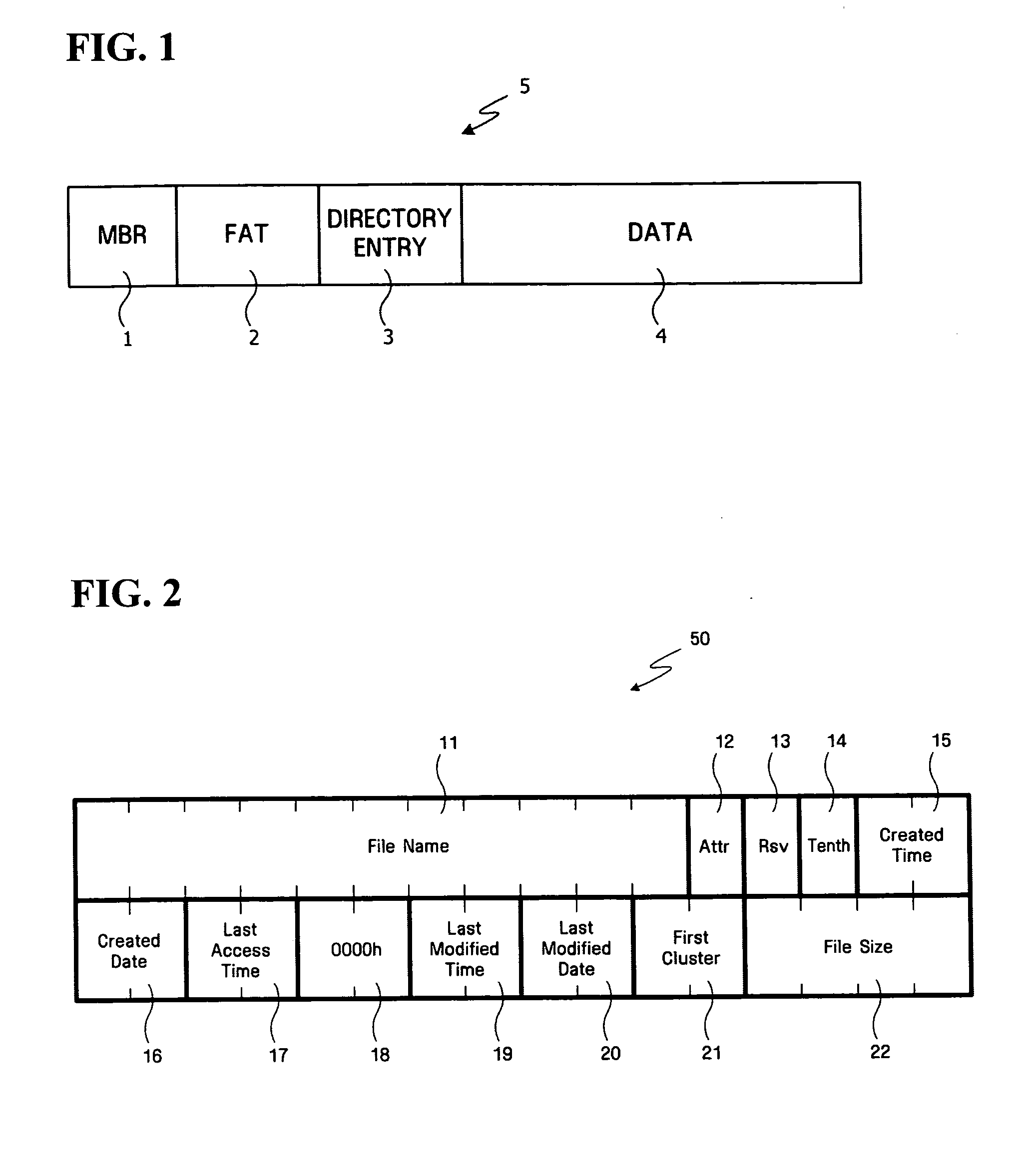
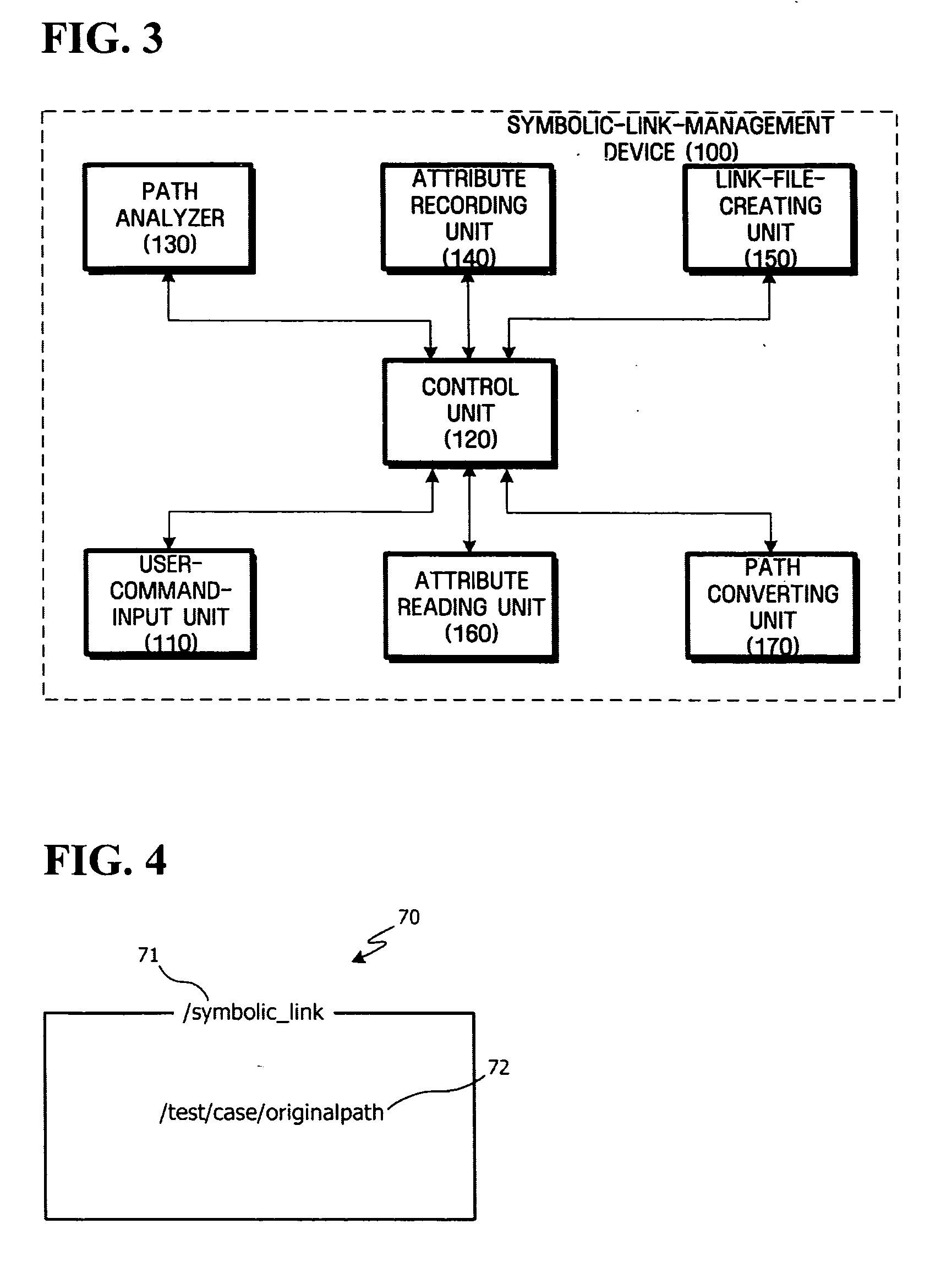
Patents
Literature
91 results about "Symbolic link" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
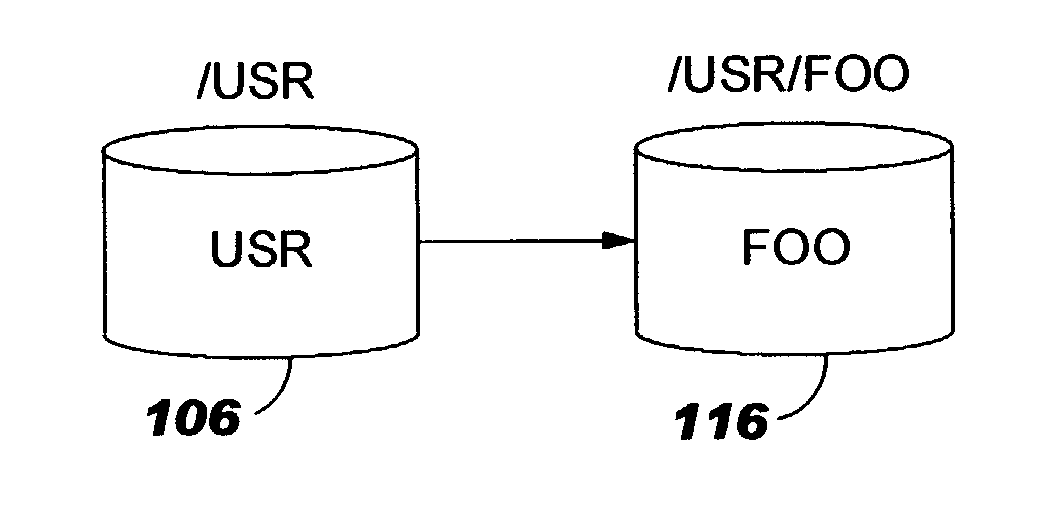
In computing, a symbolic link (also symlink or soft link) is a term for any file that contains a reference to another file or directory in the form of an absolute or relative path and that affects pathname resolution.
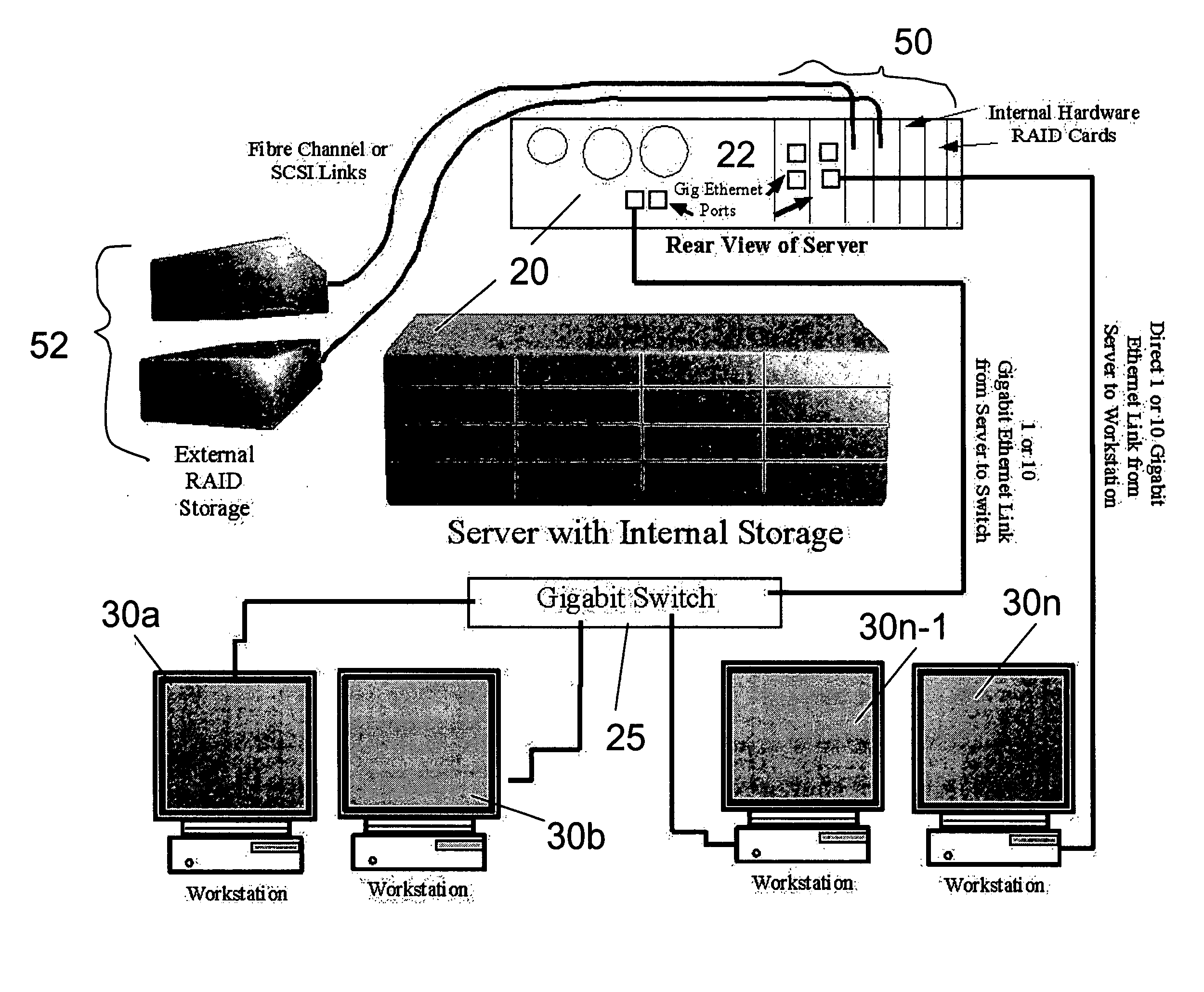
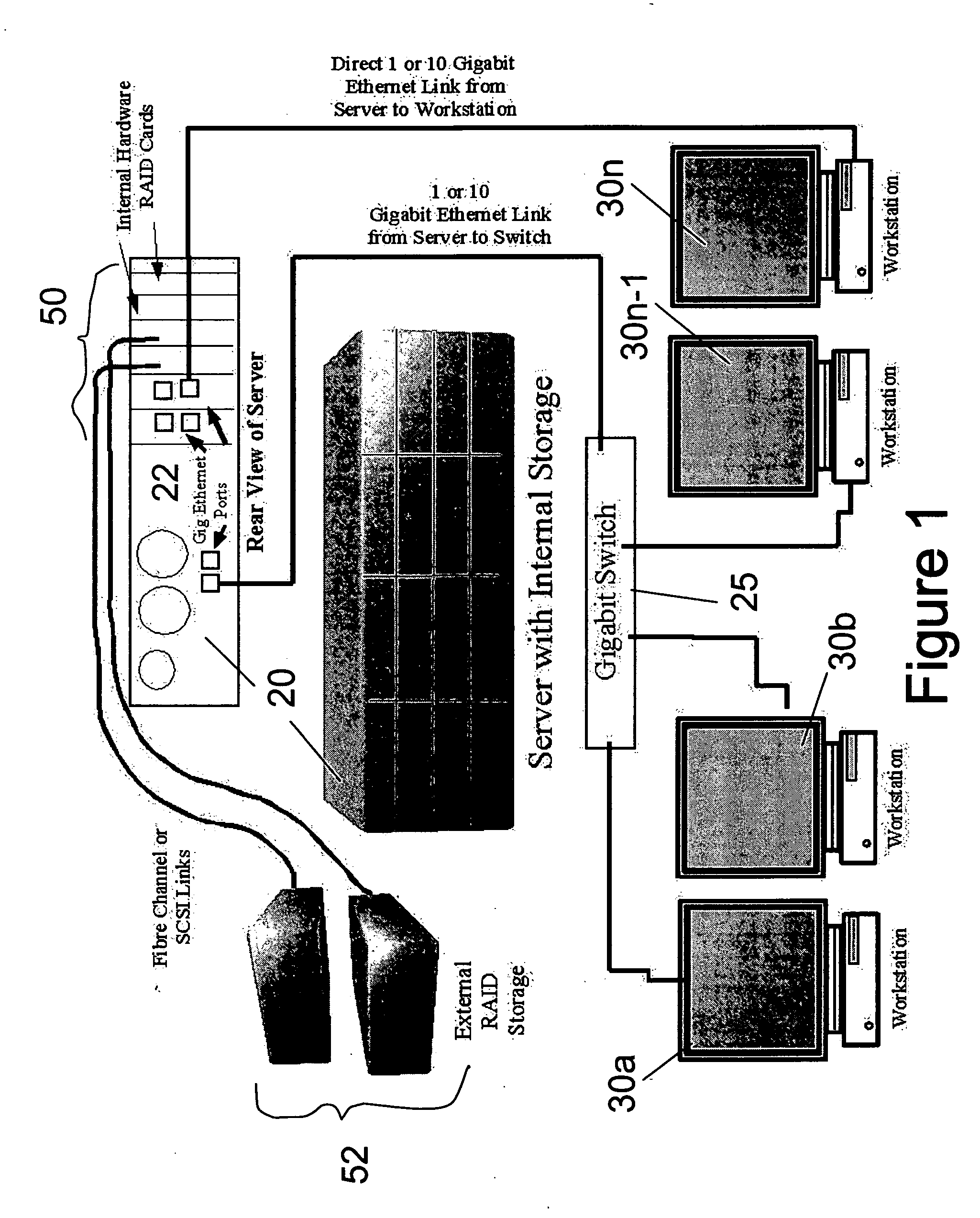
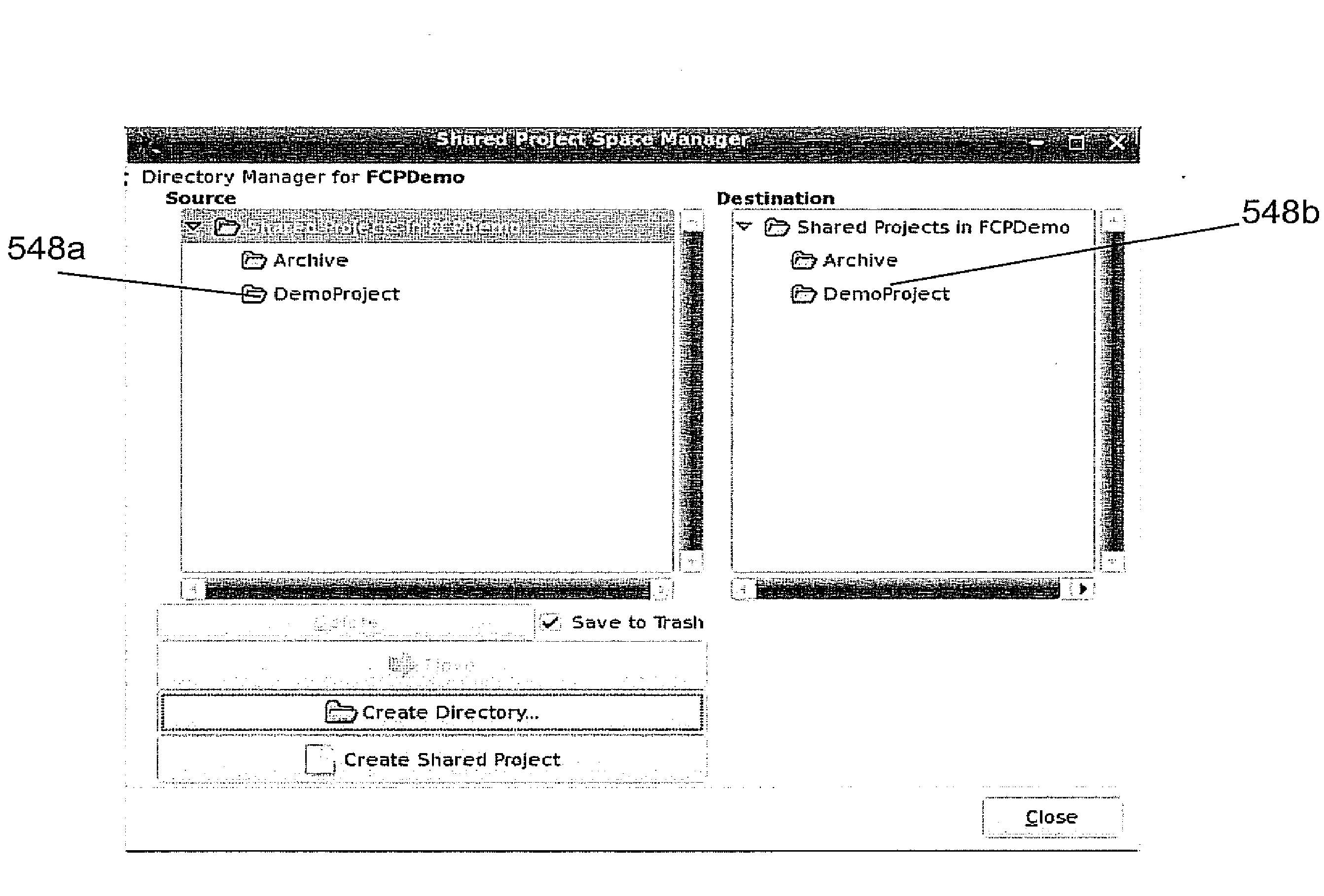
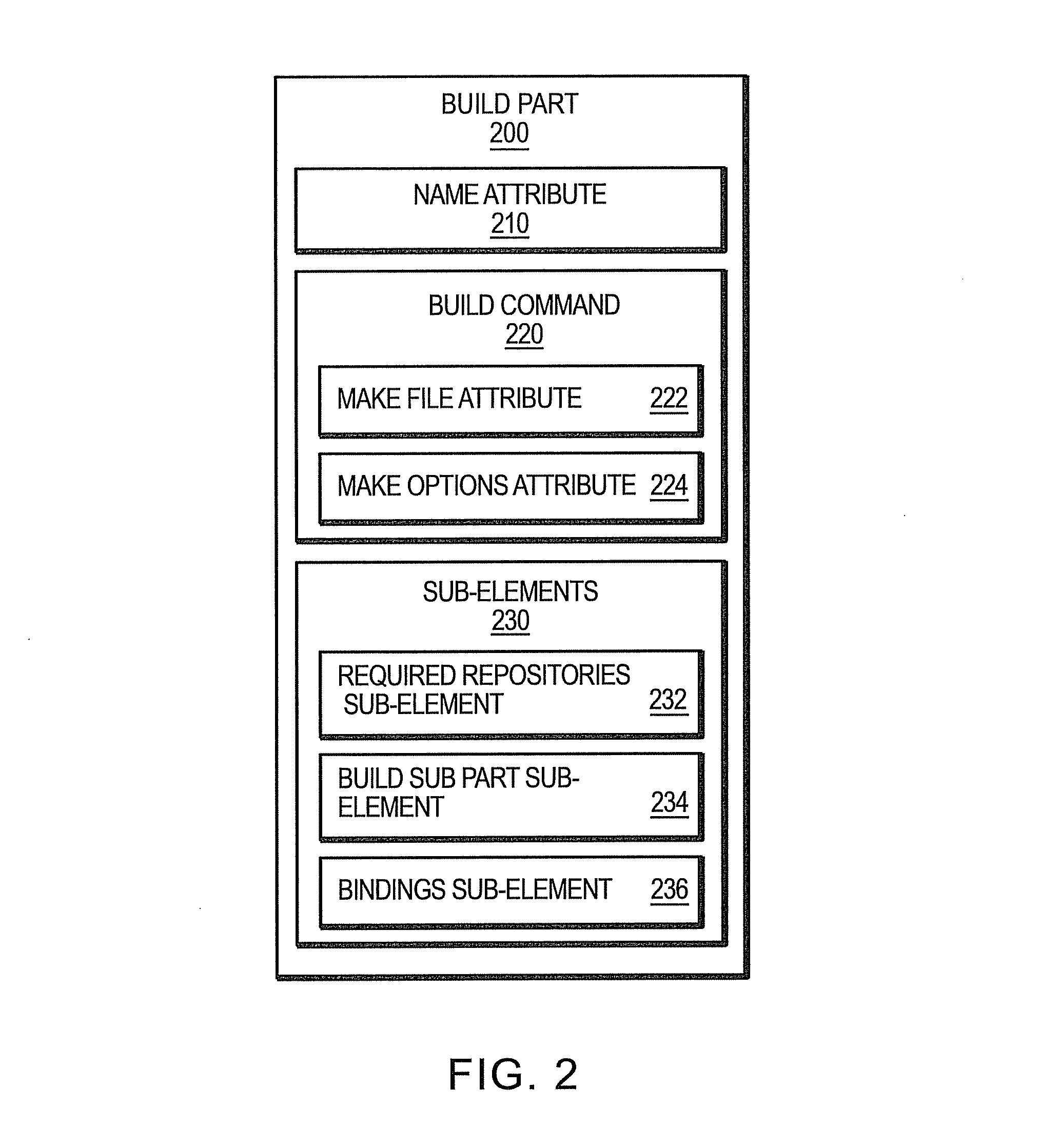
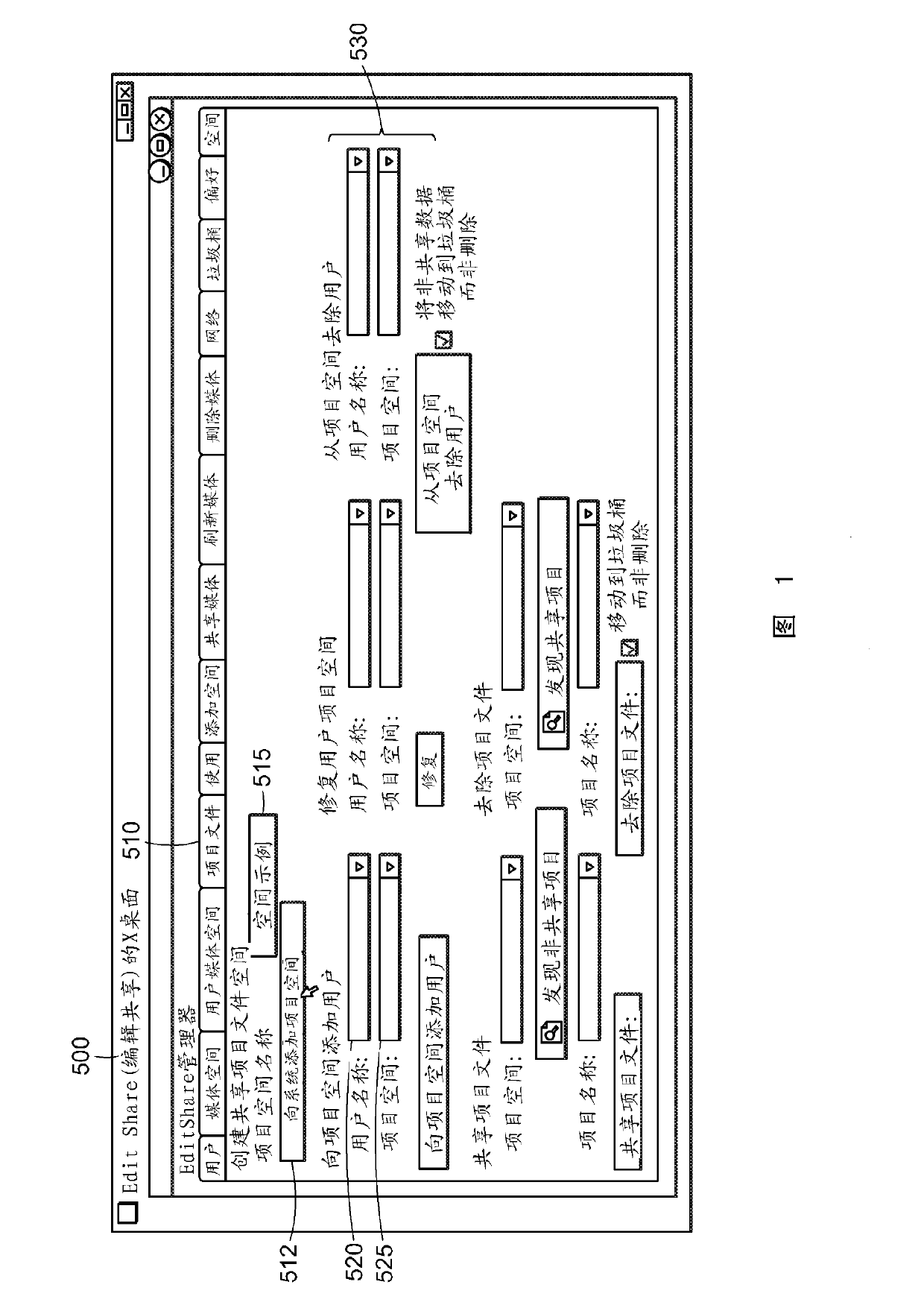
Novel media file access and storage solution for multi-workstation/multi-platform non-linear video editing systems
ActiveUS20060184673A1Digital data processing detailsElectronic editing digitised analogue information signalsSymbolic linkMulti platform
Owner:EDITSHARE LLC
Dynamic link
InactiveUS6856989B1Data processing applicationsDigital data processing detailsWeb serviceSymbolic link
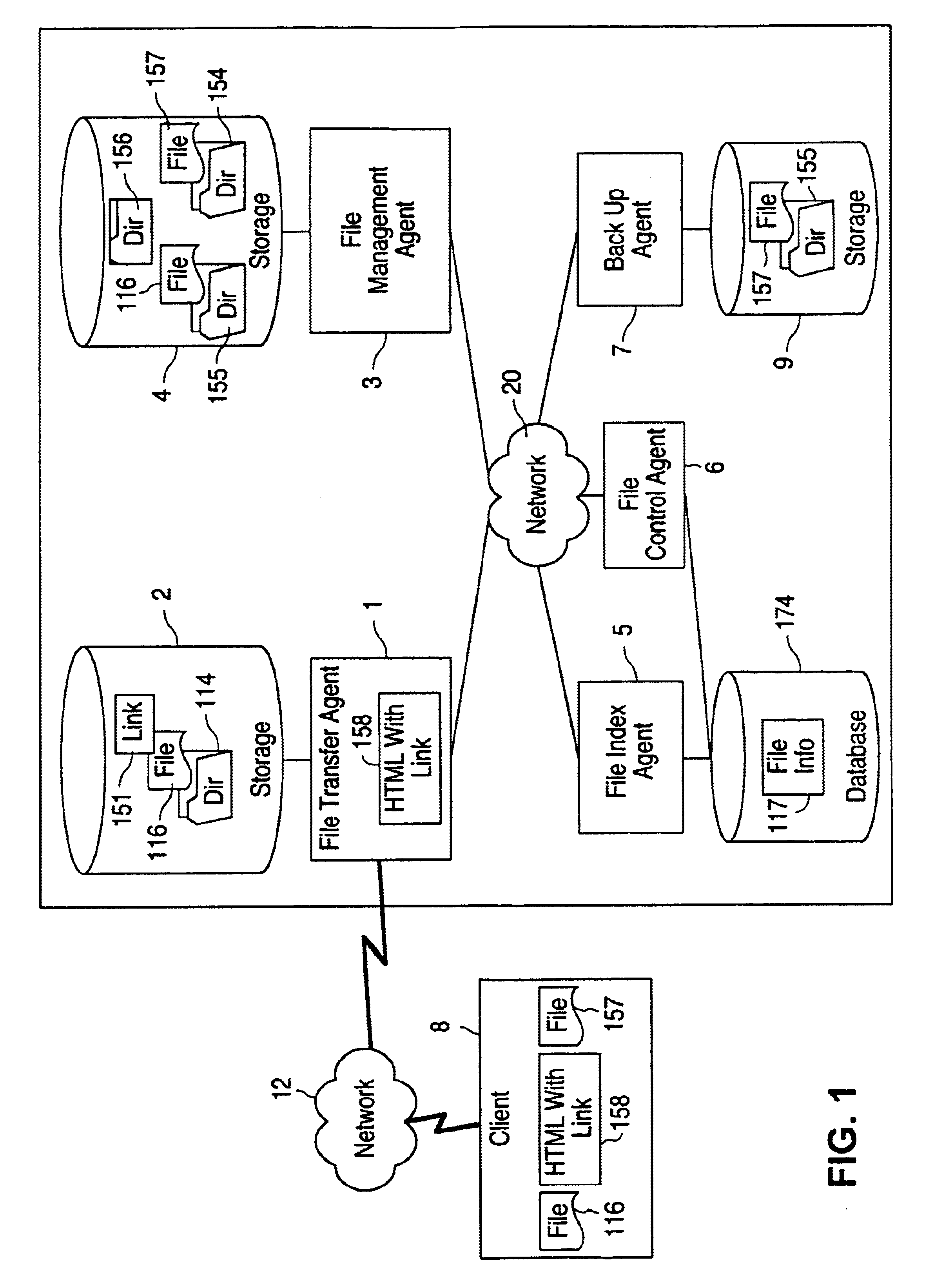
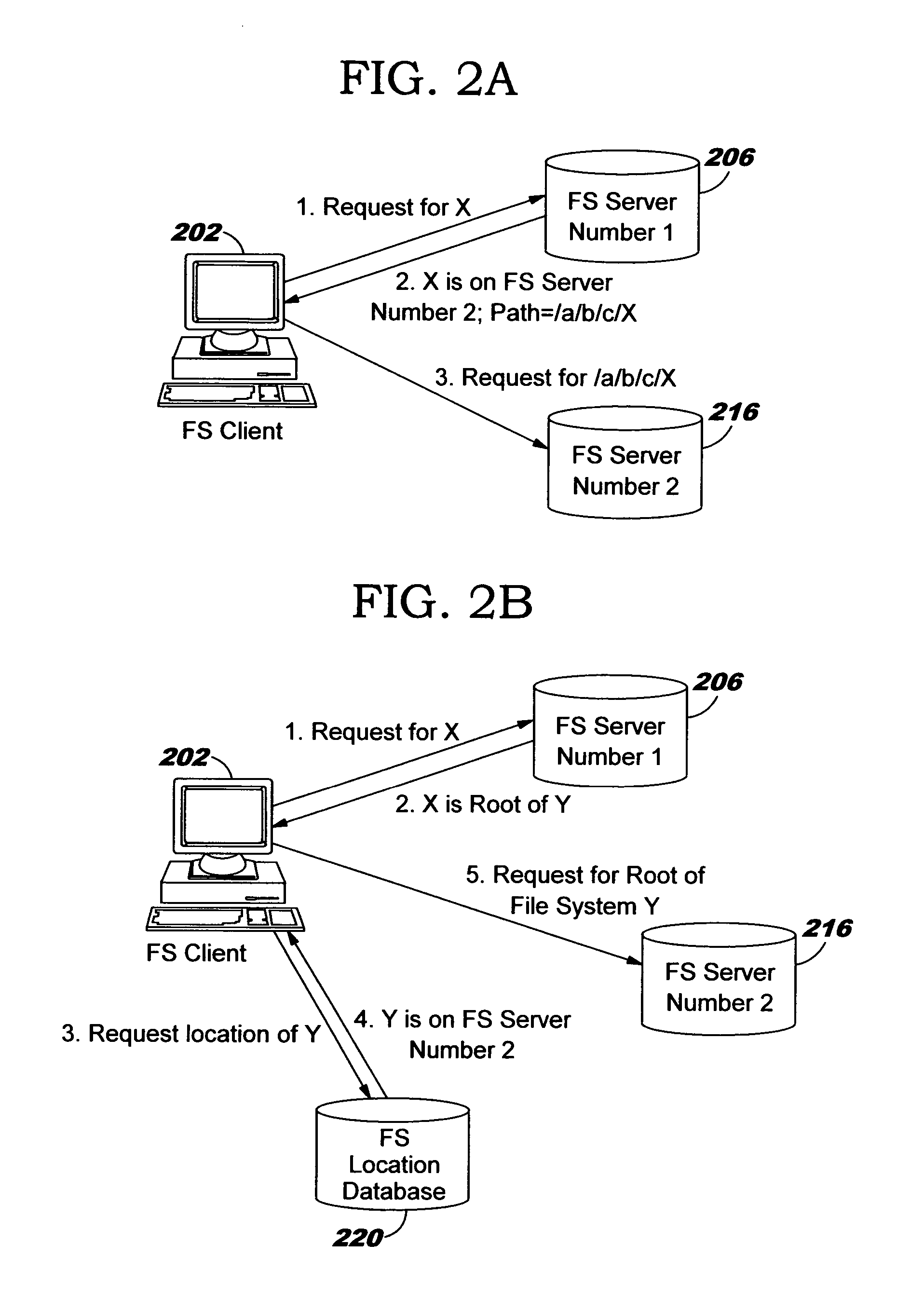
A file system for file sharing includes a web server that creates a temporary directory for each session between the web server and a client computer. When the client computer requests a file located in a file server, the web server creates a symbolic link to the file in the temporary directory and a web page including an URL to the symbolic link. The web server transmits the web page, and therefore the file, to the client computer. Client computer can also upload files to the web server. The web server saves the uploaded files to the temporary directory and then moves the files to the file server. At the end of the session, the web server deletes the temporary directory. Thus, files are not saved on the web server and therefore not accessible to others from the Internet. In this file system, file and directory names are orderly incremented in the file server to simplify the back up process of the file server. Furthermore, previously backed up directories are checked for their current size to determine if they should be backed up again. By backing up previously backed up directories that are now smaller speeds up the restoration of file serve when necessary.
