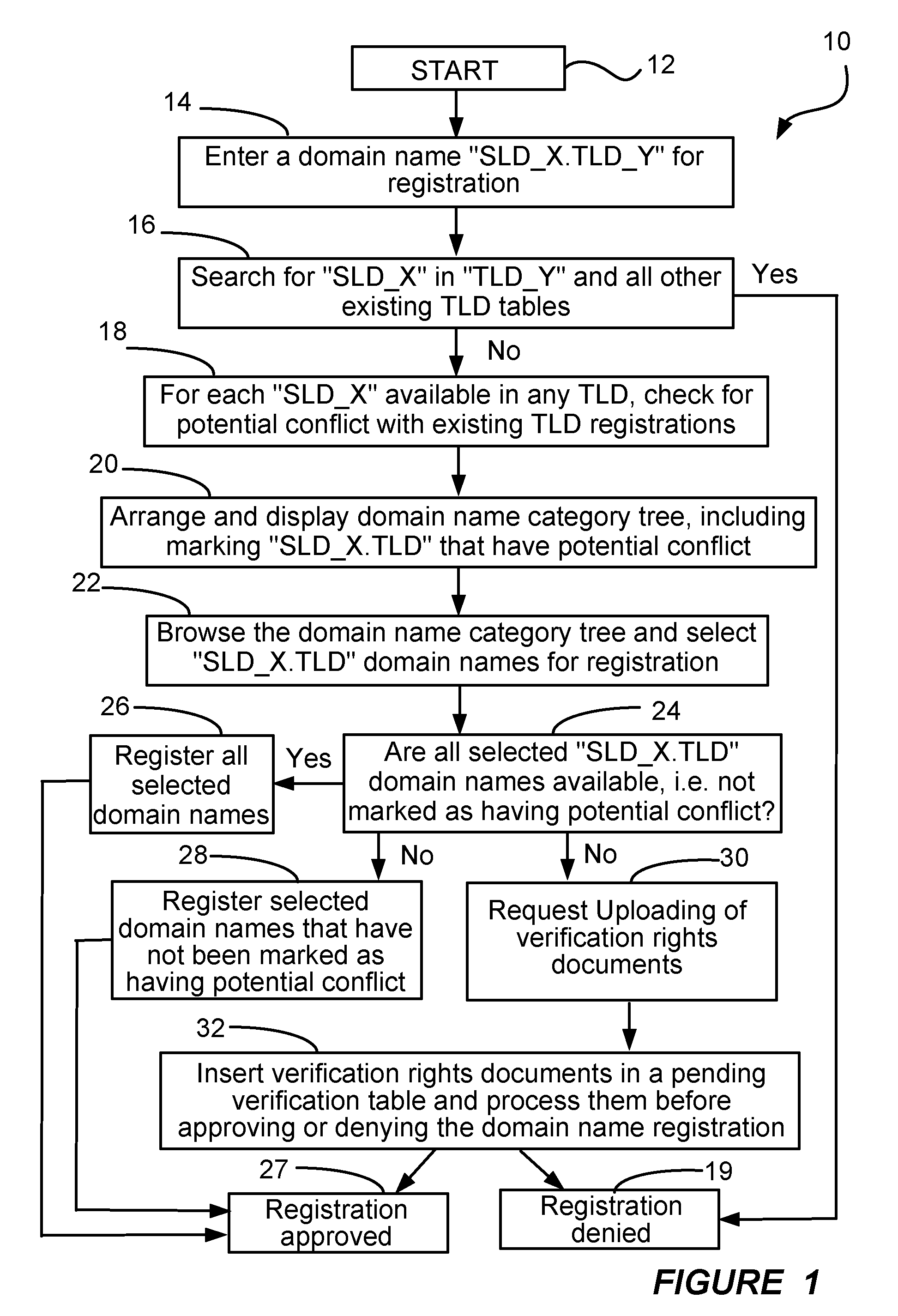
Inventor
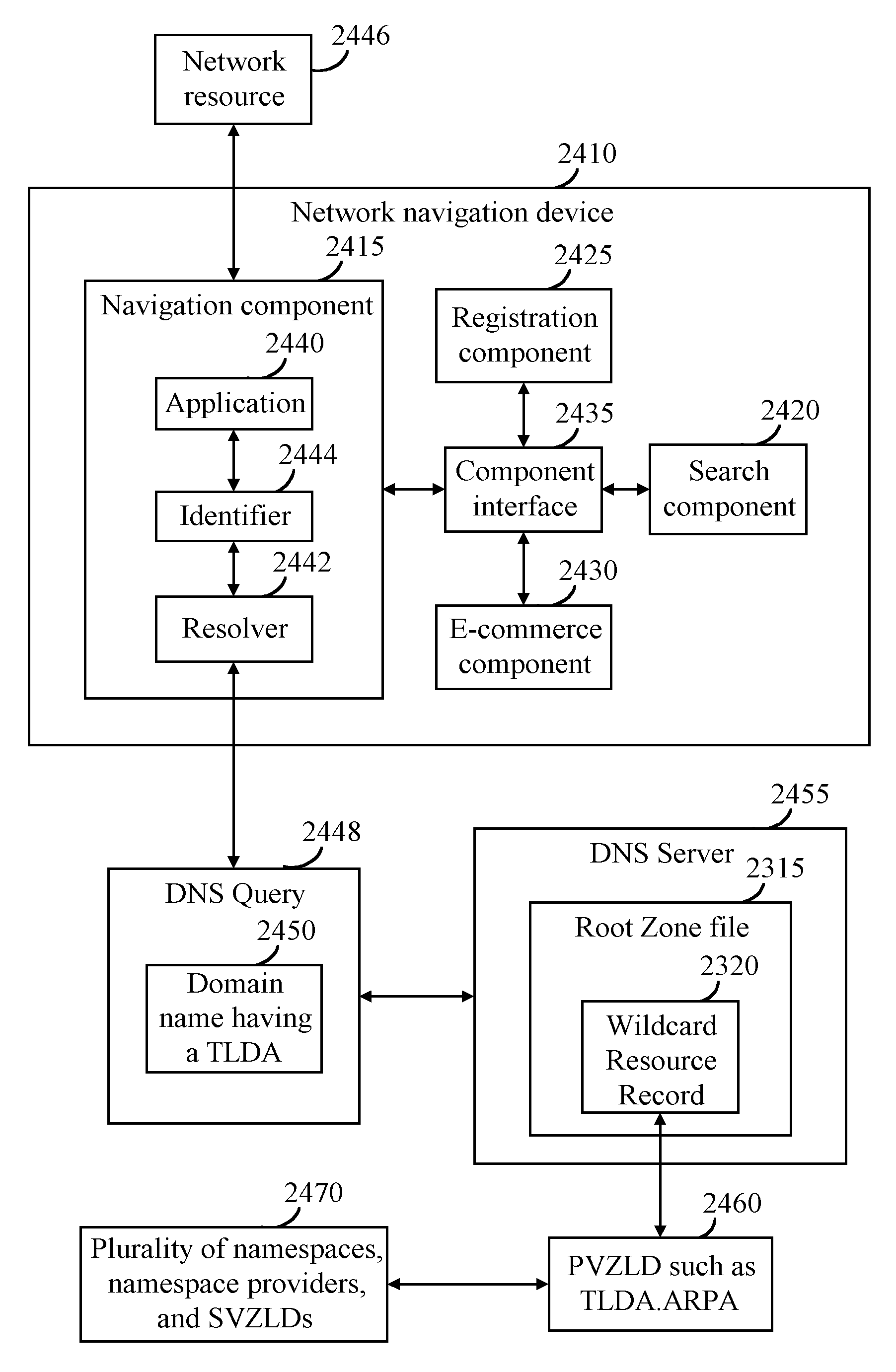
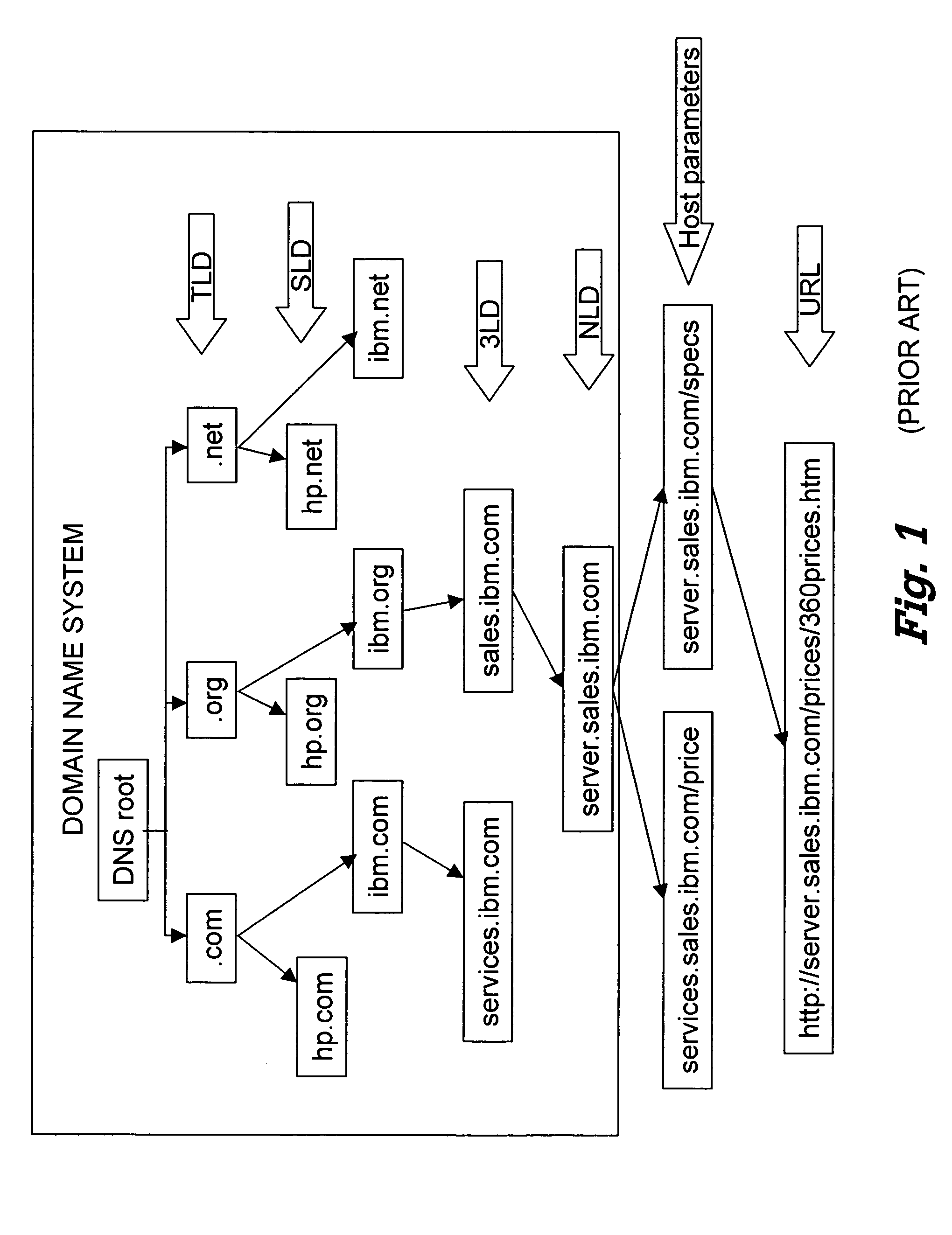
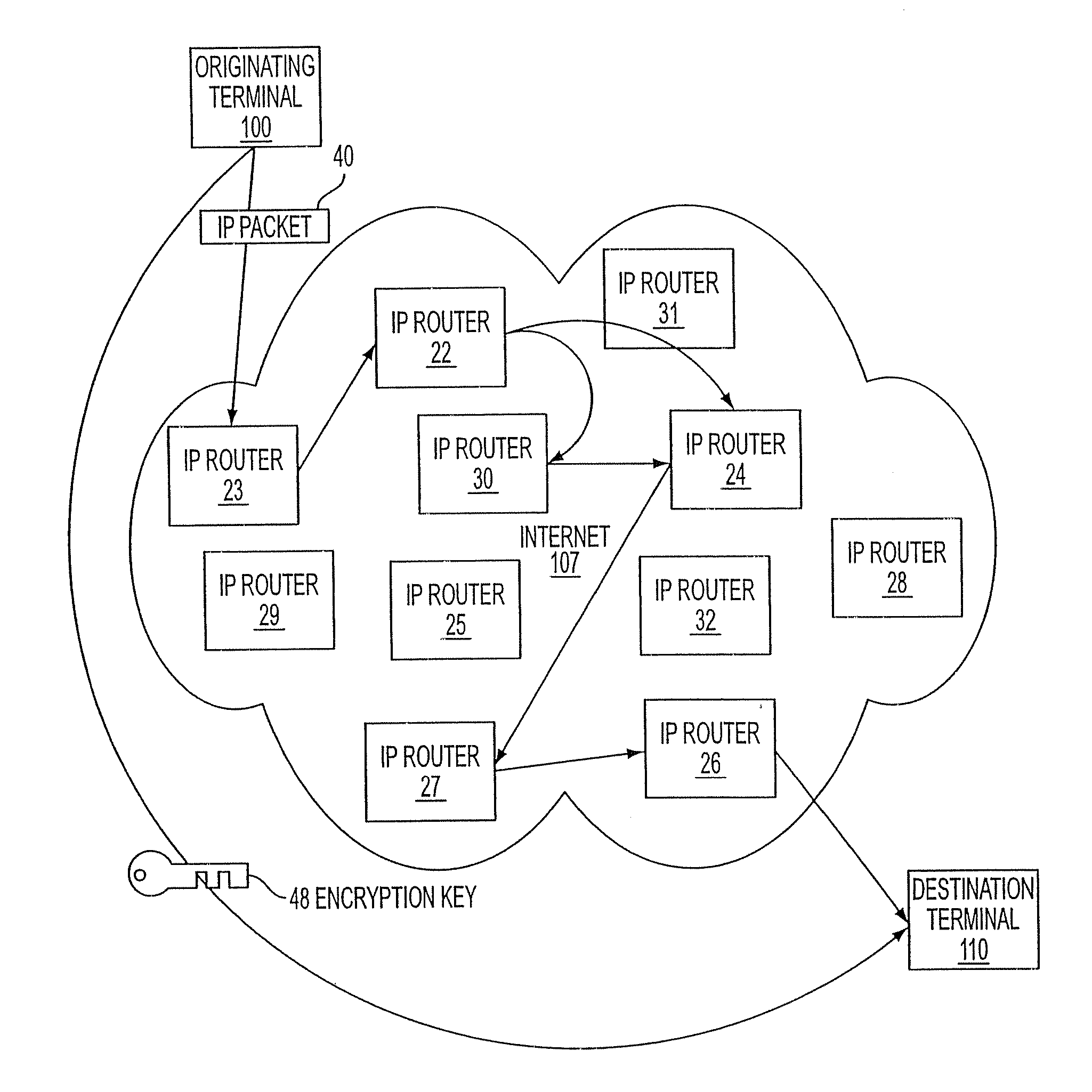
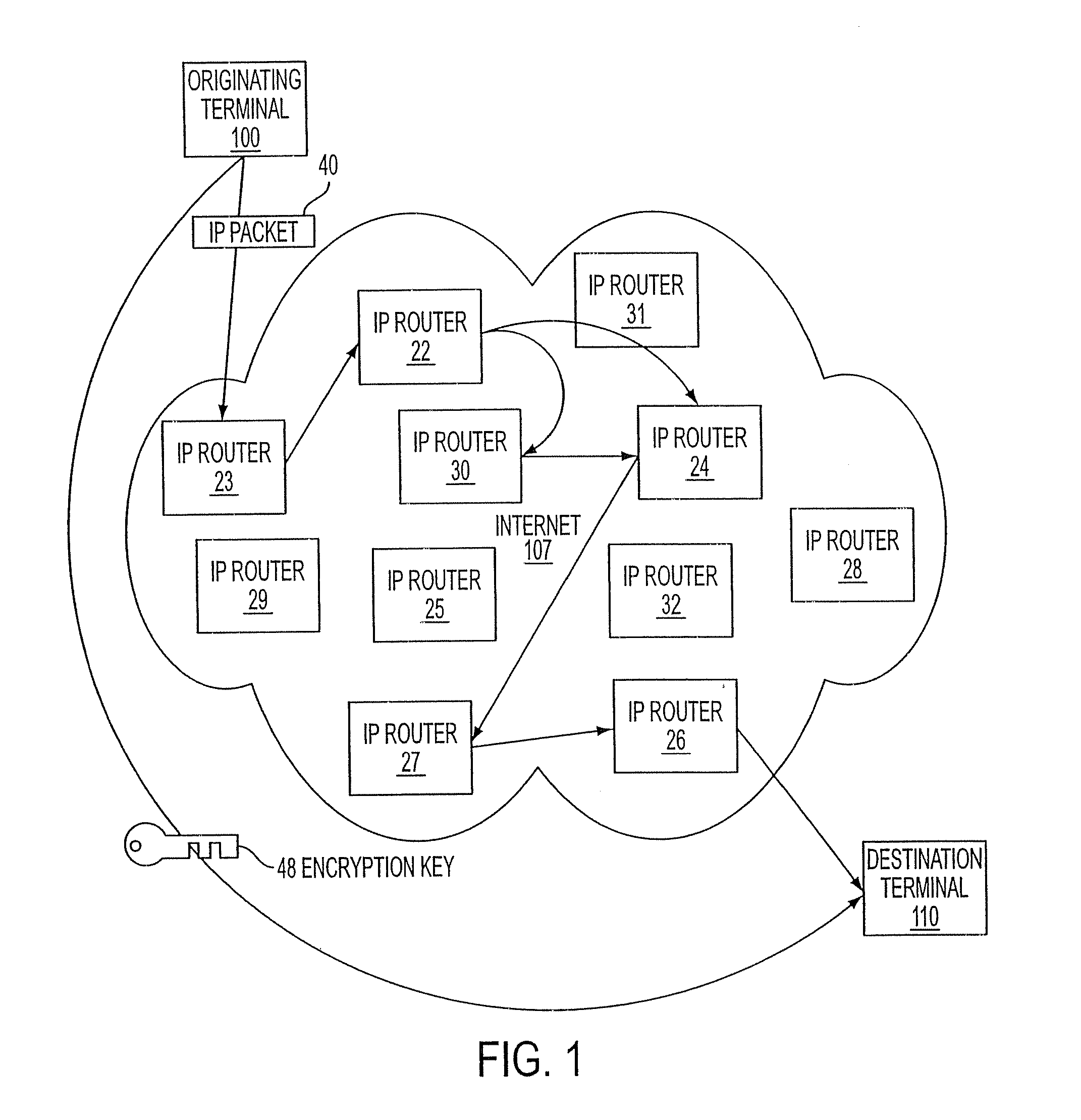
A top-level domain ( TLD) is one of the domains at the highest level in the hierarchical Domain Name System of the Internet. The top-level domain names are installed in the root zone of the name space.
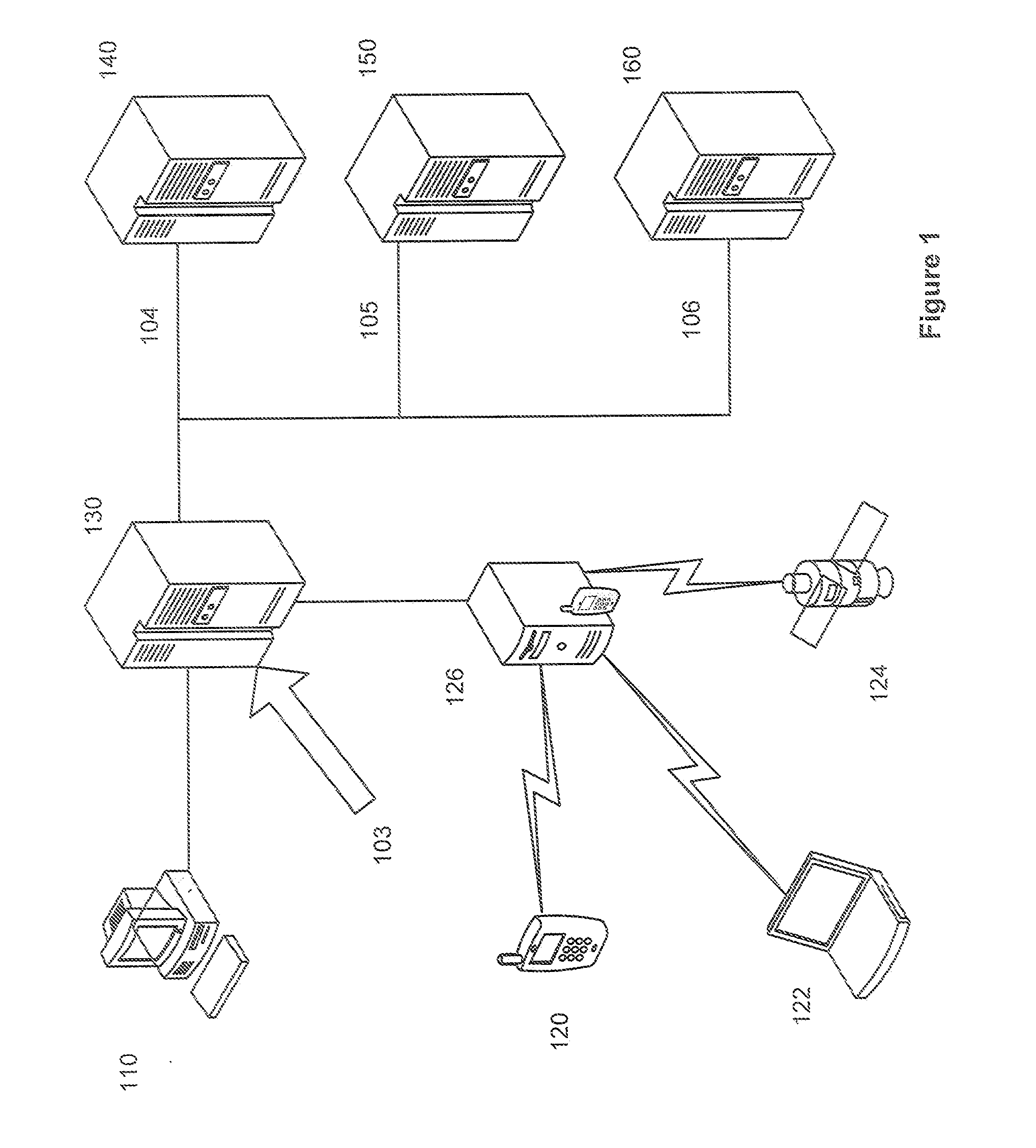
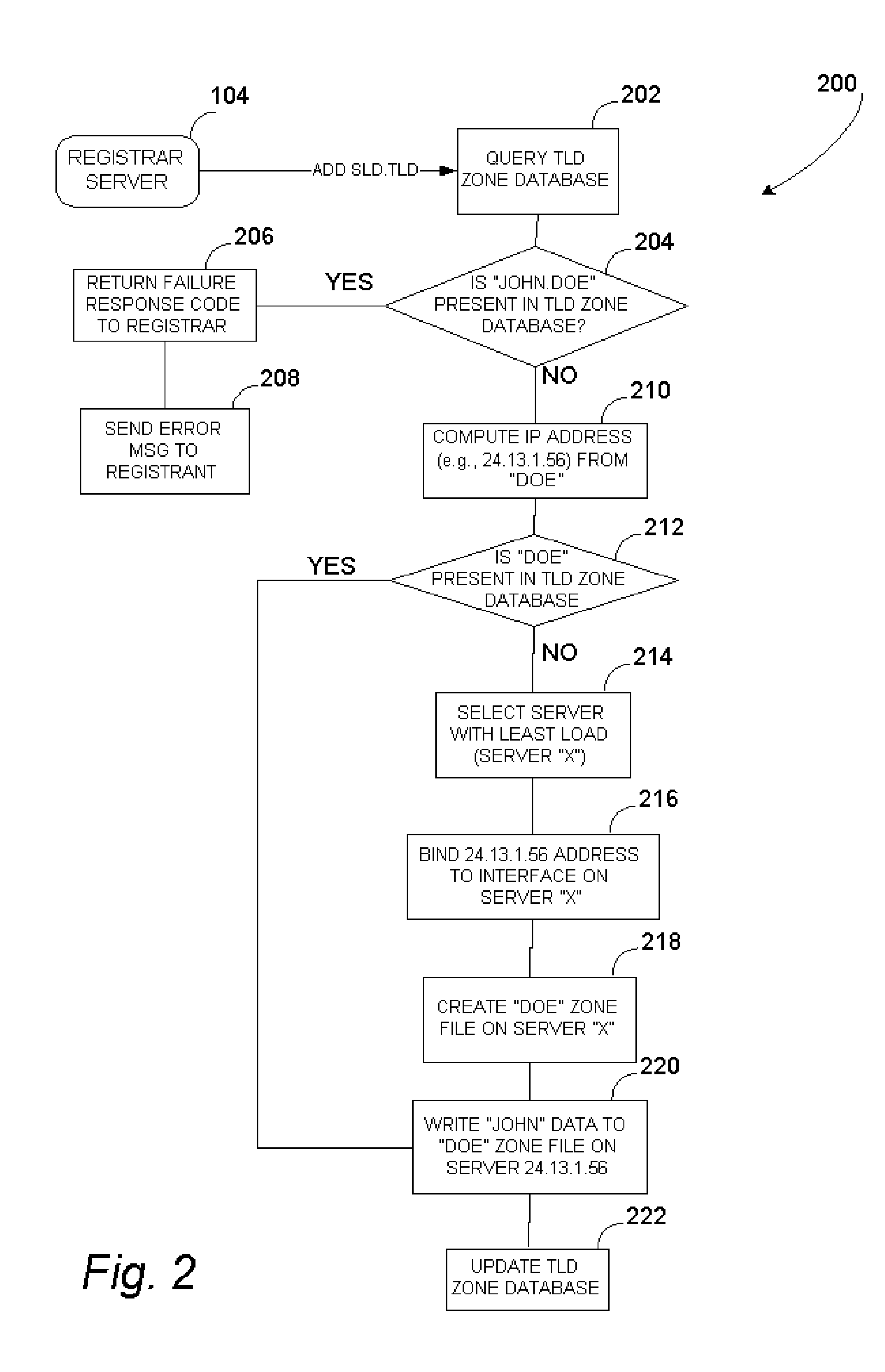
Fictitious domain name method, system, product, and apparatus
InactiveUS8224994B1Prevent excessive inputFew stepsMultiple digital computer combinationsMarketingComputer networkDomain Name System
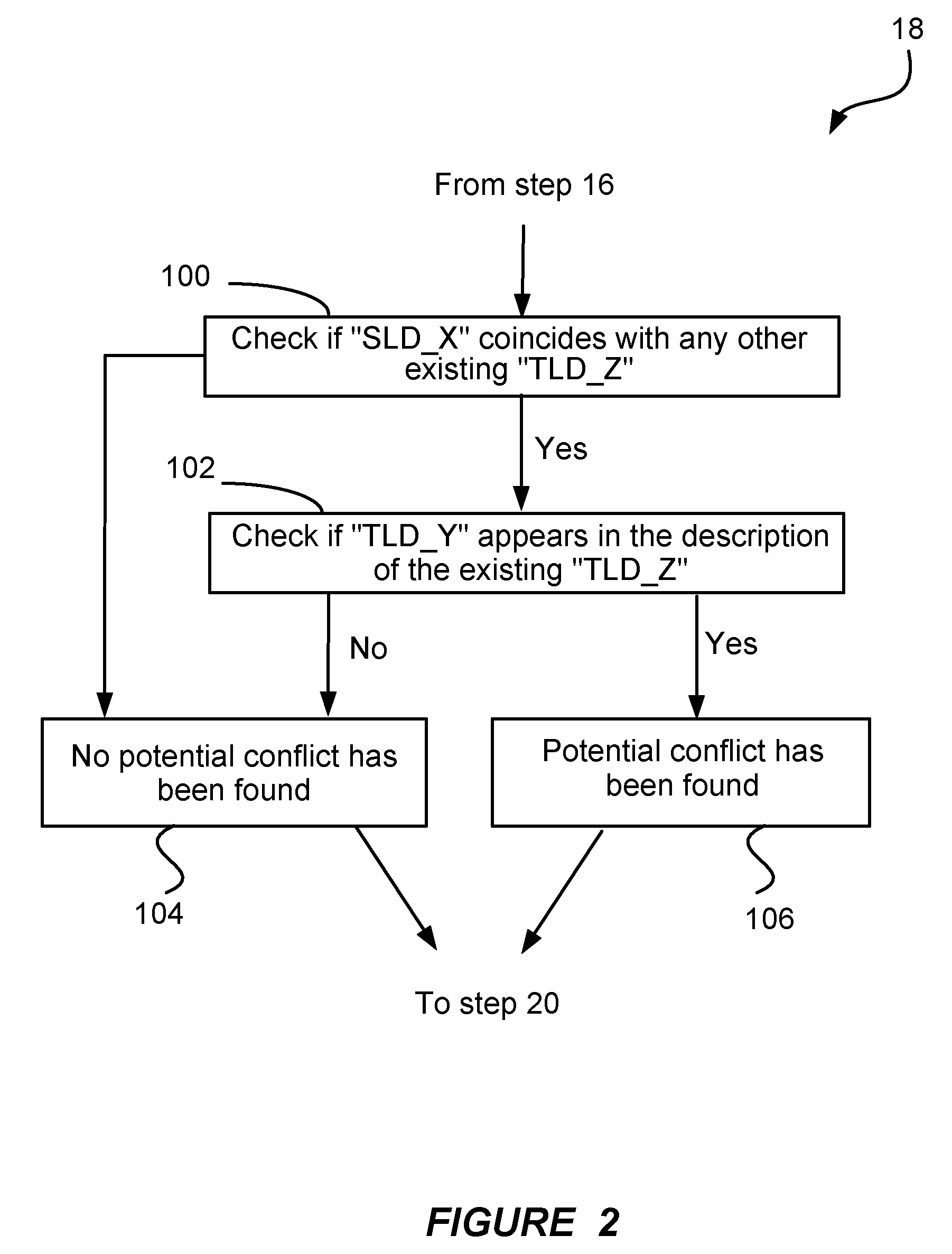
Owner:MEC MANAGEMENT LLC
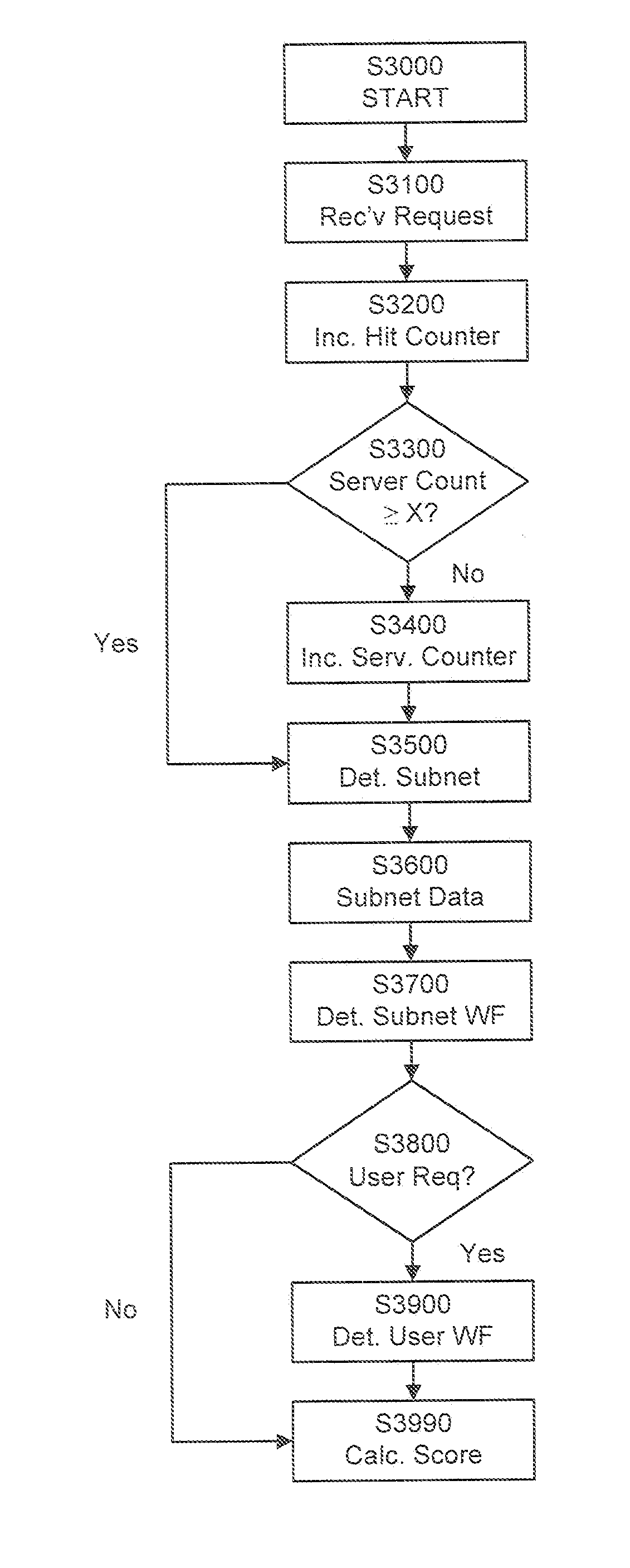
Domain Traffic Ranking
ActiveUS20100257024A1Accurate pictureReduce the amount requiredAdvertisementsMultiple digital computer combinationsName serverRanking
An automated method for determining domain traffic including receiving at authoritative name server a request to resolve a domain name that has n labels separated by periods. The leftmost label is the first label and the top level domain is the nth label. If the first label of the received domain name includes the string “www”, then a www hit counter and / or a www requesting server counter for the domain name are incremented. If the received domain name has only two labels, then an exact hit counter and / or an exact requesting server counter for the domain name are incremented. If the first label of the received domain name does not include the string “www” and does not have only two labels, then another hit counter and / or another requesting server counter for the domain name are incremented. A domain traffic score is calculated based upon a plurality of the counters, and calculating the domain traffic score includes applying a weighting factor to at least one of the counters.
