WEB single sign-on method completely transparent to user and application
A single sign-on, fully transparent technology, applied in the field of network security, can solve the problems of user impact, inability to support browsers and operating systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
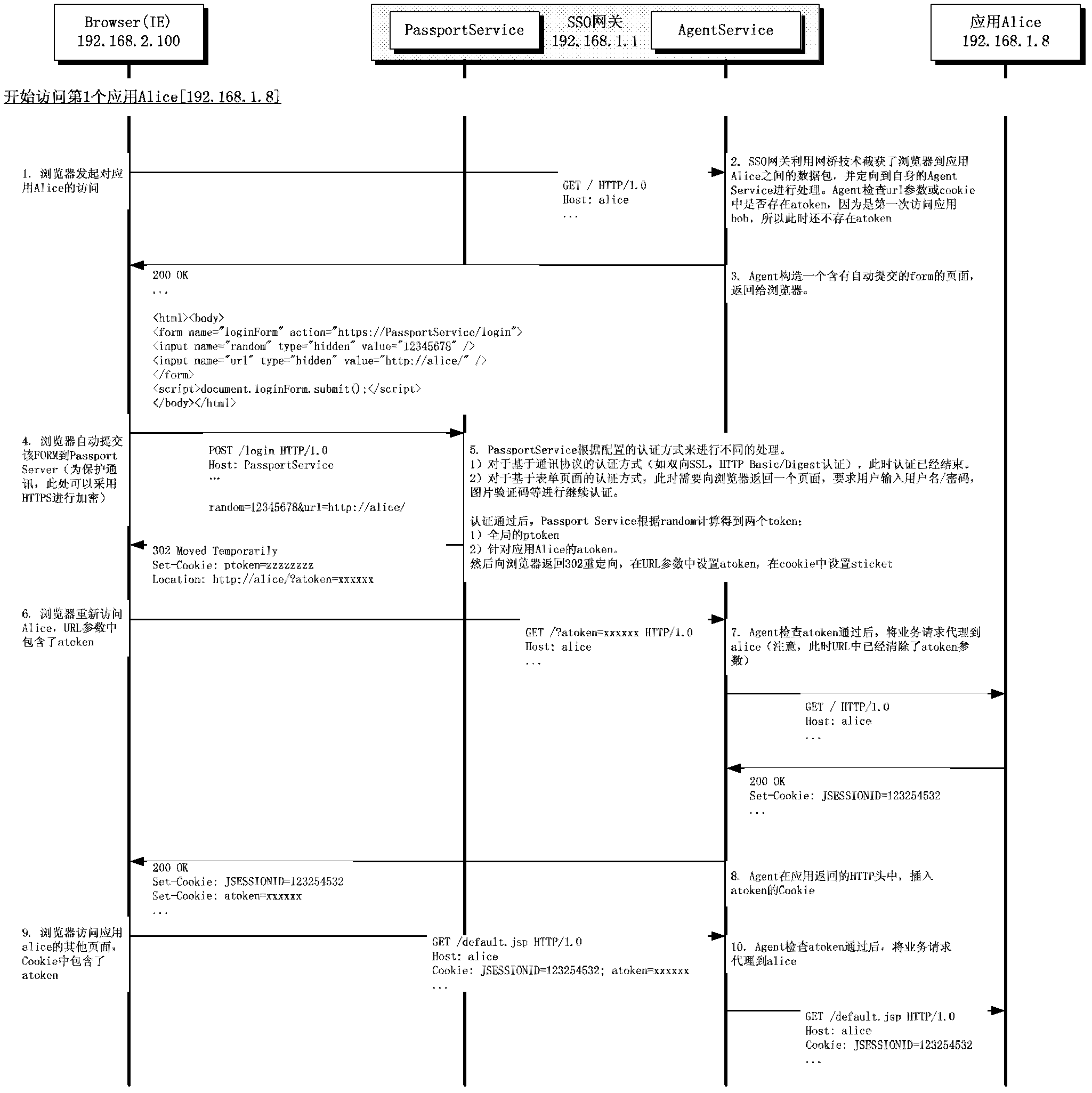
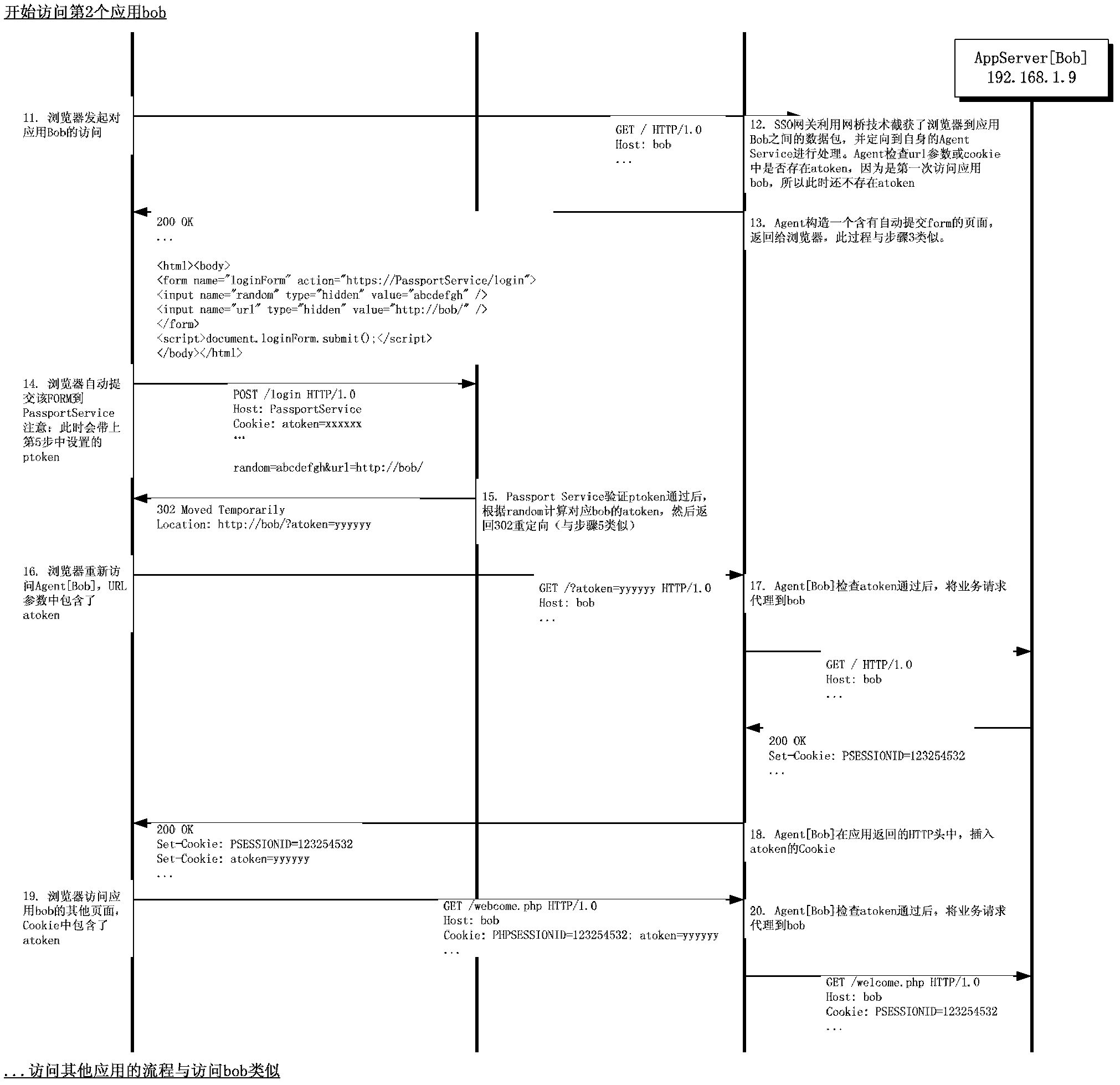
