Patents
Literature
322 results about "Name space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
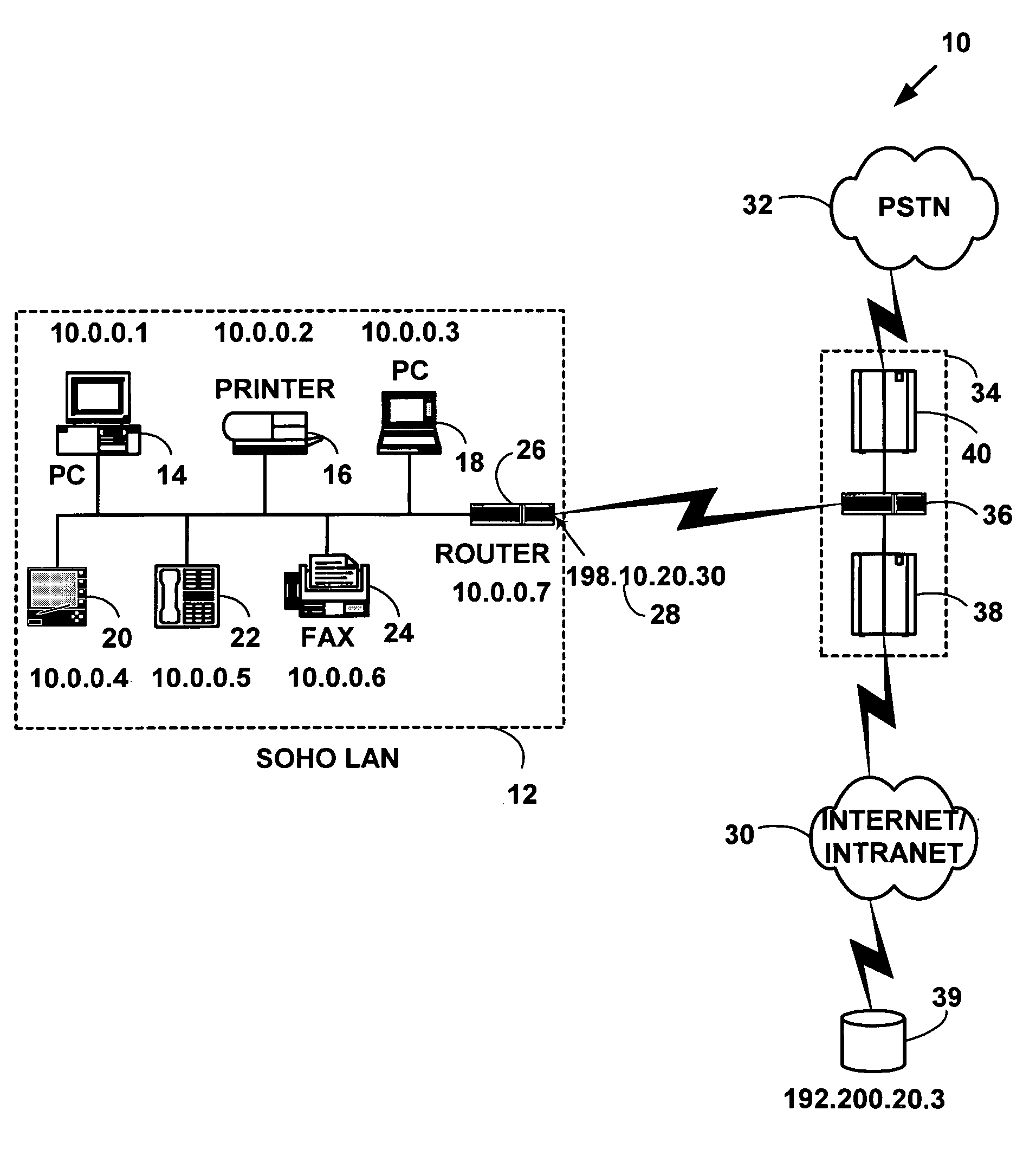
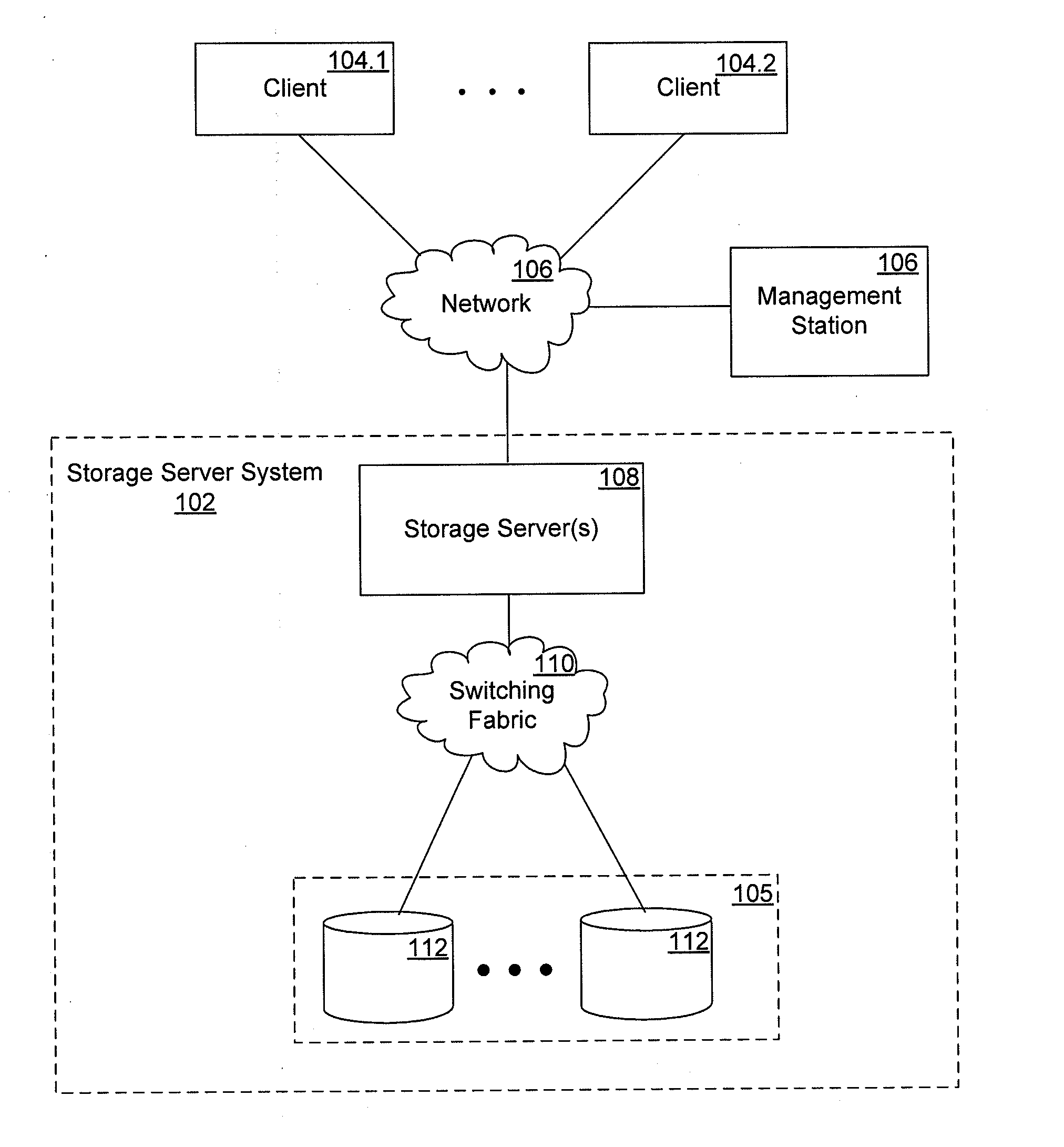
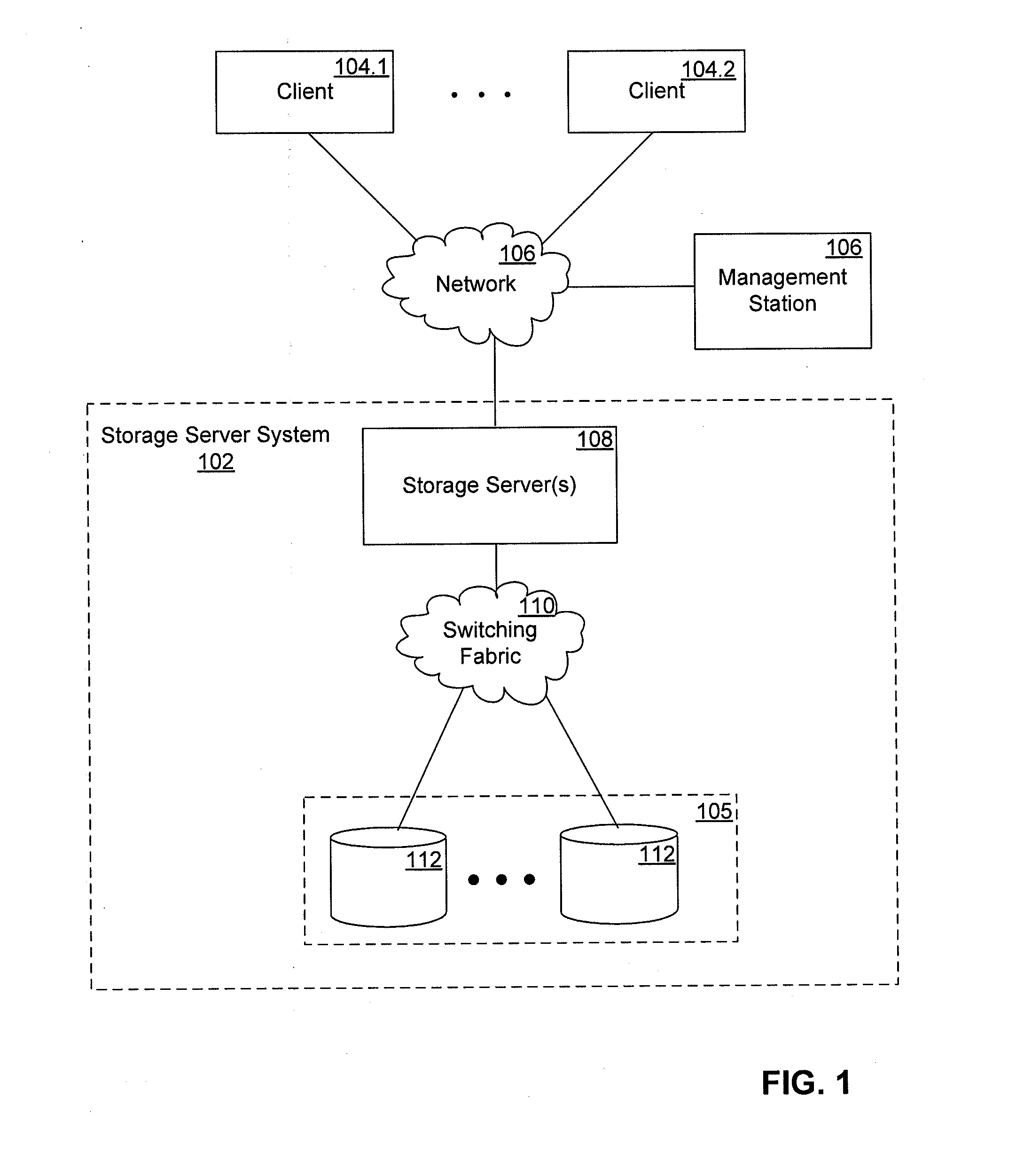
Method and system for distributed network address translation with network security features
InactiveUS7032242B1Digital data processing detailsUser identity/authority verificationSecurity associationIp address
A method and system for distributed network address translation with security features. The method and system allow Internet Protocol security protocol (“IPsec”) to be used with distributed network address translation. The distributed network address translation is accomplished with IPsec by mapping a local Internet Protocol (“IP”) address of a given local network device and a IPsec Security Parameter Index (“SPI”) associated with an inbound IPsec Security Association (“SA”) that terminates at the local network device. A router allocates locally unique security values that are used as the IPsec SPIs. A router used for distributed network address translation is used as a local certificate authority that may vouch for identities of local network devices, allowing local network devices to bind a public key to a security name space that combines a global IP address for the router with a set of locally unique port numbers used for distributed network address translation. The router issues security certificates and may itself be authenticated by a higher certificate authority. Using a security certificate, a local network device may initiate and be a termination point of an IPsec security association to virtually any other network device on an IP network like the Internet or an intranet. The method and system may also allow distributed network address translation with security features to be used with Mobile IP or other protocols in the Internet Protocol suite.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
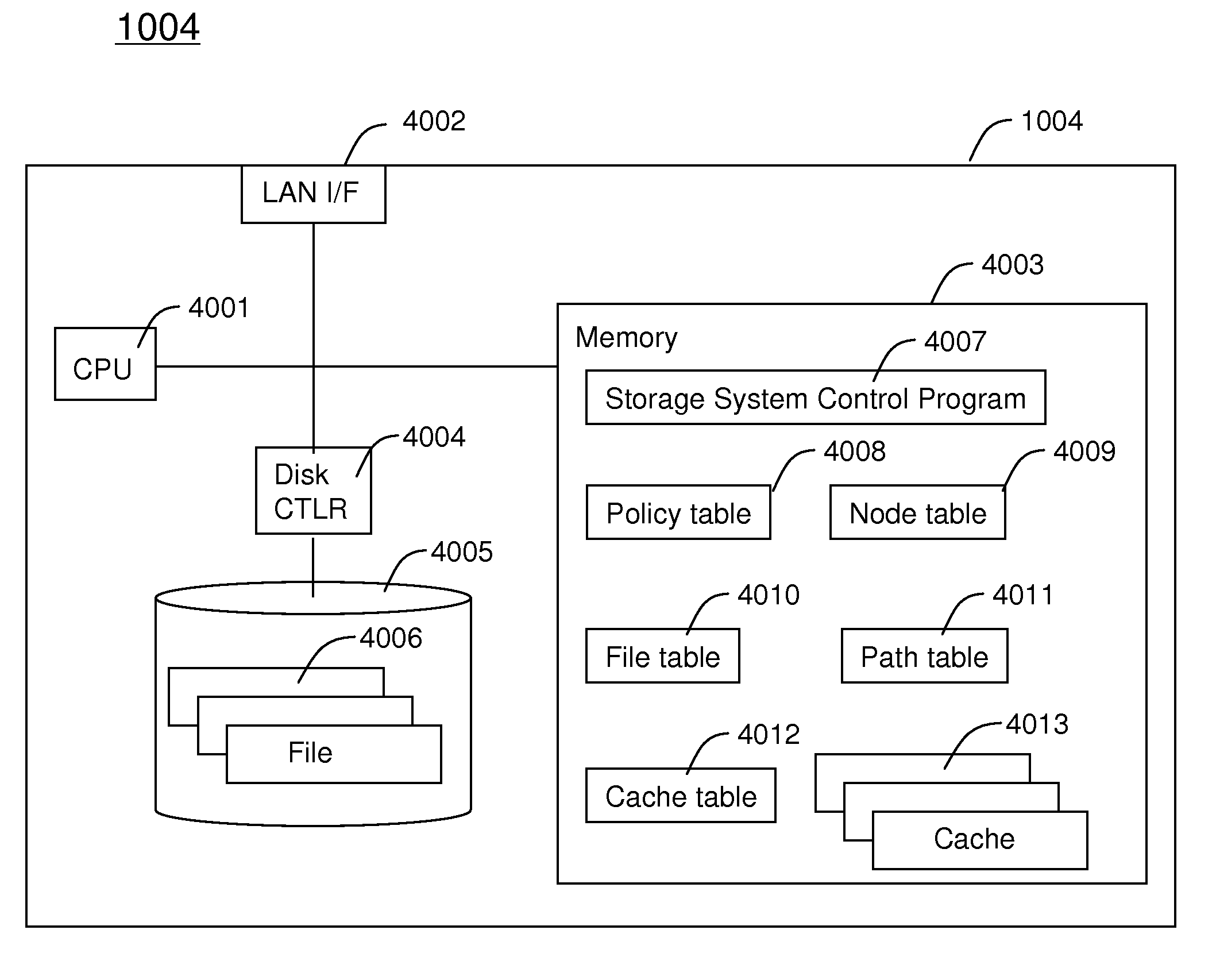
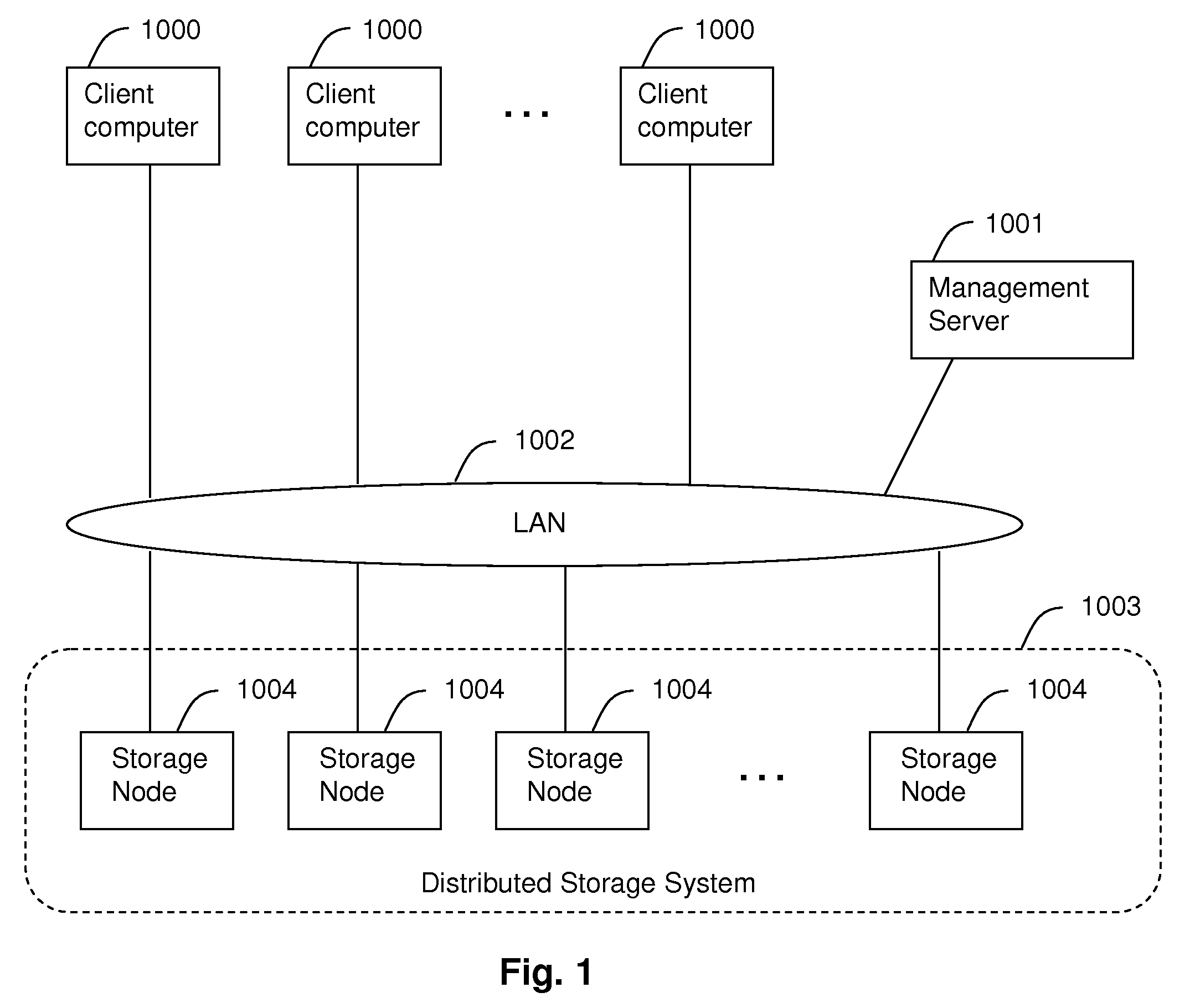
Method and apparatus for improving file access performance of distributed storage system
InactiveUS8086634B2Improve performanceReduce overheadDigital data information retrievalDigital data processing detailsNetwork connectivityDistributed memory systems
Embodiments of the invention provide methods and apparatus for improving the performance of file transfer to a client from a distributed storage system which provides single name space to clients. In one embodiment, a system for providing access to files in a distributed storage system comprises a plurality of storage nodes and at least one computer device connected via a network. Each storage node is configured, upon receiving a file access request for a file from one of the at least one computer device as a receiver storage node, to determine whether or not to inform the computer device making the file access request to redirect the file access request to an owner storage node of the file according to a preset policy. The preset policy defines conditions for whether to redirect the file access request based on at least one of file type or file size of the file.