Owner:VERISIGN
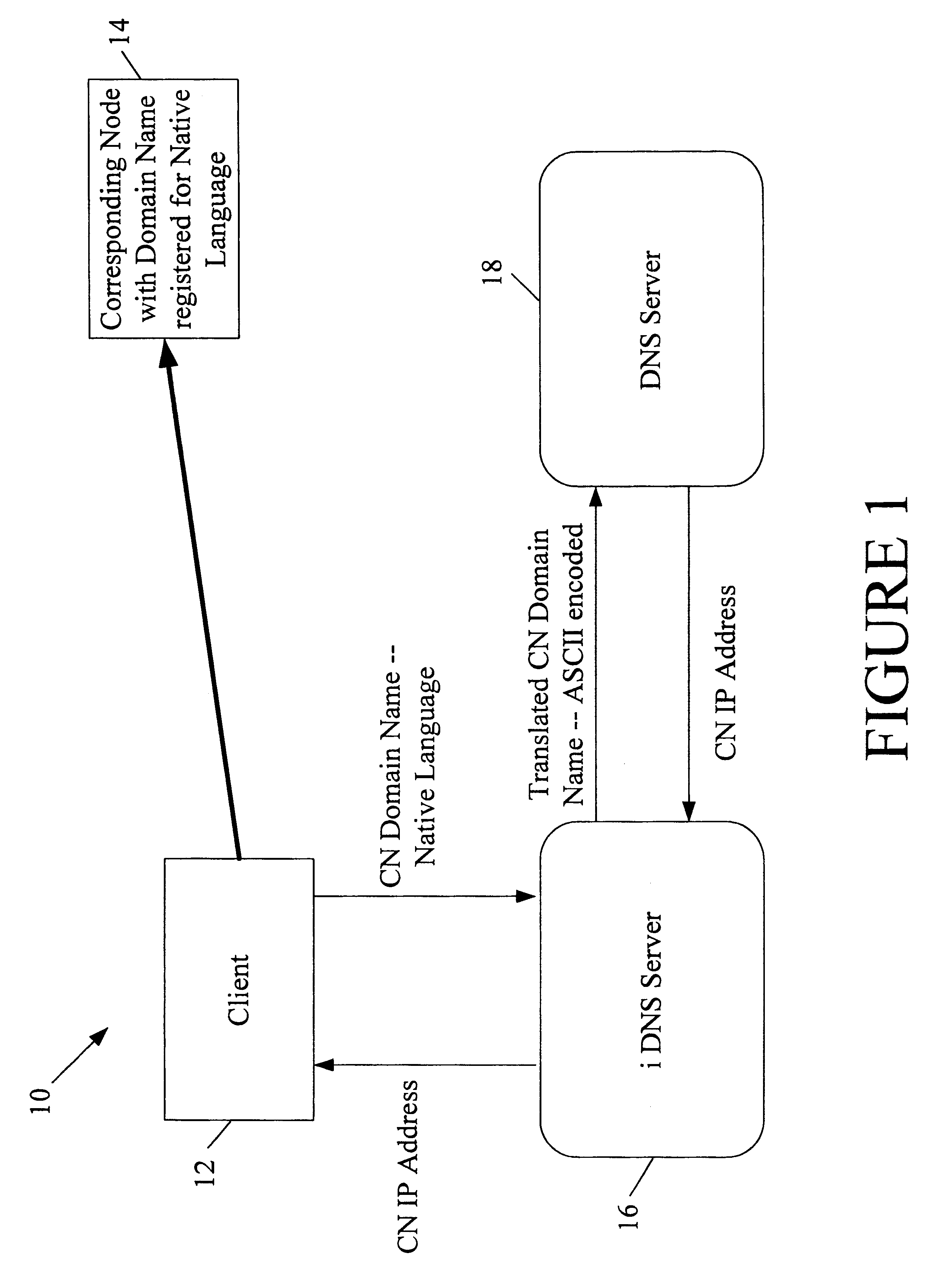
Multi-language domain name service
InactiveUS6314469B1Avoid ambiguityAvoid placingDigital data processing detailsNatural language data processingIp addressMulti language
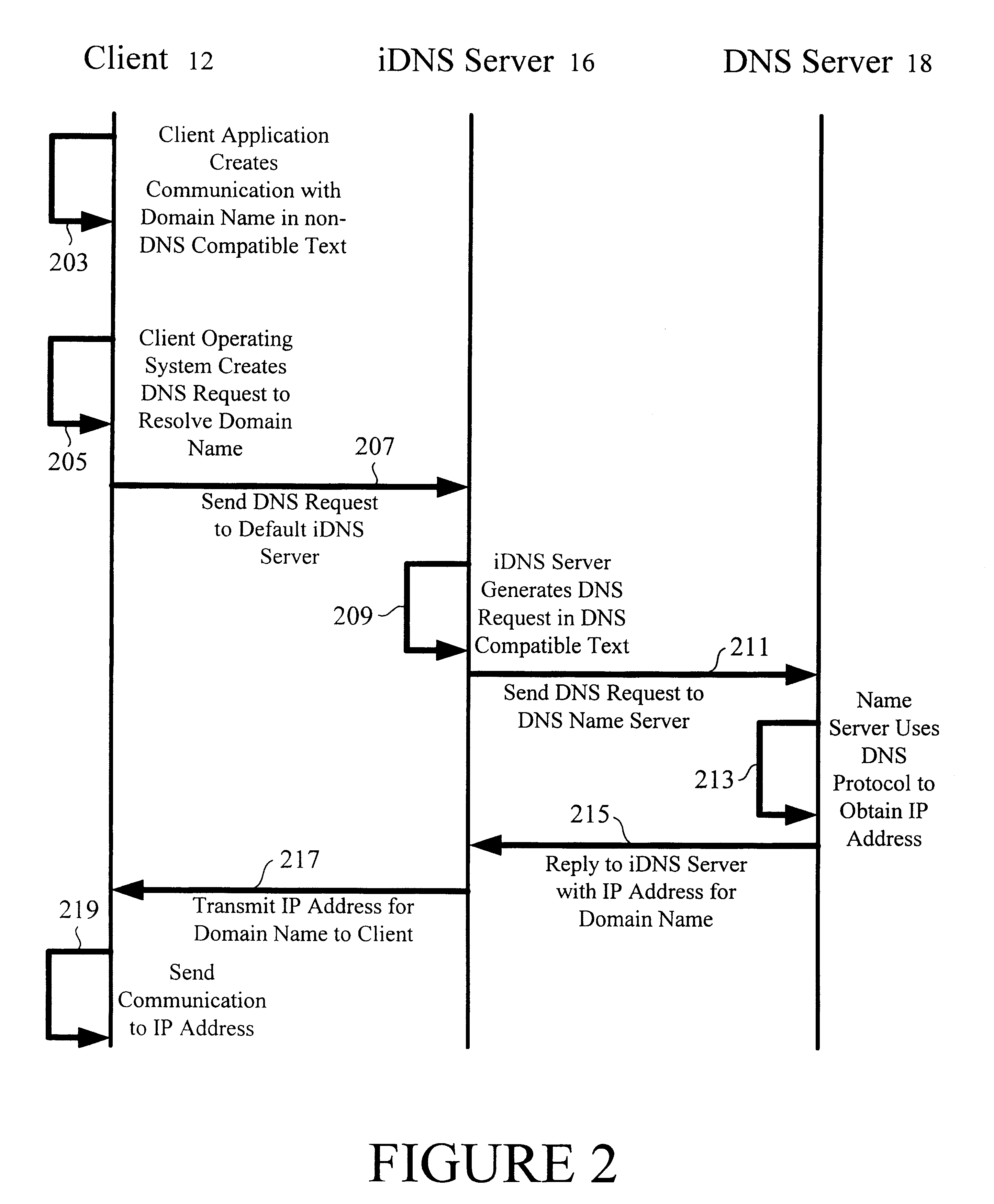
A multilingual Domain Name System allows users to use Domain Names in non-Unicode or ASCII encodings. An international DNS server (or iDNS server) receives multilingual DNS requests and converts them to a format that can be used in the conventional Domain Name System. When the iDNS server first receives a DNS request, it determines the encoding type of that request. It may do this by considering the bit string in the top-level domain (or other portion) of the Domain Name and matching that string against a list of known bit strings for known top-level domains of various encoding types. One entry in the list may be the bit string for ".com" in Chinese BIG5, for example. After the iDNS server identifies the encoding type of the Domain Name, it converts the encoding of the Domain Name to Unicode. It then translates the Unicode representation to an ASCII representation conforming to the universal DNS standard. This is then passed into a conventional Domain Name System, which recognizes the ASCII format Domain Name and returns the associated IP address.
Owner:I DNS NET INT
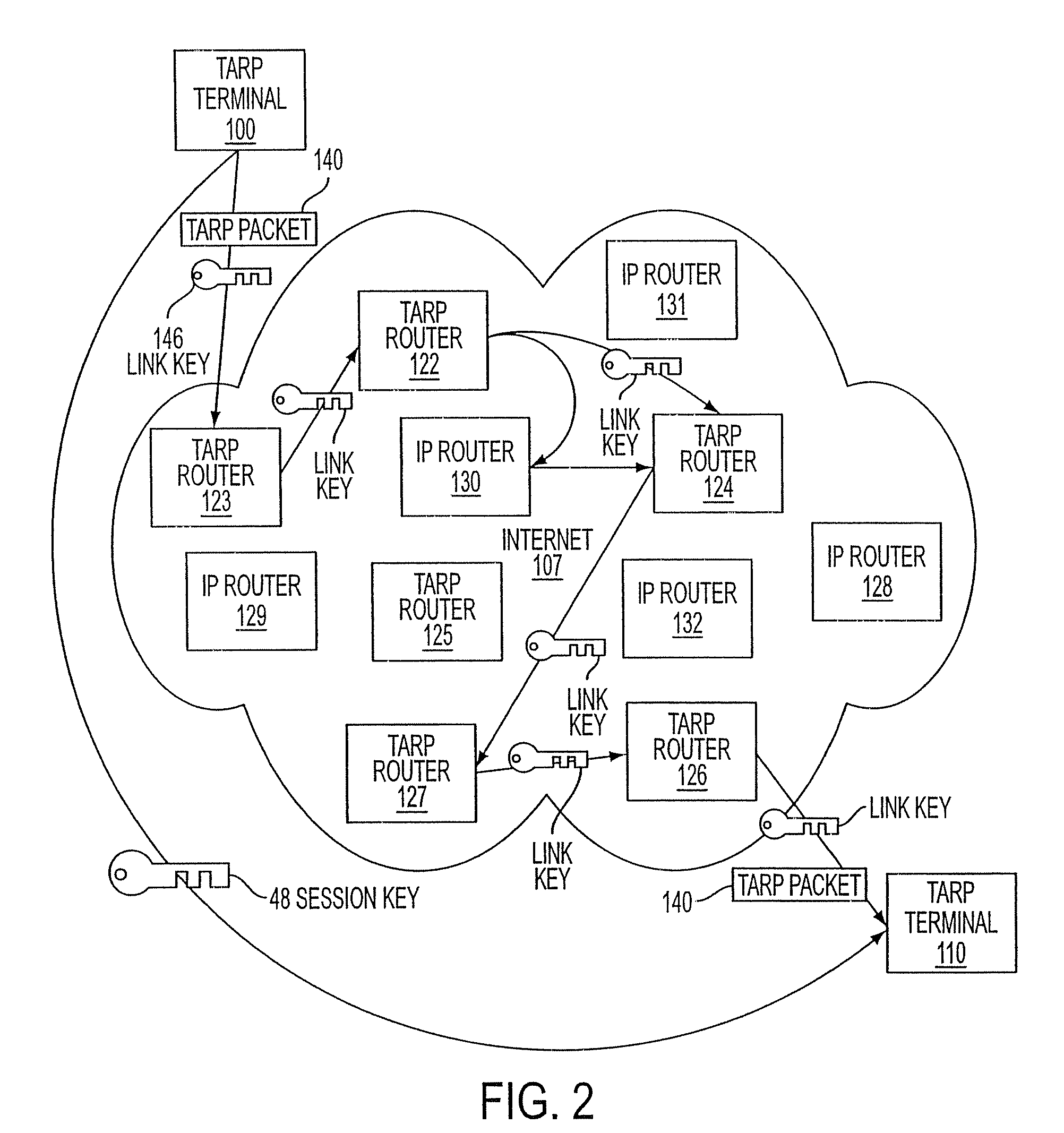
Agile network protocol for secure communications using secure domain names
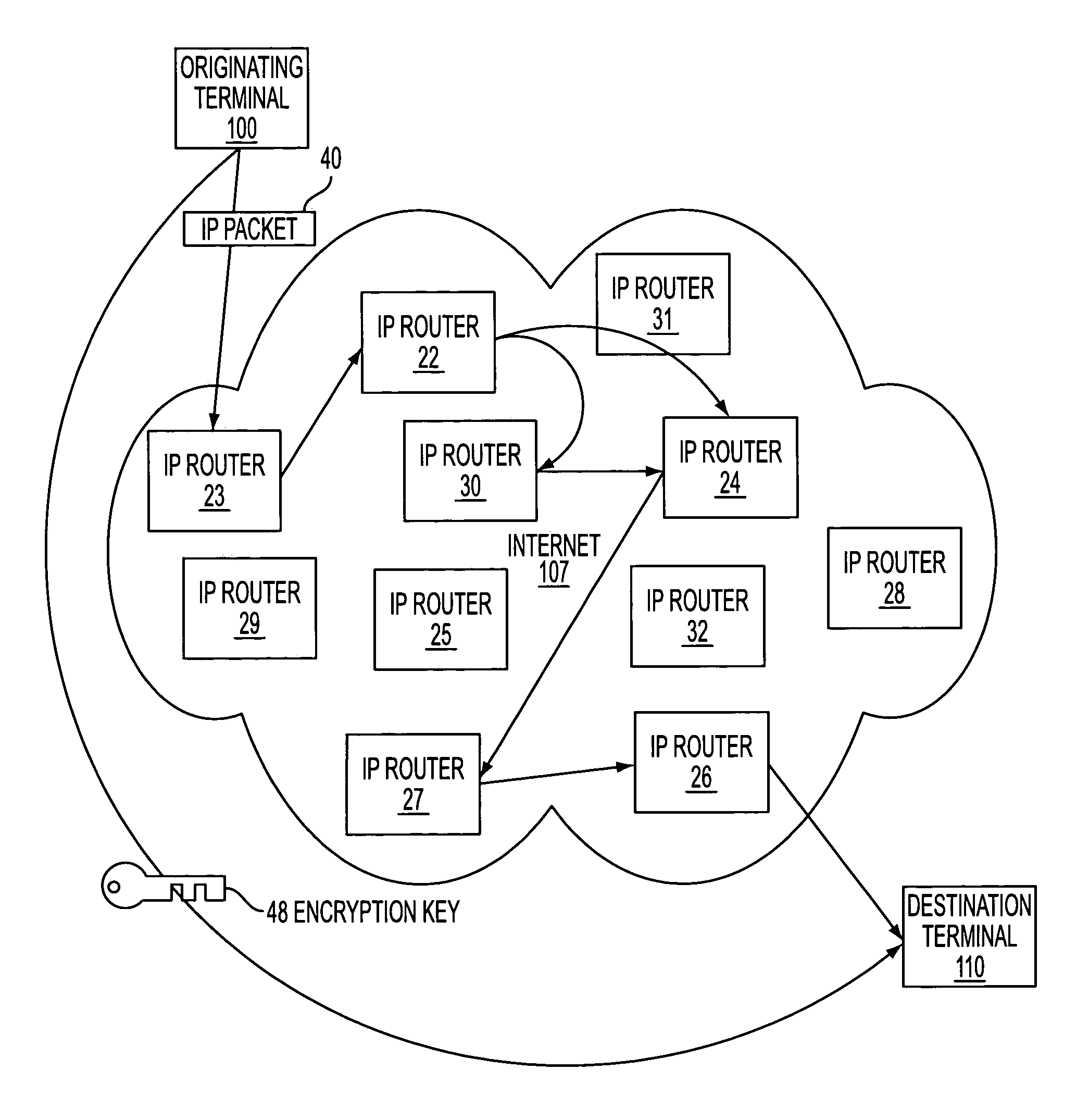
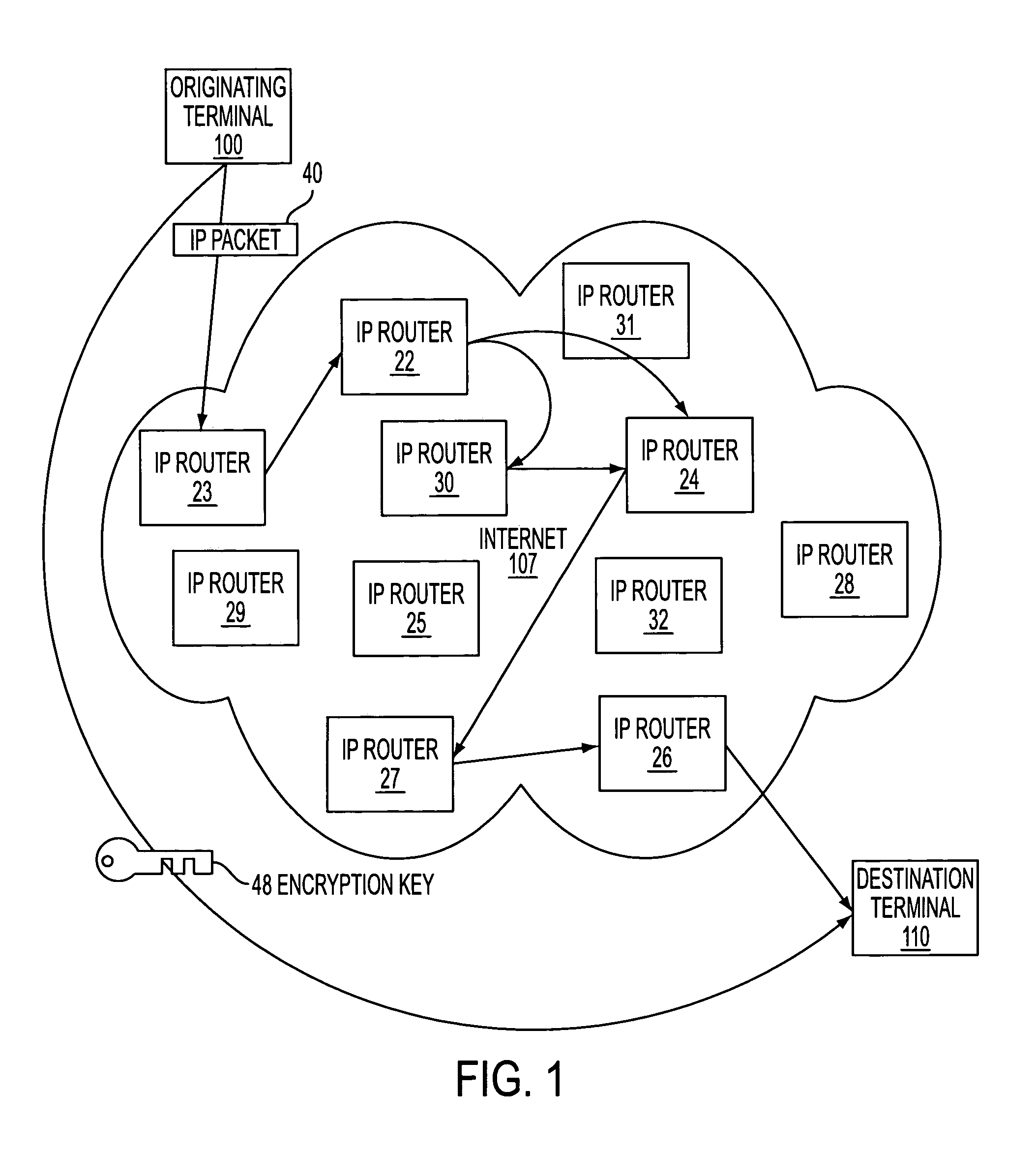
InactiveUS7418504B2Conveniently establishedWeb data indexingDigital computer detailsSecure communicationNetwork addressing
A secure domain name service for a computer network is disclosed that includes a portal connected to a computer network, such as the Internet, and a domain name database connected to the computer network through the portal. The portal authenticates a query for a secure computer network address, and the domain name database stores secure computer network addresses for the computer network. Each secure computer network address is based on a non-standard top-level domain name, such as .scom, .sorg, .snet, .snet, .sedu, .smil and .sint.