Owner:ARCSOFT
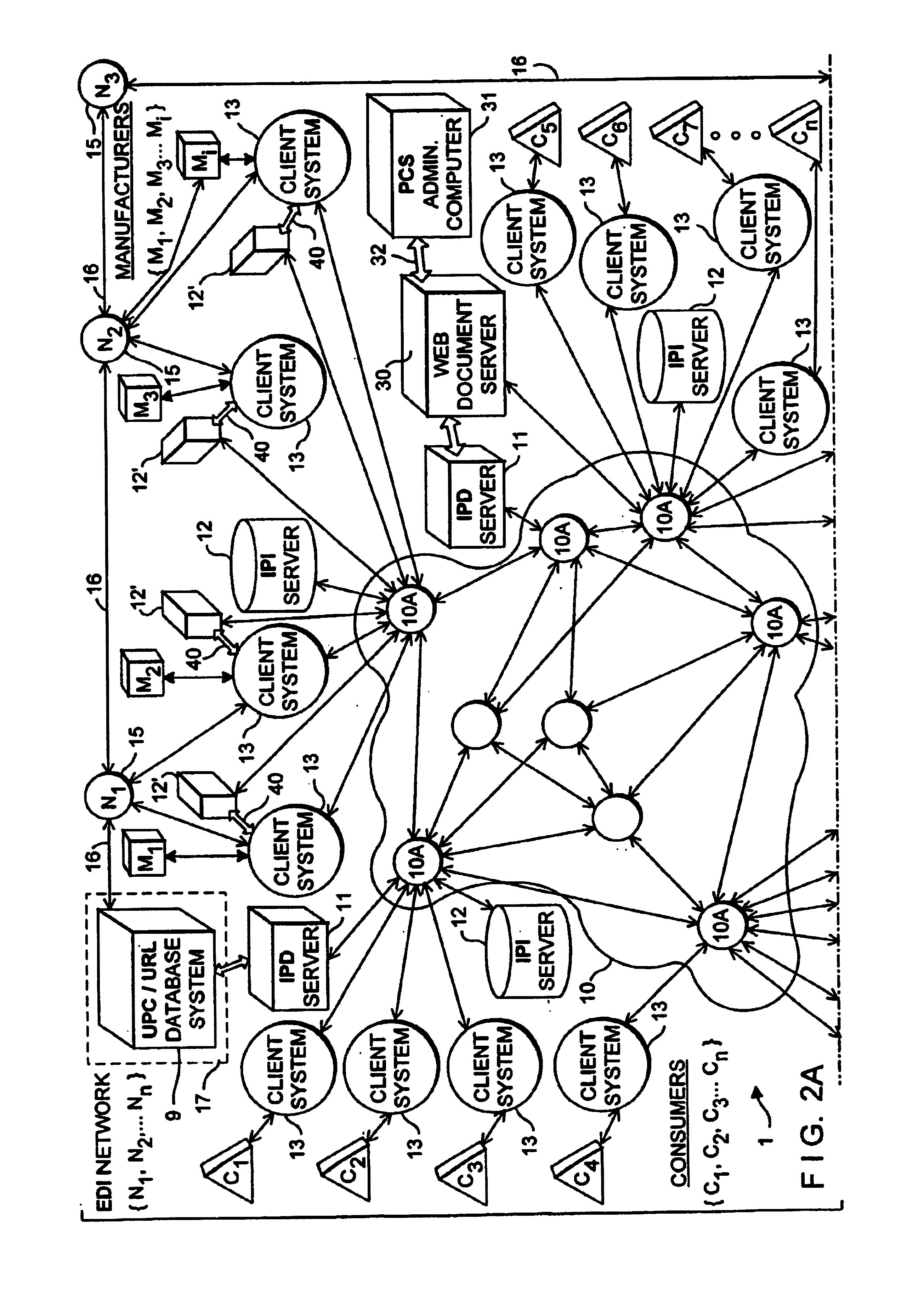
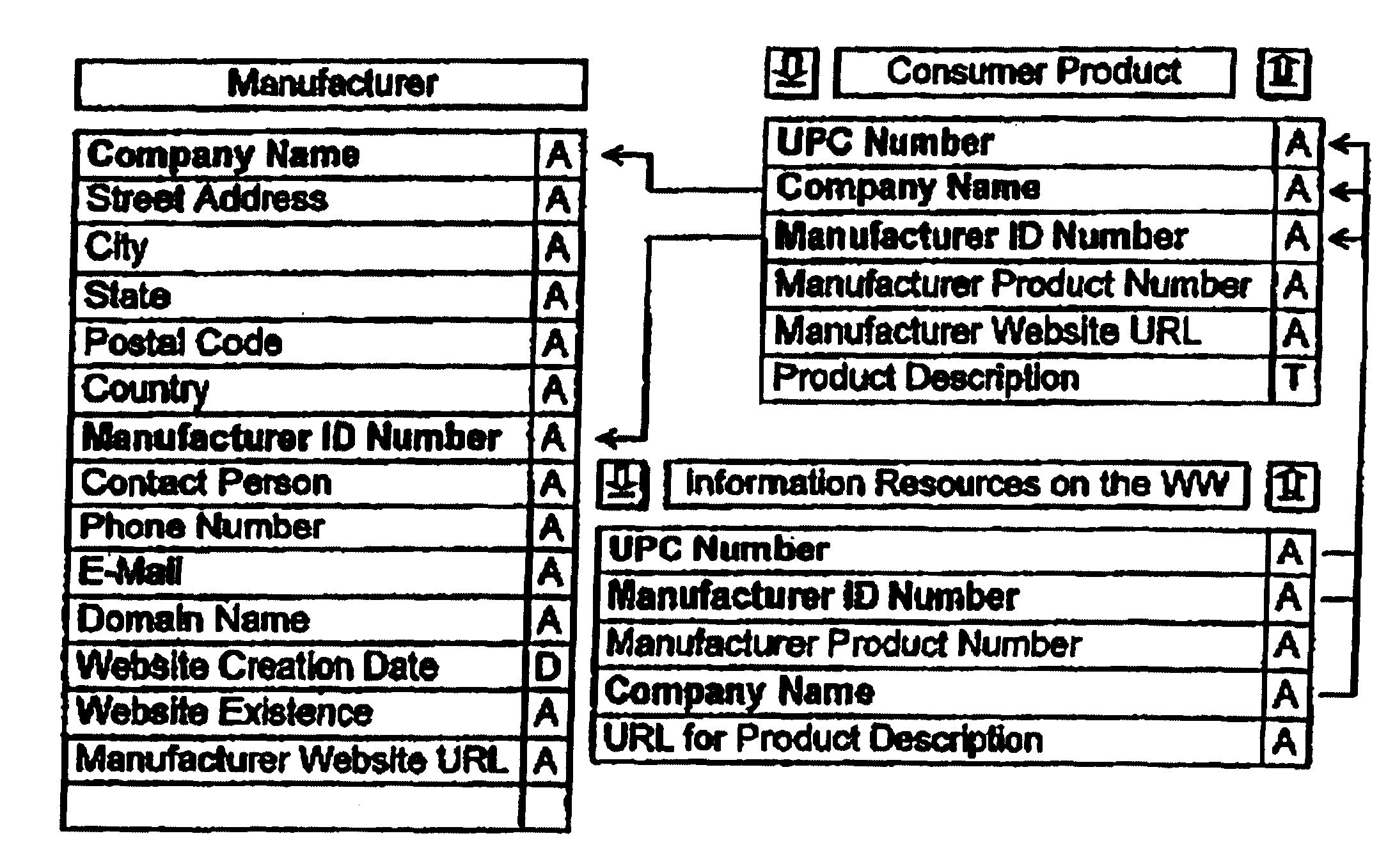
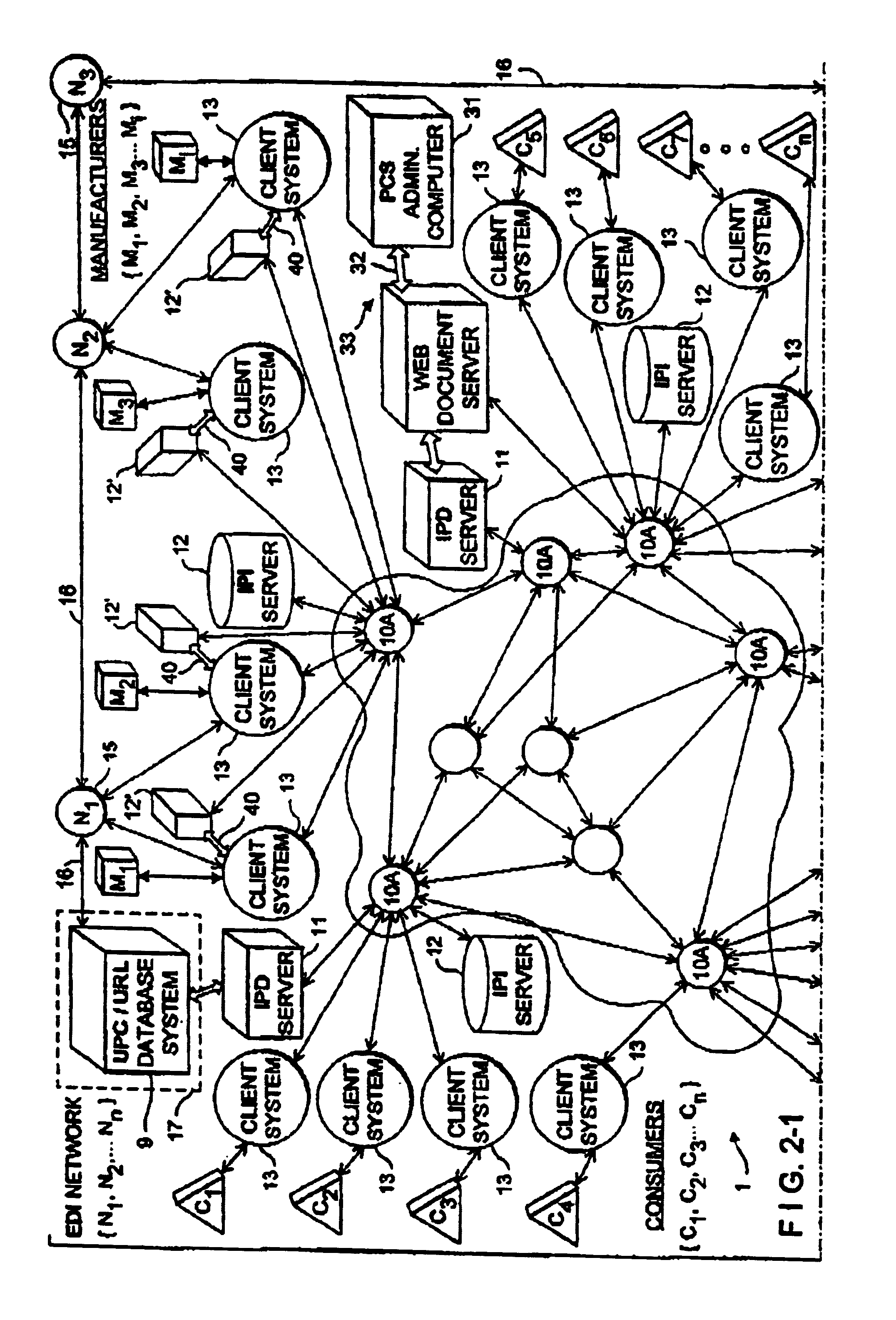
Internet-based system for collecting, managing and serving consumer product-related information over the internet using trademarks and universal resource locators (URLS) symbolically-linked by manufacturers of consumer products and/or their agents
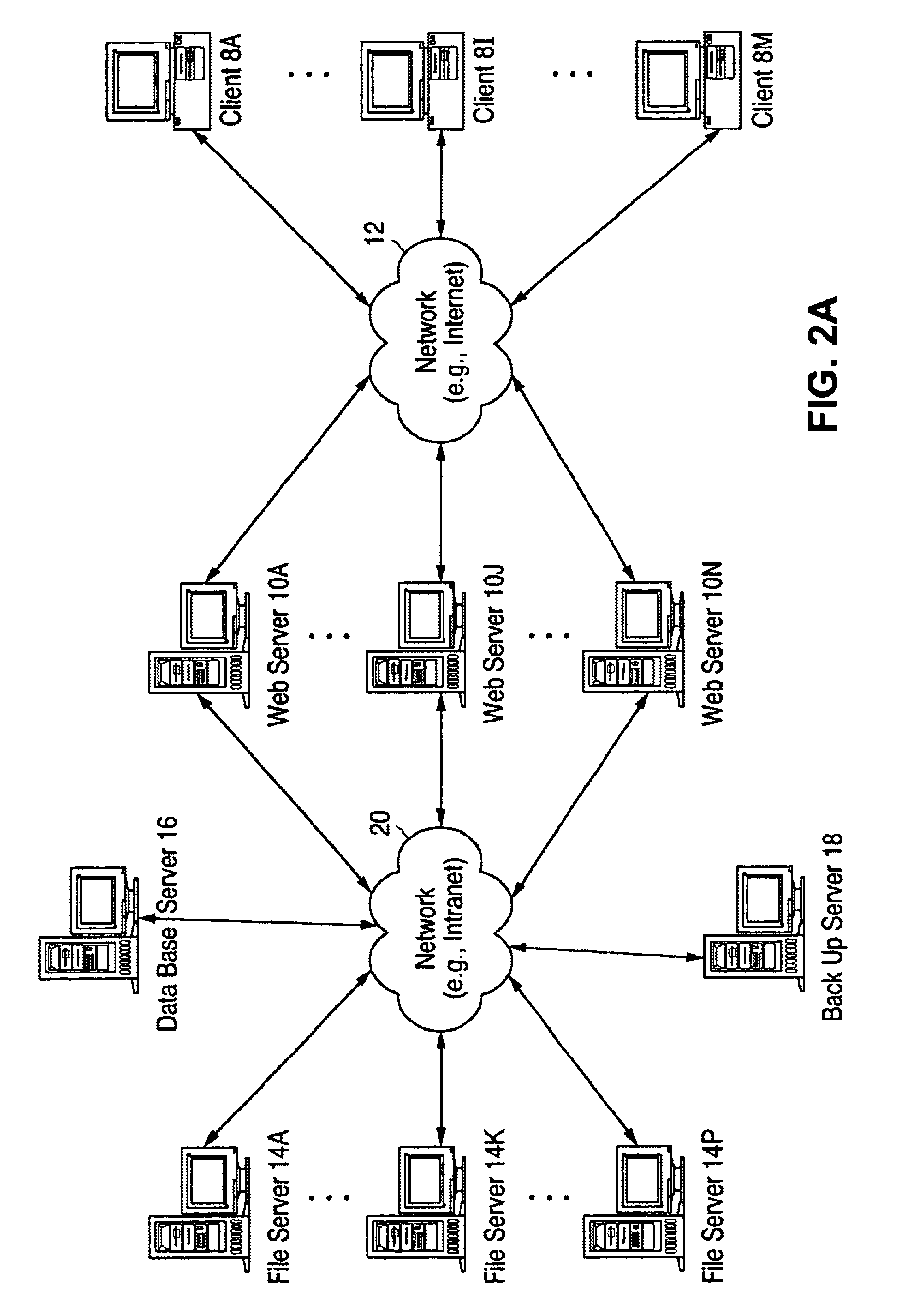
An Internet-based system for collecting, managing and serving consumer product-related information over the Internet. The system comprises a database management subsystem for storing and managing information representative of (i) a plurality of trademarks placed on or used in connection with a plurality of consumer products, and (ii) a plurality of Uniform Resource Locators (URLs) symbolically linked to the trademarks and specifying the location of a plurality of Web documents stored in one or more Internet-based information servers, by manufacturers, their agents and / or third parties, and contain particular kinds of information related to consumer products on which the trademarks are placed and used in commerce. A trademark / URL information server accesses one or more URLs from the database management subsystem in response to a request placed therewith by a consumer-operated client computer subsystem. Each manufacturer uses a manufacturer-managed client computer subsystem to transmit to the database management subsystem, information representative of a plurality of symbolically linked trademarks and URLs. Each consumer uses a consumer-operated client computer subsystem to access one or more URLs from the database management subsystem in response to a request transmitted to the trademark / URL information server. The accessed URLs are then used to access and display Web documents specified by the URLs and containing consumer product related information. Using the present invention, large databases containing symbolically linked trademarks and URLs can be created and managed, so that corresponding consumer product related information on the World Wide Web (WWW) can be reliably accessed and displayed by consumers using trademarks.
Owner:PERKOWSKI THOMAS J
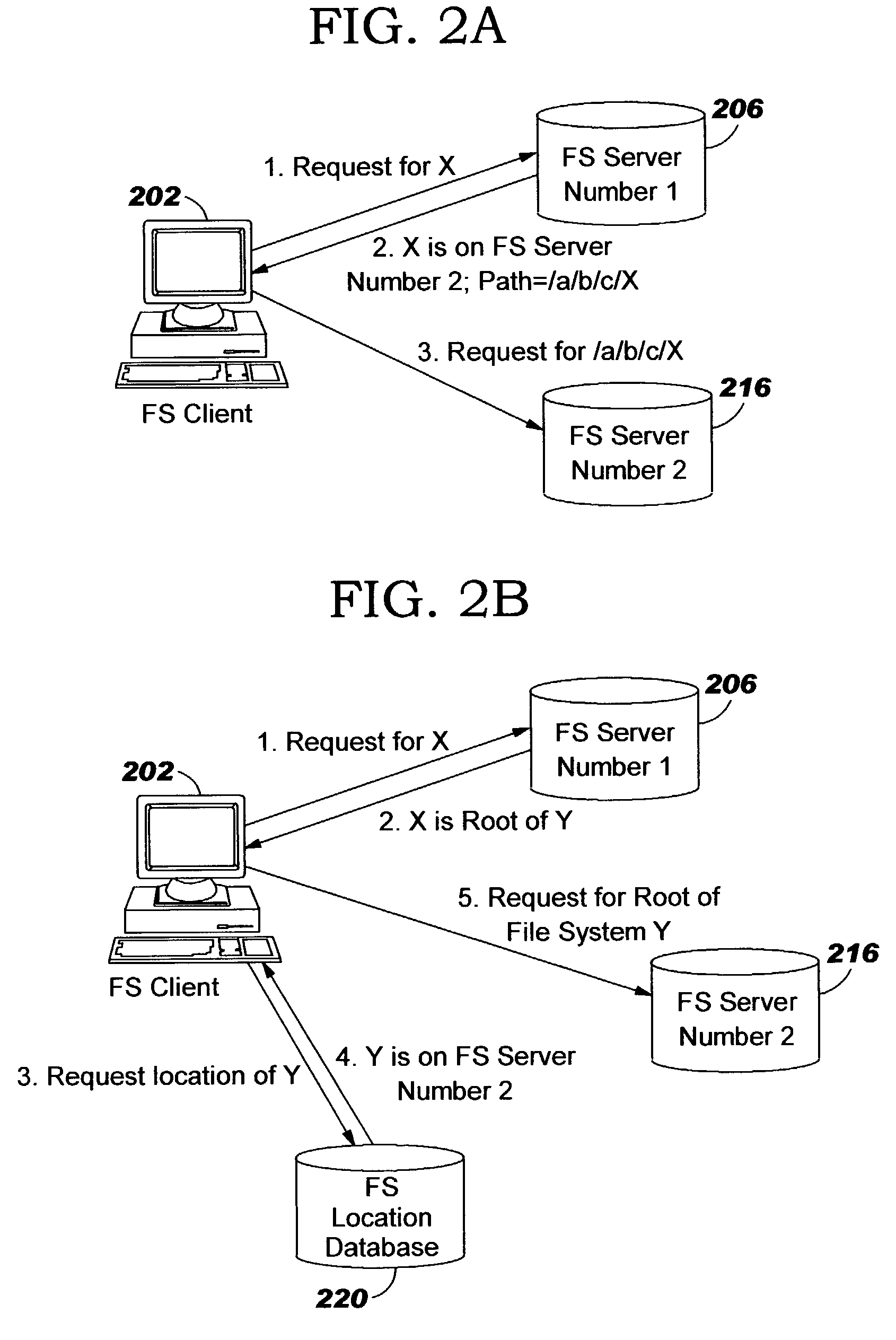
Technique to enable support for symbolic link access by windows clients
ActiveUS6968345B1Solve problemsEnhanced levelData processing applicationsMultiple digital computer combinationsDistributed File SystemSymbolic link
A widelink directive provides an enhanced level of indirection with respect to a resource, such as a unit of storage, attached to a destination, such as a storage system. The widelink has a scope of indirection that is “wider” than a conventional symbolic link (“symlink”). The novel widelink directive is similar to the distributed file system (DFS) facility that allows DFS-enabled common internet file system clients to resolve uniform naming convention paths to locations that may or may not be on an original storage system, such as a multi-protocol filer, or original protocol server of the filer. By taking advantage of clients that support the DFS facility, the widelink directive is quite flexible in that it can be used to resolve symlinks that “leave” a share.