Owner:HITACHI LTD
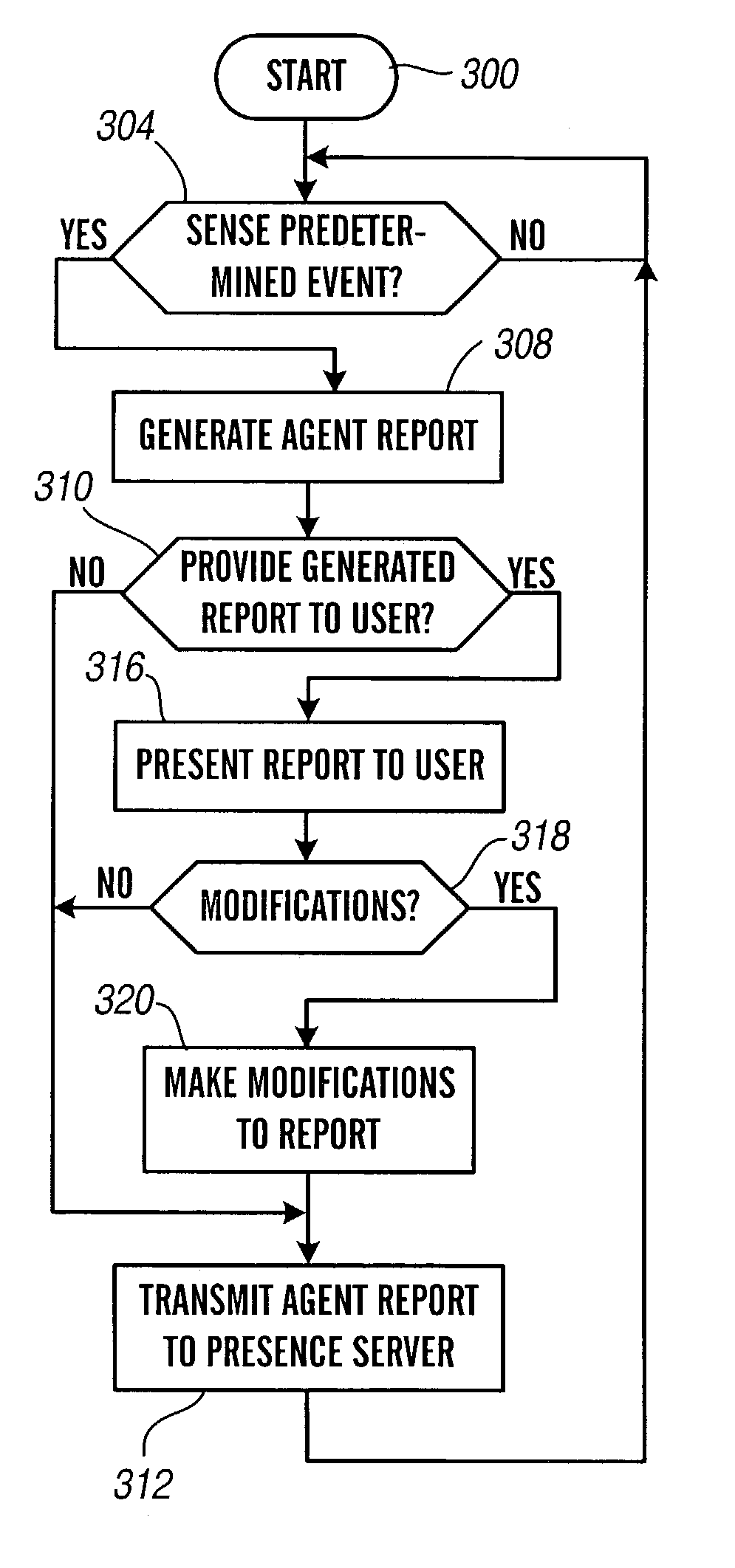
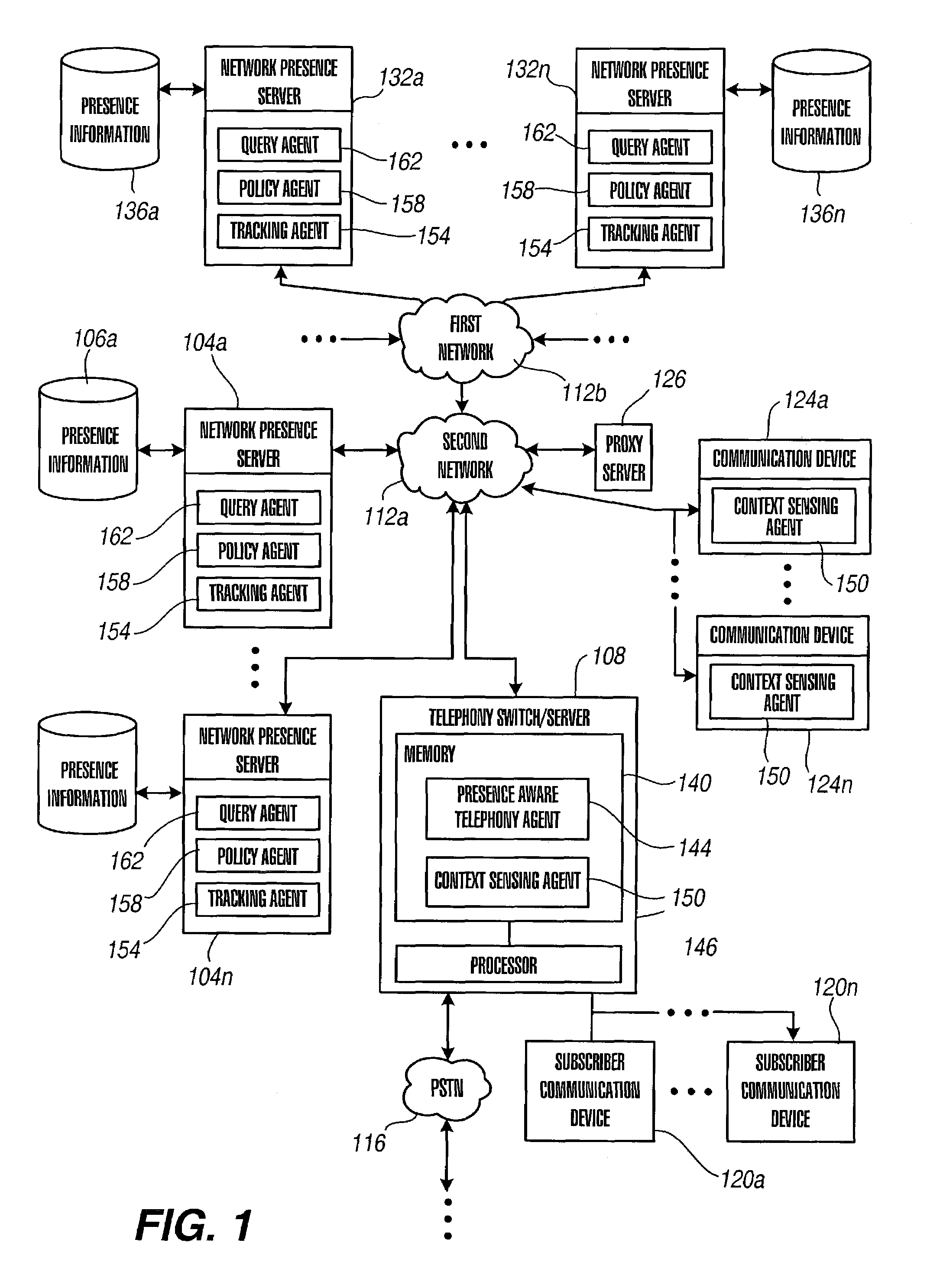
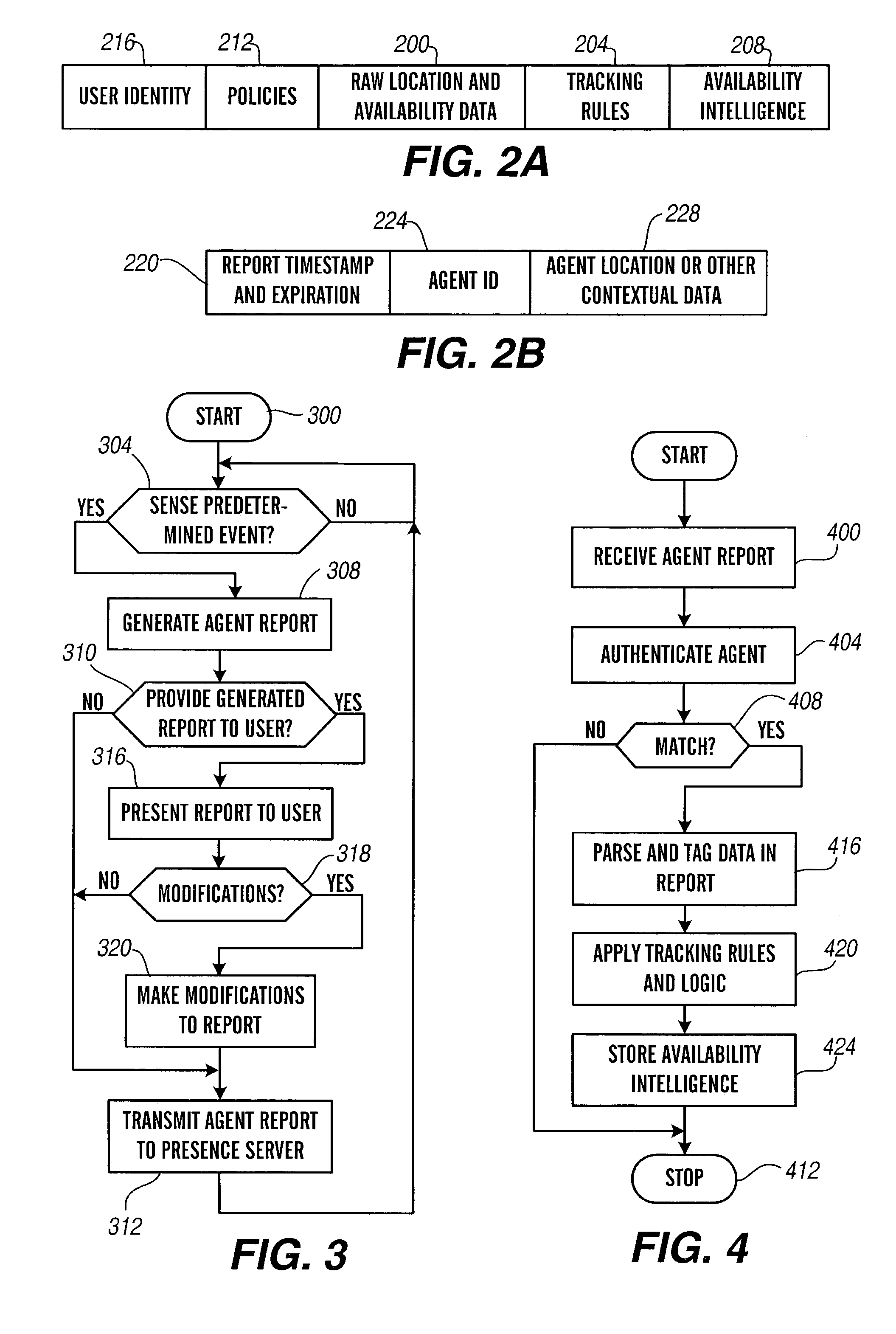
Presence tracking and name space interconnection techniques
ActiveUS7536437B2Multiple digital computer combinationsAutomatic exchangesContext sensingInterconnection
Owner:AVAYA INC
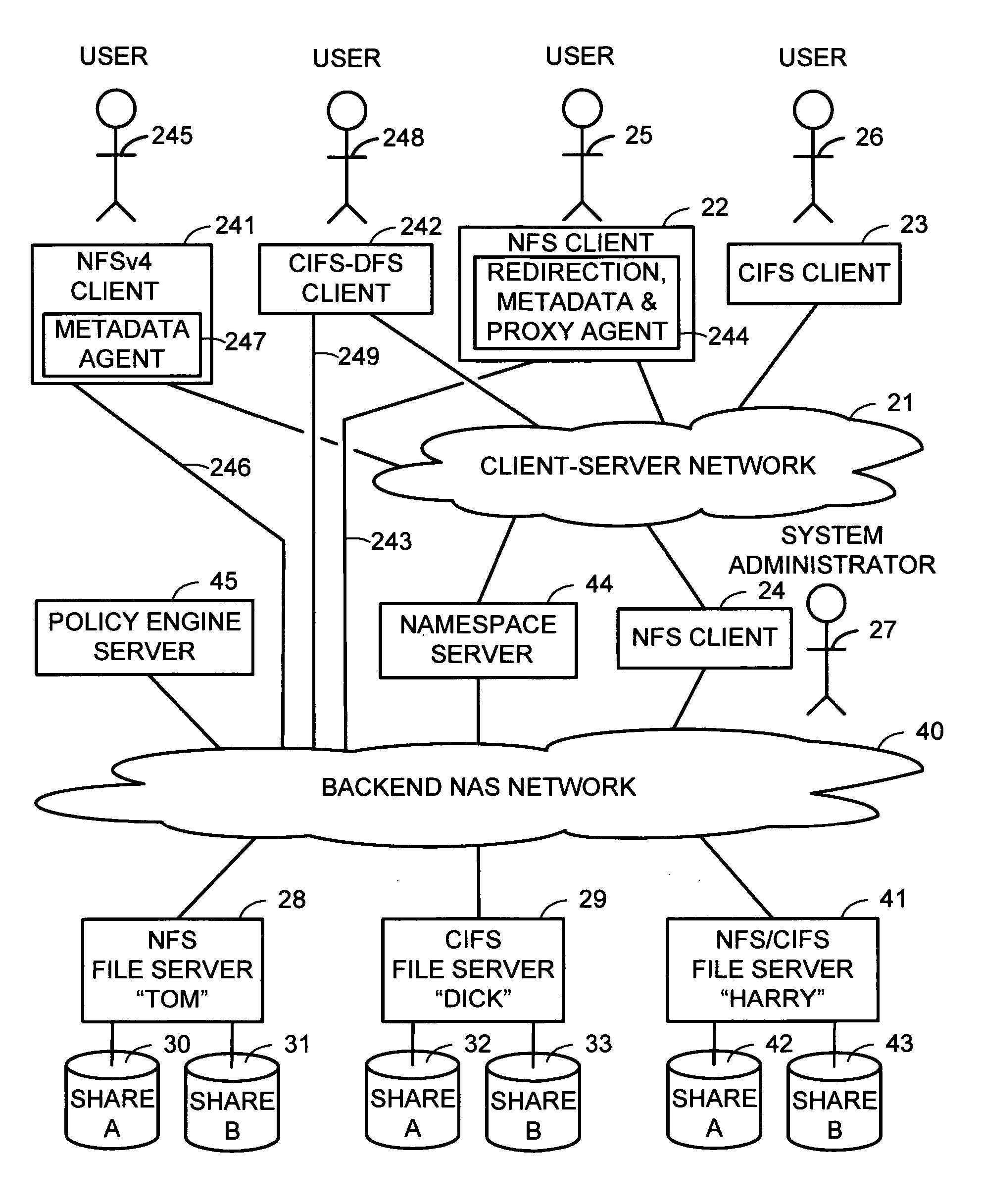
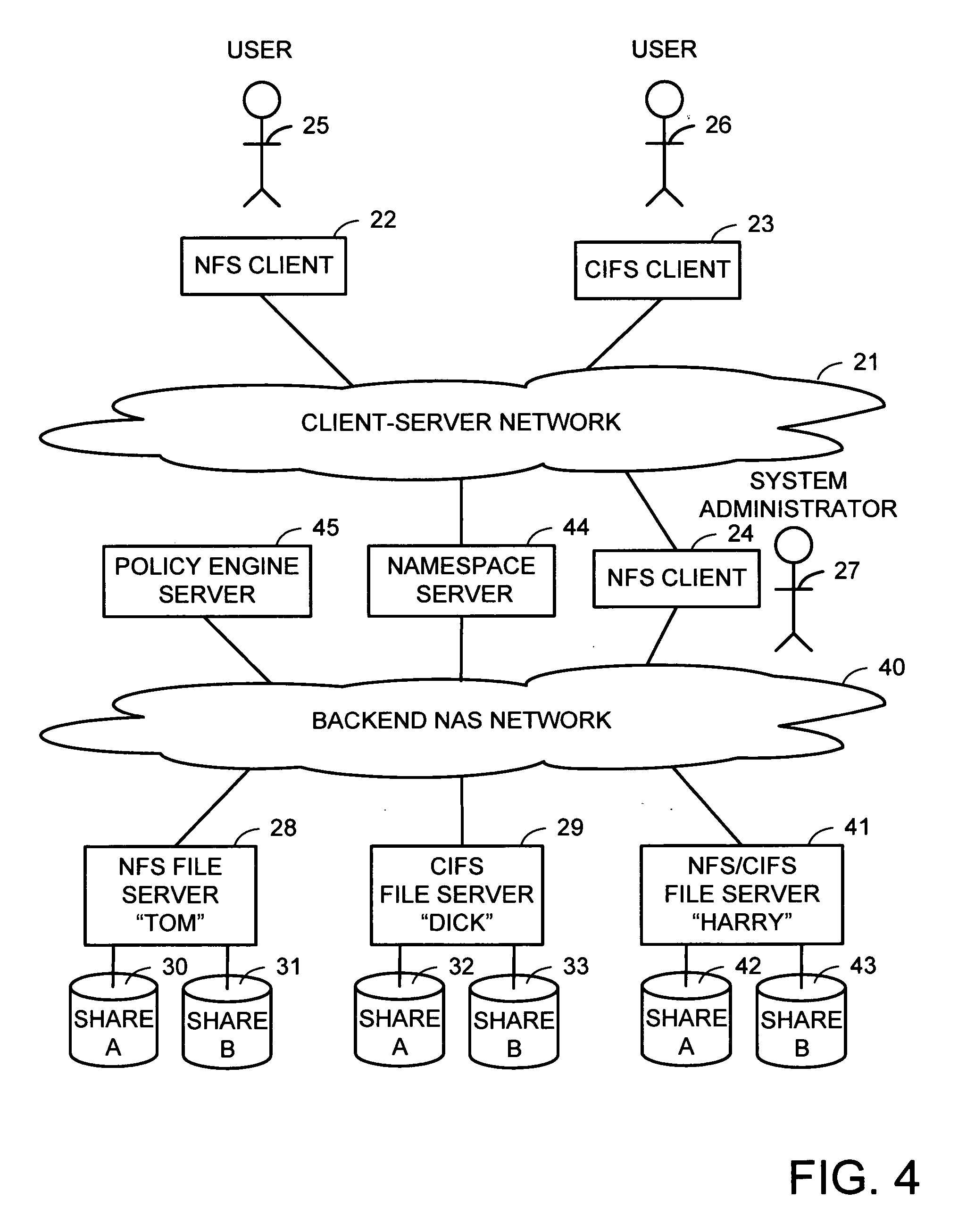
Namespace server using referral protocols
A namespace server translates client requests for access to files referenced by pathnames in a client-server namespace into requests for access to files referenced by pathnames in a NAS network namespace. The namespace server also translates between different file access protocols. If a client supports redirection and is requesting access to a file in a file server that supports the client's redirection, then the namespace server may redirect the client to the NAS network pathname of the file. Otherwise, the namespace server forwards a translated client request to the file server, and returns a reply from the file server to the client. A file server may redirect a redirection-capable client's access back to the namespace server for access to a share, directory, or file that is offline for migration, or for a deletion or name change that would require a change in translation information in the namespace server.
Owner:EMC CORP
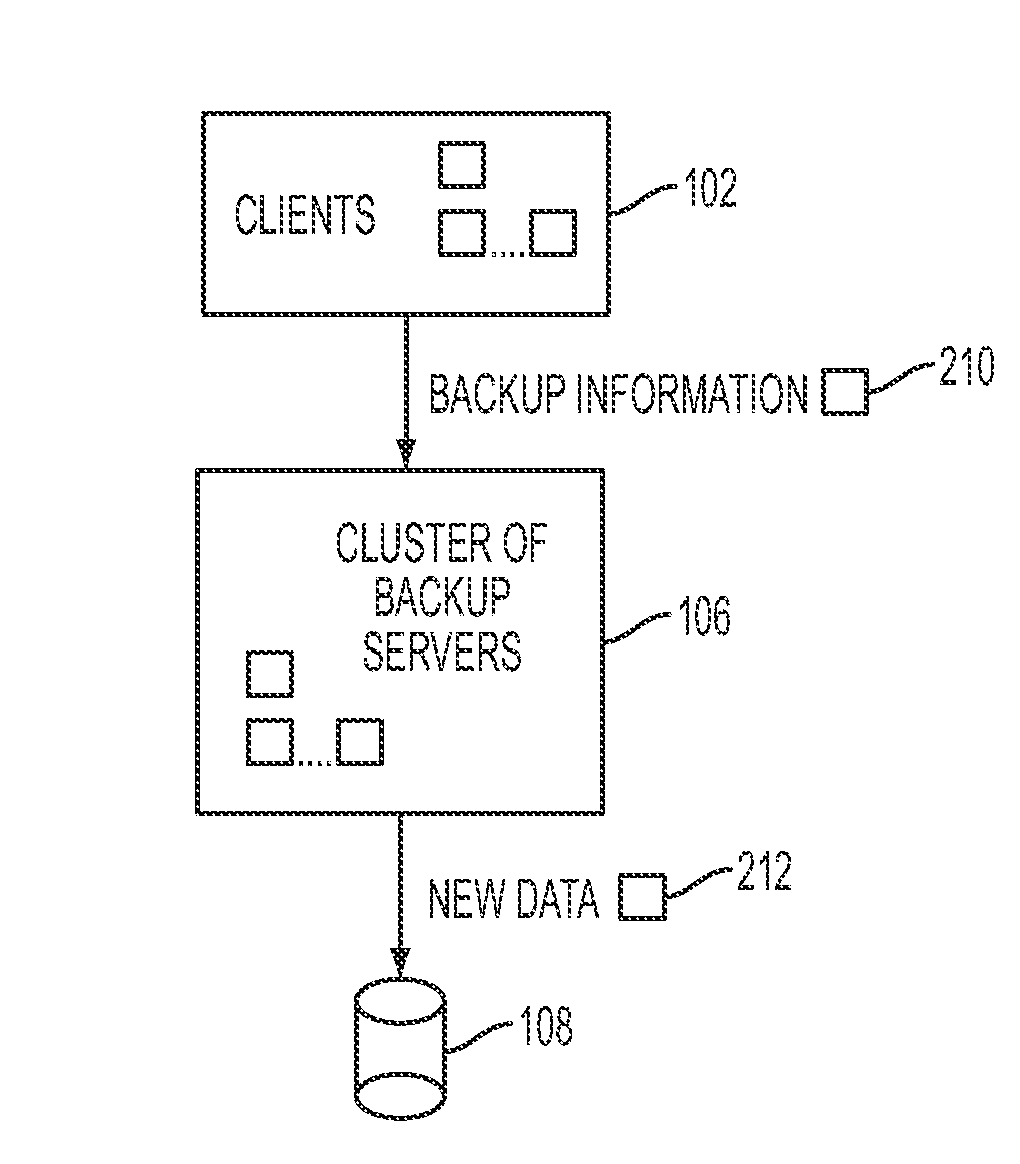
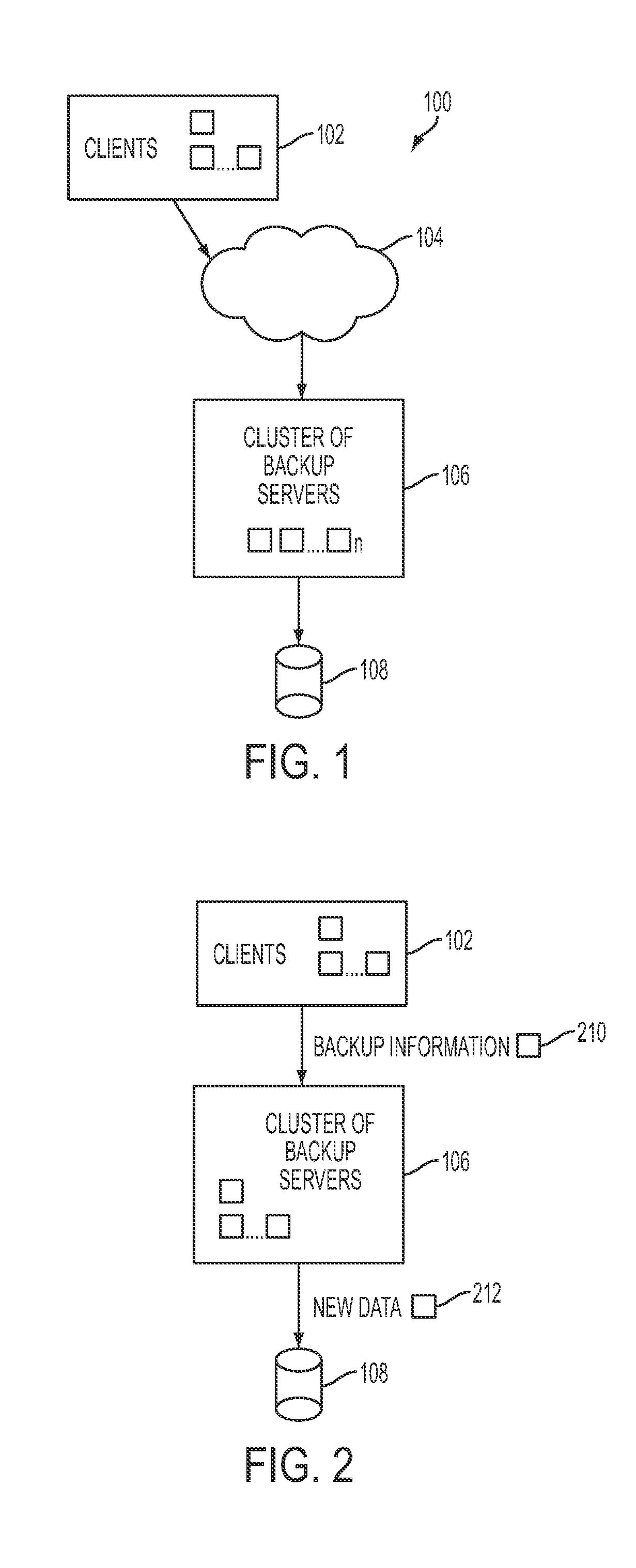
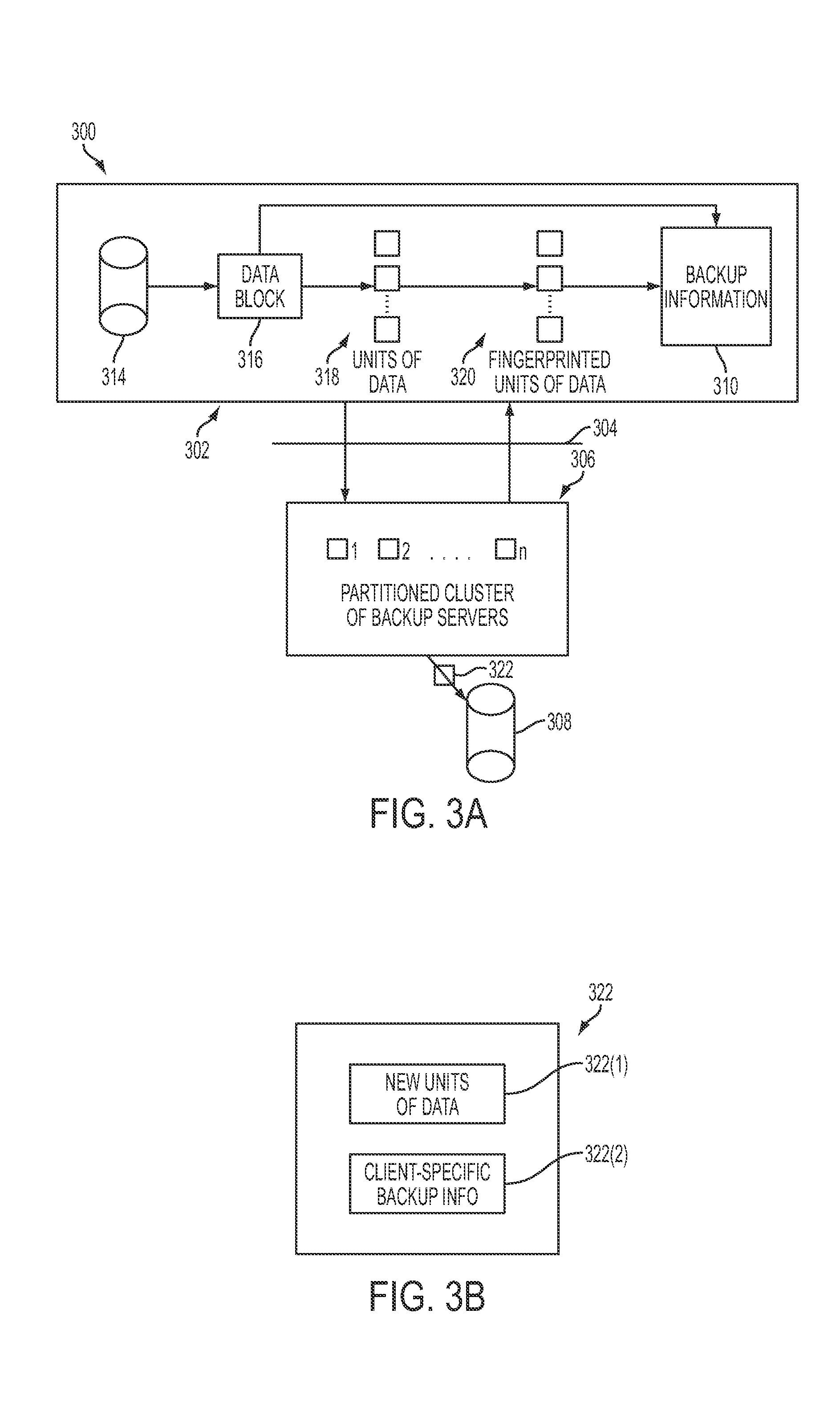
Remote backup and restore
ActiveUS20100106691A1Memory loss protectionDigital data processing detailsNamespaceData deduplication
In one embodiment of the present invention, a data-backup method includes partitioning a fingerprint namespace among a cluster of backup servers, the fingerprint namespace comprising fingerprints for representing units of data, each backup server of the cluster of backup servers managing units of data having fingerprints corresponding to an assigned partition of the fingerprint namespace. The method further includes receiving backup information from a client computing device for a block of data comprising units of data, the backup information including at least a fingerprint for each of the units of data and client-specific backup information. In addition, the method includes, utilizing the fingerprint for each of the units of data, deduplicating the units of data in parallel at the cluster of backup servers in accordance with the partitioning step, the deduplicating step comprising identifying ones of the units data already stored by the cluster of backup servers.
Owner:QUEST SOFTWARE INC
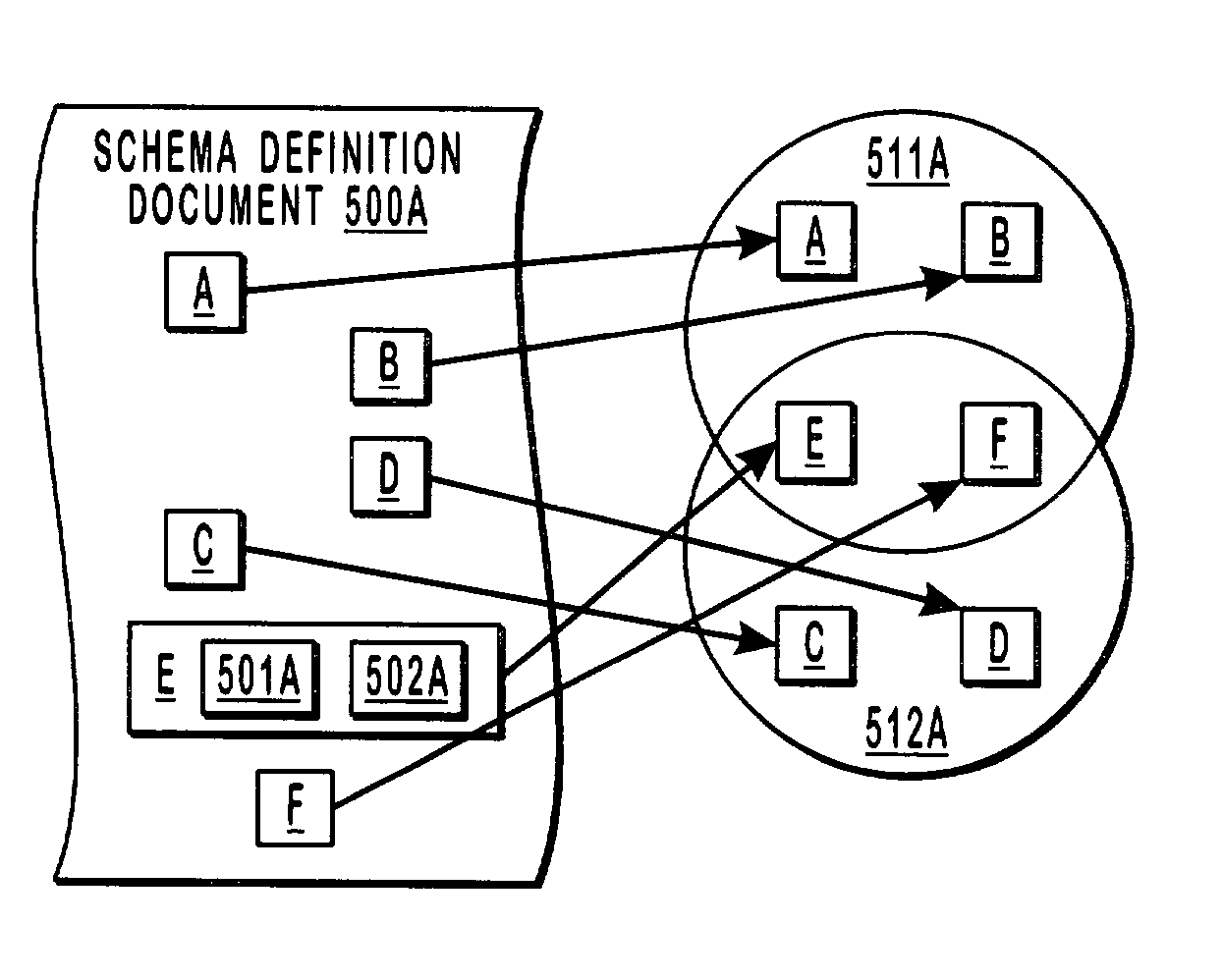
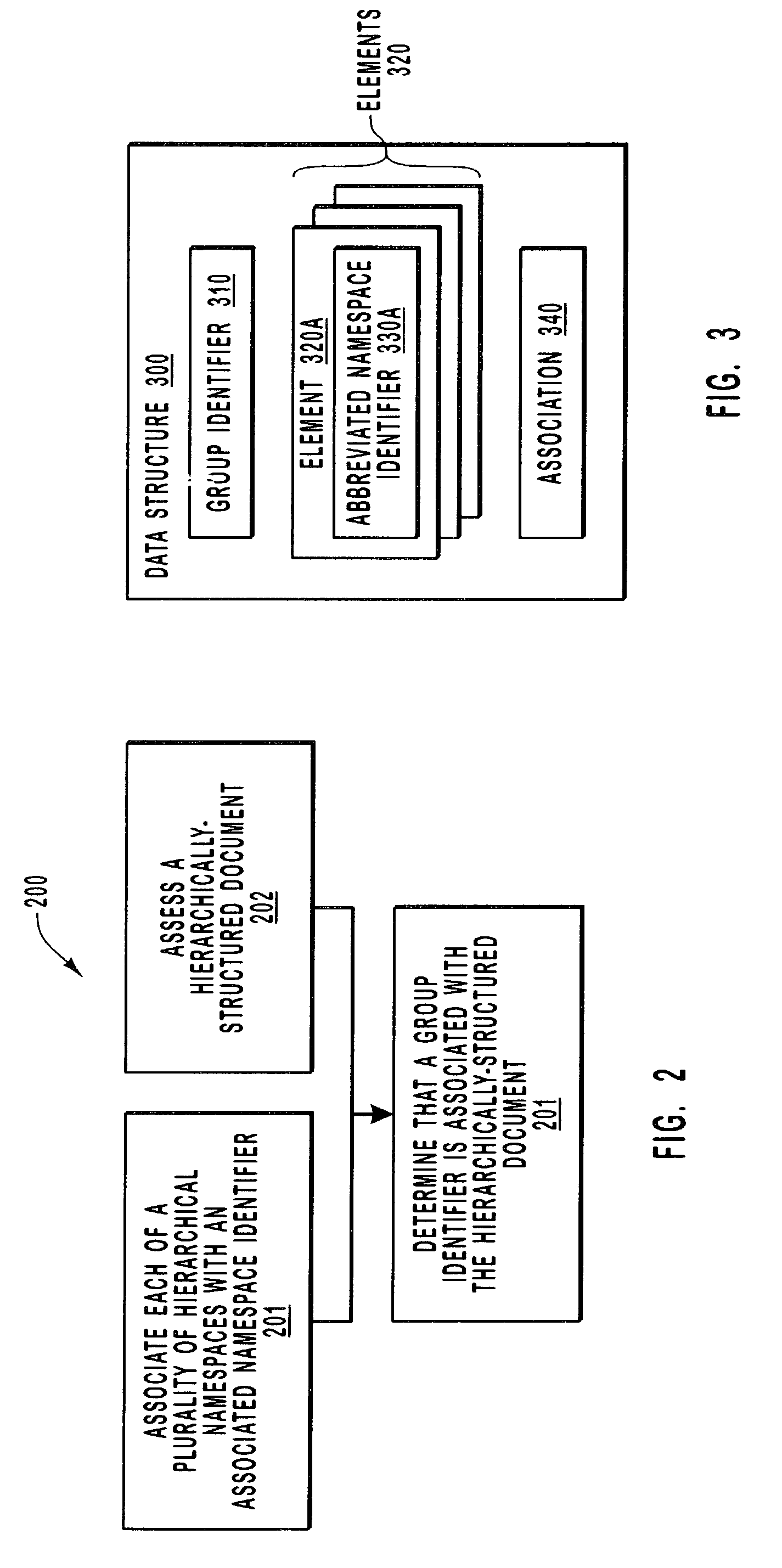
Grouping and nesting hierarchical namespaces
InactiveUS6993714B2Reduce sizeDigital data information retrievalDigital computer detailsXML namespaceIdenticon
A group identifier represents an association between each of a number of different abbreviated namespace identifiers with a corresponding hierarchical namespace (e.g., an XML namespace). A hierarchically-structured document (e.g., an XML document) is accessed by a computing system that determines that the group identifier is associated with the hierarchically-structured document. Hence, when using the abbreviated namespace identifiers in the hierarchically-structured document, the computing system knows that the corresponding namespace is associated with the designated portions of the hierarchically-structured document. Also, a schema description language document (e.g., an XSD document) may specify multiple target namespaces for a single element. Accordingly, groupings of elements may be included in different namespaces to creating overlapping or even nested namespaces.