Owner:VIRNETX
Systems and methods for detection of infected websites
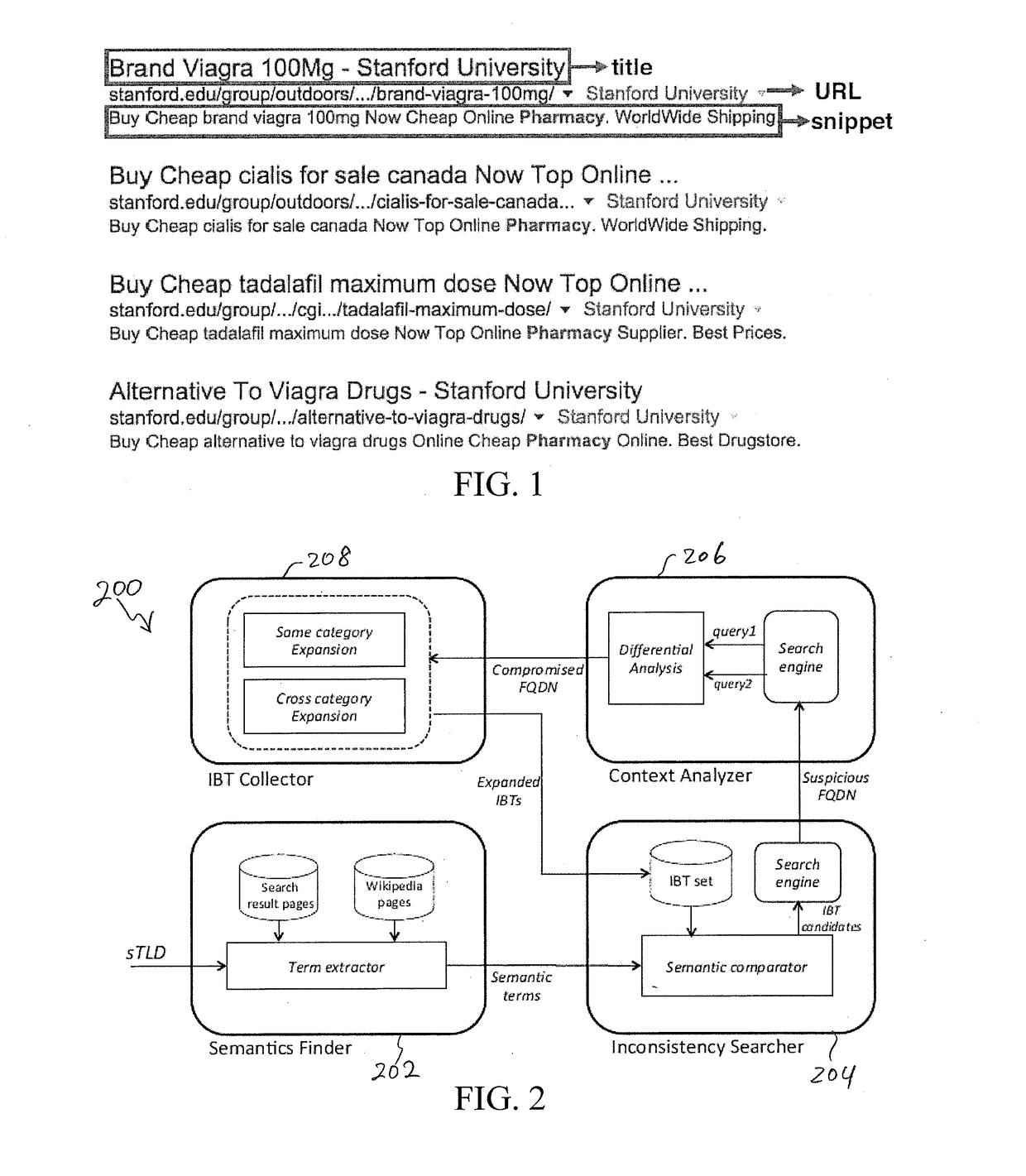
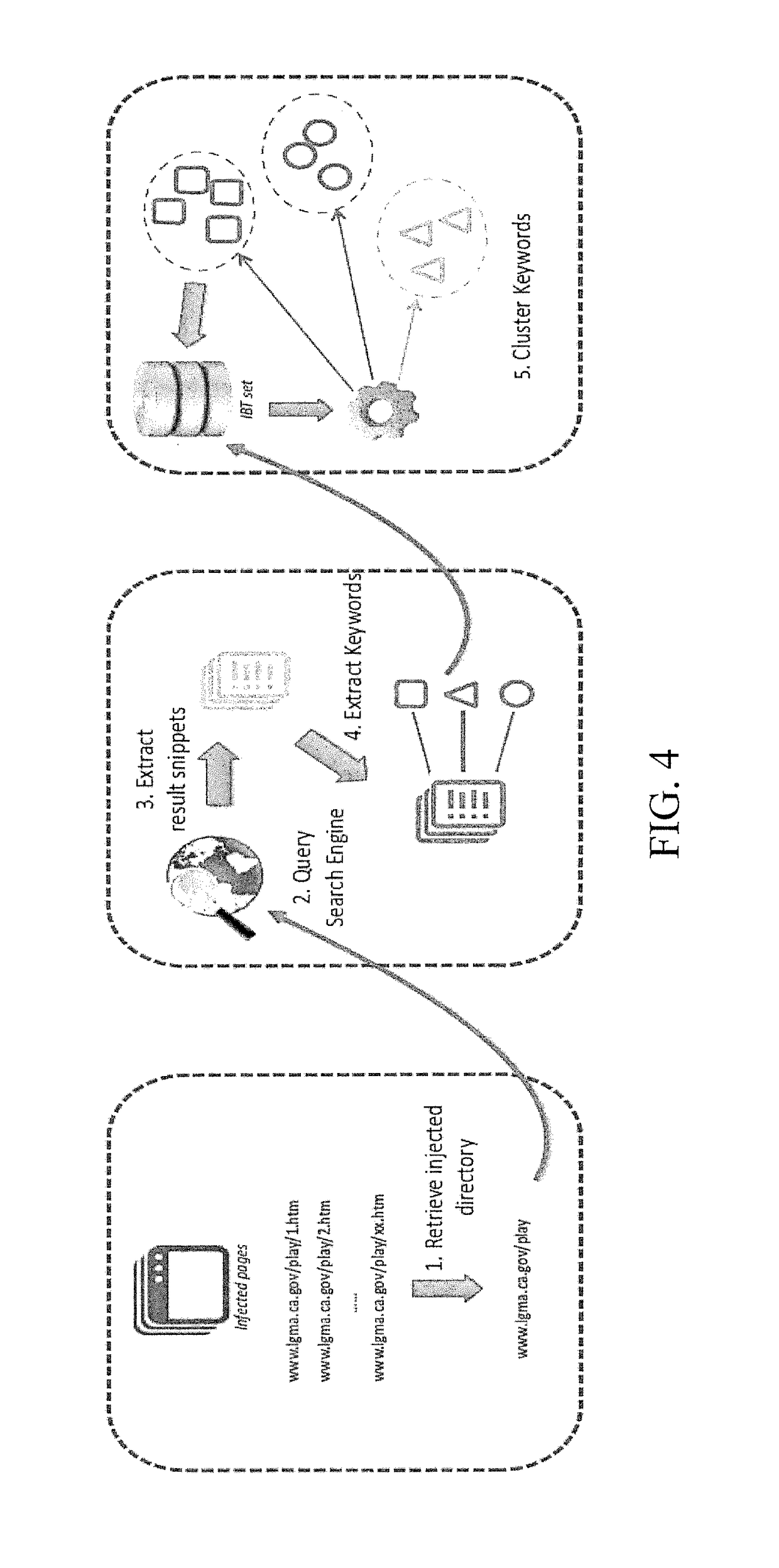
ActiveUS20180375896A1Efficient detectionRaise the barSemantic analysisComputer security arrangementsFully qualified domain nameSemantics
System and method for detecting an infected website are disclosed. A semantic finder receives top-level domains and identifies keywords of the top-level domains representing a predetermined semantics. The keywords are compared with irrelevant bad terms to find at least one irrelevant term. An inconsistency searcher searches the top-level domains and detects at least one fully-qualified domain name carrying the at least one irrelevant term. A context analyzer evaluates context information associated with the irrelevant term, identifies at least one frequently-used term identified in the context information, and determines whether the at least one frequently-used term is unrelated to a generic content of the at least one fully-qualified domain name An irrelevant bad term collector extracts the at least one frequently-used term unrelated to the generic content and adds the extracted frequently-used term to an irrelevant bad term list for detecting the infected website.
Owner:INDIANA UNIV RES & TECH CORP +1
Systems and methods of registering and utilizing domain names
The present invention provides methods and systems for registering unlimited non-ICANN top-level domain (TLD) names that are created on demand, and for utilizing them in a network environment in parallel with those specified by the Internet Corporation for Assigned Names and Numbers (ICANN) or other authority authorized to approve standardized top-level domain names. One embodiment of the present invention provides systems and methods for registering a non-ICANN TLD name by mapping it to an IP address using a predefined mapping function, assigning the resulting IP address to a server system that acts as the name server for TLD name, and subsequently using the said predefined function when a user enters an Internet address containing said TLD name on a client computer in order to compute the IP address of the said name server and access it. Further, one embodiment of the present invention is operable with proxy servers.
Owner:ASSAD ELIAS
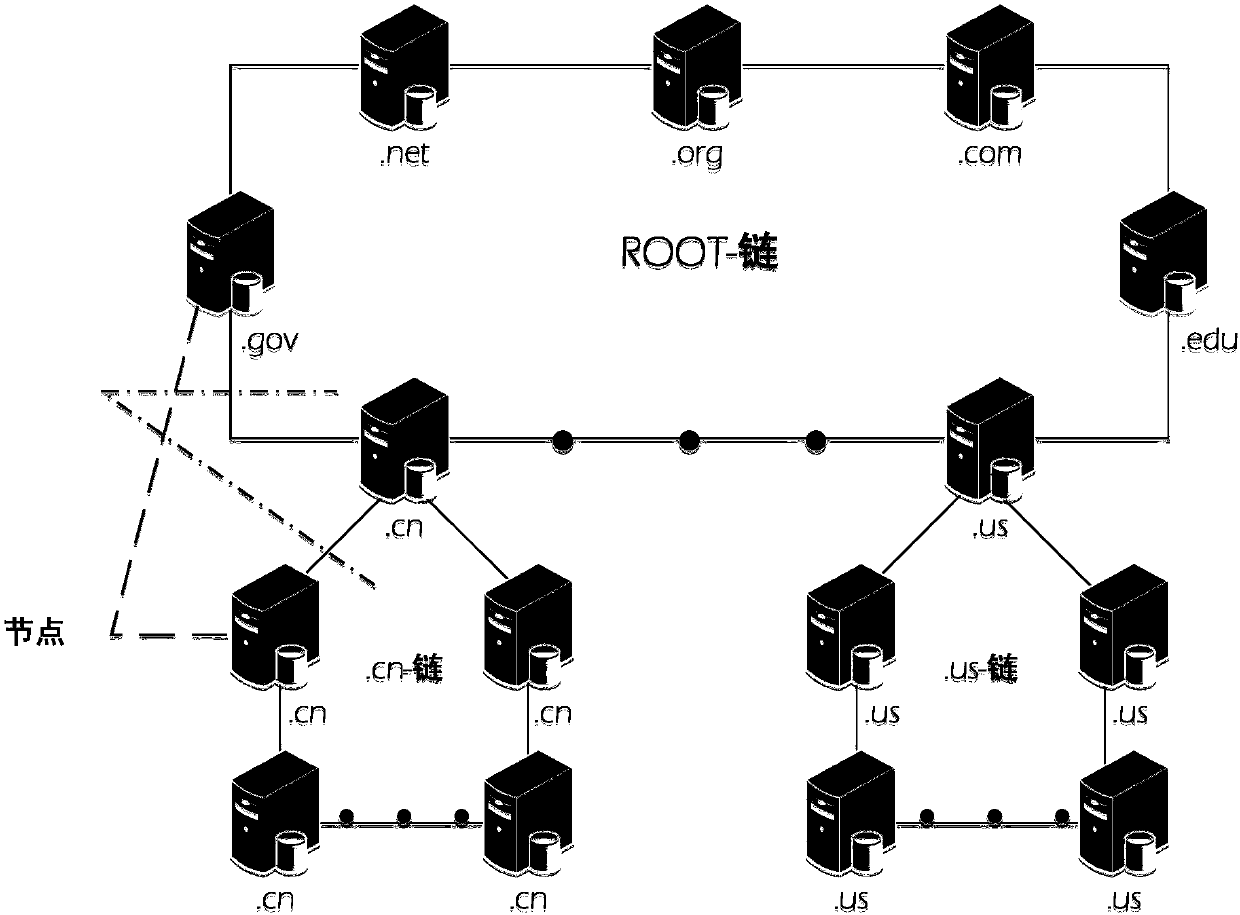
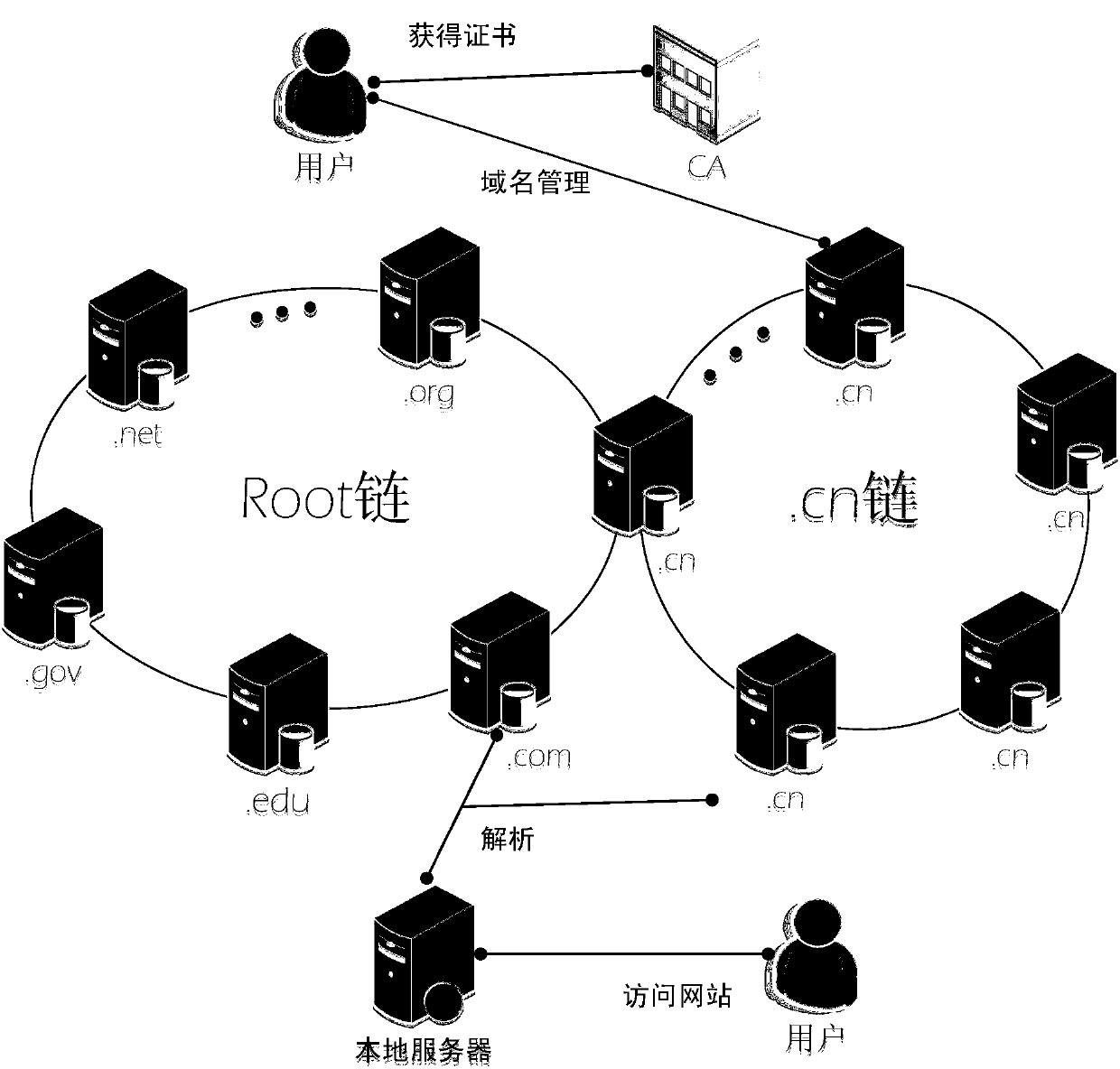
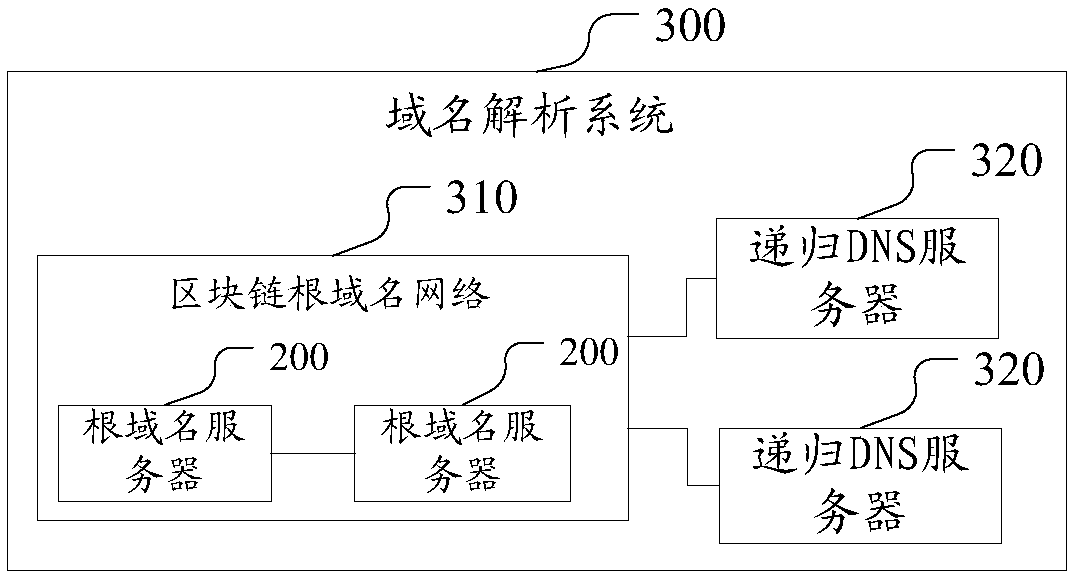
Domain name management system, domain name management method and domain name analysis method based on block chain
ActiveCN107613041AEnsure safetyRealize managementKey distribution for secure communicationStructure of Management InformationAnycast
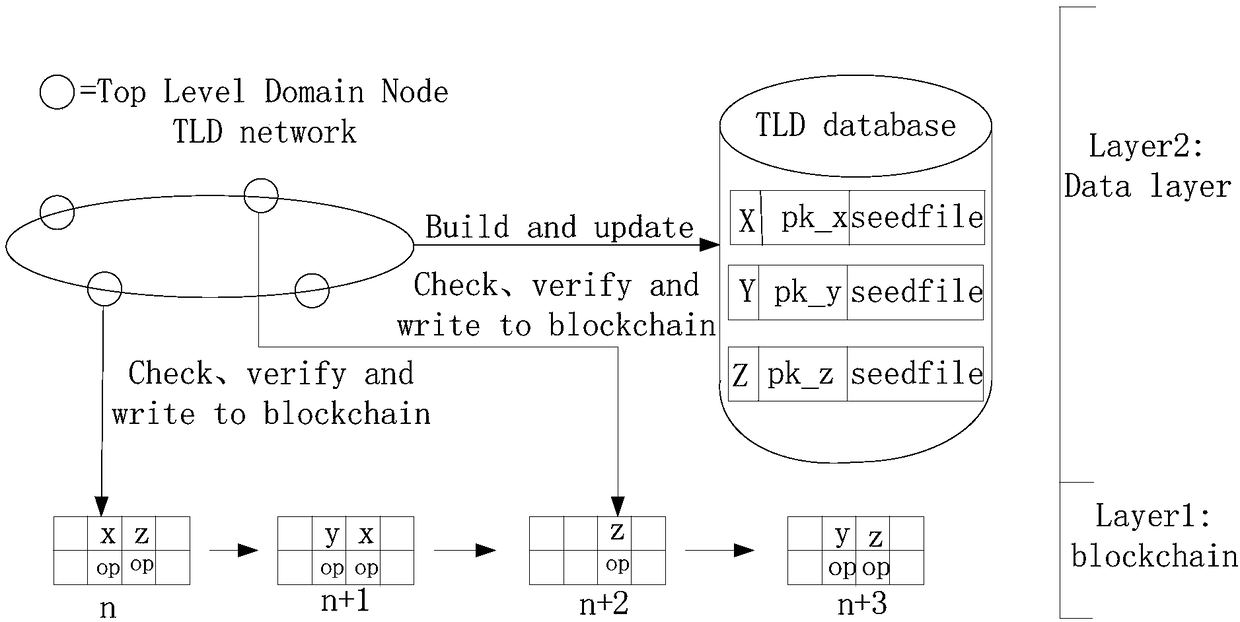
The invention relates to a domain name management system, a domain name management method and a domain name analysis method based on a block chain. The domain name management system based on the blockchain comprises a block chain of a hierarchical structure, the block chain of the hierarchical structure comprises a root chain and a plurality of top level domain name chains; the root chain and thetop level domain name chains are alliance chains; and the root chain manages and stores the information of all top level domain name chains, and each top level domain name chain manages and stores the information of the same top level domain name. The domain name management system based on the block chain realizes the decentration management of the domain names, eliminates the number limitation of the root server, and enables different organizations to impartially share the domain name management authority; and on the synchronous mode, each node can be synchronized at any time, thereby changing the problem that the original anycast mode has a synchronization sequence. The problem of domain name hijacking can also be solved by managing and updating an analysis database by using the block chain.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Processing taxonomic extensions on the world wide web to implement an integrity-rich intelligence apparatus
InactiveUS20070266141A1Enhanced interactionQuality improvementDigital computer detailsTransmissionData setOperational system
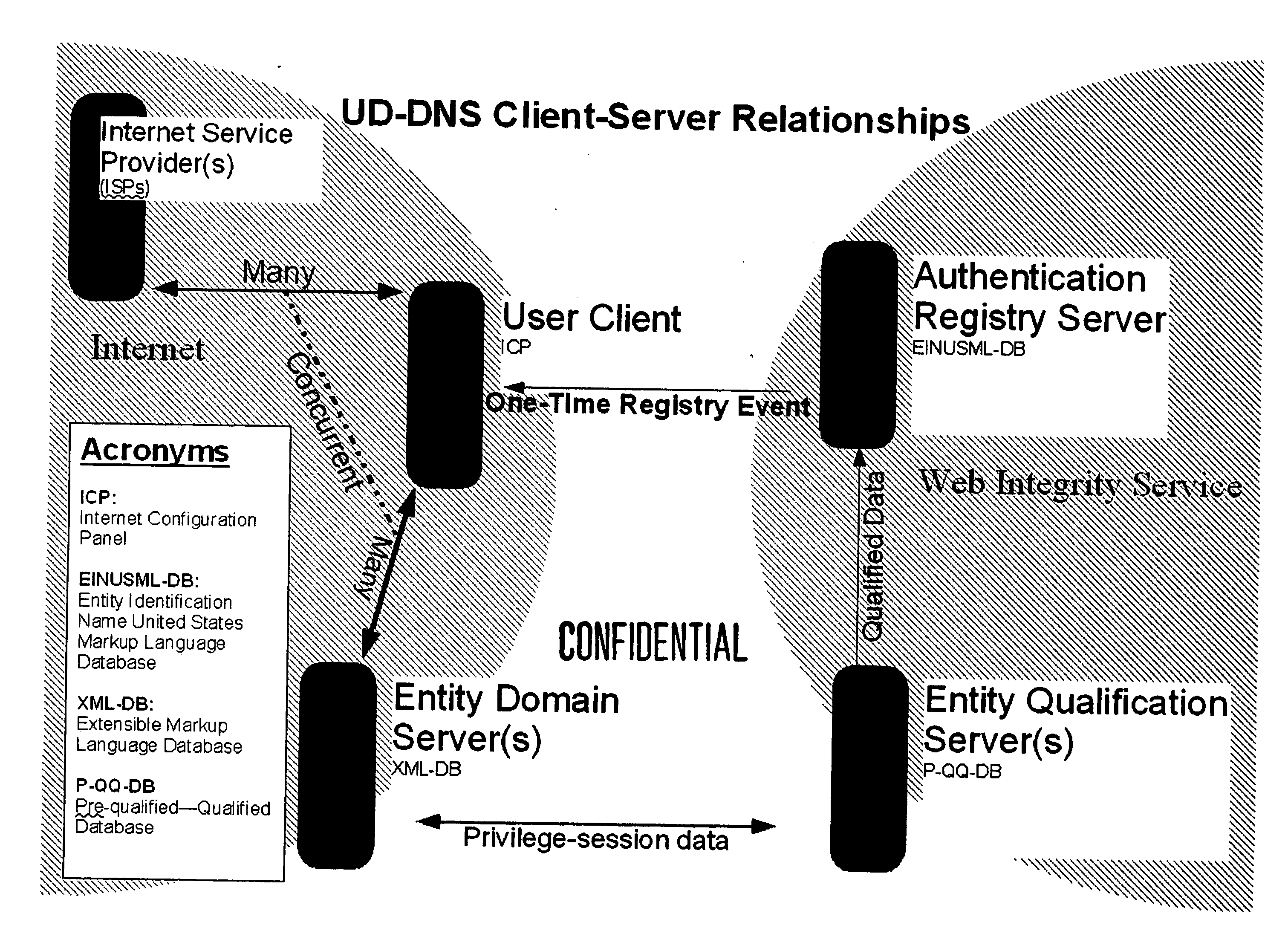
Methods for implementing an Internet Operating System are described at the core as a Unified-Dynamic Domain Name Server (UD-DNS) system and may be referred to as a web integrity service (WIS). A list of root http addresses resides in a database. The top level domain (TLD) is parsed from the list. New TLD extensions representing human-based networks of integrity-founded information are bound to the previously parsed second-level domain names and assigned a Registry Identifier Number (RIN). The list is transferred to an authentication registry server. For each new http address / RIN, a dataset component template is imported and encrypted into a global encryption key. A bindery service connects the end-user of the Internet to a validation service through which a dataset component template may be populated and, per each new TLD's entity domain and qualification servers, displayed. Methods for conveying populated information comprise a software program of graphical user interface (GUI) systems with USML-(United States Markup Language)-encrypted stylesheets which are browsed via methods described herein. An Internet Configuration Panel (ICP) comprises the GUI system that connects a user with the UD-DNS system.