Owner:NETWORK APPLIANCE INC
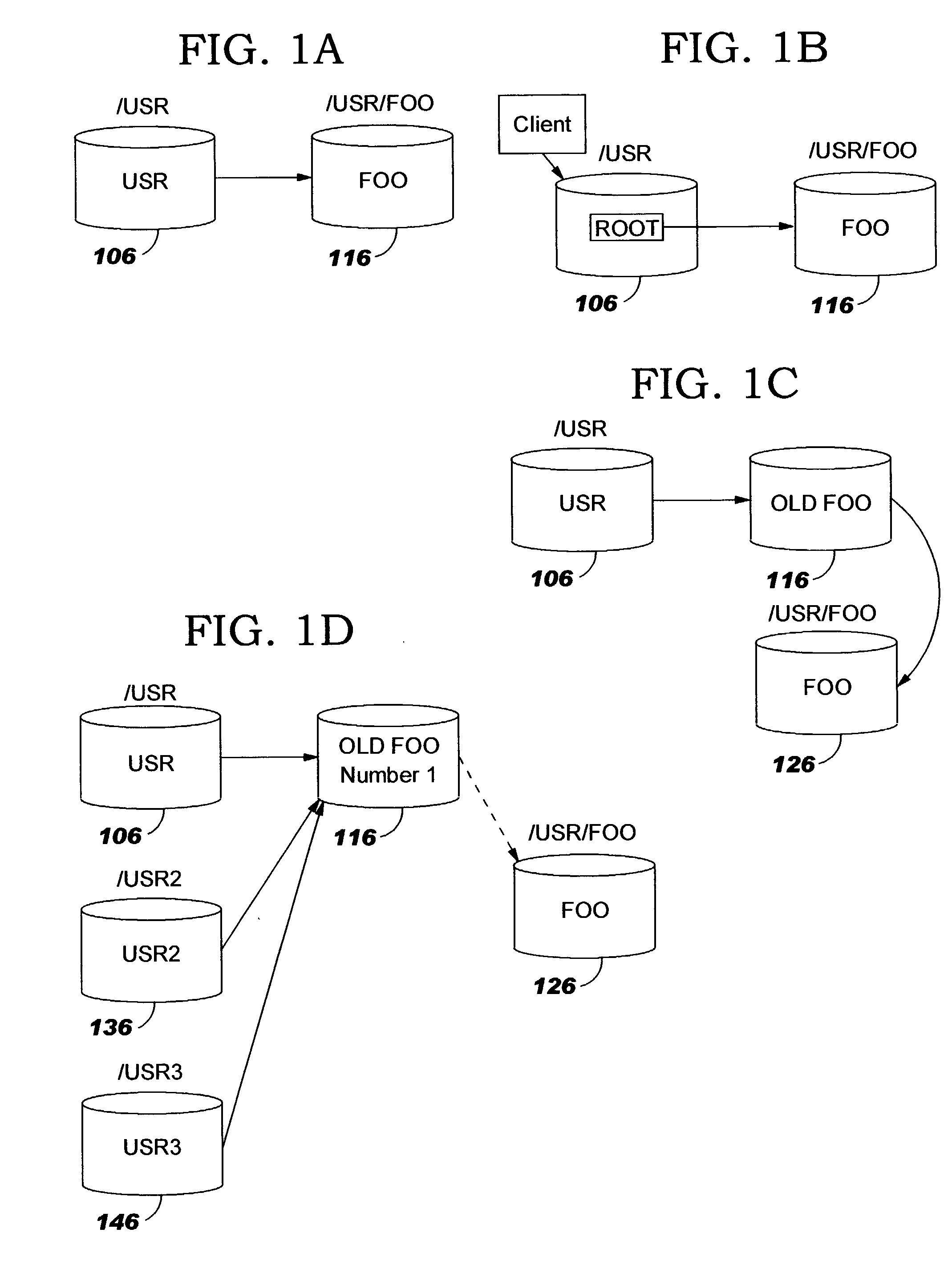
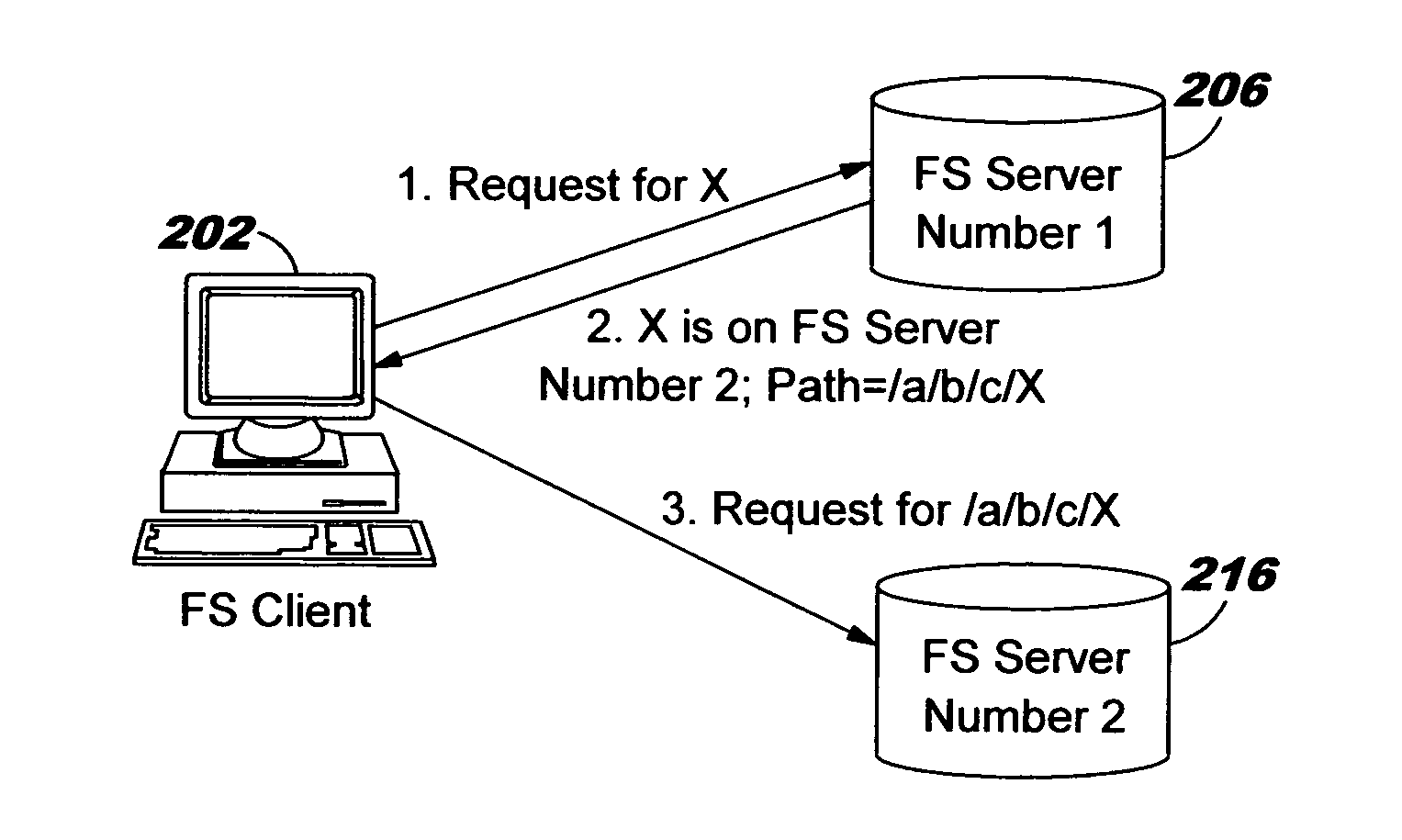
Uniform name space referrals with location independence
InactiveUS20040024786A1Digital data processing detailsMultiple digital computer combinationsSymbolic linkNetwork File System
Improved techniques are disclosed for accessing content in file systems, allowing file system clients to realize advantages of file system referrals even though a file access protocol used by the client is not specifically adapted for referral objects. (For example, the client may have a legacy file system protocol or a proprietary file system protocol which does not support referrals.) These advantages include a uniform name space view of content in a network file system, and an ability to locate content in a (nearly) seamless and transparent manner, even though the content may be dynamically moved from one location to another or replicated in different locations. A file system server returns a symbolic link in place of a referral, and an automated file mounting process on the client is leveraged to access the content using the link. Built-in crash recovery techniques of the file system client are leveraged to access moved content.
Owner:IBM CORP
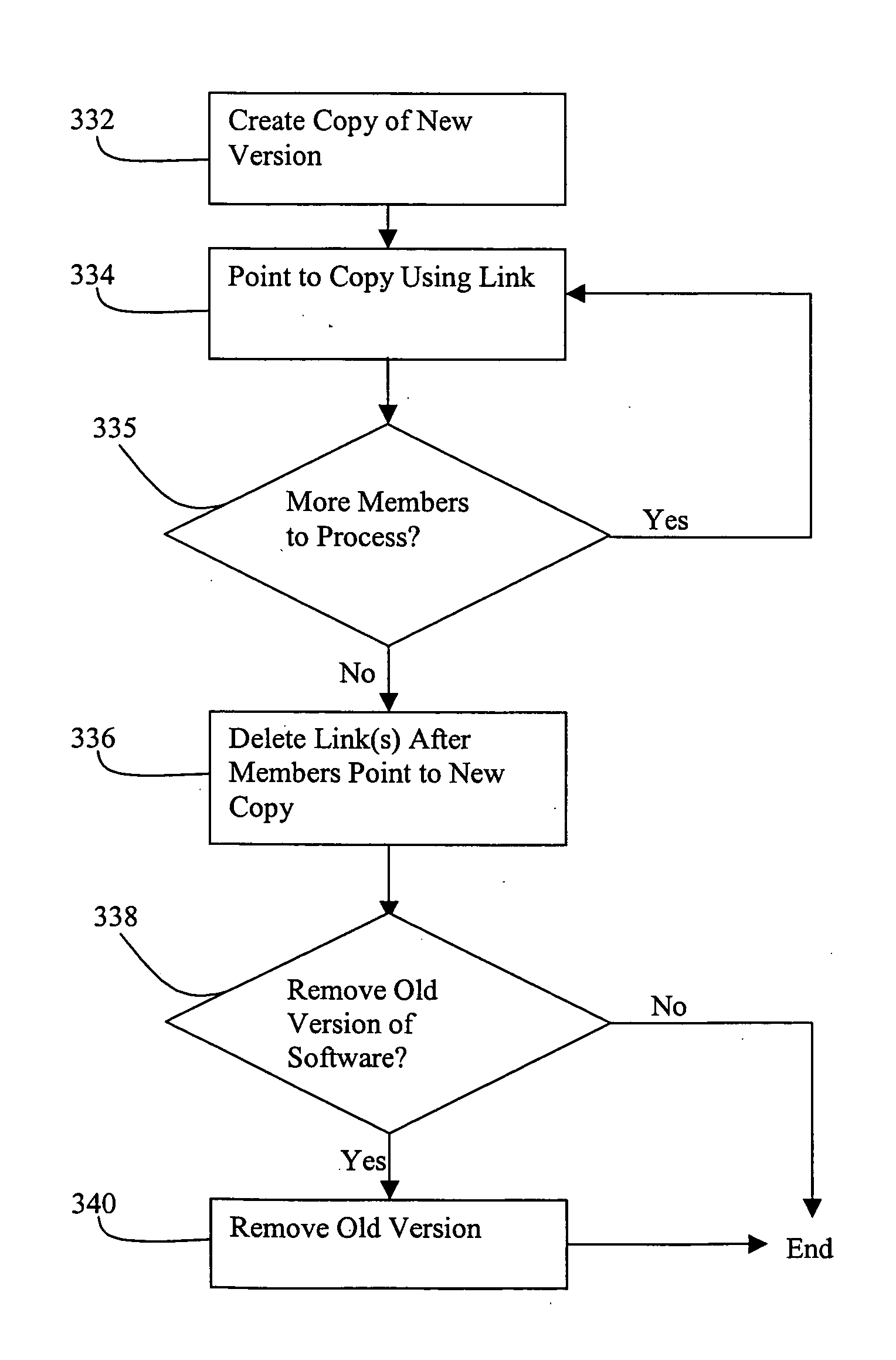
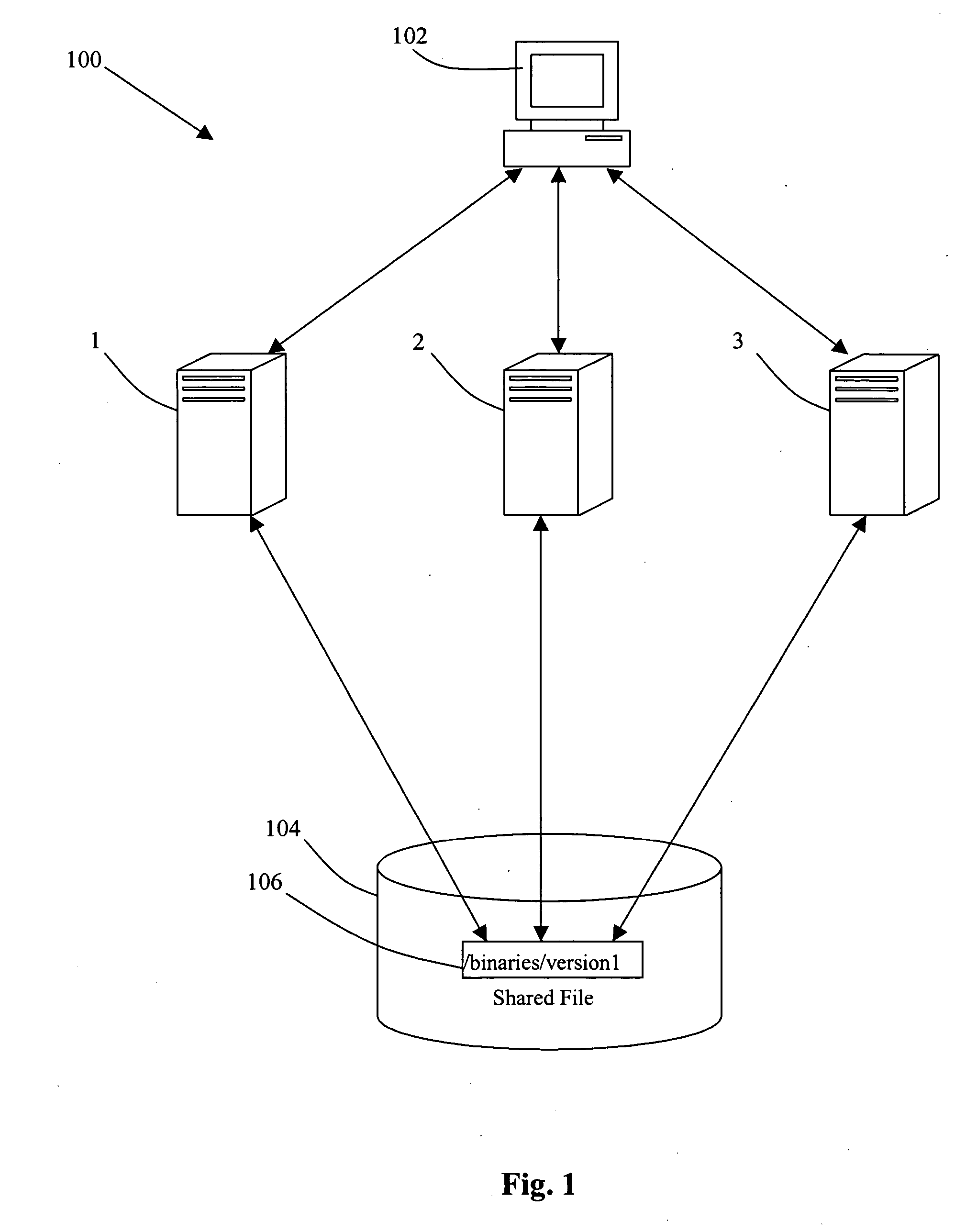
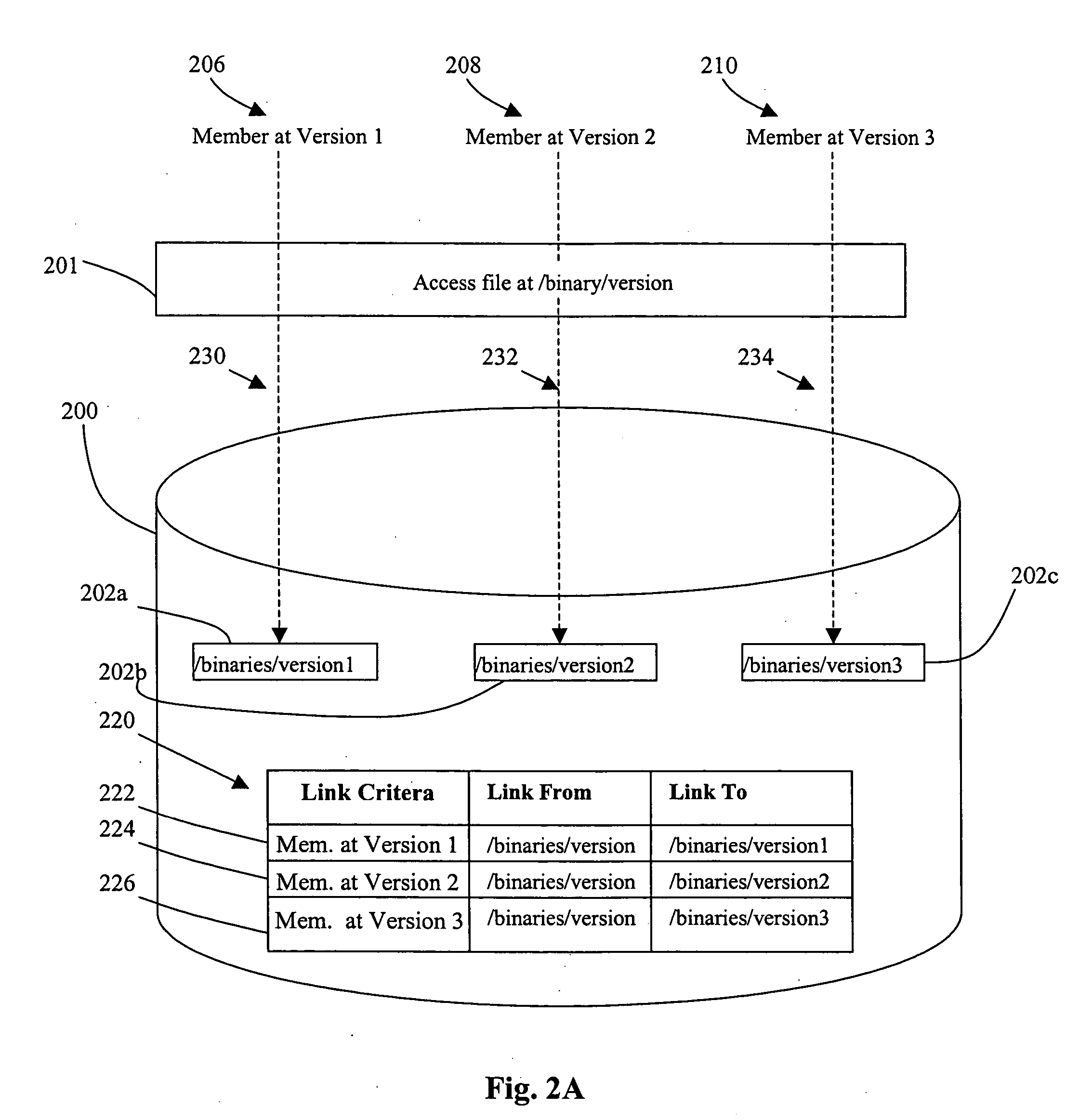
Method and mechanism for performing a rolling upgrade of distributed computer software
ActiveUS20050210461A1Minimizes or eliminates planned downtimeImprove usabilityProgram loading/initiatingMemory systemsDowntimeSoftware engineering
An improved method and mechanism for performing rolling upgrades to distributed software installations is disclosed. The present approach eliminates or minimizes extraneous downtime when performing a rolling upgrade, thereby improving performance an availability for users of the software installation. A rolling upgrade can be performed by defining a private symbolic link for each member that is upgraded to reference the upgraded version of the software installation.
Owner:ORACLE INT CORP
Uniform name space referrals with location independence
InactiveUS20050149528A1Simple technologyDigital data processing detailsMultiple digital computer combinationsSymbolic linkClient-side
Improved techniques are disclosed for accessing content in file systems, allowing file system clients to realize advantages of file system referrals even though a file access protocol used by the client is not specifically adapted for referral objects. (For example, the client may have a legacy file system protocol or a proprietary file system protocol which does not support referrals.) These advantages include a uniform name space view of content in a network file system, and an ability to locate content in a (nearly) seamless and transparent manner, even though the content may be dynamically moved from one location to another or replicated in different locations. A file system server returns a symbolic link in place of a referral, and an automated file mounting process on the client is leveraged to access the content using the link. Built-in crash recovery techniques of the file system client are leveraged to access moved content.
Owner:IBM CORP
System for and method of managing and delivering manufacturer-specified consumer product information to consumers in the marketplace
InactiveUS7089199B2High acceptanceEasy to disassembleAcutation objectsDigital data information retrievalTrademarkInformation resource
A method of managing and delivering manufacturer-specified consumer product information to consumers in the marketplace. For a plurality of UPN-labeled consumer products offered for sale within a the marketplace, the manufacturer of the plurality of UPN-labeled consumer products or an agent thereof, accesses an Internet-enabled relational database and store therein, information elements representative of (1) a plurality of universal product numbers (UPNs) assigned to the plurality of UPN-labeled consumer products manufactured by the manufacturer and registered with the relational database, and (2A) a trademark (TM) symbolically linked to each the UPN, (2B) a product description (PD) symbolically linked to each the UPN, and (2C) one or more uniform resource locators (URLs) symbolically linked to each the UPN, wherein each the URL specifies the location of an information resource located on the Internet and related to one of the plurality of UPN-labeled consumer products registered with the relational database by the manufacturer, and wherein a UPN / TM / PD / URL data link is created and maintained in the relational database for each the UPN-labeled consumer product registered with the relational database by the manufacturer. A consumer within the marketplace transmits a request to the relational database from the Internet-enabled client computer. The UPN, TM and / or PD contained in the request enabled the consumer to access the URLs symbolically linked to the UPN, TM and / or PD, and the URLS are then transmitted to the Internet-enabled client computer for display to and use by a consumer in accessing information resources stored in the Internet-based product information servers, at the URLs.