Owner:MICROSOFT TECH LICENSING LLC
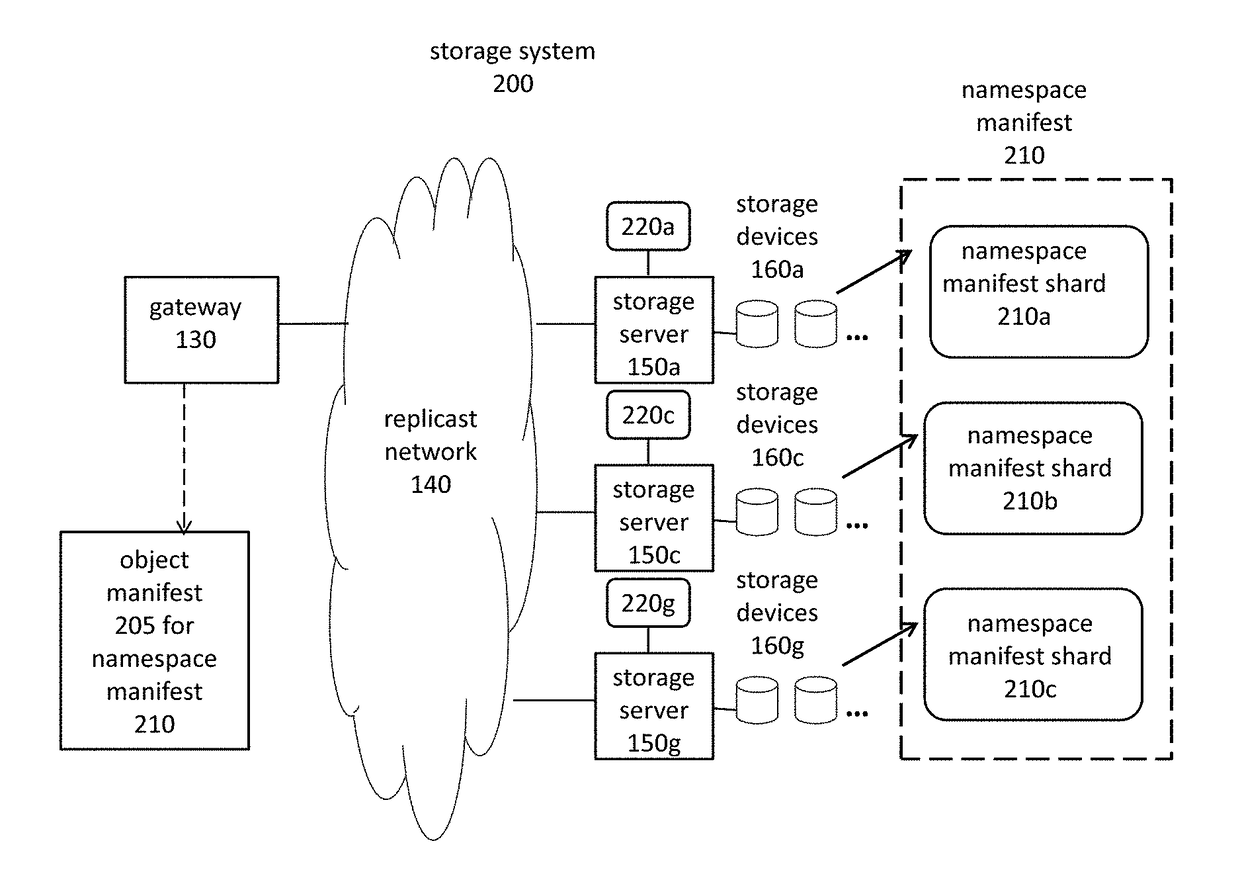
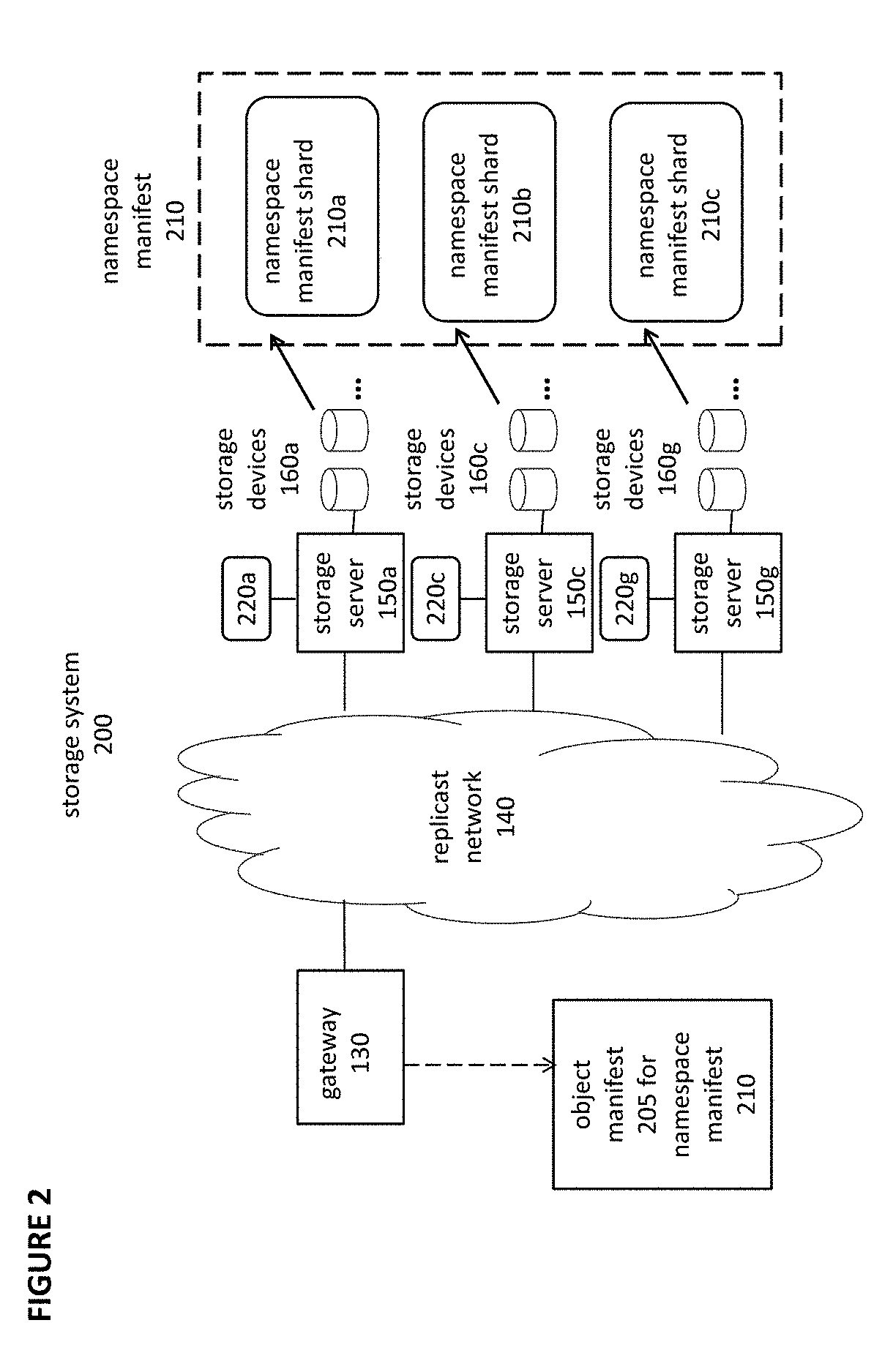
Object storage system with local transaction logs, a distributed namespace, and optimized support for user directories
ActiveUS9710535B2Maintain efficiencyProvide benefitsDigital data information retrievalUser identity/authority verificationTransaction logObject storage
The present invention relates to object storage systems that support hierarchical directories within a namespace manifest stored as an object. The namespace manifest is stored as namespace manifest shards that are determined based on a partial key derived from the full name of the referenced version manifest in each directory entry. Each storage server maintains a local transaction log that keeps track of changes to the namespace manifest in response to put transactions. The namespace manifest can be updated after each put transaction is acknowledged, which minimizes the number of write operations required for a put transaction. Updates to the namespace manifest are batched, distributed, and processed concurrently and in parallel by the storage servers that store the corresponding shards. This reduces the latency that would otherwise exist in the object storage cluster as a result of a put transaction. Updates to namespace manifest shards optionally occur in a batch process using MapReduce techniques.
Owner:NEXENTA BY DDN INC
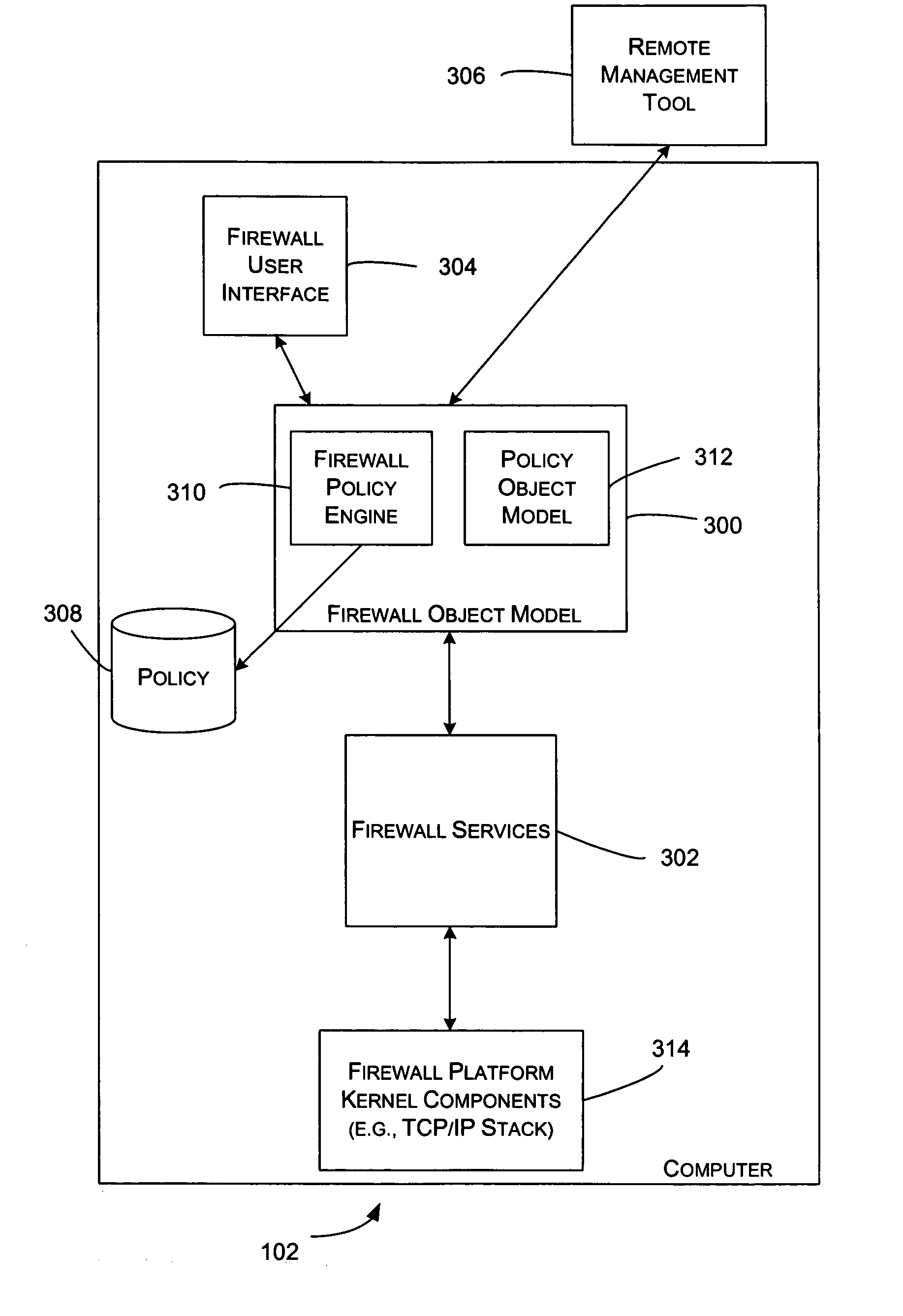
Object model for managing firewall services
InactiveUS20050138416A1Well formedData taking preventionDigital data processing detailsNetwork serviceDistributed computing
An object model is provided as a general framework for managing network services, such as firewall services. A user or an administrator of a computer may utilize the object model to manage and configure the firewall services. The object model isolates a user and / or an administrator from having to deal with the many possible issues involved in configuring the services. The object model includes two main name spaces: a policy engine platform and a policy object model. The policy engine platform is the central point for interacting with the policy for the services and the kernel components that actually perform the services. The policy object model is used to specify policies that the services support.
Owner:MICROSOFT TECH LICENSING LLC
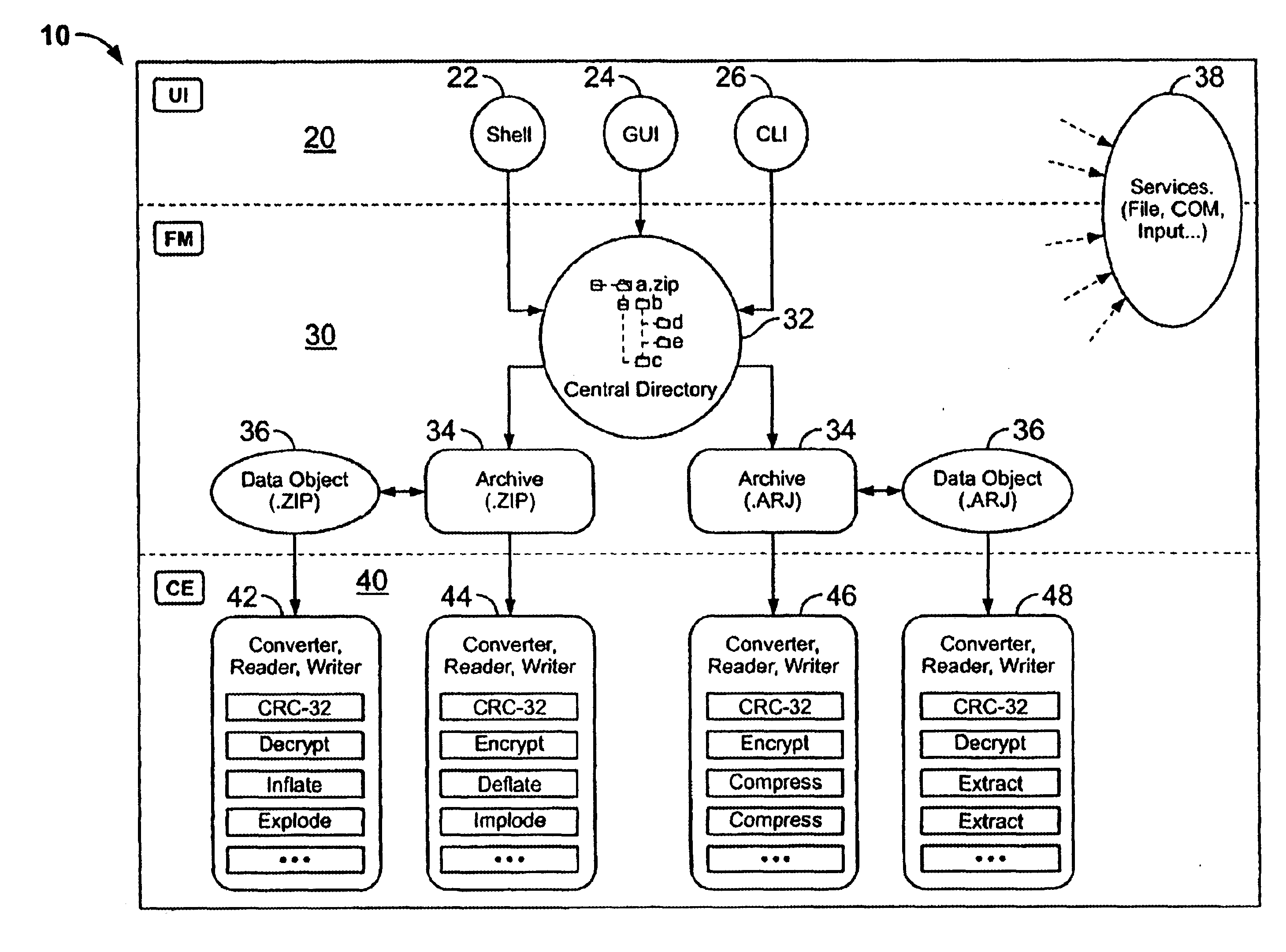
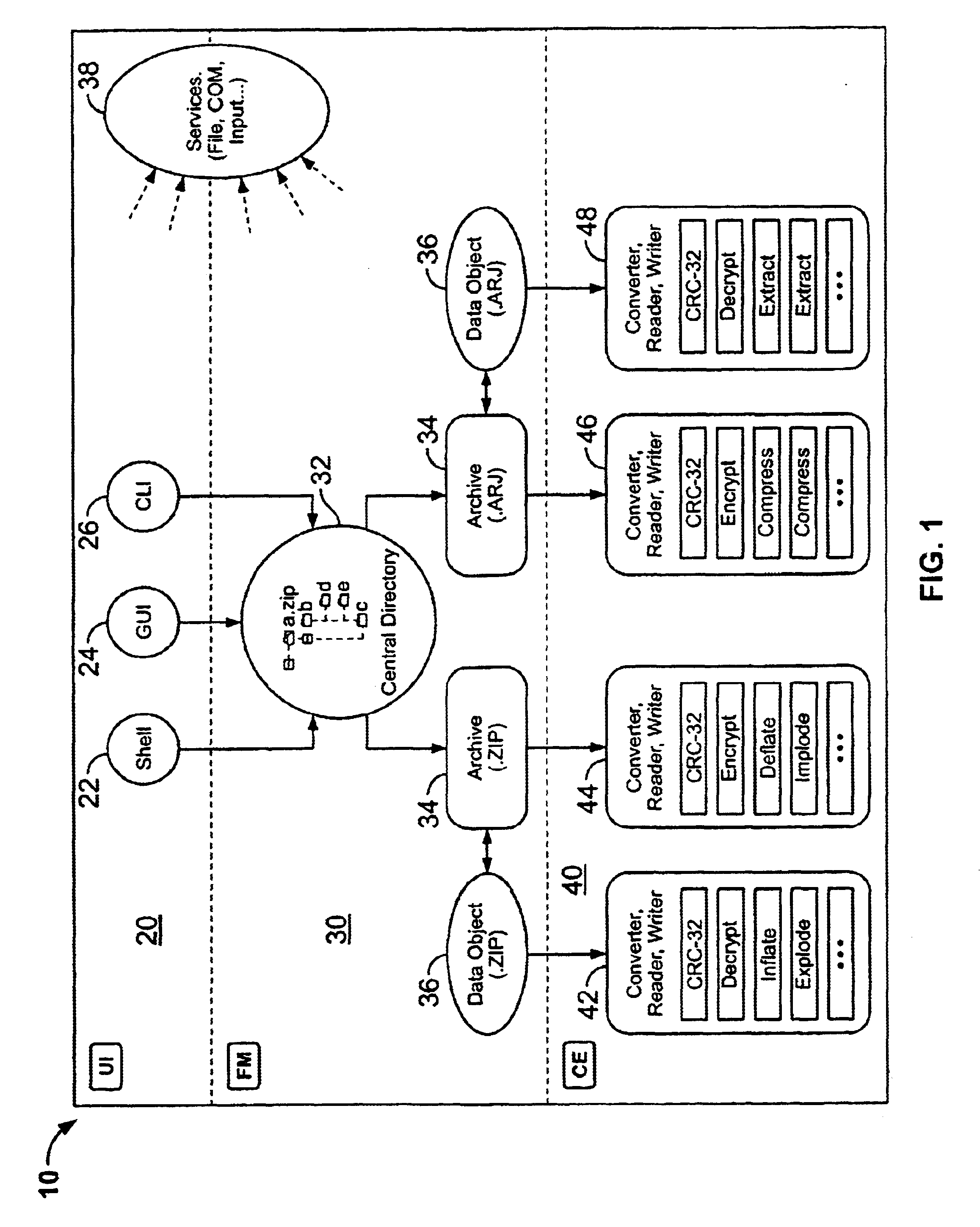
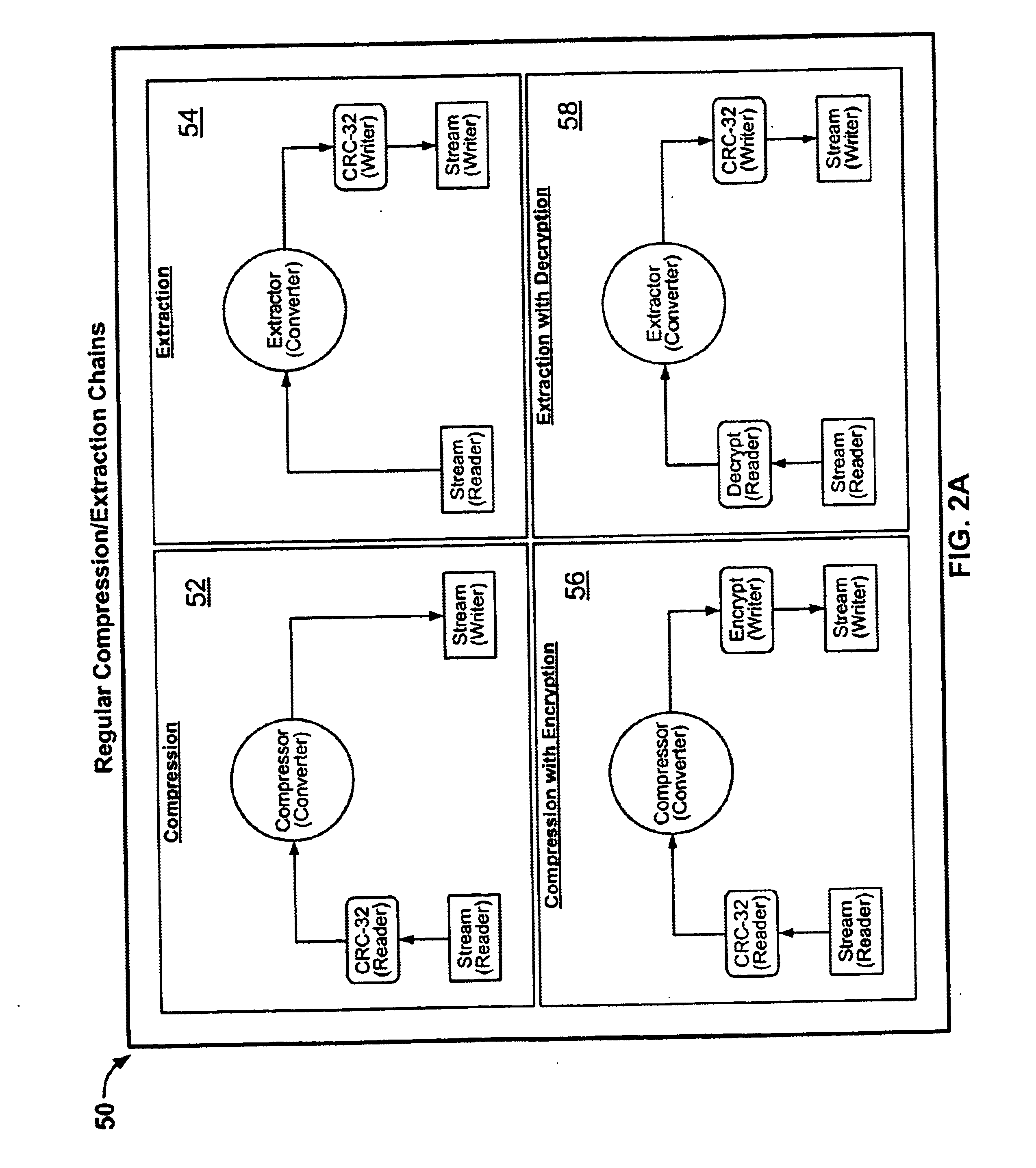
System and method for manipulating and managing computer archive files
InactiveUS6879988B2Easy to carryQuick and easy management and manipulationData processing applicationsDigital data information retrievalDrag and dropResource management
A computer program for managing and manipulating archive zip files of a computer. The program includes a system and method for opening, creating, modifying, and extracting zip archive files. The program is fully integrated into Microsoft Windows Explorer and is accessed via Explorer menus, toolbars, and / or drag and drop operations. An important feature of the program is the archive manager which may be used to open a zip file, create a new zip file, extract zip files, modify zip files, etc. The program is integrated into Microsoft Windows Explorer using the shell name space extension application program interface developed by Microsoft.