Owner:NORTON MICHAEL ANTHONY
Detecting malware infestations in large-scale networks
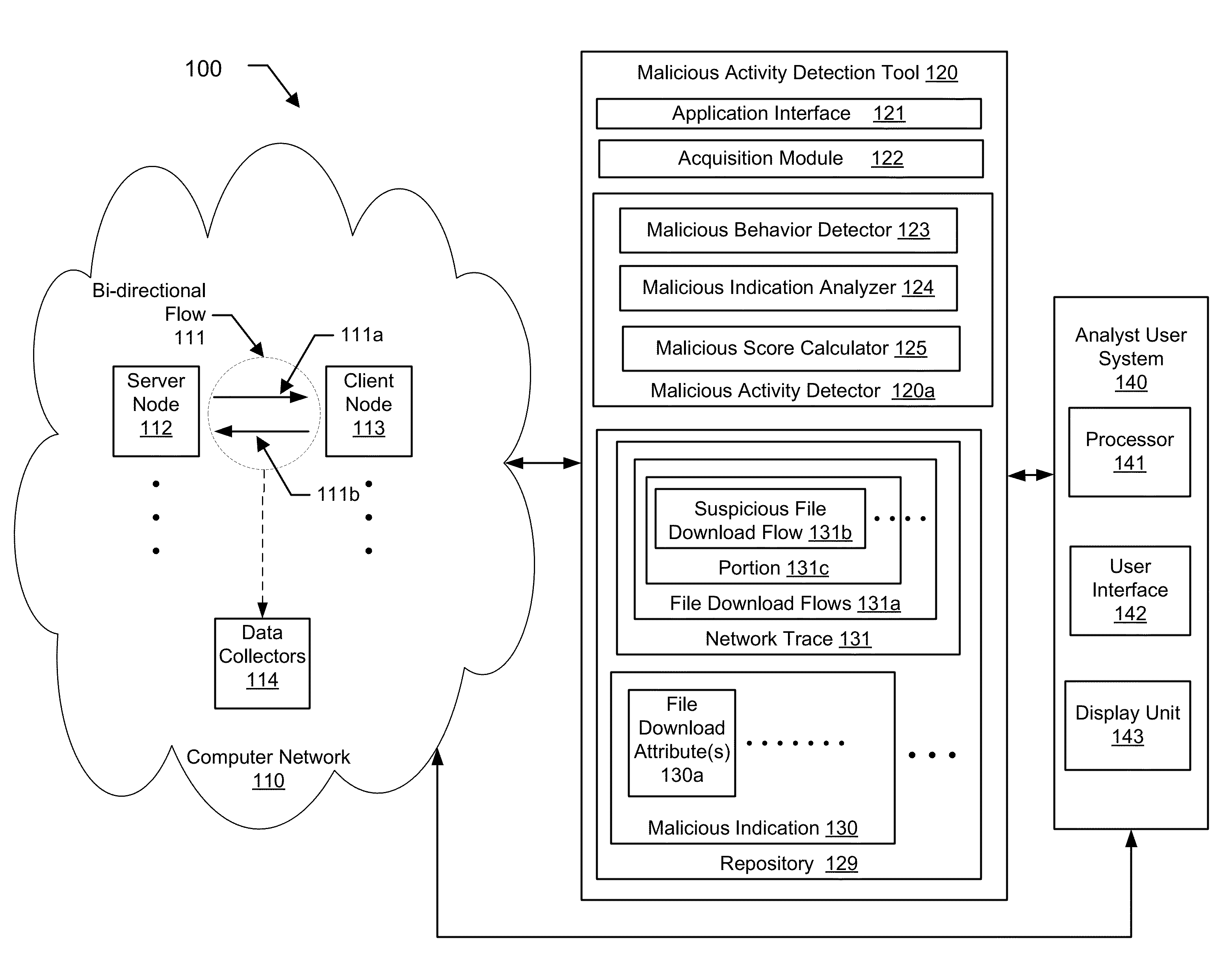
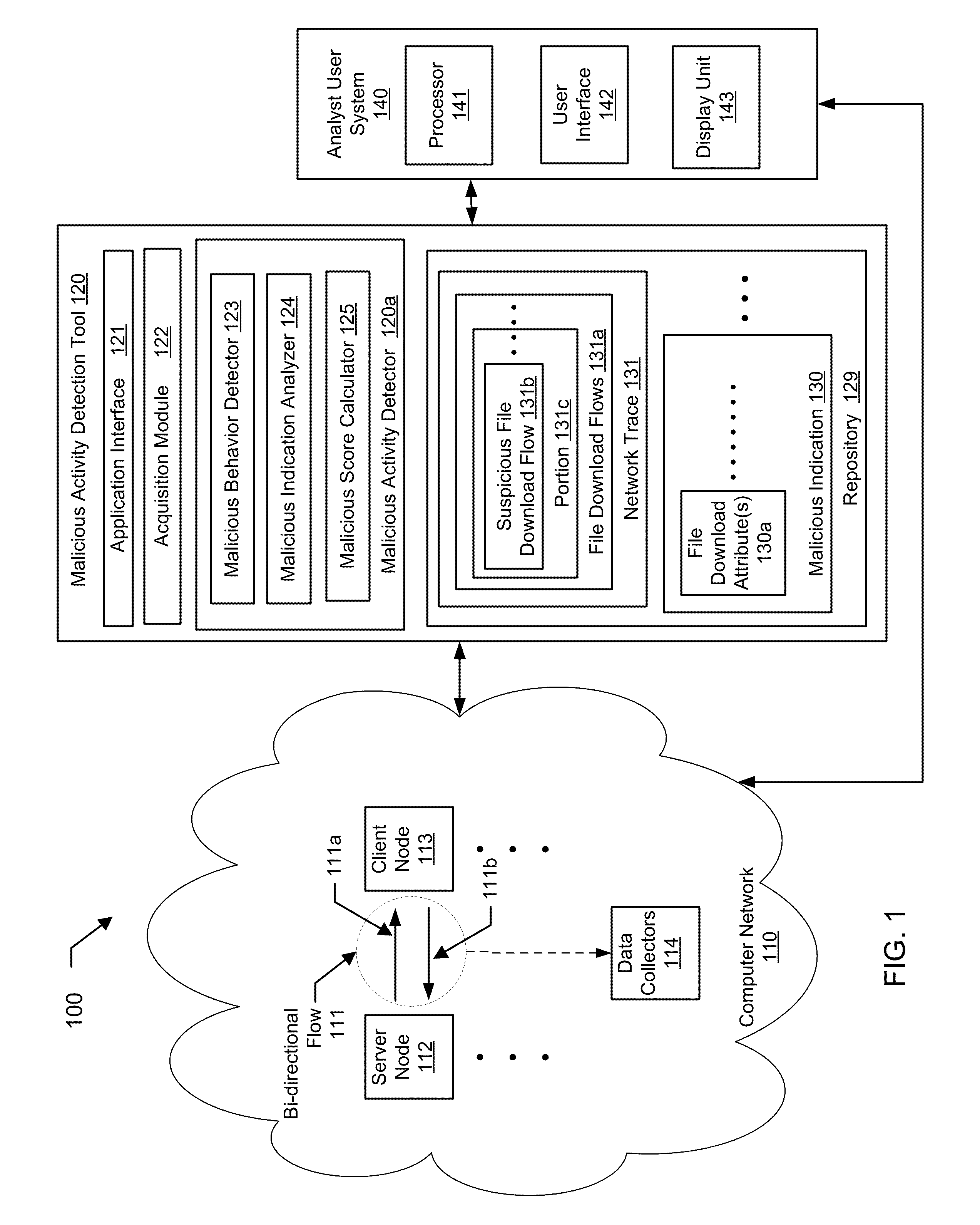
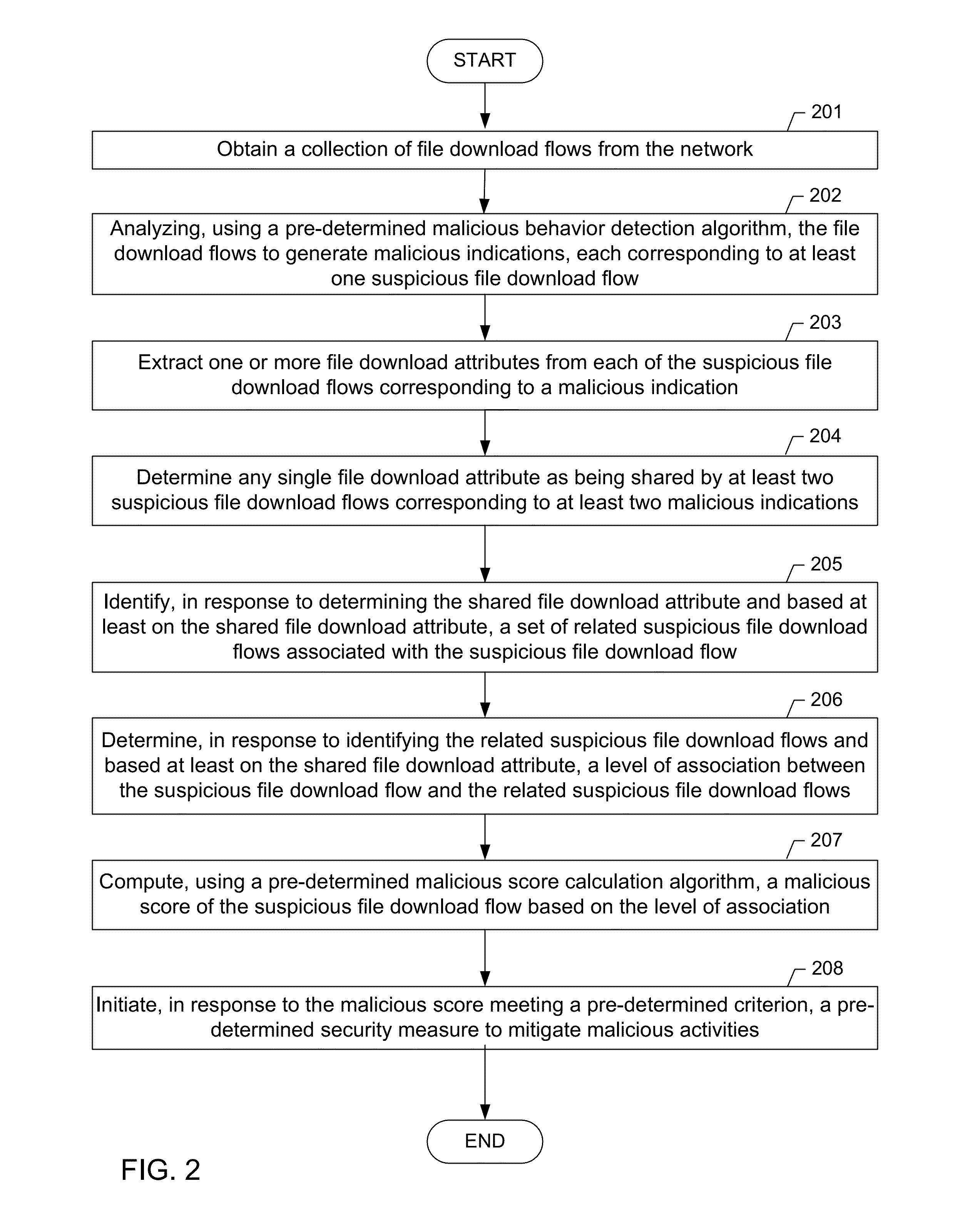
A method for detecting a malicious activity in a network. The method includes obtaining file download flows from the network, analyzing, the file download flows to generate malicious indications using a pre-determined malicious behavior detection algorithm, extracting a file download attribute from a suspicious file download flow of a malicious indication, wherein the file download attribute represents one or more of the URL, the FQDN, the top-level domain name, the URL path, the URL file name, and the payload of the suspicious file download flow, determining the file download attribute as being shared by at least two suspicious file download flows, identifying related suspicious file download flows and determining a level of association between based at least on the file download attribute, computing a malicious score of the suspicious file download flow based on the level of association, and presenting the malicious score to an analyst user of the network.
Owner:THE BOEING CO
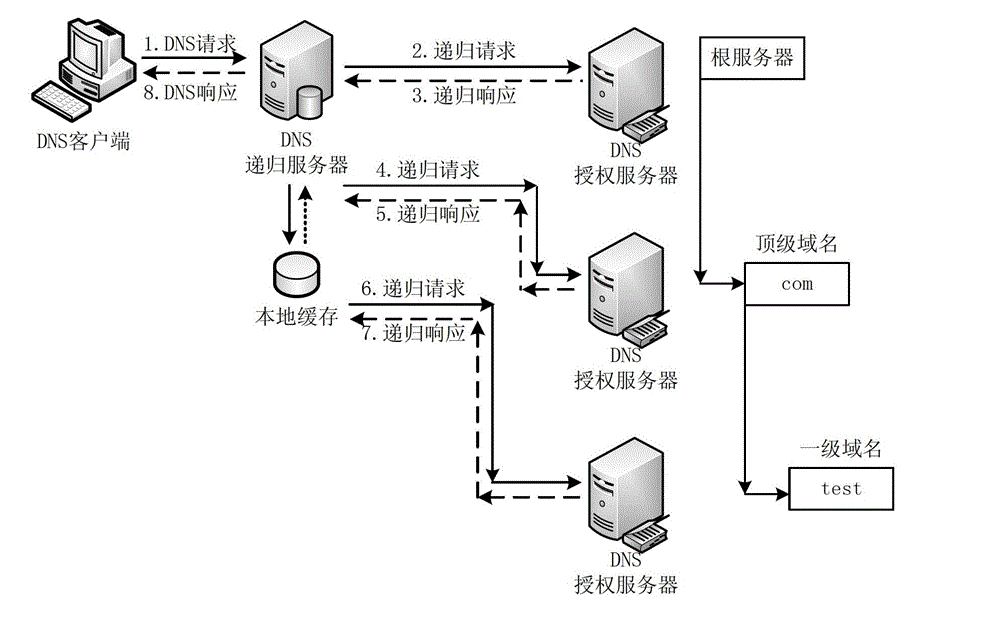
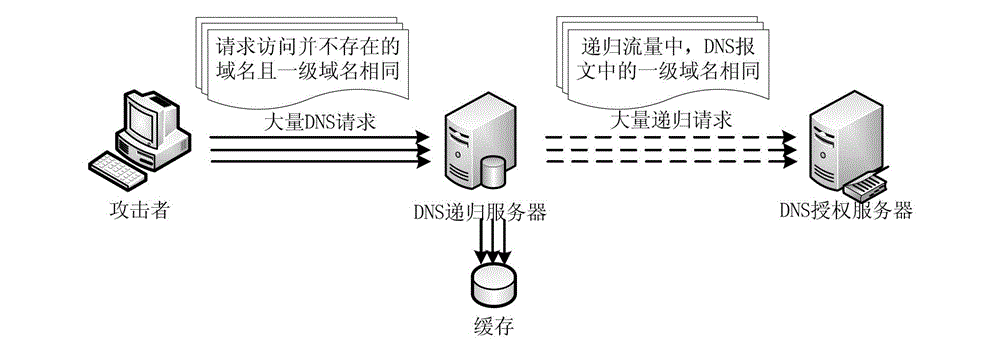
Defense method, device and system for DNS (Domain Name System) services
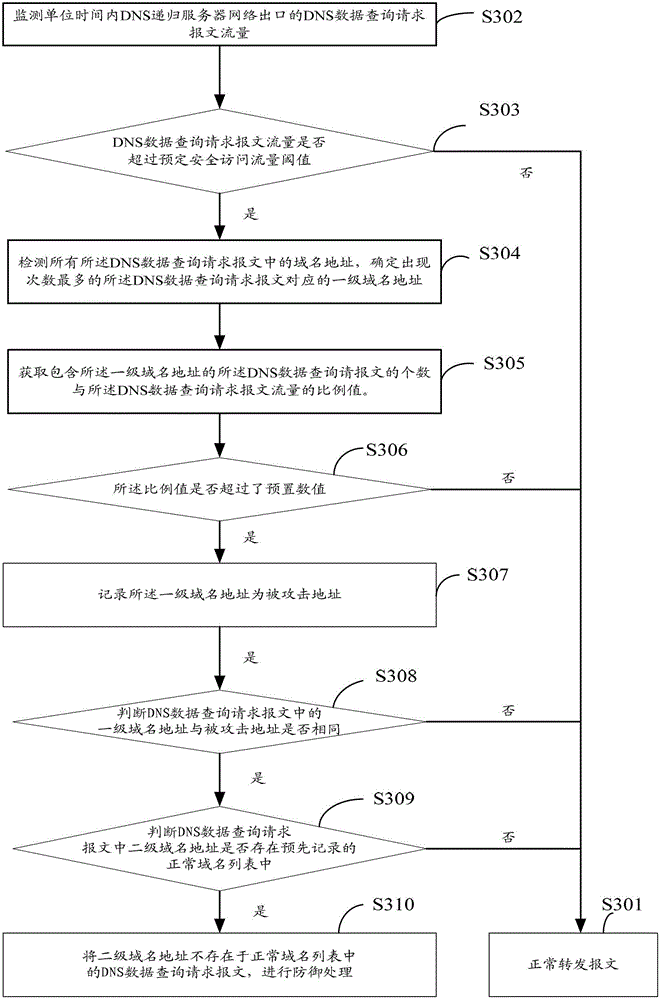
The invention provides a defense method, a defense device and a defense system for DNS (Domain Name System) services. The method comprises: monitoring a DNS data query request message flux of a DNS recursive server network gateway within unit time; judging whether the DNS data query request message flux exceeds a predetermined safety access flux threshold value or not; obtaining a proportional value between the quantity of DNS data query request messages containing top-level domain addresses and the DNS data query request message flux; in the case of judging the proportional value to exceed the predetermined value, recording the top-level domain addresses as attacked addresses; transmitting the DNS data query request messages of which the domain addresses are not the attacked addresses; judging whether second-level domain addresses of the DNS data query request messages corresponding to the attacked addresses exist in a normal domain name list or not; and performing defense processing on the DNS data query request messages of which the second-level domain name addresses do not exist in the normal domain name list. The transmission of attack messages can be effectively decreased, so that the defense of a DNS server is realized; and meanwhile, the normal DNS data query request is not affected.
Owner:BEIJING LEADSEC TECH
Method, system, and computer useable medium to facilitate name preservation across an unrestricted set of TLDS
InactiveUS20050210149A1Easy to storeInexpensive and dependable and fully effectiveMultiple digital computer combinationsTransmissionThe InternetPeriodic fee
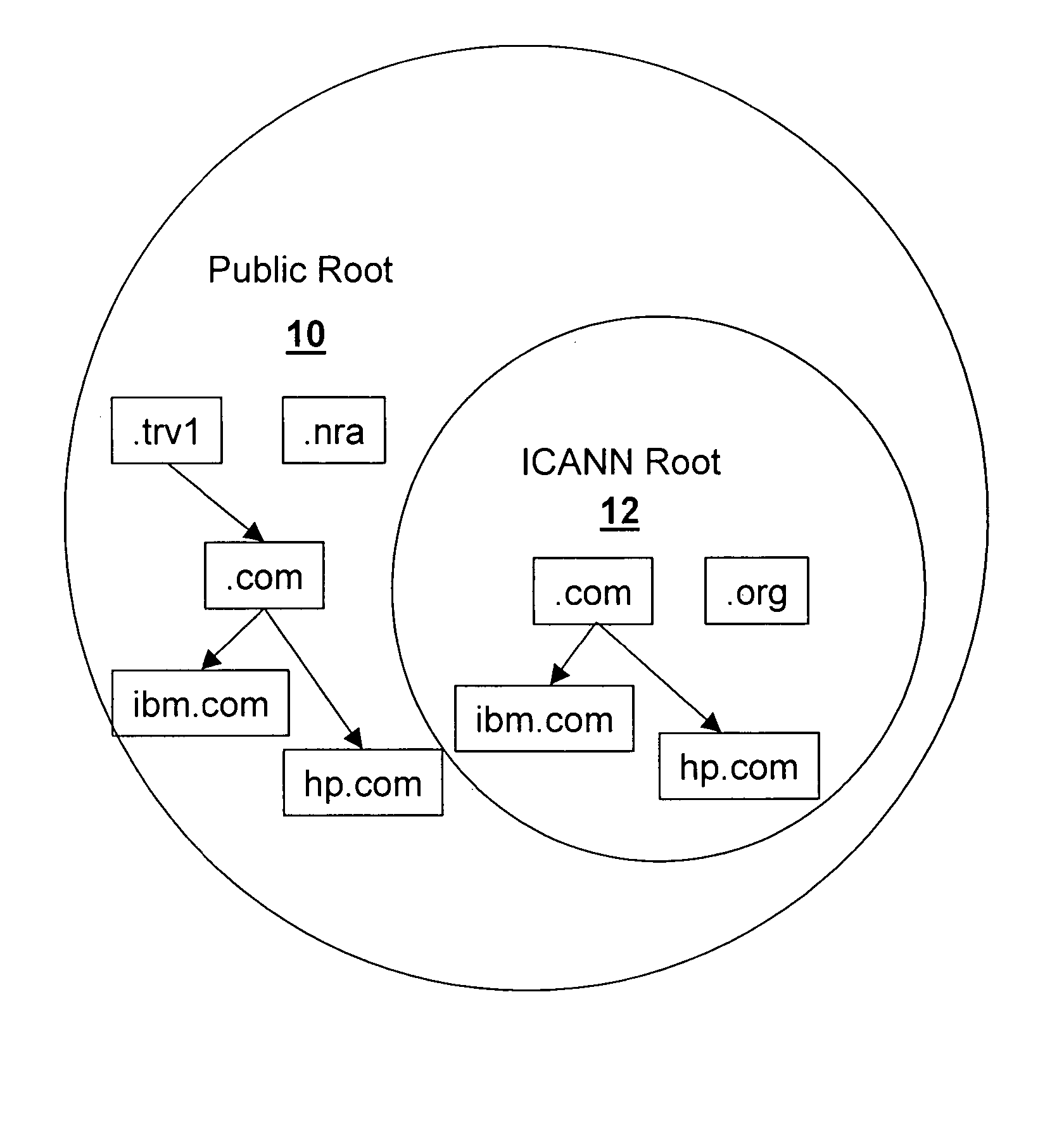
A method, system, and / or computer useable medium to facilitate name preservation across an unrestricted set of TLDs. TOP LEVEL DOMAIN TOPOLOGY (TLDT) software is executed in a TLDT system. A register is chosen to register a predetermined secondary level domain (SLD) name / inclusive name space for a particular TLD. Data is retrieved for a desired SLD name to register the SLD name in association with at least one TLD in at least one of a Public Root and an Internet Corporation for assigned Names and Numbers (ICANN) Root. A search is conducted of at least one of a Public Root and an ICANN Root and it is determined whether the desired SLD is associated with any TLDs that exist. The desired SLD is registered with all of those TLDs if the user agrees to pay the periodic fee.
Owner:KIMBALL JORDAN L
Apparatus and method for gathering of objectional web sites
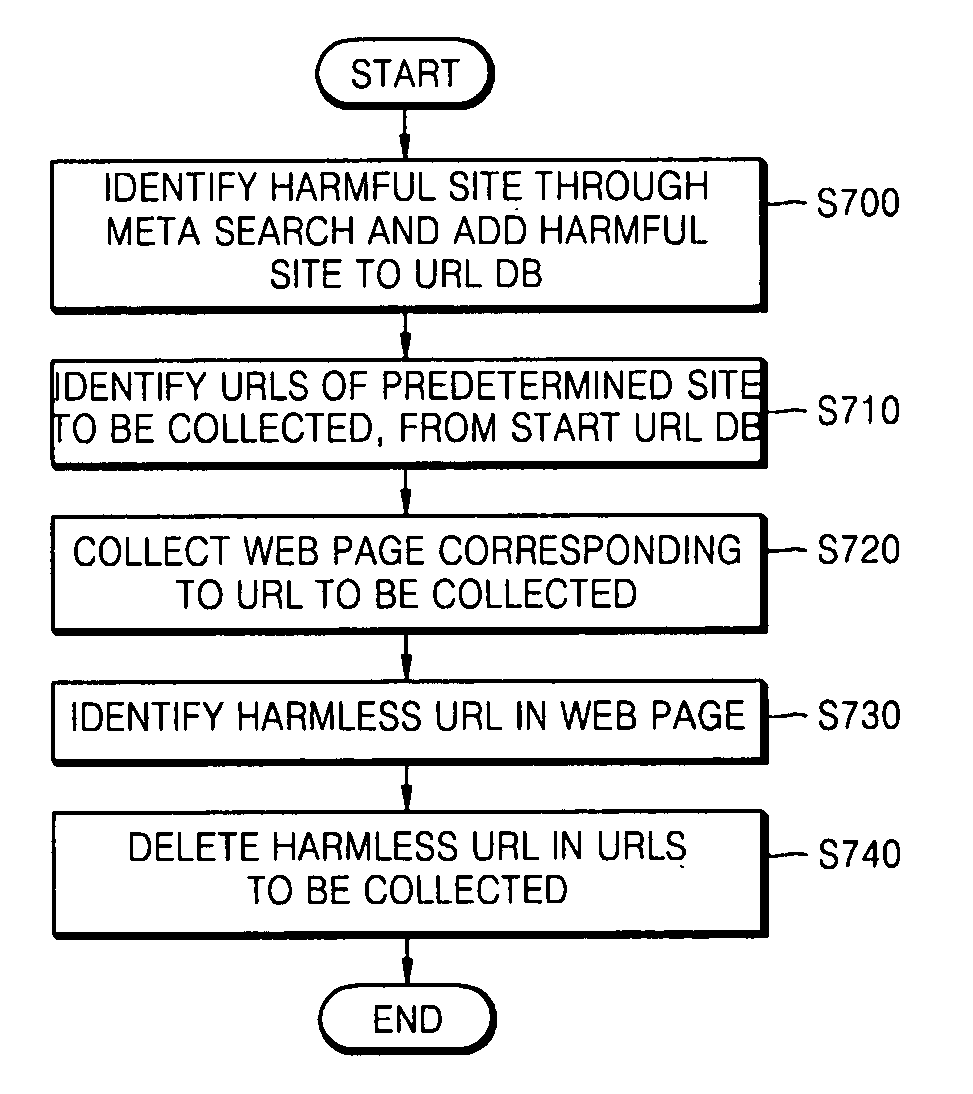
InactiveUS20070005652A1Special data processing applicationsWeb data retrieval using information identifiersWeb siteUniform resource locator
An apparatus and method for collecting harmful web sites are provided. In the apparatus, a start uniform resource locator (URL) database (DB) stores URLs of harmful web pages. A URL examination and distribution unit provides URLs grouped in relation to predetermined hosts, the URLs obtained by removing redundant URLs that are different to each other but indicate identical web pages, among the URLs stored in the start URL DB, and then among the remaining URLs, removing URLs corresponding web sites already collected. A web site collection unit collects web contents of the web sites corresponding to the URLs received from the URL examination and distribution unit. A URL extraction unit extracts URLs in the links included in the web contents collected by the web site collection unit, identifies harmless URLs based on top-level domain names and a harmless URL list among the extracted URLs, and removes the identified harmless URLs from the URLs that are the object of the collection. According to the apparatus and method, the harmful site database is helped to maintain accurate, abundant, and latest information.