Owner:PERKOWSKI THOMAS J
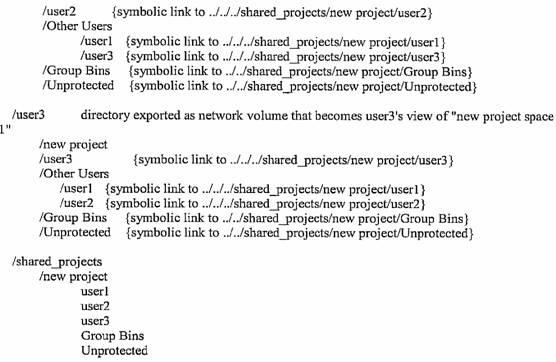
Novel media file access and storage solution for multi-workstation/multi-platform non-linear video editing systems
ActiveUS20110167036A1Easy and safe to accessDigital data processing detailsElectronic editing digitised analogue information signalsMulti platformSymbolic link
A novel system, method and computer program product for accessing digital media files stored in a media storage device via a server device in communication with the media storage device. The method provides a Project Sharing feature for enabling collaborative sharing of Non Linear Editing (NLE) Projects, even though the NLE application might normally define and save Projects as a single monolithic project file. The system and method provides a file directory and symlink scheme that allows ALL editors who are “members” of a Project Space to see all the bins created by all other editors, but controlling the WRITE ACCESS to the bins according to whose “User Folder” the bins resided in, i.e., a user-based locking scheme is provided to allow control over who can and cannot write to a file. The system and method further treats a single monolithic project file as a collection of smaller Project files, the permissions and ownerships of which could each be controlled independently.
Owner:EDITSHARE LLC
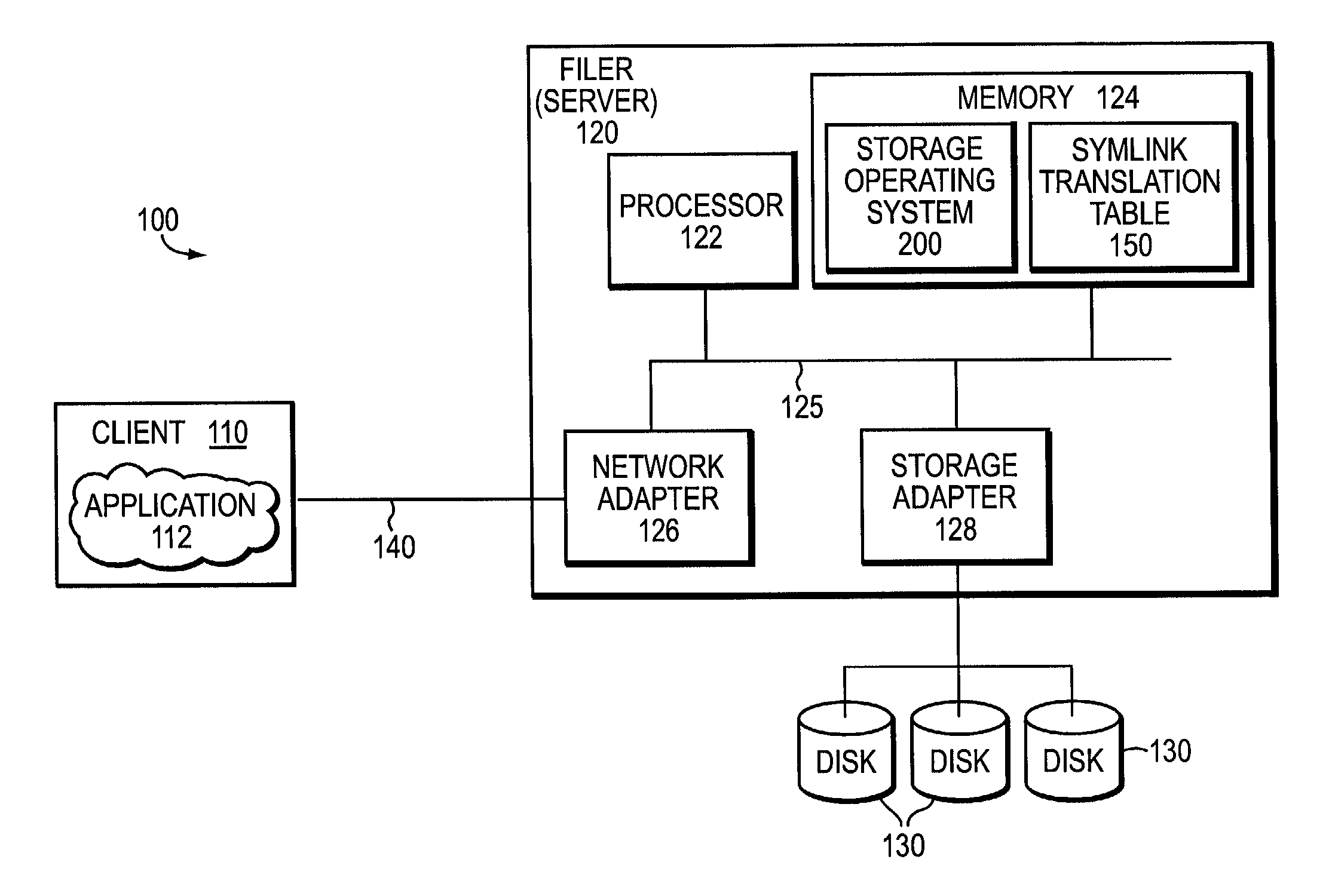
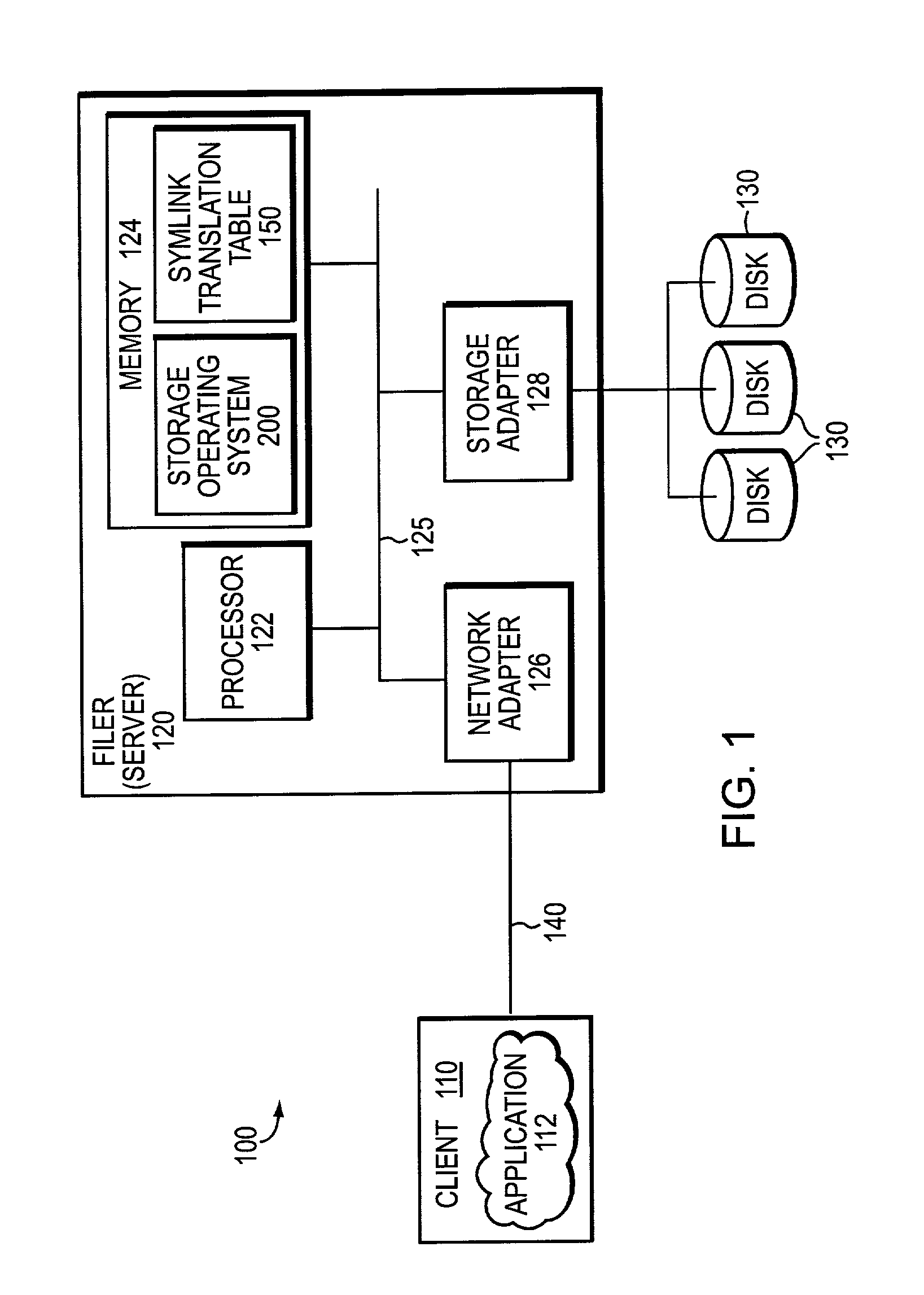
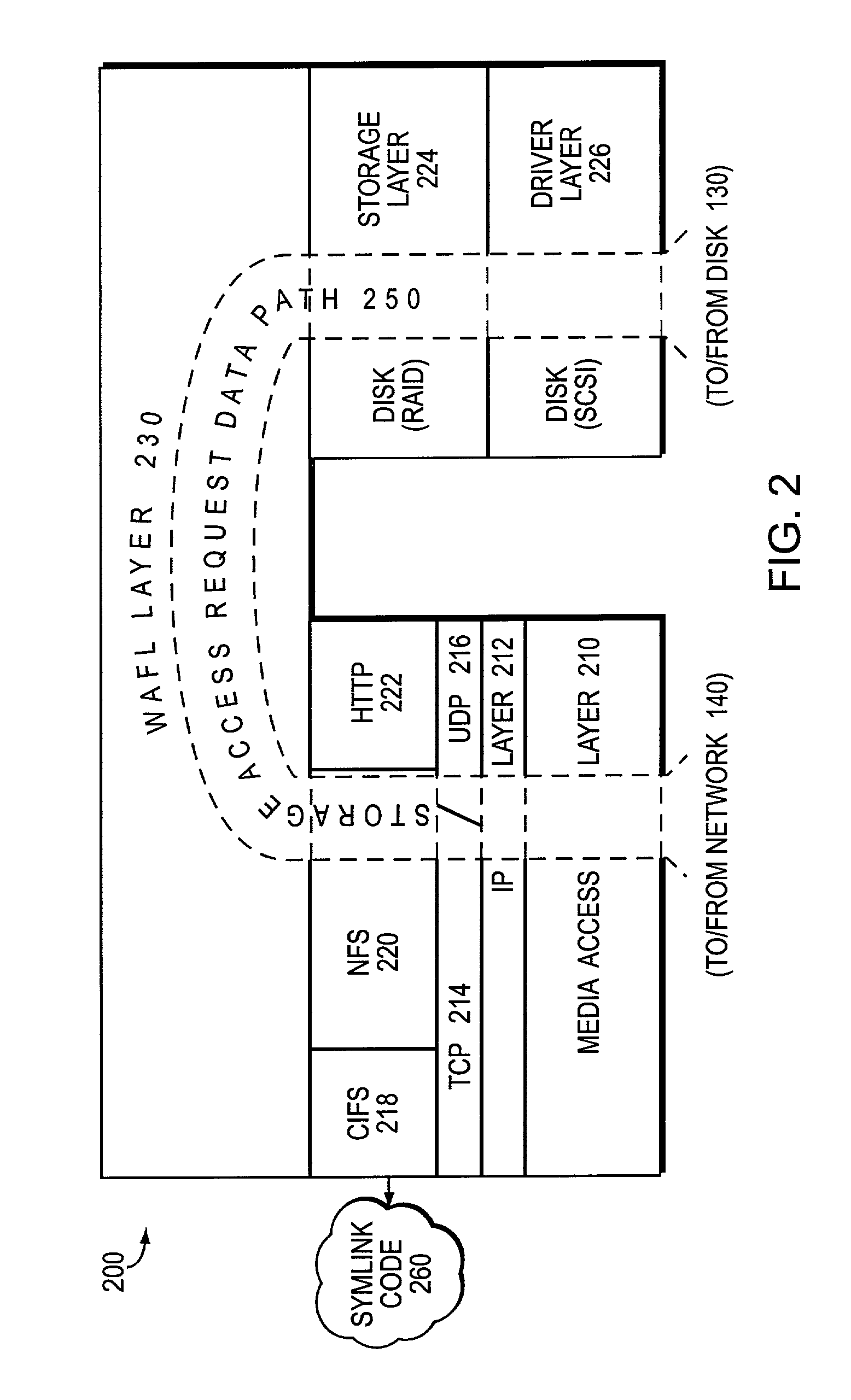
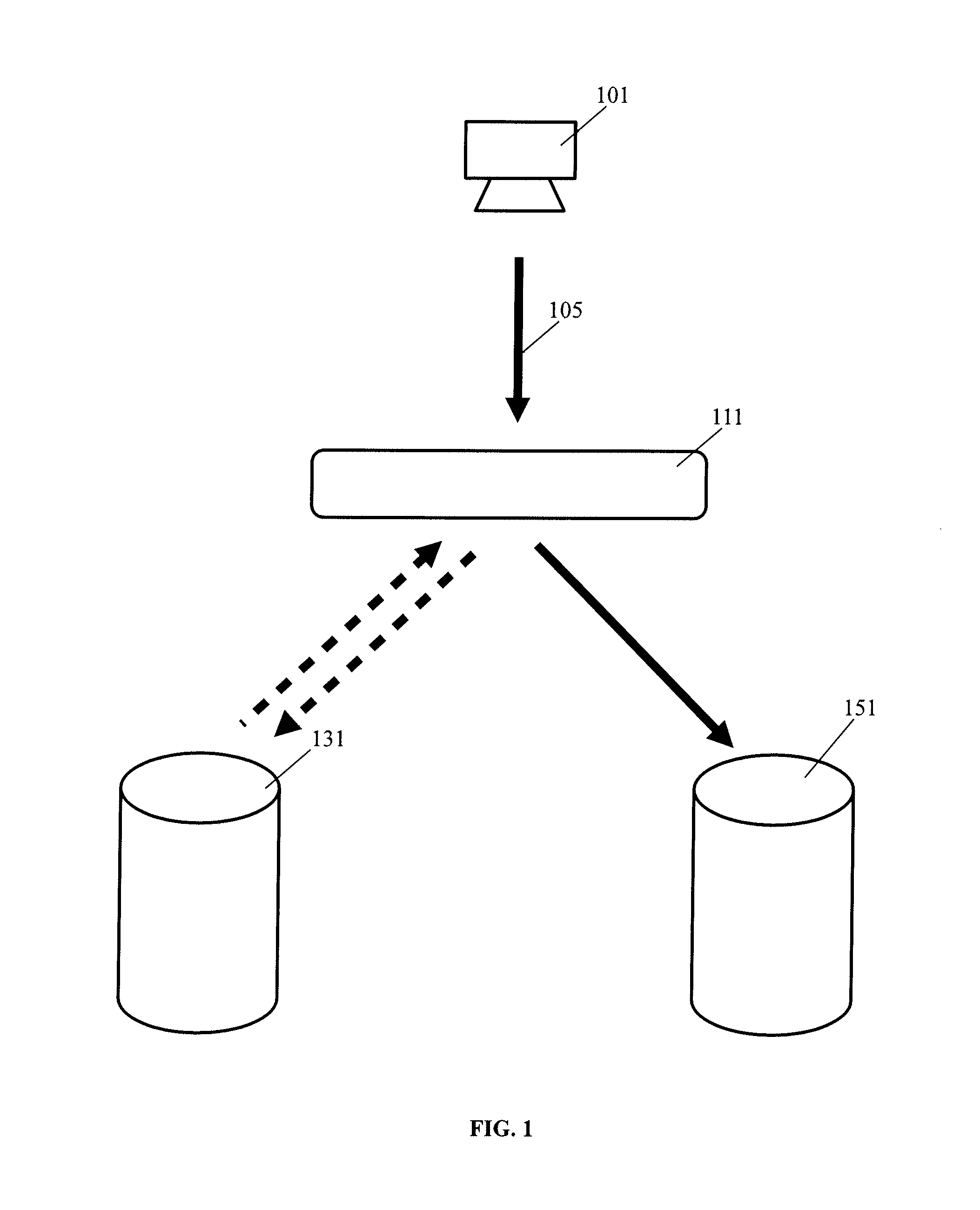
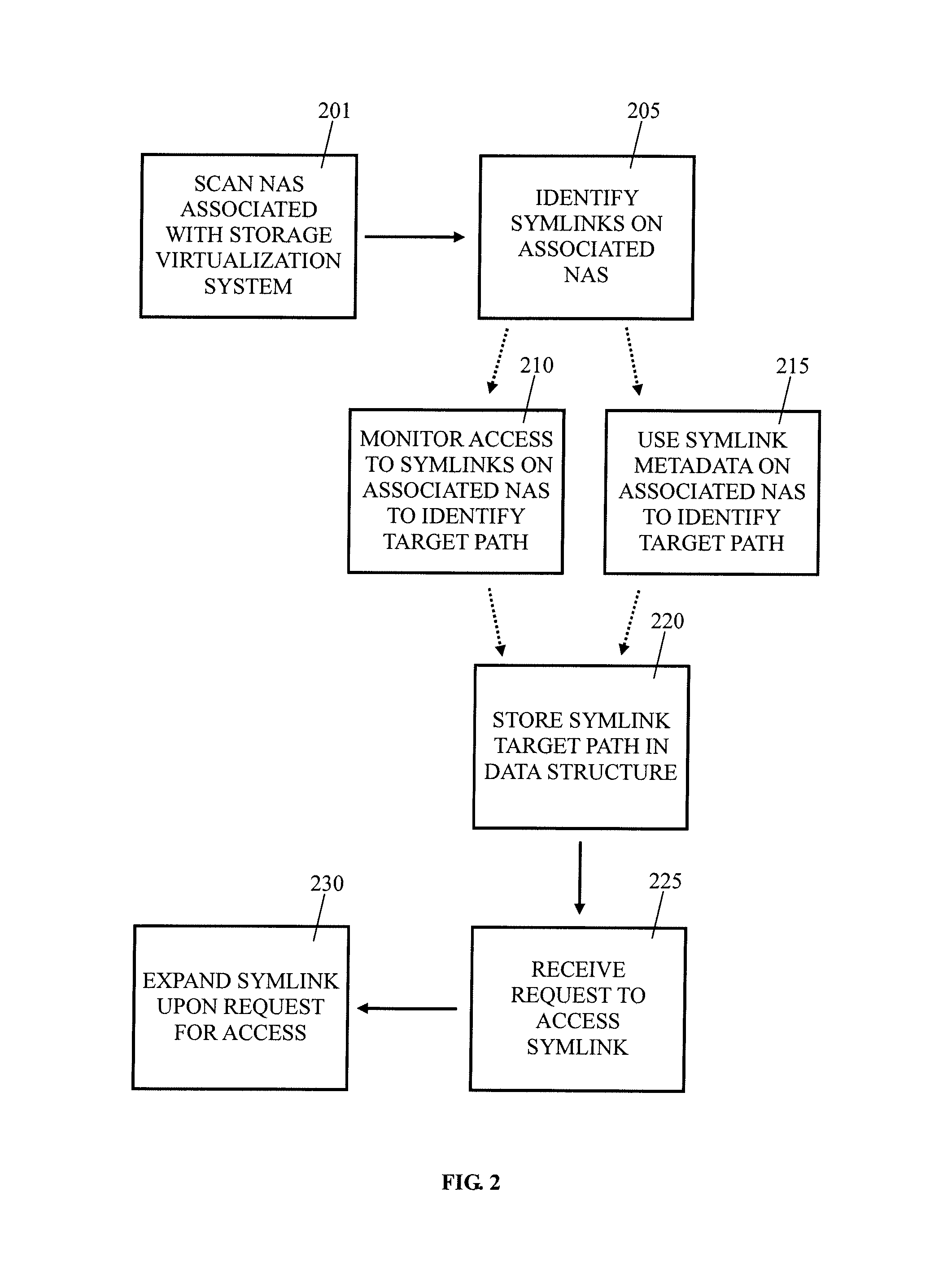
System and method for preserving symbolic links by a storage virtualization system
ActiveUS8667034B1File access structuresSpecial data processing applicationsSymbolic linkMulti protocol
The present invention enables a storage virtualization system to identify and preserve symlinks stored in a mixed protocol NFS+CIFS NAS system. Using the results of a multi-protocol scan, a storage virtualization system may identify which data objects are symlinks. The storage virtualization system may also determine the symlinks' target path information either by monitoring access or by referring to metadata discovered during the scan. After recording this target path information, the storage virtualization system may provide symlink expansion capabilities separate from the client computer or the NAS system. In addition, this target path information may be preserved upon symlink migration to a second NAS system.
Owner:EMC IP HLDG CO LLC
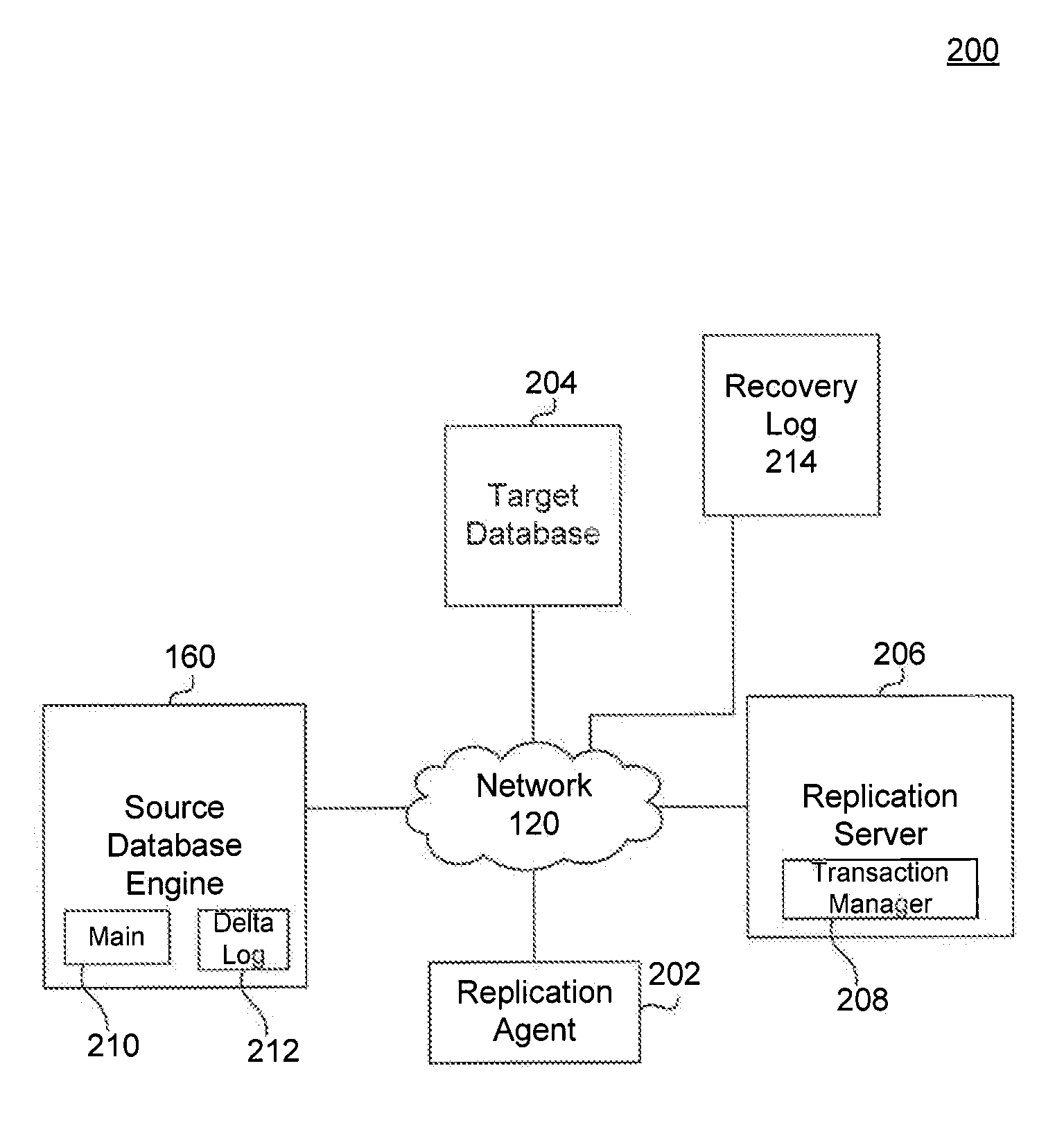
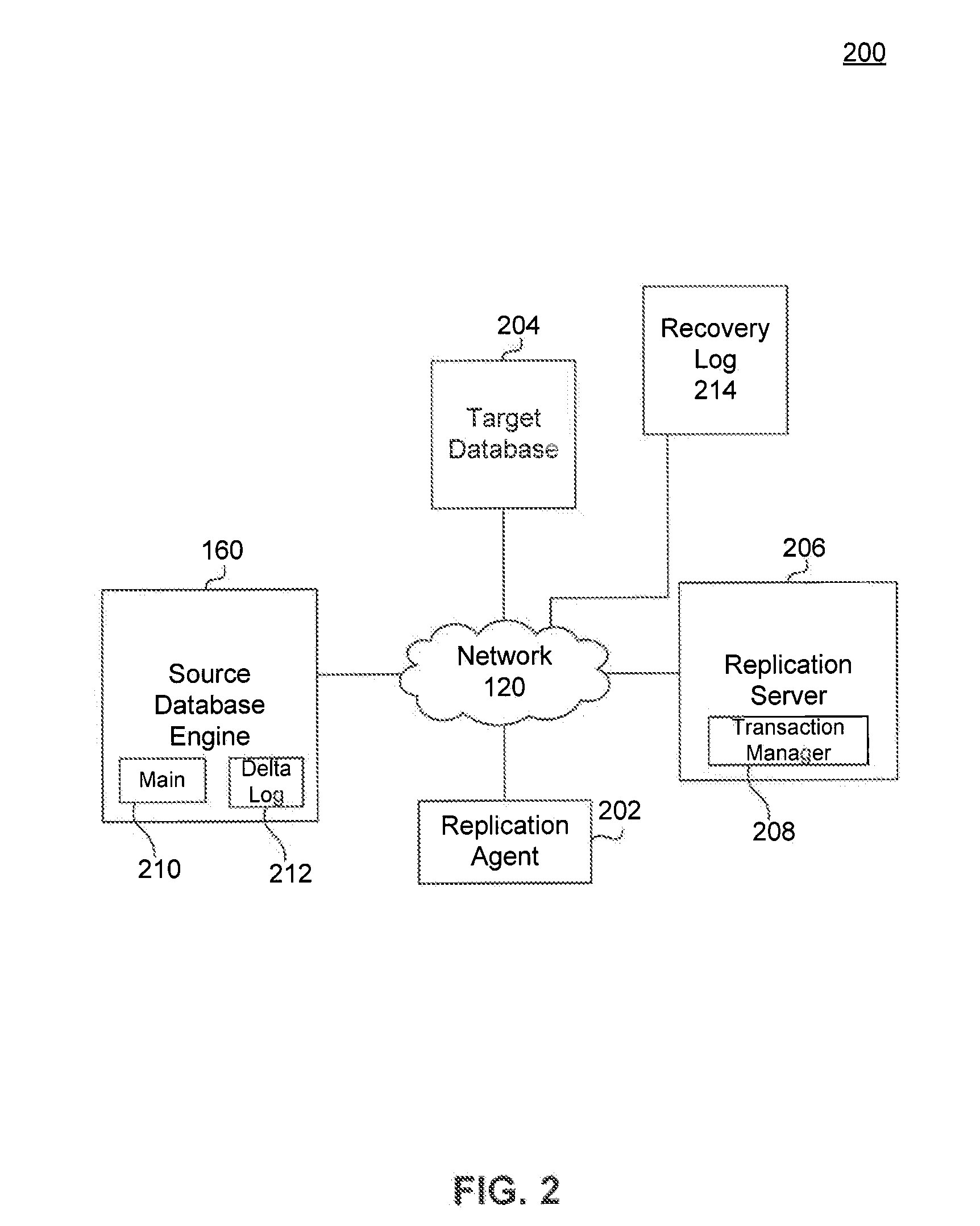
Replication Mechanisms for Database Environments
ActiveUS20140172794A1Digital data processing detailsDatabase distribution/replicationSymbolic linkDatabase engine
Data replication in a database includes identifying a source database system. The source database includes a main index file and a delta log file. To create a replica, one or more symbolic links to the source database system are generated. The symbolic links identify a path to a physical location of the source database. A replica of the source database is generated based on the symbolic links. The replica includes a copy of the main index file and delta log file. Information associated with the replica and the symbolic links is stored in a recovery log. Replica are provided transparently to most database engine components by re-using partitioning infrastructure. Components “see” replica as tables with a single partition; that partition is a local replica.
Owner:SAP AG
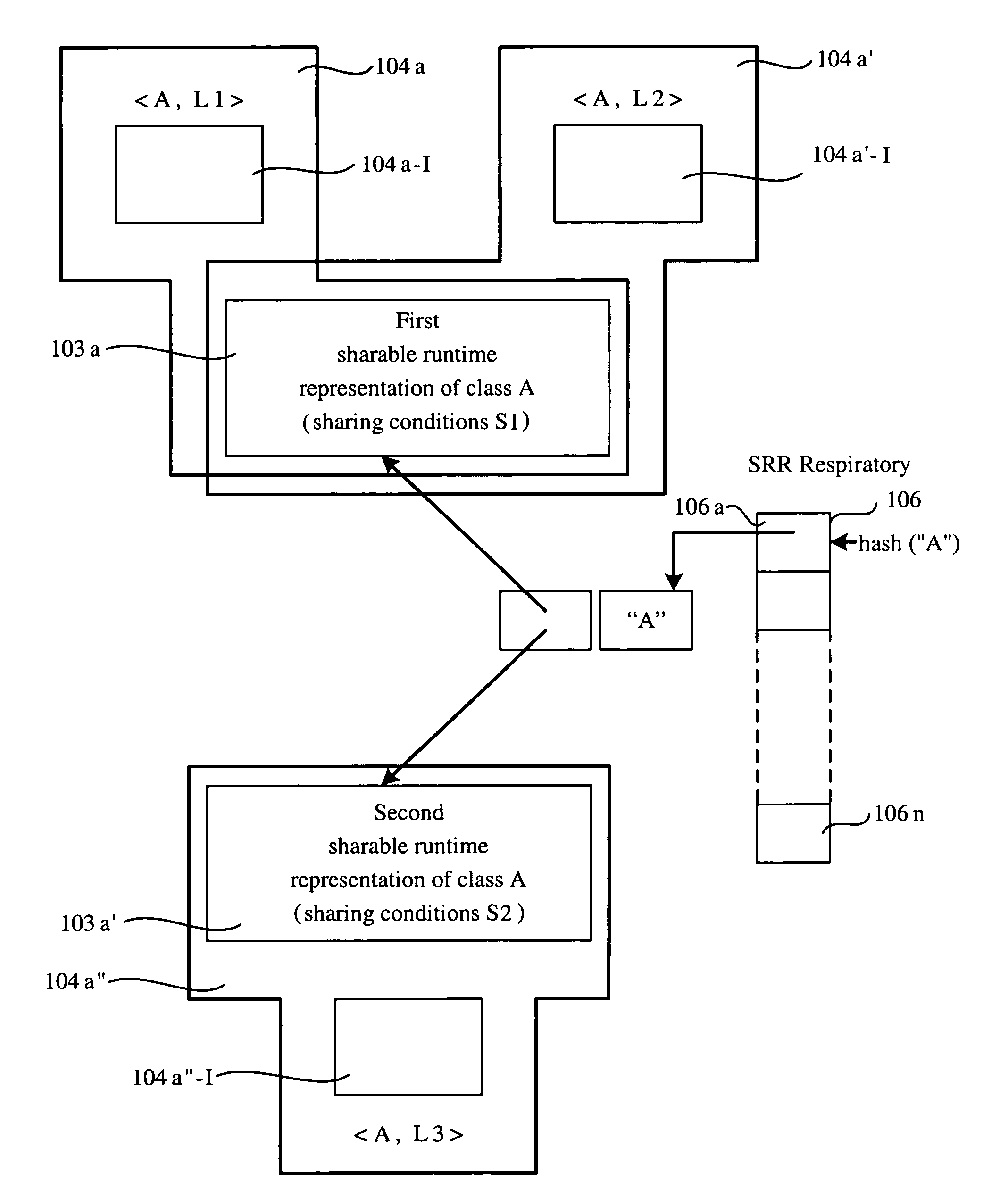
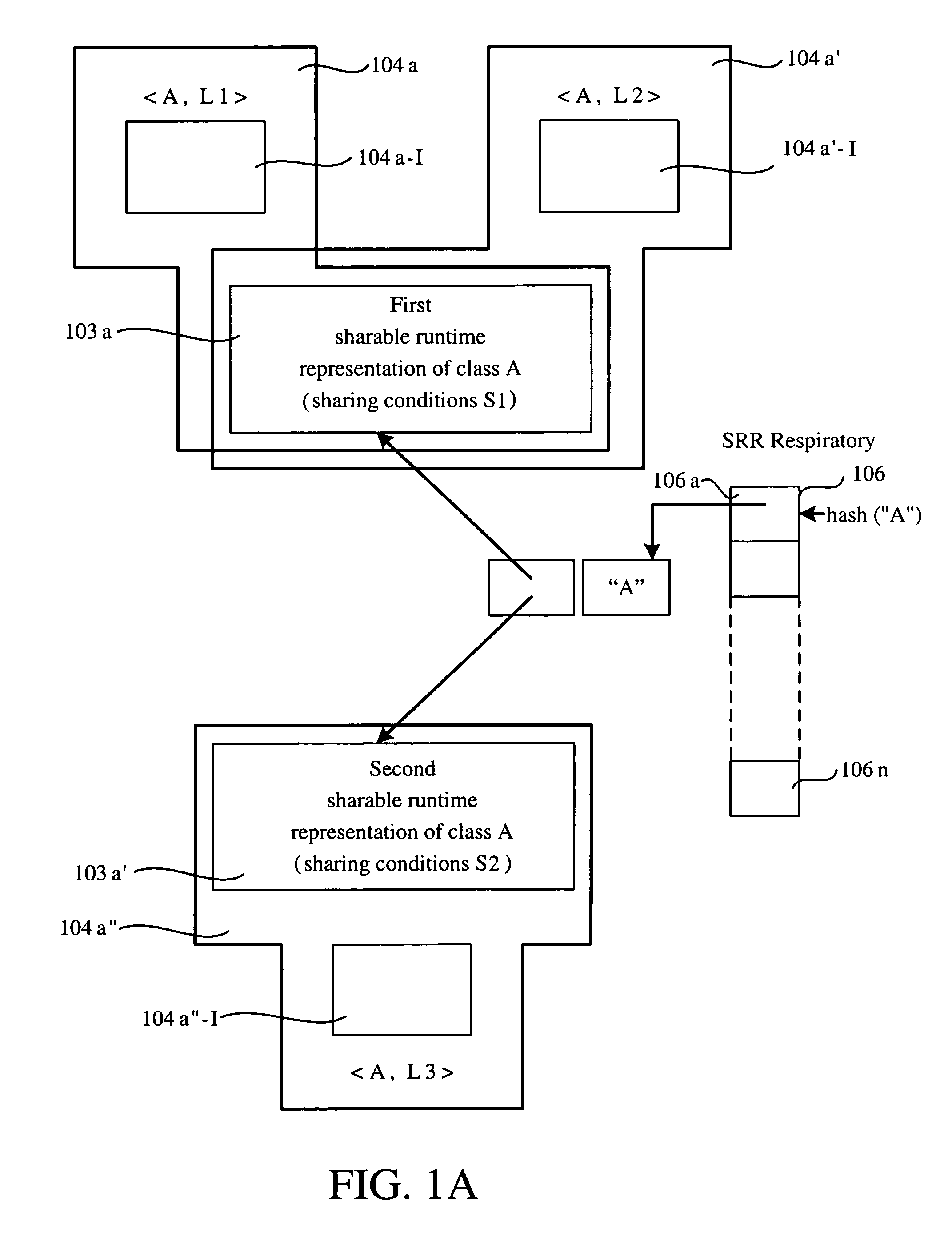
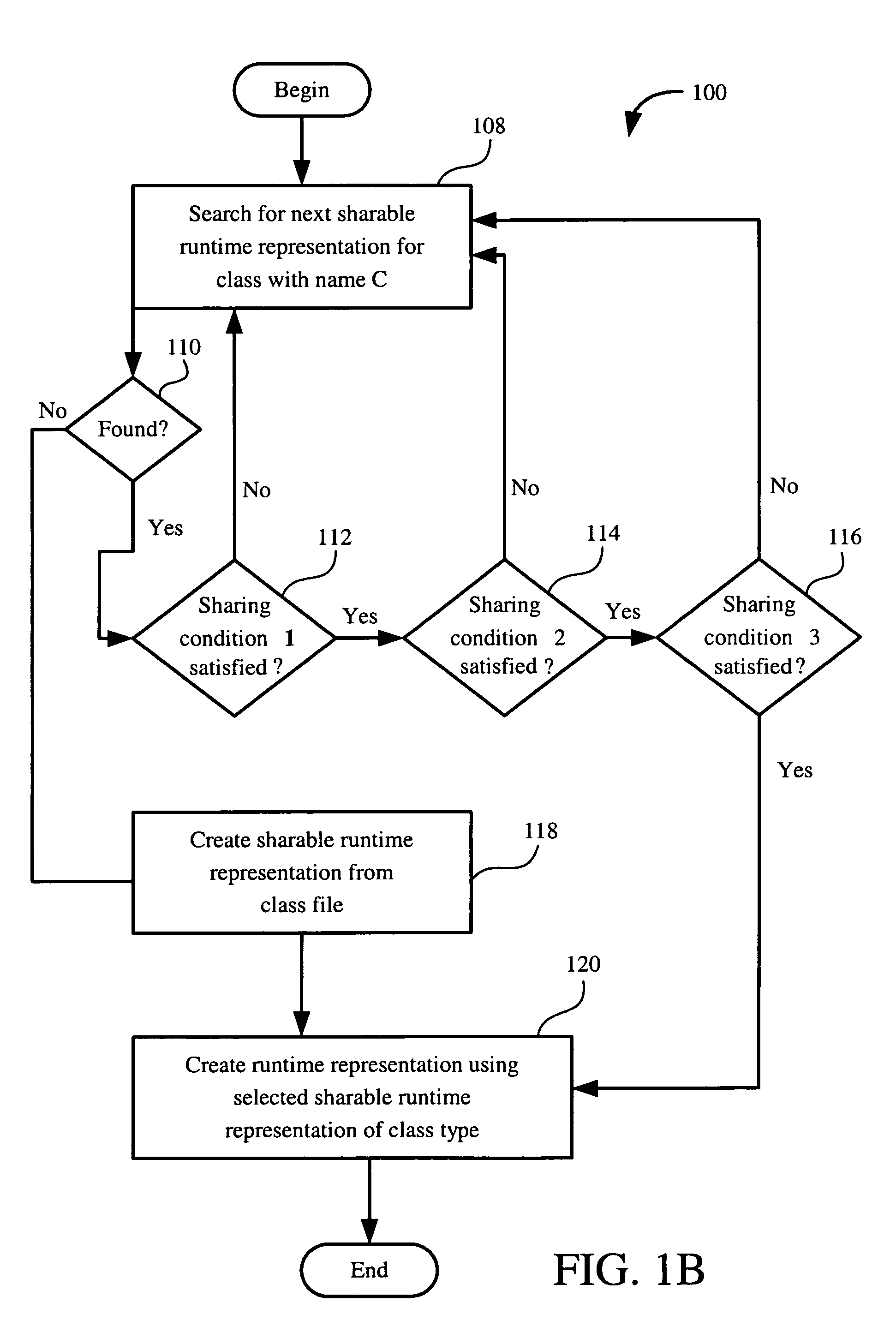
Methods for sharing of dynamically compiled code across class loaders by making the compiled code loader reentrant
A method for sharing dynamically compiled code between different class loaders is provided. In this method, loader-reentrant compiled code is produced from bytecodes by generating native code implementing a class initialization barrier when compiling bytecodes that require a class to be initialized, by generating native code implementing a link resolution barrier when compiling bytecodes that require a symbolic link to be resolved, and by generating code to retrieve loader-dependent data from a loader-dependent table when compiling bytecodes that use data computed from a resolved symbolic link.