Owner:PKWARE
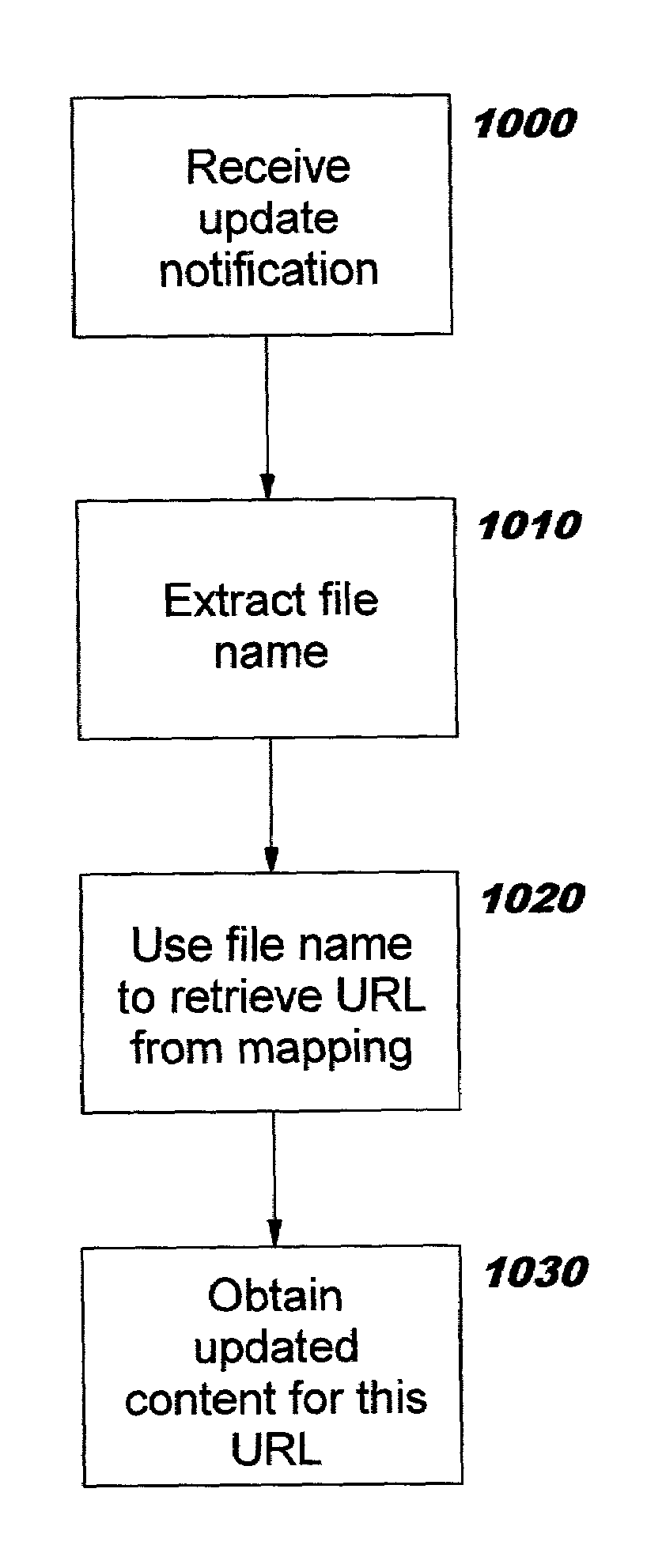
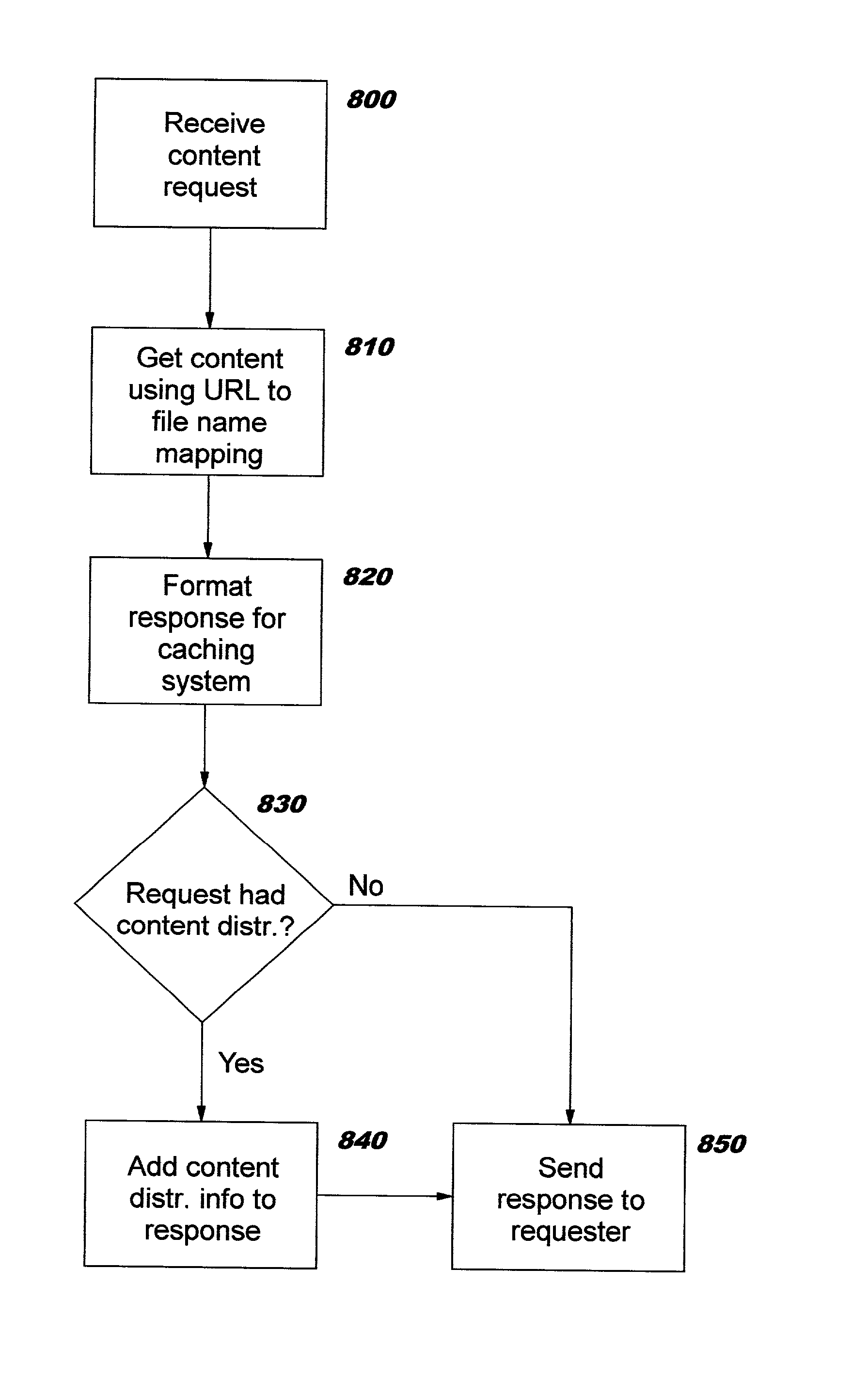
Addressing the name space mismatch between content servers and content caching systems
InactiveUS6985936B2Improve efficiencyEfficiently interoperatingDigital data information retrievalDigital data processing detailsUniform resource locatorExtensible markup
Techniques are disclosed for addressing the name space mismatch between content caching systems (which use Uniform Resource Locators, or “URLs”) and content servers (which use file and path names). A file name-to-URL mapping is created for use by content caching systems, and data in protocol response messages (and optionally in protocol request messages) is augmented to transmit information for use in creating this mapping, enabling a content caching system to automatically and dynamically populate its file name-to-URL mapping. By having the file name available, the caching system can now respond to content management messages which identify the cached content by only the content's associated file name. Techniques for encoding the message extensions include: use of new directives on existing cache-control headers in Hypertext Transfer Protocol (“HTTP”) messages; addition of new headers in HTTP messages; and use of meta-data in markup languages such as Hypertext Markup Language (“HTML”) or Extensible Markup Language (“XML”) format.
Owner:INT BUSINESS MASCH CORP
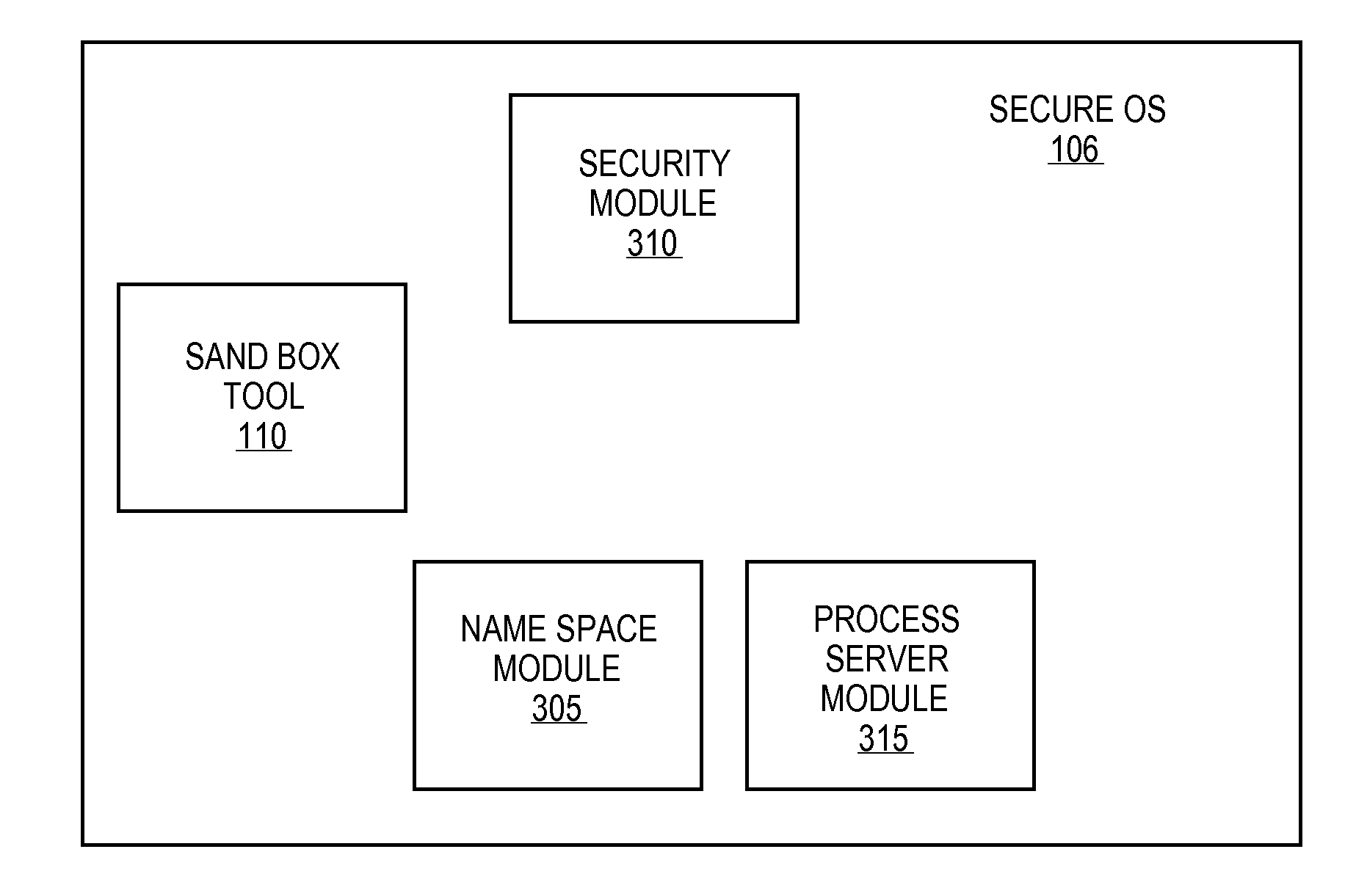
Systems and methods for providing multiple isolated execution environments for securely accessing untrusted content
ActiveUS20110154431A1Memory loss protectionError detection/correctionOperational systemOperating system
A sandbox tool can create and maintain multiple isolated execution environments, simultaneously. The sandbox tool can assign a unique security label to each isolated execution environment. In order to ensure the security labels are unique, the sandbox tool, for each security label, can bind a communication socket in an abstract name space of the operating system with a name that is the same as the security label. If the operating system returns an error that the name for the communication socket is already in use, the sandbox tool can determine that the security label is already in use by another isolated execution environment or other process.
Owner:RED HAT
Fine grit document and catalogs version management method based on snapshot
InactiveCN101162469AShort execution timeFlexible configuration version generation strategySpecial data processing applicationsGranularityUsability
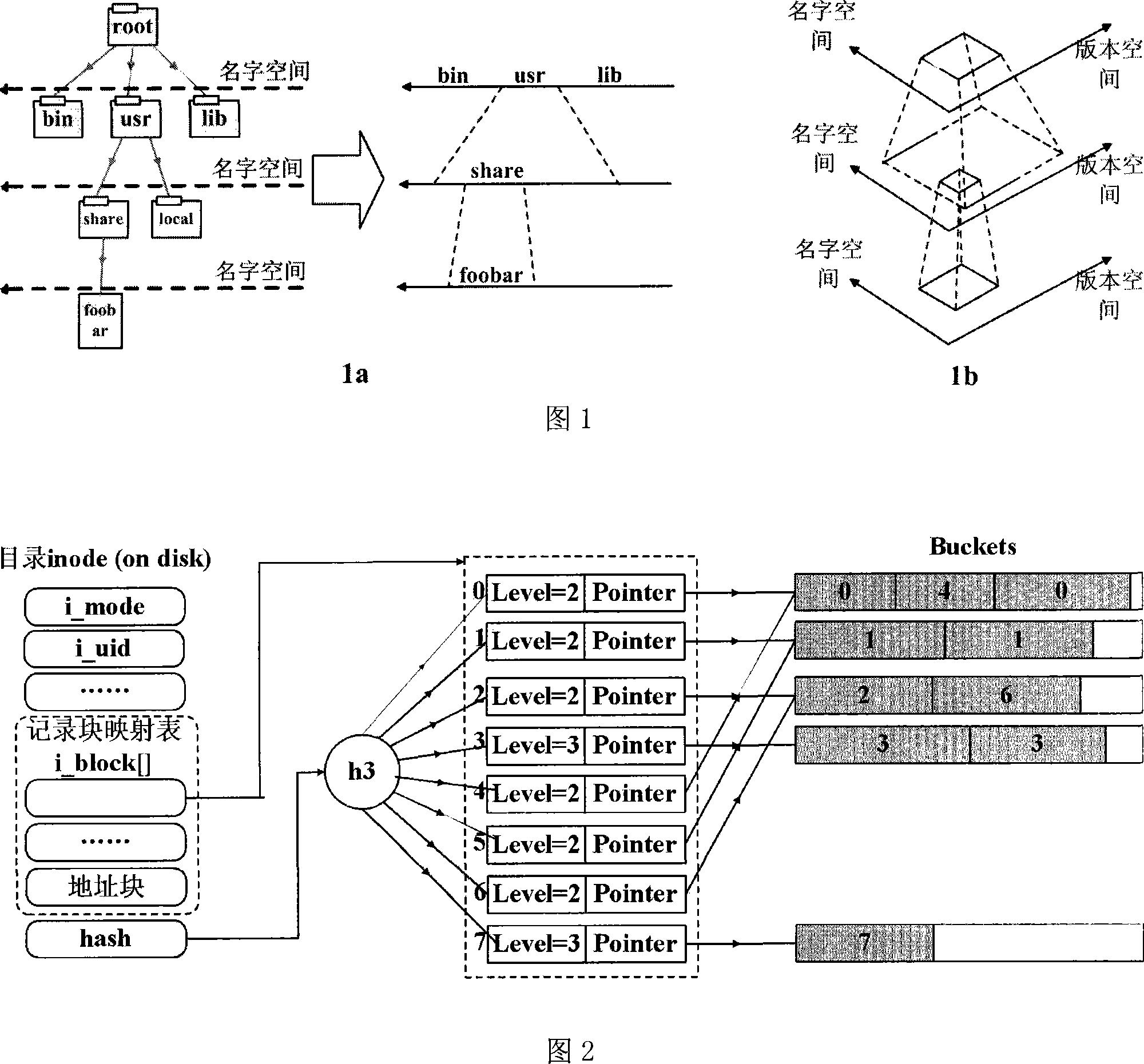
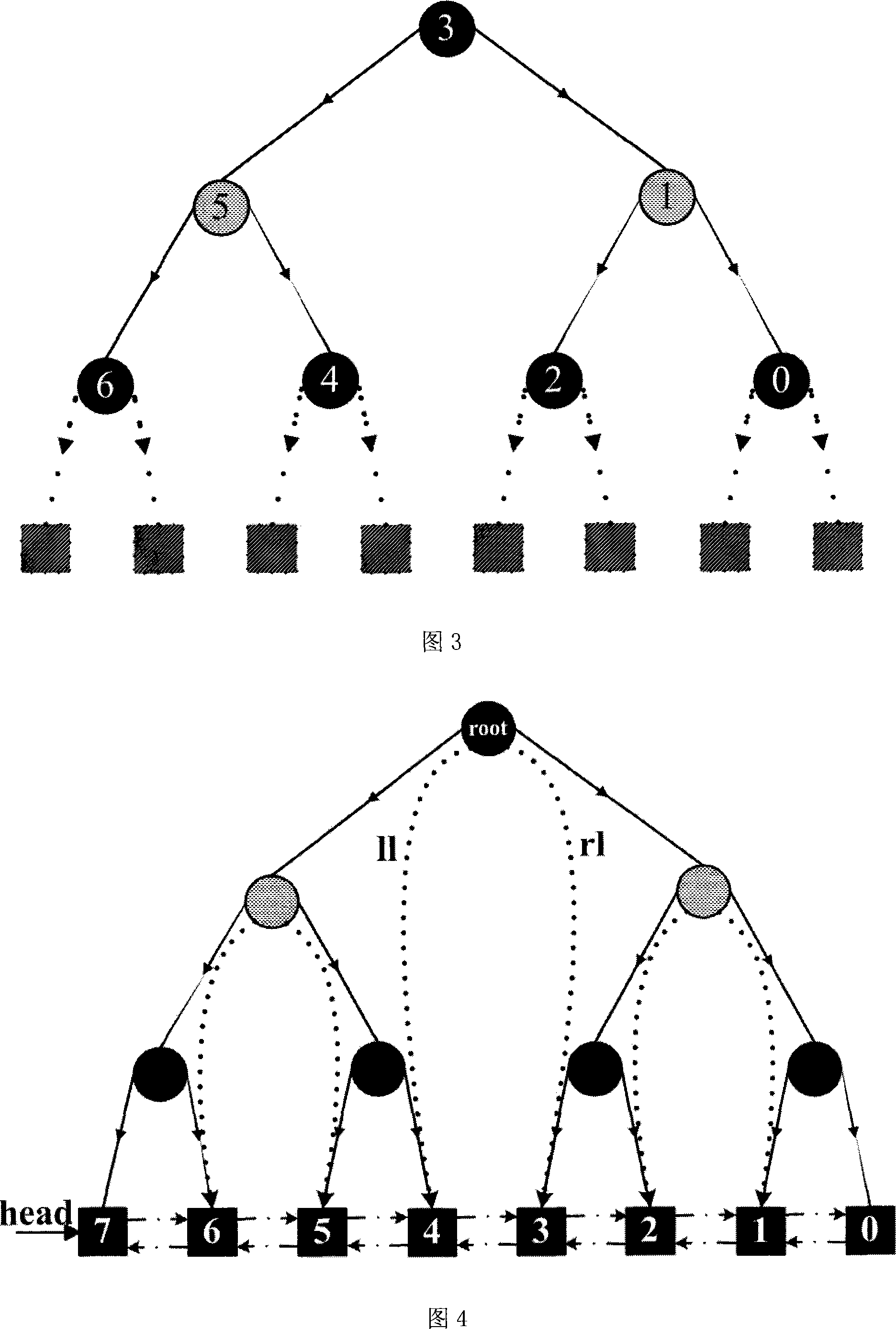
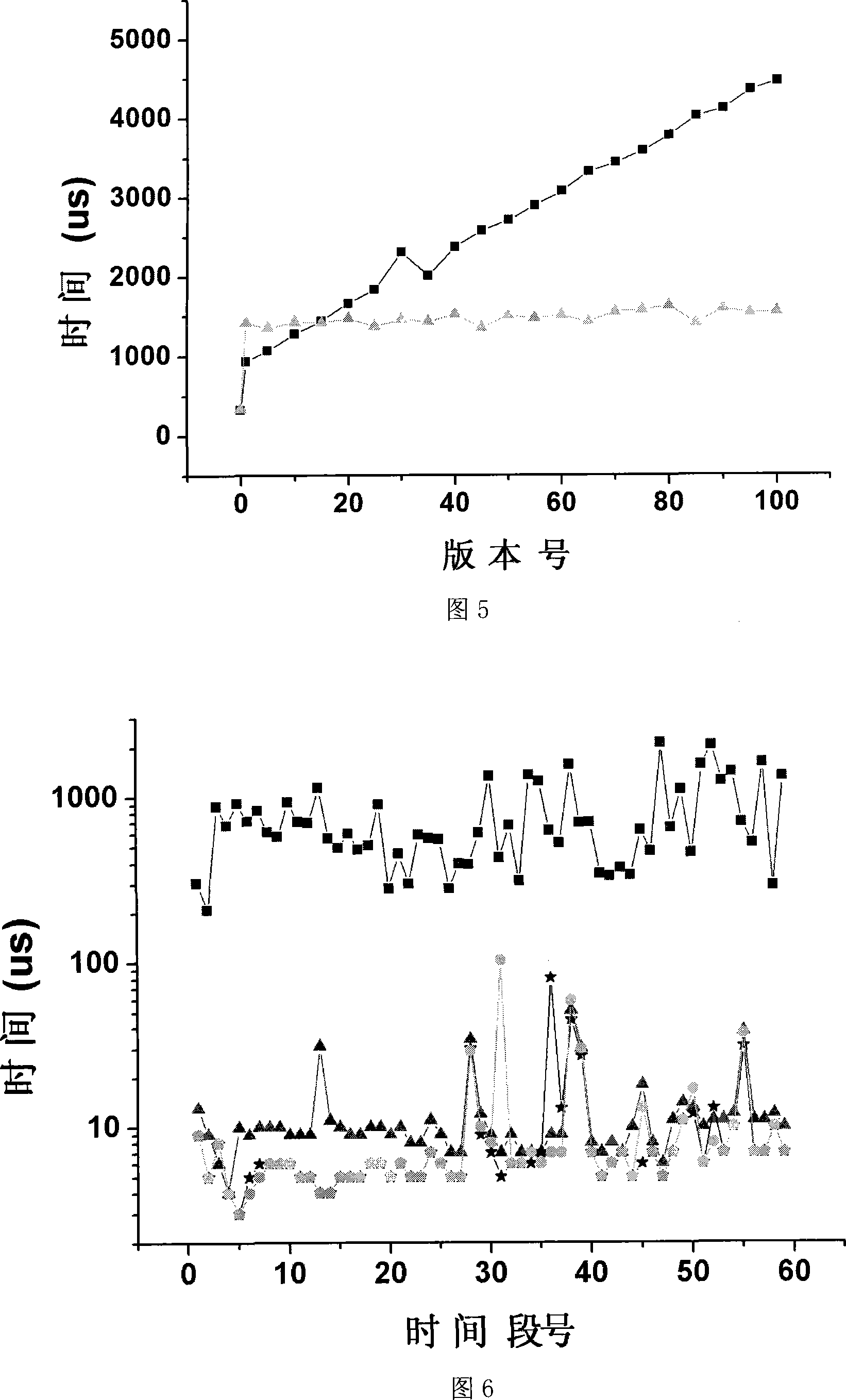
The present invention relates to a fine-granularity files and directory edition management method based on snapshots, belonging to the multi-version document system field. The present invention separates a name space consisting of files and dirnames in a whole file system from an edition space representing the generating periods of different editions, and adopts relatively independent strategies to execute management, forming a hierarchical two-dimensional structure, i.e. forming a hierarchical structure from a root directory to a file in the name space; in the edition space, the editions of files and directory are organized through an index structure chronologically, forming a hierarchical structure in the edition space. The retrieval of the name space adopts an index strategy based on dynamic hash. The retrieval of the edition space adopts an index strategy based on a red-black tree. The directory edition and file edition respectively adopt a red-black tree structure variant aiming at the respective characteristics. The present invention can greatly improve the usability and the performance of the system, and controls the amount of consumption of time and space resulting from the maintenance of historical editions in an acceptable scope.
Owner:TSINGHUA UNIV
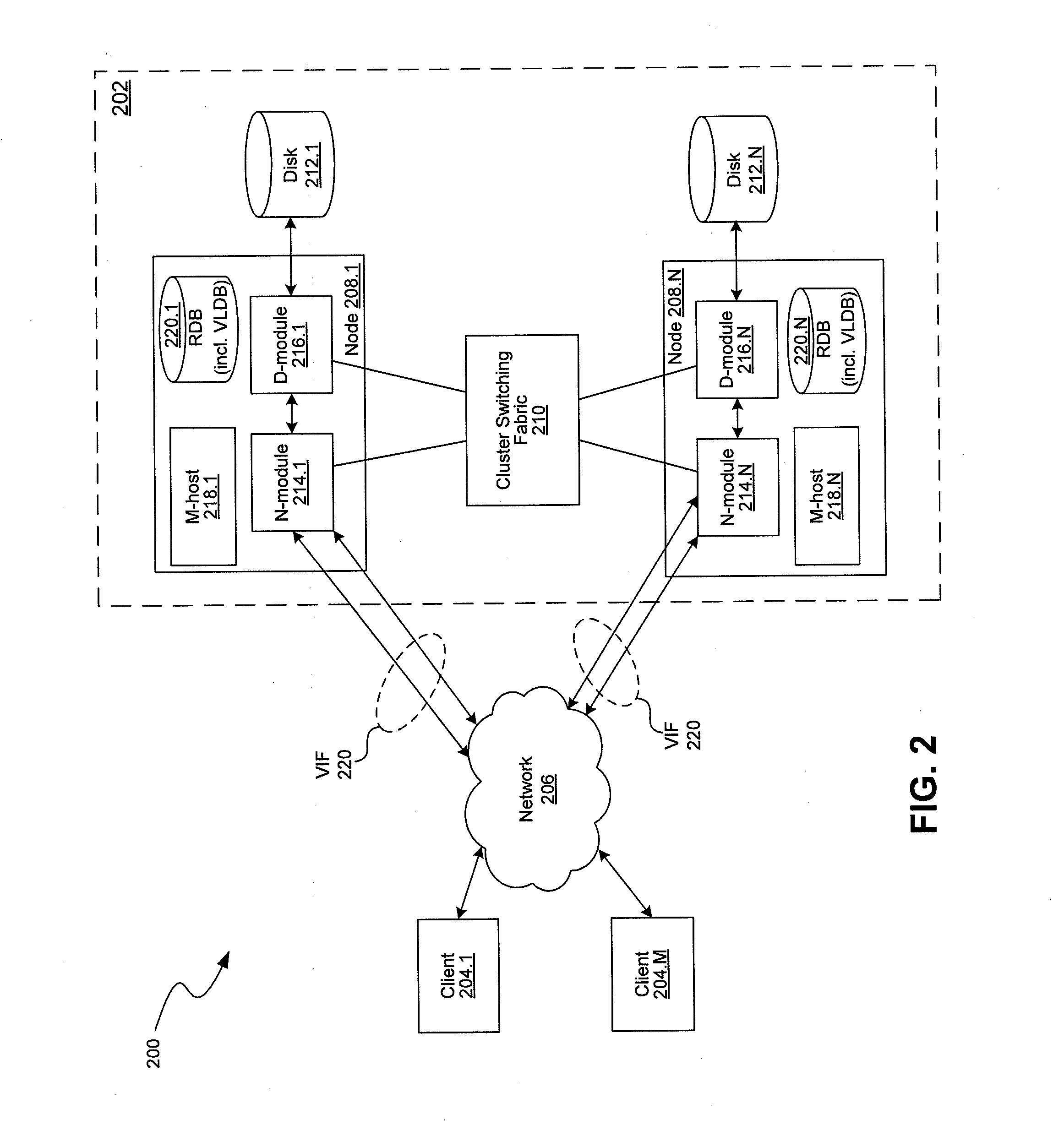
Methods and systems for providing a unified namespace for multiple network protocols
InactiveUS20110137966A1Easy data migrationEasy to navigateTransmissionSpecial data processing applicationsObject handlingObject store
A network storage server system includes a presentation layer that presents multiple namespaces over the same data stored in an object store, allowing users to simultaneously access data over multiple protocols. The system supports object location independence of the stored data objects by introducing a layer of indirection between directory entries and storage locations of stored data objects. In one embodiment, the directory entry of a data object points to a redirector file that includes an object locator (e.g., an object handle or a global object ID) of the data object. The directory entries of data objects are stored in a directory namespace (e.g., NAS path namespace). In another embodiment, a global object ID of the data object is directly encoded within the directory entry of the data object.