Owner:ELECTRONICS & TELECOMM RES INST
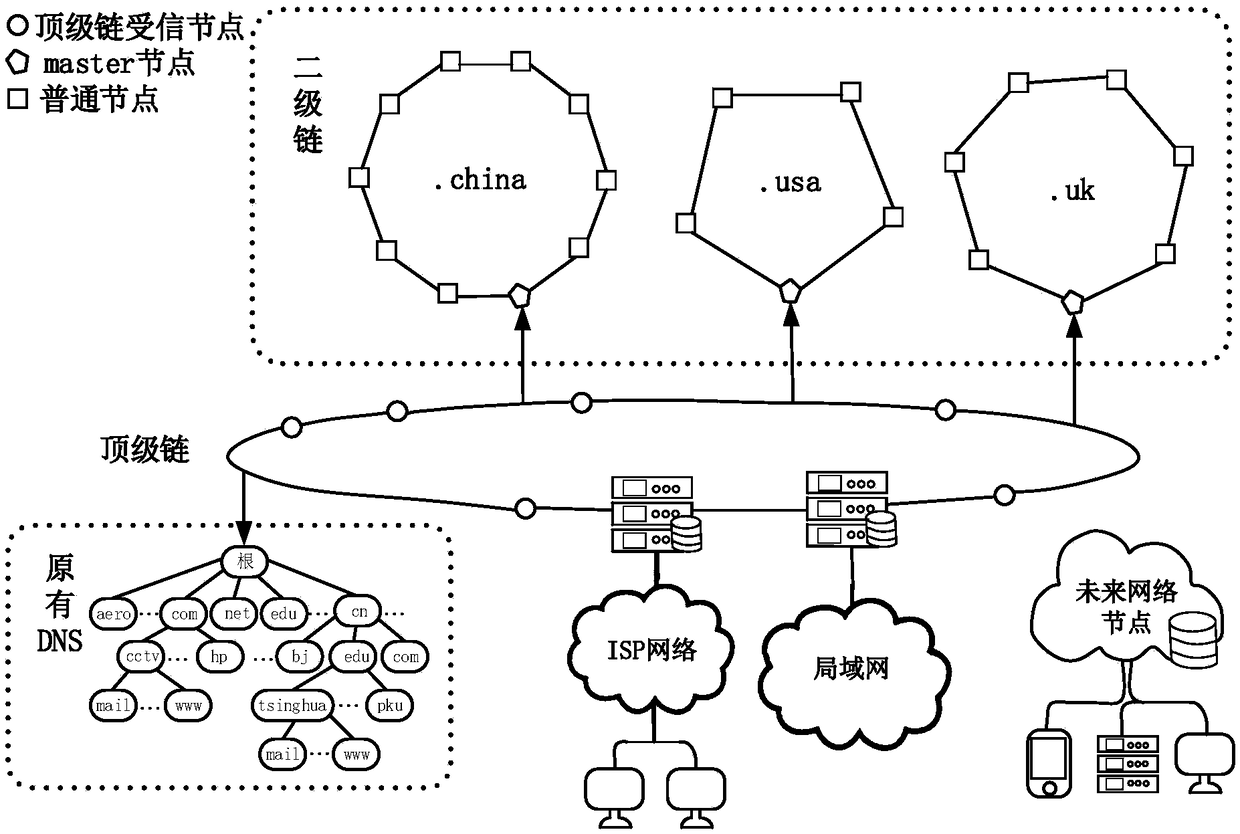
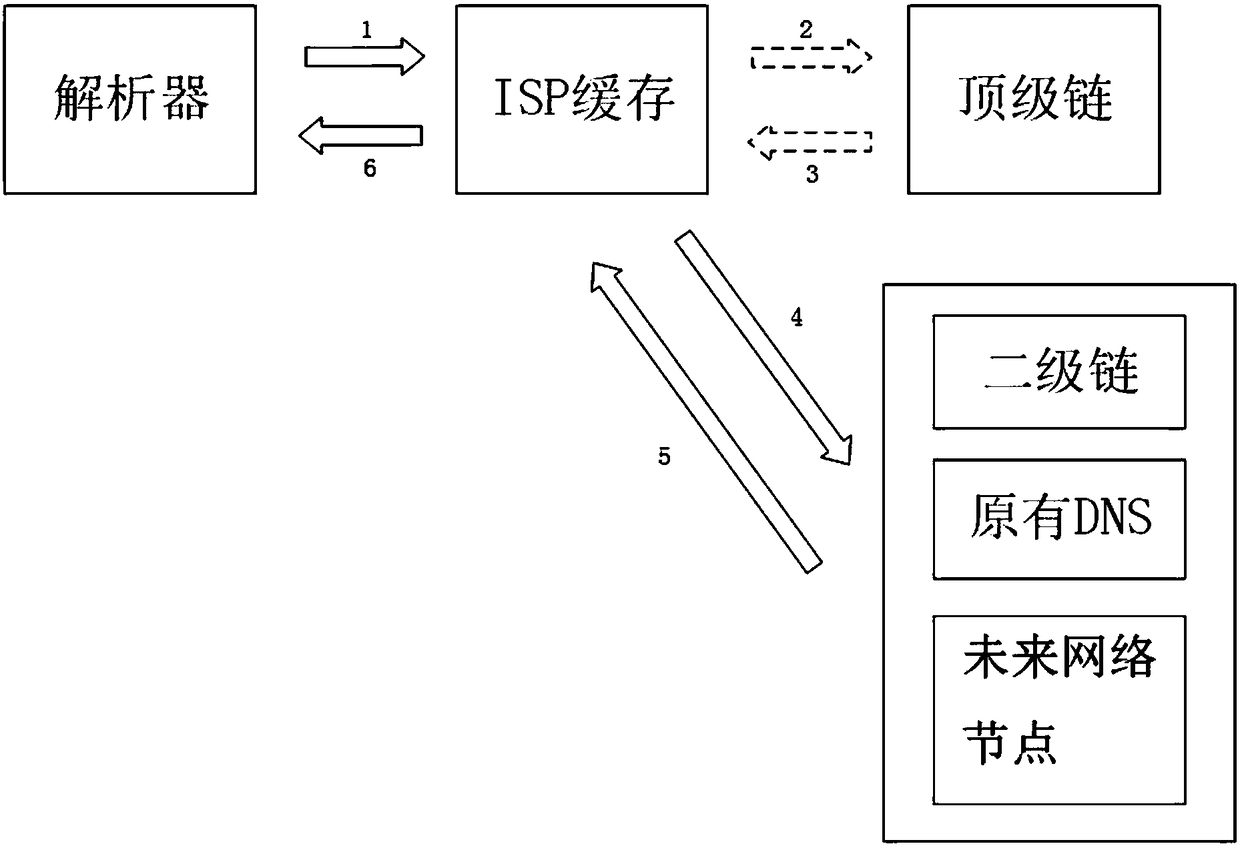
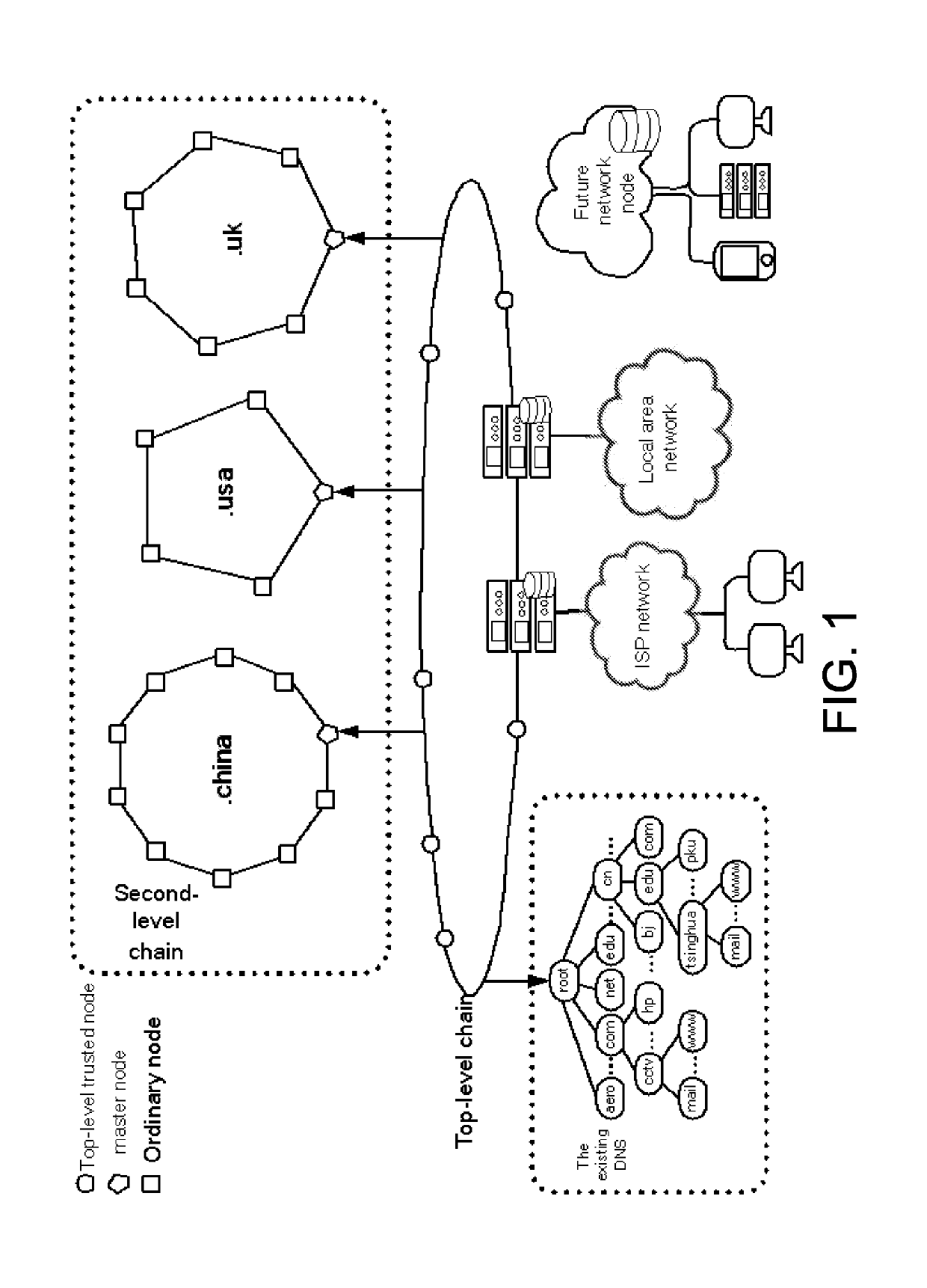
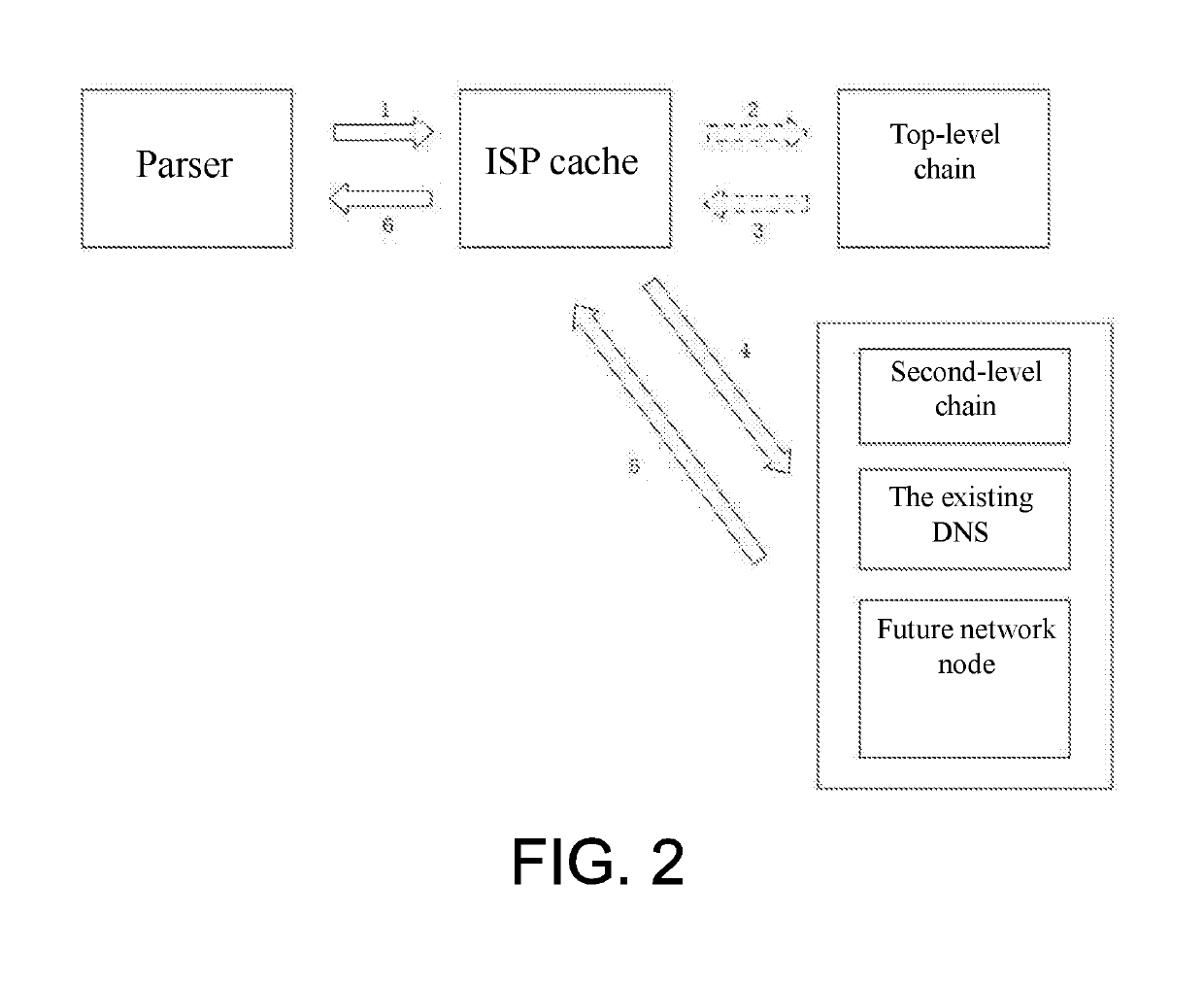
Blockchain-based domain name resolution system
ActiveCN108064444AImprove management efficiencyEfficient managementSecuring communicationChain networkChain link
The invention relates to a blockchain-based domain name resolution system. The domain name resolution system adopts a hierarchical structure, including a top-level domain name chain network, a second-level domain name chain network, a future network node and an original DNS system network, and the top-level domain name chain links the second-level domain name chain network, the future network nodeand the original DNS system network; the top-level domain name chain network is used for each professional organization to deploy reliable server nodes to form an allied blockchain network, each nodeserver records information about all current top-level domain names, second-level domain name chain nodes, future network nodes, and existing DNS system root nodes; the second-level domain name chainnetwork is used for domain name registration and management, and records a record of all second-level domain names and subdomain names to which they belong; the future network node is used for storing metadata and indexes thereof in the future network. The resolution request is reduced and the efficiency of domain name resolution is effectively improved.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
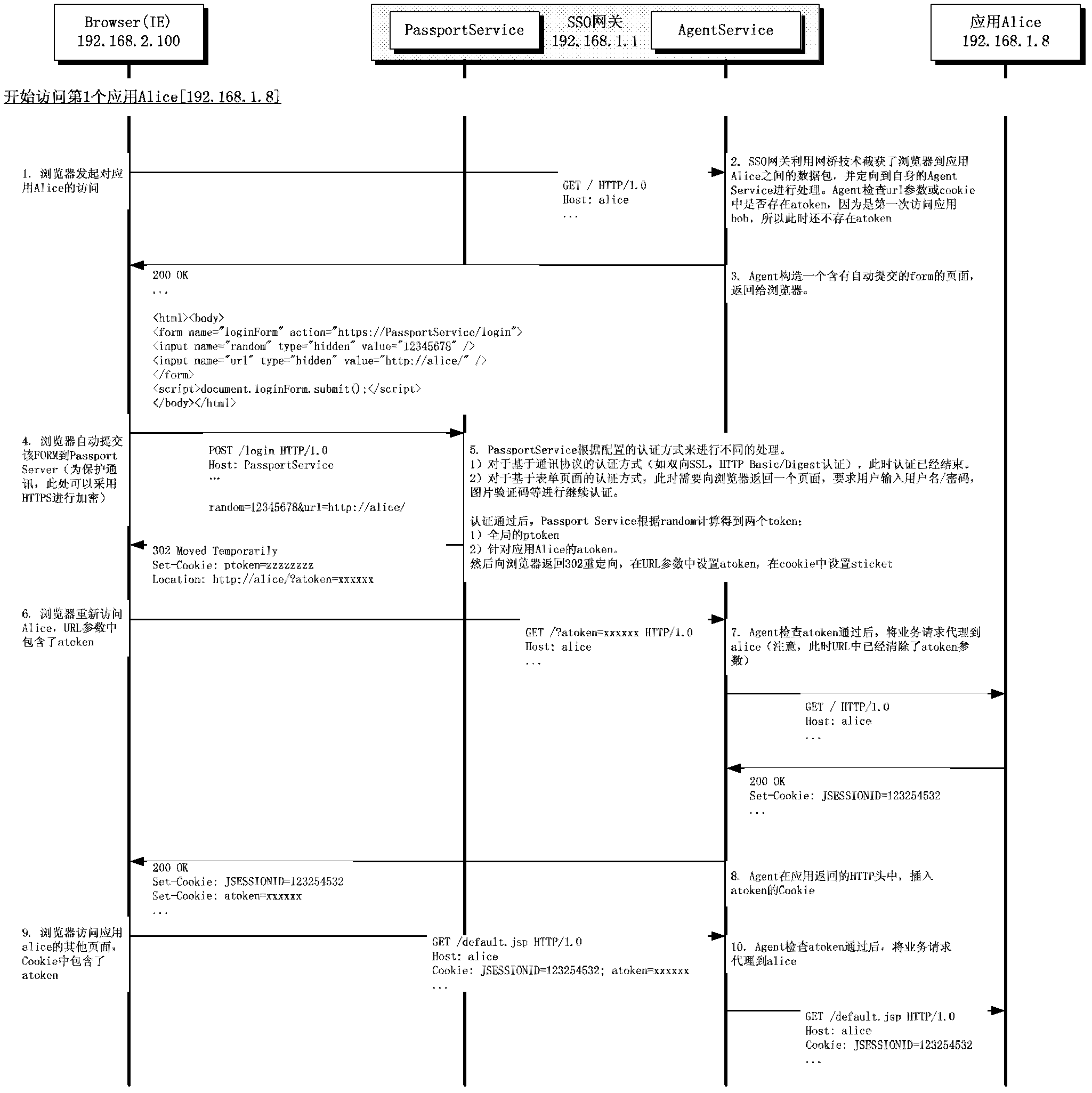
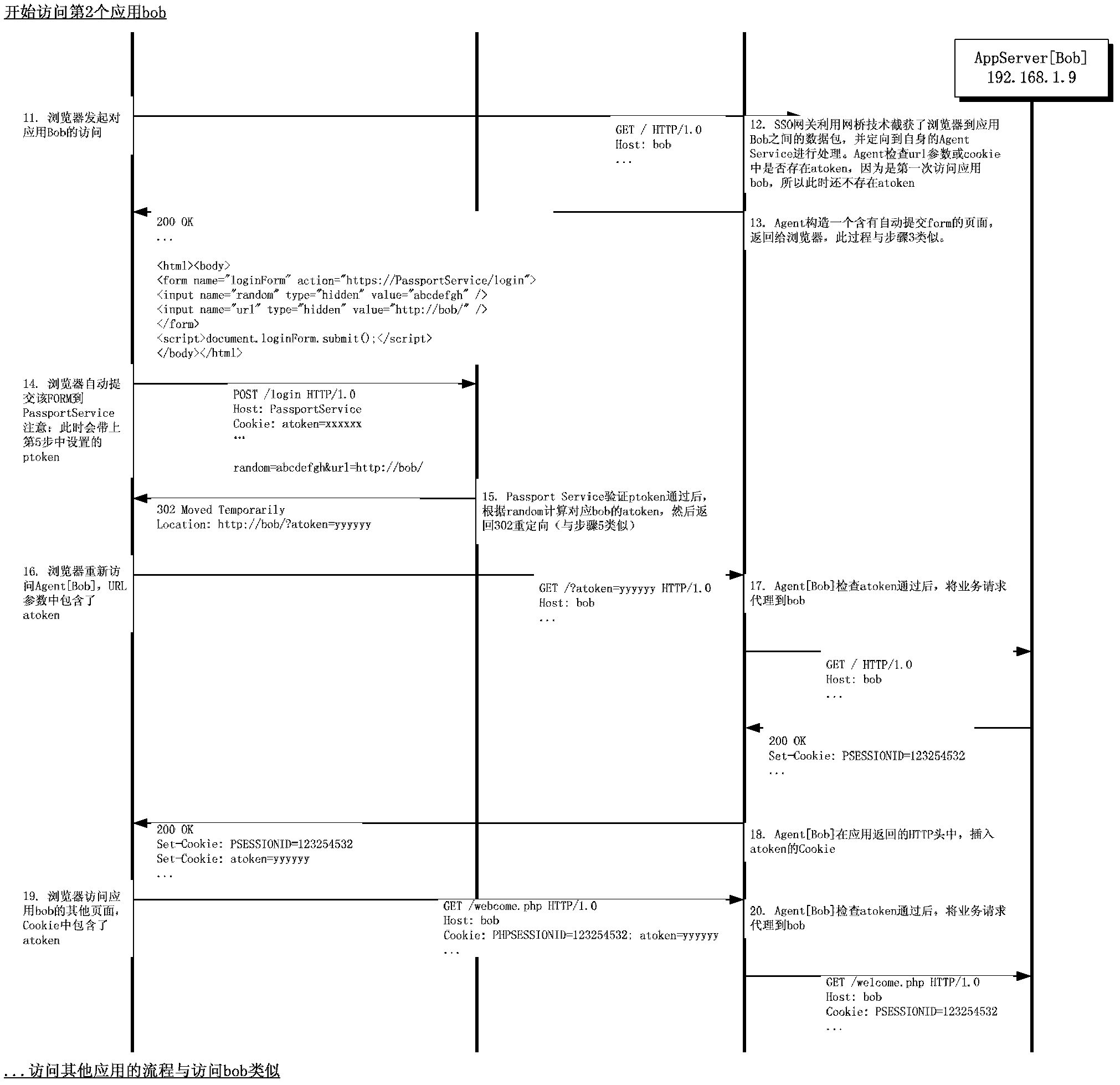
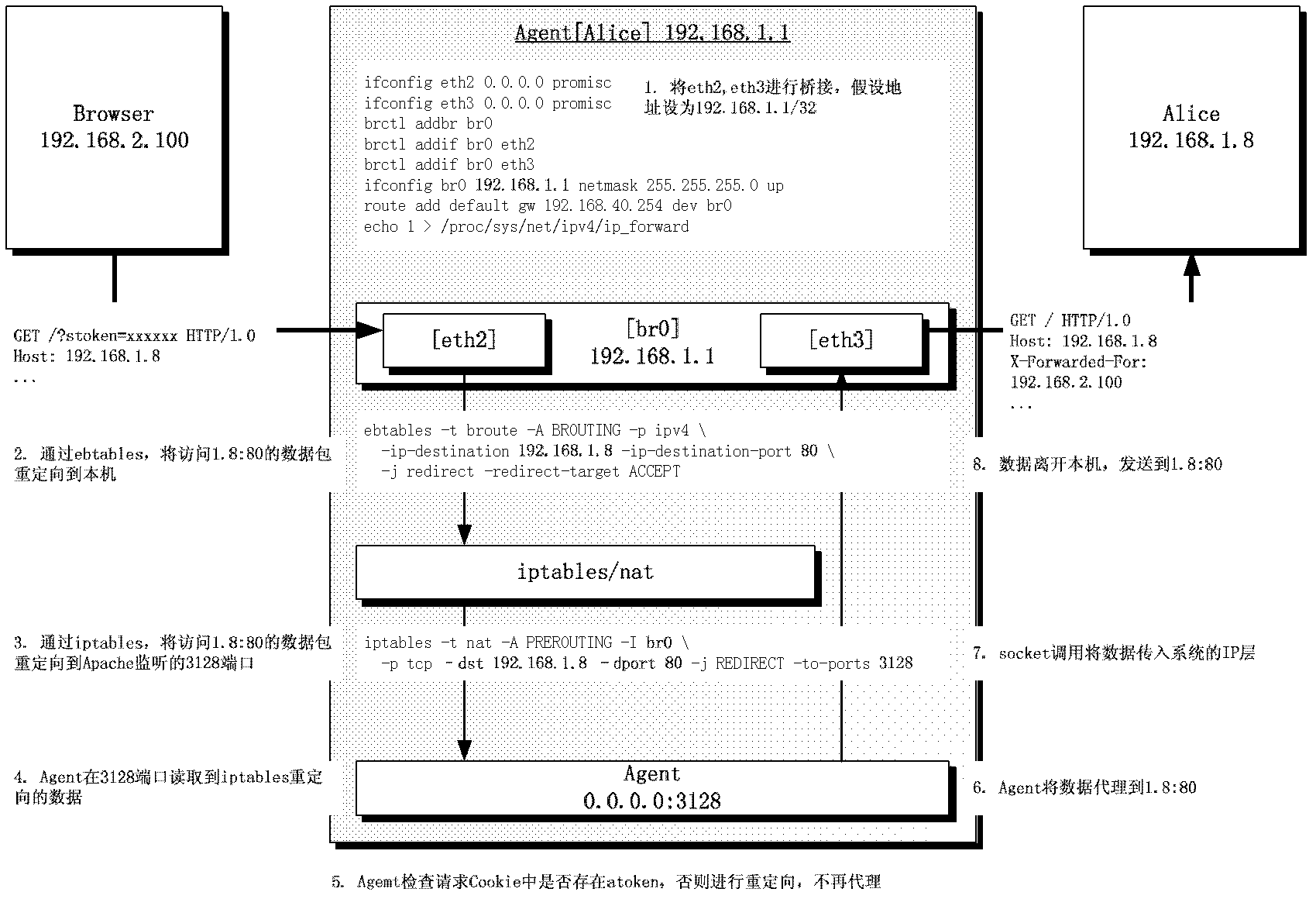
WEB single sign-on method completely transparent to user and application
InactiveCN103188295ANo need to change network deploymentNo need to change access habitsTransmissionWeb applicationNetwork packet
The invention discloses a WEB single sign-on method completely transparent to a user and an application. The method comprises the following steps that: 1, an HTTP (Hyper Text Transport Protocol) data packet between the user (a browser) and the WEB application is intercepted by a transparent bridge technology, 2, the user is redirected to an SSO (Single Sign-on) server by a page redirection technology during first access, 3, after SSO service is certified, the browser is redirected back to the WEB application and a security Token is set, and 4, when the browser accesses the application again, an SSO gateway inspects the security Token, and the access is passed if the security Token is valid. According to the WEB single sign-on method, the single sign-on of the WEB application can be achieved under the conditions that a client or plugin is not required to be installed and the application is not required to be modified, and a top-level domain can be crossed.
Owner:KOAL SOFTWARE CO LTD
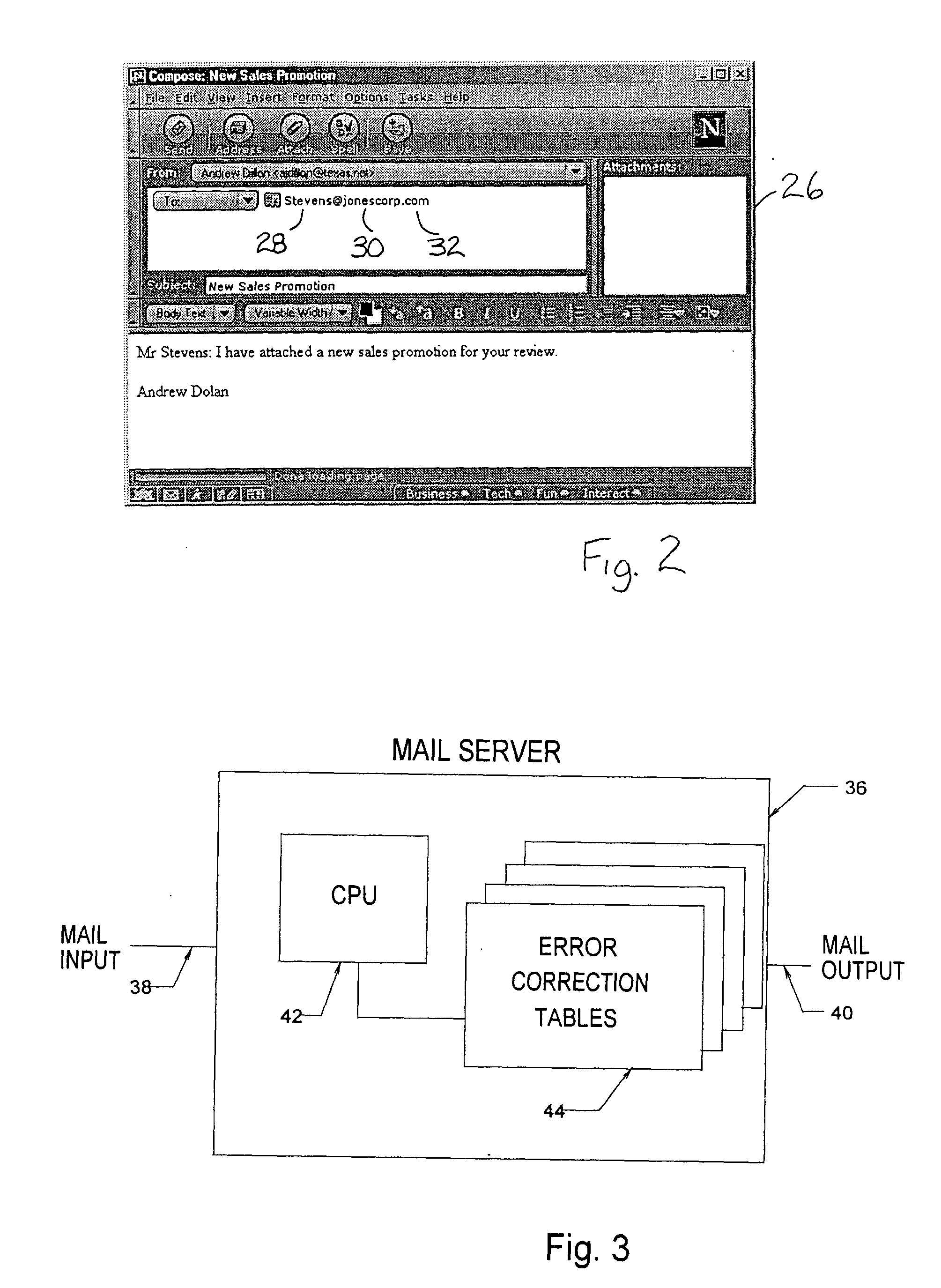
Method and system for automatic error recovery in an electronic mail system
InactiveUS20050039100A1Improve efficiencyError preventionTransmission systemsWorld Wide WebElectronic mail
A method and system for automatic address error recovery in an electronic mail system where electronic mail messages are transferred by identifying an address which includes a user name and a domain name which includes a top level domain suffix. In the event an electronic mail message destination cannot be determined, likely appropriate destinations are automatically determined by systematically determining common alternate spellings of the user name, likely alternate domain names or an alternate top level domain suffix. Alternately, a table of expired addresses and corresponding new addresses can be maintained and examined to determine a likely appropriate address. At least one likely appropriate address is presented to a sender and the electronic mail message is then transmitted to a destination by the sender.