Owner:ORACLE INT CORP
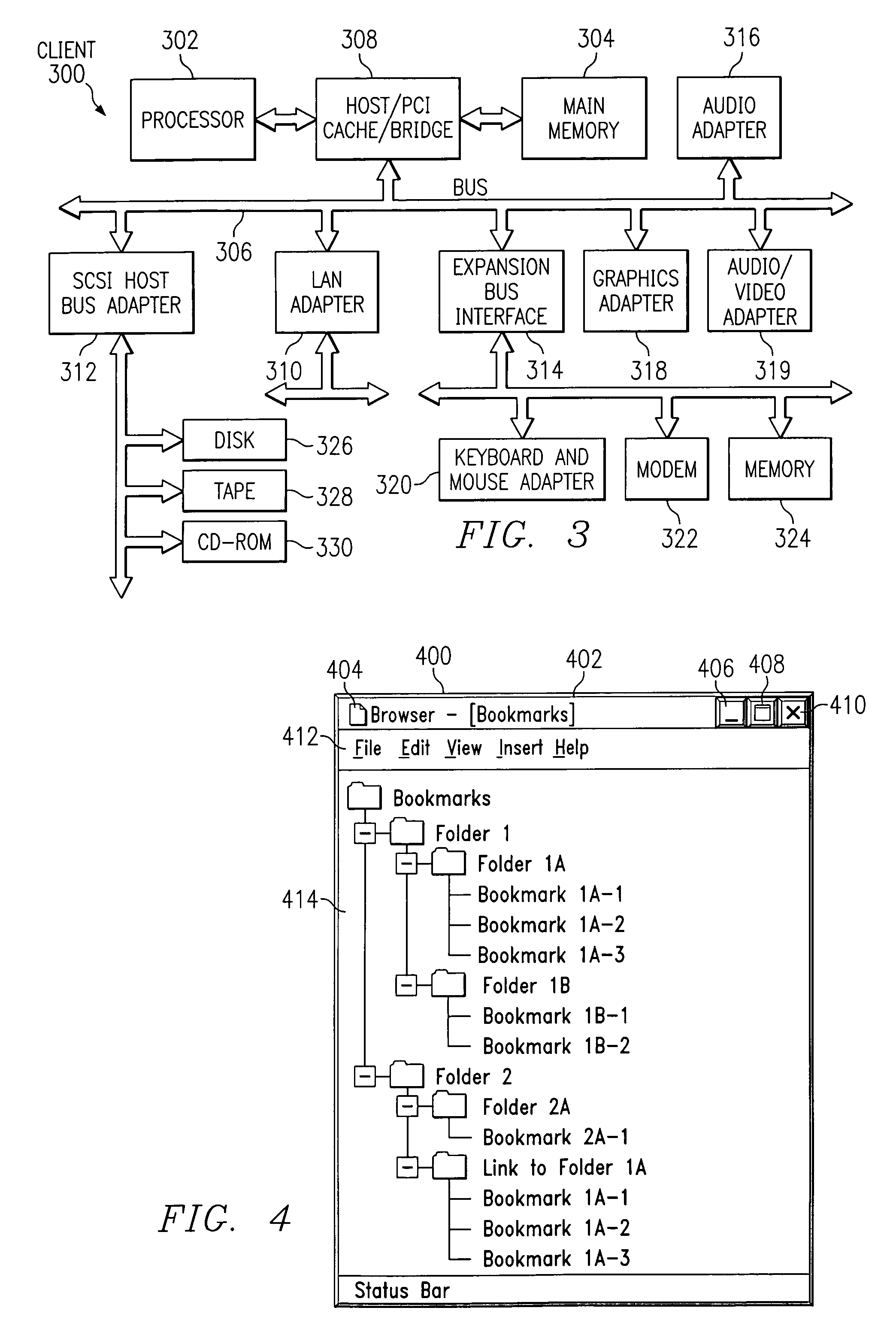
Method, apparatus, and program for creating bookmark symlinks
A bookmark editor in an Internet web browser application allows a user to create symbolic links between bookmarks and bookmark folders. The bookmark editor may also detect when a bookmark already exists for a document and prompt the user to create a link rather than a new bookmark for the same document. The user may then keep a folder, subfolder, or bookmark and link to it via a symbolic link. When a bookmark is added to a folder or subfolder, the user does not need to duplicate that bookmark for a linked folder or subfolder.
Owner:IBM CORP
Method of creating symoblic link capable of being compatible with file system, and method and apparatus for accessing file or directory by using symbolic link
ActiveUS20070162419A1Reduce inconvenienceFile access structuresPlant protectionProgramming languageSymbolic link
Provided are a method and apparatus for supporting a symbolic link at an application level while keeping the structure of an existing file system that does not support a symbolic link. The method includes receiving a symbolic link creation command including an absolute path and a symbolic link path from a user, creating a symbolic link file for the symbolic link path when the absolute path exists but the symbolic link path does not exit, and changing a value of a specified field of a directory entry of the created symbolic link file to a specified value representing the symbolic link.
Owner:SAMSUNG ELECTRONICS CO LTD
Dynamic symbolic links for referencing in a file system
InactiveUS20150100705A1Digital computer detailsData switching networksProgramming languageSymbolic link
Embodiments of the invention relate to providing dynamic absolute-path symbolic links. According to one embodiment, indication of a symbolic link is received, which references a target, the indication including an absolute path of the target that includes a target mount point and a name of the target. A current mount point of the target is identified, and a verification is made that the target mount point is identical to the current mount point. When the target mount point is identical to the current mount point, a string length of the current mount point is determined, and an in-memory record of the symbolic link is created. The in-memory record includes the string length of the current mount point associated with the symbolic link.
Owner:IBM CORP
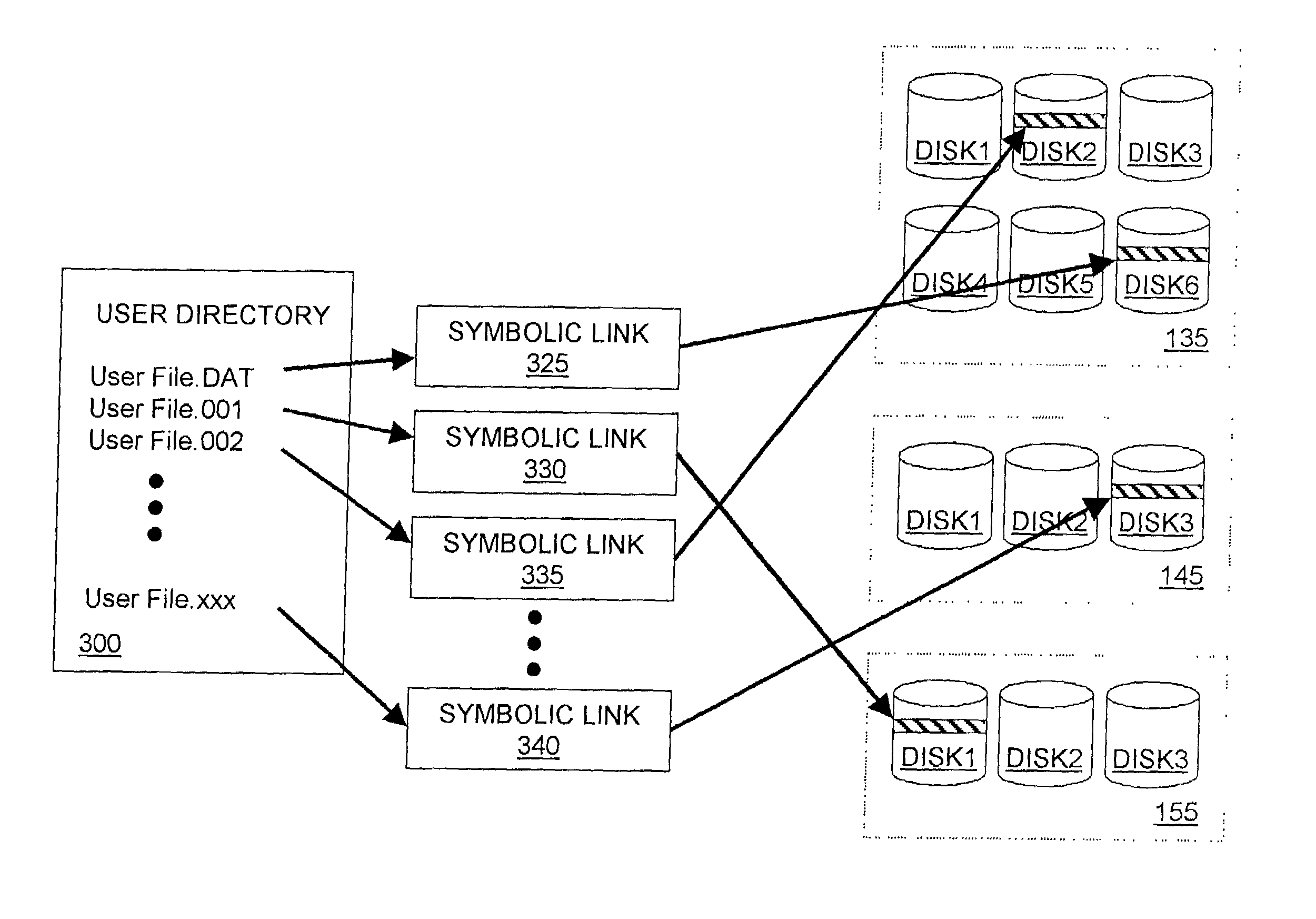
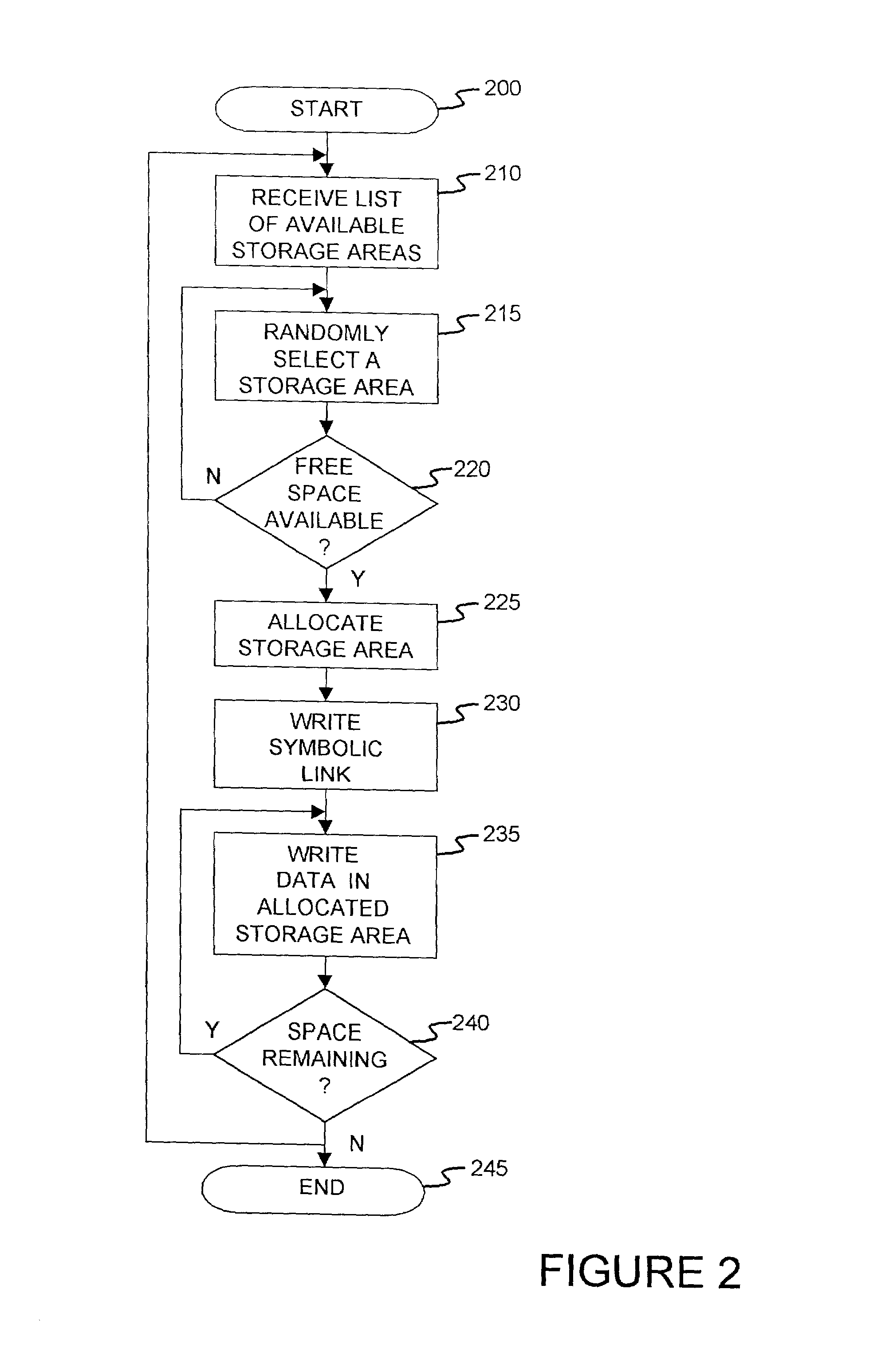
Method and apparatus for creating a virtual storage volume with a file size independent of a file size limitation
ActiveUS7136981B2Input/output to record carriersSpecial data processing applicationsSymbolic linkFile size
A method and apparatus for creating a virtual storage volume with a file size independent of a file size limitation of a computer. In one embodiment, a storage area is randomly selected from among a plurality of available storage areas. A determination is made as to whether the selected storage area contains at least a predetermined amount of free space. If so, the predetermined amount of free space is allocated on the selected storage area to create an allocated storage area. A symbolic link to the allocated storage area is written in a directory associated with the virtual storage volume. Data destined for the virtual storage volume is then written in the allocated storage area.
Owner:CONOCOPHILLIPS CO
Method and mechanism for performing a rolling upgrade of distributed computer software
ActiveUS7757226B2Minimizes or eliminates planned downtimeImprove usabilityProgram loading/initiatingMemory systemsDowntimeSymbolic link
An improved method and mechanism for performing rolling upgrades to distributed software installations is disclosed. The present approach eliminates or minimizes extraneous downtime when performing a rolling upgrade, thereby improving performance an availability for users of the software installation. A rolling upgrade can be performed by defining a private symbolic link for each member that is upgraded to reference the upgraded version of the software installation.
Owner:ORACLE INT CORP
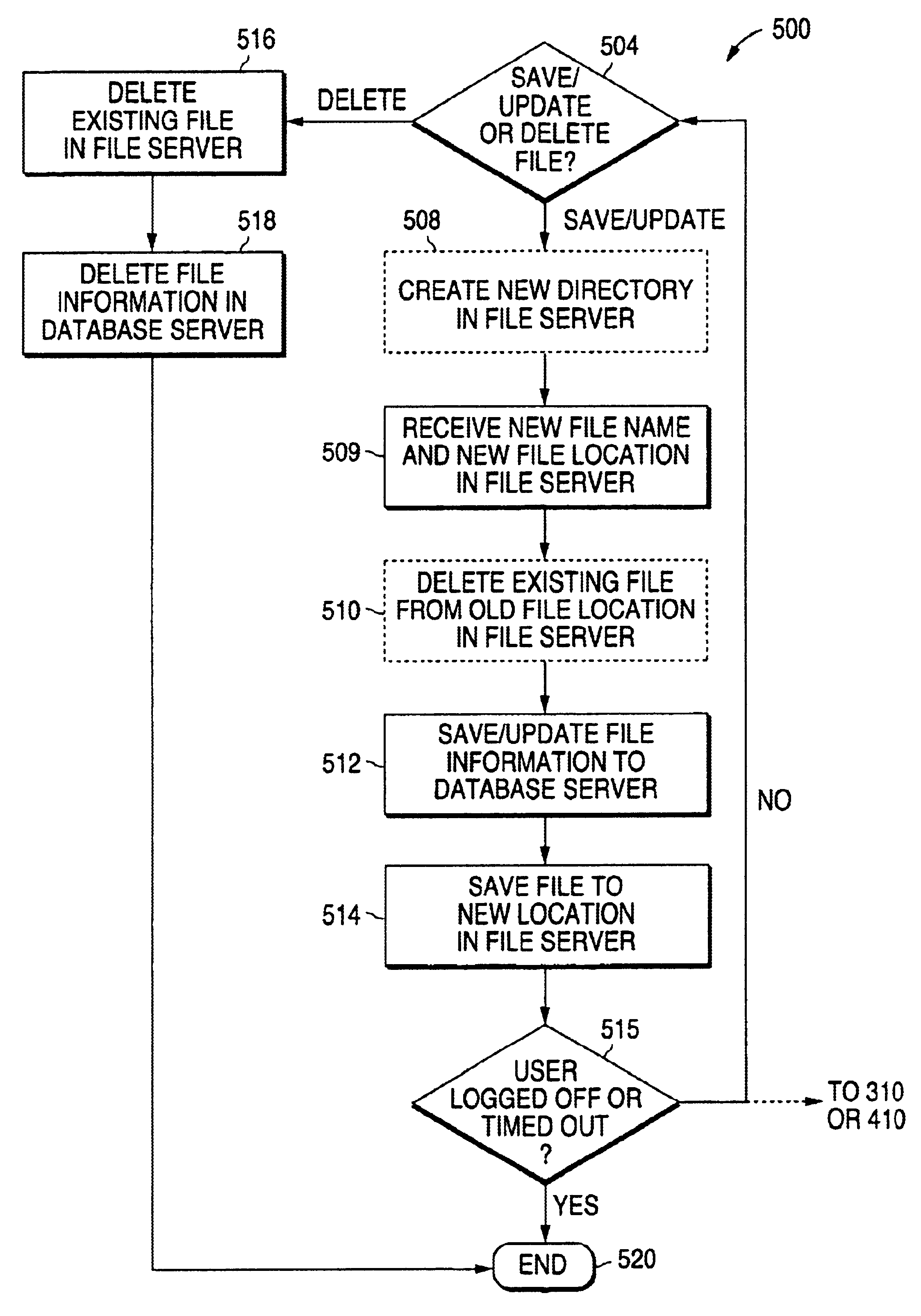
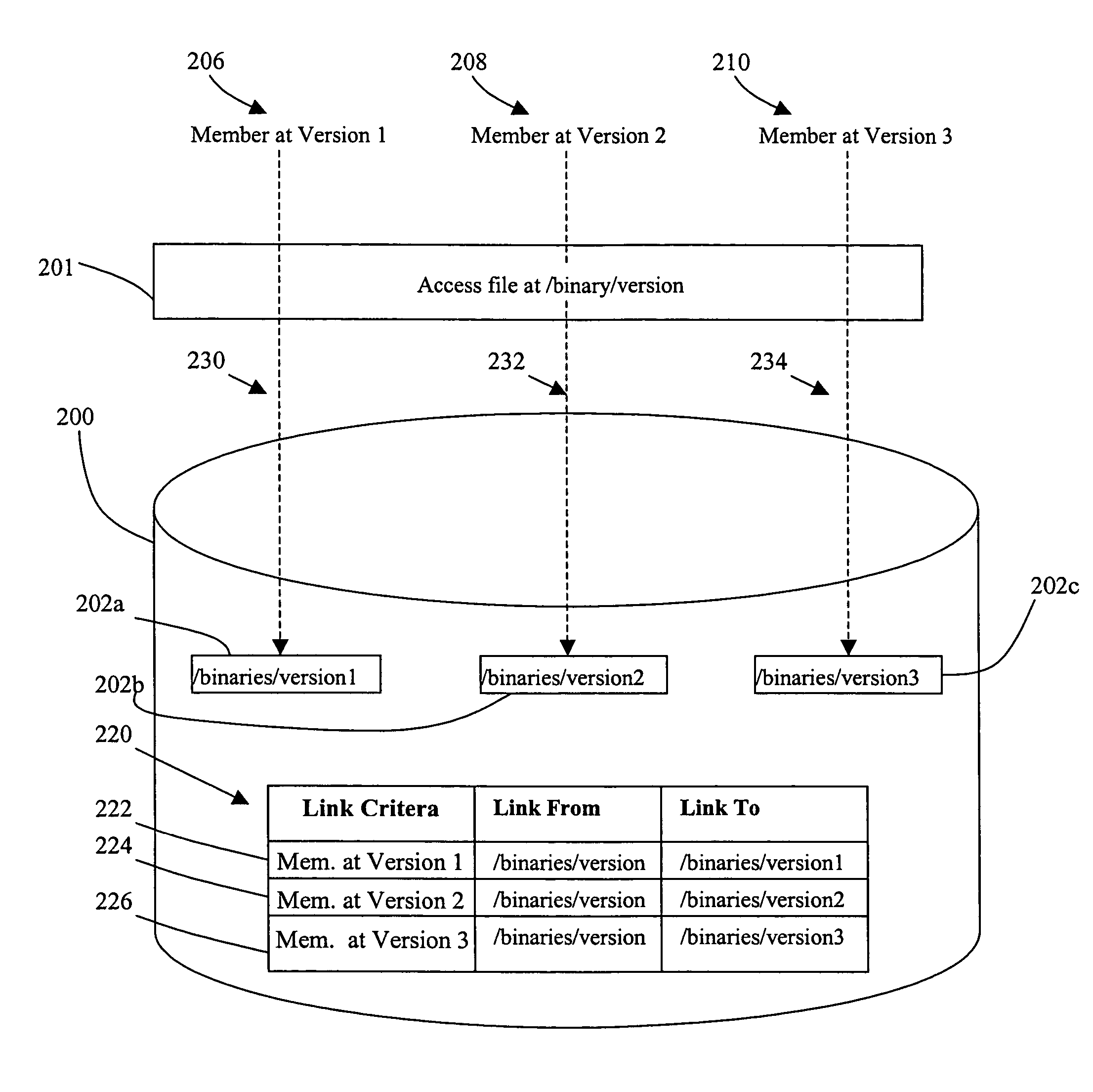
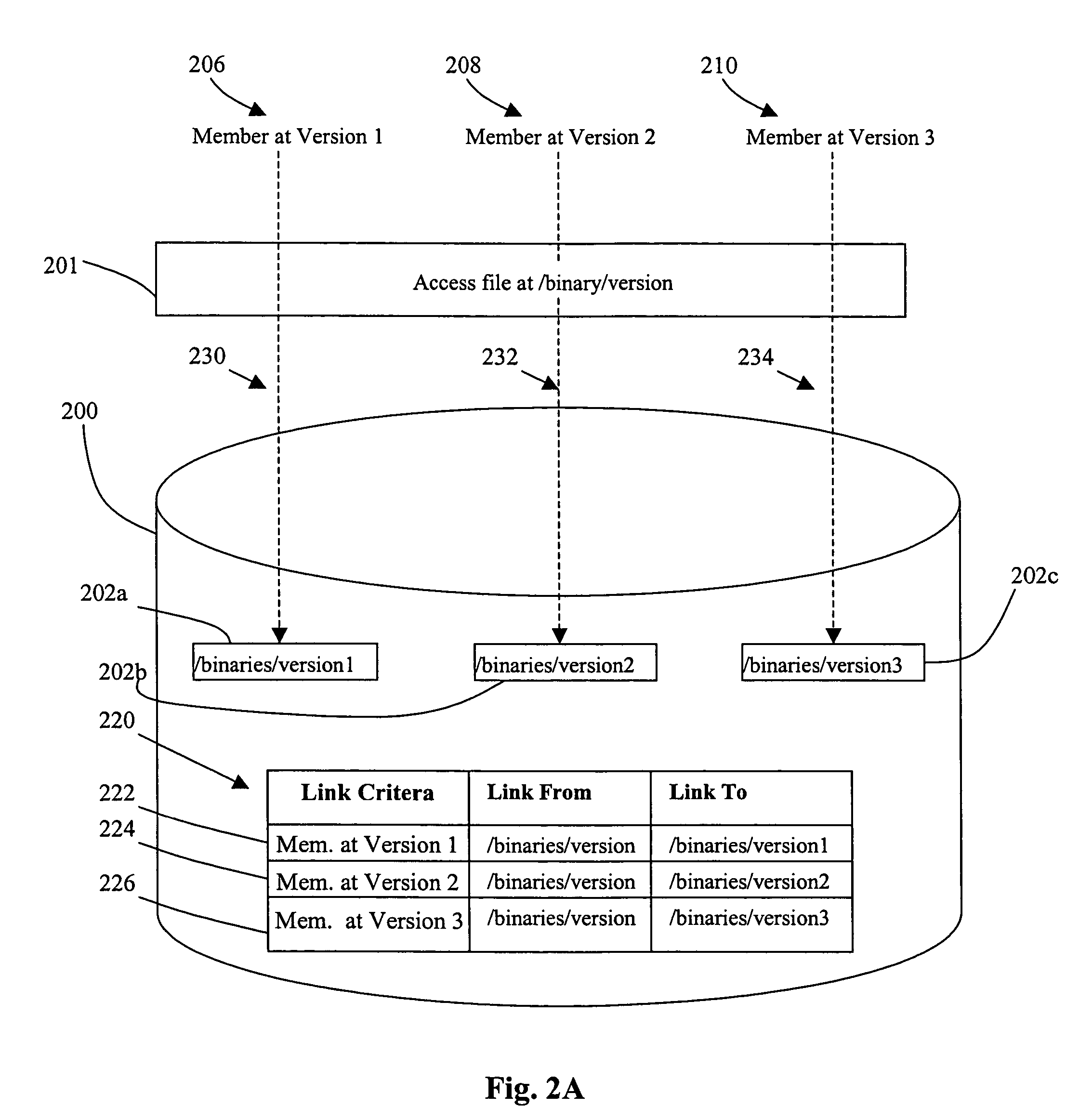
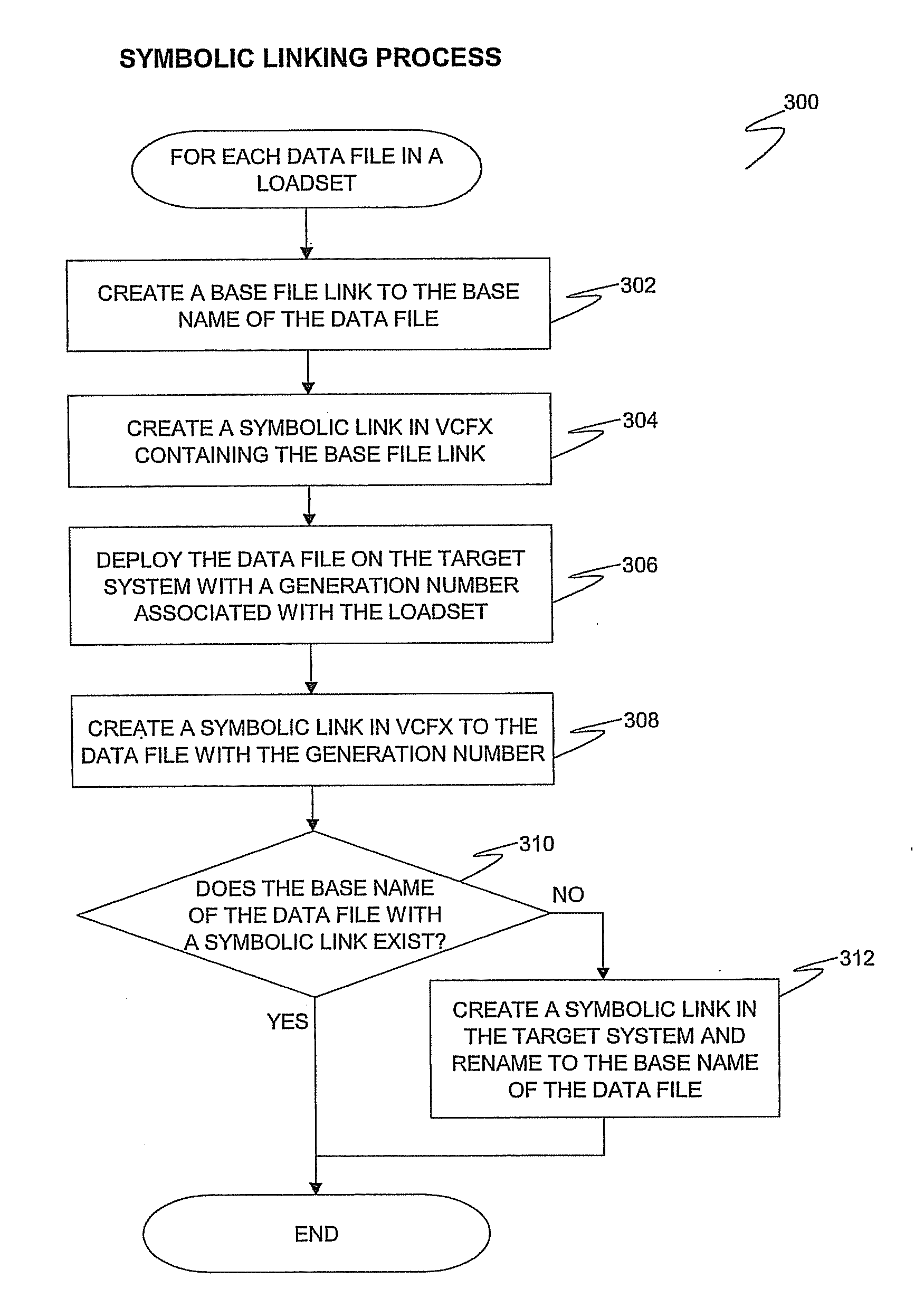
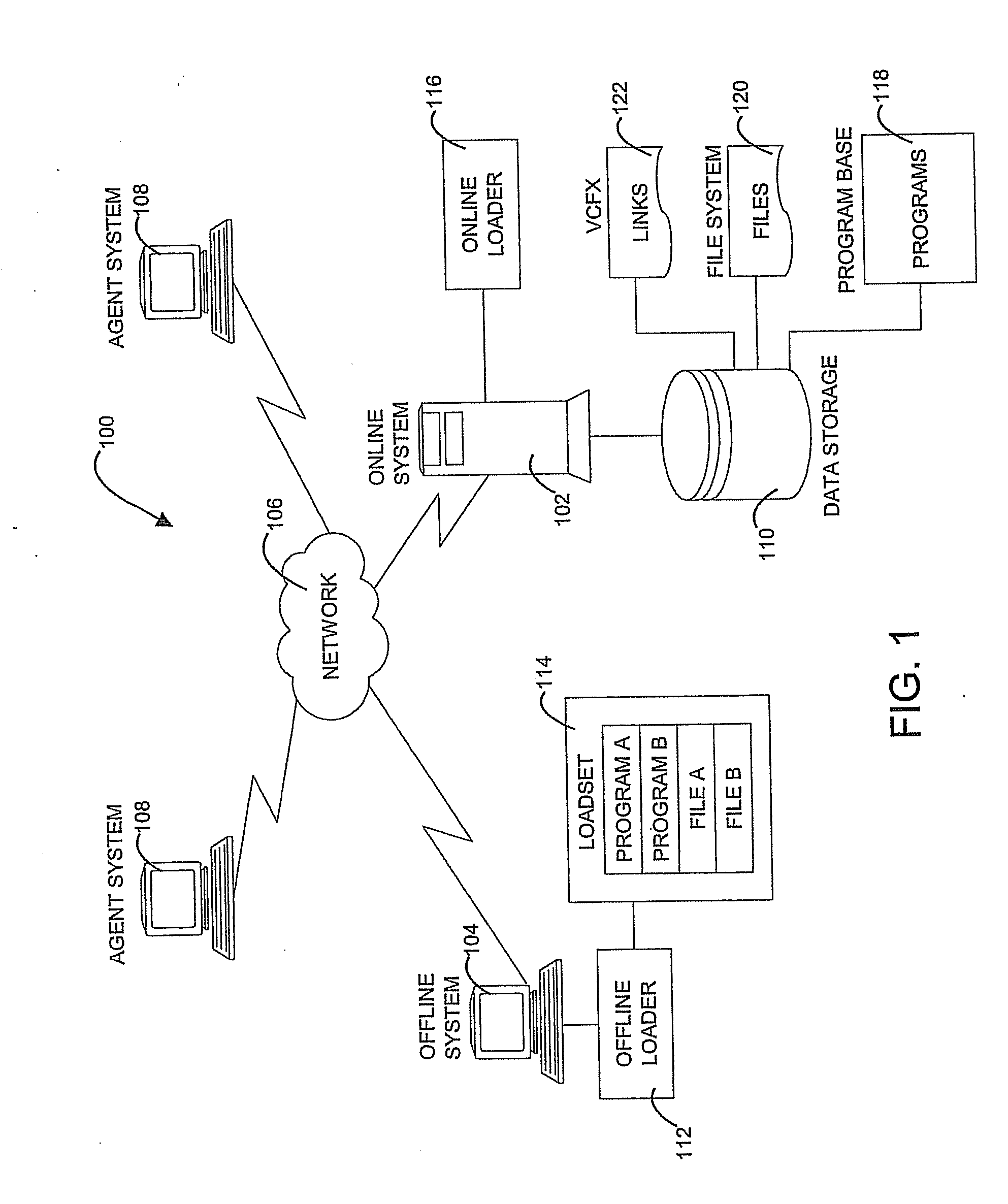
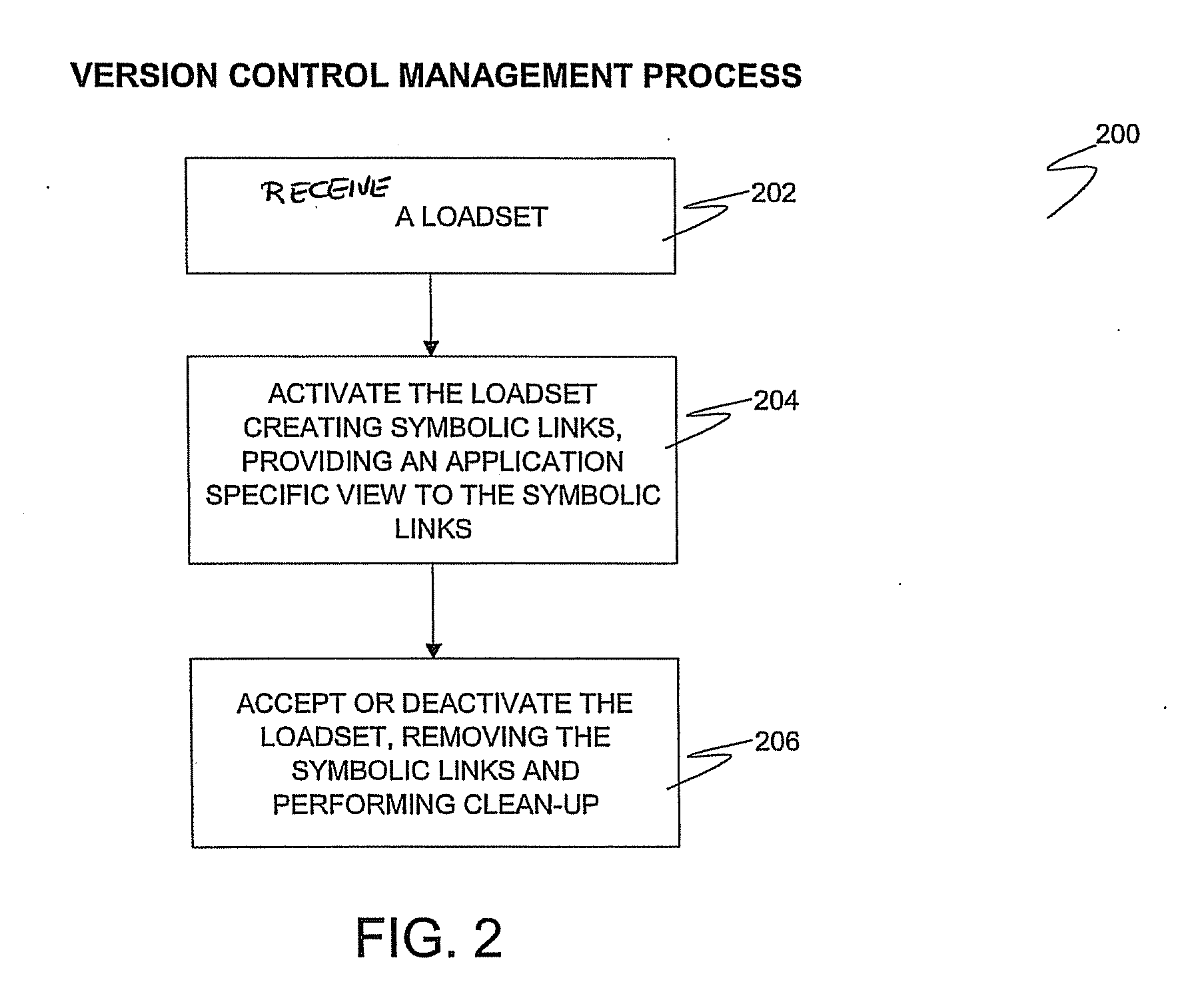
Methods, systems, and computer program products for file version control management
InactiveUS20080126440A1Limited viewData processing applicationsDigital data information retrievalData fileSymbolic link
Methods, systems, and computer program products for file version control management are provided. Methods include receiving a loadset of at least one data file and activating the loadset. For each data file in the loadset, the data file is written to a target system and identified by a base name and a generation number. A symbolic link with an activation number is created in a version control file index (VCFX) to the data file written to the target system. An application view to the symbolic link is provided as the base name of the data file, and the application view to the symbolic link is limited based on an activation number of the application corresponding to the activation number of the symbolic link.