Owner:NETWORK APPLIANCE INC
Addressing the name space mismatch between content servers and content caching systems
InactiveUS20030061278A1Digital data information retrievalMultiple digital computer combinationsUniform resource locatorExtensible markup
Techniques are disclosed for addressing the name space mismatch between content servers (which use Uniform Resource Locators, or "URLs") and content caching systems (which use file and path names). A file name-to-URL mapping is created for use by content caching systems, and data in protocol response messages (and optionally in protocol request messages) is augmented to transmit information for use in creating this mapping, enabling a content caching system to automatically and dynamically populate its file name-to-URL mapping. By having the file name available, the caching system can now respond to content management messages which identify the cached content by only the content's associated file name. Techniques for encoding the message extensions include: use of new directives on existing cache-control headers in Hypertext Transfer Protocol ("HTTP") messages; addition of new headers in HTTP messages; and use of meta-data in markup languages such as Hypertext Markup Language ("HTML") or Extensible Markup Language ("XML") format.
Owner:IBM CORP
System and method for generating a consistent user name-space on networked devices
ActiveUS20050198385A1Digital data information retrievalMultiple digital computer combinationsNetwork connectionRemote computer
A system and method for implementing a consistent user name-space on networked computing devices is provided. When a network connection between a local or host computing device and one or more remote computing devices is present, remote items are represented using the same methodology as items located on the host computing device. To the user, remote and local items are indistinguishable. When the network connection is lost or items located on a remote computer are otherwise unavailable, the unavailable items remain represented on the host computing device. Unavailable items are represented in a way that informs the user that the items may not be fully accessed.
Owner:MICROSOFT TECH LICENSING LLC
Protecting resources in a distributed computer system
InactiveUS6658573B1Improve visibilitySpecific access rightsData processing applicationsCommunications systemConfidentiality
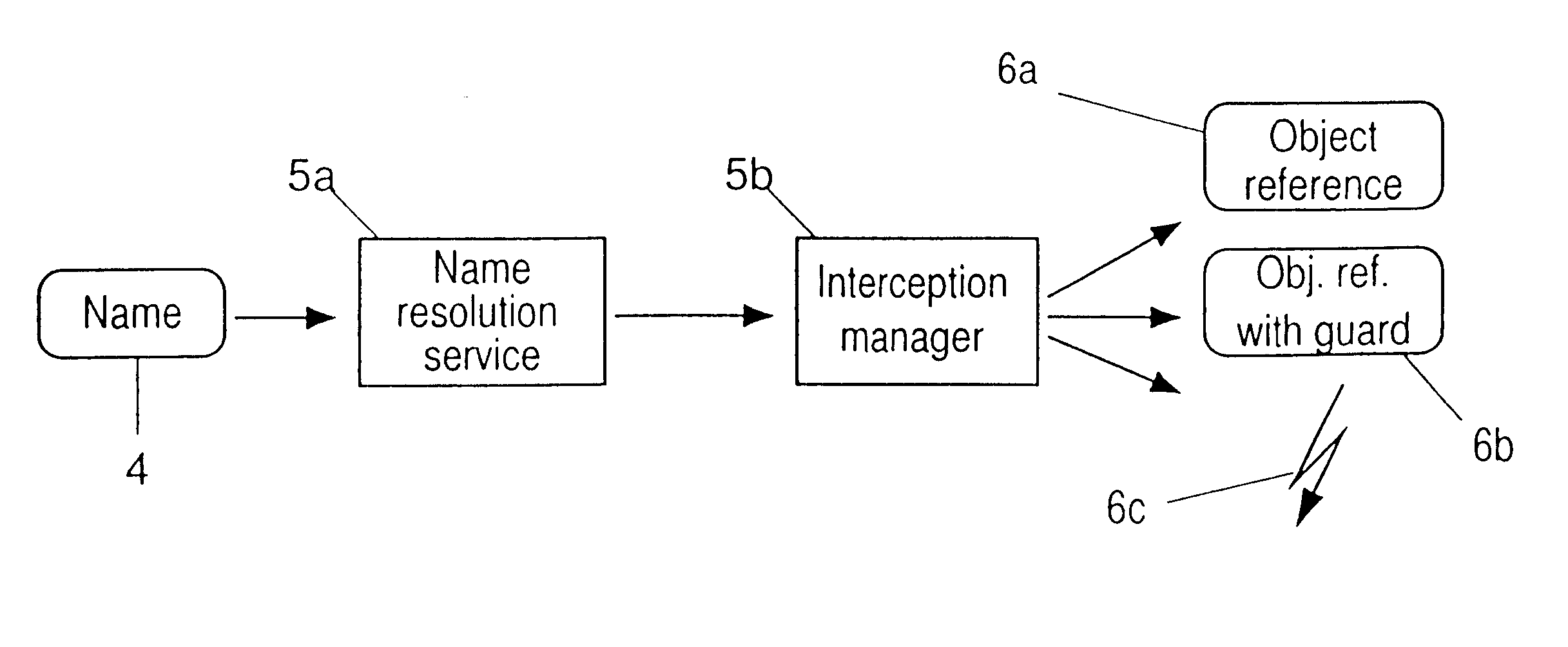
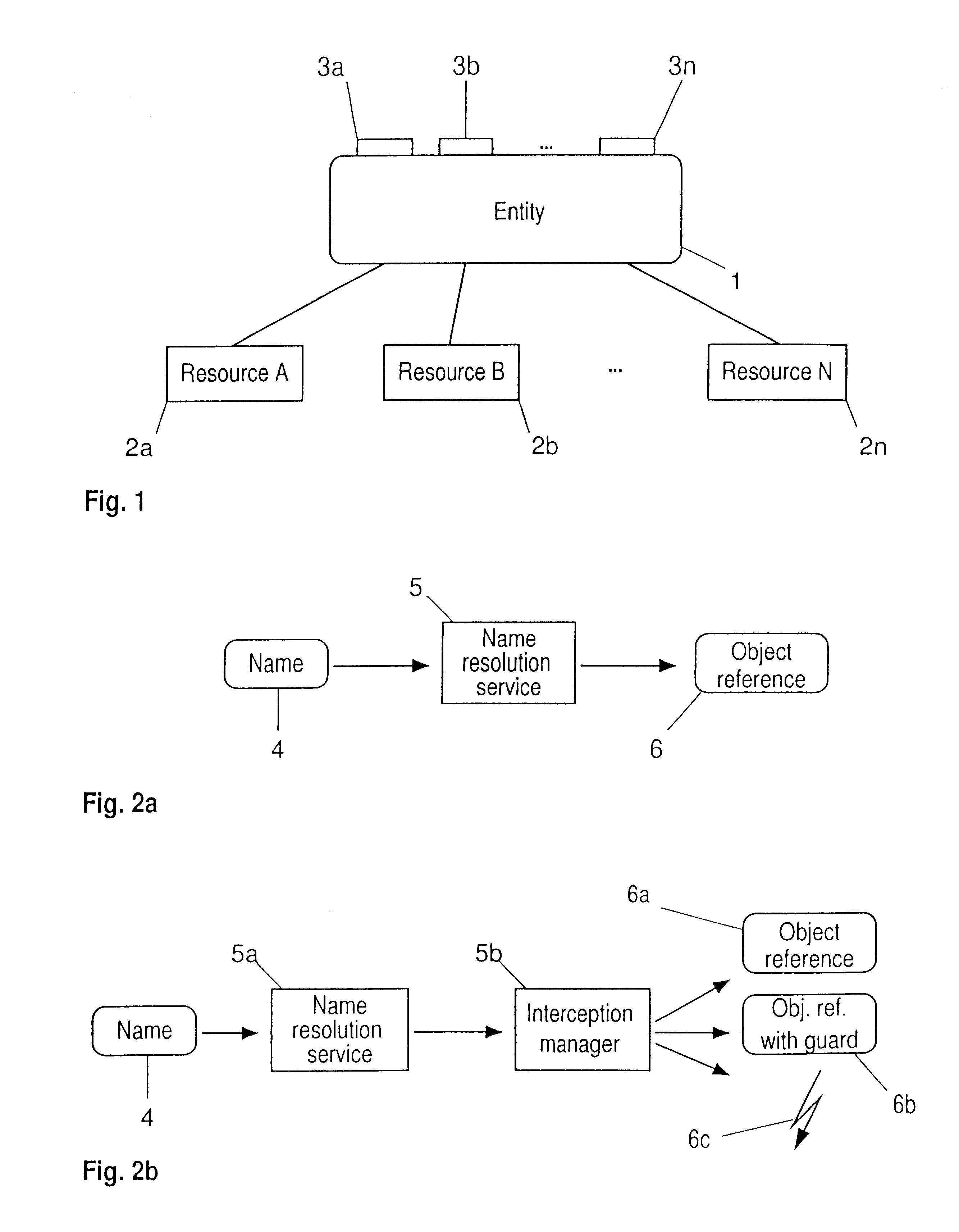
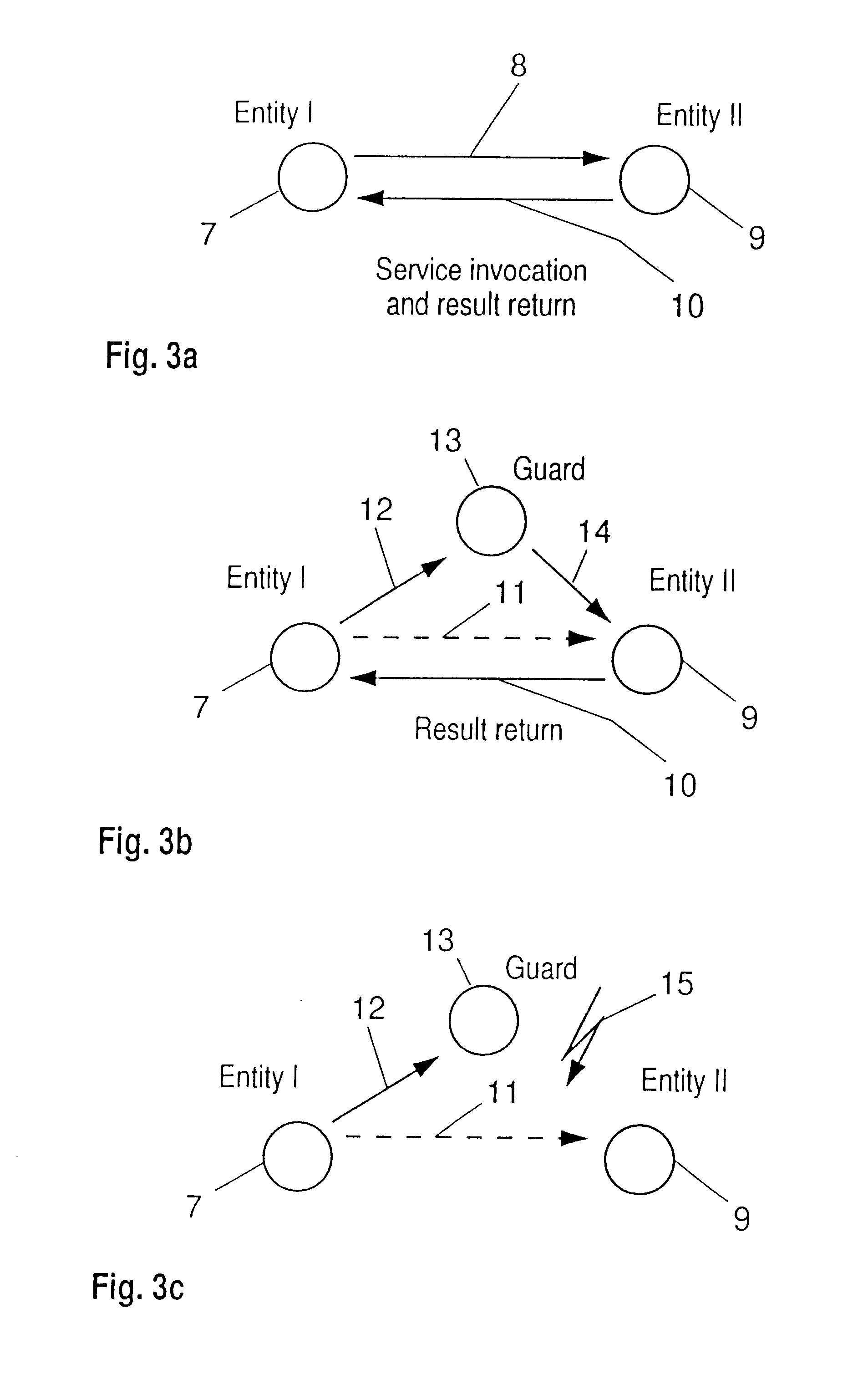
This invention concerns methods for the protection of resources in an open digital communication system, which resources are residing in or owned by physically and organizationally distributed, independent entities connected through that system, e.g. the Internet. Since, in such an open system, any entity can in principle access any resource of any other entity, precautions must be taken to avoid or minimize the danger of resource corruption and destruction, to maintain privacy and, where necessary, confidentiality. Thus, protection of resources is of ultimate importance to warrant integrity and function of an entity. For the intelligent protection of such resources, in particular against unauthorized access, a variable-grained control of the name space (consisting of all names an entity provides) and / or the provision of attachable and detachable guards accompanying each call for a file and / or service is provided.
Owner:GOOGLE LLC
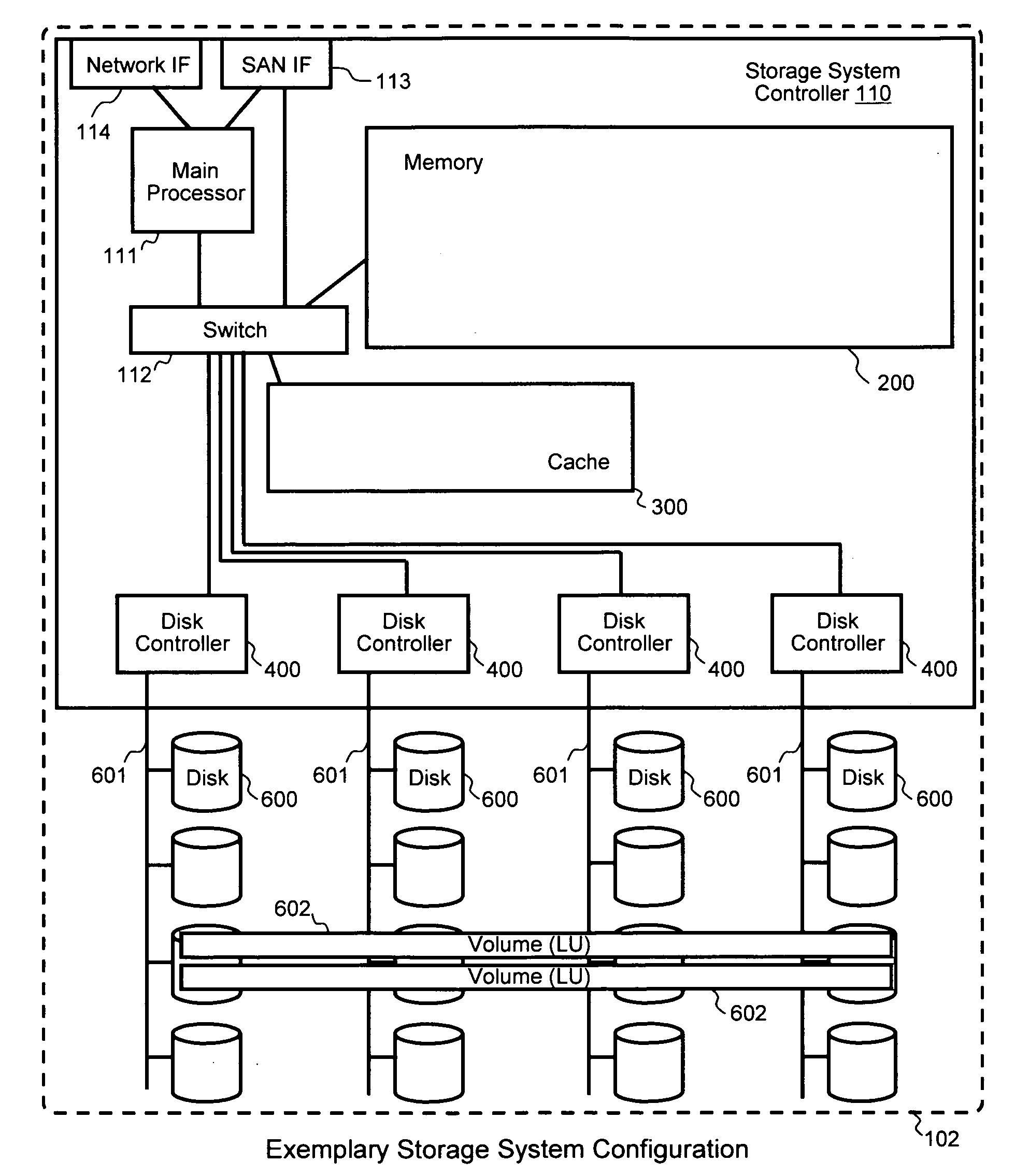
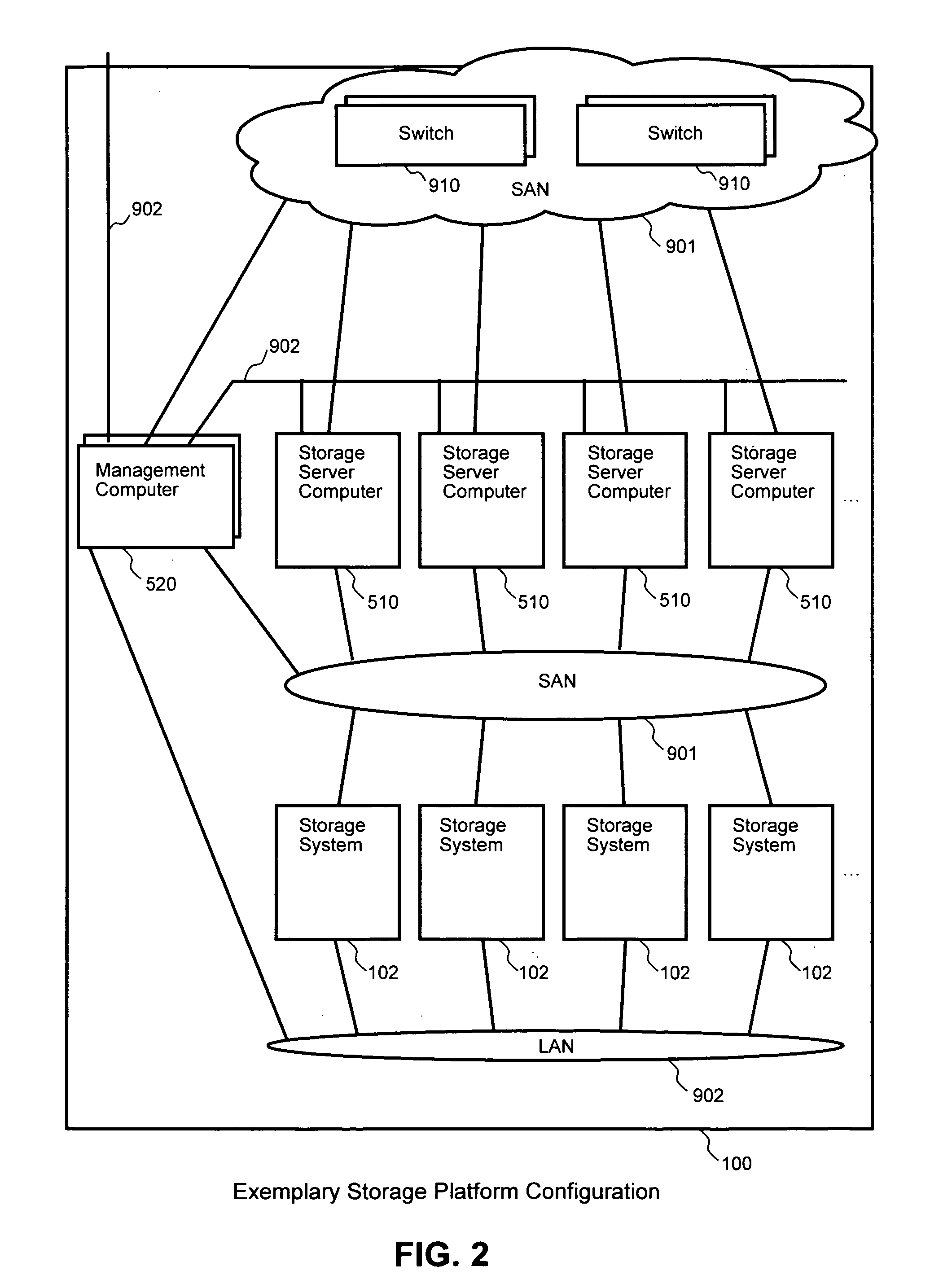
Methods, systems and programs for partitioned storage resources and services in dynamically reorganized storage platforms
Exemplary embodiments establish durable partitions that are unified across storage systems and storage server computers. The partitions provide independent name spaces and are able to maintain specified services and conditions regardless of operations taking place in other partitions, and regardless of configuration changes in the information system. A management computer manages and assigns resources and functions provided by storage server computers and storage systems to each partition. By using the assigned resources, a partition is able to provide storage and other services to users and applications on host computers. When a configuration change occurs, such as addition or deletion of equipment, the management computer performs reassignment of resources, manages migration of services and / or data, and otherwise maintains the functionality of the partition for the user or application. Additionally, a partition can be migrated within the information system for various purposes, such as improved performance, load balancing, and the like.
Owner:HITACHI LTD
Automated design partitioning
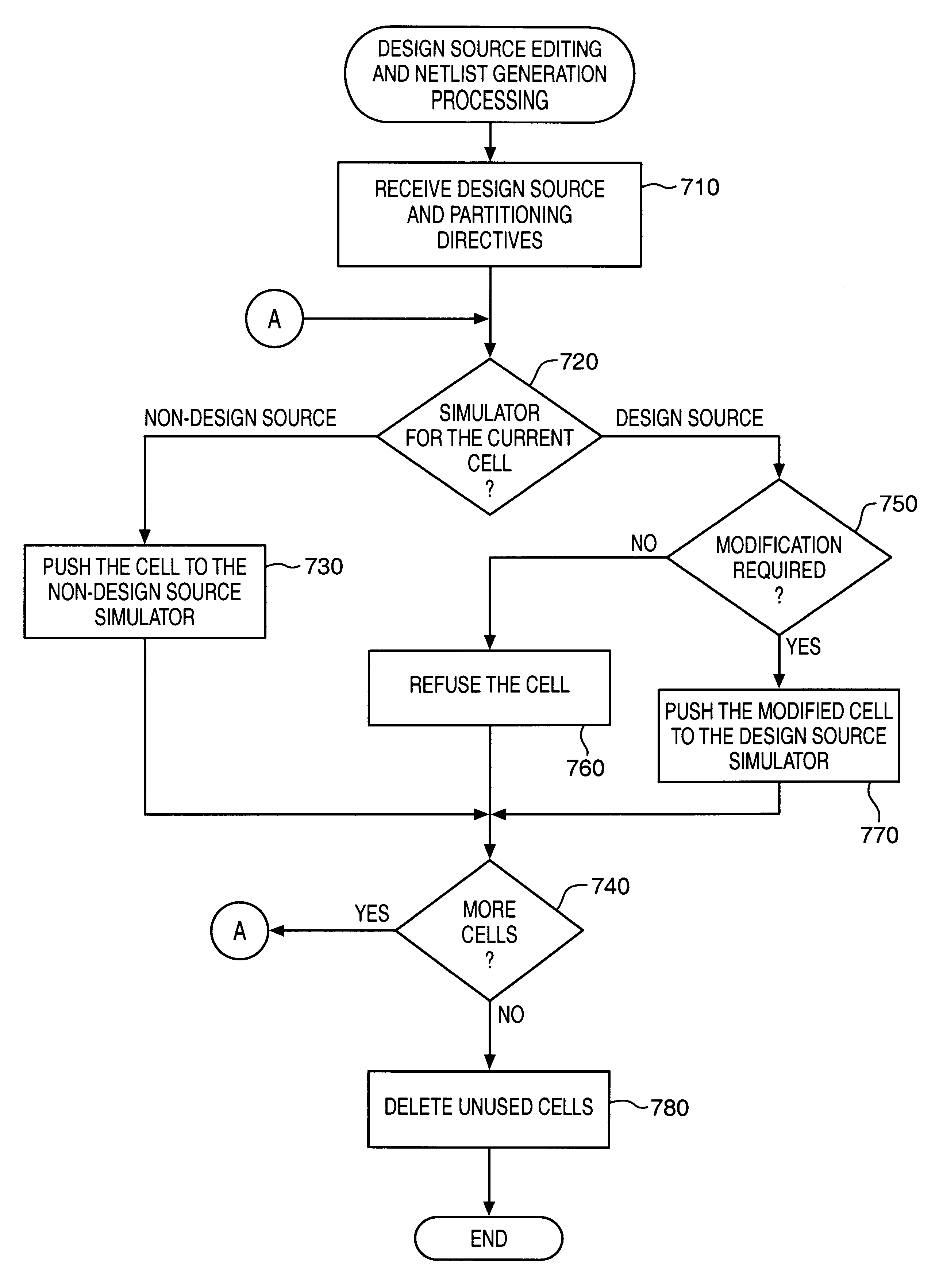
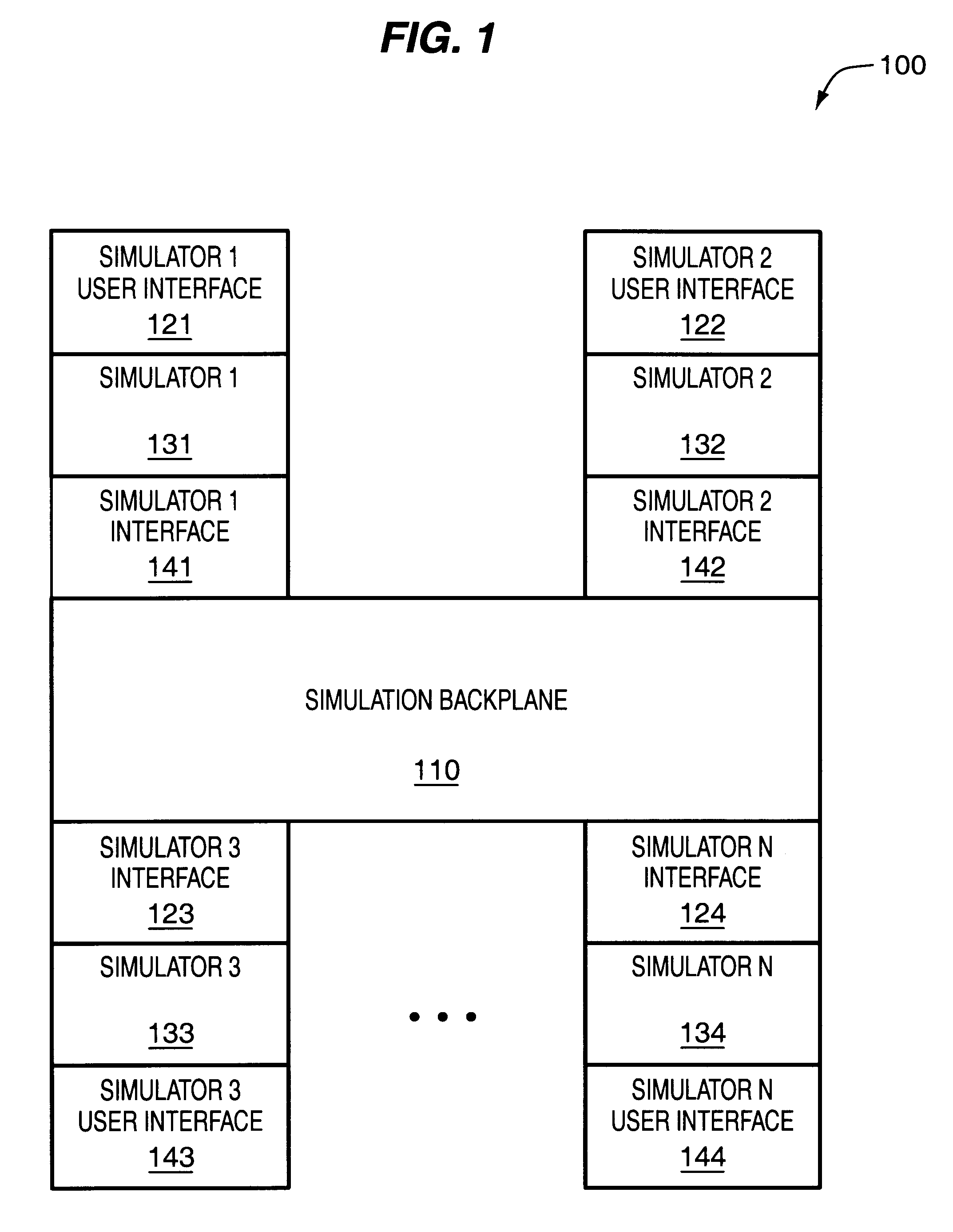
InactiveUS6339836B1Detecting faulty computer hardwareCAD circuit designTheoretical computer scienceNetlist
A flexible and extensible automated design partitioning mechanism that facilitates simulation sessions employing two or more simulators is provided. A simulation backplane includes partitioning logic that identifies the design blocks of an overall design pertaining to each of a plurality of simulators. Once the partitions have been identified, nets that cross simulator boundaries (e.g., mixed nets) are determined and inter-simulator connectivity information is generated for the simulators. According to one aspect of the present invention, the partitioning logic is able to accomodate arbitrary (e.g., instance-based) partitioning. A design source expressed in a design representation upon which a first simulator may operate is received. Design blocks to be partitioned to each of a plurality of solvers are identified based upon one or more partitioning directives and the design source. A first instance of a cell is assigned to a first solver and a second instance of the cell is assigned to a second solver. Netlist like information is generated for those of the design blocks that are partitioned to a non-design source solver. To accomodate a folded representation of a design block containing the first or second instance of the cell, one or more additional cells are created. According to another aspect of the present invention, name space mapping is retained across all simulators. A design source upon which a first simulator may operate is read. Based upon a set of rules, a primary partition that is to be simulated by a first solver is identified. The primary partition includes a top cell of the design representation. Additionally, a secondary partition that is to be simulated by a second solver is identified. Subsequently, netlist information is generated for the second solver while retaining name space mapping in the secondary partition by adding one or more levels of hierarchy so as to include information about the top cell in the secondary partition.