[0040] In order to realize SSO that is completely transparent to users and applications, and fully support all browsers and operating systems, the present invention designs a unique technical solution, the main principles of which are as follows:
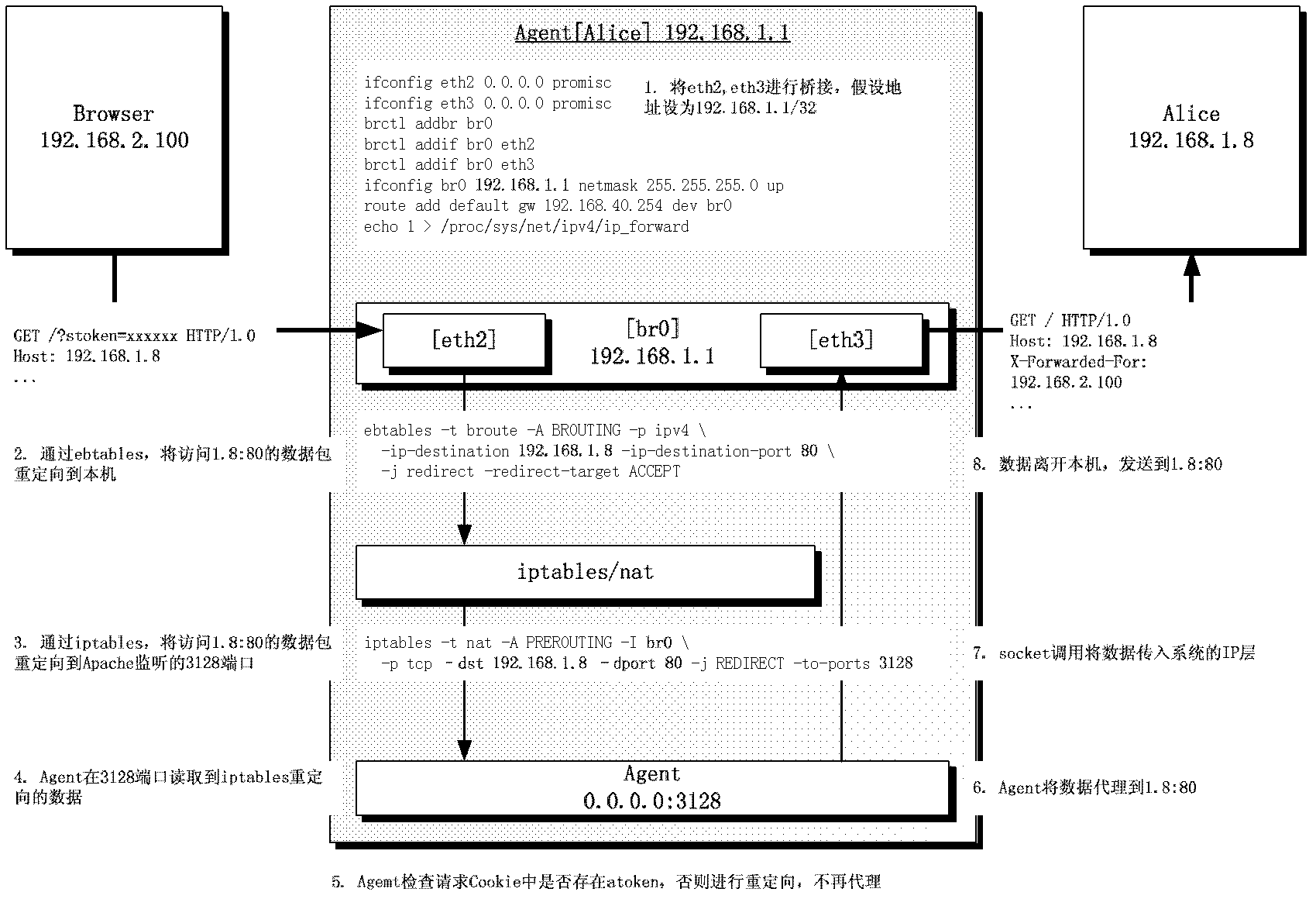
[0041] (1) Intercept HTTP packets between users (browsers) and WEB applications through transparent bridge technology;
[0042] (2) Use page redirection technology to redirect users to the SSO server when they visit for the first time;
[0043] (3) After the SSO service completes the authentication, redirect the browser back to the WEB application, and set two security tokens, one ptoken for the SSO authentication service itself and the other atoken for the application;
[0044] (4) When the browser ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com