Owner:IBM CORP
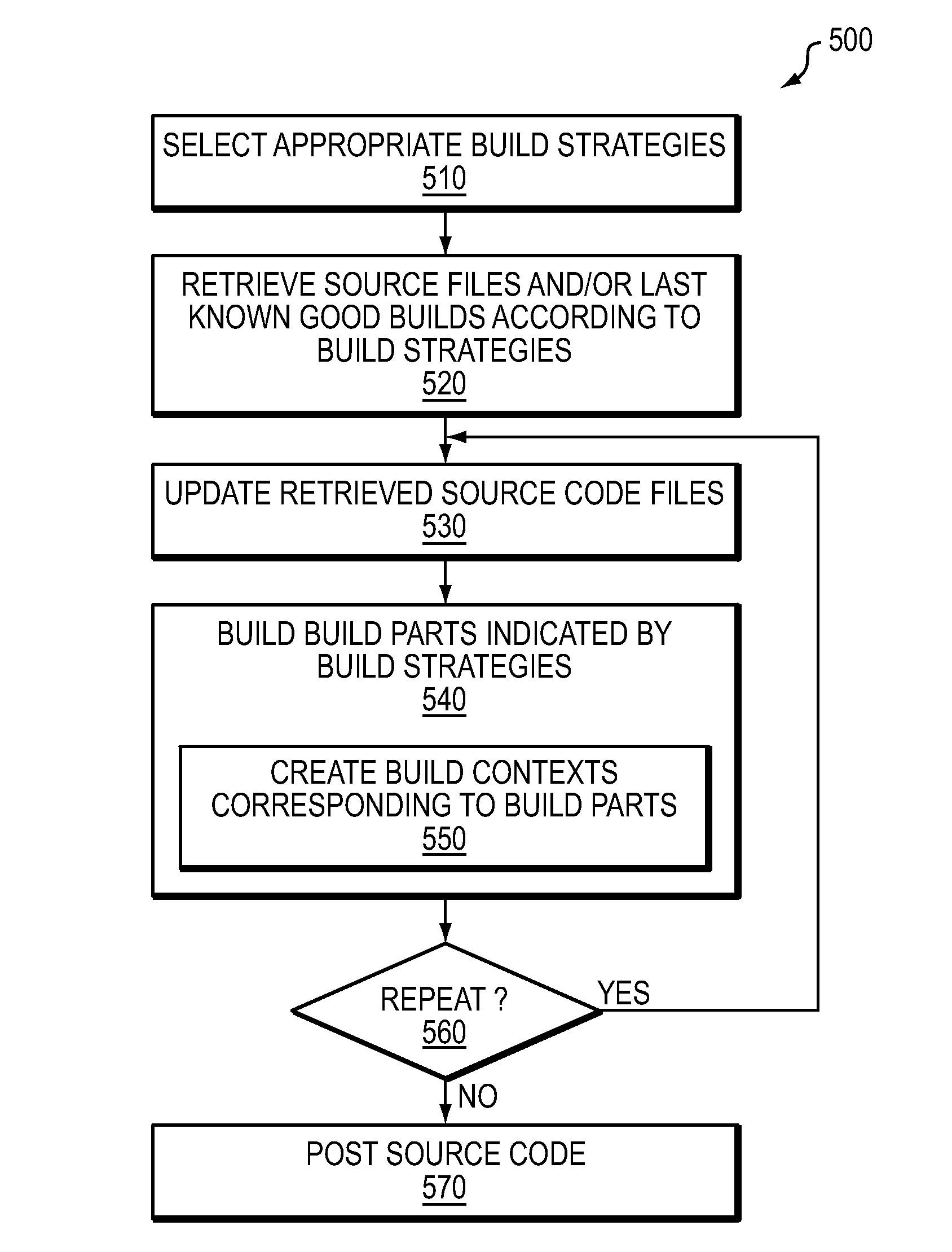
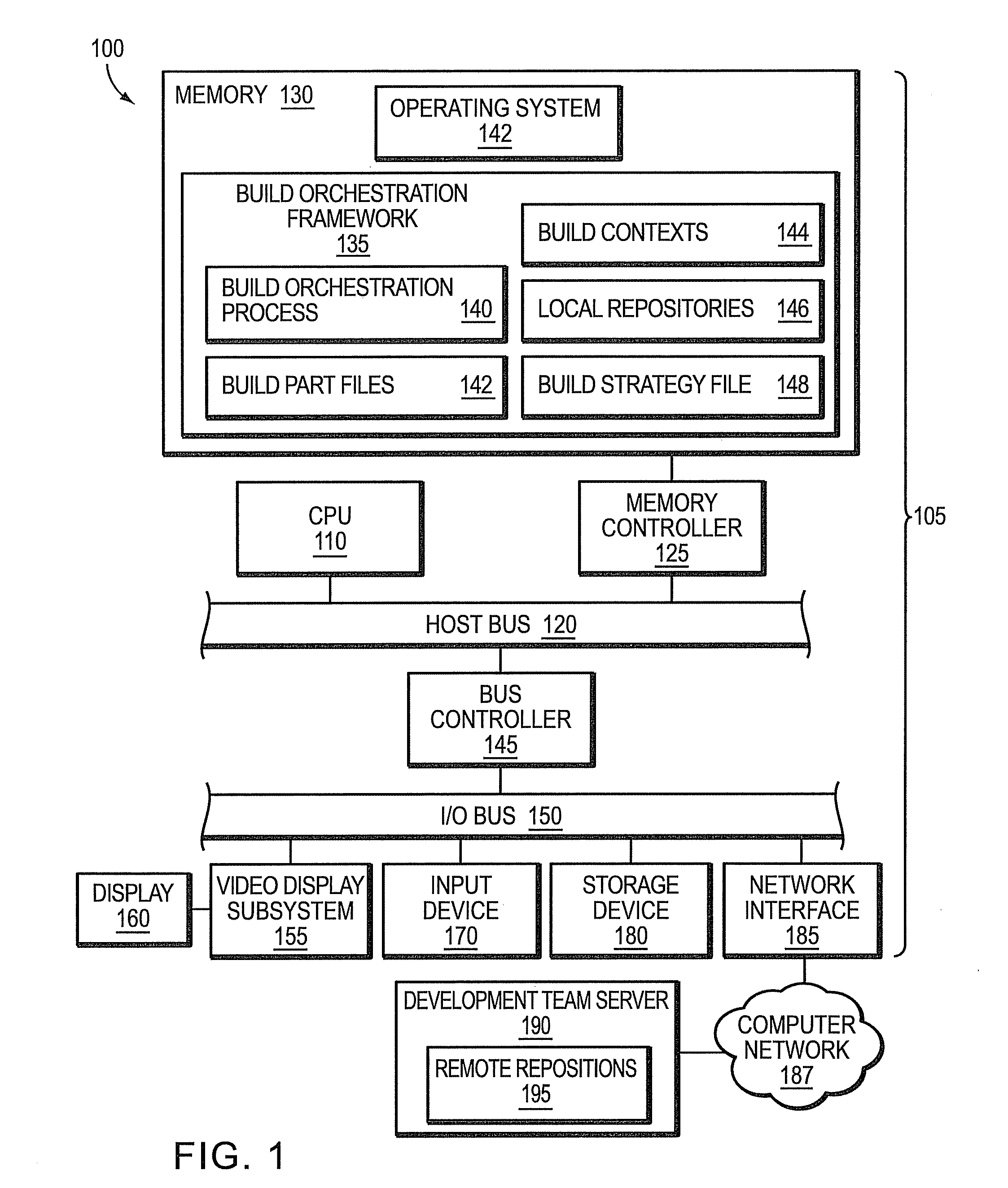
Software build orchestration framework
ActiveUS8381176B1Efficient and reliable buildingVersion controlSpecific program execution arrangementsSymbolic linkOrchestration
In one embodiment, a build orchestration framework orchestrates building of one or more individual buildable components of a deliverable software product. At least some buildable components reference respective sub components on which they depend. Building creates a structure associated with each respective buildable component of the one or more buildable components. In this structure, if the respective buildable component references a sub component on which the respective buildable component depends, a symbolic link is created to an output of a build of the sub component to provide access to the output of the sub component for use in building the respective buildable component. Further, in this structure, if the respective buildable component is used by another buildable component, a symbolic link is created to an output of a build of the respective buildable component.
Owner:BENTLEY SYST INC
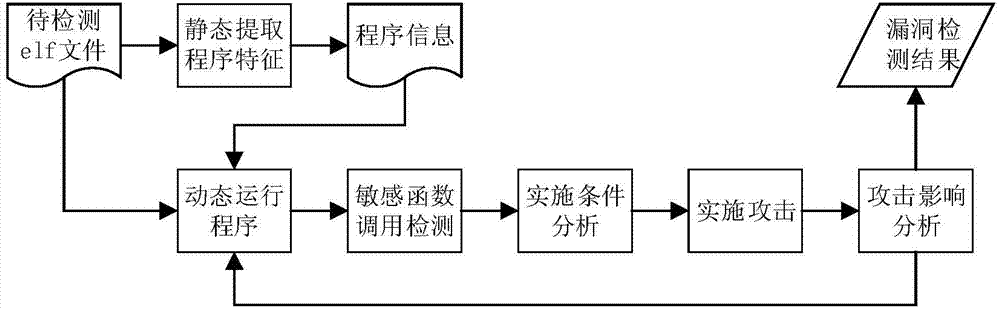
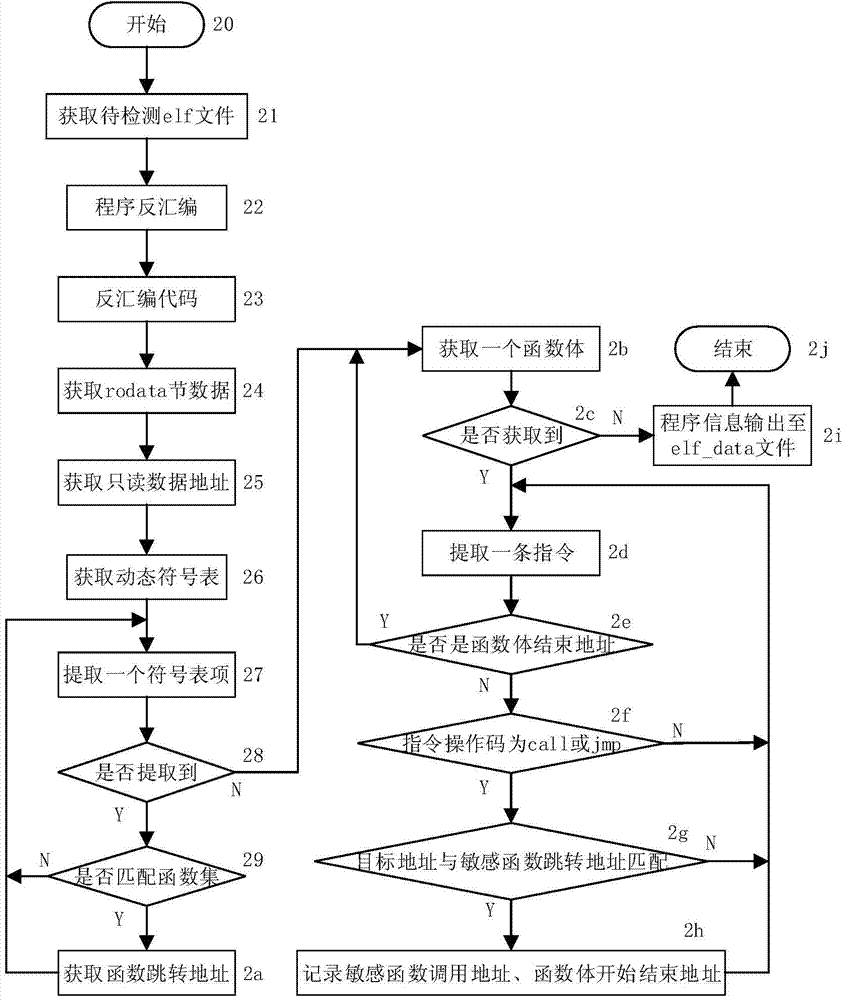
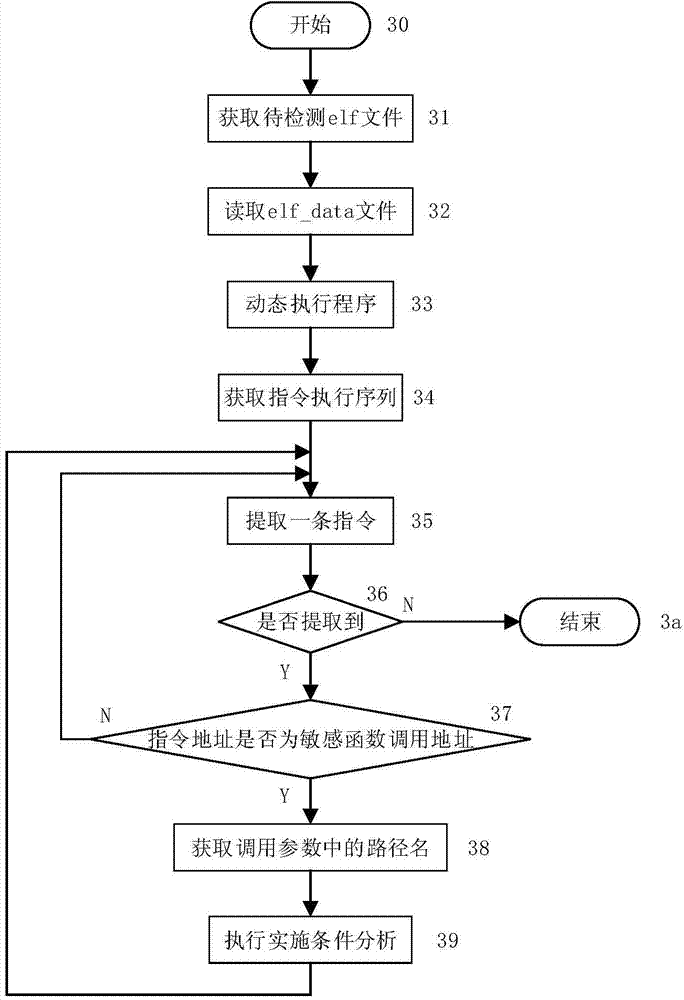
Software vulnerability detection method based on simulation attack
ActiveCN104778413AEfficient detectionReduce false positivesPlatform integrity maintainanceSimulation basedSymbolic link
The invention discloses a software vulnerability detection method based on simulation attack. Function information related to sensitive operation is acquired through a static disassembling tool, and the processes of monitoring, attack simulation, attack influence analysis and the like are realized by using a dynamic inserting pile platform. The method mainly comprises the following steps: (1) executing static analysis to obtain program information; (2) dynamically executing a program, and detecting sensitive function calling; (3) analyzing an attack implementation condition; (4) executing simulation attack; (5) analyzing attack influences, and making a vulnerability judgment according to an attack influence result. In specific implementation, simulation attack is performed on the program by adopting a symbolic link, a corresponding vulnerability type is type I file access vulnerability, and through utilizing the vulnerability, a local attacker updates the program through the symbolic link to access a file as expected, so that access to file resources beyond the right of the attacker is realized.
Owner:NANJING UNIV
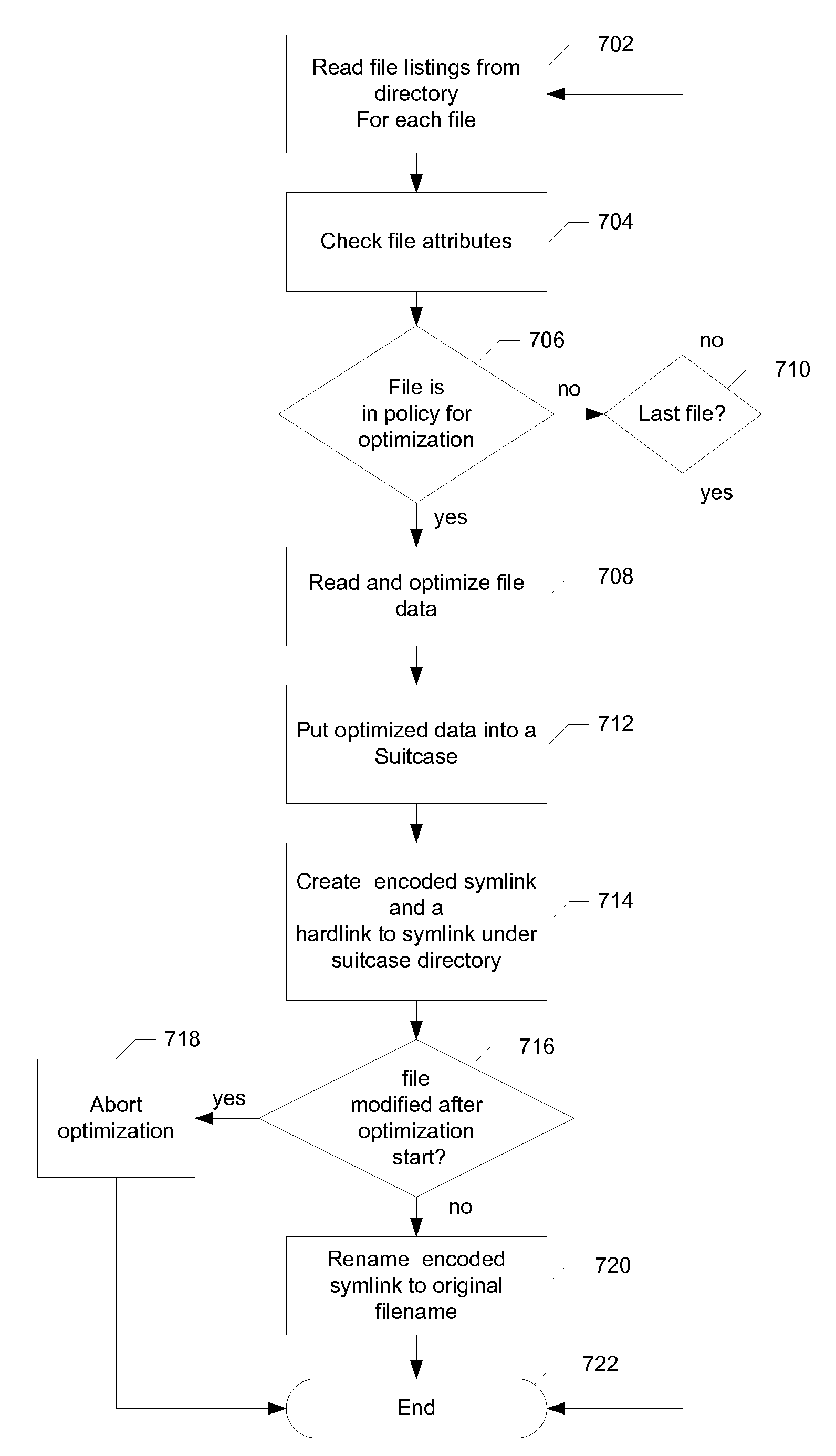
Representing and storing an optimized file system using a system of symlinks, hardlinks and file archives
ActiveUS20100094813A1Efficient formationDigital data information retrievalDigital data processing detailsSymbolic linkData loss
A data de-duplication system is used with network attached storage and serves to reduce data duplication and file storage costs. Techniques utilizing both symlinks and hardlinks ensure efficient deletion file / data cleanup and avoid data loss in the event of crashes.