Owner:MENTOR GRAPHICS CORP
Systems and methods for integrating access control with a namespace
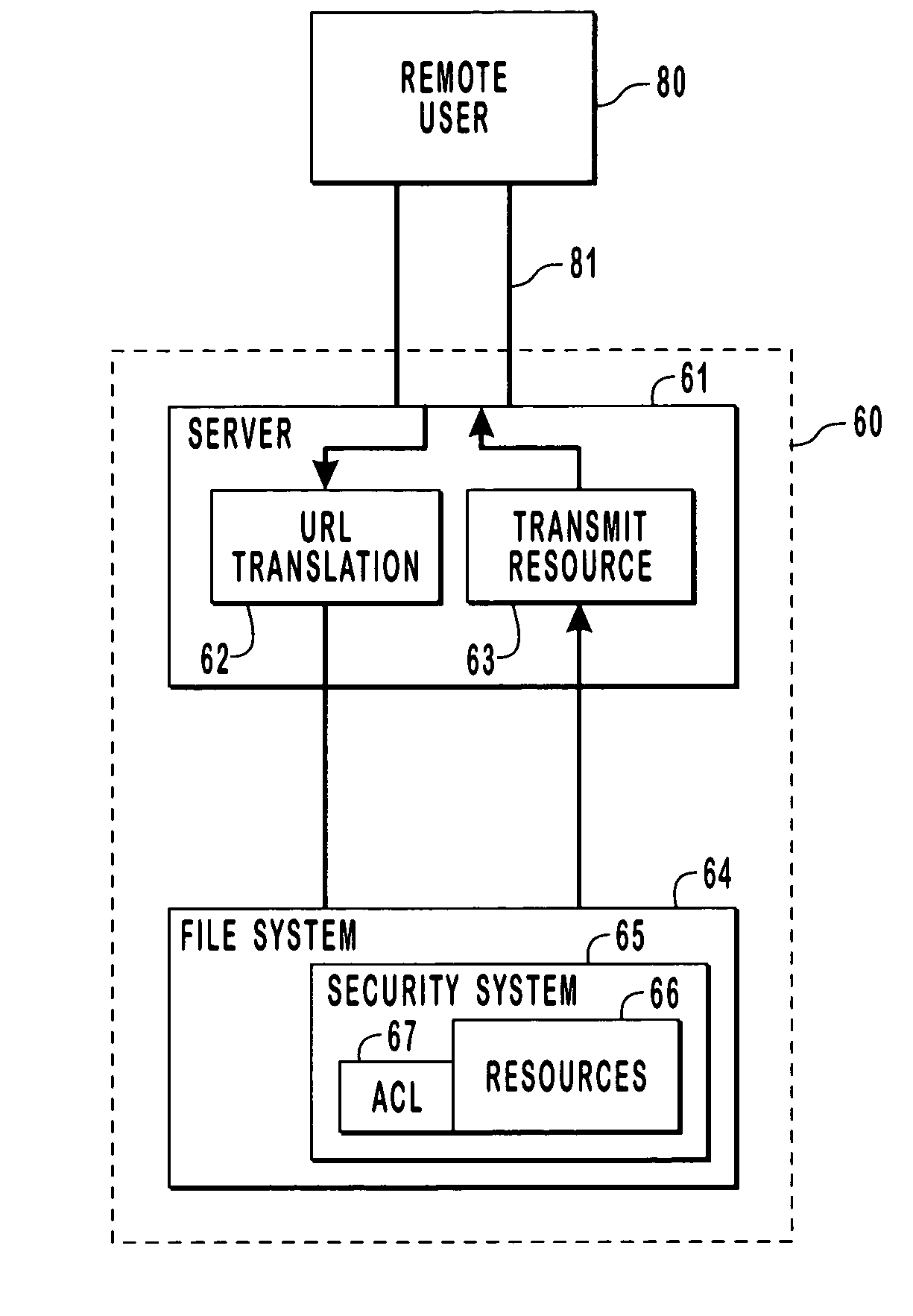
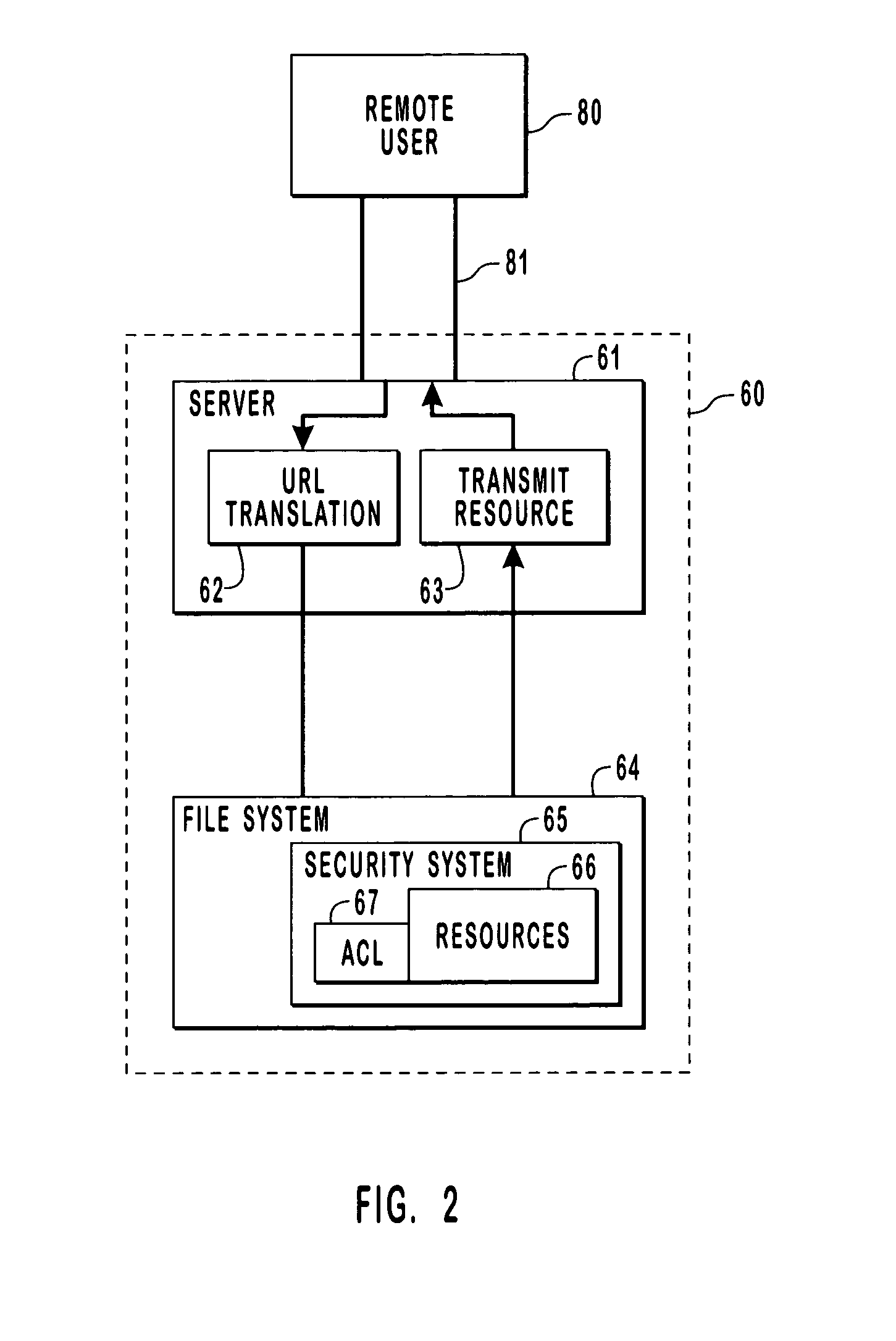
InactiveUS7065784B2Digital data processing detailsUser identity/authority verificationComputer resourcesData access control
Provided are methods and systems for integrating the access controls of computer resources into a namespace or domain. For a remote user, a computer network or system is a namespace represented by a URL. In order to enforce the access controls of the computer network being accesses, a remote user is impersonated by a server of the computer system such that access requests to the resources of a system are made by the server in the security context of the remote user. By impersonating the remote user, the actual rights of the remote user are being presented to the access controls rather than the rights of the server. In this manner, the access control of the system can be enforced directly on the remote user and the access control is effectively extended to the namespace.
Owner:MICROSOFT TECH LICENSING LLC
Managed forwarding element executing in separate namespace of public cloud data compute node than workload application
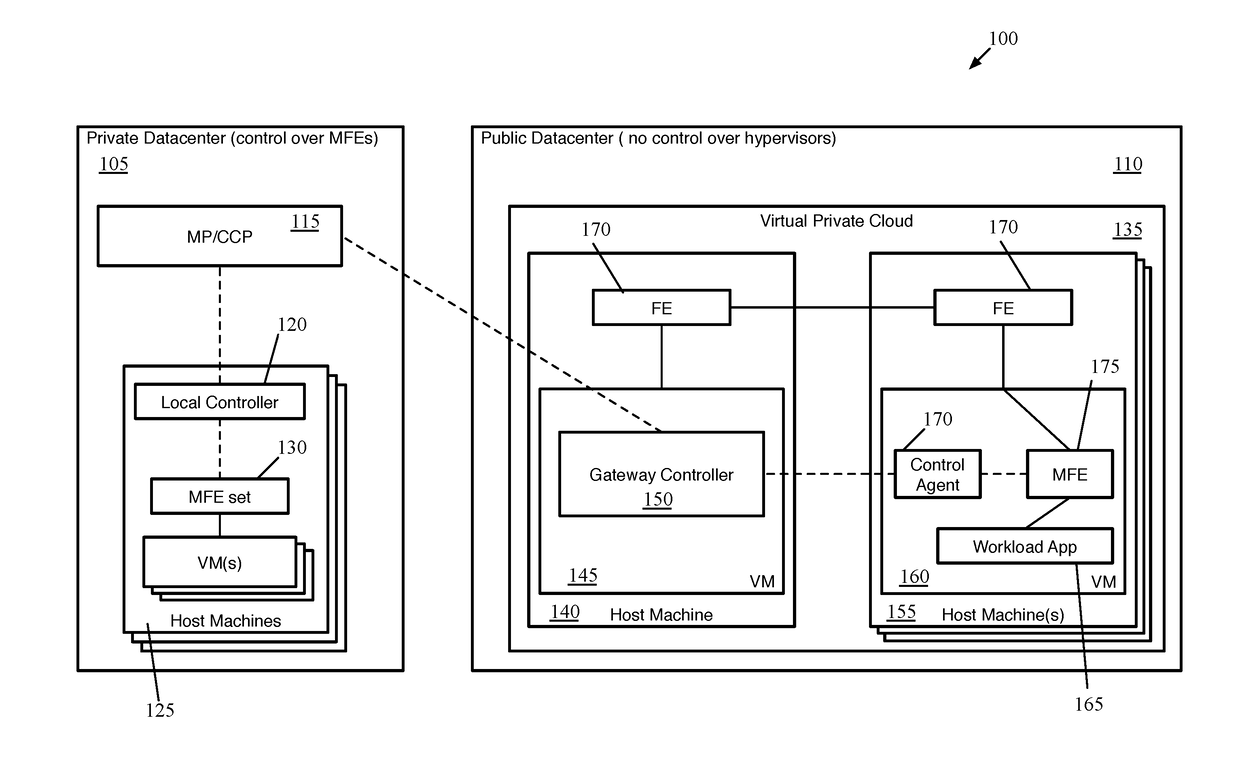
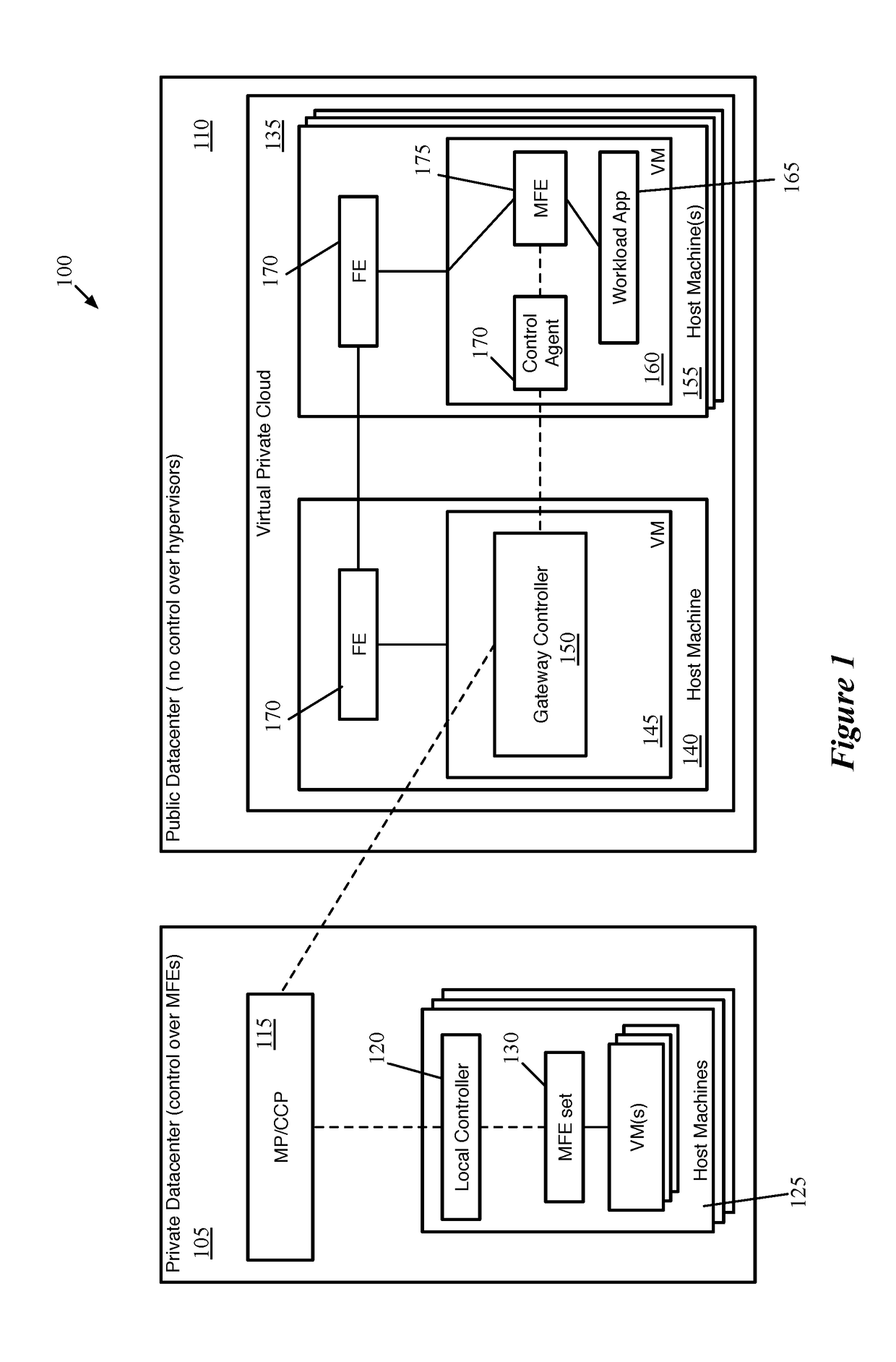
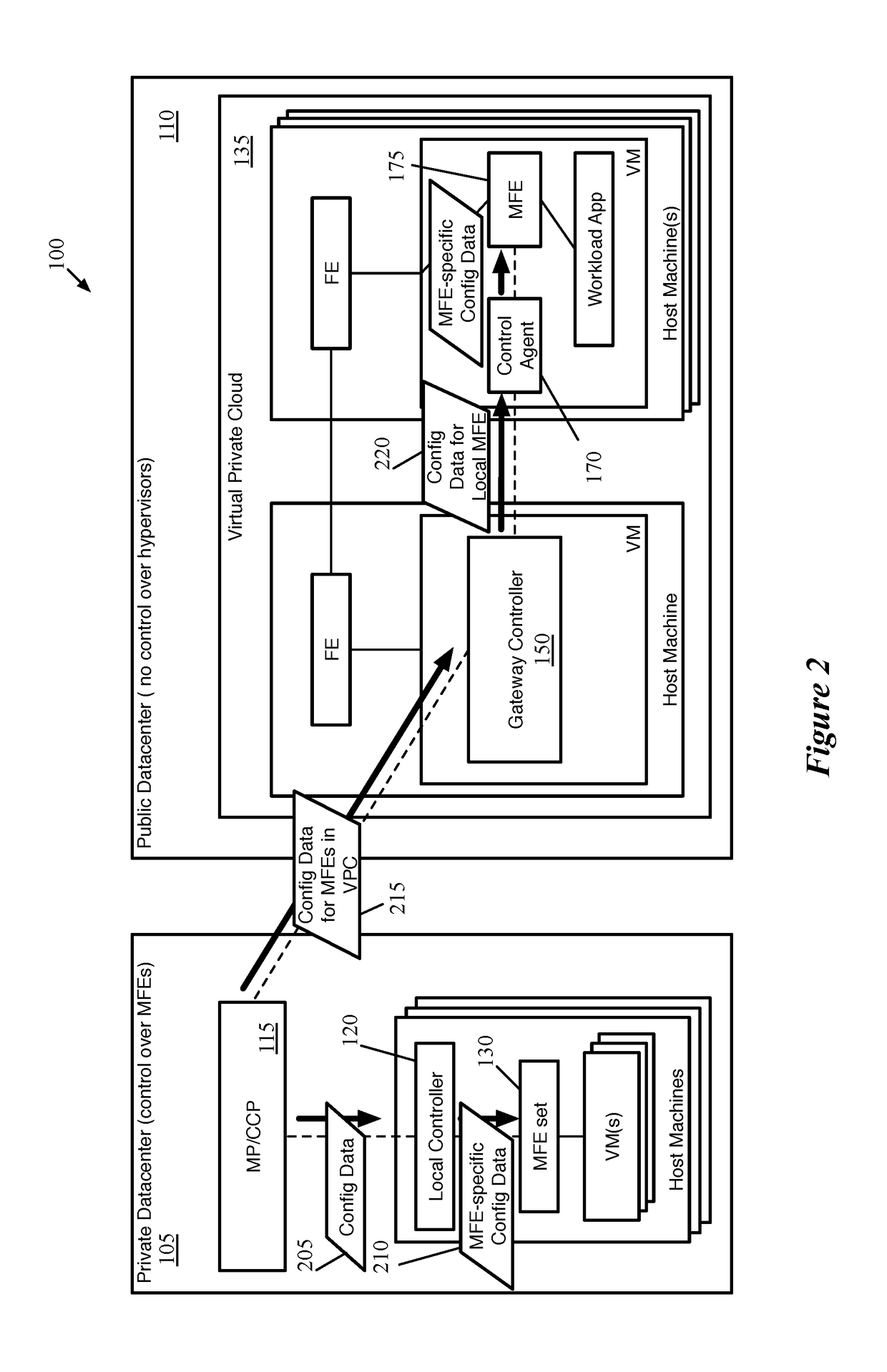
ActiveUS20180063087A1Digital computer detailsReliability/availability analysisData centerNetwork control
Some embodiments provide a method for a network controller that manages a logical network implemented in a datacenter having forwarding elements to which the network controller does not have access. The method identifies a data compute node (DCN) operating on a host machine in the datacenter, to attach to the logical network. The DCN has a network interface with an address provided by a datacenter management system. A workload application executes in a first namespace of the DCN. The method distributes configuration data for configuring a managed forwarding element (MFE) executing in a second namespace of the DCN to receive data packets sent from the application via an interface pairing between the first and second namespaces. The data packets sent by the application have the provided address as a source address when received by the MFE and are encapsulated by the MFE using the provided address as a source address.
Owner:NICIRA
Publish/subscribe mechanism for web services
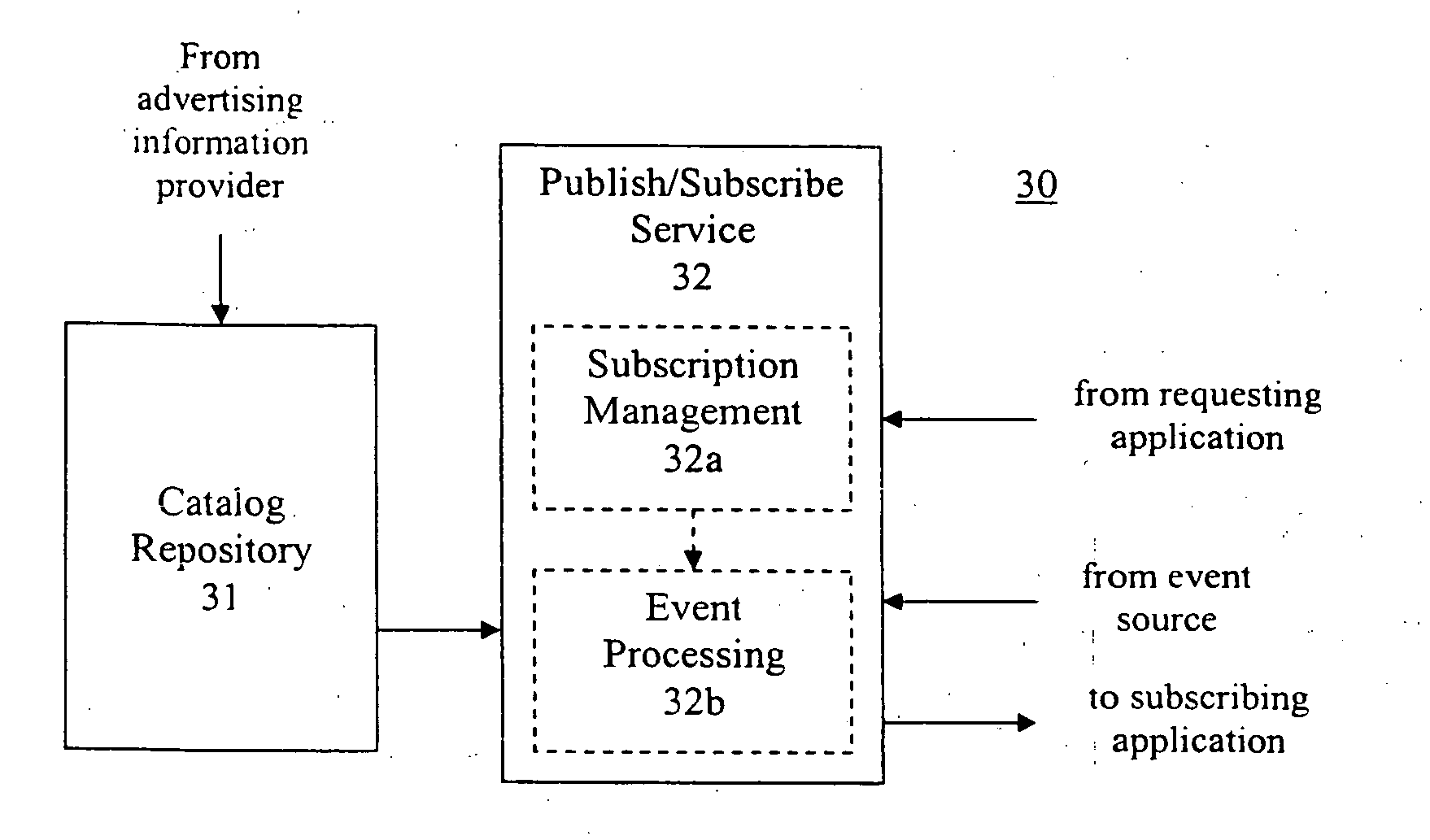
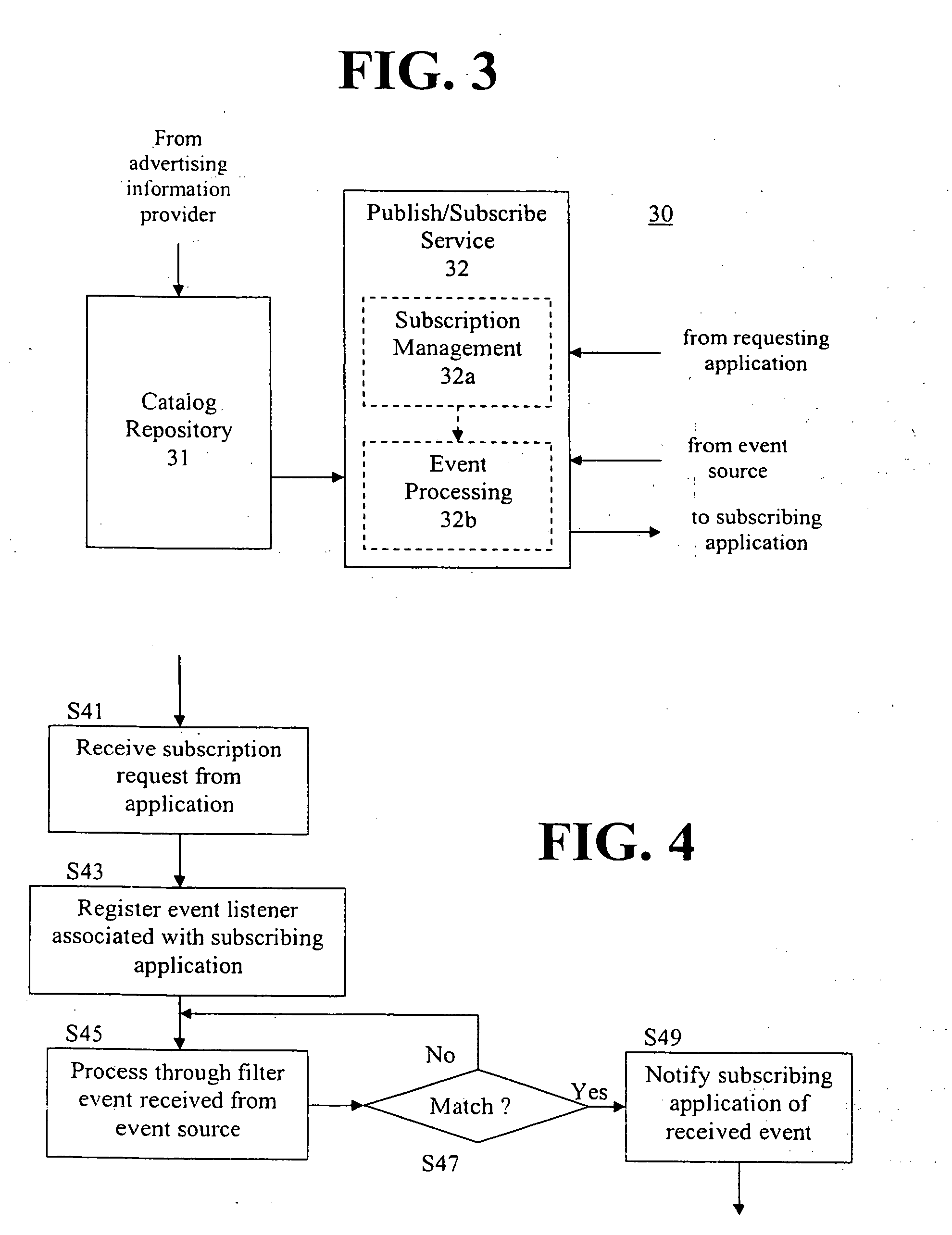
InactiveUS20060080120A1Special service provision for substationMultiprogramming arrangementsWeb serviceNamespace
A method for managing events in a web service environment is provided. A request for a subscription to desired events in an event class in an associated catalog namespace of a catalog repository is received from a subscribing application. The subscription request includes an event filter to select the desired events from a plurality of events described by the event class. An event which is received from a web evens source and described by the event class is processed through the event filter. If the received event matches the event filter, the received event is forwarded to the subscribing application through an event listener associated with the subscribing application.