Owner:IBM CORP
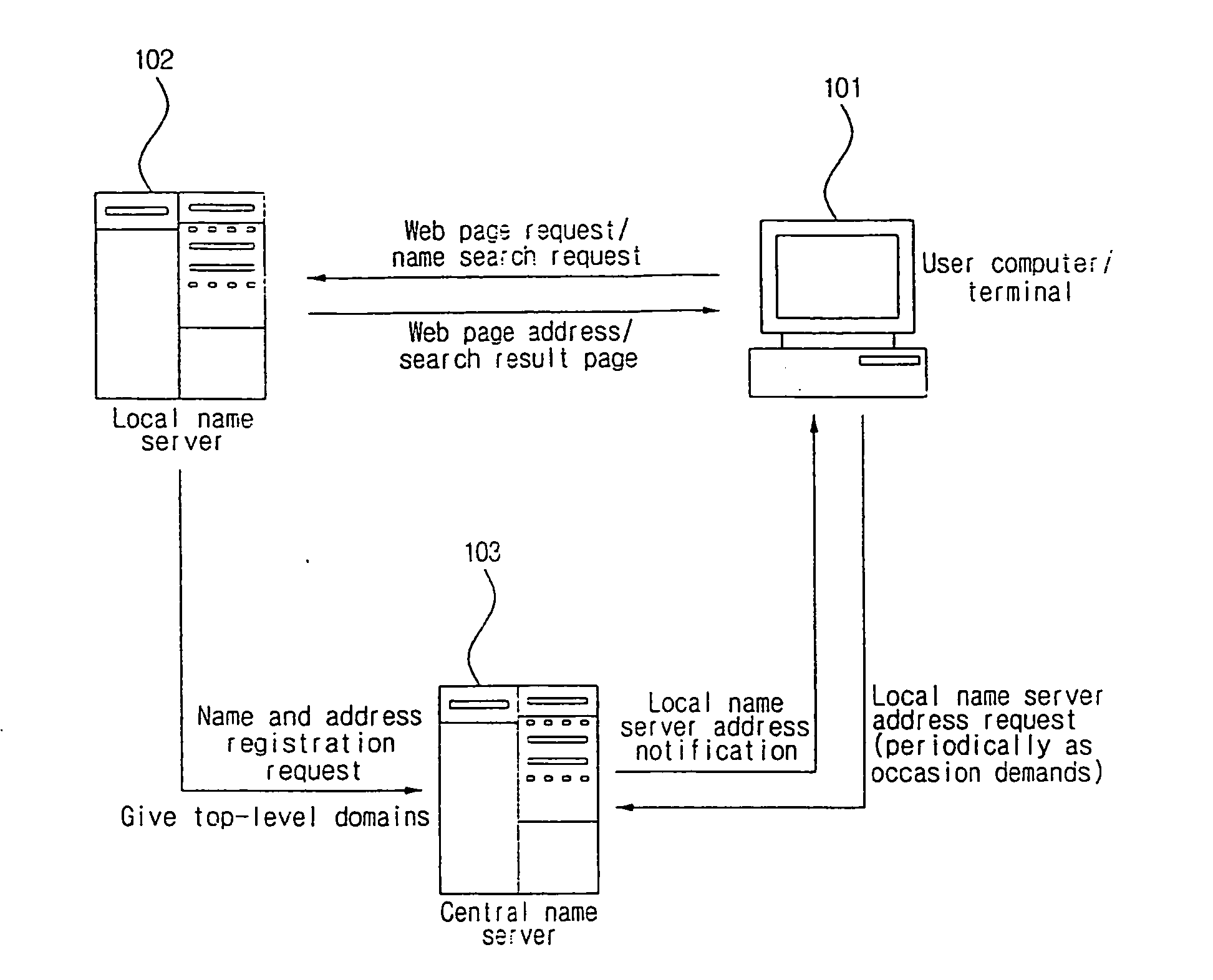
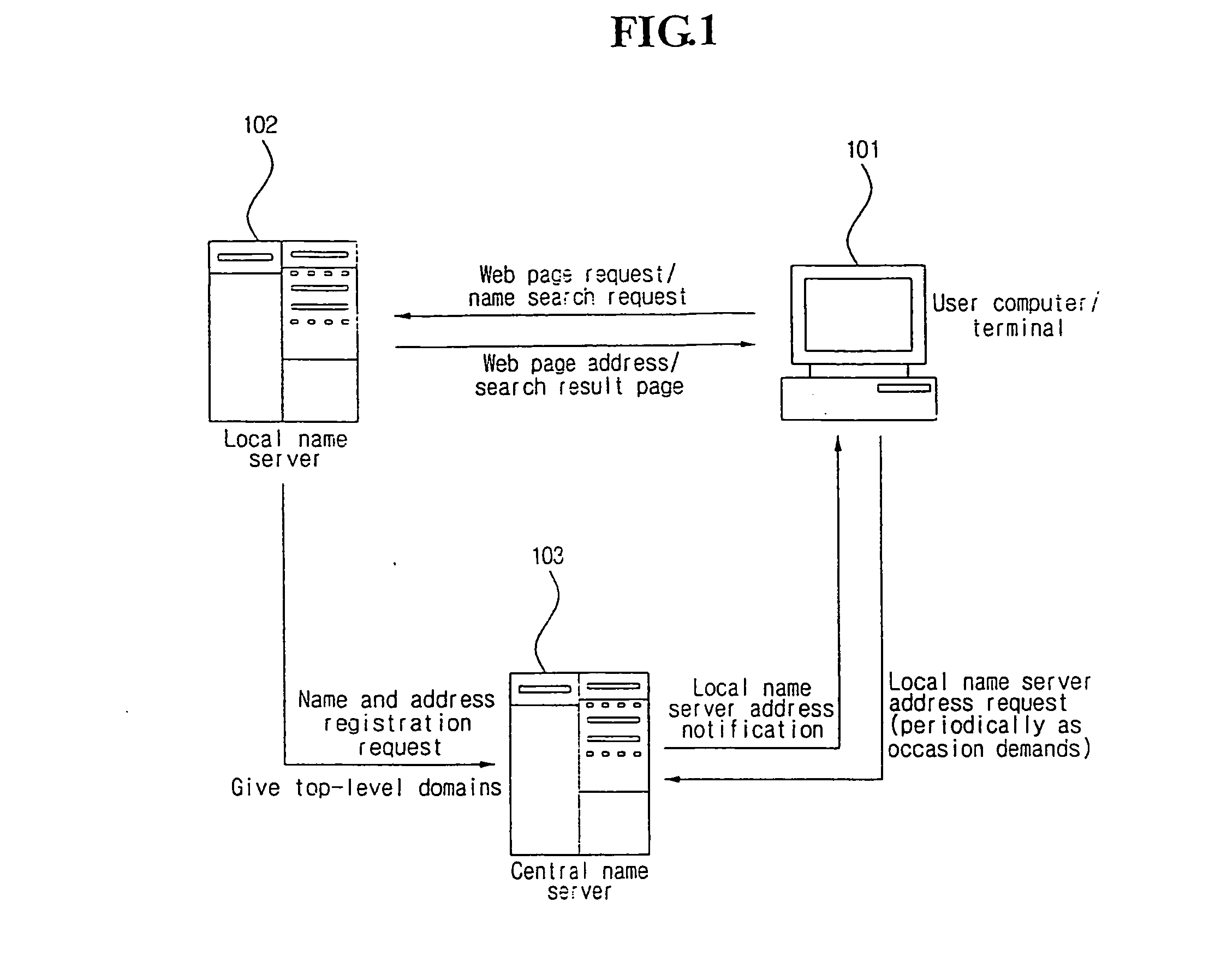
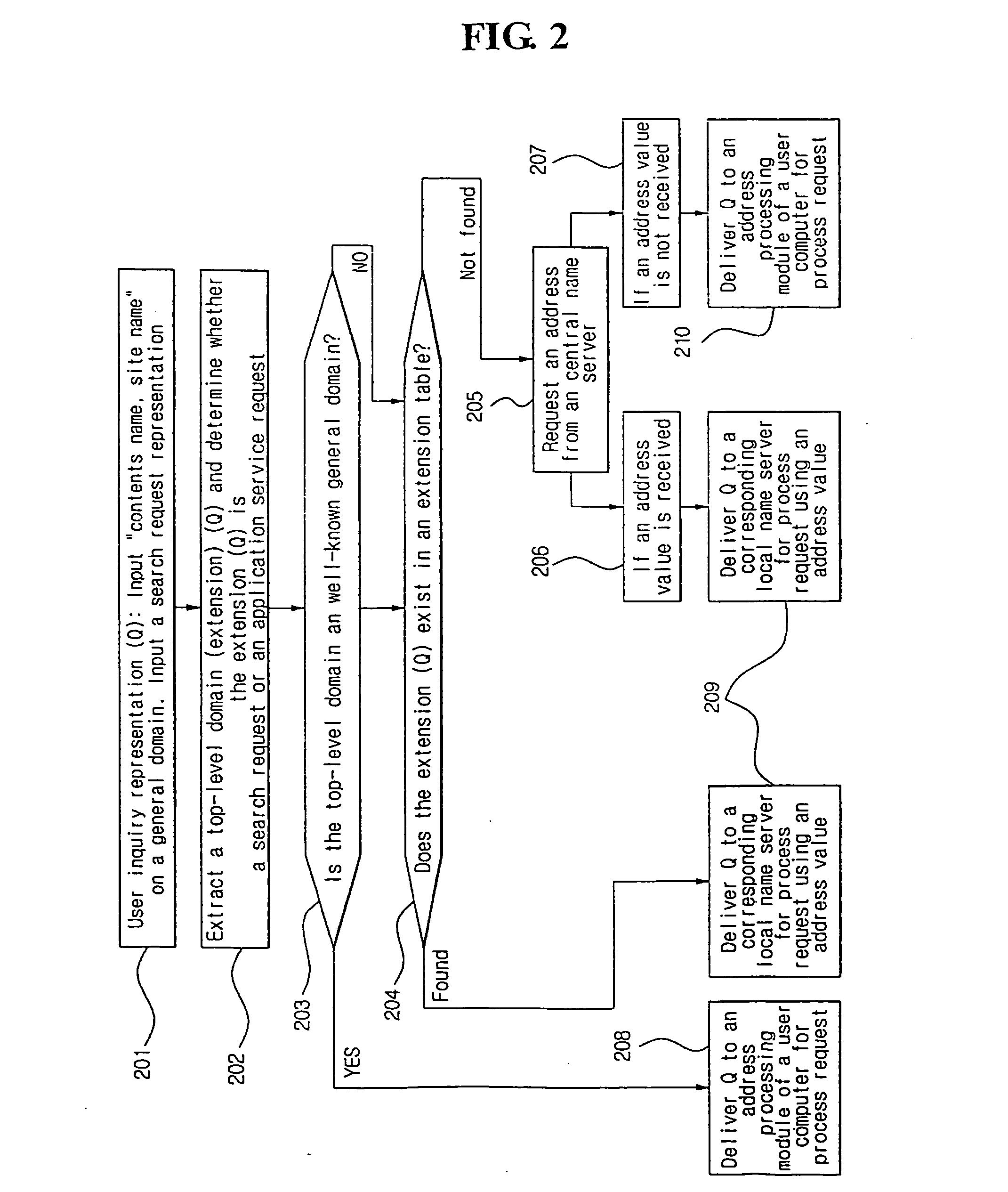
Internal natural domain service system with local name servers for flexible top-level domains
InactiveUS20060195609A1Data processing applicationsDigital data processing detailsName serverUser input
Extended internal domain name service of URI taking distributed service scheme, wherein site names or proper nouns that are not formal top-level domains are used as top-level domains. A central name server, a local name server and a user computer, each of which is loaded with a program for domain service. A service preparation step, the local name server registers a name and address of a site into the central name server and is given a top-level domain from the central name server. A name registration step, the local name server gives names to resources inside a site or site user registers names of information into the local name server. A domain inquiry step, the user computer inquires internal domains of particular local name server without confusion to existing domain service when user inputs internal domains according to a domain scheme.
Owner:HAN YOUNG SEOK +1
Blockchain-based domain name resolution system
InactiveUS20190166085A1Improve management efficiencyImprove analysis efficiencyEncryption apparatus with shift registers/memoriesChain networkBase domain
The invention relates to a blockchain-based domain name resolution system, characterized in that the domain name resolution system adopts a layered structure comprising a top-level domain name chain network, a second-level domain name chain network, a future network node and an existing DNS system network; the top-level domain name chain network links the second-level domain name chain network, the future network node and the existing DNS system network respectively, and the top-level domain name chain network is used for each professional organization to deploy the server nodes having a reliable performance respectively to form a union blockchain network, wherein each node server records the information of all the current top-level domain names, the second-level domain name chain nodes, the future network nodes and the root nodes of the existing DNS system; the second-level domain name chain network is used for the registration and management of domain names, and recording of all the second-level domain names and their subdomain names; the future network node is used for the storage of the metadata and index in the future network. The invention reduces the resolution request, thus effectively improving the efficiency of domain name resolution.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
Device and Method for World Wide Web Organization
InactiveUS20090006351A1Website content managementSpecial data processing applicationsWeb contentInformation retrieval
A method and a device for locating World Wide Web content includes defining a plurality of top-level domain names with each top-level domain name including a different unique category term and a prefix common to all the top-level domain names, associating a plurality of subcategories with each unique category term, where each subcategory is logically related to the unique category term, presenting a first web page located by a first top-level domain name within the plurality of top-level domain names, the first web page including a first content related to at least one of the plurality of subcategories associated with a unique category term in the first top-level domain name, storing the unique category term in the first top-level domain name in a history, receiving a first at least one search-narrowing input from a user, storing the first at least one search-narrowing input in the history, combining the first at least one search-narrowing input with the unique category term to form a first new search criteria, presenting a second web page located by a second top-level domain name within the plurality of top-level domain names, the second web page including a second content related to the first new search criteria, receiving a second at least one search-narrowing input from a user, storing the second at least one search-narrowing input in the history, and combining the second at least one search-narrowing input with the first at least one search-narrowing input and the unique category term to form a second new search criteria.
Owner:VAN DER MOST DAVID J
Richard and Preston super network, "The Super Net"
InactiveUS20050114484A1Multiple digital computer combinationsOffice automationWeb siteInternet users
We have invented extensions to the current Domain Name System which include top level domains that create more available domain names. Some of the newly introduced top level domains provide information on a web sites location of operation. This will enable search engines to categorize search results based on location. Also the domain name systems we introduce, provide a long term method of expanding the current domain name system. They also offer domain names which include words internet users are familiar with. Some of the new top level domains address growing internet related areas in which domain name usage will be pertinent. Areas such as communications and internet capable devices will benefit from the top level domains created specifically for them. Another area addressed by the new top level domains is countries with large internet usage. Countries like Japan United States and China can use multiple top level domains created specifically for them because of their large number of internet users and high tech businesses. The need for personal web sites is also increasing. Internet profiles are means for people to allow others to view information about them. A new extension for personal websites will allow more people to have a web address to post information about them. The domain name systems and top level domains we have invented will coexist with the current domain name system.
Owner:WILSON RICHARD PHILLIP +1
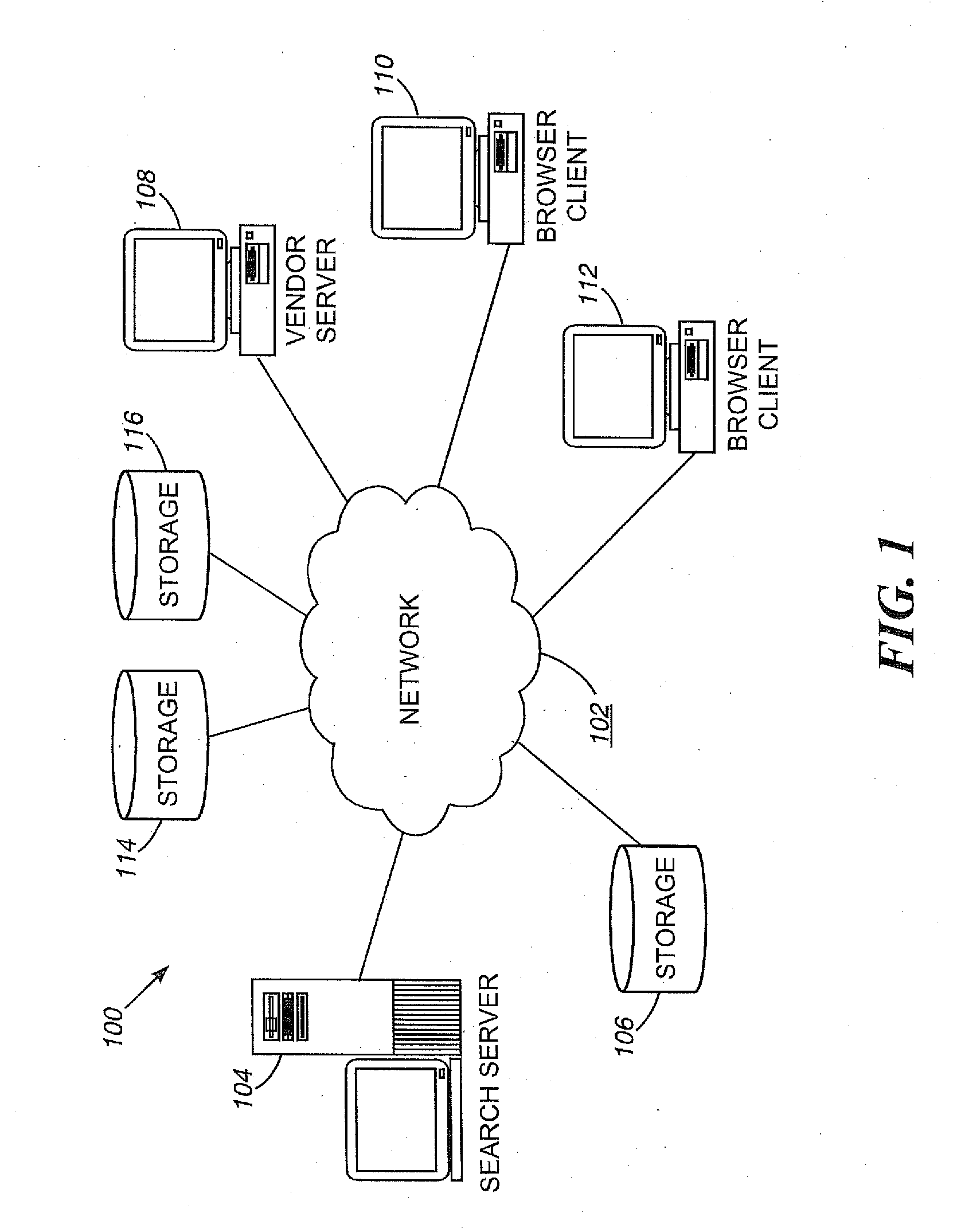
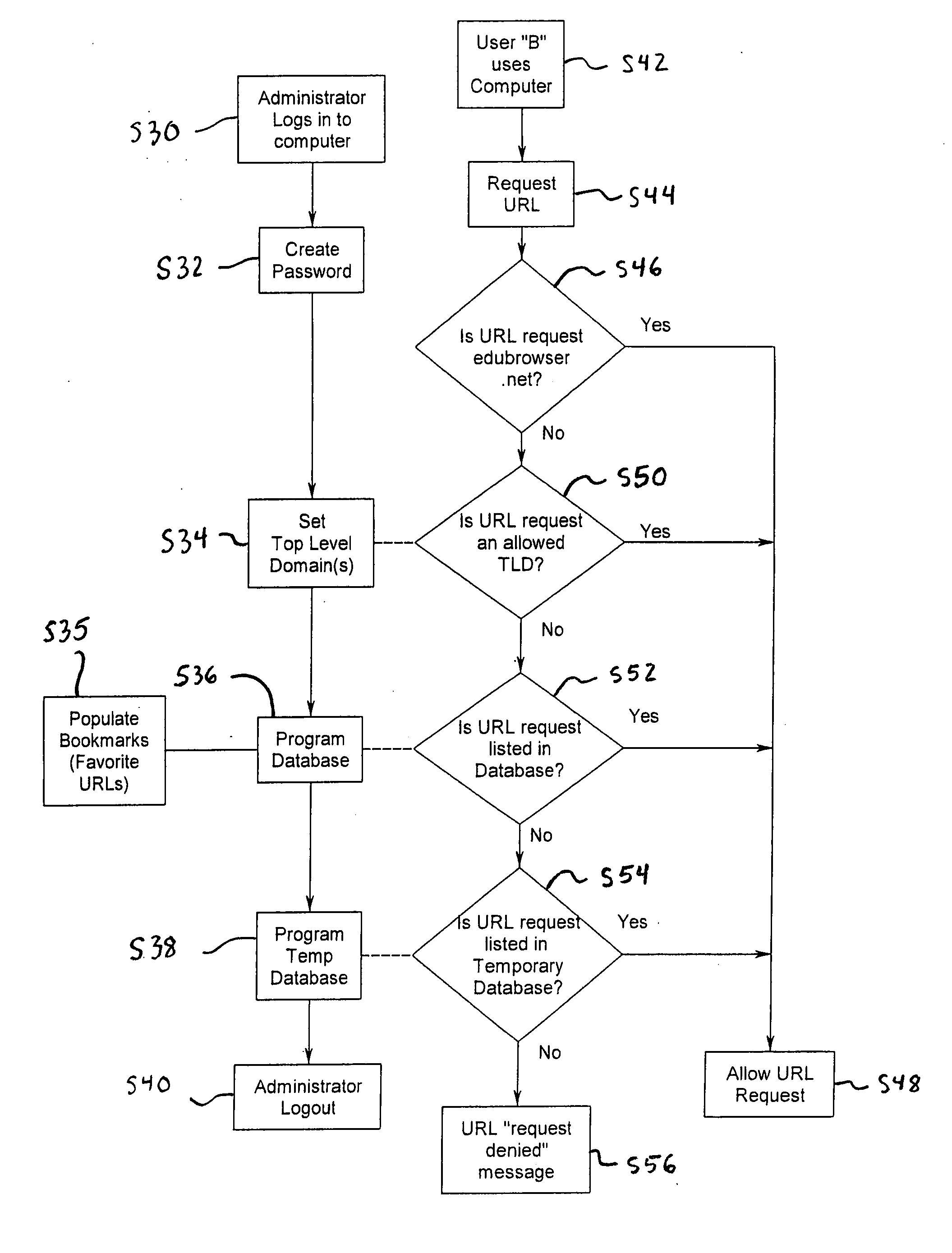
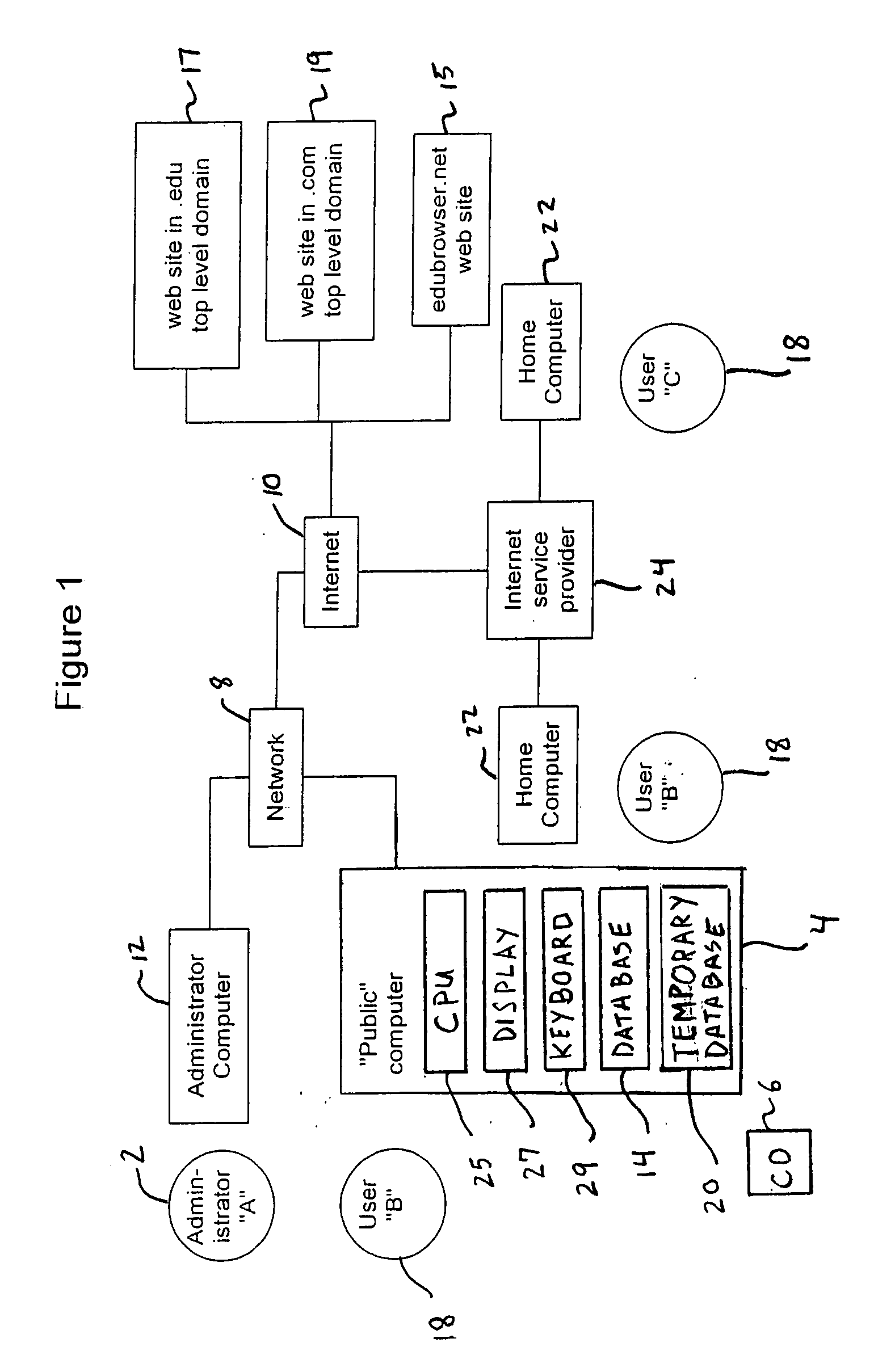
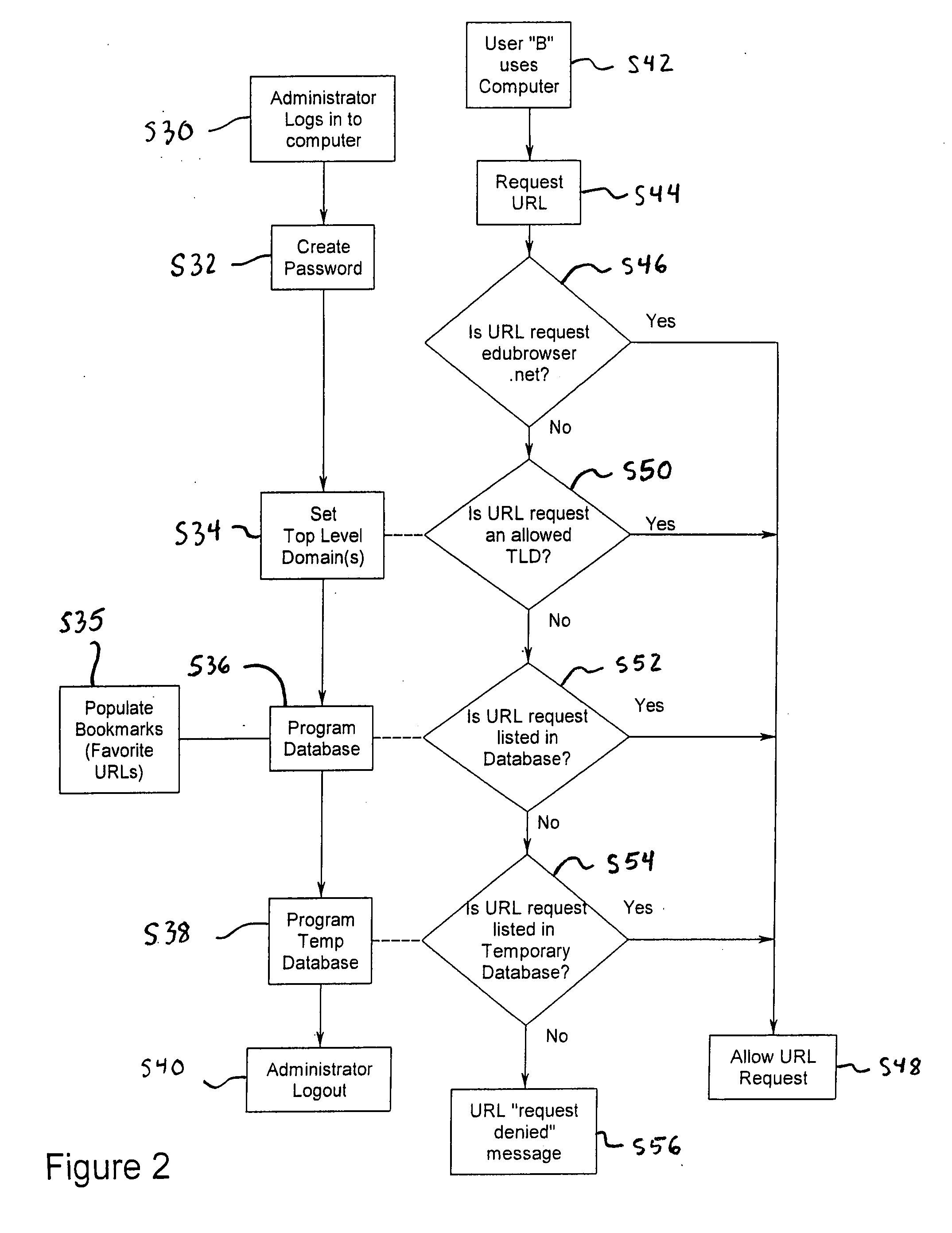
System and method for restricting internet access of a computer
InactiveUS20080059634A1Avoid disadvantagesEasy to useDigital data information retrievalMultiple digital computer combinationsWeb siteWeb browser
A system for selectively allowing and restricting access to websites requested by a user includes a computer having a central processing unit, a display, a keyboard and a web browser installed on the central processing unit. The web browser has a list of allowable top level domains (TLDs), and the central processing unit includes a database having a list of allowable uniform resource locators (URLs). The web browser compares the TLD and URL associated with a requested website to respectively determine if they are the same as a TLD or URL in the lists of allowable TLDs and URLs. If either the TLD or URL associated with the requested website is the same as a TLD or URL on the lists, the user is allowed to access the requested website on the computer. If neither the TLD nor the URL associated with the requested website is the same as a TLD or URL on the lists of allowable TLDs and URLs, the user is denied access to the requested website on the computer.