Owner:QUEST SOFTWARE INC
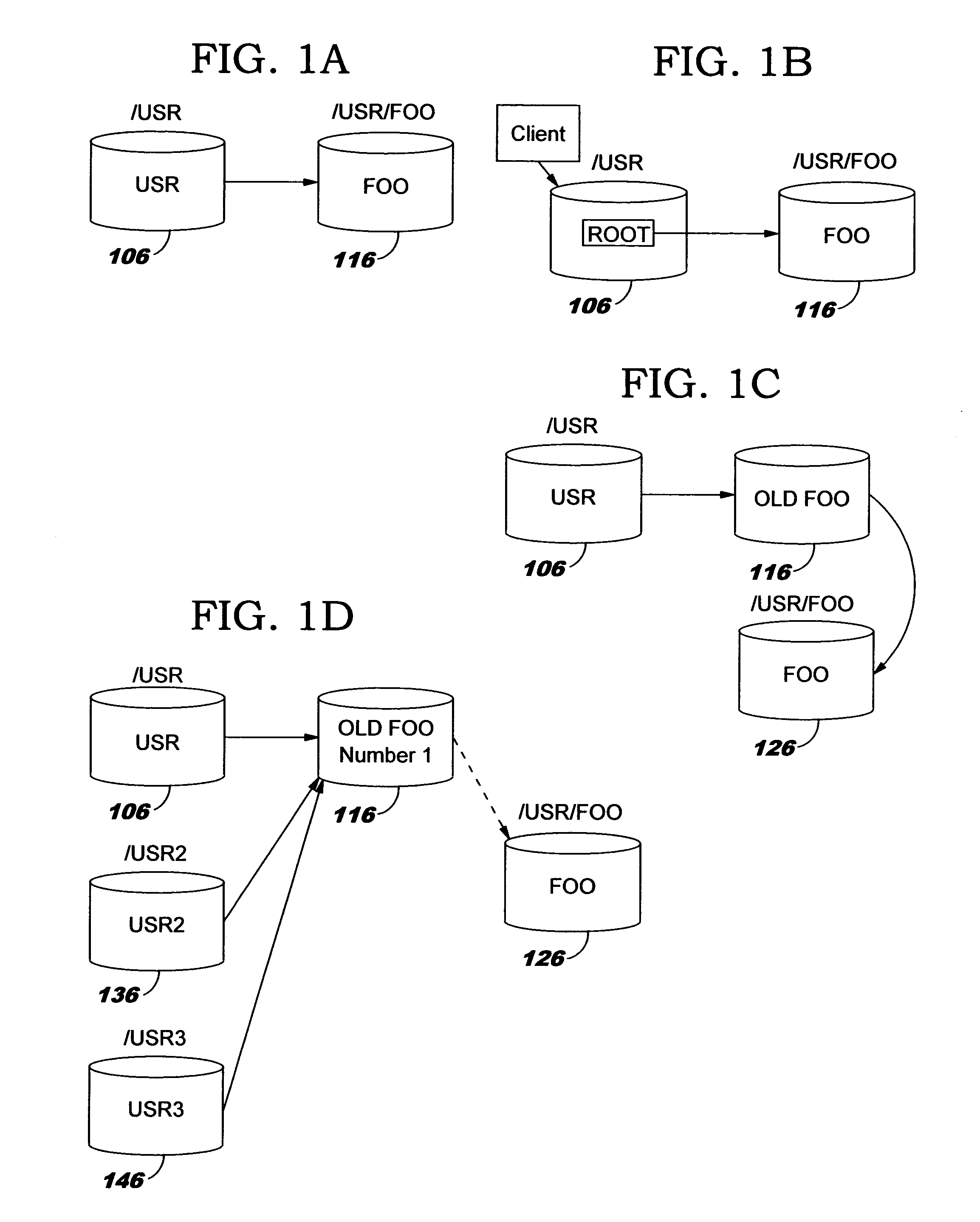
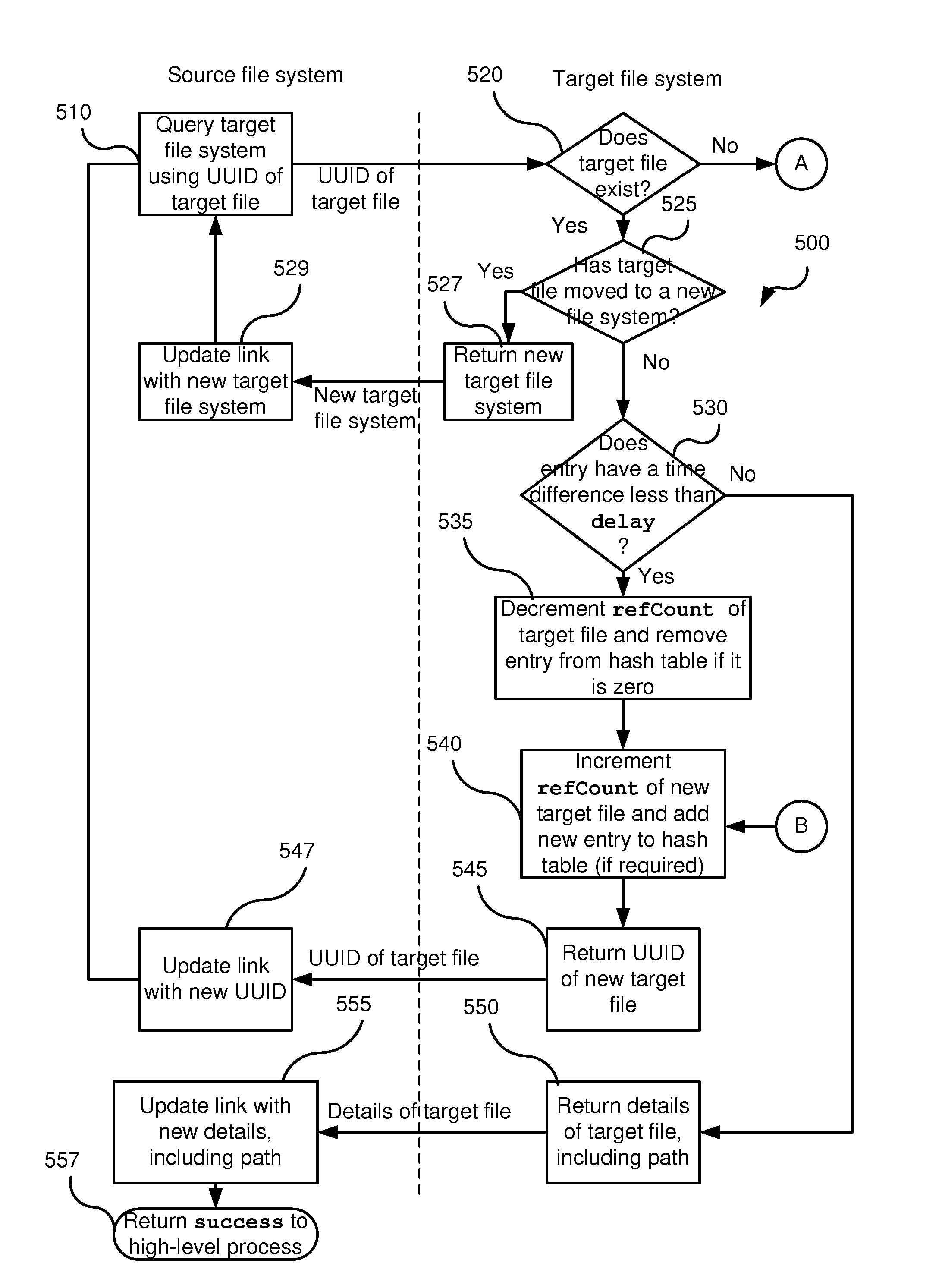
Management of symbolic links
ActiveUS20100030739A1Improve robustnessDigital data processing detailsFile/folder operationsSymbolic linkEngineering
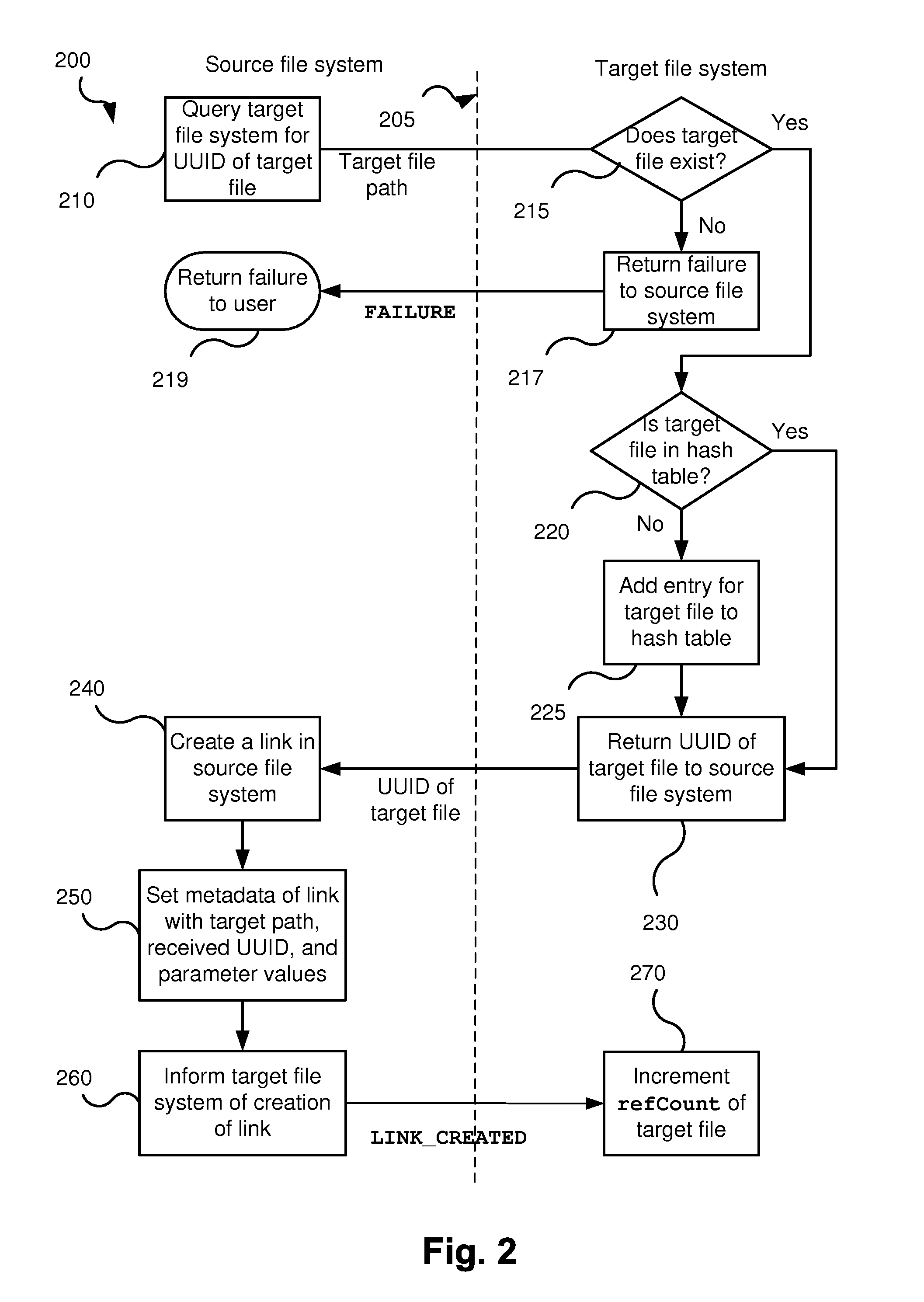
Disclosed is a method of creating a symbolic link in a source file system to a target file in a target file system, the method including querying the target file system for an identifier of the target file; incrementing a reference counter of the target file, the reference counter indicating how many symbolic links the target file is a target of; and creating the symbolic link in the source file system, the symbolic link including the identifier received from the target file system in response to the query.
Owner:IBM CORP
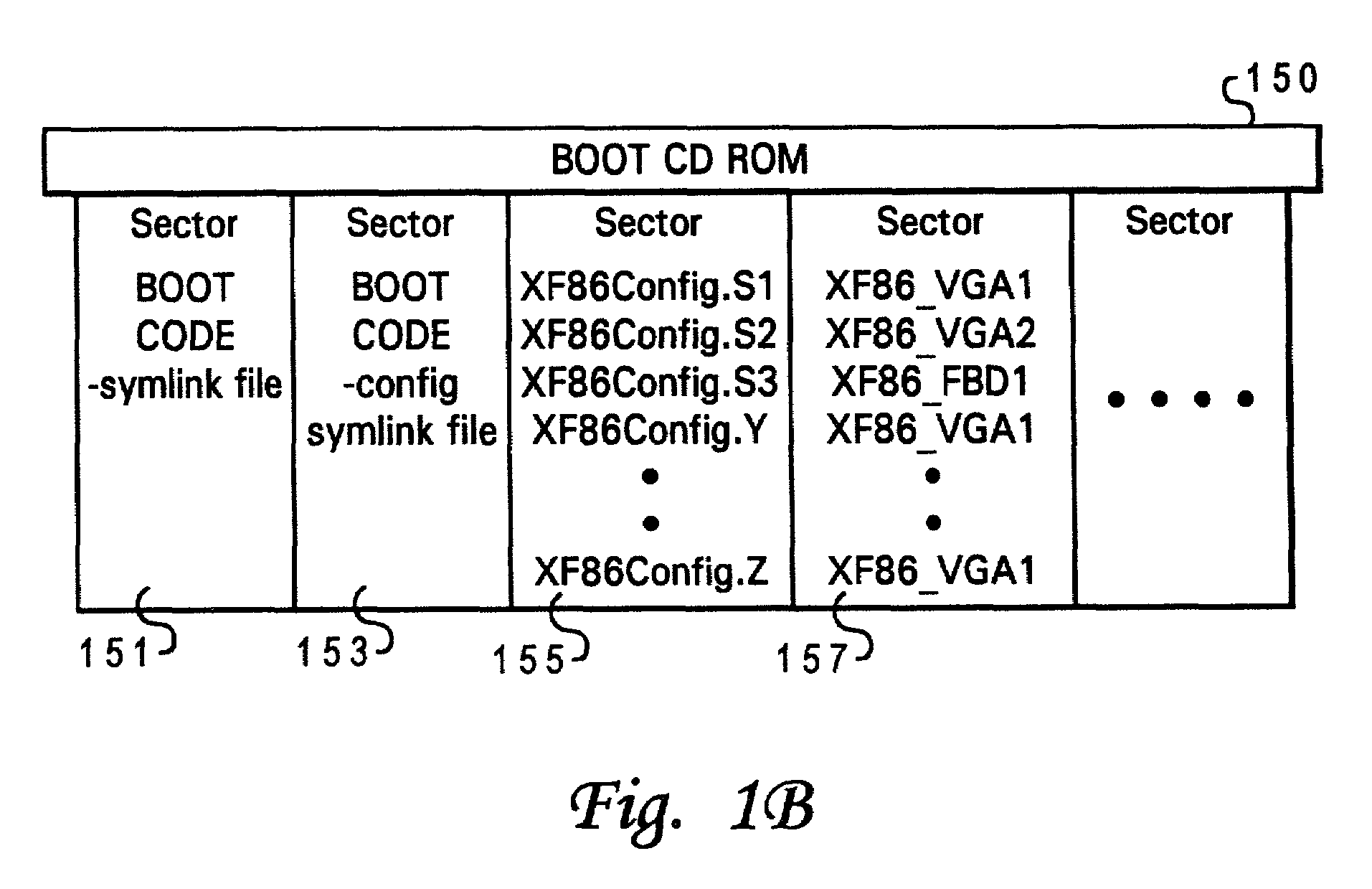
Method and system of dynamic video driver selection on a bootable CD via symbolic links
InactiveUS6993643B2Digital computer detailsProgram loading/initiatingData processing systemSymbolic link
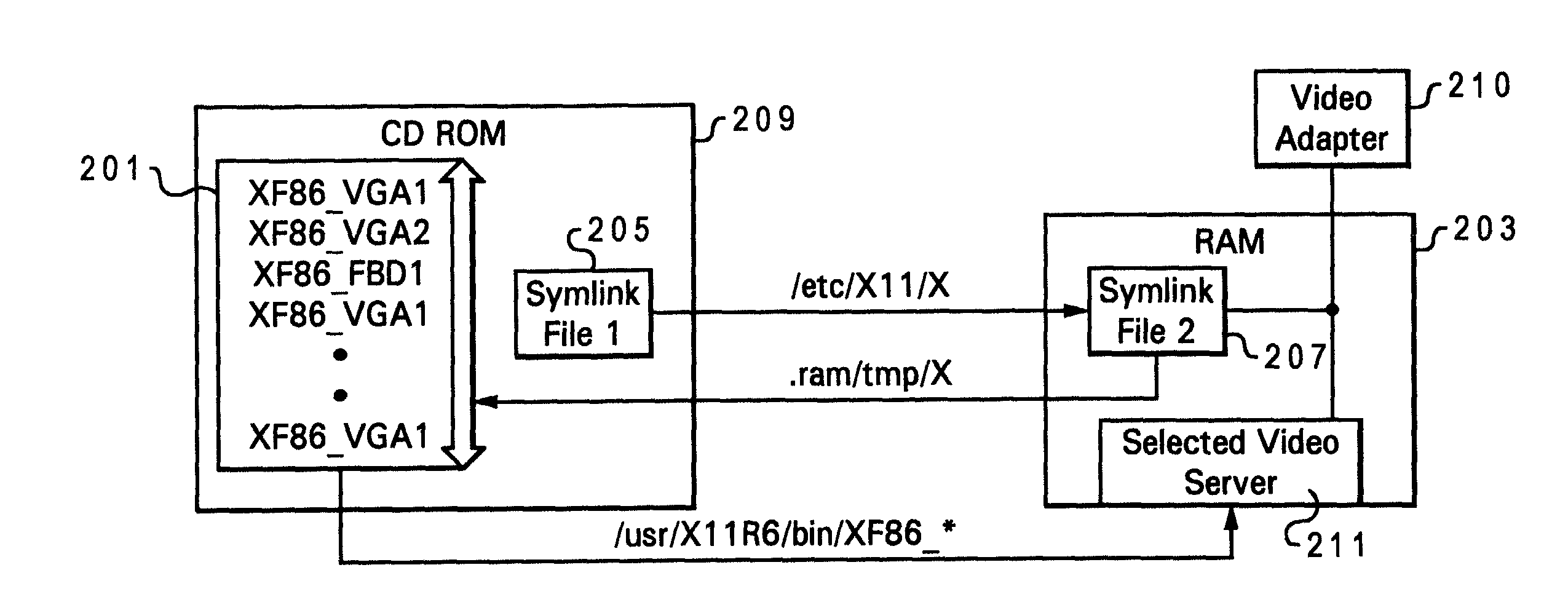
A method, system, and program product for enabling selection of appropriate, available resources for a hardware component of a data processing system during system boot via a read only medium. The method comprises various steps including first initiating a boot process from the read only medium on the data processing system. The type of hardware component is then detected and, responsive to the detection of a specific component type, an object of a symlink file located on RAM is dynamically set to reflect the particular resource required for optimal operation of the hardware component. A symlink file located on the read only medium points to and triggers the activation of the symlink file on RAM. The first symlink file on RAM points to and selects the particular resource set as its object from among multiple available resources located on the read only medium. The selected resource is utilized to support the hardware component during operation of the data processing system.
Owner:LENOVO GLOBAL TECH INT LTD
System and method of managing documents using bookmarks
InactiveUS7664825B2Natural language data processingMultiple digital computer combinationsHard disc driveDocumentation procedure
A system and method for managing documents within a shared peripheral includes a network-based document management system. A document management module of defines a bookmark or symbolic link to a document stored inside or outside a document management module repository. The symbolic link is treated analogously to other documents managed by the document management module. Upon linking to a document networked, the system enables users to download a document stored in the repository to devices including a local machine or network hard drive.
Owner:TOSHIBA TEC KK
Implementing standards-based file operations in proprietary operating systems
InactiveUS6970892B2Reduce the numberData processing applicationsSpecial data processing applicationsOperational systemSymbolic link
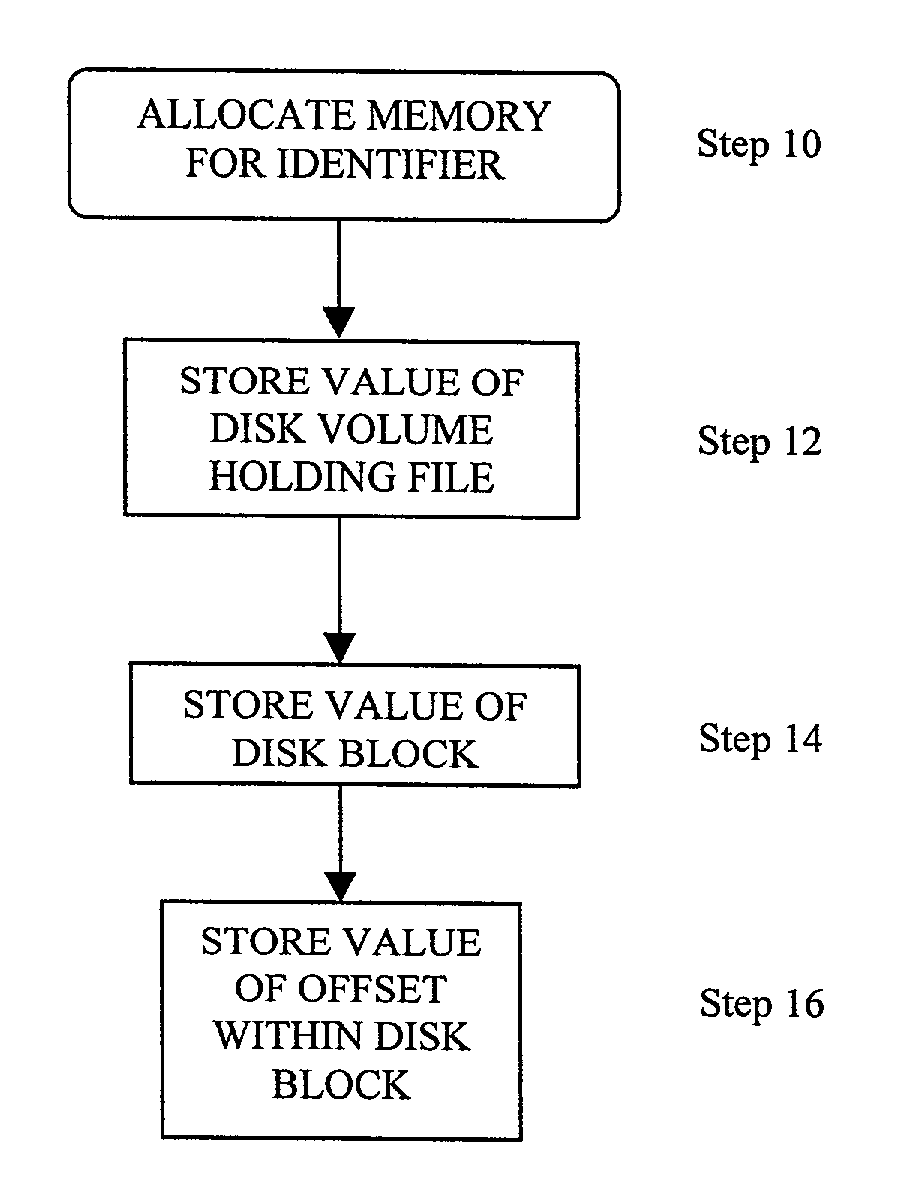
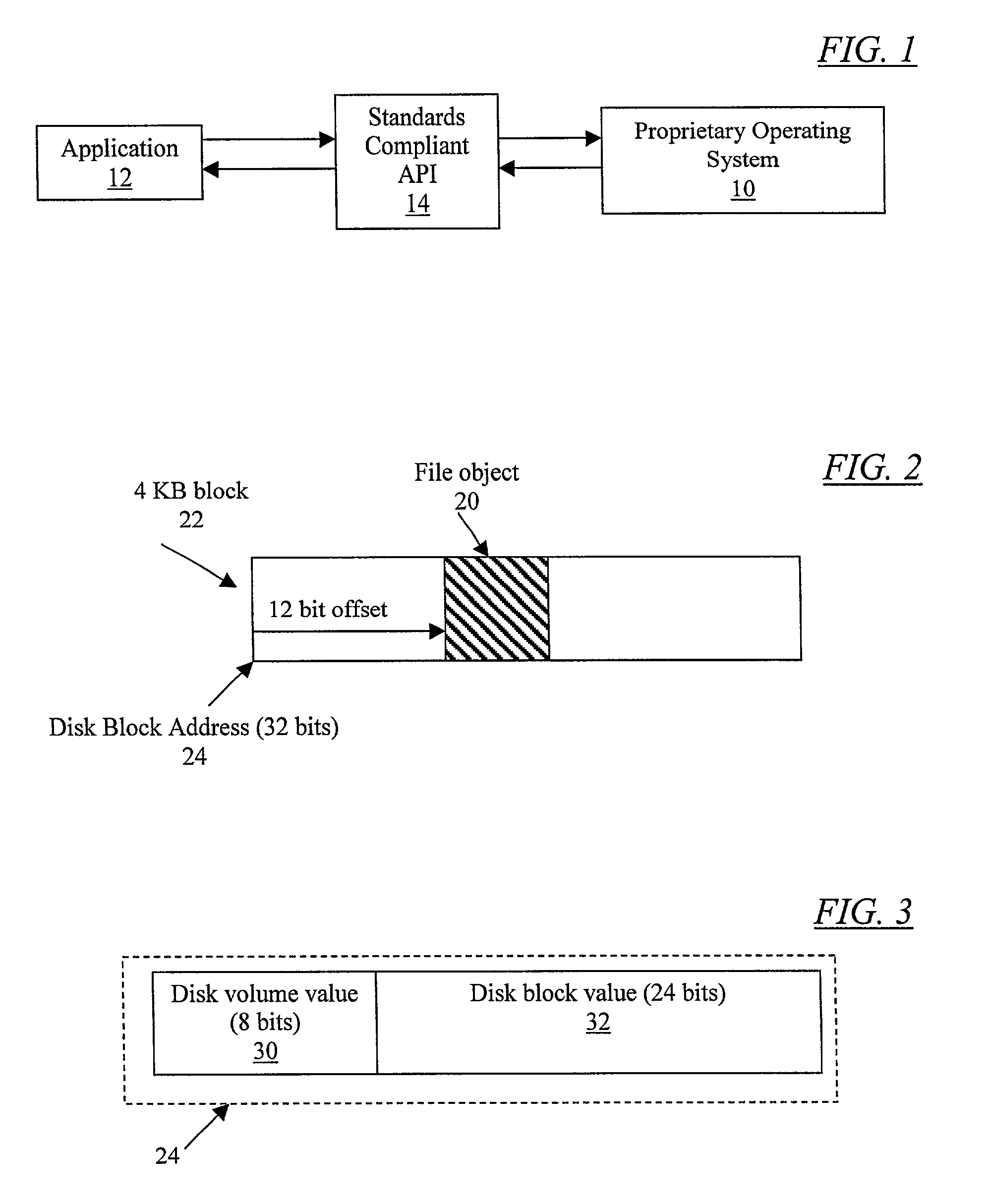
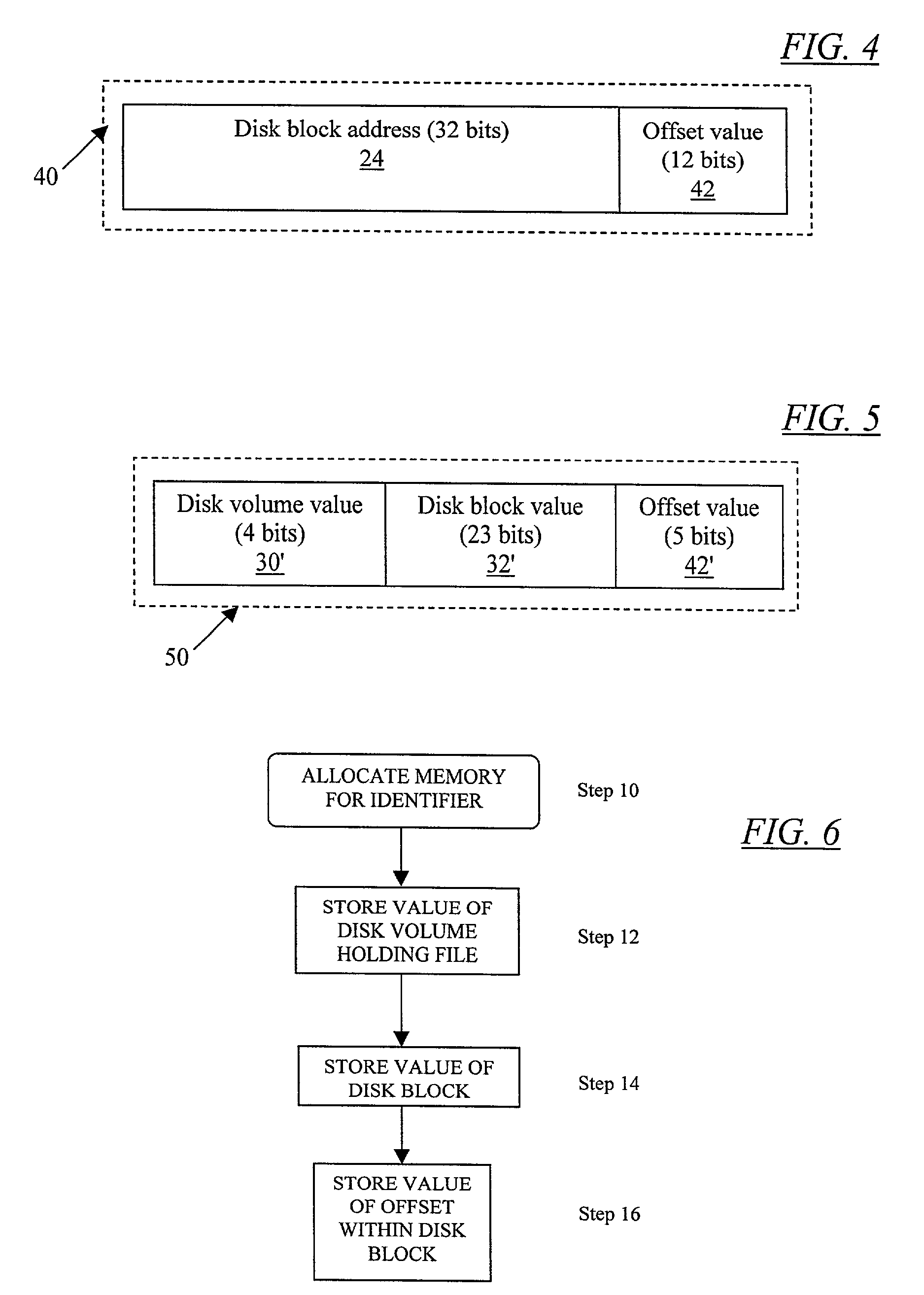
A method for generating a file object identifier. A computer allocates memory to store the identifier. The disk volume holding the file object, the disk block holding the file object, and the value of the offset within the disk block holding the file object are stored in the allocated memory. In one embodiment, the file object is a file, a directory, or a symbolic link. In another embodiment, the memory allocated is 32 bits. In yet another embodiment, the disk volume value is a 4-bit value. In still another embodiment, the disk block value is a 23-bit value. In another embodiment, the block offset value is a 5-bit value. In another embodiment, the offset within the disk block is a multiple of 128 byte increments. In one embodiment, the generated file object identifier is a PORTABLE OPERATING SYSTEM INTERFACE (POSIX) file serial number.
Owner:STRATUS TECH IRELAND LTD
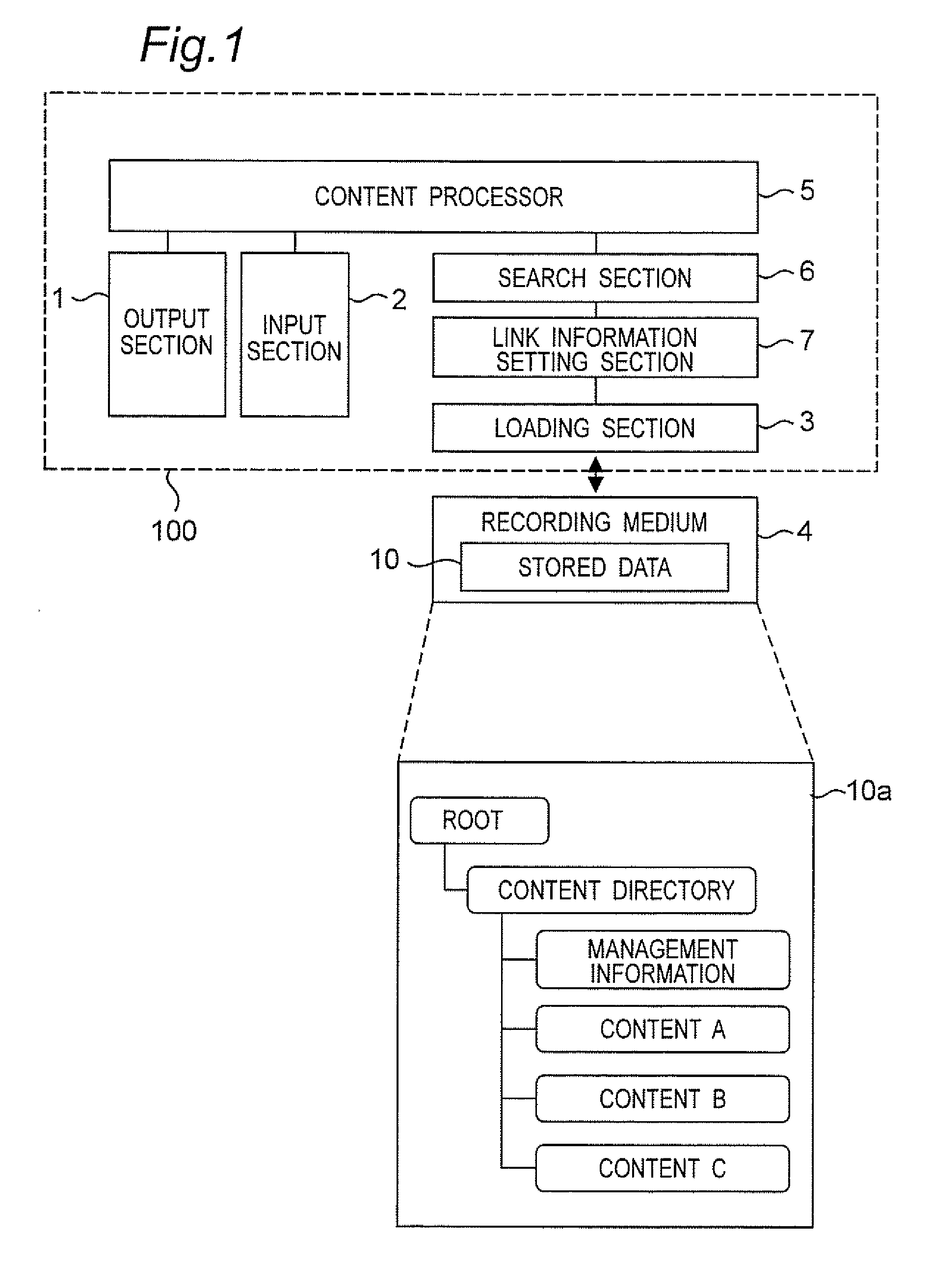
Data processing apparatus and data processing method
InactiveUS20070174334A1Large capacityImprove portabilityDigital data processing detailsColor television signals processingSymbolic linkManagement information systems
A data processing apparatus is capable of playing back contents stored in a specified area in a recording medium. The recording medium stores content data and management information for managing the content data. When playing back a content which is managed by the management information on the recording medium but of which entity data is not present in the specified area of the recording medium, the data processing apparatus, searches, for the content, the other area of the recording medium with a search section. When the corresponding content is found, the link information setting section sets the link information (symbolic link, shortcut, etc.) on the recording medium so that the content can be accessed with the management information.