Owner:COMP ASSOC THINK INC
Mapping XML schema components to qualified java components
InactiveUS7194485B2Data processing applicationsSemi-structured data mapping/conversionXML schemaComputer science
The present invention provides a method, apparatus, and computer instructions for mapping and labeling XML schema elements and types. In an exemplary embodiment, each XML schema element and type is uniquely labeled, using distinguishing parameters such as namespace to create name parts like a Hashing code and suffixes in order to achieve unique mapping. The parameters selected are predetermined in order to achieve naming that remains distinct across successive consumptions of a schema. The selection disclosed accomplishes unique labeling, while also permitting one to still adhere to the strict naming standards of the target language (e.g., Java). As a result, schema components belonging to multiple namespaces can be mapped to Java components belonging to a single package.
Owner:INT BUSINESS MASCH CORP
Multi-level cache architecture and cache management method for peer-to-peer name resolution protocol
InactiveUS6912622B2Efficient solutionLess resourcesMemory adressing/allocation/relocationMultiple digital computer combinationsGranularityParallel computing
A peer-to-peer cache architecture stores peer address certificates in different cache segments according to the number of IDs being stored and their relative distance in the peer name space. The cache instantiates regions of decreased range and increased granularity as additional information from close peers is learned. In a large peer cloud where the number of instantiated IDs is not known, each succeeding cache region covers one tenth of the preceding cache region. For peers with multiple IDs registered locally, the segmented cache of the present invention combines overlapping segments of the same granularity to eliminate the duplication of information that would otherwise occur. A cache tree, an instantiated segment tree, and an uninstantiated segment tree are arranged in red-black trees to simplify the search and proper placement and instantiation of information.
Owner:MICROSOFT TECH LICENSING LLC
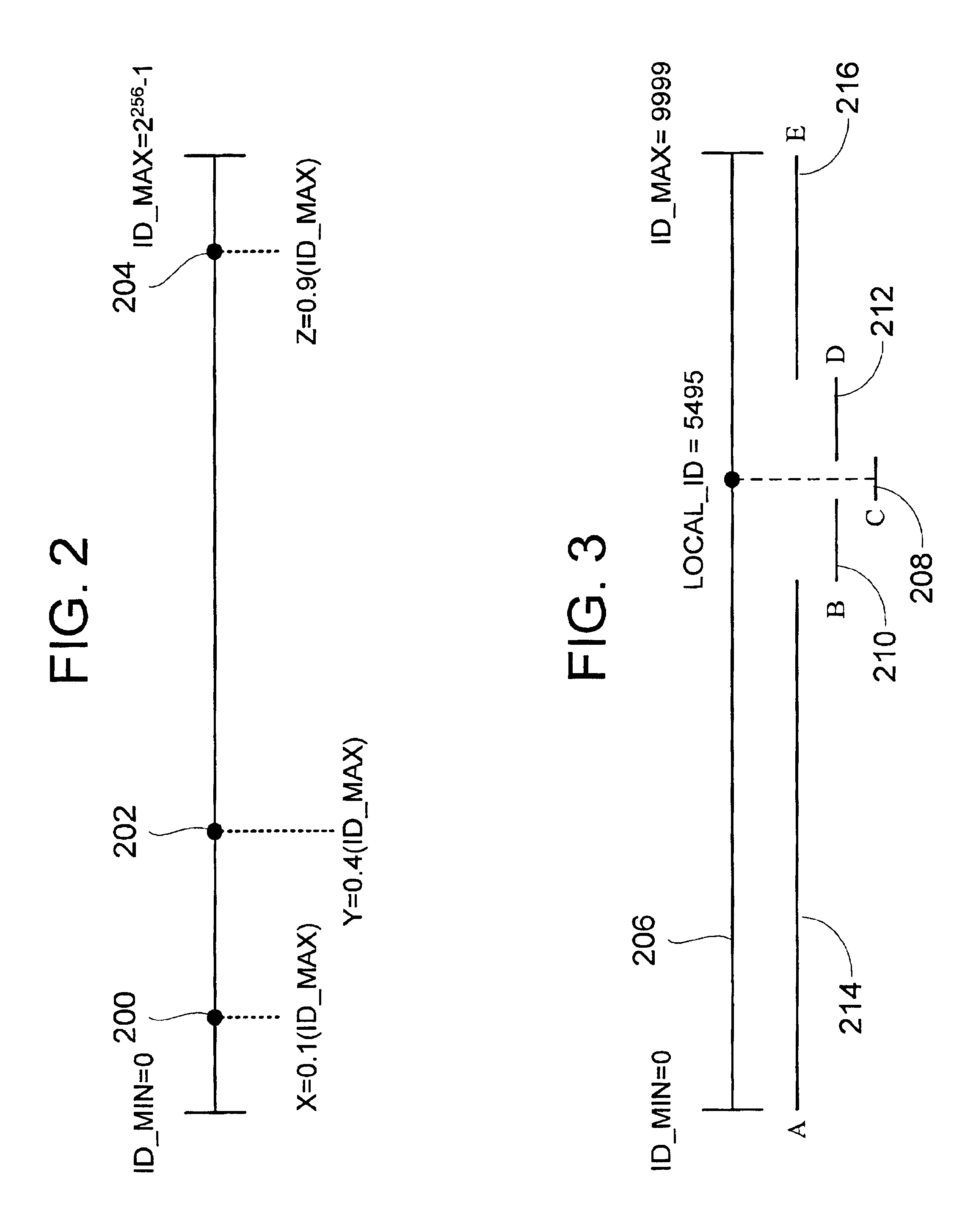
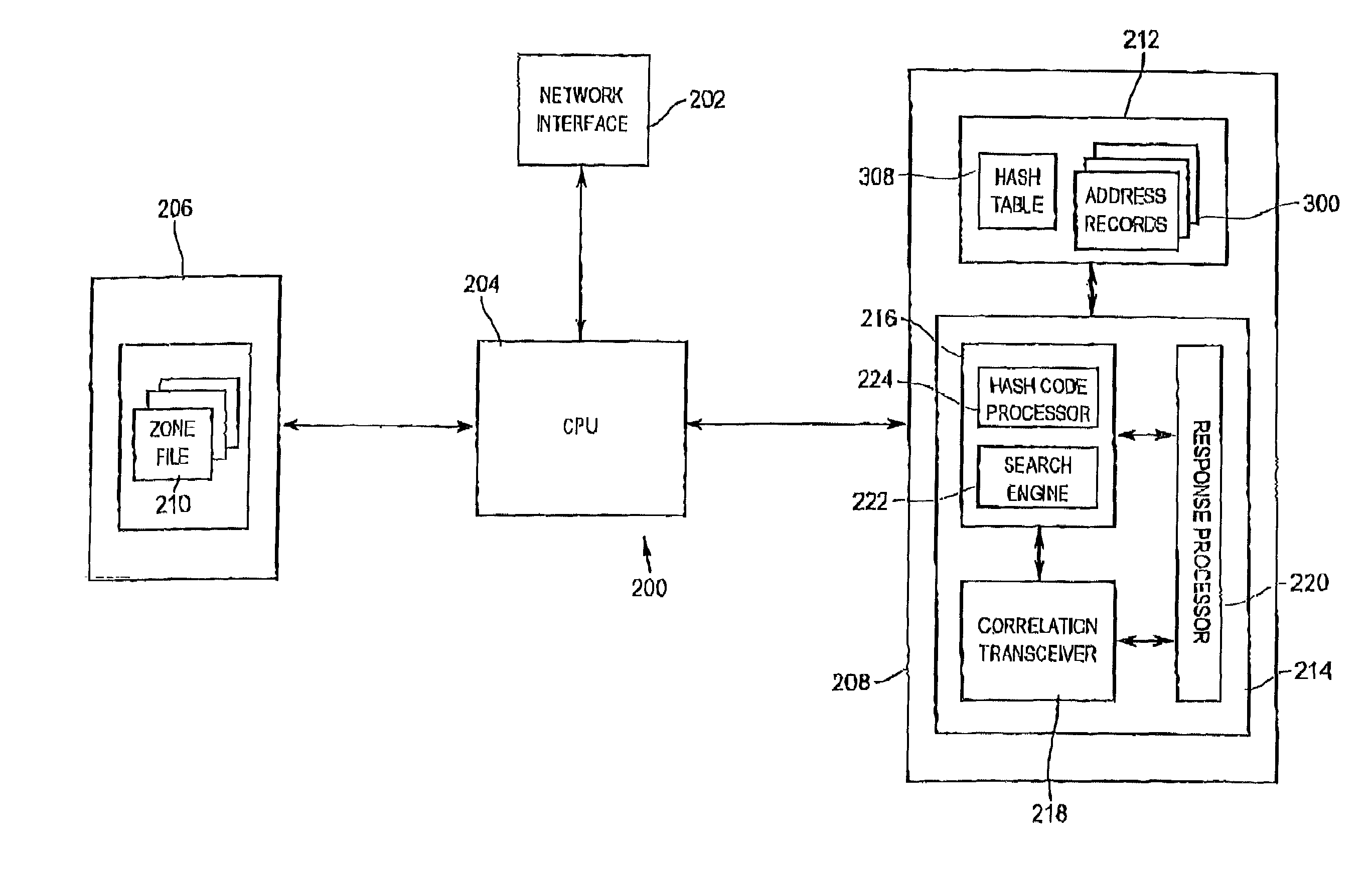
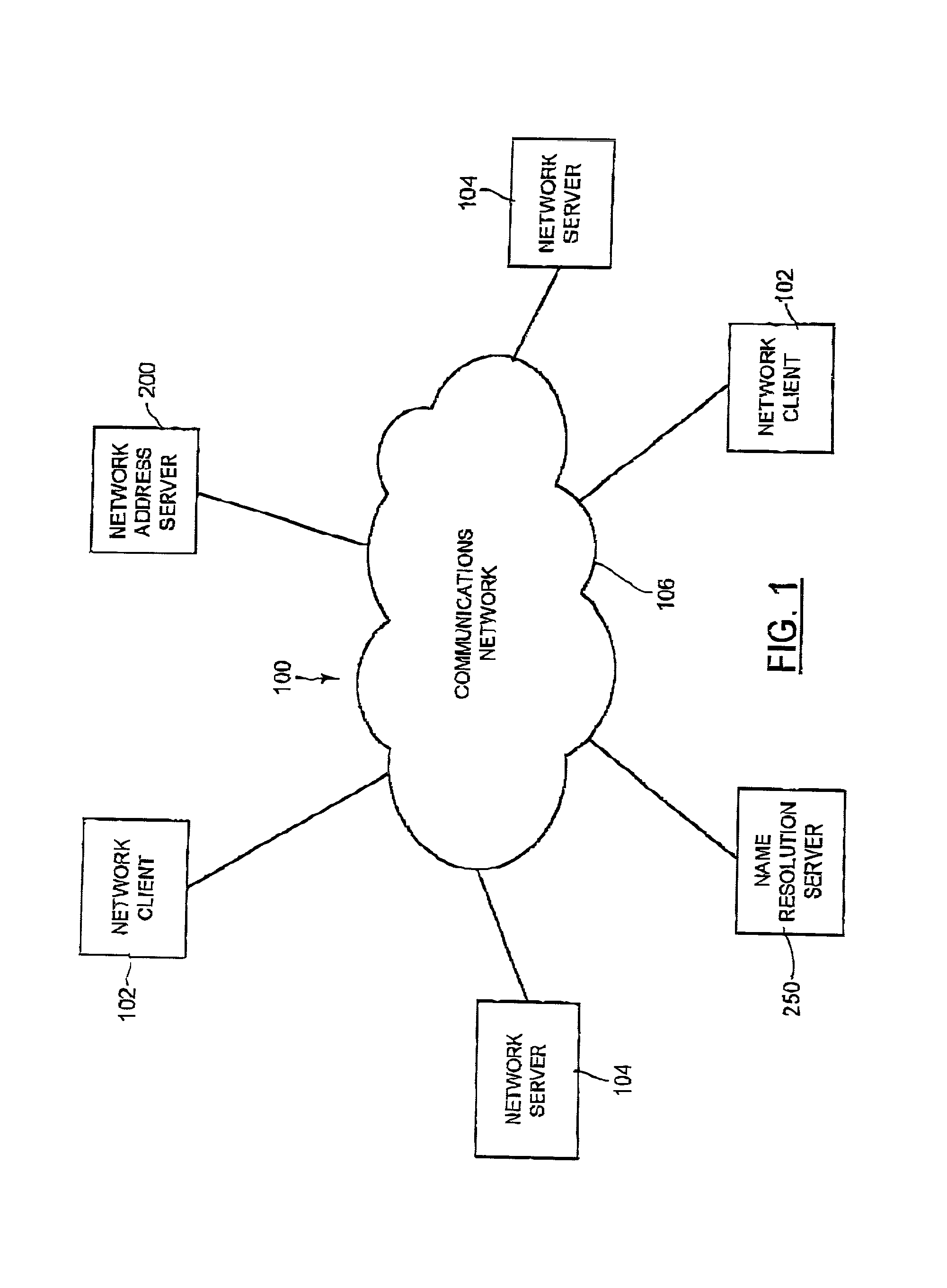
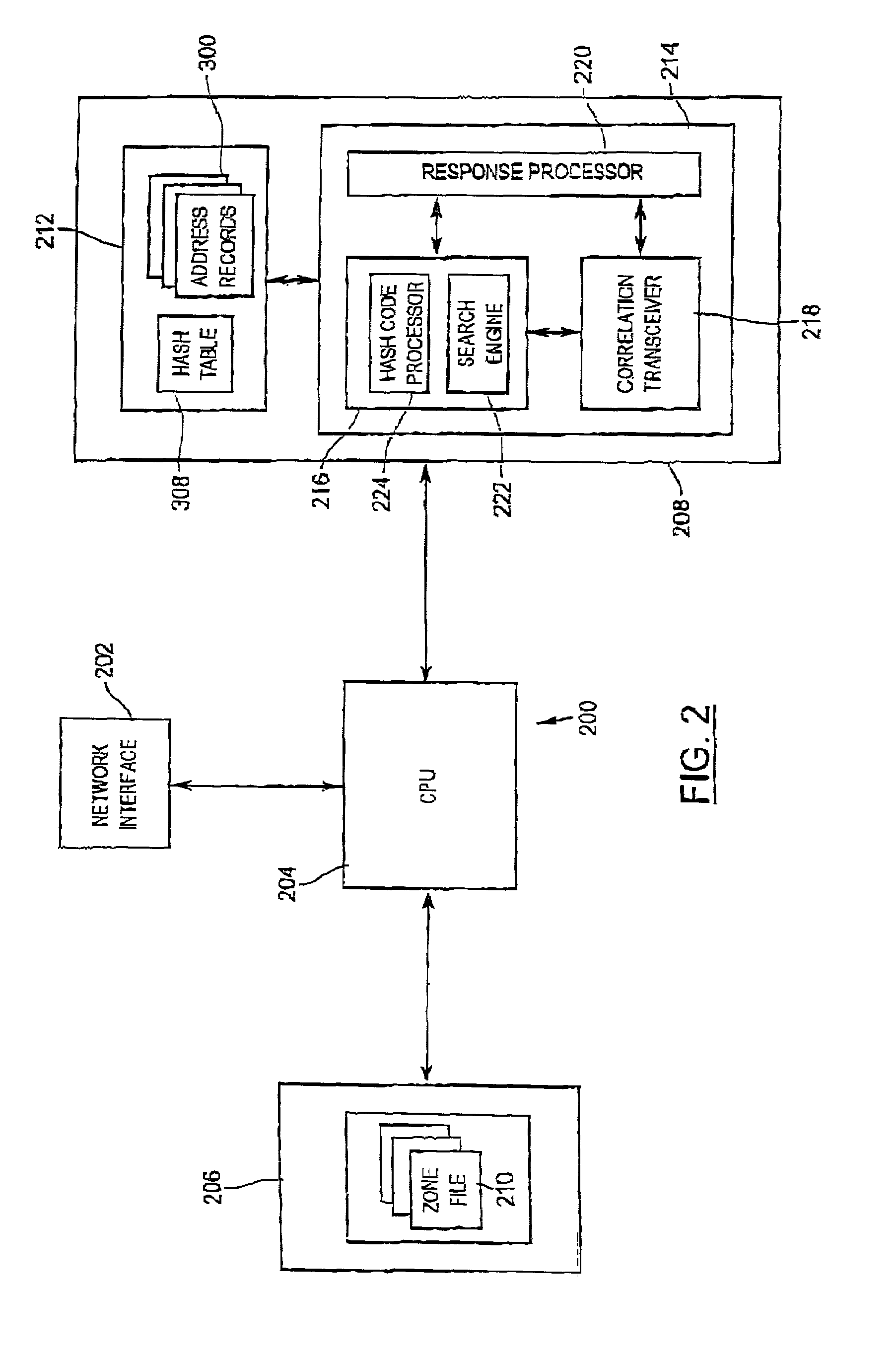
Network address server
InactiveUS7280999B2Data processing applicationsDigital data processing detailsUnique local addressTransceiver
A network address server is configured to resolve a target network address name label with a network address, with the target address name label defining a branch of one level of a multi-level network address name space. The network address server is one of a plurality of network address servers each being uniquely associated with a respective region of the address name space level. The network server includes an address name database, and an address name processor in communication with the address name database for providing a response to a query for the network address corresponding to the target address name label. The address name database includes a number of database records, each identifying a unique address name label and a network address uniquely associated with the address name label. The address name processor includes a correlation processor, a correlation transceiver in communication with the correlation processor, and a response processor in communication with the correlation processor and the correlation transceiver. The correlation processor is configured to determine a correlation between the target address name label and the respective unique address name region. The correlation transceiver is configured to provide the other network address servers with a respective indication of the determined correlation and for receiving a corresponding correlation indication from at least one of the other network address servers. The response processor is configured to provide a response to the query in accordance with the correlation indications.
Owner:AFILIAS LTD
Mechanism for downloading software components from a remote source for use by a local software application
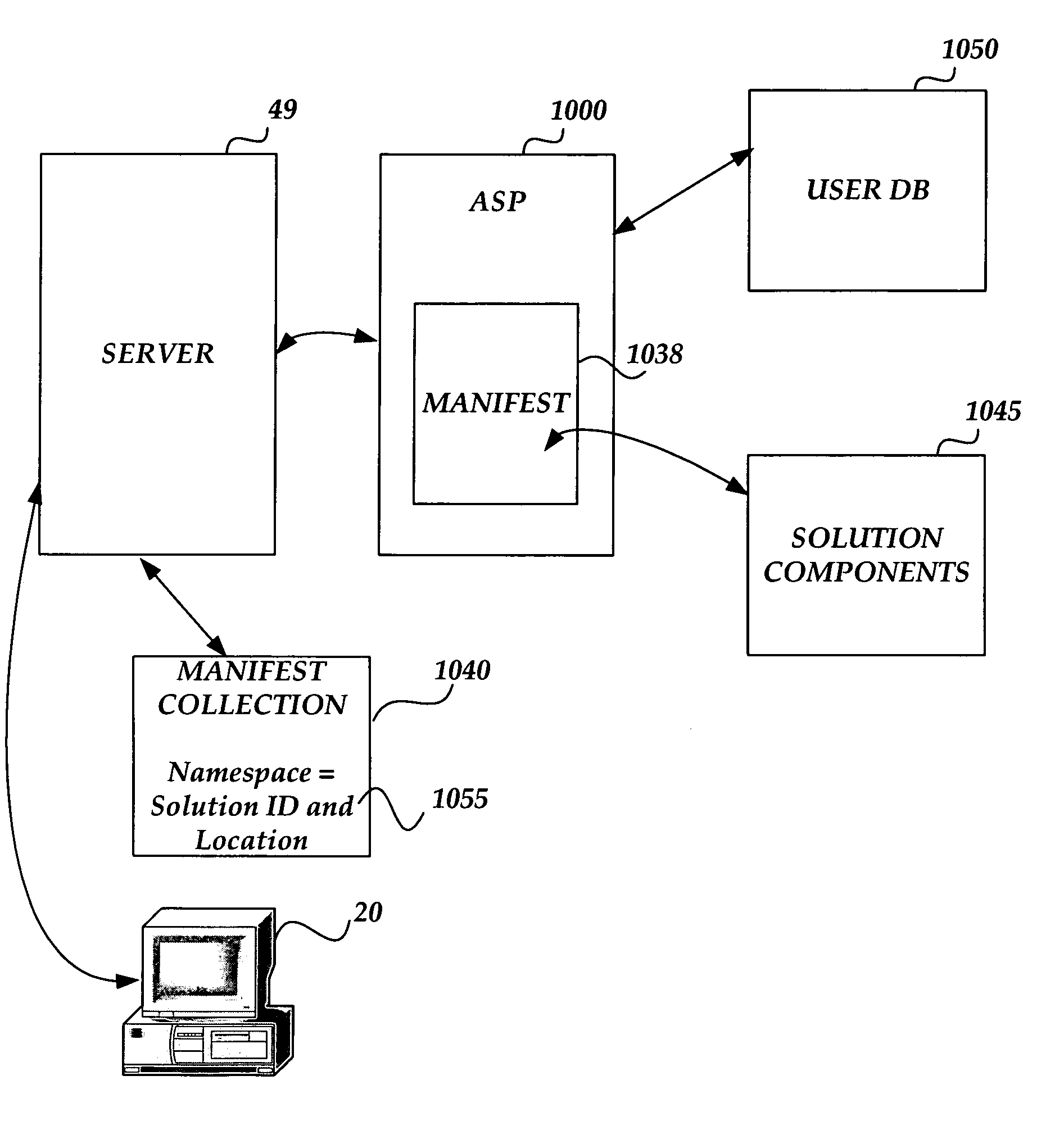
InactiveUS7827546B1Specific program execution arrangementsMemory systemsJob descriptionDocumentation procedure
Methods and systems are provided for dynamically configuring document solutions and for obtaining desired or required components of such document solutions for use with computer-generated documents. If a document is associated with a document solution, a request for components of the solution is sent to a manifest of document solutions. Identification of a user of the document is also passed to the manifest. At the manifest, identification information for the user is used to query a user database to determine a profile of the user such as the user's job description, location, security clearance, and the like. Based on the user's profile, the document solution is configured dynamically to include solution components most helpful to the particular user. A manifest collection is provided for serving as a repository of document solution location information for many different namespaces (schemas) that may be associated with one or more user documents.