Owner:COMMONS RICHARD
Suggesting concept-based top-level domain names
ActiveUS20090248735A1Improve relationshipDigital data processing detailsSpecial data processing applicationsComputer scienceTop level domain
Methods and systems of the present invention allow for displaying suggested concept-based results. An exemplary method may comprise the steps of receiving a combination domain name and top level domain (TLD), determining from ontological calculations suggested TLDs related to the concept of the combination and displaying the suggested combination of the domain name with suggested TLDs.
Owner:GO DADDY OPERATING
Domain name registration system and methods for open top level domain environment
InactiveUS20070180056A1Multiple digital computer combinationsTransmissionImproved methodComputer science
Owner:ASSAD ELIAS
Alliance chain based top level domain management method and system
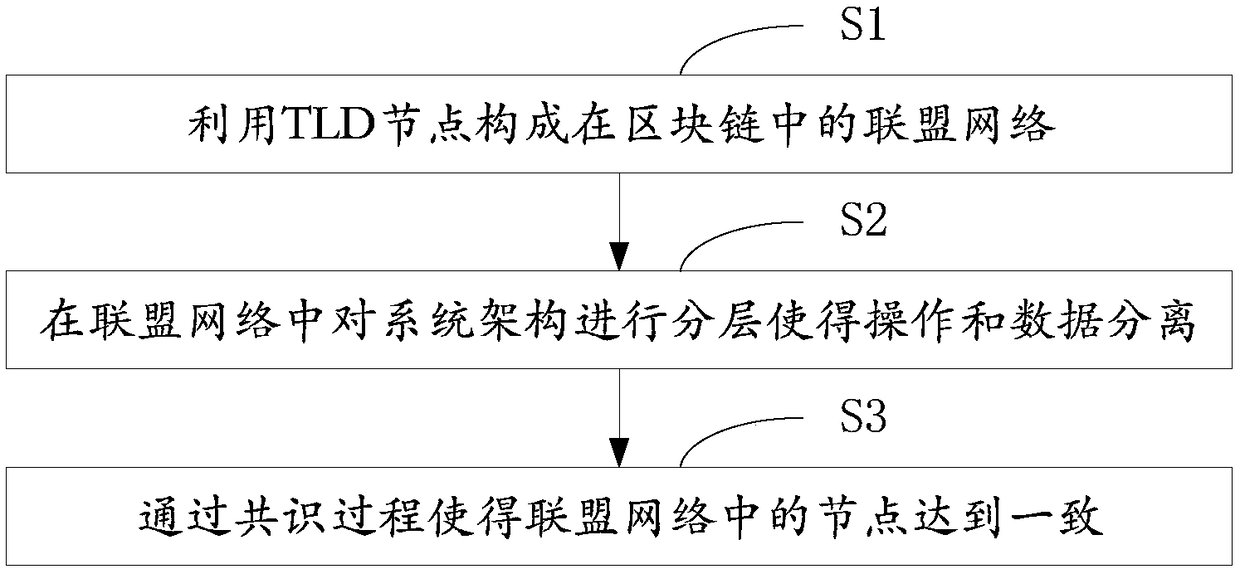
ActiveCN108124502ASimple and efficient consensus processGuaranteed safety and reliabilityData switching networksStructure of Management InformationSystem structure
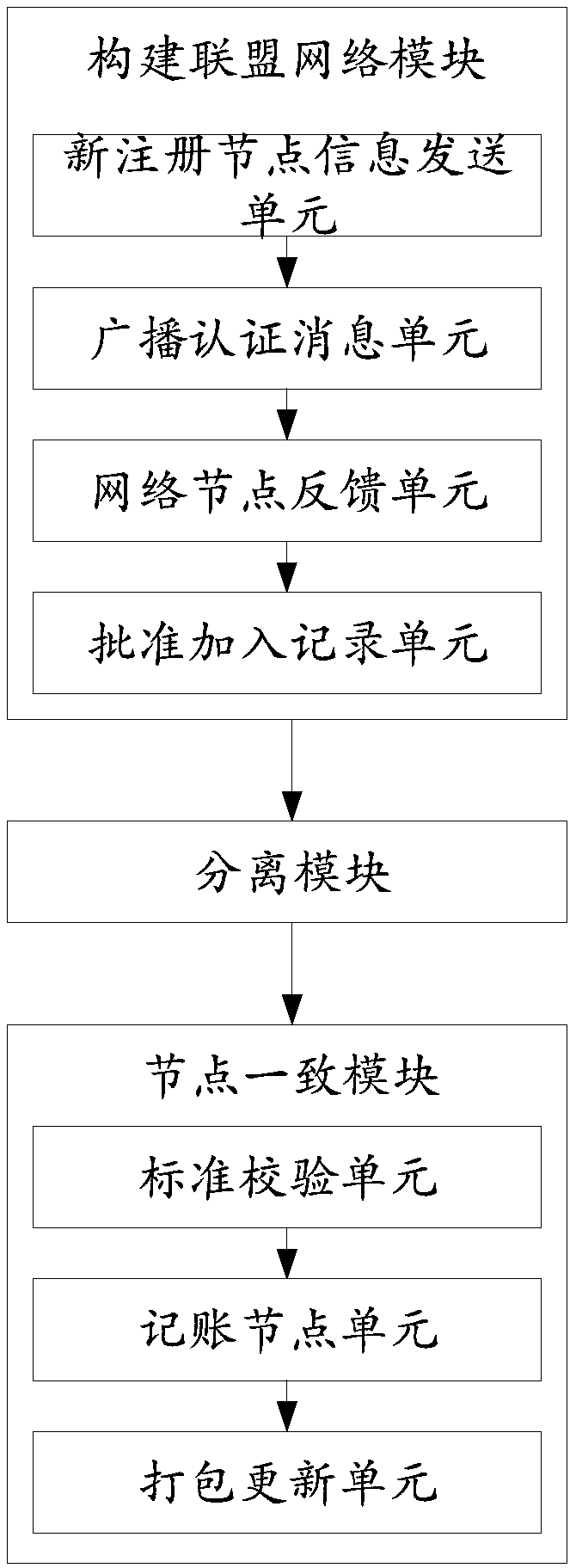
The invention is suitable for a field of Internet technology improvement and provides a block chain based top level domain management method. The method includes steps of A, utilizing TLD nodes to form an alliance network in a block chain; B, performing layering on a system structure in the alliance network so as to separate operation from data; C, enabling consistence among nodes in the alliancenetwork through a consensus building process. Through the simpler and more efficient consensus building process, system safety and reliability are ensured and system efficiency is improved; through structural layering on the system, system efficiency and transportability are ensured.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
Cross-domain single-point registration system and method facing system integration
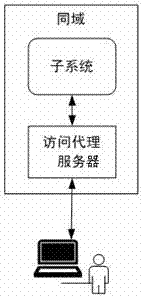
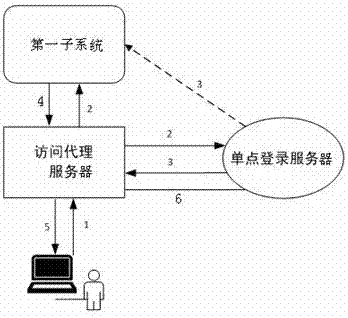
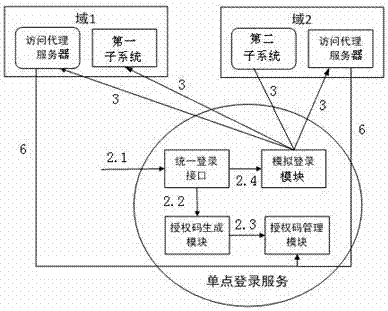
ActiveCN106936853AImplement single sign-onSupport free loginTransmissionSystem integrationProxy server
The invention discloses a cross-domain single-point registration system and method facing system integration. The system comprises a terminal, access proxy servers and a single-point registration server. Each access proxy server is disposed in front of a subsystem, positioned in the same top level domain with the subsystem, and used to process and forward all requests to the subsystem in full authority; and the single-point registration server comprises a unified registration interface, an authorization code generation module, an authorization code management module and a simulated registration module. Under the condition that codes of the system are not invaded and system setting is not changed, cross-domain cross-development-platform single-point registration is realized, and the system is suitable for a high concurrent scene and supports a registration-free condition. When a user access the subsystem, the corresponding access proxy server redirects a request to a unified registration interface, and a unique authorization code is generated after that the user succeeds in registration. A simulated registration manner is used to send the authorization code and registration information to the subsystem. The user can use the authorization code to access the system or other systems directly needless of registration again.
Owner:HOHAI UNIV +1
Agile network protocol for secure communications using secure domain names
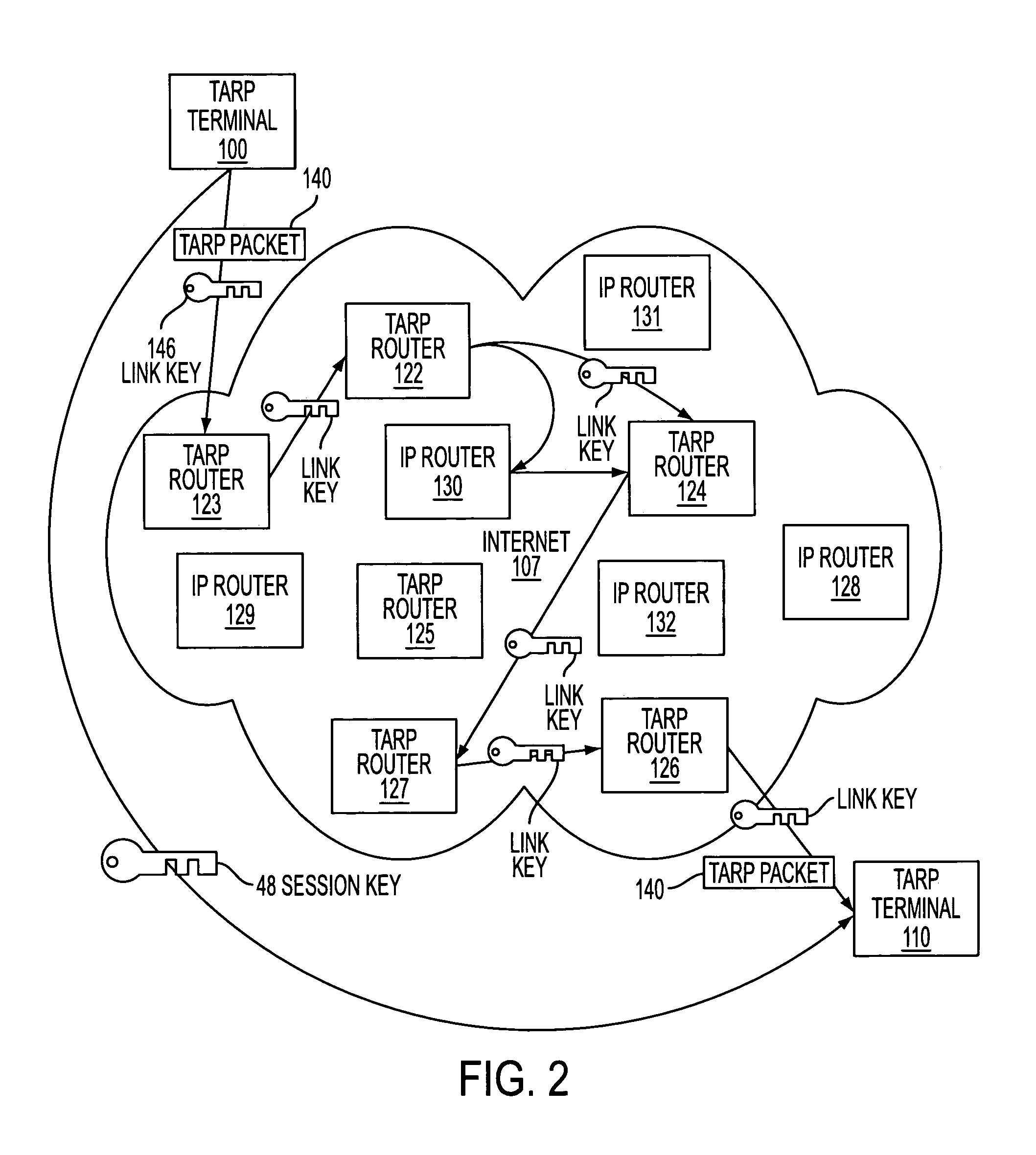
InactiveUS20080040792A1Reduce network loadSmall sizeWeb data indexingComputer security arrangementsSecure communicationNetwork addressing
A secure domain name service for a computer network is disclosed that includes a portal connected to a computer network, such as the Internet, and a domain name database connected to the computer network through the portal. The portal authenticates a query for a secure computer network address, and the domain name database stores secure computer network addresses for the computer network. Each secure computer network address is based on a non-standard top-level domain name, such as .scom, .sorg, .snet, .snet, .sedu, .smil and .sint.
Owner:VIRNETX
Agile network protocol for secure communications using secure domain names
InactiveUS20080040783A1Reduce network loadSmall sizeWeb data indexingDigital data processing detailsSecure communicationNetwork addressing
A secure domain name service for a computer network is disclosed that includes a portal connected to a computer network, such as the Internet, and a domain name database connected to the computer network through the portal. The portal authenticates a query for a secure computer network address, and the domain name database stores secure computer network addresses for the computer network. Each secure computer network address is based on a non-standard top-level domain name, such as .scom, .sorg, .snet, .snet, .sedu, .smil and .sint.
Owner:VIRNETX
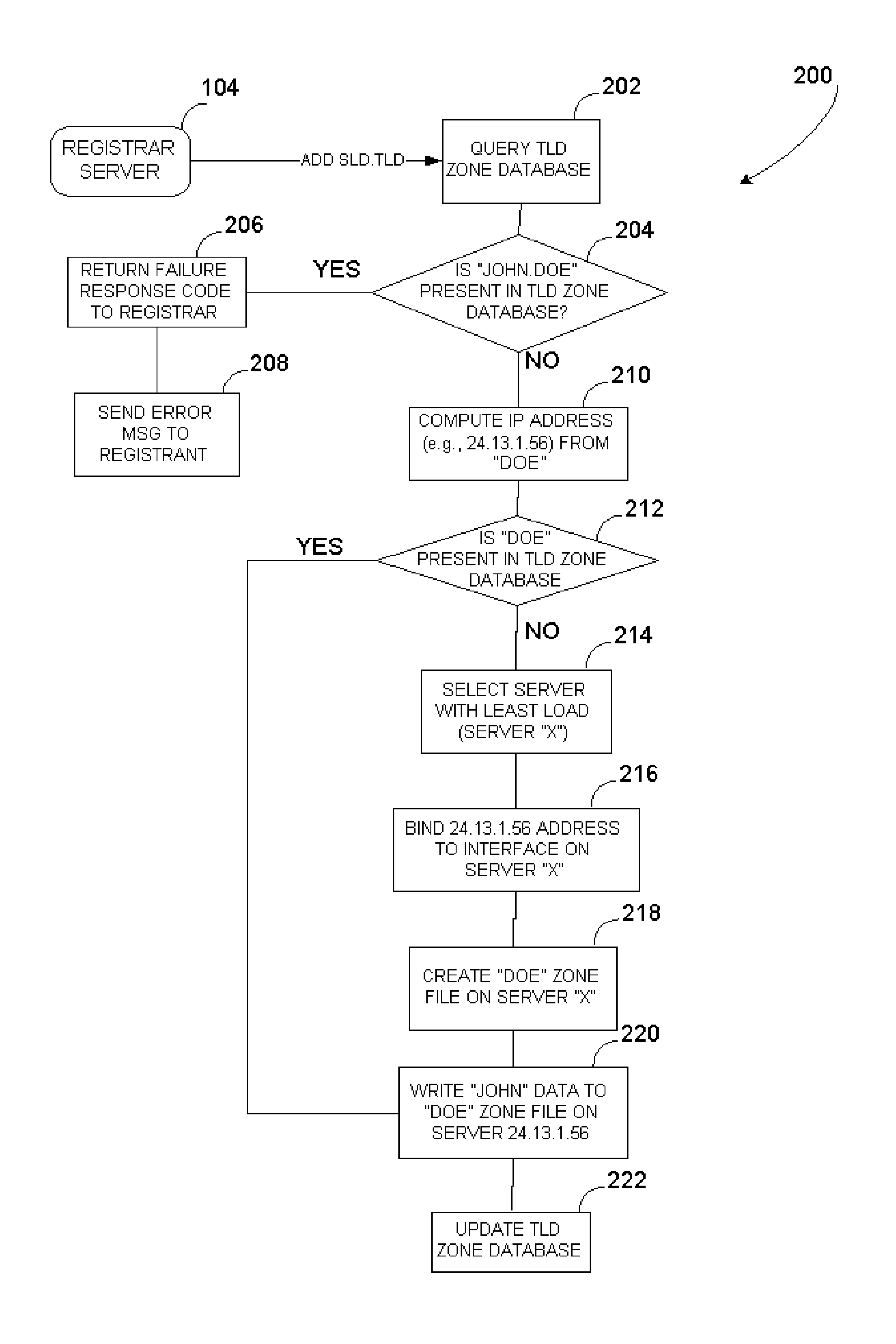
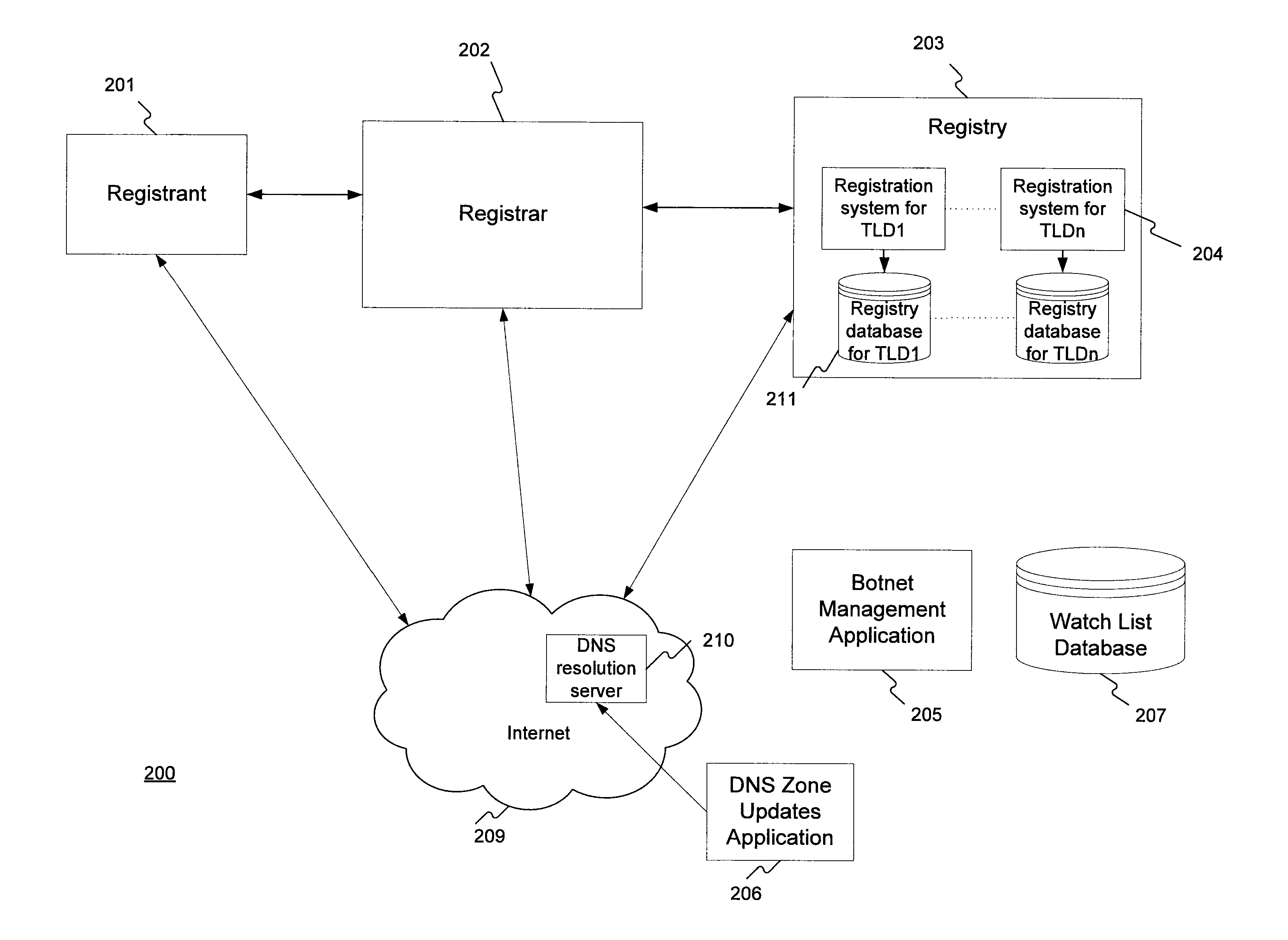
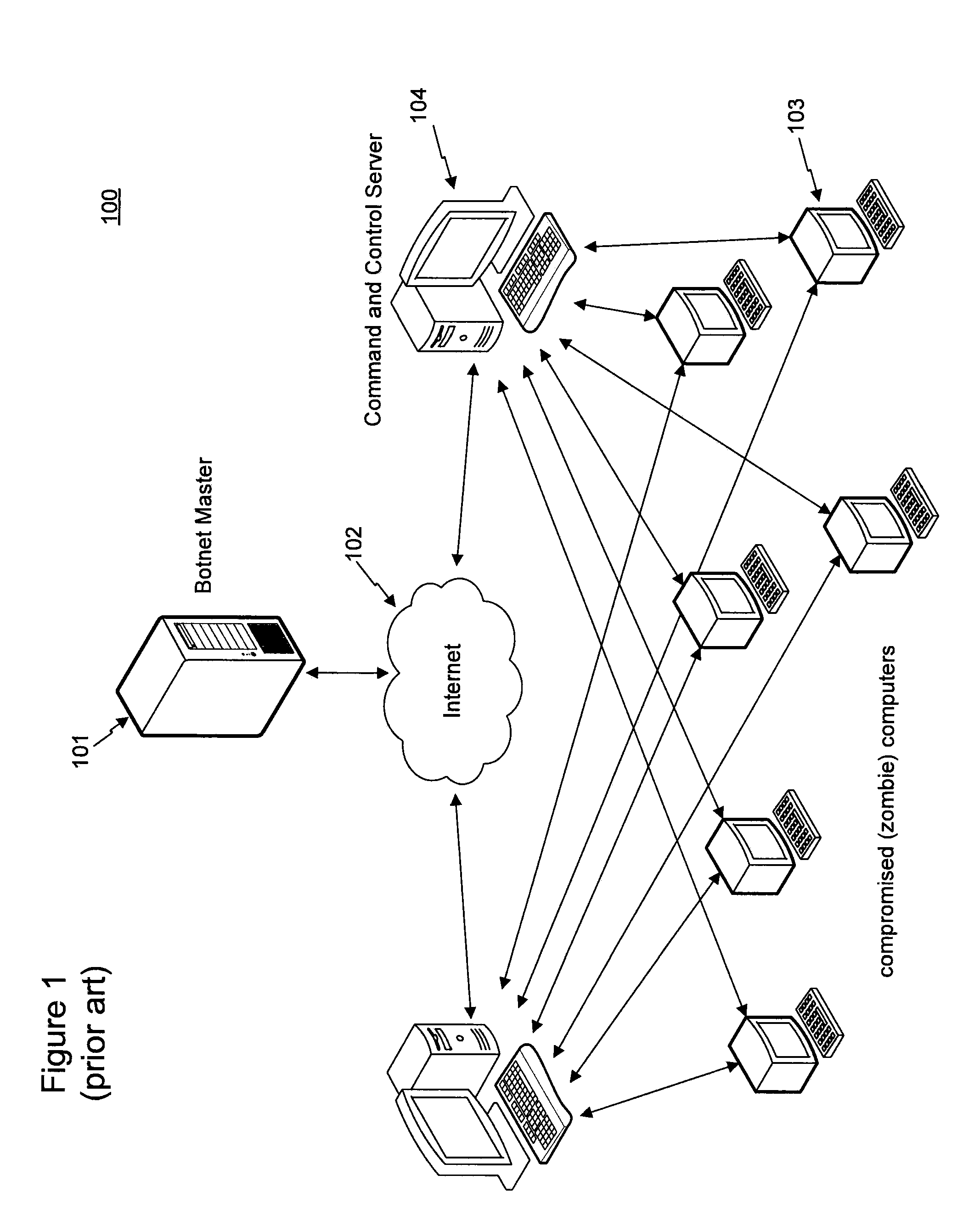
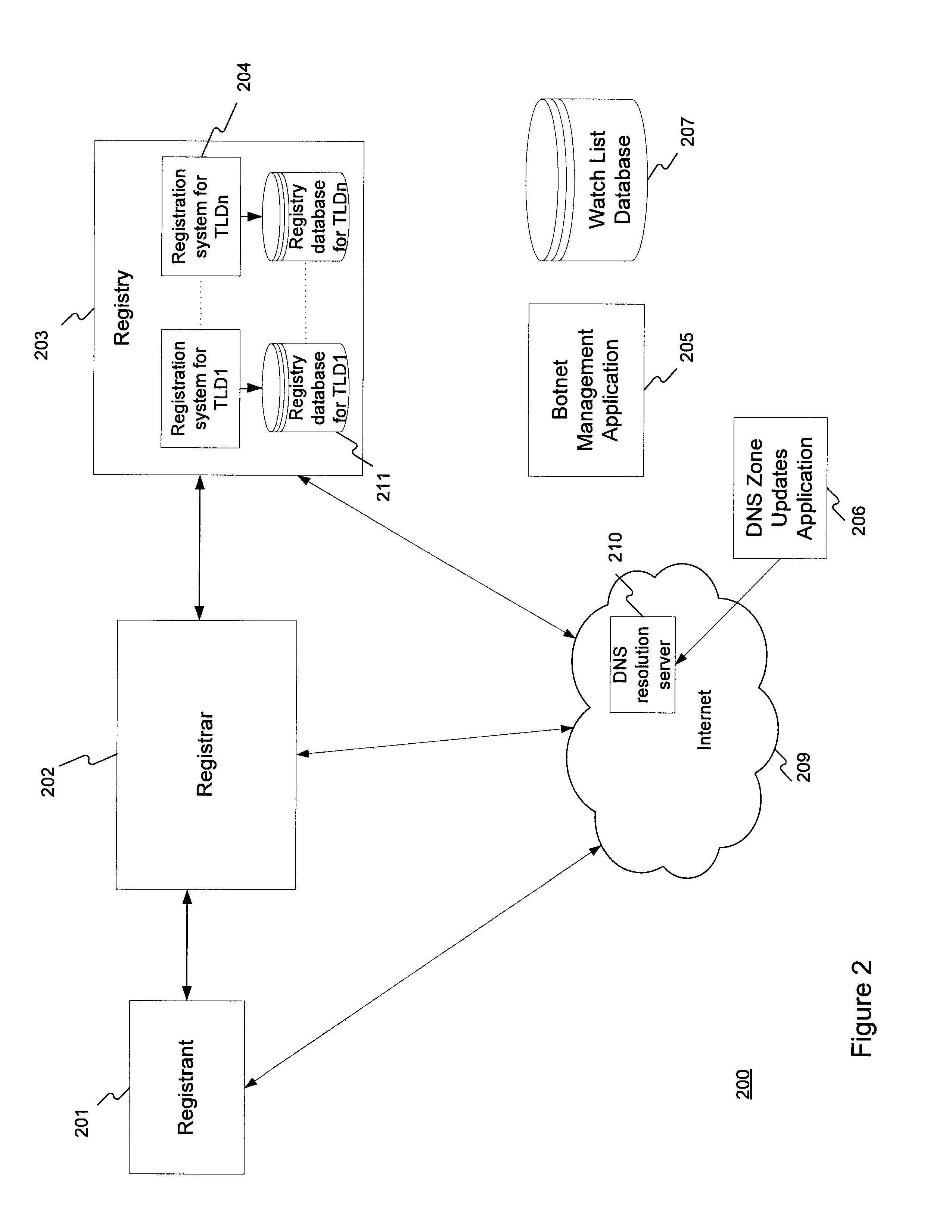
Method for administering a top-level domain
A method for administering a top-level domain by analyzing domain name registrations for requests for suspicious or malicious domain names. A request to register a domain name is received. The requested domain name's information may be stored in a registry database. The requested domain name may also be conditionally stored in the domain name system (DNS) zone. The requested domain name is compared to a list of botnet domain names stored in a watch list database. If the requested domain name corresponds to one of the botnet domain names, the requested domain name is prevented from being added to the DNS zone or is removed from the DNS zone, if it has already been stored there. The information regarding the requested domain name is stored in the registry database, even if the domain name does not ultimately stay in the DNS zone.