Owner:GK BRIDGE 1
Method and system for transparent restore of junction file types
ActiveUS8412896B1Error detection/correctionSpecial data processing applicationsThird partyData stream
A method and system for backing up and restoring data in a file system that includes junctions is provided. In a backup operation, a junction is encoded as a symbolic link (“symlink”) directive, and sent with a sequential image data stream in the backup operation and written to a tape or disk. In a restore operation, when the encoded symlink directive is encountered after data is read from the tape, the symlink is decoded by an administrator to obtain the embedded junction information contained in the symlink directive. The administrator can then recreate the junction using the information. The junction information is thereby transmitted as part of the backup and restore operation while remaining transparent to third party software performing the backup and restore processes.
Owner:NETWORK APPLIANCE INC
Virtual System Administration Environment For Non-Root User
InactiveUS20110264718A1Specific access rightsDigital data information retrievalVirtual file systemSystems management
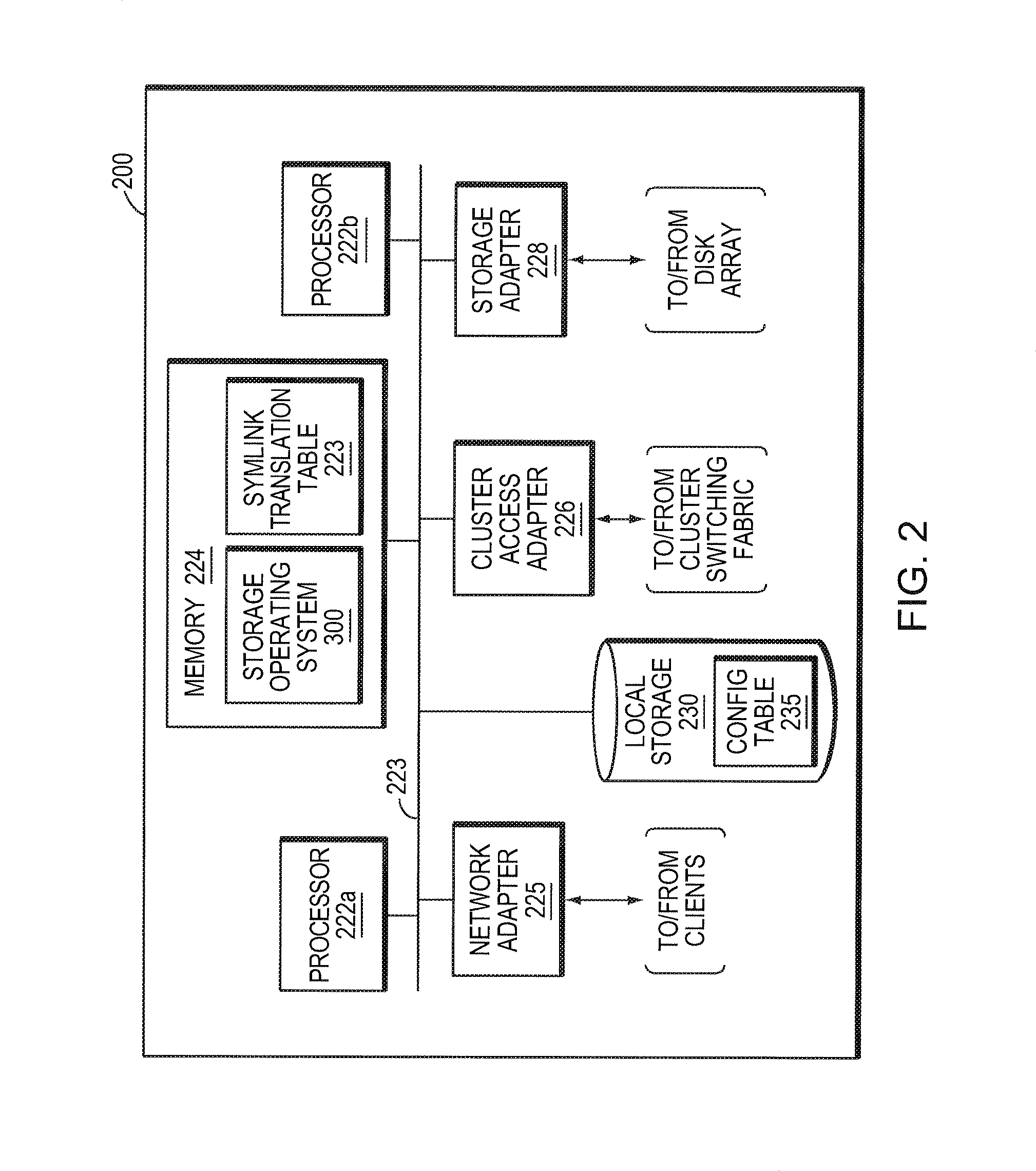
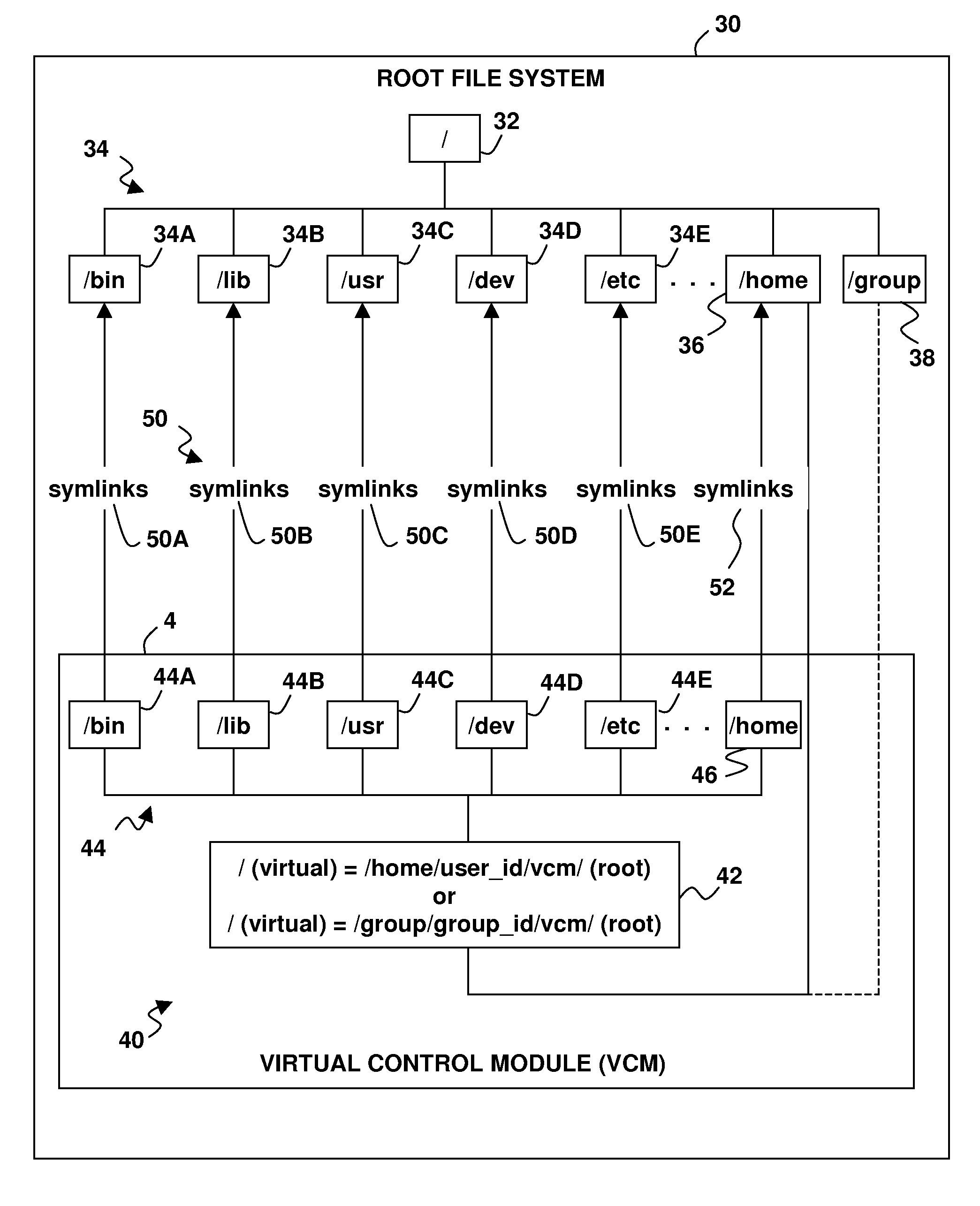
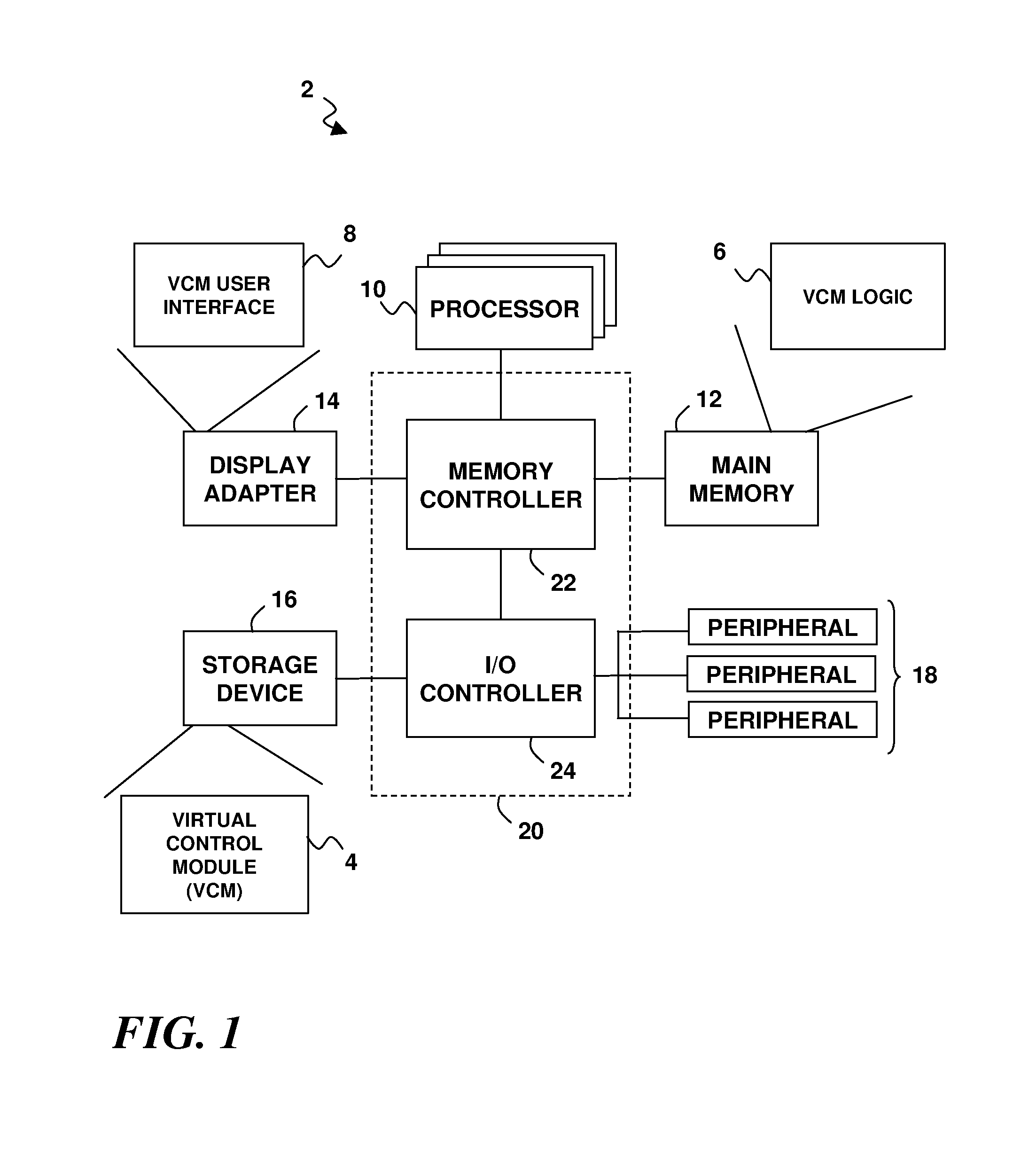
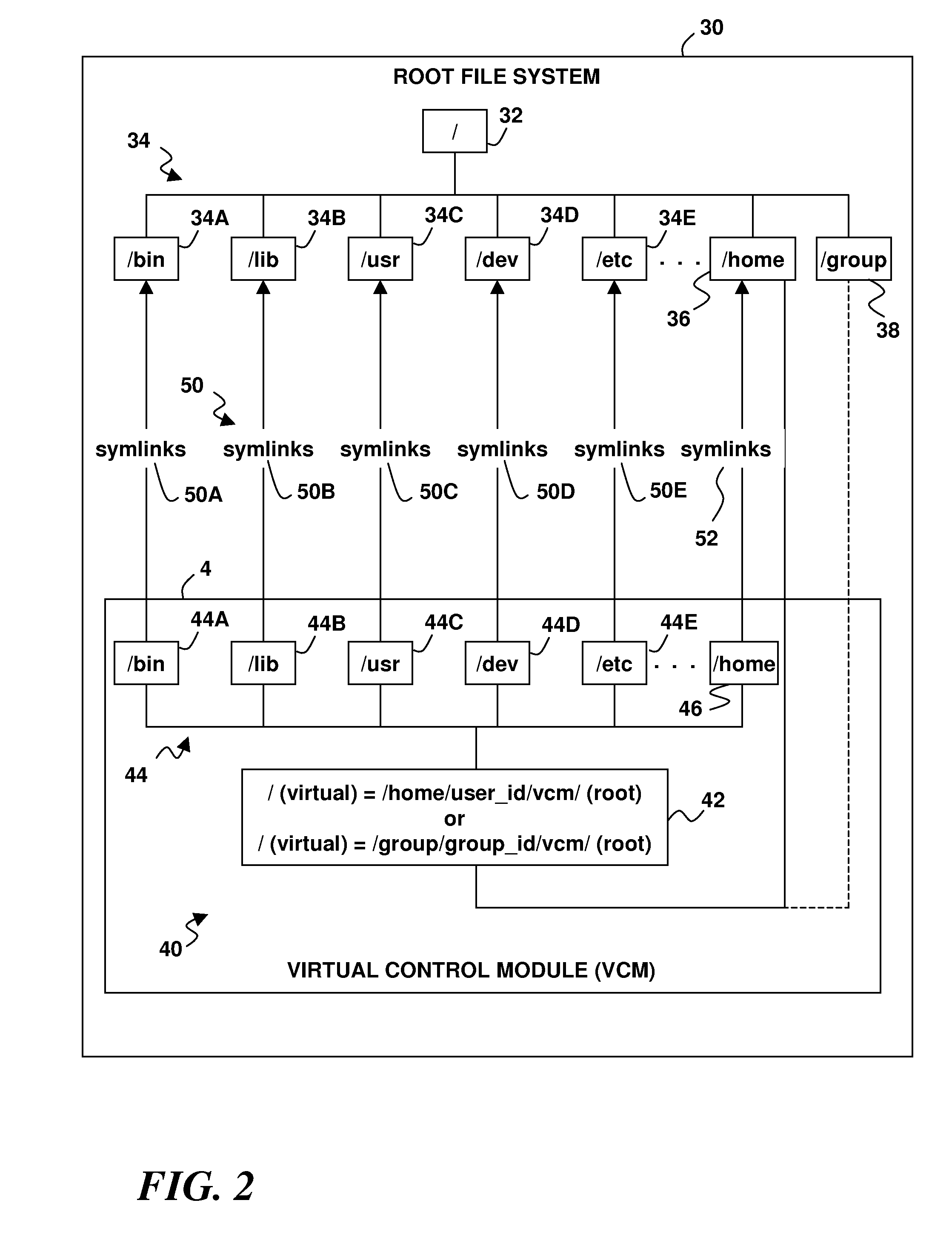
A virtual system environment in a computing system allows non-root users to perform administrative operations normally requiring root privileges. A virtual control module has a virtual file system with virtual directories corresponding to one or more of the system directories of a root file system. Each virtual directory contains one or more symbolic links symbolically linking to one or more system files as link targets. The symbolic links have non-root permissions that allow the non-root users to perform administrative operations in the virtual control module that delete, change or replace the symbolic links. A capability is provided to resolve the symbolic links within the virtual control module to allow the non-root users to execute the link targets via the symbolic links. One or more non-root users may be placed in the virtual control module by setting their apparent root directory to a root directory of the virtual file system.
Owner:IBM CORP
A novel media file access and storage solution for multi-workstation/multi-platform non-linear video editing systems
InactiveCN102132269AElectronic editing digitised analogue information signalsRecord information storageMulti platformSymbolic link
A novel system, method and computer program product for accessing digital media files stored in a media storage device via a server device in communication with the media storage device. The method provides a Project Sharing feature for enabling collaborative sharing of Non Linear Editing (NLE) Projects, even though the NLE application might normally define and save Projects as a single monolithic project file. The system and method provides a file directory and symlink scheme that allows ALL editors who are ''members'' of a Project Space to see all the bins created by all other editors, but controlling the WRITE ACCESS to the bins according to whose ''User Folder'' the bins resided in, i.e., a user-based locking scheme is provided to allow control over who can and cannot write to a file. The system and method further treats a single monolithic project file as a collection of smaller Project files, the permissions and ownerships of which could each be controlled independently.
Owner:安德鲁·利布曼
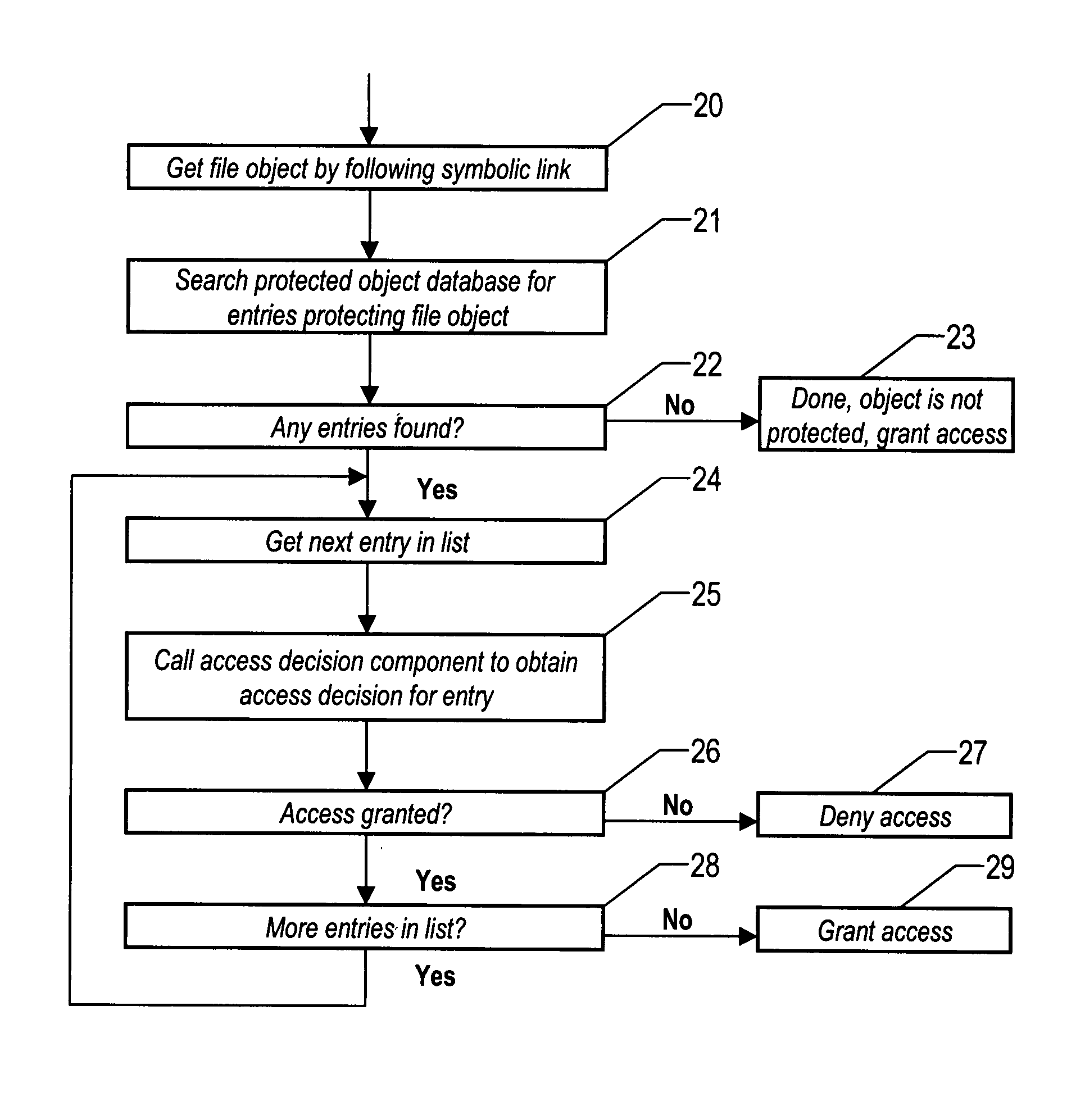
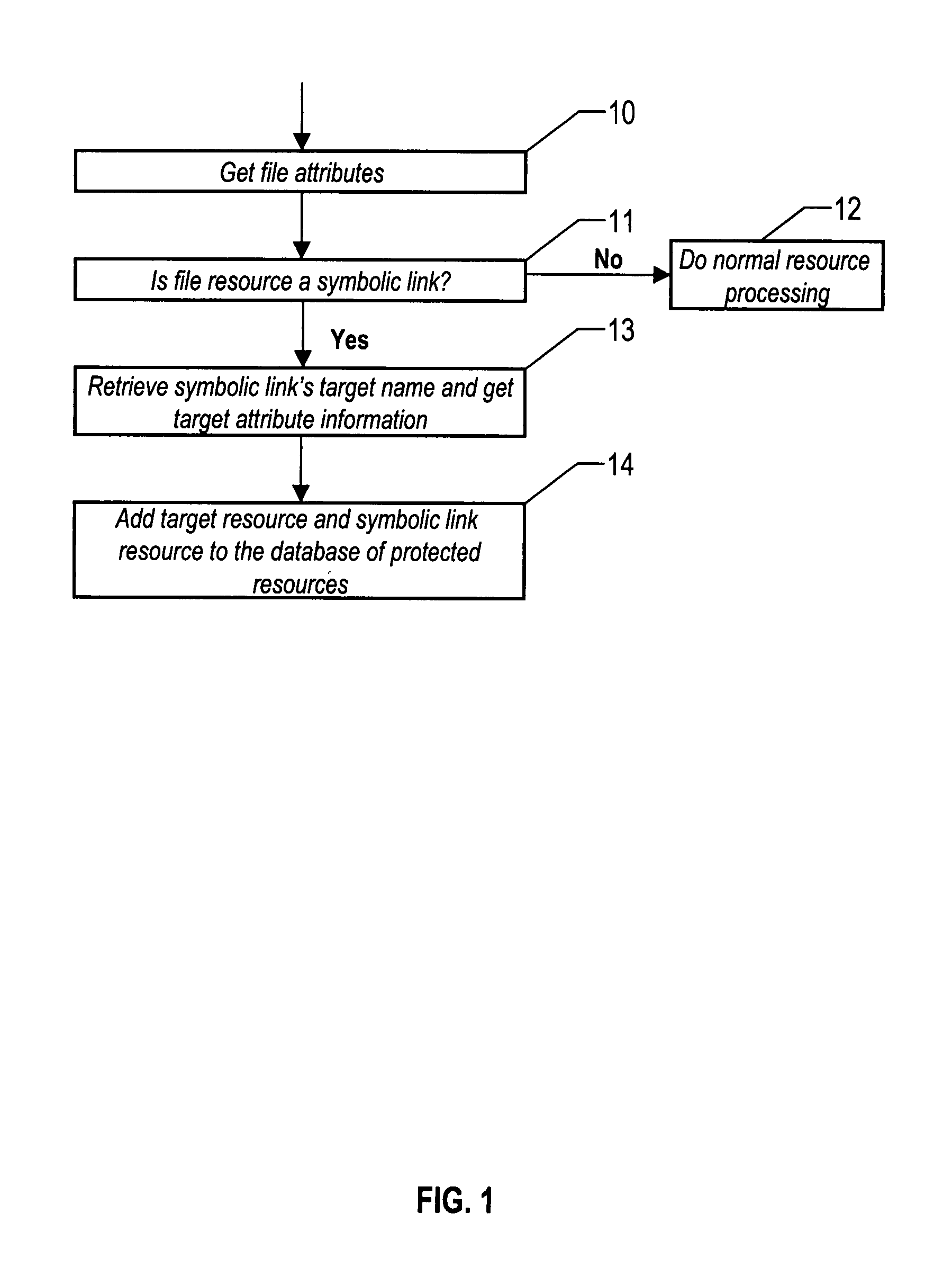
Method for adding external security to file system resources through symbolic link references
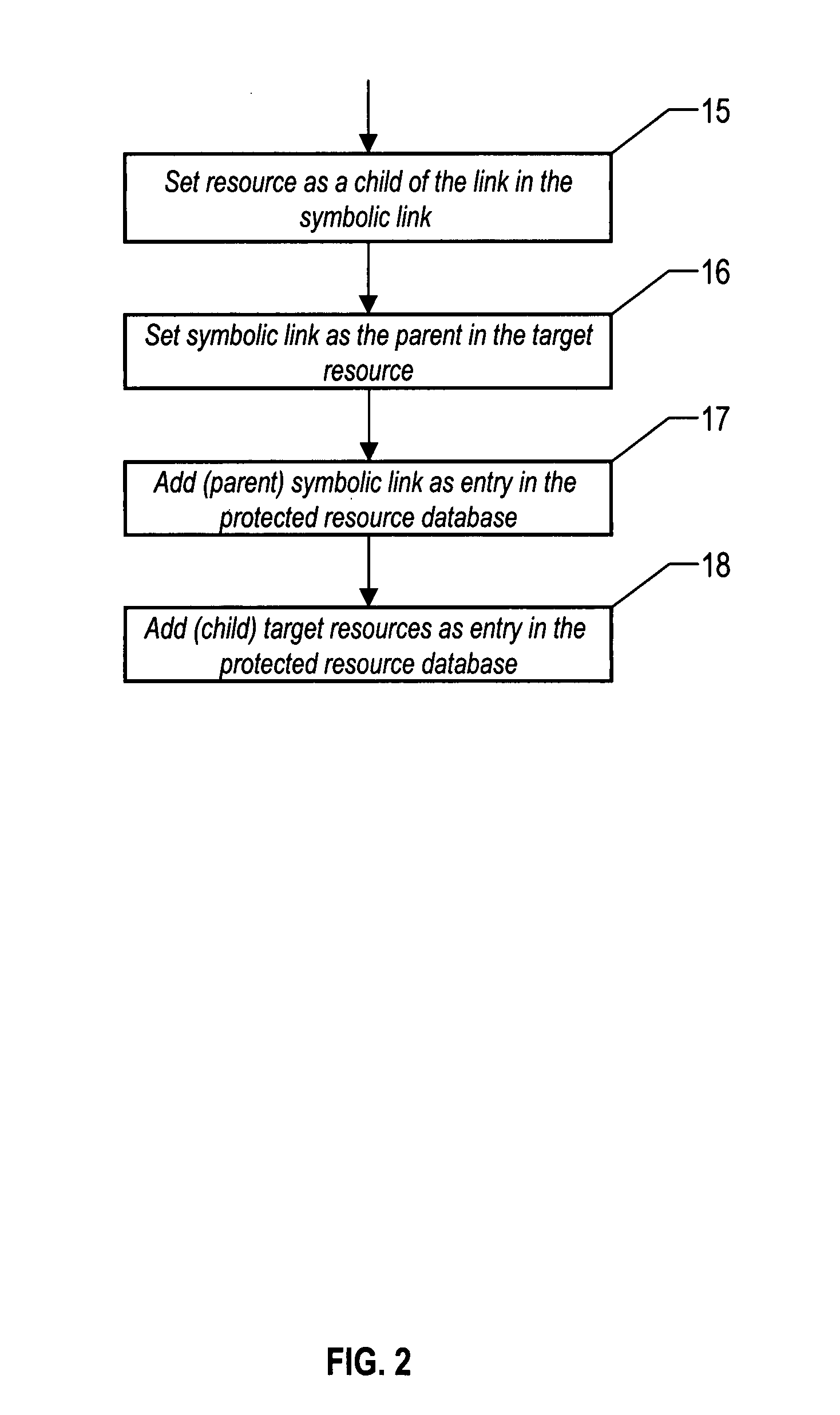
ActiveUS7260718B2Data processing applicationsDigital data processing detailsSymbolic linkResource based
The method of the invention assumes there is a security manager and mechanism present for defining, attaching, and evaluating external authorization policy to file resources based on the file's path name. In this invention, protected symbolic links and the resources that the link points to are stored in a protected object database. When a system access attempt occurs, the file attribute is extracted from the file used in the access. The file attribute is then used to search the protected object database. If a matching system resource is found, and that resource is protected but does not have independent security policy on it, then the resource will have the security policy of a symbolic link that points to it. In this case, the security of each protected symbolic link pointing to the system resource has to grant access in order for allowance of the access attempt. This approach insures that the most restrictive outcome prevails.
Owner:TREND MICRO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com