Owner:MICROSOFT TECH LICENSING LLC
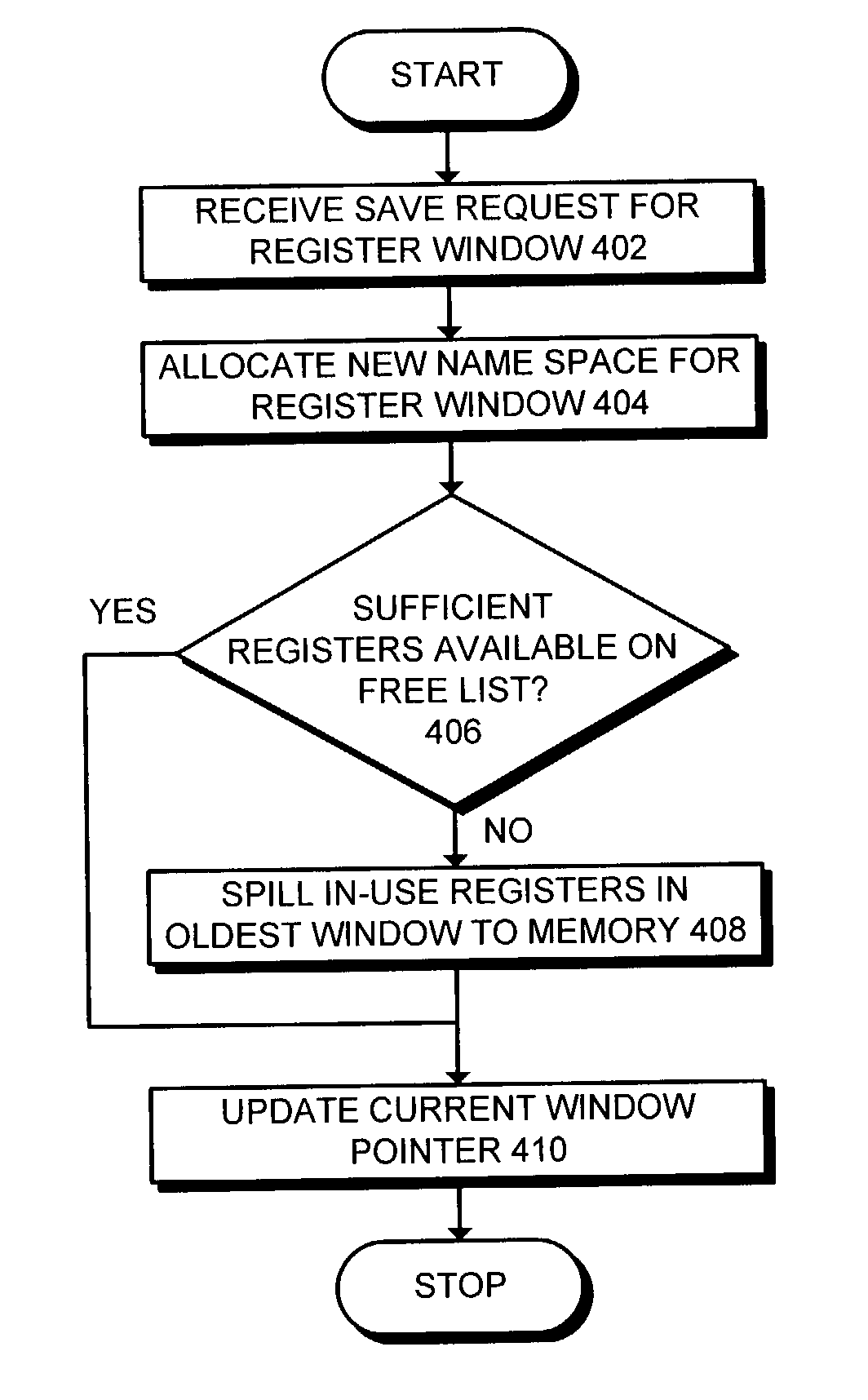
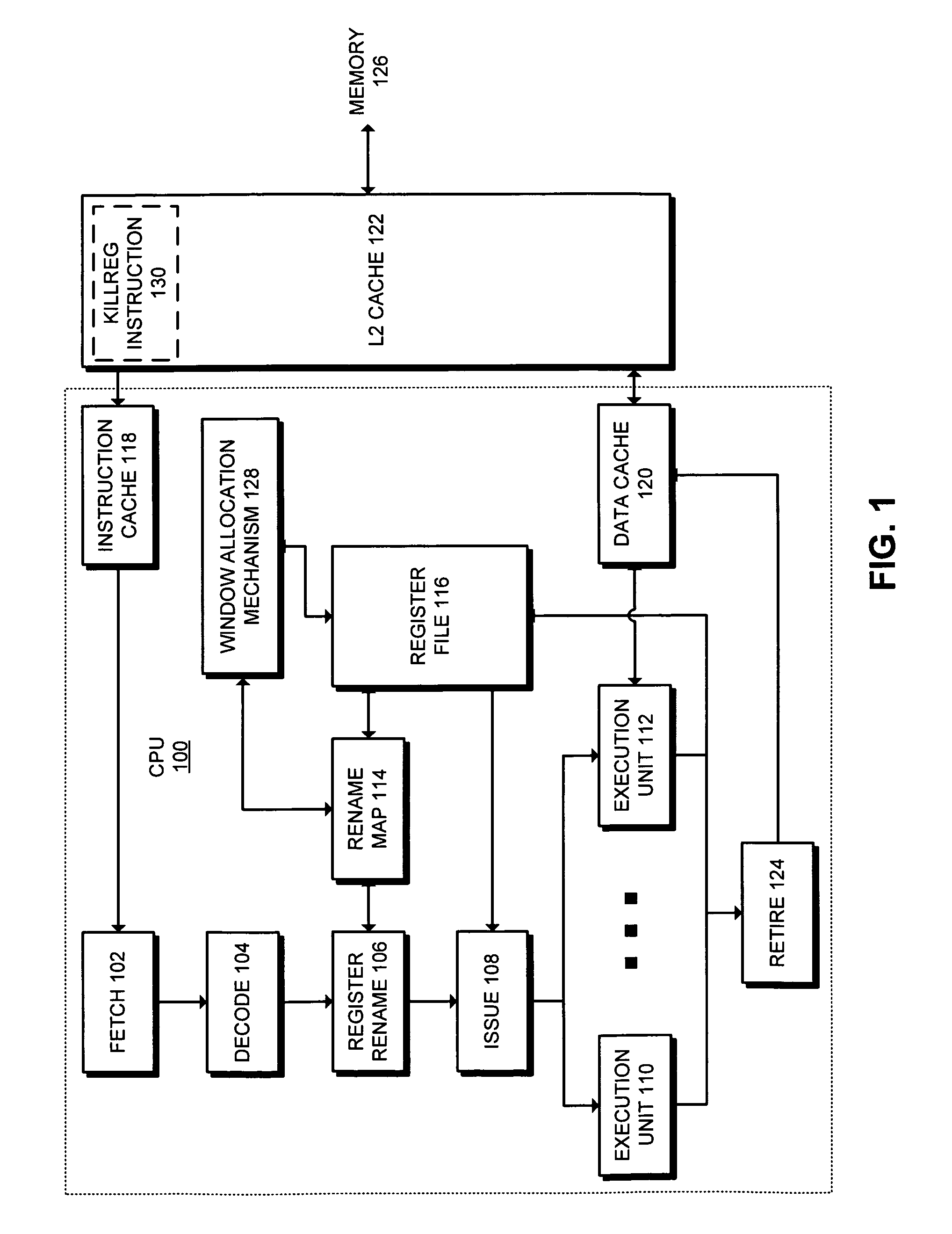
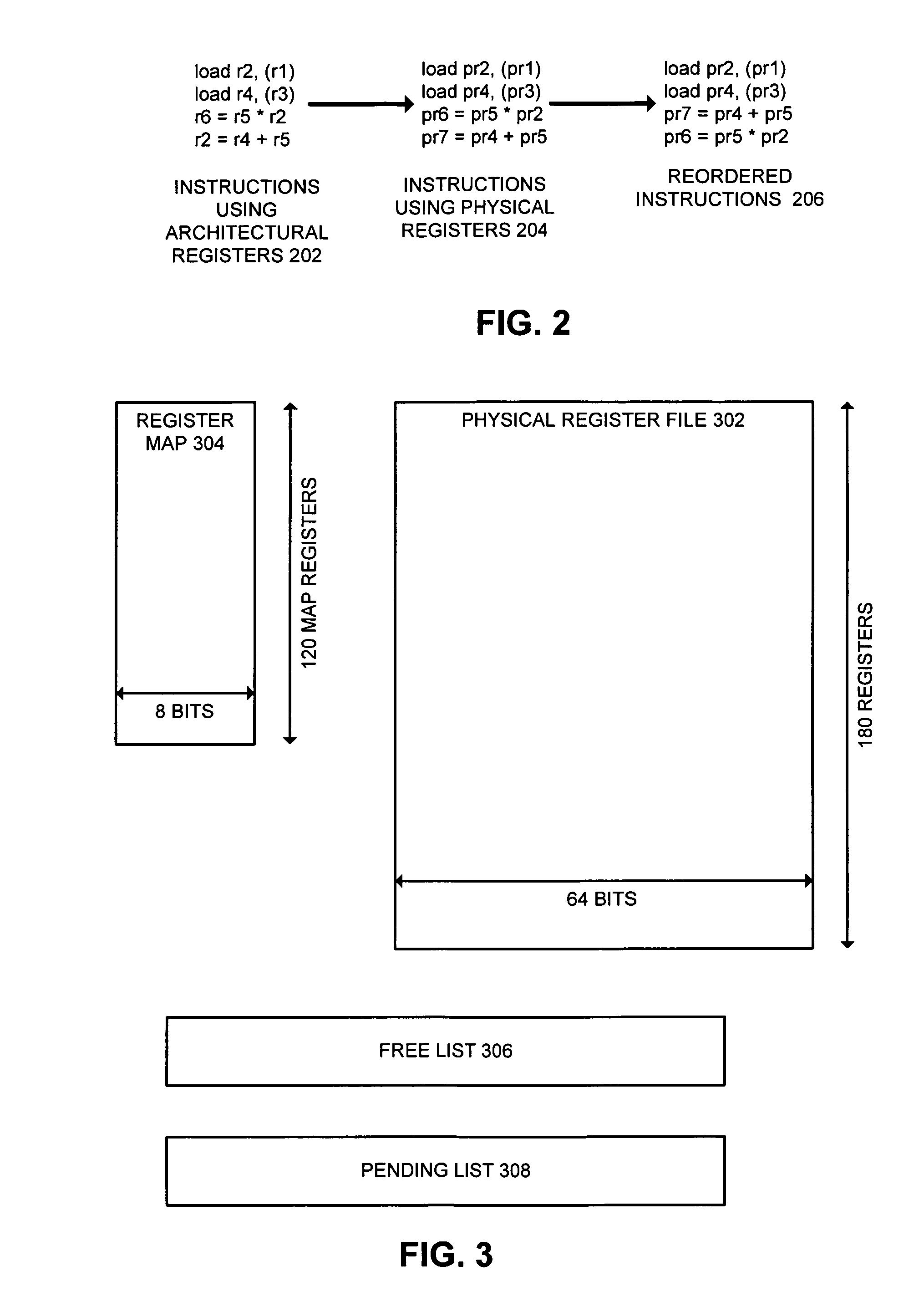
Method and apparatus for dynamically allocating registers in a windowed architecture
ActiveUS7127592B2Digital computer detailsConcurrent instruction executionRegister windowRegister file
One embodiment of the present invention provides a system that dynamically allocates physical registers in a windowed processor architecture. The system includes a physical register file and a register map that maps architectural registers defined within an executing program to physical registers within the physical register file. The system also includes a window allocation mechanism that allocates a new name space for a register window without allocating physical registers for the register window, thereby allowing the physical registers to be dynamically allocated as needed instead of being allocated at window initialization time.
Owner:ORACLE INT CORP
Uniform name space referrals with location independence
InactiveUS20040024786A1Digital data processing detailsMultiple digital computer combinationsSymbolic linkNetwork File System
Improved techniques are disclosed for accessing content in file systems, allowing file system clients to realize advantages of file system referrals even though a file access protocol used by the client is not specifically adapted for referral objects. (For example, the client may have a legacy file system protocol or a proprietary file system protocol which does not support referrals.) These advantages include a uniform name space view of content in a network file system, and an ability to locate content in a (nearly) seamless and transparent manner, even though the content may be dynamically moved from one location to another or replicated in different locations. A file system server returns a symbolic link in place of a referral, and an automated file mounting process on the client is leveraged to access the content using the link. Built-in crash recovery techniques of the file system client are leveraged to access moved content.
Owner:IBM CORP
Method, system, and computer useable medium to facilitate name preservation across an unrestricted set of TLDS
InactiveUS20050210149A1Easy to storeInexpensive and dependable and fully effectiveMultiple digital computer combinationsTransmissionThe InternetPeriodic fee
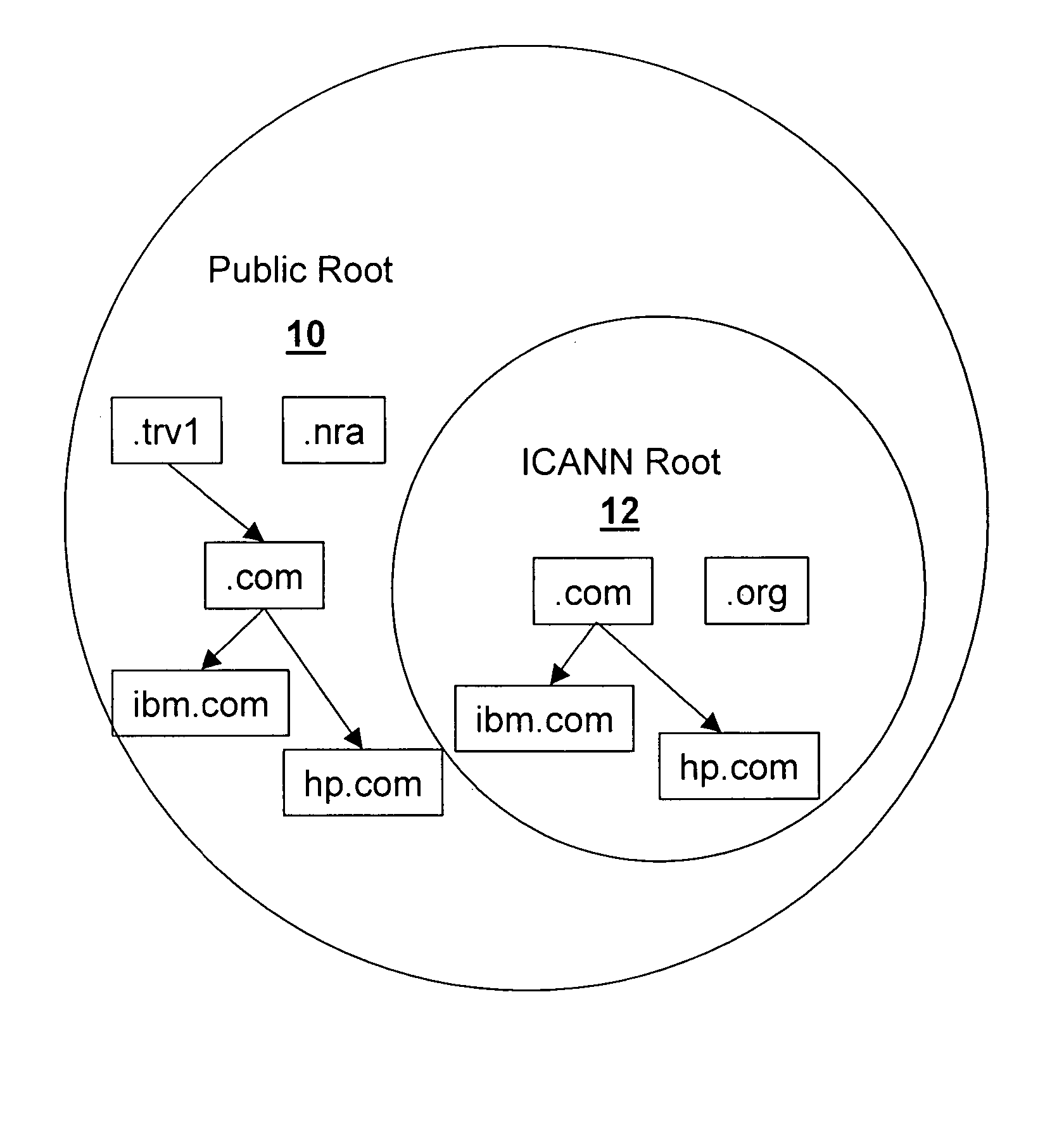
A method, system, and / or computer useable medium to facilitate name preservation across an unrestricted set of TLDs. TOP LEVEL DOMAIN TOPOLOGY (TLDT) software is executed in a TLDT system. A register is chosen to register a predetermined secondary level domain (SLD) name / inclusive name space for a particular TLD. Data is retrieved for a desired SLD name to register the SLD name in association with at least one TLD in at least one of a Public Root and an Internet Corporation for assigned Names and Numbers (ICANN) Root. A search is conducted of at least one of a Public Root and an ICANN Root and it is determined whether the desired SLD is associated with any TLDs that exist. The desired SLD is registered with all of those TLDs if the user agrees to pay the periodic fee.
Owner:KIMBALL JORDAN L
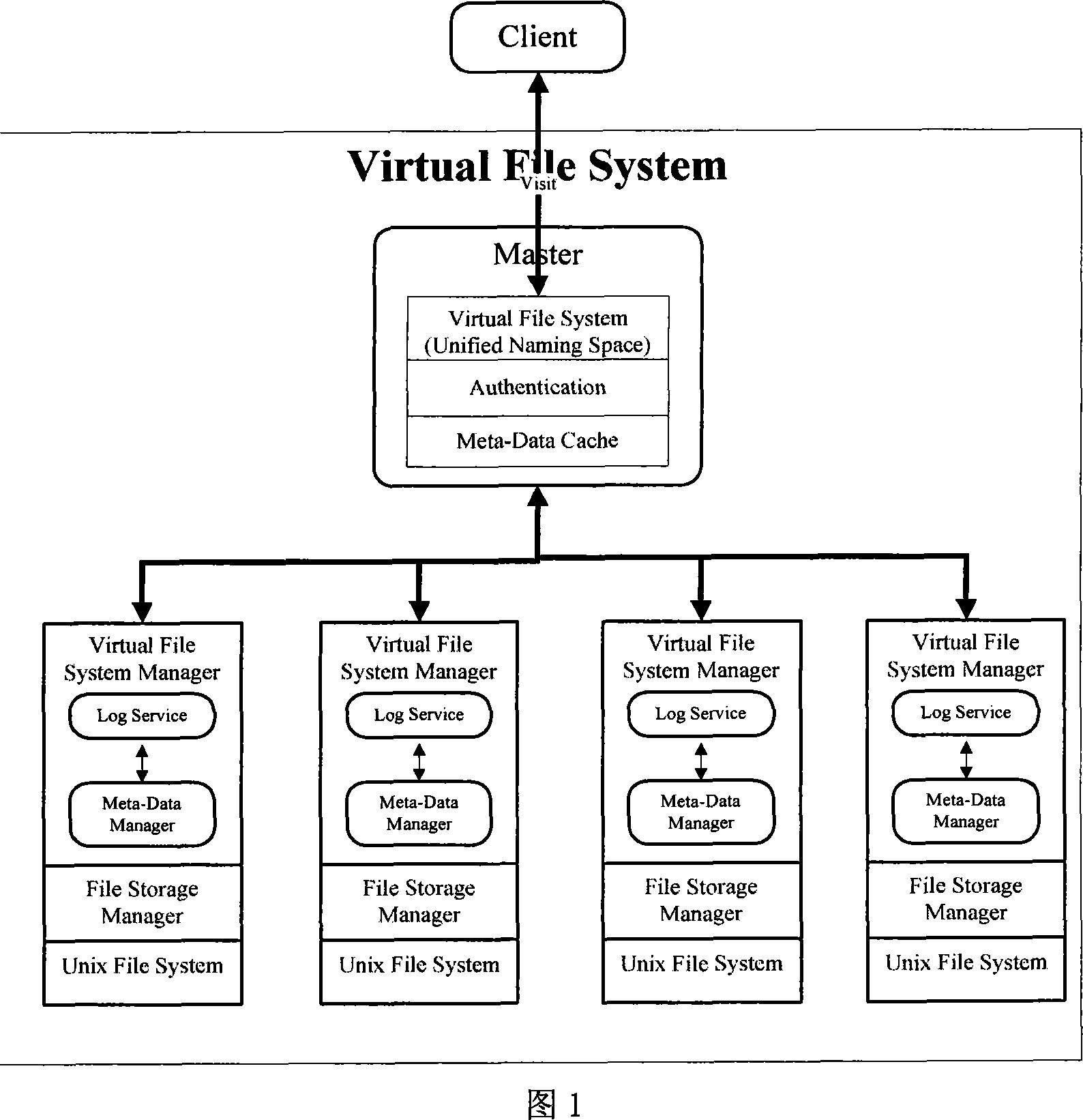
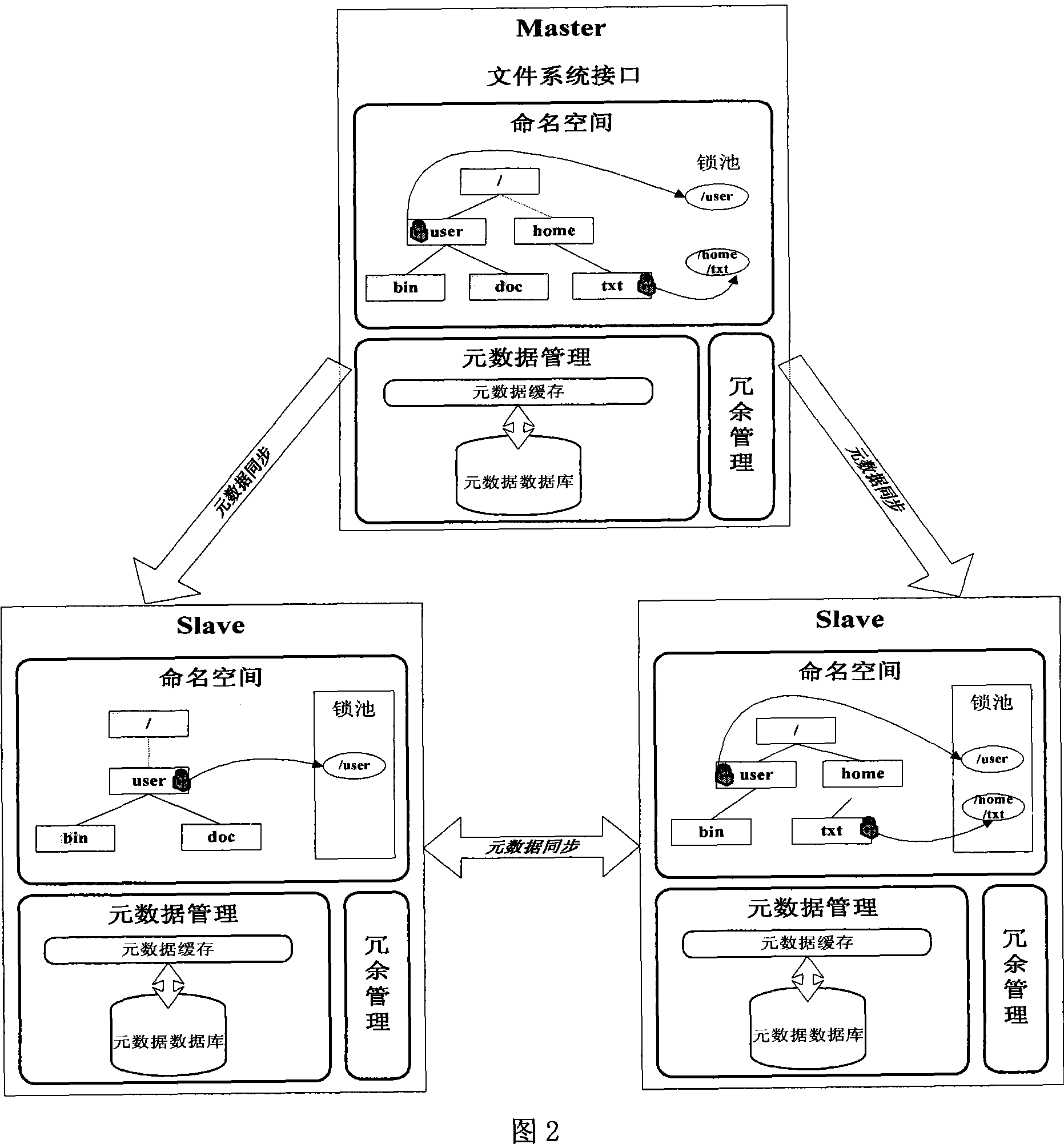
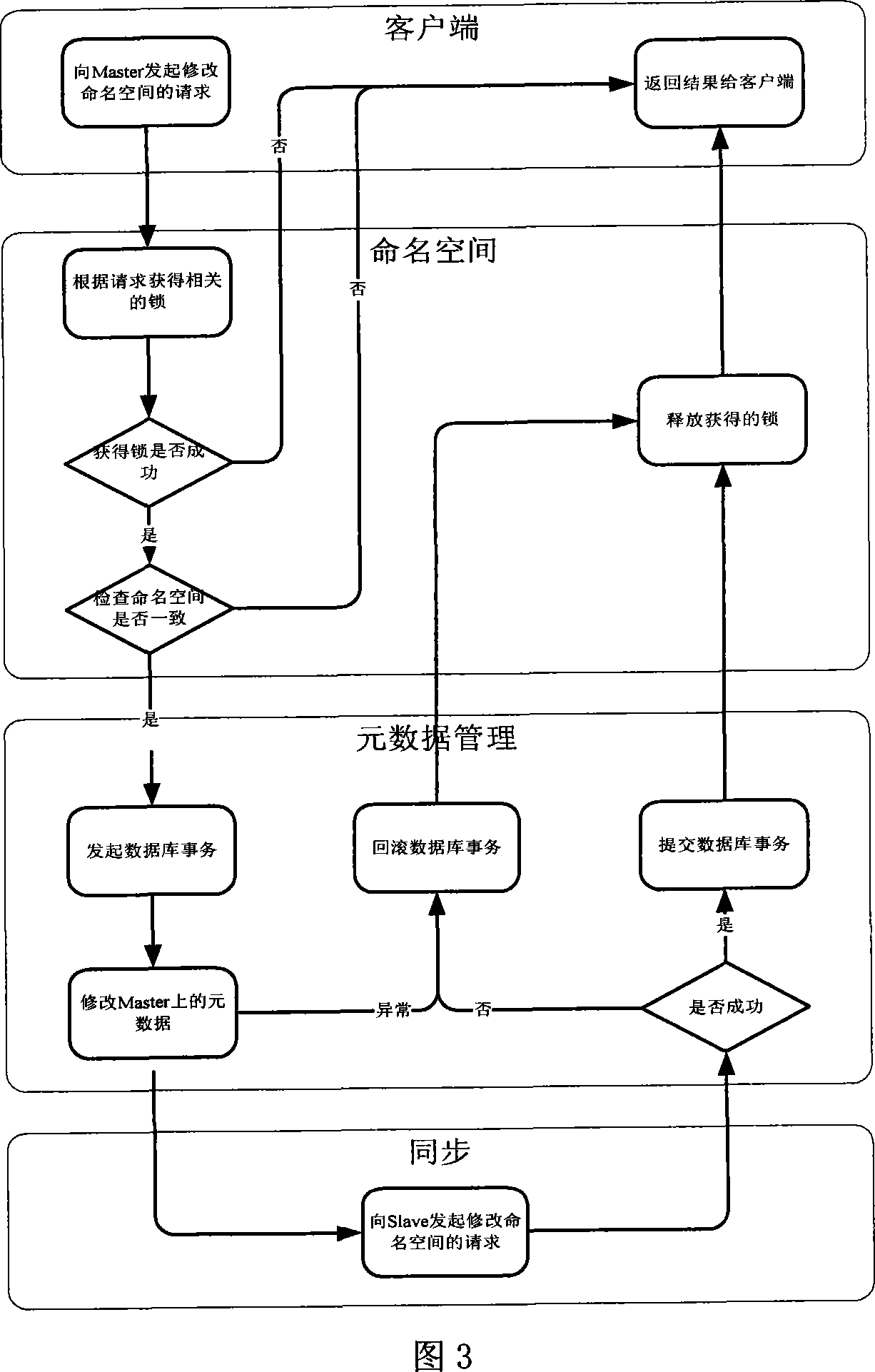
Distribution type file system dummy directory and name space implementing method
InactiveCN101187930AEasy to operateGuaranteed correctnessMultiprogramming arrangementsSpecial data processing applicationsOperational systemVirtual file system
The invention relates to a distributed file system virtual catalog and the implementation of a naming space. A primary server creates a uniform virtual catalog in the whole storage network, takes the concrete information of each file in store, and makes a mapping for the actual storage position of the file and the address in the virtual catalog, as well as shields the difference among hardware, an operation system and a file storage structure; in view of a client, the client does not know where the file is stored, the file in the whole system is seen to be stored in a uniform way without any difference from a common file system, namely, the system is a virtual file system; a secondary server stores the relevant information of the file stored on the secondary server, thereby forming an own file system. The invention has the advantages that the operation of the user is convenient through the system virtual catalog, and the file storage is transparent for the user. The consistency when a plurality of users access the file together is ensured through the chain-type operation of the naming space, thereby solving the problem of name collision, and obtaining good effect.
Owner:ZHEJIANG UNIV
Bridging human machine interface technologies in a process automation and information management environment
An industrial control and automation human machine interface (HMI) technology migration scheme is embodied in object management, graphics technologies, and namespace handlers for HMI applications. Newfeatures of the second technology are supported for HMI graphics while retaining the functionality of systems embodying the first technology, including the ability to export to the first technology,graphics developed and / or managed in the second technology. A combination of facilities is provided to accommodate both the first and second HMI graphics technologies: name space integration, graphicsrendering integration, and HMI application management integration.
Owner:AVEVA SOFTWARE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com