Owner:VERISIGN
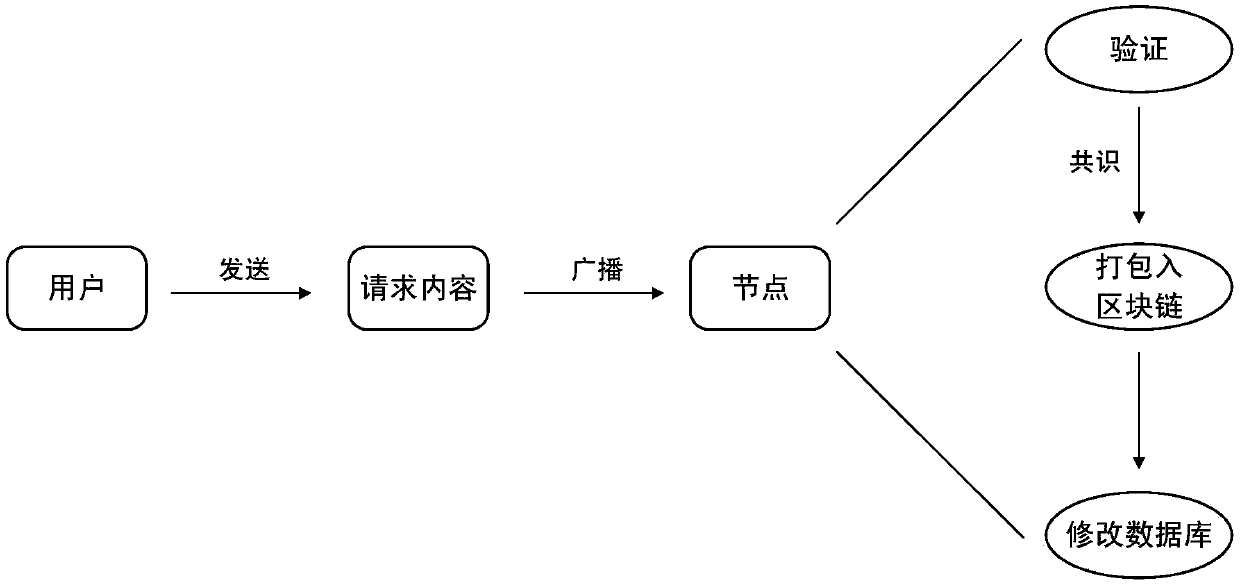
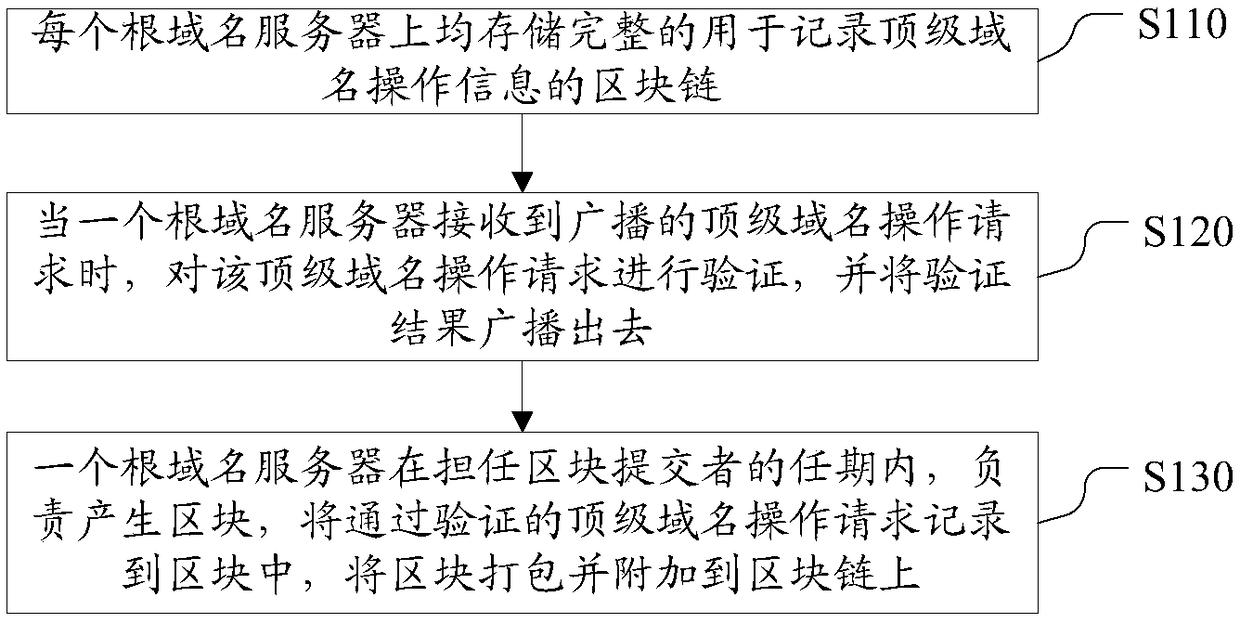
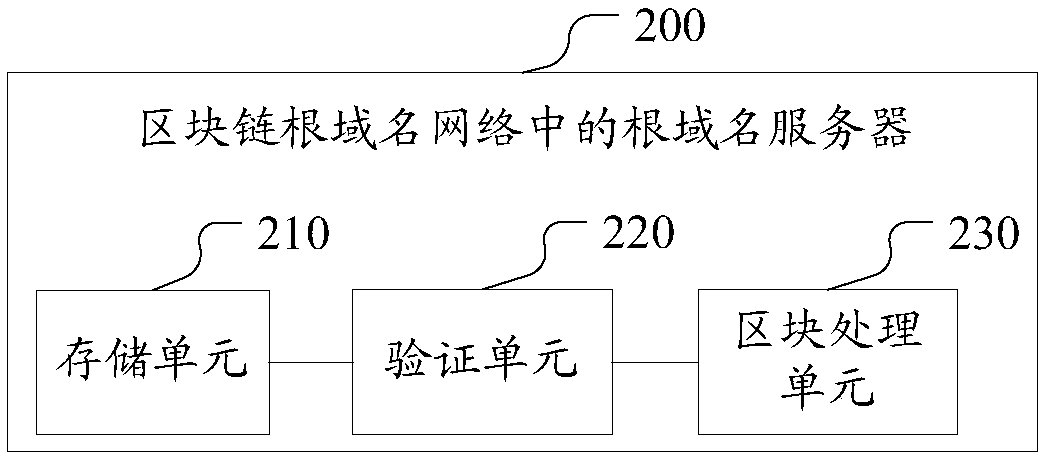
Method for realizing domain name resolution based on blockchain, server and system
The invention discloses a method for realizing domain name resolution based on a blockchain, a root name server in a blockchain root domain name network, a domain name resolution system, a root name server and a computer readable storage medium. A plurality of root name servers form the blockchain root domain name network based on the blockchain technology, the root name server performs the following steps: a complete blockchain for recording top level domain operation information is stored on each root name server; when one root name server receives a broadcasted top level domain operation request, the root name server verifies the top level domain operation request and broadcasts a verification result; and one root name server is responsible for generating a block during the term of a block submitter, recording the verified top level domain operation request in the block, packaging the block and adding the block to the blockchain. Therefore, by adoption of the technical scheme, thesecurity of the domain name resolution is improved; and the appearance of a super administrator is avoided.
Owner:BEIJING QIHOO TECH CO LTD
Internet domain name registration system
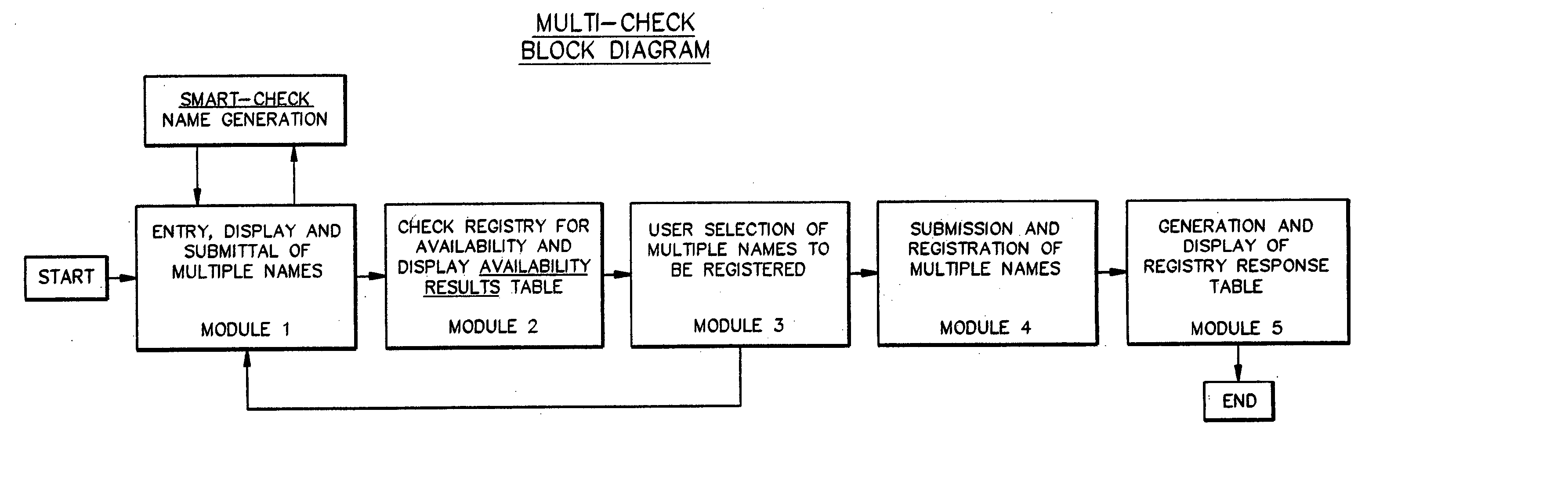
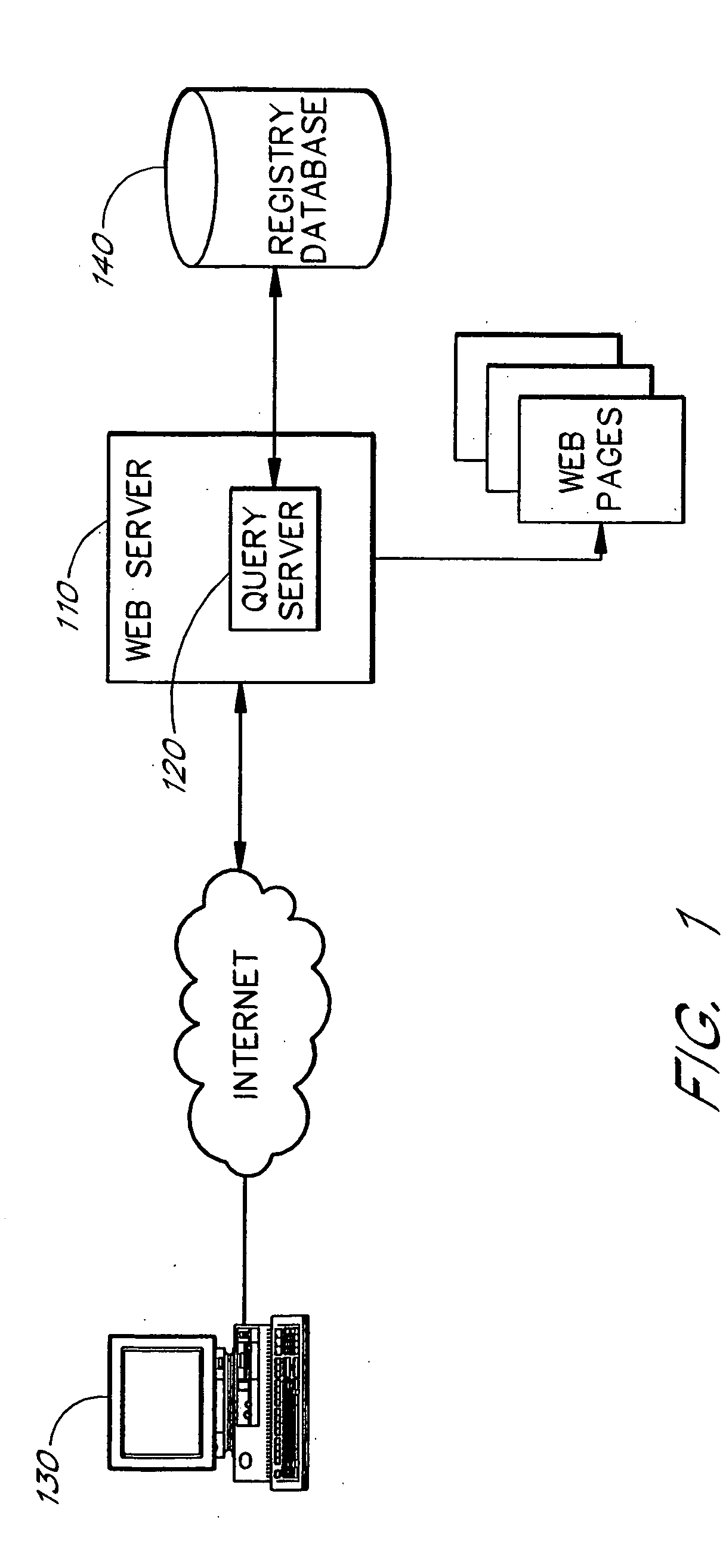
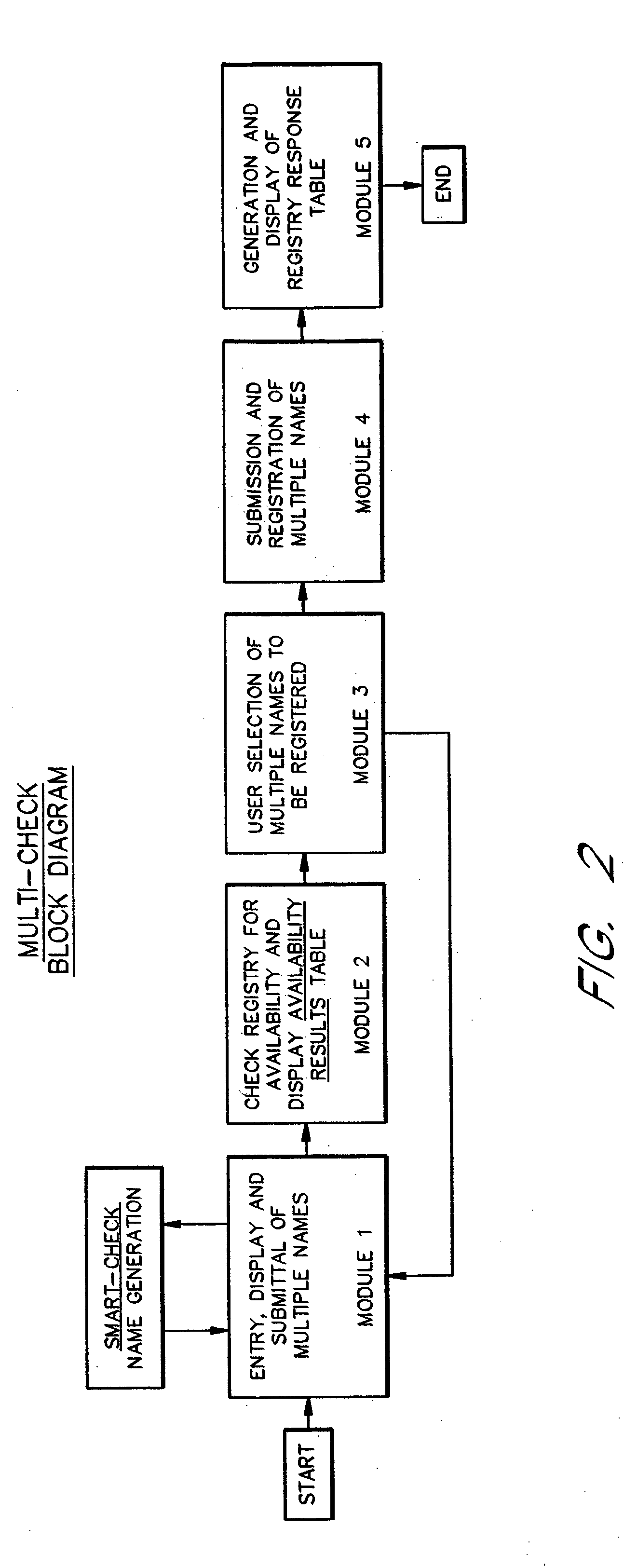
InactiveUS20050256853A1Convenient queryReduce amountData processing applicationsDigital data processing detailsRegistry dataResponse table
A domain name registration system includes a user interface through which a user can submit multiple names to a query server to determine the availability of the names for domain name registration. After the query results are returned for each of the multiple names submitted, the user is presented with a table listing the availability of each name in combination with multiple Top-Level Domain (TLD) extensions. The user is able to select one or more names from the table for registration in the registry database. After the query server has attempted to register each of the selected names, the user is presented with a Registry Response Table indicating which of the selected names were successfully registered as domain names. Thus, the system and method increases the speed and productivity of querying and updating a domain name registry or other database.
Owner:MULTICHECK SYST
Network identification root zone data management method and system based on blockchain technology
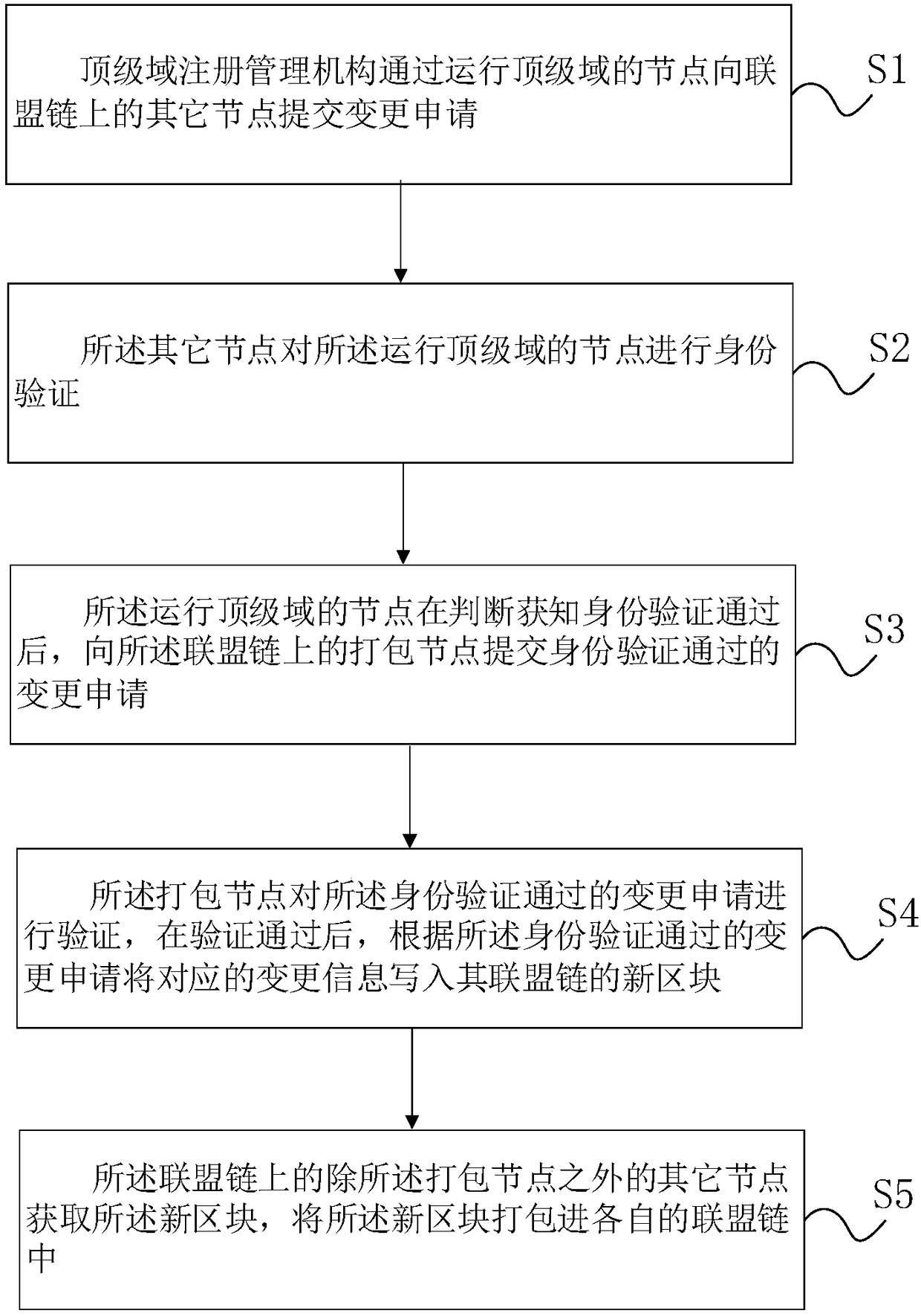
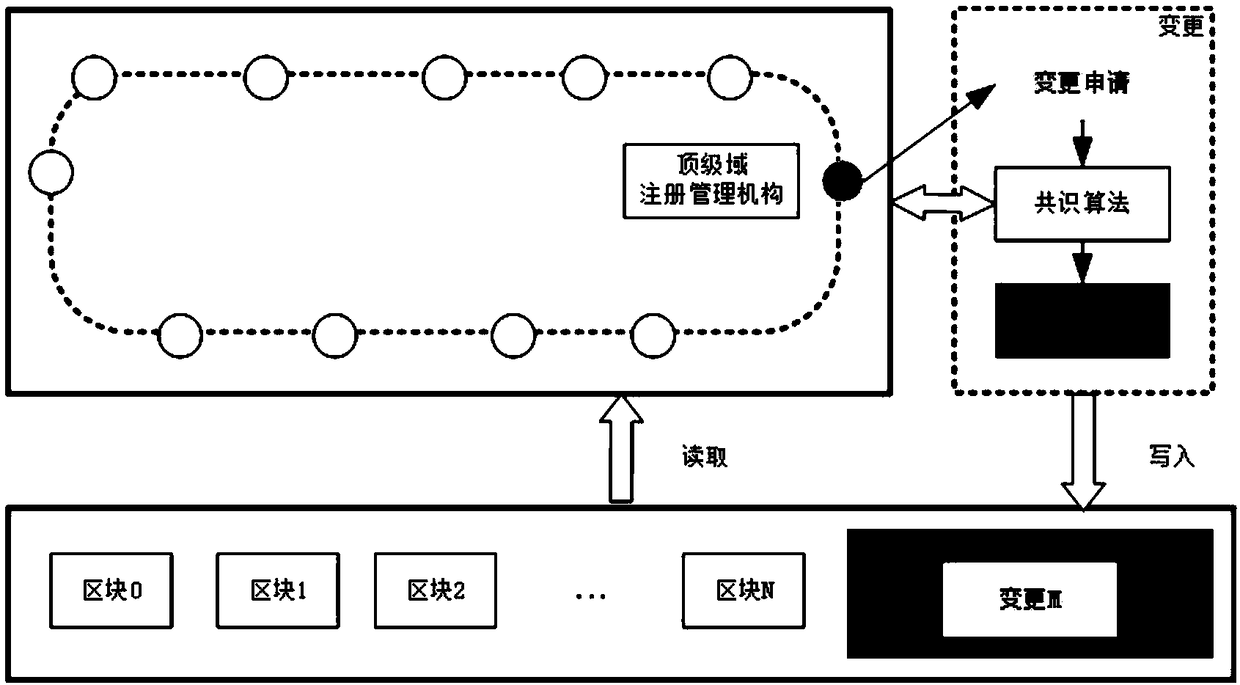
InactiveCN108389045AEnhance management rightsRealize common maintenancePayment protocolsSystems managementData management
The embodiment of the invention discloses a network identification root zone data management method and system based on a blockchain technology. On the basis of an alliance blockchain technology, thejoint maintenance of root zone data management is realized, and the partial decentration of root system management is realized. The method comprises the following steps that: a top level domain registration management mechanism submits a change application to other nodes on an alliance chain through a node which operates the top level domain; other nodes carry out identity verification on the nodewhich operates the top level domain; after the node which operates the top level domain judges to obtain a situation that the identity verification is qualified, the change application of which the identity verification is qualified is submitted to a packaging node on the alliance chain; the packaging node verifies the change application which passes the identity verification, and after verification is qualified, according to the change application which passes the identity verification, the corresponding change information is written into the new block of the alliance chain; and other nodesexcept the packaging node on the alliance chain obtains the new block, and the new block is packaged into the respective alliance chain.
Owner:CHINA ACADEMY OF INFORMATION & COMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com