Software vulnerability detection method based on simulation attack
A technology for simulating attacks and detection methods, applied in the field of software vulnerability detection, which can solve problems such as vulnerabilities that cannot be exploited, false positives, and lack of attack factors.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
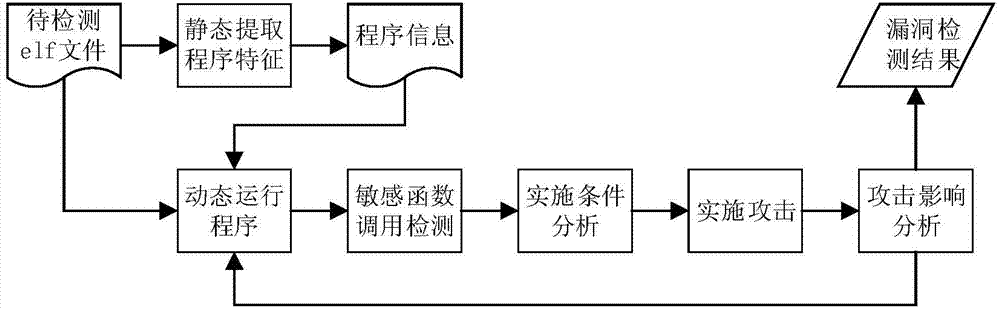
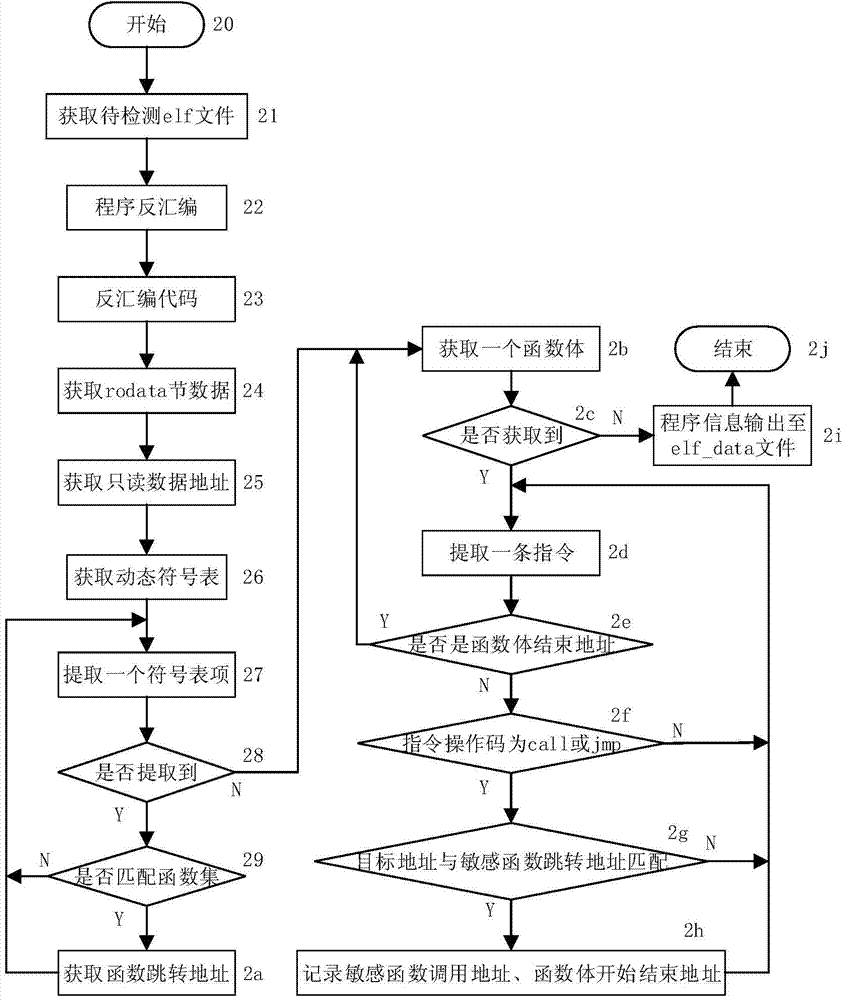
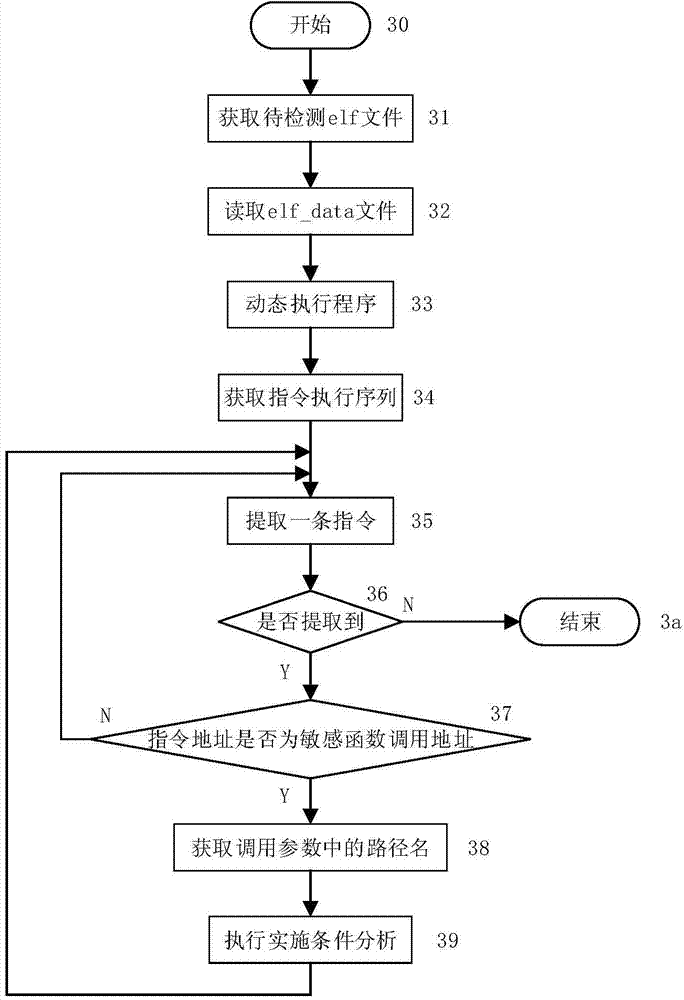
[0036] Figure 1 shows the overall structure and workflow of this method, which is divided into two stages: static analysis and dynamic detection. In the static analysis stage, the static disassembly tool IDA Pro is used to disassemble the elf file to be detected to obtain the disassembly code, and the program information, including function information and constant information, is obtained through the analysis of the disassembly code. The program information extracted by the static analysis is stored in the elf_data file for use in the dynamic detection phase. In the dynamic detection stage, use the dynamic instrumentation platform PIN to run the program to be detected, and read the program information in the elf_data file for the detection of sensitive function calls and implementation conditions. The sensitive function information in the program information includes the sensitive function call address, and the sensitive function call detection mainly detects the match betwee...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com